Agile and Secure Can We Be Both? Chicago OWASP. June 20 th, 2007
|
|
|
- Meryl Blankenship
- 10 years ago
- Views:
Transcription
1 Agile and Secure Can We Be Both? Chicago OWASP June 20 th, 2007
2 The Agile Practitioner s Dilemma Agile Forces: Be more responsive to business concerns Increase the frequency of stable releases Decrease the time it takes to deploy new features Do not waste time on superfluous documentation and planning Secure Forces: Comply with more aggressive regulatory environment Focus on need for security Traditional approaches to security require additional documentation and planning (D Oh!) 1
3 Objectives Background Basics of Agile Development Methods Basics of Secure Development Methods Review of Microsoft Secure Development Lifecycle (SDL) Review the Momentum of Agile Methods Look at An Integrated Process Challenges & Compromises 2
4 Background Programmer by background Both.NET and JEE: MCSD, Java 2 Certified Programmer Developer focused on security, not a security professional looking at development Denim Group Software Development:.NET and JEE Software / Application Security Vulnerability Assessments, Penetration Tests, Training, Mentoring Basis for this presentation: Work with our customers doing SDLC security mentoring Challenges facing our own agile development teams Deliver projects in an economically-responsible manner Uphold security goals 3
5 Notable Agile Methods extreme Programming (XP) Feature Driven Development (FDD) SCRUM MSF for Agile Software Development Agile Unified Process (AUP) Crystal 4
6 Manifesto for Agile Software Development Individuals and interactions over processes and tools Working software over comprehensive documentation Customer collaboration over contract negotiation Responding to change over following a plan Source: 5
7 Agile s Core Values Communication Simplicity Feedback Courage 6
8 Principles of Agile Development Rapid Feedback Simple Design The system is appropriate for the intended audience. The code passes all the tests. Incremental Change Embracing Change Quality Work The code communicates everything it needs to. Thecodehasthesmallestnumber has smallest of classes and methods. 7
9 Agile Practices The Planning Game The Driving Metaphor Customer:scope, priorities and release dates Developer: estimates, consequences and detailed scheduling Shared Vision On-Site Customer Small Releases Development iterations or cycles that last 1-4 weeks. Release iterations as soon as possible (weekly, monthly, quarterly). 8
10 More Agile Practices Collective Ownership Test Driven Continuous Integration Coding Standards Pair Programming 9
11 Definition of Secure A secure product is one that protects the confidentiality, integrity, and availability of the customers information, and the integrity and availability of processing resources under control of the system s stem s owner or administrator. -- Source: Writing Secure Code (Microsoft.com) com) 10
12 A Secure Development Process Strives To Be A Repeatable Process Requires Team Member Education Tracks Metrics and Maintains Accountability Sources: Writing Secure Code 2 nd Ed., Howard & LeBlanc The Trustworthy Computing Security Development Lifecycle by Lipner & Howard 11
13 Secure Development Principles SD 3 : Secure by Design, Secure by Default, and in Deployment Learn From Mistakes Minimize Your Attack Surface Assume External Systems Are Insecure Plan On Failure Never Depend on Security Through Obscurity Alone Fix Security Issues Correctly 12
14 Secure Development Practices Threat Modeling / Architectural Risk Assessment Education, Education, Education Secure Coding Via standards and practitioner knowledge Security Reviews Architecture t Design Code Security Testing (Penetration Testing) 13
15 Microsoft s s Secure Development Lifecycle (SDL) Requirements Design Implementation Verification Release (Waterfall!) 14
16 Observations of the SDL in Practice Threat Modeling is the Highest-Priority Component Drives other aspects of the process design, coding, testing Penetration Testing Alone is Not the Answer Badness-ometer (Gary McGraw) Tools Should be Complementary Security is not a checkbox to be checked with a tool 15
17 Threat Modeling STRIDE classify threats Spoofing Identity Tampering with Data Repudiation Information Disclosure Denial of Service Elevation of Privilege DREAD rank vulnerabilities Damage Potential Reproducibility Exploitability Affected Users Discoverability 16
18 Dr. Dobb s says Agile Methods Are Catching On 41% of organizations have adopted an agile methodology Of the 2,611 respondents doing agile 37% using extreme Programming 19% using Feature Driven Development (FDD) 16% using SCRUM 7% using MSF for Agile Software Development Source: 17
19 Agile Teams are Quality Infected 60% reported increased productivity 66% reported improved quality 58% improved stakeholder satisfaction 18
20 Adoption Rate for Agile Practices Of the respondents using an agile method 36% have active customer participation 61% have adopted common coding guidelines 53% perform code regression testing 37% utilize pair programming 19
21 Let s Look at Some Specific Agile Methods extreme Programming (XP) Feature Driven Development (FDD) SCRUM MSF for Agile Software Development 20
22 extreme Programming (XP) 21
23 Feature Driven Development (FDD) Develop an Overall Model Startup Phase Build Features List Planning Design by Feature Build by Feature Construction Phase Source: 22
24 SCRUM Commonly Used to Enhance Existing Systems Feature Backlog 30 Day Sprints Daily Team Meeting Source: 23
25 MSF for Agile Software Development Adapted from the Spiral / Waterfall Hybrid Product definition, development and testing occurs in overlapping iterations Different iterations have a different focus 24
26 An Integrated Process Making Agile Trustworthy 25
27 Project Roles Product Manager / Customer Program Manager / Coach Architect Developer Tester Security Adviser 26
28 Organization Setup Education & Training (include Security) Developers Testers Customers User Stories / Use Case Driven Processes Enterprise Architecture Decisions Organizational adoption of Threat Modeling 27
