The Social Network Mining of BBS
|
|
|
- Norah Shaw
- 8 years ago
- Views:
Transcription
1 298 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE 2009 The Social Network Mining of BBS Lixin Zhou School of Software and Microelectronics, Peking University, Beijing, China Jichang Ding, Yi Wang, Bowen Cheng,Fei Cao School of Software and Microelectronics, Peking University, Beijing, China {yifeiyangx, Abstract Because of the rich and varied resources in internet and social entertainment communities, more and more people or groups are spending their time on discovering the social relationship between others, or finding the core figures for business, political or security reason. In this paper, we build up an SNM solution by analyzing users static attribute and interaction of BBS to mine what kinds of attitudes they show to others and what kind of relationship between them using data mining technology, to establish users social network, and to find out the key figures in networks. Index Terms Social Network, Data Mining, Core Figure, Six-degree Separation I. INTRODUCTION The rapid development of information technology makes the Internet play an increasingly important role in our lives. Because of its rich and varied resources, the Internet is gradually infiltrated into every aspect of our lives. More and more people would like to spend their time on the Internet especially on some kinds of large social entertainment community. And the more they communicate with each other, the more likely the relationship between them is getting closer. When one organizational leader is asked to interpret how he/she get the key information that lead to the success of one project, it is not only related to his/her knowledge, but also he/she can effectively find useful information though all of these factors are related to his/her own experience. Information acknowledgement has made an important but often overlooked part is how a person through his relationships to obtain necessary information. A present research shows that people tend to seek help from friends or colleagues 5 times more than other information resources such as databases or documents. What is more, Internets play a very important role in the procedure of dissemination of knowledge. Social network analysis is a method of inquiry that focuses on relationships between subjects such as individuals, organizations or nation states. However, it has also been applied to analysis relationships between objects as diverse as the Internet, scientific papers, organisms, and molecules. Social network analysis has emerged as a set of methods for the analysis of social structures, methods which are specifically geared towards an investigation of the relational aspects of these structures. The use of these methods, therefore, depends on the availability of relational rather than attribute data. Social network analysis is a method of inquiry that focuses on relationships between subjects such as individuals, organizations or nation states[1][2][3]. If we already had an existing exchange platform for organizations to analyze social Internet to understand the internal and external association of an organization, it will be particularly helpful in enhancing the collaboration, innovating knowledge and disseminating knowledge. Social network analysis is focused on uncovering the patterning of people's interaction. Network analysis is based on the intuitive notion that these patterns are important features of the lives of the individuals who display them. Network analysts believe that how an individual lives depends in large part on how that individual is tied into the larger web of social connections. Many believe, moreover, that the success or failure of societies and organizations often depends on the patterning of their internal structure. From the outset, the network approach to the study of behavior has involved two commitments: (1) it is guided by formal theory organized in mathematical terms, and (2) it is grounded in the systematic analysis of empirical data. It was not until the 1970s, therefore--when modern discrete combinatorics (particularly graph theory) experienced rapid development and relatively powerful computers became readily available--that the study of social networks really began to take off as an interdisciplinary specialty. Since then its growth has been rapid. It has found important applications in organizational behavior, inter-organizational relations, the spread of contagious diseases, mental health, social support, the diffusion of information and animal social organization.[4] Therefore, our goal is to build a social network mining system based on the BBS community. In this system, we will extract personal information and the interaction information between them, doing some data analysis processing, judging the relationship between people and establishing organizations in Internets, to get the organization's internal and external features.
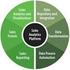
2 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE In this paper, we analyze every useful message during their interaction through BBS to mine what kinds of attitudes they show to others, and also get some personal information using data mining technology, to establish the social network, to find out the key figures who are the more active or important BBS users than others. We do some research works through the networks and these key figures. Section 1 is an introduction, Section 2 gives out the solution overview of SNM, Section 3 described the algorithm implementation of SNM, Section 4 described implementation and experiments, Section 5 described the future work, and Section 6 is the conclusion. II.SOLUTION OVERVIEW OF SNM In recent years, the SNS websites and social network research has advanced significantly, but there still many difficult in mining the BBS, especially using for the BBS evaluation system. In tradition evaluation system, to find out the key figures of the website, to discover the social network, to make a decision who will be the best person to publish an advertisement or notes, to make a choice whether to invested the community, we can only used the statistics from network administrator. Just like: new posts (daily/monthly/yearly), new repliers (daily/monthly/ yearly), person liveness, reputation, it s very hard to find out the relationship between them, and mostly incorrect. In order to have a deeper understanding about the BBS user, we build up an SNM system. In this solution, we using data mining algorithm on social network to analyze the relationship between users and establish the social network of the BBS for deeper analysis. To address these concerns, we adopted the solution illustrated in Fig. 1. Firstly, the raw information from BBS are crawled by the web crawler component and gathered into temp files. Secondly, the pre-treatment component process the raw information from the temp files, which are saved into database after pre-converted. Thirdly, the analysis component analyzes the users static attribute and interaction between users, and the relationship score will be given. Fourthly, the networks built component create the social networks for the giving groups, members or crowds. Fifthly, the find out core figures component is used to find out the core figures from the social network built. III. ALGORITHM IMPLEMENTATION of SNM A. Construction of Data Sources Construction of data sources include the following processes: 1) Downloading pages: a Cookie supported system should be deployed, which will simulate the steps to enter the BBS system. And then All the Cookies should be saved. For each HTTP request, Cookie information should be added in, thus we can download the response pages, including personnel information pages and pages on the theme. 2) Mapping data into XHTML: we can use the class library which performs the same functions. 3) Finding the key data: whether in Web pages or the source of XHTML view, most information is the information that we do not care. In this process, we need to filter the unrelated data. 4) Mapping data into XML. Our next task is to find a particular region in the XML tree, thus we can get the related data without the need to care about external information. For a more complex extraction situation, we may need to find several examples of these regions in a single page. 5) Merging results and processing data: the system will read the node in a XML tree and convert it into required format, and then it will insert the converted data into the corresponding tables in database. Pretreatment Fig. 1. The SNM architecture Database Component B. Analyze the Static Attribute Information of Personnel Personnel information including the following: UID, registration date, last visit, final page visiting, on-line time, nickname, user group, posting level, reading permission, integration, prestige, money, posts, average posts per day, cream posts, sex, hometown, birthday. In this process, we try to find some available rue to derive the similarity between two people directly. However, the result will be influenced by a particular platform. We use classified technology according to the messages we already have, refine some useful rules, and then according to the refined rules, following algorithms to analyze the similarity between one person and others: 1) Mining-frequency. 2) Impact factor : Assume the personnel information of people A and B contains m items, each score of item similar is s1, s2, s3 sm, and each impact factor of
3 300 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE 2009 relationship is p1, p2, p3 pm, so the total similar score of people A and B is: The more similar two persons information are, the more probability they will become friends. And based on the information mentioned above, we will analyze the similarity between two persons as a potential factor of judging the relationship between two persons. C. Analyze the Members Interaction Content information may include the following: the author, publish time, theme and content. If two persons frequently interact with each other, the level of their friendly or hostile may increase. We analyze each word of posts at the same theme according to their response to judge the positive or negative meaning. It will become an important factor to determine the relationship between them. As for a theme, it is define as a word vector: Theme ::= [word [,word] 0..* ] As for a text block of content, it is segmented into Chinese words, and also defined as a word vector: Content ::= [word[,word] 0..* ] For each word, it is defined as a positive, negative or others by HowNet[5] semantic dictionary. We select a theme as beginning, with word vector matching algorithm, analyze all words of each sentence to determine a person's attitude on the subject (positive or negative), thus we will get to know the friendly or hostile attitude between two persons on the theme. Finally after integrating all topics, we can determine the degree of their relationship in friendly or hostile way. D. Establish the network organizations In order to find network organizations for BBS data, we have defined a set of organizational rules for a network organization at first. The organizational rules have been stored into a system database for advanced using and the rules can be adjusted for specific targets. In order to find the organization's more internal and external features, we need to establish a network of organizations, for further analysis of the object. Combining the first two parts results and accordance with the rules established in advance, the relationship between any two persons could be figured out. Then we can set a threshold of intimacy and choose a certain target as a start point, and groups the points who s intimate level with is more than the threshold, which will form a social network with "weight". The other nodes can be done followed by this way to expand the network. In order to prevent the continuous network expansion, the threshold could be auto-adjusted based on the network si The network organizations established were showed in a social network graph. A graph is composed of nodes (or users or points) connected by edges (or relations or ties). A graph may represent a single type of relations among the users (simplex), or more than one kind of relation (multiplex) E. Find out the Core Figure The core figure may be the most energy or respected members in the organization, his activity may have a significant impact to organization [6]. For the constructed "weight" network, we can calculate the shortest path between the nodes easily. According to the six-degree separation theorem, SPLINE algorithm and center-based for mining network sub-groups, we can find out who is the core figure. The six-degree separation theorem describes the nature of network connectivity: The linkers between any two people in any society, only four intermediaries are needed. In other words, any two people on the earth want to know each other, and only jumping 5 steps is enough, also known as the "Tianya 5 neighbor". The theorem came out under the ideal assumption conditions, also the researchers made a large number of social experiments to prove the theorem. Therefore, for an effective society, there will be not more than four intermediaries to avoid the low efficiency communication, and the shortest path algorithm SPLINE (Shortest Path based on Link weight) was based on the six-degree separation theorem. The point is: 1) The frequency nodes via will be set as the weight value between any two nodes; 2) Using Dijistra algorithm to find the shortest path between any two nodes; 3) Pruning, retain the shortest paths which are less than 6. Basis on SPLINE algorithm, the key points of KMM algorithm to mining the core figure in network groups are: 1) Establish the network while according to the internal communications; 2) The level of clustering approach to mining organization; 3) Using SPLINE and center algorithm to digging in the core figure; 4) Verification of the validity of the algorithm through the experiment, the accurately forecast core rate is 91.2%. F. The Impact to Organization while Core Figures Mobilize The core figures mobilization will have an impact on the organizational structure. Analysis the structure s change while remove a core figure from the organization; analysis the difference while exchange a central figure location between an organization and another; to find if a core figure from other organization join in, whether the two organizations will be merger into one or something else changed?
