OpenText Secure MFT Network and Firewall Requirements
|
|
|
- Ferdinand Blankenship
- 10 years ago
- Views:
Transcription
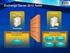
1 NETWORK OpenText Secure MFT Network and Firewall Requirements Secure MFT is a client-server solution that provides accelerated transfer of large files over any network connection. The solution architecture includes a multitude of components all communicating over the network using different protocols and ports. This document reviews Secure MFT network architecture and offers firewall considerations when deploying it in the corporate network. Network Components and Architecture Secure MFT is built on many components to provide authentication, record storage, data storage, and transfer logic and acceleration. The diagram below denotes the relationship of these components: / WEB TRANSFER SMTP: 25 SQL: 1433 SMB: 445 MAIL RELAY SQL FILE SYSTEM
2 NETWORK The inter-communication between all those components requires different network protocols operating on different ports. The following table describes the primary function of each component and its network requirements. All ports shown in the table are based on the standard or default configuration. In some cases, customers can modify the port assignment. NAME DESCRIPTION PROTOCOL PORT WEB Provides page rendering services, auditing, reporting, HTTP/S transfer fallback capability for clients that cannot establish OpenText Fuel connection with the server. HTTP/HTTPS 80/443 TRANSFER Provides the support for OpenText Fuel protocol. OpenText Fuel DIRECTORY S MICROSOFT SQL SMTP MAIL RELAY FILE SYSTEM Provides user authentication services including LDAP/AD integration and SSO support. RDBMS back-end that stores server and user settings, transaction audit trail, and user database. Sends s with links to assets in Secure MFT server to recipients, and notifications to senders and administrators. A network accessible file storage for Secure MFT to store the file assets. HTTP/HTTPS 80/443 SQL 1443 SMTP 25 SMB 445 The counterpart of Secure MFT Enterprise Server, allows users to authenticate and initiate file transfer. HTTP/HTTPS 80/443
3 NETWORK Deployment Scenarios Depending on the placement of the Secure MFT Client and Server, there may be any number of firewalls separating those two parties. Scenario 1: Secure MFT is inside the corporate network If the whole stack of the Secure MFT Server components is deployed within the corporate network, in order for external users to access Secure MFT, the corporate network firewall will need to be configured to allow inbound and outbound Secure MFT network connections. INTERNET EXTERNAL DMZ CORP NET SMTP: 25 SQL: 1433 SMB: 445 MAIL RELAY SQL FILE SYSTEM
4 NETWORK Scenario 2: Secure MFT is in the DMZ If the whole stack of the Secure MFT Server components is deployed in the DMZ but outside of the corporate network, both the corporate network firewall and the DMZ firewall will need to be configured to allow inbound and outbound Secure MFT network connections. Depending on what components the organization wants to keep inside the corporate network, additional ports may need to be opened on the corporate network firewall to allow that network traffic. INTERNET EXTERNAL DMZ SQL SQL: 1433 SMTP: 25 SMB: 445 MAIL RELAY FILE SYSTEM CORP NET INTERNAL
5 NETWORK Scenario 3: Secure MFT is outside of the corporate network If Secure MFT is hosted by OpenText in the OpenText Cloud, or hosted by the customer in other cloud services, in order for users inside the corporate network to interact with the remote Secure MFT in the Cloud, the customer s corporate network and DMZ firewalls need to be configured to allow outbound network connections to the Secure MFT Server. This also applies to external users who wish to access the Secure MFT Server, which is inside your corporate network. Those external users will need to make sure their firewall settings are set to allow outbound connections to your Secure MFT Server. CLOUD SQL SQL: 1433 SMTP: 25 SMB: 445 MAIL RELAY FILE SYSTEM DMZ CORP NET INTERNAL
6 NETWORK Transfer Workflow The following diagram outlines the step-by-step process of the Secure MFT Transfer workflow, and ports that it uses in different stages of the communication. It focuses solely on the communication between Secure MFT Client and the Server services. NETWORK 1a Client connects to Secure MFT Web Service via HTTPS to authenticate and negotiate transfer settings ANY 443 USER 1b Web service replies with the security token, permissions/settings, the Transfer Service IP, and its and receive ports WEB 2 Client uses a random port to connect to Transfer Service port, and tells the Transfer Service its receive port (uses same port number as the random port) ANY Client connects to Transfer Service port 4 Client connects to Client port (SAME PORT NUMBER AS THE OUTBOUND PORT IN STEP 2) 3000 ANY TRANSFER Secure MFT -Transfer Workflow Firewall Configurations As mentioned previously, ports need to be opened on the firewalls to allow Secure MFT network traffic to pass through. The discussion continues to focus on the Secure MFT client/server communication, and default ports are used. But depending on the actual deployment scenarios, other ports (SQL, SMTP, SMB, etc) may also need to be opened. HTTP or HTTPS (80 or 443 over ) OpenText Fuel (3000 over and ) Server-side firewall configuration On the server side, the server computer is actively awaiting and accepting incoming requests from client computers over specific and ports, and reply to the client s requests with outbound and traffic. On the server-side firewall, the following configurations have to be made: Allow inbound connections to the server on ports (HTTP/HTTPS and OpenText Fuel) Allow inbound connections to the server on a port (OpenText Fuel) Allow outbound connections from the server on ports (HTTP/HTTPS and OpenText Fuel) Allow outbound connections from the server on a port (OpenText Fuel)
