UvA Psychology Data Protocol. Jaap Murre
|
|
|
- Hollie Knight
- 10 years ago
- Views:
Transcription
1 UvA Psychology Data Protocol Jaap Murre
2 Overview History Preliminaries Four goals of the data protocol Life cycle of an experiment
3 Case 1 "Help, my hard disk crashed! Now I cannot get my Ph.D. because all my data was stored there."
4 Case 2 "I would show you some of my amazing results that were recently published in Nature but unfortunately the dog ate the USB stick with my data."
5 Case 3 "What the heck was NOX again? And were the women coded as 0s or 1s?"
6 Case 4 "In response to your request for my data, please, find enclosed a zip file of the directory that contains my data from the 1986 paper. There are 37 folders and over 500 files, some of which may be corrupted or incomplete. I have no doubts that you can reconstruct the intricate system I used to name the files. Enjoy!"
7 Goal 1: Data safety Data should be safe and secure They should be backed-up in at least two physically separate locations Check: If your computer crashed right now, you should not lose any data? Backups should themselves be verified as they sometimes fail (sometimes there seems to be a backup procedure but it is faulty)
8 Goal 2: Accountability Researchers are accountable for their data They know where it is and how it is organized When asked for it, they can access it The Data Section on the website of the Ethical Committee has been completed At least two researchers are accountable for each data set (possibly with a 'data buddy') Experimenters should keep a lab log of ongoing events (with dates and times).
9 Goal 3: Efficiency (and continuity) Data should be well-organized and documented There should be clear hierarchy of folders and files It is recommended to describe complex file structures in a readme file in the root directory There should be a code book that documents variables, methods, analyses Enough detail should be available to replicate an experiment, simulation, or analysis
10 Goal 4: Sharing of data (etc.) No longer always optional anymore Data may be placed in an online repository, such as DANS or OSF (Open Science Framework, see Usually additional work uploading the data possibly converting it into the right format additional documentation or existing documentation in the repository's format Access may vary from public (anyone may access) to private (nobody may access)
11 Life cycle of an experiment Study design Data collection Data analysis Reporting
12 Study design Lead scientist is identified The lead scientist creates a project folder Clear folder layout Recommended: a readme file in the root
13 Study design Folder structure /White Dog Experiment 2014 readme.txt /Ethics protocol.pdf approval.pdf informed_consent.pdf information_brochure.pdf debriefing_brochure.pdf /informed_consent_forms form1.pdf form2.pdf form3.pdf /Design white_dog_experiment_design.pdf /Data /Raw white_dog_experiment_raw_frozen.zip /Cleaned /Analyses /Report
14 Study design readme file Title of the research project Principal investigator(s) Geographic location(s) where the data were collected Start and end date of data collection Type of sampling (e.g., random sample) Mode of data collection (e.g., lab experiment, survey) Field of study Abstract research report (update at end) Keywords
15 Study design ethics approval etc. Ethics approval is now mandatory for all Psychology Projects May select (strict) confirmatory study Think it through before starting: Main hypothesis? Design and procedure? Subjects recruitment? What type of data is expected and how analyzed?
16 Data storage space should by like office furniture: Available to researchers for free
17 Data Collection stage Archive raw data files Brief report on subject recruitment Informed consent forms (go to TOP) Stimuli Experiment scripts Intermediate, processed data Code book (0: women, 1: men; etc.) Lab log
18 Data analysis All (R, Matlab, ) scripts, SPSS syntax files EEG (etc.) analysis scripts List of dropped subjects (with reason) Final preprocessed data (before analysis) Files with outcomes of analysis (SPSS, Excel, ) Perhaps: Folder or files with analyses tried but not reported
19 Sharing Data are moved into a repository Meta data and files must provided in accordance with the repositories demands If only a selection is shared, mention this fact in the meta data (readme file) Several repositories (e.g., DANS and OSF) have very few official documentation demands If the guidelines have been followed this should also suffice for effortless sharing good idea to add an abstract, reference to publications, and additional roadmaps of your data
20
Data Protocol UvA Psychology - background information
 Data Protocol UvA Psychology - background information Data storage at various points of the experimental research life cycle Jaap Murre, Department of Psychology, University of Amsterdam Introduction This
Data Protocol UvA Psychology - background information Data storage at various points of the experimental research life cycle Jaap Murre, Department of Psychology, University of Amsterdam Introduction This
Directory Backup and Restore
 Directory Backup and Restore Overview Active Directory is backed up as part of system state, a collection of system components that depend on each other. You must backup and restore system state components
Directory Backup and Restore Overview Active Directory is backed up as part of system state, a collection of system components that depend on each other. You must backup and restore system state components
Introduction to Research Data Management
 Introduction to Research Data Management Marta Teperek, Veronica Phillips 30/10/2015 University of Cambridge TODAY: Mixture of activities and talking Introduction 1. Backup and exchange strategies 2. How
Introduction to Research Data Management Marta Teperek, Veronica Phillips 30/10/2015 University of Cambridge TODAY: Mixture of activities and talking Introduction 1. Backup and exchange strategies 2. How
LJMU Research Data Policy: information and guidance
 LJMU Research Data Policy: information and guidance Prof. Director of Research April 2013 Aims This document outlines the University policy and provides advice on the treatment, storage and sharing of
LJMU Research Data Policy: information and guidance Prof. Director of Research April 2013 Aims This document outlines the University policy and provides advice on the treatment, storage and sharing of
Data Availability Policies & Author Responsibility Policies Time of Evaluation: May 2014
 Data policies found in a sample of 346 journals in economic sciences Data Availability Policies & Author Responsibility Policies Time of Evaluation: May 2014 Table of Contents: Data Availability Policies:...
