EAL4+ Security Target
|
|
|
- Austen Wade
- 10 years ago
- Views:
Transcription
1 EAL4+ Security Target Common Criteria: EAL4 augmented with ALC_FLR.3 Version DEC-10
2 Document management Document identification Document ID Document title Release authority E14_EAL4_ASE Microsoft Exchange 2010 SP1 EAL4 Security Target Amy Blumenfield (amyblu) Product version Exchange 2010 SP1 Enterprise (English) 64-bit (Build: ) Document history Version Date Description DEC-10 Initial release. 2 of 66
3 Table of Contents 1 Security Target introduction (ASE_INT) ST and TOE identification Document organization TOE overview TOE description Logical scope of the TOE Conformance Claim (ASE_CCL) Security problem definition (ASE_SPD) Overview Assumptions Threats Organizational security policies Security objectives (ASE_OBJ) Overview Security objectives for the TOE Security objectives for the IT environment Security objectives for the non-it environment Security requirements (ASE_REQ) Overview SFR conventions Security functional requirements TOE security assurance requirements TOE summary specification (ASE_TSS) Overview Connection Filtering Message filtering Attachment Filtering of 66
4 6.5 Transport Filtering Access Control Identification and Authentication Distribution Group Restriction Remote Device Wipe Rationale Overview Security objectives rationale Security objectives for the IT and non-it environment Security requirements rationale TOE summary specification rationale of 66
5 1 Security Target introduction (ASE_INT) 1.1 ST and TOE identification ST Title ST Version Microsoft Exchange 2010 EAL4+ Security Target 1.0, 21-DEC-10 TOE Reference Microsoft Exchange 2010 SP1 Enterprise (English) 64-bit Build Assurance Level CC Identification EAL4 augmented with ALC_FLR.3 Common Criteria for Information Technology (IT) Security Evaluation, Version 3.1, July 2009, incorporating: Part One Introduction and General Model, Revision Three, July 2009; Part Two Security Functional Components, Revision Three, July 2009; and Part Three Security Assurance Components, Revision Three, July International Standard International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) 15408: Document organization This document is organized into the following sections: Section 1 provides the introductory material for the ST as well as the TOE description including the physical and logical scope of the TOE. Section 2 provides the conformance claims for the evaluation. Section 3 describes the expected environment for the TOE. This section also defines the set of threats that are to be addressed by either TOE security functions or environmental controls. Section 4 defines the security objectives for the TOE and environment. Section 5 contains the functional and assurance requirements derived from the Common Criteria, Part 2 and 3, respectively that must be satisfied by the TOE. 5 of 66
6 Section 6 provides a summary of the TOE, identifying the IT security functions provided by the TOE and also the assurance measures designed to meet the assurance requirements. Section 7 provides a rationale to explicitly demonstrate that security objectives have been satisfied by the TOE. 1.3 TOE overview TOE type and usage The Target of Evaluation (TOE) is Microsoft Exchange 2010 SP1 Enterprise (English) 64-bit (Build ) and is referred to as both Exchange and Exchange 2010 in this document. The TOE is an and collaboration server that provides secure access to personal and shared data for a variety of clients using various protocols TOE security functions The following table highlights the range of security functions and features implemented by the TOE. Security function Connection filtering Message filtering Attachment filtering Transport filtering Access control Identification and authentication Distribution group restriction Remote device wipe Description Protects from unwanted spam or Unsolicited Commercial (UCE) by blocking messages from specified IP addresses. Filters potential spam messages based on Administrator configured SMTP filters, including local and third party block/allow lists. Provides a mechanism to filter potentially harmful attachments. Allows the administrator to define mail policies to prevent specific internal and/or external users from ing each other. Protects mailboxes and public folders from unauthorized access. Provides identification and authentication mechanism for the Outlook Voice Access functionality in cases where Outlook Voice Access is not secured by the use of the TLS protocol. Requires users sending mail to a distribution group to be successfully authenticated and to be authorized. An Administrator can issue a command to wipe a managed Windows Mobile device in the event that the device may have been compromised. 6 of 66
7 Security function Security management Description Provides a set of task based commands for use by an Administrator to manage Microsoft Exchange. 1.4 TOE description Physical scope of the TOE The TOE comprises the Exchange software and is installed on a Windows server operating system supported by suitable hardware. A typical installation of the TOE can be found in Figure 1 below and identifies the various server roles and components of the TOE. The underlying platform for the evaluated version of Exchange is the Windows Server 2008 R2 Enterprise Edition x64 Edition (English) operating system with patches as listed in the Exchange Server Guidance Addendum. This includes Internet protocol support using the Internet Information Services (IIS) component in Windows and the Active Directory for directory services. TOE Boundary TOE Boundary Unified Messaging Role Hub Transport Role Firewall Edge Transport Role IP gateway IP PBX PBX Client Access Role Mailbox Role Firewall PSTN Firewall Internet External Phones Fax Internal Phones Internet Internal Outlook Client External SMTP Server Exchange Activesync Outlook Web App Outlook 7 of 66
8 Figure 1 Exchange 2010 SP1 architecture All roles, with the exception of the Edge Transport Server, can be installed on a single machine; however, for reasons of performance, in medium and large organization installations, these roles may be installed on individual servers. The TOE roles communicate in the same way whether they are installed on one server or many servers. More information about the installation of the TOE is provided in the related guidance documents. The following table describes each of the Exchange Server roles specified in Figure 1 above. Server role Mailbox Server Role Client Access Server Role Unified Messaging Server Role Hub Transport Server Role Description The Mailbox server role hosts mailbox and public folder databases. The administrator manages mail Lifecycle folders and policies from a Mailbox server. The mailbox server role, in conjunction with the environment, provides access control for users, mail, fax, and voice messages. This is the server that hosts the client protocols. The Client Access Server also exposes a Web Services interface for application developers. The Client Access server role accepts connections to the Exchange server from a variety of different clients. See Section for more details on client applications and protocols. Unified Messaging combines voice messaging, fax, calendaring and , which are accessible from a telephone or a computer. The Exchange Unified Messaging server integrates Exchange Server with telephony networks and brings Unified Messaging features to the core of Exchange Server. Outlook Voice Access (OVA) is a feature of the Unified Messaging Role and lets users access their mailbox using telephone communication. OVA can optionally be secured by the Transport Layer Security Protocol (TLS). This is the mail routing server that routes mail within the Exchange organization. The Hub Transport server role handles all mail flow inside the organization, applies transport rules, applies journaling policies, and delivers messages to the recipient's mailbox. Messages that are sent to the Internet are relayed by the Hub Transport server to the Edge Transport server role that is deployed in the perimeter network. 8 of 66
9 Server role Edge Transport Server Role Description This is the mail routing server that sits at the perimeter of the network topology and routes mail into and out of the Exchange organization. The Edge Transport server role handles the following scenarios: Mail Flow - The Edge Transport server role accepts mail coming into the Exchange organization from the Internet and routes all outbound messages to the Internet. Filtering - The Edge Transport server role helps protect the Exchange organization from spam by filtering inbound messages as they arrive and before they are delivered to the internal private network. 1.5 Logical scope of the TOE Supported protocols and clients The TOE offers its services for users via a variety of protocols including: RPC for applications like Microsoft Office Outlook, SMTP for generic clients and servers sending to the TOE, HTTP for Web Browsers (using Outlook Web Access) and for ActiveSync clients, RPC tunneled over HTTP, Web Services Application Programming Interface (API) for in-house applications, and SIP/RTP for Outlook Voice Access (OVA). Outlook Voice Access (OVA) can optionally be secured by enabling the TLS protocol with mutual authentication for SIP/RTP. In this case, the identification and authentication of OVA users is not performed by the TOE but is the sole responsibility of the TLS authenticated application which is part of the IT environment. These protocols can be used to connect to the TOE via different clients. Clients can be categorized into the following groups: Generic Client (also known as Internet Client): A client of this type could be any mail client that uses SMTP to connect to the TOE or a web browser that uses HTTP or Web Services to connect to the TOE. 9 of 66
10 Outlook client: In contrast to the generic clients, an Outlook client uses RPC (or RPC over http) to connect to the TOE. In addition to the above clients, the TOE allows users to connect using a standard or IP telephone via Outlook Voice Access. To use standard telephones, a PBX must be connected to the TOE. A PBX may also forward IP calls. The Unified Messaging server role in Exchange lets users access voice mail, , fax messages, and calendar information located in their Exchange mailbox from an client such as Microsoft Outlook or Outlook Web Access, from a mobile device that has Microsoft Exchange ActiveSync enabled, such as a Windows Mobile powered Smartphone or a personal digital assistant (PDA), or from a telephone. Further, the SMTP protocol can be used by a SMTP server to connect to the TOE. The scope of the TOE ends at the interfaces where it provides its services and does not include any functionality of any client Excluded features The following components and features are considered outside the scope of the evaluation: the IMAP4 and POP3 protocols, all clients that can be used to connect to the TOE, and all externally compiled lists that the TOE relies on for filtering of messages. 10 of 66
11 2 Conformance Claim (ASE_CCL) The ST and TOE are conformant to version 3.1 (Revision 3) of the Common Criteria for Information Technology Security Evaluation. The following conformance claims are made for the TOE and ST: Part 2 conformant. Conformant with Common Criteria for Information Technology Security Evaluation Part 2: Security functional requirements, version 3.1, July Part 3 conformant, EAL4 augmented. Conformant with Common Criteria for Information Technology Security Evaluation Part 3: Security assurance requirements, version 3.1, Revision 3. Evaluation is EAL4 augmented with ALC_FLR of 66
12 3 Security problem definition (ASE_SPD) 3.1 Overview This section describes the nature of the security problem that the TOE is designed to address. The security problem is described through assumptions about the security aspects of the environment and any threats to the assets that the TOE will be providing protection. 3.2 Assumptions Identifier A.COM_PROT A.INSTALL A.PLATFORM Assumption statement It is assumed that the communication channels between all server roles are appropriately secured against eavesdropping and manipulation by physical protection of the wire or by using encryption. Any internet connection to a server role is assumed to be appropriately secured by a firewall. Finally, it is assumed that the connection between the TOE and the user (connecting to the Unified Messaging role, the Mailbox Role, the Hub role, or the Client Access Server role) is appropriately secured by a physical protection of the wire or by using encryption to avoid eavesdropping or manipulation of the communication. It is assumed that the TOE will be delivered, installed, configured and set up in accordance with documented delivery and installation/setup procedures. The platform upon which the TOE resides is Windows Server 2008 R2 Enterprise Edition x64 (English). The platform provides: Access Control to restrict modification to TOE executables, the platform itself, configuration files and databases (mailboxes and public folders) only to the administrators authorized to perform these functions. Functionality for supporting and enforcing Identification and Authentication of users. It is assumed that the platform ensures the identification and authentication of users except for the case that they connect via a non TLS encrypted Outlook Voice Access connection. Methods to store and manage TSF data for the TOE. Further, the platform will provide a role concept for administrative roles and restrict the access to TSF data where necessary. Other than the software necessary for the management and operation of the 12 of 66
13 Identifier A.BLOCKLIST A.NO_EVIL_ADM A.PHYS_PROTECT Assumption statement TOE (e.g. management tools) it is assumed that no untrusted software is installed on the machines the TOE is installed on. It is assumed that the administrator ensures that the machines the TOE is installed on support the secure operation of the TOE. Block/allow lists from third parties which are used to evaluate messages have to be of sufficient quality and trustworthy. Therefore it is assumed that only third party block/allow lists from trustworthy sources will be used and that the download of these block/allow lists is appropriately secured with respect to the integrity and authenticity of the block/allow lists There will be one or more competent administrator(s) assigned to manage the TOE, its platform and the security of the information both of them contain. The administrator(s) are not careless, willfully negligent, nor hostile, and will follow and abide by the instructions provided by the administration documentation. The TOE and its platform will be located within facilities providing controlled access to prevent unauthorized physical access. 3.3 Threats Identifier T.UNAUTH_DAC T.AUTH_DAC Threat statement An unauthenticated user may attempt to read, create, modify or delete information contained in private stores (i.e. mailboxes) or public stores (i.e., public folders), which are managed by the TOE. An attacker may try to get access to mailboxes or public folders although he has no account information and is not authenticated. A user who has been authenticated may attempt to read, delete or modify information contained in another user s private store for which this user has not been authorized. For example: A user could use his account information to authenticate against Windows (the TOE relies on identification and authentication of the operating system). Once authenticated he could try to get unauthorized access to mailboxes belonging to other users of the TOE. 13 of 66
14 T.UNAUTHUSE T.SPAM T.DL_MISUSE An authenticated user may attempt to read, delete or modify information contained in a public folder (e.g. shared folders and documents) that belongs to a group the user is not a member of or is not authorized to use. This scenario is similar to the scenario described in T.AUTH_DAC but in this case the authenticated user tries to get unauthorized access to a public folder instead of a private store, although he is not a member of a group that is allowed to access the folder or is not authorized to use. An attacker could send Unsolicited Commercial (UCE or spam) through the TOE, and have it delivered to mailboxes controlled by the TOE. The threat is an external entity that may send unsolicited messages to TOE users consuming TOE resources or delivering unwanted information to TOE users. For example, this unwanted information may result in an attempt to obtain financial information from the end-user (a phishing attack) An unauthenticated user or an authenticated but unauthorized user may send messages that consume TOE resources by delivering inappropriate , such as UCE to a distribution group. A distribution group may be restricted in a way that only authenticated and authorized users shall be allowed to send messages to a distribution group. An attacker may attempt to send mail for such a distribution group although he is not allowed to deliver to this distribution group. 3.4 Organizational security policies Identifier OSP.MAIL_FLOW OSP.WIPE Organizational security policy statements Administrators shall be able to control flow within their organization. The administrator shall be able to prevent flow between specific senders and recipients based on the flowing characteristics of an sender, recipients, subject, classification, header, attachment name, attachment size, attachment MIME type, importance, and keywords contained in the subject or body. The Administrators should also be able to prevent specific attachments from being sent to, from or around the organization. Administrators shall be able to send wipe commands to supported mobile device platforms. 14 of 66