7 NETWORK Client-side firewall configuration On the client side, the client computer needs to make and outbound requests to the Secure MFT server (web service and the transfer service), and the server services will respond to the client requests through the corresponding ports, which the client machine chooses. On the client-side firewall, the following configurations have to be made: Allow outbound connections from within the firewall to the Secure MFT Server on ports (HTTPS and OpenText Fuel) Allow outbound connections from within the firewall to the Secure MFT Server on a port (OpenText Fuel) Final Words Secure MFT is a complex network application, but with good understanding of its network architecture, requirements, and careful planning, it is easy to modify the firewall and proxy settings to allow Secure MFT traffic to traverse the corporate network and DMZ without sacrificing network security. For more information on how Secure MFT ensures data security, please read the Secure MFT Security Overview whitepaper. NORTH AMERICA EUROPE +31 (0) AFRICA, MIDDLE EAST JAPAN CHINA HONG KONG AUSTRALIA Copyright 2016 Open Text Corporation OpenText is a trademark or registered trademark of Open Text SA and/or Open Text ULC. The list of trademarks is not exhaustive of other trademarks, registered trademarks, product names, company names, brands and service names mentioned herein are property of Open Text SA or other respective owners. All rights reserved. For more information, visit: (01/2016)04146EN
OpenText Fax Servers and Microsoft Office 365
 OpenText Fax Servers and Microsoft Office 365 Integrating Fax with Office 365 E N T E R P R I S E I N F O R M A T I O N M A N A G E M E N T 1 Abstract Cloud-based information technologies promise a number
OpenText Fax Servers and Microsoft Office 365 Integrating Fax with Office 365 E N T E R P R I S E I N F O R M A T I O N M A N A G E M E N T 1 Abstract Cloud-based information technologies promise a number
DeltaV System Health Monitoring Networking and Security
 DeltaV Distributed Control System White Paper DeltaV System Health Monitoring Networking and Security Introduction Emerson Process Management s DeltaV System Health Monitoring service enables you to proactively
DeltaV Distributed Control System White Paper DeltaV System Health Monitoring Networking and Security Introduction Emerson Process Management s DeltaV System Health Monitoring service enables you to proactively
For over 25 years, OpenText Cloud Fax Services has. OpenText Cloud Fax Services. The Market Leader in Cloud Fax Technology
 OpenText Cloud Fax Services The Market Leader in Cloud Fax Technology For over 25 years, OpenText Cloud Fax Services has helped many companies go paperless with solutions that integrate with both email
OpenText Cloud Fax Services The Market Leader in Cloud Fax Technology For over 25 years, OpenText Cloud Fax Services has helped many companies go paperless with solutions that integrate with both email
OpenText Managed File Transfer (MFT) is an enterprise
 OpenText IX Secure MFT Simplified, accelerated, and managed enterprise file exchange OpenText Managed File Transfer (MFT) is an enterprise solution for managing the exchange of rich digital content inside
OpenText IX Secure MFT Simplified, accelerated, and managed enterprise file exchange OpenText Managed File Transfer (MFT) is an enterprise solution for managing the exchange of rich digital content inside
OpenText RightFax Express
 OpenText RightFax Express TM One solution. Multiple choices. Small and medium-sized businesses (SMBs) have issues similar to those of larger enterprise organizations but have fewer resources to handle
OpenText RightFax Express TM One solution. Multiple choices. Small and medium-sized businesses (SMBs) have issues similar to those of larger enterprise organizations but have fewer resources to handle
Interwise Connect. Working with Reverse Proxy Version 7.x
 Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Novar Database Mail Setup Guidelines
 Database Mail Setup Guidelines August 2015 Delivering the Moment Publication Information 2015 Imagine Communications Corp. Proprietary and Confidential. Imagine Communications considers this document and
Database Mail Setup Guidelines August 2015 Delivering the Moment Publication Information 2015 Imagine Communications Corp. Proprietary and Confidential. Imagine Communications considers this document and
Serial Deployment Quick Start Guide
 PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
PaperClip em 4 11/19/2007 Serial Deployment Quick Start Guide This checklist should be completed before installing the em4 Relay. Your answers with the associated screens will enable you to install and
How To Use Netscaler As An Afs Proxy
 Deployment Guide Guide to Deploying NetScaler as an Active Directory Federation Services Proxy Enabling seamless authentication for Office 365 use cases Table of Contents Introduction 3 ADFS proxy deployment
Deployment Guide Guide to Deploying NetScaler as an Active Directory Federation Services Proxy Enabling seamless authentication for Office 365 use cases Table of Contents Introduction 3 ADFS proxy deployment
FreeFlow Core, Version 4.0 August 2014 702P02837. Xerox FreeFlow Core Security Guide
 FreeFlow Core, Version 4.0 August 2014 702P02837 2014 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, and FreeFlow are trademarks of Xerox Corporation in the United States and/or other
FreeFlow Core, Version 4.0 August 2014 702P02837 2014 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, and FreeFlow are trademarks of Xerox Corporation in the United States and/or other
This article describes a detailed configuration example that demonstrates how to configure Cyberoam to provide the access of internal resources.