4 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE Assume that the core figures mobilize, observed the changes in the organizational structure. 1) Removed a core figure from the organization; and then re-build network, find out the core figure, analyze the change of overall numbers and the core figure 2) Exchange a central figure location between an organization and another; retaining the comment relationship between the two people and delete the uncomment relationship or use of replacement threshold; and then re-build network, find out the core figure, analyze the change of overall numbers and the core figure 3) A core figure from other organization joined in; establish the link between other organizations and the core figures, the intimate level is the threshold for larger network (usually more); then re-build network below the threshold from a smaller network (usually is small), find out the core figure, analyze the change of overall numbers and the core figure. IV. IMPLEMENTATION AND EXPERIMENTS A. The Hardware Environment We use a personal PC as the system server, which has the following configurations: Intel Dual Core Processor 2.66GHz, 2G Memory, 160GB*SATA Hard disk. The computers are connected to Internet by local network in campus. The system adopted client server style. Client also run at PC desktop computer. B. The Software Environment In the software environment, the OS is Microsoft Windows Vista, database system is Microsoft SQL Server. Use the C # programming language under.net Platform to build a social network mining system based on the BBS community. C. Major Software Components The first software component is the web crawler. The web crawler browses the BBS in our campus in an automated manner, providing up-to-date BBS data. The web crawler are used to create a copy of all the visited pages for later processing and social network analyzing, and used to gather specific types of information from BBS for further social network analyzing. The second component is the pretreatment component. The role of the pretreatment module of our social network mining system is to analyze the structure of the HTML page and to find fields that are relevant to the domain theme. The proper (semantic) way to give the label of a HTML field is the use of the HTML element label, whose attribute must correspond to the name attribute of HTML field. Unfortunately, this tag maybe wrongly used by Web developers and we thus have to resort to other contextual information, such as the name or id attribute, or the text appearing before the field (in the source code). An alternative is to use the graphical lay out of the HTML, and rules indicating where the label of a field most often lies relative to the field. Structural analysis of an HTML page is as following steps : Input: URL of a HTML page. Output: List of fields with theme annotations. (a) Retrieve the Web page at the given URL from database. (b) For each HTML field: (i) Gather all text of the textual content : name and id attributes, content of the corresponding label element, text appearing in the field. (ii) Segment the text into Chinese words. (iii) Remove stop-words. (iv) Check whether any resulting word matches a theme related words as given by HowNet[4]. (v) Annotate the fields with matching themes, with the associated confidence as the probability that this field represents this theme. The Third component is the analysis component, which analyze the users static attributes and interaction between others, and calculate the relationship score between users of BBS. The users static attributes are extracted from the text data processed by the pretreatment component. The theme word vectors and content word vectors are also created from the data processed by the pretreatment component. Then, we use vector matching algorithm to calculate the relationship score between users of BBS, and calculate a user's attitude score on the theme. Relationship Score = word of user1 word of user2 Attitude Score on the theme = word of user1 word of theme The fourth component is the network built component, which create the social networks for the giving groups, members or crowds. We use the theme word vectors, users content word vectors, users static attributes, group attributes and organizational rules to find groups, members of a groups, and members relations, then social networks are to be established. The fifth component is the component for finding out core figures, which is used to find out the core figures from the social network built. By the networks established in the network built component, the core figures are to be found with Graphic Analysis Algorithms[3]. An prototype of social network mining system have been developed and built. The five software component can run on Windows Vista correctly. The experiment results obtained by the prototype system are described and discussed in the following Section D. Social network analysis can be done by the social network mining system developed. The social network
5 302 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE 2009 perspective emphasizes multiple levels of analysis. Differences among users are traced to the constraints and opportunities that arise from how they are embedded in networks; the structure and behavior of networks grounded in, and enacted by local interactions among users. D. Experiment Results The test data was collected from BBS website in School of Software and Microelectronics, Peking University. We have collected 5964 user information HTML pages and 5861 communication information pages from the campus BBS web site. After extracted the users attributes, parsed analyzed the HTML pages, information of 5964 users and posts field have been obtained. There are 6 groups which has more than 3 persons mining from the BBS data, whose core figures have been found. The fundamental data structure is one that leads us to compare how users are similar or dissimilar to each other across attributes (by comparing rows). Or, perhaps more commonly, we examine how variables are similar or dissimilar to each other in their distributions across users (by comparing or correlating columns). "Network" data (in their purest form) consist of a square array of measurements. The rows of the array are the cases, or subjects, or observations. The columns of the array are -- and note the key difference from conventional data -- the same set of cases, subjects, or observations. In each cell of the array describes a relationship between the users. We emphasized that the social network perspective leads us to focus our attention on the relations between users, more than on the attributes of users. This approach often results in data that have a different "structure" in which both rows and columns refer to the same users, and the cells report information on one variable that describes variation (in the case of the example below, simple presence of absence of a tie) in the relations between each pair of users. Fig.2 is User Information pages parsed results. There are eight fields in the table including user id, user name, user last access date, user last post date, access pages etc. These user attributes information were extracted from 5964 user information HTML pages users were extracted. Fig.3 is HTML pages parsed results. There are eight fields in the table including page id, title, content, tid, uid and date published etc. These text interaction information between users were extracted from 5861 communication information pages on our campus BBS website. The menu item in Fig.3 high lighted is Web Parser, which means the posts information are to be analyzed and extracted from communication information HTML pages obtained from BBS website posts were extracted. Your goal is to simulate the usual appearance of papers in a Journal of the Academy Publisher. We are requesting that you follow these guidelines as closely as possible Fig. 2 User Information Parsed Result Fig. 3 HTML Pages Parsed Result These materials aim to help beginners to appreciate and use social network analysis in their own work and pursue further developments on their own. With the social network mining system we developed, after users personal information and the interaction information between them extracted from HTML pages on BBS website, we can do some data analysis, judge the relationship between people, establish organizations in Internets, and get the organization's internal and external features. Fig.4 to Fig.7 are some analysis results mined from BBS HTML pages. Full network methods[3] require that we collect information about each user's ties with all other users. In essence, this approach is taking a census of ties in a population of users -- rather than a sample. Full network data allows for very powerful descriptions and analyses of social structures. Unfortunately, full network data can also be very expensive and difficult to collect. Obtaining data from every member of a population, and having every member rank or rate every other member can be very challenging tasks in any but the smallest groups.