15 4 Security objectives (ASE_OBJ) 4.1 Overview The security objectives are concise statements of the TOE s response to the security problem. Some objectives are to be achieved through the security functionality of the TOE and some elements of the problem will be addressed through the establishment of a secure environment in which the TOE must operate. 4.2 Security objectives for the TOE Identifier O.DAC Objective statements The TOE shall prevent unauthorized access to objects maintained in the Exchange Store (i.e. mailboxes, public folders) based on the identity of the user. Therefore the TOE shall provide discretionary access controls to private mailboxes and public folders so that only authorized users can read, modify or delete messages and documents. O.CONBLK To keep the level of spam as low as possible, the TOE shall provide the ability to reject an SMTP connection based on the IP address or hostname of the remote SMTP sender using accept and block/allow lists configurable by the administrator. The TOE shall further be able to calculate a reputation level for SMTP servers that express how likely this server is used for SPAM. The TOE shall be able to block messages based on the sending server s reputation level. O.RESTDIST O.REDUCE_SPAM O.MAIL_FLOW The TOE shall allow Administrators to restrict mail routing to distribution groups 1 by only allowing mail to be delivered to the distribution group from authenticated and authorized users. Also, Administrators can specify which users can or cannot send mail to specific distribution groups. The TOE shall allow Administrators to reduce unwanted or unsolicited mail (UCE or spam) by providing a filter mechanism based on the sender and receiver information of an . The TOE shall allow Administrators to control flow within their organization. The TOE will provide the administrator with filters to prevent 1 A distribution group may be either a statically defined group in the Active Directory or created dynamically based on a LDAP query. 15 of 66
16 Identifier Objective statements flow between specific senders and receivers based on the following characteristics of an sender, recipients (including copied recipients), subject, classification, header, attachment name, attachment size, importance and also keywords contained in the subject or body. Also, the TOE will allow Administrators to prevent specific types of attachments (characterized by the extension or the MIME type of the attachment) from being sent to, from or around the organization. O.I&A O.WIPE The TOE shall provide an identification and authentication mechanism for users using Outlook Voice Access in cases the access is not secured by TLS 2. The resulting information about the identity of the user is then used by other policies of the TOE. The TOE shall be able to send remote wipe commands to compatible mobile device platforms. Note: The action of the device on receipt of the command is dependent on the platform and configuration and considered out of scope. 4.3 Security objectives for the IT environment Identifier OE.PLATFORM Objective statements The platform upon which the TOE resides shall be Windows Server 2008R2 Enterprise Edition x64 (English).The platform provides: Access Control to restrict modification to TOE executables, the platform itself, configuration files and databases (mailboxes and public folders) only to the authorized administrators. Functionality for supporting and enforcing Identification and Authentication of users. The platform shall ensure the identification and authentication of users except for the case that they connect via a non TLS encrypted Outlook Voice Access connection. Methods to store and manage TSF data for the TOE. Further, the platform will provide a role concept for administrative roles and restrict access to TSF data where necessary. 2 In case of a connection that is secured via a mutually authenticated TLS channel, the environment will be responsible for the identification and authentication of the user. 16 of 66
17 4.4 Security objectives for the non-it environment Identifier OE.COM_PROT OE.INSTALL Objective statements The administrator of the TOE shall ensure that the communication channels between all server roles are appropriately secured against eavesdropping and manipulation by physical protection of the wire or by using encryption. Any internet connection to a server role shall be appropriately secured by a firewall. The administrator shall ensure that the connection between the TOE and the user is appropriately secured by a physical protection of the wire or by using encryption to avoid eavesdropping or manipulation of the communication. The TOE shall be delivered, installed, configured and set up in accordance with documented delivery and installation/setup procedures and only by trustworthy staff. The administrator must ensure that the TOE is delivered, installed, configured, managed and operated in a manner that is consistent with IT security. Beside the software necessary for the management and operation of the TOE (e.g. management tools) no untrusted software shall be installed on the machines the TOE is installed on. The administrator(s) shall ensure during TOE installation and operation - that the platform the TOE is running on allows the secure operation of the TOE. OE.BLOCKLIST Block/allow lists from third parties - which are used to evaluate messages - have to be of sufficient quality and trustworthy. Therefore, the administrator shall ensure that only third party block/allow lists from trustworthy sources will be used and that the download of these block/allow lists is appropriately secured with respect to the integrity and authenticity of the block/allow lists OE.PHYSICAL The administrators shall ensure that those parts of the TOE and its platform that are critical to security policy are protected from any physical attack. 17 of 66
18 5 Security requirements (ASE_REQ) 5.1 Overview This section defines the security requirements satisfied by the TOE. Each requirement has been extracted from version 3.1 of the Common Criteria, part 2 providing functional requirements and part 3 providing assurance requirements. 5.2 SFR conventions Part 2 of the Common Criteria defines an approved set of operations that may be applied to security functional requirements. Following are the approved operations and the document conventions that are used within this ST to depict their application: Assignment. The assignment operation provides the ability to specify an identified parameter within a requirement. Assignments are depicted using bolded text and are surrounded by square brackets as follows [assignment]. Selection. The selection operation allows the specification of one or more items from a list. Selections are depicted using bold italics text and are surrounded by square brackets as follows [selection]. Refinement. The refinement operation allows the addition of extra detail to a requirement. Refinements are indicated using bolded text, for additions, and strike-through, for deletions. Iteration. The iteration operation allows a component to be used more than once with varying operations. Iterations are depicted by placing a letter at the end of the component identifier as follows FDP_IFF.1a and FDP_IFF.1b. 18 of 66
19 5.3 Security functional requirements Overview The security functional requirements are expressed using the notation stated in Section 5.2 and summarized in the table below. Identifier FDP_ACC.1a FDP_ACC.1b FDP_ACF.1a FDP_ACF.1b FDP_IFC.1a FDP_IFC.1b FDP_IFC.1c FDP_IFC.1d FDP_IFC.1e FDP_IFF.1a FDP_IFF.1b FDP_IFF.1c FDP_IFF.1d FDP_IFF.1e FIA_SOS.1 FIA_UAU.2 FIA_UID.2 FIA_USB.1 FMT_MOF.1 Title Subset access control (Folder) Subset access control (Group) Security attribute based access control (Folder) Security attribute based access control (Group) Subset information flow control (Connect) Subset information flow control (SRL) Subset information flow control (Message) Subset information flow control (AttachmentFilter) Subset information flow control (Transport) Simple security attributes (Connect) Simple security attributes (SRL) Simple security attributes (Message) Simple security attributes (AttachmentFilter) Simple security attributes (Transport) Verification of secrets User authentication before any action User identification before any action User-subject binding Management of security functions behavior (Remote Wipe) 19 of 66
20 Identifier FMT_SMF.1 FMT_MSA.1 FMT_MSA.3a FMT_MSA.3b FMT_MSA.3c FMT_MSA.3d FMT_MSA.3e FMT_MSA.3f FMT_MSA.3g Title Specification of Management Functions Management of security attributes Static attribute initialization (Folder) Static attribute initialization (Group) Static attribute initialization (Connect) Static attribute initialization (SRL) Static attribute initialization (Message) Static attribute initialization (AttachmentFilter) Static attribute initialization (Transport) 20 of 66
21 5.3.2 FDP_ACC.1a Subset access control (Folder) Hierarchical to: No other components. FDP_ACC.1a.1 The TSF shall enforce the [Discretionary Access Control SFP] on [ Subjects: a) processes acting on behalf of users Objects: a) Mailbox, public folder items 3 and (sub)folders Mailbox operations: a) List folder b) Create subfolder c) Create item d) Read item e) Edit item f) Delete item g) Modify folder permissions h) Send item Public folder operations: a) List Folder b) Create subfolder c) Create item d) Read item e) Edit item f) Delete item g) Modify folder permissions]. Dependencies: Notes: FDP_ACF.1 - Security attribute based access control None. 3 Mailbox and public folder items include all objects that are stored in a mailbox or public folder (e.g. s, contacts or certificates) 21 of 66
22 5.3.3 FDP_ACC.1b Subset access control (Group) Hierarchical to: No other components. FDP_ACC.1b.1 The TSF shall enforce the [Distribution Group Restriction SFP] on [ Subjects: a) users sending objects: a) distribution groups operation: a) use, i.e. send messages to a distribution group]. Dependencies: Notes: FDP_ACF.1 - Security attribute based access control None FDP_ACF.1a Security attribute based access control (Folder) Hierarchical to: FDP_ACF.1a.1 No other components. The TSF shall enforce the [Discretionary Access Control SFP] to objects based on the following: [ Subject attribute: a) ID 4 of the user and its corresponding role Object attributes: a) Object name b) Owner of the folder]. FDP_ACF.1a.2 The TSF shall enforce the following rules to determine if an operation among controlled subjects and controlled objects is allowed: [ The operation is allowed if the ID of the user is linked 5 to a role permitted to perform the request operation on the object.]. FDP_ACF.1a.3 The TSF shall explicitly authorize access of subjects to objects based on the 4 The ID of the current user is provided by the Windows Operating System or by the authentication policy as expressed in FIA_UAU.2 (only when the user is connected via non-tls secured Outlook Voice Access). 5 The link from a user ID to a role may not be direct. A user may be linked to a role assignment which is then linked to an enduser role. 22 of 66
23 following additional rules: [None]. FDP_ACF.1a.4 Dependencies: Notes: The TSF shall explicitly deny access of subjects to objects based on the following additional rules: [None]. FDP_ACC.1 Subset access control FMT_MSA.3 Static attribute initialization None FDP_ACF.1b Security attribute based access control (Group) Hierarchical to: FDP_ACF.1b.1 FDP_ACF.1b.2 No other components. The TSF shall enforce the [Distribution Group Restriction SFP] to objects based on the following: [ Object attributes (distribution groups): a) Message Delivery Restrictions Subject attribute: 1. Require that all senders are authenticated restriction 2. Accept messages from a specific list of senders list 3. Reject messages from a specific list of senders list]. a) ID of the user and its corresponding role b) Authentication status within exchange]. The TSF shall enforce the following rules to determine if an operation among controlled subjects and controlled objects is allowed: [ The operation is allowed, if: a) the require that all senders are authenticated is set to false; or b) the require that all senders are authenticated is set to true and the subject is authenticated (i.e. the corresponding ID is available), and a) the ID of the sending user is in the Accept messages from a specific list of senders list and not the Reject messages from a specific list of senders list]. FDP_ACF.1b.3 The TSF shall explicitly authorize access of subjects to objects based on the following additional rules: [None]. 23 of 66
24 FDP_ACF.1b.4 Dependencies: Notes: The TSF shall explicitly deny access of subjects to objects based on the following additional rules: [None]. FDP_ACC.1 Subset access control FMT_MSA.3 Static attribute initialization None FDP_IFC.1a Subset information flow control (Connect) Hierarchical to: No other components. FDP_IFC.1a.1 The TSF shall enforce the [Connection Filtering SFP] on [ Subjects: a) External SMTP Servers b) Edge Transport Server Role Information: a) messages Operations: a) transfer]. Dependencies: Notes: FDP_IFF.1 Simple security attributes None FDP_IFC.1b Subset information flow control (SRL) Hierarchical to: No other components. FDP_IFC.1b.1 The TSF shall enforce the [Sender Reputation SFP] on [ Subjects: a) External SMTP Servers b) Edge Transport Server Role Information: a) messages Operations: a) transfer]. 24 of 66
25 Dependencies: Notes: FDP_IFF.1 Simple security attributes None FDP_IFC.1c Subset information flow control (Message) Hierarchical to: No other components. FDP_IFC.1c.1 The TSF shall enforce the [Message Filtering SFP] on [ Subjects: a) External SMTP Servers b) Edge Transport Server Role Information: a) messages Operations: a) transfer]. Dependencies: Notes: FDP_IFF.1 Simple security attributes None FDP_IFC.1d Subset information flow control (AttachmentFilter) Hierarchical to: No other components. FDP_IFC.1d.1 The TSF shall enforce the [Attachment SFP] on [ Subjects: a) External SMTP Servers b) Edge Transport Server Role Information: a) messages Operations: a) transfer]. Dependencies: Notes: FDP_IFF.1 Simple security attributes None. 25 of 66
26 FDP_IFC.1e Subset information flow control (Transport) Hierarchical to: No other components. FDP_IFC.1e.1 The TSF shall enforce the [Hub Transport SFP] on [ Subjects: a) Hub Transport Server Role Information: a) messages Operations: a) transfer]. Dependencies: Notes: FDP_IFF.1 Simple security attributes None FDP_IFF.1aSimple security attributes (Connect) Hierarchical to: FDP_IFF.1a.1 FDP_IFF.1a.2 No other components. The TSF shall enforce the [Connection Filtering SFP] based on the following types of subject and information security attributes: [ Subject attributes: a) IP address of the external SMTP server b) allow/block lists of the Edge Transport Server Role c) list of exceptional recipients 6 of the Edge Transport Server Role Information attributes: a) recipients of the ]. The TSF shall permit an information flow between a controlled subject and controlled information via a controlled operation if the following rules hold: [None]. FDP_IFF.1a.3 The TSF shall enforce the additional ordered rules [ a) If the IP address of the sending external SMTP server is listed on a local allow list, the message will be accepted 6 Exceptional Recipients are recipients within the Exchange Organization which are permitted to receive s from senders on the block lists. Exceptional recipients must be explicitly added as exceptions to block lists, 26 of 66
