Security Features and Considerations
|
|
|
- Colin Wells
- 10 years ago
- Views:
Transcription
1 Securing the Unified Communications Enabled Enterprise Integrated communications systems are inherently more secure than traditional standalone phone and messaging systems. Business Communications Challenges In today s global economy, traditional time and geographical boundaries are vanishing. Many businesses have adopted a 24-hours-a-day approach to serving customers, who may be located anywhere in the world, in any time zone. For businesses, government agencies, and academic organizations to thrive in this dynamic market, personnel must remain accessible to colleagues and customers worldwide. Employees who, like the customers they serve, are geographically distributed and mobile require the capability to securely obtain information from wherever they are to help their organizations compete successfully. In fact, research reveals a significant business effect when workgroups experience delays in reaching primary decision makers (Figure 1). Delays are exacerbated when organizations run multiple, standalone systems that do not provide employees with an integrated and secure way to conduct and manage their many forms of communication. Figure 1. Business Effect of Delays in Reaching Primary Decision Makers How Cisco Unified Communications Helps Tying multiple types of communication together into a unified experience supports the increased accessibility needs of global organizations. Cisco Unified Communications a set of telephonyfocused products and technologies accomplishes this by merging voice, video, data, and collaboration applications securely across desktops and mobile devices. Cisco Unified Communications consists of a range of Cisco and partner offerings that include integrated IP telephony, messaging, presence (users location information and availability status), mobility, whiteboarding, and audio and video conferencing. When combined, these collaborative functions boost employee accessibility and, ultimately, customer service. All contents are Copyright Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 5
2 Accelerated Decision Making Combining functions so that they work together greatly helps speed internal communication. For example, clicking names in an electronic directory to automatically generate a conference call yields faster information exchanges and decision making than looking up multiple names and numbers in separate directories, dialing them all, and possibly having to leave callback messages. Having both mobile and desktop phones ring when a call comes through helps avoid unproductive telephone tag because employees can answer calls from nearly anywhere. Improved accessibility helps keep business processes flowing. Improved Call Center and Customer Service Unifying telephony with customer data also allows call center and other personnel throughout the organization to access up-to-date customer histories. This access to current customer information combined with chat and instant messaging for quick consultations with colleagues and experts allows employees ultimately to improve the overall customer experience. Productivity Gains Similarly, a single, secured electronic mailbox that collects messages from multiple phones, systems, and fax machines streamlines the time and effort spent checking and managing multiple messaging systems. These unified mailboxes enhance productivity by making individuals more responsive and by reducing the potential for overlooked messages and delayed replies, which can have costly business consequences. According to a 2005 study by The Radicati Group, Inc., unified messaging alone can add up to 40 minutes of productive time per worker per day. Sage Research, which conducted a study in 2005 for Cisco involving interviews with more than 200 organizations, reports that workers with access to full-featured unified communications systems gain an average of 55 minutes per day in productivity. Aside from the basic capital and operational savings that come from convergence, Cisco Unified Communications offers numerous benefits that boost productivity and help companies ultimately compete with better customer service. To fully reap these benefits, however, organizations must make sure that their unified communications networks remain secured. Unified communications brings several new security challenges to enterprise voice networks; however, conversations and messages actually remain more private than in traditional telephony networks. Security Features and Considerations Some security concerns and solutions, such as toll fraud, remain the same in the unified communications environment as in traditional telephone networks. Today s organizations, however, also face increased regulatory requirements for conversation privacy, message confidentiality, and user and device authentication. Therefore, unified communications strategies must address the security aspects of Sarbanes-Oxley, Gramm-Leach-Bliley (GLB), Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard, European Basel II, and other mandates affecting global organizations directly within the unified communications architecture. Integrating security within the underlying infrastructure also thwarts denial-of-service (DoS) attacks, worms, and other malicious activity that is usually aimed at the data network, but, if successful, could have ramifications for the voice network, too. All contents are Copyright Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 2 of 5
3 Here is an overview of how integrated Cisco Unified Communications security provides protection. Conversation Privacy As indicated, organizations adding telephone calls and related applications (directories, messaging systems, calendars, etc.) to their corporate data networks must protect the privacy of conversations. Voice conversations are actually more secure in a Cisco Unified Communications network environment than in traditional telephone systems. The reason for this security is that Cisco Unified Communications systems allow voice conversations to be encrypted. This encryption takes place from phone to phone, so that the conversation remains secured from end to end. As a result, if a would-be eavesdropper were somehow able to tap into an encrypted phone conversation, the discussion would be unintelligible. Message Confidentiality Similarly, today s integrated voic systems allow enhanced levels of privacy. Businesses can now place conditions on phone extensions that dictate rules about what can and cannot be done. A business, for example, can configure its voic system to allow certain messages to be forwarded but to disallow forwarding on messages marked private. Similarly, the phone system can be configured to allow certain individuals to receive voice messages from third parties through while restricting other employees from doing so. Authentication and Verification Authentication and verification of users, devices, and traffic on a network are essential to any security strategy. An unsecured voice system can sometimes be used as an access point for attacking an organization s data network and disrupting business processes. In such cases, individuals will try to disguise malicious data as voice traffic in hopes that the counterfeit voice traffic will be allowed to pass through traditional data security systems to its