Data policies found in a sample of 346 journals in economic sciences Data Availability Policies & Author Responsibility Policies Time of Evaluation: May 2014 Table of Contents: Data Availability Policies:...
File Space / Web Space / Database Space - Self-Service Allocation August 2009
 File Space / Web Space / Database Space - Self-Service Allocation August 2009 All Purchase students can use this self-service application to obtain file space, web publishing space, and database space.
File Space / Web Space / Database Space - Self-Service Allocation August 2009 All Purchase students can use this self-service application to obtain file space, web publishing space, and database space.
Introduction to industrial/organizational psychology
 Introduction to industrial/organizational psychology Chapter 1 Industrial/Organizational Psychology: A branch of psychology that applies the principles of psychology to the workplace I/O psychologists
Introduction to industrial/organizational psychology Chapter 1 Industrial/Organizational Psychology: A branch of psychology that applies the principles of psychology to the workplace I/O psychologists
Security Correlation Server Backup and Recovery Guide
 orrelog Security Correlation Server Backup and Recovery Guide This guide provides information to assist administrators and operators with backing up the configuration and archive data of the CorreLog server,
orrelog Security Correlation Server Backup and Recovery Guide This guide provides information to assist administrators and operators with backing up the configuration and archive data of the CorreLog server,
File-System Implementation
 File-System Implementation 11 CHAPTER In this chapter we discuss various methods for storing information on secondary storage. The basic issues are device directory, free space management, and space allocation
File-System Implementation 11 CHAPTER In this chapter we discuss various methods for storing information on secondary storage. The basic issues are device directory, free space management, and space allocation
inforouter Version 8.0 Administrator s Backup, Restore & Disaster Recovery Guide
 inforouter Version 8.0 Administrator s Backup, Restore & Disaster Recovery Guide Active Innovations, Inc. Names of all products herein are used for identification purposes only and are trademarks and/or
inforouter Version 8.0 Administrator s Backup, Restore & Disaster Recovery Guide Active Innovations, Inc. Names of all products herein are used for identification purposes only and are trademarks and/or
Preservation and Dissemination Policy of the LISS Data Archive
 Preservation and Dissemination Policy of the LISS Data Archive date 21 March 2016 authors Marika de Bruijne, Arnaud Wijnant, Edwin de Vet, Eric Balster version 1.3 classification standard CentERdata, Tilburg,
Preservation and Dissemination Policy of the LISS Data Archive date 21 March 2016 authors Marika de Bruijne, Arnaud Wijnant, Edwin de Vet, Eric Balster version 1.3 classification standard CentERdata, Tilburg,
A grant number provides unique identification for the grant.
 Data Management Plan template Name of student/researcher(s) Name of group/project Description of your research Briefly summarise the type of your research to help others understand the purposes for which
Data Management Plan template Name of student/researcher(s) Name of group/project Description of your research Briefly summarise the type of your research to help others understand the purposes for which
Enterprise Storage Management System
 Enterprise Storage Management System Dan Glasser 1, Madeline Hardojo 1, Anand Sundaram 1, Nate Wells 1 Abstract: {dglasser, anands, mhardojo, nwells}@cse.unl.edu and Mohamed Fayad, PhD 2 [email protected]
Enterprise Storage Management System Dan Glasser 1, Madeline Hardojo 1, Anand Sundaram 1, Nate Wells 1 Abstract: {dglasser, anands, mhardojo, nwells}@cse.unl.edu and Mohamed Fayad, PhD 2 [email protected]
Ocster Backup - Rescue System
 Overview Ocster Backup - Rescue System The software allows you to create a rescue CD, DVD or USB-Stick. This rescue system is intended for two kinds of situations: 1. To restore a backup to your main hard
Overview Ocster Backup - Rescue System The software allows you to create a rescue CD, DVD or USB-Stick. This rescue system is intended for two kinds of situations: 1. To restore a backup to your main hard
MapGuide Open Source Repository Management Back up, restore, and recover your resource repository.
