Trusted Personal Data Management A User-Centric Approach
|
|
|
- Thomasine Underwood
- 10 years ago
- Views:
Transcription
1 GRUPPO TELECOM ITALIA Future Cloud Seminar Oulu, August 13th 2014 A User-Centric Approach SKIL Lab, Trento - Italy
2 Why are we talking about #privacy and #personaldata today?
3 3
4 Our data footprint Every day we are handing over 20+ types of personal data 4
5 5
6 The economic opportunity bytes That is more than 1,000 gigabytes of data for every person on earth! to the organization to the customers $1 trillion In 2020! 7 zettabytes 45% 2/3 1/3 2/ Amount of available data is expected to grow by 45% per year through 2015, to roughly 7 zettabytes. The value created through digital identity is expected to grow at 22% CAGR and by 2020 contribute 8% to GDP of the developed economies However, two-thirds of potential value generation $ 1 Trillion in 2020 is at risk if stakeholders fail to establish a trusted flow of data. 6
7 Let s do a step back to the privacy principles
8 Privacy: EU vs US For the EU, privacy is considered a fundamental right and remains highly regulated. In the US, it is deemed a consumer right and is lightly regulated. 8
9 The EU regulatory framework 1) Principles and obligations Data minimization Purpose limitation Personal data must be: relevant and not excessive in relation to the purposes of their collection and processing; kept in a form which permits identification for no longer than is necessary for the purposes for which they are collected or processed. The purposes of the processing must be defined prior to the collection of personal data. Personal data can not be further processed in a way incompatible with such purposes. Consent In general terms, the specific consent of the data subject is needed for processing operations not related to the execution of a contract signed with the data subject or to fulfill a legal obligation. (The other legitimate grounds for data processing apply rarely (1) in the private sector or are subjected to specific restrictions (2) ). (1) E.g. processing necessary to protect the vital interests of the data subject or for a task carried out in the public interest. (2) For instance, under the Italian privacy law, data processing based on a legitimate interest of the data controller must be authorized by the national DPA. 9
10 The EU regulatory framework 2) Scope of application The EU Data Protection Directive does NOT apply to companies based outside Europe, even when they process (with equipment situated outside the EU) personal data of European citizens. Furthermore, OTTs are not subject to the same restrictive rules that apply to Telcos and ISPs under the EU e-privacy Directive. 10
11 The EU regulatory framework 3) Possible evolutions On January 2012, the EC presented a proposal for a new Regulation on the protection of personal data, to replace the current Data Protection Directive. The draft Regulation aims to harmonize EU data protection legislation and to adapt to technological developments. Once approved, it will be directly applicable in the member states. While presenting various innovations, the draft Regulation confirms the basic setting of the current Data Protection Directive with regard to the principles of data minimization, purpose limitation and consent of the data subject. At the same time, the new Regulation may introduce a definition of pseudonymous data and provide for more flexible rules concerning their processing, for instance in relation to the assessment of the data controller s legitimate interest or for profiling activities [1]. [1] European Parliament s Report on a proposal for a General Data Protection Regulation, notably amendments to Recital 38 and 58a and to Article 4(2a) 11
12 The EU regulatory framework: possible openings (1/2) The EU legal framework, however, offers possible openings which, if properly implemented, might allow the balancing of the legitimate interests of businesses and customers and mitigate the regulatory asymmetry which adversely affects European companies. Notably: Dir. 95/49/CE, Recital 26 To determine whether a person is identifiable, account should be taken of all the means likely reasonable to be used to identify the said person. The principles of protection shall not apply to data rendered anonymous in such a way that the data subject is no longer identifiable. WP 29 (1) Opinion 4/2007 on the concept of personal data Retraceably pseudonymised (2) data may be considered as information on indirectly identifiable individuals. In that case, although data protection rules apply, the risks for the individuals will most often be low, so that the application of these rules will justifiably be more flexible. (1) The Article 29 Working Party (WP 29) is made up of a representative from the data protection authority of each EU member state, the European Data Protection Supervisor and the EC. (2) Pseudonymization is the process of disguising identities, often implemented through one-way cryptographic algorithms. 12
13 The EU regulatory framework: possible openings (2/2) WP 29 Opinion 3/2013 on purpose limitation Regarding Big Data, two possible scenarios are described: When the analysis aims at predicting the personal preferences, behavior and attitudes of individual customers, in order to inform measures or decisions that are taken toward them, the relevant consent (opt-in) is necessary; When the analysis only aims at detecting trends and correlations in the information, without effects on single individuals, the concept of functional separation plays a key role. To this end, measures such as anonymization should be taken, to ensure that the data are not available to support measures or decisions toward individuals. WP 29 Opinion 5/2014 on anonymization Inter alia, the WP 29 indicates that: When a data controller hands over a dataset, after removal or masking of identifiable data but without deleting the original (identifiable) data at event-level, the dataset is still personal data. Only if the data controller aggregates the data so that individual events are no longer identifiable, the resulting dataset can be qualified as anonymous [1]. On the other hand, a third party may lawfully process a dataset anonymised and released by the original data controller, without needing to take account of data protection requirements, provided they cannot (directly or indirectly) identify the data subjects in the original dataset. Pseudonymisation reduces the lindability of a dataset with the original identity of a data subject; as such, it is a useful security measure but not a method of anonymisation. (1) E.g. if an organisation collects mobility data, the individual travel patterns at event level would still qualify as personal data for any party, as long as the data controller (or any other party) still has access to the original raw data, even if direct identifiers have been removed from the set provided to third parties. But if the data controller would delete the raw data, and only provide aggregate statistics to third parties (such as 'on Mondays on trajectory X there are 160% more passengers than on Tuesdays ), that would qualify as anonymous data. 13