29 Project / Release Planning User Stories / Use Cases Drive Acceptance Test Scenarios Estimations may affect priorities and thus the composition of the release Inputs for Threat Modeling Security Testing Scenarios Determine the qualitative risk budget Keep the customer involved in making risk tradeoffs Finalize Architecture & Development Guidelines Common Coding Standards (include security) Crucial for collective code ownership Data Classification standards Conduct Initial Threat Modeling (assets & threats) Agree on STRIDE and DREAD classifications Designer s Security Checklist 28
30 Iteration Planning 1-4 Weeks in Length (2 weeks is very common) Begins with an Iteration ti Planning Meeting User Stories are broken down into Development Tasks Developers estimate their own tasks Document the Attack Surface (Story Level) Model the threats alongside the user story documentation Crucial in documentation-light processes Capture these and keep them Code will tell you what decision was made, threat models will tell you why decisions were made Crucial for refactoring in the face of changing security priorities Never Slip the Date Add or Remove Stories As Necessary 29
31 Executing an Iteration Daily Stand-ups Continuous Integration Code Scanning Tools Security Testing Tools Adherence to Common Coding Standards and Security Guidelines Crucial for communal code ownership Developer s Checklist 30
32 Closing an Iteration Automation of Customer Acceptance Tests Include negative testing for identified threats Security Code Review Some may have happened informally during pair programming 31
33 Stabilizing a Release Schedule Defects & Vulnerabilities Prioritize vulnerabilities with client input based on agreed-upon STRIDE and DREAD standards d Security Push Include traditional penetration testing 32
34 Compromises We ve Made Security Compromises: Short term, iterative focus removes top down control Focus on individual features can blind process to cross-feature security issues Agile Compromises: More documentation than is required in pure Agile development Security coding standards Data classification standards Project-specific STRIDE and DREAD standards User story threat models Additional tasks increase development time Forces customers to accept security (isn t this a good thing?) 33
35 Characteristics of an Agile and Secure Process Customer-focused Responsive Iterative Trustworthy 34
36 Questions Dan Cornell (210) Website: Blog 1: Blog 2: denimgroup.typepad.com 35
Agile and Secure: OWASP AppSec Seattle Oct 2006. The OWASP Foundation http://www.owasp.org/
 Agile and Secure: Can We Be Both? OWASP AppSec Seattle Oct 2006 Dan Cornell, OWASP San Antonio Leader Principal, Denim Group Ltd. [email protected] (210) 572-4400 Copyright 2006 - The OWASP Foundation
Agile and Secure: Can We Be Both? OWASP AppSec Seattle Oct 2006 Dan Cornell, OWASP San Antonio Leader Principal, Denim Group Ltd. [email protected] (210) 572-4400 Copyright 2006 - The OWASP Foundation
Agile and Secure: Can We Be Both?
 Agile and Secure: Can We Be Both? OWASP AppSec Seattle Oct 2006 Keith Landrus Director of Technology Denim Group Ltd. [email protected] (210) 572-4400 Copyright 2006 - The OWASP Foundation Permission
Agile and Secure: Can We Be Both? OWASP AppSec Seattle Oct 2006 Keith Landrus Director of Technology Denim Group Ltd. [email protected] (210) 572-4400 Copyright 2006 - The OWASP Foundation Permission
Vulnerability Management in an Application Security World. AppSec DC November 12 th, 2009. The OWASP Foundation http://www.owasp.
 Vulnerability Management in an Application Security World AppSec DC November 12 th, 2009 Dan Cornell Global Membership Committee Denim Group [email protected] (210) 572-4400 Twitter: @danielcornell The
Vulnerability Management in an Application Security World AppSec DC November 12 th, 2009 Dan Cornell Global Membership Committee Denim Group [email protected] (210) 572-4400 Twitter: @danielcornell The
Entire contents 2011 Praetorian. All rights reserved. Information Security Provider and Research Center www.praetorian.com
 Entire contents 2011 Praetorian. All rights reserved. Information Security Provider and Research Center www.praetorian.com Threat Modeling "Threat modeling at the design phase is really the only way to
Entire contents 2011 Praetorian. All rights reserved. Information Security Provider and Research Center www.praetorian.com Threat Modeling "Threat modeling at the design phase is really the only way to
Topics covered. Agile methods Plan-driven and agile development Extreme programming Agile project management Scaling agile methods
 Topics covered Chapter 3 Agile Software Development Agile methods Plan-driven and agile Extreme programming Agile project management Scaling agile methods 1 2 Need for rapid software Rapid software Changing
Topics covered Chapter 3 Agile Software Development Agile methods Plan-driven and agile Extreme programming Agile project management Scaling agile methods 1 2 Need for rapid software Rapid software Changing
Introduction to Web Application Security. Microsoft CSO Roundtable Houston, TX. September 13 th, 2006
 Introduction to Web Application Security Microsoft CSO Roundtable Houston, TX September 13 th, 2006 Overview Background What is Application Security and Why Is It Important? Examples Where Do We Go From
Introduction to Web Application Security Microsoft CSO Roundtable Houston, TX September 13 th, 2006 Overview Background What is Application Security and Why Is It Important? Examples Where Do We Go From
Secure By Design: Security in the Software Development Lifecycle
 Secure By Design: Security in the Software Development Lifecycle Twin Cities Rational User s Group Security Briefing by Arctec Group (www.arctecgroup.net) Integrating Security into Software Development
Secure By Design: Security in the Software Development Lifecycle Twin Cities Rational User s Group Security Briefing by Arctec Group (www.arctecgroup.net) Integrating Security into Software Development
Agile Practitioner: PMI-ACP and ScrumMaster Aligned
 Agile Practitioner: PMI-ACP and ScrumMaster Aligned The PMI Agile Certified Practitioner (PMI-ACP) ScrumMaster credential validates your ability to understand agile principles, agile concepts, and establishes
Agile Practitioner: PMI-ACP and ScrumMaster Aligned The PMI Agile Certified Practitioner (PMI-ACP) ScrumMaster credential validates your ability to understand agile principles, agile concepts, and establishes
Threat Modeling: The Art of Identifying, Assessing, and Mitigating security threats
 Threat Modeling: The Art of Identifying, Assessing, and Mitigating security threats Mohamed Ali Saleh Abomhara University of Agder [email protected] Winter School in Information Security, Finse May