 How To Configure Port Forwarding using Virtual Host to access devices on Internal network Applicable to versions 9.5.3 build 14 or above This article describes a detailed configuration example that demonstrates
How To Configure Port Forwarding using Virtual Host to access devices on Internal network Applicable to versions 9.5.3 build 14 or above This article describes a detailed configuration example that demonstrates
Kaseya Server Instal ation User Guide June 6, 2008
 Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Proxies. Chapter 4. Network & Security Gildas Avoine
 Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Proxies Chapter 4 Network & Security Gildas Avoine SUMMARY OF CHAPTER 4 Generalities Forward Proxies Reverse Proxies Open Proxies Conclusion GENERALITIES Generalities Forward Proxies Reverse Proxies Open
Service Overview & Installation Guide
 Service Overview & Installation Guide Contents Contents... 2 1.0 Overview... 3 2.0 Simple Setup... 4 3.0 OWA Setup... 5 3.1 Receive Test... 5 3.2 Send Test... 6 4.0 Advanced Setup... 7 4.1 Receive Test
Service Overview & Installation Guide Contents Contents... 2 1.0 Overview... 3 2.0 Simple Setup... 4 3.0 OWA Setup... 5 3.1 Receive Test... 5 3.2 Send Test... 6 4.0 Advanced Setup... 7 4.1 Receive Test
Websense Web Security Gateway: Integrating the Content Gateway component with Third Party Data Loss Prevention Applications
 Websense Web Security Gateway: Integrating the Content Gateway component with Third Party Data Loss Prevention Applications November, 2010 2010 Websense, Inc. All rights reserved. Websense is a registered
Websense Web Security Gateway: Integrating the Content Gateway component with Third Party Data Loss Prevention Applications November, 2010 2010 Websense, Inc. All rights reserved. Websense is a registered
Setting up Microsoft Office 365
 Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
MCSE SYLLABUS. Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003:
 MCSE SYLLABUS Course Contents : Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003: Managing Users, Computers and Groups. Configure access to shared folders. Managing and Maintaining
MCSE SYLLABUS Course Contents : Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003: Managing Users, Computers and Groups. Configure access to shared folders. Managing and Maintaining
Setting up Microsoft Office 365
 Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Security in Fax: Minimizing Breaches and Compliance Risks
 Security in Fax: Minimizing Breaches and Compliance Risks Maintaining regulatory compliance is a major business issue facing organizations around the world. The need to secure, track and store information
Security in Fax: Minimizing Breaches and Compliance Risks Maintaining regulatory compliance is a major business issue facing organizations around the world. The need to secure, track and store information
WhatsUp Event Archiver v10 and v10.1 Quick Setup Guide
 WhatsUp Event Archiver v10 and v10.1 Quick Setup Guide Contents WhatsUp Event Archiver Quick Setup Guide WhatsUp Event Archiver Quick Setup Guide... 2 Installation Requirements... 3 Manually Creating Firewall
WhatsUp Event Archiver v10 and v10.1 Quick Setup Guide Contents WhatsUp Event Archiver Quick Setup Guide WhatsUp Event Archiver Quick Setup Guide... 2 Installation Requirements... 3 Manually Creating Firewall
HARDWARE, SOFTWARE AND CONFIGURATION REQUIREMENTS
 Team Services PREMISE INSTALLATION REQUIREMENTS HARDWARE, SOFTWARE AND CONFIGURATION REQUIREMENTS Team Services may require reconfiguration of a client s existing environment to support our new dedicated
Team Services PREMISE INSTALLATION REQUIREMENTS HARDWARE, SOFTWARE AND CONFIGURATION REQUIREMENTS Team Services may require reconfiguration of a client s existing environment to support our new dedicated
Landscape Design and Integration. SAP Mobile Platform 3.0 SP02
 Landscape Design and Integration SAP Mobile Platform 3.0 SP02 DOCUMENT ID: DC01916-01-0302-01 LAST REVISED: February 2014 Copyright 2014 by SAP AG or an SAP affiliate company. All rights reserved. No part
Landscape Design and Integration SAP Mobile Platform 3.0 SP02 DOCUMENT ID: DC01916-01-0302-01 LAST REVISED: February 2014 Copyright 2014 by SAP AG or an SAP affiliate company. All rights reserved. No part
Technical Note. Configuring Outlook Web Access with Secure WebMail Proxy for eprism
 Technical Note Configuring Outlook Web Access with Secure WebMail Proxy for eprism Information in this document is subject to change without notice. This document may be distributed freely only in whole,
Technical Note Configuring Outlook Web Access with Secure WebMail Proxy for eprism Information in this document is subject to change without notice. This document may be distributed freely only in whole,
FoIP Interoperability Guide
 FoIP Interoperability Guide OpenText RightFax OpenText RightFax is the proven market leader in fax server, document delivery and fax software. It delivers the most reliable and robust fax software solutions
FoIP Interoperability Guide OpenText RightFax OpenText RightFax is the proven market leader in fax server, document delivery and fax software. It delivers the most reliable and robust fax software solutions
Firewalls and VPNs. Principles of Information Security, 5th Edition 1
 Firewalls and VPNs Principles of Information Security, 5th Edition 1 Learning Objectives Upon completion of this material, you should be able to: Understand firewall technology and the various approaches
Firewalls and VPNs Principles of Information Security, 5th Edition 1 Learning Objectives Upon completion of this material, you should be able to: Understand firewall technology and the various approaches
Ignify ecommerce. Item Requirements Notes
 wwwignifycom Tel (888) IGNIFY5 sales@ignifycom Fax (408) 516-9006 Ignify ecommerce Server Configuration 1 Hardware Requirement (Minimum configuration) Item Requirements Notes Operating System Processor
wwwignifycom Tel (888) IGNIFY5 sales@ignifycom Fax (408) 516-9006 Ignify ecommerce Server Configuration 1 Hardware Requirement (Minimum configuration) Item Requirements Notes Operating System Processor
This presentation describes the IBM Tivoli Monitoring 6.1 Firewall Implementation: KDE Gateway Component.
