Defining Distributed Systems. Distribuerade system. Exemples of DS: Intranet. Exemples of DS: Internet. Exemples of DS: Mobile Computing
|
|
|
- Damian Shaw
- 10 years ago
- Views:
Transcription
1 Defining Distributed Systems Distribuerade system C-kurs 5 poäng HT-02 A distributed system is one in which components located at networked computers communicate and coordinate their actions only by passing messages Om en maskin som du aldrig hört talas om går ner och det hindrar dig från att jobba så har du ett distribuerat system 3/9-02 Distribuerade system - Jonny Pettersson, UmU 1 3/9-02 Distribuerade system - Jonny Pettersson, UmU 2 Exemples of DS: Internet Exemples of DS: Intranet print and other s Desktop computers ISP intranet Web Local area network backbone File print desktop computer: : network link: satellite link the rest of the Internet router/firewall other s 3/9-02 Distribuerade system - Jonny Pettersson, UmU 3 3/9-02 Distribuerade system - Jonny Pettersson, UmU 4 Exemples of DS: Mobile Computing Consequences of DS Internet Concurrency No global clock Independent failures Host intranet Wireless LAN WAP gateway Home intranet Printer Camera Mobile phone Laptop Host site 3/9-02 Distribuerade system - Jonny Pettersson, UmU 5 3/9-02 Distribuerade system - Jonny Pettersson, UmU 6 1
2 Vad händer i dag? Kursledning Kursplan Förra året Årets kurs Registrering Introduktion till Distribuerade system Kursplan Kursdeltagarna ska förvärva kunskaper om teoretiska modeller för distribuerade system kunskaper om problem och lösningar i samband med design och konstruktion av distribuerade system Kursen behandlar: Arkitekturmodeller för distribuerade system Klient-, peer-to-peer, transaktioner, transparens, namngivning, felhantering, resursfördelning och synkronisering Datasäkerhetsaspekter i ett brett perspektiv Metoder och tekniker för datasäkerhet Distribuerad programmering och middleware 3/9-02 Distribuerade system - Jonny Pettersson, UmU 7 3/9-02 Distribuerade system - Jonny Pettersson, UmU 8 Kursplan (forts) Moment 1, teoridel, 3 poäng Teorier, metoder, algoritmer och principer Moment 2, laborationsdel, 2 poäng Obligatoriska uppgifter 3/9-02 Distribuerade system - Jonny Pettersson, UmU 9 Förra året Flera föreläsare Kursdisposition Bra, men spridda åsikter Gruppövningar Den var bra Kurslitteratur Bra, men formell och tungläst Koppling teori och labbar Okej, blandat Tyngd på labbar Lagom Lite högre arbetsbelastning än snittet 3/9-02 Distribuerade system - Jonny Pettersson, UmU 10 Årets kurs Kurslitteratur Fokus på Middleware programmering Säkerhet Distribuerade algoritmer Upplägg Föreläsningar Gruppövningar Laborationer Laborationer 3 stycken Debatt om säkerhet E-handelssystem, huvudlabben En liten om EJB Tid till förfogande Grupper om 2 eller 3, gäller ej debatten Koppling till teorin MA336 3/9-02 Distribuerade system - Jonny Pettersson, UmU 11 3/9-02 Distribuerade system - Jonny Pettersson, UmU 12 2
3 Undervisning Pedagogisk tanke Val av presentationshjälpmedel OH-bilder Källa Innehåll Språk Vad bör man lära sig? The rest of today Challenges Architectural models Fundamental models 3/9-02 Distribuerade system - Jonny Pettersson, UmU 13 3/9-02 Distribuerade system - Jonny Pettersson, UmU 14 Resource sharing: The Web Distributed Systems File system of Web s Protocols Browsers Internet What is distributed? Data Computing power Services Entities Security Name space Time Challenges Heterogeneity Openness Security Scalability Failure handling Concurrency Transparency Activity.html 3/9-02 Distribuerade system - Jonny Pettersson, UmU 15 3/9-02 Distribuerade system - Jonny Pettersson, UmU 16 Heterogeneity Openness Applies to Networks Computer hardware Operating systems Programming languages Implementations by different developers Middleware - software layer that provides programming abstraction and mask heterogeneity Mobile code - code that can be sent from one computer to another Extended and reimplemented Very important in the industry RFC (requests for comments) You ll use it in your work. In this course. And probably in the rest of your life Open systems; Key interfaces are published Open distributed systems can be constructed from heterogeneous hardware and software. 3/9-02 Distribuerade system - Jonny Pettersson, UmU 17 3/9-02 Distribuerade system - Jonny Pettersson, UmU 18 3
4 Scalability Scalability Controlling the cost of physical resourses Controlling the performance loss Preventing software resourse running out Avoiding performance bottlenecks Date Computers Web s 1979, Dec , July 130, , July 56,218,000 5,560,866 3/9-02 Distribuerade system - Jonny Pettersson, UmU 19 Date Computers Web s Percentage 1993, July 1,776, , July 6,642,000 23, , July 19,540,000 1,203, , July 56,218,000 6,598, /9-02 Distribuerade system - Jonny Pettersson, UmU 20 Failure handling Techniques for dealing with failures Detecting failures Masking failures Tolerating failures Recovery from failures Redundancy 3/9-02 Distribuerade system - Jonny Pettersson, UmU 21 Transparency Access transparency: enables local and remote resources to be accessed using identical operations. Location transparency: enables resources to be accessed without knowledge of their location. Concurrency transparency: enables several processes to operate concurrently using shared resources without interference between them. Replication transparency: enables multiple instances of resources to be used to increase reliability and performance without knowledge of the replicas by users or application programmers. Failure transparency: enables the concealment of faults, allowing users and application programs to complete their tasks despite the failure of hardware or software components. Mobility transparency: allows the movement of resources and clients within a system without affecting the operation of users or programs. Performance transparency: allows the system to be reconfigured to improve performance as loads vary. Scaling transparency: allows the system and applications to expand in scale without change to the system structure or the application algorithms. 3/9-02 Distribuerade system - Jonny Pettersson, UmU 22 System Models Software and hardware layers Architectural models Concerned with the placements of its parts and the relationships between them. Examples - Peer-to-peer Fundamental models Concerned with a more formal description of the properties that are common in architetural models Models Interaction model Failure model Security model Applications, services Middleware Operating system Platform Computer and network hardware 3/9-02 Distribuerade system - Jonny Pettersson, UmU 23 3/9-02 Distribuerade system - Jonny Pettersson, UmU 24 4
