Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices
|
|
|
- Fay Melton
- 9 years ago
- Views:
Transcription
1 Situation Microsoft employees need to be able to use their mobile devices, including mobile phones and slates, to access mission-crucial data anytime, anywhere. With more than 170,000 user mailboxes, MSIT needed a robust solution, and found it with Exchange ActiveSync. Solution Exchange ActiveSync is a synchronization protocol that works with high-latency and low-bandwidth networks. Exchange ActiveSync enables users to use their mobile devices to access up-to-date corporate , calendar, and contacts that are on a Microsoft Exchange Server. Meanwhile, it enables MSIT to enforce security policies on those devices that protect valuable intellectual property from malicious users, should employees lose their mobile devices or have them stolen. Benefits Enables employees to access their corporate , calendar, and contacts by using their personal portable devices Increases employee productivity significantly by enabling anywhere, anytime access to corporate data Boosts employee satisfaction notably Enables Microsoft to attract potential employees who are technologicallysavvy, and who want the ability to work remotely Minimizes the risk of inadvertent data exposure and loss Provides institutional management of Exchange Server policies and configurations Enables cross-team collaboration between security, hardware, and teams within an enterprise Products & Technologies Microsoft Exchange ActiveSync Microsoft Exchange Server 2010 Microsoft System Center 2012 Windows PowerShell Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Published: July 2012 The following content may no longer reflect Microsoft s current position or infrastructure. This content should be viewed as reference documentation only, to inform IT business decisions within your own company or organization. Microsoft Exchange Server 2010 has functionality that enables users to access their corporate , calendar, global address list, and tasks with their personal portable devices. Using Microsoft Exchange ActiveSync within Exchange Server 2010, Microsoft IT (MSIT) delivers significant improvements in employee productivity and satisfaction by enabling employee access to this business-critical information in more than 170,000 user mailboxes. Situation Only a few years ago, IT departments still procured and managed electronic devices for their employees. Today, employees want to use their personal electronic devices to do their jobs, and utilize the same technologies and applications at work that they use at home. This blending of consumer and enterprise technologies is the Consumerization of IT, and it significantly boosts employee productivity and satisfaction. Employees can work just about anywhere, at any time, as long as their personal electronic devices can connect to their enterprise s corporate network. However, this anytime, anywhere access to corporate data can make it difficult for IT departments to ensure the protection of enterprise data. Microsoft supports a hybrid, mixed-ownership model of enterprise-standard and consumerstandard hardware, and offers support to employees who want to use their own mobile devices, including phones and slates. These devices must meet minimum hardware requirements that MSIT specifies. However, if they do, then MSIT provides a way for employees to access key corporate data, but also to protect that data from inadvertent exposure and malicious users. The answer for MSIT was Microsoft Exchange ActiveSync, a feature of Microsoft Exchange Server If employees use mobile devices that are Exchange ActiveSync enabled, then they also can use that device to access their: Corporate calendar, so they can view their appointments, accept and reject meeting requests, and create new appointments and meeting requests Global address lists, or contacts Tasks Line-of-business (LOB) applications
2 By deploying Exchange ActiveSync, MSIT enables employees to access this often missioncritical data, while also enforcing security policies within an Exchange Server environment. However, MSIT had to ensure that enabling Exchange ActiveSync, and the mailbox-client traffic that it would produce, would not overtax the existing Client Access Server (CAS) infrastructure. Enabling users to access this data resulted in a quick and significant surge from approximately 50,000 clients accessing Exchange Server to more than 100,000 clients. Currently, not all employees use their mobile devices to access their corporate , calendar, contacts, and tasks, but a large portion of them do. The Exchange ActiveSync deployment at Microsoft was smooth and seamless--most users likely did not even notice any change in their service or use, except for a message or two on which they had to act so that they could connect to the corporate network. Furthermore, Microsoft has promoted active management for its Exchange ActiveSync deployment by: Evaluating the default Exchange ActiveSync policies before deployment, to determine which ones to configure to meet enterprise needs. Reviewing these policies periodically to ensure that they continue to meet enterprise needs for data protection, while also enabling continued successful data access by users. Among the policies that MSIT initially reviewed and configured during its Exchange ActiveSync deployment were the: Ability to enable and disable Exchange ActiveSync for specific users or groups of users. Length and type of lock password that users had to establish on their mobile devices. Number of lock password attempts allowable on a device. Action taken when the number of device password attempts is reached. Ability to wipe the device remotely. The user can wipe the device remotely by using Microsoft Office Outlook Web Access, or an MSIT administrator can use Windows PowerShell commands to wipe the device remotely to its factory settings. Solution Microsoft has approximately 170,000 user mailboxes, to support its employees around the globe. Users want to access their , calendar, and LOB applications not just from their work computer, but also from their personal laptops and mobile devices. This means that MSIT is supporting a widely heterogeneous environment, which can be challenging and costly. However, to continue boosting the productivity and satisfaction of its existing employees, it was imperative that MSIT flow with the Consumerization of IT. Additionally, millennials, the technologically advanced generation of young adults joining the workforce today, often will not work for an enterprise unless telecommuting and remote operations are part of the package. Therefore, MSIT no longer supports only devices that it procures for users, but also a wide variety of consumer devices. The sheer variety of devices and operating systems from which users can select drives up cost-of-ownership from a support perspective. Then there is the issue of data protection: how can MSIT protect data if user devices are lost or stolen? MSIT needed to find a mechanism through which it could provide that access, while simultaneously protecting data. The mechanism is Exchange ActiveSync and is a feature Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Page 2
3 within Exchange Server. Exchange Active Sync is essential to managing employee access to proprietary data in this vast mixed-ownership environment. Exchange ActiveSync is a synchronization protocol that works with high-latency and lowbandwidth networks to enable users to access mission-critical, up-to-date corporate , calendar, and contacts on a Microsoft Exchange Server, by using their mobile devices. While some people feel that having on your phone is a little onerous, it can be really useful, too. You are able to complete work after you ve left the office, without having to sit home, and be in front of your PC. There is no doubt that it increases productivity. I don t think anyone could argue that. Also, you could argue that it actually improves your work-life balance, because you can leave and go do something with your family, and still be reachable. Mark Riley Principal Program Manager, Mobile Services, for MSIT Microsoft Corporation While some people feel that having on your phone is a little onerous, it can be really useful, too, said Mark Riley, Principal Program Manager, Mobile Services, for MSIT. If you have an ongoing issue at work, not only can you be bothered about it, but you can also be notified when it s resolved. I think that is a huge thing. You are able to complete work after you ve left the office, without having to sit home, and be in front of your PC. There is no doubt that it increases productivity. I don t think anyone could argue that. Also, you could argue that it actually improves your work-life balance, because you can leave and go do something with your family, and still be reachable. Exchange ActiveSync allows an enterprise to provide its employee with this