Message-IDs helpful for forensic analysis?
|
|
|
- Francine Hill
- 10 years ago
- Views:
Transcription
1 Message-IDs helpful for forensic analysis? Satheesaan Pasupatheeswaran School of Computer and Information Science Edith Cowan University Perth, Western Australia Abstract Finding the source of spoofed is a challenging task for forensic investigators. Header of an has several fields that can be used for investigation. An investigator can easily understand the evidences embedded within most of the header fields of an , except the message-id field. Therefore, there is a need to understand how message-ids are constructed and what useful information can be recovered from them. The immediate aim of the analysis is to find the message-id construction mechanism of Sendmail mail transfer agent (MTA) version 8. and how the findings can be used successfully in forensic analysis. Source code of the Sendmail MTA is made use of during analysis. This analysis will uncover several information that will help to find source and validate other header fields also. The drawbacks in message-id based forensic analysis also discussed here. Keywords header, message-id, msgid, sendmail forensics, forensics, header analysis, network forensics. INTRODUCTION An electronic mail consists of two parts, the header and the body. The header part carries information that is needed for routing, subject line and time stamps while the body contains the actual message/data of an . The header and the body are separated by a blank line. The header contains several mandatory and optional fields (Resnick, ). In order to uniquely identify each all mail transfer agents (MTAs) use some sort of unique identifier. This identifier is referred to as Message-ID. Message-ID field is inserted into a header either by mail user agent (MUA) or the first MTA. Even though the Message-ID is optional as per RF8 it recommends using it. Sendmail is one of MTA that handles delivery and relaying process. Sendmail uses message-id for tracing s and for logging process ids (Costales, Janse, Abmann, & Shapiro, 7, p). Sendmail recommends including message-id in s and also it recommends setting relevant macros in its configuration file in order to implement compulsory checking of message-ids (Costales et al, 7, p77). Unlike spoofing other fields in the header, spoofing message-id needs special knowledge. Only technical envy spammers can spoof the message-id cleverly. So deep analysis on message-ids may reveal some sort of information that will open a window to trace the source of an . Also the message-id will help to find a particular log entry within a log file of server. Like conventional mail service, when is routed from source to destination all intermediate relay servers (SMTP) insert their stamp at the beginning of the header. This stamping procedure helps to trace the if such a demand arises. The stamp consists of three fields known as From, SMTP ID, and For (Klensin, ). Figure shows an header that passed through several MTAs. Each MTA inserted a unique-id in the header of (Al-Zarouni, ). There are several IDs in the header field of an that may help to trace the source of the but this discussion is limited to sendmail message-id only. Analyzing intermediate SMTP IDs is beyond the scope of the discussion. However this paper briefly discusses intermediate SMTP-Ids also.
2 Received: from search.org ([..8.]) by sgiserver.search.org with SMTP (Microsoft Exchange Internet Mail Service Version...) id K9HBBC; Mon, May 9:7: -7 Received: from web.mail.yahoo.com ([...9]) by SEARCH.ORG with SMTP (IPAD.) id 797; Mon, May 8:7: -8 Message-ID: Received: from [..8.8] by web.mail.yahoo.com; Mon, May 9:: PDT Date: Mon, May 9:: -7 (PDT) From: Subject: check out this header To: Figure: header with several identifiers (ID) Message-ID RFC 8 states that each must have a globally unique identifier. This must be included into the header of an . The RFC 8 also defines the syntax of message-id. It should be like a legitimate address and it must be included within a pair of angle brackets. According to RFC 8, message-id can appear in three header fields. They are message-id header, in-reply-to header and references header. But message-id of the present must be included against the message-id header. Sendmail Message-ID Sendmail Message-ID is formatted with two parts and they are connected sign. It looks like a legitimate address. Right hand side (RHS) of sign is a fully qualified domain name (FQDN) and left hand side (LHS) of sign has two parts separated by.. The LHS part is created with date, time, process id and a few random numbers. Shown below is a sample message-id. Message-ID: <[email protected]> Message-ID is always included within a pair of angle brackets. FQDN makes the MTA globally unique. The date and time with the combination of process id and special random numbers make the message unique in a particular MTA. This combination makes message-ids globally unique. Figure shows sample sendmail header field (Costales et al, 7, p7). Message-id is typed in blue bolded font. From [email protected] Fri Dec 8:: 8 Received: (from you@localhost) by Here.US.EDU (8..7/8..7) id d8bilug8 for you; Fri, Dec 7 8:: - (MDT) Date: Fri, Aug 8 8:: From: [email protected] (Your Full Name) Message-Id: msgid=<[email protected]> Subject: a test note To: you This blank line separates body and header part. Body part of starts here. Header Body Figure: Sample sendmail structure
3 MESSAGE-ID GENERATION Sendmail message-id is defined in the following format (Costales et al., 7, p77). Message-id: E.g.: Following paragraphs discuss each part of message-id. $t $t macro is a current UTC date and time. This is formatted in yyyymmddhhmm. It consists of decimal values. In the above e.g. the $t part is 887. If it is decoded the final results will be 8-8- :7. That means the is handed over to delivery or delivered at :7 on -8-8 UTC (Sendmail, 7). $i $i is referred as a queue id. It is generated with a special algorithm. Queue id has three different formats with respect to sendmail versions. Queue id versions are categorised as before V8., starting with V8. and starting with V8.. Format of queue-id with respect to sendmail versions are given below (Costales et al., 7). Before V8. AApid From V8. houraapid From V8. YMDhmsSEQpid Following paragraphs will present a brief description about components AA and hour and discusses sendmail V8. in detail. AA AA is a combination of English alphabet and other characters. RHS clocks from A-Z ( characters) and LHS clocks from A- ~ ( characters) until it generates a unique-id. This provides more than combinations (Costales et al., 7, p97). hour AA AB AZ ~Y. So on....so on... ~Z failure So on... This maps hour clock to uppercase alphabet. The time starts at midnight and midnight is mapped as A. Then o clock is B and so on (Costales et al., 7, p97).
