CIS 523/423 Disaster Recovery Business Continuity
|
|
|
- Justina Montgomery
- 10 years ago
- Views:
Transcription
1 CIS 523/423 Disaster Recovery Business Continuity Course Description A study of disaster recovery and business continuity as related to the information technology function in organizations. Topics will include (but not limited to) security risk evaluation and management, creation of threat profiles, continuity of operations planning, contingency planning, and incident reporting. Text Course Objectives Guide to Disaster Recovery, Michael Erbschloe, Thomson Course Technology. ISBN To provide theoretical knowledge and background about the key issues relating to disaster recovery and business continuity as related to information systems. This will be done through case analyses, research and the study of current and emerging techniques and technologies. Course Learning Objective: Create a notification directory. Understand what is involved in getting management support. Describe and understand the process involved in securing resources. Explain how to prepare your resources. Define the risks that may impact your organization. Investigate different risk assessments and business impact assessments. Set priorities for preventive measures and the recovery from any disaster situation. Choose a risk assessment method to be used to identify and quantify risk in an organization. Perform risk assessments as they might pertain to an organization. Use tools such as OCTAVE to assist in risk assessment. Identify all assets and functions in the organization. Prioritize disaster recovery efforts based on assets and functions. Differentiate between tier 1, tier 2, and tier 3 recovery targets to prioritize systems that must be recovered in the event of a disaster. Determine dependencies between different data, functions, and assets. Distinguish between an inconvenient situation and a true disaster using disaster declaration threshold criteria. Determine the best way or ways to back up your data so that it can be recovered later. Evaluate your off-site storage options. Acknowledge information as well as hardware and software as an asset. Determine recovery site options. Examine recovery site types. Develop recovery site selection criteria. Outline a recovery solution. Determine what documents and contact information is necessary to support the disaster recovery effort. Choose the tools necessary to support the disaster recovery effort. Determine the best way to direct the disaster recovery team. Choose a backup strategy that will allow you to meet your recovery objectives. Describe how upstream vendors can affect your organization s ability to do work. Understand how your organization can affect downstream clients ability to do their jobs. Describe how the organization s SLA impacts not only itself, but also its downstream partners.
2 Begin to pull together the recovery documentation. Identify emergency situations that may occur during a recovery. Determine what can be done if an emergency occurs during an emergency situation. Assess the risks associated with disaster recovery. Identify gaps in emergency recovery situations and plan accordingly. Explain the necessity of practicing the DR plan. Describe the different kinds of tests that can be performed. Explain reasons for testing. Determine the impact of testing activities. Understand the need for change control. Describe methods of change control. Determine the lessons that were learned during the test disaster recovery. Decide how to overcome the threats that were uncovered. Use SWOT (strengths, weaknesses, opportunities, threats) analysis as an additional method of determining threats. Plan for eliminating threats going forward. Grading Criteria Assignment Pct. Article Presentations 5% Mid-term Exam 25% Final Exam 25% Paper/Presentation 10% Group Disaster Recovery Plan Project 25% Class Contribution & Participation Total 10% 100% Class contribution & participation includes amount and quality of participation in case, chapters, articles and class discussions. Quality and quantity of participation is important. You can t participate if you are not present! Articles Students must present two (2) high quality articles that complement class material. You must present one (1) articles before the midterm exam. This will be a short formal presentation made to the class. Expect presentations to be about 3-5 minutes in length. A written summary on the article is be to handed in with a photocopy of the first page of the article. All written work must be done on a word processor. It shoud be double spaced, have 1 inch margins, be a 12 pitch easy to read font. Written work will be graded on content and presentation (i.e., grammar, spelling, organization, etc.). Late work is NOT accepted without prior approval. Paper Students must write and present a 5-6 page paper on a topic of interest to Disaster Recovery or Business Continuity. It could be a case study paper and presentation. Disaster Recovery Plan Student groups will develop a disaster recovery plan for a local business. This is a quarter long project where students will assess risks and needs for the organization if a disaster would occur. Business continuity will be included in the project.
3 Tentative Schedule Week 1 Introduction Module 1 Erbschloe Chapter 1` 1.1 Disaster Recovery Philosophy 1.2 Principles of Disaster Recovery Planning 1.3 Contingency Plan Components 1.4 Agency Response Procedures and Continuity of Operations 1.5 Planning Processes 1.6 Continuity and Recovery Function 1.7 Steps of Disaster Recovery Planning 1.8 Role of IT and Network Management in Disaster Recovery Week 2 Module 2 Erbschloe Chapter Developing the Disaster Recovery Plan 2.2 Development of Plans for Recovery Actions After a Disruptive Event 2.3 Executive Support 2.4 DRP Leadership 2.5 Cross Department Subcommittee 2.6 Department Level Teams 2.7 Relationship between IT and Network Staff with Departments 2.8 Planning Team Skill Inventory 2.9 DRP Team Training 2.10 DRP Awareness Campaign 2.11 Standards and Regulatory Bodies Week 3 Module 3 Erbschloe Chapter Assessing Organizational Risk 3.2 Documenting Business Processes 3.3 Business Process Inventory 3.4 Identifying Threats and Vulnerabilities 3.5 Measuring and Quantifying Threats 3.6 Risk Reports Week 4 Module 4 Erbschloe Chapter Prioritizing systems and Functions for Recovery 4.2 Classifying Systems 4.3 Determination of Backup Requirements
