Seventeenth Meeting of the IMF Committee on Balance of Payments Statistics Pretoria, October 26 29, 2004
|
|
|
- Amanda Chase
- 8 years ago
- Views:
Transcription
1 BOPCOM-04/11 Seventeenth Meeting of the IMF Committee on Balance of Payments Statistics Pretoria, October 26 29, 2004 Development of Japan s Internet Reporting System Prepared by the International Department Bank of Japan
2 September 30, 2004 International Department, Bank of Japan Development of Japan s Internet Reporting System Japan s Internet reporting system has been named as BOP system. BOP stands for Bank of Japan Open Network for Electronic Procedures under the Foreign Exchange and Foreign Trade Law (the Law). The BOP system will enable on-line reporting of international transaction and position data (see Attachment for BOP s system configuration). Development of the BOP system is at its final stage. It has been developed on schedule and is planned to start in January In November and December 2004, we will conduct final program tests with major participating respondents. The background of the Internet reporting project is threefold. First, an e-government strategy was established in Under this strategy, the Ministry of Finance and the Bank of Japan (BOJ) were required to prepare for Internet reporting of international transaction and position data under the Law. Second, our legacy (current) system for the compilation of Japan s balance of payments statistics had to be updated. This was a good opportunity for us to initiate the project of Internet reporting system. Third, efficiency of data compilation had to be further improved. It was considered that the workload associated with validating collected data and inputting them had to be largely reduced. The development of the Internet reporting system has demanded the allocation of huge resources, which will amount to 2,000 man-months (1 man-month corresponds to 1 million yen). However, it is considered that benefits of the Internet reporting system will be large enough to overweigh the costs in five to ten years. Eventually, necessary human resources will be reduced by 20%, in the case that 50% of reports are transmitted on-line. Such reduction is possible simply because our staff will not need to check the reports submitted in hardcopies nor manually input the data. In addition, the development of the new system has given us a very good opportunity to conduct business process reengineering. For example, reports required by the Law will be streamlined and the number of report forms will be reduced by 50%. 1
3 One of the most important key success factors is cooperation of respondents. The campaign to collect respondents applications started in July As of September , first deadline of the application, 484 organizations indicated their agreement to participate. We expect that the number of participants will increase after the BOP system becomes readily available. The totality of Japan s major respondents agreed to participate in the BOP system; these major respondents are required to submit daily reports on cross-border portfolio investment. 1 We believe that such a high participation rate is due to following reasons. First, the BOP system will provide convenience to its participants. They will be able to report data easily at any time, saving mailing time and costs and reducing labor costs of preparing reports on a paper basis. Second, BOP system s implementation cost will be low. The BOJ will provide participants with client application software free of charge. Third, robust security measures will be incorporated to protect data confidentiality when information is transmitted. We explained those measures at the last BOPCOM meeting. 2 In the future, we may need to update the BOP system if we change our data collection system from an ITRS to a survey system. The BOP system is based on the ITRS, which largely depends on individual reports for all international cash transactions. We are currently exploring the possibility of introducing a survey system, which focuses more on major players of international transactions than on individual international cash transactions. We do not know yet the impact of this change on the BOP system; however, we believe that the basic structure of the Internet reporting could be maintained. Finally, we are ready to share with BOPCOM members or other statistics compilers our experiences and expertise of developing an Internet reporting system. For this purpose, we would like to meet the needs of international statistical community as much as possible. 1 For cross-border portfolio investment, large investors whose gross trading amount exceeds 1 trillion yen per year are required to report their portfolio investment trading on a daily basis under the Law. Currently, 88 organizations, including major securities companies, banks, and other institutional investors, are legally obliged to submit such daily reports. 2 The System offers following security measures; 1) server authentication, 2) data encryption, 3) multi-layered firewalls, 4) intrusion detection system, 5) access logging. For detail, please refer to 2
4
5 4 Summary of System Configuration of BOJ Open Network for Electronic Procedures on the Foreign Exchange and Foreign Trade Law (BOP) Internet BOP on-line system Reporter F W Original Document Server Tray MOF F W MOF METI METI IDS F W ID/Password - Server/Client Authentication Retrieval Filing - File/Communication Encryption LEGEND: F/W: Firewall IDS: Intrusion Detection System BOJ Personnel MOF: Ministry of Finance METI: Ministry of Economy, Trade and Industry
Security Measures for the BOJ Open Network for Electronic Procedures on the Foreign Exchange and Foreign Trade Law
 Security Measures for the BOJ Open Network for Electronic Procedures on the Foreign Exchange and Foreign Trade Law Prepared by the Balance of Payments Division, International Department Bank of Japan October,
Security Measures for the BOJ Open Network for Electronic Procedures on the Foreign Exchange and Foreign Trade Law Prepared by the Balance of Payments Division, International Department Bank of Japan October,
Sixteenth Meeting of the IMF Committee on Balance of Payments Statistics Washington D.C., December 1 5, 2003
 BOPCOM-03/21 Sixteenth Meeting of the IMF Committee on Balance of Payments Statistics Washington D.C., December 1 5, 2003 Employee Stock Options in Balance of Payments Statistics Prepared by the International
BOPCOM-03/21 Sixteenth Meeting of the IMF Committee on Balance of Payments Statistics Washington D.C., December 1 5, 2003 Employee Stock Options in Balance of Payments Statistics Prepared by the International
M&T BANK CANADIAN PRIVACY POLICY
 M&T BANK CANADIAN PRIVACY POLICY At M&T Bank, we are committed to safeguarding your personal information and maintaining your privacy. This has always been a priority for us and this is why M&T Bank (
M&T BANK CANADIAN PRIVACY POLICY At M&T Bank, we are committed to safeguarding your personal information and maintaining your privacy. This has always been a priority for us and this is why M&T Bank (
Is it Possible to Live Without Having Real Estate?