14 Then, why doesn t it work?
15 Titolo della Relazione Nome del Relatore, Nome Struttura 15
16 Titolo della Relazione Nome del Relatore, Nome Struttura 16
17 Titolo della Relazione Nome del Relatore, Nome Struttura 17
18 The Organization-centric Personal Data Management Persons Personal Data are stored in IT systems of private enterprises /organizations: data stored in independent silos (no integrated view of individuals) Limited involvement and/or awareness of the persons in the use and valorization of their Personal Data, explicitly or implicitly generated: Need to create a Personal Data ecosystem more fair for all the involved actors * Personal data collected from/on individuals (explicitly provided, observed, inferred) Greater attention of the authorities to the possible violations of individuals privacy rather than to enable an exploitation of Personal Data under the control of individuals Data disclosure perceived less relevant than Data protection (*) Enterprises, Public Admin,, E-Gov, Service Providers, Network Providers, etc. 18
19 The role of trust 19
20 The role of trust 20
21 Limite estremo Do you #trust this guy? Titolo della Relazione Nome del Relatore, Nome Struttura 21
22 The User-centric Personal Data Management Individuals become the owners of their personal data: from data protection to data control to enable full data exploitation Increase the control that individuals have over their personal data collection, management, usage and sharing - will: spur a host of new services and applications exploiting their value with direct benefits for individuals restore trust in the personal data ecosystem International initiatives, both from regulatory and economic sides, are sponsoring such a shift from organization-centric paradigm to usercentric paradigm Request for personal data sharing (access, synchronization, etc.) Rules for personal data sharing (access, synchronization, etc.) 22
23 Towards the User-centric Personal Data Management Regulation EU is proposing a data protection reform strengthening citizens rights and aligning regulation with the realities of the Internet (e.g., right of copy, privacy by default ) EU e-privacy directive, requires prior consent for organization to place cookies in users terminals Concerted pressure in US and EU in favour of Do Not Track services Economy Government UK Government launched the midata project promoting the key principle that data should be released back to consumers has announced the Federated Authentication ID Assurance strategy initiative to reinvent the way identity assurance is handled according to a more person-centric approach US Government has a programme called Smart Disclosure similar to midata project has announced its National Strategy for Trusted Identities in Cyberspace (NSTIC) allowing people to choose among multiple identity providers Blue Button initiative releases medical records back to US Army veterans WEF launched the project Rethinking Personal Data to understand how a collaborative and balanced personal data ecosystem can evolve By the way, User-centric Personal Data model is gaining evidence on the specialized Press e.g., 23
24 The Personal Data Store model Digital footprint Digital record of everything a person makes and does online and in the world Big Data produced by or about a person Personal Devices (integrated sensors) Utilities (online) Service Provider (real world) Organizations Payment Providers Telco (*) Environmental sensors Personal Data Store gathers data about persons from multiple sources, to have an holistic view of individuals A PDS Provider acts on behalf of its customers: it provides personal data services to individuals enabling them to control the collection, manage, use and share their personal data (*) These data are voluntary collected by individuals (opt-in) and disjoint from those normally used by Telcos for their traditional business and operation 24
25 Personal Data Store: value proposition Persons: High personalized applications (e.g., life monitoring, information retrieval, behavior awareness, personal decision making support) Controlled information exchange with external services Ownership-preserving content sharing in social networks Personal data as «currency» in the cyberspace, by disclosing data to get economic or social advantages Organizations (e.g., Companies and Public Administrations): Access to aggregations and analytics on personal data disclosed by persons groups to analyze/identify social phenomena (e.g., for marketing, smart territory applications) Data exchange to improve and automatize service delivery processes and better satisfy customers needs (e.g., needs-offers matching, personalization) Trust increase Avoid Personal Data segmentation Application Providers: Simple personal data access via APIs 25
26 User-centric Personal Data Management at work
27 MOBILE TERRITORIAL LAB THE MOBILE TERRITORIAL LAB GOALS Understand the value of Personal (Big) Data Exploit smartphones as social sensors to perform User Behaviour and Social Analysis Design and test prototype applications in a real-life scenario THROUGH A PLATFORM FOR COLLECTING THE DATA SENSED BY MOBILE PHONES DESIGN PERSONAL-DATA DRIVEN SERVICES EXPLOIT AGGREGATED PERSONAL DATA FOR SMART CITY APPLICATIONS DEVELOP PRIVACY- PRESEERVING SERVICES FOR PERSONAL DATA 27 MANAGEMENT
28 MOBILE THE MOBILE TERRITORIAL TERRITORIAL LAB LAB CONSORTIUM A joint effort between industrial and academic research institutions 28
29 MOBILE TERRITORIAL LAB PROJECT SETUP PARENTS (KIDS 0-10) A smartphone (Android +NFC) and a prepaid SIM card to every user An onboard sensing software + 70 NOV 2012 MTL KICK-OFF
30 MOBILE TERRITORIAL LAB The smartphone as the door to your life QUANTITATIVE DATA QUALITATIVE DATA Sociability, mood, contents, preferences, app usage, etc. 30
31 SECOND NOSE DYNAMIC COLLECTIVE MAP OF THE CITY The platform aggregates data from all the sensors each collecting a data point every five minutes. DAILY INDIVIDUAL MAP An app provides users real time information about the collected locations indicating the quality of the air breathed during a day. 31
32 MOBILE THE MOBILE TERRITORIAL TERRITORIAL LAB LAB APP ECOSYSTEM / Examples PERSONAL DATA PLATFORM 32
33 THE MOBILE TERRITORIAL LAB MOBILE TERRITORIAL LAB LOGICAL ARCHITECTURE 33
34 MOBILE TERRITORIAL LAB 34
35 MOBILE THE MOBILE TERRITORIAL TERRITORIAL LAB LAB My Data Store Web Mobile 35
36 MOBILE THE MOBILE TERRITORIAL TERRITORIAL LAB LAB My Data Store Set your collection preferences. 36
37 MOBILE THE MOBILE TERRITORIAL TERRITORIAL LAB LAB My Data Store Set your sharing level. 37
38 MOBILE TERRITORIAL LAB My Data Store Explore your data. 38
39 MOBILE TERRITORIAL LAB My Data Store Compare with others. 39
40 MOBILE TERRITORIAL LAB My Data Store Mobile 40
41 The MTL My Data Store mentioned as reference case at the World Economic Forum Unlocking the Value of Personal Data: From Collection to Usage "Exploring the opportunities and risk of using personal data in a real world context through living labs." 41