4 4.4 Emergency Destruction Procedures 4.5 Responsibility Charts 4.6 Guidelines for Determining Critical and Essential Workload 4.7 Team Member Responsibilities in Responding to an Emergency Situation 4.8 Insurance Coverage Requirements Week 5 Midterm Exam Module 5 Erbschloe Chapter Developing Plans and Procedures 5.2 Facility Index 5.3 DRP Staff 5.4 Disaster Classification 5.5 Direction, Control, and Administrative Procedures 5.6 Safety and Health Procedures 5.7 Internal and External Communication Procedures 5.8 Containment and Property Protection 5.9 Resuming and Recovering Operations 5.10 Restoring Facilities and Normalizing Operations 5.11 Development of Procedures for Off-Site Processing Week 6 Module 6 Erbschloe Chapter Disaster Recovery Relationships 6.2 DRP Partnerships 6.3 Public Service Providers 6.4 Insurance Providers 6.5 Private Service Providers 6.6 Business Arena (Partners, suppliers, customers) 6.7 Media 6.8 Stakeholders Week 7 Module 7 Erbschloe Chapter Computer Attack Procedures 7.2 Cyber attacks 7.3 Privacy Laws 7.4 Types of Attacks 7.5 Security Breach Procedures
5 7.6 Working with Law Enforcement 7.7 Economic Losses 7.8 IT Recovery Procedures (network and systems) 7.9 Computer Incident Response Team Week 8 Module 8 Erbschloe Chapter Special Circumstance Procedures 8.2 Hazardous Materials 8.3 Art 8.4 Historic Documents 8.5 Perishables 8.6 Controlled Substances 8.7 Trade Secrets 8.8 Animals 8.9 Precision Equipment 8.10 Rare Materials Week 9 Module 9 Erbschloe Chapter Implementing DRP 9.2 Implementation Plans 9.3 Assigning Responsibilities 9.4 Set Schedule 9.5 DRP Implementation Documentation 9.6 Internal and External Awareness Program 9.7 Training Program Week 10 Module 10 Erbschloe Chapter Testing and Rehearsal 10.2 Testing Process 10.3 Test Scenarios 10.4 Testing Subunits 10.5 Measuring Effectiveness 10.6 Assessment Process 10.7 Using the Plan in a disaster Final Exam Group Project Due
Summer 2014 3 Credit Hours
 College of Hospitality and Technology Leadership CIS 4365 Computer Security Policies & Disaster Preparedness Summer 2014 3 Credit Hours University of South Florida Sarasota/Manatee 8350 North Tamiami Trail,
College of Hospitality and Technology Leadership CIS 4365 Computer Security Policies & Disaster Preparedness Summer 2014 3 Credit Hours University of South Florida Sarasota/Manatee 8350 North Tamiami Trail,
State Agency Cyber Security Survey v 3.4 2 October 2014. State Agency Cybersecurity Survey v 3.4
 State Agency Cybersecurity Survey v 3.4 The purpose of this survey is to identify your agencies current capabilities with respect to information systems/cyber security and any challenges and/or successes
State Agency Cybersecurity Survey v 3.4 The purpose of this survey is to identify your agencies current capabilities with respect to information systems/cyber security and any challenges and/or successes
Continuity of Operations Planning. A step by step guide for business
 What is a COOP? Continuity of Operations Planning A step by step guide for business A Continuity Of Operations Plan (COOP) is a MANAGEMENT APPROVED set of agreed-to preparations and sufficient procedures
What is a COOP? Continuity of Operations Planning A step by step guide for business A Continuity Of Operations Plan (COOP) is a MANAGEMENT APPROVED set of agreed-to preparations and sufficient procedures
Attachment to Data Center Services Multisourcing Service Integrator Master Services Agreement
 Attachment to Data Center Services Multisourcing Service Integrator Master Services Agreement DIR Contract No. DIR-DCS-MSI-MSA-001 Between The State of Texas, acting by and through the Texas Department
Attachment to Data Center Services Multisourcing Service Integrator Master Services Agreement DIR Contract No. DIR-DCS-MSI-MSA-001 Between The State of Texas, acting by and through the Texas Department
Overview of how to test a. Business Continuity Plan
 Overview of how to test a Business Continuity Plan Prepared by: Thomas Bronack Phone: (718) 591-5553 Email: [email protected] BRP/DRP Test Plan Creation and Exercise Page: 1 Table of Contents BCP/DRP Test
Overview of how to test a Business Continuity Plan Prepared by: Thomas Bronack Phone: (718) 591-5553 Email: [email protected] BRP/DRP Test Plan Creation and Exercise Page: 1 Table of Contents BCP/DRP Test
CISM Certified Information Security Manager
 CISM Certified Information Security Manager Firebrand Custom Designed Courseware Chapter 4 Information Security Incident Management Exam Relevance Ensure that the CISM candidate Establish an effective
CISM Certified Information Security Manager Firebrand Custom Designed Courseware Chapter 4 Information Security Incident Management Exam Relevance Ensure that the CISM candidate Establish an effective
Success or Failure? Your Keys to Business Continuity Planning. An Ingenuity Whitepaper
 Success or Failure? Your Keys to Business Continuity Planning An Ingenuity Whitepaper May 2006 Overview With the level of uncertainty in our world regarding events that can disrupt the operation of an
Success or Failure? Your Keys to Business Continuity Planning An Ingenuity Whitepaper May 2006 Overview With the level of uncertainty in our world regarding events that can disrupt the operation of an
Technology Recovery Plan Instructions
 State of California California Information Security Office Technology Recovery Plan Instructions SIMM 5325-A (Formerly SIMM 65A) September 2013 REVISION HISTORY REVISION DATE OF RELEASE OWNER SUMMARY OF
State of California California Information Security Office Technology Recovery Plan Instructions SIMM 5325-A (Formerly SIMM 65A) September 2013 REVISION HISTORY REVISION DATE OF RELEASE OWNER SUMMARY OF
Business Unit CONTINGENCY PLAN
 Contingency Plan Template Business Unit CONTINGENCY PLAN Version 1.0 (Date submitted) Submitted By: Business Unit Date Version 1.0 Page 1 1 Plan Review and Updates... 3 2 Introduction... 3 2.1 Purpose...
Contingency Plan Template Business Unit CONTINGENCY PLAN Version 1.0 (Date submitted) Submitted By: Business Unit Date Version 1.0 Page 1 1 Plan Review and Updates... 3 2 Introduction... 3 2.1 Purpose...
