TPM Key Backup and Recovery. For Trusted Platforms
|
|
|
- Janis Hoover
- 10 years ago
- Views:
Transcription
1 TPM Key Backup and Recovery For Trusted Platforms White paper for understanding and support proper use of backup and recovery procedures for Trusted Computing Platforms V0.95 Page 1 / 17
2 Contents 1. Introduction Implementation: Emergency Recovery Token, Password and Archive Tokens, Archives and other TPM security management files Initialize or restore a Trusted Security Platform Generating Emergency Recovery Data Wizard Page Elements Restore Emergency Recovery Data Step by Step Administrative Steps User Step Frequently Asked Questions (FAQ) Is it a security problem to store Emergency Recovery data on a remote machine? What information is left on a system after a successful uninstallation of the Trusted Security SW package? How can a Trusted Security Platform be prepared for a successful system backup? Which files are essential for a successful restoration of a Trusted Security Platform using system mechanisms? How has the Backup Archive to be configured and handled, especially with respect to the policy settings? Annex 1: Trusted Platform Module: Security Key and Data Hierarchy V0.95 Page 2 / 17
3 Executive Summary The complete trust and security functionality of a Trusted Computing Platform (TCP) is based on the Trusted Platform Module (TPM) silicon chip and its capabilities to store a set of keys safely inside. These keys and certificates have different tasks and usage scenarios: A. Signing and verifying other key material to show its validity and its integrity within the TP usage and application scenario. A1 Signing data and keys which belong to this specific TPM and should not be used or are not useful on another TPM (Non migratable keys, e.g. certificate tree inside the TPM based on TPM specific root keys). A2 Signing data and keys which are referenced to specific users and their application fields (migratable keys, e.g. user specific certificates like mail signing and encryption, user specific SW authentication or service access keys and similar. It could be even necessary that such migratable keys are required on different platforms, which are handled by a user alternatively. This is especially the case for access rights or licenses for SW and similar use areas, where the user wants to have access independently of the platform and related TPM, where he is currently working. The most dangerous, assumable accident which could happen with a TP is either the defect of a TPM itself or even any damage of a motherboard. It is unusual to repair single components of a motherboard in a maintenance situation; usually the whole motherboard will be replaced. And this is also valid for the TPM on such a motherboard. If critical data e.g. in a PC are secured by encryption and the related user key is stored in the TPM which can not be replaced in a maintenance situation, a loss of complete information could occur in such a situation. This is even more problematic because one of the ideas behind the TPM is the protection of any key material inside the TPM against all type of attacks and damage and also against denial of service by hardware defects. To prevent such problems and solve critical situations the TCG standardization group has created some protocol elements to do a secure backup on such critical TPM data and store the backup data on an external storage device. These procedures encrypt all the TPM data for external storage, store them on a safe location selected by the owner and decrypt them again during a recovery procedure V0.95 Page 3 / 17
4 1. Introduction The Backup Procedures are designed to offer large scale support not only for standard work flows, but especially also for recovery operations on the system in case of a severe error situation (Motherboard or even TPM damage and replacement). The worst kind of problem is damage to the Trusted Platform Module (TPM) Security Chip or even with a much higher probability the replacement of a motherboard where out of repair policy the replacement of the old PC will not be possible. A situation with the loss of the TPM would also result in a loss of the TPM Owner key, which is the physical root for secrets as well as the logical root for all User specific keys. Whenever the TPM Security Chip must be replaced, a new Owner key is created, as there is no way to transfer an existing key from one Embedded Security Chip to another. This transfer is not possible due to the digital signing of the owner key which chip specific credentials (like the handle to the chip individual Endorsement key). A transfer of such an SRK to another TPM would disable signature verification with the new TPM and produce loss of validity of all keys and certificates within the chips internal certificate chain. To overcome this potential problem, an Emergency Recovery mechanism is available together with the Infineon TPM professional SW package. This backup and migration capability is one of the cornerstones to allow the user a comfortable use of the applications without the danger of total data loss due to system errors and missing backup support. For a simple integration and activation of all this backup and migration features the necessary keys and TPM backup storage reservation will be made already during the TPM activation and take ownership procedure during the installation and set up phase. For an easy handling all the required activities are handled by the TPM owner (usually the system administrator by using the Initialization Wizard. The restoration in case of emergency is done using the Backup Wizard. 1.1 Implementation: All these functions are implemented within the Infineon Professional Package which is available as an OEM product and is part of a PC package outfitted with an Infineon TPM. This OEM package will be delivered from nearly every PC manufacturers, which integrates and sells trusted Computing (PC)-Platforms based on an Infineon TPM chip. In an organization with a large PC fleet and a dedicated IT department it is also advisable to handle these backup versions by a centralized Backup-Server under the control of the IT department, which also initiates the necessary backup, recovery and migration tools and procedures. For planning and installation of such backup infrastructure either the PC manufacturer or also Infineon may have made available some implementation examples and hints. 1.2 Emergency Recovery Token, Password and Archive The Emergency Recovery concept is similar to Password Reset concerning the usage of token, password and archive V0.95 Page 4 / 17
5 Restoring user keys in case of emergency requires some information stored in an archive. Emergency Recovery data in this archive can only be used in combination with a recovery token which is protected with a dedicated password. The archive contains encrypted copies of Basic User keys in order to allow restoration in case of Embedded Security Chip failure. If Emergency Recovery is not set up, users may not be able to restore their encrypted data in case of Embedded Security failure. Emergency Recovery is set up once, and the concerned archive is automatically accessed later by Embedded Security components. The archive file must be accessible for all users of this Embedded Security. For some general aspects on handling Emergency Recovery refer to the Frequently Asked Questions V0.95 Page 5 / 17
6 2 Tokens, Archives and other TPM security management files The Trusted Security SW package uses several files for management tasks such as backup, Emergency Recovery or Password Reset (e.g. tokens and archives). Some of them are for the TPM Owner or Administrator, others are for TPM Security Users. Please make sure not to mix up these file types. The following table gives an overview of TPM Security management files. File Used by... Purpose/Explanation Archives used for restoration, Emergency Recovery and Password Reset Emergency Token Recovery Password Reset Token Migration Archive Personal Secret for Password Reset Reset Code File Authorization PKCS #12 file (Personal Information Exchange file) Administrator/User Administrator Administrator User User Administrator/User User Contain TPM Security credentials, TPM Security settings and Personal Secure Drive backups. Created by automatic and manual backup. Required for restoration in case of a broken hard disk or lost data, exchange of complete motherboard or a broken TPM Security Chip. The Password Reset data in an archive is required to reset Basic User Passwords. Created during the configuration of Trusted Security Features. Required for restoration, if Emergency Recovery is needed (broken TPM Security Chip). Created during the configuration of Trusted Security Features. Required to prepare the Password Reset for a specific user. Contains user keys and certificates to be migrated to another Trusted Computing Platform. Created during the Export step of migration. Required during the Import step of migration. Created during the configuration of Trusted Security User Settings. Required to reset a user's Basic User Password. Contains the Reset Authorization Code which is needed to reset a user's Basic User Password. Created during the administrative steps of Password Reset. Required during the user steps of Password Reset. Contains a user's private key and certificate. Needed to import a certificate V0.95 Page 6 / 17
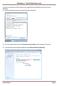
