Setting Policies Using RF Director
|
|
|
- Olivia Small
- 8 years ago
- Views:
Transcription
1 CHAPTER 11 Firewall Configuration Setting Policies Using RF Director Aliases Aliases are a convenient way to associate a human understanable name with a specific object. AirOS enables administrators to assign easily understandable names to network ports (services) and specific IP Addresses or groups of IP Addresses Defining Service Aliases Service aliases apply to protocol/port numbers. Service aliases may be configured in RF Director. Normally only one alias need be defined for a particular service, however some services use more than one protocol. In the case where a service uses multiple protocols, a separate alias must be defined for each protocol. Firewall Configuration 189 Chapter 11
2 Navigate to the Configuration > Security > Advanced > Services page. Add a new Service Alias. Click the Add button. The Add Service page will appear. The options and parameters available for configuration on the Add Service page are: Service Name A plane language name that identifies the alias. NOTE Default service aliases begin with svc- followed by the name of the protocol. Protocol Specify the protocol, either by using the radio buttons or by entering the protocol number ( 0-255). Starting Port Sets the lower port number of a protocol port range. End Port Sets the upper port number of a protocol port range. NOTE If the service uses a single port, enter the starting port number here also. 190 Doc Title Part #######X Doc Type Month YYYY
3 Enter a name in the Service Name text field. Check the appropriate Protocol radio button. Enter the Starting Port. Enter the End Port (If this service uses only a single port, enter the starting port number here). Click Apply and Save Configuration Defining Source and Destination Aliases Source and destination aliases may be configured in RF Director. Source and destination aliases apply to specific IP addresses or groups of IP addresses. The alias is a convenient method to identify these addresses in easily readable way. They are used with traffic policies to specify the source or destination of a packet. Navigate to the Configuration > Security > Advanced > Destinations page. You may add, delete, or modify source and destination aliases on this page. Aruba provides 3 pre-defined aliases which should not be altered or deleted. User Whan applied to an authenticated user the alias is replaced by an IP Addressed assigned to that user. Mswitch Represents the IP Address, loopback address, or VLAN 1 address of the switch upon which the policy is running. Any Represents any IP Address Firewall Configuration 191 Chapter 11
4 Add a new alias by clicking the Add button, the Add Destinations page appears Click the Add button to expand the page and expose the Add Rule section, near the bottom. Enter a name for the new destination in the Destination Name text box. Select a rule type using the Rule Type pull-down menu. The choices for rule types are: Host Use this selection to specify a single address. Do not enter anything in the Network Mask/Range field. Network Use this selection when specifying an IP subnet. It comprises a Range Use this selection when specifying an sequential range of IP Addresses. When specifying a range enter the upper address in the Network Mask/Range field. The maximum number of addresses is 16 when specifying a range. 4 5 Enter an IP Address in the IP Address field. Enter a netmask or upper address of an IP range in the Network Mask/Range field. 192 Doc Title Part #######X Doc Type Month YYYY
5 NOTE If you wish to specify a range with more than 16 addresses, select the Network Rule Type then enter network number and subnet mask in the IP Address and Network Mask fields. 6 Click Add, then click Apply and Save Configuration. Firewall Policies Aruba AirOS firewall policies are stateful and bi-directional. Stateful policies mean that when a packet matches a rule, they must match exactly, the policy will creat a session entry so that the session may continue in both directions. Firewall policies consist of a set of rules that are applied in a specific order against network traffic presented at the firewall. The rule at the top of the list is applied first. Rules are organized in top-down lists where the first rule applied to the traffic is at the top of the list. Traffic is tested against each rule in order until a match is found. When a match occurs the rule is applied and no other testing occurs. Policies can be applied to physical ports or to user roles. Navigate to the Configuration > Security > Policies page. From the Firwall Policies page you may Edit, Delete, or Add policies. Firewall Configuration 193 Chapter 11
6 Rules in Firewall Policies. Rules in firewall policies are applied to traffic that presents itself to the switch. Rules examine the source address, destination address, and the kind of information (service) the packet contains. The Source and Destination elements of a rule have the same 5 options. Those options are: any This option will test true for traffic from any source or to any destination. user This option will test true only for traffic to or from a known user. host This option will test true only for traffic to or from a specific IP Address. network This option will test true only for traffic to or from a network specified by a network address and subnet mask alias This option willtest true only for traffic to or from the address or addresses defined in a specified alias, see Defining Source and Destination Aliases on page 191. The Service element of a rule has 5 options. Those options are: any This option will test true for any type of traffic. tcp This option will test true for only tcp traffic. udp This option will test true for only udp traffic.. service This option will test true for only traffic to or from a specified service alias. protocol This option will test true for only traffic with a specified protocol number. The Action element of a rule has 5 options. Those options are: Permit Forward the packet without modification. Deny Drop the packet with no notification. src-nat Change the source IP address of the packet and forward it. If no source NAT pool is specified the IP address of the Aruba switch will be substituted for the original source address. 194 Doc Title Part #######X Doc Type Month YYYY
7 dst-net Change the destination IP address of the packed and to the switch IP address and forward it. redirect Add a policy by clicking on the Add button, the Add New Policy page appears. The Add New Policy page is where you name your new policy and define rules for that policy Enter a meaningful name in the Policy Name field at the right hand side of the page. Select a traffic source from the Source pull-down menu. Select a traffic destination from the Destination pull-down menu. Select an action from the Action pull-down menu. Select Log in you wish each packet matching this rule to be recorded in the systam logfile. Set a queue priority, high or low by selecting the cooresponding Queue radio button. Queue priority sets the priority of outbound wireless traffic. Click Add. When you are done adding rules, click Apply and Save Configuration. Firewall Configuration 195 Chapter 11
8 Applying Policies to Physical Ports Policies may be applied to either physical ports or user roles. Navigate to the Configuration > Switch > Port page. Select the port to which you wish to apply a policy, then use the pull-down menu to select a policy to apply. Click Apply and Save Configuration. 196 Doc Title Part #######X Doc Type Month YYYY
9 Defining Roles Using RF Director Role Design A role is assigned to a user when they connect to the network, and possibly again after they are authenticated. Roles determine what network resources the user may access. Roles may be very broad-based,allowing access to many resources or they may be very narrow in scope, allowing access to very limited resources. Sometimes, a role is used to grant a particular user, or group of users, access to a specific resource that other users are not. Configuring Roles Navigate to the Configuration > Security > Roles page to view roles. Firewall Configuration 197 Chapter 11
10 Click the Add button to begin adding a new role to the list. The Add Role page will appear. 198 Doc Title Part #######X Doc Type Month YYYY
11 Adding Firewall Policies Add firewall policies, begin by clicking the Add button under the Firewall Policies header on the page. The Configure Firewall Policy page then appears. You may choose one of three options on this page: Specify an existing policy. Create a new policy using an existing policy as a model. Create a new policy from scratch Specify an existing policy. Select the Choose from Configured Policies radio box. Specify a particular AP ( if you wish to apply this policy only when using the specifed AP) by entering the its location in the Location text box. Click Done. Create a New Policy From an Existing Policy Select the Create New Policy From Existing Policy radio button. Firewall Configuration 199 Chapter 11