Ohio Supercomputer Center
 Ohio Supercomputer Center IT Business Continuity Planning No: Effective: OSC-13 06/02/2009 Issued By: Kevin Wohlever Director of Supercomputer Operations Published By: Ohio Supercomputer Center Original
Ohio Supercomputer Center IT Business Continuity Planning No: Effective: OSC-13 06/02/2009 Issued By: Kevin Wohlever Director of Supercomputer Operations Published By: Ohio Supercomputer Center Original
Business Continuity Planning for Risk Reduction
 Business Continuity Planning for Risk Reduction Ion PLUMB [email protected] Andreea ZAMFIR [email protected] Delia TUDOR [email protected] Faculty of Management Academy of Economic Studies
Business Continuity Planning for Risk Reduction Ion PLUMB [email protected] Andreea ZAMFIR [email protected] Delia TUDOR [email protected] Faculty of Management Academy of Economic Studies
Virginia Commonwealth University School of Medicine Information Security Standard
 Virginia Commonwealth University School of Medicine Information Security Standard Title: Scope: Business Continuity Management Standard for IT Systems This standard is applicable to all VCU School of Medicine
Virginia Commonwealth University School of Medicine Information Security Standard Title: Scope: Business Continuity Management Standard for IT Systems This standard is applicable to all VCU School of Medicine
Business Continuity Plan
 Business Continuity Plan October 2007 Agenda Business continuity plan definition Evolution of the business continuity plan Business continuity plan life cycle FFIEC & Business continuity plan Questions
Business Continuity Plan October 2007 Agenda Business continuity plan definition Evolution of the business continuity plan Business continuity plan life cycle FFIEC & Business continuity plan Questions
FINRMFS9 Facilitate Business Continuity Planning and disaster recovery for a financial services organisation
 Facilitate Business Continuity Planning and disaster recovery for a Overview This unit is suitable for those working in risk management roles who have responsibility for facilitating business continuity
Facilitate Business Continuity Planning and disaster recovery for a Overview This unit is suitable for those working in risk management roles who have responsibility for facilitating business continuity
How to Plan for Disaster Recovery and Business Continuity
 A TAMP Systems White Paper TAMP Systems 1-516-623-2038 www.drsbytamp.com How to Plan for Disaster Recovery and Business Continuity By Tom Abruzzo, President and CEO Contents Introduction 1 Definitions
A TAMP Systems White Paper TAMP Systems 1-516-623-2038 www.drsbytamp.com How to Plan for Disaster Recovery and Business Continuity By Tom Abruzzo, President and CEO Contents Introduction 1 Definitions
Information Technology Engineers Examination. Information Technology Service Manager Examination. (Level 4) Syllabus
 Information Technology Engineers Examination Information Technology Service Manager Examination (Level 4) Syllabus Details of Knowledge and Skills Required for the Information Technology Engineers Examination
Information Technology Engineers Examination Information Technology Service Manager Examination (Level 4) Syllabus Details of Knowledge and Skills Required for the Information Technology Engineers Examination
Why Should Companies Take a Closer Look at Business Continuity Planning?
 whitepaper Why Should Companies Take a Closer Look at Business Continuity Planning? How Datalink s business continuity and disaster recovery solutions can help organizations lessen the impact of disasters
whitepaper Why Should Companies Take a Closer Look at Business Continuity Planning? How Datalink s business continuity and disaster recovery solutions can help organizations lessen the impact of disasters
PAPER-6 PART-1 OF 5 CA A.RAFEQ, FCA
 1 Chapter-4: Business Continuity Planning and Disaster Recovery Planning PAPER-6 PART-1 OF 5 CA A.RAFEQ, FCA Learning Objectives 2 To understand the concept of Business Continuity Management To understand
1 Chapter-4: Business Continuity Planning and Disaster Recovery Planning PAPER-6 PART-1 OF 5 CA A.RAFEQ, FCA Learning Objectives 2 To understand the concept of Business Continuity Management To understand
DRAFT Disaster Recovery Policy Template
 DRAFT Disaster Recovery Policy Template NOTE: This is a boiler plate template much information is needed from to finalizeconsider this document pre-draft FOREWARD... 3 Policy Overview...
DRAFT Disaster Recovery Policy Template NOTE: This is a boiler plate template much information is needed from to finalizeconsider this document pre-draft FOREWARD... 3 Policy Overview...
Flinders University IT Disaster Recovery Framework
 Flinders University IT Disaster Recovery Framework Establishment: Flinders University, 1 August 2013 Last Amended: Manager, ITS Security Services, 4 October 2013 Nature of Amendment: Initial release Date
Flinders University IT Disaster Recovery Framework Establishment: Flinders University, 1 August 2013 Last Amended: Manager, ITS Security Services, 4 October 2013 Nature of Amendment: Initial release Date
NEEDS BASED PLANNING FOR IT DISASTER RECOVERY
 The Define/Align/Approve Reference Series NEEDS BASED PLANNING FOR IT DISASTER RECOVERY Disaster recovery planning is essential it s also expensive. That s why every step taken and dollar spent must be
The Define/Align/Approve Reference Series NEEDS BASED PLANNING FOR IT DISASTER RECOVERY Disaster recovery planning is essential it s also expensive. That s why every step taken and dollar spent must be
Q uick Guide to Disaster Recovery Planning An ITtoolkit.com White Paper
 This quick reference guide provides an introductory overview of the key principles and issues involved in IT related disaster recovery planning, including needs evaluation, goals, objectives and related
This quick reference guide provides an introductory overview of the key principles and issues involved in IT related disaster recovery planning, including needs evaluation, goals, objectives and related
Post-Class Quiz: Business Continuity & Disaster Recovery Planning Domain
 1. What is the most common planned performance duration for a continuity of operations plan (COOP)? A. 30 days B. 60 days C. 90 days D. It depends on the severity of a disaster. 2. What is the business
1. What is the most common planned performance duration for a continuity of operations plan (COOP)? A. 30 days B. 60 days C. 90 days D. It depends on the severity of a disaster. 2. What is the business
External Supplier Control Requirements BCM
 External Supplier Control Requirements BCM BCM Requirement Description BCM Tiers Recovery Time Objective Why this is important 1. Business Continuity Policy Supplier will have a documented Business Continuity