 S max n i 1 a i q maxi n a i i 1 1 - - - - - - - - Information Security Goals Confidentiality Requirements Integrity Requirements Availability Requirements Mission Criticality C0 C1 C2 C3 I0
S max n i 1 a i q maxi n a i i 1 1 - - - - - - - - Information Security Goals Confidentiality Requirements Integrity Requirements Availability Requirements Mission Criticality C0 C1 C2 C3 I0
SBA s E-Tran. Electronic Loan Processing/Servicing
 SBA s E-Tran Electronic Loan Processing/Servicing What is E-Tran? E-Tran is an SBA loan guaranty origination/servicing solution that: Leverages internet technology to reduce the turnaround time on loan
SBA s E-Tran Electronic Loan Processing/Servicing What is E-Tran? E-Tran is an SBA loan guaranty origination/servicing solution that: Leverages internet technology to reduce the turnaround time on loan
Cathay Business Online Banking
 Cathay Business Online Banking A QUICK GUIDE TO CATHAY BUSINESS ONLINE BANKING R6119 CATHAY 8_5x11 Cover V2.indd 1 6/11/13 5:50 PM Welcome Welcome to Cathay Business Online Banking (formerly known as Cathay
Cathay Business Online Banking A QUICK GUIDE TO CATHAY BUSINESS ONLINE BANKING R6119 CATHAY 8_5x11 Cover V2.indd 1 6/11/13 5:50 PM Welcome Welcome to Cathay Business Online Banking (formerly known as Cathay
ACCESS CONTROL TO A NETWORKED COMPUTER SYSTEM
 Mestrado em Ciência da Informação Segurança da Informação 2013/2014 ACCESS CONTROL TO A NETWORKED COMPUTER SYSTEM André Pinto & Ricardo Silva Summary 1 2 Introduction 1.1 Information Security 1.2 Work
Mestrado em Ciência da Informação Segurança da Informação 2013/2014 ACCESS CONTROL TO A NETWORKED COMPUTER SYSTEM André Pinto & Ricardo Silva Summary 1 2 Introduction 1.1 Information Security 1.2 Work
NOTIFICATION OF THE STOCK EXCHANGE OF THAILAND Re: Standards of the Trading of Securities Through Internet, 2005
 NOTIFICATION OF THE STOCK EXCHANGE OF THAILAND Re: Standards of the Trading of Securities Through Internet, 2005 By virtue of Clause 14 of the Regulations of the Stock Exchange of Thailand Re: Trading
NOTIFICATION OF THE STOCK EXCHANGE OF THAILAND Re: Standards of the Trading of Securities Through Internet, 2005 By virtue of Clause 14 of the Regulations of the Stock Exchange of Thailand Re: Trading
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems
 Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
Our Commitment to Your Security and Privacy
 Our Commitment to Your Security and Privacy The First American Corporation, founded in 1889, is the leading provider of real estate-related financial services. First American is committed to offering an
Our Commitment to Your Security and Privacy The First American Corporation, founded in 1889, is the leading provider of real estate-related financial services. First American is committed to offering an
Course: Information Security Management in e-governance. Day 1. Session 5: Securing Data and Operating systems
 Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
Course: Information Security Management in e-governance Day 1 Session 5: Securing Data and Operating systems Agenda Introduction to information, data and database systems Information security risks surrounding
Configuring User Identification via Active Directory
 Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos johan@accessdenied.be User Identification Overview User Identification allows you to create security policies based
Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos johan@accessdenied.be User Identification Overview User Identification allows you to create security policies based
COLUMBUS STATE COMMUNITY COLLEGE POLICY AND PROCEDURES MANUAL
 PAYMENT CARD INDUSTRY COMPLIANCE (PCI) Effective June 1, 2011 Page 1 of 6 (1) Definitions a. Payment Card Industry Data Security Standards (PCI-DSS): A set of standards established by the Payment Card
PAYMENT CARD INDUSTRY COMPLIANCE (PCI) Effective June 1, 2011 Page 1 of 6 (1) Definitions a. Payment Card Industry Data Security Standards (PCI-DSS): A set of standards established by the Payment Card
FINAL May 2005. Guideline on Security Systems for Safeguarding Customer Information
 FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
FINAL May 2005 Guideline on Security Systems for Safeguarding Customer Information Table of Contents 1 Introduction 1 1.1 Purpose of Guideline 1 2 Definitions 2 3 Internal Controls and Procedures 2 3.1
The Japan Society of Mechanical Engineers C 2010
 The Japan Society of Mechanical Engineers C 2010 The Japan Society of Mechanical Engineers 2010 C The Japan Society of Mechanical Engineers 2010 C The Japan Society of Mechanical Engineers C 2010 The Japan
The Japan Society of Mechanical Engineers C 2010 The Japan Society of Mechanical Engineers 2010 C The Japan Society of Mechanical Engineers 2010 C The Japan Society of Mechanical Engineers C 2010 The Japan
The U.S. Current Account Deficit and The Dollar
 The U.S. Current Account Deficit and The Dollar Olivier Blanchard paper available on web page 1 The U.S. current account deficit: The basic facts Large and getting larger: -5.7% in 2004, -6.2% in 2005?
The U.S. Current Account Deficit and The Dollar Olivier Blanchard paper available on web page 1 The U.S. current account deficit: The basic facts Large and getting larger: -5.7% in 2004, -6.2% in 2005?
