Online Harassment and Victimization of College Students
|
|
|
- Felix Patrick
- 10 years ago
- Views:
Transcription
1 Online Harassment and Victimization of College Students M. Alexis Kennedy and Melanie A. Taylor* Volume 7 No. 1 Spring 2010 *M. Alexis Kennedy is an Assistant Professor in the Department of Criminal Justice at the University of Nevada, Las Vegas. Melanie A. Taylor is completing her Ph.D. in the Department of Criminology and Criminal Justice at Arizona State University.
2 Abstract The purpose of this study was to examine the prevalence of victimization occurring through social networking sites. Information was also sought on the internet behavior of college students. Data were collected from 354 college students from September 2007 through April Anonymous, self-report surveys were completed polling experiences with harassment, stalking, and sexual assault. Analyses showed that the majority of victimization types were reported infrequently, while rates of sexual assault overall were quite high compared to prior research. The types of victimization varied by where they were occurring online or offline. Acts such as verbal harassment, pestering, unwanted behaviors, and sexual harassment were all fairly prevalent online, while other victimizations, such as being threatened or stalked, occurred more offline. The rates of victimization initiated through online contact suggest that although social networking sites may provide opportunities for certain types of victimization, college students are still at a greater risk from people they meet offline. 2
3 About the Authors M. Alexis Kennedy is an Assistant Professor in the Department of Criminal Justice at the University of Nevada, Las Vegas. She has a Ph.D. in Forensic Psychology and was formerly an attorney. Her areas of expertise include the sexual exploitation of children and sexual victimization. Her contact information is: Department of Criminal Justice, University of Nevada, Las Vegas, 4505 Maryland Parkway, Box 5009, Las Vegas, NV Phone (702) Fax (702) [email protected] Melanie A. Taylor is completing her Ph.D. in the Department of Criminology and Criminal Justice at Arizona State University. Her master s thesis focused on victimization on social networking sites. Her research interests include juvenile delinquency and prevention, victims rights, gender and crime. Her contact information is: Department of Criminology and Criminal Justice, Arizona State University, 411 N Central Ave, Mail Code 4420, Phoenix, AZ E- mail: [email protected] 3
4 Online Harassment and Victimization of College Students Introduction The current study is in response to recent media reports that have portrayed online social networking sites as dangerous locations where individuals are commonly harassed, stalked, or exposed to sexual predators. We propose that social networks are less dangerous than has been reported in the media, and that the most serious dangers to Internet users still exist offline. To investigate this issue, we focused on empirical research that has not revealed high rates of stranger sexual solicitations of young people online. One well cited study of 1,501 teens aged found that of those who were solicited or propositioned for any type of sexual contact, only 24% were solicited by a person aged 18 or over, while the rest of the solicitations were made by juveniles (Finkelhor, Wolak & Mitchell 2000). Less than 5% were actually aggressively solicited, which meant that the solicitor asked the teen to meet, talk on the phone, or sent something through the mail. Routine activities theory was used to explore whether there is an increased risk while using online sites and whether the use of social networking sites should be deemed a risky act that may lead to various types of victimization. Routine activities theory looks for a convergence in time and location of motivated offenders, targets that are deemed suitable by the offender and a lack of guardianship over desired persons or things (De Coster, Estes, & Mueller 1999). The existence of motivated offenders is assumed in many studies including this one. Previous research has explored the selection of suitable targets of harassment and stalking among college students (Mustaine and Tewksbury 1999). The online behavior of college students, however, has not yet been examined as a potentially risky routine activity. Also worth exploring is the potential lack of capable guardianship which may occur in online settings. Research with teen 4
5 computer users found that they were not guarding themselves but were less cautious about sharing personal information because they didn t perceive Internet communications to be a threat to their personal safety (Pierce 2006). Harassment, stalking, and sexual victimization are all occurring in both online and offline situations. Offline, Fisher, Cullen, and Turner (2002) claim that actual rates of harassment are unknown, yet it is likely that many females in college are at some time victims of harassment. They found that stalking also appears to be fairly prevalent, with research finding that one in ten college students are stalked each year. While sexual assault rates may differ from those not attending college, the American College Health Association s survey of over 50,000 college students showed that 2% of female and.8% of male students had been sexually assaulted during a one year period (2006). Victimization may also be experienced online due to greater numbers of individuals accessing the Internet. College students are becoming more reliant upon computers, with as many as 90% accessing them daily and over 10% primarily using the Internet to meet others or experiment socially (Forston, Scotti, Chen, Malone & Ben 2007). Few studies have looked at online harassment, stalking, and sexual assault, but those that have looked into the issue have found relatively low levels of victimization. Mitchell, Becker-Blease, and Finkelhor (2005) found that individuals reported being victimized while using online sites in two forms, sexual and nonsexual. One method is harassment, which can be accomplished by posting defamatory or embarrassing personal information about others, impersonating others online, stalking people online, threatening violence, and physical and emotional abuse (Mitchell et al. 2005: 503). Despite this, it appears 5
6 that online harassment is rarely reported to law enforcement because most individuals perceive that the victimization is not that serious (Finn 2004). Rosen s study of 1,257 users of the social networking site MySpace found that the prevalence of stalking while using the website was extremely low (2006a). Rosen concluded that only 1.5% of the sample reported being stalked, while only 4.6% of those sampled claimed they had been propositioned for sexual intercourse. Those stalking victims were both men and women but women were more likely to have been propositioned sexually. Also, those who had been actively using the site for a longer period had a greater risk of victimization. Follow up research by Rosen (2006b) reported that a high number of those users who had reported being either harassed or solicited for sex, blocked the user from contacting him or her, or took some other action to end the contact. The first major study that analyzed the prevalence of teenage victimization on social networking sites was the 1999 Youth Internet Safety Survey (Mitchell, Finkelhor & Wolak 2001). In the study, 1,501 individuals between the ages of (63% were 14 or older) who were deemed frequent Internet users were surveyed, with 56% frequenting chat rooms, and 56% talking to strangers while online. It was found that nearly one-fifth of the sample had been sexually solicited, which meant that an individual had made requests for sex, discussed sex when it was unwanted, or consensually discussed sex. It was also found that females and those who were between the ages of 14 and 17 were solicited at higher rates than those aged 10 to 13, while those between the ages of 10 and 13 reported being distressed by the solicitations more frequently than older teens. The researchers concluded that while none of those surveyed were sexually assaulted and solicitation may not be problematic for all teens, there may be an 6
7 increased risk of exploitation for troubled youth (e.g. experienced depression, death of a family member) who are solicited online. A second Youth Internet Safety Survey (YISS-2; Mitchell, Finkelhor & Wolak 2007) conducted in 2005 found that there was a decrease in the number of sexual solicitations of juveniles, while the number of aggressive solicitations was unchanged. Of those who were nonaggressively sexually solicited, 82% were between the ages of 14 and 17, nearly three quarters had posted personal information online (72%), and over half used the Internet primarily for talking in chat rooms (54%). Of the 3%-4% who had been aggressively solicited online, 81% had posted personal information and nearly 70% were using the Internet for chat rooms. Risk factors for solicitations were being female, using chat rooms frequently, talking about sex frequently online, revealing personal information, and being abused offline. The rise in the popularity of the Internet for U.S. citizens has essentially changed daily routine activities (U.S. Department of Commerce 2004). Rather than communicating with one another at meetings, social events, and work, practically all individuals have the option of using the Internet as a means for communication. This research considers whether this social networking behavior is leading to new victimization. Considered were college students internet behavior, protections used to safeguard privacy and different types of victimization such as stalking, harassment and sexual assault experienced both online and offline. The current study was designed to determine the victimization rates of harassment, stalking, and sexual assault in both online and offline settings among college students. Also considered were factors that may impact these types of victimization (e.g., protections taken while on social networks, the type of information given to strangers), and how the victimization was conducted, whether it was in person or online. 7
8 Methods Measures The research was conducted at a large university in the Southwest United States. A 77- question self-report survey was created to poll personal use of social networking sites, activities conducted while online, and types of victimization that may have occurred as a result of social networking use. Also included were 13 questions from the Sexual Experiences Survey (SES; Koss, Gidycz & Wisniewski 1987). It has been demonstrated that the SES is a reliable measure of both rape and sexual assault involving coercion (Testa, Vanzile-Tamsen, Livingston & Koss 2004). The study was approved by the University Institutional Review Board. To maximize accuracy in data entry, the Nearly Perfect Data Entry (Barchard & Pace 2006) system was used, which required that data from each survey be entered twice, with inconsistent entries being highlighted in order to reduce the possibility of human error during data entry Participants were recruited from criminal justice introductory classes in exchange for course credit. Participants signed an informed consent form prior to being given the survey. Participation was voluntary and the participants were informed that they could choose not to complete any portion of the survey and still receive full participation credit. Upon completion of the survey, participants received a debriefing form that included contact information for counseling services in case they found the material to be upsetting. Participants A total of 354 students completed the survey. More of the participants were female (60.5%) than male. The average age was 22, with 25% of the sample being 18 and the majority of participants being under 21. Participants were predominantly Caucasian (60%), with 13% of the sample being Hispanic, 10.5% African-American, 8.8% Asian, and 7.7% other. 8