7 3 Initialize or restore a Trusted Security Platform There exists a wizard (Application advise and support routine) for supporting you for this feature. The wizard page asks whether you want to initialize or restore the trusted Security SW and data package. Wizard Page Element Explanation Initialize a new Trusted Security Restore a Trusted Security from a Backup Archive Click here if you want to set up a new Trusted Security. In this case new platform and user credentials will be created. Click here if you want to restore a Trusted Security package after a failure, replacement or reset of hardware, storage media or Trusted Platform Module (TPM) Chip. Trusted Security Platform Restoration reestablishes access to Trusted Security Platform Software features for all users V0.95 Page 7 / 17
8 4 Generating Emergency Recovery Data Availability of function: This function is only available, if you have selected to configure automatic Trusted Security backups. This functionality is supported by a wizard (Application advise and support routine) for supporting you for this feature. This wizard is accessible via the Trusted Security management menu. 4.1 Wizard Page Elements Note that your options within this wizard page may be restricted depending on system policies. The following table gives hints on how to use this wizard page. Wizard Page Element Explanation Create new recovery token Select this option, if you want to create a new token to be used for Emergency Recovery. The token will be written to the location you have specified. You will have to set a new token password. Select this option, if the following conditions are met: Use existing recovery token In case of emergency, you want to restore your system using an Emergency Recovery Token which was created before. This token and the token password are currently accessible. You will have to verify the token password, i.e. you need to enter the password only once. Select this option, if the following conditions are met: Use existing recovery archive In case of emergency, you want to restore your system using an Emergency Recovery Token which was created before. You have access to an archive containing the token's public key. You will not need to enter the token password now. File location Browse... Configuring Emergency Recovery to use an existing token requires only the token's public key. Performing a restoration including Emergency Recovery requires access to the token and knowledge of the token password in any case. If your policy settings permit a manual specification of the file location, you may change file name and path. Type in path and file name or browse for it. This file has XML format, the extension *.xml must be used V0.95 Page 8 / 17
9 If you selected Create new recovery token: The Emergency Recovery Token should be saved in a secure location such as a removable media stored in a secure environment. Do not store the recovery token on your hard drive. Otherwise in case of system or hard drive failure, your token will not be accessible and will result in data loss. Store the recovery token on a backup medium like a memory drive or a CD in order to prevent loss of this token and ensure that only you have access to this recovery token. If you selected Create new recovery token, you need to set a new token password. Enter a password for the Emergency Recovery Token. Consider general hints regarding passwords. Password If you selected Use existing recovery token, you need to verify the token password. Enter the existing token's password. Password If you selected Use existing recovery archive, you do not need to enter a password. Confirm If you selected Create new recovery token, you need to confirm your new password. Enter the password again to confirm V0.95 Page 9 / 17
10 5 Restore Emergency Recovery Data Step by Step With the Emergency Recovery data you can restore the main data from the TPM (which contains all user specific key material) in case of failure and subsequent replacement of your TPM Security Chip. The restoration process has two parts: Part to be performed by an Embedded Security Administrator: Recreation of the fundamental TPM functionality (includes the activation of the TPM Security Chip, initialization of the TPM Security Management Functions and restoring Emergency Recovery data). Performed by all Embedded Security Users: Restoration of Basic User Keys in order to gain access to protected data again, or generation of new Basic User Keys (which will result in overwriting existing key material and therefore loss of all existing protected data). Preconditions: Backup Archive including Emergency Recovery data: This file is created when the Trusted Security feature Backup is configured. Configuring Backup including Emergency Recovery is highly recommended in order to preserve user data in case of severe system failure. The Backup Archive must be accessible for the restoration process. It should be stored in a fail safe location like a network folder with regular backup. If located on a local hard disk, it is recommended to include this file in a periodical backup. The frequently asked questions cover additional tips on setting up Emergency Recovery data correctly. Emergency Recovery Token: This file protects Emergency Recovery data in an encrypted form from unauthorized use and requires knowledge of a separate password. It is created when the Embedded Security feature Backup is configured. It should be stored separately from the Backup Archive on a removable storage device in a secure environment. The Emergency Recovery Token must be accessible for the restoration process. 5.1 Administrative Steps Step 1 - Preparation of the TPM Security Chip How To: One possible restoration reason is a failure of your TPM Embedded Security Chip. If this happens, the new chip must be enabled in the system BIOS first. This operation is performed by a system If other hardware caused the malfunction (e.g. hard administrator. A specific description on how to enable disk failure), the system must be set up properly the chip is available here: (operating system restored, user profile and protected data restored) before the Trusted Security SW can be restored. Step 2 - Initialization and Restoration of Emergency Recovery Data How To: After the TPM Security Chip has been enabled, you Only the Trusted platform Owner (usually the must initialize the Security SW package and restore system Administrator can restore Emergency the Emergency Recovery data. Both the Backup Recovery data. Start the Trusted Computing TPM Archive file and Emergency Recovery Token file must Initialization Wizard and select Restore an Embedded be accessible to perform this step. Security from a backup archive V0.95 Page 10 / 17
11 5.2 User Step Recovery of Trusted Computing TPM User and data How To: Start the Embedded Security User Initialization Wizard. The wizard automatically detects the recovery state immediately after it is started. It offers the choice After the administrative operations are finalized, of creating a new Basic User Key or restoring an restoration operation for TPM Users can be performed. existing key from a Backup Archive. Usually an Restoration must be done for each individual User in existing key should be recovered, because otherwise a separate step. all previously encrypted data (still protected by the old Basic User Key) will not be accessible. Follow the on screen directions to finish the process. Background Information: Forced User Initialization when Backup Archive is not available: If the Basic User Key cannot be loaded (for example as a result of clearing Embedded Security Chip ownership and taking ownership again) then Embedded Security User Initialization Wizard does not allow to proceed with user initialization. The correct step in this situation is to restore Emergency Recovery data. If for some reason the Backup Archive is not available (for example it was lost or corrupted) then the Basic User Key cannot be restored. To proceed with the creation of a new Basic User Key in this situation the Embedded Security User Initialization Wizard must be started with command line parameter: SpUserWz.exe /forceinit. Note: A new Basic User Key will be created and therefore all previously protected data will be lost V0.95 Page 11 / 17
12 6 Frequently Asked Questions (FAQ) Is it a security problem to store Emergency Recovery data on a remote machine? There is no security problem. The data is protected (encrypted) by the Emergency Recovery Token, which in turn is protected by the Emergency Recovery Token password What information is left on a system after a successful uninstallation of the Trusted Security SW package? If the Trusted Security Software is uninstalled, some TPM backup information and similar data is left on the system. Keeping the platform and user settings and credentials, after a re-installation the system will have the same state as before. Thus no previously encrypted data will be lost after a reinstallation of the Trusted Security Software. However, if this data is no longer needed and the system is to be completely cleaned up, the following data should be deleted. Backup Archives: The location of automatically written Backup Archives is specified by the administrators. Please note that an automatically written Backup Archive is represented on the file system by an XML file and a folder with the same name, e.g. file SPSystemBackup.xml and folder SPSystemBackup. Additionally, there may be some manually written Backup Archives. Emergency Recovery Token: The location is specified by the Embedded Security Owner during Embedded Security initialization. Emergency Restoration Archive: \%ALLUSERPROFILE%\<Application Data>\Infineon\TPM Software 2.0\RestoreData\<Machine SID>\Users\<User SIDs>\SHTempRestore.xml System Data and System Keys Files: \%ALLUSERPROFILE%\<Application Data>\Infineon\TPM Software 2.0\PlatformKeyData IFXConfigSys.xml IFXFeatureSys.xml TCSps.xml Local Shadow Backup Files: \%ALLUSERPROFILE%\<Application Data>\Infineon\TPM Software 2.0\BackupData\<Machine SID>\System\SHBackupSys.xml \%ALLUSERPROFILE%\<Application Data>\Infineon\TPM Software 2.0\BackupData\<Machine SID>\Users\<User SIDs\SHBackup.xml User Key Files: \%AppData%\Infineon\TPM Software 2.0\UserKeyData\TSPps.xml V0.95 Page 12 / 17