6 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE In this paper, we use Full network methods in social network analysis. Fig.4 shows the analysis results of relations between users. There are three fields in the table including user1 name, user2 name and relation between user1 and user2. The value in the relation column is 1, means the user1 and user2 has relation in this row relations information between users were obtained. The menu item in Fig.4 high lighted is Communication Analysis, which means the communication relations between users are to be analyzed and extracted from communication information HTML pages obtained from BBS website. If one user answered another user s post, there is a relation between the two users. Fig.5 shows the analysis results of groups on BBS website. There are two fields in the table including user name and Group ID, named gid. There are six group information showed in Fig.5. A record in a row in the table means the user belongs to the group with the gid. The menu item in Fig.5 high lighted is Social Network Creator, which means the relations between users are to be analyzed and group information to be mined from HTML pages obtained from BBS website. Fig.6 shows the analysis results of Key Figures of each group. There are two fields in the table including user name and Group ID, named gid. A record in a row in the table means the user belongs to the group with the gid. Fig.7 shows the graphic results of networks created. In this result, we find 张 莉 ( Zhang Li ) is the core figure, who has the most ties (relations) with others. This figure was created by using the Graphs tool that is built in our social network mining system. A visual inspection of the diagram with the highlighted node color is much more informative about core figure. There are only a part of members in a group showed in Fig.7. If all member of a group showed in Fig.7, the density of lines between group members will be very high. When all member must be showed in a graph, a more efficient plotting algorithm should be adopted. Fig. 5 Group Information Fig.6 Core Figures Found out Fig.4 Analysis Results of Relations Between Users Fig.7 Core Figures Finding out
7 304 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE 2009 The most widely used software for social network analysis is UCINET[7] and it is now in its sixth version. It is available for a small license fee for academic use from Analytic Technologies. We will do more useful analysis with UCINET. Fig.8 Attribute Analysis Results Fig.8 shows the user attribute analysis results of networks. The attributes include user register date, access pages, online time, nickname, user group, permission, mark, prestige, articles, elite, gender, home place, and birthday. There are two users attributes showed in Fig.7. relation can be predicted by users information. Differences among individuals in how connected they are can be extremely consequential for understanding their attributes and behavior. More connections often mean that individuals are exposed to more, and more diverse, information. Highly connected individuals may be more influential, and may be more influenced by others. Ⅴ. FUTURE WORK Network analysis (or social network analysis) is a set of mathematical methods used in social psychology, sociology, ethology, and anthropology. Network analysis assumes that the way the members of a group can communicate to each other affect some important features of that group (efficiency when performing a task, moral satisfaction, leadership). Network analysis makes use of mathematical tools and concepts that belong to graph theory. A network models a communication group. In many network studies, all of the ties of a given type among all of the selected nodes are studied -- that is, a census is conducted. But, sometimes different approaches are used (because they are less expensive, or because of a need to generalize) that sample ties. There is also a second kind of sampling of ties that always occurs in network data. We have obtained some useful results on social network analysis for BBS data mining. In the future, we will increase the scale of the networks and do more kinds of analysis by social network mining. We also want to add more semantic information in social network analyzing to improve analysis efficiency. We will do more dynamic analysis of social networks. Ⅵ. CONCLUSION In this paper, we build up an SNM solution by analyzing users static attribute and interaction of BBS to mine what kinds of attitudes they show to others and what kind of relationship between them using data mining technology, to establish users social network, and to find out the key figures in networks. We have described the solution to discover the social network, users relationship, key figures and impaction to the organization on BBS website. Our key idea and contribution is to exploit algorithm and regularities to implementation a solution to discover the potential relationship and social network. The solution and algorithm can be applied to any SNS system that conforms to the implementation conventions, to yield a network in that style. In this paper, our test data are from Internet and were collected automatically. It is possible to build a large social network. The social network analyzing and mining tools presented in this paper are useful for organizations to analyze social network to understand the internal and external association of an organization, it will be particularly helpful in enhancing the collaboration, innovating knowledge and disseminating knowledge. REFERENCES [1] Stanley Wasserman, Katherine Faust. Social Network Analysis: Methods and Applications (Structural Analysis in the Social Sciences). Cambridge: Cambridge University Press, [2] Scott, John. Social Network Analysis : A Handbook. Newbury Park, CA : Sage Publications [3] Hanneman, Robert A. and Mark Riddle. Introduction to social network methods. Riverside, CA: University of California, Riverside [4] Lin Freeman: na_inf.html [5] HowNet Knowledge Database. [6] Tang Changjie, Liu Wei, Wen Fenlian, Qiao Shaojie. Three probes into the social network analysis and consortium information mining mining the structure, core and communication behavior of virtual consortium. Journal of Computer Applications, Vol. 26, No. 9, (in Chinese). [7] UCINET, Network Analysis program. Available through: Lixin Zhou, obtained Ph.D. in computer science from Zhejiang University, China in He is currently working as an associate professor in Peking University. His areas of
8 JOURNAL OF NETWORKS, VOL. 4, NO. 4, JUNE interests include data mining, information retrieval and natural language processing. Jichang Ding, obtained B.E. degree in Software Engineering from Huazhong University of Science and Technology, China in He is now studying Master degree in Peking University. His research areas include data mining, parallel computing and software engineering. Yi Wang, obtained B.E. degree in Software Engineering from Huazhong University of Science and Technology, China in She is now studying Master degree in Peking University. Her major field of study are data mining. Bowen Cheng, is now a graduate student in Peking University. He earned his bachelor's degree in Software Engineering in Huazhong University of Science and Technology, China in His major field of study is software engineering and data mining. Fei Cao, obtained B.E. degree in information management from Beijing University of Posts & Telecommunications in He is currently studying in Peking University. His areas of interests include data mining, data modeling and data analysis.
So today we shall continue our discussion on the search engines and web crawlers. (Refer Slide Time: 01:02)
 Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #39 Search Engines and Web Crawler :: Part 2 So today we
Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #39 Search Engines and Web Crawler :: Part 2 So today we
Understanding Web personalization with Web Usage Mining and its Application: Recommender System
 Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
Web Database Integration
 Web Database Integration Wei Liu School of Information Renmin University of China Beijing, 100872, China gue2@ruc.edu.cn Xiaofeng Meng School of Information Renmin University of China Beijing, 100872,
Web Database Integration Wei Liu School of Information Renmin University of China Beijing, 100872, China gue2@ruc.edu.cn Xiaofeng Meng School of Information Renmin University of China Beijing, 100872,
Blog Post Extraction Using Title Finding
 Blog Post Extraction Using Title Finding Linhai Song 1, 2, Xueqi Cheng 1, Yan Guo 1, Bo Wu 1, 2, Yu Wang 1, 2 1 Institute of Computing Technology, Chinese Academy of Sciences, Beijing 2 Graduate School
Blog Post Extraction Using Title Finding Linhai Song 1, 2, Xueqi Cheng 1, Yan Guo 1, Bo Wu 1, 2, Yu Wang 1, 2 1 Institute of Computing Technology, Chinese Academy of Sciences, Beijing 2 Graduate School
Financial Trading System using Combination of Textual and Numerical Data
 Financial Trading System using Combination of Textual and Numerical Data Shital N. Dange Computer Science Department, Walchand Institute of Rajesh V. Argiddi Assistant Prof. Computer Science Department,
Financial Trading System using Combination of Textual and Numerical Data Shital N. Dange Computer Science Department, Walchand Institute of Rajesh V. Argiddi Assistant Prof. Computer Science Department,
Online Computer Science Degree Programs. Bachelor s and Associate s Degree Programs for Computer Science
 Online Computer Science Degree Programs EDIT Online computer science degree programs are typically offered as blended programs, due to the internship requirements for this field. Blended programs will
Online Computer Science Degree Programs EDIT Online computer science degree programs are typically offered as blended programs, due to the internship requirements for this field. Blended programs will
How to Design and Create Your Own Custom Ext Rep
 Combinatorial Block Designs 2009-04-15 Outline Project Intro External Representation Design Database System Deployment System Overview Conclusions 1. Since the project is a specific application in Combinatorial
Combinatorial Block Designs 2009-04-15 Outline Project Intro External Representation Design Database System Deployment System Overview Conclusions 1. Since the project is a specific application in Combinatorial
FEAWEB ASP Issue: 1.0 Stakeholder Needs Issue Date: 03/29/2000. 04/07/2000 1.0 Initial Description Marco Bittencourt
 )($:(%$63 6WDNHKROGHU1HHGV,VVXH 5HYLVLRQ+LVWRU\ 'DWH,VVXH 'HVFULSWLRQ $XWKRU 04/07/2000 1.0 Initial Description Marco Bittencourt &RQILGHQWLDO DPM-FEM-UNICAMP, 2000 Page 2 7DEOHRI&RQWHQWV 1. Objectives
)($:(%$63 6WDNHKROGHU1HHGV,VVXH 5HYLVLRQ+LVWRU\ 'DWH,VVXH 'HVFULSWLRQ $XWKRU 04/07/2000 1.0 Initial Description Marco Bittencourt &RQILGHQWLDO DPM-FEM-UNICAMP, 2000 Page 2 7DEOHRI&RQWHQWV 1. Objectives
Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2
 Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2 Department of Computer Engineering, YMCA University of Science & Technology, Faridabad,
Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2 Department of Computer Engineering, YMCA University of Science & Technology, Faridabad,
The Scientific Data Mining Process
 Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
CHAPTER 1 INTRODUCTION
 1 CHAPTER 1 INTRODUCTION Exploration is a process of discovery. In the database exploration process, an analyst executes a sequence of transformations over a collection of data structures to discover useful
1 CHAPTER 1 INTRODUCTION Exploration is a process of discovery. In the database exploration process, an analyst executes a sequence of transformations over a collection of data structures to discover useful
Tutorial for proteome data analysis using the Perseus software platform
 Tutorial for proteome data analysis using the Perseus software platform Laboratory of Mass Spectrometry, LNBio, CNPEM Tutorial version 1.0, January 2014. Note: This tutorial was written based on the information
Tutorial for proteome data analysis using the Perseus software platform Laboratory of Mass Spectrometry, LNBio, CNPEM Tutorial version 1.0, January 2014. Note: This tutorial was written based on the information
not possible or was possible at a high cost for collecting the data.