essential data, when they are travelling and working remotely, while protecting its data should an employee lose a device or it is stolen. An enterprise also can configure it to use Secure Sockets Layer (SSL) encryption for communications between the Exchange server and the mobile-device client. Additionally, it uses certificate-based authentication that works with self-signed certificates, a certificate from an existing public key infrastructure (PKI), or a third-party commercial certification authority (CA). Additionally, Exchange ActiveSync works in conjunction with security policies to: Enable a data wipe on the mobile device if an unauthorized user attempts to synchronize with the Exchange Server from that device. Provide more security by deploying RSA SecurID two-factor authentication on the Exchange Server. Enable configurable device-password policies. Deploying Exchange ActiveSync at Microsoft Three crucial steps ensured a smooth Exchange ActiveSync deployment for Microsoft users and MSIT, including: Analysis of the CAS infrastructure and how the potential Exchange ActiveSync load would affect it. Configuration of Exchange ActiveSync security policies to ensure data protection if mobile devices were lost or stolen. Active management of Exchange ActiveSync security policies to ensure continued data protection as the environment changes, new threats emerge, and regulatory requirements change. Analyzing the CAS Infrastructure In 2003, MSIT began analyzing its CAS infrastructure. CAS accepts incoming protocol connections for Exchange Server, and users can connect to Exchange Server via Microsoft Office Outlook, Outlook Web Access, Outlook Anywhere, and Exchange ActiveSync. This means that there typically is significant traffic on the CAS servers, and MSIT needed to determine what the potential Exchange ActiveSync load would be prior to deployment. If the Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Page 3
4 load was going to be too high, the existing CAS infrastructure could overload and crash. This, in turn, could cause service degradation for users and potential downtime. CAS analysis was a crucial first step in the Exchange ActiveSync deployment, and led MSIT to arrive at its current CAS infrastructure, which includes: 41 CAS servers in Redmond for North American and South American users. These 41 CAS servers service approximately 80,000 users alone. 14 in Dublin, Ireland, which service approximately 30,000 users in Europe and parts of the Middle East and Africa. 12 in Singapore, which service approximately 25,000 users in parts of the Far East and Australia. Again, this analysis was essential. When MSIT turned on Exchange ActiveSync, the phone clients accessing CAS servers exploded literally overnight, from approximately 50,000 to more than 100,000. However, there was no interruption in service nor did most users even notice the change, save for a message that requested they accept a policy on their mobile device. Configuring Exchange ActiveSync Policies, and Establishing Reporting Procedures The Consumerization of IT at Microsoft means that users more often than not are selecting, procuring, and managing their own mobile devices. When added to the fact that there are 170,000 user mailboxes at Microsoft, that makes for a significant and broad management task for MSIT. Some users do not access their mailboxes with their mobile phones or devices, but other users synchronize several mobile devices with Exchange Server. The ultimate question for MSIT, as it deployed Exchange ActiveSync to enable users to access their mail and other data via their mobile devices, was how best to protect that data from inadvertent exposure and malicious users. MSIT had to take a multifaceted approach to data protection, which included: Determining what threats or potential threats existed, for which MSIT needed to mitigate exposure on mobile devices. These threats included known malware on certain phone operating systems that synchronize to the Exchange Server environment, and which are exposed to the public Internet. Ensuring that Microsoft security standards were upheld and that Microsoft complied with regulatory requirements, such as reporting. MSIT uses Microsoft System Center 2012 for reporting, which utilizes back-end Windows PowerShell commands to poll devices that synchronize to the Exchange Server. System Center reporting enables MSIT to see specifically what devices are connecting to what mailboxes. This provides MSIT with a thorough look at the Exchange environment and the devices working within it. System Center 2012 includes the Exchange Connector feature, which reads information on the devices that are connecting to Exchange Server, and then can set Exchange ActiveSync policies accordingly. This enables a view through a single pane of glass, regardless of whether a user is connecting from a desktop computer, laptop computer, or mobile device. Analyzing the Exchange Server environment regularly to ensure that the central processing unit (CPU) load was not overburdening the CAS infrastructure. This analysis is important to perform regularly, to ensure that no service interruptions occur. Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Page 4
5 MSIT knew that active management of Exchange ActiveSync policies was crucial (and it continues to be). While the Exchange ActiveSync out-of-box configuration would work well for many enterprises, MSIT opted to look at each configuration policy separately, and then make a decision regarding whether to keep the default setting or modify it. MSIT then configured policies in several areas, including: Exchange ActiveSync Policies Exchange ActiveSync Throttle Policies Mail Client Service Policies Authentication Policies Configuring EAS Policies for the Microsoft Environment MSIT wanted to make it as simple as possible for users to synchronize their mobile devices to their Exchange-hosted mailboxes. MSIT succeeded, after deciding initially not to ban any devices or operating system from connecting to the Exchange Server environment. However, this likely will change as the threat landscape changes. MSIT currently has opted not to block any devices. However, to ensure data protection, MSIT decided to actively manage its Exchange ActiveSync policies. Here is a sampling of the Exchange ActiveSync policies that MSIT looked at before deploying Exchange ActiveSync: AllowSimpleDevicePassword AlphanumericDevicePasswordRequired DeviceEncryptionEnabled DevicePasswordEnabled DevicePasswordExpiration DevicePasswordHistory DevicePolicyRefreshInterval MinimumDevicePasswordLength MaxInactivityTimeDeviceLock MaxDevicePasswordFailedAttempts PasswordRecoveryEnabled RequireDeviceEncryption While the specifics of how Microsoft configured Exchange ActiveSync policies is out of scope for this paper, here is a quick look at the basic device security that MSIT enforced via Exchange ActiveSync policies, including the: Minimum password length that the users must utilize for their mobile devices. MSIT opted to enforce a four-digit PIN, which the user selects. Users can establish an alphanumeric PIN, although that is not required. Maximum time that a device can be inactive before it locks. If the mobile device is inactive for 15 minutes, the device locks. The user has to unlock the device with the fourdigit PIN. Users can opt to set this time to a shorter period, such as two minutes or five minutes. Ability for a user or administrator to wipe the device remotely, which deletes data and reverts it to its factory settings. A user can logon to Outlook Web Access, navigate to the particular mobile device in question, and select to remotely wipe the device the next time Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Page 5