5 - Multiple - s Service invocation result invocation result Key: Process: Computer: 3/9-02 Distribuerade system - Jonny Pettersson, UmU 25 3/9-02 Distribuerade system - Jonny Pettersson, UmU 26 Web proxy Peer processes Application Application Proxy Web Coordination code Coordination code Web Application Coordination code 3/9-02 Distribuerade system - Jonny Pettersson, UmU 27 3/9-02 Distribuerade system - Jonny Pettersson, UmU 28 Mobile code - web applets Thin clients a) client request results in the downloading of applet code b) client interacts with the applet Applet code Web Network computer or PC Thin network Compute Application Process Applet Web 3/9-02 Distribuerade system - Jonny Pettersson, UmU 29 3/9-02 Distribuerade system - Jonny Pettersson, UmU 30 5
6 Mobile devices and spontaneous networking Mobile devices and spontaneous networking (cont.) Internet Discovery service gateway TV/PC Hotel wireless network Music service Laptop PDA Alarm service Camera Guests devices Key features and other issues Easy connection to a local network Easy integration with local services Other issues Limited connectivity Security and privacy Discovery services Registration Lookup services 3/9-02 Distribuerade system - Jonny Pettersson, UmU 31 3/9-02 Distribuerade system - Jonny Pettersson, UmU 32 Desgn requirements for distributed architectures Fundamental models Performance issues Quality-of-service Use-of-caching and replication Depedandability issues Fault tolerance Security Questions Main entities? How do they interact? Behaviour? Purpose Make all relevant assumtions explicit Make generalization Interaction Failure Security 3/9-02 Distribuerade system - Jonny Pettersson, UmU 33 3/9-02 Distribuerade system - Jonny Pettersson, UmU 34 Interaction model Two significant factors affecting interaction Communication performance is often a limiting characteristic. It is impossimble to maintain a single notion of time. Performance of communication channels Latency Bandwidth Jitter 3/9-02 Distribuerade system - Jonny Pettersson, UmU 35 3/9-02 Distribuerade system - Jonny Pettersson, UmU 36 6
7 X Y Z A send 1 m 1 2 Event ordering send 3 m 2 4 send m 3 m 1 m 2 t 1 t 2 t 3 Physical time process p Communication omission failures send m Outgoing message buffer Communication channel Omission and arbitrary failures Fail-stop Crash Omission Send-omission Receive-omission Arbitrary (Byzantine) process q Incoming message buffer 3/9-02 Distribuerade system - Jonny Pettersson, UmU 37 3/9-02 Distribuerade system - Jonny Pettersson, UmU 38 Timing failures Class of Failure Affects Description Clock Process Process s local clock exceeds the bounds on its rate of drift from real time. Performance Process Process exceeds the bounds on the interval between two steps. Performance Channel A message s transmission takes longer than the stated bound. Reliability of one-to-one communication Validity Integrity Threats Retransmitting Malicious users 3/9-02 Distribuerade system - Jonny Pettersson, UmU 39 3/9-02 Distribuerade system - Jonny Pettersson, UmU 40 Security models: Protecting objects The enenmy invocation Access rights Object Threats to processes Threats to communication channels Principal (user) result Network Principal () Process p Copy of m The enemy m m Communication channel Process q 3/9-02 Distribuerade system - Jonny Pettersson, UmU 41 3/9-02 Distribuerade system - Jonny Pettersson, UmU 42 7
8 Defeating security threats Summary Cryptography and shared secrets Authentication Secure channels Principal A Process p Secure channel Process q Principal B Introduction to the course What is a distributed system A distributed system is one in which components located at networked computers communicate and coordinate their actions only by passing messages Consequences Concurrency No global clock Independent failures 3/9-02 Distribuerade system - Jonny Pettersson, UmU 43 3/9-02 Distribuerade system - Jonny Pettersson, UmU 44 Summary (cont.) Challenges Heterogeneity Openness Security Scalability Failure handling Concurrency Transparency Architectural models Fundamental models 3/9-02 Distribuerade system - Jonny Pettersson, UmU 45 8
Chapter 1: Distributed Systems: What is a distributed system? Fall 2008 Jussi Kangasharju
 Chapter 1: Distributed Systems: What is a distributed system? Fall 2008 Jussi Kangasharju Course Goals and Content Distributed systems and their: Basic concepts Main issues, problems, and solutions Structured
Chapter 1: Distributed Systems: What is a distributed system? Fall 2008 Jussi Kangasharju Course Goals and Content Distributed systems and their: Basic concepts Main issues, problems, and solutions Structured
Middleware and Distributed Systems. System Models. Dr. Martin v. Löwis. Freitag, 14. Oktober 11
 Middleware and Distributed Systems System Models Dr. Martin v. Löwis System Models (Coulouris et al.) Architectural models of distributed systems placement of parts and relationships between them e.g.
Middleware and Distributed Systems System Models Dr. Martin v. Löwis System Models (Coulouris et al.) Architectural models of distributed systems placement of parts and relationships between them e.g.