12 2 Click the Creat button. The Add New Policy page appears Create a new policy in exactly the same way you would in Firewall Policies on page 193. Create a New Policy from Scratch Select the Create New Policy radio button. Click Create. The Add New Policy page appears. Create a new policy in exactly the same way you would in Firewall Policies on page Doc Title Part #######X Doc Type Month YYYY
13 Configuring Other Policy Options In addition to creating new policies for a role, you may add or adjust 6 additional options. Re-authentication Interval By default a user will remain authenticated until the login session is terminated. Use this option to force periodic re-authentication. Role VLAN ID When a VLAN is specified for this option, the user will be mapped to that VLAN. NOTE This option only applies if authentication is done at Layer 2. Bandwidth Contract This option applies a bandwidth contract to the role. VPN Dialer Use this option to assign a specific VPN dialer to a user role. For more information about configuring VPN dialers, see VPN Configuration on page 207. L2TP Pool Use this option to specify the address pool from which a VPN user will be assigned an IP address when the user negotiates an L2TP/IPSEC session. For more information see VPN Configuration on page 207. PPTP Pool Use this option to specify the address pool from which a VPN user will be assigned an IP address when that user negotiates a PPTP session. For more information see VPN Configuration on page 207. Firewall Configuration 201 Chapter 11
14 Setting Policies Using the CLI This portion of the chapter describes the process of configuring firewall (traffic) policies using the Command Line Interface. The processed describe here mirror the processes in the first part of the chapter which describes firewall configuration using RF Director, a web-based graphical user interface. Defining Service Aliases Define a service alias using the netservice <name> {ProtocolNum TCP <startaddr> <endaddr> UDP <startaddr> <endaddr>}command from the CLI. You may define a service alias by giving it a name, then choosing to specify one of three options:. UDP Use this option to specify UDP as the service. Specify a port for the service by including a single value after the UDP specifier or a range of ports by including two values representing startaddr and endaddr. The valid range for ports is TCP Use this option to specify TCP as the service. Specify a port for the service by including a single value after the UDP specifier or a range of ports by including two values representing startaddr and endaddr. The valid range for ports is Protocol Number Use this option to specify the service by its protocol number. No port or port range may be specified when using this option. Define the service alias. (Aruba) (config) #netservice svc-foo-udp udp (Aruba) (config) #netservice svc-foo-tcp tcp (Aruba) (config) #netservice svc-foo-chaos Doc Title Part #######X Doc Type Month YYYY
15 The current service alias configurations may be viewed using the show netservice command from the CLI. (Aruba) (config) #show netservice Services Name Protocol Ports svc-snmp-trap udp 162 svc-syslog udp 514 svc-l2tp udp 1701 svc-ike udp 500 svc-https tcp 443 svc-smb-tcp tcp 445 svc-dhcp udp Defining Source and Destination Aliases Define a source/destination alias and enter the config-dest mode using the netdestination <name> command from the CLI. After entering the config-dest mode you may specify one of 3 types of destinations for your alias: host Use this command to specify a specific host IP address for the alias. network Use this command to specify a network or sub-net as a soruce or destination. Specify a network number followed by a subnet mask. range Use this command to specify a range of valid IP addresses. Specify the lower address followed by the higher. 1 Enter the config-dest mode and define the name for the alias (Aruba) (config) #netdestination dest-foo-any 2 Configure the alias as host with an IP address of (Aruba) (config-dest) #host Firewall Configuration 203 Chapter 11
16 Firewall Policies Firewall policies are configured using the ip access-list session <name> command from the CLI. 1 Enter the config-sess-aclname mode. (Aruba) (config) #ip access-list session foo-acl (Aruba) (config-sess-foo-acl)# 2 Enter rules in the order you wish them to be applied. (Aruba) (config-sess-foo-acl)# user alias Int_net svc-dhcp permit (Aruba) (config-sess-foo-acl)# user alias Int_net svc-dns permit (Aruba) (config-sess-foo-acl)# user any svc-http permit (Aruba) (config-sess-foo-acl)# user any svc-https permit (Aruba) (config-sess-foo-acl)# user any svc-ike permit (Aruba) (config-sess-foo-acl)# user any any deny If you wish to change the position of a rule in the list, use the position option to move the rule to a specific line. (Aruba) (config-sess-foo-acl)# user any svc-ike permit position 3 Use the show access-list <aclname> command from the CLI to view a specific firewall policy. Use the show access-list brief command to see a listing of the current ACLs (Aruba) (config) #show access-list brief Access list table Name Type Use Count Roles control session 4 logon ap-role stateful guest captiveportal session 1 logon allowall session 1 trusted-ap vpnlogon session 1 logon cplogout session 1 guest guest session 0 stateful-dot1x session 0 ap-acl session 1 ap-role stateful-kerberos session Doc Title Part #######X Doc Type Month YYYY
17 Applying Policies to Physical Ports Add a policy to a specific port from the CLI using the interface fastethernet mode commands. 1 Enter the config-if mode. (Aruba) (config) #interface fastethernet 1/22 (Aruba) (config-if)# 2 Assign a policy to a the port used when entering the config-if mode. (Aruba) (config-if)#ip access-group guest session Defining Roles Using the CLI Configuring Roles Roles are configured in the CLI using the config-role mode commands. Define a user role and enter the config-role mode. (Aruba) (config) #user-role foo-user (Aruba) (config-role) # Begin to enter the role parameters. (Aruba) (config-role) #dialer default-dialer (Aruba) (config-role) #pool pptp-pool-1 Firewall Configuration 205 Chapter 11
18 Defining Access Control Lists in the CLI ACL are applied to physical interfaces using the ip access-group command in the CLI. (Aruba) (config) #ip access-list standard foo-1 (Aruba) (config-std-foo-1)# Standard ACLs Create standard ACLs using the standard option of the access-list command. (Aruba) (config-std-foo-1)# permit (Aruba) (config-std-foo-1)# permit host (Aruba) (config-std-foo-1)# deny any Extended ACLs Create extended ACLs using the extended option of the access-list command. (Aruba) (config) #ip access-list extended foo-ext-1 (Aruba) (config-ext-foo-ext-1)# permit tcp any host range (Aruba) (config-ext-foo-ext-1)#permit icmp any echo-reply MAC ACLs Create MAC ACLs using the mac option of the access-list command. (Aruba) (config) #ip access-list mac foo-mac-1 (Aruba) (config-mac-foo-mac-1)# permit host 00:01:01:03:04:05 (Aruba) (config-mac-foo-mac-1)# permit 00:0a:ff:02:ad:01 ff:ff:ff:00:00: Doc Title Part #######X Doc Type Month YYYY
19 Ethertype ACLs Create Ethertype ACLs using the eth option of the access-list command. (Aruba) (config) #ip access-list eth foo-eth-1 (Aruba) (config-eth-foo-eth-1)# permit 2048 Firewall Configuration 207 Chapter 11
20 208 Doc Title Part #######X Doc Type Month YYYY
Firewall Defaults and Some Basic Rules
 Firewall Defaults and Some Basic Rules ProSecure UTM Quick Start Guide This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSecure Unified
Firewall Defaults and Some Basic Rules ProSecure UTM Quick Start Guide This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSecure Unified
ArubaOS v2.4. User Guide
 ArubaOS v2.4 User Guide TM ArubsOS v2.4: User Guide Copyright Copyright 2005 Aruba Wireless Networks, Inc. All rights reserved. Specifications in this manual are subject to change without notice. Originated
ArubaOS v2.4 User Guide TM ArubsOS v2.4: User Guide Copyright Copyright 2005 Aruba Wireless Networks, Inc. All rights reserved. Specifications in this manual are subject to change without notice. Originated
Appendix A: Configuring Firewalls for a VPN Server Running Windows Server 2003
 http://technet.microsoft.com/en-us/library/cc757501(ws.10).aspx Appendix A: Configuring Firewalls for a VPN Server Running Windows Server 2003 Updated: October 7, 2005 Applies To: Windows Server 2003 with
http://technet.microsoft.com/en-us/library/cc757501(ws.10).aspx Appendix A: Configuring Firewalls for a VPN Server Running Windows Server 2003 Updated: October 7, 2005 Applies To: Windows Server 2003 with
Configuring IP Load Sharing in AOS Quick Configuration Guide
 Configuring IP Load Sharing in AOS Quick Configuration Guide ADTRAN Operating System (AOS) includes IP Load Sharing for balancing outbound IP traffic across multiple interfaces. This feature can be used
Configuring IP Load Sharing in AOS Quick Configuration Guide ADTRAN Operating System (AOS) includes IP Load Sharing for balancing outbound IP traffic across multiple interfaces. This feature can be used
To configure firewall policies, you must install the Policy Enforcement Firewall license.