6 it attempts to synchronize to the Exchange Server. Conversely, a user can call the Microsoft help desk, and the help-desk technician will escalate the ticket to an administrator, who uses a Windows PowerShell command to issue the device wipe. Maximum password attempts a user can make and the action that occurs when that maximum is reached. A user has five tries to enter the correct password. On the sixth try, a local wipe of the device occurs. Schedule on which policies are refreshed on mobile devices. The default is 24 hours, but MSIT opted to change that to one hour. This ensures devices stay synchronized and data stays protected. Maintenance of password histories, password-history lengths, and password expirations. MSIT opted not to enforce these options because configuring the remote-wipe capability was deemed sufficient to protect device data. Enabling of policy exceptions. Some users, such as executives and developers, required exceptions to Exchange ActiveSync policies. MSIT used an innovative approach to managing these exceptions, by leveraging security groups to differentiate user access to various mail protocols, including Exchange ActiveSync. While MSIT did not opt to configure every Exchange ActiveSync default policy, it did look at each one, and made a decision regarding it. MSIT managed its Exchange ActiveSync deployment actively, and continues to do so today. Actively Managing Exchange ActiveSync Policies MSIT continually evolves its Exchange ActiveSync policies and configurations. They are not standardized, but rather are malleable. This enables MSIT to respond quickly as client traffic increases, environmental changes occur, threats emerge to devices and operating systems, and regulatory requirements change. MSIT recently completed its regular CAS infrastructure analysis, and will deploy 10 new Mach-1 servers, at a cost of approximately $30,000. Additionally, MSIT carefully monitors CPU load in the CAS environment, by parsing log files to see if CPU usage is trending up. The analysis schedule is determined by CPU load, rather than a fixed date on a calendar. This enables MSIT to respond with alacrity to any service spike that may cause service degradation for users. Additionally, MSIT: Works closely with the Exchange operations team to ensure that it has the necessary hardware to support its users. MSIT uses a hardware load balancer that enables it to separate the traffic coming through the CAS infrastructure into different protocols and rates of CPU usage. As manufacturers roll out more and more mobile devices, the number of clients that will be hitting the CAS infrastructure will continue to climb. Monitors operating systems and devices carefully. While MSIT currently does not ban any devices from connecting through Exchange ActiveSync, MSIT is carefully looking at all device operating systems, to ensure the protection of Microsoft intellectual property. Some device operating systems are open-source, which means that malicious users can infect them with malware much easier. MSIT may institute policies regarding the ability of these devices to synchronize to the Microsoft Exchange environment via Exchange ActiveSync. Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Page 6
7 MSIT also is in the process of deploying device encryption. When MSIT deployed Exchange ActiveSync several years ago, mobile-device encryption was not possible technically. Today it is, and can provide an additional level of protection for Microsoft intellectual property and data. Best Practices Deploying Exchange ActiveSync is relatively straightforward, particularly if an enterprise has Exchange Server running already. Here are several best practices that MSIT determined from its Exchange ActiveSync deployment: You need to monitor your traffic so that you can scale your environment as needed, and you need to be cognizant of how these devices are connecting to your Exchange environment, so that you can put policies in place to manage them. Shad Morris Network Engineer for Service Engineering Microsoft Corporation Manage your Exchange ActiveSync policies actively. Periodically review the devices and operating systems that will attempt to synchronize with your Exchange Server; monitor ongoing threats to those devices and operating systems; and determine your risk tolerance. Determine your review rhythm. If an annual review is enough, stay with that schedule. However, if your risk tolerance is lower (such as in the banking industry), a semiannual or quarterly review may be necessary. Continue to monitor what policies you have turned on or off, depending on your environment and other factors. Monitor your CAS infrastructure carefully and regularly. If CPU loads begins to increase, or spikes suddenly, this could cause the CAS servers to fail, which leads to downtime and service interruptions to users. Review logs at least quarterly. You need to monitor your traffic so that you can scale your environment as needed, and you need to be cognizant of how these devices are connecting to your Exchange environment, so that you can put policies in place to manage them, said Shad Morris, network engineer for service engineering at Microsoft. Manage exceptions to Exchange ActiveSync policies. Some users will require exceptions to policies. Think out of the box, as MSIT did when opting to manage other protocols, such as IMAP and POP settings, for specific security groups, while simultaneously enabling their access to data and securing that data. Benefits There are several benefits to deploying Exchange ActiveSync, including that it: Increases employee productivity significantly by enabling them to access their missioncritical , calendar, tasks, and contacts from anywhere, at any time, by using their mobile devices. Boosts employee satisfaction notably, by allowing employees to work remotely, on devices of their choosing. Enables Microsoft to attract employees who are technologically proficient, and who demand the ability to work remotely, while utilizing the devices and applications with which they are familiar and comfortable. Enables an organization s IT department to mitigate risk to data from inadvertent exposure or loss of a mobile device, as well as provide institutional management for Exchange security settings. Facilitates cross-team collaboration. Most IT organizations use Exchange Server to run their system, and most of those probably have mobile devices connecting to Exchange. Typically, however, the people who establish and configure security policies and manage the enterprise s network are not the same people who manage the Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Page 7
8 enterprise s infrastructure. Furthermore, most enterprises typically have another team that manages server hardware. Thus, cross-team collaboration is essential to a successful Exchange ActiveSync deployment. Providing an easy reporting mechanism, as MSIT can use System Center 2012 and back-end Windows PowerShell commands to poll devices that synchronize to the Exchange Server. This enables MSIT to determine specifically what devices are connecting to what mailboxes, and provides a thorough look at the Exchange environment. Conclusion Exchange ActiveSync, a feature of Exchange Server, provides an invaluable mechanism through which an IT organization can provide its employees with anytime, anywhere access to synchronized data from Exchange Server, while simultaneously protecting that data from inadvertent exposure and malicious users. MSIT capitalized on the functionality of Exchange ActiveSync to continue its support for the Consumerization of IT, and the resulting mixed-ownership hybrid environment of portable electronic devices that its employees choose to use. Employee productivity and satisfaction are boosted significantly, because they can use their chosen portable electronic devices to access their , contacts, tasks, and applications, regardless of whether they are at work, at home, or working while on the go. Furthermore, protection of valuable Microsoft data and intellectual property is assured through MSIT s active management of Exchange ActiveSync policies. Currently, approximately 100,000 Microsoft employees utilize Exchange ActiveSync functionality to access their data. However, with 170,000 user mailboxes, not to mention the plethora of mobile and slate devices that continue to come to market seemingly on a daily basis, the number is sure to rise. However, with continued active management of Exchange ActiveSync policies, MSIT can assure the protection of Microsoft data, with little or no interruption to its users, who will continue to be productive and happy, and hopefully continue to have a positive life-work balance as they help Microsoft continue its dominance in the world of software and hardware development. For More Information For more information about Microsoft products or services, call the Microsoft Sales Information Center at (800) In Canada, call the Microsoft Canada Order Centre at (800) Outside the 50 United States and Canada, please contact your local Microsoft subsidiary. To access information via the World Wide Web, go to: Microsoft Corporation. All rights reserved. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY. Microsoft, Microsoft Exchange ActiveSync, Microsoft Exchange Server, and Windows PowerShell are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Using Microsoft Exchange ActiveSync to Actively Manage Consumerization of IT Devices Page 8
Windows Phone 8 Device Management Overview
 Windows Phone 8 Device Management Overview This white paper is part of a series of technical papers designed to help IT professionals evaluate Windows Phone 8 and understand how it can play a role in their
Windows Phone 8 Device Management Overview This white paper is part of a series of technical papers designed to help IT professionals evaluate Windows Phone 8 and understand how it can play a role in their
ONE Mail Direct for Mobile Devices
 ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
Microsoft IT Increases Security and Streamlines Antimalware Management by Using Microsoft Forefront Endpoint. Protection 2010.