intended target. Cisco Unified Communications systems, however, prevent this from happening. They examine all the traffic on the network, separate voice from data traffic, and then verify that what appears to be voice traffic is, indeed, voice. Similarly, personal computers controlled by hackers attached to the network masquerading as printers, fax machines, and telephones can serve as launching pads for attacks. Attackers will sometimes use this device-spoofing method to avoid detection and subsequent removal of the unauthorized devices. To prevent such attacks, the Cisco Unified Communications network authenticates all phones, both wired and wireless, and other telephony-related equipment to verify that they are authorized for use on the network. This helps protect the integrity of communications integral to enterprise, workgroup, and individual productivity. One of the simplest, but most common, threats is an attacker who makes a call and pretends to be someone else to gain access to confidential information. Some businesses have adopted the practice of using Caller ID the incoming phone number paired with the calling party s name to identify callers for automated customer service purposes. Unfortunately, attackers have responded to this tactic by sending fake Caller ID information and masquerading as legitimate callers. Using recently approved worldwide security technology standards, however, unified communications systems now require the calling device to present an additional set of credentials, which are verified by the network. This check helps ensure the authenticity of the device and reduces identity fraud risks. All contents are Copyright Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 3 of 5
4 Foiling Toll Fraud Toll fraud involves someone dialing into an enterprise s phone system and back out onto a longdistance network to steal phone calls from the enterprise. To protect against this type of attack, the IT or telecom department simply sets up the phone system to disallow transfers to extensions that can make outside phone calls. Unified Communications integrates capabilities that allow IT or telecom personnel to control the phone numbers that can be used to transfer calls, send message notification, and provide other functions. Implementing the right policies and systems helps prevent access to long-distance phone numbers; in addition, IT or telecom staff can restrict numbers typically associated with toll fraud, such as international numbers. Preventing Distributed-Denial-of-Service Attacks Perhaps the biggest threat to unified communications comes from distributed DoS (DDoS) attacks aimed at operating systems and applications in the computer data network. Sound security practices, designed to protect the underlying data network, inherently guard the unified communications system against DDoS attacks and the resulting downtime caused by malicious flooding of the network with bogus messages. Deployed at strategic locations throughout a network, Cisco Unified Communications security solutions not only detect DDoS attacks but also identify and block malicious traffic in real time without affecting the flow of legitimate, business-critical transactions. As a result, Cisco DDoS products quickly mitigate even the largest attacks, preserve the continuity of your communications traffic, and help ensure that your critical assets remain protected. Best Practices Securing unified communications can be successfully achieved by taking advantage of the security capabilities already built into your organization s network infrastructure for data protection. Using best practices for securing the underlying data network infrastructure against viruses, unauthorized access, and eavesdropping is important in protecting voice conversations and related applications. Securing the unified communications network requires considering voice, data, and video communications as a system and protecting all the system s components, including the following: Underlying network and application infrastructure Phone switch (also called a call server) Individual phones Various unified applications To protect each of these components, enterprises should merge different skill sets throughout the organization, bringing together voice, network operations, security operations, telephone operations, and business decision makers in an interdisciplinary manner. With more employees becoming geographically dispersed, enterprises should also build in redundant connections from remote locations. This step helps prevent downtime between distributed unified communications equipment and centralized phone switches. IT and telecom staff will be able to logically segment all voice communications-related network traffic from data traffic and help ensure that the voice traffic segment is never sent to data network resources. Summary All contents are Copyright Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 4 of 5
5 Cisco Unified Communications a set integrated, telephony-focused applications, devices, and systems that run on the data network provides a number of benefits: Enhanced worker productivity and accessibility, which ultimately increases customer service levels; accessibility is becoming increasingly important in today s global marketplace, which transcends geographic boundaries and time zones Higher security levels, which help maintain continuity of critical voice services and address global privacy mandates Time savings related to employee communications management Capital and operating cost savings associated with network integration and consolidation Security concerns that arise when adding telephony communications to the network most notably, DDoS threats can be addressed by taking advantage of protection already built into the existing data network. In addition, mechanisms in today s systems for encryption and use policies make unified communications conversations and messaging systems more secure than they were in traditional telephony environments. Circumventing toll fraud involves practices similar to those used in the traditional telephony environment. As your organization adds unified communications applications to the network, you should take a systemic approach to security, addressing all aspects of security in the network infrastructure, including phones, applications, and phone switches. Security also includes building redundant connections from remote locations to ensure continuous unified communications availability. Securely deploying unified communications requires the cross-functional participation of the expert personnel in your organization, combined with the careful planning, development, and implementation of a comprehensive communications security policy. To assist you in this, Cisco provides a broad range of design, testing, and implementation services to help ensure that your company has a unified communications solution in place with full security. To learn more about the business value of Cisco Unified Communication, visit Printed in USA C /07 All contents are Copyright Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 5 of 5
Cisco Advanced Services for Network Security
 Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Data Sheet Cisco Advanced Services for Network Security IP Communications networking the convergence of data, voice, and video onto a single network offers opportunities for reducing communication costs