Basics. Topics to be covered. Definition of a Distributed System. Definition of a Distributed System
 Topics to be covered Basics Definitions and Examples Goals Models (architectural, fundamental) Hardware and Software Concepts The -Server Model 1 2 Historical Definition of a Distributed System Two developments
Topics to be covered Basics Definitions and Examples Goals Models (architectural, fundamental) Hardware and Software Concepts The -Server Model 1 2 Historical Definition of a Distributed System Two developments
Distributed Systems Lecture 1 1
 Distributed Systems Lecture 1 1 Distributed Systems Lecturer: Therese Berg [email protected]. Recommended text book: Distributed Systems Concepts and Design, Coulouris, Dollimore and Kindberg. Addison
Distributed Systems Lecture 1 1 Distributed Systems Lecturer: Therese Berg [email protected]. Recommended text book: Distributed Systems Concepts and Design, Coulouris, Dollimore and Kindberg. Addison
Distributed System Principles
 Distributed System Principles 1 What is a Distributed System? Definition: A distributed system consists of a collection of autonomous computers, connected through a network and distribution middleware,
Distributed System Principles 1 What is a Distributed System? Definition: A distributed system consists of a collection of autonomous computers, connected through a network and distribution middleware,
Distributed Systems. Security concepts; Cryptographic algorithms; Digital signatures; Authentication; Secure Sockets
 I. Introduction II. Fundamental Concepts of Architecture models; network architectures: OSI, Internet and LANs; interprocess communication III. Time and Global States Clocks and concepts of time; Event
I. Introduction II. Fundamental Concepts of Architecture models; network architectures: OSI, Internet and LANs; interprocess communication III. Time and Global States Clocks and concepts of time; Event
Introduction to CORBA. 1. Introduction 2. Distributed Systems: Notions 3. Middleware 4. CORBA Architecture
 Introduction to CORBA 1. Introduction 2. Distributed Systems: Notions 3. Middleware 4. CORBA Architecture 1. Introduction CORBA is defined by the OMG The OMG: -Founded in 1989 by eight companies as a non-profit
Introduction to CORBA 1. Introduction 2. Distributed Systems: Notions 3. Middleware 4. CORBA Architecture 1. Introduction CORBA is defined by the OMG The OMG: -Founded in 1989 by eight companies as a non-profit
Introduktion till SAS 9 Plattformen Helikopterkursen
 Introduktion till SAS 9 Plattformen Helikopterkursen Kursens mål: Denna kurs/workshop ger dig en samlad överblick över den nye SAS 9 Intelligenta Plattformen. Denna dag är en bra start för att förstå SAS
Introduktion till SAS 9 Plattformen Helikopterkursen Kursens mål: Denna kurs/workshop ger dig en samlad överblick över den nye SAS 9 Intelligenta Plattformen. Denna dag är en bra start för att förstå SAS
Virtual machine interface. Operating system. Physical machine interface
 Software Concepts User applications Operating system Hardware Virtual machine interface Physical machine interface Operating system: Interface between users and hardware Implements a virtual machine that
Software Concepts User applications Operating system Hardware Virtual machine interface Physical machine interface Operating system: Interface between users and hardware Implements a virtual machine that
CHAPTER 2 MODELLING FOR DISTRIBUTED NETWORK SYSTEMS: THE CLIENT- SERVER MODEL
 CHAPTER 2 MODELLING FOR DISTRIBUTED NETWORK SYSTEMS: THE CLIENT- SERVER MODEL This chapter is to introduce the client-server model and its role in the development of distributed network systems. The chapter
CHAPTER 2 MODELLING FOR DISTRIBUTED NETWORK SYSTEMS: THE CLIENT- SERVER MODEL This chapter is to introduce the client-server model and its role in the development of distributed network systems. The chapter
Portable Wireless Mesh Networks: Competitive Differentiation
 Portable Wireless Mesh Networks: Competitive Differentiation Rajant Corporation s kinetic mesh networking solutions combine specialized command and control software with ruggedized, high-performance hardware.
Portable Wireless Mesh Networks: Competitive Differentiation Rajant Corporation s kinetic mesh networking solutions combine specialized command and control software with ruggedized, high-performance hardware.
SAS Data Integration SAS Business Intelligence
 Kursöversikt 2010 SAS Education Providing knowledge through global training and certification SAS Data Integration SAS Business Intelligence Specialkurser SAS Forum 2010 Kontaktinformation Stora Frösunda
Kursöversikt 2010 SAS Education Providing knowledge through global training and certification SAS Data Integration SAS Business Intelligence Specialkurser SAS Forum 2010 Kontaktinformation Stora Frösunda
Case Study for Layer 3 Authentication and Encryption
 CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
VPN. Date: 4/15/2004 By: Heena Patel Email:[email protected]
 VPN Date: 4/15/2004 By: Heena Patel Email:[email protected] What is VPN? A VPN (virtual private network) is a private data network that uses public telecommunicating infrastructure (Internet), maintaining
VPN Date: 4/15/2004 By: Heena Patel Email:[email protected] What is VPN? A VPN (virtual private network) is a private data network that uses public telecommunicating infrastructure (Internet), maintaining
Configuring and Administering Hyper-V in Windows Server 2012
 Configuring and Administering Hyper-V in Windows Server 2012 Längd: 2 Days Kurskod: M55021 Sammanfattning: Denna kurs lär dig hur du konfigurerar och administrerar Hyper-V i Windows Server 2012. Efter
Configuring and Administering Hyper-V in Windows Server 2012 Längd: 2 Days Kurskod: M55021 Sammanfattning: Denna kurs lär dig hur du konfigurerar och administrerar Hyper-V i Windows Server 2012. Efter
Distributed System: Definition
 Distributed System: Definition A distributed system is a piece of software that ensures that: A collection of independent computers that appears to its users as a single coherent system Two aspects: (1)
Distributed System: Definition A distributed system is a piece of software that ensures that: A collection of independent computers that appears to its users as a single coherent system Two aspects: (1)
6306 Advanced Operating Systems
 6306 Advanced Operating Systems Instructor : Dr. Mohan Kumar Room : 315 NH [email protected] Class : TTh 7-8:20PM Office Hours : TTh1-3 PM GTA : Byung Sung [email protected] Kumar CSE@UTA 1 All email messages
6306 Advanced Operating Systems Instructor : Dr. Mohan Kumar Room : 315 NH [email protected] Class : TTh 7-8:20PM Office Hours : TTh1-3 PM GTA : Byung Sung [email protected] Kumar CSE@UTA 1 All email messages
CORBA and object oriented middleware. Introduction
 CORBA and object oriented middleware Introduction General info Web page http://www.dis.uniroma1.it/~beraldi/elective Exam Project (application), plus oral discussion 3 credits Roadmap Distributed applications
CORBA and object oriented middleware Introduction General info Web page http://www.dis.uniroma1.it/~beraldi/elective Exam Project (application), plus oral discussion 3 credits Roadmap Distributed applications
SAS Education Providing knowledge through global training and certification. SAS Foundation. Kursöversikt 2010
 Kursöversikt 2010 SAS Education Providing knowledge through global training and certification SAS Foundation SAS Forum 2010 och specialkurser SAS Master Class Kontaktinformation Stora Frösunda Gård Box
Kursöversikt 2010 SAS Education Providing knowledge through global training and certification SAS Foundation SAS Forum 2010 och specialkurser SAS Master Class Kontaktinformation Stora Frösunda Gård Box
Chapter 1 Instructor Version
 Name Date Objectives: Instructor Version Explain how multiple networks are used in everyday life. Explain the topologies and devices used in a small to medium-sized business network. Explain the basic
Name Date Objectives: Instructor Version Explain how multiple networks are used in everyday life. Explain the topologies and devices used in a small to medium-sized business network. Explain the basic
ICS 434 Advanced Database Systems
 ICS 434 Advanced Database Systems Dr. Abdallah Al-Sukairi [email protected] Second Semester 2003-2004 (032) King Fahd University of Petroleum & Minerals Information & Computer Science Department Outline
ICS 434 Advanced Database Systems Dr. Abdallah Al-Sukairi [email protected] Second Semester 2003-2004 (032) King Fahd University of Petroleum & Minerals Information & Computer Science Department Outline
Distributed Systems. Outline. What is a Distributed System?
