SAFETY-CRITICAL VERSUS SECURITY-CRITICAL SOFTWARE
|
|
|
- Jasper Tyler
- 10 years ago
- Views:
Transcription
1 SAFETY-CRITICAL VERSUS SECURITY-CRITICAL SOFTWARE Findings in this area from research work with leading Professionals and Academics and in conjunction with BCS, Resource Engineering Projects and SCSC Dr Adele-Louise Carter TD, MBA, BSc (Hons), FBCS, CITP, CENG, MCMI, CMgr Fellow of the BCS, REP Software Sales Manager and member of the SCSC Dr Adele-Louise Carter, Version 1.0 August 2010
2 1. Introduction In the past, safety and security-critical software systems may have been considered completely separate due to the differences between 'safety-critical' and 'security-critical', with the latter having the added implication of loss of human life. The functions of both types of digital systems have become increasingly software intensive and this has contributed to a blurring of the difference between safety and security-critical. For example, the fault on an aircraft s flight control function could lead to a catastrophic failure condition, which results in the loss of human life and hence the need for a safety-critical system. On the other hand, a fault with a cryptographic function could lead to a breach of security or financial loss and hence a security-critical system is required. However, in current times, such a breach in security could typically result in a successful terrorist attack, which could lead to loss of human life, and this leads to the need for a security-critical system to be a safety-critical system. It can be argued that both types of system require strong partitioning in order to prevent unintended interactions. Safetycritical systems define five levels of failure conditions to which software might contribute: catastrophic, hazardous, major, minor, and no effect. Software functions of varying levels of criticality are often hosted together (on the same module for example) and therefore interference must be considered and prevented. For security-critical systems the Multiple Independent Level of Security (MILS) specification has been developed. The core of MILS is the separation kernel (SK), which allows multiple software functions from different development and verification sources to share common resources such as CPU, but have no unwanted interference. This security-critical partitioning using formal methods needs enforcing and proving (i.e.: can the SK really do it) and this potentially drives architectural differences. These different standards and specifications do not necessarily cover the same areas however and this leads to more confusion as the safety-critical standards ensure that the code is well constructed whereas the MILS specifications are not designed for this. Also is it therefore necessary, and indeed, is it possible to interchange these two types of systems and is that sometimes, never or partially? Are the technical differences between the two types of systems too great to support this? Clarity and new understanding is required in this area particularly in the light of the reasons for the Nimrod disaster recently released. Dr Adele-Louise Carter, Fellow of the BCS, The Chartered Institute for IT and Member of its prestigious Security Forum and Software Manager at REP, brought the need to debate this hot topic to the three organisations. All parties readily accepted the challenge and Adele worked with the organisations to bring all the relevant experts together to consider this area in detail and look at ways of taking it forward. The work has culminated in this report, authored by Adele. This paper will detail the results, discussions and conclusions that emerged from the resultant Technical Day, Safety- Critical versus Security-Critical Software, on 6th May 2010 at the BCS premises in Covent Garden. Areas covered included policies, processes, staffing, risks and technical aspects, and business and commercial considerations. 2. Research method Qualitative Research was undertaken using the Action Research methodology utilising focus groups and information exchange sessions. The idea behind Action Research is that the actual activity of undertaking this research contributes to taking forward of the ideas raised within the research. The outcome of the research is changed or influenced literally by its undertaking. Significant discussion on this topic has been taking place for a number of years and Adele felt that it was time to draw all the previous work undertaken in this area together, collate this knowledge, analyse it and draw conclusions and support these conclusions with an action plan. To this end, Adele pulled on all her work contacts to establish a Technical Day which drew together as many of the most notable leading professional and academic businesses in these two domains to do just this. The day consisted of six key speeches on aspects of safety and security-critical software, a series of round table focus groups to explore specific subjects in more depth and a Q&A (Question and Answer) session to further raise issues and define the next stages. Each focus group was chaired and facilitated by REP volunteer staff. All the attendees, speakers and focus group contributors at the technical day were carefully selected in order to ensure all angles were represented and therefore significant progress able to be made. Their attendance in such financially tight times shows the commitment of the community to this problem area. Those recommended from initial invitees provided reasoning for their inclusion which actually further contributed to ensuring all areas were covered. Unfortunately, on the actual day, five representatives from the Security-critical arena were absent. Potentially, this limits the number of attendees from a purely security background. The businesses represented can be divided as follows:
3 Large companies in the areas of Engineering, IT and Science including: BAE Systems, QinetiQ, Rolls- Royce, Invensys Rail, Logica, NATS, Atkins, Fujitsu and Ultra Electronics; Small and Medium Enterprises (SMEs) such as: Resource Engineering Projects (REP), Trango, BBS IT Associates Ltd, Amethyst Risk Management Ltd and a number of Independents; Leading academics from the Universities of York, Newcastle, City, Gloucester, Middlesex and Surrey; Government and associated organisations including: CPNI (Centre for the Protection of National Infrastructure), CESG (the National Technical Authority for Information Assurance), TSB (Technology Strategy Board), SITC (Security Innovation and Technology Consortium) and the Electronics KTN (Knowledge Transfer Network); Professional bodies: BCS, The Chartered Institute for IT, Safety Critical Systems Club (SCSC), the Royal Academy of Engineering and the IET (Institute of Engineering and Technology). This representation meant that software experts from all the relevant industries were in attendance, although in different quantities such as: transport; rail, aerospace and automotive, NATS (National Air Traffic Control); MoD, Defence and Homeland Security, the energy and medical sectors. 3. Data presented The following topics were covered at the Technical Day. 1. The methods and practicalities of combining safety and security assurance this highlighted the paid work to date in this area. 2. What makes safety critical software different? 3. Risk management and assurance from the security world. 4. Security and Safety or Malicious and Accidental. 5. Considerations when using COTS software within safety-critical systems. 6. Security and safety in networked information systems: issues and challenges. The cost of safety re-certification relates to the size and complexity of the system and not the actual change, which would be preferable. To such an end modular construction and certification would therefore be more desirable. However, sometimes there is an issue when there are conflicts between safety and security. This could be reduced as there is common ground in terms of risk and threats and assurance methods can usually be identified. Both areas could do with common terminology, although this may raise more cultural issues rather than practicalities of terminology. The difference with security is that it may have to deal with intelligent malicious agents, not just flawed operators. Currently safety can thus use more statistical methods than security. In the safety area a complete specification of analysis can be undertaken such as in the case of an accident. Within security this is much tougher and the facets can often change, such as 'motivation'. When it comes to impact, it is much tougher to quantify this for security. In security for example, risk can often be classified, unlike as yet in the safety arena. The traditional view is that malicious issues are not considered in safety. Safety has got away with assumptions of no maliciousness and no common mode failure for years but can no longer do this. As yet there is no conclusive proof of software causing a fatality in aviation and it could be that there are lots of standards for the software. In fact the latest standard DO178-C is about to be published and will cover complex and potentially non-deterministic object oriented techniques. It will also replace text evidence with formal analysis evidence and use modelling tools in development and verification. The latter though is seen by some as being rather contentious. Risk management seems to be at the crux of the debate. CESG found that much of the equipment that is tested was not robust to electronic attack. Many of the incidents CESG respond to are due to software bugs, reduction in the number of these bugs through good development and testing strategies is an important factor in reducing the risks to information. It is possible to consider security and safety as simply different attributes of dependability. Also within safety software, COTS products need to deal with unexpected inputs and be compatible with the systems they support. This can easily be applied to security. Finally security can be considered to be about protecting valuable information assets, in general or via computer networks and it can be considered to be about how exploitable a vulnerability might be (and how determined the attacked is); whereas safety is about protecting physical assets (life, property, environ) and this is more complex now and its likelihood of occurrence is often guessed.