Cisco Unified CallConnector for Microsoft Windows
 for Microsoft Windows Cisco Unified Communications is a comprehensive IP communications system of voice, video, data, and mobility products and applications. It enables more effective, more secure, more
for Microsoft Windows Cisco Unified Communications is a comprehensive IP communications system of voice, video, data, and mobility products and applications. It enables more effective, more secure, more
Cisco Unified MobilityManager Version 1.2
 Cisco Unified MobilityManager Version 1.2 Cisco Unified MobilityManager Version 1.1, Release 1.2 The Cisco Unified Communications system of voice and IP communications products and applications enables
Cisco Unified MobilityManager Version 1.2 Cisco Unified MobilityManager Version 1.1, Release 1.2 The Cisco Unified Communications system of voice and IP communications products and applications enables
White Paper A SECURITY GUIDE TO PROTECTING IP PHONE SYSTEMS AGAINST ATTACK. A balancing act
 A SECURITY GUIDE TO PROTECTING IP PHONE SYSTEMS AGAINST ATTACK With organizations rushing to adopt Voice over IP (VoIP) technology to cut costs and integrate applications designed to serve customers better,
A SECURITY GUIDE TO PROTECTING IP PHONE SYSTEMS AGAINST ATTACK With organizations rushing to adopt Voice over IP (VoIP) technology to cut costs and integrate applications designed to serve customers better,
Deploying Firewalls Throughout Your Organization
 Deploying Firewalls Throughout Your Organization Avoiding break-ins requires firewall filtering at multiple external and internal network perimeters. Firewalls have long provided the first line of defense
Deploying Firewalls Throughout Your Organization Avoiding break-ins requires firewall filtering at multiple external and internal network perimeters. Firewalls have long provided the first line of defense
Cisco Unified CallConnector for Microsoft Dynamics CRM
 Cisco Unified CallConnector for Microsoft Dynamics CRM Cisco Unified Communications is a complete IP communications system of voice, video, data, and mobility products and applications. It brings together
Cisco Unified CallConnector for Microsoft Dynamics CRM Cisco Unified Communications is a complete IP communications system of voice, video, data, and mobility products and applications. It brings together
WHITE PAPER. www.fusionstorm.com. The Business Benefits of Upgrading Legacy IP Communications Systems. www.fusionstorm.com
 WHITE PaPEr: Easing the Way to the Cloud: 1 WHITE PAPER The Business Benefits of Upgrading Legacy IP Communications Systems 2 WHITE PAPER: The Business Benefits of Upgrading Legacy IP Communications Systems
WHITE PaPEr: Easing the Way to the Cloud: 1 WHITE PAPER The Business Benefits of Upgrading Legacy IP Communications Systems 2 WHITE PAPER: The Business Benefits of Upgrading Legacy IP Communications Systems
Cisco Unified CallConnector for Microsoft Windows
 Cisco Unified CallConnector for Microsoft Windows Cisco Unified Communications is a comprehensive IP communications system of voice, video, data, and mobility products and applications. It enables more
Cisco Unified CallConnector for Microsoft Windows Cisco Unified Communications is a comprehensive IP communications system of voice, video, data, and mobility products and applications. It enables more
The Business Case for Unified Communications November 2013
 Wikipedia s definition of Unified Communications (UC): UC is the integration of real-time communication services, such as: Instant messaging (chat) Presence information Telephony (including IP telephony)
Wikipedia s definition of Unified Communications (UC): UC is the integration of real-time communication services, such as: Instant messaging (chat) Presence information Telephony (including IP telephony)
How To Deploy Cisco Jabber For Windows 2.5.1 On A Server Or A Network (For A Non-Profit) For A Corporate Network (A.Net) For Free (For Non Profit) For An Enterprise) Or
 Deployment Models Cisco Jabber for Windows provides two deployment models, on-premises or cloud-based. Learn about each deployment model and review the available options for on-premises and cloud-based
Deployment Models Cisco Jabber for Windows provides two deployment models, on-premises or cloud-based. Learn about each deployment model and review the available options for on-premises and cloud-based
How To Use Blackberry Mobile Voice System On A Blackberry Phone
 B l a c k B e r r y M o b i l e Vo i c e S y s t e m BlackBerry Mobile Voice System Mobile Unified Communications Mobile Voice System ( MVS) is designed to unify desk phone features on smartphones and
B l a c k B e r r y M o b i l e Vo i c e S y s t e m BlackBerry Mobile Voice System Mobile Unified Communications Mobile Voice System ( MVS) is designed to unify desk phone features on smartphones and
The Cisco Smart Business Communications System
 The Cisco Smart Business Communications System Connect Your Employees to Suppliers and Customers, and Your Business to the World. For a small business like yours to communicate effectively with suppliers
The Cisco Smart Business Communications System Connect Your Employees to Suppliers and Customers, and Your Business to the World. For a small business like yours to communicate effectively with suppliers
Mitigating the Security Risks of Unified Communications
 2009 International Conference on Computer Engineering and Applications IPCSIT vol.2 (2011) (2011) IACSIT Press, Singapore Mitigating the Security Risks of Unified Communications Fernando Almeida 1 +, Jose
2009 International Conference on Computer Engineering and Applications IPCSIT vol.2 (2011) (2011) IACSIT Press, Singapore Mitigating the Security Risks of Unified Communications Fernando Almeida 1 +, Jose
Written Testimony of John L. Barnes Director of Product Development Verizon Business. Hearing on VoIP: Who Has Jurisdiction to Tax It?
 Written Testimony of John L. Barnes Director of Product Development Verizon Business Hearing on VoIP: Who Has Jurisdiction to Tax It? House Committee on the Judiciary Subcommittee on Commercial and Administrative
Written Testimony of John L. Barnes Director of Product Development Verizon Business Hearing on VoIP: Who Has Jurisdiction to Tax It? House Committee on the Judiciary Subcommittee on Commercial and Administrative
COSC 472 Network Security
 COSC 472 Network Security Instructor: Dr. Enyue (Annie) Lu Office hours: http://faculty.salisbury.edu/~ealu/schedule.htm Office room: HS114 Email: [email protected] Course information: http://faculty.salisbury.edu/~ealu/cosc472/cosc472.html
COSC 472 Network Security Instructor: Dr. Enyue (Annie) Lu Office hours: http://faculty.salisbury.edu/~ealu/schedule.htm Office room: HS114 Email: [email protected] Course information: http://faculty.salisbury.edu/~ealu/cosc472/cosc472.html
How To Protect Your Network From Attack From A Network Security Threat
 Cisco Security Services Cisco Security Services help you defend your business from evolving security threats, enhance the efficiency of your internal staff and processes, and increase the return on your
Cisco Security Services Cisco Security Services help you defend your business from evolving security threats, enhance the efficiency of your internal staff and processes, and increase the return on your
The all-in-one Unified Communications solution for SMBs.