 MapGuide Open Source Repository Management Back up, restore, and recover your resource repository. Page 1 of 5 Table of Contents 1. Introduction...3 2. Supporting Utility...3 3. Backup...4 3.1 Offline
MapGuide Open Source Repository Management Back up, restore, and recover your resource repository. Page 1 of 5 Table of Contents 1. Introduction...3 2. Supporting Utility...3 3. Backup...4 3.1 Offline
WIM Image Upgrade Instructions
 v2.1 v2.1 Publication Information 2015 Imagine Communications Corp. Proprietary and Confidential. Imagine Communications considers this document and its contents to be proprietary and confidential. Except
v2.1 v2.1 Publication Information 2015 Imagine Communications Corp. Proprietary and Confidential. Imagine Communications considers this document and its contents to be proprietary and confidential. Except
Installing, Uninstalling, and Upgrading Service Monitor
 CHAPTER 2 Installing, Uninstalling, and Upgrading Service Monitor This section contains the following topics: Preparing to Install Service Monitor, page 2-1 Installing Cisco Unified Service Monitor, page
CHAPTER 2 Installing, Uninstalling, and Upgrading Service Monitor This section contains the following topics: Preparing to Install Service Monitor, page 2-1 Installing Cisco Unified Service Monitor, page
OpenAIRE Research Data Management Briefing paper
 OpenAIRE Research Data Management Briefing paper Understanding Research Data Management February 2016 H2020-EINFRA-2014-1 Topic: e-infrastructure for Open Access Research & Innovation action Grant Agreement
OpenAIRE Research Data Management Briefing paper Understanding Research Data Management February 2016 H2020-EINFRA-2014-1 Topic: e-infrastructure for Open Access Research & Innovation action Grant Agreement
C6 Easy Imaging Total Computer Backup. User Guide
 C6 Easy Imaging Total Computer Backup User Guide Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation. Other product names used in this guide are recognized
C6 Easy Imaging Total Computer Backup User Guide Clickfree and the Clickfree logo are trademarks or registered trademarks of Storage Appliance Corporation. Other product names used in this guide are recognized
C6 Easy Imaging Total Computer Backup. Frequently Asked Questions
 Frequently Asked Questions (FAQs) C6 Easy Imaging Total Computer Backup Frequently Asked Questions (FAQs) Frequently Asked Questions (FAQs) Clickfree and the Clickfree logo are trademarks or registered
Frequently Asked Questions (FAQs) C6 Easy Imaging Total Computer Backup Frequently Asked Questions (FAQs) Frequently Asked Questions (FAQs) Clickfree and the Clickfree logo are trademarks or registered
How To Package In Composer 2.5.2.2 (Amd64)
 Composer User Guide Version 9.1 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave S Suite
Composer User Guide Version 9.1 JAMF Software, LLC 2013 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave S Suite
A. I do not have my own personal certificate I am a new client or want to download a new certificate
 This user guide will help you to create your personal certificate in file/browser or smart card certificate. If you already own a personal certificate in file that you have saved on your computer, you
This user guide will help you to create your personal certificate in file/browser or smart card certificate. If you already own a personal certificate in file that you have saved on your computer, you
Configuring, Managing and Maintaining Windows Server 2008 Servers
 Configuring, Managing and Maintaining Windows Server 2008 Servers MOC6419 About this Course This five-day instructor-led course combines five days worth of instructor-led training content from the Network
Configuring, Managing and Maintaining Windows Server 2008 Servers MOC6419 About this Course This five-day instructor-led course combines five days worth of instructor-led training content from the Network
Moxa Device Manager 2.0 User s Guide
 First Edition, March 2009 www.moxa.com/product 2009 Moxa Inc. All rights reserved. Reproduction without permission is prohibited. Moxa Device Manager 2.0 User Guide The software described in this manual
First Edition, March 2009 www.moxa.com/product 2009 Moxa Inc. All rights reserved. Reproduction without permission is prohibited. Moxa Device Manager 2.0 User Guide The software described in this manual
Configuring Advanced Windows Server 2012 Services
 Course 20412D: Configuring Advanced Windows Server 2012 Services Course Details Course Outline Module 1: Implementing Advanced Network Services In this module students will be able to configure advanced
Course 20412D: Configuring Advanced Windows Server 2012 Services Course Details Course Outline Module 1: Implementing Advanced Network Services In this module students will be able to configure advanced
Open Exeter Research Data Survey
 Page 1 of 1 Back to My surveys Home About Bristol Online Surveys Contact Us Open Exeter Research Data Survey Welcome Page 1 of 6 Welcome to the Open Exeter Research Data Management Survey. As part of our
Page 1 of 1 Back to My surveys Home About Bristol Online Surveys Contact Us Open Exeter Research Data Survey Welcome Page 1 of 6 Welcome to the Open Exeter Research Data Management Survey. As part of our
Library Recovery Center
 Library Recovery Center Ever since libraries began storing bibliographic information on magnetic disks back in the 70 s, the challenge of creating useful back-ups and preparing for a disaster recovery
Library Recovery Center Ever since libraries began storing bibliographic information on magnetic disks back in the 70 s, the challenge of creating useful back-ups and preparing for a disaster recovery
Windows 7 Hard Disk Recovery
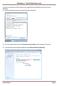 In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
SIP-DECT Knowledge Base SIP-DECT System Update
 SIP-DECT Knowledge Base SIP-DECT System Update MAI 2015 DEPL-2046 VERSION 1.6 KNOWLEDGE BASE TABLE OF CONTENT 1) Introduction... 2 2) Update (New Service Pack in the same Release)... 3 2.1 OMM HOSTED ON