4 4. Results There was a staggering amount of agreement within the Technical Day community over the issues surrounding safety versus security-critical software. The overwhelming view was that this is a simple issue to resolve in theory, but in practice it is extremely complex with a large cultural hearts and minds exercise needed to be undertaken in order to establish any improvement in the security-critical software. The attendees consisted of a significant collection of professional and academic experts within this area and to add to this, those leading Governmental bodies and Institutions that might need to be part of any changes required. The overriding point that was raised was that 90% of security-critical software contains bad coding bugs which detracts from making them secure and this was unanimously viewed as of paramount interest by the attendees. It was agreed that that one of the key ideas that emerged from this was the lack of standards in security-critical software, unlike in safety-critical software and that the BSI should be approached to take this forward. Below are the results from each of the round table focus groups. 4.1 Real life problems of safety and security-critical software Standards and guidelines in safety-critical software are assumed to be sufficient, for example DO 178B in use on the Boeing 777 still allowed room for error. Further to the above, standards such as DO 178B are software specific and do not necessarily look at the system or environment as a whole. Levels of assurance are inconsistent across different industries and indeed different parts of the world and the quality of the software can differ. There are too many standards. For example safety has a standard for each industry: aerospace, defence, automotive, rail, nuclear etc. Integrating systems such as SCADA, which is dated, with the outside world can be problematic due to the rate of development. Also certain systems are not developed to be integrated or seen by the outside world. There is a pressure to create saleable products from software that is perhaps not of the desired quality. The long term cost is thought to be high when doing things properly. Similarly development (e.g. producing prototypes) is expensive and not always possible due to the short lead time. Supply chain is passing risk/liability further down, this affects the cost and forces the behaviour of subcontractors by covering all bases when this is not always necessary. Is this enhancing the overall quality or just making it more expensive for the fear of legal action later on? One possible solution would be for the regulatory bodies to liaise across software industry, not just safety or security. Alternatively there could be a body for each that work together. 4.2 Technical similarities and differences between safety and security The safety community suffers from having too many standards and it would be virtually impossible to create one common standard. The security community doesn t tend to share information and this can hinder the learning process. The security industry could improve vastly but implement some of the processes that have been used in the safety industry for several years. The security industry also needs to spend a little more time employing good software practices (mainly in terms of verification and validation). The security industry reacts to change very quickly. The safety industry needs to develop techniques to help improve the time it takes to make changes to its certified system. Safety industry has always worked on the assumption that failures and errors are not malicious. This may not be a valid assumption in the current times. This should be taking into account as part of the risk assessment. The security industry would benefit from a formalisation of software security levels. A long term goal would be the safety and security industry sharing a common set of levels. The security industry is always going to suffer from not having a configured working environment. Safety generally has a stable known working environment which makes development a lot easier. Regardless of standards (both security and safety) the certification authorities need to help developers. Concerns were raised with the certification authorities statement that the compliance to standards may depend on an individual. 4.3 Combining processes and working practices
5 Security-critical development has no real process or standards to aid a consistent approach to software development. This was evident by the largest problem with security-critical software, was not the failings of either architecture or systems requirements, but by the number of errors found in the software. Conversely it was believed that the process of developing the software in the safety-critical arena was robust, reducing the likelihood of error propagation in the development but perhaps where it lacked control was at the systems requirement level, specifically in addressing the potential of malicious error injection. It was generally agreed that systems should not be treated as safety or security system but as a safe secure system. Bringing the prescribed software development process from the safety standards into the security arena. Additionally bringing security risk hazard analysis principles into the safety arena. Ideally this would lead to a general set of processes which could be applied to either, the question is would the certification assessors and the industries be able to agree on this? 4.4 Skills swapping It was unanimously agreed, not just in the discussion but from the speakers, that all systems should be developed as safe secure systems. As a result those skills that are currently unique in each arena should be pushed as high up the software life-cycle as possible to allow for a complementary software skill set in software development (tools and language dependent). This would require a common development process rather than a skill change. This would lead to the conclusion that risk and hazard analysis, for both a security and safety assessment, should be conducted and therefore requires skills from both arenas, to define a set of safety and security software requirements to flow down through a standard development process. Independence of this skill set at this high level may be required though to ensure there is no bias towards contradicting risks. 4.5 Safety and Security-Critical Software from a risk perspective What are the risks / barriers to implementing safety and security systems as one discipline? There are many standards in the safety industry, such as, DO-178, 61508, to name just a few. These standards have a lot of common requirements, but also differences, not least in the definitions and labelling of the SIL levels (SIL A is the highest for Aerospace, SIL 4 is the highest for and ASIL D is the highest for 26262). With this in mind, trying to standardise the security needs into these standards or into a generic standard would be extremely difficult. There are ongoing internet discussions about how the different Safety Integrity Levels of all these standards map onto each other and whether they are equivalent or not. For example there are suggestions that ASIL D in is equivalent to SIL 3 in and that there is no equivalent to SIL 4. Therefore, where currently industries can claim that they have developed their software to the highest integrity (for that industry) they might not be able to if there was a common standard. This could open the door for litigation based around the premise that the software could have been developed to a higher safety level. It was felt that for this reason there would be pressure against any combining of standards and industries requirements. Discussions amongst the group concluded that while the techniques and methodologies used were similar, and could be considered as transferable, the terminology between the different disciplines was different and therefore placed conceptual barriers to this transferral. For instance, if the safety / hazard analysis from the safety domain and the security analysis from the security domain were both considered as risk analysis then the use of techniques could be more easily standardised and the two disciplines seen as one. Questions of certification and accreditation were seen as a barrier. Would the applicant need to have their system qualified in both domains along with its associated costs. But more fundamentally, would the applicant need to develop the software with two sets of plans, development paths and results, just to comply with the requirements of each discipline. 4.6 What is needed to change standards? The topic was broken down into four questions: 1. Who should do it? 2. What does it need to say? 3. How do we get it adopted? 4. Do we need to revise existing standards or propose a new one?