4 Sendmail V8. The message ID of V8. consists of three parts. The below example clearly indicates each part (Sendmail, 7). In order to make it more understandable each group of components are named as section x where x=,,, within brackets directly below each description. E.g. m7dckvem987 Year/month/date Process ID (Section) (Section) Hour/Min/Sec (UTC) Sequence number (Section) (Section) The first eight characters can be of any combination from the characters given in table (Costales et al., 7, p97). The last digits are process id. Decimal Numbers Mapping character A B C D E F G H I J K L M N O P Q R S T U V W X Y Z b a b c d e f g h i j k l m n o p q r s t u v x y z table Table: Mapping Section This part is current UTC time. Number of years is calculated from 9 and then is divided by. The reminder is mapped to its relevant single character value (Costales et al., 7, p97). See below example Formula: Reminder (R) = (Current year- 9) % Reminder = (8-9) % = 8 Map 8 in table m
5 Months January through December is numbered from to. Therefore number 7 must be August. Date is represented by D. From the map table it is th. Hence the encoded year, month and date is Section This is current UTC time. This is ordered as hour, minute and seconds. This is coded as hour, minute modulo and seconds modulo (Sendmail, 7). Reverse mapping of each letter will decode the originating UTC time of the message. C, K, V. So the is originated or submitted for delivery at :: UTC. Section This is referred to as sequence number. These two are generated from a random number. Right hand side number is quotient and left hand side is reminder (modulo) of a random number. Seed of the random number is created with dynamic unique numbers in order to make the best possible random number. The time period since epoch to current time is calculated in seconds and microseconds. Then the total number of seconds, microseconds and process id is summed up. This sum is used as seed for the random number generator Figure shows the sequence number generation process (Sendmail, 7). F (u, us, PID) Random Number Generator Creates unique Sequence numbers per second per process Modulo by Quotient LHS_Seq Reminder RHS_Seq Where F (u, us, pid) = seconds (since epoch) + microseconds+ Process-ID Figure: Sequence numbers generator Section This is a digit process identifier (PID or Process-ID). This process ID is relevant to the process that attempted to deliver the (Hunt, ). Sendmail tries to make Process-ID unique for each queuing process (Costales et al., 7). $j This macro represents the fully qualified domain name (FQDN). This part starts with local host name followed by a dot and other parts of domain information (Costales et al., 7). Domain names are globally unique. In our previous example the $j part was Here.US.EDU. Local host name is Here and the local domain name is US.EDU. TRACING In Message-ID generation section we found that the factors used to construct message-id themselves carried important information that can be used to trace source of an . The following paragraphs discuss how this will help trace the source of an message.
6 $j: Fully qualified domain name FQDN contains local host name, from where the was originated or the first sendmail MTA, and other domain information. In our previous example Here.US.EDU the first part, preceding the first dot is the local host or the first MTA server name. Right side of the first dot is other domain information. Once domain name is found then domain s point of contact and other domain registration details can be found with readily available tools (Nelson, Philips, Enfinger, & Steuart, 8, p8). Some of such web based tools are and a command line tool is whois (Mulligan, 999, p). Once the domain administrator is identified then forensic analysers can get her/his help to track the source with messageid. $t: Date and time Time is a critical factor in forensic investigation. The time part of message-id provides when the message was handed over for delivery. This time information will help to solve some of the problem stated below. Dynamic IP addressing In order to conserve IP address space most ISPs provide dynamic IP addresses. During investigation if IP address of the sender is found to be dynamic then the time information will help to search in the billing server who used this particular IP address at the specified time. This will help to identify the sender. Billing servers contain session information such as period of login and allocated IP address for billing purposes. If sender used company s SMTP server then both SMTP log and DHCP log must be collected for analysis (Al- Zarouni, ). Remember the time retrieved from message-id is UTC. So it is important to find out actual zone time. This can be done in several ways. Country of origin of can be found from domain name as discussed in section $j. Once the country is known then time difference can be determined from several timing servers. Even this will help to verify the originating date and time of the . The calculated time will help forensic analysers to check whether the source MTA is in sync with any standard time reference or not. -server log file Sendmail records all SMTP communication between servers in mail.log file. This log file contains date, host, process-id, queue-id and the log information. This log file maintains queue-id as a unique-id to distinguish each record (Costales et al., 7, p7). By analysing the log file of source MTA with either message-id or queueid, the expected record can be found. Time stamp and hostname/ip address found in the record can be verified with suspected header so as to confirm the sender. Below figure shows a typical sendmail log file. Message-ID Queue-ID Figure: Typical sendmail log file The source MTA may be maintained by ISP or it may belong to a company. Forensic analysers will require legal authorisation to access the log files. In-Reply-To header In-reply-to header holds message-id of original message to which it is replying to. Also this may include comma separated several message-ids, as a reply to several s (Costales et al., 7, p8). Checking this header will help to find other suspicious s.
7 In-Reply-To: Figure: An in-reply-to header with a few message-ids References header In case of threaded s, continuous correspondence between parties, the reference header holds all messageids from the first to the last (Loshin,, p 9). Supposing the message-id of the interested is spoofed the other message-ids will help to trace the source. Figure 7 shows reference header with two message-ids. Masquerade options Sendmail and even some of the other MTAs like Microsoft exchange server support an option called masquerade. This option is used to hide the local host behind a local domain name or central server. It usually rewrites sender address field with local domain name. Then any outgoing will not have FQDN or $j. It might be tricky when tracing with source address domain name. But this option does not affect FQDN of message-id (Costales et al., 7, p). In most of the situations analysing a message-id will help to directly locate the local host or the mail server which handled the initial delivery process. Figure shows an header with masqueraded source address. Return-Path: <[email protected]> Received: from smtp.unsw.edu.au ([7...]) by localhost (snarl.comms.unsw.edu.au [7...]) (amavisd-new, port ) with ESMTP id jnhwsbjmdj7 for <[email protected]>; Mon, 8 May 7 ::9 + (EST) Received: from central-eng.eng.unsw.edu.au (central-eng.eng.unsw.edu.au [9.9..]) by smtp.unsw.edu.au (8../8..) with ESMTP id lsq9gm; Mon, 8 May 7 ::9 + (EST) Date: Mon, 8 May 7 ::7 + Local host or Local mail server Message-ID: <[email protected]> In-Reply-To: <C879D.BDAC%[email protected]> References: <[email protected]> msgid <C879D.BDAC%[email protected]> Reference header with multiple From: [email protected] To: <[email protected]> Masquerade with local domain name Figure : Reference and masquerade header In the above figure From: field has local domain name unsw.edu.au but Message-id field and Received field have the local server that handled the first delivery process. If investigators can provide the server details that handled the delivery process, it will help to speed up the process. Consequently it will reduce the burden of log file analysis. Intermediate SMTP-ID As s go through intermediate MTAs (hops) each MTA insert their unique-id (SMTP-ID) on the header. If it is necessary to analyse intermediate server log file this unique-id is important. Knowledge about
8 intermediate smtp-id also will help to identify any fake smtp-id. Intermediate sendmail servers create a queue id as stated in section $i and use it as smtp-id (Costales et al., 7, p8). Intermediate mail servers stamp starts with Received: header. Figure shows an that is routed through three sendmail MTAs. Each MTA insert their stamp with smtp-id. This smtp-id can be used in log file analysis. Return-Path: <[email protected]> Authentication-Results: mta79.mail.mud.yahoo.com from=slt.com.lk; domainkeys=neutral (no sig) Received: from (EHLO xmail.slt.com.lk) (..9.99) by mta79.mail.mud.yahoo.com with SMTP; Fri, Jun ::8-7 Received: from smtp.slt.com.lk (smtp.slt.com.lk [7...]) by xmail.slt.com.lk (8../8..) with ESMTP id kn9lmio8; Fri, Jun ::8 + Received: from slt.com.lk (pop.slt.com.lk [7...]) by smtp.slt.com.lk (8../8..) with ESMTP id knkrsua9; Fri, Jun ::8 - (GMT) Received: from slt.com.lk (slt.com.lk [7...]) by slt.com.lk (8../8..) with ESMTP id kn8rfwp8; Fri, Jun :: + From: <[email protected]> To: [email protected], Subject: Fw: you've got to see this Date: Fri, Jun :: +7 Message-Id: <[email protected]> In-Reply-To: <7c99f$78ff9e$79ac@RAIN> Figure7: Intermediate SMTP-ID The pattern of smtp-id and reverse mapping of smtp-id proves that smtp-id is a queue-id. FAKE MESSAGE-ID Just like spoofing other header fields of , spoofing message-id is also possible. By observing a few headers where the first MTA is sendmail, it is possible to make a message-id that look legitimate. E.g.: [email protected] LHS of the dot is simply date and time and RHS of the dot contains characters, first 8 characters are a combination of numbers and English alphabets and other are just numbers. So before using message-id for forensic analysis the message-id must be verified for its validity. Message-id verification Knowledge of sendmail message-id construction will help to verify the message-id. With the help of mapping table, $t part can be verified with first characters of $i. The sequence number and process id are dynamically created characters so verifying them is difficult. Spam identification Spam mail filters check for empty message-id or illegal message-id pattern only. The message-id is an optional field and it also can be spoofed. So message-id cannot be a reliable spam indicator( Allman, Assmann, & Shapiro, n.d). Spam mail senders harvest addresses through several ways one such method is scanning USENET articles ( Costale & Flynt, ). If any received from known source is suspected to be sent by spammers, the suspected can be verified by comparing message-id of the against known good message-id from the same source. However, checking message-id is not a consistent spam checking method because a good spammer can create same pattern of message-id.