42 Thanks.
43 ANNEX My Data Store DEMO 43
ESOMAR PRACTICAL GUIDE ON COOKIES JULY 2012
 ESOMAR PRACTICAL GUIDE ON COOKIES JULY 2012 Copyright ESOMAR 2012 TABLE OF CONTENTS 2 Objectives 2 Introduction 3 Definitions 4 SECTION 1: APPLICABLE LAW 4 SECTION 2: WHAT YOU NEED TO KNOW SOME FAQs 5
ESOMAR PRACTICAL GUIDE ON COOKIES JULY 2012 Copyright ESOMAR 2012 TABLE OF CONTENTS 2 Objectives 2 Introduction 3 Definitions 4 SECTION 1: APPLICABLE LAW 4 SECTION 2: WHAT YOU NEED TO KNOW SOME FAQs 5
Multi-Jurisdictional Study: Cloud Computing Legal Requirements. Julien Debussche Associate January 2015
 Multi-Jurisdictional Study: Cloud Computing Legal Requirements Julien Debussche Associate January 2015 Content 1. General Legal Framework 2. Data Protection Legal Framework 3. Security Requirements 4.
Multi-Jurisdictional Study: Cloud Computing Legal Requirements Julien Debussche Associate January 2015 Content 1. General Legal Framework 2. Data Protection Legal Framework 3. Security Requirements 4.
AlixPartners, LLP. General Data Protection Statement
 AlixPartners, LLP General Data Protection Statement GENERAL DATA PROTECTION STATEMENT 1. INTRODUCTION 1.1 AlixPartners, LLP ( AlixPartners ) is committed to fulfilling its obligations under the data protection
AlixPartners, LLP General Data Protection Statement GENERAL DATA PROTECTION STATEMENT 1. INTRODUCTION 1.1 AlixPartners, LLP ( AlixPartners ) is committed to fulfilling its obligations under the data protection
Council of the European Union Brussels, 5 March 2015 (OR. en)
 Council of the European Union Brussels, 5 March 2015 (OR. en) Interinstitutional File: 2013/0027 (COD) 6788/15 LIMITE TELECOM 59 DATAPROTECT 23 CYBER 13 MI 139 CSC 55 CODEC 279 NOTE From: Presidency To:
Council of the European Union Brussels, 5 March 2015 (OR. en) Interinstitutional File: 2013/0027 (COD) 6788/15 LIMITE TELECOM 59 DATAPROTECT 23 CYBER 13 MI 139 CSC 55 CODEC 279 NOTE From: Presidency To:
HERON (No: 649690): Deliverable D.2.6 DATA MANAGEMENT PLAN AUGUST 2015. Partners: Oxford Brookes University and Università Commerciale Luigi Bocconi
 HERON (No: 649690): Deliverable D.2.6 DATA MANAGEMENT PLAN AUGUST 2015 Partners: Oxford Brookes University and Università Commerciale Luigi Bocconi Institutions: Low Carbon Building Group, Oxford Brookes
HERON (No: 649690): Deliverable D.2.6 DATA MANAGEMENT PLAN AUGUST 2015 Partners: Oxford Brookes University and Università Commerciale Luigi Bocconi Institutions: Low Carbon Building Group, Oxford Brookes
Big Data, Not Big Brother: Best Practices for Data Analytics Peter Leonard Gilbert + Tobin Lawyers
 Big Data, Not Big Brother: Best Practices for Data Analytics Peter Leonard Gilbert + Tobin Lawyers March 2013 How Target Knew a High School Girl Was Pregnant Before Her Parents Did just because you can,
Big Data, Not Big Brother: Best Practices for Data Analytics Peter Leonard Gilbert + Tobin Lawyers March 2013 How Target Knew a High School Girl Was Pregnant Before Her Parents Did just because you can,
8970/15 FMA/AFG/cb 1 DG G 3 C
 Council of the European Union Brussels, 19 May 2015 (OR. en) 8970/15 NOTE RECH 141 TELECOM 119 COMPET 228 IND 80 From: Permanent Representatives Committee (Part 1) To: Council No. prev. doc.: 8583/15 RECH
Council of the European Union Brussels, 19 May 2015 (OR. en) 8970/15 NOTE RECH 141 TELECOM 119 COMPET 228 IND 80 From: Permanent Representatives Committee (Part 1) To: Council No. prev. doc.: 8583/15 RECH
INERTIA ETHICS MANUAL
 SEVENTH FRAMEWORK PROGRAMME Smart Energy Grids Project Title: Integrating Active, Flexible and Responsive Tertiary INERTIA Grant Agreement No: 318216 Collaborative Project INERTIA ETHICS MANUAL Responsible
SEVENTH FRAMEWORK PROGRAMME Smart Energy Grids Project Title: Integrating Active, Flexible and Responsive Tertiary INERTIA Grant Agreement No: 318216 Collaborative Project INERTIA ETHICS MANUAL Responsible
Data Sharing Protocol
 Data Sharing Protocol Agreement for Sharing Data Between Partners of the South Dublin Childrens Services Committee Version 0.4 Final Draft June 2009 Contents 1 Preface...3 2 Introduction & Overview...3
Data Sharing Protocol Agreement for Sharing Data Between Partners of the South Dublin Childrens Services Committee Version 0.4 Final Draft June 2009 Contents 1 Preface...3 2 Introduction & Overview...3
Unleashing the Potential of Cloud Computing in Europe - What is it and what does it mean for me?