 Situation Microsoft IT had limited monitoring and reporting functionality with its existing antimalware system. Although the system could scan for malware, there was no reporting capability or configurable
Situation Microsoft IT had limited monitoring and reporting functionality with its existing antimalware system. Although the system could scan for malware, there was no reporting capability or configurable
Windows Phone 8 devices will be used remotely over 3G, 4G and non-captive Wi-Fi networks to enable a variety of remote working approaches such as
 GOV.UK Guidance End User Devices Security Guidance: Windows Phone 8 Updated 14 October 2013 Contents 1. Usage Scenario 2. Summary of Platform Security 3. How the Platform Can Best Satisfy the Security
GOV.UK Guidance End User Devices Security Guidance: Windows Phone 8 Updated 14 October 2013 Contents 1. Usage Scenario 2. Summary of Platform Security 3. How the Platform Can Best Satisfy the Security
iphone in Business Security Overview
 iphone in Business Security Overview iphone can securely access corporate services and protect data on the device. It provides strong encryption for data in transmission, proven authentication methods
iphone in Business Security Overview iphone can securely access corporate services and protect data on the device. It provides strong encryption for data in transmission, proven authentication methods
Desktop as a Service (DaaS): A Solution for Modern Agencies
 Desktop as a Service (DaaS): A Solution for Modern Agencies Control unpredictable costs, increase efficiency, and enhance security with a cloud-based approach to desktop management. A solution for modern
Desktop as a Service (DaaS): A Solution for Modern Agencies Control unpredictable costs, increase efficiency, and enhance security with a cloud-based approach to desktop management. A solution for modern
ipad in Business Security
 ipad in Business Security Device protection Strong passcodes Passcode expiration Passcode reuse history Maximum failed attempts Over-the-air passcode enforcement Progressive passcode timeout Data security
ipad in Business Security Device protection Strong passcodes Passcode expiration Passcode reuse history Maximum failed attempts Over-the-air passcode enforcement Progressive passcode timeout Data security
Outlook Express POP Instructions - Bloomsburg University Students
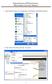 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
Technical Brief ActiveSync Configuration for WatchGuard SSL 100
 Introduction Technical Brief ActiveSync Configuration for WatchGuard SSL 100 October 2009 With ActiveSync, users get push functionality to keep email, calendar, tasks, and contacts up to date on a mobile
Introduction Technical Brief ActiveSync Configuration for WatchGuard SSL 100 October 2009 With ActiveSync, users get push functionality to keep email, calendar, tasks, and contacts up to date on a mobile
EasiShare Whitepaper - Empowering Your Mobile Workforce
 Accessing files on mobile devices and sharing them with external parties presents serious security risks for companies. However, most current solutions are either too cumbersome or not secure enough for
Accessing files on mobile devices and sharing them with external parties presents serious security risks for companies. However, most current solutions are either too cumbersome or not secure enough for
Microsoft Exchange ActiveSync Administrator s Guide
 Microsoft Exchange ActiveSync Administrator s Guide Copyright 2005 palmone, Inc. All rights reserved. palmone, HotSync, Treo, VersaMail, and Palm OS are among the trademarks or registered trademarks owned
Microsoft Exchange ActiveSync Administrator s Guide Copyright 2005 palmone, Inc. All rights reserved. palmone, HotSync, Treo, VersaMail, and Palm OS are among the trademarks or registered trademarks owned
Integrating F5 Application Delivery Solutions with VMware View 4.5
 APPLICATION READY SOLUTION GUIDE What s inside: 2 Improving user experience 2 Enhancing security and access control 3 Application Performance and Availability 4 F5 and global configuration diagram 5 More
APPLICATION READY SOLUTION GUIDE What s inside: 2 Improving user experience 2 Enhancing security and access control 3 Application Performance and Availability 4 F5 and global configuration diagram 5 More
RSA Authentication Manager 7.1 Security Best Practices Guide. Version 2
 RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
RSA Authentication Manager 7.1 Security Best Practices Guide Version 2 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks
Security Guide. BlackBerry Enterprise Service 12. for ios, Android, and Windows Phone. Version 12.0
 Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Deploy secure, corporate access for mobile device users with the Junos Pulse Mobile Security Suite
 WHITE PAPER Mobile Device Security in the Enterprise Deploy secure, corporate access for mobile device users with the Junos Pulse Mobile Security Suite Copyright 2010, Juniper Networks, Inc. Table of Contents
WHITE PAPER Mobile Device Security in the Enterprise Deploy secure, corporate access for mobile device users with the Junos Pulse Mobile Security Suite Copyright 2010, Juniper Networks, Inc. Table of Contents
Windows Phone 8.1 Mobile Device Management Overview
 Windows Phone 8.1 Mobile Device Management Overview Published April 2014 Executive summary Most organizations are aware that they need to secure corporate data and minimize risks if mobile devices are
Windows Phone 8.1 Mobile Device Management Overview Published April 2014 Executive summary Most organizations are aware that they need to secure corporate data and minimize risks if mobile devices are
iphone in Business How-To Setup Guide for Users
 iphone in Business How-To Setup Guide for Users iphone is ready for business. It supports Microsoft Exchange ActiveSync, as well as standards-based services, delivering email, calendars, and contacts over