SIP-DECT Knowledge Base SIP-DECT System Update MAI 2015 DEPL-2046 VERSION 1.6 KNOWLEDGE BASE TABLE OF CONTENT 1) Introduction... 2 2) Update (New Service Pack in the same Release)... 3 2.1 OMM HOSTED ON
Tk20 Backup Procedure
 Tk20 Backup Procedure 1 TK20 BACKUP PROCEDURE OVERVIEW 3 FEATURES AND ADVANTAGES: 3 TK20 BACKUP PROCEDURE 4 DAILY BACKUP CREATION 4 TRANSFER OF BACKUPS 5 AUDITING PROCESS 5 BACKUP REPOSITORY 5 WRITE TO
Tk20 Backup Procedure 1 TK20 BACKUP PROCEDURE OVERVIEW 3 FEATURES AND ADVANTAGES: 3 TK20 BACKUP PROCEDURE 4 DAILY BACKUP CREATION 4 TRANSFER OF BACKUPS 5 AUDITING PROCESS 5 BACKUP REPOSITORY 5 WRITE TO
Configuring Managing and Maintaining Windows Server 2008 Servers (6419B)
 Configuring Managing and Maintaining Windows Server 2008 Servers (6419B) Who Should Attend This course is intended for Windows Server administrators who operate Windows Servers on a daily basis and want
Configuring Managing and Maintaining Windows Server 2008 Servers (6419B) Who Should Attend This course is intended for Windows Server administrators who operate Windows Servers on a daily basis and want
StreamServe Persuasion SP5 Control Center
 StreamServe Persuasion SP5 Control Center User Guide Rev C StreamServe Persuasion SP5 Control Center User Guide Rev C OPEN TEXT CORPORATION ALL RIGHTS RESERVED United States and other international patents
StreamServe Persuasion SP5 Control Center User Guide Rev C StreamServe Persuasion SP5 Control Center User Guide Rev C OPEN TEXT CORPORATION ALL RIGHTS RESERVED United States and other international patents
WS_FTP Professional 12
 WS_FTP Professional 12 Tools Guide Contents CHAPTER 1 Introduction Ways to Automate Regular File Transfers...5 Check Transfer Status and Logs...6 Building a List of Files for Transfer...6 Transfer Files
WS_FTP Professional 12 Tools Guide Contents CHAPTER 1 Introduction Ways to Automate Regular File Transfers...5 Check Transfer Status and Logs...6 Building a List of Files for Transfer...6 Transfer Files
Suite. How to Use GrandMaster Suite. Backup and Restore
 Suite How to Use GrandMaster Suite Backup and Restore This page intentionally left blank Backup and Restore 3 Table of Contents: HOW TO USE GRANDMASTER SUITE - PAYROLL BACKUP AND RESTORE...4 OVERVIEW...4
Suite How to Use GrandMaster Suite Backup and Restore This page intentionally left blank Backup and Restore 3 Table of Contents: HOW TO USE GRANDMASTER SUITE - PAYROLL BACKUP AND RESTORE...4 OVERVIEW...4
Partek Flow Installation Guide
 Partek Flow Installation Guide Partek Flow is a web based application for genomic data analysis and visualization, which can be installed on a desktop computer, compute cluster or cloud. Users can access
Partek Flow Installation Guide Partek Flow is a web based application for genomic data analysis and visualization, which can be installed on a desktop computer, compute cluster or cloud. Users can access
ultimo theme Update Guide Copyright 2012-2013 Infortis All rights reserved
 ultimo theme Update Guide Copyright 2012-2013 Infortis All rights reserved 1 1. Update Before you start updating, please refer to 2. Important changes to check if there are any additional instructions
ultimo theme Update Guide Copyright 2012-2013 Infortis All rights reserved 1 1. Update Before you start updating, please refer to 2. Important changes to check if there are any additional instructions
Data storage, collaboration, backup, transfer and encryption
 Data storage, collaboration, backup, transfer and encryption Scott Summers UK Data Archive Practical research data management 19 April 2016 Overview Looking after research data for the longer-term and
Data storage, collaboration, backup, transfer and encryption Scott Summers UK Data Archive Practical research data management 19 April 2016 Overview Looking after research data for the longer-term and
USB Functions for Windows 7
 USB Functions for Windows 7 Getting Started Position the DSL-2750B in your desired location, and connect the power cable to the rear of the device. From the ADSL micro filter device that provides the separated
USB Functions for Windows 7 Getting Started Position the DSL-2750B in your desired location, and connect the power cable to the rear of the device. From the ADSL micro filter device that provides the separated
EnterpriseLink Benefits
 EnterpriseLink Benefits GGY AXIS 5001 Yonge Street Suite 1300 Toronto, ON M2N 6P6 Phone: 416-250-6777 Toll free: 1-877-GGY-AXIS Fax: 416-250-6776 Email: [email protected] Web: www.ggy.com Table of Contents
EnterpriseLink Benefits GGY AXIS 5001 Yonge Street Suite 1300 Toronto, ON M2N 6P6 Phone: 416-250-6777 Toll free: 1-877-GGY-AXIS Fax: 416-250-6776 Email: [email protected] Web: www.ggy.com Table of Contents
Cobian9 Backup Program - Amanita
 The problem with backup software Cobian9 Backup Program - Amanita Due to the quixotic nature of Windows computers, viruses and possibility of hardware failure many programs are available for backing up
The problem with backup software Cobian9 Backup Program - Amanita Due to the quixotic nature of Windows computers, viruses and possibility of hardware failure many programs are available for backing up
Technote 20 Using MSIE to FTP into an AcquiSuite
 Technote 20 Using MSIE to FTP into an AcquiSuite Author: Stephen Herzog This document discusses the use of Microsoft Internet Explorer to FTP into the AcquiSuite. Other browsers such as Firefox should
Technote 20 Using MSIE to FTP into an AcquiSuite Author: Stephen Herzog This document discusses the use of Microsoft Internet Explorer to FTP into the AcquiSuite. Other browsers such as Firefox should
... 2 HARDWARE AND FIRMWARE
 General hints BEETLE systems are delivered with a pre installed operating system and therefore do not need any download of driver for proper function of the hardware. For customers with special project
