MailMarshal 6.X Architecture Guide
|
|
|
- Gabriel Cannon
- 7 years ago
- Views:
Transcription
1 Technical White Paper MailMarshal 6.X Architecture Guide Contents MailMarshal SMTP 6.X Architecture 2 MailMarshal SMTP 6.X Components 2 Installation Scenarios 5 Customer Deployment Scenarios 8 This document introduces MailMarshal SMTP 6.X concepts and installation scenarios. The first section of the paper briefly describes the architecture model. The second section of the paper details the individual components and explains how each interacts with the other components. It also discusses the benefits that this architecture provides, and how you can take advantage of these benefits. The third section covers the different installation scenarios for MailMarshal. It presents and discusses five different scenarios for deployment of the product. The final section looks at a number of company use case examples, and discusses several different ways that MailMarshal could be implemented for them. These examples are based on small, medium, large and enterprise companies. m86security.com
2 MAILMARSHAL SMTP 6.X ARCHITECTURE The main thinking behind the architecture of this version was to improve scalability and manageability as compared to the MailMarshal 5.5 product, especially to meet the requirements and needs of Enterprise size installations. The main goals were to: Provide a single configuration console enterprise wide Provide a simplified, more secure security model for DMZ deployment Allow the MailMarshal processing node to update their configuration using minimal bandwidth Provide a unified management console enterprise wide with the ability to manage high volumes of quarantined messages no matter what MailMarshal processing node Server they are quarantined on Provide rolled up enterprise wide reports, with remote data delivered over low bandwidth links The resulting design uses a split security model where Configuration and policy is managed using the Array Manager component and subsequently stored into the SQL Database. Configuration and policy is sent from the Array Manager to the MailMarshal processing node servers and is applied on each server. Note: Each of the components is shown as a separate computer in the expanded diagram below, but in most cases the components do not require separate servers. A decision about the number of servers, and the location where each component is installed, depends on the existing company infrastructure and size. MAILMARSHAL SMTP 6.X COMPONENTS Array Manager Recommendations The location of the Array Manager can affect the performance of the administration and configuration tools used in MailMarshal, but will not necessarily affect the mail processing performance. The recommended locations for the Array Manager are listed below, from most to least preferred: 1. On the same server as the SQL Server holding the MailMarshal database. This location is preferred because the Array Manager is the only component that actually communicates directly to the MailMarshal database. All the other components communicate to the database through the Array Manager. 2. On a server that is as close as possible to the SQL Server holding the MailMarshal database, and has a LAN speed network connection to it. 3. On the same server as an Active Directory Global Catalog. The Array Manager communicates to the Global Catalog on a regular basis if the installation uses Active directory user groups. The Array Manager can also communicate through LDAP to another existing directory server. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 2
3 4. On a smaller site, the Array Manager, the MailMarshal processing node and the SQL Database (SQL Server or SQL Express installation) could all be on the same server. Product Configuration As mentioned above, the Array Manager is the point where you define Configuration and Policy. The MailMarshal Configurator tool connects to the Array Manager to retrieve the current configuration. The configuration that is displayed in the Configurator is retrieved from the registry on the Array Manager. As policy or configuration information is changed in the Configurator the changes are written to the registry on the Array Manager. When the administrator Commits Configuration Change, a snapshot of the configuration stored in the registry is stored in the SQL database and also exported to a XML Document. The Array Manager then notifies the MailMarshal processing node servers that an update is available. The node servers also check for updates periodically. All communication between the Array Manager and Nodes is through a single TPC port (port by default). When the MailMarshal Node server recognizes a new update, the XML document is requested from the Array Manager. The Array Manager compresses the XML document and delivers it to the MailMarshal Node. When this new XML configuration document arrives at the MailMarshal Node and is uncompressed, the new configuration settings are dynamically applied to any new threads that start after the new configuration is available, except for some server values like local domain lists which will require the associated service to be restarted. SpamCensor Updates The Array Manager also retrieves updates to the M86 Security SpamCensor over the Internet. The Array Manager checks for these updates frequently. If an update is received then the standard process for configuration changes as explained above will take place to get the updates out the MailMarshal nodes. Database Communications The Array Manager is the only component that communicates directly to the MailMarshal Database. This communication uses TCP and defaults to the standard SQL port, port Some examples of data passed between the Array Manager and the database are: Logging data passed on from the MailMarshal Node Servers Lists of quarantined messages retrieved to populate the folder listing views in the Console Message details such as the quarantine location, used when viewing the details of a quarantined message in the Console Transactional information from the MailMarshal processing nodes relating to administrative tasks such as message release, forwarding, etc. Directory Connections The Array Manager is also the component that communicates with any organizational directories, as defined by the Connectors set up through the MailMarshal Configurator tool. Depending on the type of connector, the Array Manager communicates with Active Directory natively using ADSI, or with a LDAP directory using TCP port 389 or a custom port (including SSL). The Array Manager uses the directory to maintain a list of groups and members referenced in the MailMarshal policy. Native Active Directory support provides greater flexibility in queries. MailMarshal can retrieve all the aliases assigned to each user for use in policy or in the Spam Quarantine Management tool. The administrator can specify how often each directory is checked for changes to group membership. If any changes have been made the Array Manager refreshes the affected group to ensure it is up to date. The changes to group membership take effect immediately. They do not require you to commit configuration. MailMarshal MMC Console Actions The MailMarshal Console provides an enterprise wide view of the MailMarshal implementation. It connects to the Array Manager and uses data from the MailMarshal database. For example if an administrator running the MailMarshal Console application views the contents of a quarantine folder, the information comes from the MailMarshal database and is a list of all the messages quarantined in that particular folder on all MailMarshal nodes enterprise wide. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 3