iphone in Business How-To Setup Guide for Users iphone is ready for business. It supports Microsoft Exchange ActiveSync, as well as standards-based services, delivering email, calendars, and contacts over
Windows Mail POP Instructions - Bloomsburg University Students
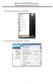 1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
McAfee Enterprise Mobility Management Versus Microsoft Exchange ActiveSync
 McAfee Enterprise Mobility Management Versus Microsoft Secure, easy, and scalable mobile device management Table of Contents What Can Do? 3 The smartphone revolution is sweeping the enterprise 3 Can enterprises
McAfee Enterprise Mobility Management Versus Microsoft Secure, easy, and scalable mobile device management Table of Contents What Can Do? 3 The smartphone revolution is sweeping the enterprise 3 Can enterprises
Information Systems. Connecting Smartphones to NTU s Email System
 Information Systems Connecting Smartphones to NTU s Email System Connecting Smartphones to NTU s Email System Contents Things to be aware of before you start 3 Connecting a Windows Mobile 6 (6.0-6.5) Phone
Information Systems Connecting Smartphones to NTU s Email System Connecting Smartphones to NTU s Email System Contents Things to be aware of before you start 3 Connecting a Windows Mobile 6 (6.0-6.5) Phone
Cortado Corporate Server
 Cortado Corporate Server 100 % On Premise Installed & Run Entirely On Your Corporate Network Feature Mobile Device Device Policy Application E-mail Push Wi-Fi Configuration Push Enable secure BYOD and
Cortado Corporate Server 100 % On Premise Installed & Run Entirely On Your Corporate Network Feature Mobile Device Device Policy Application E-mail Push Wi-Fi Configuration Push Enable secure BYOD and
Endpoint protection for physical and virtual desktops
 datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
RoadSync. Administrator s Guide. www.dataviz.com/roadsync. Mobilizing Microsoft Office Life for Businesses & Professionals Around the World
 Access Corporate Outlook E-mail & Data on the World s Most Popular Smartphones via Secure, Wireless & Direct Synchronization with Microsoft Exchange 2003 RoadSync Administrator s Guide Mobilizing Microsoft
Access Corporate Outlook E-mail & Data on the World s Most Popular Smartphones via Secure, Wireless & Direct Synchronization with Microsoft Exchange 2003 RoadSync Administrator s Guide Mobilizing Microsoft
Only 8% of corporate laptop data is actually backed up to corporate servers. Pixius Advantage Outsourcing Managed Services
 Pixius Advantage Outsourcing Managed Services Move forward with endpoint protection by understanding its unique requirements. As the number of information workers rises, so does the growth and importance
Pixius Advantage Outsourcing Managed Services Move forward with endpoint protection by understanding its unique requirements. As the number of information workers rises, so does the growth and importance
Monitor Mobile Devices via ActiveSync Using EventTracker
 Monitor Mobile Devices via ActiveSync Using EventTracker White Paper Publication Date: March 1, 2013 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Exchange
Monitor Mobile Devices via ActiveSync Using EventTracker White Paper Publication Date: March 1, 2013 EventTracker 8815 Centre Park Drive Columbia MD 21045 www.eventtracker.com About This Guide Exchange
Windows Phone 8 Security Overview
 Windows Phone 8 Security Overview This white paper is part of a series of technical papers designed to help IT professionals evaluate Windows Phone 8 and understand how it can play a role in their organizations.
Windows Phone 8 Security Overview This white paper is part of a series of technical papers designed to help IT professionals evaluate Windows Phone 8 and understand how it can play a role in their organizations.
ConnectMail Mobile Email Configuration
 ConnectMail Mobile Email Configuration Introduction/Utility ConnectMail allows you to use your mobile phone to access information in your account. This includes e mail messages, calendar, and contacts.
ConnectMail Mobile Email Configuration Introduction/Utility ConnectMail allows you to use your mobile phone to access information in your account. This includes e mail messages, calendar, and contacts.
McAfee Enterprise Mobility Management
 McAfee Enterprise Mobility Management Providing mobile application enablement and HIPAA security compliance Table of Contents HIPAA and ephi 3 Overview of 3 HIPAA Compliance for Remote Access 4 Table 1.
McAfee Enterprise Mobility Management Providing mobile application enablement and HIPAA security compliance Table of Contents HIPAA and ephi 3 Overview of 3 HIPAA Compliance for Remote Access 4 Table 1.
An Oracle White Paper December 2010. Integrating Oracle Enterprise Single Sign-On Suite Plus with Strong Authentication
 An Oracle White Paper December 2010 Integrating Oracle Enterprise Single Sign-On Suite Plus with Strong Authentication Introduction Protecting data in the digital age is critical. A security breach, if
An Oracle White Paper December 2010 Integrating Oracle Enterprise Single Sign-On Suite Plus with Strong Authentication Introduction Protecting data in the digital age is critical. A security breach, if
Software Token. Installation and User Guide. 2013 MasterCard Proprietary. All rights reserved.
 Software Token Installation and User Guide 2013 MasterCard Proprietary. All rights reserved. Contents Overview... 1 Install the RSA Client Desktop Application... 1 Download and Save the RSA Desktop Application...
Software Token Installation and User Guide 2013 MasterCard Proprietary. All rights reserved. Contents Overview... 1 Install the RSA Client Desktop Application... 1 Download and Save the RSA Desktop Application...