 2. Select either the AP Group or AP Specific tab. Click Edit for the AP group or AP name. 3. Under Profiles, select AP to display the AP profiles. 4. Select the AP system profile you want to modify. 5.
2. Select either the AP Group or AP Specific tab. Click Edit for the AP group or AP name. 3. Under Profiles, select AP to display the AP profiles. 4. Select the AP system profile you want to modify. 5.
Chapter 3 Using Access Control Lists (ACLs)
 Chapter 3 Using Access Control Lists (ACLs) Access control lists (ACLs) enable you to permit or deny packets based on source and destination IP address, IP protocol information, or TCP or UDP protocol
Chapter 3 Using Access Control Lists (ACLs) Access control lists (ACLs) enable you to permit or deny packets based on source and destination IP address, IP protocol information, or TCP or UDP protocol
Using the NetVanta 7100 Series
 MENU OK CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL 1 2
MENU OK CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL CANCEL 1 2 3 4 5 6 7 8 9 * 0 # MENU OK CANCEL 1 2
Adding an Extended Access List
 CHAPTER 11 This chapter describes how to configure extended access lists (also known as access control lists), and it includes the following topics: Information About Extended Access Lists, page 11-1 Licensing
CHAPTER 11 This chapter describes how to configure extended access lists (also known as access control lists), and it includes the following topics: Information About Extended Access Lists, page 11-1 Licensing
How To: Configure a Cisco ASA 5505 for Video Conferencing
 How To: Configure a Cisco ASA 5505 for Video Conferencing There are five main items which will need to be addressed in order to successfully permit H.323 video conferencing traffic through the Cisco ASA.
How To: Configure a Cisco ASA 5505 for Video Conferencing There are five main items which will need to be addressed in order to successfully permit H.323 video conferencing traffic through the Cisco ASA.
1:1 NAT in ZeroShell. Requirements. Overview. Network Setup
 1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
Multi-Homing Security Gateway
 Multi-Homing Security Gateway MH-5000 Quick Installation Guide 1 Before You Begin It s best to use a computer with an Ethernet adapter for configuring the MH-5000. The default IP address for the MH-5000
Multi-Homing Security Gateway MH-5000 Quick Installation Guide 1 Before You Begin It s best to use a computer with an Ethernet adapter for configuring the MH-5000. The default IP address for the MH-5000
Configuring the BIG-IP and Check Point VPN-1 /FireWall-1
 Configuring the BIG-IP and Check Point VPN-1 /FireWall-1 Introducing the BIG-IP and Check Point VPN-1/FireWall-1 LB, HALB, VPN, and ELA configurations Configuring the BIG-IP and Check Point FireWall-1
Configuring the BIG-IP and Check Point VPN-1 /FireWall-1 Introducing the BIG-IP and Check Point VPN-1/FireWall-1 LB, HALB, VPN, and ELA configurations Configuring the BIG-IP and Check Point FireWall-1
Configuration Guide for RFMS 3.0 Initial Configuration. WiNG5 How-To Guide. Network Address Translation. July 2011 Revision 1.0
 Configuration Guide for RFMS 3.0 Initial Configuration XXX-XXXXXX-XX WiNG5 How-To Guide Network Address Translation July 2011 Revision 1.0 MOTOROLA and the Stylized M Logo are registered in the US Patent
Configuration Guide for RFMS 3.0 Initial Configuration XXX-XXXXXX-XX WiNG5 How-To Guide Network Address Translation July 2011 Revision 1.0 MOTOROLA and the Stylized M Logo are registered in the US Patent
Configuring Network Address Translation (NAT)
 8 Configuring Network Address Translation (NAT) Contents Overview...................................................... 8-3 Translating Between an Inside and an Outside Network........... 8-3 Local and
8 Configuring Network Address Translation (NAT) Contents Overview...................................................... 8-3 Translating Between an Inside and an Outside Network........... 8-3 Local and
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address
 Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
Firewall Defaults, Public Server Rule, and Secondary WAN IP Address This quick start guide provides the firewall defaults and explains how to configure some basic firewall rules for the ProSafe Wireless-N
Lab 8.3.13 Configure Cisco IOS Firewall CBAC
 Lab 8.3.13 Configure Cisco IOS Firewall CBAC Objective Scenario Topology In this lab, the students will complete the following tasks: Configure a simple firewall including CBAC using the Security Device
Lab 8.3.13 Configure Cisco IOS Firewall CBAC Objective Scenario Topology In this lab, the students will complete the following tasks: Configure a simple firewall including CBAC using the Security Device
Lab 8.4.2 Configuring Access Policies and DMZ Settings
 Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
Lab 8.4.2 Configuring Access Policies and DMZ Settings Objectives Log in to a multi-function device and view security settings. Set up Internet access policies based on IP address and application. Set
How To Block On A Network With A Group Control On A Router On A Linux Box On A Pc Or Ip Access Group On A Pnet 2 On A 2G Router On An Ip Access-Group On A Ip Ip-Control On A Net
 Using Access-groups to Block/Allow Traffic in AOS When setting up an AOS unit, it is important to control which traffic is allowed in and out. In many cases, the built-in AOS firewall is the most efficient
Using Access-groups to Block/Allow Traffic in AOS When setting up an AOS unit, it is important to control which traffic is allowed in and out. In many cases, the built-in AOS firewall is the most efficient
This chapter describes how to set up and manage VPN service in Mac OS X Server.