Threat Modeling: The Art of Identifying, Assessing, and Mitigating security threats Mohamed Ali Saleh Abomhara University of Agder [email protected] Winter School in Information Security, Finse May
How to manage agile development? Rose Pruyne Jack Reed
 How to manage agile development? Rose Pruyne Jack Reed What will we cover? Introductions Overview and principles User story exercise Retrospective exercise Getting started Q&A About me: Jack Reed Geospatial
How to manage agile development? Rose Pruyne Jack Reed What will we cover? Introductions Overview and principles User story exercise Retrospective exercise Getting started Q&A About me: Jack Reed Geospatial
The Agile approach Extreme Programming (XP) Implementing XP into a software project Introducing HCI design into agile software development Summary
 ! " # $%&' ()**+ % The Agile approach Extreme Programming (XP) Implementing XP into a software project Introducing HCI design into agile software development Summary , 75% of the enterprise software products
! " # $%&' ()**+ % The Agile approach Extreme Programming (XP) Implementing XP into a software project Introducing HCI design into agile software development Summary , 75% of the enterprise software products
Agile with XP and Scrum
 Agile with XP and Scrum Amit Goel National Agile Software Workshop @ Indore Agile India Conference Agile Software Community of India Disclaimer and Credits Most of material in this presentation has been
Agile with XP and Scrum Amit Goel National Agile Software Workshop @ Indore Agile India Conference Agile Software Community of India Disclaimer and Credits Most of material in this presentation has been
Challenges of Software Security in Agile Software Development
 Challenges of Software Security in Agile Software Development Dr. Panayotis Kikiras INFS133 March 2015 Agenda Lean Principles and Agile Development Usable Security Secure software development in Agile
Challenges of Software Security in Agile Software Development Dr. Panayotis Kikiras INFS133 March 2015 Agenda Lean Principles and Agile Development Usable Security Secure software development in Agile
ISSECO Syllabus Public Version v1.0
 ISSECO Syllabus Public Version v1.0 ISSECO Certified Professional for Secure Software Engineering Date: October 16th, 2009 This document was produced by the ISSECO Working Party Syllabus Introduction to
ISSECO Syllabus Public Version v1.0 ISSECO Certified Professional for Secure Software Engineering Date: October 16th, 2009 This document was produced by the ISSECO Working Party Syllabus Introduction to
Agile Development Overview
 Presented by Jennifer Bleen, PMP Project Services Practice of Cardinal Solutions Group, Inc. Contact: Agile Manifesto We are uncovering better ways of developing software by doing it and helping others
Presented by Jennifer Bleen, PMP Project Services Practice of Cardinal Solutions Group, Inc. Contact: Agile Manifesto We are uncovering better ways of developing software by doing it and helping others
Agile Development for Application Security Managers
 Agile Development for Application Security Managers www.quotium.com When examining the agile development methodology many organizations are uncertain whether it is possible to introduce application security
Agile Development for Application Security Managers www.quotium.com When examining the agile development methodology many organizations are uncertain whether it is possible to introduce application security
Agile Project Management By Mark C. Layton
 Agile Project Management By Mark C. Layton Agile project management focuses on continuous improvement, scope flexibility, team input, and delivering essential quality products. Agile project management
Agile Project Management By Mark C. Layton Agile project management focuses on continuous improvement, scope flexibility, team input, and delivering essential quality products. Agile project management
Building Security into the Software Life Cycle
 Building Security into the Software Life Cycle A Business Case Marco M. Morana Senior Consultant Foundstone Professional Services, a Division of McAfee Outline» Glossary» What is at risk, what we do about
Building Security into the Software Life Cycle A Business Case Marco M. Morana Senior Consultant Foundstone Professional Services, a Division of McAfee Outline» Glossary» What is at risk, what we do about
AGIL JA, ABER SICHER? 29.07.2015, ANDREAS FALK, 34. SCRUM TISCH
 AGIL JA, ABER SICHER? 29.07.2015, ANDREAS FALK, 34. SCRUM TISCH Vorstellung: Andreas Falk Langjährige Erfahrungen als Entwickler, Architekt und Tester in verschiedenen Projekten mit Fokus Enterprise-Anwendungen
AGIL JA, ABER SICHER? 29.07.2015, ANDREAS FALK, 34. SCRUM TISCH Vorstellung: Andreas Falk Langjährige Erfahrungen als Entwickler, Architekt und Tester in verschiedenen Projekten mit Fokus Enterprise-Anwendungen
Turning the Battleship: How to Build Secure Software in Large Organizations. Dan Cornell May 11 th, 2006
 Turning the Battleship: How to Build Secure Software in Large Organizations Dan Cornell May 11 th, 2006 Overview Background and key questions Quick review of web application security The web application
Turning the Battleship: How to Build Secure Software in Large Organizations Dan Cornell May 11 th, 2006 Overview Background and key questions Quick review of web application security The web application
Extreme Programming, an agile software development process
 Extreme Programming, an agile software development process Paul Jackson School of Informatics University of Edinburgh Recall: Waterfall and Spiral Models Waterfall: Spiral: Split project into controlled
Extreme Programming, an agile software development process Paul Jackson School of Informatics University of Edinburgh Recall: Waterfall and Spiral Models Waterfall: Spiral: Split project into controlled
CSE 435 Software Engineering. Sept 16, 2015
 CSE 435 Software Engineering Sept 16, 2015 2.1 The Meaning of Process A process: a series of steps involving activities, constraints, and resources that produce an intended output of some kind A process
CSE 435 Software Engineering Sept 16, 2015 2.1 The Meaning of Process A process: a series of steps involving activities, constraints, and resources that produce an intended output of some kind A process
Agile Software Development