BUSINESS PLAN: Finance
 BUSINESS PLAN: Finance How does this service contribute to the results identified in the City of London Strategic Plan? A strong economy A vibrant and diverse community A green and growing City A sustainable
BUSINESS PLAN: Finance How does this service contribute to the results identified in the City of London Strategic Plan? A strong economy A vibrant and diverse community A green and growing City A sustainable
Your Setup Guide to Consumer Online Banking What s Inside:
 Your Setup Guide to Consumer Online Banking What s Inside: Enroll in Online Banking Advanced Authentication Logging In estatements ENROLL IN Online BANKING TODAY! Go to www.renasantbank.com to see how
Your Setup Guide to Consumer Online Banking What s Inside: Enroll in Online Banking Advanced Authentication Logging In estatements ENROLL IN Online BANKING TODAY! Go to www.renasantbank.com to see how
Walton Centre. Document History Date Version Author Changes 01/10/2004 1.0 A Cobain L Wyatt 07/01/2005 1.1 L Wyatt Update to procedure
 Page 1 Walton Centre Network Monitoring Document History Date Version Author Changes 01/10/2004 1.0 A Cobain L Wyatt 07/01/2005 1.1 L Wyatt Update to procedure Page 2 Table of Contents Section Contents
Page 1 Walton Centre Network Monitoring Document History Date Version Author Changes 01/10/2004 1.0 A Cobain L Wyatt 07/01/2005 1.1 L Wyatt Update to procedure Page 2 Table of Contents Section Contents
6-8065 Payment Card Industry Compliance
 0 0 0 Yosemite Community College District Policies and Administrative Procedures No. -0 Policy -0 Payment Card Industry Compliance Yosemite Community College District will comply with the Payment Card
0 0 0 Yosemite Community College District Policies and Administrative Procedures No. -0 Policy -0 Payment Card Industry Compliance Yosemite Community College District will comply with the Payment Card
Database Security Guideline. Version 2.0 February 1, 2009 Database Security Consortium Security Guideline WG
 Database Security Guideline Version 2.0 February 1, 2009 Database Security Consortium Security Guideline WG Table of Contents Chapter 1 Introduction... 4 1.1 Objective... 4 1.2 Prerequisites of this Guideline...
Database Security Guideline Version 2.0 February 1, 2009 Database Security Consortium Security Guideline WG Table of Contents Chapter 1 Introduction... 4 1.1 Objective... 4 1.2 Prerequisites of this Guideline...
Corporate Property Automated Information System CPAIS. Privacy Impact Assessment
 Corporate Property Automated Information System CPAIS Privacy Impact Assessment May 2003 CONTENTS Background...3 Access to the Data...5 Maintenance of Administrative Controls...9 1 Introduction The Office
Corporate Property Automated Information System CPAIS Privacy Impact Assessment May 2003 CONTENTS Background...3 Access to the Data...5 Maintenance of Administrative Controls...9 1 Introduction The Office
Problems and Measures Regarding Waste 1 Management and 3R Era of public health improvement Situation subsequent to the Meiji Restoration

Japan Economic Monthly
 Japan Economic Monthly Sustained Strong Corporate Profits Point to Increasing Employment and Capital Expenditures REI TSURUTA TOORU KANAHORI ECONOMIC RESEARCH OFFICE 1 OCTOBER (ORIGINAL JAPANESE VERSION
Japan Economic Monthly Sustained Strong Corporate Profits Point to Increasing Employment and Capital Expenditures REI TSURUTA TOORU KANAHORI ECONOMIC RESEARCH OFFICE 1 OCTOBER (ORIGINAL JAPANESE VERSION
Secure Mail Registration and Viewing Procedures
 Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
UMHLABUYALINGANA MUNICIPALITY FIREWALL MANAGEMENT POLICY
 UMHLABUYALINGANA MUNICIPALITY FIREWALL MANAGEMENT POLICY Firewall Management Policy Approval and Version Control Approval Process: Position or Meeting Number: Date: Originator: Recommended by Director
UMHLABUYALINGANA MUNICIPALITY FIREWALL MANAGEMENT POLICY Firewall Management Policy Approval and Version Control Approval Process: Position or Meeting Number: Date: Originator: Recommended by Director
Your Setup Guide to Consumer Internet Banking What s Inside:
 Your Setup Guide to Consumer Internet Banking What s Inside: Enroll in Internet Banking Advanced Authentication Logging In estatements ENROLL IN INTERNET BANKING TODAY! Go to www.renasantbank.com to see
Your Setup Guide to Consumer Internet Banking What s Inside: Enroll in Internet Banking Advanced Authentication Logging In estatements ENROLL IN INTERNET BANKING TODAY! Go to www.renasantbank.com to see
Keyfort Cloud Services (KCS)
 Keyfort Cloud Services (KCS) Data Location, Security & Privacy 1. Executive Summary The purposes of this document is to provide a common understanding of the data location, security, privacy, resiliency
Keyfort Cloud Services (KCS) Data Location, Security & Privacy 1. Executive Summary The purposes of this document is to provide a common understanding of the data location, security, privacy, resiliency
Release: 1. ICTNWK607 Design and implement wireless network security
 Release: 1 ICTNWK607 Design and implement wireless network security ICTNWK607 Design and implement wireless network security Modification History Release Release 1 Comments This version first released
Release: 1 ICTNWK607 Design and implement wireless network security ICTNWK607 Design and implement wireless network security Modification History Release Release 1 Comments This version first released
API-Security Gateway Dirk Krafzig
 API-Security Gateway Dirk Krafzig Intro Digital transformation accelerates application integration needs Dramatically increasing number of integration points Speed Security Industrial robustness Increasing
API-Security Gateway Dirk Krafzig Intro Digital transformation accelerates application integration needs Dramatically increasing number of integration points Speed Security Industrial robustness Increasing
APPENDIX G ASP/SaaS SECURITY ASSESSMENT CHECKLIST
 APPENDIX G ASP/SaaS SECURITY ASSESSMENT CHECKLIST Application Name: Vendor Name: Briefly describe the purpose of the application. Include an overview of the application architecture, and identify the data
APPENDIX G ASP/SaaS SECURITY ASSESSMENT CHECKLIST Application Name: Vendor Name: Briefly describe the purpose of the application. Include an overview of the application architecture, and identify the data
Investors G u i d e 201 0 1 Investors Guide 2011
 2011 Investors 2011 Guide 1. 2. 3. 01 Investors Guide 2011 1 2 5 3 4 6 Investors Guide 2011 02 03 Investors Guide 2011 1 2 3 4 5 Investors Guide 2011 04 1 2 2 2 05 Investors Guide 2011 3 3 3 4 5 5 5 Investors
2011 Investors 2011 Guide 1. 2. 3. 01 Investors Guide 2011 1 2 5 3 4 6 Investors Guide 2011 02 03 Investors Guide 2011 1 2 3 4 5 Investors Guide 2011 04 1 2 2 2 05 Investors Guide 2011 3 3 3 4 5 5 5 Investors
BeamYourScreen Security
 BeamYourScreen Security Table of Contents BeamYourScreen Security... 1 The Most Important Facts in a Nutshell... 3 Content Security... 3 User Interface Security... 3 Infrastructure Security... 3 In Detail...