External Supplier Control Requirements BCM BCM Requirement Description BCM Tiers Recovery Time Objective Why this is important 1. Business Continuity Policy Supplier will have a documented Business Continuity
IT Disaster Recovery Plan Template
 HOPONE INTERNET CORP IT Disaster Recovery Plan Template Compliments of: Tim Sexton 1/1/2015 An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned
HOPONE INTERNET CORP IT Disaster Recovery Plan Template Compliments of: Tim Sexton 1/1/2015 An information technology (IT) disaster recovery (DR) plan provides a structured approach for responding to unplanned
<Client Name> IT Disaster Recovery Plan Template. By Paul Kirvan, CISA, CISSP, FBCI, CBCP
 IT Disaster Recovery Plan Template By Paul Kirvan, CISA, CISSP, FBCI, CBCP Revision History REVISION DATE NAME DESCRIPTION Original 1.0 2 Table of Contents Information Technology Statement
IT Disaster Recovery Plan Template By Paul Kirvan, CISA, CISSP, FBCI, CBCP Revision History REVISION DATE NAME DESCRIPTION Original 1.0 2 Table of Contents Information Technology Statement
Network Security: Policies and Guidelines for Effective Network Management
 Network Security: Policies and Guidelines for Effective Network Management Department of Electrical and Computer Engineering, Federal University of Technology, Minna, Nigeria. [email protected], [email protected]
Network Security: Policies and Guidelines for Effective Network Management Department of Electrical and Computer Engineering, Federal University of Technology, Minna, Nigeria. [email protected], [email protected]
SECTION 15 INFORMATION TECHNOLOGY
 SECTION 15 INFORMATION TECHNOLOGY 15.1 Purpose 15.2 Authorization 15.3 Internal Controls 15.4 Computer Resources 15.5 Network/Systems Access 15.6 Disaster Recovery Plan (DRP) 15.1 PURPOSE The Navajo County
SECTION 15 INFORMATION TECHNOLOGY 15.1 Purpose 15.2 Authorization 15.3 Internal Controls 15.4 Computer Resources 15.5 Network/Systems Access 15.6 Disaster Recovery Plan (DRP) 15.1 PURPOSE The Navajo County
Cybersecurity Framework Security Policy Mapping Table
 Cybersecurity Framework Security Policy Mapping Table The following table illustrates how specific requirements of the US Cybersecurity Framework [1] are addressed by the ISO 27002 standard and covered
Cybersecurity Framework Security Policy Mapping Table The following table illustrates how specific requirements of the US Cybersecurity Framework [1] are addressed by the ISO 27002 standard and covered
Table of Contents... 1
 ... 1 Chapter 1 Introduction... 4 1.1 Executive Summary... 4 1.2 Goals and Objectives... 5 1.3 Senior Management and Board of Directors Responsibilities... 5 1.4 Business Continuity Planning Processes...
... 1 Chapter 1 Introduction... 4 1.1 Executive Summary... 4 1.2 Goals and Objectives... 5 1.3 Senior Management and Board of Directors Responsibilities... 5 1.4 Business Continuity Planning Processes...
Disaster Recovery Plan Documentation for Agencies Instructions
 California Office of Information Security Disaster Recovery Plan Documentation for Agencies Instructions () November 2009 SCOPE AND PURPOSE The requirements included in this document are applicable to
California Office of Information Security Disaster Recovery Plan Documentation for Agencies Instructions () November 2009 SCOPE AND PURPOSE The requirements included in this document are applicable to
State of South Carolina Policy Guidance and Training
 State of South Carolina Policy Guidance and Training Policy Workshop All Agencies Business Continuity Management Policy June 2014 Agenda Questions & Follow-Up Policy Workshop Overview & Timeline Policy
State of South Carolina Policy Guidance and Training Policy Workshop All Agencies Business Continuity Management Policy June 2014 Agenda Questions & Follow-Up Policy Workshop Overview & Timeline Policy
Running head: COMPONENTS OF A DISASTER RECOVERY PLAN 1
 Running head: COMPONENTS OF A DISASTER RECOVERY PLAN 1 Components of a Disaster Recovery Plan DeVry Institute of Technology 2 Components of a Disaster Recovery Plan Disasters do strike without warning.
Running head: COMPONENTS OF A DISASTER RECOVERY PLAN 1 Components of a Disaster Recovery Plan DeVry Institute of Technology 2 Components of a Disaster Recovery Plan Disasters do strike without warning.
Department of Information Technology Data Center Disaster Recovery Audit Report Final Report. September 2006
 Department of Information Technology Data Center Disaster Recovery Audit Report Final Report September 2006 promoting efficient & effective local government Executive Summary Our audit found that a comprehensive
Department of Information Technology Data Center Disaster Recovery Audit Report Final Report September 2006 promoting efficient & effective local government Executive Summary Our audit found that a comprehensive
STEP-BY-STEP BUSINESS CONTINUITY AND EMERGENCY PLANNING MAY 27 2015
 STEP-BY-STEP BUSINESS CONTINUITY AND EMERGENCY PLANNING MAY 27 2015 AGENDA: Emergency Management Business Continuity Planning Q & A MONTH DAY, YEAR TITLE OF THE PRESENTATION 2 CANADIAN RED CROSS Disaster
STEP-BY-STEP BUSINESS CONTINUITY AND EMERGENCY PLANNING MAY 27 2015 AGENDA: Emergency Management Business Continuity Planning Q & A MONTH DAY, YEAR TITLE OF THE PRESENTATION 2 CANADIAN RED CROSS Disaster
Creating a Business Continuity Plan for your Health Center
 Creating a Business Continuity Plan for your Health Center 1 Page Left Intentionally Blank 2 About This Manual This tool is the result of collaboration between the Primary Care Development Corporation
Creating a Business Continuity Plan for your Health Center 1 Page Left Intentionally Blank 2 About This Manual This tool is the result of collaboration between the Primary Care Development Corporation
Disaster Preparedness & Response
 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 A B C E INTRODUCTION AND PURPOSE REVIEW ELEMENTS ABBREVIATIONS NCUA REFERENCES EXTERNAL REFERENCES Planning - Ensuring
3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 A B C E INTRODUCTION AND PURPOSE REVIEW ELEMENTS ABBREVIATIONS NCUA REFERENCES EXTERNAL REFERENCES Planning - Ensuring
Vendor Management. Outsourcing Technology Services
 Vendor Management Outsourcing Technology Services Objectives Board and Senior Management Responsibilities Risk Management Program Risk Assessment Service Provider Selection Contracts Ongoing Monitoring
Vendor Management Outsourcing Technology Services Objectives Board and Senior Management Responsibilities Risk Management Program Risk Assessment Service Provider Selection Contracts Ongoing Monitoring
The CIPM certification is comprised of two domains: Privacy Program Governance (I) and Privacy Program Operational Life Cycle (II).