 EUROPEAN COMMISSION MEMO Brussels, 27 September 2012 Unleashing the Potential of Cloud Computing in Europe - What is it and what does it mean for me? See also IP/12/1025 What is Cloud Computing? Cloud
EUROPEAN COMMISSION MEMO Brussels, 27 September 2012 Unleashing the Potential of Cloud Computing in Europe - What is it and what does it mean for me? See also IP/12/1025 What is Cloud Computing? Cloud
The U.K. Information Commissioner s Office Report on Big Data and Data Protection
 reau of National Affairs, Inc. (800-372-1033) http://www.bna.com WORLD DATA PROTECTION REPORT >>> News and analysis of data protection developments around the world. For the latest updates, visit www.bna.com
reau of National Affairs, Inc. (800-372-1033) http://www.bna.com WORLD DATA PROTECTION REPORT >>> News and analysis of data protection developments around the world. For the latest updates, visit www.bna.com
Privacy & Big Data: Enable Big Data Analytics with Privacy by Design. Datenschutz-Vereinigung von Luxemburg Ronald Koorn DRAFT VERSION 8 March 2014
 Privacy & Big Data: Enable Big Data Analytics with Privacy by Design Datenschutz-Vereinigung von Luxemburg Ronald Koorn DRAFT VERSION 8 March 2014 Agenda? What is 'Big Data'? Privacy Implications Privacy
Privacy & Big Data: Enable Big Data Analytics with Privacy by Design Datenschutz-Vereinigung von Luxemburg Ronald Koorn DRAFT VERSION 8 March 2014 Agenda? What is 'Big Data'? Privacy Implications Privacy
Overview. Data protection in a swirl of change 28.03.2014. Cloud computing. Software as a service. Infrastructure as a service. Platform as a service
 Data protection in a swirl of change Overview 1 Data protection issues in cloud computing 2 Consent for mobile applications Security Seminar 2014: Privacy Radboud University Nijmegen 3 The WhatsApp case
Data protection in a swirl of change Overview 1 Data protection issues in cloud computing 2 Consent for mobile applications Security Seminar 2014: Privacy Radboud University Nijmegen 3 The WhatsApp case
Response of the German Medical Association
 Response of the German Medical Association To the Green Paper on mobile Health ( mhealth ) of the European Commission Berlin, 3 July 2014 Bundesärztekammer Herbert-Lewin-Platz 1 10623 Berlin We are grateful
Response of the German Medical Association To the Green Paper on mobile Health ( mhealth ) of the European Commission Berlin, 3 July 2014 Bundesärztekammer Herbert-Lewin-Platz 1 10623 Berlin We are grateful
Cookies and consent. The Article 29 Working Party has identified seven types of cookies that are not subject to the consent requirement.
 Cookies and consent Cookies are small text files placed on a computer and accessed by the browser when opening a webpage. - DDMA 2012 The statutory requirements governing the placement of cookies were
Cookies and consent Cookies are small text files placed on a computer and accessed by the browser when opening a webpage. - DDMA 2012 The statutory requirements governing the placement of cookies were
Prof. Udo Helmbrecht
 Prof. Udo Helmbrecht Guiding EU Cybersecurity from Policy to Implementation Udo Helmbrecht Executive Director Information Security for the Public Sector 2015 Stockholm 02/09/15 European Union Agency for
Prof. Udo Helmbrecht Guiding EU Cybersecurity from Policy to Implementation Udo Helmbrecht Executive Director Information Security for the Public Sector 2015 Stockholm 02/09/15 European Union Agency for
Working Document 02/2013 providing guidance on obtaining consent for cookies
 ARTICLE 29 DATA PROTECTION WORKING PARTY 1676/13/EN WP 208 Working Document 02/2013 providing guidance on obtaining consent for cookies Adopted on 2 October 2013 This Working Party was set up under Article
ARTICLE 29 DATA PROTECTION WORKING PARTY 1676/13/EN WP 208 Working Document 02/2013 providing guidance on obtaining consent for cookies Adopted on 2 October 2013 This Working Party was set up under Article
What is Quantified Self (QS)?