9 ISSUES RELATED TO MESSAGE-IDS No Standard algorithm RFC8 standard states every should have a unique identifier and provides syntax of message-id and some suggestion to create unique identifier. However, it does not define how it should be generated. software developers use their own algorithm to generate message-ids. Forensic analyser or relevant technical advisor must be well informed on the different vendor message ids as he/she might come across different types of message-ids. This drawback makes it difficult to make a tool for checking validity of message-ids. Sendmail checks messageid header, if it is blank it will insert a new message-id otherwise it will not alter the available message-id (Costales et al., 7, p8). This vulnerability aids the successful transmission of s with spoofed message-ids. Spoofed message-id will compromise forensic analysis results. Open source and closed source In case of open source softwares it is possible to find out the construction mechanism of message-ids but it will be difficult to determine the message-id construction mechanism in closed source softwares. Identifying Source MTA There are several MTAs in use. In order to select the suitable analysis procedure investigator must know the source MTA. If the source MTA is known it will help to verify the message-id against fake ids. Sendmail will not generate new message-id if the already has a message-id. Some MUA also generate message-ids (Costales et al., 7, p9). Even the first MTA is a sendmail; the message-id might not be sendmail compatible. In this case first smtp-id will help log analysis. This area needs the special attention of researchers. Versions The message id algorithm of sendmail has already changed thrice (Costales et al., 7, p87). Therefore for analysis, continuous research and updates on message-ids is important. Determining the version of the sendmail is also necessary before start of message-id analysis. Host time MTA host time must be synchronized with reliable time reference. Since forensic investigation is time sensitive, if there is any difference it time it may invalidate the case in court or it may be very difficult to prove in court. There are some tools, such as NTP, STIME and GPS clock, that can be used to synchronise the host time (Al- Zarouni, ). Incorrect timing and time setting may cause message-id collision in the specific host itself. Spoofed message-ids Spoofing message-ids is possible and it will compromise the forensic analysis. If message-id is spoofed with an earlier valid message-id then this will change the direction of the investigation. This will create unnecessary problems and delay in the investigation. Figure8 shows an header with spoofed message-id. Return Path: <[email protected]> Received: from.9.9. (HELO..9.) (.9.9.) by mta.mail.sc.yahoo.com with SMTP; Sun, 7 Jun 7:: Received: from...7 by.9.9.; Sun, 7 Jun :: - Message-ID: <P[ Fighure8: An header with spoofed message-id from my inbox
10 Headers without message-id Some s, especially drafted for illegal activity or spam, do not have message-ids in their headers. In such circumstances message-id forensic is not applicable. Below figure shows a successfully delivered webmail without message-id. Return-Path: <[email protected]> Authentication-Results: mta.mail.mud.yahoo.com from=yahoo.com; domainkeys=neutral Received: from..8. (HELO fpyd.net) (..8.) by mta.mail.mud.yahoo.com with SMTP; Fri, Sep 8 :: -7 From: <[email protected]> To: <[email protected]> Subject: Hurry.. Buy US based medications here!..save your money! MIME-Version:. Content-Type: multipart/mixed;boundary= "----=_NextPart CA_AC88.8C8DC" Content-Length: 9 Figure9: Fake header without message-id In the above header both From and To header fields have same address. Thus it is confirmed that the is a fake. Also it does not have a message-id. International cooperation Message-ID based forensics analysis needs log file analysis. In some occasions the source server might be located in another country. To handle this type of situation investigator needs cooperation from that foreign country to carry out the analysis successfully. CONCLUSION: This discussion reveals that message-id plays an important role in forensic analysis. The global unique feature of message-id helps to distinguish each and so help in forensic analysis. Knowledge of message-id construction part will help to identify spoofed s, source host, log file analysis and time details. This paper also discussed the ways to determine fake message-ids. Beyond some of the identified weaknesses in message-id, the information that is carried by the message-id is highly important in tracing the source. This study is carried out only on sendmail message-id. However this area needs more study on other messageids that are created by different software. The key factor in message-id analysis is that the source software must be known to the investigator in order to apply suitable methods during analysis.