 Data Mining and Knowledge Discovery Generating knowledge from data Knowledge Discovery Data Mining White Paper Organizations collect a vast amount of data in the process of carrying out their day-to-day
Data Mining and Knowledge Discovery Generating knowledge from data Knowledge Discovery Data Mining White Paper Organizations collect a vast amount of data in the process of carrying out their day-to-day
Visualizing e-government Portal and Its Performance in WEBVS
 Visualizing e-government Portal and Its Performance in WEBVS Ho Si Meng, Simon Fong Department of Computer and Information Science University of Macau, Macau SAR ccfong@umac.mo Abstract An e-government
Visualizing e-government Portal and Its Performance in WEBVS Ho Si Meng, Simon Fong Department of Computer and Information Science University of Macau, Macau SAR ccfong@umac.mo Abstract An e-government
On the Design of an Advanced Web-Based System for Supporting Thesis Research Process and Knowledge Sharing
 Yan, Y., Han, X., Yang, J., & Zhou, Q. (2012). On the design of an advanced web-based system for supporting thesis research process and knowledge sharing. Journal of Educational Technology Development
Yan, Y., Han, X., Yang, J., & Zhou, Q. (2012). On the design of an advanced web-based system for supporting thesis research process and knowledge sharing. Journal of Educational Technology Development
Zoomer: An Automated Web Application Change Localization Tool
 Journal of Communication and Computer 9 (2012) 913-919 D DAVID PUBLISHING Zoomer: An Automated Web Application Change Localization Tool Wenhua Wang 1 and Yu Lei 2 1. Marin Software Company, San Francisco,
Journal of Communication and Computer 9 (2012) 913-919 D DAVID PUBLISHING Zoomer: An Automated Web Application Change Localization Tool Wenhua Wang 1 and Yu Lei 2 1. Marin Software Company, San Francisco,
Data Mining Solutions for the Business Environment
 Database Systems Journal vol. IV, no. 4/2013 21 Data Mining Solutions for the Business Environment Ruxandra PETRE University of Economic Studies, Bucharest, Romania ruxandra_stefania.petre@yahoo.com Over
Database Systems Journal vol. IV, no. 4/2013 21 Data Mining Solutions for the Business Environment Ruxandra PETRE University of Economic Studies, Bucharest, Romania ruxandra_stefania.petre@yahoo.com Over
Search Result Optimization using Annotators
 Search Result Optimization using Annotators Vishal A. Kamble 1, Amit B. Chougule 2 1 Department of Computer Science and Engineering, D Y Patil College of engineering, Kolhapur, Maharashtra, India 2 Professor,
Search Result Optimization using Annotators Vishal A. Kamble 1, Amit B. Chougule 2 1 Department of Computer Science and Engineering, D Y Patil College of engineering, Kolhapur, Maharashtra, India 2 Professor,
Search and Information Retrieval
 Search and Information Retrieval Search on the Web 1 is a daily activity for many people throughout the world Search and communication are most popular uses of the computer Applications involving search
Search and Information Retrieval Search on the Web 1 is a daily activity for many people throughout the world Search and communication are most popular uses of the computer Applications involving search
SUGI 29 Systems Architecture. Paper 223-29
 Paper 223-29 SAS Add-In for Microsoft Office Leveraging SAS Throughout the Organization from Microsoft Office Jennifer Clegg, SAS Institute Inc., Cary, NC Stephen McDaniel, SAS Institute Inc., Cary, NC
Paper 223-29 SAS Add-In for Microsoft Office Leveraging SAS Throughout the Organization from Microsoft Office Jennifer Clegg, SAS Institute Inc., Cary, NC Stephen McDaniel, SAS Institute Inc., Cary, NC
Visualization Method of Trajectory Data Based on GML, KML
 Visualization Method of Trajectory Data Based on GML, KML Junhuai Li, Jinqin Wang, Lei Yu, Rui Qi, and Jing Zhang School of Computer Science & Engineering, Xi'an University of Technology, Xi'an 710048,
Visualization Method of Trajectory Data Based on GML, KML Junhuai Li, Jinqin Wang, Lei Yu, Rui Qi, and Jing Zhang School of Computer Science & Engineering, Xi'an University of Technology, Xi'an 710048,
131-1. Adding New Level in KDD to Make the Web Usage Mining More Efficient. Abstract. 1. Introduction [1]. 1/10
![131-1. Adding New Level in KDD to Make the Web Usage Mining More Efficient. Abstract. 1. Introduction [1]. 1/10 131-1. Adding New Level in KDD to Make the Web Usage Mining More Efficient. Abstract. 1. Introduction [1]. 1/10](/thumbs/25/4963058.jpg) 1/10 131-1 Adding New Level in KDD to Make the Web Usage Mining More Efficient Mohammad Ala a AL_Hamami PHD Student, Lecturer m_ah_1@yahoocom Soukaena Hassan Hashem PHD Student, Lecturer soukaena_hassan@yahoocom
1/10 131-1 Adding New Level in KDD to Make the Web Usage Mining More Efficient Mohammad Ala a AL_Hamami PHD Student, Lecturer m_ah_1@yahoocom Soukaena Hassan Hashem PHD Student, Lecturer soukaena_hassan@yahoocom
In this presentation, you will be introduced to data mining and the relationship with meaningful use.
 In this presentation, you will be introduced to data mining and the relationship with meaningful use. Data mining refers to the art and science of intelligent data analysis. It is the application of machine
In this presentation, you will be introduced to data mining and the relationship with meaningful use. Data mining refers to the art and science of intelligent data analysis. It is the application of machine
BIG DATA IN THE CLOUD : CHALLENGES AND OPPORTUNITIES MARY- JANE SULE & PROF. MAOZHEN LI BRUNEL UNIVERSITY, LONDON
 BIG DATA IN THE CLOUD : CHALLENGES AND OPPORTUNITIES MARY- JANE SULE & PROF. MAOZHEN LI BRUNEL UNIVERSITY, LONDON Overview * Introduction * Multiple faces of Big Data * Challenges of Big Data * Cloud Computing
BIG DATA IN THE CLOUD : CHALLENGES AND OPPORTUNITIES MARY- JANE SULE & PROF. MAOZHEN LI BRUNEL UNIVERSITY, LONDON Overview * Introduction * Multiple faces of Big Data * Challenges of Big Data * Cloud Computing
THE ROLE OF SOCIOGRAMS IN SOCIAL NETWORK ANALYSIS. Maryann Durland Ph.D. EERS Conference 2012 Monday April 20, 10:30-12:00
 THE ROLE OF SOCIOGRAMS IN SOCIAL NETWORK ANALYSIS Maryann Durland Ph.D. EERS Conference 2012 Monday April 20, 10:30-12:00 FORMAT OF PRESENTATION Part I SNA overview 10 minutes Part II Sociograms Example
THE ROLE OF SOCIOGRAMS IN SOCIAL NETWORK ANALYSIS Maryann Durland Ph.D. EERS Conference 2012 Monday April 20, 10:30-12:00 FORMAT OF PRESENTATION Part I SNA overview 10 minutes Part II Sociograms Example
Research on Application of Web Log Analysis Method in Agriculture Website Improvement
 Research on Application of Web Log Analysis Method in Agriculture Website Improvement Jian Wang 1 ( 1 Agricultural information institute of CAAS, Beijing 100081, China) wangjian@caas.net.cn Abstract :
Research on Application of Web Log Analysis Method in Agriculture Website Improvement Jian Wang 1 ( 1 Agricultural information institute of CAAS, Beijing 100081, China) wangjian@caas.net.cn Abstract :
KEYWORD SEARCH IN RELATIONAL DATABASES
 KEYWORD SEARCH IN RELATIONAL DATABASES N.Divya Bharathi 1 1 PG Scholar, Department of Computer Science and Engineering, ABSTRACT Adhiyamaan College of Engineering, Hosur, (India). Data mining refers to
KEYWORD SEARCH IN RELATIONAL DATABASES N.Divya Bharathi 1 1 PG Scholar, Department of Computer Science and Engineering, ABSTRACT Adhiyamaan College of Engineering, Hosur, (India). Data mining refers to
CHAPTER 4 PERFORMANCE ANALYSIS OF CDN IN ACADEMICS
 CHAPTER 4 PERFORMANCE ANALYSIS OF CDN IN ACADEMICS The web content providers sharing the content over the Internet during the past did not bother about the users, especially in terms of response time,
CHAPTER 4 PERFORMANCE ANALYSIS OF CDN IN ACADEMICS The web content providers sharing the content over the Internet during the past did not bother about the users, especially in terms of response time,
A Comparative Approach to Search Engine Ranking Strategies
 26 A Comparative Approach to Search Engine Ranking Strategies Dharminder Singh 1, Ashwani Sethi 2 Guru Gobind Singh Collage of Engineering & Technology Guru Kashi University Talwandi Sabo, Bathinda, Punjab