Content Protection in Silverlight. Microsoft Corporation
 Content Protection in Silverlight Microsoft Corporation April 2010 Contents Contents...2 Introduction...3 What is Content Protection?... 3 Why Should You Protect Online Content?... 3 Techniques for Protecting
Content Protection in Silverlight Microsoft Corporation April 2010 Contents Contents...2 Introduction...3 What is Content Protection?... 3 Why Should You Protect Online Content?... 3 Techniques for Protecting
Two-Factor Authentication
 Two-Factor Authentication IT Professional & Customer Service Desk Feature Guide Two-Factor Authentication for Exchange Online Office 365 Dedicated & ITAR-Support Plans April 26, 2013 The information contained
Two-Factor Authentication IT Professional & Customer Service Desk Feature Guide Two-Factor Authentication for Exchange Online Office 365 Dedicated & ITAR-Support Plans April 26, 2013 The information contained
NHSmail mobile configuration guide Android mobile devices
 NHSmail mobile configuration guide Android mobile devices Version: V.6 Date: September 2011 THIS INFORMATION IS FOR NHS STAFF AND IS NOT TO BE DISTRIBUTED OR COPIED OUTSIDE OF THE NHS Version 6.0 Crown
NHSmail mobile configuration guide Android mobile devices Version: V.6 Date: September 2011 THIS INFORMATION IS FOR NHS STAFF AND IS NOT TO BE DISTRIBUTED OR COPIED OUTSIDE OF THE NHS Version 6.0 Crown
Exchange Server Hybrid Deployment for Exchange Online Dedicated
 Dedicated and ITAR-support Plans Hybrid Deployment for Exchange Online Dedicated Applies to: Office 365 Dedicated - Legacy 2013 Platform Release Topic Last Modified: 31-Jan-2013 Topic Last Modified: 31-Jan-2013
Dedicated and ITAR-support Plans Hybrid Deployment for Exchange Online Dedicated Applies to: Office 365 Dedicated - Legacy 2013 Platform Release Topic Last Modified: 31-Jan-2013 Topic Last Modified: 31-Jan-2013
Vodafone Global Enterprise Deploy the Apple iphone across your Enterprise with confidence
 Vodafone Global Enterprise Deploy the Apple iphone across your Enterprise with confidence White Paper Vodafone Global Enterprise 3 The Apple iphone has become a catalyst for changing the way both users
Vodafone Global Enterprise Deploy the Apple iphone across your Enterprise with confidence White Paper Vodafone Global Enterprise 3 The Apple iphone has become a catalyst for changing the way both users
Deploying iphone and ipad Security Overview
 Deploying iphone and ipad Security Overview ios, the operating system at the core of iphone and ipad, is built upon layers of security. This enables iphone and ipad to securely access corporate services
Deploying iphone and ipad Security Overview ios, the operating system at the core of iphone and ipad, is built upon layers of security. This enables iphone and ipad to securely access corporate services
White Paper. The risks of authenticating with digital certificates exposed
 White Paper The risks of authenticating with digital certificates exposed Table of contents Introduction... 2 What is remote access?... 2 Authentication with client side digital certificates... 2 Asymmetric
White Paper The risks of authenticating with digital certificates exposed Table of contents Introduction... 2 What is remote access?... 2 Authentication with client side digital certificates... 2 Asymmetric
SmarterMail 9.x and Microsoft Exchange: An End User Comparison
 SmarterMail 9.x and Microsoft Exchange: An End User Comparison Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2012 SmarterTools Inc.
SmarterMail 9.x and Microsoft Exchange: An End User Comparison Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2012 SmarterTools Inc.
Microsoft Exchange Information Services and Security Policies Supported by Android 2.2
 Microsoft Exchange Information Services and Security Policies Supported by Android 2.2 Overview Requirements Supported Information Services Supported Security Policies Require password Require alphanumeric
Microsoft Exchange Information Services and Security Policies Supported by Android 2.2 Overview Requirements Supported Information Services Supported Security Policies Require password Require alphanumeric
Windows Phone 8.1 in the Enterprise
 Windows Phone 8.1 in the Enterprise Version 1.4 MobileIron 415 East Middlefield Road Mountain View, CA 94043 USA Tel. +1.650.919.8100 Fax +1.650.919.8006 [email protected] Introduction 3 Why Windows
Windows Phone 8.1 in the Enterprise Version 1.4 MobileIron 415 East Middlefield Road Mountain View, CA 94043 USA Tel. +1.650.919.8100 Fax +1.650.919.8006 [email protected] Introduction 3 Why Windows
Securing end-user mobile devices in the enterprise
 IBM Global Technology Services Thought Leadership White Paper January 2012 Securing end-user mobile devices in the enterprise Develop an enforceable mobile security policy and practices for safer corporate
IBM Global Technology Services Thought Leadership White Paper January 2012 Securing end-user mobile devices in the enterprise Develop an enforceable mobile security policy and practices for safer corporate
When enterprise mobility strategies are discussed, security is usually one of the first topics
 Acronis 2002-2014 Introduction When enterprise mobility strategies are discussed, security is usually one of the first topics on the table. So it should come as no surprise that Acronis Access Advanced
Acronis 2002-2014 Introduction When enterprise mobility strategies are discussed, security is usually one of the first topics on the table. So it should come as no surprise that Acronis Access Advanced
Xperia TM Email and apps
 Xperia TM Email and apps in Business Read about how Xperia TM devices manage email and synchronisation in a corporate IT environment Exchange ActiveSync IMAP4 and POP3 The Xperia Email application The
Xperia TM Email and apps in Business Read about how Xperia TM devices manage email and synchronisation in a corporate IT environment Exchange ActiveSync IMAP4 and POP3 The Xperia Email application The
Cybersecurity and Secure Authentication with SAP Single Sign-On
 Solution in Detail SAP NetWeaver SAP Single Sign-On Cybersecurity and Secure Authentication with SAP Single Sign-On Table of Contents 3 Quick Facts 4 Remember One Password Only 6 Log In Once to Handle
Solution in Detail SAP NetWeaver SAP Single Sign-On Cybersecurity and Secure Authentication with SAP Single Sign-On Table of Contents 3 Quick Facts 4 Remember One Password Only 6 Log In Once to Handle
EMC SYNCPLICITY FILE SYNC AND SHARE SOLUTION
 EMC SYNCPLICITY FILE SYNC AND SHARE SOLUTION Automated file synchronization Flexible, cloud-based administration Secure, on-premises storage EMC Solutions January 2015 Copyright 2014 EMC Corporation. All
EMC SYNCPLICITY FILE SYNC AND SHARE SOLUTION Automated file synchronization Flexible, cloud-based administration Secure, on-premises storage EMC Solutions January 2015 Copyright 2014 EMC Corporation. All
Xperia TM Email and apps
 Xperia TM Email and apps in Business Read about how Xperia TM devices manage email and synchronisation in a corporate IT environment Exchange ActiveSync IMAP4 and POP3 The Xperia Email application The