11 REFERENCES: Al-Zarouni, M. (). Tracing Headers. Retrieved -Sep-8, from Allman, E., Assmann, C., & Shapiro, G. N. Sendmail Installation and operation Guide. Retrieved -Sep- 8, from Costales, B., & Flynt, M. (). Sendmail Milters AGuide for Fighting Spam. NJ: Addison-Wesley. Costales, B., Janse, G., Abmann, C., & Shapiro, G. N. (7). Sendmail (th ed.). Sebastopol: O'Reilly. Hunt, C. (). Linux Sendmail Administration. Retrieved -Sep-8, from Klensin, J. (). RFC8:Simple Mail Transfer Protocol. Retrieved -Sep-8, from Loshin, P. (). Essential Standards: RFCs and Protocols Made Practical. NY: Wiley. Mulligan, G. (999). Removing the Spam: Processing and Filtering. Reading: Addison-Wesley. Nelson, B., Philips, A., Enfinger, F., & Steuart, C. (8). Guide to Computer Forensics and Investigations (rd ed.). Boston: THOMSON COURSE TECHNOLOGY. Resnick, P. (). RFC8: Internet Message Format. Retrieved -Sep-8, from Sendmail [Computer Software]. (7). Sendmail (Version V8..): Sendmail Inc. COPYRIGHT [Satheesaan Pasupatheeswaran] 8. The author/s assigns Edith Cowan University a non-exclusive license to use this document for personal use provided that the article is used in full and this copyright statement is reproduced. Such documents may be published on the World Wide Web, CD-ROM, in printed form, and on mirror sites on the World Wide Web. The authors also grant a non-exclusive license to ECU to publish this document in full in the Conference Proceedings. Any other usage is prohibited without the express permission of the authors
Email. MIME is the protocol that was devised to allow non-ascii encoded content in an email and attached files to an email.
 Email Basics: Email protocols were developed even before there was an Internet, at a time when no one was anticipating widespread use of digital graphics or even rich text format (fonts, colors, etc.),
Email Basics: Email protocols were developed even before there was an Internet, at a time when no one was anticipating widespread use of digital graphics or even rich text format (fonts, colors, etc.),
Email Management CSCU9B2 CSCU9B2 1
 Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
Email Management CSCU9B2 CSCU9B2 1 Contents Email clients choosing and using Email message header and content Emailing to lists of people In and out message management Mime attachments and HTML email SMTP,
Mail system components. Electronic Mail MRA MUA MSA MAA. David Byers
 Electronic Mail PRINCIPLES DNS ARCHITECTURES SPAM Mail system components () () David Byers MRA [email protected] IDA/ADIT/IISLAB Mail User Agent Reads and writes e-mail Writes e-mail to using (usually)
Electronic Mail PRINCIPLES DNS ARCHITECTURES SPAM Mail system components () () David Byers MRA [email protected] IDA/ADIT/IISLAB Mail User Agent Reads and writes e-mail Writes e-mail to using (usually)
SPAM UNDERSTANDING & AVOIDING
 SPAM UNDERSTANDING & AVOIDING Modified: September 28, 2006 SPAM UNDERSTANDING & AVOIDING...5 What is Spam?...6 How to avoid Spam...6 How to view message headers...8 Setting up a spam rule...10 Checking
SPAM UNDERSTANDING & AVOIDING Modified: September 28, 2006 SPAM UNDERSTANDING & AVOIDING...5 What is Spam?...6 How to avoid Spam...6 How to view message headers...8 Setting up a spam rule...10 Checking
2014-10-07. Email security
 Email security Simple Mail Transfer Protocol First defined in RFC821 (1982), later updated in RFC 2821 (2001) and most recently in RFC5321 (Oct 2008) Communication involves two hosts SMTP Client SMTP Server
Email security Simple Mail Transfer Protocol First defined in RFC821 (1982), later updated in RFC 2821 (2001) and most recently in RFC5321 (Oct 2008) Communication involves two hosts SMTP Client SMTP Server
Email. Daniel Zappala. CS 460 Computer Networking Brigham Young University
 Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
CS43: Computer Networks Email. Kevin Webb Swarthmore College September 24, 2015
 CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
Simple Mail Transfer Protocol
 Page 1 of 6 Home : Network Programming Simple Mail Transfer Protocol Contents What is SMTP? Basics of SMTP SMTP Commands Relaying of Messages Time Stamps and Return Path in Message Header Mail Exchangers
Page 1 of 6 Home : Network Programming Simple Mail Transfer Protocol Contents What is SMTP? Basics of SMTP SMTP Commands Relaying of Messages Time Stamps and Return Path in Message Header Mail Exchangers
SMTP Servers. Determine if an email message should be sent to another machine and automatically send it to that machine using SMTP.
 SMTP Servers SMTP: Simple Mail Transfer Protocol (TCP Port 25) The Simple Mail Transfer Protocol (SMTP) is an Internet standard for transferring electronic mail between computers. UNIX systems implement
SMTP Servers SMTP: Simple Mail Transfer Protocol (TCP Port 25) The Simple Mail Transfer Protocol (SMTP) is an Internet standard for transferring electronic mail between computers. UNIX systems implement
Internet Security [1] VU 184.216. Engin Kirda [email protected]
![Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at Internet Security [1] VU 184.216. Engin Kirda engin@infosys.tuwien.ac.at](/thumbs/33/15826620.jpg) Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
Internet Security [1] VU 184.216 Engin Kirda [email protected] Christopher Kruegel [email protected] Administration Challenge 2 deadline is tomorrow 177 correct solutions Challenge 4 will
CipherMail Gateway Quick Setup Guide
 CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
CIPHERMAIL EMAIL ENCRYPTION CipherMail Gateway Quick Setup Guide October 10, 2015, Rev: 9537 Copyright 2015, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Typical setups 4 2.1 Direct delivery............................
Network Services. Email SMTP, Internet Message Format. Johann Oberleitner SS 2006
 Network Services Email SMTP, Internet Message Format Johann Oberleitner SS 2006 Agenda Email SMTP Internet Message Format Email Protocols SMTP Send emails POP3/IMAPv4 Read Emails Administrate mailboxes
Network Services Email SMTP, Internet Message Format Johann Oberleitner SS 2006 Agenda Email SMTP Internet Message Format Email Protocols SMTP Send emails POP3/IMAPv4 Read Emails Administrate mailboxes
Libra Esva. Whitepaper. Glossary. How Email Really Works. Email Security Virtual Appliance. May, 2010. It's So Simple...or Is It?
 Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
Libra Esva Email Security Virtual Appliance Whitepaper May, 2010 How Email Really Works Glossary 1 2 SMTP is a protocol for sending email messages between servers. DNS (Domain Name System) is an internet
An overview of IT Security Forensics
 An overview of IT Security Forensics Manu Malek, Ph.D. Stevens Institute of Technology [email protected] www.cs.stevens.edu/~mmalek April 2008 IEEE Calif. 1 Outline Growing Threats/Attacks Need for Security
An overview of IT Security Forensics Manu Malek, Ph.D. Stevens Institute of Technology [email protected] www.cs.stevens.edu/~mmalek April 2008 IEEE Calif. 1 Outline Growing Threats/Attacks Need for Security
Internet Technologies Internet Protocols and Services
 QAFQAZ UNIVERSITY Computer Engineering Department Internet Technologies Internet Protocols and Services Dr. Abzetdin ADAMOV Chair of Computer Engineering Department [email protected] http://ce.qu.edu.az/~aadamov
QAFQAZ UNIVERSITY Computer Engineering Department Internet Technologies Internet Protocols and Services Dr. Abzetdin ADAMOV Chair of Computer Engineering Department [email protected] http://ce.qu.edu.az/~aadamov
Solution Brief FortiMail for Service Providers. Nathalie Rivat
 Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Mail agents. Introduction to Internet Mail. Message format (2) Authenticating senders
 Mail agents Introduction to Internet Mail Philip Hazel University of Cambridge MUA = Mail User Agent Interacts directly with the end user Pine, MH, Elm, mutt, mail, Eudora, Marcel, Mailstrom, Mulberry,
Mail agents Introduction to Internet Mail Philip Hazel University of Cambridge MUA = Mail User Agent Interacts directly with the end user Pine, MH, Elm, mutt, mail, Eudora, Marcel, Mailstrom, Mulberry,
sendmail Cookbook Craig Hunt O'REILLY' Beijing Cambridge Farnham Koln Paris Sebastopol Taipei Tokyo
 sendmail Cookbook Craig Hunt O'REILLY' Beijing Cambridge Farnham Koln Paris Sebastopol Taipei Tokyo Table of Contents Preface xi 1. Getting Started 1 1.1 Downloading the Latest Release 5 1.2 Installing
sendmail Cookbook Craig Hunt O'REILLY' Beijing Cambridge Farnham Koln Paris Sebastopol Taipei Tokyo Table of Contents Preface xi 1. Getting Started 1 1.1 Downloading the Latest Release 5 1.2 Installing
How To Block Ndr Spam
 How to block NDR spam Spam generates an enormous amount of traffic that is both time-consuming to handle and resource intensive. Apart from that, a large number of organizations have been victims of NDR
How to block NDR spam Spam generates an enormous amount of traffic that is both time-consuming to handle and resource intensive. Apart from that, a large number of organizations have been victims of NDR
Email Electronic Mail
 Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Cannot send Autosupport e-mail, error message: Unknown User
 Cannot send Autosupport e-mail, error message: Unknown User Symptoms Unable to send Autosupport e-mails and the following error message is reported: asup.smtp.fail http://now.netapp.com/eservice/ems?emsaction=details&eventid=200573&software=ontap&em
Cannot send Autosupport e-mail, error message: Unknown User Symptoms Unable to send Autosupport e-mails and the following error message is reported: asup.smtp.fail http://now.netapp.com/eservice/ems?emsaction=details&eventid=200573&software=ontap&em
Articles Fighting SPAM in Lotus Domino
 Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
Page 1 of 5 Articles Fighting SPAM in Lotus Domino For many e-mail administrators these days, the number one complaint from the users and managers is unsolicited emails flooding the system, commonly called
Networking Applications
 Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport Electronic Mail 1 Outline Introduction SMTP MIME Mail Access
Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport Electronic Mail 1 Outline Introduction SMTP MIME Mail Access
SMTP Best Practices, Configurations and Troubleshooting on Lotus Domino.
 SMTP Best Practices, Configurations and Troubleshooting on Lotus Domino. 9 th th June 2011 Chandra Shekhar Anumandla - Lotus Technical Support Engineer Presenter Seema Janjirkar Lotus Technical Advisor
SMTP Best Practices, Configurations and Troubleshooting on Lotus Domino. 9 th th June 2011 Chandra Shekhar Anumandla - Lotus Technical Support Engineer Presenter Seema Janjirkar Lotus Technical Advisor
Government of Canada Managed Security Service (GCMSS) Annex A-5: Statement of Work - Antispam
 Government of Canada Managed Security Service (GCMSS) Date: June 8, 2012 TABLE OF CONTENTS 1 ANTISPAM... 1 1.1 QUALITY OF SERVICE...1 1.2 DETECTION AND RESPONSE...1 1.3 MESSAGE HANDLING...2 1.4 CONFIGURATION...2
Government of Canada Managed Security Service (GCMSS) Date: June 8, 2012 TABLE OF CONTENTS 1 ANTISPAM... 1 1.1 QUALITY OF SERVICE...1 1.2 DETECTION AND RESPONSE...1 1.3 MESSAGE HANDLING...2 1.4 CONFIGURATION...2
Trustwave SEG Cloud Customer Guide
 Trustwave SEG Cloud Customer Guide Legal Notice Copyright 2015 Trustwave Holdings, Inc. All rights reserved. This document is protected by copyright and any distribution, reproduction, copying, or decompilation
Trustwave SEG Cloud Customer Guide Legal Notice Copyright 2015 Trustwave Holdings, Inc. All rights reserved. This document is protected by copyright and any distribution, reproduction, copying, or decompilation
Introduction. -- some basic concepts and terminology -- examples for attacks on protocols -- main network security services
 Introduction -- some basic concepts and terminology -- examples for attacks on protocols -- main network security services (c) Levente Buttyán ([email protected]) Attack, threat, and vulnerability security
Introduction -- some basic concepts and terminology -- examples for attacks on protocols -- main network security services (c) Levente Buttyán ([email protected]) Attack, threat, and vulnerability security
CS 164 Winter 2009 Term Project Writing an SMTP server and an SMTP client (Receiver-SMTP and Sender-SMTP) Due & Demo Date (Friday, March 13th)
 CS 164 Winter 2009 Term Project Writing an SMTP server and an SMTP client (Receiver-SMTP and Sender-SMTP) Due & Demo Date (Friday, March 13th) YOUR ASSIGNMENT Your assignment is to write an SMTP (Simple
CS 164 Winter 2009 Term Project Writing an SMTP server and an SMTP client (Receiver-SMTP and Sender-SMTP) Due & Demo Date (Friday, March 13th) YOUR ASSIGNMENT Your assignment is to write an SMTP (Simple
Serial Deployment Quick Start Guide
 PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
AXIGEN Mail Server. Quick Installation and Configuration Guide. Product version: 6.1 Document version: 1.0
 AXIGEN Mail Server Quick Installation and Configuration Guide Product version: 6.1 Document version: 1.0 Last Updated on: May 28, 2008 Chapter 1: Introduction... 3 Welcome... 3 Purpose of this document...
AXIGEN Mail Server Quick Installation and Configuration Guide Product version: 6.1 Document version: 1.0 Last Updated on: May 28, 2008 Chapter 1: Introduction... 3 Welcome... 3 Purpose of this document...
How to make the Emails you Send from Outlook 2010 appear to Originate from different Email Addresses
 How to make the Emails you Send from Outlook 2010 appear to Originate from different Email Addresses If you only use a single email address to send out all your business and personal emails then you're
How to make the Emails you Send from Outlook 2010 appear to Originate from different Email Addresses If you only use a single email address to send out all your business and personal emails then you're
Introduction... 2. Configuration & Spam Detection... 2. WinWare Webmail... 3. Email Accounts... 3. Email Account Notes... 4. Definitions...