BeamYourScreen Security Table of Contents BeamYourScreen Security... 1 The Most Important Facts in a Nutshell... 3 Content Security... 3 User Interface Security... 3 Infrastructure Security... 3 In Detail...
5 TIPS TO PAY LESS FOR PCI COMPLIANCE
 Ebook 5 TIPS TO PAY LESS FOR PCI COMPLIANCE SIMPLE STEPS TO REDUCE YOUR PCI SCOPE 2015 SecurityMetrics 5 TIPS TO PAY LESS FOR PCI COMPLIANCE 1 5 TIPS TO PAY LESS FOR PCI COMPLIANCE SIMPLE STEPS TO REDUCE
Ebook 5 TIPS TO PAY LESS FOR PCI COMPLIANCE SIMPLE STEPS TO REDUCE YOUR PCI SCOPE 2015 SecurityMetrics 5 TIPS TO PAY LESS FOR PCI COMPLIANCE 1 5 TIPS TO PAY LESS FOR PCI COMPLIANCE SIMPLE STEPS TO REDUCE
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on Mail Tab.
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Level 3 Public Use. Information Technology. Log/Event Management Guidelines
 Page 1 of 5 Prepared by: Leigh Lopez Approved by: Chris Olsen, ISO Date: May 12, 2009 Date: June 8, 2009 Last revised by: Chris Olsen Last approved by: Chris Olsen, ISO Date: June 6, 2009 Date: January
Page 1 of 5 Prepared by: Leigh Lopez Approved by: Chris Olsen, ISO Date: May 12, 2009 Date: June 8, 2009 Last revised by: Chris Olsen Last approved by: Chris Olsen, ISO Date: June 6, 2009 Date: January
GE Measurement & Control. Cyber Security for Industrial Controls
 GE Measurement & Control Cyber Security for Industrial Controls Contents Overview...3 Cyber Asset Protection (CAP) Software Update Subscription....4 SecurityST Solution Options...5 Centralized Account
GE Measurement & Control Cyber Security for Industrial Controls Contents Overview...3 Cyber Asset Protection (CAP) Software Update Subscription....4 SecurityST Solution Options...5 Centralized Account
ReadyNAS Remote. Add-on Manual. 350 East Plumeria Drive San Jose, CA 95134 USA. May 2012 202-10958-01
 Add-on Manual 350 East Plumeria Drive San Jose, CA 95134 USA May 2012 202-10958-01 2012 All rights reserved No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Add-on Manual 350 East Plumeria Drive San Jose, CA 95134 USA May 2012 202-10958-01 2012 All rights reserved No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Deploying secure wireless network services The Avaya Identity Engines portfolio offers flexible, auditable management for secure wireless networks.
 Table of Contents Section 1: Executive summary...1 Section 2: The challenge...2 Section 3: WLAN security...3 and the 802.1X standard Section 4: The solution...4 Section 5: Security...4 Section 6: Encrypted
Table of Contents Section 1: Executive summary...1 Section 2: The challenge...2 Section 3: WLAN security...3 and the 802.1X standard Section 4: The solution...4 Section 5: Security...4 Section 6: Encrypted
CÚRAM. Government of Alberta. Privacy Impact Assessment. Final Report. March 2009
 Government of Alberta Final Report Submitted by: Information and Privacy Office Employment and Immigration Table of Contents 1. Background...1 2. Purpose of This Review...2 3. Managing Access and System
Government of Alberta Final Report Submitted by: Information and Privacy Office Employment and Immigration Table of Contents 1. Background...1 2. Purpose of This Review...2 3. Managing Access and System
WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance
 WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance SEC-STM-072014 07/2014 Contents Patient Choice... 2 Security Protections... 2 Participation Agreement... 2 Controls... 3 Break the Glass...
WISHIN Pulse Statement on Privacy, Security and HIPAA Compliance SEC-STM-072014 07/2014 Contents Patient Choice... 2 Security Protections... 2 Participation Agreement... 2 Controls... 3 Break the Glass...
Work With Genesis Insurance Company
 IN F O R M AT ION TEC HNOLOGY (IT ) SECURIT Y AT GEN ES I S security peace of mind You re covered. Access Control Application Security Business Continuity and Disaster Recovery Planning Cryptography Information
IN F O R M AT ION TEC HNOLOGY (IT ) SECURIT Y AT GEN ES I S security peace of mind You re covered. Access Control Application Security Business Continuity and Disaster Recovery Planning Cryptography Information
Host Hardening. Presented by. Douglas Couch & Nathan Heck Security Analysts for ITaP 1
 Host Hardening Presented by Douglas Couch & Nathan Heck Security Analysts for ITaP 1 Background National Institute of Standards and Technology Draft Guide to General Server Security SP800-123 Server A
Host Hardening Presented by Douglas Couch & Nathan Heck Security Analysts for ITaP 1 Background National Institute of Standards and Technology Draft Guide to General Server Security SP800-123 Server A
WebEx Remote Access White Paper. The CBORD Group, Inc.