 E Learning Volume 5 Number 1 2008 www.wwwords.co.uk/elea Agile Software Development SOLY MATHEW BIJU University of Wollongong in Dubai, United Arab Emirates ABSTRACT Many software development firms are
E Learning Volume 5 Number 1 2008 www.wwwords.co.uk/elea Agile Software Development SOLY MATHEW BIJU University of Wollongong in Dubai, United Arab Emirates ABSTRACT Many software development firms are
Agile Scrum Workshop
 Agile Scrum Workshop What is agile and scrum? Agile meaning: Able to move quickly and easily. Scrum meaning: a Rugby play Agile Scrum: It is an iterative and incremental agile software development framework
Agile Scrum Workshop What is agile and scrum? Agile meaning: Able to move quickly and easily. Scrum meaning: a Rugby play Agile Scrum: It is an iterative and incremental agile software development framework
Extreme Programming, an agile software development process
 Extreme Programming, an agile software development process Nigel Goddard School of Informatics University of Edinburgh Recall: Waterfall and Spiral Models Waterfall: Spiral: Split project into controlled
Extreme Programming, an agile software development process Nigel Goddard School of Informatics University of Edinburgh Recall: Waterfall and Spiral Models Waterfall: Spiral: Split project into controlled
Introduction to Agile Software Development Process. Software Development Life Cycles
 Introduction to Agile Software Development Process Presenter: Soontarin W. (Senior Software Process Specialist) Date: 24 November 2010 AGENDA Software Development Life Cycles Waterfall Model Iterative
Introduction to Agile Software Development Process Presenter: Soontarin W. (Senior Software Process Specialist) Date: 24 November 2010 AGENDA Software Development Life Cycles Waterfall Model Iterative
RISK MANAGMENT ON AN AGILE PROJECT
 BIO PRESENTATION W3 6/28/ 11:30 AM RISK MANAGMENT ON AN AGILE PROJECT Michele Sliger Rally Software Development Better Software Conference June 26 29, Las Vegas, NV USA Michele Sliger Michele Sliger has
BIO PRESENTATION W3 6/28/ 11:30 AM RISK MANAGMENT ON AN AGILE PROJECT Michele Sliger Rally Software Development Better Software Conference June 26 29, Las Vegas, NV USA Michele Sliger Michele Sliger has
Contents. 3 Agile Modelling 31 3.1 Introduction 31 3.2 Modelling Misconceptions 31
 Contents 1 Introduction 1 1.1 WhyThisBook? 1 1.2 A Bit of History 1 1.3 What Is Agile Software Development? 2 1.4 WhyBe Agile? 3 1.5 What This Book Is About? 3 1.6 Implementation Languages 3 1.7 The Structure
Contents 1 Introduction 1 1.1 WhyThisBook? 1 1.2 A Bit of History 1 1.3 What Is Agile Software Development? 2 1.4 WhyBe Agile? 3 1.5 What This Book Is About? 3 1.6 Implementation Languages 3 1.7 The Structure
Secure Code Development
 ISACA South Florida 7th Annual WOW! Event Copyright Elevate Consult LLC. All Rights Reserved 1 Agenda i. Background ii. iii. iv. Building a Business Case for Secure Coding Top-Down Approach to Develop
ISACA South Florida 7th Annual WOW! Event Copyright Elevate Consult LLC. All Rights Reserved 1 Agenda i. Background ii. iii. iv. Building a Business Case for Secure Coding Top-Down Approach to Develop
Mobile Application Threat Analysis
 The OWASP Foundation http://www.owasp.org Mobile Application Threat Analysis Ari Kesäniemi Nixu Copyright The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under
The OWASP Foundation http://www.owasp.org Mobile Application Threat Analysis Ari Kesäniemi Nixu Copyright The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under
XP & Scrum. extreme Programming. XP Roles, cont!d. XP Roles. Functional Tests. project stays on course. about the stories
 XP & Scrum Beatrice Åkerblom [email protected] extreme Programming XP Roles XP Roles, cont!d! Customer ~ Writes User Stories and specifies Functional Tests ~ Sets priorities, explains stories ~ May or
XP & Scrum Beatrice Åkerblom [email protected] extreme Programming XP Roles XP Roles, cont!d! Customer ~ Writes User Stories and specifies Functional Tests ~ Sets priorities, explains stories ~ May or
Getting Started with Agile Project Management Methods for Elearning
 Getting Started with Agile Project Management Methods for Elearning Megan Torrance TorranceLearning Training2013 Session 108 February 18, 2013 8am Megan Torrance has 20 years of experience in the learning
Getting Started with Agile Project Management Methods for Elearning Megan Torrance TorranceLearning Training2013 Session 108 February 18, 2013 8am Megan Torrance has 20 years of experience in the learning
Agile Software Development Methodologies and Its Quality Assurance
 Agile Software Development Methodologies and Its Quality Assurance Aslin Jenila.P.S Assistant Professor, Hindustan University, Chennai Abstract: Agility, with regard to software development, can be expressed
Agile Software Development Methodologies and Its Quality Assurance Aslin Jenila.P.S Assistant Professor, Hindustan University, Chennai Abstract: Agility, with regard to software development, can be expressed
Introduction to Agile and Scrum
 Introduction to Agile and Scrum Matthew Renze @matthewrenze COMS 309 - Software Development Practices Purpose Intro to Agile and Scrum Prepare you for the industry Questions and answers Overview Intro
Introduction to Agile and Scrum Matthew Renze @matthewrenze COMS 309 - Software Development Practices Purpose Intro to Agile and Scrum Prepare you for the industry Questions and answers Overview Intro
From Agile by Design. Full book available for purchase here.
 From Agile by Design. Full book available for purchase here. Contents Introduction xiii About the Author xix Chapter 1 Adjusting to a Customer-Centric Landscape 1 It s a Whole New World 1 From Customer-Aware
From Agile by Design. Full book available for purchase here. Contents Introduction xiii About the Author xix Chapter 1 Adjusting to a Customer-Centric Landscape 1 It s a Whole New World 1 From Customer-Aware
Software Development Life Cycle (SDLC)
 Software Development Life Cycle (SDLC) Supriyo Bhattacharjee MOF Capability Maturity Model (CMM) A bench-mark for measuring the maturity of an organization s software process CMM defines 5 levels of process
Software Development Life Cycle (SDLC) Supriyo Bhattacharjee MOF Capability Maturity Model (CMM) A bench-mark for measuring the maturity of an organization s software process CMM defines 5 levels of process
How can I be agile and still satisfy the auditors?