6 It was agreed that a cross-industry approach was best, to avoid the situation that now exists in the safety critical world, where each industry (aeronautical, railway, automotive etc:) has its own standard. Whether a combined safety and security standard would be feasible was considered. It was felt that in the area of risk management, at least, it was possible. Given the results, the approach recommended was for an overarching document that would refer to the best parts of the various existing standards. An initial white paper was proposed, offering guidance and inviting feedback. This would lead to an initially UK standard (BSI) and then ultimately, a European one. It was felt that changing existing standards was unrealistic. In particular, recent experience in revising safety standards in the railway industry indicated that such a process would be much too slow. 4.7 Next steps Adele to compile report for IET to stimulate further discussion. Identify key stakeholders from relevant organisations and approach with relevant concepts (e.g. Government, CESG, Cyber security). Use TSB Secure Software Development Partnership as a vehicle to provide further discussions or form own working party with key industry figures, covering both safety and security domains (e.g. BAE Systems, REP, Qinetiq, Logica). Could REP consider security further as part of their normal working practices and build this into their quality assurance processes? Use working party to assess current difficulties within the security industry, for example the need to know culture that has been developed (CESG could be used for this) and also for assisting with developments within academia (e.g. City University). The Q&A session covered standards, architecture, requirements and users of the software. It was concluded that there was a need for a common integrated approach and common goal between safety and security-critical software. 5. Conclusions The overall conclusions from the event were: 1. A core community consisting of all the relevant parties is required in order to keep everything together. The attendees at the Technical Day were considered to represent these and perhaps join forces with the TSB's Secure Software Development Forum. 2. Both domains have common issues. Both have to deal with the implications of risk and the need to minimise those risks. One has a security risk assessment and the other a safety case. 3. The lack of common terminology between the two areas produces an artificial barrier when you consider that the safety and security-critical domains are as one. 4. The techniques for determining safety requirements and security requirements are fundamentally the same. 5. Security software tends to have a rapid development life cycle to mitigate threats quickly, which tends to result in a level of software errors. 6. Safety software has a longer development life cycle and hence is less prone to software errors? 7. Both domains are suspect to system errors i.e.: failure to define correctly what you required the system/software to do. 8. Education in addition to regulation and standards was required in security-critical software and this should potentially stem from Universities. The Secure Software Development Partnership of the TSB wrote a white paper on this, Software Security Failures Who should correct them and how?, Issue V 1.0 June 2008, Bill Whyte and John Harrison. 6. Recommendations The Technical Day attendees highlighted the following main recommendations: 1. The security domain would benefit from using software development techniques from the safety domain but cost and time-scale implications may be a barrier. There is regulation in the safety critical domain but it is not apparent for software developed for the security domain and therefore this area should be investigated. 2. The safety domain would benefit from considering malicious attack on its systems and defining requirements and techniques that mitigate these vulnerabilities.
7 3. Safety and security-critical systems should be considered as one, safe secure systems and a common terminology would go a long way to supporting this. 7. Action Plan The following action plan has been formed to ensure that these ideas are taken forward and do not just end up written into another report that is forwarded around and ignored. 1. Identify further key stakeholders (if necessary) from other relevant organisations that have influence and power and approach as appropriate. 2. Further Meetings with CESG, CPNI, Office of Cyber Security, OGC Buying Solutions at Norwich, H&S Executive and the Nuclear Executive to discuss measures to take matters forward. 3. Potential TSB Submissions to their current competition on trusted systems. 4. Web report to be provided for awareness on CPNI/CESG websites. 5. Paper to be produced for IET Conference. 6. Support TSB's Secure Software Development Partnership as a vehicle to provide further discussions covering standards, tools and techniques, education and training, embedded real time and formal methods. 7. Contact BSI about security software standards as we have the group for creating these standards via the CPNI. 8. Ensure that the community from the technical day is maintained and possibly use it to assess current difficulties within the security industry, for example the 'need to know' culture that has been developed and also for assisting with developments in academia. Finally, as all work to date to create this report has been undertaken on a voluntary level, in order to take anything further, it is now necessary to consider funding opportunities. In addition, a suitable 'Character' is required to take these actions forward. To date some work on these actions had already been stimulated by Dr Adele-Louise Carter, particularly with TSB and CPNI.
Moving from BS 25999-2 to ISO 22301. The new international standard for business continuity management systems. Transition Guide
 Transition Guide Moving from BS 25999-2 to ISO 22301 The new international standard for business continuity management systems Extract from The Route Map to Business Continuity Management: Meeting the
Transition Guide Moving from BS 25999-2 to ISO 22301 The new international standard for business continuity management systems Extract from The Route Map to Business Continuity Management: Meeting the
A Guide to the Cyber Essentials Scheme
 A Guide to the Cyber Essentials Scheme Published by: CREST Tel: 0845 686-5542 Email: [email protected] Web: http://www.crest-approved.org/ Principal Author Jane Frankland, Managing Director, Jane
A Guide to the Cyber Essentials Scheme Published by: CREST Tel: 0845 686-5542 Email: [email protected] Web: http://www.crest-approved.org/ Principal Author Jane Frankland, Managing Director, Jane
Introduction to Software Engineering
 CS1Ah Lecture Note 7 Introduction to Software Engineering In this note we provide an overview of Software Engineering. The presentation in this lecture is intended to map out much of what we will study
CS1Ah Lecture Note 7 Introduction to Software Engineering In this note we provide an overview of Software Engineering. The presentation in this lecture is intended to map out much of what we will study
A GOOD PRACTICE GUIDE FOR EMPLOYERS
 MITIGATING SECURITY RISK IN THE NATIONAL INFRASTRUCTURE SUPPLY CHAIN A GOOD PRACTICE GUIDE FOR EMPLOYERS April 2015 Disclaimer: Reference to any specific commercial product, process or service by trade
MITIGATING SECURITY RISK IN THE NATIONAL INFRASTRUCTURE SUPPLY CHAIN A GOOD PRACTICE GUIDE FOR EMPLOYERS April 2015 Disclaimer: Reference to any specific commercial product, process or service by trade
Analyzing the Security Significance of System Requirements
 Analyzing the Security Significance of System Requirements Donald G. Firesmith Software Engineering Institute [email protected] Abstract Safety and security are highly related concepts [1] [2] [3]. Both
Analyzing the Security Significance of System Requirements Donald G. Firesmith Software Engineering Institute [email protected] Abstract Safety and security are highly related concepts [1] [2] [3]. Both
Sytorus Information Security Assessment Overview
 Sytorus Information Assessment Overview Contents Contents 2 Section 1: Our Understanding of the challenge 3 1 The Challenge 4 Section 2: IT-CMF 5 2 The IT-CMF 6 Section 3: Information Management (ISM)
Sytorus Information Assessment Overview Contents Contents 2 Section 1: Our Understanding of the challenge 3 1 The Challenge 4 Section 2: IT-CMF 5 2 The IT-CMF 6 Section 3: Information Management (ISM)
National Occupational Standards. Compliance
 National Occupational Standards Compliance NOTES ABOUT NATIONAL OCCUPATIONAL STANDARDS What are National Occupational Standards, and why should you use them? National Occupational Standards (NOS) are statements
National Occupational Standards Compliance NOTES ABOUT NATIONAL OCCUPATIONAL STANDARDS What are National Occupational Standards, and why should you use them? National Occupational Standards (NOS) are statements
INFORMATION SECURITY TESTING
 INFORMATION SECURITY TESTING SERVICE DESCRIPTION Penetration testing identifies potential weaknesses in a technical infrastructure and provides a level of assurance in the security of that infrastructure.