26 A Comparative Approach to Search Engine Ranking Strategies Dharminder Singh 1, Ashwani Sethi 2 Guru Gobind Singh Collage of Engineering & Technology Guru Kashi University Talwandi Sabo, Bathinda, Punjab
Network Attack Platform
 Design and Implementation of a Network Attack Platform Based on Plug-in Technology Li Gen, Wang Bailing *, Liu Yang, Bai Xuefeng and Yuan Xinling Department of Computer Science & Technology Harbin Institute
Design and Implementation of a Network Attack Platform Based on Plug-in Technology Li Gen, Wang Bailing *, Liu Yang, Bai Xuefeng and Yuan Xinling Department of Computer Science & Technology Harbin Institute
A Knowledge Management Framework Using Business Intelligence Solutions
 www.ijcsi.org 102 A Knowledge Management Framework Using Business Intelligence Solutions Marwa Gadu 1 and Prof. Dr. Nashaat El-Khameesy 2 1 Computer and Information Systems Department, Sadat Academy For
www.ijcsi.org 102 A Knowledge Management Framework Using Business Intelligence Solutions Marwa Gadu 1 and Prof. Dr. Nashaat El-Khameesy 2 1 Computer and Information Systems Department, Sadat Academy For
Make search become the internal function of Internet
 Make search become the internal function of Internet Wang Liang 1, Guo Yi-Ping 2, Fang Ming 3 1, 3 (Department of Control Science and Control Engineer, Huazhong University of Science and Technology, WuHan,
Make search become the internal function of Internet Wang Liang 1, Guo Yi-Ping 2, Fang Ming 3 1, 3 (Department of Control Science and Control Engineer, Huazhong University of Science and Technology, WuHan,
Traffic Prediction in Wireless Mesh Networks Using Process Mining Algorithms
 Traffic Prediction in Wireless Mesh Networks Using Process Mining Algorithms Kirill Krinkin Open Source and Linux lab Saint Petersburg, Russia kirill.krinkin@fruct.org Eugene Kalishenko Saint Petersburg
Traffic Prediction in Wireless Mesh Networks Using Process Mining Algorithms Kirill Krinkin Open Source and Linux lab Saint Petersburg, Russia kirill.krinkin@fruct.org Eugene Kalishenko Saint Petersburg
(Refer Slide Time: 01:52)
 Software Engineering Prof. N. L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture - 2 Introduction to Software Engineering Challenges, Process Models etc (Part 2) This
Software Engineering Prof. N. L. Sarda Computer Science & Engineering Indian Institute of Technology, Bombay Lecture - 2 Introduction to Software Engineering Challenges, Process Models etc (Part 2) This
A case study of social network analysis of the discussion area of a virtual learning platform
 World Transactions on Engineering and Technology Education Vol.12, No.3, 2014 2014 WIETE A case study of social network analysis of the discussion area of a virtual learning platform Meimei Wu & Xinmin
World Transactions on Engineering and Technology Education Vol.12, No.3, 2014 2014 WIETE A case study of social network analysis of the discussion area of a virtual learning platform Meimei Wu & Xinmin
Supporting Knowledge Collaboration Using Social Networks in a Large-Scale Online Community of Software Development Projects
 Supporting Knowledge Collaboration Using Social Networks in a Large-Scale Online Community of Software Development Projects Masao Ohira Tetsuya Ohoka Takeshi Kakimoto Naoki Ohsugi Ken-ichi Matsumoto Graduate
Supporting Knowledge Collaboration Using Social Networks in a Large-Scale Online Community of Software Development Projects Masao Ohira Tetsuya Ohoka Takeshi Kakimoto Naoki Ohsugi Ken-ichi Matsumoto Graduate
The Architectural Design of FRUIT: A Family of Retargetable User Interface Tools
 The Architectural Design of : A Family of Retargetable User Interface Tools Yi Liu Computer Science University of Mississippi University, MS 38677 H. Conrad Cunningham Computer Science University of Mississippi
The Architectural Design of : A Family of Retargetable User Interface Tools Yi Liu Computer Science University of Mississippi University, MS 38677 H. Conrad Cunningham Computer Science University of Mississippi
PSG College of Technology, Coimbatore-641 004 Department of Computer & Information Sciences BSc (CT) G1 & G2 Sixth Semester PROJECT DETAILS.
 PSG College of Technology, Coimbatore-641 004 Department of Computer & Information Sciences BSc (CT) G1 & G2 Sixth Semester PROJECT DETAILS Project Project Title Area of Abstract No Specialization 1. Software
PSG College of Technology, Coimbatore-641 004 Department of Computer & Information Sciences BSc (CT) G1 & G2 Sixth Semester PROJECT DETAILS Project Project Title Area of Abstract No Specialization 1. Software
Visualizing Relationships and Connections in Complex Data Using Network Diagrams in SAS Visual Analytics
 Paper 3323-2015 Visualizing Relationships and Connections in Complex Data Using Network Diagrams in SAS Visual Analytics ABSTRACT Stephen Overton, Ben Zenick, Zencos Consulting Network diagrams in SAS
Paper 3323-2015 Visualizing Relationships and Connections in Complex Data Using Network Diagrams in SAS Visual Analytics ABSTRACT Stephen Overton, Ben Zenick, Zencos Consulting Network diagrams in SAS
Arti Tyagi Sunita Choudhary
 Volume 5, Issue 3, March 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Web Usage Mining
Volume 5, Issue 3, March 2015 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Web Usage Mining
Performance Management Platform
 Open EMS Suite by Nokia Performance Management Platform Functional Overview Version 1.4 Nokia Siemens Networks 1 (16) Performance Management Platform The information in this document is subject to change
Open EMS Suite by Nokia Performance Management Platform Functional Overview Version 1.4 Nokia Siemens Networks 1 (16) Performance Management Platform The information in this document is subject to change
MEng, BSc Applied Computer Science
 School of Computing FACULTY OF ENGINEERING MEng, BSc Applied Computer Science Year 1 COMP1212 Computer Processor Effective programming depends on understanding not only how to give a machine instructions
School of Computing FACULTY OF ENGINEERING MEng, BSc Applied Computer Science Year 1 COMP1212 Computer Processor Effective programming depends on understanding not only how to give a machine instructions
Oracle Big Data SQL Technical Update
 Oracle Big Data SQL Technical Update Jean-Pierre Dijcks Oracle Redwood City, CA, USA Keywords: Big Data, Hadoop, NoSQL Databases, Relational Databases, SQL, Security, Performance Introduction This technical
Oracle Big Data SQL Technical Update Jean-Pierre Dijcks Oracle Redwood City, CA, USA Keywords: Big Data, Hadoop, NoSQL Databases, Relational Databases, SQL, Security, Performance Introduction This technical
Natural Language to Relational Query by Using Parsing Compiler
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 3, March 2015,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 4, Issue. 3, March 2015,
FUZZY CLUSTERING ANALYSIS OF DATA MINING: APPLICATION TO AN ACCIDENT MINING SYSTEM
 International Journal of Innovative Computing, Information and Control ICIC International c 0 ISSN 34-48 Volume 8, Number 8, August 0 pp. 4 FUZZY CLUSTERING ANALYSIS OF DATA MINING: APPLICATION TO AN ACCIDENT
International Journal of Innovative Computing, Information and Control ICIC International c 0 ISSN 34-48 Volume 8, Number 8, August 0 pp. 4 FUZZY CLUSTERING ANALYSIS OF DATA MINING: APPLICATION TO AN ACCIDENT
Interactive Dynamic Information Extraction
 Interactive Dynamic Information Extraction Kathrin Eichler, Holmer Hemsen, Markus Löckelt, Günter Neumann, and Norbert Reithinger Deutsches Forschungszentrum für Künstliche Intelligenz - DFKI, 66123 Saarbrücken
Interactive Dynamic Information Extraction Kathrin Eichler, Holmer Hemsen, Markus Löckelt, Günter Neumann, and Norbert Reithinger Deutsches Forschungszentrum für Künstliche Intelligenz - DFKI, 66123 Saarbrücken
IT services for analyses of various data samples
 IT services for analyses of various data samples Ján Paralič, František Babič, Martin Sarnovský, Peter Butka, Cecília Havrilová, Miroslava Muchová, Michal Puheim, Martin Mikula, Gabriel Tutoky Technical
IT services for analyses of various data samples Ján Paralič, František Babič, Martin Sarnovský, Peter Butka, Cecília Havrilová, Miroslava Muchová, Michal Puheim, Martin Mikula, Gabriel Tutoky Technical