 This presentation describes the IBM Tivoli Monitoring 6.1 Firewall Implementation: KDE Gateway Component. Functional Overview of Gateway Topology, Gateway Configuration, and Gateway XML Structure Page
This presentation describes the IBM Tivoli Monitoring 6.1 Firewall Implementation: KDE Gateway Component. Functional Overview of Gateway Topology, Gateway Configuration, and Gateway XML Structure Page
OpenText Media Management Audit Module FAQ
 OpenText Media Management Audit Module FAQ Collect valuable metrics, analytics, and information about your OpenText Media Management system Introduction Audit capability is a must-have for next-generation
OpenText Media Management Audit Module FAQ Collect valuable metrics, analytics, and information about your OpenText Media Management system Introduction Audit capability is a must-have for next-generation
Security perimeter white paper. Configuring a security perimeter around JEP(S) with IIS SMTP
 Security perimeter white paper Configuring a security perimeter around JEP(S) with IIS SMTP Document control Document name: JEP(S) Security perimeter Author: Proxmea, Proxmea Last update: March 23, 2008
Security perimeter white paper Configuring a security perimeter around JEP(S) with IIS SMTP Document control Document name: JEP(S) Security perimeter Author: Proxmea, Proxmea Last update: March 23, 2008
Configuring Email Notification for Business Glossary
 Configuring Email Notification for Business Glossary 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Configuring Email Notification for Business Glossary 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Application Note. Onsight Connect Network Requirements v6.3
 Application Note Onsight Connect Network Requirements v6.3 APPLICATION NOTE... 1 ONSIGHT CONNECT NETWORK REQUIREMENTS V6.3... 1 1 ONSIGHT CONNECT SERVICE NETWORK REQUIREMENTS... 3 1.1 Onsight Connect Overview...
Application Note Onsight Connect Network Requirements v6.3 APPLICATION NOTE... 1 ONSIGHT CONNECT NETWORK REQUIREMENTS V6.3... 1 1 ONSIGHT CONNECT SERVICE NETWORK REQUIREMENTS... 3 1.1 Onsight Connect Overview...
Transport server data paths
 1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
ACE Management Server Deployment Guide VMware ACE 2.0
 Technical Note ACE Management Server Deployment Guide VMware ACE 2.0 This technical note provides guidelines for the deployment of VMware ACE Management Servers, including capacity planning and best practices.
Technical Note ACE Management Server Deployment Guide VMware ACE 2.0 This technical note provides guidelines for the deployment of VMware ACE Management Servers, including capacity planning and best practices.
Introduction to the AirWatch Cloud Connector (ACC) Guide
 Introduction to the AirWatch Cloud Connector (ACC) Guide The AirWatch Cloud Connector (ACC) provides organizations the ability to integrate AirWatch with their back-end enterprise systems. This document
Introduction to the AirWatch Cloud Connector (ACC) Guide The AirWatch Cloud Connector (ACC) provides organizations the ability to integrate AirWatch with their back-end enterprise systems. This document
1 Product. Open Text is the leading fax server vendor in the world. *
 1 Product Open Text Fax s Replace fax machines and inefficient paper processes with efficient and secure computer-based faxing and electronic document delivery Open Text is the leading fax server vendor
1 Product Open Text Fax s Replace fax machines and inefficient paper processes with efficient and secure computer-based faxing and electronic document delivery Open Text is the leading fax server vendor
Payment Card Industry and Citrix XenApp and XenDesktop Deployment Scenarios
 Payment Card Industry and Citrix XenApp and XenDesktop Deployment Scenarios Overview Citrix XenApp, XenDesktop and NetScaler are commonly used in the creation of Payment Card Industry (PCI), Data Security
Payment Card Industry and Citrix XenApp and XenDesktop Deployment Scenarios Overview Citrix XenApp, XenDesktop and NetScaler are commonly used in the creation of Payment Card Industry (PCI), Data Security
Deployment for Network Proxy in Simpana Environment
 Deployment for Network Proxy in Simpana Environment There are multiple ways you can use the proxy for Simpana communication. 1. Use proxy to communicate for CommNet DataCenter CS will also have CommNet
Deployment for Network Proxy in Simpana Environment There are multiple ways you can use the proxy for Simpana communication. 1. Use proxy to communicate for CommNet DataCenter CS will also have CommNet
Installing Policy Patrol on a separate machine
 Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Sage HRMS 2014 Sage Employee Self Service Tech Installation Guide for Windows 2003, 2008, and 2012. October 2013
 Sage HRMS 2014 Sage Employee Self Service Tech Installation Guide for Windows 2003, 2008, and 2012 October 2013 This is a publication of Sage Software, Inc. Document version: October 17, 2013 Copyright
Sage HRMS 2014 Sage Employee Self Service Tech Installation Guide for Windows 2003, 2008, and 2012 October 2013 This is a publication of Sage Software, Inc. Document version: October 17, 2013 Copyright
Introduction WHITE PAPER. OpenText RightFax
 F E B R U A R Y 2 0 1 4 FoIP Interoperability Guide O pentext RightFax is the proven market leader in fax server, document delivery and fax software. It delivers the most reliable and robust fax software
F E B R U A R Y 2 0 1 4 FoIP Interoperability Guide O pentext RightFax is the proven market leader in fax server, document delivery and fax software. It delivers the most reliable and robust fax software
Secure, Mobile Access to Corporate Email, Applications, and Intranet Resources
 APPLICATION NOTE Juniper NETWORKS SSL VPN and Windows Mobile Secure, Mobile Access to Corporate Email, Applications, and Intranet Resources Table of Contents Introduction.........................................................................................