 Distributed Systems 1-1 Outline What is a Distributed System? Examples of Distributed Systems Distributed System Requirements in Distributed System 1-2 What is a Distributed System? 1-3 1 What is a Distributed
Distributed Systems 1-1 Outline What is a Distributed System? Examples of Distributed Systems Distributed System Requirements in Distributed System 1-2 What is a Distributed System? 1-3 1 What is a Distributed
CHAPTER 1: OPERATING SYSTEM FUNDAMENTALS
 CHAPTER 1: OPERATING SYSTEM FUNDAMENTALS What is an operating? A collection of software modules to assist programmers in enhancing efficiency, flexibility, and robustness An Extended Machine from the users
CHAPTER 1: OPERATING SYSTEM FUNDAMENTALS What is an operating? A collection of software modules to assist programmers in enhancing efficiency, flexibility, and robustness An Extended Machine from the users
2.1 What are distributed systems? What are systems? Different kind of systems How to distribute systems? 2.2 Communication concepts
 Chapter 2 Introduction to Distributed systems 1 Chapter 2 2.1 What are distributed systems? What are systems? Different kind of systems How to distribute systems? 2.2 Communication concepts Client-Server
Chapter 2 Introduction to Distributed systems 1 Chapter 2 2.1 What are distributed systems? What are systems? Different kind of systems How to distribute systems? 2.2 Communication concepts Client-Server
Proactive, Resource-Aware, Tunable Real-time Fault-tolerant Middleware
 Proactive, Resource-Aware, Tunable Real-time Fault-tolerant Middleware Priya Narasimhan T. Dumitraş, A. Paulos, S. Pertet, C. Reverte, J. Slember, D. Srivastava Carnegie Mellon University Problem Description
Proactive, Resource-Aware, Tunable Real-time Fault-tolerant Middleware Priya Narasimhan T. Dumitraş, A. Paulos, S. Pertet, C. Reverte, J. Slember, D. Srivastava Carnegie Mellon University Problem Description
Enterprise Security Management CheckPoint SecuRemote VPN v4.0 for pcanywhere
 Enterprise Security Management CheckPoint SecuRemote VPN v4.0 for pcanywhere White Paper 7KH#&KDOOHQJH Virtual Private Networks (VPNs) provides a powerful means of protecting the privacy and integrity
Enterprise Security Management CheckPoint SecuRemote VPN v4.0 for pcanywhere White Paper 7KH#&KDOOHQJH Virtual Private Networks (VPNs) provides a powerful means of protecting the privacy and integrity
Mobile Devices: Server and Management Lesson 05 Service Discovery
 Mobile Devices: Server and Management Lesson 05 Service Discovery Oxford University Press 2007. All rights reserved. 1 Service discovery An adaptable middleware in a device (or a mobile computing system)
Mobile Devices: Server and Management Lesson 05 Service Discovery Oxford University Press 2007. All rights reserved. 1 Service discovery An adaptable middleware in a device (or a mobile computing system)
Scrum Kandidatprojekt datateknik - TDDD83
 14-23- 1 Agenda Scrum Kandidatprojekt datateknik - TDDD83 Vad är scrum? Hur fungerar det? Hur ska scrum användas i kursen? Aseel Berglund IDA Agile Approaches - Agile Alliance Lightweight approaches to
14-23- 1 Agenda Scrum Kandidatprojekt datateknik - TDDD83 Vad är scrum? Hur fungerar det? Hur ska scrum användas i kursen? Aseel Berglund IDA Agile Approaches - Agile Alliance Lightweight approaches to
Computer Networking Networks
 Page 1 of 8 Computer Networking Networks 9.1 Local area network A local area network (LAN) is a network that connects computers and devices in a limited geographical area such as a home, school, office
Page 1 of 8 Computer Networking Networks 9.1 Local area network A local area network (LAN) is a network that connects computers and devices in a limited geographical area such as a home, school, office
White Paper on NETWORK VIRTUALIZATION
 White Paper on NETWORK VIRTUALIZATION INDEX 1. Introduction 2. Key features of Network Virtualization 3. Benefits of Network Virtualization 4. Architecture of Network Virtualization 5. Implementation Examples
White Paper on NETWORK VIRTUALIZATION INDEX 1. Introduction 2. Key features of Network Virtualization 3. Benefits of Network Virtualization 4. Architecture of Network Virtualization 5. Implementation Examples
Core Syllabus. Version 2.6 C OPERATE KNOWLEDGE AREA: OPERATION AND SUPPORT OF INFORMATION SYSTEMS. June 2006
 Core Syllabus C OPERATE KNOWLEDGE AREA: OPERATION AND SUPPORT OF INFORMATION SYSTEMS Version 2.6 June 2006 EUCIP CORE Version 2.6 Syllabus. The following is the Syllabus for EUCIP CORE Version 2.6, which
Core Syllabus C OPERATE KNOWLEDGE AREA: OPERATION AND SUPPORT OF INFORMATION SYSTEMS Version 2.6 June 2006 EUCIP CORE Version 2.6 Syllabus. The following is the Syllabus for EUCIP CORE Version 2.6, which