BillQuick Agent 2010 Getting Started Guide
 Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Agent 2010 Getting Started Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
Time Billing and Project Management Software Built With Your Industry Knowledge BillQuick Agent 2010 Getting Started Guide BQE Software, Inc. 2601 Airport Drive Suite 380 Torrance CA 90505 Support: (310)
Building a Question Classifier for a TREC-Style Question Answering System
 Building a Question Classifier for a TREC-Style Question Answering System Richard May & Ari Steinberg Topic: Question Classification We define Question Classification (QC) here to be the task that, given
Building a Question Classifier for a TREC-Style Question Answering System Richard May & Ari Steinberg Topic: Question Classification We define Question Classification (QC) here to be the task that, given
ECS 235A Project - NVD Visualization Using TreeMaps
 ECS 235A Project - NVD Visualization Using TreeMaps Kevin Griffin Email: kevgriffin@ucdavis.edu December 12, 2013 1 Introduction The National Vulnerability Database (NVD) is a continuously updated United
ECS 235A Project - NVD Visualization Using TreeMaps Kevin Griffin Email: kevgriffin@ucdavis.edu December 12, 2013 1 Introduction The National Vulnerability Database (NVD) is a continuously updated United
The Data Mining Process
 Sequence for Determining Necessary Data. Wrong: Catalog everything you have, and decide what data is important. Right: Work backward from the solution, define the problem explicitly, and map out the data
Sequence for Determining Necessary Data. Wrong: Catalog everything you have, and decide what data is important. Right: Work backward from the solution, define the problem explicitly, and map out the data
White Paper. How Streaming Data Analytics Enables Real-Time Decisions
 White Paper How Streaming Data Analytics Enables Real-Time Decisions Contents Introduction... 1 What Is Streaming Analytics?... 1 How Does SAS Event Stream Processing Work?... 2 Overview...2 Event Stream
White Paper How Streaming Data Analytics Enables Real-Time Decisions Contents Introduction... 1 What Is Streaming Analytics?... 1 How Does SAS Event Stream Processing Work?... 2 Overview...2 Event Stream
A Survey on Product Aspect Ranking
 A Survey on Product Aspect Ranking Charushila Patil 1, Prof. P. M. Chawan 2, Priyamvada Chauhan 3, Sonali Wankhede 4 M. Tech Student, Department of Computer Engineering and IT, VJTI College, Mumbai, Maharashtra,
A Survey on Product Aspect Ranking Charushila Patil 1, Prof. P. M. Chawan 2, Priyamvada Chauhan 3, Sonali Wankhede 4 M. Tech Student, Department of Computer Engineering and IT, VJTI College, Mumbai, Maharashtra,
Method of Fault Detection in Cloud Computing Systems
 , pp.205-212 http://dx.doi.org/10.14257/ijgdc.2014.7.3.21 Method of Fault Detection in Cloud Computing Systems Ying Jiang, Jie Huang, Jiaman Ding and Yingli Liu Yunnan Key Lab of Computer Technology Application,
, pp.205-212 http://dx.doi.org/10.14257/ijgdc.2014.7.3.21 Method of Fault Detection in Cloud Computing Systems Ying Jiang, Jie Huang, Jiaman Ding and Yingli Liu Yunnan Key Lab of Computer Technology Application,
International Journal of Engineering Technology, Management and Applied Sciences. www.ijetmas.com November 2014, Volume 2 Issue 6, ISSN 2349-4476
 ERP SYSYTEM Nitika Jain 1 Niriksha 2 1 Student, RKGITW 2 Student, RKGITW Uttar Pradesh Tech. University Uttar Pradesh Tech. University Ghaziabad, U.P., India Ghaziabad, U.P., India ABSTRACT Student ERP
ERP SYSYTEM Nitika Jain 1 Niriksha 2 1 Student, RKGITW 2 Student, RKGITW Uttar Pradesh Tech. University Uttar Pradesh Tech. University Ghaziabad, U.P., India Ghaziabad, U.P., India ABSTRACT Student ERP
The multilayer sentiment analysis model based on Random forest Wei Liu1, Jie Zhang2
 2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2016) The multilayer sentiment analysis model based on Random forest Wei Liu1, Jie Zhang2 1 School of
2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2016) The multilayer sentiment analysis model based on Random forest Wei Liu1, Jie Zhang2 1 School of
The Design Study of High-Quality Resource Shared Classes in China: A Case Study of the Abnormal Psychology Course
 The Design Study of High-Quality Resource Shared Classes in China: A Case Study of the Abnormal Psychology Course Juan WANG College of Educational Science, JiangSu Normal University, Jiangsu, Xuzhou, China
The Design Study of High-Quality Resource Shared Classes in China: A Case Study of the Abnormal Psychology Course Juan WANG College of Educational Science, JiangSu Normal University, Jiangsu, Xuzhou, China
Parallel Compression and Decompression of DNA Sequence Reads in FASTQ Format
 , pp.91-100 http://dx.doi.org/10.14257/ijhit.2014.7.4.09 Parallel Compression and Decompression of DNA Sequence Reads in FASTQ Format Jingjing Zheng 1,* and Ting Wang 1, 2 1,* Parallel Software and Computational
, pp.91-100 http://dx.doi.org/10.14257/ijhit.2014.7.4.09 Parallel Compression and Decompression of DNA Sequence Reads in FASTQ Format Jingjing Zheng 1,* and Ting Wang 1, 2 1,* Parallel Software and Computational
Dr. Pat Mirenda. Software Design Specification Document
 CPSC 319 Team 2 Dr. Pat Mirenda Software Design Specification Document Version: 1.2 Date: (03/17/2006) 2Communicate SDS Revisions Version Primary Author(s) Description of Version Date Completed 1.0 Wei
CPSC 319 Team 2 Dr. Pat Mirenda Software Design Specification Document Version: 1.2 Date: (03/17/2006) 2Communicate SDS Revisions Version Primary Author(s) Description of Version Date Completed 1.0 Wei
Corporate Leaders Analytics and Network System (CLANS): Constructing and Mining Social Networks among Corporations and Business Elites in China
 Corporate Leaders Analytics and Network System (CLANS): Constructing and Mining Social Networks among Corporations and Business Elites in China Yuanyuan Man, Shuai Wang, Yi Li, Yong Zhang, Long Cheng,
Corporate Leaders Analytics and Network System (CLANS): Constructing and Mining Social Networks among Corporations and Business Elites in China Yuanyuan Man, Shuai Wang, Yi Li, Yong Zhang, Long Cheng,
Research of Postal Data mining system based on big data
 3rd International Conference on Mechatronics, Robotics and Automation (ICMRA 2015) Research of Postal Data mining system based on big data Xia Hu 1, Yanfeng Jin 1, Fan Wang 1 1 Shi Jiazhuang Post & Telecommunication
3rd International Conference on Mechatronics, Robotics and Automation (ICMRA 2015) Research of Postal Data mining system based on big data Xia Hu 1, Yanfeng Jin 1, Fan Wang 1 1 Shi Jiazhuang Post & Telecommunication
MEng, BSc Computer Science with Artificial Intelligence
 School of Computing FACULTY OF ENGINEERING MEng, BSc Computer Science with Artificial Intelligence Year 1 COMP1212 Computer Processor Effective programming depends on understanding not only how to give
School of Computing FACULTY OF ENGINEERING MEng, BSc Computer Science with Artificial Intelligence Year 1 COMP1212 Computer Processor Effective programming depends on understanding not only how to give
Available online at www.sciencedirect.com Available online at www.sciencedirect.com. Advanced in Control Engineering and Information Science
 Available online at www.sciencedirect.com Available online at www.sciencedirect.com Procedia Procedia Engineering Engineering 00 (2011) 15 (2011) 000 000 1822 1826 Procedia Engineering www.elsevier.com/locate/procedia
Available online at www.sciencedirect.com Available online at www.sciencedirect.com Procedia Procedia Engineering Engineering 00 (2011) 15 (2011) 000 000 1822 1826 Procedia Engineering www.elsevier.com/locate/procedia
Scatter Chart. Segmented Bar Chart. Overlay Chart
 Data Visualization Using Java and VRML Lingxiao Li, Art Barnes, SAS Institute Inc., Cary, NC ABSTRACT Java and VRML (Virtual Reality Modeling Language) are tools with tremendous potential for creating
Data Visualization Using Java and VRML Lingxiao Li, Art Barnes, SAS Institute Inc., Cary, NC ABSTRACT Java and VRML (Virtual Reality Modeling Language) are tools with tremendous potential for creating
SCADE System 17.0. Technical Data Sheet. System Requirements Analysis. Technical Data Sheet SCADE System 17.0 1