 How can I be agile and still satisfy the auditors? Welcome & Introductions Steve Ropa [email protected] Agile Coach Certified Scrum Master Certified Scrum Product Owner 19 years software development
How can I be agile and still satisfy the auditors? Welcome & Introductions Steve Ropa [email protected] Agile Coach Certified Scrum Master Certified Scrum Product Owner 19 years software development
Software Development Life Cycle Models - Process Models. Week 2, Session 1
 Software Development Life Cycle Models - Process Models Week 2, Session 1 PROCESS MODELS Many life cycle models have been proposed } Traditional Models (plan-driven) } Classical waterfall model } Iterative
Software Development Life Cycle Models - Process Models Week 2, Session 1 PROCESS MODELS Many life cycle models have been proposed } Traditional Models (plan-driven) } Classical waterfall model } Iterative
In the IEEE Standard Glossary of Software Engineering Terminology the Software Life Cycle is:
 In the IEEE Standard Glossary of Software Engineering Terminology the Software Life Cycle is: The period of time that starts when a software product is conceived and ends when the product is no longer
In the IEEE Standard Glossary of Software Engineering Terminology the Software Life Cycle is: The period of time that starts when a software product is conceived and ends when the product is no longer
PLM - Agile. Design Code Test. Sprints 1, 2, 3, 4.. Define requirements, perform system design, develop and test the system. Updated Project Plan
 PLM - Agile Agile Development Evolved in the 1990s as a response to heavyweight methodologies. In 2001 representatives of various new methodologies met to discuss the need for lighter alternatives. The
PLM - Agile Agile Development Evolved in the 1990s as a response to heavyweight methodologies. In 2001 representatives of various new methodologies met to discuss the need for lighter alternatives. The
Vragen. Software development model. Software development model. Software development model
 Vragen Noem de belangrijkste activiteiten in een software engineeringsproject Welke vormen van onderhoud kan men onderscheiden? Karakteriseer het waterval model Waterfall model Document oriented Suited
Vragen Noem de belangrijkste activiteiten in een software engineeringsproject Welke vormen van onderhoud kan men onderscheiden? Karakteriseer het waterval model Waterfall model Document oriented Suited
SOFTWARE PROCESS MODELS
 SOFTWARE PROCESS MODELS Slide 1 Software Process Models Process model (Life-cycle model) - steps through which the product progresses Requirements phase Specification phase Design phase Implementation
SOFTWARE PROCESS MODELS Slide 1 Software Process Models Process model (Life-cycle model) - steps through which the product progresses Requirements phase Specification phase Design phase Implementation
Agile So)ware Development
 Software Engineering Agile So)ware Development 1 Rapid software development Rapid development and delivery is now often the most important requirement for software systems Businesses operate in a fast
Software Engineering Agile So)ware Development 1 Rapid software development Rapid development and delivery is now often the most important requirement for software systems Businesses operate in a fast
Agile and lean methods for managing application development process
 Agile and lean methods for managing application development process Hannu Markkanen 24.01.2013 1 Application development lifecycle model To support the planning and management of activities required in
Agile and lean methods for managing application development process Hannu Markkanen 24.01.2013 1 Application development lifecycle model To support the planning and management of activities required in
Development Processes (Lecture outline)
 Development*Process*for*Secure* So2ware Development Processes (Lecture outline) Emphasis on building secure software as opposed to building security software Major methodologies Microsoft's Security Development
Development*Process*for*Secure* So2ware Development Processes (Lecture outline) Emphasis on building secure software as opposed to building security software Major methodologies Microsoft's Security Development
Bottlenecks in Agile Software Development Identified Using Theory of Constraints (TOC) Principles
 Master thesis in Applied Information Technology REPORT NO. 2008:014 ISSN: 1651-4769 Department of Applied Information Technology or Department of Computer Science Bottlenecks in Agile Software Development
Master thesis in Applied Information Technology REPORT NO. 2008:014 ISSN: 1651-4769 Department of Applied Information Technology or Department of Computer Science Bottlenecks in Agile Software Development
Agile Project Management and Agile Practices Training; with a Scrum Project that you will do.