Xperia TM Email and apps in Business Read about how Xperia TM devices manage email and synchronisation in a corporate IT environment Exchange ActiveSync IMAP4 and POP3 The Xperia Email application The
EXPERT STRATEGIES FOR LOG COLLECTION, ROOT CAUSE ANALYSIS, AND COMPLIANCE
 EXPERT STRATEGIES FOR LOG COLLECTION, ROOT CAUSE ANALYSIS, AND COMPLIANCE A reliable, high-performance network is critical to your IT infrastructure and organization. Equally important to network performance
EXPERT STRATEGIES FOR LOG COLLECTION, ROOT CAUSE ANALYSIS, AND COMPLIANCE A reliable, high-performance network is critical to your IT infrastructure and organization. Equally important to network performance
iphone in Business How-To Setup Guide for Users
 iphone in Business How-To Setup Guide for Users iphone 3G is ready for business. It supports Microsoft Exchange ActiveSync, delivering push email, calendars, and contacts. And it gives mobile users secure
iphone in Business How-To Setup Guide for Users iphone 3G is ready for business. It supports Microsoft Exchange ActiveSync, delivering push email, calendars, and contacts. And it gives mobile users secure
Secure Remote Access Give users in office remote access anytime, anywhere
 Secure Remote Access Give users in office remote access anytime, anywhere June 2008 Introduction As organizations strive to increase productivity, secure remote access to network resources becomes increasingly
Secure Remote Access Give users in office remote access anytime, anywhere June 2008 Introduction As organizations strive to increase productivity, secure remote access to network resources becomes increasingly
FileCloud Security FAQ
 is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
Exchange Online. Helps Solve IT Challenges WHITEPAPER
 WHITEPAPER How Microsoft Exchange Online Helps Solve IT Challenges Exchange Online is designed to help organizations such as yours meet common IT and operational challenges, while still offering the flexibility
WHITEPAPER How Microsoft Exchange Online Helps Solve IT Challenges Exchange Online is designed to help organizations such as yours meet common IT and operational challenges, while still offering the flexibility
Android support for Microsoft Exchange in pure Google devices
 Android support for Microsoft Exchange in pure Google devices Note: The information presented here is intended for Microsoft Exchange administrators who are planning and implementing support for any of
Android support for Microsoft Exchange in pure Google devices Note: The information presented here is intended for Microsoft Exchange administrators who are planning and implementing support for any of
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
Symantec Mobile Management for Configuration Manager 7.2
 Symantec Mobile Management for Configuration Manager 7.2 Scalable, Secure, and Integrated Device Management Data Sheet: Endpoint Management and Mobility Overview The rapid proliferation of mobile devices
Symantec Mobile Management for Configuration Manager 7.2 Scalable, Secure, and Integrated Device Management Data Sheet: Endpoint Management and Mobility Overview The rapid proliferation of mobile devices
Strong Authentication: Enabling Efficiency and Maximizing Security in Your Microsoft Environment
 Strong Authentication: Enabling Efficiency and Maximizing Security in Your Microsoft Environment IIIIII Best Practices www.gemalto.com IIIIII Table of Contents Strong Authentication and Cybercrime... 1
Strong Authentication: Enabling Efficiency and Maximizing Security in Your Microsoft Environment IIIIII Best Practices www.gemalto.com IIIIII Table of Contents Strong Authentication and Cybercrime... 1
NHSmail and mobile devices overview
 NHSmail and mobile devices overview Version: V.7 Date: May 2011 THIS INFORMATION IS FOR NHS STAFF AND IS NOT TO BE DISTRIBUTED OR COPIED OUTSIDE OF THE NHS Version 7 Crown Copyright, May 2011 Contents
NHSmail and mobile devices overview Version: V.7 Date: May 2011 THIS INFORMATION IS FOR NHS STAFF AND IS NOT TO BE DISTRIBUTED OR COPIED OUTSIDE OF THE NHS Version 7 Crown Copyright, May 2011 Contents
Android App User Guide
 www.novell.com/documentation Android App User Guide ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
www.novell.com/documentation Android App User Guide ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
Security Overview Enterprise-Class Secure Mobile File Sharing
 Security Overview Enterprise-Class Secure Mobile File Sharing Accellion, Inc. 1 Overview 3 End to End Security 4 File Sharing Security Features 5 Storage 7 Encryption 8 Audit Trail 9 Accellion Public Cloud
Security Overview Enterprise-Class Secure Mobile File Sharing Accellion, Inc. 1 Overview 3 End to End Security 4 File Sharing Security Features 5 Storage 7 Encryption 8 Audit Trail 9 Accellion Public Cloud
Manufacturer to Enhance Efficiency with Improved Identity Management
 Microsoft Forefront: Security Products for Business Customer Solution Case Study Manufacturer to Enhance Efficiency with Improved Identity Management Overview Country or Region: United States Industry:
Microsoft Forefront: Security Products for Business Customer Solution Case Study Manufacturer to Enhance Efficiency with Improved Identity Management Overview Country or Region: United States Industry:
iphone in Business Mobile Device Management
 19 iphone in Business Mobile Device Management iphone supports Mobile Device Management, giving businesses the ability to manage scaled deployments of iphone across their organizations. These Mobile Device
19 iphone in Business Mobile Device Management iphone supports Mobile Device Management, giving businesses the ability to manage scaled deployments of iphone across their organizations. These Mobile Device
RSA SecurID Software Token Security Best Practices Guide
 RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
RSA SecurID Software Token Security Best Practices Guide Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA, the RSA
Digital certificates and SSL
 Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Exchange 2010 migration guide
 HOW-TO GUIDE Exchange 2010 migration guide This guide details the best practices to follow when migrating from Microsoft Exchange 2003 to Microsoft Exchange 2010. The guidelines provided explain how to
HOW-TO GUIDE Exchange 2010 migration guide This guide details the best practices to follow when migrating from Microsoft Exchange 2003 to Microsoft Exchange 2010. The guidelines provided explain how to
Exchange 2010 ActiveSync: Connection
 Westlands School Exchange 2010 ActiveSync: Connection Staff mobile phone email access Exchange 2010 ActiveSync provides Westlands School Staff with external access to their school email account from a
Westlands School Exchange 2010 ActiveSync: Connection Staff mobile phone email access Exchange 2010 ActiveSync provides Westlands School Staff with external access to their school email account from a
Mobile Workforce. Connect, Protect, and Manage Mobile Devices and Users with Junos Pulse and the Junos Pulse Mobile Security Suite.