13 TPM Cryptographic Service Provider Container: \%AppData%\Infineon\TPM Software 2.0\UserKeyData\TPMcp.xml TPM PKCS #11 Provider File: \%AppData%\Infineon\TPM Software 2.0\UserKeyData\TPMck.xml User Configuration Files: \%AppData%\Infineon\TPM Software 2.0\UserKeyData\ IFXConfig.xml IFXFeature.xml Registry keys: HKEY_LOCAL_MACHINE\SOFTWARE\Infineon\TPM Software HKEY_CURRENT_USER\Software\Infineon\TPM software The following Personal Secure Drive registry keys have to be deleted manually, when the Personal Secure Drive security feature is uninstalled: [HKEY_LOCAL_MACHINE\SOFTWARE\Infineon\TPM Software\PSD] [HKEY_CURRENT_USER\SOFTWARE\Infineon\TPM Software\PSD] [HKEY_USERS\.DEFAULT\Software\Microsoft\SystemCertificates\PSD] [HKEY_USERS\S \Software\Microsoft\SystemCertificates\PSD] Personal Secure Drive Directories: Additionally, the following directories have to be deleted manually: x:\embedded Security\Personal Secure Drive\System Data where x: is the drive where Personal Secure Drives are located. This drive is either selected during Personal Secure Drive creation and can therefore be any local hard disk or else is defined by the Personal Secure Drive local user policy. Miscellaneous: Registered TPM Embedded Security Chip based certificates Scheduled Backup Task (e.g. C:\WINDOWS\Tasks\Embedded Security Backup Schedule) How can a Trusted Security Platform be prepared for a successful system backup? Which files are essential for a successful restoration of a Trusted Security Platform using system mechanisms? The core files of the Trusted Security Platform do not include the applications of the Trusted Security SW package. It can be re-installed after a system backup has been restored. The Trusted Security Platform Software specific data is backed up using the Trusted Security Platform Backup Wizard. The Trusted Security Platform Backup Wizard does not backup protected data like your encrypted files or which have to be backed up utilizing other backup tools. You should include the Backup Archive of the Trusted Security Platform in your routine mass data backup. Automatic system backups set up by the Embedded Security Administrator include also Emergency Recovery data V0.95 Page 13 / 17
14 If you do not use the Trusted Security Platform Backup Wizard for the Software specific data, then please make sure to backup all the data listed in the section What information is left on a system after a successful uninstallation? How has the Backup Archive to be configured and handled, especially with respect to the policy settings? You can configure all your enterprise Trusted Platforms to use a common Backup Archive by setting a policy. In case a new Backup Archive file has to be created, it is very important not to import the policies before the Trusted Security Platform Software has been setup using the Trusted Security Platform Software Initialization Wizard. The Backup Archive has to be a file with the extension *.xml. This is checked by the system. Any other extension will result in an error situation. After this, the policy administration has to be started and the policy has to be configured correctly by setting the location of the previously created Backup Archive. Finally the configured file will be used by the Trusted Security Platform Software Initialization Wizard automatically while enrolling the enterprise Embedded Securities V0.95 Page 14 / 17
15 7 Annex 1: Trusted Platform Module: Security Key and Data Hierarchy A1.1 Key and certificate chain in the TPM as starting point of the chain of trust As the TPM Specification in accordance with the trust requirements of the TCG is completely public and accessible to all, someone could clone their own TPM on a processor in conformance with this Specification. If e.g. secure e-commerce processes are then transacted, the owner of this "special" TPM could easily modify the internal data to his advantage: such a module would certainly enjoy the full trust of its owner, but would be totally unsuitable for exchanging trusted processes. A trust structure has therefore been implemented which is already known from high-security bank cards: A1.1.1 Endorsement Key At the end of TPM chip fabrication (after final testing), the manufacturer generates a 2048 bit private/public key pair in the TPM, the so-called Endorsement Key. This is stored in such a way that the private key (PK) can no longer be read out, but can only be used internally in the TPM. The EK is additionally protected by a special certificate. The manufacturer thereby confirms electronically that this TPM has been produced in a trusted process by an inspected manufacturer and meets the requirements of the Specification. The trustworthiness of the entire TPM system is based for the most part on this process and the uniqueness of the EK. The user must trust the manufacture that the private part of the key is not stored anywhere, and that it is not accessible to anyone else. This aspect is also intensively tested as part of the security evaluation. In the case of qualified manufacturers such as Infineon, this fundamental process is performed in the same certified high-security area as for smart cards. A1.1.2 Storage Root Key (SRK) The SRK forms the root of a key hierarchy in which other lower-order keys, but also data (blobs), are securely stored, their trustworthiness therefore depending on the SRK. The SRK is automatically generated by the owner in a Take Ownership operation. If the owner of a TPM gives up this ownership, this also deletes the SRK and also makes all the keys protected by it completely unusable, which is welcome for data protection purposes. A1.1.3 Basic User Key (BUK) The SRK forms the root of a key hierarchy in which other lower-order keys, but also data (blobs), are securely stored, their trustworthiness therefore depending on the SRK. The SRK is automatically generated by the owner in a Take Ownership operation. If the owner of a TPM gives up this ownership, this also deletes the SRK and also makes all the keys protected by it completely unusable, which is welcome for data protection purposes. A1.1.4 Certificates Additional confidence in the correctness of the platform is created using further cryptographic certificates which are likewise stored in the TPM: The Endorsement Certificate confirms that the TPM originates from a trusted source. It contains the public key (PK) of the EK and is used for forming the AIK. The Platform Certificate is brought in by the motherboard/pc manufacturer and confirms that a valid TPM has been mounted in a correct platform. It is likewise used for forming AIKs V0.95 Page 15 / 17
16 The Conformance Certificate is issued by a test laboratory and confirms that the security functions of the TPM and motherboard have been positively checked and are compliant with the protection profile of the TCG. The concatenation of these various certificates, credentials and keys in order to be able to make various security declarations constitutes a highly sophisticated logical system. The interested reader is referred to [TCG01] TCG Specification Architecture Overview, Sect TPM Endorsement Key Storage Root Key Key Cache Manager Authorization Data Platform Cert. Keys 1 n External Storage (Disk) Conformance Cert. PCRs Storage Key AIK Key Signature Key Gen. Data Fig. 5: Certificate chain A1.2 Key migration As both platform-related and person-related keys (user keys) can be stored via the TPM, the need arises to transfer the user keys securely to other platforms. For this purpose the TCG has defined a set over rules under the term migration: A1.2.1 Non-migratable keys (bound to the platform) Examples :! EK: Endorsement Key of the TPM manufacturer! SRK: Storage Root Key These keys basically cannot be transferred to other TPMs as they are platform-specific. Under the rules, backup (maintenance) is possible as provided for in the Specification. A1.2.2 Migratable keys (transferable to other platforms) V0.95 Page 16 / 17
17 Example:! All the keys (if generated in a migratable manner) and data employed by the user and stored under the storage key. A1.3 Transport modes A1.3.1 Migration (Transfer to other TPMs) For migration a special authorization process is used and the data material is transported in a password-protected container for security purposes. In practical terms this can be accomplished by a special migration server A1.3.2 Maintenance (backing up and restoring key material) This feature is used for data/key backup in the event of a hardware defect (recommendation only). Implementation by backup server or e.g. smart cards References [TCG01] Trusted Computing Group Website: Published by: Infineon Technologies AG St.-Martin-Strasse Munich, Germany Phone: [email protected] Infineon Technologies AG. All rights reserved V0.95 Page 17 / 17
TPM. (Trusted Platform Module) Installation Guide V2.1
 TPM (Trusted Platform Module) Installation Guide V2.1 Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM... 6 2.2 Installing
TPM (Trusted Platform Module) Installation Guide V2.1 Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM... 6 2.2 Installing
TPM. (Trusted Platform Module) Installation Guide V3.3.0. for Windows Vista
 TPM (Trusted Platform Module) Installation Guide V3.3.0 for Windows Vista Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM...