9 Results Online Behavior Use of social networking sites (SNS) is prevalent among college students. Over 80% of the participants were currently using some form of social network, while nearly 92% had used a social network at some point in their lives. The most popular site used was MySpace with 75.1% of students solely using it and another 15.9% using both MySpace and Facebook. An additional 8.7% of students only used Facebook. Those with profiles were somewhat open with their personal information, with approximately one-third having completely public profiles. Another one-third maintained semi-private profiles and one-third had completely private profiles. Furthermore, college students appear outgoing with their sites as they are including relatively high numbers of personal pictures, with 30% posting between pictures and another 23% with over 100 pictures. Most students shared some personal information across the different privacy levels. For example, over 75% of the sample provided their city and state, over two-thirds stated their present school, and about one-third revealed their place of employment. The vast majority of SNS users did so to stay in contact with current friends (80.7%). In addition to staying in touch with existing friends, students were also making new social contacts online. Nearly a third (31.3%) of participants met up with someone in person that they had first made contact with online. Even with the high levels of use, only 15.1% reported ever fearing for their safety after using such a site. The relatively low levels of fear for safety may be the result of users having the ability to use strategies to protect themselves. The first strategy would be to block other users that they no longer wished to communicate with, which was done by 29% of participants. A second strategy would be to change information provided on their sites. A few students changed 9
10 their phone numbers, addresses, or addresses in response to unwanted incidents online. In this study, 2.9% changed personal information as a result of fears of stalking or harassment. Most of these changes to profiles (90%) were in response to stalkers or harassers that participants met online; only 10% of the changes were in response to harassers that victims had met offline. Another possible response to being victimized could be deleting profiles. Twenty-six individuals deleted profiles after being harassed or stalked by an individual online, while two people deleted social networking profiles after being physically stalked. Finally, one participant filed a formal restraining order due to an online incident, while 22 participants (6.2%) had filed a restraining order due to an offline incident. Online and Offline Victimization Some types of victimization occurred more in online settings, some more in offline settings and others in comparable rates online and offline. Two types of harassment occurred more frequently in online situations. First, sexual harassment occurred more frequently online. Types of sexual harassment experienced are presented in Table 1. Second, pestering, incessant and unyielding attention also occurred more frequently in online situations. While being irritated to the point of wanting to end a friendship occurred in both settings, more students had their requests to cease contact ignored in online situations. The third type of harassing behavior, verbal harassment, occurred in similar levels online and offline. The majority of students (53.4%) had been verbally attacked in one setting or another. 10
11 Table 1. Harassing Behavior Sexual Harassment I have had verbal statements made to me which I considered inappropriate due to their sexual nature. I have been sent unwanted material of a sexual nature. No n (%) Yes n (%) Victimized Online Victimized Offline 208 (58.8%) 145 (41.0%) 86 (24.3%) 67 (18.9%) 265 (74.9%) 89 (25.1%) 84 (23.7%) 7 (2.0%) Pestering Behavior I have been pestered or irritated by an individual to the point that I no longer wished to be friends. I have requested that an individual or individuals no longer contact me, but these requests were ignored. I have been repeatedly contacted online unwantedly by an individual. 167 (47.2%) 187 (52.8%) 102 (28.8%) 92 (26.0%) 268 (75.7%) 86 (24.3%) 60 (17.0%) 31 (8.8%) 277 (78.2%) 76 (21.5%) 73 (20.6%) 7 (2.0%) Verbal Harassment I have been verbally attacked. 164 (46.3%) 189 (53.4%) 101 (28.5%) 104 (29.4%) I have been verbally harassed. 187 (52.8%) 166 (46.9%) 85 (24.0%) 91 (25.7%) I have had verbal statements made to me which I considered derogatory. 191 (54.0%) 162 (45.8%) 82 (23.2%) 91 (25.7%) Note. Some people reported both online and offline victimization. Threatening behavior was also measured and it occurred more frequently in offline situations. Experience with these behaviors is presented in Table 2. Threats that did not cause fear were actually received more in offline situations than online. Twice as many students were threatened offline as online in a manner that did not make them fear for their lives (18.6% offline, 9.3% online). Threats that did cause fear were also occurring more frequently offline 11
12 than with online. More participants responded to these real world threats by filing restraining orders, with 22 participants (6.2%) filing in response to offline threats in contrast to only one participant (0.3%) filing one after an online threat. Table 2. Threatening Behavior Threats that did not cause fear I have been threatened physically, but I did not fear for my life. I have had pictures taken of me which I did not consent to. I have been watched by another without my consent. No n (%) Yes n (%) Victimized Online Victimized Offline 259 (73.2%) 95 (26.8%) 33 (9.3%) 66 (18.6%) 326 (92.1%) 27 (7.6%) 9 (2.5%) 17 (4.8%) 320 (90.4%) 32 (9.0%) 4 (1.1%) 28 (7.9%) Threats causing fear I have been threatened physically, and did fear for my life. I have feared for my safety because of a person. I filed a restraining order against someone out of fear for my safety. Physical threats have been made against me, family, or friends. I have asked someone to no longer contact me because I feared for my safety because of that individual. I have had threats made against me that made me fear for my life. 326 (92.1%) 28 (7.9%) 6 (1.7%) 22 (6.2%) 254 (71.8%) 100 (28.2%) 14 (4.0%) 86 (24.3%) 331 (93.5%) 23 (6.5%) 1 (0.3%) 22 (6.2%) 283 (79.9%) 70 (19.8%) 30 (8.5%) 42 (11.9%) 317 (89.5%) 36 (10.2%) 36 (10.2%) 13 (3.7%) 331 (93.5%) 21 (5.9%) 4 (1.1%) 17 (4.8%) Note. Some people reported both online and offline victimization. 12
13 Stalking behavior also occurred more frequently offline than online. Over 13% of the participants reported being stalked, 10.1% offline and 3.1% online. Participants stalked online did not report changing their daily routine in response, but 10 (2.8%) did report changing their personal information available online. Participants stalked offline did change their behavior due to stalking (13 or 3.7%). Participants also reported changing their personal information in response to being stalked offline (24 or 6.8%). Table 3. Stalking Behavior Stalking I have been forced to change my daily routine due to fears resulting from stalking. I have been under more stress due to fears resulting from being stalked. I have changed my phone number, address, or address due to a stalking or harassment incident. I have quit my job or moved from my home due to a stalking or harassment incident. No n (%) Yes n (%) Victimized Online Victimized Offline 340 (96.0%) 13 (3.7%) 0 13 (3.7%) 339 (95.8%) 14 (4.0%) 1 (0.3%) 13 (3.7%) 319 (90.1%) 34 (9.6%) 10 (2.8%) 24 (6.8%) 339 (95.8%) 14 (4.0%) 1 (0.3%) 13 (3.7%) I have been stalked 306 (86.7%) 47 (13.3%) 11 (3.1%) 36 (10.1%) Note. Some people reported both online and offline victimization. Sexual Victimization The majority of the college students reported being sexually active; 78.7% disclosed engaging in consensual sexual intercourse. Results from the SES questions indicated that 31.7% of the female student population had been sexually assaulted. Of the 31.7% of females 13
14 victimized, 26.1% self-identified themselves as sexual assault victims, while another 5.6% of the female students described having experienced coercive sexual experiences that would meet the legal definition of sexual assault but they did not identify themselves as sexual assault victims. Furthermore, 4.3% of the male participants reported being sexually assaulted. Internet Behavior To look further into the differences in victimization, analyses were run considering differences in internet behavior. The variable that was focused on was the level of privacy employed in participants profiles, which were self-reported to be a profile that was public, semiprivate, or completely private. Close to a third of respondents (34.9%) reported having a public profile, 31.5% used some restrictions (semi-private), and 33.6% had completely private profiles. ANOVAs were also used to determine whether there were group differences based on the three levels of privacy. To avoid increased errors due to multiple analyses, a Bonferroni correction was applied and only results with a p <.01 were considered significant. Levels of privacy did not distinguish some types of victimization. For example, rates of harassment or of receiving unwanted material did not vary significantly between the privacy levels. Other victimizations approached significance but did not meet the Bonferroni corrected level. Rates of sexual assault almost varied significantly (p <.043) with the private profiles reporting higher levels of sexual assault than semi-private or public. Being stalked also approached significance (p <.019) with the public profiles reporting lower rates than semiprivate or private profiles. To further understand the participants, privacy was considered in relation to other online behaviors like hours spent online, number of friends added to site, and publishing of specific personal information on profile (e.g., home address). These behaviors did not vary significantly 14
15 between the privacy levels. Only one variable, having a school listed on a profile, was found to have significant differences with public profiles more likely to include that information than semi-private or private profiles (F = 4.65 (2, 295), p <.01). The use of two protective strategies varied significantly by privacy level. First, blocking a user from further contact was used significantly more by public profile users than by private profile users (F = 4.87 (2, 295), p<.01). The semi-private group did not vary significantly from the other two groups. Second, the semi-private group reported having deleted profiles in response to harassment significantly more than the public or private groups (F = 4.65 (2, 295), p <.01). This curvilinear relationship was interesting as harassment victims deleted profiles but did not change to a completely private profile. Discussion and Conclusion The current study has shown that most college students use social networking sites (91.8%). Also revealed in this study were high rates of victimization occurring among students, both online and offline. Koss Sexual Experiences Survey showed that female students experienced higher than average rates of sexual assault with 31.7% of female participants reporting that they had been sexually assaulted (68 of the 215 female participants). Six men (4.3% of the male participants) reported having been sexually assaulted. These findings for women are higher than previous studies utilizing the SES, which found that 20% of college aged females reported sexual assault and should be investigated in future research (Koss 1998; Koss et al. 1987; Testa et al. 2004). Students in this sample population often met the routine activities theory criteria of suitable and available targets as they were sharing a high amount of personal information in a public arena - over two-thirds of the sample either had public or semi-public profiles. 15