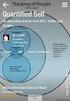 Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
Smartphones, social network and instant messaging services
 GRUPPO TELECOM ITALIA Global Trends in Online Safety. Creating a National Framework Rome, 16 September 2015 Smartphones, social network and instant messaging services Challenges for children, parents and
GRUPPO TELECOM ITALIA Global Trends in Online Safety. Creating a National Framework Rome, 16 September 2015 Smartphones, social network and instant messaging services Challenges for children, parents and
Opinion 04/2012 on Cookie Consent Exemption
 ARTICLE 29 DATA PROTECTION WORKING PARTY 00879/12/EN WP 194 Opinion 04/2012 on Cookie Consent Exemption Adopted on 7 June 2012 This Working Party was set up under Article 29 of Directive 95/46/EC. It is
ARTICLE 29 DATA PROTECTION WORKING PARTY 00879/12/EN WP 194 Opinion 04/2012 on Cookie Consent Exemption Adopted on 7 June 2012 This Working Party was set up under Article 29 of Directive 95/46/EC. It is
Big Data challenges to foster AI research and applications
 GRUPPO TELECOM ITALIA Workshop on Embracing Potential of Big Data Pisa, 12 Dicembre 2014 Big Data challenges to foster AI research and applications Fabrizio Antonelli SKIL Lab The Joint Open Labs of Telecom
GRUPPO TELECOM ITALIA Workshop on Embracing Potential of Big Data Pisa, 12 Dicembre 2014 Big Data challenges to foster AI research and applications Fabrizio Antonelli SKIL Lab The Joint Open Labs of Telecom
EU Directive on Network and Information Security SWD(2013) 31 & SWD(2013) 32. A call for views and evidence
 EU Directive on Network and Information Security SWD(2013) 31 & SWD(2013) 32 A call for views and evidence 22 nd May 2013 Contents Contents... 2 Overview: The EU Directive on Network and Information Security...
EU Directive on Network and Information Security SWD(2013) 31 & SWD(2013) 32 A call for views and evidence 22 nd May 2013 Contents Contents... 2 Overview: The EU Directive on Network and Information Security...
IEEE IoT IoT Scenario & Use Cases: Social Sensors
 IEEE IoT IoT Scenario & Use Cases: Social Sensors Service Description More and more, people have the possibility to monitor important parameters in their home or in their surrounding environment. As an
IEEE IoT IoT Scenario & Use Cases: Social Sensors Service Description More and more, people have the possibility to monitor important parameters in their home or in their surrounding environment. As an
IAB Europe Guidance. Five Practical Steps to help companies comply with the E-Privacy Directive
 IAB Europe Guidance Five Practical Steps to help companies comply with the E-Privacy Directive Foreword The steps laid out below are intended to help brand advertisers, publishers and advertising businesses
IAB Europe Guidance Five Practical Steps to help companies comply with the E-Privacy Directive Foreword The steps laid out below are intended to help brand advertisers, publishers and advertising businesses
Business Model Designing the 9 blocks
 GRUPPO TELECOM ITALIA Catania, 28 Marzo 2014 Business Model Designing the 9 blocks The Open Innovation perspective Telecom Italia Head of Joint Open Lab WAVE @valdamico Agenda Business Model Innovation
GRUPPO TELECOM ITALIA Catania, 28 Marzo 2014 Business Model Designing the 9 blocks The Open Innovation perspective Telecom Italia Head of Joint Open Lab WAVE @valdamico Agenda Business Model Innovation
RAYSAFE S1 SECURITY WHITEPAPER VERSION B. RaySafe S1 SECURITY WHITEPAPER
 RaySafe S1 SECURITY WHITEPAPER Contents 1. INTRODUCTION 2 ARCHITECTURE OVERVIEW 2.1 Structure 3 SECURITY ASPECTS 3.1 Security Aspects for RaySafe S1 Data Collector 3.2 Security Aspects for RaySafe S1 cloud-based
RaySafe S1 SECURITY WHITEPAPER Contents 1. INTRODUCTION 2 ARCHITECTURE OVERVIEW 2.1 Structure 3 SECURITY ASPECTS 3.1 Security Aspects for RaySafe S1 Data Collector 3.2 Security Aspects for RaySafe S1 cloud-based
BIG DATA AND THE INTERNET OF THINGS
 BIG DATA AND THE INTERNET OF THINGS 12 September 2013 Robert Bond Partner and Notary Public Janine Regan Solicitor Tughan Thuraisingam Paralegal Our team Speechly Bircham is an ambitious, full-service
BIG DATA AND THE INTERNET OF THINGS 12 September 2013 Robert Bond Partner and Notary Public Janine Regan Solicitor Tughan Thuraisingam Paralegal Our team Speechly Bircham is an ambitious, full-service
Data protection compliance checklist
 Data protection compliance checklist What is this checklist for? This checklist is drawn up on the basis of analysis of the relevant provisions of European law. Although European law aims at harmonizing
Data protection compliance checklist What is this checklist for? This checklist is drawn up on the basis of analysis of the relevant provisions of European law. Although European law aims at harmonizing
9360/15 FMA/AFG/cb 1 DG G 3 C
 Council of the European Union Brussels, 29 May 2015 (OR. en) 9360/15 OUTCOME OF PROCEEDINGS From: To: Council Delegations RECH 183 TELECOM 134 COMPET 288 IND 92 No. prev. doc.: 8970/15 RECH 141 TELECOM
Council of the European Union Brussels, 29 May 2015 (OR. en) 9360/15 OUTCOME OF PROCEEDINGS From: To: Council Delegations RECH 183 TELECOM 134 COMPET 288 IND 92 No. prev. doc.: 8970/15 RECH 141 TELECOM
1. Understanding Big Data
 Big Data and its Real Impact on Your Security & Privacy Framework: A Pragmatic Overview Erik Luysterborg Partner, Deloitte EMEA Data Protection & Privacy leader Prague, SCCE, March 22 nd 2016 1. 2016 Deloitte
Big Data and its Real Impact on Your Security & Privacy Framework: A Pragmatic Overview Erik Luysterborg Partner, Deloitte EMEA Data Protection & Privacy leader Prague, SCCE, March 22 nd 2016 1. 2016 Deloitte
DSCI Inputs on TRAI Consultation on Regulatory Framework for OTT services
 DSCI Inputs on TRAI Consultation on Regulatory Framework for OTT services April 24, 2015 DSCI Inputs on TRAI Consultation on Regulatory Framework for OTT Services 1 Question 6: How should the security
DSCI Inputs on TRAI Consultation on Regulatory Framework for OTT services April 24, 2015 DSCI Inputs on TRAI Consultation on Regulatory Framework for OTT Services 1 Question 6: How should the security
H2020-EUJ-2016: EU-Japan Joint Call. EUJ-02-2016: IoT/Cloud/Big Data platforms in social application contexts
 H2020-EUJ-2016: EU-Japan Joint Call EUJ-02-2016: IoT/Cloud/Big Data platforms in social application contexts EUJ-02-2016: IoT/Cloud/Big Data The Challenge The Integration and federation of IoT with Big
H2020-EUJ-2016: EU-Japan Joint Call EUJ-02-2016: IoT/Cloud/Big Data platforms in social application contexts EUJ-02-2016: IoT/Cloud/Big Data The Challenge The Integration and federation of IoT with Big
Summary of feedback on Big data and data protection and ICO response
 Summary of feedback on Big data and data protection and ICO response Contents Introduction... 2 Question 1... 3 Impacts and benefits; privacy impact assessments (PIAs)... 3 New approaches to data protection...