 WebEx Remote Access White Paper The CBORD Group, Inc. Document Revision: 1 Last revised: October 30, 2007 Changes are periodically made to the information contained in this document. While every effort
WebEx Remote Access White Paper The CBORD Group, Inc. Document Revision: 1 Last revised: October 30, 2007 Changes are periodically made to the information contained in this document. While every effort
This brief, published April 2014, replaces a previous version published December 2012. Changes include the following:
 Volume Licensing brief Multiplexing Client Step-up licenses Access License (CAL) requirements This brief applies to all Microsoft Volume Licensing programs. Table of Contents Summary... 1 What s New in
Volume Licensing brief Multiplexing Client Step-up licenses Access License (CAL) requirements This brief applies to all Microsoft Volume Licensing programs. Table of Contents Summary... 1 What s New in
Electronic Document and Record Compliance for the Life Sciences
 Electronic Document and Record Compliance for the Life Sciences Kiran Thakrar, SoluSoft Inc. SoluSoft, Inc. 300 Willow Street South North Andover, MA 01845 Website: www.solu-soft.com Email: solusoftsales@solu-soft.com
Electronic Document and Record Compliance for the Life Sciences Kiran Thakrar, SoluSoft Inc. SoluSoft, Inc. 300 Willow Street South North Andover, MA 01845 Website: www.solu-soft.com Email: solusoftsales@solu-soft.com
Introduction...3. Conclusion...8. 2 White paper: IT SECURITY FOR SMART SCHOOLS
 White Paper IT Security for Smart Schools msc trustgate.com (478231-X) (CA License No.: LK0022000) G / F, Belatuk Block, Cyberview Garden, 63000 Cyberjaya, Selangor Darul Ehsan, Malaysia. Tel: + 603 8318
White Paper IT Security for Smart Schools msc trustgate.com (478231-X) (CA License No.: LK0022000) G / F, Belatuk Block, Cyberview Garden, 63000 Cyberjaya, Selangor Darul Ehsan, Malaysia. Tel: + 603 8318
MIKOGO SECURITY DOCUMENT
 MIKOGO SECURITY DOCUMENT Table of Contents Page 2. 6. 6. The Most Important Facts in a Nutshell In Detail Application Firewall Compatibility Quality Management: ISO 9001 Certification Data Compression
MIKOGO SECURITY DOCUMENT Table of Contents Page 2. 6. 6. The Most Important Facts in a Nutshell In Detail Application Firewall Compatibility Quality Management: ISO 9001 Certification Data Compression
I want EDUCATION with personal services to keep
 I want EDUCATION with personal services to keep things SIMPLE Improving SERVICE-Based EDUCATION the simple step to SERVICE-BaSED EDUCatIOn Education is one of the most decisive success factors for today
I want EDUCATION with personal services to keep things SIMPLE Improving SERVICE-Based EDUCATION the simple step to SERVICE-BaSED EDUCatIOn Education is one of the most decisive success factors for today
Privacy Impact Assessment. For Person Authentication Service (PAS) Date: January 9, 2015
 For Person Authentication Service (PAS) Date: January 9, 2015 Point of Contact and Author: Hanan Abu Lebdeh Hanan.Abulebdeh@ed.gov System Owner: Ganesh Reddy Ganesh.Reddy@ed.gov Office of Federal Student
For Person Authentication Service (PAS) Date: January 9, 2015 Point of Contact and Author: Hanan Abu Lebdeh Hanan.Abulebdeh@ed.gov System Owner: Ganesh Reddy Ganesh.Reddy@ed.gov Office of Federal Student
Developing Network Security Strategies
 NETE-4635 Computer Network Analysis and Design Developing Network Security Strategies NETE4635 - Computer Network Analysis and Design Slide 1 Network Security Design The 12 Step Program 1. Identify network
NETE-4635 Computer Network Analysis and Design Developing Network Security Strategies NETE4635 - Computer Network Analysis and Design Slide 1 Network Security Design The 12 Step Program 1. Identify network
IPv6 Transport Support and Market Segmentations
 Survey of IPv6 Support in Commercial Firewalls David Piscitello Fellow to the ICANN SSAC 1 Purpose and Scope of Study Determine IPv6 transport support and security service availability among commercial
Survey of IPv6 Support in Commercial Firewalls David Piscitello Fellow to the ICANN SSAC 1 Purpose and Scope of Study Determine IPv6 transport support and security service availability among commercial
BKDconnect Security Overview
 BKDconnect Security Overview 1 Introduction 1.1 What is BKDconnect 1.2 Site Creation 1.3 Client Authentication and Access 2 Security Design 2.1 Confidentiality 2.1.1 Least Privilege and Role Based Security
BKDconnect Security Overview 1 Introduction 1.1 What is BKDconnect 1.2 Site Creation 1.3 Client Authentication and Access 2 Security Design 2.1 Confidentiality 2.1.1 Least Privilege and Role Based Security
Secure Clouds - Secure Services Trend Micro best-in-class solutions enable data center to deliver trusted and secure infrastructures and services
 Secure Clouds - Secure Services Trend Micro best-in-class solutions enable data center to deliver trusted and secure infrastructures and services Udo Schneider Trend Micro Udo_Schneider@trendmicro.de 26.03.2013