27 b) If the IP address of the sending external SMTP server is listed on a local block list, the message will be rejected c) If the IP address of the sending external SMTP server is listed on a remote allow list, the message will be accepted d) If one of the recipients of the is on the local list of exceptional recipients the message will be accepted e) If the IP address of the sending external SMTP server is listed on a remote block list, the message will be rejected f) Else the message will be accepted]. FDP_IFF.1a.4 FDP_IFF.1a.5 Dependencies: Notes: The TSF shall explicitly authorize an information flow based on the following rules: [None]. The TSF shall explicitly deny an information flow based on the following rules: [None]. FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization This functionality utilizes the following kinds of allow and block lists: a) Local allow and block lists maintained by Administrators b) Remote allow and block lists retrieved from external service providers (so called block list service providers ) c) A local list of exceptional recipients. The remote lists are not considered to be Security Attributes in the context of this policy as they are not stored locally FDP_IFF.1b Simple security attributes (SRL) Hierarchical to: FDP_IFF.1b.1 No other components. The TSF shall enforce the [Sender Reputation SFP] based on the following types of subject and information security attributes: [ Subject attributes a) Sender Reputation Level (SRL) of the external SMTP server (calculated by the TOE) b) SRL Threshold c) local list of SRL values from the Edge Transport Server Role Information attributes: a) None]. 27 of 66
28 FDP_IFF.1b.2 FDP_IFF.1b.3 FDP_IFF.1b.4 FDP_IFF.1b.5 Dependencies: Notes: The TSF shall permit an information flow between a controlled subject and controlled information via a controlled operation if the following rules hold: [None]. The TSF shall enforce the [additional rules If: a) the local list of SRL values contains an entry for the external SMTP server with a SRL value greater than or equal to the SRL threshold; or b) The SRL value (calculated by the TOE) for the external SMTP server is greater than or equals the SRL Threshold; the server will be added to the local block list of FDP_IFF.1a (Connect) for an Authorized Administrator configurable period of time]. The TSF shall explicitly authorize an information flow based on the following rules: [None]. The TSF shall explicitly deny an information flow based on the following rules: [None]. FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization None FDP_IFF.1c Simple security attributes (Message) Hierarchical to: FDP_IFF.1c.1 No other components. The TSF shall enforce the [Message Filtering SFP] based on the following types of subject and information security attributes: [ Subject attributes: a) sender and recipient filtering lists from the Edge Transport Server Role b) local address book 7 from the Edge Transport Server Role Information attributes: a) MAIL FROM: field of the RFC 2821 envelope b) RFC 2822 header c) RCPT TO: field of the RFC 2821 envelope]. 7 The local address book is a list of local SMTP addresses. 28 of 66
29 FDP_IFF.1c.2 The TSF shall permit an information flow between a controlled subject and controlled information via a controlled operation if the following rules hold: [ The will be accepted unless: a) the sender listed in the MAIL FROM: field of the (RFC 2821) message envelope is on the sender filtering list or b) the sender in the FROM header of the message (RFC 2822) is on the sender filtering list or c) the MAIL FROM: field of the RFC 2821 message envelope is blank 8 and the FROM header of the message (RFC 2822) does not contain a valid e- mail address 9 or d) the recipient listed in the RCPT TO: field of the RFC 2821 message envelope is on the recipient filtering list or e) the recipient does not exist in the local address book]. FDP_IFF.1c.3 FDP_IFF.1c.4 FDP_IFF.1c.5 Dependencies: The TSF shall enforce the [None]. The TSF shall explicitly authorize an information flow based on the following rules: [None]. The TSF shall explicitly deny an information flow based on the following rules: [None]. FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization Notes: None FDP_IFF.1d Simple security attributes (AttachmentFilter) Hierarchical to: FDP_IFF.1d.1 No other components. The TSF shall enforce the [Attachment SFP] based on the following types of subject and information security attributes: [ Subject attributes: a) Attachment Policy of the Edge Transport Server Role Information attributes: 8 As this field can never be completely empty, the term blank refers to a so called null address which is a MAIL FROM field that contains the characters "<>" 9 A valid address in this context means a string in the structure of [recipient]@[domain].[top level domain] 29 of 66
30 a) MIME Type b) extension of the attachment]. FDP_IFF.1d.2 FDP_IFF.1d.3 FDP_IFF.1d.4 FDP_IFF.1d.5 Dependencies: Notes: The TSF shall permit an information flow between a controlled subject and controlled information via a controlled operation if the following rules hold: [ The information flow is permitted if not explicitly prohibited by the Attachment policy]. The TSF shall enforce the [additional rule: Attachments will be stripped or s containing attachments will be blocked in accordance with the Attachment policy]. The TSF shall explicitly authorize an information flow based on the following rules: [None]. The TSF shall explicitly deny an information flow based on the following rules: [None]. FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization The attachment policy as defined in FDP_IFF.1d (AttachmentFilter) comprises a set of ordered rules that are defined by the administrator of the TOE. These rules are evaluated in order to determine how an attachment shall be handled. The MIME type and Attachment extension information attributes are used by these rules to define whether a rule shall be applied to an attachment. Each rule is comprised of: a) A set of criteria that defines the attachments to which the rule shall apply (based on MIME type and Attachment extension). b) A set of exceptions to which the rule shall not be applied. c) An action to perform when an attachment meets the rule criteria FDP_IFF.1e Simple security attributes (Transport) Hierarchical to: FDP_IFF.1e.1 No other components. The TSF shall enforce the [Hub Transport SFP] based on the following types of subject and information security attributes: [ subject attributes: a) Hub Transport Policy of the Hub Transport Server Role Information attributes: a) Sender 30 of 66
31 b) Recipients c) CC: d) Subject e) Classification f) Header g) Attachment Name h) Attachment Size i) Attachment extension j) Importance k) Key words in Subject or body]. FDP_IFF.1e.2 FDP_IFF.1e.3 FDP_IFF.1e.4 FDP_IFF.1e.5 Dependencies: Notes: The TSF shall permit an information flow between a controlled subject and controlled information via a controlled operation if the following rules hold: [None]. The TSF shall enforce the [following additional rule: For each the Hub Transport policy shall be evaluated and each rule that fits to the shall be applied]. The TSF shall explicitly authorize an information flow based on the following rules: [None]. The TSF shall explicitly deny an information flow based on the following rules: [None]. FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization The Hub transport policy as defined in FDP_IFF.1e (Transport) comprises a set of ordered rules that are defined by the administrator of the TOE. The rules are evaluated in order to determine how an message shall be handled. Each rule is comprised of: a) A set of criteria that define the mails to which the rule shall be applied (based on the information attributes). b) A set of exceptions to which the rule shall not be applied. c) An action to perform when a mail meets the rule criteria. 31 of 66
32 FIA_SOS.1 Verification of secrets Hierarchical to: No other components. FIA_SOS.1.1 The TSF shall provide a mechanism to verify that secrets meet [ Outlook Voice Access PIN quality metrics as defined by the administrator including an Outlook Voice Access PIN of at least 8 digits]. Dependencies: Notes: No dependencies. The Outlook Voice Access PINs are the only secrets maintained by the TOE in the context of this requirement FIA_UAU.2User authentication before any action Hierarchical to: FIA_UAU.2.1 Dependencies: Notes: FIA_UAU.1 Timing of authentication The TSF shall require each user connecting via non TLS-secured Outlook Voice Access to be successfully authenticated before allowing any other TSF-mediated actions on behalf of that user. FIA_UID.1 Timing of identification The environment is responsible for user authentication prior to any action for users connecting via RPC, SMTP, HTTP, RPC over HTTP, Web Services, TLS-secured OVA FIA_UID.2User identification before any action Hierarchical to: FIA_UID.2.1 Dependencies: Notes: FIA_UID.1 Timing of identification The TSF shall require each user connecting via non TLS-secured Outlook Voice Access to be successfully identified before allowing any other TSF-mediated actions on behalf of that user. No dependencies. The environment is responsible for user identification prior to any action for users connecting via RPC, SMTP, HTTP, RPC over HTTP, Web Services, TLS-secured OVA. 32 of 66
33 FIA_USB.1User-subject binding Hierarchical to: FIA_USB.1.1 FIA_USB.1.2 FIA_USB.1.3 Dependencies: Notes: No other components. The TSF shall associate the following user security attributes with subjects acting on the behalf of that user: [ a) ID (user s identity) b) Group Memberships]. The TSF shall enforce the following rules on the initial association of user security attributes with subjects acting on the behalf of users: [None]. The TSF shall enforce the following rules governing changes to the user security attributes associated with subjects acting on the behalf of users: [None]. FIA_ATD.1 User attribute definition None FMT_MOF.1 Management of security functions behavior (Remote Wipe) Hierarchical to: No other components. FMT_MOF.1.1 The TSF shall restrict the ability to [modify the behavior of] the functions [ a) Issue the remote wipe command. ] to [Authorized Administrators]. Dependencies: Notes: FMT_SMR.1 Security roles FMT_SMF.1 Specification of Management Functions None FMT_SMF.1 Specification of Management Functions Hierarchical to: No other components. FMT_SMF.1.1 The TSF shall be capable of performing the following management functions: [ a) Management of security attributes for the Discretionary Access Control SFP (FDP_ACC.1a (Folder)) b) Management of security attributes for the Distribution Group 33 of 66
34 Restriction SFP (FDP_ACC.1b (Group)) c) Management of security attributes for the Message Filtering SFP (FDP_IFF.1c (Message)) d) Management of security attributes for the Connection Filtering SFP(FDP_IFF.1a (Connect)) e) Management of security attributes for the Sender Reputation SFP (FDP_IFF.1b (SRL)) f) Management of security attributes for the Attachment SFP (FDP_IFF.1d (AttachmentFilter)) g) Management of security attributes for the Hub Transport SFP (FDP_IFF.1e (Transport)) h) Management of attributes for authentication via Outlook Voice Access (FIA_UAU.2) i) Management of quality metric for user PINs (FIA_SOS.1) j) Issue a remote wipe command to a Windows Mobile Device (FMT_MOF.1)]. Dependencies: Notes: No dependencies. None FMT_MSA.1 Management of security attributes Hierarchical to: FMT_MSA.1.1 Dependencies: Notes: No other components. The TSF shall enforce the [All access control and information flow control SFPs] to restrict the ability to [query, modify, delete, change default] the security attributes [RBAC Roles] to [Authorized Administrators and Users with the appropriate role assignment]. [FDP_ACC.1 Subset access control, or FDP_IFC.1 Subset information flow control] FMT_SMR.1 Security roles FMT_SMF.1 Specification of Management Functions None. 34 of 66
35 FMT_MSA.3a Static attribute initialization (Folder) Hierarchical to: FMT_MSA.3a.1 FMT_MSA.3a.2 Dependencies: Notes: No other components. The TSF shall enforce the [Discretionary Access Control SFP] to provide [restrictive] default values for security attributes that are used to enforce the SFP. The TSF shall allow the [nobody] to specify alternative initial values to override the default values when an object or information is created. FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles Every user with an Exchange mailbox, including administrators, is given a role assignment policy by default. Administrators can decide which role assignment policy should be assigned by default, choose what the default role assignment policy should include, override the default for certain mailboxes, or not assign role assignment policies by default at all FMT_MSA.3b Static attribute initialization (Group) Hierarchical to: FMT_MSA.3b.1 FMT_MSA.3b.2 Dependencies: Notes: No other components. The TSF shall enforce the [Distribution Group Restriction SFP] to provide [administratively defined] default values for security attributes that are used to enforce the SFP. The TSF shall allow the [Authorized Administrator and users with the appropriate role] to specify alternative initial values to override the default values when an object or information is created. FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles None. 35 of 66
36 FMT_MSA.3c Static attribute initialization (Connect) Hierarchical to: FMT_MSA.3c.1 FMT_MSA.3c.2 Dependencies: Notes: No other components. The TSF shall enforce the [Connection Filtering SFP] to provide [permissive] default values for security attributes that are used to enforce the SFP. The TSF shall allow the [Authorized Administrator and users with the appropriate role] to specify alternative initial values to override the default values when an object or information is created. FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles None FMT_MSA.3d Static attribute initialization (SRL) Hierarchical to: FMT_MSA.3d.1 FMT_MSA.3d.2 Dependencies: No other components. The TSF shall enforce the [Sender Reputation SFP] to provide [permissive] default values for security attributes that are used to enforce the SFP. The TSF shall allow the [Authorized Administrator and users with the appropriate role] to specify alternative initial values to override the default values when an object or information is created. FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles Notes: Here permissive means an SRL threshold of FMT_MSA.3e Static attribute initialization (Message) Hierarchical to: FMT_MSA.3e.1 FMT_MSA.3e.2 Dependencies: No other components. The TSF shall enforce the [Message Filtering SFP] to provide [permissive] default values for security attributes that are used to enforce the SFP. The TSF shall allow the [Authorized Administrator and users with the appropriate role] to specify alternative initial values to override the default values when an object or information is created. FMT_MSA.1 Management of security attributes 36 of 66
37 FMT_SMR.1 Security roles Notes: None FMT_MSA.3f Static attribute initialization (AttachmentFilter) Hierarchical to: FMT_MSA.3f.1 FMT_MSA.3f.2 Dependencies: Notes: No other components. The TSF shall enforce the [Attachment SFP] to provide [restrictive] default values for security attributes that are used to enforce the SFP. The TSF shall allow the [Authorized Administrator and users with the appropriate role] to specify alternative initial values to override the default values when an object or information is created. FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles None FMT_MSA.3g Static attribute initialization (Transport) Hierarchical to: FMT_MSA.3g.1 FMT_MSA.3g.2 Dependencies: Notes: No other components. The TSF shall enforce the [Hub Transport SFP] to provide [permissive] default values for security attributes that are used to enforce the SFP. The TSF shall allow the [Authorized Administrator and users with the appropriate role] to specify alternative initial values to override the default values when an object or information is created. FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles In the context of this ST, the functionality required by FMT_MSA.3.2 shall be seen in the way that the TOE does not provide any functionality to change the default values rather than restricting the access to such functionality. 37 of 66
38 5.4 TOE security assurance requirements The assurance package for the evaluation of Exchange 2010 is Evaluation Assurance Level 4 (EAL4), augmented by the life cycle support component that provides systematic flaw remediation (ALC_FLR.3). EAL4 assurance requirements provide confidence in the security functionality of the TOE by analysis using a functional and interface specification, guidance documentation and the high-level design of the TOE to understand the security behavior. The analysis is supported by independent testing of the TOE security functions, evidence of developer testing based on the functional specification, selective independent confirmation of the developer test results, strength of function analysis, and evidence of a developer search for obvious vulnerabilities. EAL4 also provides assurance through a configuration list for the TOE, and evidence of secure delivery procedures. The table below provides a summary of the TOE security assurance requirements for this evaluation. Complete details of all assurance components are located in part 3 of the Common Criteria. Assurance class ADV: Development Assurance components ADV_ARC.1 Security architecture description ADV_FSP.4 Complete functional specification ADV_IMP.1 Implementation representation of the TSF ADV_TDS.3 Basic Modular Design AGD: Guidance documents AGD_OPE.1 Operational user guidance AGD_PRE.1 Preparative procedures ALC: Life cycle support ALC_CMC.4 Production support, acceptance procedures and automation ALC_CMS.4 Problem tracking CM coverage ALC_DEL.1 Delivery procedures ALC_DVS.1 Identification of security measures ALC_FLR.3 Systematic flaw remediation ALC_LCD.1 Developer defined life-cycle model 38 of 66