 6 Working with VPN Service 6 This chapter describes how to set up and manage VPN service in Mac OS X Server. By configuring a Virtual Private Network (VPN) on your server you can give users a more secure
6 Working with VPN Service 6 This chapter describes how to set up and manage VPN service in Mac OS X Server. By configuring a Virtual Private Network (VPN) on your server you can give users a more secure
10.3.1.8 Lab - Configure a Windows 7 Firewall
 5.0 10.3.1.8 Lab - Configure a Windows 7 Firewall Print and complete this lab. In this lab, you will explore the Windows 7 Firewall and configure some advanced settings. Recommended Equipment Step 1 Two
5.0 10.3.1.8 Lab - Configure a Windows 7 Firewall Print and complete this lab. In this lab, you will explore the Windows 7 Firewall and configure some advanced settings. Recommended Equipment Step 1 Two
Chapter 2 Quality of Service (QoS)
 Chapter 2 Quality of Service (QoS) Software release 06.6.X provides the following enhancements to QoS on the HP 9304M, HP 9308M, and HP 6208M-SX routing switches. You can choose between a strict queuing
Chapter 2 Quality of Service (QoS) Software release 06.6.X provides the following enhancements to QoS on the HP 9304M, HP 9308M, and HP 6208M-SX routing switches. You can choose between a strict queuing
FSM73xx GSM73xx GMS72xxR Shared access to the Internet across Multiple routing VLANs using a Prosafe Firewall
 FSM73xx GSM73xx GMS72xxR Shared access to the Internet across Multiple routing VLANs using a Prosafe Firewall This document describes how to: - Create multiple routing VLANs - Obtain Internet access on
FSM73xx GSM73xx GMS72xxR Shared access to the Internet across Multiple routing VLANs using a Prosafe Firewall This document describes how to: - Create multiple routing VLANs - Obtain Internet access on
Chapter 3 LAN Configuration
 Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
Securepoint Network Access Controller (NAC)
 Securepoint Network Access Controller (NAC) Administration Guide Business Class Secure Mobility Version 1 2 Securepoint NAC Administration Guide 1 Table of contents 1 Table of contents... 2 2 Table of
Securepoint Network Access Controller (NAC) Administration Guide Business Class Secure Mobility Version 1 2 Securepoint NAC Administration Guide 1 Table of contents 1 Table of contents... 2 2 Table of
In this lab you will explore the Windows XP Firewall and configure some advanced settings.
 16.3.2 Lab: Configure Windows XP Firewall Print and complete this lab. In this lab you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Two computers directly
16.3.2 Lab: Configure Windows XP Firewall Print and complete this lab. In this lab you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Two computers directly
Configuring IPSec VPN Tunnel between NetScreen Remote Client and RN300
 Configuring IPSec VPN Tunnel between NetScreen Remote Client and RN300 This example explains how to configure pre-shared key based simple IPSec tunnel between NetScreen Remote Client and RN300 VPN Gateway.
Configuring IPSec VPN Tunnel between NetScreen Remote Client and RN300 This example explains how to configure pre-shared key based simple IPSec tunnel between NetScreen Remote Client and RN300 VPN Gateway.
Network Load Balancing
 Network Load Balancing Step by Step installation of Network Load Balancing in Windows Server 2008 R2. Prerequisite for NLB Cluster 1. Log on to NODE1 Windows Server 2008 R2 system with a domain account
Network Load Balancing Step by Step installation of Network Load Balancing in Windows Server 2008 R2. Prerequisite for NLB Cluster 1. Log on to NODE1 Windows Server 2008 R2 system with a domain account
Chapter 9 Monitoring System Performance
 Chapter 9 Monitoring System Performance This chapter describes the full set of system monitoring features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. You can be alerted to important
Chapter 9 Monitoring System Performance This chapter describes the full set of system monitoring features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. You can be alerted to important
INTEGRATION GUIDE. DIGIPASS Authentication for Cisco ASA 5505
 INTEGRATION GUIDE DIGIPASS Authentication for Cisco ASA 5505 Disclaimer DIGIPASS Authentication for Cisco ASA5505 Disclaimer of Warranties and Limitation of Liabilities All information contained in this
INTEGRATION GUIDE DIGIPASS Authentication for Cisco ASA 5505 Disclaimer DIGIPASS Authentication for Cisco ASA5505 Disclaimer of Warranties and Limitation of Liabilities All information contained in this
This Technical Support Note shows the different options available in the Firewall menu of the ADTRAN OS Web GUI.
 TECHNICAL SUPPORT NOTE Introduction to the Firewall Menu in the Web GUI Featuring ADTRAN OS and the Web GUI Introduction This Technical Support Note shows the different options available in the Firewall
TECHNICAL SUPPORT NOTE Introduction to the Firewall Menu in the Web GUI Featuring ADTRAN OS and the Web GUI Introduction This Technical Support Note shows the different options available in the Firewall
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding
 Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
10.3.1.10 Lab - Configure a Windows XP Firewall
 5.0 10.3.1.10 Lab - Configure a Windows XP Firewall Print and complete this lab. In this lab, you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Step 1
5.0 10.3.1.10 Lab - Configure a Windows XP Firewall Print and complete this lab. In this lab, you will explore the Windows XP Firewall and configure some advanced settings. Recommended Equipment Step 1
RSA Security Analytics
 RSA Security Analytics Event Source Log Configuration Guide Cisco IOS Last Modified: Thursday, February 19, 2015 Event Source Product Information: Vendor: Cisco Event Source: IOS Versions: IOS 12.4, 15.x
RSA Security Analytics Event Source Log Configuration Guide Cisco IOS Last Modified: Thursday, February 19, 2015 Event Source Product Information: Vendor: Cisco Event Source: IOS Versions: IOS 12.4, 15.x
Configuring NetFlow Secure Event Logging (NSEL)
 73 CHAPTER This chapter describes how to configure NSEL, a security logging mechanism that is built on NetFlow Version 9 technology, and how to handle events and syslog messages through NSEL. The chapter
73 CHAPTER This chapter describes how to configure NSEL, a security logging mechanism that is built on NetFlow Version 9 technology, and how to handle events and syslog messages through NSEL. The chapter
Configuring Class Maps and Policy Maps
 CHAPTER 4 Configuring Class Maps and Policy Maps This chapter describes how to configure class maps and policy maps to provide a global level of classification for filtering traffic received by or passing
CHAPTER 4 Configuring Class Maps and Policy Maps This chapter describes how to configure class maps and policy maps to provide a global level of classification for filtering traffic received by or passing
PIX/ASA: Allow Remote Desktop Protocol Connection through the Security Appliance Configuration Example
 PIX/ASA: Allow Remote Desktop Protocol Connection through the Security Appliance Configuration Example Document ID: 77869 Contents Introduction Prerequisites Requirements Components Used Related Products
PIX/ASA: Allow Remote Desktop Protocol Connection through the Security Appliance Configuration Example Document ID: 77869 Contents Introduction Prerequisites Requirements Components Used Related Products
Deployment Guide AX Series for Palo Alto Networks Firewall Load Balancing
 Deployment Guide AX Series for Palo Alto Networks Firewall Load Balancing DG_PAFWLB_120718.1 TABLE OF CONTENTS 1 Overview... 4 2 Deployment Prerequisites... 4 3 Architecture Overview... 5 4 Access Credentials...