INFORMATION SECURITY TESTING SERVICE DESCRIPTION Penetration testing identifies potential weaknesses in a technical infrastructure and provides a level of assurance in the security of that infrastructure.
Reduce Medical Device Compliance Costs with Best Practices. [email protected]
 Reduce Medical Device Compliance Costs with Best Practices [email protected] 1 Agenda Medical Software Certification How new is Critical Software Certification? What do we need to do? What Best Practises
Reduce Medical Device Compliance Costs with Best Practices [email protected] 1 Agenda Medical Software Certification How new is Critical Software Certification? What do we need to do? What Best Practises
Chartered Manager Degree Apprenticeship Assessment Plan
 Chartered Manager Degree Apprenticeship Assessment Plan Crown copyright 2015 You may re-use this information (not including logos) free of charge in any format or medium, under the terms of the Open Government
Chartered Manager Degree Apprenticeship Assessment Plan Crown copyright 2015 You may re-use this information (not including logos) free of charge in any format or medium, under the terms of the Open Government
Preparation of a Rail Safety Management System Guideline
 Preparation of a Rail Safety Management System Guideline Page 1 of 99 Version History Version No. Approved by Date approved Review date 1 By 20 January 2014 Guideline for Preparation of a Safety Management
Preparation of a Rail Safety Management System Guideline Page 1 of 99 Version History Version No. Approved by Date approved Review date 1 By 20 January 2014 Guideline for Preparation of a Safety Management
AUSTRALIAN GOVERNMENT INFORMATION MANAGEMENT OFFICE CYBER SECURITY CAPABILITY FRAMEWORK & MAPPING OF ISM ROLES
 AUSTRALIAN GOVERNMENT INFORMATION MANAGEMENT OFFICE CYBER SECURITY CAPABILITY FRAMEWORK & MAPPING OF ISM ROLES Final Report Prepared by Dr Janet Tweedie & Dr Julie West June 2010 Produced for AGIMO by
AUSTRALIAN GOVERNMENT INFORMATION MANAGEMENT OFFICE CYBER SECURITY CAPABILITY FRAMEWORK & MAPPING OF ISM ROLES Final Report Prepared by Dr Janet Tweedie & Dr Julie West June 2010 Produced for AGIMO by
CYBER SECURITY Audit, Test & Compliance
 www.thalescyberassurance.com CYBER SECURITY Audit, Test & Compliance 02 The Threat 03 About Thales 03 Our Approach 04 Cyber Consulting 05 Vulnerability Assessment 06 Penetration Testing 07 Holistic Audit
www.thalescyberassurance.com CYBER SECURITY Audit, Test & Compliance 02 The Threat 03 About Thales 03 Our Approach 04 Cyber Consulting 05 Vulnerability Assessment 06 Penetration Testing 07 Holistic Audit
GUIDELINE NO. 22 REGULATORY AUDITS OF ENERGY BUSINESSES
 Level 37, 2 Lonsdale Street Melbourne 3000, Australia Telephone.+61 3 9302 1300 +61 1300 664 969 Facsimile +61 3 9302 1303 GUIDELINE NO. 22 REGULATORY AUDITS OF ENERGY BUSINESSES ENERGY INDUSTRIES JANUARY
Level 37, 2 Lonsdale Street Melbourne 3000, Australia Telephone.+61 3 9302 1300 +61 1300 664 969 Facsimile +61 3 9302 1303 GUIDELINE NO. 22 REGULATORY AUDITS OF ENERGY BUSINESSES ENERGY INDUSTRIES JANUARY
Technology management in warship acquisition
 management in warship acquisition A J Shanks B.Eng(Hons) MIET BMT Defence Services Limited SYNOPSIS Today s warship designers and engineers look to technology to provide warships and systems better, cheaper
management in warship acquisition A J Shanks B.Eng(Hons) MIET BMT Defence Services Limited SYNOPSIS Today s warship designers and engineers look to technology to provide warships and systems better, cheaper
How To Manage Risk In Ancient Health Trust
 SharePoint Location Non-clinical Policies and Guidelines SharePoint Index Directory 3.0 Corporate Sub Area 3.1 Risk and Health & Safety Documents Key words (for search purposes) Risk, Risk Management,
SharePoint Location Non-clinical Policies and Guidelines SharePoint Index Directory 3.0 Corporate Sub Area 3.1 Risk and Health & Safety Documents Key words (for search purposes) Risk, Risk Management,
Information System Audit Guide
 Australian Government Department of Defence Information System Audit Guide VERSION 11.1 January 2012 Commonwealth of Australia 2011 Page 1 TABLE OF CONTENTS 1. INTRODUCTION TO ACCREDITATION...4 2. THE
Australian Government Department of Defence Information System Audit Guide VERSION 11.1 January 2012 Commonwealth of Australia 2011 Page 1 TABLE OF CONTENTS 1. INTRODUCTION TO ACCREDITATION...4 2. THE
Advanced File Integrity Monitoring for IT Security, Integrity and Compliance: What you need to know
 Whitepaper Advanced File Integrity Monitoring for IT Security, Integrity and Compliance: What you need to know Phone (0) 161 914 7798 www.distology.com [email protected] detecting the unknown Integrity
Whitepaper Advanced File Integrity Monitoring for IT Security, Integrity and Compliance: What you need to know Phone (0) 161 914 7798 www.distology.com [email protected] detecting the unknown Integrity
CYBER SECURITY TRAINING SAFE AND SECURE
 CYBER SECURITY TRAINING KEEPING YOU SAFE AND SECURE Experts in Cyber Security training. Hardly a day goes by without a cyber attack being reported. With this ever-increasing threat there is a growing need
CYBER SECURITY TRAINING KEEPING YOU SAFE AND SECURE Experts in Cyber Security training. Hardly a day goes by without a cyber attack being reported. With this ever-increasing threat there is a growing need
The introduction covers the recent changes is security threats and the effect those changes have on how we protect systems.