 1 PMI Agile Certified Practitioner (PMI-ACP) workshop course details. We are unique and specialists in Agile! Your workshop trainer by passion and is a senior Agile Coach who coached many teams and Kanban
1 PMI Agile Certified Practitioner (PMI-ACP) workshop course details. We are unique and specialists in Agile! Your workshop trainer by passion and is a senior Agile Coach who coached many teams and Kanban
Agile processes. Extreme Programming, an agile software development process. Extreme Programming. Risk: The Basic Problem
 Agile processes Extreme Programming, an agile software development process Perdita Stevens School of Informatics University of Edinburgh What the spiral models were reaching towards was that software development
Agile processes Extreme Programming, an agile software development process Perdita Stevens School of Informatics University of Edinburgh What the spiral models were reaching towards was that software development
Testing in an Agile Environment
 Testing in an Agile Environment Marie Walsh [email protected] http://www.linkedin.com/in/mariewalsh In this presentation, Marie will share her experiences working in agile teams across multiple projects
Testing in an Agile Environment Marie Walsh [email protected] http://www.linkedin.com/in/mariewalsh In this presentation, Marie will share her experiences working in agile teams across multiple projects
Agile Beyond The Team 1
 Agile Beyond The Team 1 Dilbert Agile 2 What Does Your Organization Value? Projects over Teams? Do new teams spools up for new projects? On-Time/On-Budget Delivery over Zero Maintenance Products Deliver
Agile Beyond The Team 1 Dilbert Agile 2 What Does Your Organization Value? Projects over Teams? Do new teams spools up for new projects? On-Time/On-Budget Delivery over Zero Maintenance Products Deliver
Agile Requirements Generation Model: A Soft-structured Approach to Agile Requirements Engineering. Shvetha Soundararajan
 Agile Requirements Generation Model: A Soft-structured Approach to Agile Requirements Engineering Shvetha Soundararajan Thesis submitted to the faculty of the Virginia Polytechnic Institute and State University
Agile Requirements Generation Model: A Soft-structured Approach to Agile Requirements Engineering Shvetha Soundararajan Thesis submitted to the faculty of the Virginia Polytechnic Institute and State University
Threat modeling. Tuomas Aura T-110.4206 Information security technology. Aalto University, autumn 2011
 Threat modeling Tuomas Aura T-110.4206 Information security technology Aalto University, autumn 2011 Threats Threat = something bad that can happen Given an system or product what are the threats against
Threat modeling Tuomas Aura T-110.4206 Information security technology Aalto University, autumn 2011 Threats Threat = something bad that can happen Given an system or product what are the threats against
Ingegneria del Software Corso di Laurea in Informatica per il Management. Agile software development
 Ingegneria del Software Corso di Laurea in Informatica per il Management Agile software development Davide Rossi Dipartimento di Informatica Università di Bologna The problem Efficiency: too much effort
Ingegneria del Software Corso di Laurea in Informatica per il Management Agile software development Davide Rossi Dipartimento di Informatica Università di Bologna The problem Efficiency: too much effort
Software Application Control and SDLC
 Software Application Control and SDLC Albert J. Marcella, Jr., Ph.D., CISA, CISM 1 The most effective way to achieve secure software is for its development life cycle processes to rigorously conform to
Software Application Control and SDLC Albert J. Marcella, Jr., Ph.D., CISA, CISM 1 The most effective way to achieve secure software is for its development life cycle processes to rigorously conform to
Lean and Agile in Safety-critical Software Development Research and Practice. Henrik Jonsson 21.05.2014
 Lean and Agile in Safety-critical Software Development Research and Practice Henrik Jonsson 21.05.2014 About me 2012 Henrik Jonsson Professional Software engineer +13 years Employed by Etteplan Part-time
Lean and Agile in Safety-critical Software Development Research and Practice Henrik Jonsson 21.05.2014 About me 2012 Henrik Jonsson Professional Software engineer +13 years Employed by Etteplan Part-time
CHAPTER 3 : AGILE METHODOLOGIES. 3.3 Various Agile Software development methodologies. 3.4 Advantage and Disadvantage of Agile Methodology
 CHAPTER 3 : AGILE METHODOLOGIES 3.1Introductions 3.2 Main Stages in Agile project 3.3 Various Agile Software development methodologies 3.4 Advantage and Disadvantage of Agile Methodology 3.1Introductions
CHAPTER 3 : AGILE METHODOLOGIES 3.1Introductions 3.2 Main Stages in Agile project 3.3 Various Agile Software development methodologies 3.4 Advantage and Disadvantage of Agile Methodology 3.1Introductions
Water-Scrum-Fall Agile Reality for Large Organisations. By Manav Mehan Principal Agile consultant [email protected]
 Water-Scrum-Fall Agile Reality for Large Organisations By Manav Mehan Principal Agile consultant [email protected] Interests and Experience Leading Change and Transformation in Large, Complex organisations
Water-Scrum-Fall Agile Reality for Large Organisations By Manav Mehan Principal Agile consultant [email protected] Interests and Experience Leading Change and Transformation in Large, Complex organisations
When is Agile the Best Project Management Method? Lana Tylka
 When is Agile the Best Project Management Method? Lana Tylka Staged Incremental Deliveries Prototypes Plan Develop Design Deploy Test Maintain Sequential Steps Multiple Iterations Waterfall Sprints, Spirals
When is Agile the Best Project Management Method? Lana Tylka Staged Incremental Deliveries Prototypes Plan Develop Design Deploy Test Maintain Sequential Steps Multiple Iterations Waterfall Sprints, Spirals
How Product Management Must Change To Enable the Agile Enterprise
 How Product Management Must Change To Enable the Agile Enterprise Catherine Connor Agile Product Manager [email protected] Copyright 2003-2009, Rally Software Development Corp Why Are We Here? 2 About
How Product Management Must Change To Enable the Agile Enterprise Catherine Connor Agile Product Manager [email protected] Copyright 2003-2009, Rally Software Development Corp Why Are We Here? 2 About
Agile So6ware Development
 h(p://home.hit.no/~hansha/?page=so6ware_development Agile So6ware Development S. Adams. Dilbert. Available: h(p://dilbert.com Hans- Pe(er Halvorsen, M.Sc. 1 Agile? I ll go up and find out what they need
h(p://home.hit.no/~hansha/?page=so6ware_development Agile So6ware Development S. Adams. Dilbert. Available: h(p://dilbert.com Hans- Pe(er Halvorsen, M.Sc. 1 Agile? I ll go up and find out what they need
Mariusz Chrapko. Before: Software Quality Engineer/ Agile Coach, Motorola, Poland. My Public Profile: http://www.linkedin.
 Gathering Customer Requirements in an Agile Environment Mariusz Chrapko ReConf 2009, Munich Mariusz Chrapko Now: Process Consultant/ Agile Coach@Kugler Maag CIE, Stuttgart Supported Areas: - CMMI - SPICE/
Gathering Customer Requirements in an Agile Environment Mariusz Chrapko ReConf 2009, Munich Mariusz Chrapko Now: Process Consultant/ Agile Coach@Kugler Maag CIE, Stuttgart Supported Areas: - CMMI - SPICE/
Software Development Going Incremental, Iterative and Agile:
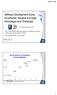 Software Development Going Incremental, Iterative and Agile: Advantages and Challenges An Industrial Case Study Prof. Claes Wohlin, Blekinge Institute of Technology, Sweden Professorial Visiting Fellow,
Software Development Going Incremental, Iterative and Agile: Advantages and Challenges An Industrial Case Study Prof. Claes Wohlin, Blekinge Institute of Technology, Sweden Professorial Visiting Fellow,
Transitioning Your Software Process To Agile Jeffery Payne Chief Executive Officer Coveros, Inc. [email protected] www.coveros.