General hints BEETLE systems are delivered with a pre installed operating system and therefore do not need any download of driver for proper function of the hardware. For customers with special project
System Administration of Windchill 10.2
 System Administration of Windchill 10.2 Overview Course Code Course Length TRN-4340-T 3 Days In this course, you will gain an understanding of how to perform routine Windchill system administration tasks,
System Administration of Windchill 10.2 Overview Course Code Course Length TRN-4340-T 3 Days In this course, you will gain an understanding of how to perform routine Windchill system administration tasks,
6419: Configuring, Managing, and Maintaining Server 2008
 6419: Configuring, Managing, and Maintaining Server 2008 Course Number: 6419 Category: Technical Duration: 5 days Course Description This five-day instructor-led course combines five days worth of instructor-led
6419: Configuring, Managing, and Maintaining Server 2008 Course Number: 6419 Category: Technical Duration: 5 days Course Description This five-day instructor-led course combines five days worth of instructor-led
An Introduction to Managing Research Data
 An Introduction to Managing Research Data Author University of Bristol Research Data Service Date 1 August 2013 Version 3 Notes URI IPR data.bris.ac.uk Copyright 2013 University of Bristol Within the Research
An Introduction to Managing Research Data Author University of Bristol Research Data Service Date 1 August 2013 Version 3 Notes URI IPR data.bris.ac.uk Copyright 2013 University of Bristol Within the Research
ManageEngine EventLog Analyzer. Best Practices Document
 ManageEngine EventLog Analyzer Best Practices Document Table of Contents System Requirements... 3 Up to 50 hosts... 3 Up to 100 hosts... 3 Up to 200 hosts... 3 Up to 500 hosts... 3 Above 500 hosts... 4
ManageEngine EventLog Analyzer Best Practices Document Table of Contents System Requirements... 3 Up to 50 hosts... 3 Up to 100 hosts... 3 Up to 200 hosts... 3 Up to 500 hosts... 3 Above 500 hosts... 4
NSS Volume Data Recovery
 NSS Volume Data Recovery Preliminary Document September 8, 2010 Version 1.0 Copyright 2000-2010 Portlock Corporation Copyright 2000-2010 Portlock Corporation Page 1 of 20 The Portlock storage management
NSS Volume Data Recovery Preliminary Document September 8, 2010 Version 1.0 Copyright 2000-2010 Portlock Corporation Copyright 2000-2010 Portlock Corporation Page 1 of 20 The Portlock storage management
FTP Accounts Contents
 FTP Accounts Contents Goal... 2 1. Add an FTP Account... 2 2. The FTP Account Management Table... 3 3. Remove an FTP Account... 4 4. Edit an FTP Account's Quota... 4 5. Change an FTP Account's Password...
FTP Accounts Contents Goal... 2 1. Add an FTP Account... 2 2. The FTP Account Management Table... 3 3. Remove an FTP Account... 4 4. Edit an FTP Account's Quota... 4 5. Change an FTP Account's Password...
National Quali cations SPECIMEN ONLY
 H National Qualications SPECIMEN ONLY SQ39/H/01 Psychology Date Not applicable Duration 2 hours Total s 60 SECTION 1 RESEARCH 20 s Attempt ALL parts of ALL questions. SECTION 2 INDIVIDUAL BEHAVIOUR 20
H National Qualications SPECIMEN ONLY SQ39/H/01 Psychology Date Not applicable Duration 2 hours Total s 60 SECTION 1 RESEARCH 20 s Attempt ALL parts of ALL questions. SECTION 2 INDIVIDUAL BEHAVIOUR 20
How To Install Docushare Software On A Pc Or Mac Or Macbook Or Macode (For Mac) Or Macro (For Pc) (For Linux) (Or Macode) (Macode) Or Ipad Or Macromode
 Publication date: November 2011 This document supports DocuShare Release 6.6 and greater Prepared by: Xerox Corporation DocuShare Business Unit 3400 Hillview Avenue Palo Alto, California 94304 USA 2011
Publication date: November 2011 This document supports DocuShare Release 6.6 and greater Prepared by: Xerox Corporation DocuShare Business Unit 3400 Hillview Avenue Palo Alto, California 94304 USA 2011
Acronis Backup & Recovery 10 Server for Linux. Installation Guide
 Acronis Backup & Recovery 10 Server for Linux Installation Guide Table of contents 1 Before installation...3 1.1 Acronis Backup & Recovery 10 components... 3 1.1.1 Agent for Linux... 3 1.1.2 Management
Acronis Backup & Recovery 10 Server for Linux Installation Guide Table of contents 1 Before installation...3 1.1 Acronis Backup & Recovery 10 components... 3 1.1.1 Agent for Linux... 3 1.1.2 Management
StreamServe Persuasion SP4 StreamServe Connect for SAP - Business Processes
 StreamServe Persuasion SP4 StreamServe Connect for SAP - Business Processes User Guide Rev A StreamServe Persuasion SP4StreamServe Connect for SAP - Business Processes User Guide Rev A SAP, mysap.com,
StreamServe Persuasion SP4 StreamServe Connect for SAP - Business Processes User Guide Rev A StreamServe Persuasion SP4StreamServe Connect for SAP - Business Processes User Guide Rev A SAP, mysap.com,
Enterprise Historian 3BUF 001 152 D1 Version 3.2/1 Hot Fix 1 for Patch 4 Release Notes
 Industrial IT Inform IT Enterprise Historian Enterprise Historian 3BUF 001 152 D1 Version 3.2/1 Hot Fix 1 for Patch 4 Release Notes Introduction This document provides release information for hot fix 1
Industrial IT Inform IT Enterprise Historian Enterprise Historian 3BUF 001 152 D1 Version 3.2/1 Hot Fix 1 for Patch 4 Release Notes Introduction This document provides release information for hot fix 1
CTERA Portal Datacenter Edition
 Installing a Security Certificate on the CTERA Portal CTERA Portal Datacenter Edition Aug 2013 Versions 3.2, 4.0 2013, CTERA Networks. All rights reserved. 1 Introduction Certificates are used as part
Installing a Security Certificate on the CTERA Portal CTERA Portal Datacenter Edition Aug 2013 Versions 3.2, 4.0 2013, CTERA Networks. All rights reserved. 1 Introduction Certificates are used as part
Research Data Archival Guidelines
 Research Data Archival Guidelines LEROY MWANZIA RESEARCH METHODS GROUP APRIL 2012 Table of Contents Table of Contents... i 1 World Agroforestry Centre s Mission and Research Data... 1 2 Definitions:...