Summary of feedback on Big data and data protection and ICO response Contents Introduction... 2 Question 1... 3 Impacts and benefits; privacy impact assessments (PIAs)... 3 New approaches to data protection...
Online Security, Traffic Data and IP Addresses. Review of the Regulatory Framework for Electronic Communications
 Brussels, October 8 th 2008 Online Security, Traffic Data and IP Addresses Review of the Regulatory Framework for Electronic Communications Francisco Mingorance Senior Director Government Affairs [email protected]
Brussels, October 8 th 2008 Online Security, Traffic Data and IP Addresses Review of the Regulatory Framework for Electronic Communications Francisco Mingorance Senior Director Government Affairs [email protected]
Opinion 02/2013 on apps on smart devices
 ARTICLE 29 DATA PROTECTION WORKING PARTY 00461/13/EN WP 202 Opinion 02/2013 on apps on smart devices Adopted on 27 February 2013 This Working Party was set up under Article 29 of Directive 95/46/EC. It
ARTICLE 29 DATA PROTECTION WORKING PARTY 00461/13/EN WP 202 Opinion 02/2013 on apps on smart devices Adopted on 27 February 2013 This Working Party was set up under Article 29 of Directive 95/46/EC. It
Opinion 02/2013 on apps on smart devices
 ARTICLE 29 DATA PROTECTION WORKING PARTY 00461/13/EN WP 202 Opinion 02/2013 on apps on smart devices Adopted on 27 February 2013 This Working Party was set up under Article 29 of Directive 95/46/EC. It
ARTICLE 29 DATA PROTECTION WORKING PARTY 00461/13/EN WP 202 Opinion 02/2013 on apps on smart devices Adopted on 27 February 2013 This Working Party was set up under Article 29 of Directive 95/46/EC. It
Smart Grid and Privacy An International View
 Smart Grid and Privacy An International View 27 November 2013 By: Nader Farah President ESTA International One US Consumer s Reaction in Texas! 2 Source: SmartGridNews.com July 20, 2012 ESTA International
Smart Grid and Privacy An International View 27 November 2013 By: Nader Farah President ESTA International One US Consumer s Reaction in Texas! 2 Source: SmartGridNews.com July 20, 2012 ESTA International
DATA ANALYTICS@DT. Dr. Jan Krancke, VP Regulatory Strategy & Projects CERRE Expert Workshop, Brussels. re3rerererewr
 DATA ANALYTICS@DT Dr. Jan Krancke, VP Regulatory Strategy & Projects CERRE Expert Workshop, Brussels re3rerererewr SMART DATA MARKET SMART DATA BENEFITS ECONOMY AS A WHOLE Use Case Spectrum Enterprise
DATA ANALYTICS@DT Dr. Jan Krancke, VP Regulatory Strategy & Projects CERRE Expert Workshop, Brussels re3rerererewr SMART DATA MARKET SMART DATA BENEFITS ECONOMY AS A WHOLE Use Case Spectrum Enterprise
Opinion 8/2014 on the on Recent Developments on the Internet of Things
 ARTICLE 29 DATA PROTECTION WORKING PARTY 14/EN WP 223 Opinion 8/2014 on the on Recent Developments on the Internet of Things Adopted on 16 September 2014 This Working Party was set up under Article 29
ARTICLE 29 DATA PROTECTION WORKING PARTY 14/EN WP 223 Opinion 8/2014 on the on Recent Developments on the Internet of Things Adopted on 16 September 2014 This Working Party was set up under Article 29
IoT-03-2017 R&I on IoT integration and platforms INTERNET OF THINGS FOCUS AREA
 HORIZON 2020 WP 2016-17 IoT-03-2017 R&I on IoT integration and platforms INTERNET OF THINGS DG CONNECT European Commission Internet of Things As enabler of a future hyper-connected society, the Internet
HORIZON 2020 WP 2016-17 IoT-03-2017 R&I on IoT integration and platforms INTERNET OF THINGS DG CONNECT European Commission Internet of Things As enabler of a future hyper-connected society, the Internet
Healthcare Coalition on Data Protection
 Healthcare Coalition on Data Protection Recommendations and joint statement supporting citizens interests in the benefits of data driven healthcare in a secure environment Representing leading actors in
Healthcare Coalition on Data Protection Recommendations and joint statement supporting citizens interests in the benefits of data driven healthcare in a secure environment Representing leading actors in
EUK-02-2016: South Korea: IoT joint research
 HORIZON 2020 WP 2016-17 EUK-02-2016: South Korea: IoT joint research DG CONNECT/DG AGRI/DG MOVE/DG RTD European Commission RIA EUK-02-2016: South Korea: IoT joint research Challenge: IoT has moved from
HORIZON 2020 WP 2016-17 EUK-02-2016: South Korea: IoT joint research DG CONNECT/DG AGRI/DG MOVE/DG RTD European Commission RIA EUK-02-2016: South Korea: IoT joint research Challenge: IoT has moved from
The potential legal consequences of a personal data breach
 The potential legal consequences of a personal data breach Tue Goldschmieding, Partner 16 April 2015 The potential legal consequences of a personal data breach 15 April 2015 Contents 1. Definitions 2.