 OpenScape Business The all-in-one Unified Communications solution for SMBs. Improve your performance and take your business to the next level with Unified Communications. Amplifying opportunities The success
OpenScape Business The all-in-one Unified Communications solution for SMBs. Improve your performance and take your business to the next level with Unified Communications. Amplifying opportunities The success
VoIP: The Evolving Solution and the Evolving Threat. Copyright 2004 Internet Security Systems, Inc. All rights reserved worldwide
 VoIP: The Evolving Solution and the Evolving Threat Copyright 2004 Internet Security Systems, Inc. All rights reserved worldwide VoIP: The Evolving Solution and the Evolving Threat An ISS Whitepaper 2
VoIP: The Evolving Solution and the Evolving Threat Copyright 2004 Internet Security Systems, Inc. All rights reserved worldwide VoIP: The Evolving Solution and the Evolving Threat An ISS Whitepaper 2
Avaya Unified Communications Can Reduce Cell Phone Expenses
 WHITE PAPER Avaya Unified Communications Can Reduce Cell Phone Expenses June 2008 Table of Contents Introduction... 1 Section 1: Reduce Inbound Minutes... 1 Section 2: Reduce Outbound Minutes... 2 Section
WHITE PAPER Avaya Unified Communications Can Reduce Cell Phone Expenses June 2008 Table of Contents Introduction... 1 Section 1: Reduce Inbound Minutes... 1 Section 2: Reduce Outbound Minutes... 2 Section
VOIP SECURITY: BEST PRACTICES TO SAFEGUARD YOUR NETWORK ======
 VOIP SECURITY: BEST PRACTICES TO SAFEGUARD YOUR NETWORK ====== Table of Contents Introduction to VoIP Security... 2 Meet Our Expert - Momentum Telecom... 2 BroadWorks... 2 VoIP Vulnerabilities... 3 Call
VOIP SECURITY: BEST PRACTICES TO SAFEGUARD YOUR NETWORK ====== Table of Contents Introduction to VoIP Security... 2 Meet Our Expert - Momentum Telecom... 2 BroadWorks... 2 VoIP Vulnerabilities... 3 Call
Cisco Virtualization Experience Infrastructure: Secure the Virtual Desktop
 White Paper Cisco Virtualization Experience Infrastructure: Secure the Virtual Desktop What You Will Learn Cisco Virtualization Experience Infrastructure (VXI) delivers a service-optimized desktop virtualization
White Paper Cisco Virtualization Experience Infrastructure: Secure the Virtual Desktop What You Will Learn Cisco Virtualization Experience Infrastructure (VXI) delivers a service-optimized desktop virtualization
Cisco Unified Communications
 Cisco Unified Communications More Effectively Connecting People to Improve the Communications Experience Today s organizations must contend with increasingly complex communications environments featuring
Cisco Unified Communications More Effectively Connecting People to Improve the Communications Experience Today s organizations must contend with increasingly complex communications environments featuring
The Cisco ASA 5500 as a Superior Firewall Solution
 The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
Fabrizio Volpe. MVP Directory Services MCITP Lync 2010. @Fabriziovlp. [email protected]. http://www.linkedin.com/in/fabriziov
 Fabrizio Volpe MVP Directory Services MCITP Lync 2010 @Fabriziovlp [email protected] http://www.linkedin.com/in/fabriziov Agenda Intro to Lync Server Lync Features : Presence Integration with Sharepoint,
Fabrizio Volpe MVP Directory Services MCITP Lync 2010 @Fabriziovlp [email protected] http://www.linkedin.com/in/fabriziov Agenda Intro to Lync Server Lync Features : Presence Integration with Sharepoint,
Unified Communications. Fulfilling the promise of UNIVERGE 360
 Unified Communications Fulfilling the promise of UNIVERGE 360 Unified Communications in Today s World Businesses today are suffering from communication and information overload. Unified Communications
Unified Communications Fulfilling the promise of UNIVERGE 360 Unified Communications in Today s World Businesses today are suffering from communication and information overload. Unified Communications
Security and Risk Analysis of VoIP Networks
 Security and Risk Analysis of VoIP Networks S.Feroz and P.S.Dowland Network Research Group, University of Plymouth, United Kingdom e-mail: [email protected] Abstract This paper address all
Security and Risk Analysis of VoIP Networks S.Feroz and P.S.Dowland Network Research Group, University of Plymouth, United Kingdom e-mail: [email protected] Abstract This paper address all
IP TELEPHONY. Incorporating Voice over Internet Protocol (VoIP)
 Incorporating Voice over Internet Protocol (VoIP) IP Telephony Incorporating Voice over Internet Protocol (VoIP) Dramatically improve the way you work. Everyone's talking about Voice over Internet Protocol
Incorporating Voice over Internet Protocol (VoIP) IP Telephony Incorporating Voice over Internet Protocol (VoIP) Dramatically improve the way you work. Everyone's talking about Voice over Internet Protocol
Network Virtualization
 . White Paper Network Services Virtualization What Is Network Virtualization? Business and IT leaders require a more responsive IT infrastructure that can help accelerate business initiatives and remove
. White Paper Network Services Virtualization What Is Network Virtualization? Business and IT leaders require a more responsive IT infrastructure that can help accelerate business initiatives and remove
How to Determine TCO for IP Telephone Systems
 How to Determine TCO for IP Telephone Systems HOW TO DETERMINE TCO FOR IP TELEPHONE SYSTEMS 2 INSIDE: 3 4 5 6 7 8 9 10 11 12 Getting Started What is TCO for UC? Count up Operational Costs Consider the
How to Determine TCO for IP Telephone Systems HOW TO DETERMINE TCO FOR IP TELEPHONE SYSTEMS 2 INSIDE: 3 4 5 6 7 8 9 10 11 12 Getting Started What is TCO for UC? Count up Operational Costs Consider the
Cisco and IBM: Enhancing the Way People Work Through Unified Communications
 Cisco and IBM: Enhancing the Way People Work Through Unified Communications WHITEPAPER August 2007 Cisco and IBM Strategic Alliance: Whitepaper Table of Contents Executive Summary... 1 A Winning Approach...