16 Furthermore, over 90% of the sample reported use of these sites sometime in their lives, which created a large base of potential targets for motivated offenders. Finally, a lack of capable guardianship is likely occurring online due to the high levels of personal information reported to be disclosed online. For example, over 75% of the sample posted their city and state, over twothirds disclosed their current school affiliation, and about one-third revealed their place of employment. When comparing online and offline victimization, it was found that certain behaviors were seen more commonly either online or offline. The only exception to this was verbal harassment, which had comparable rates of victimization occurring online and offline. Types of victimization exhibited more frequently offline were non-fearful and fearful threats, physical harassment, and stalking. Victimization reported at high levels by participants in online settings were verbal harassment, pestering behaviors, and sexual harassment. This is likely due to the ease by which others are able to perpetrate such acts through social networking sites. Also, fearful threats occurred more frequently in online settings than non-fearful threats did online. When analyses were conducted to see if exposure online affected victimization, it was expected that there would be a linear relationship, with those having the lowest levels of privacy being victimized the most, those with moderate protections being victimized less, and those with private profiles having the lowest amounts of victimization. This was not always the case for some types of victimization. For example, those who deleted profiles due to stalking or harassment incidents did not necessarily change to private profiles, with those with both public and private profiles having lower rates of victimization than those with semi-private profiles. 16
17 It is an interesting finding that the relationship with privacy in some cases was curvilinear. This finding may reflect that those who had initially had public profiles may have experienced some type of victimization and then as a result changed their profile to semi-private, but were unwilling to make completely private profiles. Future research should look for reasons why people choose to change their levels of privacy. Also important to explore further is the trend that 31.3% of the students moved an online relationship into the real world by agreeing to meet in person someone that they first made contact with online. While these students did not disclose being victimized by these new acquaintances, it is clear that students are forming relationships through social networking. It is easier to protect oneself in an online environment by blocking contact, a strategy employed by 29% of the students. This research study is a good first step in determining the risk of victimization while using social networking sites and future research can focus further on the differences between victims who experience negative incidents online, offline, or in both venues. The preliminary analyses in this project indicate that these groups differ, so the next step is to predict what independent characteristics show where an individual is most at risk of being victimized. Although there may be some risks while using social networking sites (i.e., sexual harassment and pestering unwanted contacts), there is still a much greater risk of being severely victimized offline during the everyday routine activities of individuals. Limitations The current study does have a few limitations. The primary limitation is that those surveyed were from introduction to criminal justice courses. This implies that the majority of the students surveyed represent those who have just begun school, which limits the ability to capture 17
18 the victimization rates of students throughout their entire college careers. Future research may be conducted which measures those entering college, as well as collecting data from those in their last semester, in order to have two groups for comparisons. Additionally, only students in criminal justice courses from one university were surveyed, which limits the ability to generalize all academic majors, as well as other college campuses. More extensive research may be conducted to examine the victimization rates on social networking sites of various majors throughout the United States in order to determine if the results from the current study are consistent throughout the country. Recommendations for Future Research It was found that there was an unexpected curvilinear relationship of victimization based upon the privacy of a user s profile. Due to the lack of questions regarding the reasons behind the choice of privacy level, it was impossible to determine whether the participant was victimized and then changed a profile to private or if the profile was initially private and the victimization occurred anyways. Further analyses should be conducted in this area in order to determine if having a profile set to private provides a high degree of protection, or if individuals are still being victimized even with such settings in place. The goal of the current study was to determine where the victimization was more prevalent and what factors may have led to victimization, so the quantity or frequency of victimizations, both online and offline, were not surveyed. Future research should delve into the number of times students are being victimized in order to determine if certain individual characteristics lead to repeat victimization, whether online or offline. Finally, future studies should be conducted using sample populations other than collegeaged individuals. Previous researchers have explored victimization of children under the age of 18
19 17, while research on those 18 and over has been scant. The current study included those 18 and over, but only included individuals in college. Comprehensive research spanning all age groups and professions is necessary in order to determine the full extent of victimization while using social networking sites. 19
20 References American College Health Association (2006). American college health association national college health assessment (ACHA-NCHA) Spring 2005 reference group data report (abridged). Journal of American College Health, 55, Barchard K. & Pace L. (2006). Nearly perfect data entry: An inexpensive, easy, double-entry system. Paper presented at the 2006 meeting of the Western Psychological Association, Palm Springs, CA. De Coster, S., Estes, S., & Mueller, C. (1999). Routine activities and sexual harassment in the workplace. Work and Occupations, 26, Finkelhor D, Wolak J, & Mitchell, K. (2000). Online victimization: A report on the nation s youth. Retrieved from Fisher B, Cullen F, Turner M. (2002). Being pursued: Stalking victimization in a national study of college women. Criminology & Public Policy, 1, Finn, J. (2004). A survey of online harassment at a university campus. Journal of Interpersonal Violence, 19, Forston B, Scotti J, Chen Y, Malone J, & Ben K. (2007). Internet use, abuse, and dependence among students at a Southeastern regional university. Journal of American College Health, 2, Koss, M. (1998). Hidden rape: Sexual aggression and victimization in a national sample in higher education. Rape and Sexual Assault, 2, Koss M, Gidycz C, & Wisniewski N. (1987). The scope of rape: Incidence and prevalence of sexual aggression and victimization in a national sample of higher education students. Journal of Consulting and Clinical Psychology, 55, Mitchell K, Becker-Blease K, & Finkelhor D. (2005). Inventory of problematic Internet experiences encountered in clinical practice. Professional Psychology, 36, Mitchell K, Finkelhor D, & Wolak, J. (2001). Risk factors for and impact of online sexual solicitation of youth. Journal of American Medical Association, 285, Mitchell K, Finkelhor D, Wolak J. (2007). Youth Internet users at risk for the most serious online sexual solicitations. American Journal of Preventive Medicine, 32, Mustaine, E., & Tewksbury, R. (1999). A routine activity theory explanation for women's stalking victimizations. Violence Against Women, 5(1),
21 Pierce, T. (2006). Talking to strangers on MySpace: Teens' use of Internet social networking sites. Journal of Media Psychology, 11(3). Retrieved from Rosen L. (2006a). Blocking sexual predators on MySpace: The kids are alright. Retrieved from Rosen L. (2006b). Sexual predators on MySpace: A deeper look at teens being stalked or approached for sexual liaisons. Retrieved from Testa M, Vanzile-Tamsen C, Livingston J, & Koss M. (2004). Assessing women s experiences of sexual aggression using the sexual experiences survey: Evidence for validity and implications for research. Psychology of Women Quarterly. 28, U.S. Department of Commerce (2004). A nation online: Entering the broadband age. Retrieved from 21
National Statistics. Domestic Violence/Sexual Assault Fact Sheet: Oklahoma Department of Mental Health and Substance Abuse Services
 National Statistics Domestic Violence/Sexual Assault Fact Sheet: Oklahoma Department of Mental Health and Substance Abuse Services The National Domestic Violence Hotline has received more than 700,000
National Statistics Domestic Violence/Sexual Assault Fact Sheet: Oklahoma Department of Mental Health and Substance Abuse Services The National Domestic Violence Hotline has received more than 700,000
Internet Safety Fact Sheet Facts about Social Networking:
 Internet Safety Fact Sheet Facts about Social Networking: 96% of students ages 9 to 17 who have access to the Internet have used social networking technologies (Grunwald Associates, "Creating & Connecting
Internet Safety Fact Sheet Facts about Social Networking: 96% of students ages 9 to 17 who have access to the Internet have used social networking technologies (Grunwald Associates, "Creating & Connecting
Are Social Networking Sites a Source of Online Harassment for Teens? Evidence from Survey Data
 Are Social Networking Sites a Source of Online Harassment for Teens? Evidence from Survey Data Anirban Sengupta 1 Anoshua Chaudhuri 2 Abstract Media reports on incidences of abuse on the internet, particularly
Are Social Networking Sites a Source of Online Harassment for Teens? Evidence from Survey Data Anirban Sengupta 1 Anoshua Chaudhuri 2 Abstract Media reports on incidences of abuse on the internet, particularly
ONLINE PREDATORS & PREDATORS
 the myths and realities of ONLINE PREDATORS & PREDATORS Center For Child Advocacy Sixth Annual National Conference Crimes Against Children: The Multiple Faces of Child Victimization Joseph Hanley B.A.