Deployment Guide AX Series for Palo Alto Networks Firewall Load Balancing DG_PAFWLB_120718.1 TABLE OF CONTENTS 1 Overview... 4 2 Deployment Prerequisites... 4 3 Architecture Overview... 5 4 Access Credentials...
ARUBA WIRELESS AND CLEARPASS 6 INTEGRATION GUIDE. Technical Note
 ARUBA WIRELESS AND CLEARPASS 6 INTEGRATION GUIDE Technical Note Copyright 2013 Aruba Networks, Inc. Aruba Networks trademarks include, Aruba Networks, Aruba Wireless Networks, the registered Aruba the
ARUBA WIRELESS AND CLEARPASS 6 INTEGRATION GUIDE Technical Note Copyright 2013 Aruba Networks, Inc. Aruba Networks trademarks include, Aruba Networks, Aruba Wireless Networks, the registered Aruba the
How To Configure Apple ipad for Cyberoam L2TP
 How To Configure Apple ipad for Cyberoam L2TP VPN Connection Applicable to Version: 10.00 (All builds) Layer 2 Tunneling Protocol (L2TP) can be used to create VPN tunnel over public networks such as the
How To Configure Apple ipad for Cyberoam L2TP VPN Connection Applicable to Version: 10.00 (All builds) Layer 2 Tunneling Protocol (L2TP) can be used to create VPN tunnel over public networks such as the
Chapter 4 Firewall Protection and Content Filtering
 Chapter 4 Firewall Protection and Content Filtering This chapter describes how to use the content filtering features of the ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN to protect your network.
Chapter 4 Firewall Protection and Content Filtering This chapter describes how to use the content filtering features of the ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN to protect your network.
VMware vcloud Air Networking Guide
 vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
FIREWALLS & CBAC. philip.heimer@hh.se
 FIREWALLS & CBAC philip.heimer@hh.se Implementing a Firewall Personal software firewall a software that is installed on a single PC to protect only that PC All-in-one firewall can be a single device that
FIREWALLS & CBAC philip.heimer@hh.se Implementing a Firewall Personal software firewall a software that is installed on a single PC to protect only that PC All-in-one firewall can be a single device that
Guest Access with ArubaOS. Version 1.0
 Version 1.0 Copyright 2012 Aruba Networks, Inc. AirWave, Aruba Networks, Aruba Mobility Management System, Bluescanner, For Wireless That Works, Mobile Edge Architecture, People Move. Networks Must Follow,
Version 1.0 Copyright 2012 Aruba Networks, Inc. AirWave, Aruba Networks, Aruba Mobility Management System, Bluescanner, For Wireless That Works, Mobile Edge Architecture, People Move. Networks Must Follow,
10.3.1.9 Lab - Configure a Windows Vista Firewall
 5.0 10.3.1.9 Lab - Configure a Windows Vista Firewall Print and complete this lab. In this lab, you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Step
5.0 10.3.1.9 Lab - Configure a Windows Vista Firewall Print and complete this lab. In this lab, you will explore the Windows Vista Firewall and configure some advanced settings. Recommended Equipment Step
FortiGate High Availability Overview Technical Note
 FortiGate High Availability Overview Technical Note FortiGate High Availability Overview Technical Note Document Version: 2 Publication Date: 21 October, 2005 Description: This document provides an overview
FortiGate High Availability Overview Technical Note FortiGate High Availability Overview Technical Note Document Version: 2 Publication Date: 21 October, 2005 Description: This document provides an overview
Chapter 6 Virtual Private Networking Using SSL Connections
 Chapter 6 Virtual Private Networking Using SSL Connections The FVS336G ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN provides a hardwarebased SSL VPN solution designed specifically to provide
Chapter 6 Virtual Private Networking Using SSL Connections The FVS336G ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN provides a hardwarebased SSL VPN solution designed specifically to provide
CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC
 CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC 1 Introduction Release date: 11/12/2003 This application note details the steps for creating an IKE IPSec VPN tunnel
CREATING AN IKE IPSEC TUNNEL BETWEEN AN INTERNET SECURITY ROUTER AND A WINDOWS 2000/XP PC 1 Introduction Release date: 11/12/2003 This application note details the steps for creating an IKE IPSec VPN tunnel
MilsVPN VPN Tunnel Port Translation. Table of Contents...1 1. Introduction...2 2. VPN Tunnel Settings...2
 Page 1 of 8 Table of Contents Table of Contents...1 1. Introduction...2 2. VPN Tunnel Settings...2 2.1 VPN Settings...2 2.2 MilsVPN Service Properties...3 3. Service Object Creation...3 4. Firewall rules
Page 1 of 8 Table of Contents Table of Contents...1 1. Introduction...2 2. VPN Tunnel Settings...2 2.1 VPN Settings...2 2.2 MilsVPN Service Properties...3 3. Service Object Creation...3 4. Firewall rules
Deploying the Barracuda Link Balancer with Cisco ASA VPN Tunnels
 Deploying the Barracuda Link Balancer with Cisco ASA VPN Tunnels This article provides a reference for deploying a Barracuda Link Balancer under the following conditions: 1. 2. In transparent (firewall-disabled)
Deploying the Barracuda Link Balancer with Cisco ASA VPN Tunnels This article provides a reference for deploying a Barracuda Link Balancer under the following conditions: 1. 2. In transparent (firewall-disabled)
Configuring NetFlow Secure Event Logging (NSEL)
 75 CHAPTER This chapter describes how to configure NSEL, a security logging mechanism that is built on NetFlow Version 9 technology, and how to handle events and syslog messages through NSEL. The chapter
75 CHAPTER This chapter describes how to configure NSEL, a security logging mechanism that is built on NetFlow Version 9 technology, and how to handle events and syslog messages through NSEL. The chapter
About Firewall Protection
 1. This guide describes how to configure basic firewall rules in the UTM to protect your network. The firewall then can provide secure, encrypted communications between your local network and a remote
1. This guide describes how to configure basic firewall rules in the UTM to protect your network. The firewall then can provide secure, encrypted communications between your local network and a remote
Configuration Guide for RFMS 3.0 Initial Configuration. WiNG 5 How-To Guide. Firewall. June 2011 Revision 1.0
 Configuration Guide for RFMS 3.0 Initial Configuration XXX-XXXXXX-XX WiNG 5 How-To Guide Firewall June 2011 Revision 1.0 MOTOROLA and the Stylized M Logo are registered in the US Patent & Trademark Office.
Configuration Guide for RFMS 3.0 Initial Configuration XXX-XXXXXX-XX WiNG 5 How-To Guide Firewall June 2011 Revision 1.0 MOTOROLA and the Stylized M Logo are registered in the US Patent & Trademark Office.