TPM (Trusted Platform Module) Installation Guide V3.3.0 for Windows Vista Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM...
DIGIPASS CertiID. Getting Started 3.1.0
 DIGIPASS CertiID Getting Started 3.1.0 Disclaimer Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without any other warranties, or conditions, express
DIGIPASS CertiID Getting Started 3.1.0 Disclaimer Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without any other warranties, or conditions, express
Table of Contents. TPM Configuration Procedure... 2. 1. Configuring the System BIOS... 2
 Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Opal SSDs Integrated with TPMs
 Opal SSDs Integrated with TPMs August 21, 2012 Robert Thibadeau, Ph.D. U.S. Army SSDs Must be Opal s We also Studied using the TPM (Trusted Platform Module) with an Opal SSD (Self-Encrypting Drive) 2 Security
Opal SSDs Integrated with TPMs August 21, 2012 Robert Thibadeau, Ph.D. U.S. Army SSDs Must be Opal s We also Studied using the TPM (Trusted Platform Module) with an Opal SSD (Self-Encrypting Drive) 2 Security
HP ProtectTools Embedded Security Guide
 HP ProtectTools Embedded Security Guide Document Part Number: 364876-001 May 2004 This guide provides instructions for using the software that allows you to configure settings for the HP ProtectTools Embedded
HP ProtectTools Embedded Security Guide Document Part Number: 364876-001 May 2004 This guide provides instructions for using the software that allows you to configure settings for the HP ProtectTools Embedded
Motion Computing Tablet PC
 Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Motion Computing Tablet PC TRUSTED PLATFORM MODULE (TPM) ACTIVATION User Guide Trusted Platform Module Activation With the Infineon Security Platform Tools and the built-in Trusted Computing Group compliant
Smart TPM. User's Manual. Rev. 1001 12MD-STPM-1001R
 Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
Acronym Term Description
 This glossary contains definitions of terms created by TCG, or terms that have a particular meaning in trusted computing, or terms that cause particular confusion in trusted computing. Acronym Term Description
This glossary contains definitions of terms created by TCG, or terms that have a particular meaning in trusted computing, or terms that cause particular confusion in trusted computing. Acronym Term Description
SecureStore I.CA. User manual. Version 2.16 and higher
 User manual Version 2.16 and higher Contents SecureStore I.CA 1. INTRODUCTION...3 2. ACCESS DATA FOR THE CARD...3 2.1 Card initialisation...3 3. MAIN SCREEN...4 4. DISPLAYING INFORMATION ABOUT THE PAIR
User manual Version 2.16 and higher Contents SecureStore I.CA 1. INTRODUCTION...3 2. ACCESS DATA FOR THE CARD...3 2.1 Card initialisation...3 3. MAIN SCREEN...4 4. DISPLAYING INFORMATION ABOUT THE PAIR
BitLocker Drive Encryption Hardware Enhanced Data Protection. Shon Eizenhoefer, Program Manager Microsoft Corporation
 BitLocker Drive Encryption Hardware Enhanced Data Protection Shon Eizenhoefer, Program Manager Microsoft Corporation Agenda Security Background BitLocker Drive Encryption TPM Overview Building a BitLocker
BitLocker Drive Encryption Hardware Enhanced Data Protection Shon Eizenhoefer, Program Manager Microsoft Corporation Agenda Security Background BitLocker Drive Encryption TPM Overview Building a BitLocker
UNICORN 7.0. Administration and Technical Manual
 UNICORN 7.0 Administration and Technical Manual Page intentionally left blank Table of Contents Table of Contents 1 Introduction... 1.1 Administrator functions overview... 1.2 Network terms and concepts...
UNICORN 7.0 Administration and Technical Manual Page intentionally left blank Table of Contents Table of Contents 1 Introduction... 1.1 Administrator functions overview... 1.2 Network terms and concepts...
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 3 Installing Windows
 : Managing, Maintaining, and Troubleshooting, 5e Chapter 3 Installing Windows Objectives How to plan a Windows installation How to install Windows Vista How to install Windows XP How to install Windows
: Managing, Maintaining, and Troubleshooting, 5e Chapter 3 Installing Windows Objectives How to plan a Windows installation How to install Windows Vista How to install Windows XP How to install Windows
Trusted Platforms for Homeland Security
 Trusted Platforms for Homeland Security By Kevin Schutz, Product Manager Secure Products Summary Ongoing threats from hackers, viruses, and worms continue to make security a top priority for IT and business
Trusted Platforms for Homeland Security By Kevin Schutz, Product Manager Secure Products Summary Ongoing threats from hackers, viruses, and worms continue to make security a top priority for IT and business
Windows 7 Hard Disk Recovery
 In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
In order to restore your hard drive back to the original factory settings you will need to do the following: 1) Press the start button and in the search area type Recovery 2) From the search results, launch
UNICORN 6.4. Administration and Technical Manual
 UNICORN 6.4 Administration and Technical Manual Page intentionally left blank Table of Contents Table of Contents 1 Introduction... 1.1 Administrator functions overview... 1.2 Network terms and concepts...