Secure Clouds - Secure Services Trend Micro best-in-class solutions enable data center to deliver trusted and secure infrastructures and services Udo Schneider Trend Micro Udo_Schneider@trendmicro.de 26.03.2013
ensure prompt restart of critical applications and business activities in a timely manner following an emergency or disaster
 Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
HIPAA Security. Jeanne Smythe, UNC-CH Jack McCoy, ECU Chad Bebout, UNC-CH Doug Brown, UNC-CH
 HIPAA Security Jeanne Smythe, UNC-CH Jack McCoy, ECU Chad Bebout, UNC-CH Doug Brown, UNC-CH What is this? Federal Regulations August 21, 1996 HIPAA Became Law October 16, 2003 Transaction Codes and Identifiers
HIPAA Security Jeanne Smythe, UNC-CH Jack McCoy, ECU Chad Bebout, UNC-CH Doug Brown, UNC-CH What is this? Federal Regulations August 21, 1996 HIPAA Became Law October 16, 2003 Transaction Codes and Identifiers
How To Protect Your Credit Card Information From Being Stolen
 Visa Account Information Security Tool Kit Welcome to the Visa Account Information Security Program 2 Contents 1. Securing cardholder data is everyone s concern 4 2. Visa Account Information Security (AIS)
Visa Account Information Security Tool Kit Welcome to the Visa Account Information Security Program 2 Contents 1. Securing cardholder data is everyone s concern 4 2. Visa Account Information Security (AIS)
Compilation of Financial Account on a Gross Basis
 BOPCOM 12/14 Twenty-Fifth Meeting of the IMF Committee on Balance of Payments Statistics Washington, D.C. January 14 16, 2013 (Rescheduled from October 29 31, 2012) Compilation of Financial Account on
BOPCOM 12/14 Twenty-Fifth Meeting of the IMF Committee on Balance of Payments Statistics Washington, D.C. January 14 16, 2013 (Rescheduled from October 29 31, 2012) Compilation of Financial Account on
E-gov Asset Handling and Labelling Guidelines
 Asset Handling Labeling guidelines for e-governance Draft DEPARTMENT OF ELECTRONICS AND INFORMATION TECHNOLOGY Ministry of Communication and Information Technology, Government of India. Document Control
Asset Handling Labeling guidelines for e-governance Draft DEPARTMENT OF ELECTRONICS AND INFORMATION TECHNOLOGY Ministry of Communication and Information Technology, Government of India. Document Control
PRIVACY POLICY. Last updated February 2, 2009 INTRODUCTION
 PRIVACY POLICY Last updated February 2, 2009 INTRODUCTION This Privacy Policy explains how personal information about you may be collected, used, or disclosed by the Canadian Education and Research Institute
PRIVACY POLICY Last updated February 2, 2009 INTRODUCTION This Privacy Policy explains how personal information about you may be collected, used, or disclosed by the Canadian Education and Research Institute
To configure Outlook Express for your InfoMetrics E-mail address:
 To configure Outlook Express for your InfoMetrics E-mail address: 1. Open Outlook Express 2. Click the Tools menu, and select Accounts... 3. Internet Accounts window will open, click Add and menu will
To configure Outlook Express for your InfoMetrics E-mail address: 1. Open Outlook Express 2. Click the Tools menu, and select Accounts... 3. Internet Accounts window will open, click Add and menu will
Security Solutions. Concerned about information security? You should be!
 Security Solutions Concerned about information security? You should be! Various security threats surrounding the office Ricoh s proposal for a security management system. Information technology is the
Security Solutions Concerned about information security? You should be! Various security threats surrounding the office Ricoh s proposal for a security management system. Information technology is the
What s happening in the area of E-security for the Financial Transactions in China
 What s happening in the area of E-security for the Financial Transactions in China Dr. Wang Jun Head of E-banking Division, Bank of China Sep. 26, 2002 A Tremendous Potential E-financing Market is is coming
What s happening in the area of E-security for the Financial Transactions in China Dr. Wang Jun Head of E-banking Division, Bank of China Sep. 26, 2002 A Tremendous Potential E-financing Market is is coming
Spillemyndigheden s Certification Programme Information Security Management System
 SCP.03.00.EN.1.0 Table of contents Table of contents... 2 1 Objectives of the... 3 1.1 Scope of this document... 3 1.2 Version... 3 2 Certification... 3 2.1 Certification frequency... 3 2.1.1 Initial certification...
SCP.03.00.EN.1.0 Table of contents Table of contents... 2 1 Objectives of the... 3 1.1 Scope of this document... 3 1.2 Version... 3 2 Certification... 3 2.1 Certification frequency... 3 2.1.1 Initial certification...
National Healthcare Safety Network (NHSN) NHSN Enrollment
 National Healthcare Safety Network (NHSN) NHSN Enrollment Target Audience This training is designed for those who may be assigned as the NHSN Facility Administrator for a facility interested in NHSN Enrollment.
National Healthcare Safety Network (NHSN) NHSN Enrollment Target Audience This training is designed for those who may be assigned as the NHSN Facility Administrator for a facility interested in NHSN Enrollment.