 1 Cyber-attacks frequently take advantage of software weaknesses unintentionally created during development. This presentation discusses some ways that improved acquisition practices can reduce the likelihood
1 Cyber-attacks frequently take advantage of software weaknesses unintentionally created during development. This presentation discusses some ways that improved acquisition practices can reduce the likelihood
Cyber Essentials Scheme. Protect your business from cyber threats and gain valuable certification
 Cyber Essentials Scheme Protect your business from cyber threats and gain valuable certification Why you need it Cybercrime appears in the news on an almost daily basis - but it s not just the large and
Cyber Essentials Scheme Protect your business from cyber threats and gain valuable certification Why you need it Cybercrime appears in the news on an almost daily basis - but it s not just the large and
developing your potential Cyber Security Training
 developing your potential Cyber Security Training The benefits of cyber security awareness The cost of a single cyber security incident can easily reach six-figure sums and any damage or loss to a company
developing your potential Cyber Security Training The benefits of cyber security awareness The cost of a single cyber security incident can easily reach six-figure sums and any damage or loss to a company
CESG Certification of Cyber Security Training Courses
 CESG Certification of Cyber Security Training Courses Supporting Assessment Criteria for the CESG Certified Training (CCT) Scheme Portions of this work are copyright The Institute of Information Security
CESG Certification of Cyber Security Training Courses Supporting Assessment Criteria for the CESG Certified Training (CCT) Scheme Portions of this work are copyright The Institute of Information Security
Corporate Security in 2016.
 Corporate Security in 2016. A QA Report Study Highlights According to ThreatMetrix, businesses in the UK are at greater risk of cybercrime than any other country in the world. In a recent survey carried
Corporate Security in 2016. A QA Report Study Highlights According to ThreatMetrix, businesses in the UK are at greater risk of cybercrime than any other country in the world. In a recent survey carried
Securing business data. CNS White Paper. Cloud for Enterprise. Effective Management of Data Security
 Securing business data CNS White Paper Cloud for Enterprise Effective Management of Data Security Jeff Finch, Head of Business Development, CNS Mosaic 2nd July 2015 Contents 1 Non-Disclosure Statement...
Securing business data CNS White Paper Cloud for Enterprise Effective Management of Data Security Jeff Finch, Head of Business Development, CNS Mosaic 2nd July 2015 Contents 1 Non-Disclosure Statement...
Best Practice in Design of Public-Private Partnerships (PPPs) for Social Infrastructure, particularly in Health Care and Education
 EMAIL [email protected] WEB www.fosterinfrastructure.com Best Practice in Design of Public-Private Partnerships (PPPs) for Social Infrastructure, particularly in Health Care and Education
EMAIL [email protected] WEB www.fosterinfrastructure.com Best Practice in Design of Public-Private Partnerships (PPPs) for Social Infrastructure, particularly in Health Care and Education
Software Process for QA
 Software Process for QA Basic approaches & alternatives CIS 610, W98 / M Young 1/7/98 1 This introduction and overview is intended to provide some basic background on software process (sometimes called
Software Process for QA Basic approaches & alternatives CIS 610, W98 / M Young 1/7/98 1 This introduction and overview is intended to provide some basic background on software process (sometimes called
The complete provider for. Gauging Products and Measurement Systems
 The complete provider for Gauging Products and Measurement Systems The Gauging Requirement Effective clearance assessment is something that concerns all railways and demands for significantly increased
The complete provider for Gauging Products and Measurement Systems The Gauging Requirement Effective clearance assessment is something that concerns all railways and demands for significantly increased
How To Choose the Right Vendor Information you need to select the IT Security Testing vendor that is right for you.
 Information you need to select the IT Security Testing vendor that is right for you. Netragard, Inc Main: 617-934- 0269 Email: [email protected] Website: http://www.netragard.com Blog: http://pentest.netragard.com
Information you need to select the IT Security Testing vendor that is right for you. Netragard, Inc Main: 617-934- 0269 Email: [email protected] Website: http://www.netragard.com Blog: http://pentest.netragard.com
Business Plan 2012/13
 Business Plan 2012/13 Contents Introduction 3 About the NFA..4 Priorities for 2012/13 4 Resources.6 Reporting Arrangements.6 Objective 1 7 To raise the profile and awareness of fraud among individuals,
Business Plan 2012/13 Contents Introduction 3 About the NFA..4 Priorities for 2012/13 4 Resources.6 Reporting Arrangements.6 Objective 1 7 To raise the profile and awareness of fraud among individuals,
Who s next after TalkTalk?
 Who s next after TalkTalk? Frequently Asked Questions on Cyber Risk Fraud threat to millions of TalkTalk customers TalkTalk cyber-attack: website hit by significant breach These are just two of the many
Who s next after TalkTalk? Frequently Asked Questions on Cyber Risk Fraud threat to millions of TalkTalk customers TalkTalk cyber-attack: website hit by significant breach These are just two of the many
Module 7 Study Guide
 Module 7 Study Guide Change Evaluation Welcome to your Study Guide. This document is supplementary to the information available to you online, and should be used in conjunction with the videos, quizzes
Module 7 Study Guide Change Evaluation Welcome to your Study Guide. This document is supplementary to the information available to you online, and should be used in conjunction with the videos, quizzes
Submission in response to the Life Insurance and Advice Working Group Interim Report on Retail Life Insurance
 30 January 2015 Mr John Trowbridge Chairman Life Insurance and Advice Working Group Email: [email protected] Dear Mr Trowbridge, Submission in response to the Life Insurance and Advice Working
30 January 2015 Mr John Trowbridge Chairman Life Insurance and Advice Working Group Email: [email protected] Dear Mr Trowbridge, Submission in response to the Life Insurance and Advice Working
SAFE SOFTWARE FOR SPACE APPLICATIONS: BUILDING ON THE DO-178 EXPERIENCE. Cheryl A. Dorsey Digital Flight / Solutions cadorsey@df-solutions.
 SAFE SOFTWARE FOR SPACE APPLICATIONS: BUILDING ON THE DO-178 EXPERIENCE Cheryl A. Dorsey Digital Flight / Solutions [email protected] DIGITAL FLIGHT / SOLUTIONS Presentation Outline DO-178 Overview
SAFE SOFTWARE FOR SPACE APPLICATIONS: BUILDING ON THE DO-178 EXPERIENCE Cheryl A. Dorsey Digital Flight / Solutions [email protected] DIGITAL FLIGHT / SOLUTIONS Presentation Outline DO-178 Overview
Cyber Defence Capability Assessment Tool (CDCAT ) Improving cyber security preparedness through risk and vulnerability analysis
 Cyber Defence Capability Assessment Tool (CDCAT ) Improving cyber security preparedness through risk and vulnerability analysis An analogue approach to a digital world What foundations is CDCAT built on?
Cyber Defence Capability Assessment Tool (CDCAT ) Improving cyber security preparedness through risk and vulnerability analysis An analogue approach to a digital world What foundations is CDCAT built on?
Cyber Security Consultancy Standard. Version 0.2 Crown Copyright 2015 All Rights Reserved. Page 1 of 13
 Cyber Security Consultancy Standard Version 0.2 Crown Copyright 2015 All Rights Reserved Page 1 of 13 Contents 1. Overview... 3 2. Assessment approach... 4 3. Requirements... 5 3.1 Service description...
Cyber Security Consultancy Standard Version 0.2 Crown Copyright 2015 All Rights Reserved Page 1 of 13 Contents 1. Overview... 3 2. Assessment approach... 4 3. Requirements... 5 3.1 Service description...