4 When the administrator selects a message from the folder list and views the details of that message, the Array Manager communicates with the node where the message is quarantined. The node invokes the unpacking engine which returns the message data. The Console provides a safe view of the message components in a protected sandbox. When an administrator decides to forward, release or delete a particular message, the Array Manager communicates this request to the MailMarshal node where the message has been quarantined, and the node takes the appropriate action. The Array Manager also updates the information about the message in the database. All the other views in the MailMarshal Console, such as the MailMarshal Today page and the domain views, are populated by data the Array Manager has retrieved from the database. The MailMarshal Console does not communicate directly with the database. MailMarshal Web Console Actions The Web based version of the MailMarshal Console provides exactly the same functionality as the MMC based version described above. The pages are created by an ASP.NET application running on a Microsoft Internet Information Services server, using content provided by the Array Manager. Spam Quarantine Management Actions The end-user focused Spam Quarantine Management tool is also an ASP.NET application running on an IIS server, using content provided by the Array Manager. The process of viewing quarantined messages in the Spam Quarantine Management tool is similar to that used in the Console. A user will only be able to view the messages that have been quarantined for their address, including any aliases they may have. MailMarshal Node Server The function of the MailMarshal node servers is solely to process incoming and outgoing SMTP messages according to the policy defined by the organization. A MailMarshal node generates SMTP traffic and management communication. The SMTP traffic generated by the standard SMTP gateway function consists of the incoming and outgoing mail streams. You can also configure MailMarshal as a POP3 mail server, which adds POP3 traffic. (This option is only available for installations with a single node.) All management communication traffic is between the node and the Array Manager using a single TCP port. By default MailMarshal uses port for this purpose. Nodes retrieve configuration from an XML settings file that is local on the node itself. The configuration is loaded when the MailMarshal services are started, and reloaded after the node downloads an updated XML file from the Array. The only other incoming management communication happens when the Array Manager requests the node to take some action on a quarantined message. For example the Array Manager can request the node to send the data required to view the message in the Console, or to release, forward or delete a particular message. The only outgoing management communication initiated by the node is delivery of the batched logging information to the Array Manager to be written to the MailMarshal database. A MailMarshal node creates one or more log entries for each message it processes. These log entries are written to a local file queue on each MailMarshal node. A Log Follower process batches this queue content to the Array Manager on a regular basis (typically every 15 seconds, or 100 records per batch). If the Log Follower cannot communicate with the Array Manager, the node continues to store records locally until it can contact the Array Manager. This design provides a highly efficient and fault tolerant method of getting the logging information into the MailMarshal database. SQL Database Server The SQL database server (SQL Server, or the free SQL Express for smaller installations) hosts the MailMarshal Database. The database contains logging information, configuration and policy information, and quarantine folder information. As previously described the only component that talks directly to the SQL Server is the Array Manager. It is good practice to place the Array Manager on the same server as the SQL Server, or as close as possible. For sizing recommendations, please see the MailMarshal User Guide or sizing whitepaper. MailMarshal includes a tool to migrate the contents of an older (5.x) database if required. MailMarshal also provides a tool to checks that all the messages quarantined on a particular MailMarshal node are detailed in the MailMarshal database, so that they will be shown in the folder listings within the Consoles and the Spam Quarantine Management tool. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 4
5 IIS Web Server The MailMarshal Web components install on an Internet Information Services (IIS) server. These components are only required if an organization wants to make use of the Spam Quarantine Management tool or the Web Console. The Web components use ASP.NET. Requirements for specific versions and applications are detailed in the product Release Notes. You can use a secure Web site (HTTPS) to protect user data and authentication information. The web application on the IIS server communicates with the Array Manager to get the content for these pages. Internal Mail Server An organization s internal server communicates through SMTP to the MailMarshal processing node servers, typically using TCP port 25 in both directions. The processing nodes do not require any other access to the internal server. If the internal server is the organization s LDAP directory server, and you are using LDAP to provide user and group information in support of the MailMarshal policy, the Array Manager uses LDAP to retrieve this information. Network Ports Required Typically MailMarshal uses the following network protocols and ports: SMTP (port 25) from MailMarshal processing servers to the Internet and to the internal servers and/or clients. DNS (port 53, both TCP and UDP) from MailMarshal processing servers for resolution of external server names. TCP port for communication between the processing servers, Array Manager, and Console. This connection can be changed to another port of your choice. HTTP and HTTPS from the Array Manager to the Internet for access to SpamCensor updates (ports 80 and 443). You can use a proxy server for Web access if your environment requires it. SQL server connection (port 1433 by default) between the Array Manager and the SQL database, and between the database and any Reports Console. The Array Manager and the Configurator would typically be deployed within the trusted LAN, not through a firewall for both performance and security reasons. POP3 (port 110) if MailMarshal is functioning as a POP3 server. INSTALLATION SCENARIOS This section discusses some typical options for the deployment of the MailMarshal components. Each option provides all the required functions of an gateway. Five different scenarios are explained below: 1. Install MailMarshal on its own physical server, as an relay within an organization 2. Install MailMarshal as a POP3/SMTP server providing all server functions for a small organization 3. Install MailMarshal on a Proxy Server 4. Install MailMarshal on the same physical server as the organizations server software 5. Install MailMarshal nodes into the DMZ, with the Array Manager in the trusted network. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 5
6 1. Install MailMarshal on its own physical server, as an relay within an organization In this case the MailMarshal installation is a standalone server including all management and processing components. This option is suitable for small to medium sized organizations with a single Internet gateway and server. All workstations within the organization send through the server. The server forwards all external messages to the MailMarshal server for processing and delivery. The DNS MX record (or the firewall s relay setting) is set so that the MailMarshal server receives all inbound to the organization. Install the MailMarshal database on an available SQL server in the local network. In smaller organizations, it will be possible to install SQL Express on the MailMarshal server. Install the MailMarshal Spam Quarantine Management Web site on an intranet Web server. Install MailMarshal Reports and optionally management consoles on one or more workstations in the local network. 2. Install MailMarshal as a POP3/SMTP server providing all server functions for a small organization In this example, workstations within the organization send to the MailMarshal server on port 25 for processing. MailMarshal delivers for internal addresses to MailMarshal POP3 mailboxes for collection by clients. Retrieve and send to and from external addresses over a dialup or other link to an ISP. In this case the MailMarshal installation is a standalone server including all management and processing components. In most organizations that choose this scenario, it will be possible to install SQL Express on the MailMarshal server. Install the MailMarshal Spam Quarantine Management Web site on an intranet Web server. Install MailMarshal Reports and optionally management consoles on one or more workstations in the local network. 3. Install MailMarshal on a Proxy Server This environment is simple to implement and fits logically with the concept of a proxy server and no environmental or configuration changes need be made to the proxy server. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 6
7 MailMarshal effectively proxys SMTP between the interfaces of the proxy server and passes them to the existing server. The existing server simply forwards all outbound to the internal interface of the proxy. If no firewall is used in the environment the MX records for the organization will point to the external interface of the proxy. 4. Install MailMarshal on the same physical server as the organizations server software In this case, all sent from outside the organization arrives at the server computer on the default SMTP port, port 25. MailMarshal forwards processed inbound to the other server software using the localhost IP address and port 97. The other server sends for outside delivery to MailMarshal using the localhost IP address and port 25. Install the MailMarshal database on an available SQL server in the local network. MailMarshal is installed as a standalone server including all management and processing components. Install the MailMarshal Spam Quarantine Management Web site on an intranet Web server. Install MailMarshal Reports on one or more workstations in the local network Note: This installation option depends on the server having sufficient resources to support both MailMarshal and another server application. 5. Install MailMarshal nodes in the DMZ, with the Array Manager in the trusted network This environment is straightforward to implement as well, and would be the environment of choice for larger organizations. In this example, the MailMarshal installation includes a load balanced array of MailMarshal processing servers in the DMZ. All sent from within the organization passes through the local server, which delivers outbound messages to the MailMarshal servers on port 25. MailMarshal delivers incoming to the local server. Install the MailMarshal Array Manager on a SQL server or a dedicated server within the LAN to perform configuration and connect to the MailMarshal database. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 7
8 Install the MailMarshal Spam Quarantine Management Web site and the MailMarshal Web console on an intranet Web server. Open TCP port (or a single port of your choice) in the firewall between the DMZ and the Array Manager, to allow MailMarshal configuration and logging traffic. A distributed enterprise with more than one gateway can install one or more MailMarshal processing servers at each gateway. If the enterprise uses the same policies at all locations, it can use a single MailMarshal Array Manager to control configuration and perform logging for all locations. All the processing servers must be able to communicate with the Array Manager on port Install MailMarshal Reports and optionally management consoles on one or more workstations in the local network. CUSTOMER DEPLOYMENT SCENARIOS This final section looks at some typical actual customer sites and shows how you might integrate not only MailMarshal, but also the WebMarshal product as well. The section discusses four different sized companies: Small Company 200 Users, single site Medium Company 750 users, single site Large Company 3000 users, multiple sites, 1 Internet Gateway Enterprise Company 50,000 users, multiple sites, multiple Internet Gateways The information and guidance provided here is only a guide and is not guaranteed to meet every customer s specific needs. Please contact a M86 representative for detailed guidance about your specific situation. This section does not provide hardware sizing guidelines. For more information on hardware sizing, please refer to the MailMarshal User Guide and sizing whitepaper. Small Company The first example is a small company with 200 users at a single site. The company has a firewall device which connects through a router to the internet. The firewall has only two security domains, Public (Un-trusted) and the Internal Network (Trusted). The company uses a Microsoft Small business server environment. The integrated Exchange server is the internal server, and the integrated Microsoft ISA server is their web access server. MailMarshal is installed on this same server along with the other required resources such as IIS and the Domain Controller. This solution is based on a single server providing all of these functions which is realistic for a site with only 200 users. In this scenario, remember to configure MailMarshal to send the inbound SMTP on a different port to the internal mail server, perhaps port 97. The internal mail server will need to receive on port 97 as well. This configuration scenario is the same as option 4 of the Installation scenarios. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 8