 Transitioning Your Software Process To Agile Jeffery Payne Chief Executive Officer Coveros, Inc. [email protected] www.coveros.com 1 About Coveros Coveros helps organizations accelerate the delivery
Transitioning Your Software Process To Agile Jeffery Payne Chief Executive Officer Coveros, Inc. [email protected] www.coveros.com 1 About Coveros Coveros helps organizations accelerate the delivery
Agile Testing. What Students Learn
 Agile Testing Transition sound traditional test practices into an Agile development environment. By using a step-by-step approach, this course documents how to transition from traditional test practices
Agile Testing Transition sound traditional test practices into an Agile development environment. By using a step-by-step approach, this course documents how to transition from traditional test practices
IBM Innovate 2011. AppScan: Introducin g Security, a first. Bobby Walters Consultant, ATSC [email protected] Application Security & Compliance
 IBM Innovate 2011 Bobby Walters Consultant, ATSC [email protected] Application Security & Compliance AppScan: Introducin g Security, a first June 5 9 Orlando, Florida Agenda Defining Application Security
IBM Innovate 2011 Bobby Walters Consultant, ATSC [email protected] Application Security & Compliance AppScan: Introducin g Security, a first June 5 9 Orlando, Florida Agenda Defining Application Security
Managing Vulnerabilities for PCI Compliance White Paper. Christopher S. Harper Managing Director, Agio Security Services
 Managing Vulnerabilities for PCI Compliance White Paper Christopher S. Harper Managing Director, Agio Security Services PCI STRATEGY Settling on a PCI vulnerability management strategy is sometimes a difficult
Managing Vulnerabilities for PCI Compliance White Paper Christopher S. Harper Managing Director, Agio Security Services PCI STRATEGY Settling on a PCI vulnerability management strategy is sometimes a difficult
Using Simulation to teach project management skills. Dr. Alain April, ÉTS Montréal [email protected]
 Using Simulation to teach project management skills Dr. Alain April, ÉTS Montréal [email protected] Agenda of the workshop 1 The software project management theory overview (40 minutes) 2 Why use SDLC
Using Simulation to teach project management skills Dr. Alain April, ÉTS Montréal [email protected] Agenda of the workshop 1 The software project management theory overview (40 minutes) 2 Why use SDLC
AGILE & SCRUM. Revised 9/29/2015
 AGILE & SCRUM Revised 9/29/2015 This Page Intentionally Left Blank Table of Contents Scrum Fundamentals Certified Course... 1 Scrum Developer Certified (SDC)... 2 Scrum Master Certified (SMC)... 3 Scrum
AGILE & SCRUM Revised 9/29/2015 This Page Intentionally Left Blank Table of Contents Scrum Fundamentals Certified Course... 1 Scrum Developer Certified (SDC)... 2 Scrum Master Certified (SMC)... 3 Scrum
Integrating Security into the Application Development Process. Jerod Brennen, CISSP CTO & Principal Security Consultant, Jacadis
 Integrating Security into the Application Development Process Jerod Brennen, CISSP CTO & Principal Security Consultant, Jacadis Agenda Seek First to Understand Source Code Security AppSec and SQA Analyzing
Integrating Security into the Application Development Process Jerod Brennen, CISSP CTO & Principal Security Consultant, Jacadis Agenda Seek First to Understand Source Code Security AppSec and SQA Analyzing
Software Development Process
 Software Development Process A software development process, also known as software development lifecycle, is a structure imposed on the development of a software product. Similar terms include software
Software Development Process A software development process, also known as software development lifecycle, is a structure imposed on the development of a software product. Similar terms include software
Agile Testing and Extreme Programming
 Agile Testing and Extreme Programming [email protected] www.pettichord.com March 2003 Copyright 2003 Bret Pettichord. All rights reserved. The Agile Alliance Values We have come to value: Individuals
Agile Testing and Extreme Programming [email protected] www.pettichord.com March 2003 Copyright 2003 Bret Pettichord. All rights reserved. The Agile Alliance Values We have come to value: Individuals
Agile processes. Extreme Programming, an agile software development process
 Agile processes Extreme Programming, an agile software development process Nigel Goddard School of Informatics University of Edinburgh What the spiral models were reaching towards was that software development
Agile processes Extreme Programming, an agile software development process Nigel Goddard School of Informatics University of Edinburgh What the spiral models were reaching towards was that software development
Secure Development LifeCycles (SDLC)
 www.pwc.com Feb 2014 Secure Development LifeCycles (SDLC) Bart De Win Bart De Win? 15+ years of Information Security Experience Ph.D. in Computer Science - Application Security Author of >60 scientific
www.pwc.com Feb 2014 Secure Development LifeCycles (SDLC) Bart De Win Bart De Win? 15+ years of Information Security Experience Ph.D. in Computer Science - Application Security Author of >60 scientific
Chapter 6. Iteration 0: Preparing for the First Iteration
 Chapter 6. Iteration 0: Preparing for the First Iteration People only see what they are prepared to see. Ralph Waldo Emerson There are no secrets to success. It is the result of preparation, hard work,
Chapter 6. Iteration 0: Preparing for the First Iteration People only see what they are prepared to see. Ralph Waldo Emerson There are no secrets to success. It is the result of preparation, hard work,
A Capability Maturity Model (CMM)
 Software Development Life Cycle (SDLC) and Development Methods There are some enterprises in which a careful disorderliness is the true method. Herman Melville Capability Maturity Model (CMM) A Capability
Software Development Life Cycle (SDLC) and Development Methods There are some enterprises in which a careful disorderliness is the true method. Herman Melville Capability Maturity Model (CMM) A Capability
Integrating Software Development Security Activities with Agile Methodologies
 Integrating Software Development Activities with Agile Methodologies Hossein Keramati, Seyed-Hassan Mirian-Hosseinabadi Sharif University of Technology [email protected], [email protected]
Integrating Software Development Activities with Agile Methodologies Hossein Keramati, Seyed-Hassan Mirian-Hosseinabadi Sharif University of Technology [email protected], [email protected]
Agile Methodologies and Its Processes
 International Journal of Computational Engineering Research Vol, 03 Issue, 9 Agile Methodologies and Its Processes 1, Akanksha, 2, Akansha Rakheja, 3, Latika Kapur, 4, Kanika Ahuja 1,2,3,, Information
International Journal of Computational Engineering Research Vol, 03 Issue, 9 Agile Methodologies and Its Processes 1, Akanksha, 2, Akansha Rakheja, 3, Latika Kapur, 4, Kanika Ahuja 1,2,3,, Information
Functional vs. Load Testing
 Best Practices in Performance & Security Testing March 26, 2009 CVN www.sonata-software.com Functional vs. Load Testing Functional test Objective Functionality Example Do business processes function properly
Best Practices in Performance & Security Testing March 26, 2009 CVN www.sonata-software.com Functional vs. Load Testing Functional test Objective Functionality Example Do business processes function properly
Agile Security Successful Application Security Testing for Agile Development
 WHITE PAPER Agile Security Successful Application Security Testing for Agile Development Software Security Simplified Abstract It is an imperative to include security testing in application development.