Cisco and IBM: Enhancing the Way People Work Through Unified Communications WHITEPAPER August 2007 Cisco and IBM Strategic Alliance: Whitepaper Table of Contents Executive Summary... 1 A Winning Approach...
CompleteCare+ Enterprise Voice
 There s more to communications than email: Unified communication and collaboration, information sharing and team productivity services Contents 1. Executive Summary 2. Introduction Enterprise-level communications
There s more to communications than email: Unified communication and collaboration, information sharing and team productivity services Contents 1. Executive Summary 2. Introduction Enterprise-level communications
Introducing Cisco Unified Communications Express
 CHAPTER 1 Introducing Cisco Unified Communications Express Cisco Unified Communications Express is an award-winning communications solution that is provided with the Cisco Integrated Services Router portfolio.
CHAPTER 1 Introducing Cisco Unified Communications Express Cisco Unified Communications Express is an award-winning communications solution that is provided with the Cisco Integrated Services Router portfolio.
VoIP Solutions Guide Everything You Need to Know
 VoIP Solutions Guide Everything You Need to Know Simplify, Save, Scale VoIP: The Next Generation Phone Service Ready to Adopt VoIP? 10 Things You Need to Know 1. What are my phone system options? Simplify,
VoIP Solutions Guide Everything You Need to Know Simplify, Save, Scale VoIP: The Next Generation Phone Service Ready to Adopt VoIP? 10 Things You Need to Know 1. What are my phone system options? Simplify,
Plans Comparison. 855.900.KUMO (5866) [email protected]. [email protected] www.joinkumo.com 855.900.KUMO
 Plans Comparison 855.900.KUMO (5866) [email protected] Page 1 of 5 Elevate your business with scalable solutions and accessible services in the cloud. ON-DEMAND FLEXIBILITY Fully On-Demand Cloud Services
Plans Comparison 855.900.KUMO (5866) [email protected] Page 1 of 5 Elevate your business with scalable solutions and accessible services in the cloud. ON-DEMAND FLEXIBILITY Fully On-Demand Cloud Services
Cisco Unified Personal Communicator
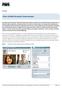 Data Sheet Cisco Unified Personal Communicator An integral part of the Cisco Unified Communications family of products, Cisco Unified Personal Communicator is a desktop computer application that helps
Data Sheet Cisco Unified Personal Communicator An integral part of the Cisco Unified Communications family of products, Cisco Unified Personal Communicator is a desktop computer application that helps
Securing SIP Trunks APPLICATION NOTE. www.sipera.com
 APPLICATION NOTE Securing SIP Trunks SIP Trunks are offered by Internet Telephony Service Providers (ITSPs) to connect an enterprise s IP PBX to the traditional Public Switched Telephone Network (PSTN)
APPLICATION NOTE Securing SIP Trunks SIP Trunks are offered by Internet Telephony Service Providers (ITSPs) to connect an enterprise s IP PBX to the traditional Public Switched Telephone Network (PSTN)
Security Practices for Online Collaboration and Social Media
 Cisco IT Best Practice Collaboration Security Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 2013 Cisco and/or its affiliates. All rights reserved.
Cisco IT Best Practice Collaboration Security Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 2013 Cisco and/or its affiliates. All rights reserved.
Solution Brief. Secure and Assured Networking for Financial Services
 Solution Brief Secure and Assured Networking for Financial Services Financial Services Solutions Page Introduction To increase competitiveness, financial institutions rely heavily on their networks to
Solution Brief Secure and Assured Networking for Financial Services Financial Services Solutions Page Introduction To increase competitiveness, financial institutions rely heavily on their networks to
BlackBerry Mobile Voice System
 BlackBerry Mobile Voice System Mobile Unified Communications BlackBerry Mobile Voice System (BlackBerry MVS) brings desk phone features to BlackBerry smartphones. Work with one business number at the office
BlackBerry Mobile Voice System Mobile Unified Communications BlackBerry Mobile Voice System (BlackBerry MVS) brings desk phone features to BlackBerry smartphones. Work with one business number at the office
ipecs UCS Unified Communications Solution Easy to access and activate Highlights Single server solution
 ipecs UCS Unified Communications Solution In today s world of remote and dispersed workers, the ipecs UCS application provides tools to enhance productivity and mobility while improving employee collaboration
ipecs UCS Unified Communications Solution In today s world of remote and dispersed workers, the ipecs UCS application provides tools to enhance productivity and mobility while improving employee collaboration
BlackBerry Mobile Voice System
 BlackBerry Mobile Voice System BlackBerry Mobile Voice System Mobile Unified Communications BlackBerry Mobile Voice System (BlackBerry MVS) brings desk phone features to BlackBerry smartphones. Work with
BlackBerry Mobile Voice System BlackBerry Mobile Voice System Mobile Unified Communications BlackBerry Mobile Voice System (BlackBerry MVS) brings desk phone features to BlackBerry smartphones. Work with
Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media
 January 2012 Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 All contents are Copyright 1992 2012 Cisco Systems, Inc. All rights reserved. This document
January 2012 Cisco on Cisco Best Practice Security Practices for Online Collaboration and Social Media January 2012 All contents are Copyright 1992 2012 Cisco Systems, Inc. All rights reserved. This document
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE
 AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
White paper. TrusGuard DPX: Complete Protection against Evolving DDoS Threats. AhnLab, Inc.