UNICORN 6.4 Administration and Technical Manual Page intentionally left blank Table of Contents Table of Contents 1 Introduction... 1.1 Administrator functions overview... 1.2 Network terms and concepts...
safend a w a v e s y s t e m s c o m p a n y
 safend a w a v e s y s t e m s c o m p a n y SAFEND Data Protection Suite Installation Guide Version 3.4.5 Important Notice This guide is delivered subject to the following conditions and restrictions:
safend a w a v e s y s t e m s c o m p a n y SAFEND Data Protection Suite Installation Guide Version 3.4.5 Important Notice This guide is delivered subject to the following conditions and restrictions:
How To Backup In Cisco Uk Central And Cisco Cusd (Cisco) Cusm (Custodian) (Cusd) (Uk) (Usd).Com) (Ucs) (Cyse
 This chapter includes the following sections: Backup and Import in Cisco UCS Central, page 1 Backing up and Restoring Cisco UCS Central, page 4 Backing up and Restoring Cisco UCS Domains, page 8 Import
This chapter includes the following sections: Backup and Import in Cisco UCS Central, page 1 Backing up and Restoring Cisco UCS Central, page 4 Backing up and Restoring Cisco UCS Domains, page 8 Import
Secure Data Management in Trusted Computing
 1 Secure Data Management in Trusted Computing Ulrich Kühn Deutsche Telekom Laboratories, TU Berlin Klaus Kursawe (KU Leuven) Stefan Lucks (U Mannheim) Ahmad-Reza Sadeghi (RU Bochum) Christian Stüble (RU
1 Secure Data Management in Trusted Computing Ulrich Kühn Deutsche Telekom Laboratories, TU Berlin Klaus Kursawe (KU Leuven) Stefan Lucks (U Mannheim) Ahmad-Reza Sadeghi (RU Bochum) Christian Stüble (RU
Recipe for Mobile Data Security: TPM, Bitlocker, Windows Vista and Active Directory
 Recipe for Mobile Data Security: TPM, Bitlocker, Windows Vista and Active Directory Tom Olzak October 2007 If your business is like mine, laptops regularly disappear. Until recently, centrally managed
Recipe for Mobile Data Security: TPM, Bitlocker, Windows Vista and Active Directory Tom Olzak October 2007 If your business is like mine, laptops regularly disappear. Until recently, centrally managed
Whitepaper Enhancing BitLocker Deployment and Management with SimplySecure. Addressing the Concerns of the IT Professional Rob Weber February 2015
 Whitepaper Enhancing BitLocker Deployment and Management with SimplySecure Addressing the Concerns of the IT Professional Rob Weber February 2015 Page 2 Table of Contents What is BitLocker?... 3 What is
Whitepaper Enhancing BitLocker Deployment and Management with SimplySecure Addressing the Concerns of the IT Professional Rob Weber February 2015 Page 2 Table of Contents What is BitLocker?... 3 What is
HP ProtectTools User Guide
 HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
Dell ControlPoint Security Manager
 Dell ControlPoint Security Manager www.dell.com support.dell.com Notes NOTE: A NOTE indicates important information that helps you make better use of your computer. Information in this document is subject
Dell ControlPoint Security Manager www.dell.com support.dell.com Notes NOTE: A NOTE indicates important information that helps you make better use of your computer. Information in this document is subject
VERITAS Backup Exec TM 10.0 for Windows Servers
 VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
Administration guide. Host software WinCCU Installation. Complete gas volume and energy data management
 Administration guide Host software WinCCU Installation Complete gas volume and energy data management Contents 1 Introduction... 1 Safety first... 1 Warning... 1 Typographic conventions... 1 Product versioning...
Administration guide Host software WinCCU Installation Complete gas volume and energy data management Contents 1 Introduction... 1 Safety first... 1 Warning... 1 Typographic conventions... 1 Product versioning...
SEZ SEZ Online Manual Digital Signature Certficate [DSC] V Version 1.2
![SEZ SEZ Online Manual Digital Signature Certficate [DSC] V Version 1.2 SEZ SEZ Online Manual Digital Signature Certficate [DSC] V Version 1.2](/thumbs/32/15683057.jpg) SEZ SEZ Online Manual Digital Signature Certficate [DSC] V Version 1.2 Table of Contents 1 Introduction...2 2 Procurement of DSC...3 3 Installation of DSC...4 4 Procedure for entering the DSC details of
SEZ SEZ Online Manual Digital Signature Certficate [DSC] V Version 1.2 Table of Contents 1 Introduction...2 2 Procurement of DSC...3 3 Installation of DSC...4 4 Procedure for entering the DSC details of
Trusted Platform Module (TPM) Quick Reference Guide
 Trusted Platform Module (TPM) Quick Reference Guide System builders/integrators should pass this Guide on to the system owner to assist them in enabling and activating the TPM. Warning of Potential Data
Trusted Platform Module (TPM) Quick Reference Guide System builders/integrators should pass this Guide on to the system owner to assist them in enabling and activating the TPM. Warning of Potential Data
SafeGuard Enterprise Web Helpdesk
 SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
SafeGuard Enterprise Web Helpdesk Product version: 5.60 Document date: April 2011 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Help Desk
SafeGuard Enterprise Web Helpdesk. Product version: 6 Document date: February 2012
 SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6 Document date: February 2012 Contents 1 SafeGuard web-based Challenge/Response...3 2 Installation...5 3 Authentication...8 4 Select the Web Helpdesk
EMBASSY Remote Administration Server (ERAS) Administrator Manual
 EMBASSY Remote Administration Server (ERAS) Administrator Manual Part III BitLocker, Trusted Platform Module, SafeNet ProtectDrive and Dell BIOS & CV Management ERAS Version 2.8 Document Version 1.0.0.20
EMBASSY Remote Administration Server (ERAS) Administrator Manual Part III BitLocker, Trusted Platform Module, SafeNet ProtectDrive and Dell BIOS & CV Management ERAS Version 2.8 Document Version 1.0.0.20
Shakambaree Technologies Pvt. Ltd.
 Welcome to Support Express by Shakambaree Technologies Pvt. Ltd. Introduction: This document is our sincere effort to put in some regular issues faced by a Digital Signature and USB Token user doing on
Welcome to Support Express by Shakambaree Technologies Pvt. Ltd. Introduction: This document is our sincere effort to put in some regular issues faced by a Digital Signature and USB Token user doing on
BackupAssist v6 quickstart guide
 Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Guidelines on use of encryption to protect person identifiable and sensitive information
 Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
SafeGuard Enterprise Web Helpdesk. Product version: 6.1
 SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
SafeGuard Enterprise Web Helpdesk Product version: 6.1 Document date: February 2014 Contents 1 SafeGuard web-based Challenge/Response...3 2 Scope of Web Helpdesk...4 3 Installation...5 4 Allow Web Helpdesk
Upgrading to advanced editions of Acronis Backup & Recovery 10. Technical white paper
 Upgrading to advanced editions of Acronis Backup & Recovery 10 Technical white paper Table of contents 1 Introduction...3 2 Choosing the way to upgrade...3 2.1 Gradual upgrade... 3 2.2 Importing backup
Upgrading to advanced editions of Acronis Backup & Recovery 10 Technical white paper Table of contents 1 Introduction...3 2 Choosing the way to upgrade...3 2.1 Gradual upgrade... 3 2.2 Importing backup
BDR for ShadowProtect Solution Guide and Best Practices
 BDR for ShadowProtect Solution Guide and Best Practices Updated September 2015 - i - Table of Contents Process Overview... 3 1. Assess backup requirements... 4 2. Provision accounts... 4 3. Install ShadowProtect...
BDR for ShadowProtect Solution Guide and Best Practices Updated September 2015 - i - Table of Contents Process Overview... 3 1. Assess backup requirements... 4 2. Provision accounts... 4 3. Install ShadowProtect...
ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference. May 2016
 ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference May 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
ZENworks 11 Support Pack 4 Full Disk Encryption Agent Reference May 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government
Microsoft Exchange 2003 Disaster Recovery Operations Guide
 Microsoft Exchange 2003 Disaster Recovery Operations Guide Microsoft Corporation Published: December 12, 2006 Author: Exchange Server Documentation Team Abstract This guide provides installation and deployment
Microsoft Exchange 2003 Disaster Recovery Operations Guide Microsoft Corporation Published: December 12, 2006 Author: Exchange Server Documentation Team Abstract This guide provides installation and deployment
Cloning Utility for Rockwell Automation Industrial Computers
 Technical Data Cloning Utility for Rockwell Automation Industrial Computers Topic Page About the Cloning Utility 2 Recovery Partition Considerations 2 Prepare to Boot from the Accessories CD 3 Start the
Technical Data Cloning Utility for Rockwell Automation Industrial Computers Topic Page About the Cloning Utility 2 Recovery Partition Considerations 2 Prepare to Boot from the Accessories CD 3 Start the
ACER ProShield. Table of Contents
 ACER ProShield Table of Contents Revision History... 3 Legal Notices... 4 Executive Summary... 5 Introduction... 5 Protection against unauthorized access... 6 Why ACER ProShield... 7 ACER ProShield...
ACER ProShield Table of Contents Revision History... 3 Legal Notices... 4 Executive Summary... 5 Introduction... 5 Protection against unauthorized access... 6 Why ACER ProShield... 7 ACER ProShield...
MTA Course: 10753 Windows Operating System Fundamentals Topic: Understand backup and recovery methods File name: 10753_WindowsOS_SA_6.
 STUDENT ACTIVITY 6.1: UNDERSTAND BACKUP AND RECOVERY METHODS MTA Course: 10753 Windows Operating System Fundamentals Topic: Understand backup and recovery methods File name: 10753_WindowsOS_SA_6.1 Lesson
STUDENT ACTIVITY 6.1: UNDERSTAND BACKUP AND RECOVERY METHODS MTA Course: 10753 Windows Operating System Fundamentals Topic: Understand backup and recovery methods File name: 10753_WindowsOS_SA_6.1 Lesson
BackupAssist v6 quickstart guide
 New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
Trusted Platform Module (TPM) Quick Reference Guide
 Trusted Platform Module (TPM) Quick Reference Guide System builders/integrators should give this Guide to the system owners to assist them in enabling and activating the Trusted Platform Module. Warning
Trusted Platform Module (TPM) Quick Reference Guide System builders/integrators should give this Guide to the system owners to assist them in enabling and activating the Trusted Platform Module. Warning
Lesson Plans Microsoft s Managing and Maintaining a Microsoft Windows Server 2003 Environment
 Lesson Plans Microsoft s Managing and Maintaining a Microsoft Windows Server 2003 Environment (Exam 70-290) Table of Contents Table of Contents... 1 Course Overview... 2 Section 0-1: Introduction... 4
Lesson Plans Microsoft s Managing and Maintaining a Microsoft Windows Server 2003 Environment (Exam 70-290) Table of Contents Table of Contents... 1 Course Overview... 2 Section 0-1: Introduction... 4
Attestation and Authentication Protocols Using the TPM
 Attestation and Authentication Protocols Using the TPM Ariel Segall June 21, 2011 Approved for Public Release: 11-2876. Distribution Unlimited. c 2011. All Rights Reserved. (1/28) Motivation Almost all
Attestation and Authentication Protocols Using the TPM Ariel Segall June 21, 2011 Approved for Public Release: 11-2876. Distribution Unlimited. c 2011. All Rights Reserved. (1/28) Motivation Almost all
FAQ - Frequently Asked Questions Sections of Questions
 FAQ - Frequently Asked Questions Sections of Questions Bell Business Backup Service Installation & Setup Firewall Settings Connections & Backups Account Information Restoring Files Uninstalling the Bell
FAQ - Frequently Asked Questions Sections of Questions Bell Business Backup Service Installation & Setup Firewall Settings Connections & Backups Account Information Restoring Files Uninstalling the Bell
How to Encrypt your Windows 7 SDS Machine with Bitlocker
 How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
BCTextEncoder Help File
 BCTextEncoder Help File Introduction Introduction Main Features BCTextEncoder Requirements BCTextEncoder Specifications 2 Introduction BCTextEncoder is a line in BestCrypt family of encryption software
BCTextEncoder Help File Introduction Introduction Main Features BCTextEncoder Requirements BCTextEncoder Specifications 2 Introduction BCTextEncoder is a line in BestCrypt family of encryption software
Selected Windows XP Troubleshooting Guide
 1 Selected Windows XP Troubleshooting Guide To locate lost files: Compiled by: Jason M. Cohen Check these locations to locate lost files: The My Documents folder Click Start, and then click My Documents.
1 Selected Windows XP Troubleshooting Guide To locate lost files: Compiled by: Jason M. Cohen Check these locations to locate lost files: The My Documents folder Click Start, and then click My Documents.
Acronis SharePoint Explorer. User Guide
 Acronis SharePoint Explorer User Guide Table of contents 1 Introducing Acronis SharePoint Explorer... 3 1.1 Supported Microsoft SharePoint versions... 3 1.2 Supported backup locations... 3 1.3 Licensing...
Acronis SharePoint Explorer User Guide Table of contents 1 Introducing Acronis SharePoint Explorer... 3 1.1 Supported Microsoft SharePoint versions... 3 1.2 Supported backup locations... 3 1.3 Licensing...
SOLUTION GUIDE AND BEST PRACTICES
 SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
Hiva-network.com. Microsoft_70-680_v2011-06-22_Kat. Exam A
 Exam A Microsoft_70-680_v2011-06-22_Kat QUESTION 1 You have a computer that runs Windows 7. The computer has a single volume. You install 15 applications and customize the environment. You complete the
Exam A Microsoft_70-680_v2011-06-22_Kat QUESTION 1 You have a computer that runs Windows 7. The computer has a single volume. You install 15 applications and customize the environment. You complete the
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE
 VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
SECURE EMAIL USER GUIDE OUTLOOK 2000
 WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
Symantec Backup Exec 12.5 for Windows Servers. Quick Installation Guide
 Symantec Backup Exec 12.5 for Windows Servers Quick Installation Guide 13897290 Installing Backup Exec This document includes the following topics: System requirements Before you install About the Backup
Symantec Backup Exec 12.5 for Windows Servers Quick Installation Guide 13897290 Installing Backup Exec This document includes the following topics: System requirements Before you install About the Backup
Patterns for Secure Boot and Secure Storage in Computer Systems
 Patterns for Secure Boot and Secure Storage in Computer Systems Hans Löhr, Ahmad-Reza Sadeghi, Marcel Winandy Horst Görtz Institute for IT Security, Ruhr-University Bochum, Germany {hans.loehr,ahmad.sadeghi,marcel.winandy}@trust.rub.de
Patterns for Secure Boot and Secure Storage in Computer Systems Hans Löhr, Ahmad-Reza Sadeghi, Marcel Winandy Horst Görtz Institute for IT Security, Ruhr-University Bochum, Germany {hans.loehr,ahmad.sadeghi,marcel.winandy}@trust.rub.de
SafeGuard Enterprise upgrade guide. Product version: 7
 SafeGuard Enterprise upgrade guide Product version: 7 Document date: December 2014 Contents 1 About this guide...3 2 Check the system requirements...4 3 Download installers...5 4 About upgrading...6 4.1
SafeGuard Enterprise upgrade guide Product version: 7 Document date: December 2014 Contents 1 About this guide...3 2 Check the system requirements...4 3 Download installers...5 4 About upgrading...6 4.1
HIGHSEC eid App Administration User Manual
 HIGHSEC eid App Administration User Manual Contents 1 Introduction... 3 2 Application overview... 3 3 Managing HIGHSEC eid App... 3 3.1 Deleting card pairings... 4 4 Inspecting smart card contents... 5
HIGHSEC eid App Administration User Manual Contents 1 Introduction... 3 2 Application overview... 3 3 Managing HIGHSEC eid App... 3 3.1 Deleting card pairings... 4 4 Inspecting smart card contents... 5
Hyper-V Protection. User guide
 Hyper-V Protection User guide Contents 1. Hyper-V overview... 2 Documentation... 2 Licensing... 2 Hyper-V requirements... 2 2. Hyper-V protection features... 3 Windows 2012 R1/R2 Hyper-V support... 3 Custom
Hyper-V Protection User guide Contents 1. Hyper-V overview... 2 Documentation... 2 Licensing... 2 Hyper-V requirements... 2 2. Hyper-V protection features... 3 Windows 2012 R1/R2 Hyper-V support... 3 Custom
FileMaker Server 7. Administrator s Guide. For Windows and Mac OS
 FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
FileMaker Server 7 Administrator s Guide For Windows and Mac OS 1994-2004, FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker is a trademark
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
DNS must be up and running. Both the Collax server and the clients to be backed up must be able to resolve the FQDN of the Collax server correctly.