WHITE PAPER Agile Security Successful Application Security Testing for Agile Development Software Security Simplified Abstract It is an imperative to include security testing in application development.
An Agile Project Management Model
 Agile Project Management Jim Highsmith Chapter 5 An Agile Project Management Model We improve effectiveness and reliability through situationally specific strategies, processes, and practices. One of the
Agile Project Management Jim Highsmith Chapter 5 An Agile Project Management Model We improve effectiveness and reliability through situationally specific strategies, processes, and practices. One of the
Table of contents. Performance testing in Agile environments. Deliver quality software in less time. Business white paper
 Performance testing in Agile environments Deliver quality software in less time Business white paper Table of contents Executive summary... 2 Why Agile? And, why now?... 2 Incorporating performance testing
Performance testing in Agile environments Deliver quality software in less time Business white paper Table of contents Executive summary... 2 Why Agile? And, why now?... 2 Incorporating performance testing
Scrum. in five minutes
 Scrum in five minutes Scrum and agile methods are hot topics these days A simple method for the management of complex projects... Older methods focus on staying on track; Scrum is aimed at delivering business
Scrum in five minutes Scrum and agile methods are hot topics these days A simple method for the management of complex projects... Older methods focus on staying on track; Scrum is aimed at delivering business
CSSE 372 Software Project Management: More Agile Project Management
 CSSE 372 Software Project Management: More Agile Project Management Shawn Bohner Office: Moench Room F212 Phone: (812) 877-8685 Email: [email protected] Learning Outcomes: Plan Create a plan for
CSSE 372 Software Project Management: More Agile Project Management Shawn Bohner Office: Moench Room F212 Phone: (812) 877-8685 Email: [email protected] Learning Outcomes: Plan Create a plan for
Software Development: The Next Security Frontier
 James E. Molini, CISSP, CSSLP Microsoft Member, (ISC)² Advisory Board of the Americas [email protected] http://www.codeguard.org/blog Software Development: The Next Security Frontier De-perimiterization
James E. Molini, CISSP, CSSLP Microsoft Member, (ISC)² Advisory Board of the Americas [email protected] http://www.codeguard.org/blog Software Development: The Next Security Frontier De-perimiterization
Basic Trends of Modern Software Development
 DITF LDI Lietišķo datorsistēmu programmatūras profesora grupa e-business Solutions Basic Trends of Modern Software Development 2 3 Software Engineering FAQ What is software engineering? An engineering
DITF LDI Lietišķo datorsistēmu programmatūras profesora grupa e-business Solutions Basic Trends of Modern Software Development 2 3 Software Engineering FAQ What is software engineering? An engineering
Agile project management: A magic bullet?
 Agile project management: A magic bullet? Prof. Darren Dalcher [email protected] Conferencia Iberoamericana de Calidad del Software Prof. Darren Dalcher 1 Outline I. What is agilility? The agile manifesto
Agile project management: A magic bullet? Prof. Darren Dalcher [email protected] Conferencia Iberoamericana de Calidad del Software Prof. Darren Dalcher 1 Outline I. What is agilility? The agile manifesto
Agile and lean methods for managing application development process
 Agile and lean methods for managing application development process Hannu Markkanen 27.01.2012 1 Lifecycle model To support the planning and management of activities required in the production of e.g.
Agile and lean methods for managing application development process Hannu Markkanen 27.01.2012 1 Lifecycle model To support the planning and management of activities required in the production of e.g.
SECC Agile Foundation Certificate Examination Handbook
 Versions 2.0 Version Date Remarks 1.0 12/4/2012 Initial version 2.0 3/8/2008 REVISION HISTORY Updated knowledge areas Added questions examples Updated suggested readings section Page 2 of 15 Version 2.0
Versions 2.0 Version Date Remarks 1.0 12/4/2012 Initial version 2.0 3/8/2008 REVISION HISTORY Updated knowledge areas Added questions examples Updated suggested readings section Page 2 of 15 Version 2.0
Course Title: Managing the Agile Product Development Life Cycle
 Course Title: Managing the Agile Product Development Life Cycle Course ID: BA25 Credits: 28 PDUs Course Duration: 4 days (with optional Executive session) Course Level: Intermediate/Advanced Course Description:
Course Title: Managing the Agile Product Development Life Cycle Course ID: BA25 Credits: 28 PDUs Course Duration: 4 days (with optional Executive session) Course Level: Intermediate/Advanced Course Description:
Getting Business Value from Agile
 Getting Business Value from Agile Presented by: Dennis Baldwin Project Management, Business Analysis & Agile Service Line Manager, Development Solutions Practice, Experis Tom Mullen Business Planning &
Getting Business Value from Agile Presented by: Dennis Baldwin Project Management, Business Analysis & Agile Service Line Manager, Development Solutions Practice, Experis Tom Mullen Business Planning &