 Page 1 of 7 The CIPM certification is comprised of two domains: Privacy Program Governance (I) and Privacy Program Operational Life Cycle (II). Domain I provides a solid foundation for the governance of
Page 1 of 7 The CIPM certification is comprised of two domains: Privacy Program Governance (I) and Privacy Program Operational Life Cycle (II). Domain I provides a solid foundation for the governance of
Disaster Recovery Checklist Disaster Recovery Plan for <System One>
 Disaster Recovery Plan for SYSTEM OVERVIEW PRODUCTION SERVER HOT SITE SERVER APPLICATIONS (Use bold for Hot Site) ASSOCIATED SERVERS KEY CONTACTS Hardware Vendor System Owners Database Owner
Disaster Recovery Plan for SYSTEM OVERVIEW PRODUCTION SERVER HOT SITE SERVER APPLICATIONS (Use bold for Hot Site) ASSOCIATED SERVERS KEY CONTACTS Hardware Vendor System Owners Database Owner
EMERGENCY PREPAREDNESS PLAN Business Continuity Plan
 EMERGENCY PREPAREDNESS PLAN Business Continuity Plan GIS Bankers Insurance Group Powered by DISASTER PREPAREDNESS Implementation Small Business Guide to Business Continuity Planning Surviving a Catastrophic
EMERGENCY PREPAREDNESS PLAN Business Continuity Plan GIS Bankers Insurance Group Powered by DISASTER PREPAREDNESS Implementation Small Business Guide to Business Continuity Planning Surviving a Catastrophic
Overview TECHIS60851. Manage information security business resilience activities
 Overview Information security business resilience encompasses business continuity and disaster recovery from information security threats. As well as addressing the consequences of a major security incident,
Overview Information security business resilience encompasses business continuity and disaster recovery from information security threats. As well as addressing the consequences of a major security incident,
Disaster Recovery Planning Process
 Disaster Recovery Planning Process By Geoffrey H. Wold Part I of III This is the first of a three-part series that describes the planning process related to disaster recovery. Based on the various considerations
Disaster Recovery Planning Process By Geoffrey H. Wold Part I of III This is the first of a three-part series that describes the planning process related to disaster recovery. Based on the various considerations
INFORMATION SECURITY GOVERNANCE ASSESSMENT TOOL FOR HIGHER EDUCATION
 INFORMATION SECURITY GOVERNANCE ASSESSMENT TOOL FOR HIGHER EDUCATION Information security is a critical issue for institutions of higher education (IHE). IHE face issues of risk, liability, business continuity,
INFORMATION SECURITY GOVERNANCE ASSESSMENT TOOL FOR HIGHER EDUCATION Information security is a critical issue for institutions of higher education (IHE). IHE face issues of risk, liability, business continuity,
Supplier Security Assessment Questionnaire
 HALKYN CONSULTING LTD Supplier Security Assessment Questionnaire Security Self-Assessment and Reporting This questionnaire is provided to assist organisations in conducting supplier security assessments.
HALKYN CONSULTING LTD Supplier Security Assessment Questionnaire Security Self-Assessment and Reporting This questionnaire is provided to assist organisations in conducting supplier security assessments.
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0
 Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies Effective Date: October 1, 2015 Version 1.0 Unless otherwise stated, these Oracle Maps Cloud Service Enterprise Hosting and Delivery Policies
CENTRAL BANK OF KENYA (CBK) PRUDENTIAL GUIDELINE ON BUSINESS CONTINUITY MANAGEMENT (BCM) FOR INSTITUTIONS LICENSED UNDER THE BANKING ACT
 CENTRAL BANK OF KENYA (CBK) PRUDENTIAL GUIDELINE ON BUSINESS CONTINUITY MANAGEMENT (BCM) FOR INSTITUTIONS LICENSED UNDER THE BANKING ACT JANUARY 2008 GUIDELINE ON BUSINESS CONTINUITY GUIDELINE CBK/PG/14
CENTRAL BANK OF KENYA (CBK) PRUDENTIAL GUIDELINE ON BUSINESS CONTINUITY MANAGEMENT (BCM) FOR INSTITUTIONS LICENSED UNDER THE BANKING ACT JANUARY 2008 GUIDELINE ON BUSINESS CONTINUITY GUIDELINE CBK/PG/14
How to measure your business resiliency
 How to measure your business resiliency Define the KPI s/kri s and scorecards to control your security and business continuity capabilities Krzysztof Pulkiewicz BCMLogic [email protected]
How to measure your business resiliency Define the KPI s/kri s and scorecards to control your security and business continuity capabilities Krzysztof Pulkiewicz BCMLogic [email protected]
Information Shield Solution Matrix for CIP Security Standards
 Information Shield Solution Matrix for CIP Security Standards The following table illustrates how specific topic categories within ISO 27002 map to the cyber security requirements of the Mandatory Reliability
Information Shield Solution Matrix for CIP Security Standards The following table illustrates how specific topic categories within ISO 27002 map to the cyber security requirements of the Mandatory Reliability
CISM ITEM DEVELOPMENT GUIDE
 CISM ITEM DEVELOPMENT GUIDE Updated January 2015 TABLE OF CONTENTS Content Page Purpose of the CISM Item Development Guide 3 CISM Exam Structure 3 Writing Quality Items 3 Multiple-Choice Items 4 Steps
CISM ITEM DEVELOPMENT GUIDE Updated January 2015 TABLE OF CONTENTS Content Page Purpose of the CISM Item Development Guide 3 CISM Exam Structure 3 Writing Quality Items 3 Multiple-Choice Items 4 Steps
Domain 1 The Process of Auditing Information Systems
 Certified Information Systems Auditor (CISA ) Certification Course Description Our 5-day ISACA Certified Information Systems Auditor (CISA) training course equips information professionals with the knowledge
Certified Information Systems Auditor (CISA ) Certification Course Description Our 5-day ISACA Certified Information Systems Auditor (CISA) training course equips information professionals with the knowledge
Office of Inspector General
 DEPARTMENT OF HOMELAND SECURITY Office of Inspector General Security Weaknesses Increase Risks to Critical United States Secret Service Database (Redacted) Notice: The Department of Homeland Security,
DEPARTMENT OF HOMELAND SECURITY Office of Inspector General Security Weaknesses Increase Risks to Critical United States Secret Service Database (Redacted) Notice: The Department of Homeland Security,
Disaster Recovery Policy