Asset Management Policy March 2014
 Asset Management Policy March 2014 In February 2011, we published our current Asset Management Policy. This is the first update incorporating further developments in our thinking on capacity planning and
Asset Management Policy March 2014 In February 2011, we published our current Asset Management Policy. This is the first update incorporating further developments in our thinking on capacity planning and
Business Continuity Policy and Business Continuity Management System
 Business Continuity Policy and Business Continuity Management System Summary: This policy sets out the structure for ensuring that the PCT has effective Business Continuity Plans in place in order to maintain
Business Continuity Policy and Business Continuity Management System Summary: This policy sets out the structure for ensuring that the PCT has effective Business Continuity Plans in place in order to maintain
The Road from Software Testing to Theorem Proving
 The Road from Software Testing to Theorem Proving A Short Compendium of my Favorite Software Verification Techniques Frédéric Painchaud DRDC Valcartier / Robustness and Software Analysis Group December
The Road from Software Testing to Theorem Proving A Short Compendium of my Favorite Software Verification Techniques Frédéric Painchaud DRDC Valcartier / Robustness and Software Analysis Group December
European Security Standards Reference Implementation Initiative (ESSRII)
 European Security Standards Reference Implementation Initiative (ESSRII) A Proposal for Action in Europe on International Information Security Standards Brian Gladman, European Technical Director, Trusted
European Security Standards Reference Implementation Initiative (ESSRII) A Proposal for Action in Europe on International Information Security Standards Brian Gladman, European Technical Director, Trusted
Principal risks and uncertainties
 Principal risks and uncertainties Our risk management approach We have a well-established risk management methodology which we use throughout the business to allow us to identify and manage the principal
Principal risks and uncertainties Our risk management approach We have a well-established risk management methodology which we use throughout the business to allow us to identify and manage the principal
Risks and uncertainties
 Risks and uncertainties Our risk management approach We have a well-established risk management methodology which we use throughout the business to allow us to identify and manage the principal risks that
Risks and uncertainties Our risk management approach We have a well-established risk management methodology which we use throughout the business to allow us to identify and manage the principal risks that
A specification for security-minded building information modelling, digital built environments and smart asset management
 Introduction to PAS 1192-5:2015 A specification for security-minded building information modelling, digital built environments and smart asset management Introduction PAS 1192-5:2015 is a specification
Introduction to PAS 1192-5:2015 A specification for security-minded building information modelling, digital built environments and smart asset management Introduction PAS 1192-5:2015 is a specification
Relationship Manager (Banking) Assessment Plan
 1. Introduction and Overview Relationship Manager (Banking) Assessment Plan The Relationship Manager (Banking) is an apprenticeship that takes 3-4 years to complete and is at a Level 6. It forms a key
1. Introduction and Overview Relationship Manager (Banking) Assessment Plan The Relationship Manager (Banking) is an apprenticeship that takes 3-4 years to complete and is at a Level 6. It forms a key
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY?
 WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
AUTHORED BY: George W. Gray CTO, VP Software & Information Systems Ivenix, Inc. ADDRESSING CYBERSECURITY IN INFUSION DEVICES
 AUTHORED BY: George W. Gray CTO, VP Software & Information Systems Ivenix, Inc. ADDRESSING CYBERSECURITY IN INFUSION DEVICES INTRODUCTION Cybersecurity has become an increasing concern in the medical device
AUTHORED BY: George W. Gray CTO, VP Software & Information Systems Ivenix, Inc. ADDRESSING CYBERSECURITY IN INFUSION DEVICES INTRODUCTION Cybersecurity has become an increasing concern in the medical device
CQI briefing note. Annex SL
 CQI briefing note Annex SL The most important event since ISO 9001? A quarter of a century ago, in December 1987, ISO 9001 Quality systems Model for quality assurance in design/development, production,
CQI briefing note Annex SL The most important event since ISO 9001? A quarter of a century ago, in December 1987, ISO 9001 Quality systems Model for quality assurance in design/development, production,
EARSC Views on the. Procurement of the Copernicus Services
 EARSC Views on the Procurement of the Copernicus Services EARSC, the European Association of Remote Sensing Companies represents the Earth Observation geoinformation services sector in Europe. Today EARSC
EARSC Views on the Procurement of the Copernicus Services EARSC, the European Association of Remote Sensing Companies represents the Earth Observation geoinformation services sector in Europe. Today EARSC
TLP WHITE. Denial of service attacks: what you need to know
 Denial of service attacks: what you need to know Contents Introduction... 2 What is DOS and how does it work?... 2 DDOS... 4 Why are they used?... 5 Take action... 6 Firewalls, antivirus and updates...
Denial of service attacks: what you need to know Contents Introduction... 2 What is DOS and how does it work?... 2 DDOS... 4 Why are they used?... 5 Take action... 6 Firewalls, antivirus and updates...
How To Manage Risk On A Scada System
 Risk Management for Industrial Control Systems (ICS) And Supervisory Control Systems (SCADA) Information For Senior Executives (Revised March 2012) Disclaimer: To the extent permitted by law, this document
Risk Management for Industrial Control Systems (ICS) And Supervisory Control Systems (SCADA) Information For Senior Executives (Revised March 2012) Disclaimer: To the extent permitted by law, this document
Lot 1 Service Specification MANAGED SECURITY SERVICES
 Lot 1 Service Specification MANAGED SECURITY SERVICES Fujitsu Services Limited, 2013 OVERVIEW OF FUJITSU MANAGED SECURITY SERVICES Fujitsu delivers a comprehensive range of information security services
Lot 1 Service Specification MANAGED SECURITY SERVICES Fujitsu Services Limited, 2013 OVERVIEW OF FUJITSU MANAGED SECURITY SERVICES Fujitsu delivers a comprehensive range of information security services
ENGINEERING COUNCIL. Guidance on Risk for the Engineering Profession. www.engc.org.uk/risk
 ENGINEERING COUNCIL Guidance on Risk for the Engineering Profession www.engc.org.uk/risk This guidance describes the role of professional engineers and technicians in dealing with risk, and their responsibilities
ENGINEERING COUNCIL Guidance on Risk for the Engineering Profession www.engc.org.uk/risk This guidance describes the role of professional engineers and technicians in dealing with risk, and their responsibilities
Section VI Principles of Laboratory Biosecurity
 Section VI Principles of Laboratory Biosecurity Since the publication of the 4th edition of BMBL in 1999, significant events have brought national and international scrutiny to the area of laboratory security.
Section VI Principles of Laboratory Biosecurity Since the publication of the 4th edition of BMBL in 1999, significant events have brought national and international scrutiny to the area of laboratory security.