 SCADE System 17.0 SCADE System is the product line of the ANSYS Embedded software family of products and solutions that empowers users with a systems design environment for use on systems with high dependability
SCADE System 17.0 SCADE System is the product line of the ANSYS Embedded software family of products and solutions that empowers users with a systems design environment for use on systems with high dependability
Data Mining. SPSS Clementine 12.0. 1. Clementine Overview. Spring 2010 Instructor: Dr. Masoud Yaghini. Clementine
 Data Mining SPSS 12.0 1. Overview Spring 2010 Instructor: Dr. Masoud Yaghini Introduction Types of Models Interface Projects References Outline Introduction Introduction Three of the common data mining
Data Mining SPSS 12.0 1. Overview Spring 2010 Instructor: Dr. Masoud Yaghini Introduction Types of Models Interface Projects References Outline Introduction Introduction Three of the common data mining
ATM Network Performance Evaluation And Optimization Using Complex Network Theory
 ATM Network Performance Evaluation And Optimization Using Complex Network Theory Yalin LI 1, Bruno F. Santos 2 and Richard Curran 3 Air Transport and Operations Faculty of Aerospace Engineering The Technical
ATM Network Performance Evaluation And Optimization Using Complex Network Theory Yalin LI 1, Bruno F. Santos 2 and Richard Curran 3 Air Transport and Operations Faculty of Aerospace Engineering The Technical
Mobile Storage and Search Engine of Information Oriented to Food Cloud
 Advance Journal of Food Science and Technology 5(10): 1331-1336, 2013 ISSN: 2042-4868; e-issn: 2042-4876 Maxwell Scientific Organization, 2013 Submitted: May 29, 2013 Accepted: July 04, 2013 Published:
Advance Journal of Food Science and Technology 5(10): 1331-1336, 2013 ISSN: 2042-4868; e-issn: 2042-4876 Maxwell Scientific Organization, 2013 Submitted: May 29, 2013 Accepted: July 04, 2013 Published:
Mathematical models to estimate the quality of monitoring software systems for electrical substations
 Mathematical models to estimate the quality of monitoring software systems for electrical substations MIHAIELA ILIESCU 1, VICTOR URSIANU 2, FLORICA MOLDOVEANU 2, RADU URSIANU 2, EMILIANA URSIANU 3 1 Faculty
Mathematical models to estimate the quality of monitoring software systems for electrical substations MIHAIELA ILIESCU 1, VICTOR URSIANU 2, FLORICA MOLDOVEANU 2, RADU URSIANU 2, EMILIANA URSIANU 3 1 Faculty
#jenkinsconf. Jenkins as a Scientific Data and Image Processing Platform. Jenkins User Conference Boston #jenkinsconf
 Jenkins as a Scientific Data and Image Processing Platform Ioannis K. Moutsatsos, Ph.D., M.SE. Novartis Institutes for Biomedical Research www.novartis.com June 18, 2014 #jenkinsconf Life Sciences are
Jenkins as a Scientific Data and Image Processing Platform Ioannis K. Moutsatsos, Ph.D., M.SE. Novartis Institutes for Biomedical Research www.novartis.com June 18, 2014 #jenkinsconf Life Sciences are
ANALYSIS OF WEBSITE USAGE WITH USER DETAILS USING DATA MINING PATTERN RECOGNITION
 ANALYSIS OF WEBSITE USAGE WITH USER DETAILS USING DATA MINING PATTERN RECOGNITION K.Vinodkumar 1, Kathiresan.V 2, Divya.K 3 1 MPhil scholar, RVS College of Arts and Science, Coimbatore, India. 2 HOD, Dr.SNS
ANALYSIS OF WEBSITE USAGE WITH USER DETAILS USING DATA MINING PATTERN RECOGNITION K.Vinodkumar 1, Kathiresan.V 2, Divya.K 3 1 MPhil scholar, RVS College of Arts and Science, Coimbatore, India. 2 HOD, Dr.SNS
Data Visualization in Julia
 Introduction: Data Visualization in Julia Andres Lopez-Pineda December 13th, 211 I am Course 6 and 18, and I am primarily interested in Human Interfaces and Graphics. I took this class because I believe
Introduction: Data Visualization in Julia Andres Lopez-Pineda December 13th, 211 I am Course 6 and 18, and I am primarily interested in Human Interfaces and Graphics. I took this class because I believe
Diploma Of Computing
 Diploma Of Computing Course Outline Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June, October 022638B
Diploma Of Computing Course Outline Campus Intake CRICOS Course Duration Teaching Methods Assessment Course Structure Units Melbourne Burwood Campus / Jakarta Campus, Indonesia March, June, October 022638B
OPINION MINING IN PRODUCT REVIEW SYSTEM USING BIG DATA TECHNOLOGY HADOOP
 OPINION MINING IN PRODUCT REVIEW SYSTEM USING BIG DATA TECHNOLOGY HADOOP 1 KALYANKUMAR B WADDAR, 2 K SRINIVASA 1 P G Student, S.I.T Tumkur, 2 Assistant Professor S.I.T Tumkur Abstract- Product Review System
OPINION MINING IN PRODUCT REVIEW SYSTEM USING BIG DATA TECHNOLOGY HADOOP 1 KALYANKUMAR B WADDAR, 2 K SRINIVASA 1 P G Student, S.I.T Tumkur, 2 Assistant Professor S.I.T Tumkur Abstract- Product Review System
Data Mining Algorithms Part 1. Dejan Sarka
 Data Mining Algorithms Part 1 Dejan Sarka Join the conversation on Twitter: @DevWeek #DW2015 Instructor Bio Dejan Sarka (dsarka@solidq.com) 30 years of experience SQL Server MVP, MCT, 13 books 7+ courses
Data Mining Algorithms Part 1 Dejan Sarka Join the conversation on Twitter: @DevWeek #DW2015 Instructor Bio Dejan Sarka (dsarka@solidq.com) 30 years of experience SQL Server MVP, MCT, 13 books 7+ courses
Flexible Web Visualization for Alert-Based Network Security Analytics
 Flexible Web Visualization for Alert-Based Network Security Analytics Lihua Hao 1, Christopher G. Healey 1, Steve E. Hutchinson 2 1 North Carolina State University, 2 U.S. Army Research Laboratory lhao2@ncsu.edu
Flexible Web Visualization for Alert-Based Network Security Analytics Lihua Hao 1, Christopher G. Healey 1, Steve E. Hutchinson 2 1 North Carolina State University, 2 U.S. Army Research Laboratory lhao2@ncsu.edu
Authoring for System Center 2012 Operations Manager
 Authoring for System Center 2012 Operations Manager Microsoft Corporation Published: November 1, 2013 Authors Byron Ricks Applies To System Center 2012 Operations Manager System Center 2012 Service Pack
Authoring for System Center 2012 Operations Manager Microsoft Corporation Published: November 1, 2013 Authors Byron Ricks Applies To System Center 2012 Operations Manager System Center 2012 Service Pack
Analysis of Email Fraud Detection Using WEKA Tool
 Analysis of Email Fraud Detection Using WEKA Tool Author:Tarushi Sharma, M-Tech(Information Technology), CGC Landran Mohali, Punjab,India, Co-Author:Mrs.Amanpreet Kaur (Assistant Professor), CGC Landran
Analysis of Email Fraud Detection Using WEKA Tool Author:Tarushi Sharma, M-Tech(Information Technology), CGC Landran Mohali, Punjab,India, Co-Author:Mrs.Amanpreet Kaur (Assistant Professor), CGC Landran
Quick Start. Creating a Scoring Application. RStat. Based on a Decision Tree Model
 Creating a Scoring Application Based on a Decision Tree Model This Quick Start guides you through creating a credit-scoring application in eight easy steps. Quick Start Century Corp., an electronics retailer,
Creating a Scoring Application Based on a Decision Tree Model This Quick Start guides you through creating a credit-scoring application in eight easy steps. Quick Start Century Corp., an electronics retailer,
Component visualization methods for large legacy software in C/C++
 Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
Deposit Identification Utility and Visualization Tool
 Deposit Identification Utility and Visualization Tool Colorado School of Mines Field Session Summer 2014 David Alexander Jeremy Kerr Luke McPherson Introduction Newmont Mining Corporation was founded in
Deposit Identification Utility and Visualization Tool Colorado School of Mines Field Session Summer 2014 David Alexander Jeremy Kerr Luke McPherson Introduction Newmont Mining Corporation was founded in
Automatic Mining of Internet Translation Reference Knowledge Based on Multiple Search Engines
 , 22-24 October, 2014, San Francisco, USA Automatic Mining of Internet Translation Reference Knowledge Based on Multiple Search Engines Baosheng Yin, Wei Wang, Ruixue Lu, Yang Yang Abstract With the increasing
, 22-24 October, 2014, San Francisco, USA Automatic Mining of Internet Translation Reference Knowledge Based on Multiple Search Engines Baosheng Yin, Wei Wang, Ruixue Lu, Yang Yang Abstract With the increasing
How to Analyze Company Using Social Network?