the myths and realities of ONLINE PREDATORS & PREDATORS Center For Child Advocacy Sixth Annual National Conference Crimes Against Children: The Multiple Faces of Child Victimization Joseph Hanley B.A.
Violence against women: key statistics
 Violence against women: key statistics Research from the 2012 ABS Personal Safety Survey and Australian Institute of Criminology shows that both men and women in Australia experience substantial levels
Violence against women: key statistics Research from the 2012 ABS Personal Safety Survey and Australian Institute of Criminology shows that both men and women in Australia experience substantial levels
Capstone Project Minnesota State University Crime and Victimization Survey
 Capstone Project Minnesota State University Crime and Victimization Survey Sherrise Truesdale, PhD Department of Sociology and Corrections Minnesota State University April 28, 2005 1 Alan Hughes (2005)
Capstone Project Minnesota State University Crime and Victimization Survey Sherrise Truesdale, PhD Department of Sociology and Corrections Minnesota State University April 28, 2005 1 Alan Hughes (2005)
Quantitative research findings on RAPE in Kenya between Dec.30 th 2007 to June 30 th 2008. Estimated Statistics of Rape & pedophilia 40,500.
 CRIME SCENE INVESTIGATION NAIROBI P. O. Box 12130-00400, Nairobi Tel: 254 20 240011 Fax: 254 20 343844 Quantitative research findings on RAPE in Kenya between Dec.30 th 2007 to June 30 th 2008. Estimated
CRIME SCENE INVESTIGATION NAIROBI P. O. Box 12130-00400, Nairobi Tel: 254 20 240011 Fax: 254 20 343844 Quantitative research findings on RAPE in Kenya between Dec.30 th 2007 to June 30 th 2008. Estimated
Melanie A. Taylor. Department of Criminal Justice (775)784-6517 1664 N. Virginia St, MS/214 Reno, NV 89557-214
 Melanie A. Taylor University of Nevada, Reno [email protected] Department of Criminal Justice (775)784-6517 1664 N. Virginia St, MS/214 Reno, NV 89557-214 Education 2013 Doctor of Philosophy, Criminology
Melanie A. Taylor University of Nevada, Reno [email protected] Department of Criminal Justice (775)784-6517 1664 N. Virginia St, MS/214 Reno, NV 89557-214 Education 2013 Doctor of Philosophy, Criminology
effects on youth Daniel J. Flannery PhD Dr. Semi J. and Ruth Begun Professor
 Social Media and its effects on youth Daniel J. Flannery PhD Dr. Semi J. and Ruth Begun Professor Director, Begun Center for Violence Prevention Research & Education Mandel School of Applied Social Sciences
Social Media and its effects on youth Daniel J. Flannery PhD Dr. Semi J. and Ruth Begun Professor Director, Begun Center for Violence Prevention Research & Education Mandel School of Applied Social Sciences
I N F O R M A T I O N B U L L E T I N. Considerations for Sexual Assault Coordination
 I N F O R M A T I O N B U L L E T I N Considerations for Sexual Assault Coordination This information bulletin is based on the information available at April 4, 2002. In addition to the sources cited,
I N F O R M A T I O N B U L L E T I N Considerations for Sexual Assault Coordination This information bulletin is based on the information available at April 4, 2002. In addition to the sources cited,
In 2014, U.S. residents age 12 or older experienced
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised September 29, 2015 Criminal Victimization, 2014 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised September 29, 2015 Criminal Victimization, 2014 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians
CHILDHOOD SEXUAL ABUSE FACT SHEET
 CHILDHOOD SEXUAL ABUSE FACT SHEET Emily M. Douglas and David Finkelhor PART 1: HOW MANY CHILDREN ARE THE VICTIMS OF CHILD SEXUAL ABUSE? There are many estimates of the number of children who are the victims
CHILDHOOD SEXUAL ABUSE FACT SHEET Emily M. Douglas and David Finkelhor PART 1: HOW MANY CHILDREN ARE THE VICTIMS OF CHILD SEXUAL ABUSE? There are many estimates of the number of children who are the victims
Indiana Report. 2011 Action Plan Domestic Violence and Sexual Assault Services
 Indiana Report 2011 Action Plan Domestic Violence and Sexual Assault Services Introduction Every five years a committee of domestic and sexual violence victim service providers, coalitions, and vested
Indiana Report 2011 Action Plan Domestic Violence and Sexual Assault Services Introduction Every five years a committee of domestic and sexual violence victim service providers, coalitions, and vested
4 Criminal and Family Law
 4 Criminal and Family Law ENG 004/2010 FAMILY LAW FOR WOMEN IN ONTARIO All Women. One Family Law. Know your Rights. Criminal and Family Law This booklet is meant to give you a basic understanding of legal
4 Criminal and Family Law ENG 004/2010 FAMILY LAW FOR WOMEN IN ONTARIO All Women. One Family Law. Know your Rights. Criminal and Family Law This booklet is meant to give you a basic understanding of legal
Teen Online Safety & Digital Reputation Survey
 Teen Online Safety & Digital Reputation Survey Cox Communications Teen Online Safety & Digital Reputation Survey in Partnership with the National Center for Missing & Exploited Children (NCMEC) (Fielded
Teen Online Safety & Digital Reputation Survey Cox Communications Teen Online Safety & Digital Reputation Survey in Partnership with the National Center for Missing & Exploited Children (NCMEC) (Fielded
By Augusta Epuli Anjoh April 2013 Cyber security forum 2013
 By Augusta Epuli Anjoh April 2013 Cyber security forum 2013 What is a cyber space? The electronic medium of computer networks, in which online communication takes place. The American Heritage Science Dictionary
By Augusta Epuli Anjoh April 2013 Cyber security forum 2013 What is a cyber space? The electronic medium of computer networks, in which online communication takes place. The American Heritage Science Dictionary
Violent Victimization of College Students, 1995-2002
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report National Crime Victimization Survey January 25, NCJ 26836 Violent Victimization of College Students, By
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report National Crime Victimization Survey January 25, NCJ 26836 Violent Victimization of College Students, By
SOUTH DAKOTA BOARD OF REGENTS. Policy Manual
 Prevention of Sexual Assault, Domestic Violence, and Stalking Page 1 of 5 SOUTH DAKOTA BOARD OF REGENTS Policy Manual SUBJECT: Prevention of, Dating Violence, Domestic Violence Sexual Assault and Stalking
Prevention of Sexual Assault, Domestic Violence, and Stalking Page 1 of 5 SOUTH DAKOTA BOARD OF REGENTS Policy Manual SUBJECT: Prevention of, Dating Violence, Domestic Violence Sexual Assault and Stalking
Results. Contact sexual crimes based on PSI and self-report after SOTP participation
 Self-Reported Contact Sexual Offenses by Participants in the Federal Bureau of Prisons Sex Offender Treatment Program: Implications for Internet Sex Offenders Andres E. Hernandez, Psy.D. Director, Sex
Self-Reported Contact Sexual Offenses by Participants in the Federal Bureau of Prisons Sex Offender Treatment Program: Implications for Internet Sex Offenders Andres E. Hernandez, Psy.D. Director, Sex
What Employers Need to Know to Help
 Occupational Health & Safety Council of Ontario (OHSCO) WORKPLACE VIOLENCE PREVENTION SERIES Domestic Violence Doesn t Stop When Your Worker Arrives at Work: What Employers Need to Know to Help What is
Occupational Health & Safety Council of Ontario (OHSCO) WORKPLACE VIOLENCE PREVENTION SERIES Domestic Violence Doesn t Stop When Your Worker Arrives at Work: What Employers Need to Know to Help What is
BERKELEY COLLEGE Equal Opportunity Policy
 BERKELEY COLLEGE Equal Opportunity Policy Purpose Recognizing that its diversity greatly enhances the workplace and opportunities for learning, Berkeley is firmly committed to providing all associates,