Research Data Archival Guidelines LEROY MWANZIA RESEARCH METHODS GROUP APRIL 2012 Table of Contents Table of Contents... i 1 World Agroforestry Centre s Mission and Research Data... 1 2 Definitions:...
Digital Forensics Tutorials Acquiring an Image with FTK Imager
 Digital Forensics Tutorials Acquiring an Image with FTK Imager Explanation Section Digital Forensics Definition The use of scientifically derived and proven methods toward the preservation, collection,
Digital Forensics Tutorials Acquiring an Image with FTK Imager Explanation Section Digital Forensics Definition The use of scientifically derived and proven methods toward the preservation, collection,
StreamServe Persuasion SP5 Upgrading instructions
 StreamServe Persuasion SP5 Upgrading instructions Reference Guide Rev A Upgrading instructionsstreamserve Persuasion SP5 Reference Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States
StreamServe Persuasion SP5 Upgrading instructions Reference Guide Rev A Upgrading instructionsstreamserve Persuasion SP5 Reference Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United States
ROUNDTABLE TSMS 11.5 Installation Guide
 ROUNDTABLE TSMS 11.5 Installation Guide Copyright 2015 by Ledbetter & Harp, LLC Roundtable software products are licensed by Roundtable Software, Inc. and copyrighted by Ledbetter & Harp, LLC, with all
ROUNDTABLE TSMS 11.5 Installation Guide Copyright 2015 by Ledbetter & Harp, LLC Roundtable software products are licensed by Roundtable Software, Inc. and copyrighted by Ledbetter & Harp, LLC, with all
Introducing ESSEXLab. David Hugh-Jones ESSEXLab Director [email protected]
 Introducing ESSEXLab David Hugh-Jones ESSEXLab Director [email protected] Introducing ESSEXLab The Essex Social Science EXperimental Laboratory A new resource funded by the University 32-seat laboratory,
Introducing ESSEXLab David Hugh-Jones ESSEXLab Director [email protected] Introducing ESSEXLab The Essex Social Science EXperimental Laboratory A new resource funded by the University 32-seat laboratory,
M6419 Configuring, Managing and Maintaining Windows Server 2008 Servers
 M6419 Configuring, Managing and Maintaining Windows Server 2008 Servers Looking at Training Differently... Course 6419A: Configuring, Managing and Maintaining Windows Server 2008 Servers Length: Published:
M6419 Configuring, Managing and Maintaining Windows Server 2008 Servers Looking at Training Differently... Course 6419A: Configuring, Managing and Maintaining Windows Server 2008 Servers Length: Published:
MS 6419 Configuring, Managing and Maintaining Windows Server 2008-based Servers
 MS 6419 Configuring, Managing and Maintaining Windows Server 2008-based Servers Description: Days: 5 Prerequisites: This five-day instructor-led course provides students with the knowledge and skills that
MS 6419 Configuring, Managing and Maintaining Windows Server 2008-based Servers Description: Days: 5 Prerequisites: This five-day instructor-led course provides students with the knowledge and skills that
ultimo theme Update Guide Copyright 2012-2013 Infortis All rights reserved
 ultimo theme Update Guide Copyright 2012-2013 Infortis All rights reserved 1 1. Update Before you start updating, please refer to 2. Important changes to check if there are any additional instructions
ultimo theme Update Guide Copyright 2012-2013 Infortis All rights reserved 1 1. Update Before you start updating, please refer to 2. Important changes to check if there are any additional instructions
Home Course Catalog Schedule Pricing & Savings Training Options Resources About Us
 1 of 14 12/04/2012 06:46 PM Hello, Jonathan Earl My Account Logout GS-35F-0556S CONTACT US Search TOLL FREE 877-932-8228 Home Course Catalog Schedule Pricing & Savings Training Options Resources About
1 of 14 12/04/2012 06:46 PM Hello, Jonathan Earl My Account Logout GS-35F-0556S CONTACT US Search TOLL FREE 877-932-8228 Home Course Catalog Schedule Pricing & Savings Training Options Resources About
MOC 6419: Configuring, Managing, and Maintaining Windows Server 2008