APPLICATION NOTE Juniper NETWORKS SSL VPN and Windows Mobile Secure, Mobile Access to Corporate Email, Applications, and Intranet Resources Table of Contents Introduction.........................................................................................
Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123. Instructor Manual
 Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123 Instructor Manual Published: 2013-07-02 SWD-20130702091645092 Contents Advance preparation...7 Required materials...7 Topics
Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123 Instructor Manual Published: 2013-07-02 SWD-20130702091645092 Contents Advance preparation...7 Required materials...7 Topics
Server Software Installation Guide
 Server Software Installation Guide This guide provides information on...... The architecture model for GO!Enterprise MDM system setup... Hardware and supporting software requirements for GO!Enterprise
Server Software Installation Guide This guide provides information on...... The architecture model for GO!Enterprise MDM system setup... Hardware and supporting software requirements for GO!Enterprise
DEPLOYMENT GUIDE Version 1.0. Deploying the BIG-IP Edge Gateway for Layered Security and Acceleration Services
 DEPLOYMENT GUIDE Version 1.0 Deploying the BIG-IP Edge Gateway for Layered Security and Acceleration Services Table of Contents Table of Contents Using the BIG-IP Edge Gateway for layered security and
DEPLOYMENT GUIDE Version 1.0 Deploying the BIG-IP Edge Gateway for Layered Security and Acceleration Services Table of Contents Table of Contents Using the BIG-IP Edge Gateway for layered security and
Firewall Audit Techniques. K.S.Narayanan HCL Technologies Limited
 Firewall Audit Techniques K.S.Narayanan HCL Technologies Limited Firewall Management Technology Network Security Architecture Firewall Placement Firewall Appliance Rule base compliance with security policy
Firewall Audit Techniques K.S.Narayanan HCL Technologies Limited Firewall Management Technology Network Security Architecture Firewall Placement Firewall Appliance Rule base compliance with security policy
Web Application Hosting Cloud Architecture
 Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
How Your Computer Accesses the Internet through your Wi-Fi for Boats Router
 How Your Computer Accesses the Internet through your Wi-Fi for Boats Router By default, a router blocks any inbound traffic from the Internet to your computers except for replies to your outbound traffic.
How Your Computer Accesses the Internet through your Wi-Fi for Boats Router By default, a router blocks any inbound traffic from the Internet to your computers except for replies to your outbound traffic.