BERKELEY COLLEGE Equal Opportunity Policy Purpose Recognizing that its diversity greatly enhances the workplace and opportunities for learning, Berkeley is firmly committed to providing all associates,
Online Victimization of Youth: Five Years Later
 Online Victimization of Youth: Five Years Later Online Victimization of Youth: Five Years Later 2006 JANIS WOLAK, KIMBERLY MITCHELL, AND DAVID FINKELHOR OF THE CRIMES AGAINST CHILDREN RESEARCH CENTER
Online Victimization of Youth: Five Years Later Online Victimization of Youth: Five Years Later 2006 JANIS WOLAK, KIMBERLY MITCHELL, AND DAVID FINKELHOR OF THE CRIMES AGAINST CHILDREN RESEARCH CENTER
4 What is Sexual Assault? 5 Why Me? 6 Common Reactions Following an Assault. 7 What Next? 10 Civil Legal Remedies. 13 Idaho Crime Victims Rights Act
 sexual assault No one deserves to be sexually assaulted. Most victims are sexually assaulted by someone they know. This handbook provides information on sexual assault and available resources. This handbook
sexual assault No one deserves to be sexually assaulted. Most victims are sexually assaulted by someone they know. This handbook provides information on sexual assault and available resources. This handbook
Internet Safety/CIPA Lesson Plan
 Internet Safety/CIPA Lesson Plan Social Networking Overview Students need to safely use the Internet for learning, socializing, and for preparing for college and work. While firewalls, antivirus software,
Internet Safety/CIPA Lesson Plan Social Networking Overview Students need to safely use the Internet for learning, socializing, and for preparing for college and work. While firewalls, antivirus software,
SEXUAL ASSAULT POLICY
 SEXUAL ASSAULT POLICY California State University, Stanislaus is strongly committed to the establishment of an educational environment in which students, faculty, and staff can work together in an atmosphere
SEXUAL ASSAULT POLICY California State University, Stanislaus is strongly committed to the establishment of an educational environment in which students, faculty, and staff can work together in an atmosphere
Understanding the Statistics about Male Violence Against Women
 Understanding the Statistics about Male Violence Against Women White Ribbon Research Series Paper No. 5 Professor Donna Chung May 2013 White Ribbon White Ribbon Australia Understanding the Statistics about
Understanding the Statistics about Male Violence Against Women White Ribbon Research Series Paper No. 5 Professor Donna Chung May 2013 White Ribbon White Ribbon Australia Understanding the Statistics about
Violent Crime in Ohio s Primary and Secondary Schools
 State of Ohio Office of Criminal Justice Services Violent Crime in Ohio s Primary and Secondary Schools Ohio Office of Criminal Justice Services 1970 W. Broad Street, 4th Floor Columbus, Ohio 43223 Toll-Free:
State of Ohio Office of Criminal Justice Services Violent Crime in Ohio s Primary and Secondary Schools Ohio Office of Criminal Justice Services 1970 W. Broad Street, 4th Floor Columbus, Ohio 43223 Toll-Free:
Adolescent Sexual Offenders
 Adolescent Sexual Offenders Information from... The National Clearinghouse on Family Violence Who Are Adolescent Sexual Offenders? The adolescent sexual offender is defined as a youth, from 12 to 17 years
Adolescent Sexual Offenders Information from... The National Clearinghouse on Family Violence Who Are Adolescent Sexual Offenders? The adolescent sexual offender is defined as a youth, from 12 to 17 years
THE EFFECTS OF FAMILY VIOLENCE ON CHILDREN. Where Does It Hurt?
 THE EFFECTS OF FAMILY VIOLENCE ON CHILDREN Where Does It Hurt? Child Abuse Hurts Us All Every child has the right to be nurtured and to be safe. According to: Family Violence in Canada: A Statistical Profile
THE EFFECTS OF FAMILY VIOLENCE ON CHILDREN Where Does It Hurt? Child Abuse Hurts Us All Every child has the right to be nurtured and to be safe. According to: Family Violence in Canada: A Statistical Profile
Domestic Assaults by Juvenile Offenders
 U.S. Department of Justice Office of Justice Programs Office of Juvenile Justice and Delinquency Prevention J. Robert Flores, Administrator November 2008 Office of Justice Programs Innovation Partnerships
U.S. Department of Justice Office of Justice Programs Office of Juvenile Justice and Delinquency Prevention J. Robert Flores, Administrator November 2008 Office of Justice Programs Innovation Partnerships
Sarah Smythe Youth Community Developer Western Ottawa Community Resource Centre. Genevieve Hupe School Resource Officer Ottawa Police Service
 Sarah Smythe Youth Community Developer Western Ottawa Community Resource Centre Genevieve Hupe School Resource Officer Ottawa Police Service From the choices below, which screen name is the worst for
Sarah Smythe Youth Community Developer Western Ottawa Community Resource Centre Genevieve Hupe School Resource Officer Ottawa Police Service From the choices below, which screen name is the worst for
Trends in Arrests for Child Pornography Possession: The Third National Juvenile Online Victimization Study (NJOV 3)
 April 2012 Trends in Arrests for Child Pornography Possession: The Third National Juvenile Online Victimization Study (NJOV 3) Abstract Arrests for the possession of child pornography (CP) increased between
April 2012 Trends in Arrests for Child Pornography Possession: The Third National Juvenile Online Victimization Study (NJOV 3) Abstract Arrests for the possession of child pornography (CP) increased between
Spring 2015 Sexual Harassment Survey Results
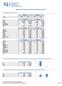 Spring 2015 Sexual Harassment Survey Results Response Rates by Demographic Variable Overall 23048 1724 7.48% Gender Male 11530 50.03% 620 35.96% Female 11517 49.97% 1039 60.27% t Specified 1 0.0 0 0.0
Spring 2015 Sexual Harassment Survey Results Response Rates by Demographic Variable Overall 23048 1724 7.48% Gender Male 11530 50.03% 620 35.96% Female 11517 49.97% 1039 60.27% t Specified 1 0.0 0 0.0
Online grooming: What changes with the new legislation?
 Online grooming: What changes with the new legislation? The use of new technologies has considerably increased in recent years, particularly among young people. In Belgium, 96% of children between 12 to
Online grooming: What changes with the new legislation? The use of new technologies has considerably increased in recent years, particularly among young people. In Belgium, 96% of children between 12 to
Sample Language and Definitions of Prohibited Conduct for a School s Sexual Misconduct Policy
 Sample Language and Definitions of Prohibited Conduct for a School s Sexual Misconduct Policy Under Title IX of the Education Amendments of 1972, any educational institution receiving Federal financial
Sample Language and Definitions of Prohibited Conduct for a School s Sexual Misconduct Policy Under Title IX of the Education Amendments of 1972, any educational institution receiving Federal financial
SOUTH DAKOTA STATE UNIVERSITY Policy and Procedure Manual
 Office/Contact: Office of Human Resources Source: SDBOR Policy 1:17.1 and 1:18 Link: http://www.sdbor.edu/policy/1-governance/documents/1-17-1.pdf http://www.sdbor.edu/policy/1-governance/documents/1-18.pdf
Office/Contact: Office of Human Resources Source: SDBOR Policy 1:17.1 and 1:18 Link: http://www.sdbor.edu/policy/1-governance/documents/1-17-1.pdf http://www.sdbor.edu/policy/1-governance/documents/1-18.pdf
Table A. Characteristics of Respondents that completed the survey
 Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un- weighted Number % Number % Age 18 years old 4,111 8.8 700 8.4 19 years old 8,605 18.3 1,421 17.0 20
Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un- weighted Number % Number % Age 18 years old 4,111 8.8 700 8.4 19 years old 8,605 18.3 1,421 17.0 20
Executive Summary. How extensive is sexual harassment, stalking, and intimate partner violence?