The potential legal consequences of a personal data breach Tue Goldschmieding, Partner 16 April 2015 The potential legal consequences of a personal data breach 15 April 2015 Contents 1. Definitions 2.
European Commission initiatives on e- and mhealth
 European Commission initiatives on e- and mhealth Fundamental Rights Forum, 22 June 2016 WG 24: E-health: improving rights fulfilment through innovation Claudia Prettner, Unit for Health and Well-Being,
European Commission initiatives on e- and mhealth Fundamental Rights Forum, 22 June 2016 WG 24: E-health: improving rights fulfilment through innovation Claudia Prettner, Unit for Health and Well-Being,
Knowledge based energy management for public buildings through holistic information modeling and 3D visualization. Ing. Antonio Sacchetti TERA SRL
 Knowledge based energy management for public buildings through holistic information modeling and 3D visualization Ing. Antonio Sacchetti TERA SRL About us-1 Tera is a SME born in year 2007, based on the
Knowledge based energy management for public buildings through holistic information modeling and 3D visualization Ing. Antonio Sacchetti TERA SRL About us-1 Tera is a SME born in year 2007, based on the
Privacy Seminar - Social Networks
 Privacy Seminar - Social Networks Robert Kleinpenning & Judith van Stegeren 5th June 2015 Defining social networks What is a social network anyway? Defining social networks What is a social network anyway?
Privacy Seminar - Social Networks Robert Kleinpenning & Judith van Stegeren 5th June 2015 Defining social networks What is a social network anyway? Defining social networks What is a social network anyway?
New EU Data Protection legislation comes into force today. What does this mean for your business?
 24 th May 2016 New EU Data Protection legislation comes into force today. What does this mean for your business? After years of discussion and proposals, the General Data Protection Regulation ( GDPR )
24 th May 2016 New EU Data Protection legislation comes into force today. What does this mean for your business? After years of discussion and proposals, the General Data Protection Regulation ( GDPR )
ESTRO PRIVACY AND DATA SECURITY NOTICE
 ESTRO PRIVACY AND DATA SECURITY NOTICE This Data Privacy and Security Policy is a dynamic document, which will reflect our continuing vigilance to properly handle and secure information that we are trusted
ESTRO PRIVACY AND DATA SECURITY NOTICE This Data Privacy and Security Policy is a dynamic document, which will reflect our continuing vigilance to properly handle and secure information that we are trusted
International Working Group on Data Protection in Telecommunications
 International Working Group on Data Protection in Telecommunications 675.42.10 4 April 2011 Working Paper Event Data Recorders (EDR) on Vehicles Privacy and data protection issues for governments and manufacturers
International Working Group on Data Protection in Telecommunications 675.42.10 4 April 2011 Working Paper Event Data Recorders (EDR) on Vehicles Privacy and data protection issues for governments and manufacturers
ECRIN (European Clinical Research Infrastructures Network)
 ECRIN (European Clinical Research Infrastructures Network) Wolfgang Kuchinke University of Duesseldorf (HHU) and ECRIN EUDAT 1st User Forum 7 March 2012 8 March 2012, Barcelona 1 What is ECRIN? European
ECRIN (European Clinical Research Infrastructures Network) Wolfgang Kuchinke University of Duesseldorf (HHU) and ECRIN EUDAT 1st User Forum 7 March 2012 8 March 2012, Barcelona 1 What is ECRIN? European
Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) 2014: 245 incidents reported
 Protecting What Matters Most Christian Fahlke, Regional Sales Manager ALPS March 2015 Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) 2014: 245 incidents reported (Source: https://ics-cert.us-cert.gov/sites/default/files/monitors/ics-cert_monitor_sep2014-feb2015.pdf)
Protecting What Matters Most Christian Fahlke, Regional Sales Manager ALPS March 2015 Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) 2014: 245 incidents reported (Source: https://ics-cert.us-cert.gov/sites/default/files/monitors/ics-cert_monitor_sep2014-feb2015.pdf)
Adaptive Business Management Systems Privacy Policy
 Adaptive Business Management Systems Privacy Policy Updated policy: Effective on July 01, 2013 This privacy statement describes how Adaptive Business Management Systems collects and uses the personal information
Adaptive Business Management Systems Privacy Policy Updated policy: Effective on July 01, 2013 This privacy statement describes how Adaptive Business Management Systems collects and uses the personal information
Towards a data-driven economy in Europe
 Towards a data-driven economy in Europe Trusting Big Data Trust in the Digital World Conference 26 February 2015 Dr. Márta NAGY-ROTHENGASS Head of Unit CNECT.G3 (Data Value Chain) Why is data-driven economy
Towards a data-driven economy in Europe Trusting Big Data Trust in the Digital World Conference 26 February 2015 Dr. Márta NAGY-ROTHENGASS Head of Unit CNECT.G3 (Data Value Chain) Why is data-driven economy
ROADMAP. Initial IA screening & planning of further work
 ROADMAP Title of the initiative: Youth programme post 2013 Type of initiative (CWP/Catalogue/Comitology): CWP Lead DG: DG EAC/E-2, Youth in Action Unit Expected date of adoption of the initiative (month/year):
ROADMAP Title of the initiative: Youth programme post 2013 Type of initiative (CWP/Catalogue/Comitology): CWP Lead DG: DG EAC/E-2, Youth in Action Unit Expected date of adoption of the initiative (month/year):