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-2685 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P.
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-2685 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P.
Quality of Service (QoS) Setup Guide (NB604n)
 Quality of Service (QoS) Setup Guide (NB604n) NB604n and Quality of Service (QoS) The following Quality of Service (QoS) settings offer a basic setup example, setting up 2 devices connecting to an NB604n
Quality of Service (QoS) Setup Guide (NB604n) NB604n and Quality of Service (QoS) The following Quality of Service (QoS) settings offer a basic setup example, setting up 2 devices connecting to an NB604n
Configuring a FortiGate unit as an L2TP/IPsec server
 Configuring a FortiGate unit as an L2TP/IPsec server The FortiGate implementation of L2TP enables a remote dialup client to establish an L2TP/IPsec tunnel with the FortiGate unit directly. Creating an
Configuring a FortiGate unit as an L2TP/IPsec server The FortiGate implementation of L2TP enables a remote dialup client to establish an L2TP/IPsec tunnel with the FortiGate unit directly. Creating an
How To Authenticate An Ssl Vpn With Libap On A Safeprocess On A Libp Server On A Fortigate On A Pc Or Ipad On A Ipad Or Ipa On A Macbook Or Ipod On A Network
 Authenticating SSL VPN users using LDAP This example illustrates how to configure a FortiGate to use LDAP authentication to authenticate remote SSL VPN users. With a properly configured LDAP server, user
Authenticating SSL VPN users using LDAP This example illustrates how to configure a FortiGate to use LDAP authentication to authenticate remote SSL VPN users. With a properly configured LDAP server, user
Flow Monitor Configuration. Content CHAPTER 1 MIRROR CONFIGURATION... 1-1 CHAPTER 2 RSPAN CONFIGURATION... 2-1 CHAPTER 3 SFLOW CONFIGURATION...
 Content Content CHAPTER 1 MIRROR CONFIGURATION... 1-1 1.1 INTRODUCTION TO MIRROR... 1-1 1.2 MIRROR CONFIGURATION TASK LIST 1.3 MIRROR EXAMPLES 1.4 DEVICE MIRROR TROUBLESHOOTING... 1-1... 1-2... 1-3 CHAPTER
Content Content CHAPTER 1 MIRROR CONFIGURATION... 1-1 1.1 INTRODUCTION TO MIRROR... 1-1 1.2 MIRROR CONFIGURATION TASK LIST 1.3 MIRROR EXAMPLES 1.4 DEVICE MIRROR TROUBLESHOOTING... 1-1... 1-2... 1-3 CHAPTER
Firewall VPN Router. Quick Installation Guide M73-APO09-380
 Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Topic 7 DHCP and NAT. Networking BAsics.
 Topic 7 DHCP and NAT Networking BAsics. 1 Dynamic Host Configuration Protocol (DHCP) IP address assignment Default Gateway assignment Network services discovery I just booted. What network is this? What
Topic 7 DHCP and NAT Networking BAsics. 1 Dynamic Host Configuration Protocol (DHCP) IP address assignment Default Gateway assignment Network services discovery I just booted. What network is this? What
Lab VI Capturing and monitoring the network traffic
 Lab VI Capturing and monitoring the network traffic 1. Goals To gain general knowledge about the network analyzers and to understand their utility To learn how to use network traffic analyzer tools (Wireshark)
Lab VI Capturing and monitoring the network traffic 1. Goals To gain general knowledge about the network analyzers and to understand their utility To learn how to use network traffic analyzer tools (Wireshark)
Protecting the Home Network (Firewall)
 Protecting the Home Network (Firewall) Basic Tab Setup Tab DHCP Tab Advanced Tab Options Tab Port Forwarding Tab Port Triggers Tab DMZ Host Tab Firewall Tab Event Log Tab Status Tab Software Tab Connection
Protecting the Home Network (Firewall) Basic Tab Setup Tab DHCP Tab Advanced Tab Options Tab Port Forwarding Tab Port Triggers Tab DMZ Host Tab Firewall Tab Event Log Tab Status Tab Software Tab Connection
Router configuration manual for I3 Micro Vood 322
 Router configuration manual for I3 Micro Vood 322 v1.0 1 (25) Table of contents 1 LED BEHAVIOUR... 4 1.1 POWER... 4 1.2 STATUS... 4 1.3 WAN... 4 1.4 LAN... 4 1.5 PHONE 1 VOIP... 4 1.6 PHONE 1 HOOK... 4
Router configuration manual for I3 Micro Vood 322 v1.0 1 (25) Table of contents 1 LED BEHAVIOUR... 4 1.1 POWER... 4 1.2 STATUS... 4 1.3 WAN... 4 1.4 LAN... 4 1.5 PHONE 1 VOIP... 4 1.6 PHONE 1 HOOK... 4
Chapter 2 Connecting the FVX538 to the Internet
 Chapter 2 Connecting the FVX538 to the Internet Typically, six steps are required to complete the basic connection of your firewall. Setting up VPN tunnels are covered in Chapter 5, Virtual Private Networking.
Chapter 2 Connecting the FVX538 to the Internet Typically, six steps are required to complete the basic connection of your firewall. Setting up VPN tunnels are covered in Chapter 5, Virtual Private Networking.