What s New in Media Management v10.5
 What s New in Media Management v10.5 WHITEPAPER Title Here Contents Introduction Media Management v10.5...3 Forrester Wave : Digital Asset Management for Customer Experience, Q4 2014...4 What s New in
What s New in Media Management v10.5 WHITEPAPER Title Here Contents Introduction Media Management v10.5...3 Forrester Wave : Digital Asset Management for Customer Experience, Q4 2014...4 What s New in
www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013
 www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
DMZ Gateways: Secret Weapons for Data Security
 A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security EXECUTIVE
A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security A L I N O M A S O F T W A R E W H I T E P A P E R DMZ Gateways: Secret Weapons for Data Security EXECUTIVE
Placing the BlackBerry Enterprise Server for Microsoft Exchange in a demilitarized zone
 Placing the for Originally posted: June 2002 Affected software versions BlackBerry Enterprise version 2.0 for Microsoft Exchange version 2.1 for Microsoft Exchange version 3.5 for Microsoft Exchange Summary
Placing the for Originally posted: June 2002 Affected software versions BlackBerry Enterprise version 2.0 for Microsoft Exchange version 2.1 for Microsoft Exchange version 3.5 for Microsoft Exchange Summary
Citrix NetScaler and Microsoft SharePoint 2013 Hybrid Deployment Guide
 Citrix NetScaler and Microsoft SharePoint 2013 Hybrid Deployment Guide 2013 Deployment Guide Table of Contents Overview 3 SharePoint Hybrid Deployment Overview 3 Workflow 4 Step by Step Configuration on
Citrix NetScaler and Microsoft SharePoint 2013 Hybrid Deployment Guide 2013 Deployment Guide Table of Contents Overview 3 SharePoint Hybrid Deployment Overview 3 Workflow 4 Step by Step Configuration on
Introduction to Computer Security Benoit Donnet Academic Year 2015-2016
 Introduction to Computer Security Benoit Donnet Academic Year 2015-2016 1 Agenda Networking Chapter 1: Firewalls Chapter 2: Proxy Chapter 3: Intrusion Detection System Chapter 4: Network Attacks Chapter
Introduction to Computer Security Benoit Donnet Academic Year 2015-2016 1 Agenda Networking Chapter 1: Firewalls Chapter 2: Proxy Chapter 3: Intrusion Detection System Chapter 4: Network Attacks Chapter
Preparing for GO!Enterprise MDM On-Demand Service
 Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
Designing and Implementing a Server Infrastructure
 Course 20413C: Designing and Implementing a Server Infrastructure Page 1 of 7 Designing and Implementing a Server Infrastructure Course 20413: 4 days; Instructor-Led Introduction This 4-day instructor-led
Course 20413C: Designing and Implementing a Server Infrastructure Page 1 of 7 Designing and Implementing a Server Infrastructure Course 20413: 4 days; Instructor-Led Introduction This 4-day instructor-led
Optus EmailSMS for MS Outlook and Lotus Notes
 Optus EmailSMS for MS Outlook and Lotus Notes Service Description, August 2005. OVERVIEW This document provides an overview of the Optus EmailSMS service delivered jointly by Optus and redcoal. It highlights
Optus EmailSMS for MS Outlook and Lotus Notes Service Description, August 2005. OVERVIEW This document provides an overview of the Optus EmailSMS service delivered jointly by Optus and redcoal. It highlights
Installing and Configuring vcenter Multi-Hypervisor Manager
 Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
redcoal EmailSMS for MS Outlook and Lotus Notes
 redcoal EmailSMS for MS Outlook and Lotus Notes Technical Support: [email protected] Or visit http://www.redcoal.com/ All Documents prepared or furnished by redcoal Pty Ltd remains the property of redcoal
redcoal EmailSMS for MS Outlook and Lotus Notes Technical Support: [email protected] Or visit http://www.redcoal.com/ All Documents prepared or furnished by redcoal Pty Ltd remains the property of redcoal
SSL VPN Technology White Paper
 SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
A Guide to New Features in Propalms OneGate 4.0
 A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
eprism Email Security Suite
 Guide eprism 2505 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered
Guide eprism 2505 eprism Email Security Suite 800-782-3762 www.edgewave.com 2001 2012 EdgeWave. All rights reserved. The EdgeWave logo is a trademark of EdgeWave Inc. All other trademarks and registered
We will give some overview of firewalls. Figure 1 explains the position of a firewall. Figure 1: A Firewall
 Chapter 10 Firewall Firewalls are devices used to protect a local network from network based security threats while at the same time affording access to the wide area network and the internet. Basically,
Chapter 10 Firewall Firewalls are devices used to protect a local network from network based security threats while at the same time affording access to the wide area network and the internet. Basically,
Kodak Remote Support System - RSS VPN
 Kodak Graphic Communications Canada Company 4225 Kincaid Street Burnaby, B.C., Canada V5G 4P5 Tel: +1.604.451.2700 Fax: +1.604.437.9891 Request support: partnerplace.kodak.com http://graphics.kodak.com
Kodak Graphic Communications Canada Company 4225 Kincaid Street Burnaby, B.C., Canada V5G 4P5 Tel: +1.604.451.2700 Fax: +1.604.437.9891 Request support: partnerplace.kodak.com http://graphics.kodak.com
Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: [email protected]
 Manual Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: [email protected] Information in this document is subject to change without notice. Companies names and data used in examples herein are fictitious
Manual Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: [email protected] Information in this document is subject to change without notice. Companies names and data used in examples herein are fictitious
How to Secure a Groove Manager Web Site
 How to Secure a Groove Manager Web Site Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the companies, organizations,
How to Secure a Groove Manager Web Site Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the companies, organizations,
McAfee Email Gateway 7.x Encryption and IronPort Integration Guide
 Sample deployment architecture For this guide, we have provided a deployment architecture example. This example includes an IronPort Email Gateway sending outbound email, and the McAfee Email Gateway Encryption