Domestic Insurance Business Strategy. Hideo TERAMOTO, Director, Senior Managing Executive Officer
 Domestic Insurance Business Strategy Hideo TERAMOTO, Director, Senior Managing Executive Officer Growth Initiatives for Domestic Insurance Business Catering to the changing needs of our customers Product
Domestic Insurance Business Strategy Hideo TERAMOTO, Director, Senior Managing Executive Officer Growth Initiatives for Domestic Insurance Business Catering to the changing needs of our customers Product
Remote Access Procedure. e-governance
 for e-governance Draft DEPARTMENT OF ELECTRONICS AND INFORMATION TECHNOLOGY Ministry of Communication and Information Technology, Government of India. Document Control S/L Type of Information Document
for e-governance Draft DEPARTMENT OF ELECTRONICS AND INFORMATION TECHNOLOGY Ministry of Communication and Information Technology, Government of India. Document Control S/L Type of Information Document
StreamServe Encryption and Authentication
 StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
You Can Survive a PCI-DSS Assessment
 WHITE PAPER You Can Survive a PCI-DSS Assessment A QSA Primer on Best Practices for Overcoming Challenges and Achieving Compliance The Payment Card Industry Data Security Standard or PCI-DSS ensures the
WHITE PAPER You Can Survive a PCI-DSS Assessment A QSA Primer on Best Practices for Overcoming Challenges and Achieving Compliance The Payment Card Industry Data Security Standard or PCI-DSS ensures the
Best Practices For Department Server and Enterprise System Checklist
 Best Practices For Department Server and Enterprise System Checklist INSTRUCTIONS Information Best Practices are guidelines used to ensure an adequate level of protection for Information Technology (IT)
Best Practices For Department Server and Enterprise System Checklist INSTRUCTIONS Information Best Practices are guidelines used to ensure an adequate level of protection for Information Technology (IT)
Permit Power of Attorney (PoA) to establish an agreement on behalf of the taxpayer
 NOTE: The following reflects the information entered in the PIAMS website. A. SYSTEM DESCRIPTION Authority: Office of Management Budget (OMB) Memorandum (M) 03-22, OMB Guidance for Implementing the Privacy
NOTE: The following reflects the information entered in the PIAMS website. A. SYSTEM DESCRIPTION Authority: Office of Management Budget (OMB) Memorandum (M) 03-22, OMB Guidance for Implementing the Privacy
Security. Tiffany Trent-Abram VP, Global Product Management. November 6 th, 2015. One Connection - A World of Opportunities
 One Connection - A World of Opportunities Security Tiffany Trent-Abram VP, Global Product Management November 6 th, 2015 2015 TNS Inc. All Rights Reserved. Bringing Global Credibility and History TNS Specializes
One Connection - A World of Opportunities Security Tiffany Trent-Abram VP, Global Product Management November 6 th, 2015 2015 TNS Inc. All Rights Reserved. Bringing Global Credibility and History TNS Specializes
Security from a customer s perspective. Halogen s approach to security
 September 18, 2015 Security from a customer s perspective Using a cloud-based talent management program can deliver tremendous benefits to your organization, including aligning your workforce, improving
September 18, 2015 Security from a customer s perspective Using a cloud-based talent management program can deliver tremendous benefits to your organization, including aligning your workforce, improving
Configuring Personal Firewalls and Understanding IDS. Securing Networks Chapter 3 Part 2 of 4 CA M S Mehta, FCA
 Configuring Personal Firewalls and Understanding IDS Securing Networks Chapter 3 Part 2 of 4 CA M S Mehta, FCA 1 Configuring Personal Firewalls and IDS Learning Objectives Task Statements 1.4 Analyze baseline
Configuring Personal Firewalls and Understanding IDS Securing Networks Chapter 3 Part 2 of 4 CA M S Mehta, FCA 1 Configuring Personal Firewalls and IDS Learning Objectives Task Statements 1.4 Analyze baseline
JusticeConnect AVL for Windows SETUP GUIDE
 JusticeConnect AVL for Windows SETUP GUIDE 1 Table of Contents JusticeConnect AVL Procure Software... 3 JusticeConnect AVL Deploy Software... 3 JusticeConnect AVL First Time Setup... 4 JusticeConnect AVL
JusticeConnect AVL for Windows SETUP GUIDE 1 Table of Contents JusticeConnect AVL Procure Software... 3 JusticeConnect AVL Deploy Software... 3 JusticeConnect AVL First Time Setup... 4 JusticeConnect AVL
Four Top Emagined Security Services
 Four Top Emagined Security Services. www.emagined.com Emagined Security offers a variety of Security Services designed to support growing security needs. This brochure highlights four key Emagined Security
Four Top Emagined Security Services. www.emagined.com Emagined Security offers a variety of Security Services designed to support growing security needs. This brochure highlights four key Emagined Security
Access Control Policy. Document Status. Security Classification. Level 4 - PUBLIC. Version 1.0. Approval. Review By June 2012
 Access Control Policy Document Status Security Classification Version 1.0 Level 4 - PUBLIC Status DRAFT Approval Life 3 Years Review By June 2012 Owner Secure Research Database Analyst Retention Change
Access Control Policy Document Status Security Classification Version 1.0 Level 4 - PUBLIC Status DRAFT Approval Life 3 Years Review By June 2012 Owner Secure Research Database Analyst Retention Change
COL FINANCIAL GROUP, INC. RISK MANAGEMENT SYSTEM
 COL FINANCIAL GROUP, INC. RISK MANAGEMENT SYSTEM RISK MANAGEMENT PHILOSOPHY The analysis of risk and the identification of opportunities in evolving situations are inherent to the business of a stock brokerage.
COL FINANCIAL GROUP, INC. RISK MANAGEMENT SYSTEM RISK MANAGEMENT PHILOSOPHY The analysis of risk and the identification of opportunities in evolving situations are inherent to the business of a stock brokerage.
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on. User Information
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
Commodity Futures Trading Commission Privacy Impact Assessment
 Commodity Futures Trading Commission Privacy Impact Assessment System Name: CFTC Portal OPERA (Updated April 16, 2015) 1. Overview The Commodity Futures Trading Commission s ( Commission or CFTC ) Portal
Commodity Futures Trading Commission Privacy Impact Assessment System Name: CFTC Portal OPERA (Updated April 16, 2015) 1. Overview The Commodity Futures Trading Commission s ( Commission or CFTC ) Portal
Net 2. NetApp Electronic Library. User Guide for Net 2 Client Version 6.0a
 Net 2 NetApp Electronic Library User Guide for Net 2 Client Version 6.0a Table of Contents 1 INTRODUCTION AND KEY FEATURES... 3 SOME OF THE KEY FEATURES INCLUDE:... 3 INSTALLATION PREREQUISITES:... 3 2
Net 2 NetApp Electronic Library User Guide for Net 2 Client Version 6.0a Table of Contents 1 INTRODUCTION AND KEY FEATURES... 3 SOME OF THE KEY FEATURES INCLUDE:... 3 INSTALLATION PREREQUISITES:... 3 2
Interwise Connect. Working with Reverse Proxy Version 7.x
 Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
How to configure your email client
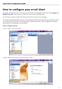 How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection
 User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection Outline How do you protect your critical confidential data?