39 Assurance class Assurance components ALC_TAT.1 Well-defined development tools ASE: Security Target evaluation ASE_CCL.1 Conformance claims ASE_ECD.1 Extended components definition ASE_INT.1 ST Introduction ASE_OBJ.2 Security objectives ASE_REQ.2 Derived security requirements ASE_SPD.1 Security problem definition ASE_TSS.1 TOE summary specification ATE: Tests ATE_COV.2 Analysis of coverage ATE_DPT.1 Testing: basic design ATE_FUN.1 Functional testing ATE_IND.2 Independent testing sample AVA: Vulnerability assessment AVA_VAN.3 Focused vulnerability analysis 39 of 66
40 6 TOE summary specification (ASE_TSS) 6.1 Overview This section provides the TOE summary specification, a high-level definition of the security functions claimed to meet the functional and assurance requirements. The TOE security functions include the following: Connection Filtering. The TOE protects from unwanted spam or Unsolicited Commercial (UCE) by blocking messages from specified IP addresses. Message Filtering. Filters potential spam messages based on Administrator configured SMTP filters, including local and third party block/allow lists. Attachment Filtering. Provides a mechanism to filter potentially harmful attachments from external networks. Transport Filtering. Allows the administrator to define mail policies to prevent specific internal and/or external users from ing each other Access Control. Protects mailboxes and public folders from unauthorized access. Identification and Authentication. Provides identification and authentication mechanism for the Outlook Voice Access functionality in cases where Outlook Voice Access is not secured by the use of the TLS protocol. Distribution Group Restriction. Requires users sending mail to a distribution group to be successfully authenticated and to be authorized. Remote device wipe. An Administrator can issue a command to wipe a Windows Mobile device in the event that the device may have been compromised. Security Management. Provides a set of task based commands for use by an Administrator to manage Microsoft Exchange. As security management pertains to the configuration and management of the remaining security functions, details are included within the description of each of these security functions.. 40 of 66
41 6.2 Connection Filtering Exchange will reject SMTP connections based on IP address of the connecting external SMTP server 10. To do so, Exchange references allow lists, block lists and a list of exceptional recipients. These lists which may contain IP addresses or IP address ranges. The TOE references local and remote allow and block lists. Local lists are defined by an authorized Administrator while remote allow and block lists are retrieved from external service providers (so called block list service providers). When an SMTP connection is established, Exchange enforces the following ordered rules, according to the IP address of the external SMTP server: If the IP address of the sending SMTP server is listed on a local allow list, the message will be accepted; If the IP address of the sending SMTP server is listed on a local block list, the message will be rejected; If the IP address of the sending SMTP server is listed on a remote allow list, the message will be accepted; If one of the recipients of the is on the local list of exception recipients, the message will be accepted; If the IP address of the sending SMTP server is listed on a remote block list, the message will be rejected; Else the message will be accepted. By default, the local allow and block lists that are used in this Security Function are empty. The TOE also calculates the Sender Reputation Level (SRL) of a remote SMTP server after at least 20 mails have been received from this server. This SRL is a numeric value between 0 and 9 that serves as an indicator of how likely the sending server is a spammer. Further, the environment of the TOE maintains a local list of SRL values for known SMTP servers. This list is updated on a regular basis. 10 An external SMTP server is an SMTP server logically outside the Exchange organization that connects to an Edge Server. 41 of 66
42 If the local SRL for a sending SMTP server or the calculated SRL has reached or exceeded an administrator configurable value (the SRL Threshold which is 7 by default), the SMTP server will be added to the local block list for an administrator defined period of time. Functional Requirements Satisfied: FDP_IFC.1a (Connect), FDP_IFC.1b (SRL), FDP_IFF.1a (Connect), FDP_IFF.1b (SRL),FMT_MSA.3c (Connect) and FMT_MSA.3d (SRL). Security Management for Connection Filtering: The TOE will provide functionality to: manage local allow and block lists, manage the list of exceptional recipients, manage the use of remote block and allow lists, manage the use of the list of local SRL values, and configure SRL threshold settings and the period of time for which servers exceeding the threshold will be added to the block list. 6.3 Message filtering Exchange allows the administrators to configure the TOE to reduce spam received by an organization. The Message Filter will accept or reject messages based on the rules of the following policies. By default, messages will be accepted by this policy. Messages will be rejected if: the sender listed in the MAIL FROM: field of the RFC 2821 message envelope is on the sender filtering list, or the sender in the FROM header of the message (RFC 2822) is on the sender filtering list, or the MAIL FROM: field of the RFC 2821 message envelope is blank 11 and the FROM header of the message (RFC 2822) does not contain a valid address, or the recipient listed in the RCPT TO: field of the RFC 2821 message envelope is on the recipient filtering list, or 11 As this field can never be completely empty the term blank refers to a so called null address which is a MAIL FROM field that contains only the characters "<>" 42 of 66
43 the recipient does not exist in the local address book Finally, the TOE evaluates the SPF record for the sending domain and stamps the result on the message. This SPF record is published by domain servers in addition to their standard DNS information and identifies the machines that are allowed to send s on behalf of the domain. In this way, the SPF record can help to identify forged addresses. By default, the sender and recipient filtering list for this Security Function are empty. Functional Requirements Satisfied: FDP_IFC.1c (Message), FDP_IFF.1c (Message), and FMT_MSA.3e (Message). Security Management for Message Filtering: The TOE will provide functionality to manage sender and recipient filtering lists. 6.4 Attachment Filtering The TOE applies an attachment filter to incoming mail based on the attachments. The TOE provides the administrator the ability to specify that messages that contain a specified attachment or attachment type be subject to a predefined action. The Administrator can choose to block the whole message while optionally advising the sender that the message was not delivered, or remove the attachment and deliver the message. This policy is defined by the Administrator based on the Attachment MIME Type or the Attachment extension. The default policy is to remove all attachments of the following MIME types and extensions: MIME Type: application/x-msdownload, message/partial, text/scriptlet, application/prg, application/msaccess, text/javascript, application/x-javascript, application/javascript, x-internetsignup, application/hta Extensions: *.xnk, *.wsh, *.wsf, *.wsc, *.vbs, *.vbe, *.vb, *.url, *.shs, *.shb, *.sct, *.scr, *.scf, *.reg, *.prg, *.prf, *.pif, *.pcd, *.ops, *.mst, *.msp, *.msi, *.psc2, *.psc1, *.ps2xml, *.ps2, *.ps11xml, *.ps11, *.ps1xml, *.ps1, *.msc, *.mdz, *.mdw, *.mdt, *.mde, *.mdb, *.mda, *.lnk, *.ksh, *.jse, *.js, *.isp, *.ins, *.inf, *.hta, *.hlp, *.fxp, *.exe, *.csh, *.crt, *.cpl, *.com, *.cmd, *.chm, *.bat, *.bas, *.asx, *.app, *.adp, *.ade. Functional Requirements Satisfied: FDP_IFC.1d (AttachmentFilter), FDP_IFF.1d (AttachmentFilter), and FMT_MSA.3f (AttachmentFilter). 43 of 66
44 Security Management for Attachment Filtering: The TOE will provide functionality to manage the Attachment Filtering Policy. This functionality will allow authorized Administrators to add or delete rules to the Attachment Filtering Policy. 6.5 Transport Filtering The TOE allows an administrator to configure a set of ordered rules that can be applied to all messages passing through the Hub Transport server role. The Hub server will evaluate all the rules in order and execute any rules that apply. By default, no rules exist for this policy initially. The administrator can define rules for messages based on the following attributes of an Sender, Recipients, CC:, Subject, Classification, Header, Attachment name, Attachment size, Attachment extension, Importance, and Key words in Subject or body. Functional Requirements Satisfied: FDP_IFC.1e (Transport), FDP_IFF.1e (Transport), and FMT_MSA.3g (Transport). Security Management for Transport Filtering: The TOE will provide functionality to manage the Hub Transport Policy. This functionality will allow authorized Administrators to add or delete rules to the Hub Transport Policy. 44 of 66
45 6.6 Access Control The TOE uses Role Based Access Control (RBAC) permissions for the Mailbox, Hub Transport, Unified Messaging, and Client Access server roles. RBAC has two primary ways of assigning permissions to users in the organization, depending on whether the user is an administrator or specialist user, or an enduser: management role groups and management role assignment policies. Each method associates users with the permissions to control access to all functions and data within the TOE. Permissions available for the mailbox and public folders include: Mailbox permissions: The AccessRights parameter specifies the rights needed to perform the operation. Valid values include: FullAccess SendAs ExternalAccount DeleteItem ReadPermission ChangePermission ChangeOwner Public folders: The AccessRights parameter specifies the rights being added. This parameter accepts the following values: ReadItems - The user has the right to read items within the specified public folder. CreateItems - The user has the right to create items within the specified public folder. EditOwnedItems - The user has the right to edit the items that the user owns in the specified public folder. DeleteOwnedItems - The user has the right to delete items that the user owns in the specified public folder. EditAllItems - The user has the right to edit all items in the specified public folder. 45 of 66
46 DeleteAllItems - The user has the right to delete all items in the specified public folder. CreateSubfolders - The user has the right to create subfolders in the specified public folder. FolderOwner - The user is the owner of the specified public folder. The user has the right to view and move the public folder and create subfolders. The user can't read items, edit items, delete items, or create items. FolderContact - The user is the contact for the specified public folder. FolderVisible - The user can view the specified public folder, but can't read or edit items within the specified public folder. In addition to access rights, an Administrator can create rights based upon roles, which includes multiple access rights. This parameter accepts the following values for roles: None - FolderVisible Owner - CreateItems, ReadItems, CreateSubfolders, FolderOwner, FolderContact, FolderVisible, EditOwnedItems, EditAllItems, DeleteOwnedItems, DeleteAllItems PublishingEditor - CreateItems, ReadItems, CreateSubfolders, FolderVisible, EditOwnedItems, EditAllItems, DeleteOwnedItems, DeleteAllItems Editor - CreateItems, ReadItems, FolderVisible, EditOwnedItems, EditAllItems, DeleteOwnedItems, DeleteAllItems PublishingAuthor - CreateItems, ReadItems, CreateSubfolders, FolderVisible, EditOwnedItems, DeleteOwnedItems Author - CreateItems, ReadItems, FolderVisible, EditOwnedItems, DeleteOwnedItems NonEditingAuthor - CreateItems, ReadItems, FolderVisible Reviewer - ReadItems, FolderVisible Contributor - CreateItems, FolderVisible Functional Requirements Satisfied: FDP_ACC.1 (Folder), FDP_ACF.1 (Folder), FMT_MSA.1, FMT_MSA.3 (Folder). 46 of 66
47 Security Management for Access Control: The RBAC permission model has removed the administrative task of modifying and managing access control lists (ACLs), present in versions of Exchange prior to Exchange Server RBAC allows administrators to control, at both broad and granular levels, what administrators and endusers can do. RBAC also enables administrators to more closely align the roles assigned to users and administrators to the actual roles they hold within the organization. In Exchange 2010, RBAC now controls both the administrative tasks that can be performed and the extent to which users can now administer their own mailbox and distribution groups; implemented through role groups and role assignment policies. Both role groups and role assignment policies associate users with the permissions they need to perform their jobs. In addition to these methods, a third and more advanced method, direct user role assignment, can also be used. Role groups: One or more Administrators can be members of a role group. They can also be members of more than one role group. The role group is assigned one or more role assignments. These link the role group with one or more administrative roles that define what tasks can be performed. The role assignments can contain management scopes that define where the users of the role group can perform actions. The scopes determine where the users of the role group can modify configuration. Role assignment policies: One or more users can be associated with a role assignment policy. The role assignment policy is assigned one or more role assignments. These link the role assignment policy with one or more end-user roles. The end-user roles define what the user can configure on his or her mailbox. The role assignments between role assignment policies and roles have built-in scopes that restrict the scope of assignments to the user's own mailbox or distribution groups. Direct role assignment (advanced): 47 of 66
48 A role assignment can be created directly between a user or Universal Security Group (USG) and one or more roles. The role defines what tasks the user or USG can perform. The role assignments can contain management scopes that define where the user or USG can perform actions. The scopes determine where the user or USG can modify configuration. Figure 2 RBAC Overview Functional Requirements Satisfied: FDP_ACC.1a (Folder), FDP_ACC.1b (Group), FDP_ACF.1a (Folder), FDP_ACF.1b (Group), FMT_MSA.3a (Folder) FMT_MSA.3b (Group) and FMT_MSA Identification and Authentication The TOE will identify and authenticate all users connecting to the TOE via Outlook Voice Access utilizing a SIP/RTP connection, with the exception of users who connect utilizing a mutually authenticated TLS connection. The identity of the user in the context of this Security Function is represented by the user s mailbox number or a telephone number that is transmitted from the PBX to the TOE (caller ID). When a user initiates a phone call to OVA, the TOE references the associated Caller Id that is transmitted from the PBX as an additional mechanism to identify the user. If the Caller Id matches a user, the user does not have to enter their mailbox number, but still must enter their PIN prior to gaining access to any TOE resources 12. If the Caller ID is not transmitted or the transmitted number has not been assigned to a mailbox, the user is asked to enter their mailbox number. After this identification, the user is asked to 12 Please note that the caller ID and the mailbox number are only mechanisms for the TOE to map the calling user to their corresponding ID. 48 of 66