 Page 1 Table of Contents Introduction... 2 Configuration & Spam Detection... 2 WinWare Webmail... 3 Email Accounts... 3 Email Account Notes... 4 Definitions... 5 Sender Policy Framework (SPF)... 5 Email
Page 1 Table of Contents Introduction... 2 Configuration & Spam Detection... 2 WinWare Webmail... 3 Email Accounts... 3 Email Account Notes... 4 Definitions... 5 Sender Policy Framework (SPF)... 5 Email
Workflow Configuration on R12/R11. High Level Steps. SENDMAIL configuration mostly done by System Administrator Workflow configuration for R12
 Workflow Configuration on R12/R11 High Level Steps SENDMAIL configuration mostly done by System Administrator Workflow configuration for R12 SENDMAIL Configuration tested on RedHat 4 update 5 -------------------------------------------------------------------
Workflow Configuration on R12/R11 High Level Steps SENDMAIL configuration mostly done by System Administrator Workflow configuration for R12 SENDMAIL Configuration tested on RedHat 4 update 5 -------------------------------------------------------------------
Exim4U. Email Server Solution For Unix And Linux Systems
 Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
Email Server Solution For Unix And Linux Systems General Overview, Feature Comparison and Screen Shots Exim4U Email Server Solution For Unix And Linux Systems Version 2.x.x October 12, 2012 Copyright 2009
To install the SMTP service:
 To install the SMTP service: From the Start menu, click Control Panel. 2. Double-click Add or Remove Programs. 3. From the left pane, click Add/Remove Windows Components. 4. From the Components list, click
To install the SMTP service: From the Start menu, click Control Panel. 2. Double-click Add or Remove Programs. 3. From the left pane, click Add/Remove Windows Components. 4. From the Components list, click
MailEnable Web Mail End User Manual V 2.x
 MailEnable Web Mail End User Manual V 2.x MailEnable Messaging Services for Microsoft Windows NT/2000/2003 MailEnable Pty. Ltd. 486 Neerim Road Murrumbeena VIC 3163 Australia t: +61 3 9569 0772 f: +61
MailEnable Web Mail End User Manual V 2.x MailEnable Messaging Services for Microsoft Windows NT/2000/2003 MailEnable Pty. Ltd. 486 Neerim Road Murrumbeena VIC 3163 Australia t: +61 3 9569 0772 f: +61
SMTP Status Codes & SMTP Error Codes Reference
 & SMTP Error Codes Reference There comes a time in the life of a Computer Consultant where, one day, he/she will have to deal with email server problems. It is inevitable. Sometimes these problems will
& SMTP Error Codes Reference There comes a time in the life of a Computer Consultant where, one day, he/she will have to deal with email server problems. It is inevitable. Sometimes these problems will
9236245 Issue 2EN. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
Technical Note. ISP Protection against BlackListing. FORTIMAIL Deployment for Outbound Spam Filtering. Rev 2.2
 Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
Technical Note ISP Protection against BlackListing FORTIMAIL Deployment for Outbound Spam Filtering Rev 2.2 April 14, 2009 Table of Contents 1 Objective IP address protection... 3 1.1 Context... 3 1.2
ModusMail Software Instructions.
 ModusMail Software Instructions. Table of Contents Basic Quarantine Report Information. 2 Starting A WebMail Session. 3 WebMail Interface. 4 WebMail Setting overview (See Settings Interface).. 5 Account
ModusMail Software Instructions. Table of Contents Basic Quarantine Report Information. 2 Starting A WebMail Session. 3 WebMail Interface. 4 WebMail Setting overview (See Settings Interface).. 5 Account
How To Configure Forefront Threat Management Gateway (Forefront) For An Email Server
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
A New Approach to Enhance E-mail Performance Through SMTP Protocol
 IJCSNS International Journal of Computer Science and Network Security, VOL.8 No.4, April 2008 299 A New Approach to Enhance E-mail Performance Through SMTP Protocol Hussein A.Al bazar,sureswaran Ramadass,
IJCSNS International Journal of Computer Science and Network Security, VOL.8 No.4, April 2008 299 A New Approach to Enhance E-mail Performance Through SMTP Protocol Hussein A.Al bazar,sureswaran Ramadass,
SECURING INFORMATION SYSTEMS
 SECURING INFORMATION SYSTEMS (November 9, 2015) BUS3500 - Abdou Illia - Fall 2015 1 LEARNING GOALS Understand security attacks preps Discuss the major threats to information systems. Discuss protection
SECURING INFORMATION SYSTEMS (November 9, 2015) BUS3500 - Abdou Illia - Fall 2015 1 LEARNING GOALS Understand security attacks preps Discuss the major threats to information systems. Discuss protection
DKIM last chance for mail service? TFMC2 01/2006
 DKIM last chance for mail service? TFMC2 01/2006 Mail service status More and more spam, fishing, spoofing, virus More and more energy in spam fighting More and more messages lost because : Imperfect automatic
DKIM last chance for mail service? TFMC2 01/2006 Mail service status More and more spam, fishing, spoofing, virus More and more energy in spam fighting More and more messages lost because : Imperfect automatic
TREND MICRO. InterScan VirusWall 6. SMTP Configuration Guide. Integrated virus and spam protection for your Internet gateway.
 TM TREND MICRO TM TM InterScan VirusWall 6 Integrated virus and spam protection for your Internet gateway for Linux TM SMTP Configuration Guide Trend Micro Incorporated reserves the right to make changes
TM TREND MICRO TM TM InterScan VirusWall 6 Integrated virus and spam protection for your Internet gateway for Linux TM SMTP Configuration Guide Trend Micro Incorporated reserves the right to make changes
How To Upgrade To Symantec Mail Security Appliance 7.5.5
 Release notes Information Foundation 2007 Symantec Mail Security Appliance 7.5 Copyright 1999-2007 Symantec Corporation. All rights reserved. Before installing or upgrading: Migration issues If you are
Release notes Information Foundation 2007 Symantec Mail Security Appliance 7.5 Copyright 1999-2007 Symantec Corporation. All rights reserved. Before installing or upgrading: Migration issues If you are
Cre-X-Mice Database. User guide
 Cre-X-Mice Database User guide Table of Contents Table of Figure... ii Introduction... 1 Searching the Database... 1 Quick Search Mode... 1 Advanced Search... 1 Viewing Search Results... 2 Registration...
Cre-X-Mice Database User guide Table of Contents Table of Figure... ii Introduction... 1 Searching the Database... 1 Quick Search Mode... 1 Advanced Search... 1 Viewing Search Results... 2 Registration...