 TrusGuard DPX: Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls...
TrusGuard DPX: Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls...
Ingate Firewall/SIParator SIP Security for the Enterprise
 Ingate Firewall/SIParator SIP Security for the Enterprise Ingate Systems February, 2013 Ingate Systems AB (publ) Tel: +46 8 600 77 50 BACKGROUND... 1 1 NETWORK SECURITY... 2 2 WHY IS VOIP SECURITY IMPORTANT?...
Ingate Firewall/SIParator SIP Security for the Enterprise Ingate Systems February, 2013 Ingate Systems AB (publ) Tel: +46 8 600 77 50 BACKGROUND... 1 1 NETWORK SECURITY... 2 2 WHY IS VOIP SECURITY IMPORTANT?...
Boosting Business Mobility and Responsiveness with the Cisco Unified Wireless Network
 Solution Overivew Boosting Business Mobility and Responsiveness with the Cisco Unified Wireless Network EXECUTIVE SUMMARY Today s businesses are turning to wireless networking to give employees immediate
Solution Overivew Boosting Business Mobility and Responsiveness with the Cisco Unified Wireless Network EXECUTIVE SUMMARY Today s businesses are turning to wireless networking to give employees immediate
Voice Over Internet Protocol (VOIP)
 Voice Over Internet Protocol (VOIP) Helping with your telecoms management Voice over Internet Protocol (VoIP) What is VoIP? VoIP is the ability to transmit voice over the Internet VoIP was adopted by the
Voice Over Internet Protocol (VOIP) Helping with your telecoms management Voice over Internet Protocol (VoIP) What is VoIP? VoIP is the ability to transmit voice over the Internet VoIP was adopted by the
Whitepaper WHY VOICE IN THE CLOUD
 WHY VOICE IN THE CLOUD Why Voice in the Cloud 2 TABLE OF CONTENTS Introduction... 3 Lower Cost... 4 MINIMAL CAPITAL REQUIREMENTS... 4 COMMODITY EQUIPMENT... 4 HIGHER RESOURCE UTILIZATION... 4 PREDICTABLE
WHY VOICE IN THE CLOUD Why Voice in the Cloud 2 TABLE OF CONTENTS Introduction... 3 Lower Cost... 4 MINIMAL CAPITAL REQUIREMENTS... 4 COMMODITY EQUIPMENT... 4 HIGHER RESOURCE UTILIZATION... 4 PREDICTABLE
Best Practices for Securing IP Telephony
 Best Practices for Securing IP Telephony Irwin Lazar, CISSP Senior Analyst Burton Group Agenda VoIP overview VoIP risks Mitigation strategies Recommendations VoIP Overview Hosted by VoIP Functional Diagram
Best Practices for Securing IP Telephony Irwin Lazar, CISSP Senior Analyst Burton Group Agenda VoIP overview VoIP risks Mitigation strategies Recommendations VoIP Overview Hosted by VoIP Functional Diagram
Leveraging innovative security solutions for government. Helping to protect government IT infrastructure, meet compliance demands and reduce costs
 IBM Global Technology Services Leveraging innovative security solutions for government. Helping to protect government IT infrastructure, meet compliance demands and reduce costs Achieving a secure government
IBM Global Technology Services Leveraging innovative security solutions for government. Helping to protect government IT infrastructure, meet compliance demands and reduce costs Achieving a secure government
Unified Communications, Diverse Benefits
 TECHNOLOGY SOLUTIONS Unified Communications, Diverse Benefits Adopting a unified communications platform increases productivity, reduces costs and improves end-user service. Your staff may sit in cubicles
TECHNOLOGY SOLUTIONS Unified Communications, Diverse Benefits Adopting a unified communications platform increases productivity, reduces costs and improves end-user service. Your staff may sit in cubicles
Fundamentals of Information Systems Security Unit 1 Information Systems Security Fundamentals
 Fundamentals of Information Systems Security Unit 1 Information Systems Security Fundamentals Learning Objective Explain the concepts of information systems security (ISS) as applied to an IT infrastructure.
Fundamentals of Information Systems Security Unit 1 Information Systems Security Fundamentals Learning Objective Explain the concepts of information systems security (ISS) as applied to an IT infrastructure.