9 Medium Company For this example, a medium company is defined as having 750 users in a single site. They have a firewall device which connects through a router to the internet. The firewall has only two security domains, Public (Un-trusted) and the Internal Network (Trusted). The organization uses two main servers. One is used as a Domain Controller and also has SQL or SQL Express installed, as well as IIS and the incumbent mail application such as Lotus Notes, GroupWise, or Exchange. The second server runs all the Content Security products with MailMarshal processing, and the Array Manager together. This medium company has two servers, with the load split between them. The configuration is the same as option 1 of the Installation scenarios. Large Company The Large Company is defined as 3000 users spread across multiple sites. They have one central point for Internet access where all the SMTP mail and other Internet traffic is received and sent. The remote sites utilize Frame Relay based Wide Area Networks (WAN) for connectivity with the main office. The larger remote sites have their own exchange environment while the smaller ones rely on the main office Exchange infrastructure. This large company uses the same configuration scenario as option 5 above, and since they have the MailMarshal nodes in the DMZ they are able to take advantage of the new security features. Since there is only a single Internet Gateway, there is only one group of MailMarshal processing nodes. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 9
10 This scenario is the same as option 5 of the Installation scenarios. Enterprise Company For this last example an Enterprise company is defined as having 50,000 employees spread over several countries, and multiple office locations in each country. As such they have multiple points for Internet access where SMTP mail and other internet traffic is routed. These multiple points are set up to load balance between each other based on load and location. All the sites are joined to each other by an Internet based VPN solution. There is one main office for each country that handles the core services for that country such as Internet access but all the core services in each country are managed from the world headquarters. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 10
11 The configuration of this solution is also the same as option 5 of the Installation scenarios. Technical Whitepaper: MailMarshal SMTP 6.X Architecture Guide Page 11
12 ABOUT M86 SECURITY M86 Security is a global provider of Web and messaging security products, delivering comprehensive protection to more than 20,000 customers and over 16 million users worldwide. As one of the largest independent internet security companies, we have the expertise, product breadth and technology to protect organizations from both current and emerging threats. Our appliance, software and cloud-based solutions leverage real-time threat data to proactively secure customers networks from malware and spam; protect their sensitive information; and maintain employee productivity. The company is based in Orange, California with international headquarters in London and offices worldwide. For more information about M86 Security, please visit TRY BEFORE YOU BUY M86 Security offers free product trials and evaluations. Simply contact us or visit Corporate Headquarters 828 West Taft Avenue Orange, CA United States Phone: +1 (714) Fax: +1 (714) International Headquarters Renaissance 2200 Basing View, Basingstoke Hampshire RG21 4EQ United Kingdom Phone: +44 (0) Fax: +44 (0) Asia-Pacific Millennium Centre, Bldg C, Level Great South Road Ellerslie, Auckland, 1051 New Zealand Phone: +64 (0) Fax: +64 (0) Version Copyright 2010 M86 Security. All rights reserved. M86 Security is a registered trademark of M86 Security. All other product and company names mentioned herein are trademarks or registered trademarks of their respective companies.
SWG Installation Utility
 Technical Brief SWG Installation Utility Contents Introduction 2 Usage Instructions 2 Known Limitations 7 m86security.com INTRODUCTION The new SWG Installation Utility replaces the Finjan OS version upgrade
Technical Brief SWG Installation Utility Contents Introduction 2 Usage Instructions 2 Known Limitations 7 m86security.com INTRODUCTION The new SWG Installation Utility replaces the Finjan OS version upgrade
M86 MailMarshal SMTP USER GUIDE. Software Version: 6.8.4
 M86 MailMarshal SMTP USER GUIDE Software Version: 6.8.4 M86 MAILMARSHAL SMTP USER GUIDE 2010 M86 Security All rights reserved. Published October 2010 for software release 6.8.4 No part of this Documentation
M86 MailMarshal SMTP USER GUIDE Software Version: 6.8.4 M86 MAILMARSHAL SMTP USER GUIDE 2010 M86 Security All rights reserved. Published October 2010 for software release 6.8.4 No part of this Documentation
User Guide. MailMarshal SMTP. Version 6.0
 User Guide MailMarshal SMTP Version 6.0 THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT OR A NON-DISCLOSURE AGREEMENT.
User Guide MailMarshal SMTP Version 6.0 THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT OR A NON-DISCLOSURE AGREEMENT.
Installing Policy Patrol on a separate machine
 Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Steps for Basic Configuration
 1. This guide describes how to use the Unified Threat Management appliance (UTM) Basic Setup Wizard to configure the UTM for connection to your network. It also describes how to register the UTM with NETGEAR.
1. This guide describes how to use the Unified Threat Management appliance (UTM) Basic Setup Wizard to configure the UTM for connection to your network. It also describes how to register the UTM with NETGEAR.
How To Plan A Desktop Workspace Infrastructure
 Dell Copyright 2014 Moka5, Inc. All rights reserved. Moka5, MokaFive, LivePC, and the Moka5 logo are trademarks of Moka5, Inc. All other product or company names may be trademarks of their respective owners.
Dell Copyright 2014 Moka5, Inc. All rights reserved. Moka5, MokaFive, LivePC, and the Moka5 logo are trademarks of Moka5, Inc. All other product or company names may be trademarks of their respective owners.