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Malicious Email Mitigation Strategy Guide
 CYBER SECURITY OPERATIONS CENTRE Malicious Email Mitigation Strategy Guide Introduction (UPDATED) SEPTEMBER 2012 1. Socially engineered emails containing malicious attachments and embedded links are commonly
CYBER SECURITY OPERATIONS CENTRE Malicious Email Mitigation Strategy Guide Introduction (UPDATED) SEPTEMBER 2012 1. Socially engineered emails containing malicious attachments and embedded links are commonly
QMAIL & SMTP: A Secure Application for an Unsecure Protocol. Orr Dunkelman. [email protected]. January 27, 2004 SMTP and QMAIL Slide 1
 QMAIL & SMTP: A Secure Application for an Unsecure Protocol Orr Dunkelman January 27, 2004 SMTP and QMAIL Slide 1 SMTP, MUA and MTA Speak English Whenever we deal with protocols we (=Internet geeks) like
QMAIL & SMTP: A Secure Application for an Unsecure Protocol Orr Dunkelman January 27, 2004 SMTP and QMAIL Slide 1 SMTP, MUA and MTA Speak English Whenever we deal with protocols we (=Internet geeks) like
Advanced Settings. Help Documentation
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Advanced Settings Abuse Detection SmarterMail has several methods
Guardian Digital Secure Mail Suite Quick Start Guide
 Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Guardian Digital Secure Mail Suite Quick Start Guide Copyright c 2004 Guardian Digital, Inc. Contents 1 Introduction 1 2 Contacting Guardian Digital 2 3 Purpose of This Document 3 3.1 Terminology...............................
Celframe - Easy Linux - Lesson 8 - Email Server
 - Easy Linux - Lesson 8 - Email Server October 2007 Contents 1 Summary 2 2 Theoretical presentation 2 2.1 Introduction............................... 2 2.2 SMTP................................... 2 2.3
- Easy Linux - Lesson 8 - Email Server October 2007 Contents 1 Summary 2 2 Theoretical presentation 2 2.1 Introduction............................... 2 2.2 SMTP................................... 2 2.3
XGENPLUS SECURITY FEATURES...
 Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Analysis of Spam Filter Methods on SMTP Servers Category: Trends in Anti-Spam Development
 Analysis of Spam Filter Methods on SMTP Servers Category: Trends in Anti-Spam Development Author André Tschentscher Address Fachhochschule Erfurt - University of Applied Sciences Applied Computer Science
Analysis of Spam Filter Methods on SMTP Servers Category: Trends in Anti-Spam Development Author André Tschentscher Address Fachhochschule Erfurt - University of Applied Sciences Applied Computer Science
Simple Scan to Email Setup Guide
 Simple Scan to Email Setup Guide Document Centre 555/545/535 Dc04cc0336 Scan to Email Scanning to email from a Xerox DC 555/545/535 requires the support of external email services on a network. These services
Simple Scan to Email Setup Guide Document Centre 555/545/535 Dc04cc0336 Scan to Email Scanning to email from a Xerox DC 555/545/535 requires the support of external email services on a network. These services
Configuration Information
 Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
ESET Mail Security 4. User Guide. for Microsoft Exchange Server. Microsoft Windows 2000 / 2003 / 2008
 ESET Mail Security 4 for Microsoft Exchange Server User Guide Microsoft Windows 2000 / 2003 / 2008 Content 1. Introduction...4 1.1 System requirements... 4 1.2 Methods Used... 4 1.2.1 Mailbox scanning
ESET Mail Security 4 for Microsoft Exchange Server User Guide Microsoft Windows 2000 / 2003 / 2008 Content 1. Introduction...4 1.1 System requirements... 4 1.2 Methods Used... 4 1.2.1 Mailbox scanning
Setup Local Mail Server Using Postfix, Dovecot And Squirrelmail On CentOS 6.5/6.4
 Setup Local Mail Server Using Postfix, Dovecot And Squirrelmail On CentOS 6.5/6.4 For this tutorial, I use CentOS 6.5 32 bit minimal installation, with SELinux disabled. My test box details are given below.
Setup Local Mail Server Using Postfix, Dovecot And Squirrelmail On CentOS 6.5/6.4 For this tutorial, I use CentOS 6.5 32 bit minimal installation, with SELinux disabled. My test box details are given below.
1. The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP; e-mail: SMTP.
 Chapter 2 Review Questions 1. The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP; e-mail: SMTP. 2. Network architecture refers to the organization of the communication process
Chapter 2 Review Questions 1. The Web: HTTP; file transfer: FTP; remote login: Telnet; Network News: NNTP; e-mail: SMTP. 2. Network architecture refers to the organization of the communication process
Collax Mail Server. Howto. This howto describes the setup of a Collax server as mail server.
 Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
eprism Email Security Suite
 Guide eprism 2505 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered
Guide eprism 2505 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered
Peer-to-Peer Support for Distributed Mail Transfer Mechanism. Abstract
 Peer-to-Peer Support for Distributed Mail Transfer Mechanism Kai-Hsiang Yang, Jenq-Haur Wang, Chi-Chien Pan, and Tzao-Lin Lee Department of Computer Science and Information Engineering, National Taiwan
Peer-to-Peer Support for Distributed Mail Transfer Mechanism Kai-Hsiang Yang, Jenq-Haur Wang, Chi-Chien Pan, and Tzao-Lin Lee Department of Computer Science and Information Engineering, National Taiwan
Remote login (Telnet):
 SFWR 4C03: Computer Networks and Computer Security Feb 23-26 2004 Lecturer: Kartik Krishnan Lectures 19-21 Remote login (Telnet): Telnet permits a user to connect to an account on a remote machine. A client
SFWR 4C03: Computer Networks and Computer Security Feb 23-26 2004 Lecturer: Kartik Krishnan Lectures 19-21 Remote login (Telnet): Telnet permits a user to connect to an account on a remote machine. A client
Internet Technology 2/13/2013
 Internet Technology 03r. Application layer protocols: email Email: Paul Krzyzanowski Rutgers University Spring 2013 1 2 Simple Mail Transfer Protocol () Defined in RFC 2821 (April 2001) Original definition
Internet Technology 03r. Application layer protocols: email Email: Paul Krzyzanowski Rutgers University Spring 2013 1 2 Simple Mail Transfer Protocol () Defined in RFC 2821 (April 2001) Original definition
WEBMAIL USER MANUAL AN INTRODUCTION TO WLINK WEBMAIL. Table of content:
 WEBMAIL USER MANUAL Table of content: An introduction to Wlink WebMail Interface guide Read/Delete Email Compose/Send Email Attachment Searching Email Message filter Spam setting Whitelist/Blacklist Email
WEBMAIL USER MANUAL Table of content: An introduction to Wlink WebMail Interface guide Read/Delete Email Compose/Send Email Attachment Searching Email Message filter Spam setting Whitelist/Blacklist Email
Proxy Services: Good Practice Guidelines
 Programme NPFIT DOCUMENT RECORD ID KEY Sub-Prog / Project Information Governance Prog. Director Mark Ferrar Owner Tim Davis Version 1.0 Author James Wood Version Date 26/01/2006 Status APPROVED Proxy Services:
Programme NPFIT DOCUMENT RECORD ID KEY Sub-Prog / Project Information Governance Prog. Director Mark Ferrar Owner Tim Davis Version 1.0 Author James Wood Version Date 26/01/2006 Status APPROVED Proxy Services:
DKIM Enabled Two Factor Authenticated Secure Mail Client
 DKIM Enabled Two Factor Authenticated Secure Mail Client Saritha P, Nitty Sarah Alex M.Tech Student[Software Engineering], New Horizon College of Engineering, Bangalore, India Sr. Asst Prof, Department
DKIM Enabled Two Factor Authenticated Secure Mail Client Saritha P, Nitty Sarah Alex M.Tech Student[Software Engineering], New Horizon College of Engineering, Bangalore, India Sr. Asst Prof, Department
eprism Email Security Suite
 V8.4 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks
V8.4 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered trademarks
Visendo Email Suite a reliable solution for SMBs
 Visendo Email Suite a reliable solution for SMBs Visendo offers a range of Email solutions to assist companies in meeting complex e-mail requirements Visendo Security for Email Servers Multi-engine spam
Visendo Email Suite a reliable solution for SMBs Visendo offers a range of Email solutions to assist companies in meeting complex e-mail requirements Visendo Security for Email Servers Multi-engine spam
Emails and anti-spam Page 1
 Emails and anti-spam Page 1 As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send emails from your webcrm system, we use the webcrm servers to send emails
Emails and anti-spam Page 1 As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send emails from your webcrm system, we use the webcrm servers to send emails
Manage. Help Documentation. This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc.