Implementing Network Address Translation and Port Redirection in epipe
 Implementing Network Address Translation and Port Redirection in epipe Contents 1 Introduction... 2 2 Network Address Translation... 2 2.1 What is NAT?... 2 2.2 NAT Redirection... 3 2.3 Bimap... 4 2.4
Implementing Network Address Translation and Port Redirection in epipe Contents 1 Introduction... 2 2 Network Address Translation... 2 2.1 What is NAT?... 2 2.2 NAT Redirection... 3 2.3 Bimap... 4 2.4
Chapter 4 Firewall Protection and Content Filtering
 Chapter 4 Firewall Protection and Content Filtering The ProSafe VPN Firewall 50 provides you with Web content filtering options such as Block Sites and Keyword Blocking. Parents and network administrators
Chapter 4 Firewall Protection and Content Filtering The ProSafe VPN Firewall 50 provides you with Web content filtering options such as Block Sites and Keyword Blocking. Parents and network administrators
UIP1868P User Interface Guide
 UIP1868P User Interface Guide (Firmware version 0.13.4 and later) V1.1 Monday, July 8, 2005 Table of Contents Opening the UIP1868P's Configuration Utility... 3 Connecting to Your Broadband Modem... 4 Setting
UIP1868P User Interface Guide (Firmware version 0.13.4 and later) V1.1 Monday, July 8, 2005 Table of Contents Opening the UIP1868P's Configuration Utility... 3 Connecting to Your Broadband Modem... 4 Setting
NetVanta 7100 Exercise Service Provider SIP Trunk
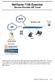 NetVanta 7100 Exercise Service Provider SIP Trunk PSTN NetVanta 7100 FXS 0/1 x2001 SIP Eth 0/0 x2004 SIP Server 172.23.102.87 Hosted by x2003 www.voxitas.com In this exercise, you will create a SIP trunk
NetVanta 7100 Exercise Service Provider SIP Trunk PSTN NetVanta 7100 FXS 0/1 x2001 SIP Eth 0/0 x2004 SIP Server 172.23.102.87 Hosted by x2003 www.voxitas.com In this exercise, you will create a SIP trunk
Multi-Homing Dual WAN Firewall Router
 Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
LINK AGGREGATION INTEROPERABILITY OF THE DELL POWERCONNECT 6200 SERIES
 LINK AGGREGATION INTEROPERABILITY OF THE DELL POWERCONNECT 6200 SERIES WITH CISCO IOS OR CISCO CATOS BASED SWITCHES By Bruce Holmes CONTENTS INTRODUCTION 3 LINK AGGREGATION WITH GIGABIT ETHERNET CISCO
LINK AGGREGATION INTEROPERABILITY OF THE DELL POWERCONNECT 6200 SERIES WITH CISCO IOS OR CISCO CATOS BASED SWITCHES By Bruce Holmes CONTENTS INTRODUCTION 3 LINK AGGREGATION WITH GIGABIT ETHERNET CISCO
Troubleshooting IP Access Lists
 CHAPTER 21 This chapter describes how to troubleshoot IPv4 and IPv6 access lists (IP-ACLs) created and maintained in the Cisco MDS 9000 Family. It includes the following sections: Overview, page 21-1 Initial
CHAPTER 21 This chapter describes how to troubleshoot IPv4 and IPv6 access lists (IP-ACLs) created and maintained in the Cisco MDS 9000 Family. It includes the following sections: Overview, page 21-1 Initial
Configuring Security for FTP Traffic
 2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
Deployment Guide: Cisco Guest Access Using the Cisco Wireless LAN Controller
 Deployment Guide: Cisco Guest Access Using the Cisco Wireless LAN Controller August 2006 Contents Overview section on page 1 Configuring Guest Access on the Cisco Wireless LAN Controller section on page
Deployment Guide: Cisco Guest Access Using the Cisco Wireless LAN Controller August 2006 Contents Overview section on page 1 Configuring Guest Access on the Cisco Wireless LAN Controller section on page
Configure an IPSec Tunnel between a Firebox Vclass & a Check Point FireWall-1
 Configure an IPSec Tunnel between a Firebox Vclass & a Check Point FireWall-1 This document describes how to configure an IPSec tunnel between a WatchGuard Firebox Vclass appliance (Vcontroller version
Configure an IPSec Tunnel between a Firebox Vclass & a Check Point FireWall-1 This document describes how to configure an IPSec tunnel between a WatchGuard Firebox Vclass appliance (Vcontroller version
FAQs: MATRIX NAVAN CNX200. Q: How to configure port triggering?
 FAQs: MATRIX NAVAN CNX200 Q: How to configure port triggering? Port triggering is a type of port forwarding where outbound traffic on predetermined ports sends inbound traffic to specific incoming ports.
FAQs: MATRIX NAVAN CNX200 Q: How to configure port triggering? Port triggering is a type of port forwarding where outbound traffic on predetermined ports sends inbound traffic to specific incoming ports.
Controlling Network Access
 Chapter 4 Controlling Network Access This chapter covers the following topics: Packet filtering Configuring traffic filtering Advanced ACL features Content and URL filtering Deployment scenarios using
Chapter 4 Controlling Network Access This chapter covers the following topics: Packet filtering Configuring traffic filtering Advanced ACL features Content and URL filtering Deployment scenarios using
Chapter 4 Customizing Your Network Settings
 . Chapter 4 Customizing Your Network Settings This chapter describes how to configure advanced networking features of the Wireless-G Router Model WGR614v9, including LAN, WAN, and routing settings. It
. Chapter 4 Customizing Your Network Settings This chapter describes how to configure advanced networking features of the Wireless-G Router Model WGR614v9, including LAN, WAN, and routing settings. It
Understanding Slow Start
 Chapter 1 Load Balancing 57 Understanding Slow Start When you configure a NetScaler to use a metric-based LB method such as Least Connections, Least Response Time, Least Bandwidth, Least Packets, or Custom
Chapter 1 Load Balancing 57 Understanding Slow Start When you configure a NetScaler to use a metric-based LB method such as Least Connections, Least Response Time, Least Bandwidth, Least Packets, or Custom
Innominate mguard Version 6
 Innominate mguard Version 6 Configuration Examples mguard smart mguard PCI mguard blade mguard industrial RS EAGLE mguard mguard delta Innominate Security Technologies AG Albert-Einstein-Str. 14 12489
Innominate mguard Version 6 Configuration Examples mguard smart mguard PCI mguard blade mguard industrial RS EAGLE mguard mguard delta Innominate Security Technologies AG Albert-Einstein-Str. 14 12489
1 PC to WX64 direction connection with crossover cable or hub/switch
 1 PC to WX64 direction connection with crossover cable or hub/switch If a network is not available, or if it is desired to keep the WX64 and PC(s) completely separated from other computers, a simple network
1 PC to WX64 direction connection with crossover cable or hub/switch If a network is not available, or if it is desired to keep the WX64 and PC(s) completely separated from other computers, a simple network
Chapter 8 Router and Network Management
 Chapter 8 Router and Network Management This chapter describes how to use the network management features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. These features can be found by
Chapter 8 Router and Network Management This chapter describes how to use the network management features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. These features can be found by
Configuring PA Firewalls for a Layer 3 Deployment
 Configuring PA Firewalls for a Layer 3 Deployment Configuring PAN Firewalls for a Layer 3 Deployment Configuration Guide January 2009 Introduction The following document provides detailed step-by-step
Configuring PA Firewalls for a Layer 3 Deployment Configuring PAN Firewalls for a Layer 3 Deployment Configuration Guide January 2009 Introduction The following document provides detailed step-by-step
Troubleshooting the Firewall Services Module
 25 CHAPTER This chapter describes how to troubleshoot the FWSM, and includes the following sections: Testing Your Configuration, page 25-1 Reloading the FWSM, page 25-6 Performing Password Recovery, page
25 CHAPTER This chapter describes how to troubleshoot the FWSM, and includes the following sections: Testing Your Configuration, page 25-1 Reloading the FWSM, page 25-6 Performing Password Recovery, page
11.1. Performance Monitoring
 11.1. Performance Monitoring Windows Reliability and Performance Monitor combines the functionality of the following tools that were previously only available as stand alone: Performance Logs and Alerts
11.1. Performance Monitoring Windows Reliability and Performance Monitor combines the functionality of the following tools that were previously only available as stand alone: Performance Logs and Alerts
Multi-Homing Gateway. User s Manual
 Multi-Homing Gateway User s Manual Contents System 5 Admin Setting Date/Time Multiple Subnet Hack Alert Route Table DHCP DNS Proxy Dynamic DNS Language Permitted IPs Logout Software Update 8 12 21 22 33
Multi-Homing Gateway User s Manual Contents System 5 Admin Setting Date/Time Multiple Subnet Hack Alert Route Table DHCP DNS Proxy Dynamic DNS Language Permitted IPs Logout Software Update 8 12 21 22 33
vcloud Air - Virtual Private Cloud OnDemand Networking Guide
 vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
vcloud Air - Virtual Private Cloud OnDemand Networking Guide vcloud Air This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Author: Seth Scardefield 1/8/2013
 Author: Seth Scardefield 1/8/2013 pfsense VoIP QoS Guide This guide will walk you through configuring the traffic shaper in pfsense to prioritize VoIP traffic. This is a very basic configuration intended
Author: Seth Scardefield 1/8/2013 pfsense VoIP QoS Guide This guide will walk you through configuring the traffic shaper in pfsense to prioritize VoIP traffic. This is a very basic configuration intended
Configuring Network Address Translation
 CHAPTER5 Configuring Network Address Translation The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. This chapter contains the following major sections
CHAPTER5 Configuring Network Address Translation The information in this chapter applies to both the ACE module and the ACE appliance unless otherwise noted. This chapter contains the following major sections
Note: This case study utilizes Packet Tracer. Please see the Chapter 5 Packet Tracer file located in Supplemental Materials.