Mixed-Criticality Systems Based on Time- Triggered Ethernet with Multiple Ring Topologies. University of Siegen Mohammed Abuteir, Roman Obermaisser
 Mixed-Criticality s Based on Time- Triggered Ethernet with Multiple Ring Topologies University of Siegen Mohammed Abuteir, Roman Obermaisser Mixed-Criticality s Need for mixed-criticality systems due to
Mixed-Criticality s Based on Time- Triggered Ethernet with Multiple Ring Topologies University of Siegen Mohammed Abuteir, Roman Obermaisser Mixed-Criticality s Need for mixed-criticality systems due to
Local-Area Network -LAN
 Computer Networks A group of two or more computer systems linked together. There are many [types] of computer networks: Peer To Peer (workgroups) The computers are connected by a network, however, there
Computer Networks A group of two or more computer systems linked together. There are many [types] of computer networks: Peer To Peer (workgroups) The computers are connected by a network, however, there
Sweden National H.O.G. Rally. 23 25 July 2010
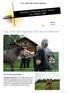 Kiss a Moose, Massage and Rock Karaoke. Ever felt like kissing a Moose? Millestgården Moose Farm in Åre, Sweden offer you the opportunity to get close to the animal the Scandinavians call "The king of
Kiss a Moose, Massage and Rock Karaoke. Ever felt like kissing a Moose? Millestgården Moose Farm in Åre, Sweden offer you the opportunity to get close to the animal the Scandinavians call "The king of
How To Understand The Concept Of A Distributed System
 Distributed Operating Systems Introduction Ewa Niewiadomska-Szynkiewicz and Adam Kozakiewicz [email protected], [email protected] Institute of Control and Computation Engineering Warsaw University of
Distributed Operating Systems Introduction Ewa Niewiadomska-Szynkiewicz and Adam Kozakiewicz [email protected], [email protected] Institute of Control and Computation Engineering Warsaw University of
Cisco Virtual Office Express
 . Q&A Cisco Virtual Office Express Overview Q. What is Cisco Virtual Office Express? A. Cisco Virtual Office Express is a solution that provides secure, rich network services to workers at locations outside
. Q&A Cisco Virtual Office Express Overview Q. What is Cisco Virtual Office Express? A. Cisco Virtual Office Express is a solution that provides secure, rich network services to workers at locations outside
1 st Symposium on Colossal Data and Networking (CDAN-2016) March 18-19, 2016 Medicaps Group of Institutions, Indore, India
 1 st Symposium on Colossal Data and Networking (CDAN-2016) March 18-19, 2016 Medicaps Group of Institutions, Indore, India Call for Papers Colossal Data Analysis and Networking has emerged as a de facto
1 st Symposium on Colossal Data and Networking (CDAN-2016) March 18-19, 2016 Medicaps Group of Institutions, Indore, India Call for Papers Colossal Data Analysis and Networking has emerged as a de facto
Highly Available Mobile Services Infrastructure Using Oracle Berkeley DB
 Highly Available Mobile Services Infrastructure Using Oracle Berkeley DB Executive Summary Oracle Berkeley DB is used in a wide variety of carrier-grade mobile infrastructure systems. Berkeley DB provides
Highly Available Mobile Services Infrastructure Using Oracle Berkeley DB Executive Summary Oracle Berkeley DB is used in a wide variety of carrier-grade mobile infrastructure systems. Berkeley DB provides
Wireless e-business by IBM Wireless Local Area Networks
 IBM Global Services October 2001 Wireless e-business by IBM Wireless Local Area Networks Jyrki Korkki Global Offerings Development Executive, Global Services Page No. 2 Contents 2 Unwiring the business
IBM Global Services October 2001 Wireless e-business by IBM Wireless Local Area Networks Jyrki Korkki Global Offerings Development Executive, Global Services Page No. 2 Contents 2 Unwiring the business
Distributed Systems. REK s adaptation of Prof. Claypool s adaptation of Tanenbaum s Distributed Systems Chapter 1
 Distributed Systems REK s adaptation of Prof. Claypool s adaptation of Tanenbaum s Distributed Systems Chapter 1 1 The Rise of Distributed Systems! Computer hardware prices are falling and power increasing.!
Distributed Systems REK s adaptation of Prof. Claypool s adaptation of Tanenbaum s Distributed Systems Chapter 1 1 The Rise of Distributed Systems! Computer hardware prices are falling and power increasing.!
Network Access Security. Lesson 10
 Network Access Security Lesson 10 Objectives Exam Objective Matrix Technology Skill Covered Exam Objective Exam Objective Number Firewalls Given a scenario, install and configure routers and switches.
Network Access Security Lesson 10 Objectives Exam Objective Matrix Technology Skill Covered Exam Objective Exam Objective Number Firewalls Given a scenario, install and configure routers and switches.