Digital Asset Manager, Digital Curator. Cultural Informatics, Cultural/ Art ICT Manager
 Role title Digital Cultural Asset Manager Also known as Relevant professions Summary statement Mission Digital Asset Manager, Digital Curator Cultural Informatics, Cultural/ Art ICT Manager Deals with
Role title Digital Cultural Asset Manager Also known as Relevant professions Summary statement Mission Digital Asset Manager, Digital Curator Cultural Informatics, Cultural/ Art ICT Manager Deals with
Business continuity management and planning
 B Business continuity management and planning This document is part of the UCISA Information Security Toolkit providing guidance on the policies and processes needed to implement an organisational information
B Business continuity management and planning This document is part of the UCISA Information Security Toolkit providing guidance on the policies and processes needed to implement an organisational information
THE BENEFITS. Facts/Figures
 PERFORMANCE BASED LOGISTICS TRACK RECORD OF SUCCESS BAE Systems Large Aircraft Mr Tim Deacon, Nimrod Project Engineering Manager says of the IFS solution: Integrated Asset Management is an innovative solution
PERFORMANCE BASED LOGISTICS TRACK RECORD OF SUCCESS BAE Systems Large Aircraft Mr Tim Deacon, Nimrod Project Engineering Manager says of the IFS solution: Integrated Asset Management is an innovative solution
How to gain accreditation for a G-Cloud Service
 www.ascentor.co.uk How to gain accreditation for a G-Cloud Service Demystify the process As a registered supplier of G-Cloud services you will be keenly aware that getting onto the G-Cloud framework does
www.ascentor.co.uk How to gain accreditation for a G-Cloud Service Demystify the process As a registered supplier of G-Cloud services you will be keenly aware that getting onto the G-Cloud framework does
REVIEW OF AS5100.1 SCOPE AND GENERAL PRINCIPLES
 REVIEW OF AS5100.1 SCOPE AND GENERAL PRINCIPLES Nigel Powers, VicRoads, Australia Frank Rapattoni, Parsons Brinckerhoff, Australia ABSTRACT AS5100, the Australian Bridge Design Code, is currently under
REVIEW OF AS5100.1 SCOPE AND GENERAL PRINCIPLES Nigel Powers, VicRoads, Australia Frank Rapattoni, Parsons Brinckerhoff, Australia ABSTRACT AS5100, the Australian Bridge Design Code, is currently under
Level 5 Diploma in Managing the Supply Chain (QCF) Qualification Specification
 Level 5 Diploma in Managing the Supply Chain (QCF) Qualification Specification Created: May 2012 Version: 1.0 Accreditation Number: 600/5605/8 Qualification Start Date: 1 st June 2012 Qualification Last
Level 5 Diploma in Managing the Supply Chain (QCF) Qualification Specification Created: May 2012 Version: 1.0 Accreditation Number: 600/5605/8 Qualification Start Date: 1 st June 2012 Qualification Last
April 2015 Issue No:1.0. Application Guidance - CCP Security and Information Risk Advisor Role, Practitioner Level
 April 2015 Issue No:1.0 Application Guidance - CCP Security and Information Risk Advisor Role, Practitioner Level Application Guidance CCP Security and Information Risk Advisor Role, Practitioner Level
April 2015 Issue No:1.0 Application Guidance - CCP Security and Information Risk Advisor Role, Practitioner Level Application Guidance CCP Security and Information Risk Advisor Role, Practitioner Level
Mauro Calvano. About Aviation Safety Management Systems
 Mauro Calvano About Aviation Safety Management Systems January 2003 1 INTRODUCTION In order to be aware of the factors that are driving the accident rate during the last decade, we must identify the hazards
Mauro Calvano About Aviation Safety Management Systems January 2003 1 INTRODUCTION In order to be aware of the factors that are driving the accident rate during the last decade, we must identify the hazards
-.% . /(.0/.1 . 201 . ) 53%/(01 . 6 (01 (%((. * 7071 (%%2 $,( . 8 / 9!0/!1 . # (3(0 31.%::((. ;.!0.!1 %2% . ".(0.1 $) (%+"",(%$.(6
 !""#"" ""$"$"# $) ""$"*$"# %%&''$ $( (%( $) (%+"",(%$ -.% Number Phase Name Description. /(.0/.1.(((%( $. 201 2,%%%% %$. %(01 3-(4%%($. ) 53%/(01 %%4.%%2%, ($. 6 (01 (%((. * 7071 (%%2. 8 / 9!0/!1 ((((($%
!""#"" ""$"$"# $) ""$"*$"# %%&''$ $( (%( $) (%+"",(%$ -.% Number Phase Name Description. /(.0/.1.(((%( $. 201 2,%%%% %$. %(01 3-(4%%($. ) 53%/(01 %%4.%%2%, ($. 6 (01 (%((. * 7071 (%%2. 8 / 9!0/!1 ((((($%
Legal Ombudsman February 2015. Report under section 120 of the Legal Services Act 2007: Transparency of the costs of legal services
 Legal Ombudsman February 2015 Report under section 120 of the Legal Services Act 2007: Transparency of the costs of legal services Contents Transparency of the costs of legal services 1 Introduction 2
Legal Ombudsman February 2015 Report under section 120 of the Legal Services Act 2007: Transparency of the costs of legal services Contents Transparency of the costs of legal services 1 Introduction 2
Guidance on Risk Analysis Requirements under the HIPAA Security Rule
 Guidance on Risk Analysis Requirements under the HIPAA Security Rule Introduction The Office for Civil Rights (OCR) is responsible for issuing annual guidance on the provisions in the HIPAA Security Rule.
Guidance on Risk Analysis Requirements under the HIPAA Security Rule Introduction The Office for Civil Rights (OCR) is responsible for issuing annual guidance on the provisions in the HIPAA Security Rule.
The Influence of Software Vulnerabilities on Business Risks 1
 The Influence of Software Vulnerabilities on Business Risks 1 Four sources of risk relevant for evaluating the influence of software vulnerabilities on business risks Authors Hilbrand Kramer, MSc (Royal
The Influence of Software Vulnerabilities on Business Risks 1 Four sources of risk relevant for evaluating the influence of software vulnerabilities on business risks Authors Hilbrand Kramer, MSc (Royal
THALES. www.thalesgroup. corn
 THALES www.thalesgroup. corn c Understanding cyber security is a challenge faced by all businesses and organisations around the world. New threats emerge on a daily basis and it can be difficult to understand
THALES www.thalesgroup. corn c Understanding cyber security is a challenge faced by all businesses and organisations around the world. New threats emerge on a daily basis and it can be difficult to understand
Cyber Security - What Would a Breach Really Mean for your Business?