 How to Analyze Company Using Social Network? Sebastian Palus 1, Piotr Bródka 1, Przemysław Kazienko 1 1 Wroclaw University of Technology, Wyb. Wyspianskiego 27, 50-370 Wroclaw, Poland {sebastian.palus,
How to Analyze Company Using Social Network? Sebastian Palus 1, Piotr Bródka 1, Przemysław Kazienko 1 1 Wroclaw University of Technology, Wyb. Wyspianskiego 27, 50-370 Wroclaw, Poland {sebastian.palus,
A Load Balancing Algorithm based on the Variation Trend of Entropy in Homogeneous Cluster
 , pp.11-20 http://dx.doi.org/10.14257/ ijgdc.2014.7.2.02 A Load Balancing Algorithm based on the Variation Trend of Entropy in Homogeneous Cluster Kehe Wu 1, Long Chen 2, Shichao Ye 2 and Yi Li 2 1 Beijing
, pp.11-20 http://dx.doi.org/10.14257/ ijgdc.2014.7.2.02 A Load Balancing Algorithm based on the Variation Trend of Entropy in Homogeneous Cluster Kehe Wu 1, Long Chen 2, Shichao Ye 2 and Yi Li 2 1 Beijing
Big Data Analytics of Multi-Relationship Online Social Network Based on Multi-Subnet Composited Complex Network
 , pp.273-284 http://dx.doi.org/10.14257/ijdta.2015.8.5.24 Big Data Analytics of Multi-Relationship Online Social Network Based on Multi-Subnet Composited Complex Network Gengxin Sun 1, Sheng Bin 2 and
, pp.273-284 http://dx.doi.org/10.14257/ijdta.2015.8.5.24 Big Data Analytics of Multi-Relationship Online Social Network Based on Multi-Subnet Composited Complex Network Gengxin Sun 1, Sheng Bin 2 and
Students who successfully complete the Health Science Informatics major will be able to:
 Health Science Informatics Program Requirements Hours: 72 hours Informatics Core Requirements - 31 hours INF 101 Seminar Introductory Informatics (1) INF 110 Foundations in Technology (3) INF 120 Principles
Health Science Informatics Program Requirements Hours: 72 hours Informatics Core Requirements - 31 hours INF 101 Seminar Introductory Informatics (1) INF 110 Foundations in Technology (3) INF 120 Principles
Website Design and Maintenance of University PE Excellent Courses Based on Web Technique
 I.J. Education and Management Engineering 2012, 5, 43-47 Published Online May 2012 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijeme.2012.05.07 Available online at http://www.mecs-press.net/ijeme
I.J. Education and Management Engineering 2012, 5, 43-47 Published Online May 2012 in MECS (http://www.mecs-press.net) DOI: 10.5815/ijeme.2012.05.07 Available online at http://www.mecs-press.net/ijeme
Structural Health Monitoring Tools (SHMTools)
 Structural Health Monitoring Tools (SHMTools) Getting Started LANL/UCSD Engineering Institute LA-CC-14-046 c Copyright 2014, Los Alamos National Security, LLC All rights reserved. May 30, 2014 Contents
Structural Health Monitoring Tools (SHMTools) Getting Started LANL/UCSD Engineering Institute LA-CC-14-046 c Copyright 2014, Los Alamos National Security, LLC All rights reserved. May 30, 2014 Contents
Vendor briefing Business Intelligence and Analytics Platforms Gartner 15 capabilities
 Vendor briefing Business Intelligence and Analytics Platforms Gartner 15 capabilities April, 2013 gaddsoftware.com Table of content 1. Introduction... 3 2. Vendor briefings questions and answers... 3 2.1.
Vendor briefing Business Intelligence and Analytics Platforms Gartner 15 capabilities April, 2013 gaddsoftware.com Table of content 1. Introduction... 3 2. Vendor briefings questions and answers... 3 2.1.
Managing DICOM Image Metadata with Desktop Operating Systems Native User Interface
 Managing DICOM Image Metadata with Desktop Operating Systems Native User Interface Chia-Chi Teng, Member, IEEE Abstract Picture Archiving and Communication System (PACS) is commonly used in the hospital
Managing DICOM Image Metadata with Desktop Operating Systems Native User Interface Chia-Chi Teng, Member, IEEE Abstract Picture Archiving and Communication System (PACS) is commonly used in the hospital
The Framework of Network Public Opinion Monitoring and Analyzing System Based on Semantic Content Identification
 The Framework of Network Public Opinion Monitoring and Analyzing System Based on Semantic Content Identification Cheng Xian-Yi1, Zhu Ling-ling,Zhu Qian,Wang Jin The Framework of Network Public Opinion
The Framework of Network Public Opinion Monitoring and Analyzing System Based on Semantic Content Identification Cheng Xian-Yi1, Zhu Ling-ling,Zhu Qian,Wang Jin The Framework of Network Public Opinion
A STUDY OF DATA MINING ACTIVITIES FOR MARKET RESEARCH
 205 A STUDY OF DATA MINING ACTIVITIES FOR MARKET RESEARCH ABSTRACT MR. HEMANT KUMAR*; DR. SARMISTHA SARMA** *Assistant Professor, Department of Information Technology (IT), Institute of Innovation in Technology
205 A STUDY OF DATA MINING ACTIVITIES FOR MARKET RESEARCH ABSTRACT MR. HEMANT KUMAR*; DR. SARMISTHA SARMA** *Assistant Professor, Department of Information Technology (IT), Institute of Innovation in Technology
Network Machine Learning Research Group. Intended status: Informational October 19, 2015 Expires: April 21, 2016
 Network Machine Learning Research Group S. Jiang Internet-Draft Huawei Technologies Co., Ltd Intended status: Informational October 19, 2015 Expires: April 21, 2016 Abstract Network Machine Learning draft-jiang-nmlrg-network-machine-learning-00
Network Machine Learning Research Group S. Jiang Internet-Draft Huawei Technologies Co., Ltd Intended status: Informational October 19, 2015 Expires: April 21, 2016 Abstract Network Machine Learning draft-jiang-nmlrg-network-machine-learning-00
Excel Companion. (Profit Embedded PHD) User's Guide
 Excel Companion (Profit Embedded PHD) User's Guide Excel Companion (Profit Embedded PHD) User's Guide Copyright, Notices, and Trademarks Copyright, Notices, and Trademarks Honeywell Inc. 1998 2001. All
Excel Companion (Profit Embedded PHD) User's Guide Excel Companion (Profit Embedded PHD) User's Guide Copyright, Notices, and Trademarks Copyright, Notices, and Trademarks Honeywell Inc. 1998 2001. All
ALIAS: A Tool for Disambiguating Authors in Microsoft Academic Search
 Project for Michael Pitts Course TCSS 702A University of Washington Tacoma Institute of Technology ALIAS: A Tool for Disambiguating Authors in Microsoft Academic Search Under supervision of : Dr. Senjuti
Project for Michael Pitts Course TCSS 702A University of Washington Tacoma Institute of Technology ALIAS: A Tool for Disambiguating Authors in Microsoft Academic Search Under supervision of : Dr. Senjuti
Easily Identify Your Best Customers
 IBM SPSS Statistics Easily Identify Your Best Customers Use IBM SPSS predictive analytics software to gain insight from your customer database Contents: 1 Introduction 2 Exploring customer data Where do
IBM SPSS Statistics Easily Identify Your Best Customers Use IBM SPSS predictive analytics software to gain insight from your customer database Contents: 1 Introduction 2 Exploring customer data Where do
ASSOCIATION RULE MINING ON WEB LOGS FOR EXTRACTING INTERESTING PATTERNS THROUGH WEKA TOOL
 International Journal Of Advanced Technology In Engineering And Science Www.Ijates.Com Volume No 03, Special Issue No. 01, February 2015 ISSN (Online): 2348 7550 ASSOCIATION RULE MINING ON WEB LOGS FOR
International Journal Of Advanced Technology In Engineering And Science Www.Ijates.Com Volume No 03, Special Issue No. 01, February 2015 ISSN (Online): 2348 7550 ASSOCIATION RULE MINING ON WEB LOGS FOR
HISTORICAL DEVELOPMENTS AND THEORETICAL APPROACHES IN SOCIOLOGY Vol. I - Social Network Analysis - Wouter de Nooy
 SOCIAL NETWORK ANALYSIS University of Amsterdam, Netherlands Keywords: Social networks, structuralism, cohesion, brokerage, stratification, network analysis, methods, graph theory, statistical models Contents
SOCIAL NETWORK ANALYSIS University of Amsterdam, Netherlands Keywords: Social networks, structuralism, cohesion, brokerage, stratification, network analysis, methods, graph theory, statistical models Contents
Time series clustering and the analysis of film style
 Time series clustering and the analysis of film style Nick Redfern Introduction Time series clustering provides a simple solution to the problem of searching a database containing time series data such
Time series clustering and the analysis of film style Nick Redfern Introduction Time series clustering provides a simple solution to the problem of searching a database containing time series data such
2015 Workshops for Professors
 SAS Education Grow with us Offered by the SAS Global Academic Program Supporting teaching, learning and research in higher education 2015 Workshops for Professors 1 Workshops for Professors As the market
SAS Education Grow with us Offered by the SAS Global Academic Program Supporting teaching, learning and research in higher education 2015 Workshops for Professors 1 Workshops for Professors As the market