 Executive Summary Summary of Results Members of the Association of American Universities (AAU) are working to combat sexual assault and misconduct on their campuses. As an association of research universities,
Executive Summary Summary of Results Members of the Association of American Universities (AAU) are working to combat sexual assault and misconduct on their campuses. As an association of research universities,
WHAT IS PTSD? A HANDOUT FROM THE NATIONAL CENTER FOR PTSD BY JESSICA HAMBLEN, PHD
 WHAT IS PTSD? A HANDOUT FROM THE NATIONAL CENTER FOR PTSD BY JESSICA HAMBLEN, PHD Posttraumatic Stress Disorder (PTSD) is an anxiety disorder that can occur following the experience or witnessing of a
WHAT IS PTSD? A HANDOUT FROM THE NATIONAL CENTER FOR PTSD BY JESSICA HAMBLEN, PHD Posttraumatic Stress Disorder (PTSD) is an anxiety disorder that can occur following the experience or witnessing of a
Sexual Assault of a Child VOIR DIRE QUESTIONS
 ATTORNEYS Sexual Assault of a Child VOIR DIRE QUESTIONS 1. What are your feelings or opinions about criminal defense attorneys? 2. Have you ever had a bad experience with a criminal defense attorney? If
ATTORNEYS Sexual Assault of a Child VOIR DIRE QUESTIONS 1. What are your feelings or opinions about criminal defense attorneys? 2. Have you ever had a bad experience with a criminal defense attorney? If
JCJR. The Journal of Criminal Justice Research RESEARCH ARTICLE SEXUAL VICTIMIZATION IN SIN CITY
 JCJR The Journal of Criminal Justice Research RESEARCH ARTICLE SEXUAL VICTIMIZATION IN SIN CITY M. Alexis Kennedy, Ph.D. University of Nevada, Las Vegas Lisa Dooley, M.A. University of Nevada, Las Vegas
JCJR The Journal of Criminal Justice Research RESEARCH ARTICLE SEXUAL VICTIMIZATION IN SIN CITY M. Alexis Kennedy, Ph.D. University of Nevada, Las Vegas Lisa Dooley, M.A. University of Nevada, Las Vegas
Know Your Rights NEW YORK STATE: WELFARE TO-WORK
 Know Your Rights NEW YORK STATE: WELFARE TO-WORK 395 Hudson Street New York, NY 10014-3684 t: 212.925.6635 f: 212.226.1066 www.legalmomentum.org Under federal welfare law, New York State receives a block
Know Your Rights NEW YORK STATE: WELFARE TO-WORK 395 Hudson Street New York, NY 10014-3684 t: 212.925.6635 f: 212.226.1066 www.legalmomentum.org Under federal welfare law, New York State receives a block
Scope of Workplace Violence Program 2, 3. Types of Workplace Violence Events 4, 5. Preventative Measures 6, 7. Responding to Workplace Violence 8, 9
 TABLE OF CONTENTS Contents Page Introduction 1 Scope of Workplace Violence Program 2, 3 Types of Workplace Violence Events 4, 5 Preventative Measures 6, 7 Responding to Workplace Violence 8, 9 1 Shasta
TABLE OF CONTENTS Contents Page Introduction 1 Scope of Workplace Violence Program 2, 3 Types of Workplace Violence Events 4, 5 Preventative Measures 6, 7 Responding to Workplace Violence 8, 9 1 Shasta
Table A. Characteristics of Respondents that completed the survey
 Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un-weighted Number % Number % Age 18 years old 759 3.0 228 3.4 19 years old 1,462 5.7 400 6.0 20 years
Table A. Characteristics of Respondents that completed the survey Characteristic Category Weighted Un-weighted Number % Number % Age 18 years old 759 3.0 228 3.4 19 years old 1,462 5.7 400 6.0 20 years
Curriculum Vitae. JAMIE ANN SNYDER, Ph.D. Assistant Professor of Criminal Justice
 Curriculum Vitae JAMIE ANN SNYDER, Ph.D. Assistant Professor of Criminal Justice Office Address College of Professional Studies Department of Criminal Justice Building 85 Room 148 850-474-3409 E-Mail:
Curriculum Vitae JAMIE ANN SNYDER, Ph.D. Assistant Professor of Criminal Justice Office Address College of Professional Studies Department of Criminal Justice Building 85 Room 148 850-474-3409 E-Mail:
The purpose of this policy is to support a comprehensive and collaborative approach to responding to child abuse and neglect by:
 SECTION 1000: STUDENTS AND SCHOOLS POLICY 1045: CHILD PROTECTION Date Adopted: June 18, 2014 POLICY STATEMENT The Board affirms that children have a right to be protected from abuse and neglect, and employees
SECTION 1000: STUDENTS AND SCHOOLS POLICY 1045: CHILD PROTECTION Date Adopted: June 18, 2014 POLICY STATEMENT The Board affirms that children have a right to be protected from abuse and neglect, and employees
Sexual Assault of People in Aged Care Settings: Towards a Better Understanding and Response
 Northern Sydney Sexual Assault Service J Blyth, L Kelly Sexual Assault of People in Aged Care Settings: Towards a Better Understanding and Response In the past 25 years there has been widespread focus
Northern Sydney Sexual Assault Service J Blyth, L Kelly Sexual Assault of People in Aged Care Settings: Towards a Better Understanding and Response In the past 25 years there has been widespread focus
FROM CHARGE TO TRIAL: A GUIDE TO CRIMINAL PROCEEDINGS
 FROM CHARGE TO TRIAL: A GUIDE TO CRIMINAL PROCEEDINGS If you are experiencing, or have experienced, domestic violence and/or sexual violence there are a number of ways the law can protect you. This includes
FROM CHARGE TO TRIAL: A GUIDE TO CRIMINAL PROCEEDINGS If you are experiencing, or have experienced, domestic violence and/or sexual violence there are a number of ways the law can protect you. This includes
Policy on Sexual Assault, Stalking, Dating Violence, and Domestic Violence
 Administrative Regulation 6:2 Responsible Office: Title IX Coordinator / VP Student Affairs Date Effective: 12/3/2014 Supersedes Version: 9/30/2014 (Interim) Policy on Sexual Assault, Stalking, Dating
Administrative Regulation 6:2 Responsible Office: Title IX Coordinator / VP Student Affairs Date Effective: 12/3/2014 Supersedes Version: 9/30/2014 (Interim) Policy on Sexual Assault, Stalking, Dating
Sexual Assault & Domestic Violence: Common Goals, Distinct Differences (Winter 2006) Last Updated Wednesday, August 26, 2009 at 04:01 pm
 The work of the anti-sexual assault and domestic violence movements is clearly interconnected. The pervasive problems of sexual assault and domestic violence are firmly embedded in our society, allowing
The work of the anti-sexual assault and domestic violence movements is clearly interconnected. The pervasive problems of sexual assault and domestic violence are firmly embedded in our society, allowing
Best Practices in Training and Compliance Around Title IX, VAWA and the Clery Act
 Best Practices in Training and Compliance Around Title IX, VAWA and the Clery Act By Sondra Solovay Increasing reports of sexual violence on college campuses across the nation have brought the subject
Best Practices in Training and Compliance Around Title IX, VAWA and the Clery Act By Sondra Solovay Increasing reports of sexual violence on college campuses across the nation have brought the subject
Risky Behaviors and Online Safety: A 2010 Literature Review (DRAFT)
 Risky Behaviors and Online Safety: A 2010 Literature Review (DRAFT) Samantha Biegler and danah boyd Harvard University, Berkman Center for Internet & Society As social media continues to play a central
Risky Behaviors and Online Safety: A 2010 Literature Review (DRAFT) Samantha Biegler and danah boyd Harvard University, Berkman Center for Internet & Society As social media continues to play a central
Current Internet Facts
 Current Internet Facts Facts about Online Predators and Strangers online: Twenty-eight percent of tweens (ages 8 to 12) have been contacted over the Internet by someone they don t know (COX Tween Internet
Current Internet Facts Facts about Online Predators and Strangers online: Twenty-eight percent of tweens (ages 8 to 12) have been contacted over the Internet by someone they don t know (COX Tween Internet
Guidelines for Setting up Security Measures to Stop Domestic Violence in the Workplace
 Guidelines for Setting up Security Measures to Stop Domestic Violence in the Workplace As of June 15, 2010, all employers in Ontario are responsible for protecting workers when domestic violence follows
Guidelines for Setting up Security Measures to Stop Domestic Violence in the Workplace As of June 15, 2010, all employers in Ontario are responsible for protecting workers when domestic violence follows
Landlords Prey on Poor Women by Extorting Sexual Favors in Lieu of Rent
 March 9, 2007 Landlords Prey on Poor Women by Extorting Sexual Favors in Lieu of Rent By Russell Goldman March 8, 2007 For four years Mary lived in fear of her landlord, describing herself as a prisoner
March 9, 2007 Landlords Prey on Poor Women by Extorting Sexual Favors in Lieu of Rent By Russell Goldman March 8, 2007 For four years Mary lived in fear of her landlord, describing herself as a prisoner
Comments made online may be misinterpreted by both receivers and third-parties, which may affect the determination of prevalence of cyberbullying.