49 enter their PIN for authentication. After successful authentication, the TOE associates the calling user with their corresponding Windows user account and the corresponding roles. In the event that a PBX establishes a connection utilizing the TLS protocol with mutual authentication for SIP/RTP, the identification and authentication of the user is not performed by the TOE, but is the responsibility of the TLS authenticated application which is part of the IT environment. Further, the TOE will ensure that PINs generated by administrators, the user or the TOE itself meet a quality metric as defined by the administrator based on: the number of digits of the PIN, the history of the last PINs, and common patterns. The TOE specifically ensures that a PIN has at least a length of 8 digits. After the user has been successfully authenticated, the user s identity is used to control the user s access to data to ensure that one user cannot access other user s data via this interface. Functional Requirements Satisfied: FIA_SOS.1, FIA_UAU.2, FIA_UID.2, and FIA_USB.1. Security Management for Identification and Authentication: The TOE will provide functionality to manage the attributes of users for Outlook Voice Access. Specifically this will allow Authorized Administrators to manage the quality metric for Outlook Voice Access PINs. 6.8 Distribution Group Restriction Exchange can place restrictions on how messages are delivered to individual recipients. Message delivery restrictions apply to all recipient types and are used for controlling access to specific recipients. An administrator can configure the following message delivery restrictions for a distribution group: Accept messages from a specific list of senders - Specify a list of senders from which to accept messages, the recipient will receive messages only from those senders. By default, all recipients are configured to accept messages from all senders. Reject messages from a specific list of senders - Specify a list of senders from which to reject messages, the recipient will reject messages from those senders. By default, all recipients are configured not to reject messages from any senders (this list has priority over the accept list). 49 of 66
50 Require that all senders are authenticated Setting that requires that all senders are authenticated; any messages from senders that don't have valid logon credentials will be rejected. Functional Requirements Satisfied: FDP_ACC.1b (Group), FDP_ACF.1b (Group), FMT_MSA.3b (Group). Security Management for Distribution Group Restriction: The TOE will provide functionality to: create and delete distribution groups, and configure message delivery restrictions. 6.9 Remote Device Wipe Microsoft Exchange enables administrators to send a command to a mobile phone that will perform a wipe of that phone. This process, known as a remote device wipe, clears all Exchange information that's stored on the mobile phone. The Remote Wipe function is implemented through the Exchange ActiveSync protocol, which utilizes a HTTP connection established between the managed mobile device (which initiates the connection) and the listening server. In order for the Remote Wipe function to work, a device must support the Provision command introduced in version 2.5 of the Exchange Active Sync protocol. For devices that do not support Provision or the claimed ability to support policies, a remote wipe command essentially blocks the device from syncing with Exchange Server. Initiating remote wipe sets the following information in the device s sync state that resides in the user s mailbox: WipeRequestTime: Current date/time WipeSendTime: Null WipeAckTime: Null LastDeviceWipeRequestor: SMTP address of cmdlet executor WipeConfirmationAddresses: SMTP Addresses specified in -Notification Addresses parameter or Null if not present 50 of 66
51 Remote wipe initiation also causes any hanging command to complete by artificially deleting a custom folder within the user s mailbox thereby immediately returning a response to the device. Any subsequent commands by a provisionable device will result in a response from the server with the unique HTTP status code 449 telling the device to send up a Provision request. The server will respond to this request with a status telling the device to remote wipe. At this time, WipeSendTime will be set to the current data/time in the device s sync state that resides in the user s mailbox. A non-provisionable device, if allowed to sync by policy, will receive an HTTP status code of 403 (Forbidden) for all subsequent requests. In order for a remote wipe request to be actioned, the device must first connect to the Exchange server and establish an ActiveSync session. Once connected, the device will be issued with the remote wipe request for the Exchange server. Upon receiving the status to remote wipe from the server, the device should send up its acknowledgement Provision request with a remote wipe status value of 1 then promptly clear its memory. When the server receives this acknowledgement request, it sets the WipeAckTime to the current data/time in the device s sync state that resides in the user s mailbox. Device wipe can be cancelled by an Administrator with the Clear-ActiveSyncDevice Cancel cmdlet/parameter combination. The command is only valid if the server has not sent a Provision response asking the device to wipe. This state is indicated by a valid WipeRequestTime date/time stamp but a null value for WipeSendTIme in the device s sync stat e that resides in the user s mailbox. Functional Requirements Satisfied: FMT_MOF.1 (Remote Wipe). Security Management for Mobile Device Wipe: Through either the Exchange Management Console (EMC) or Exchange Management Shell administrators can issue remote wipe commands. 51 of 66
52 7 Rationale 7.1 Overview This section provides the rationale for completeness and consistency of the ST. The rationale addresses the following areas: Security objectives rationale. Provides coverage for the security objectives for the TOE and the environment, ensuring that all threats and assumptions are effectively addressed. Security requirements rationale. Provides justification for TOE assurance requirements, evidence that all dependencies have been addressed, specification of strength of function for all probabilistic mechanisms and demonstration that the IT requirements address the TOE and environment objectives. TOE summary specification rationale. Provides evidence that the IT security functions and assurance measures are adequate to implement the security functional and assurance requirements. 7.2 Security objectives rationale Security objectives for the TOE Threats Objective Justification T.UNAUTH_DAC O.DAC O.I&A OE.PLATFORM The O.DAC, O.I&A and OE.PLATFORM objectives collectively address the threat (T.UNAUTH_DAC) of an unauthenticated and unauthorized user gaining access to information contained in private or public stores that are controlled by the TOE. O.DAC provides discretionary access controls on these public and private information stores which limit access to only authorized users. O.I&A provides the mechanism for Identification and Authentication for the cases where users connect via non TLS-secured OVA. OE.PLATFORM provides the mechanism for Identification and Authentication except for the case that users connect via a non TLS encrypted Outlook 52 of 66
53 Threats Objective Justification Voice Access connection. The combination of O.I&A and OE.PLATFORM ensures that all users are authenticated and that the TOE can rely on the identity of the user for access control; utilized by O.DAC to grant or deny access. T.AUTH_DAC T.UNAUTHUSE O.DAC O.I&A OE.PLATFORM O.DAC O.I&A OE.PLATFORM The O.DAC, O.I&A and OE.PLATFORM objectives collectively address the threat (T.AUTH_DAC) of an authenticated user gaining access to information contained in private stores that are controlled by the TOE, to which the user is not authorized to access. O.DAC provides discretionary access controls on these private stores which limit access to only authorized users. O.I&A provides the mechanism for Identification and Authentication for the cases where users connect via non TLS-secured OVA. OE.PLATFORM provides the mechanism for Identification and Authentication except for the case that users connect via a non TLS encrypted Outlook Voice Access connection. The combination of O.I&A and OE.PLATFORM ensures that all users are authenticated and that the TOE can rely on the identity of the user for access control; utilized by O.DAC to grant or deny access. The O.DAC, O.I&A and OE.PLATFORM objectives collectively address the threat (T.AUTH_DAC) of an authenticated user gaining access to information contained in a public store (public folder) that is controlled by the TOE, to which the user is not authorized to access. O.DAC provides discretionary access controls on these public information stores which limit access to only authorized users. O.I&A provides the mechanism for Identification and Authentication for the cases where users connect via non TLS-secured OVA. OE.PLATFORM provides the mechanism for Identification and Authentication except for the case that users connect via a non TLS encrypted Outlook Voice Access connection. 53 of 66
54 Threats Objective Justification The combination of O.I&A and OE.PLATFORM ensures that all users are authenticated and that the TOE can rely on the identity of the user for access control; utilized by O.DAC to grant or deny access. T.SPAM O.CONBLK O.CONBLK (blocking of SMTP connections from IP addresses of suspected spammers) directly traces back to T.SPAM. Blocking connections from suspected UCE SMTP hosts helps reduce the amount of UCE because the TOE is able to filter SMTP connections. Therefore T.SPAM is partly countered by O.CONBLK (the other aspect of T.SPAM about known senders of UCE is countered by O.REDUCE_SPAM. See below). T.DL_MISUSE O.REDUCE_SPAM O.RESTDIST O.I&A OE.PLATFORM Blocking messages with suspected UCE sender addresses helps reduce the amount of UCE because the TOE is able to filter the messages. Therefore, T.SPAM is partly countered by O.REDUCE_SPAM (the other aspect of T.SPAM about known IP addresses of UCE origin is countered by O.CONBLK. See above). O.RESTDIST (access control for distribution groups) directly addresses T.DL_MISUSE. T.DL_MISUSE defines misuse of distribution groups as a threat. O.RESTDIST counters this threat by allowing the administrator to restrict the use of a distribution group to only those users that have been authenticated and/or optionally identify users who are explicitly authorized to use a distribution group. O.I&A provides the mechanism for Identification and Authentication for the cases where users connect via non TLS-secured OVA. OE.PLATFORM provides the mechanism for Identification and Authentication except for the case that users connect via a non TLS encrypted Outlook Voice Access connection. The combination of O.I&A and OE.PLATFORM ensures that all users are authenticated and that the TOE can rely on the identity of the user to enforce the policy as defined in O.RESTDIST. OSP.MAIL_FLOW O.MAIL_FLOW The OSP.MAIL_FLOW is directly and completely addressed by the Security Objective O.MAIL_FLOW. The 54 of 66
55 Threats Objective Justification OSP as well as the Objective define that an administrator shall be able to control flow within their organization and use the same set of characteristics for this functionality. OSP.WIPE O.WIPE The OSP.WIPE is directly and completely addressed by the Security Objective O.WIPE. The OSP as well as the Objective define that administrators shall be able to send wipe commands. 7.3 Security objectives for the IT and non-it environment Assumptions Objectives Justification A.COM_PROT OE.COM_PROT This objective for the IT environment upholds the assumption that the environment will provide secure communication channels between all server roles, users and the TOE, and will implement a firewall between the TOE and the Internet (if Internet connectivity exists). A.INSTALL OE.INSTALL This objective for the IT environment upholds the assumption that the TOE will be delivered, installed, configured and set up in accordance with delivery documentation. A.PLATFORM OE.PLATFORM OE.INSTALL These objectives for the IT environment uphold the assumption that the environment will provide access control, user identification and authentication (except when connecting using a non-tls secured connection using the Outlook Voice Access function), and methods to store, manage and limit access to TSF data. Additionally, these objectives uphold that no untrusted software is installed on the machines supporting the TOE, and that the Administrator ensures that the TOE is operating on the correct operating system platform. A.BLOCKLIST OE.BLOCKLIST This objective for the IT environment upholds the assumption that only third party block and/or allow lists from trustworthy sources are used, and that the integrity of the block lists are maintained. 55 of 66
56 Assumptions Objectives Justification A.NO_EVIL_ADMIN OE.INSTALL This objective for the IT environment upholds the assumption that the TOE is delivered, installed, configured and set up by trustworthy staff, and operated in a manner that is consistent with IT security. A.PHYS_PROTECT OE.PHYSICAL This objective for the IT environment upholds the assumption that the environment will provide physical protection of the TOE. 56 of 66
57 7.4 Security requirements rationale Dependency analysis SFR Dependency Inclusion FDP_ACC.1a FDP_ACF.1 Security attribute based access control FDP_ACF.1a FDP_ACC.1b FDP_ACF.1 Security attribute based access control FDP_ACF.1b FDP_ACF.1a FDP_ACF.1b FDP_ACC.1 Subset access control FMT_MSA.3 Static attribute initialization FDP_ACC.1 Subset access control FMT_MSA.3 Static attribute initialization FDP_ACC.1a, FMT_MSA.3a FDP_ACC.1b, FMT_MSA.3b FDP_IFC.1a FDP_IFF.1 Simple security attributes FDP_IFF.1a FDP_IFC.1b FDP_IFF.1 Simple security attributes FDP_IFF.1b FDP_IFC.1c FDP_IFF.1 Simple security attributes FDP_IFF.1c FDP_IFC.1d FDP_IFF.1 Simple security attributes FDP_IFF.1d FDP_IFC.1e FDP_IFF.1 Simple security attributes FDP_IFF.1e FDP_IFF.1a FDP_IFF.1b FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization FDP_IFC.1a, FMT_MSA.3c FDP_IFC.1b, FMT_MSA.3d 57 of 66
58 SFR Dependency Inclusion FDP_IFF.1c FDP_IFF.1d FDP_IFF.1e FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization FDP_IFC.1 Subset information flow control FMT_MSA.3 Static attribute initialization FDP_IFC.1c, FMT_MSA.3e FDP_IFC.1d, FMT_MSA.3f FDP_IFC.1e, FMT_MSA.3g FIA_SOS.1 No dependencies N/A FIA_UAU.2 FIA_UID.1 Timing of identification FIA_UID.2 FIA_UID.2 No dependencies N/A FIA_USB.1 FIA_ATD.1 User attribute definition FIA_ATD.1 not included see rationale below FMT_MOF.1 FMT_SMR.1 Security roles FMT_SMF.1 Specification of Management Functions FMT_SMF.1 FMT_SMR.1 not included see rationale below FMT_SMF.1 No dependencies N/A FMT_MSA.1 [FDP_ACC.1 Subset access control, or FDP_IFC.1 Subset information flow control] FMT_SMR.1 Security roles FMT_SMF.1 Specification of Management Functions FDP_ACC.1a, FDP_ACF.1a, FMT_SMF.1 FMT_SMR.1 not included see rationale below 58 of 66
59 SFR Dependency Inclusion FMT_MSA.3a FMT_MSA.3b FMT_MSA.3c FMT_MSA.3d FMT_MSA.3e FMT_MSA.3f FMT_MSA.3g FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles FMT_MSA.1 Management of security attributes FMT_SMR.1 Security roles FMT_MSA.1 FMT_SMR.1 not included see rationale below FMT_MSA.1 FMT_SMR.1 not included see rationale below FMT_MSA.1 FMT_SMR.1 not included see rationale below FMT_MSA.1 FMT_SMR.1 not included see rationale below FMT_MSA.1 FMT_SMR.1 not included see rationale below FMT_MSA.1 FMT_SMR.1 not included see rationale below FMT_MSA.1 FMT_SMR.1 not included see rationale below 59 of 66
60 7.4.2 Rationale for not addressing all dependencies FIA_ATD.1 and FMT_SMR.1 have not been included as SFRs as the environment is responsible for performing the required functionality as specified in OE.PLATFORM TOE IT requirements correspondence Objective SFRs Demonstration O.DAC O.CONBLK O.RESTDIST FDP_ACC.1a FDP_ACF.1a FMT_MSA.1 FMT_MSA.3a FMT_SMF.1 FDP_IFC.1a FDP_IFF.1a FDP_IFC.1b FDP_IFF.1b FMT_MSA.3c FMT_MSA.3d FMT_SMF.1 FDP_ACC.1b FDP_ACF.1b FMT_MSA.3b Discretionary access control for user access to mailboxes and public folders is directly supported by access control components FDP_ACC.1a and FDP_ACF.1a. FMT_MSA.1 ensures that access control are also provided for the attributes that are utilized for this policy. FMT_MSA.3a ensures that appropriate default values are used for all attributes of this policy. Eventually, FMT_SMF.1 ensures that the TOE provides management functionality to query and modify the attributes of the access control policy. O.CONBLK is represented by the SFRs FDP_IFC.1a and FDP_IFF.1a, which build an information flow policy for connection blocking based on allow and block lists and FDP_IFC.1b and FDP_IFF.1b, which build an information flow policy based on the Sender Reputation Level that determines the likelihood of a sender being a spammer. Support is provided by FMT_SMF.1 to enable management of the security attributes used by this policy and by FMT_MSA.3c resp. FMT_MSA.3d to ensure appropriate default values for the policies. O.RESTDIST is represented by the SFRs FDP_ACC.1b and FDP_ACF.1b, which form an access control policy for distribution groups to restrict the ability of users to send s to Distribution Groups. 60 of 66