Distributed Systems and Recent Innovations: Challenges and Benefits
 Distributed Systems and Recent Innovations: Challenges and Benefits 1. Introduction Krishna Nadiminti, Marcos Dias de Assunção, and Rajkumar Buyya Grid Computing and Distributed Systems Laboratory Department
Distributed Systems and Recent Innovations: Challenges and Benefits 1. Introduction Krishna Nadiminti, Marcos Dias de Assunção, and Rajkumar Buyya Grid Computing and Distributed Systems Laboratory Department
Skype Connect Requirements Guide
 Skype Connect Requirements Guide Version 4.0 Copyright Skype Limited 2011 Thinking about implementing Skype Connect? Read this guide first. Skype Connect provides connectivity between your business and
Skype Connect Requirements Guide Version 4.0 Copyright Skype Limited 2011 Thinking about implementing Skype Connect? Read this guide first. Skype Connect provides connectivity between your business and
Distributed Database Design
 Distributed Databases Distributed Database Design Distributed Database System MS MS Web Web data mm xml mm dvanced Database Systems, mod1-1, 2004 1 Advanced Database Systems, mod1-1, 2004 2 Advantages
Distributed Databases Distributed Database Design Distributed Database System MS MS Web Web data mm xml mm dvanced Database Systems, mod1-1, 2004 1 Advanced Database Systems, mod1-1, 2004 2 Advantages
Local Area Networks (LANs) Blueprint (May 2012 Release)
 Local Area Networks (LANs) The CCNT Local Area Networks (LANs) Course April 2012 release blueprint lists the following information. Courseware Availability Date identifies the availability date for the
Local Area Networks (LANs) The CCNT Local Area Networks (LANs) Course April 2012 release blueprint lists the following information. Courseware Availability Date identifies the availability date for the
TCP and Wireless Networks Classical Approaches Optimizations TCP for 2.5G/3G Systems. Lehrstuhl für Informatik 4 Kommunikation und verteilte Systeme
 Chapter 2 Technical Basics: Layer 1 Methods for Medium Access: Layer 2 Chapter 3 Wireless Networks: Bluetooth, WLAN, WirelessMAN, WirelessWAN Mobile Networks: GSM, GPRS, UMTS Chapter 4 Mobility on the
Chapter 2 Technical Basics: Layer 1 Methods for Medium Access: Layer 2 Chapter 3 Wireless Networks: Bluetooth, WLAN, WirelessMAN, WirelessWAN Mobile Networks: GSM, GPRS, UMTS Chapter 4 Mobility on the
Microsoft + SOA = Sant? Joakim Linghall Principal System Engineer SOA and Business Process [email protected]
 Microsoft + SOA = Sant? Joakim Linghall Principal System Engineer SOA and Business Process [email protected] Agenda Real World SOA En plattform för SOA ESB SOA Governance Exempel Lite om framtiden
Microsoft + SOA = Sant? Joakim Linghall Principal System Engineer SOA and Business Process [email protected] Agenda Real World SOA En plattform för SOA ESB SOA Governance Exempel Lite om framtiden
TENVIS Technology Co., Ltd. User Manual. For H.264 Cameras. Version 2.0.0
 TENVIS Technology Co., Ltd User Manual For H.264 Cameras Version 2.0.0 Catalogue Basic Operation... 3 Hardware Installation... 3 Search Camera... 3 Get live video... 5 Camera Settings... 8 System... 8
TENVIS Technology Co., Ltd User Manual For H.264 Cameras Version 2.0.0 Catalogue Basic Operation... 3 Hardware Installation... 3 Search Camera... 3 Get live video... 5 Camera Settings... 8 System... 8
Client/server is a network architecture that divides functions into client and server
 Page 1 A. Title Client/Server Technology B. Introduction Client/server is a network architecture that divides functions into client and server subsystems, with standard communication methods to facilitate
Page 1 A. Title Client/Server Technology B. Introduction Client/server is a network architecture that divides functions into client and server subsystems, with standard communication methods to facilitate
Principles and characteristics of distributed systems and environments
 Principles and characteristics of distributed systems and environments Definition of a distributed system Distributed system is a collection of independent computers that appears to its users as a single
Principles and characteristics of distributed systems and environments Definition of a distributed system Distributed system is a collection of independent computers that appears to its users as a single
Technical White Paper
 Instant APN Technical White Paper Introduction AccessMyLan Instant APN is a hosted service that provides access to a company network via an Access Point Name (APN) on the AT&T mobile network. Any device
Instant APN Technical White Paper Introduction AccessMyLan Instant APN is a hosted service that provides access to a company network via an Access Point Name (APN) on the AT&T mobile network. Any device
Distributed Systems LEEC (2005/06 2º Sem.)
 Distributed Systems LEEC (2005/06 2º Sem.) Introduction João Paulo Carvalho Universidade Técnica de Lisboa / Instituto Superior Técnico Outline Definition of a Distributed System Goals Connecting Users
Distributed Systems LEEC (2005/06 2º Sem.) Introduction João Paulo Carvalho Universidade Técnica de Lisboa / Instituto Superior Técnico Outline Definition of a Distributed System Goals Connecting Users
 Albert Ludwigs University Freiburg Department of Computer Science Prof. Dr. Stefan Leue and Corina Apachite Distributed Systems - WS 2001/2002 Assignment 1 - Solutions Question 1.1 Give vetypes of hardware
Albert Ludwigs University Freiburg Department of Computer Science Prof. Dr. Stefan Leue and Corina Apachite Distributed Systems - WS 2001/2002 Assignment 1 - Solutions Question 1.1 Give vetypes of hardware
Storage Guardian Remote Backup Restore and Archive Services
 Storage Guardian Remote Backup Restore and Archive Services Storage Guardian is the unique alternative to traditional backup methods, replacing conventional tapebased backup systems with a fully automated,
Storage Guardian Remote Backup Restore and Archive Services Storage Guardian is the unique alternative to traditional backup methods, replacing conventional tapebased backup systems with a fully automated,
ehealth Ontario EMR Connectivity Guidelines
 ehealth Ontario EMR Connectivity Guidelines Version 1.3 Revised March 3, 2010 Introduction Ontario s new ehealth strategy includes the use of commercially-available high-speed Internet to meet Electronic
ehealth Ontario EMR Connectivity Guidelines Version 1.3 Revised March 3, 2010 Introduction Ontario s new ehealth strategy includes the use of commercially-available high-speed Internet to meet Electronic
Technical papers Virtual private networks
 Technical papers Virtual private networks This document has now been archived Virtual private networks Contents Introduction What is a VPN? What does the term virtual private network really mean? What
Technical papers Virtual private networks This document has now been archived Virtual private networks Contents Introduction What is a VPN? What does the term virtual private network really mean? What
Cisco WAAS Optimized for Citrix XenDesktop