All rights reserved. 2011, EuroPriSe/ULD
 January 2011 Position paper on certifiability of online behavioural advertising systems according to EuroPriSe Follow-up EuroPriSe - European Privacy Seal at the Unabhängiges Landeszentrum für Datenschutz
January 2011 Position paper on certifiability of online behavioural advertising systems according to EuroPriSe Follow-up EuroPriSe - European Privacy Seal at the Unabhängiges Landeszentrum für Datenschutz
Lunch & Learn: Big Data Analytics
 239767 Lunch & Learn: Big Data Analytics 13 April 2015 Sue McLean Alex van der Wolk 2015 Morrison & Foerster (UK) LLP All Rights Reserved mofo.com Lunch & Learn 2 nd Monday of each month 45 minutes via
239767 Lunch & Learn: Big Data Analytics 13 April 2015 Sue McLean Alex van der Wolk 2015 Morrison & Foerster (UK) LLP All Rights Reserved mofo.com Lunch & Learn 2 nd Monday of each month 45 minutes via
Utilizing big data to bring about innovative offerings and new revenue streams DATA-DERIVED GROWTH
 Utilizing big data to bring about innovative offerings and new revenue streams DATA-DERIVED GROWTH ACTIONABLE INTELLIGENCE Ericsson is driving the development of actionable intelligence within all aspects
Utilizing big data to bring about innovative offerings and new revenue streams DATA-DERIVED GROWTH ACTIONABLE INTELLIGENCE Ericsson is driving the development of actionable intelligence within all aspects
User Needs and Requirements Analysis for Big Data Healthcare Applications
 User Needs and Requirements Analysis for Big Data Healthcare Applications Sonja Zillner, Siemens AG In collaboration with: Nelia Lasierra, Werner Faix, and Sabrina Neururer MIE 2014 in Istanbul: 01-09-2014
User Needs and Requirements Analysis for Big Data Healthcare Applications Sonja Zillner, Siemens AG In collaboration with: Nelia Lasierra, Werner Faix, and Sabrina Neururer MIE 2014 in Istanbul: 01-09-2014
CP FOR DRAFT RTS ON RWS/LGDS ARTICLES 124 AND 164 CRR EBA/CP/2015/12. 6 July 2015. Consultation Paper
 EBA/CP/2015/12 6 July 2015 Consultation Paper Draft Regulatory Technical Standards on the conditions that competent authorities shall take into account when determining higher risk-weights, in particular
EBA/CP/2015/12 6 July 2015 Consultation Paper Draft Regulatory Technical Standards on the conditions that competent authorities shall take into account when determining higher risk-weights, in particular
dma How to guide Email and cookies legislation Published by The DMA Email Marketing Council and the IAB Email Marketing Council we are the
 dma we are the How to guide Email and cookies legislation Published by The DMA Email Marketing Council and the IAB Email Marketing Council First edition, April 2012 Contents Acknowledgements...2 Introduction...3
dma we are the How to guide Email and cookies legislation Published by The DMA Email Marketing Council and the IAB Email Marketing Council First edition, April 2012 Contents Acknowledgements...2 Introduction...3
Some Specific Parawise Suggestinons. 2. An application which collects and analyzes this data for further consolidation and,
 Comments by Amcham India on draft Internet of Things (IoT) Policy released by the Department of Electronics & Information Technology (DeitY), on October 16, 2014 Standards The Draft IoT Policy already
Comments by Amcham India on draft Internet of Things (IoT) Policy released by the Department of Electronics & Information Technology (DeitY), on October 16, 2014 Standards The Draft IoT Policy already
Article 29 Working Party Issues Opinion on Cloud Computing
 Client Alert Global Regulatory Enforcement If you have questions or would like additional information on the material covered in this Alert, please contact one of the authors: Cynthia O Donoghue Partner,
Client Alert Global Regulatory Enforcement If you have questions or would like additional information on the material covered in this Alert, please contact one of the authors: Cynthia O Donoghue Partner,
EXECUTIVE SUMMARY. EU Multi Stakeholder Forum on Corporate Social Responsibility 3-4 February, 2015 Brussels, Belgium
 EXECUTIVE SUMMARY EU Multi Stakeholder Forum on Corporate Social Responsibility 3-4 February, 2015 Brussels, Belgium The Multi Stakeholder Forum on Corporate Social Responsibility (CSR) was held in Brussels
EXECUTIVE SUMMARY EU Multi Stakeholder Forum on Corporate Social Responsibility 3-4 February, 2015 Brussels, Belgium The Multi Stakeholder Forum on Corporate Social Responsibility (CSR) was held in Brussels
Connected car, big data, big brother?
 Connected car, big data, big brother? Using geolocation in a trustworthy and compliant way [email protected] Trends that threaten trust 2 Connected cars with downloadable apps Location services, cloud,
Connected car, big data, big brother? Using geolocation in a trustworthy and compliant way [email protected] Trends that threaten trust 2 Connected cars with downloadable apps Location services, cloud,
Science and Technology Select Committee inquiry Social media data and real-time analytics
 techuk.org @techuk #techuk Science and Technology Select Committee inquiry Social media data and real-time analytics techuk response April 2014 About techuk techuk represents the companies and technologies
techuk.org @techuk #techuk Science and Technology Select Committee inquiry Social media data and real-time analytics techuk response April 2014 About techuk techuk represents the companies and technologies