61 Objective SFRs Demonstration FMT_SMF.1 FMT_MSA.3b ensures that appropriate default values are used for all attributes of this policy. Eventually, FMT_SMF.1 ensures that the TOE provides management functionality to query and modify the attributes of the policy. O.REDUCE_SPAM O.MAIL_FLOW O.I&A FDP_IFC.1c FDP_IFF.1c FMT_MSA.3e FMT_SMF.1 FDP_IFC.1d FDP_IFF.1d FDP_IFC.1e FDP_IFF.1e FMT_MSA.3f FMT_MSA.3g FMT_SMF.1 FIA_UAU.2 FIA_UID.2 FIA_USB.1 FIA_SOS.1 FMT_SMF.1 O.REDUCE_SPAM is represented by the SFRs FDP_IFC.1c and FDP_IFF.1c, which form an information flow policy to filter based on the RCPT TO: and MAILFROM fields of the RFC 2821 envelope and the RFC 2822 header of the . Indirect support is provided by FMT_SMF.1 to enable management of the security attributes used by this policy and by FMT_MSA.3e to ensure that appropriate default values are provided. O.MAIL_FLOW is represented by a combination of two information flow policies. FDP_IFC.1d and FDP_IFF.1d allow attachment filtering already on the Edge Transport Server Role of the TOE while FPP_IFC.1e and FDP_IFF.1e allow the administrator to specify rules for transport on the hub server role based on characteristics of the . Support is provided by FMT_SMF.1 to enable management of the security attributes used by this policy and by FMT_MSA.3f resp. FMT_MSA.3g to ensure that appropriate default values are provided. O.I&A requires the identification and authentication of users that connect to the TOE via a non TLS OVA session (for the rest of the cases the environment is responsible for identification and authentication). This identification and authentication mechanism for non TLS-secured Outlook Voice Access is defined in FIA_UID.2 and FIA_UAU.2. FIA_USB.1 defines the security attributes for subjects that are used to bind subjects to their users. Finally, FIA_SOS.1 ensures that the PINs for Outlook Voice Access follow a quality metric to reduce the likelihood that an attacker can guess the PIN of a user. 61 of 66
62 Objective SFRs Demonstration Indirect support is provided by FMT_SMF.1 components from the FMT class to enable management of the security attributes used by this policy. O.WIPE FMT_MOF.1 FMT_SMF.1 O.WIPE specifies that the TOE shall be able to send remote wipe commands to compatible platforms. This management capability is specified in FMT_MOF.1 and listed as a management function in FMT_SMF of 66
63 7.4.4 TOE assurance requirements This ST contains the assurance requirements from the CC EAL4 assurance package augmented with ALC_FLR.3. Augmentation was chosen to provide the added assurance that is provided by defining flaw remediation procedures. This ST is based on good rigorous commercial development practices and has been developed for a general environment for a TOE that is readily available and does not require modification to meet the security needs of the environment specified in this ST. The EAL chosen is based on the statement of the security environment (threats, organizational policies, assumptions) and the security objectives defined in this ST. The sufficiency of the EAL chosen is justified based on those aspects of the environment that have impact upon the assurance needed in the TOE. Specifically, that the TOE will not process information that requires protection from attackers possessing a Basic or Enhanced-Basic attack potential, and that protection from obvious vulnerabilities is required. 63 of 66
64 7.5 TOE summary specification rationale Security functions The security functions rationale has been provided as part of Section Assurance measures Assurance requirement Assurance measures Demonstration ADV_ARC.1 Security architecture description ADV_FSP.4 Complete functional specification ADV_IMP.1 Implementation representation of the TSF AGD_OPE.1 Operational user guidance AGD_PRE.1 Preparative procedures ALC_CMC.4 Production support, acceptance procedures and automation Development Guidance documents Life cycle support The development assurance measure provides all the necessary design documentation to support the effective detailed analysis of the TOE for an evaluation at EAL4. The security architecture description provides a detailed description of the TSF security architecture. The functional specification provides a detailed description of the security functions of the TOE. The design documentation provides a complete definition of the TSF, allowing for sufficient analysis to be performed. The operational user guidance documentation provides the guidance for end users, administrators and other parties who will use the TOE. These documents provide all the necessary instructions and direction for ensuring that the TOE is installed, configured, used and administered in a secure manner. The life cycle support measures provide the assurance that the TOE is developed and subsequently managed using a well defined and controlled approach. Configuration management measures provide the assurance that configured 64 of 66
65 Assurance requirement Assurance measures Demonstration ALC_CMS.4 Problem tracking configuration management ALC_DEL.1 Delivery procedures ALC_DVS.1 Identification of security measures ALC_FLR.3 Systematic flaw remediation ALC_LCD.1 Developer defined life-cycle model ALC_TAT.1 Well-defined development tools items are managed and maintained in a controlled manner, through the demonstration of well defined processes, procedures and requirements. By placing the TOE and its components into this configuration management list provides assurance that the TOE components are only modified in a controlled manner with proper authorization. Employing sufficient security measures in the delivery process of the TOE to consumers ensures that the TOE is not tampered with prior to its receipt. Procedural, personnel and physical security related documentation is used to ensure that the confidentiality and integrity of the TOE and its design are maintained throughout the development life cycle. The life cycle support assurance measures provides a set of procedures aimed at the identifying, reporting and addressing security flaws or bugs that may appear in the TOE. An established development lifecycle methodology is employed to guide the development of the TOE. A set of well established development tools exist and are employed in the development of the TOE. ASE_CCL.1 Conformance claims ASE_ECD.1 Extended components definition ASE_INT.1 ST Introduction Security Target evaluation Security Target evaluation assurance measures ensure that the claim to EAL4 (augmented with ALC_FLR.3) can be accurately appraised. ASE_OBJ.2 Security objectives 65 of 66
66 Assurance requirement Assurance measures Demonstration ASE_REQ.2 Derived security Requirements ASE_SPD.1 Security problem definition ASE_TSS.1 TOE summary specification ATE_COV.2 Analysis of coverage ATE_DPT.1 Testing: basic design ATE_FUN.1 Functional testing ATE_IND.2 Independent testing sample AVA_VAN.3 Focused vulnerability analysis Tests Vulnerability assessment The tests assurance measure ensures that the TOE has been appropriately tested for the claimed set of security functions. The test plans for the TOE identifies the set of security functions that are to be tested, the procedures for establishing the test environment and also for conducting the test cases. The results of the tests are also recorded to provide evidence of test results. The vulnerability assessment assurance measure provides confidence that the TOE and its environment have been assessed for obvious vulnerabilities or exposures. A claim is also provided for the strength of function related to probabilistic mechanisms that are non-cryptographic. 66 of 66
Mobile Billing System Security Target
 Mobile Billing System Security Target Common Criteria: EAL1 Version 1.2 25 MAY 11 Document management Document identification Document ID Document title Product version IDV_EAL1_ASE IDOTTV Mobile Billing
Mobile Billing System Security Target Common Criteria: EAL1 Version 1.2 25 MAY 11 Document management Document identification Document ID Document title Product version IDV_EAL1_ASE IDOTTV Mobile Billing
Forefront Identity Manager (FIM) 2010
 Forefront Identity Manager (FIM) 2010 Security Target Common Criteria: EAL4 augmented with ALC_FLR.3 Version 1.0 24-MAR-2012 Document history Version Date Description 0.1 28-APR-11 Initial draft for review.
Forefront Identity Manager (FIM) 2010 Security Target Common Criteria: EAL4 augmented with ALC_FLR.3 Version 1.0 24-MAR-2012 Document history Version Date Description 0.1 28-APR-11 Initial draft for review.
JMCS Northern Light Video Conferencing System Security Target
 JMCS Northern Light Video Conferencing System Security Target Common Criteria: EAL2 Version 1.2 22 FEB 12 Document management Document identification Document ID Document title Product version NLVC_ST_EAL2
JMCS Northern Light Video Conferencing System Security Target Common Criteria: EAL2 Version 1.2 22 FEB 12 Document management Document identification Document ID Document title Product version NLVC_ST_EAL2
System Center Mobile Device Manager 2008 Service Pack 1 Security Target
 System Center Mobile Device Manager 2008 Service Pack 1 EAL4 augmented with ALC_FLR.3 Version 1.1 July 2009 The information contained in this document represents the current view of Microsoft Corporation
System Center Mobile Device Manager 2008 Service Pack 1 EAL4 augmented with ALC_FLR.3 Version 1.1 July 2009 The information contained in this document represents the current view of Microsoft Corporation
Windows Mobile 6.5 Security Target
 EAL4 augmented with ALC_FLR.1 Version 1.0 January 2010 The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication.
EAL4 augmented with ALC_FLR.1 Version 1.0 January 2010 The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication.
U.S. Government Protection Profile for Application-level Firewall In Basic Robustness Environments
 U.S. Government Protection Profile for Application-level Firewall In Basic Robustness Environments Information Assurance Directorate Version 1.1 July 25, 2007 Forward This Protection Profile US Government
U.S. Government Protection Profile for Application-level Firewall In Basic Robustness Environments Information Assurance Directorate Version 1.1 July 25, 2007 Forward This Protection Profile US Government
Active Directory Federation Services 2.0
 Active Directory Federation Services 2.0 Security Target Common Criteria: EAL4 augmented with ALC_FLR.3 Version 1.0 23-MAR-12 Document history Version Date Description 0.1 10-MAY-11 Initial draft for review.
Active Directory Federation Services 2.0 Security Target Common Criteria: EAL4 augmented with ALC_FLR.3 Version 1.0 23-MAR-12 Document history Version Date Description 0.1 10-MAY-11 Initial draft for review.
Security Target. McAfee Enterprise Mobility Management 12.0. Document Version 1.16
 Security Target McAfee Enterprise Mobility Management 12.0 Document Version 1.16 September 17, 2014 Prepared For: Prepared By: McAfee, Inc. 2821 Mission College Blvd. Santa Clara, CA 95054 Primasec Ltd
Security Target McAfee Enterprise Mobility Management 12.0 Document Version 1.16 September 17, 2014 Prepared For: Prepared By: McAfee, Inc. 2821 Mission College Blvd. Santa Clara, CA 95054 Primasec Ltd
Firewall Protection Profile V2.0 2008. 4. 24
 Firewall Protection Profile V2.0 2008. 4. 24 (This page left blank on purpose for double-side printing) Protection Profile Title Firewall Protection Profile for Government Evaluation Criteria Version This
Firewall Protection Profile V2.0 2008. 4. 24 (This page left blank on purpose for double-side printing) Protection Profile Title Firewall Protection Profile for Government Evaluation Criteria Version This
Microsoft Forefront UAG 2010 Common Criteria Evaluation Security Target Microsoft Forefront Unified Access Gateway Team
 Microsoft Forefront UAG 2010 Common Criteria Evaluation Security Target Microsoft Forefront Unified Access Gateway Team Author: Microsoft Corp. Version: 1.0 Last Saved: 2011-03-10 File Name: MS_UAG_ST_1.0.docx
Microsoft Forefront UAG 2010 Common Criteria Evaluation Security Target Microsoft Forefront Unified Access Gateway Team Author: Microsoft Corp. Version: 1.0 Last Saved: 2011-03-10 File Name: MS_UAG_ST_1.0.docx
Security Target. McAfee Enterprise Mobility Management 9.7. Document Version 0.9. July 5, 2012
 Security Target McAfee Enterprise Mobility Management 9.7 Document Version 0.9 July 5, 2012 Document Version 0.9 McAfee Page 1 of 39 Prepared For: Prepared By: McAfee, Inc. 2821 Mission College Blvd. Santa
Security Target McAfee Enterprise Mobility Management 9.7 Document Version 0.9 July 5, 2012 Document Version 0.9 McAfee Page 1 of 39 Prepared For: Prepared By: McAfee, Inc. 2821 Mission College Blvd. Santa
Security Target. Symantec TM Network Access Control Version 12.1.2. Document Version 0.12. February 14, 2013
 Security Target Symantec TM Network Access Control Version 12.1.2 Document Version 0.12 February 14, 2013 Document Version 0.12 Symantec Page 1 of 39 Prepared For: Prepared By: Symantec Corporation 350
Security Target Symantec TM Network Access Control Version 12.1.2 Document Version 0.12 February 14, 2013 Document Version 0.12 Symantec Page 1 of 39 Prepared For: Prepared By: Symantec Corporation 350
Low Assurance Protection Profile for a VPN gateway
 LAPP VPN gateway Low Assurance Protection Profile for a VPN gateway Version: 1.4 Date: 29/04/2005 Filename: lapp4_14 Product: VPN gateway Sponsor: SRC Security Research & Consulting GmbH, Graurheindorfer
LAPP VPN gateway Low Assurance Protection Profile for a VPN gateway Version: 1.4 Date: 29/04/2005 Filename: lapp4_14 Product: VPN gateway Sponsor: SRC Security Research & Consulting GmbH, Graurheindorfer
Security Target: Symantec Mail Security 8300 Series Appliances Version 5.0
 Security Target: Symantec Mail Security 8300 Series Appliances Version 5.0 ST Version 1.6 August 20, 2007 Document Version 1.6 Symantec Corporation Page 1 of 55 Prepared For: Prepared By: Symantec Corporation
Security Target: Symantec Mail Security 8300 Series Appliances Version 5.0 ST Version 1.6 August 20, 2007 Document Version 1.6 Symantec Corporation Page 1 of 55 Prepared For: Prepared By: Symantec Corporation
Firewall Protection Profile
 samhällsskydd och beredskap 1 (38) ROS-ISÄK Ronny Janse 010-2404426 [email protected] Firewall Protection Profile samhällsskydd och beredskap 2 (38) Innehållsförteckning 1. Introduction... 4 1.1 PP reference...
samhällsskydd och beredskap 1 (38) ROS-ISÄK Ronny Janse 010-2404426 [email protected] Firewall Protection Profile samhällsskydd och beredskap 2 (38) Innehållsförteckning 1. Introduction... 4 1.1 PP reference...
EMC Documentum. EMC Documentum Content Server TM V5.3. and EMC Documentum Administrator TM V5.3. Security Target V2.0
 EMC Documentum EMC Documentum Content Server TM V5.3 and EMC Documentum Administrator TM V5.3 Security Target V2.0 December 8, 2005 ST prepared by Suite 5200, 4925 Jones Branch Drive McLean, VA 22102-3305
EMC Documentum EMC Documentum Content Server TM V5.3 and EMC Documentum Administrator TM V5.3 Security Target V2.0 December 8, 2005 ST prepared by Suite 5200, 4925 Jones Branch Drive McLean, VA 22102-3305
QUESTION 1 You deploy a server that has the Exchange Server 2013 Mailbox server role and Client Access server role installed.
 QUESTION 1 You deploy a server that has the Exchange Server 2013 Mailbox server role and Client Access server role installed. You need to configure anti-spam to meet the following requirements: - Email
QUESTION 1 You deploy a server that has the Exchange Server 2013 Mailbox server role and Client Access server role installed. You need to configure anti-spam to meet the following requirements: - Email
Marimba Client and Server Management from BMC Software Release 6.0.3
 Marimba Client and Server Management from BMC Software Release 6.0.3 Version 2.3.0 4 June, 2007 Prepared by: BMC Software, Inc. 2101 City West Blvd. Houston, Texas 77042 TABLE OF CONTENTS 1. Introduction...
Marimba Client and Server Management from BMC Software Release 6.0.3 Version 2.3.0 4 June, 2007 Prepared by: BMC Software, Inc. 2101 City West Blvd. Houston, Texas 77042 TABLE OF CONTENTS 1. Introduction...
CA CA, Inc. Identity Manager 12.5 Identity Manager r12.1 Security Target
 CA CA, Inc. Identity Manager 12.5 Identity Manager r12.1 Security Target Version 2.0 June Version 21, 2010 0.6 December 29, 2008 Prepared for: Prepared CA for: 100 Staples CA, Inc. Drive Framingham, 100
CA CA, Inc. Identity Manager 12.5 Identity Manager r12.1 Security Target Version 2.0 June Version 21, 2010 0.6 December 29, 2008 Prepared for: Prepared CA for: 100 Staples CA, Inc. Drive Framingham, 100
EMC Corporation Data Domain Operating System Version 5.2.1.0. Security Target. Evaluation Assurance Level (EAL): EAL2+ Document Version: 0.