User Authentication Job Tracking Fax Transmission via RightFax Server Secure Printing Functions HDD/Memory Security Fax to Ethernet Connection Outline How do you protect your critical confidential data?
Handling Data. Tim Albion Senior Database Administrator/ IT Systems Designer
 Handling Data Tim Albion Senior Database Administrator/ IT Systems Designer Data Collection Paper based questionnaires Web based forms Computer Assisted Telephone Interview Mobile applications Electronic
Handling Data Tim Albion Senior Database Administrator/ IT Systems Designer Data Collection Paper based questionnaires Web based forms Computer Assisted Telephone Interview Mobile applications Electronic
University of Central Florida Class Specification Administrative and Professional. Information Security Officer
 Information Security Officer Job Code: 2534 Serve as the information security officer for the University. Develop and computer security system standards, policies, and procedures. Serve as technical team
Information Security Officer Job Code: 2534 Serve as the information security officer for the University. Develop and computer security system standards, policies, and procedures. Serve as technical team
Hosted Testing and Grading
 Hosted Testing and Grading Technical White Paper July 2014 www.lexmark.com Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States and/or
Hosted Testing and Grading Technical White Paper July 2014 www.lexmark.com Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States and/or
Account Setup & Online Giving
 Account Setup & Online Giving 1. Go to gracechurch.us/giving. 2. From this screen, select Need an account? in the lower right corner of the gray box. 3. This will take you to the Create A New Account page.
Account Setup & Online Giving 1. Go to gracechurch.us/giving. 2. From this screen, select Need an account? in the lower right corner of the gray box. 3. This will take you to the Create A New Account page.
Project Management System Services
 Project Management System Services Today's projects need to deal with increasing amounts of information that require better tools to help navigate through all the data produced by projects. Our services
Project Management System Services Today's projects need to deal with increasing amounts of information that require better tools to help navigate through all the data produced by projects. Our services
Update and Installation Guide for Microsoft Management Reporter 2.0 Feature Pack 1
 Update and Installation Guide for Microsoft Management Reporter 2.0 Feature Pack 1 Microsoft Corporation Published: December 2010 Microsoft Dynamics is a line of integrated, adaptable business management
Update and Installation Guide for Microsoft Management Reporter 2.0 Feature Pack 1 Microsoft Corporation Published: December 2010 Microsoft Dynamics is a line of integrated, adaptable business management
Motivation Potential Solutions Samhain SAMHAIN. An open-source Host Intrusion Detection. System (HIDS) Rainer Wichmann
 Motivation Potential Solutions Samhain SAMHAIN An open-source Host Intrusion Detection System (HIDS) Motivation Potential Solutions Samhain A simple question How can you defend against Intrusions? Firewalls
Motivation Potential Solutions Samhain SAMHAIN An open-source Host Intrusion Detection System (HIDS) Motivation Potential Solutions Samhain A simple question How can you defend against Intrusions? Firewalls
Information Security Solutions
 Information Security Solutions V Kiyotaka Uchida V Noriaki Sugano V Syouichi Andou (Manuscript received December 20, 2006) Now that regulations such as the Japanese Sarbanes-Oxley (J-SOX) act have been
Information Security Solutions V Kiyotaka Uchida V Noriaki Sugano V Syouichi Andou (Manuscript received December 20, 2006) Now that regulations such as the Japanese Sarbanes-Oxley (J-SOX) act have been
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on Mail Tab.
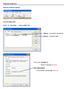 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
myedocumentsuite.com ENHANCE THE CLIENT EXPERIENCE
 myedocumentsuite.com TM ENHANCE THE CLIENT EXPERIENCE myedocumentsuite.com TM Electronic delivery of documents is rapidly becoming the standard for financial services companies. Delivering necessary documentation
myedocumentsuite.com TM ENHANCE THE CLIENT EXPERIENCE myedocumentsuite.com TM Electronic delivery of documents is rapidly becoming the standard for financial services companies. Delivering necessary documentation
H.I.P.A.A. Compliance Made Easy Products and Services
 H.I.P.A.A Compliance Made Easy Products and Services Provided by: Prevare IT Solutions 100 Cummings Center Suite 225D Beverly, MA 01915 Info-HIPAA@prevare.com 877-232-9191 Dear Health Care Professional,
H.I.P.A.A Compliance Made Easy Products and Services Provided by: Prevare IT Solutions 100 Cummings Center Suite 225D Beverly, MA 01915 Info-HIPAA@prevare.com 877-232-9191 Dear Health Care Professional,
IBM Cloud Security Draft for Discussion September 12, 2011. 2011 IBM Corporation
 IBM Cloud Security Draft for Discussion September 12, 2011 IBM Point of View: Cloud can be made secure for business As with most new technology paradigms, security concerns surrounding cloud computing
IBM Cloud Security Draft for Discussion September 12, 2011 IBM Point of View: Cloud can be made secure for business As with most new technology paradigms, security concerns surrounding cloud computing
www.cathaybank.com Cathay Business Online Banking Quick Guide
 www.cathaybank.com Cathay Business Online Banking Quick Guide Effective 06/2016 Disclaimer: The information and materials in these pages, including text, graphics, links, or other items are provided as
www.cathaybank.com Cathay Business Online Banking Quick Guide Effective 06/2016 Disclaimer: The information and materials in these pages, including text, graphics, links, or other items are provided as