 1 of 6 1/6/2010 3:23 PM MOC 6419: Configuring, Managing, and Maintaining Windows Server 2008 This five-day instructor-led course combines five days worth of instructor-led training content from the Network
1 of 6 1/6/2010 3:23 PM MOC 6419: Configuring, Managing, and Maintaining Windows Server 2008 This five-day instructor-led course combines five days worth of instructor-led training content from the Network
DATA CENTER SERVICE CATALOG
 DATA CENTER SERVICE CATALOG KING SAUD UNIVERSITY DEANSHIP OF ETRANSACTIONS & COMMUNICATION VERSION 1.1 INTERNAL USE ONLY PREPARED BY REVIEWED BY APPROVED BY NAFEZ ALBESHEETI DR.MISHARI ALMISHARI DR.MISHARI
DATA CENTER SERVICE CATALOG KING SAUD UNIVERSITY DEANSHIP OF ETRANSACTIONS & COMMUNICATION VERSION 1.1 INTERNAL USE ONLY PREPARED BY REVIEWED BY APPROVED BY NAFEZ ALBESHEETI DR.MISHARI ALMISHARI DR.MISHARI
Lightning Payroll Program Update and Backup
 Lightning Payroll Program Update and Backup As you are aware, there have been several changes to the WagezWindow Payroll Program (now called Lightning Payroll). You will need to read and follow the instructions
Lightning Payroll Program Update and Backup As you are aware, there have been several changes to the WagezWindow Payroll Program (now called Lightning Payroll). You will need to read and follow the instructions
Managing Your Lotus Notes Mail Database Size
 Managing Your Lotus Notes Mail Database Size Your Lotus Notes database consists of Mail, Calendar entries and ToDo items. For the purpose of this document, your Notes database will also be referred to
Managing Your Lotus Notes Mail Database Size Your Lotus Notes database consists of Mail, Calendar entries and ToDo items. For the purpose of this document, your Notes database will also be referred to
ManageEngine Desktop Central Training
 ManageEngine Desktop Central Training Course Objectives Who Should Attend Course Agenda Course Objectives Desktop Central training helps you IT staff learn the features offered by Desktop Central and to
ManageEngine Desktop Central Training Course Objectives Who Should Attend Course Agenda Course Objectives Desktop Central training helps you IT staff learn the features offered by Desktop Central and to
Configuring, Managing and Maintaining Windows Server 2008 Servers
 Configuring, Managing and Maintaining Windows Server 2008 Servers Elements of this syllabus are subject to change Course Details Course Code: 6419 Duration: Notes: 5 day(s) This course syllabus should
Configuring, Managing and Maintaining Windows Server 2008 Servers Elements of this syllabus are subject to change Course Details Course Code: 6419 Duration: Notes: 5 day(s) This course syllabus should
Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization
 Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization Duration: Three consecutive Saturdays About this Course This instructor led course teaches students how to implement and manage Windows
Outline SSS6422 - Microsoft Windows Server 2008 Hyper-V Virtualization Duration: Three consecutive Saturdays About this Course This instructor led course teaches students how to implement and manage Windows
Frequently Asked Questions About WebDrv Online (Remote) Backup
 Frequently Asked Questions About WebDrv Online (Remote) Backup GENERAL INFORMATION Why backup? What is online backup? What if we already have a tape backup system? How secure are online backups? What tasks
Frequently Asked Questions About WebDrv Online (Remote) Backup GENERAL INFORMATION Why backup? What is online backup? What if we already have a tape backup system? How secure are online backups? What tasks
ROADMAP TO DEFINE A BACKUP STRATEGY FOR SAP APPLICATIONS Helps you to analyze and define a robust backup strategy
 A BasisOnDemand.com White Paper ROADMAP TO DEFINE A BACKUP STRATEGY FOR SAP APPLICATIONS Helps you to analyze and define a robust backup strategy by Prakash Palani ([email protected]) Table
A BasisOnDemand.com White Paper ROADMAP TO DEFINE A BACKUP STRATEGY FOR SAP APPLICATIONS Helps you to analyze and define a robust backup strategy by Prakash Palani ([email protected]) Table
Business details. Monday Friday. 10:00am 6:00pm. Saturday 10:00am 5:00pm. Telephone: 020 8315 0005. Email: [email protected].