 This howto describes the setup of backup, bare metal recovery, and restore functionality. Collax Backup Howto Requirements Collax Business Server Collax Platform Server Collax Security Gateway Collax V-Cube
This howto describes the setup of backup, bare metal recovery, and restore functionality. Collax Backup Howto Requirements Collax Business Server Collax Platform Server Collax Security Gateway Collax V-Cube
Symantec Backup Exec TM 11d for Windows Servers. Quick Installation Guide
 Symantec Backup Exec TM 11d for Windows Servers Quick Installation Guide September 2006 Symantec Legal Notice Copyright 2006 Symantec Corporation. All rights reserved. Symantec, Backup Exec, and the Symantec
Symantec Backup Exec TM 11d for Windows Servers Quick Installation Guide September 2006 Symantec Legal Notice Copyright 2006 Symantec Corporation. All rights reserved. Symantec, Backup Exec, and the Symantec
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Property Based TPM Virtualization
 Property Based Virtualization Marcel Winandy Joint work with: Ahmad Reza Sadeghi, Christian Stüble Horst Görtz Institute for IT Security Chair for System Security Ruhr University Bochum, Germany Sirrix
Property Based Virtualization Marcel Winandy Joint work with: Ahmad Reza Sadeghi, Christian Stüble Horst Görtz Institute for IT Security Chair for System Security Ruhr University Bochum, Germany Sirrix
System Protection for Hyper-V Whitepaper
 Whitepaper Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 Hyper-V requirements... 2 Definitions... 3 Considerations... 3 2. About the BackupAssist Hyper-V solution... 4 Advantages... 4
Whitepaper Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 Hyper-V requirements... 2 Definitions... 3 Considerations... 3 2. About the BackupAssist Hyper-V solution... 4 Advantages... 4
NovaBACKUP. Storage Server. NovaStor / May 2011
 NovaBACKUP Storage Server NovaStor / May 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
NovaBACKUP Storage Server NovaStor / May 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice.
SafeGuard Enterprise Administrator help. Product version: 6.1
 SafeGuard Enterprise Administrator help Product version: 6.1 Document date: January 2014 Contents 1 About SafeGuard Enterprise 6.1...4 2 Security best practices...6 3 About SafeGuard Management Center...9
SafeGuard Enterprise Administrator help Product version: 6.1 Document date: January 2014 Contents 1 About SafeGuard Enterprise 6.1...4 2 Security best practices...6 3 About SafeGuard Management Center...9
Data At Rest Protection
 Data At Rest Protection Dell Data Protection Encryption Full Volume Encryption Whitepaper October 2011 THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL
Data At Rest Protection Dell Data Protection Encryption Full Volume Encryption Whitepaper October 2011 THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL
User guide. Business Email
 User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
User guide Business Email June 2013 Contents Introduction 3 Logging on to the UC Management Centre User Interface 3 Exchange User Summary 4 Downloading Outlook 5 Outlook Configuration 6 Configuring Outlook
Pervasive PSQL Product Authorization
 Pervasive PSQL Product Authorization A Pervasive Software Whitepaper 7/21/2011 Table of Contents Pervasive PSQL Product Authorization... 3 Introduction... 3 Product Authorization Basics... 3 Key Generation
Pervasive PSQL Product Authorization A Pervasive Software Whitepaper 7/21/2011 Table of Contents Pervasive PSQL Product Authorization... 3 Introduction... 3 Product Authorization Basics... 3 Key Generation
TrustKey Tool User Manual
 TrustKey Tool User Manual 1 Table of Contents 1 Introduction... 5 2 TrustKey Product...6 2.1 TrustKey Tool... 6 2.2 TrustKey function modules...7 2.3 TrustKey using environment...7 3 TrustKey Tool Installation...
TrustKey Tool User Manual 1 Table of Contents 1 Introduction... 5 2 TrustKey Product...6 2.1 TrustKey Tool... 6 2.2 TrustKey function modules...7 2.3 TrustKey using environment...7 3 TrustKey Tool Installation...
ScoMIS Encryption Service
 Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Disk Encryption. Aaron Howard IT Security Office
 Disk Encryption Aaron Howard IT Security Office Types of Disk Encryption? Folder Encryption Volume or Full Disk Encryption OS / Boot Volume Data Volume Managed or Unmanaged Key Backup and Data Assurance
Disk Encryption Aaron Howard IT Security Office Types of Disk Encryption? Folder Encryption Volume or Full Disk Encryption OS / Boot Volume Data Volume Managed or Unmanaged Key Backup and Data Assurance
Acronis Backup & Recovery 10 Server for Windows. Installation Guide
 Acronis Backup & Recovery 10 Server for Windows Installation Guide Table of Contents 1. Installation of Acronis Backup & Recovery 10... 3 1.1. Acronis Backup & Recovery 10 components... 3 1.1.1. Agent
Acronis Backup & Recovery 10 Server for Windows Installation Guide Table of Contents 1. Installation of Acronis Backup & Recovery 10... 3 1.1. Acronis Backup & Recovery 10 components... 3 1.1.1. Agent
Installing and Configuring vcenter Multi-Hypervisor Manager
 Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1 This document supports the version of each product listed and supports all subsequent
How to Backup and Restore a VM using Veeam
 How to Backup and Restore a VM using Veeam Table of Contents Introduction... 3 Assumptions... 3 Add ESXi Server... 4 Backup a VM... 6 Restore Full VM... 12 Appendix A: Install Veeam Backup & Replication
How to Backup and Restore a VM using Veeam Table of Contents Introduction... 3 Assumptions... 3 Add ESXi Server... 4 Backup a VM... 6 Restore Full VM... 12 Appendix A: Install Veeam Backup & Replication
NovaBACKUP xsp Version 15.0 Upgrade Guide
 NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
Full Disk Encryption Agent Reference
 www.novell.com/documentation Full Disk Encryption Agent Reference ZENworks 11 Support Pack 3 May 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or
www.novell.com/documentation Full Disk Encryption Agent Reference ZENworks 11 Support Pack 3 May 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or
Using the TPM: Data Protection and Storage
 Using the TPM: Data Protection and Storage Ariel Segall [email protected] Day 2 Approved for Public Release: 12-2749. Distribution unlimited License All materials are licensed under a Creative Commons
Using the TPM: Data Protection and Storage Ariel Segall [email protected] Day 2 Approved for Public Release: 12-2749. Distribution unlimited License All materials are licensed under a Creative Commons
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Attix5 Pro Disaster Recovery
 Attix5 Pro Disaster Recovery Recommended steps An overview of the recommended steps for a disaster recovery. Copyright notice and proprietary information This document is published by Attix5 or its local
Attix5 Pro Disaster Recovery Recommended steps An overview of the recommended steps for a disaster recovery. Copyright notice and proprietary information This document is published by Attix5 or its local
NetVanta Unified Communications Server Backup and Restore Procedures