 Chapter 7 summaries Cyberbullying definitions and prevalence Many definitions have been offered for cyberbullying. Several of these definitions explicitly or implicitly indicate that the bullying behaviour
Chapter 7 summaries Cyberbullying definitions and prevalence Many definitions have been offered for cyberbullying. Several of these definitions explicitly or implicitly indicate that the bullying behaviour
Brief. Research in SEPT. 04. When Violence Hits Home: How Economics and Neighborhood Play a Role
 SEPT. 04 U.S. Department of Justice Office of Justice Programs National Institute of Justice Research in Brief When Violence Hits Home: How Economics and Neighborhood Play a Role U.S. Department of Justice
SEPT. 04 U.S. Department of Justice Office of Justice Programs National Institute of Justice Research in Brief When Violence Hits Home: How Economics and Neighborhood Play a Role U.S. Department of Justice
Youth Online Behavior
 Youth Online Behavior Created by: Andrea Pieters, Project Researcher, Youth and Education Christine Krupin, Project Researcher, Youth and Education June 1, 2010 Harris Interactive 6/21/2010 1 Methodology
Youth Online Behavior Created by: Andrea Pieters, Project Researcher, Youth and Education Christine Krupin, Project Researcher, Youth and Education June 1, 2010 Harris Interactive 6/21/2010 1 Methodology
SCHOOL DISTRICT NO. 53 (Okanagan Similkameen) POLICY
 SCHOOL DISTRICT NO. 53 (Okanagan Similkameen) POLICY No. F-12 Adopted: June 20, 2012 CHILD PROTECTION Preamble: The Board of Education believes that the health and welfare of a child is an important element
SCHOOL DISTRICT NO. 53 (Okanagan Similkameen) POLICY No. F-12 Adopted: June 20, 2012 CHILD PROTECTION Preamble: The Board of Education believes that the health and welfare of a child is an important element
Digital Citizenship Lesson Plan
 Digital Citizenship Lesson Plan This course is to help people to understand how to use the Internet in a safe, productive way. Additional resources and links are available on the TechTECS website. http://techtecs.com/digital-citizenship
Digital Citizenship Lesson Plan This course is to help people to understand how to use the Internet in a safe, productive way. Additional resources and links are available on the TechTECS website. http://techtecs.com/digital-citizenship
REPORTING AN OFFENCE TO THE POLICE: A GUIDE TO CRIMINAL INVESTIGATIONS
 REPORTING AN OFFENCE TO THE POLICE: A GUIDE TO CRIMINAL INVESTIGATIONS If you are experiencing or have experienced domestic volence and/or sexual violence there are a number of ways the law can protect
REPORTING AN OFFENCE TO THE POLICE: A GUIDE TO CRIMINAL INVESTIGATIONS If you are experiencing or have experienced domestic volence and/or sexual violence there are a number of ways the law can protect
CAMPUS SECURITY INFORMATION ANNUAL CAMPUS SECURITY REPORT-TULSA
 CAMPUS SECURITY INFORMATION ANNUAL CAMPUS SECURITY REPORT-TULSA The following statistics are provided as part of the requirement under the Student Right- To Know and Campus Security Act, Public Law 101-542,
CAMPUS SECURITY INFORMATION ANNUAL CAMPUS SECURITY REPORT-TULSA The following statistics are provided as part of the requirement under the Student Right- To Know and Campus Security Act, Public Law 101-542,
DOMESTIC VIOLENCE AND THE WORKPLACE A TUC SURVEY REPORT
 DOMESTIC VIOLENCE AND THE WORKPLACE A TUC SURVEY REPORT THE BACKGROUND TO THE SURVEY Domestic violence may happen behind closed doors but it has far reaching consequences and is known to have an impact
DOMESTIC VIOLENCE AND THE WORKPLACE A TUC SURVEY REPORT THE BACKGROUND TO THE SURVEY Domestic violence may happen behind closed doors but it has far reaching consequences and is known to have an impact
University of Illinois at Chicago Student Sexual Misconduct and Sexual Violence Interim Policy
 University of Illinois at Chicago Student Sexual Misconduct and Sexual Violence Interim Policy Introduction The University of Illinois at Chicago is committed to creating a safe and secure community for
University of Illinois at Chicago Student Sexual Misconduct and Sexual Violence Interim Policy Introduction The University of Illinois at Chicago is committed to creating a safe and secure community for
For the 10-year aggregate period 2003 12, domestic violence
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report APRIL 2014 NCJ 244697 Nonfatal Domestic Violence, 2003 2012 Jennifer L. Truman, Ph.D., and Rachel E. Morgan,
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report APRIL 2014 NCJ 244697 Nonfatal Domestic Violence, 2003 2012 Jennifer L. Truman, Ph.D., and Rachel E. Morgan,
Abuse in Same-Sex Relationships
 1 Abuse in Same-Sex Relationships Abuse in relationships is any behavior or pattern of behavior used to coerce, dominate or isolate the other partner. It is the use of any form of power that is imposed
1 Abuse in Same-Sex Relationships Abuse in relationships is any behavior or pattern of behavior used to coerce, dominate or isolate the other partner. It is the use of any form of power that is imposed
Lt. Anthony Ritter New Jersey State Police Cyber Crimes Bureau
 Lt. Anthony Ritter New Jersey State Police Cyber Crimes Bureau Good evening, I am Lt. Anthony Ritter of the New Jersey State Police, Cyber Crimes Bureau. I will be taking the next few minutes to explain
Lt. Anthony Ritter New Jersey State Police Cyber Crimes Bureau Good evening, I am Lt. Anthony Ritter of the New Jersey State Police, Cyber Crimes Bureau. I will be taking the next few minutes to explain
SEXUAL HARASSMENT POLICY STATEMENT
 SEXUAL HARASSMENT POLICY STATEMENT The company is committed to providing a workplace that is free from all forms of discrimination, including sexual harassment. Any employee's behavior that fits the definition
SEXUAL HARASSMENT POLICY STATEMENT The company is committed to providing a workplace that is free from all forms of discrimination, including sexual harassment. Any employee's behavior that fits the definition
Human trafficking is the buying and selling of men, women and children within countries and across borders in order to exploit them for profit.