 White Paper Cisco WAAS Optimized for Citrix XenDesktop Cisco Wide Area Application Services (WAAS) provides high performance delivery of Citrix XenDesktop and Citrix XenApp over the WAN. What ou Will Learn
White Paper Cisco WAAS Optimized for Citrix XenDesktop Cisco Wide Area Application Services (WAAS) provides high performance delivery of Citrix XenDesktop and Citrix XenApp over the WAN. What ou Will Learn
STRATEGIC POLICY. Information Security Policy Documentation. Network Management Policy. 1. Introduction
 Policy: Title: Status: 1. Introduction ISP-S12 Network Management Policy Revised Information Security Policy Documentation STRATEGIC POLICY 1.1. This information security policy document covers management,
Policy: Title: Status: 1. Introduction ISP-S12 Network Management Policy Revised Information Security Policy Documentation STRATEGIC POLICY 1.1. This information security policy document covers management,
System Models for Distributed and Cloud Computing
 System Models for Distributed and Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF Classification of Distributed Computing Systems
System Models for Distributed and Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF Classification of Distributed Computing Systems
Client/Server and Distributed Computing
 Adapted from:operating Systems: Internals and Design Principles, 6/E William Stallings CS571 Fall 2010 Client/Server and Distributed Computing Dave Bremer Otago Polytechnic, N.Z. 2008, Prentice Hall Traditional
Adapted from:operating Systems: Internals and Design Principles, 6/E William Stallings CS571 Fall 2010 Client/Server and Distributed Computing Dave Bremer Otago Polytechnic, N.Z. 2008, Prentice Hall Traditional
Maskinöversättning 2008. F2 Översättningssvårigheter + Översättningsstrategier
 Maskinöversättning 2008 F2 Översättningssvårigheter + Översättningsstrategier Flertydighet i källspråket poäng point, points, credit, credits, var verb ->was, were pron -> each adv -> where adj -> every
Maskinöversättning 2008 F2 Översättningssvårigheter + Översättningsstrategier Flertydighet i källspråket poäng point, points, credit, credits, var verb ->was, were pron -> each adv -> where adj -> every
Microsoft SQL Server 2012: Designing Buisness Intelligence Solutions
 Microsoft SQL Server 2012: Designing Buisness Intelligence s Längd: 5 Days Kurskod: M20467 Version: A Sammanfattning: Denna 5-dagarskurs lär dig hur du designar och implementerar en BI-Infrastruktur. Kursen
Microsoft SQL Server 2012: Designing Buisness Intelligence s Längd: 5 Days Kurskod: M20467 Version: A Sammanfattning: Denna 5-dagarskurs lär dig hur du designar och implementerar en BI-Infrastruktur. Kursen
ORACLE S SIEBEL BUSINESS APPLICATIONS 8.0
 APPLICATION READY NETWORK GUIDE ORACLE S SIEBEL BUSINESS APPLICATIONS 8.0 Comprehensive Application Ready infrastructure that enhances the security, availability, and performance of Oracle s Siebel deployments
APPLICATION READY NETWORK GUIDE ORACLE S SIEBEL BUSINESS APPLICATIONS 8.0 Comprehensive Application Ready infrastructure that enhances the security, availability, and performance of Oracle s Siebel deployments
Configuration of Applied VoIP Sip Trunks with the Toshiba CIX40, 100, 200 and 670
 Configuration of Applied VoIP Sip Trunks with the Toshiba CIX40, 100, 200 and 670 Businesses Save Money with Toshiba s New SIP Trunking Feature Unlike gateway based solutions, Toshiba s MIPU/ GIPU8 card
Configuration of Applied VoIP Sip Trunks with the Toshiba CIX40, 100, 200 and 670 Businesses Save Money with Toshiba s New SIP Trunking Feature Unlike gateway based solutions, Toshiba s MIPU/ GIPU8 card
Base One's Rich Client Architecture
 Base One's Rich Client Architecture Base One provides a unique approach for developing Internet-enabled applications, combining both efficiency and ease of programming through its "Rich Client" architecture.
Base One's Rich Client Architecture Base One provides a unique approach for developing Internet-enabled applications, combining both efficiency and ease of programming through its "Rich Client" architecture.
Mobile Communications Chapter 9: Mobile Transport Layer
 Mobile Communications Chapter 9: Mobile Transport Layer Motivation TCP-mechanisms Classical approaches Indirect TCP Snooping TCP Mobile TCP PEPs in general Additional optimizations Fast retransmit/recovery
Mobile Communications Chapter 9: Mobile Transport Layer Motivation TCP-mechanisms Classical approaches Indirect TCP Snooping TCP Mobile TCP PEPs in general Additional optimizations Fast retransmit/recovery
Windows Web Based VPN Connectivity Details & Instructions
 VPN Client Overview UMDNJ s Web based VPN utilizes an SSL (Secure Socket Layer) Based Cisco Application that provides VPN functionality without having to install a full client for end users running Microsoft
VPN Client Overview UMDNJ s Web based VPN utilizes an SSL (Secure Socket Layer) Based Cisco Application that provides VPN functionality without having to install a full client for end users running Microsoft
International Council on Systems Engineering. ISO/IEC/IEEE 15288 SEminar Linköping 16 november 2015
 International Council on Systems Engineering ISO/IEC/IEEE 15288 SEminar Linköping 16 november 2015 WHY there is a need for SE and INCOSE Need to manage increasing complexity Technology trends Systems of
International Council on Systems Engineering ISO/IEC/IEEE 15288 SEminar Linköping 16 november 2015 WHY there is a need for SE and INCOSE Need to manage increasing complexity Technology trends Systems of
Fax Server Cluster Configuration
 Fax Server Cluster Configuration Low Complexity, Out of the Box Server Clustering for Reliable and Scalable Enterprise Fax Deployment www.softlinx.com Table of Contents INTRODUCTION... 3 REPLIXFAX SYSTEM
Fax Server Cluster Configuration Low Complexity, Out of the Box Server Clustering for Reliable and Scalable Enterprise Fax Deployment www.softlinx.com Table of Contents INTRODUCTION... 3 REPLIXFAX SYSTEM
Current and Future Research into Network Security Prof. Madjid Merabti
 Current and Future Research into Network Security Prof. Madjid Merabti School of Computing & Mathematical Sciences Liverpool John Moores University UK Overview Introduction Secure component composition
Current and Future Research into Network Security Prof. Madjid Merabti School of Computing & Mathematical Sciences Liverpool John Moores University UK Overview Introduction Secure component composition
Release the full potential of your Cisco Call Manager with Ingate Systems
 Release the full potential of your Cisco Call Manager with Ingate Systems -Save cost with flexible connection to Service Providers. -Save mobile costs, give VoIP mobility to your workforce. -Setup an effective
Release the full potential of your Cisco Call Manager with Ingate Systems -Save cost with flexible connection to Service Providers. -Save mobile costs, give VoIP mobility to your workforce. -Setup an effective
Service Catalogue. Creation Date