MailMarshal SMTP in a Load Balanced Array of Servers Technical White Paper September 29, 2003
 Contents Introduction... 1 Network Load Balancing... 2 Example Environment... 5 Microsoft Network Load Balancing (Configuration)... 6 Validating your NLB configuration... 13 MailMarshal Specific Configuration...
Contents Introduction... 1 Network Load Balancing... 2 Example Environment... 5 Microsoft Network Load Balancing (Configuration)... 6 Validating your NLB configuration... 13 MailMarshal Specific Configuration...
MailMarshal Exchange in a Windows Server Active/Passive Cluster
 MailMarshal Exchange in a Windows Server Active/Passive Cluster November, 2006 Contents Introduction 2 Preparation 3 Generic Resource Creation 4 Cluster MailMarshal Install 4 Antivirus Software 8 Known
MailMarshal Exchange in a Windows Server Active/Passive Cluster November, 2006 Contents Introduction 2 Preparation 3 Generic Resource Creation 4 Cluster MailMarshal Install 4 Antivirus Software 8 Known
A host-based firewall can be used in addition to a network-based firewall to provide multiple layers of protection.
 A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
M86 MailMarshal Exchange USER GUIDE. Software Version: 7.1
 M86 MailMarshal Exchange USER GUIDE Software Version: 7.1 M86 MAILMARSHAL EXCHANGE USER GUIDE 2011 M86 Security All rights reserved. Published November 2011 for software release 7.1 No part of this Documentation
M86 MailMarshal Exchange USER GUIDE Software Version: 7.1 M86 MAILMARSHAL EXCHANGE USER GUIDE 2011 M86 Security All rights reserved. Published November 2011 for software release 7.1 No part of this Documentation
Trend Micro Hosted Email Security. Best Practice Guide
 Trend Micro Hosted Email Security Best Practice Guide Hosted Email Security Best Practice Guide Trend Micro Incorporated reserves the right to make changes to this document and to the products described
Trend Micro Hosted Email Security Best Practice Guide Hosted Email Security Best Practice Guide Trend Micro Incorporated reserves the right to make changes to this document and to the products described
Kaseya Server Instal ation User Guide June 6, 2008
 Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
How To Protect Email From The Internet With Mailmarshal Smt And Mailmper For Exchange
 Deployment Options for Exchange March 2006 Contents What is Email Scanning? 2 What is Total Email Content Security? 3 The Solutions 3 What are my Options? 4 Key Differences between MailMarshal SMTP and
Deployment Options for Exchange March 2006 Contents What is Email Scanning? 2 What is Total Email Content Security? 3 The Solutions 3 What are my Options? 4 Key Differences between MailMarshal SMTP and
Netsweeper Whitepaper
 Netsweeper Inc. Corporate Headquarters 104 Dawson Road Suite 100 Guelph, ON, Canada N1H 1A7 CANADA T: +1 (519) 826 5222 F: +1 (519) 826 5228 Netsweeper Whitepaper Deploying Netsweeper Internet Content
Netsweeper Inc. Corporate Headquarters 104 Dawson Road Suite 100 Guelph, ON, Canada N1H 1A7 CANADA T: +1 (519) 826 5222 F: +1 (519) 826 5228 Netsweeper Whitepaper Deploying Netsweeper Internet Content
Configuration Guide. BlackBerry Enterprise Service 12. Version 12.0
 Configuration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2014-12-19 SWD-20141219132902639 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12...
Configuration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2014-12-19 SWD-20141219132902639 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12...
Installing GFI MailEssentials
 Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
Installing GFI MailEssentials Introduction to installing GFI MailEssentials This chapter shows you how to install and configure GFI MailEssentials. GFI MailEssentials can be installed in two ways: Installation
OpenText Secure MFT Network and Firewall Requirements
 NETWORK OpenText Secure MFT Network and Firewall Requirements Secure MFT is a client-server solution that provides accelerated transfer of large files over any network connection. The solution architecture
NETWORK OpenText Secure MFT Network and Firewall Requirements Secure MFT is a client-server solution that provides accelerated transfer of large files over any network connection. The solution architecture
MARSHAL REPORTING CONSOLE VERSION 2.5 INSTALLATION GUIDE
 .trust MARSHAL REPORTING CONSOLE VERSION 2.5 INSTALLATION GUIDE wave.com Updated October 9, 2007 Table of Contents About This Document 2 1 Introduction 3 2 Supported Installation Types 3 2.1 Standalone
.trust MARSHAL REPORTING CONSOLE VERSION 2.5 INSTALLATION GUIDE wave.com Updated October 9, 2007 Table of Contents About This Document 2 1 Introduction 3 2 Supported Installation Types 3 2.1 Standalone
SolarWinds Log & Event Manager
 Corona Technical Services SolarWinds Log & Event Manager Training Project/Implementation Outline James Kluza 14 Table of Contents Overview... 3 Example Project Schedule... 3 Pre-engagement Checklist...
Corona Technical Services SolarWinds Log & Event Manager Training Project/Implementation Outline James Kluza 14 Table of Contents Overview... 3 Example Project Schedule... 3 Pre-engagement Checklist...