Energy Company Reduces Costs by Upgrading Communications Solution
 Microsoft Lync Server 2010 Customer Solution Case Study Energy Company Reduces Costs by Upgrading Communications Solution Overview Country or Region: Indonesia Industry: Energy Customer Profile MedcoEnergi
Microsoft Lync Server 2010 Customer Solution Case Study Energy Company Reduces Costs by Upgrading Communications Solution Overview Country or Region: Indonesia Industry: Energy Customer Profile MedcoEnergi
KISUMU LAW COURTS: SPECIFICATIONS FOR A UNIFIED COMMUNICATION SYSTEM / VOICE OVER INTERNET PROTOCOL (VOIP) SOLUTION. Page 54 of 60
 SPECIFICATIONS FOR A UNIFIED COMMUNICATION SYSTEM / VOICE OVER INTERNET PROTOCOL (VOIP) SOLUTION Page 54 of 60 UNIFIED COMMUNICATION SYSTEM (VOIP) PROPOSAL FOR KISUMU JUDICIARY COURTS. 1.0 PARTICULARS
SPECIFICATIONS FOR A UNIFIED COMMUNICATION SYSTEM / VOICE OVER INTERNET PROTOCOL (VOIP) SOLUTION Page 54 of 60 UNIFIED COMMUNICATION SYSTEM (VOIP) PROPOSAL FOR KISUMU JUDICIARY COURTS. 1.0 PARTICULARS
Accelerate with OpenScape Office
 Accelerate with OpenScape Office Take your business to the next level with Unified Communications and Collaboration. Our UCC solutions can help your business - no matter how big or small get more done
Accelerate with OpenScape Office Take your business to the next level with Unified Communications and Collaboration. Our UCC solutions can help your business - no matter how big or small get more done
Complete Protection against Evolving DDoS Threats
 Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls... 3 Intrusion
Complete Protection against Evolving DDoS Threats AhnLab, Inc. Table of Contents Introduction... 2 The Evolution of DDoS Attacks... 2 Typical Protection against DDoS Attacks... 3 Firewalls... 3 Intrusion
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE
 AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
Oracle s Solution for Secure Remote Workers. Providing Protected Access to Enterprise Communications
 Oracle s Solution for Secure Remote Workers Providing Protected Access to Enterprise Communications Our forecast shows that the worldwide mobile worker population will increase to more than 1.3 billion
Oracle s Solution for Secure Remote Workers Providing Protected Access to Enterprise Communications Our forecast shows that the worldwide mobile worker population will increase to more than 1.3 billion
1 Product. Open Text is the leading fax server vendor in the world. *
 1 Product Open Text Fax s Replace fax machines and inefficient paper processes with efficient and secure computer-based faxing and electronic document delivery Open Text is the leading fax server vendor
1 Product Open Text Fax s Replace fax machines and inefficient paper processes with efficient and secure computer-based faxing and electronic document delivery Open Text is the leading fax server vendor
Network Security: Introduction
 Network Security: Introduction 1. Network security models 2. Vulnerabilities, threats and attacks 3. Basic types of attacks 4. Managing network security 1. Network security models Security Security has
Network Security: Introduction 1. Network security models 2. Vulnerabilities, threats and attacks 3. Basic types of attacks 4. Managing network security 1. Network security models Security Security has
Internet Content Provider Safeguards Customer Networks and Services
 Internet Content Provider Safeguards Customer Networks and Services Synacor used Cisco network infrastructure and security solutions to enhance network protection and streamline compliance. NAME Synacor
Internet Content Provider Safeguards Customer Networks and Services Synacor used Cisco network infrastructure and security solutions to enhance network protection and streamline compliance. NAME Synacor
IBM System i Integrated Collaboration
 Delivering on the Promise IBM System i Integrated Collaboration Highlights Integrate your voice, collaboration and business applications on a single system Boost customer satisfaction and loyalty by enhancing
Delivering on the Promise IBM System i Integrated Collaboration Highlights Integrate your voice, collaboration and business applications on a single system Boost customer satisfaction and loyalty by enhancing
Voice over Internet Protocol. Kristie Prinz. The Prinz Law Office
 Voice over Internet Protocol Kristie Prinz The Prinz Law Office I. What is Voice over Internet Protocol ( VoIP )? Voice over Internet Protocol ( VoIP ) is a technology, which facilitates the transmission
Voice over Internet Protocol Kristie Prinz The Prinz Law Office I. What is Voice over Internet Protocol ( VoIP )? Voice over Internet Protocol ( VoIP ) is a technology, which facilitates the transmission
Achieving Truly Secure Cloud Communications. How to navigate evolving security threats
 Achieving Truly Secure Cloud Communications How to navigate evolving security threats Security is quickly becoming the primary concern of many businesses, and protecting VoIP vulnerabilities is critical.
Achieving Truly Secure Cloud Communications How to navigate evolving security threats Security is quickly becoming the primary concern of many businesses, and protecting VoIP vulnerabilities is critical.
Security. CLOUD VIDEO CONFERENCING AND CALLING Whitepaper. October 2015. Page 1 of 9
 Security CLOUD VIDEO CONFERENCING AND CALLING Whitepaper October 2015 Page 1 of 9 Contents Introduction...3 Security risks when endpoints are placed outside of firewalls...3 StarLeaf removes the risk with
Security CLOUD VIDEO CONFERENCING AND CALLING Whitepaper October 2015 Page 1 of 9 Contents Introduction...3 Security risks when endpoints are placed outside of firewalls...3 StarLeaf removes the risk with
plantemoran.com Understanding & Applying Unified Communications
 plantemoran.com Understanding & Applying Unified Communications Confusion in the Market UC means different things Many products with Unified in the name UC is often sold as a thing you buy Integrated VM
plantemoran.com Understanding & Applying Unified Communications Confusion in the Market UC means different things Many products with Unified in the name UC is often sold as a thing you buy Integrated VM
Network Infrastructure Data Center Wireless Telephone Video Network Security Surveillance
 Network Infrastructure Data Center Wireless Telephone Video Network Security Surveillance The Coulee Regions leading Premier Certified Cisco partner Architect Enhance Install 3RT Networks provides you
Network Infrastructure Data Center Wireless Telephone Video Network Security Surveillance The Coulee Regions leading Premier Certified Cisco partner Architect Enhance Install 3RT Networks provides you