 Catalogue Creation Date Notes: The following template is provided for writing a Catalog document. [Inside each section, text in green font between brackets is included to provide guidance to the author
Catalogue Creation Date Notes: The following template is provided for writing a Catalog document. [Inside each section, text in green font between brackets is included to provide guidance to the author
Cryptography and Network Security Chapter 1
 Cryptography and Network Security Chapter 1 Acknowledgments Lecture slides are based on the slides created by Lawrie Brown Chapter 1 Introduction The art of war teaches us to rely not on the likelihood
Cryptography and Network Security Chapter 1 Acknowledgments Lecture slides are based on the slides created by Lawrie Brown Chapter 1 Introduction The art of war teaches us to rely not on the likelihood
Readme10_054.doc page 1 of 7
 Readme10_054.doc page 1 of 7 Date of production: 2007-12-03 News in 10_054 Hardware 1) New thyristor module DASD 145, 600 V - 500 A 2) Improved speed control with incremental encoder at very low speed
Readme10_054.doc page 1 of 7 Date of production: 2007-12-03 News in 10_054 Hardware 1) New thyristor module DASD 145, 600 V - 500 A 2) Improved speed control with incremental encoder at very low speed
Distribution transparency. Degree of transparency. Openness of distributed systems
 Distributed Systems Principles and Paradigms Maarten van Steen VU Amsterdam, Dept. Computer Science [email protected] Chapter 01: Version: August 27, 2012 1 / 28 Distributed System: Definition A distributed
Distributed Systems Principles and Paradigms Maarten van Steen VU Amsterdam, Dept. Computer Science [email protected] Chapter 01: Version: August 27, 2012 1 / 28 Distributed System: Definition A distributed
Network Attached Storage. Jinfeng Yang Oct/19/2015
 Network Attached Storage Jinfeng Yang Oct/19/2015 Outline Part A 1. What is the Network Attached Storage (NAS)? 2. What are the applications of NAS? 3. The benefits of NAS. 4. NAS s performance (Reliability
Network Attached Storage Jinfeng Yang Oct/19/2015 Outline Part A 1. What is the Network Attached Storage (NAS)? 2. What are the applications of NAS? 3. The benefits of NAS. 4. NAS s performance (Reliability
Zscaler Internet Security Frequently Asked Questions
 Zscaler Internet Security Frequently Asked Questions 1 Technical FAQ PRODUCT LICENSING & PRICING How is Zscaler Internet Security Zscaler Internet Security is licensed on number of Cradlepoint devices
Zscaler Internet Security Frequently Asked Questions 1 Technical FAQ PRODUCT LICENSING & PRICING How is Zscaler Internet Security Zscaler Internet Security is licensed on number of Cradlepoint devices
Network Security Administrator
 Network Security Administrator Course ID ECC600 Course Description This course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze
Network Security Administrator Course ID ECC600 Course Description This course looks at the network security in defensive view. The ENSA program is designed to provide fundamental skills needed to analyze
Client/server and peer-to-peer models: basic concepts
 Client/server and peer-to-peer models: basic concepts Dmitri Moltchanov Department of Communications Engineering Tampere University of Technology [email protected] September 04, 2013 Slides provided by
Client/server and peer-to-peer models: basic concepts Dmitri Moltchanov Department of Communications Engineering Tampere University of Technology [email protected] September 04, 2013 Slides provided by
What would you like to protect?
 Network Security What would you like to protect? Your data The information stored in your computer Your resources The computers themselves Your reputation You risk to be blamed for intrusions or cyber
Network Security What would you like to protect? Your data The information stored in your computer Your resources The computers themselves Your reputation You risk to be blamed for intrusions or cyber
Chapter 17: Distributed Systems
 Chapter 17: Distributed Systems Chapter 17: Distributed Systems Advantages of Distributed Systems Types of Network-Based Operating Systems Network Structure Communication Structure Communication Protocols
Chapter 17: Distributed Systems Chapter 17: Distributed Systems Advantages of Distributed Systems Types of Network-Based Operating Systems Network Structure Communication Structure Communication Protocols
Car Customer Service. SFK Väst, January 2016, Måns Falk, mfalk, Security Class; Proprietary 2016-01-21
 Car Customer Service SFK Väst, January 2016, Måns Falk, mfalk, Security Class; Proprietary 2016-01-21 1 Lean SERVICE En upptäcktsresa Måns Falk Volvo Car Customer Service Customer Service Lean Knowledge
Car Customer Service SFK Väst, January 2016, Måns Falk, mfalk, Security Class; Proprietary 2016-01-21 1 Lean SERVICE En upptäcktsresa Måns Falk Volvo Car Customer Service Customer Service Lean Knowledge
The next generation of knowledge and expertise Wireless Security Basics
 The next generation of knowledge and expertise Wireless Security Basics HTA Technology Security Consulting., 30 S. Wacker Dr, 22 nd Floor, Chicago, IL 60606, 708-862-6348 (voice), 708-868-2404 (fax), www.hta-inc.com
The next generation of knowledge and expertise Wireless Security Basics HTA Technology Security Consulting., 30 S. Wacker Dr, 22 nd Floor, Chicago, IL 60606, 708-862-6348 (voice), 708-868-2404 (fax), www.hta-inc.com
ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3
 ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3 TO THE Overview EXHIBIT T to Amendment No. 60 Secure Wireless Network Services are based on the IEEE 802.11 set of standards and meet the Commonwealth of Virginia
ADDENDUM 12 TO APPENDIX 8 TO SCHEDULE 3.3 TO THE Overview EXHIBIT T to Amendment No. 60 Secure Wireless Network Services are based on the IEEE 802.11 set of standards and meet the Commonwealth of Virginia
Development allowance and activity grant [Aktivitetsstöd och utvecklingsersättning]
![Development allowance and activity grant [Aktivitetsstöd och utvecklingsersättning] Development allowance and activity grant [Aktivitetsstöd och utvecklingsersättning]](/thumbs/27/10259426.jpg) Development allowance and activity grant [Aktivitetsstöd och utvecklingsersättning] If you are participating in a labour market programme, you are eligible for development allowance or an activity grant.
Development allowance and activity grant [Aktivitetsstöd och utvecklingsersättning] If you are participating in a labour market programme, you are eligible for development allowance or an activity grant.
How To Plan A Desktop Workspace Infrastructure
 Dell Copyright 2014 Moka5, Inc. All rights reserved. Moka5, MokaFive, LivePC, and the Moka5 logo are trademarks of Moka5, Inc. All other product or company names may be trademarks of their respective owners.
Dell Copyright 2014 Moka5, Inc. All rights reserved. Moka5, MokaFive, LivePC, and the Moka5 logo are trademarks of Moka5, Inc. All other product or company names may be trademarks of their respective owners.