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Manage Email Users An email user account represents a person's
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Manage Email Users An email user account represents a person's
SMTP Information gathering
 Lluis Mora, Neutralbit [email protected] Black Hat Europe Amsterdam, NL // March 2007 securityinnovation Introduction E-mail is present in nearly every organization We all understand how it works How
Lluis Mora, Neutralbit [email protected] Black Hat Europe Amsterdam, NL // March 2007 securityinnovation Introduction E-mail is present in nearly every organization We all understand how it works How
Emacs SMTP Library. An Emacs package for sending mail via SMTP. Simon Josefsson, Alex Schroeder
 Emacs SMTP Library An Emacs package for sending mail via SMTP Simon Josefsson, Alex Schroeder Copyright c 2003, 2004 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify
Emacs SMTP Library An Emacs package for sending mail via SMTP Simon Josefsson, Alex Schroeder Copyright c 2003, 2004 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify
Objective This howto demonstrates and explains the different mechanisms for fending off unwanted spam e-mail.
 Collax Spam Filter Howto This howto describes the configuration of the spam filter on a Collax server. Requirements Collax Business Server Collax Groupware Suite Collax Security Gateway Collax Platform
Collax Spam Filter Howto This howto describes the configuration of the spam filter on a Collax server. Requirements Collax Business Server Collax Groupware Suite Collax Security Gateway Collax Platform
Intercept Anti-Spam Quick Start Guide
 Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
Intercept Anti-Spam Quick Start Guide Software Version: 6.5.2 Date: 5/24/07 PREFACE...3 PRODUCT DOCUMENTATION...3 CONVENTIONS...3 CONTACTING TECHNICAL SUPPORT...4 COPYRIGHT INFORMATION...4 OVERVIEW...5
Strategies to Protect Against Distributed Denial of Service (DD
 Strategies to Protect Against Distributed Denial of Service (DD Table of Contents Strategies to Protect Against Distributed Denial of Service (DDoS) Attacks...1 Introduction...1 Understanding the Basics
Strategies to Protect Against Distributed Denial of Service (DD Table of Contents Strategies to Protect Against Distributed Denial of Service (DDoS) Attacks...1 Introduction...1 Understanding the Basics
TR-7W Configuration Guide. Before You Start
 TR-7W Configuration Guide Before You Start Take a few moments before you start to make the following simple checks. A few moments spent before you start installing your system can save a lot of time later
TR-7W Configuration Guide Before You Start Take a few moments before you start to make the following simple checks. A few moments spent before you start installing your system can save a lot of time later
Spam Protection by using Sender Address Verification Extension (SAVE)
 Spam Protection by using Sender Address Verification Extension (SAVE) Michael Conrad, Hans-Joachim Hof [conrad hof]@tm.uka.de Roland Bless [email protected] Institute of Telematics, Universität Karlsruhe
Spam Protection by using Sender Address Verification Extension (SAVE) Michael Conrad, Hans-Joachim Hof [conrad hof]@tm.uka.de Roland Bless [email protected] Institute of Telematics, Universität Karlsruhe
March 2005. PGP White Paper. Transport Layer Security (TLS) & Encryption: Complementary Security Tools
 March 2005 PGP White Paper Transport Layer Security (TLS) & Encryption: Complementary Security Tools PGP White Paper TLS & Encryption 1 Table of Contents INTRODUCTION... 2 HISTORY OF TRANSPORT LAYER SECURITY...
March 2005 PGP White Paper Transport Layer Security (TLS) & Encryption: Complementary Security Tools PGP White Paper TLS & Encryption 1 Table of Contents INTRODUCTION... 2 HISTORY OF TRANSPORT LAYER SECURITY...
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
Amicus Link Guide: Outlook/Exchange E-mail
 Amicus Link Guide: Outlook/Exchange E-mail Applies to: Amicus Premium 2015 Synchronize your Amicus and Outlook e-mail. Choose a client-side link with your local Microsoft Outlook or a Server-side link
Amicus Link Guide: Outlook/Exchange E-mail Applies to: Amicus Premium 2015 Synchronize your Amicus and Outlook e-mail. Choose a client-side link with your local Microsoft Outlook or a Server-side link
Web Mail Classic Web Mail
 April 14 Web Mail Classic Web Mail Version 2.2 Table of Contents 1 Technical Requirements... 4 2 Accessing your Web Mail... 4 3 Web Mail Features... 5 3.1 Home... 5 3.1.1 Mailbox Summary... 5 3.1.2 Announcements...
April 14 Web Mail Classic Web Mail Version 2.2 Table of Contents 1 Technical Requirements... 4 2 Accessing your Web Mail... 4 3 Web Mail Features... 5 3.1 Home... 5 3.1.1 Mailbox Summary... 5 3.1.2 Announcements...
How To Guide. SIP Trunking Configuration Using the SIP Trunk Page
 How To Guide SIP Trunking Configuration Using the SIP Trunk Page For the Ingate SIParators and Firewalls using software release 4.9.2 or later. Updated to show features available from release 4.10.x May
How To Guide SIP Trunking Configuration Using the SIP Trunk Page For the Ingate SIParators and Firewalls using software release 4.9.2 or later. Updated to show features available from release 4.10.x May
Email Marketing Glossary of Terms
 Email Marketing Glossary of Terms A/B Testing: A method of testing in which a small, random sample of an email list is split in two. One email is sent to the list A and another modified email is sent to
Email Marketing Glossary of Terms A/B Testing: A method of testing in which a small, random sample of an email list is split in two. One email is sent to the list A and another modified email is sent to
How to configure your email client
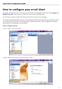 How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