How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface
 How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface How To Configure load sharing and redirect mail server traffic over preferred Gateway
How To Load balance traffic of Mail server hosted in the Internal network and redirect traffic over preferred Interface How To Configure load sharing and redirect mail server traffic over preferred Gateway
SMTP POP3 SETUP FOR EMC DOCUMENTUM eroom
 White Paper SMTP POP3 SETUP FOR EMC DOCUMENTUM eroom Abstract This white paper explains how to setup SMTP POP3 on Internet Information Services (IIS). This guide also explains about how to install and
White Paper SMTP POP3 SETUP FOR EMC DOCUMENTUM eroom Abstract This white paper explains how to setup SMTP POP3 on Internet Information Services (IIS). This guide also explains about how to install and
Core Protection Suite
 Core Protection Suite Admin Guide Spam Soap, Inc. 3193 Red Hill Avenue Costa Mesa, CA 92626 United States p.866.spam.out f.949.203.6425 e. info@spamsoap.com www.spamsoap.com Contents EMAIL PROTECTION OVERVIEW...3
Core Protection Suite Admin Guide Spam Soap, Inc. 3193 Red Hill Avenue Costa Mesa, CA 92626 United States p.866.spam.out f.949.203.6425 e. info@spamsoap.com www.spamsoap.com Contents EMAIL PROTECTION OVERVIEW...3
Sage HRMS 2014 Sage Employee Self Service Tech Installation Guide for Windows 2003, 2008, and 2012. October 2013
 Sage HRMS 2014 Sage Employee Self Service Tech Installation Guide for Windows 2003, 2008, and 2012 October 2013 This is a publication of Sage Software, Inc. Document version: October 17, 2013 Copyright
Sage HRMS 2014 Sage Employee Self Service Tech Installation Guide for Windows 2003, 2008, and 2012 October 2013 This is a publication of Sage Software, Inc. Document version: October 17, 2013 Copyright
Course Syllabus. Fundamentals of Windows Server 2008 Network and Applications Infrastructure. Key Data. Audience. Prerequisites. At Course Completion
 Key Data Product #: 3380 Course #: 6420A Number of Days: 5 Format: Certification Exams: Instructor-Led None This course syllabus should be used to determine whether the course is appropriate for the students,
Key Data Product #: 3380 Course #: 6420A Number of Days: 5 Format: Certification Exams: Instructor-Led None This course syllabus should be used to determine whether the course is appropriate for the students,
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
What is the Barracuda SSL VPN Server Agent?
 The standard communication model for outgoing calls is for the appliance to simply make a direct connection to the destination host. This paradigm does not suit all business needs. The Barracuda SSL VPN
The standard communication model for outgoing calls is for the appliance to simply make a direct connection to the destination host. This paradigm does not suit all business needs. The Barracuda SSL VPN
Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123. Instructor Manual
 Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123 Instructor Manual Published: 2013-07-02 SWD-20130702091645092 Contents Advance preparation...7 Required materials...7 Topics
Troubleshooting BlackBerry Enterprise Service 10 version 10.1.1 726-08745-123 Instructor Manual Published: 2013-07-02 SWD-20130702091645092 Contents Advance preparation...7 Required materials...7 Topics
Configuration Guide BES12. Version 12.1
 Configuration Guide BES12 Version 12.1 Published: 2015-04-22 SWD-20150422113638568 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12... 8 Product documentation...
Configuration Guide BES12 Version 12.1 Published: 2015-04-22 SWD-20150422113638568 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12... 8 Product documentation...
Configuration Guide BES12. Version 12.2
 Configuration Guide BES12 Version 12.2 Published: 2015-07-07 SWD-20150630131852557 Contents About this guide... 8 Getting started... 9 Administrator permissions you need to configure BES12... 9 Obtaining
Configuration Guide BES12 Version 12.2 Published: 2015-07-07 SWD-20150630131852557 Contents About this guide... 8 Getting started... 9 Administrator permissions you need to configure BES12... 9 Obtaining
Copyright 2011 Sophos Ltd. Copyright strictly reserved. These materials are not to be reproduced, either in whole or in part, without permissions.
 PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
PureMessage for Microsoft Exchange protects Microsoft Exchange servers and Windows gateways against email borne threats such as from spam, phishing, viruses, spyware. In addition, it controls information
A Guide to Secure Email
 White Paper A Guide to Secure Email ABOUT THIS WHITE PAPER AND TARGET AUDIENCE This document is a whitepaper discussing the concept of secure email and the way in which M86 Security enables secure email
White Paper A Guide to Secure Email ABOUT THIS WHITE PAPER AND TARGET AUDIENCE This document is a whitepaper discussing the concept of secure email and the way in which M86 Security enables secure email
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 1.1 How the product works 3 1.2 Product contents 4 2. Deployment scenarios 5 2.1 Stand-alone
Network Configuration Settings
 Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Service Overview & Installation Guide
 Service Overview & Installation Guide Contents Contents... 2 1.0 Overview... 3 2.0 Simple Setup... 4 3.0 OWA Setup... 5 3.1 Receive Test... 5 3.2 Send Test... 6 4.0 Advanced Setup... 7 4.1 Receive Test
Service Overview & Installation Guide Contents Contents... 2 1.0 Overview... 3 2.0 Simple Setup... 4 3.0 OWA Setup... 5 3.1 Receive Test... 5 3.2 Send Test... 6 4.0 Advanced Setup... 7 4.1 Receive Test
Configuration Example
 Configuration Example Use Public IP Addresses Behind an XTM Device Example configuration files created with WSM v11.7.2 Revised 3/22/2013 Use Case There are several reasons to use publicly routable IP
Configuration Example Use Public IP Addresses Behind an XTM Device Example configuration files created with WSM v11.7.2 Revised 3/22/2013 Use Case There are several reasons to use publicly routable IP
The Bomgar Appliance in the Network
 The Bomgar Appliance in the Network The architecture of the Bomgar application environment relies on the Bomgar Appliance as a centralized routing point for all communications between application components.