Securing Unified Communications for Healthcare
 Securing Unified Communications for Healthcare Table of Contents Securing UC A Unique Process... 2 Fundamental Components of a Healthcare UC Security Architecture... 3 Making Unified Communications Secure
Securing Unified Communications for Healthcare Table of Contents Securing UC A Unique Process... 2 Fundamental Components of a Healthcare UC Security Architecture... 3 Making Unified Communications Secure
collaboration Keeping people in touch efficiently
 collaboration Keeping people in touch efficiently What is collaboration? At its best, unified communications (UC) is just what it says it enables better interaction between people by integrating what were
collaboration Keeping people in touch efficiently What is collaboration? At its best, unified communications (UC) is just what it says it enables better interaction between people by integrating what were
Preemptive security solutions for healthcare
 Helping to secure critical healthcare infrastructure from internal and external IT threats, ensuring business continuity and supporting compliance requirements. Preemptive security solutions for healthcare
Helping to secure critical healthcare infrastructure from internal and external IT threats, ensuring business continuity and supporting compliance requirements. Preemptive security solutions for healthcare
DigiDial- VoIP SSMM Service Overview No Boundaries outside the box of traditional telephony P er ver OecioV
 DigiDial-VoIP is a business-grade Voice over IP service that is hosted on DigiLink s IP network and provides a robust, low-cost enterprise voice solution, replacing costly PBX or Centrex service with the
DigiDial-VoIP is a business-grade Voice over IP service that is hosted on DigiLink s IP network and provides a robust, low-cost enterprise voice solution, replacing costly PBX or Centrex service with the
Cisco Business Edition 3000
 Solution Overview Cisco Business Edition 3000 Value, Simplicity, and Essential Features for Small and Medium-Sized Businesses Cisco Business Edition 3000 provides you essential collaboration capabilities
Solution Overview Cisco Business Edition 3000 Value, Simplicity, and Essential Features for Small and Medium-Sized Businesses Cisco Business Edition 3000 provides you essential collaboration capabilities
Accelerate with OpenScape Office
 Accelerate with OpenScape Office Take your business to the next level with Unified Communications and Collaboration. Our UCC solutions can help your business - no matter how big or small get more done
Accelerate with OpenScape Office Take your business to the next level with Unified Communications and Collaboration. Our UCC solutions can help your business - no matter how big or small get more done
Six Questions to Answer When Buying a Phone System
 2016 NEW PHONE SYSTEM BUYER S GUIDE Six Questions to Answer When Buying a Phone System In addition to the most comprehensive portfolio of voice communications, data and wireless networking products in
2016 NEW PHONE SYSTEM BUYER S GUIDE Six Questions to Answer When Buying a Phone System In addition to the most comprehensive portfolio of voice communications, data and wireless networking products in
SIP Security Controllers. Product Overview
 SIP Security Controllers Product Overview Document Version: V1.1 Date: October 2008 1. Introduction UM Labs have developed a range of perimeter security gateways for VoIP and other applications running
SIP Security Controllers Product Overview Document Version: V1.1 Date: October 2008 1. Introduction UM Labs have developed a range of perimeter security gateways for VoIP and other applications running
Oracle s Session Initiation Protocol Trunking Solution. Increase Agility and Reduce Costs with Session Initiation Protocol Trunks
 Oracle s Session Initiation Protocol Trunking Solution Increase Agility and Reduce Costs with Session Initiation Protocol Trunks Oracle s SIP trunking solution is designed to enable the hyperconnected
Oracle s Session Initiation Protocol Trunking Solution Increase Agility and Reduce Costs with Session Initiation Protocol Trunks Oracle s SIP trunking solution is designed to enable the hyperconnected
For Windows. 2012 Microsoft Corporation. All rights reserved.
 For Windows 1 About Microsoft Lync... 4 Lync Window... 5 Audio... 6 Set up your audio device... 6 Make a call... 6 Answer a call... 7 Use audio call controls... 7 Check voicemail... 7 Invite more people
For Windows 1 About Microsoft Lync... 4 Lync Window... 5 Audio... 6 Set up your audio device... 6 Make a call... 6 Answer a call... 7 Use audio call controls... 7 Check voicemail... 7 Invite more people
Wireless Local Area Network Deployment and Security Practices
 HIGHLIGHTS AUDIT REPORT Wireless Local Area Network Deployment and April 24, 2014 Report Number HIGHLIGHTS BACKGROUND: The U.S. Postal Service is committed to providing a high quality, secure, and cost-effective
HIGHLIGHTS AUDIT REPORT Wireless Local Area Network Deployment and April 24, 2014 Report Number HIGHLIGHTS BACKGROUND: The U.S. Postal Service is committed to providing a high quality, secure, and cost-effective
Business Cloud Services
 Business Cloud Services Unified Communications in the Cloud Flexible. Economical. Powerful. UNIVERGE BLUE Business Cloud Services by NEC delivers enterprise-grade Voice, Mobility, Messaging, Presence,
Business Cloud Services Unified Communications in the Cloud Flexible. Economical. Powerful. UNIVERGE BLUE Business Cloud Services by NEC delivers enterprise-grade Voice, Mobility, Messaging, Presence,
IP Contact Center: Realize the Full Business Potential of IP Contact Centers
 IP Contact Center: Realize the Full Business Potential of IP Contact Centers WHITEPAPER The joint solution from Cisco and IBM provides people, processes, and technology needed to maximize the return on
IP Contact Center: Realize the Full Business Potential of IP Contact Centers WHITEPAPER The joint solution from Cisco and IBM provides people, processes, and technology needed to maximize the return on
PAVING THE PATH TO THE ELIMINATION OF THE TRADITIONAL DMZ
 PAVING THE PATH TO THE ELIMINATION A RSACCESS WHITE PAPER 1 The Traditional Role of DMZ 2 The Challenges of today s DMZ deployments 2.1 Ensuring the Security of Application and Data Located in the DMZ
PAVING THE PATH TO THE ELIMINATION A RSACCESS WHITE PAPER 1 The Traditional Role of DMZ 2 The Challenges of today s DMZ deployments 2.1 Ensuring the Security of Application and Data Located in the DMZ