 White Paper Securing Today s Mobile Workforce Connect, Protect, and Manage Mobile Devices and Users with Junos Pulse and the Junos Pulse Mobile Security Suite Copyright 2012, Juniper Networks, Inc. 1 Table
White Paper Securing Today s Mobile Workforce Connect, Protect, and Manage Mobile Devices and Users with Junos Pulse and the Junos Pulse Mobile Security Suite Copyright 2012, Juniper Networks, Inc. 1 Table
Active Directory Self-Service FAQ
 Active Directory Self-Service FAQ General Information: [email protected] Online Support: [email protected] CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
Active Directory Self-Service FAQ General Information: [email protected] Online Support: [email protected] CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
Consumerization. Managing the BYOD trend successfully. Harish Krishnan, General Manager, Wipro Mobility Solutions WWW.WIPRO.COM
 Consumerization Managing the BYOD trend successfully WWW.WIPRO.COM Harish Krishnan, General Manager, Wipro Mobility Solutions Employees dictate IT Enterprises across the world are giving in to the Consumerization
Consumerization Managing the BYOD trend successfully WWW.WIPRO.COM Harish Krishnan, General Manager, Wipro Mobility Solutions Employees dictate IT Enterprises across the world are giving in to the Consumerization
Deploying NetScaler with Microsoft Exchange 2016
 Deployment Guide Deploying NetScaler with Microsoft Exchange 2016 Deployment Guide Load balancing Microsoft Exchange 2016 with NetScaler Table of Contents Introduction 3 Configuration 5 NetScaler features
Deployment Guide Deploying NetScaler with Microsoft Exchange 2016 Deployment Guide Load balancing Microsoft Exchange 2016 with NetScaler Table of Contents Introduction 3 Configuration 5 NetScaler features
F5 and Microsoft Exchange Security Solutions
 F5 PARTNERSHIP SOLUTION GUIDE F5 and Microsoft Exchange Security Solutions Deploying a service-oriented perimeter for Microsoft Exchange WHAT'S INSIDE Pre-Authentication Mobile Device Security Web Application
F5 PARTNERSHIP SOLUTION GUIDE F5 and Microsoft Exchange Security Solutions Deploying a service-oriented perimeter for Microsoft Exchange WHAT'S INSIDE Pre-Authentication Mobile Device Security Web Application
Securing Corporate Email on Personal Mobile Devices
 Securing Corporate Email on Personal Mobile Devices Table of Contents The Impact of Personal Mobile Devices on Corporate Security... 3 Introducing LetMobile Secure Mobile Email... 3 Solution Architecture...
Securing Corporate Email on Personal Mobile Devices Table of Contents The Impact of Personal Mobile Devices on Corporate Security... 3 Introducing LetMobile Secure Mobile Email... 3 Solution Architecture...
RFI Template for Enterprise MDM Solutions
 RFI Template for Enterprise MDM Solutions 2012 Zenprise, Inc. 1 About This RFI Template A secure mobile device management solution is an integral part of any effective enterprise mobility program. Mobile
RFI Template for Enterprise MDM Solutions 2012 Zenprise, Inc. 1 About This RFI Template A secure mobile device management solution is an integral part of any effective enterprise mobility program. Mobile
How Microsoft IT manages mobile device management
 IT Insights A service of Microsoft IT Showcase How Microsoft IT manages mobile device management July 2015 Bring Your Own Device (BYOD) is no longer just a trend. It is arguably the dominant culture in
IT Insights A service of Microsoft IT Showcase How Microsoft IT manages mobile device management July 2015 Bring Your Own Device (BYOD) is no longer just a trend. It is arguably the dominant culture in
Outlook Express IMAP Instructions - Bloomsburg University Students
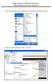 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2. Feature and Technical Overview
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Feature and Technical Overview Published: 2010-06-16 SWDT305802-1108946-0615123042-001 Contents 1 Overview: BlackBerry Enterprise
Large Nonprofit Hospital Improves Communications with Messaging Solution
 Microsoft Windows Server System Customer Solution Case Study Large Nonprofit Hospital Improves Communications with Messaging Solution Overview Country or Region: United States Industry: Healthcare Customer
Microsoft Windows Server System Customer Solution Case Study Large Nonprofit Hospital Improves Communications with Messaging Solution Overview Country or Region: United States Industry: Healthcare Customer
How To Secure An Rsa Authentication Agent
 RSA Authentication Agents Security Best Practices Guide Version 3 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA,
RSA Authentication Agents Security Best Practices Guide Version 3 Contact Information Go to the RSA corporate web site for regional Customer Support telephone and fax numbers: www.rsa.com. Trademarks RSA,
Faculty & Staff: Office 365 Email Migration
 Faculty & Staff: Office 365 Email Migration Over the next few months, Berry College faculty and staff email accounts will be migrated to Office 365. This means that all of our emails are being moved to
Faculty & Staff: Office 365 Email Migration Over the next few months, Berry College faculty and staff email accounts will be migrated to Office 365. This means that all of our emails are being moved to
Integration Guide. SafeNet Authentication Client. Using SAC CBA for Check Point Security Gateway
 SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
Installing Logos SSL Certificates on Mobile Devices
 Installing Logos SSL Certificates on Mobile Devices Phase 1: Obtain the SSL Certificate You can obtain the SSL certificate in one of 2 ways. Method 1 Download the SSL certificate from it.logostech.net
Installing Logos SSL Certificates on Mobile Devices Phase 1: Obtain the SSL Certificate You can obtain the SSL certificate in one of 2 ways. Method 1 Download the SSL certificate from it.logostech.net
Proven LANDesk Solutions
 LANDesk Solutions Descriptions Proven LANDesk Solutions IT departments face pressure to reduce costs, reduce risk, and increase productivity in the midst of growing IT complexity. More than 4,300 organizations
LANDesk Solutions Descriptions Proven LANDesk Solutions IT departments face pressure to reduce costs, reduce risk, and increase productivity in the midst of growing IT complexity. More than 4,300 organizations