The Bomgar Appliance in the Network The architecture of the Bomgar application environment relies on the Bomgar Appliance as a centralized routing point for all communications between application components.
escan SBS 2008 Installation Guide
 escan SBS 2008 Installation Guide Following things are required before starting the installation 1. On SBS 2008 server make sure you deinstall One Care before proceeding with installation of escan. 2.
escan SBS 2008 Installation Guide Following things are required before starting the installation 1. On SBS 2008 server make sure you deinstall One Care before proceeding with installation of escan. 2.
CORE Enterprise on a WAN
 CORE Enterprise on a WAN CORE Product and Process Engineering Solutions Copyright 2006-2007 Vitech Corporation. All rights reserved. No part of this document may be reproduced in any form, including, but
CORE Enterprise on a WAN CORE Product and Process Engineering Solutions Copyright 2006-2007 Vitech Corporation. All rights reserved. No part of this document may be reproduced in any form, including, but
WebMarshal User Guide
 WebMarshal User Guide Legal Notice Copyright 2014 Trustwave Holdings, Inc. All rights reserved. This document is protected by copyright and any distribution, reproduction, copying, or decompilation is
WebMarshal User Guide Legal Notice Copyright 2014 Trustwave Holdings, Inc. All rights reserved. This document is protected by copyright and any distribution, reproduction, copying, or decompilation is
WhatsUp Event Archiver v10 and v10.1 Quick Setup Guide
 WhatsUp Event Archiver v10 and v10.1 Quick Setup Guide Contents WhatsUp Event Archiver Quick Setup Guide WhatsUp Event Archiver Quick Setup Guide... 2 Installation Requirements... 3 Manually Creating Firewall
WhatsUp Event Archiver v10 and v10.1 Quick Setup Guide Contents WhatsUp Event Archiver Quick Setup Guide WhatsUp Event Archiver Quick Setup Guide... 2 Installation Requirements... 3 Manually Creating Firewall
602LAN SUITE 5.0 Groupware
 602LAN SUITE 5.0 Groupware Installation Manual 2007 Software602, Inc. 1 Table of Contents Table of Contents...2 Introduction...3 Prerequisites...4 Installation... 5 Server Configuration...7 Console...7
602LAN SUITE 5.0 Groupware Installation Manual 2007 Software602, Inc. 1 Table of Contents Table of Contents...2 Introduction...3 Prerequisites...4 Installation... 5 Server Configuration...7 Console...7
SSL VPN Technology White Paper
 SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
SSL VPN Technology White Paper Keywords: SSL VPN, HTTPS, Web access, TCP access, IP access Abstract: SSL VPN is an emerging VPN technology based on HTTPS. This document describes its implementation and
Configuration Guide BES12. Version 12.3
 Configuration Guide BES12 Version 12.3 Published: 2016-01-19 SWD-20160119132230232 Contents About this guide... 7 Getting started... 8 Configuring BES12 for the first time...8 Configuration tasks for managing
Configuration Guide BES12 Version 12.3 Published: 2016-01-19 SWD-20160119132230232 Contents About this guide... 7 Getting started... 8 Configuring BES12 for the first time...8 Configuration tasks for managing
VPN. Date: 4/15/2004 By: Heena Patel Email:hpatel4@stevens-tech.edu
 VPN Date: 4/15/2004 By: Heena Patel Email:hpatel4@stevens-tech.edu What is VPN? A VPN (virtual private network) is a private data network that uses public telecommunicating infrastructure (Internet), maintaining
VPN Date: 4/15/2004 By: Heena Patel Email:hpatel4@stevens-tech.edu What is VPN? A VPN (virtual private network) is a private data network that uses public telecommunicating infrastructure (Internet), maintaining
Deploying Layered Email Security. What is Layered Email Security?