 Learn. Act. Share. Human trafficking is the buying and selling of men, women and children within countries and across borders in order to exploit them for profit. The trafficker takes away the basic human
Learn. Act. Share. Human trafficking is the buying and selling of men, women and children within countries and across borders in order to exploit them for profit. The trafficker takes away the basic human
Internet Crimes Against Children. Sergeant Talia Divita Crimes Against Children Unit WV ICAC Task Force
 Sergeant Talia Divita Crimes Against Children Unit WV ICAC Task Force Crimes Against Children Unit SECTIONS CPU ICAC DFU WVMCC WV3C Crimes Against Children Unit WVSP Organizational Change December 1, 2009
Sergeant Talia Divita Crimes Against Children Unit WV ICAC Task Force Crimes Against Children Unit SECTIONS CPU ICAC DFU WVMCC WV3C Crimes Against Children Unit WVSP Organizational Change December 1, 2009
Social Media: Understanding User Patterns and Compliance Issues. June 2011. Electronic copy available at: http://ssrn.com/abstract=1859443
 Social Media: Understanding User Patterns and Compliance Issues June 2011 Electronic copy available at: http://ssrn.com/abstract=1859443 TABLE OF CONTENTS I. Executive Summary....3 II. Key Findings of
Social Media: Understanding User Patterns and Compliance Issues June 2011 Electronic copy available at: http://ssrn.com/abstract=1859443 TABLE OF CONTENTS I. Executive Summary....3 II. Key Findings of
Facts for Teens: Youth Violence
 P.O. Box 6003 Rockville, MD 20849-6003 [email protected] www.safeyouth.org Facts for Teens: Youth Violence Introduction Many teenagers are concerned about youth violence, and with good reason. Each
P.O. Box 6003 Rockville, MD 20849-6003 [email protected] www.safeyouth.org Facts for Teens: Youth Violence Introduction Many teenagers are concerned about youth violence, and with good reason. Each
Vulnerable Adult & Elder Abuse
 Vulnerable Adult & Elder Abuse Kathleen Flynn Peterson Brandon E. Vaughn September 10, 2013 Introduction Vulnerable adult and elder abuse often have been overlooked because of lack of awareness Abuse,
Vulnerable Adult & Elder Abuse Kathleen Flynn Peterson Brandon E. Vaughn September 10, 2013 Introduction Vulnerable adult and elder abuse often have been overlooked because of lack of awareness Abuse,
In 2013, U.S. residents age 12 or older experienced
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised 9/19/2014 Criminal Victimization, 2013 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians In
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Revised 9/19/2014 Criminal Victimization, 2013 Jennifer L. Truman, Ph.D., and Lynn Langton, Ph.D., BJS Statisticians In
Intimate Partner Violence and Firearms
 Intimate Partner Violence and Firearms According to the Centers for Disease Control and Prevention (CDC), intimate partner violence (IPV) is actual or threatened physical or sexual violence or psychological
Intimate Partner Violence and Firearms According to the Centers for Disease Control and Prevention (CDC), intimate partner violence (IPV) is actual or threatened physical or sexual violence or psychological
A U.S. Postal Inspector s Guide to Internet Safety for Children
 A U.S. Postal Inspector s Guide to Internet Safety for Children A U.S. Postal Inspector s Guide to INTERNET SAFETY FOR CHILDREN The Internet is a global community that allows people to share information
A U.S. Postal Inspector s Guide to Internet Safety for Children A U.S. Postal Inspector s Guide to INTERNET SAFETY FOR CHILDREN The Internet is a global community that allows people to share information
FEMALE PRIVACY AND CLOUD SECURITY 1
 FEMALE PRIVACY AND CLOUD SECURITY 1 Female Privacy and Cloud Security via Smartphones Jasmijn Kol, Dominik Terweh, Judith Weda Cyber-Crime Science 201100221 Prof Dr Pieter Hartel, Prof Dr Marianne Junger
FEMALE PRIVACY AND CLOUD SECURITY 1 Female Privacy and Cloud Security via Smartphones Jasmijn Kol, Dominik Terweh, Judith Weda Cyber-Crime Science 201100221 Prof Dr Pieter Hartel, Prof Dr Marianne Junger
Clustering of Internet Risk Behaviors in a Middle School Student Population
 R ESEARCHA RTICLE Clustering of Internet Risk Behaviors in a Middle School Student Population ELIZABETH B. DOWELL,PhD,RN a ANN W. BURGESS, DNSc, RN b DEBORAH J. CAVANAUGH,MA,MHC c ABSTRACT BACKGROUND:
R ESEARCHA RTICLE Clustering of Internet Risk Behaviors in a Middle School Student Population ELIZABETH B. DOWELL,PhD,RN a ANN W. BURGESS, DNSc, RN b DEBORAH J. CAVANAUGH,MA,MHC c ABSTRACT BACKGROUND:
Domestic Violence Law Reform The Victim s Voice Survey: Victim s Experience of Domestic Violence and the Criminal Justice System
 Domestic Violence Law Reform The Victim s Voice Survey: Victim s Experience of Domestic Violence and the Criminal Justice System FOREWORD We would like to thank all those who took the time to share their
Domestic Violence Law Reform The Victim s Voice Survey: Victim s Experience of Domestic Violence and the Criminal Justice System FOREWORD We would like to thank all those who took the time to share their
PART THREE: TEMPLATE POLICY ON GENDER-BASED VIOLENCE AND THE WORKPLACE
 PART THREE: TEMPLATE POLICY ON GENDER-BASED VIOLENCE AND THE WORKPLACE Draft Organization s Bulletin The Secretary-General, for the purpose of preventing and addressing cases of Genderbased Violence (as
PART THREE: TEMPLATE POLICY ON GENDER-BASED VIOLENCE AND THE WORKPLACE Draft Organization s Bulletin The Secretary-General, for the purpose of preventing and addressing cases of Genderbased Violence (as
Domestic Violence: Can the Legal System Help Protect Me?
 Domestic Violence: Can the Legal System Help Protect Me? What is domestic violence? Domestic violence is a pattern of physically and/or emotionally abusive behavior used to control another person with
Domestic Violence: Can the Legal System Help Protect Me? What is domestic violence? Domestic violence is a pattern of physically and/or emotionally abusive behavior used to control another person with
The Hidden Side of Domestic Abuse: Men abused in intimate relationships
 The Hidden Side of Domestic Abuse: Men abused in intimate relationships 2009 Pandora s Project By: Katy "Men too are victims and women too are perpetrators; neither sex has a monopoly of vice or virtue"
The Hidden Side of Domestic Abuse: Men abused in intimate relationships 2009 Pandora s Project By: Katy "Men too are victims and women too are perpetrators; neither sex has a monopoly of vice or virtue"
14 September 2012. The Director Criminal Law Review NSW Department of Attorney-General and Justice GPO Box 6 SYDNEY NSW 2001
 14 September 2012 The Director Criminal Law Review NSW Department of Attorney-General and Justice GPO Box 6 SYDNEY NSW 2001 By email: [email protected] Dear Director, RE: INQUIRY INTO THE CONSENT PROVISIONS
14 September 2012 The Director Criminal Law Review NSW Department of Attorney-General and Justice GPO Box 6 SYDNEY NSW 2001 By email: [email protected] Dear Director, RE: INQUIRY INTO THE CONSENT PROVISIONS
Dallas Police Department Computer Crimes Unit Cyber-Bullying Sexting And Criminal Consequences
 Dallas Police Department Computer Crimes Unit Cyber-Bullying Sexting And Criminal Consequences Prepared by Detective Russell Stephens Computer Crimes Unit Dallas Police Department 214-671-3545 Cyber-bullying
Dallas Police Department Computer Crimes Unit Cyber-Bullying Sexting And Criminal Consequences Prepared by Detective Russell Stephens Computer Crimes Unit Dallas Police Department 214-671-3545 Cyber-bullying
The Fourth R. A school-based program to prevent adolescent violence and related risk behaviours. Hasslet, Belgium
 A school-based program to prevent adolescent violence and related risk behaviours Hasslet, Belgium Fourth R National Team David Wolfe, Ph.D. RBC Investments Chair in Developmental Psychopathology and
A school-based program to prevent adolescent violence and related risk behaviours Hasslet, Belgium Fourth R National Team David Wolfe, Ph.D. RBC Investments Chair in Developmental Psychopathology and
California State University, Northridge Campus Plan to Address Sexual Assault
 California State University, Northridge Campus Plan to Address Sexual Assault PREPARED BY CHIEF ANNE P. GLAVIN, CHAIR on behalf of THE CSUN SEXUAL ASSAULT COMMITTEE JUNE, 2009 2 California State University,
California State University, Northridge Campus Plan to Address Sexual Assault PREPARED BY CHIEF ANNE P. GLAVIN, CHAIR on behalf of THE CSUN SEXUAL ASSAULT COMMITTEE JUNE, 2009 2 California State University,
Background. Executive Summary
 Background The Interdisciplinary Research Centre in Cyber Security at the University of Kent in Canterbury recently launched a second online survey 1 in order to get a better picture of the prevalence
Background The Interdisciplinary Research Centre in Cyber Security at the University of Kent in Canterbury recently launched a second online survey 1 in order to get a better picture of the prevalence
Domestic Violence Case Management Plan
 Domestic Violence Case Management Plan From the commencement of litigation to its resolution, whether by trial or settlement, it is the goal of this Court to reduce delay and enable just and efficient
Domestic Violence Case Management Plan From the commencement of litigation to its resolution, whether by trial or settlement, it is the goal of this Court to reduce delay and enable just and efficient
STALKING REALITIES AND RESPONSES
 State of New York h Office of the Attorney General STALKING REALITIES AND RESPONSES IF YOU BELIEVE YOU ARE IN IMMEDIATE DANGER, CALL 911 FOR EMERGENCY ASSISTANCE. IF YOU ARE IN AN ABUSIVE SITUATION, DO
State of New York h Office of the Attorney General STALKING REALITIES AND RESPONSES IF YOU BELIEVE YOU ARE IN IMMEDIATE DANGER, CALL 911 FOR EMERGENCY ASSISTANCE. IF YOU ARE IN AN ABUSIVE SITUATION, DO
For the period 1995 2013, females ages 18 to 24 had the
 U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report DECEMBER 2014 NCJ 248471 Rape and Sexual Assault Victimization Among College-Age Females, 1995 2013 Sofi
U.S. Department of Justice Office of Justice Programs Bureau of Justice Statistics Special Report DECEMBER 2014 NCJ 248471 Rape and Sexual Assault Victimization Among College-Age Females, 1995 2013 Sofi