Sample deployment architecture For this guide, we have provided a deployment architecture example. This example includes an IronPort Email Gateway sending outbound email, and the McAfee Email Gateway Encryption
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7
 WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
LifeSize Transit Deployment Guide June 2011
 LifeSize Transit Deployment Guide June 2011 LifeSize Tranist Server LifeSize Transit Client LifeSize Transit Deployment Guide 2 Firewall and NAT Traversal with LifeSize Transit Firewalls and Network Address
LifeSize Transit Deployment Guide June 2011 LifeSize Tranist Server LifeSize Transit Client LifeSize Transit Deployment Guide 2 Firewall and NAT Traversal with LifeSize Transit Firewalls and Network Address
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3 April 8, 2016. Integration Guide IBM
 IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3 April 8, 2016 Integration Guide IBM Note Before using this information and the product it supports, read the information
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3 April 8, 2016 Integration Guide IBM Note Before using this information and the product it supports, read the information
Sage HRMS 2012 Sage Employee Self Service. Technical Installation Guide for Windows Server 2003 and Windows Server 2008
 Sage HRMS 2012 Sage Employee Self Service Technical Installation Guide for Windows Server 2003 and Windows Server 2008 2011 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product
Sage HRMS 2012 Sage Employee Self Service Technical Installation Guide for Windows Server 2003 and Windows Server 2008 2011 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product
Data Security and Governance with Enterprise Enabler
 Copyright 2014 Stone Bond Technologies, L.P. All rights reserved. The information contained in this document represents the current view of Stone Bond Technologies on the issue discussed as of the date
Copyright 2014 Stone Bond Technologies, L.P. All rights reserved. The information contained in this document represents the current view of Stone Bond Technologies on the issue discussed as of the date
Microsoft Office Communications Server 2007 & Coyote Point Equalizer Deployment Guide DEPLOYMENT GUIDE
 Microsoft Office Communications Server 2007 & Coyote Point Equalizer DEPLOYMENT GUIDE Table of Contents Unified Communications Application Delivery...2 General Requirements...6 Equalizer Configuration...7
Microsoft Office Communications Server 2007 & Coyote Point Equalizer DEPLOYMENT GUIDE Table of Contents Unified Communications Application Delivery...2 General Requirements...6 Equalizer Configuration...7
BES10 Cloud architecture and data flows
 BES10 Cloud architecture and data flows Architecture: BES10 Cloud solution Component APNs BlackBerry Cloud Connector BES10 Cloud BlackBerry Infrastructure Company directory Devices GCM Other third-party
BES10 Cloud architecture and data flows Architecture: BES10 Cloud solution Component APNs BlackBerry Cloud Connector BES10 Cloud BlackBerry Infrastructure Company directory Devices GCM Other third-party
Server Scalability and High Availability
 Server Scalability and High Availability GO!Enterprise GLOBO Plc. March 2015 Copyright Notice and Usage Terms This guide is Copyright 2012 GLOBO. All Rights Reserved. Permission is granted to make and
Server Scalability and High Availability GO!Enterprise GLOBO Plc. March 2015 Copyright Notice and Usage Terms This guide is Copyright 2012 GLOBO. All Rights Reserved. Permission is granted to make and
Step-by-Step Guide to Setup Instant Messaging (IM) Workspace Datasheet
 Step-by-Step Guide to Setup Instant Messaging (IM) Workspace Datasheet CONTENTS Installation System requirements SQL Server setup Setting up user accounts Authentication mode Account options Import from
Step-by-Step Guide to Setup Instant Messaging (IM) Workspace Datasheet CONTENTS Installation System requirements SQL Server setup Setting up user accounts Authentication mode Account options Import from
How to configure the Panda GateDefender Performa explicit proxy in a Local User Database or in a LDAP server
 How to configure the Panda GateDefender Performa explicit proxy in a Local User Database or in a LDAP server Copyright notice Panda Security 2010. All rights reserved. Neither the documents nor the programs
How to configure the Panda GateDefender Performa explicit proxy in a Local User Database or in a LDAP server Copyright notice Panda Security 2010. All rights reserved. Neither the documents nor the programs
Xerox Multifunction Devices. Network Configuration. Domain 2. Domino Server 2. Notes. MIME to Notes. Port. Domino. Server 1.
 Xerox Multifunction Devices Customer Tips September 17, 2003 NOTE: Information in this document applies to the following multifunction device software levels: WorkCentre Pros - all software levels DC 555/545/535
Xerox Multifunction Devices Customer Tips September 17, 2003 NOTE: Information in this document applies to the following multifunction device software levels: WorkCentre Pros - all software levels DC 555/545/535
Technical White Paper BlackBerry Enterprise Server
 Technical White Paper BlackBerry Enterprise Server BlackBerry Enterprise Edition for Microsoft Exchange For GPRS Networks Research In Motion 1999-2001, Research In Motion Limited. All Rights Reserved Table
Technical White Paper BlackBerry Enterprise Server BlackBerry Enterprise Edition for Microsoft Exchange For GPRS Networks Research In Motion 1999-2001, Research In Motion Limited. All Rights Reserved Table
Mobile Admin Architecture
 Mobile Admin Architecture Introduction Mobile Admin is an enterprise-ready IT Management solution that enables system administrators to monitor and manage their corporate IT infrastructure from a mobile
Mobile Admin Architecture Introduction Mobile Admin is an enterprise-ready IT Management solution that enables system administrators to monitor and manage their corporate IT infrastructure from a mobile
Managing Ports and System Services using BT NetProtect Plus firewall
 Managing Ports and System Services using BT NetProtect Plus firewall To work properly, certain programs (including web servers and file-sharing server programs) must accept unsolicited connections from