 Disaster Recovery Policy INTRODUCTION This policy provides a framework for the ongoing process of planning, developing and implementing disaster recovery management for IT Services at UCD. A disaster is
Disaster Recovery Policy INTRODUCTION This policy provides a framework for the ongoing process of planning, developing and implementing disaster recovery management for IT Services at UCD. A disaster is
With the large number of. How to Avoid Disaster: RIM s Crucial Role in Business Continuity Planning. Virginia A. Jones, CRM, FAI RIM FUNDAMENTALS
 How to Avoid Disaster: RIM s Crucial Role in Business Continuity Planning The world has experienced a great deal of natural and man-made upheaval and destruction in the past few years, including tornadoes,
How to Avoid Disaster: RIM s Crucial Role in Business Continuity Planning The world has experienced a great deal of natural and man-made upheaval and destruction in the past few years, including tornadoes,
Offsite Disaster Recovery Plan
 1 Offsite Disaster Recovery Plan Offsite Disaster Recovery Plan Presented By: Natan Verkhovsky President Disty Portal Inc. 2 Offsite Disaster Recovery Plan Introduction This document is a comprehensive
1 Offsite Disaster Recovery Plan Offsite Disaster Recovery Plan Presented By: Natan Verkhovsky President Disty Portal Inc. 2 Offsite Disaster Recovery Plan Introduction This document is a comprehensive
University of Michigan Disaster Recovery / Business Continuity Administrative Information Systems 4/6/2004 1
 University of Michigan Disaster Recovery / Business Continuity Administrative Information Systems. 1 Michigan Administrative Information Services (MAIS) MAIS is responsible for the production support of
University of Michigan Disaster Recovery / Business Continuity Administrative Information Systems. 1 Michigan Administrative Information Services (MAIS) MAIS is responsible for the production support of
Unit Guide to Business Continuity/Resumption Planning
 Unit Guide to Business Continuity/Resumption Planning (February 2009) Revised June 2011 Executive Summary... 3 Purpose and Scope for a Unit Business Continuity Plan(BCP)... 3 Resumption Planning... 4 Assumptions
Unit Guide to Business Continuity/Resumption Planning (February 2009) Revised June 2011 Executive Summary... 3 Purpose and Scope for a Unit Business Continuity Plan(BCP)... 3 Resumption Planning... 4 Assumptions
Business Continuity and Disaster Recovery Planning
 Business Continuity and Disaster Recovery Planning Jennifer Brandt, CISA A p r i l 16, 2015 HISTORY OF STINNETT & ASSOCIATES Stinnett & Associates (Stinnett) is a professional advisory firm offering services
Business Continuity and Disaster Recovery Planning Jennifer Brandt, CISA A p r i l 16, 2015 HISTORY OF STINNETT & ASSOCIATES Stinnett & Associates (Stinnett) is a professional advisory firm offering services
Rogers Insurance Client Presentation
 Rogers Insurance Client Presentation Network Security and Privacy Breach Insurance Presented by Matthew Davies Director Professional, Media & Cyber Liability Chubb Insurance Company of Canada [email protected]
Rogers Insurance Client Presentation Network Security and Privacy Breach Insurance Presented by Matthew Davies Director Professional, Media & Cyber Liability Chubb Insurance Company of Canada [email protected]
Course Title: Disaster Recovery, 1st Edition
 Course Title: Disaster Recovery, 1st Edition Page 1 of 8 Course Description: The DISASTER RECOVERY/VIRTUALIZATION SECURITY SERIES is comprised of two books that are designed to fortify disaster recovery
Course Title: Disaster Recovery, 1st Edition Page 1 of 8 Course Description: The DISASTER RECOVERY/VIRTUALIZATION SECURITY SERIES is comprised of two books that are designed to fortify disaster recovery
Disaster Recovery Plan Review Checklist. A High-Level Internal Planning Tool to Assist State Agencies with Their Disaster Recovery Plans
 Disaster Recovery Plan Review Checklist A High-Level Internal Planning Tool to Assist State Agencies with Their Disaster Recovery Plans November 2008 DISASTER RECOVERY PLAN REVIEW CHECKLIST - FOR INTERNAL
Disaster Recovery Plan Review Checklist A High-Level Internal Planning Tool to Assist State Agencies with Their Disaster Recovery Plans November 2008 DISASTER RECOVERY PLAN REVIEW CHECKLIST - FOR INTERNAL
BUSINESS CONTINUITY PLANNING GUIDELINES
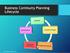 BUSINESS CONTINUITY PLANNING GUIDELINES Washington University in St. Louis The purpose of this guide is to serve as a tool to all departments, divisions, and labs across the University in building a Business
BUSINESS CONTINUITY PLANNING GUIDELINES Washington University in St. Louis The purpose of this guide is to serve as a tool to all departments, divisions, and labs across the University in building a Business
BUSINESS CONTINUITY PLANNING
 Policy 8.3.2 Business Responsible Party: President s Office BUSINESS CONTINUITY PLANNING Overview The UT Health Science Center at San Antonio (Health Science Center) is committed to its employees, students,
Policy 8.3.2 Business Responsible Party: President s Office BUSINESS CONTINUITY PLANNING Overview The UT Health Science Center at San Antonio (Health Science Center) is committed to its employees, students,
FACT SHEET: Ransomware and HIPAA
 FACT SHEET: Ransomware and HIPAA A recent U.S. Government interagency report indicates that, on average, there have been 4,000 daily ransomware attacks since early 2016 (a 300% increase over the 1,000
FACT SHEET: Ransomware and HIPAA A recent U.S. Government interagency report indicates that, on average, there have been 4,000 daily ransomware attacks since early 2016 (a 300% increase over the 1,000
PAPER-6 PART-3 OF 5 CA A.RAFEQ, FCA
 Chapter-4: Business Continuity Planning and Disaster Recovery Planning PAPER-6 PART-3 OF 5 CA A.RAFEQ, FCA Learning Objectives 2 To understand the concept of Business Continuity Management To understand
Chapter-4: Business Continuity Planning and Disaster Recovery Planning PAPER-6 PART-3 OF 5 CA A.RAFEQ, FCA Learning Objectives 2 To understand the concept of Business Continuity Management To understand
Business Continuity Planning 101. +1 610 768-4120 (800) 634-2016 www.strohlsystems.com [email protected]
 Business Continuity Planning 101 Presentation Overview What is business continuity planning Plan Development Plan Testing Plan Maintenance Future advancements in BCP Question & Answer What is a Disaster?