 EMC Corporation Data Domain Operating System Version 5.2.1.0 Security Target Evaluation Assurance Level (EAL): EAL2+ Document Version: 0.11 Prepared for: Prepared by: EMC Corporation 176 South Street Hopkinton,
EMC Corporation Data Domain Operating System Version 5.2.1.0 Security Target Evaluation Assurance Level (EAL): EAL2+ Document Version: 0.11 Prepared for: Prepared by: EMC Corporation 176 South Street Hopkinton,
BMC Real End User Experience Monitoring and Analytics 2.5. Security Target
 BMC Real End User Experience Monitoring and Analytics 2.5 Security Target Version 0.07 5 March 2015 Copyright 2015 BMC Software, Inc. All rights reserved. BMC, BMC Software, and the BMC Software logo
BMC Real End User Experience Monitoring and Analytics 2.5 Security Target Version 0.07 5 March 2015 Copyright 2015 BMC Software, Inc. All rights reserved. BMC, BMC Software, and the BMC Software logo
Enterasys Networks, Inc. Netsight/Network Access Control v3.2.2. Security Target
 Enterasys Networks, Inc. Netsight/Network Access Control v3.2.2 Security Target Evaluation Assurance Level: EAL2+ Document Version: 0.7 Prepared for: Prepared by: Enterasys Networks, Inc. Corsec Security,
Enterasys Networks, Inc. Netsight/Network Access Control v3.2.2 Security Target Evaluation Assurance Level: EAL2+ Document Version: 0.7 Prepared for: Prepared by: Enterasys Networks, Inc. Corsec Security,
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010
 10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
WATCHGUARD XCS SERVER V9.2 SECURITY TARGET
 WATCHGUARD XCS SERVER V9.2 SECURITY TARGET Evaluation Assurance Level: 4+ Augmented with ALC_FLR.2 Version: 1.9 WatchGuard Technologies Inc WatchGuard Canada 505 Fifth Avenue South, Suite 500 50 Burnhamthorpe
WATCHGUARD XCS SERVER V9.2 SECURITY TARGET Evaluation Assurance Level: 4+ Augmented with ALC_FLR.2 Version: 1.9 WatchGuard Technologies Inc WatchGuard Canada 505 Fifth Avenue South, Suite 500 50 Burnhamthorpe
EPASSPORT WITH BASIC ACCESS CONTROL AND ACTIVE AUTHENTICATION
 COMMON CRITERIA PROTECTION PROFILE EPASSPORT WITH BASIC ACCESS CONTROL AND ACTIVE AUTHENTICATION Draft Version 1.0 TURKISH STANDARDS INSTITUTION TABLE OF CONTENTS Common Criteria Protection Profile...
COMMON CRITERIA PROTECTION PROFILE EPASSPORT WITH BASIC ACCESS CONTROL AND ACTIVE AUTHENTICATION Draft Version 1.0 TURKISH STANDARDS INSTITUTION TABLE OF CONTENTS Common Criteria Protection Profile...
How To Understand The Toe
 Rapid7 Nexpose Vulnerability Management and Penetration Testing System V.5.1 Security Target Version 1.7 May 11, 2012 Prepared for: Rapid7 LLC 545 Boylston Street, Suite 400 Boston, MA 02116 Prepared By:
Rapid7 Nexpose Vulnerability Management and Penetration Testing System V.5.1 Security Target Version 1.7 May 11, 2012 Prepared for: Rapid7 LLC 545 Boylston Street, Suite 400 Boston, MA 02116 Prepared By:
MINISTERIO DE DEFENSA CENTRO NACIONAL DE INTELIGENCIA CENTRO CRIPTOLÓGICO NACIONAL ORGANISMO DE CERTIFICACIÓN
 REF: 2010-12-INF-626 V1 Distribution: Public Date: 29.04.2011 Created: CERT3 Reviewed: TECNICO Approved: JEFEAREA CERTIFICATION REPORT FOR EADS GROUND SEGMENT SYSTEMS PROTECTION PROFILE (GSS-PP) ISSUE
REF: 2010-12-INF-626 V1 Distribution: Public Date: 29.04.2011 Created: CERT3 Reviewed: TECNICO Approved: JEFEAREA CERTIFICATION REPORT FOR EADS GROUND SEGMENT SYSTEMS PROTECTION PROFILE (GSS-PP) ISSUE
Security Target. Astaro Security Gateway V8 Packet Filter Version 1.000. Assurance Level EAL4+ Common Criteria v3.1
 Astaro Security Gateway V8 Packet Filter Version 1.000 Assurance Level EAL4+ Common Criteria v3.1 This Security Target also covers the secunet wall 2 packet filter Version : 1.03 Date: 2011-05-20 Author:
Astaro Security Gateway V8 Packet Filter Version 1.000 Assurance Level EAL4+ Common Criteria v3.1 This Security Target also covers the secunet wall 2 packet filter Version : 1.03 Date: 2011-05-20 Author:
OmniPCX Enterprise Common Criteria Security Target
 OmniPCX Enterprise Common Criteria Security Target ALCATEL-LUCENT Enterprise Product Group March 2010 Ref: 3EU_29000_0019_DEZZA_03 Alcatel-Lucent All Rights Reserved Alcatel-Lucent 2010 Table of Content
OmniPCX Enterprise Common Criteria Security Target ALCATEL-LUCENT Enterprise Product Group March 2010 Ref: 3EU_29000_0019_DEZZA_03 Alcatel-Lucent All Rights Reserved Alcatel-Lucent 2010 Table of Content
Security Target Microsoft SQL Server Team
 Security Target Microsoft SQL Server Team Author: Roger French Version: 1.27 Date 2008-07-23 File Name: MS_SQL_ST_1.27 Abstract This document is the Security Target (ST) for the Common Criteria evaluation
Security Target Microsoft SQL Server Team Author: Roger French Version: 1.27 Date 2008-07-23 File Name: MS_SQL_ST_1.27 Abstract This document is the Security Target (ST) for the Common Criteria evaluation
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Low Assurance Protection Profile for a VoIP Infrastructure
 Low Assurance Protection Profile for a VoIP Infrastructure Version 1.1 Date Author(s) Dirk-Jan Out Certification ID Sponsor File name No of pages 12 TNO-ITSEF BV VoIP Low Assurance Protection Profile 1.1
Low Assurance Protection Profile for a VoIP Infrastructure Version 1.1 Date Author(s) Dirk-Jan Out Certification ID Sponsor File name No of pages 12 TNO-ITSEF BV VoIP Low Assurance Protection Profile 1.1
McAfee Web Gateway Version 7.2.0.1 EAL 2 + ALC_FLR.2 Security Target
 McAfee Web Gateway Version 7.2.0.1 EAL 2 + ALC_FLR.2 Release Date: 5 October 2012 Version: 1.0 Prepared By: Primasec Ltd. Prepared For: McAfee Inc. 3965 Freedom Circle Santa Clara, CA 95054 Document Introduction
McAfee Web Gateway Version 7.2.0.1 EAL 2 + ALC_FLR.2 Release Date: 5 October 2012 Version: 1.0 Prepared By: Primasec Ltd. Prepared For: McAfee Inc. 3965 Freedom Circle Santa Clara, CA 95054 Document Introduction
Security Target. Securonix Security Intelligence Platform 4.0. Document Version 1.12. January 9, 2015
 Security Target Securonix Security Intelligence Platform 4.0 Document Version 1.12 January 9, 2015 Document Version 1.12 Copyright Securonix Page 1 of 41 Prepared For: Prepared By: Securonix 5777 W. Century
Security Target Securonix Security Intelligence Platform 4.0 Document Version 1.12 January 9, 2015 Document Version 1.12 Copyright Securonix Page 1 of 41 Prepared For: Prepared By: Securonix 5777 W. Century
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
Security Target. Symantec Data Loss Prevention 11.1.1. Document Version 1.0. January 23, 2012
 Security Target Symantec Data Loss Prevention 11.1.1 Document Version 1.0 January 23, 2012 Document Version 1.0 Symantec Corporation Page 1 of 40 Prepared For: Prepared By: Symantec Corporation 350 Ellis
Security Target Symantec Data Loss Prevention 11.1.1 Document Version 1.0 January 23, 2012 Document Version 1.0 Symantec Corporation Page 1 of 40 Prepared For: Prepared By: Symantec Corporation 350 Ellis
Copyright 2011 Sophos Ltd. Copyright strictly reserved. These materials are not to be reproduced, either in whole or in part, without permissions.
 PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
McAfee Web Gateway Version 7.0.1.1 EAL 2 + ALC_FLR.2 Security Target
 McAfee Web Gateway Version 7.0.1.1 EAL 2 + ALC_FLR.2 Security Target Release Date: September 2010 Document ID: Version: Draft J Prepared By: Primasec Ltd. Prepared For: McAfee Inc. 3965 Freedom Circle
McAfee Web Gateway Version 7.0.1.1 EAL 2 + ALC_FLR.2 Security Target Release Date: September 2010 Document ID: Version: Draft J Prepared By: Primasec Ltd. Prepared For: McAfee Inc. 3965 Freedom Circle
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
IBM WebSphere Message Broker Security Target
 IBM WebSphere Message Broker Security Target Version 2.1.2 2007-08-22 Document History Version Date Summary Author 1.0 2006-10-23 Final EAL3 ST plus changes by IBM. SAIC / IBM 1.1 2006-12-11 Fixed inconsistencies.
IBM WebSphere Message Broker Security Target Version 2.1.2 2007-08-22 Document History Version Date Summary Author 1.0 2006-10-23 Final EAL3 ST plus changes by IBM. SAIC / IBM 1.1 2006-12-11 Fixed inconsistencies.
Natek Network Access Control (NAC)
 Natek Network Access Control (NAC) V 5.4.2 Security Target Release Date: 28.08.2014 Version 1.13 AUTHOR: NATEK BİLİŞİM BİLGİSAYAR EĞİTİM DANIŞMANLIK YAZILIM TİCARET SANAYİ ANONİM ŞİRKETİ 1 Revision History
Natek Network Access Control (NAC) V 5.4.2 Security Target Release Date: 28.08.2014 Version 1.13 AUTHOR: NATEK BİLİŞİM BİLGİSAYAR EĞİTİM DANIŞMANLIK YAZILIM TİCARET SANAYİ ANONİM ŞİRKETİ 1 Revision History
Common Criteria Security Target For 1E Power and Patch Management Pack
 Intelligent Windows Management Common Criteria Security Target For 1E Power and Patch Management Pack 30 September 2009 Document Version 1-0 1E Limited. All Rights reserved. Summary of Amendments Version
Intelligent Windows Management Common Criteria Security Target For 1E Power and Patch Management Pack 30 September 2009 Document Version 1-0 1E Limited. All Rights reserved. Summary of Amendments Version
Trustwave Secure Web Gateway Security Target
 Trustwave Secure Web Gateway Security Target Version 1.5 September 18, 2013 Trustwave 70 West Madison Street Suite 1050 Chicago, IL 60602 Prepared By: Common Criteria Consulting LLC 15804 Laughlin Lane
Trustwave Secure Web Gateway Security Target Version 1.5 September 18, 2013 Trustwave 70 West Madison Street Suite 1050 Chicago, IL 60602 Prepared By: Common Criteria Consulting LLC 15804 Laughlin Lane
Security Target. NetIQ Access Manager 4.0. Document Version 1.13. August 7, 2014. Security Target: NetIQ Access Manager 4.0
 Security Target NetIQ Access Manager 4.0 Document Version 1.13 August 7, 2014 Document Version 1.13 NetIQ Page 1 of 36 Prepared For: Prepared By: NetIQ, Inc. 1233 West Loop South Suite 810 Houston, TX
Security Target NetIQ Access Manager 4.0 Document Version 1.13 August 7, 2014 Document Version 1.13 NetIQ Page 1 of 36 Prepared For: Prepared By: NetIQ, Inc. 1233 West Loop South Suite 810 Houston, TX
IronMail Secure Email Gateway Software Version 4.0.0 Security Target April 27, 2006 Document No. CipherTrust E2-IM4.0.0
 IronMail Secure Email Gateway Software Version 4.0.0 Security Target April 27, 2006 Document No. CipherTrust E2-IM4.0.0 CipherTrust 4800 North Point Parkway Suite 400 Alpharetta, GA 30022 Phone: 678-969-9399
IronMail Secure Email Gateway Software Version 4.0.0 Security Target April 27, 2006 Document No. CipherTrust E2-IM4.0.0 CipherTrust 4800 North Point Parkway Suite 400 Alpharetta, GA 30022 Phone: 678-969-9399
U.S. Government Protection Profile for Database Management Systems
 U.S. Government Protection Profile for Database Management Systems Information Assurance Directorate Version 1.3 December 24, 2010 Protection Profile Title: 1 U.S. Government Protection Profile for Database
U.S. Government Protection Profile for Database Management Systems Information Assurance Directorate Version 1.3 December 24, 2010 Protection Profile Title: 1 U.S. Government Protection Profile for Database
Domains Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc.
 Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2016 SmarterTools Inc. Domains All Domains System administrators can use this section
SECURITY TARGET CITADEL HERCULES ENTERPRISE VULNERABILITY MANAGEMENT (EVM) VERSION 4.1
 SECURITY TARGET CITADEL HERCULES ENTERPRISE VULNERABILITY MANAGEMENT (EVM) VERSION 4.1 Document No. 1517-011-D001 Version 1.1, 3 August 2006 Prepared for: Citadel Security Software Inc. Two Lincoln Centre
SECURITY TARGET CITADEL HERCULES ENTERPRISE VULNERABILITY MANAGEMENT (EVM) VERSION 4.1 Document No. 1517-011-D001 Version 1.1, 3 August 2006 Prepared for: Citadel Security Software Inc. Two Lincoln Centre
Citrix Systems, Inc. NetScaler Platinum Edition Load Balancer Version 9.1 Security Target
 Citrix Systems, Inc. NetScaler Platinum Edition Load Balancer Version 9.1 Security Target Evaluation Assurance Level: EAL2 augmented with ALC_FLR.2 Document Version: 1 Prepared for: Prepared by: Citrix
Citrix Systems, Inc. NetScaler Platinum Edition Load Balancer Version 9.1 Security Target Evaluation Assurance Level: EAL2 augmented with ALC_FLR.2 Document Version: 1 Prepared for: Prepared by: Citrix
RSA, The Security Division of EMC RSA Data Loss Prevention Suite v6.5. Security Target
 RSA, The Security Division of EMC RSA Data Loss Prevention Suite v6.5 Security Target Evaluation Assurance Level: EAL2 Augmented with ALC_FLR.1 Document Version: 0.7 Prepared for: Prepared by: RSA, The
RSA, The Security Division of EMC RSA Data Loss Prevention Suite v6.5 Security Target Evaluation Assurance Level: EAL2 Augmented with ALC_FLR.1 Document Version: 0.7 Prepared for: Prepared by: RSA, The
MINISTERIO DE DEFENSA CENTRO NACIONAL DE INTELIGENCIA CENTRO CRIPTOLÓGICO NACIONAL ORGANISMO DE CERTIFICACIÓN
 REF: 2010-22-INF-764 V1 Distribution: Expediente Date: 21.11.2011 Created: CERT3 Reviewed: CALIDAD Approbed: TECNICO CERTIFICATION REPORT FOR FOR HUAWEI INTEGRATED MANAGEMENT APPLICATION PLATFORM VERSION
REF: 2010-22-INF-764 V1 Distribution: Expediente Date: 21.11.2011 Created: CERT3 Reviewed: CALIDAD Approbed: TECNICO CERTIFICATION REPORT FOR FOR HUAWEI INTEGRATED MANAGEMENT APPLICATION PLATFORM VERSION
Teradata Database Version 2 Release 6.1.0 (V2R6.1.0) Security Target
 Teradata Database Version 2 Release 6.1.0 (V2R6.1.0) Security Target Version 2.0 February 2007 TRP Number: 541-0006458 NCR, Teradata and BYNET are registered trademarks of NCR Corporation. Microsoft, Windows,
Teradata Database Version 2 Release 6.1.0 (V2R6.1.0) Security Target Version 2.0 February 2007 TRP Number: 541-0006458 NCR, Teradata and BYNET are registered trademarks of NCR Corporation. Microsoft, Windows,
BMC ProactiveNet Performance Management 9.5. Security Target
 BMC ProactiveNet Performance Management 9.5 Security Target Version 0.4 18 July 2014 Copyright 2014 BMC Software, Inc. All rights reserved. BMC, BMC Software, and the BMC Software logo are the exclusive
BMC ProactiveNet Performance Management 9.5 Security Target Version 0.4 18 July 2014 Copyright 2014 BMC Software, Inc. All rights reserved. BMC, BMC Software, and the BMC Software logo are the exclusive
C038 Certification Report
 C038 Certification Report TAXSAYA Online File name: Version: v1a Date of document: 15 August 2013 Document classification: For general inquiry about us or our services, please email: [email protected]
C038 Certification Report TAXSAYA Online File name: Version: v1a Date of document: 15 August 2013 Document classification: For general inquiry about us or our services, please email: [email protected]
BUILT FOR YOU. Contents. Cloudmore Exchange
 BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
Protection Profile for UK Dual-Interface Authentication Card
 Protection Profile for UK Dual-Interface Authentication Card Version 1-0 10 th July 2009 Reference: UNKT-DO-0002 Introduction This document defines a Protection Profile to express security, evaluation
Protection Profile for UK Dual-Interface Authentication Card Version 1-0 10 th July 2009 Reference: UNKT-DO-0002 Introduction This document defines a Protection Profile to express security, evaluation
IBM Security Access Manager for Enterprise Single Sign-On Version 8.2 with IMS Server Interim Fix 4 and AccessAgent Fix Pack 22 Security Target
 IBM Security Access Manager for Enterprise Single Sign-On Version 8.2 with IMS Server Interim Fix 4 and AccessAgent Fix Pack 22 Security Target Version: Status: Last Update: 1.19 Released 2014-03-05 Trademarks
IBM Security Access Manager for Enterprise Single Sign-On Version 8.2 with IMS Server Interim Fix 4 and AccessAgent Fix Pack 22 Security Target Version: Status: Last Update: 1.19 Released 2014-03-05 Trademarks
Top Layer Networks. Security Target V2.3
 Top Layer Networks IDS Balancer TM Version 2.2 Appliance (IDSB3531-CCV1.0, IDSB3532-CCV1.0, IDSB4508-CCV1.0) Security Target V2.3 August 31, 2004 AppBalancing, AppSafe, DCFD, Flow Mirror, SecureWatch,
Top Layer Networks IDS Balancer TM Version 2.2 Appliance (IDSB3531-CCV1.0, IDSB3532-CCV1.0, IDSB4508-CCV1.0) Security Target V2.3 August 31, 2004 AppBalancing, AppSafe, DCFD, Flow Mirror, SecureWatch,
This course is intended for IT professionals who are responsible for the Exchange Server messaging environment in an enterprise.
 10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course Number: 10233A Course Length: 5 Day Course Overview This instructor-led course provides you with the knowledge
10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course Number: 10233A Course Length: 5 Day Course Overview This instructor-led course provides you with the knowledge
Lesson Plans Configuring Exchange Server 2007
 Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Security Target for Cisco Secure PIX Firewall 515, 520, 525 Version 5.2(3)
 Security Target for Cisco Secure PIX Firewall 515, 520, 525 Version 5.2(3) Reference: ST January 2001 Version: 1.6 Europe: USA: CISCO Systems Ltd CISCO Systems Inc. 3 The Square 170 West Tasman Drive Stockley
Security Target for Cisco Secure PIX Firewall 515, 520, 525 Version 5.2(3) Reference: ST January 2001 Version: 1.6 Europe: USA: CISCO Systems Ltd CISCO Systems Inc. 3 The Square 170 West Tasman Drive Stockley
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling
 Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
Configuring the Hub Transport Role
 Configuring the Hub Transport Role Exchange Server 2000/2003 used the concept of bridgehead servers and connectors. A bridgehead server referred to an Exchange server that served as a connection point
Configuring the Hub Transport Role Exchange Server 2000/2003 used the concept of bridgehead servers and connectors. A bridgehead server referred to an Exchange server that served as a connection point
Common Criteria Security Target For XenApp 6.0 for Windows Server 2008 R2 Platinum Edition
 Common Criteria Security Target For XenApp 6.0 for Windows Server 2008 R2 Platinum Edition Version 1-0 7 February 2011 2011 Citrix Systems, Inc. All rights reserved. Summary of Amendments Version 1-0 7
Common Criteria Security Target For XenApp 6.0 for Windows Server 2008 R2 Platinum Edition Version 1-0 7 February 2011 2011 Citrix Systems, Inc. All rights reserved. Summary of Amendments Version 1-0 7
Secuware Virtual System (SVS)
 Secuware Virtual System (SVS) SECURITY TARGET EAL2 Copyright 2008 by SECUWARE All rights reserved. The information in this document is exclusive property of SECUWARE and may not be changed without express
Secuware Virtual System (SVS) SECURITY TARGET EAL2 Copyright 2008 by SECUWARE All rights reserved. The information in this document is exclusive property of SECUWARE and may not be changed without express
How To Protect Your Computer From Being Hacked
 Senforce Endpoint Security Suite Version 3.1.175 Security Target Version 1.0 06/19/07 Prepared for: Senforce Technologies, Inc. 147 W Election Rd Ste 110 Draper UT 84020 Prepared By: Science Applications
Senforce Endpoint Security Suite Version 3.1.175 Security Target Version 1.0 06/19/07 Prepared for: Senforce Technologies, Inc. 147 W Election Rd Ste 110 Draper UT 84020 Prepared By: Science Applications
Network Intrusion Prevention System Protection Profile V1.1
 Network Intrusion Prevention System Protection Profile V1.1 December 21, 2005 (This page left blank on purpose for double-side printing) Protection Profile Title Network Intrusion Prevention System Protection
Network Intrusion Prevention System Protection Profile V1.1 December 21, 2005 (This page left blank on purpose for double-side printing) Protection Profile Title Network Intrusion Prevention System Protection
Low Assurance Security Target for a Cisco VoIP Telephony System
 Low Assurance Security Target for a Cisco VoIP Telephony System Security Target Version 1.6 March 14, 2005 Document Control Preparation Action Name Date Prepared by: Rob Hunter of TNO-ITSEF BV on behalf
Low Assurance Security Target for a Cisco VoIP Telephony System Security Target Version 1.6 March 14, 2005 Document Control Preparation Action Name Date Prepared by: Rob Hunter of TNO-ITSEF BV on behalf
5/20/2013. The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team
 Additions and Subtractions The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team Exchange Version Exchange Server 2003 and earlier versions
Additions and Subtractions The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team Exchange Version Exchange Server 2003 and earlier versions
DataPower XS40 XML Security Gateway and DataPower XI50 Integration Appliance Version 3.6. Security Target Version 0.75
 DataPower S40 ML Security Gateway and DataPower I50 Integration Appliance Version 3.6 Security Target Version 0.75 10/09/2008 Prepared for: IBM SOA Appliance Group One Rogers St Cambridge, MA 02142 Prepared
DataPower S40 ML Security Gateway and DataPower I50 Integration Appliance Version 3.6 Security Target Version 0.75 10/09/2008 Prepared for: IBM SOA Appliance Group One Rogers St Cambridge, MA 02142 Prepared
Collax Mail Server. Howto. This howto describes the setup of a Collax server as mail server.
 Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Collax Mail Server Howto This howto describes the setup of a Collax server as mail server. Requirements Collax Business Server Collax Groupware Suite Collax Platform Server including Collax Communication
Feature and Technical
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 4 Feature and Technical Overview Published: 2013-11-07 SWD-20131107160132924 Contents 1 Document revision history...6 2 What's
How To Evaluate A Security Target Of Evaluation (Toe)
 Security Target McAfee Enterprise Security Manager with Event Receiver, Enterprise Log Manager, Advanced Correlation Engine, Application Data Monitor and Database Event Monitor 9.1 Document Version 1.1
Security Target McAfee Enterprise Security Manager with Event Receiver, Enterprise Log Manager, Advanced Correlation Engine, Application Data Monitor and Database Event Monitor 9.1 Document Version 1.1
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007
 5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
SECURITY TARGET FOR CENTRIFY SUITE VERSION 2013.2
 SECURITY TARGET FOR CENTRIFY SUITE VERSION 2013.2 Document No. 1769-000-D0007 Version: v0.89, 12 September 2013 Prepared for: Centrify Corporation 785 N. Mary Avenue, Suite 200 Sunnyvale, California USA,
SECURITY TARGET FOR CENTRIFY SUITE VERSION 2013.2 Document No. 1769-000-D0007 Version: v0.89, 12 September 2013 Prepared for: Centrify Corporation 785 N. Mary Avenue, Suite 200 Sunnyvale, California USA,
Network Device Collaborative Protection Profile (NDcPP) Extended Package Session Border Controller. July 24, 2015 Version 1
 Network Device Collaborative Protection Profile (NDcPP) Extended Package Session Border Controller July 24, 2015 Version 1 1 Table of Contents 1 Introduction... 4 1.1 Conformance Claims...4 1.2 How to
Network Device Collaborative Protection Profile (NDcPP) Extended Package Session Border Controller July 24, 2015 Version 1 1 Table of Contents 1 Introduction... 4 1.1 Conformance Claims...4 1.2 How to
AppGate Security Server, Version 8.0.4. Security Target. Document Version: 2.9 Date: 2008-04-10
 AppGate Security Server, Version 8.0.4 Security Target Document Version: 2.9 Date: 2008-04-10 Contents 1 INTRODUCTION...6 1.1 ST Identification...6 1.2 ST Overview...6 1.3 CC Conformance Claim...6 1.4
AppGate Security Server, Version 8.0.4 Security Target Document Version: 2.9 Date: 2008-04-10 Contents 1 INTRODUCTION...6 1.1 ST Identification...6 1.2 ST Overview...6 1.3 CC Conformance Claim...6 1.4
Basic Exchange Setup Guide
 Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
gateprotect Firewall Packet-Filtering-Core v10.3 Security Target Version:
 Version: Status: Last Update: Classification: 1.0 Release 2013-02-08 public Legal tice This document is provided AS IS with no express or implied warranties. Use the information in this document at your
Version: Status: Last Update: Classification: 1.0 Release 2013-02-08 public Legal tice This document is provided AS IS with no express or implied warranties. Use the information in this document at your
Protection Profile for Portable Storage Media (PSMPP) Common Criteria Protection Profile BSI-CC-PP-0081-2012 Version 1.0
 Protection Profile for Portable Storage Media (PSMPP) Common Criteria Protection Profile BSI-CC-PP-0081-2012 Version 1.0 German Federal Office for Information Security PO Box 20 03 63 D-53133 Bonn Tel.:
Protection Profile for Portable Storage Media (PSMPP) Common Criteria Protection Profile BSI-CC-PP-0081-2012 Version 1.0 German Federal Office for Information Security PO Box 20 03 63 D-53133 Bonn Tel.:
A host-based firewall can be used in addition to a network-based firewall to provide multiple layers of protection.
 A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
VAULTIVE & MICROSOFT: COMPLEMENTARY ENCRYPTION SOLUTIONS. White Paper
 COMPLEMENTARY ENCRYPTION SOLUTIONS White Paper Table of Contents Section I: Vaultive & Microsoft: Complementary Encryption Solutions... 2 Section II: Vaultive is a Microsoft ISV Partner... Appendix A:
COMPLEMENTARY ENCRYPTION SOLUTIONS White Paper Table of Contents Section I: Vaultive & Microsoft: Complementary Encryption Solutions... 2 Section II: Vaultive is a Microsoft ISV Partner... Appendix A:
Features of Exchange Server 2007
 Features of Exchange Server 2007 Built in Protection Exchange Server 2007 includes built in protection with features like Edge Transport, Hosted Filtering Integration, and anti spam filtering and extensibility
Features of Exchange Server 2007 Built in Protection Exchange Server 2007 includes built in protection with features like Edge Transport, Hosted Filtering Integration, and anti spam filtering and extensibility
McAfee Firewall Enterprise v8.2.0 and McAfee Firewall Enterprise Control Center v5.2.0 Security Target
 v8.2.0 and McAfee Firewall Enterprise Control Center v5.2.0 10 January 2012 Version 1.1 Prepared By: Primasec Ltd For McAfee Inc 2340 Energy Park Drive St. Paul, MN 55108 USA Contents 1 Introduction...
v8.2.0 and McAfee Firewall Enterprise Control Center v5.2.0 10 January 2012 Version 1.1 Prepared By: Primasec Ltd For McAfee Inc 2340 Energy Park Drive St. Paul, MN 55108 USA Contents 1 Introduction...
Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123. Instructor Manual
 Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123 Instructor Manual Published: 2013-07-02 SWD-20130702091645092 Contents Advance preparation...7 Required materials...7 Topics
Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123 Instructor Manual Published: 2013-07-02 SWD-20130702091645092 Contents Advance preparation...7 Required materials...7 Topics
Security Target. McAfee Data Loss Prevention Endpoint 9.4 and epolicy Orchestrator 5.1.3. Document Version 1.0
 Security Target McAfee Data Loss Prevention Endpoint 9.4 and epolicy Orchestrator 5.1.3 Document Version 1.0 November 24, 2015 Prepared For: Prepared By: Intel Corporation. 2821 Mission College Blvd. Santa
Security Target McAfee Data Loss Prevention Endpoint 9.4 and epolicy Orchestrator 5.1.3 Document Version 1.0 November 24, 2015 Prepared For: Prepared By: Intel Corporation. 2821 Mission College Blvd. Santa
Installing Policy Patrol on a separate machine
 Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Transport server data paths
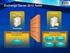 1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