 NetVanta Unified Communications Technical Note NetVanta Unified Communications Server Backup and Restore Procedures 1 Introduction 1.1 Overview This document provides backup and restore procedures to protect
NetVanta Unified Communications Technical Note NetVanta Unified Communications Server Backup and Restore Procedures 1 Introduction 1.1 Overview This document provides backup and restore procedures to protect
Acronis Backup & Recovery 10 Server for Windows. Installation Guide
 Acronis Backup & Recovery 10 Server for Windows Installation Guide Table of Contents 1. Installation of Acronis Backup & Recovery 10... 3 1.1. Acronis Backup & Recovery 10 components... 3 1.1.1. Agent
Acronis Backup & Recovery 10 Server for Windows Installation Guide Table of Contents 1. Installation of Acronis Backup & Recovery 10... 3 1.1. Acronis Backup & Recovery 10 components... 3 1.1.1. Agent
IBM Client Security Solutions. Client Security User's Guide
 IBM Client Security Solutions Client Security User's Guide December 1999 1 Before using this information and the product it supports, be sure to read Appendix B - Notices and Trademarks, on page 22. First
IBM Client Security Solutions Client Security User's Guide December 1999 1 Before using this information and the product it supports, be sure to read Appendix B - Notices and Trademarks, on page 22. First
Infineon TPM Professional Package
 Chipcard & Security Release Notes (V4.3.000.3137 RTM) Infineon TPM Professional Package Version: 1.20 Date: 2012-08-28 Release Notes Page 1 of 16 Dev. / Step Code: Sales Code: Status: Date: 2012-08-28
Chipcard & Security Release Notes (V4.3.000.3137 RTM) Infineon TPM Professional Package Version: 1.20 Date: 2012-08-28 Release Notes Page 1 of 16 Dev. / Step Code: Sales Code: Status: Date: 2012-08-28
Acronis Backup & Recovery 10 Server for Windows. Installation Guide
 Acronis Backup & Recovery 10 Server for Windows Installation Guide Table of contents 1 Before installation...3 1.1 Acronis Backup & Recovery 10 components... 3 1.1.1 Agent for Windows... 3 1.1.2 Management
Acronis Backup & Recovery 10 Server for Windows Installation Guide Table of contents 1 Before installation...3 1.1 Acronis Backup & Recovery 10 components... 3 1.1.1 Agent for Windows... 3 1.1.2 Management
How To Backup Your Computer With A Remote Drive Client On A Pc Or Macbook Or Macintosh (For Macintosh) On A Macbook (For Pc Or Ipa) On An Uniden (For Ipa Or Mac Macbook) On
 Remote Drive PC Client software User Guide -Page 1 of 27- PRIVACY, SECURITY AND PROPRIETARY RIGHTS NOTICE: The Remote Drive PC Client software is third party software that you can use to upload your files
Remote Drive PC Client software User Guide -Page 1 of 27- PRIVACY, SECURITY AND PROPRIETARY RIGHTS NOTICE: The Remote Drive PC Client software is third party software that you can use to upload your files
VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide
 VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide N109548 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes
VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide N109548 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes
Backup and Disaster Recovery Restoration Guide
 Backup and Disaster Recovery Restoration Guide Page 1 Table of Contents Table of Contents...2 Terms of Use...3 BDR...4 Creating Point-in-Time Restoration Volumes...4 Mounting a Restoration Volume...4 Dismounting
Backup and Disaster Recovery Restoration Guide Page 1 Table of Contents Table of Contents...2 Terms of Use...3 BDR...4 Creating Point-in-Time Restoration Volumes...4 Mounting a Restoration Volume...4 Dismounting
Pervasive PSQL Product Activation
 Pervasive PSQL Product Activation Introduction Licensing for Pervasive PSQL is enforced by the use of keys. Keys are associated with individual computers and can be activated and deactivated. Product activation
Pervasive PSQL Product Activation Introduction Licensing for Pervasive PSQL is enforced by the use of keys. Keys are associated with individual computers and can be activated and deactivated. Product activation
HP ProtectTools Security Manager Guide
 HP ProtectTools Security Manager Guide HP Compaq Business Desktops Copyright 2006 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. Microsoft
HP ProtectTools Security Manager Guide HP Compaq Business Desktops Copyright 2006 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. Microsoft
Click to begin. Maitre'D Full System Backup & Restore
 Click to begin Maitre'D Full System Backup & Restore Full System Backup & Restore This document will guide you through the Backup of the Maitre D Database from a Source computer and the Restoration on
Click to begin Maitre'D Full System Backup & Restore Full System Backup & Restore This document will guide you through the Backup of the Maitre D Database from a Source computer and the Restoration on
Installing Windows XP Professional
 CHAPTER 3 Installing Windows XP Professional After completing this chapter, you will be able to: Plan for an installation of Windows XP Professional. Use a CD to perform an attended installation of Windows
CHAPTER 3 Installing Windows XP Professional After completing this chapter, you will be able to: Plan for an installation of Windows XP Professional. Use a CD to perform an attended installation of Windows
User Guide. Laplink Software, Inc. Laplink DiskImage 7 Professional. User Guide. UG-DiskImagePro-EN-7 (REV. 5/2013)
 1 Laplink DiskImage 7 Professional Laplink Software, Inc. Customer Service/Technical Support: Web: http://www.laplink.com/contact E-mail: [email protected] Laplink Software, Inc. 600 108th Ave.
1 Laplink DiskImage 7 Professional Laplink Software, Inc. Customer Service/Technical Support: Web: http://www.laplink.com/contact E-mail: [email protected] Laplink Software, Inc. 600 108th Ave.
Administration GUIDE. Exchange Database idataagent. Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 233
 Administration GUIDE Exchange Database idataagent Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 233 User Guide - Exchange Database idataagent Table of Contents Overview Introduction Key Features
Administration GUIDE Exchange Database idataagent Published On: 11/19/2013 V10 Service Pack 4A Page 1 of 233 User Guide - Exchange Database idataagent Table of Contents Overview Introduction Key Features
Unicenter NSM Integration for BMC Remedy. User Guide
 Unicenter NSM Integration for BMC Remedy User Guide This documentation and any related computer software help programs (hereinafter referred to as the Documentation ) is for the end user s informational
Unicenter NSM Integration for BMC Remedy User Guide This documentation and any related computer software help programs (hereinafter referred to as the Documentation ) is for the end user s informational
RecoveryVault Express Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Understanding Backup and Recovery Methods
 Lesson 8 Understanding Backup and Recovery Methods Learning Objectives Students will learn to: Understand Local, Online, and Automated Backup Methods Understand Backup Options Understand System Restore
Lesson 8 Understanding Backup and Recovery Methods Learning Objectives Students will learn to: Understand Local, Online, and Automated Backup Methods Understand Backup Options Understand System Restore