Business Continuity Planning 101 Presentation Overview What is business continuity planning Plan Development Plan Testing Plan Maintenance Future advancements in BCP Question & Answer What is a Disaster?
Disaster Recovery and Business Continuity Plan
 Disaster Recovery and Business Continuity Plan Table of Contents 1. Introduction... 3 2. Objectives... 3 3. Risks... 3 4. Steps of Disaster Recovery Plan formulation... 3 5. Audit Procedure.... 5 Appendix
Disaster Recovery and Business Continuity Plan Table of Contents 1. Introduction... 3 2. Objectives... 3 3. Risks... 3 4. Steps of Disaster Recovery Plan formulation... 3 5. Audit Procedure.... 5 Appendix
Cybersecurity The role of Internal Audit
 Cybersecurity The role of Internal Audit Cyber risk High on the agenda Audit committees and board members are seeing cybersecurity as a top risk, underscored by recent headlines and increased government
Cybersecurity The role of Internal Audit Cyber risk High on the agenda Audit committees and board members are seeing cybersecurity as a top risk, underscored by recent headlines and increased government
Business Continuity and Capacity Building
 Business Continuity and Capacity Building April 10, 2015 Business Continuity and Capacity Building April 10, 2015 1 / 14 Developing Institutional Business Continuity Plans and Implications for Capacity
Business Continuity and Capacity Building April 10, 2015 Business Continuity and Capacity Building April 10, 2015 1 / 14 Developing Institutional Business Continuity Plans and Implications for Capacity
Business Continuity & Disaster Recovery
 Business Continuity & Disaster Recovery Safety First Quality Every Time 1 Business Continuity & Disaster Recovery Planning Who here has a formal Business Continuity & Disaster Recovery plan? The purpose
Business Continuity & Disaster Recovery Safety First Quality Every Time 1 Business Continuity & Disaster Recovery Planning Who here has a formal Business Continuity & Disaster Recovery plan? The purpose
NERC CIP Compliance with Security Professional Services
 NERC CIP Compliance with Professional Services The North American Electric Reliability Corporation (NERC) is a nonprofit corporation designed to ensure that the bulk electric system in North America is
NERC CIP Compliance with Professional Services The North American Electric Reliability Corporation (NERC) is a nonprofit corporation designed to ensure that the bulk electric system in North America is
Cyber Security Incident Handling Policy. Information Technology Services Center (ITSC) of The Hong Kong University of Science and Technology
 Cyber Security Incident Handling Policy Information Technology Services Center (ITSC) of The Hong Kong University of Science and Technology Date: Oct 9, 2015 i Document Control Document Owner Classification
Cyber Security Incident Handling Policy Information Technology Services Center (ITSC) of The Hong Kong University of Science and Technology Date: Oct 9, 2015 i Document Control Document Owner Classification
Business Continuity Overview
 Business Continuity Overview Beverley A. Retjos Senior Manager WW SWG Security & Controls 03/12/07 Business Continuity Management (BCM) Process of ensuring that a business is prepared to survive any disruption
Business Continuity Overview Beverley A. Retjos Senior Manager WW SWG Security & Controls 03/12/07 Business Continuity Management (BCM) Process of ensuring that a business is prepared to survive any disruption
BCP and DR. P K Patel AGM, MoF
 BCP and DR P K Patel AGM, MoF Key difference between BS 25999 and ISO 22301 ISO 22301 puts a much greater emphasis on setting the objectives, monitoring performance and metrics aligning BC to top management
BCP and DR P K Patel AGM, MoF Key difference between BS 25999 and ISO 22301 ISO 22301 puts a much greater emphasis on setting the objectives, monitoring performance and metrics aligning BC to top management
Hong Kong Baptist University
 Hong Kong Baptist University Disaster Recovery Standard FOR INTERNAL USE ONLY Date of Issue: JULY 2012 Revision History Version Author Date Revision 1.0 Information Security Subcommittee (ISSC) July 2012
Hong Kong Baptist University Disaster Recovery Standard FOR INTERNAL USE ONLY Date of Issue: JULY 2012 Revision History Version Author Date Revision 1.0 Information Security Subcommittee (ISSC) July 2012
AUDITING A BCP PLAN. Thomas Bronack Auditing a BCP Plan presentation Page: 1
 AUDITING A BCP PLAN Thomas Bronack Auditing a BCP Plan presentation Page: 1 What are the Objectives of a Good BCP Plan Protect employees Restore critical business processes or functions to minimize the
AUDITING A BCP PLAN Thomas Bronack Auditing a BCP Plan presentation Page: 1 What are the Objectives of a Good BCP Plan Protect employees Restore critical business processes or functions to minimize the
Chapter 4 Information Security Program Development
 Chapter 4 Information Security Program Development Introduction Formal adherence to detailed security standards for electronic information processing systems is necessary for industry and government survival.