 Business details Services and price list 2010 Monday Friday 10:00am 6:00pm Saturday 10:00am 5:00pm We offer professional IT services for home and business users at a cost effective price. We have a team
Business details Services and price list 2010 Monday Friday 10:00am 6:00pm Saturday 10:00am 5:00pm We offer professional IT services for home and business users at a cost effective price. We have a team
Administrasi dan Manajemen Jaringan 2. File Transfer Protocol (FTP)
 Administrasi dan Manajemen Jaringan 2. File Transfer Protocol (FTP) M. Udin Harun Al Rasyid, Ph.D http://lecturer.eepis-its.edu/~udinharun [email protected] Lab Jaringan Komputer (C-307) Table of
Administrasi dan Manajemen Jaringan 2. File Transfer Protocol (FTP) M. Udin Harun Al Rasyid, Ph.D http://lecturer.eepis-its.edu/~udinharun [email protected] Lab Jaringan Komputer (C-307) Table of
Best Practices for Running a Hyperfunctional Psychology Laboratory
 Best Practices for Running a Hyperfunctional Psychology Laboratory Greg J. Siegle, Ph.D. University of Pittsburgh School of Medicine These slides available at http://www.pitt.edu/~gsiegle/sieglelaboratorybestpracticescolloquium.pdf
Best Practices for Running a Hyperfunctional Psychology Laboratory Greg J. Siegle, Ph.D. University of Pittsburgh School of Medicine These slides available at http://www.pitt.edu/~gsiegle/sieglelaboratorybestpracticescolloquium.pdf
How to Back Up and Restore an ACT! Database Answer ID 19211
 How to Back Up and Restore an ACT! Database Answer ID 19211 Please note: Answer ID documents referenced in this article can be located at: http://www.act.com/support/index.cfm (Knowledge base link). The
How to Back Up and Restore an ACT! Database Answer ID 19211 Please note: Answer ID documents referenced in this article can be located at: http://www.act.com/support/index.cfm (Knowledge base link). The
Symantec Enterprise Vault 10.x for File System Archiving: Administration
 Symantec Enterprise Vault 10.x for File System Archiving: Administration Day(s): 4 Course Code: DP0164 Overview The Symantec Enterprise Vault 10.x for File System Archiving: Administration course is designed
Symantec Enterprise Vault 10.x for File System Archiving: Administration Day(s): 4 Course Code: DP0164 Overview The Symantec Enterprise Vault 10.x for File System Archiving: Administration course is designed
Backup and Restore with 3 rd Party Applications
 Backup and Restore with 3 rd Party Applications Contents Introduction...1 Backup Software Capabilities...1 Backing up a Single Autodesk Vault Site...1 Backup Process...1 Restore Process...1 Backing up
Backup and Restore with 3 rd Party Applications Contents Introduction...1 Backup Software Capabilities...1 Backing up a Single Autodesk Vault Site...1 Backup Process...1 Restore Process...1 Backing up
COMPLETE COMPUTING, INC.
 6425: Configuring and Troubleshooting Windows Server 2008 Active Directory Domain Services Five days; Instructor-Led Introduction This five-day instructor-led course provides to teach Active Directory
6425: Configuring and Troubleshooting Windows Server 2008 Active Directory Domain Services Five days; Instructor-Led Introduction This five-day instructor-led course provides to teach Active Directory
University of Bristol. Research Data Storage Facility (the Facility) Policy Procedures and FAQs
 University of Bristol Research Data Storage Facility (the Facility) Policy Procedures and FAQs This FAQs should be read in conjunction with the RDSF usage FAQs - https://www.acrc.bris.ac.uk/acrc/rdsf-faqs.html
University of Bristol Research Data Storage Facility (the Facility) Policy Procedures and FAQs This FAQs should be read in conjunction with the RDSF usage FAQs - https://www.acrc.bris.ac.uk/acrc/rdsf-faqs.html
Backing up your QuickBooks data file
 Backing up your QuickBooks data file A regular backup regime is essential to minimise disruption to the business should there be an unexpected computer or network failure. A well prepared back up regime
Backing up your QuickBooks data file A regular backup regime is essential to minimise disruption to the business should there be an unexpected computer or network failure. A well prepared back up regime
Setting up High Availability
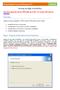 ManageEngine Password Manager Pro Tutorial Setting up High Availability (Procedure applicable only for PMP builds up to 6301. For versions 6302 and later, click here ) Overview Setting up high availability
ManageEngine Password Manager Pro Tutorial Setting up High Availability (Procedure applicable only for PMP builds up to 6301. For versions 6302 and later, click here ) Overview Setting up high availability
Using the Windows XP Backup Wizard. Introduction. Open the Backup Wizard
 Technology Department University of Maryland School of Law Office 8 [email protected] 0-706-77 Introduction A computer crash, hard drive failure or a virus can wipe out everything on your computer.
Technology Department University of Maryland School of Law Office 8 [email protected] 0-706-77 Introduction A computer crash, hard drive failure or a virus can wipe out everything on your computer.
Vembu NetworkBackup v3.1.1 GA
 Vembu NetworkBackup v3.1.1 GA VEMBU TECHNOLOGIES www.vembu.com TRUSTED BY OVER 25,000 BUSINESSES Vembu NetworkBackup v3.1.1 GA - Release Notes With enhanced features and fixes boosting stability and performance,
Vembu NetworkBackup v3.1.1 GA VEMBU TECHNOLOGIES www.vembu.com TRUSTED BY OVER 25,000 BUSINESSES Vembu NetworkBackup v3.1.1 GA - Release Notes With enhanced features and fixes boosting stability and performance,
Higher National Unit specification: general information
 Higher National Unit specification: general information Unit code: H16S 35 Superclass: CB Publication date: March 2012 Source: Scottish Qualifications Authority Version: 01 Unit purpose This Unit is intended
Higher National Unit specification: general information Unit code: H16S 35 Superclass: CB Publication date: March 2012 Source: Scottish Qualifications Authority Version: 01 Unit purpose This Unit is intended
USERS MANUAL FOR OWL A DOCUMENT REPOSITORY SYSTEM
 USERS MANUAL FOR OWL A DOCUMENT REPOSITORY SYSTEM User Manual Table of Contents Introducing OWL...3 Starting to use Owl...4 The Logging in page...4 Using the browser...6 Folder structure...6 Title Bar...6
USERS MANUAL FOR OWL A DOCUMENT REPOSITORY SYSTEM User Manual Table of Contents Introducing OWL...3 Starting to use Owl...4 The Logging in page...4 Using the browser...6 Folder structure...6 Title Bar...6