Managing Ports and System Services using BT NetProtect Plus firewall To work properly, certain programs (including web servers and file-sharing server programs) must accept unsolicited connections from
Security Overview Introduction Application Firewall Compatibility
 Security Overview Introduction ShowMyPC provides real-time communication services to organizations and a large number of corporations. These corporations use ShowMyPC services for diverse purposes ranging
Security Overview Introduction ShowMyPC provides real-time communication services to organizations and a large number of corporations. These corporations use ShowMyPC services for diverse purposes ranging
CORE Enterprise on a WAN
 CORE Enterprise on a WAN CORE Product and Process Engineering Solutions Copyright 2006-2007 Vitech Corporation. All rights reserved. No part of this document may be reproduced in any form, including, but
CORE Enterprise on a WAN CORE Product and Process Engineering Solutions Copyright 2006-2007 Vitech Corporation. All rights reserved. No part of this document may be reproduced in any form, including, but
8.7. NET SatisFAXtion Email Gateway Installation Guide. For NET SatisFAXtion 8.7. Contents
 NET SatisFAXtion Email Gateway Installation Guide For NET SatisFAXtion 8.7 Contents Install Microsoft Virtual SMTP Server 2 XP and 2003 2 2008 and 2008 R2 2 Windows 7 2 Upgrade Path 2 Configure Microsoft
NET SatisFAXtion Email Gateway Installation Guide For NET SatisFAXtion 8.7 Contents Install Microsoft Virtual SMTP Server 2 XP and 2003 2 2008 and 2008 R2 2 Windows 7 2 Upgrade Path 2 Configure Microsoft
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Xerox Digital Alternatives Security and Evaluation Guide. May 2015 Version 1.1
 Xerox Digital Alternatives Security and Evaluation Guide May 2015 Version 1.1 2015 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, and CompleteView are trademarks of Xerox Corporation
Xerox Digital Alternatives Security and Evaluation Guide May 2015 Version 1.1 2015 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, and CompleteView are trademarks of Xerox Corporation
Deployment Guide Sept-2014 rev. a. Load Balancing Windows Terminal Server with Session Directory Using Array APV Series ADCs
 Deployment Guide Sept-2014 rev. a Load Balancing Windows Terminal Server with Session Directory Using Array APV Series ADCs Table of Contents 1 Introduction... 2 1.1 Connecting to a Terminal Server Farm...
Deployment Guide Sept-2014 rev. a Load Balancing Windows Terminal Server with Session Directory Using Array APV Series ADCs Table of Contents 1 Introduction... 2 1.1 Connecting to a Terminal Server Farm...
Monitoring Nginx Server
 Monitoring Nginx Server eg Enterprise v6 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced
Monitoring Nginx Server eg Enterprise v6 Restricted Rights Legend The information contained in this document is confidential and subject to change without notice. No part of this document may be reproduced
Dell One Identity Cloud Access Manager 7.0.2. Installation Guide
 Dell One Identity Cloud Access Manager 7.0.2 2014 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under
Dell One Identity Cloud Access Manager 7.0.2 2014 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under
Filr 2.0 Administration Guide. April 2016
 Filr 2.0 Administration Guide April 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy,
Filr 2.0 Administration Guide April 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights, patent policy,
Securing access to Citrix applications using Citrix Secure Gateway and SafeWord. PremierAccess. App Note. December 2001
 Securing access to Citrix applications using Citrix Secure Gateway and SafeWord PremierAccess App Note December 2001 DISCLAIMER: This White Paper contains Secure Computing Corporation product performance
Securing access to Citrix applications using Citrix Secure Gateway and SafeWord PremierAccess App Note December 2001 DISCLAIMER: This White Paper contains Secure Computing Corporation product performance
Network Configuration/Bandwidth Planning Scope
 Network Configuration/Bandwidth Planning Scope Workshop Focus and Objective Workshop Focus Drive key planning considerations for Office 365 domain and domain name service (DNS) records configuration Network
Network Configuration/Bandwidth Planning Scope Workshop Focus and Objective Workshop Focus Drive key planning considerations for Office 365 domain and domain name service (DNS) records configuration Network
How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface
 How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface How To Configure load sharing and redirect mail server traffic over preferred Gateway
How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface How To Configure load sharing and redirect mail server traffic over preferred Gateway
Module 6. Designing and Deploying External Access. MVA Jump Start
 Module 6 Designing and Deploying External Access MVA Jump Start Module Overview Conferencing and External Capabilities of Lync Server 2013 Planning for IM and Presence Federation Designing Edge Services
Module 6 Designing and Deploying External Access MVA Jump Start Module Overview Conferencing and External Capabilities of Lync Server 2013 Planning for IM and Presence Federation Designing Edge Services
Choosing a Fax Solution Deployment Model
 Choosing a Fax Solution There is a lot of talk in the marketplace about enterprise software deployment models: on-premises, cloud, hybrid, managed/hosted. The conversation is an important one for every
Choosing a Fax Solution There is a lot of talk in the marketplace about enterprise software deployment models: on-premises, cloud, hybrid, managed/hosted. The conversation is an important one for every
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
GFI MailSecurity deployment strategies
 GFI White Paper GFI MailSecurity deployment strategies Which operating mode(s) to use in your network environment GFI MailSecurity can be deployed as an SMTP gateway or as a VS API version for Microsoft
GFI White Paper GFI MailSecurity deployment strategies Which operating mode(s) to use in your network environment GFI MailSecurity can be deployed as an SMTP gateway or as a VS API version for Microsoft