Chapter 4 Information Security Program Development Introduction Formal adherence to detailed security standards for electronic information processing systems is necessary for industry and government survival.
MHA Consulting. Business Continuity Management 101
 0 MHA Consulting Business Continuity Management 101 Presented by: Michael Herrera Brandon Magestro MHA Consulting Agenda MHA Consulting Introduction Business Continuity Management (BCM) Defined 2013 Trends
0 MHA Consulting Business Continuity Management 101 Presented by: Michael Herrera Brandon Magestro MHA Consulting Agenda MHA Consulting Introduction Business Continuity Management (BCM) Defined 2013 Trends
Documentation. Disclaimer
 HOME UTORprotect DOCUMENTATION AMS/ROSI SERVICES CONTACT Documentation Disaster Recovery Planning Disaster Recovery Planning Disclaimer The following project outline is provided solely as a guide. It is
HOME UTORprotect DOCUMENTATION AMS/ROSI SERVICES CONTACT Documentation Disaster Recovery Planning Disaster Recovery Planning Disclaimer The following project outline is provided solely as a guide. It is
Domain 3 Business Continuity and Disaster Recovery Planning
 Domain 3 Business Continuity and Disaster Recovery Planning Steps (ISC) 2 steps [Har10] Project initiation Business Impact Analysis (BIA) Recovery strategy Plan design and development Implementation Testing
Domain 3 Business Continuity and Disaster Recovery Planning Steps (ISC) 2 steps [Har10] Project initiation Business Impact Analysis (BIA) Recovery strategy Plan design and development Implementation Testing
Cybersecurity Awareness. Part 1
 Part 1 Objectives Discuss the Evolution of Data Security Define and Discuss Cybersecurity Review Threat Environment Part 1 Discuss Information Security Programs s Enhancements for Cybersecurity Risks Threat
Part 1 Objectives Discuss the Evolution of Data Security Define and Discuss Cybersecurity Review Threat Environment Part 1 Discuss Information Security Programs s Enhancements for Cybersecurity Risks Threat
Section A: Introduction, Definitions and Principles of Infrastructure Resilience
 Section A: Introduction, Definitions and Principles of Infrastructure Resilience A1. This section introduces infrastructure resilience, sets out the background and provides definitions. Introduction Purpose
Section A: Introduction, Definitions and Principles of Infrastructure Resilience A1. This section introduces infrastructure resilience, sets out the background and provides definitions. Introduction Purpose
Shankar Gawade VP IT INFRASTRUCTURE ENAM SECURITIES PVT. LTD.
 Business Continuity Management & Disaster Recovery Planning Presented by: Shankar Gawade VP IT INFRASTRUCTURE ENAM SECURITIES PVT. LTD. 1 What is Business Continuity Management? Is a holistic management
Business Continuity Management & Disaster Recovery Planning Presented by: Shankar Gawade VP IT INFRASTRUCTURE ENAM SECURITIES PVT. LTD. 1 What is Business Continuity Management? Is a holistic management
Does it state the management commitment and set out the organizational approach to managing information security?
 Risk Assessment Check List Information Security Policy 1. Information security policy document Does an Information security policy exist, which is approved by the management, published and communicated
Risk Assessment Check List Information Security Policy 1. Information security policy document Does an Information security policy exist, which is approved by the management, published and communicated
BUSINESS CONTINUITY MANAGEMENT REQUIREMENTS FOR SGX MEMBERS NEW RULES FOR INCLUSION IN SGX-ST RULES
 BUSINESS CONTINUITY MANAGEMENT REQUIREMENTS FOR SGX MEMBERS NEW RULES FOR INCLUSION IN SGX-ST RULES New rule Current Rule Proposed Rule 4.6.21 Business Continuity Requirements The following requirements
BUSINESS CONTINUITY MANAGEMENT REQUIREMENTS FOR SGX MEMBERS NEW RULES FOR INCLUSION IN SGX-ST RULES New rule Current Rule Proposed Rule 4.6.21 Business Continuity Requirements The following requirements
Data Security Incident Response Plan. [Insert Organization Name]
![Data Security Incident Response Plan. [Insert Organization Name] Data Security Incident Response Plan. [Insert Organization Name]](/thumbs/34/17160420.jpg) Data Security Incident Response Plan Dated: [Month] & [Year] [Insert Organization Name] 1 Introduction Purpose This data security incident response plan provides the framework to respond to a security
Data Security Incident Response Plan Dated: [Month] & [Year] [Insert Organization Name] 1 Introduction Purpose This data security incident response plan provides the framework to respond to a security
HIPAA CRITICAL AREAS TECHNICAL SECURITY FOCUS FOR CLOUD DEPLOYMENT
 HIPAA CRITICAL AREAS TECHNICAL SECURITY FOCUS FOR CLOUD DEPLOYMENT A Review List This paper was put together with Security in mind, ISO, and HIPAA, for guidance as you move into a cloud deployment Dr.
HIPAA CRITICAL AREAS TECHNICAL SECURITY FOCUS FOR CLOUD DEPLOYMENT A Review List This paper was put together with Security in mind, ISO, and HIPAA, for guidance as you move into a cloud deployment Dr.
Business Continuity Planning and Disaster Recovery Planning
 4 Business Continuity Planning and Disaster Recovery Planning Basic Concepts 1. Business Continuity Management: Business Continuity means maintaining the uninterrupted availability of all key business
4 Business Continuity Planning and Disaster Recovery Planning Basic Concepts 1. Business Continuity Management: Business Continuity means maintaining the uninterrupted availability of all key business
Clinic Business Continuity Plan Guidelines
 Clinic Business Continuity Plan Guidelines Published: January 2015 Table of Contents Emergency Notification Contacts Primary... 2 Emergency Notification Contacts Backups (in case primary is unavailable)...
Clinic Business Continuity Plan Guidelines Published: January 2015 Table of Contents Emergency Notification Contacts Primary... 2 Emergency Notification Contacts Backups (in case primary is unavailable)...