 Cyber Security - What Would a Breach Really Mean for your Business? August 2014 v1.0 As the internet has become increasingly important across every aspect of business, the risks posed by breaches to cyber
Cyber Security - What Would a Breach Really Mean for your Business? August 2014 v1.0 As the internet has become increasingly important across every aspect of business, the risks posed by breaches to cyber
UNDERGRADUATE PROGRAMME SPECIFICATION
 UNDERGRADUATE PROGRAMME SPECIFICATION Programme Title: Awarding Body: Teaching Institution: Final Awards: BSc(Hons) Aeronautical Technology Staffordshire University Staffordshire University BSc(Hons) Aeronautical
UNDERGRADUATE PROGRAMME SPECIFICATION Programme Title: Awarding Body: Teaching Institution: Final Awards: BSc(Hons) Aeronautical Technology Staffordshire University Staffordshire University BSc(Hons) Aeronautical
IMPROVE AWARENESS AND SKILLS
 SECURITY FOR INDUSTRIAL CONTROL SYSTEMS IMPROVE AWARENESS AND SKILLS A GOOD PRACTICE GUIDE Disclaimer Reference to any specific commercial product, process or service by trade name, trademark, manufacturer,
SECURITY FOR INDUSTRIAL CONTROL SYSTEMS IMPROVE AWARENESS AND SKILLS A GOOD PRACTICE GUIDE Disclaimer Reference to any specific commercial product, process or service by trade name, trademark, manufacturer,
The European and UK Space Agencies
 The European and UK Space Agencies A response to the House of Commons Science and Technology Select Committee April 2013 Introduction The Royal Academy of Engineering is pleased to submit evidence to the
The European and UK Space Agencies A response to the House of Commons Science and Technology Select Committee April 2013 Introduction The Royal Academy of Engineering is pleased to submit evidence to the
Risk assessment. made simple. sayer vincent consultants and auditors. Introduction 3. step1 Identifying the risks 4. step2 Assessing the risks 7
 Risk assessment made simple Introduction 3 step1 Identifying the risks 4 step2 Assessing the risks 7 step3 Establishing action points 11 step4 Developing a risk register 13 Monitoring and assessment 14
Risk assessment made simple Introduction 3 step1 Identifying the risks 4 step2 Assessing the risks 7 step3 Establishing action points 11 step4 Developing a risk register 13 Monitoring and assessment 14
Digital Industries Apprenticeship: Assessment Plan. Cyber Security Technologist. April 2016
 Digital Industries Apprenticeship: Assessment Plan Cyber Security Technologist April 2016 1 Digital Industries Apprenticeships: Assessment Plan 1. General Introduction and Overview The apprenticeship Standard
Digital Industries Apprenticeship: Assessment Plan Cyber Security Technologist April 2016 1 Digital Industries Apprenticeships: Assessment Plan 1. General Introduction and Overview The apprenticeship Standard
OPERATIONAL PROJECT MANAGEMENT (USING MS PROJECT)
 OPERATIONAL PROJECT MANAGEMENT (USING MS PROJECT) 3 DAY COURSE INTRODUCTION The principles of project management are generic and therefore can be applied to all projects regardless of business sector.
OPERATIONAL PROJECT MANAGEMENT (USING MS PROJECT) 3 DAY COURSE INTRODUCTION The principles of project management are generic and therefore can be applied to all projects regardless of business sector.
Changing Perceptions and the Skills Required by Security Managers
 Changing Perceptions and the Skills Required by Security Managers by Michael A Pepper MSc CPP PSP (First published in New Zealand Security October/November 2006) Introduction Mention of security management
Changing Perceptions and the Skills Required by Security Managers by Michael A Pepper MSc CPP PSP (First published in New Zealand Security October/November 2006) Introduction Mention of security management
MARCH 2012. Strategic Risk Policy Update March 2012 v1.10.doc
 MARCH 2012 Version 1.10 Strategic Risk Policy Update March 2012 v1.10.doc Document History Current Version Document Name Risk Management Policy Statement and Strategic Framework Last Updated By Alan Till
MARCH 2012 Version 1.10 Strategic Risk Policy Update March 2012 v1.10.doc Document History Current Version Document Name Risk Management Policy Statement and Strategic Framework Last Updated By Alan Till
ISO/IEC 27001 Information Security Management. Securing your information assets Product Guide
 ISO/IEC 27001 Information Security Management Securing your information assets Product Guide What is ISO/IEC 27001? ISO/IEC 27001 is the international standard for information security management and details
ISO/IEC 27001 Information Security Management Securing your information assets Product Guide What is ISO/IEC 27001? ISO/IEC 27001 is the international standard for information security management and details
SCOTTISH CENSUS INDEPENDENT SECURITY REVIEW REPORT
 SCOTTISH CENSUS INDEPENDENT SECURITY REVIEW REPORT Issue 1.0 Date 24/03/2011 Logica is a business and technology service company, employing 39,000 people. It provides business consulting, systems integration
SCOTTISH CENSUS INDEPENDENT SECURITY REVIEW REPORT Issue 1.0 Date 24/03/2011 Logica is a business and technology service company, employing 39,000 people. It provides business consulting, systems integration
Customer requirements. Asset management planning Inspection and assessment Route asset planning Annual work plans Contracting strategy
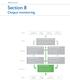 Section 8 Output monitoring Inputs Customer requirements Safety standards Outputs and funding SRA and Government Policy Network stewardship strategy Asset and operational policies Maintenance & renewal
Section 8 Output monitoring Inputs Customer requirements Safety standards Outputs and funding SRA and Government Policy Network stewardship strategy Asset and operational policies Maintenance & renewal
Access Governance. Delivering value. What you gain. Putting a project back on track for success
 What you gain Risk-managed access Having a second line of defence to identify what needs to be controlled and who owns it lowers your operational costs, while taking a risk-based approach ensures greater
What you gain Risk-managed access Having a second line of defence to identify what needs to be controlled and who owns it lowers your operational costs, while taking a risk-based approach ensures greater
Best Practices in ICS Security for System Operators. A Wurldtech White Paper
 Best Practices in ICS Security for System Operators A Wurldtech White Paper No part of this document may be distributed, reproduced or posted without the express written permission of Wurldtech Security
Best Practices in ICS Security for System Operators A Wurldtech White Paper No part of this document may be distributed, reproduced or posted without the express written permission of Wurldtech Security
Assessment of Software for Government
 Version 1.0, April 2012 Aim 1. This document presents an assessment model for selecting software, including open source software, for use across Government, and the wider UK public sector. 2. It is presented
Version 1.0, April 2012 Aim 1. This document presents an assessment model for selecting software, including open source software, for use across Government, and the wider UK public sector. 2. It is presented
Chapter 1 Introduction to Contract Management and Administration
 Chapter 1 Introduction to Contract Management and Administration Definitions What is Contract Management? Contract management is the process that ensures both parties to a contract fully understand their
Chapter 1 Introduction to Contract Management and Administration Definitions What is Contract Management? Contract management is the process that ensures both parties to a contract fully understand their
Enterprise Security Risk Assessments What are we trying to protect and why?
 DSW Consulting Pty Ltd ABN: 88 131 241 113 NSW SECURITY MASTER LICENCE: 409991858 ACT SECURITY MASTER LICENCE: 17501699 VIC SECURITY REGISTRATION: 716 877 70S QLD SECURITY ADVISOR LICENCE: 3440620 www.dswconsulting.com.au
DSW Consulting Pty Ltd ABN: 88 131 241 113 NSW SECURITY MASTER LICENCE: 409991858 ACT SECURITY MASTER LICENCE: 17501699 VIC SECURITY REGISTRATION: 716 877 70S QLD SECURITY ADVISOR LICENCE: 3440620 www.dswconsulting.com.au