 Note: This case study utilizes Packet Tracer. Please see the Chapter 5 Packet Tracer file located in Supplemental Materials. CHAPTER 5 OBJECTIVES Configure a router with an initial configuration. Use the
Note: This case study utilizes Packet Tracer. Please see the Chapter 5 Packet Tracer file located in Supplemental Materials. CHAPTER 5 OBJECTIVES Configure a router with an initial configuration. Use the
Chapter 11 Network Address Translation
 Chapter 11 Network Address Translation You can configure an HP routing switch to perform standard Network Address Translation (NAT). NAT enables private IP networks that use nonregistered IP addresses
Chapter 11 Network Address Translation You can configure an HP routing switch to perform standard Network Address Translation (NAT). NAT enables private IP networks that use nonregistered IP addresses
IP Filter/Firewall Setup
 IP Filter/Firewall Setup Introduction The IP Filter/Firewall function helps protect your local network against attack from outside. It also provides a method of restricting users on the local network from
IP Filter/Firewall Setup Introduction The IP Filter/Firewall function helps protect your local network against attack from outside. It also provides a method of restricting users on the local network from
NAT (Network Address Translation)
 NAT (Network Address Translation) Introduction NAT (Network Address Translation) is a method of mapping one or more IP addresses and/or IP service ports into different specified values. Two functions of
NAT (Network Address Translation) Introduction NAT (Network Address Translation) is a method of mapping one or more IP addresses and/or IP service ports into different specified values. Two functions of
Barracuda Link Balancer
 Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.2 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.2-110503-01-0503
Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.2 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.2-110503-01-0503
Firewall Load Balancing
 CHAPTER 6 This chapter describes the (FWLB) feature. It includes the following sections: FWLB Overview, page 6-1 FWLB Features, page 6-2 FWLB Configuration Tasks, page 6-3 Monitoring and Maintaining FWLB,
CHAPTER 6 This chapter describes the (FWLB) feature. It includes the following sections: FWLB Overview, page 6-1 FWLB Features, page 6-2 FWLB Configuration Tasks, page 6-3 Monitoring and Maintaining FWLB,
Quick Note 53. Ethernet to W-WAN failover with logical Ethernet interface.
 Quick Note 53 Ethernet to W-WAN failover with logical Ethernet interface. Digi Support August 2015 1 Contents 1 Introduction... 2 1.1 Introduction... 2 1.2 Assumptions... 3 1.3 Corrections... 3 2 Version...
Quick Note 53 Ethernet to W-WAN failover with logical Ethernet interface. Digi Support August 2015 1 Contents 1 Introduction... 2 1.1 Introduction... 2 1.2 Assumptions... 3 1.3 Corrections... 3 2 Version...
Broadband Phone Gateway BPG510 Technical Users Guide
 Broadband Phone Gateway BPG510 Technical Users Guide (Firmware version 0.14.1 and later) Revision 1.0 2006, 8x8 Inc. Table of Contents About your Broadband Phone Gateway (BPG510)... 4 Opening the BPG510's
Broadband Phone Gateway BPG510 Technical Users Guide (Firmware version 0.14.1 and later) Revision 1.0 2006, 8x8 Inc. Table of Contents About your Broadband Phone Gateway (BPG510)... 4 Opening the BPG510's
Setting up VPN Access for Remote Diagnostics Support
 Setting up VPN Access for Remote Diagnostics Support D. R. Joseph, Inc. supports both dial-up and Internet access for remote support of 3GIBC1 and LF-Sizer control systems. This document describes how
Setting up VPN Access for Remote Diagnostics Support D. R. Joseph, Inc. supports both dial-up and Internet access for remote support of 3GIBC1 and LF-Sizer control systems. This document describes how
Technical Note. Monitoring Ethernet Traffic with Tolomatic ACS & Managed Switch. Contents
 Monitoring Ethernet Traffic with Tolomatic ACS & Managed Switch Contents 1. Introduction...2 2. Equipment...2 3. Software...3 4. Definitions...3 5. Procedure...3 6. Change PC IP Address...3 7. Network
Monitoring Ethernet Traffic with Tolomatic ACS & Managed Switch Contents 1. Introduction...2 2. Equipment...2 3. Software...3 4. Definitions...3 5. Procedure...3 6. Change PC IP Address...3 7. Network
CCNA Access List Sim
 1 P a g e CCNA Access List Sim Question An administrator is trying to ping and telnet from Switch to Router with the results shown below: Switch> Switch> ping 10.4.4.3 Type escape sequence to abort. Sending
1 P a g e CCNA Access List Sim Question An administrator is trying to ping and telnet from Switch to Router with the results shown below: Switch> Switch> ping 10.4.4.3 Type escape sequence to abort. Sending
SuperLumin Nemesis. Administration Guide. February 2011
 SuperLumin Nemesis Administration Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
SuperLumin Nemesis Administration Guide February 2011 SuperLumin Nemesis Legal Notices Information contained in this document is believed to be accurate and reliable. However, SuperLumin assumes no responsibility
Flow Monitor Configuration. Content CHAPTER 1 MIRROR CONFIGURATION... 1-1 CHAPTER 2 SFLOW CONFIGURATION... 2-1 CHAPTER 3 RSPAN CONFIGURATION...
 Content Content CHAPTER 1 MIRROR CONFIGURATION... 1-1 1.1 INTRODUCTION TO MIRROR... 1-1 1.2 MIRROR CONFIGURATION TASK LIST... 1-1 1.3 MIRROR EXAMPLES... 1-2 1.4 DEVICE MIRROR TROUBLESHOOTING... 1-3 CHAPTER
Content Content CHAPTER 1 MIRROR CONFIGURATION... 1-1 1.1 INTRODUCTION TO MIRROR... 1-1 1.2 MIRROR CONFIGURATION TASK LIST... 1-1 1.3 MIRROR EXAMPLES... 1-2 1.4 DEVICE MIRROR TROUBLESHOOTING... 1-3 CHAPTER