 Deploying Layered Email Security This paper is intended for users of Websense Email Security who want to add Websense Hosted Email Security to deploy a layered email security solution. In this paper: Review
Deploying Layered Email Security This paper is intended for users of Websense Email Security who want to add Websense Hosted Email Security to deploy a layered email security solution. In this paper: Review
How To - Implement Clientless Single Sign On Authentication with Active Directory
 How To Implement Clientless Single Sign On in Single Active Directory Domain Controller Environment How To - Implement Clientless Single Sign On Authentication with Active Directory Applicable Version:
How To Implement Clientless Single Sign On in Single Active Directory Domain Controller Environment How To - Implement Clientless Single Sign On Authentication with Active Directory Applicable Version:
GFI Product Manual. Administration and Configuration Manual
 GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
GFI Product Manual Administration and Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and is provided "as is"
E-MAIL AND SERVER SECURITY
 E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
E-MAIL AND SERVER SECURITY DEPLOYMENT GUIDE 1 E-MAIL AND SERVER SECURITY Deployment Guide 2 CONTENTS 1. Overview 3 2. Deployment scenarios 5 2.1 Stand-alone server 5 2.2 Deploying the product with F-Secure
Netwrix Auditor for Exchange
 Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
Netwrix Auditor for Exchange Quick-Start Guide Version: 8.0 4/22/2016 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix
Interwise Connect. Working with Reverse Proxy Version 7.x
 Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Working with Reverse Proxy Version 7.x Table of Contents BACKGROUND...3 Single Sign On (SSO)... 3 Interwise Connect... 3 INTERWISE CONNECT WORKING WITH REVERSE PROXY...4 Architecture... 4 Interwise Web
Deploying ModusGate with Exchange Server. (Version 4.0+)
 Deploying ModusGate with Exchange Server (Version 4.0+) Active Directory and LDAP: Overview... 3 ModusGate/Exchange Server Deployment Strategies... 4 Basic Requirements for ModusGate & Exchange Server
Deploying ModusGate with Exchange Server (Version 4.0+) Active Directory and LDAP: Overview... 3 ModusGate/Exchange Server Deployment Strategies... 4 Basic Requirements for ModusGate & Exchange Server
Virtual Appliance Setup Guide
 The Barracuda SSL VPN Vx Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda SSL VPN hardware appliance. It is designed for easy deployment
The Barracuda SSL VPN Vx Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda SSL VPN hardware appliance. It is designed for easy deployment
Windows Server Update Services 3.0 SP2 Step By Step Guide
 Windows Server Update Services 3.0 SP2 Step By Step Guide Microsoft Corporation Author: Anita Taylor Editor: Theresa Haynie Abstract This guide provides detailed instructions for installing Windows Server
Windows Server Update Services 3.0 SP2 Step By Step Guide Microsoft Corporation Author: Anita Taylor Editor: Theresa Haynie Abstract This guide provides detailed instructions for installing Windows Server
FEATURE COMPARISON BETWEEN WINDOWS SERVER UPDATE SERVICES AND SHAVLIK HFNETCHKPRO
 FEATURE COMPARISON BETWEEN WINDOWS SERVER UPDATE SERVICES AND SHAVLIK HFNETCHKPRO Copyright 2005 Shavlik Technologies. All rights reserved. No part of this document may be reproduced or retransmitted in
FEATURE COMPARISON BETWEEN WINDOWS SERVER UPDATE SERVICES AND SHAVLIK HFNETCHKPRO Copyright 2005 Shavlik Technologies. All rights reserved. No part of this document may be reproduced or retransmitted in
Core Filtering Admin Guide
 Core Filtering Admin Guide 3193 Red Hill Avenue Costa Mesa, CA 92626 United States p.866.spam.out f.949.203.6425 e. info@spamsoap.com www.spamsoap.com Table of Contents Login... 3 Overview... 3 Quarantine...
Core Filtering Admin Guide 3193 Red Hill Avenue Costa Mesa, CA 92626 United States p.866.spam.out f.949.203.6425 e. info@spamsoap.com www.spamsoap.com Table of Contents Login... 3 Overview... 3 Quarantine...
Configuration Guide. BES12 Cloud
 Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Getting Started. Symantec Client Security. About Symantec Client Security. How to get started
 Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Getting Started Symantec Client Security About Security Security provides scalable, cross-platform firewall, intrusion prevention, and antivirus protection for workstations and antivirus protection for
Hardware Load Balancing for Optimal Microsoft Exchange Server 2010 Performance
 F5 White Paper Hardware Load Balancing for Optimal Microsoft Exchange Server 2010 Performance A comprehensive F5 solution readies application infrastructure for a successful implementation of the re-engineered
F5 White Paper Hardware Load Balancing for Optimal Microsoft Exchange Server 2010 Performance A comprehensive F5 solution readies application infrastructure for a successful implementation of the re-engineered
SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide
 SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide One of the typical usage cases for NowSMS is as an E-Mail to SMS & MMS Gateway. E-Mail users can send an SMS or MMS message by sending an e-mail
SME- Mail to SMS & MMS Gateway with NowSMS Quick Start Guide One of the typical usage cases for NowSMS is as an E-Mail to SMS & MMS Gateway. E-Mail users can send an SMS or MMS message by sending an e-mail
Many network and firewall administrators consider the network firewall at the network edge as their primary defense against all network woes.
 RimApp RoadBLOCK goes beyond simple filtering! Many network and firewall administrators consider the network firewall at the network edge as their primary defense against all network woes. However, traditional
RimApp RoadBLOCK goes beyond simple filtering! Many network and firewall administrators consider the network firewall at the network edge as their primary defense against all network woes. However, traditional
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
Step-by-Step Configuration Kerio Technologies C 2001-2003 Kerio Technologies. All Rights Reserved. Printing Date: December 17, 2003 This guide provides detailed description on configuration of the local
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Security Technology: Firewalls and VPNs
 Security Technology: Firewalls and VPNs 1 Learning Objectives Understand firewall technology and the various approaches to firewall implementation Identify the various approaches to remote and dial-up
Security Technology: Firewalls and VPNs 1 Learning Objectives Understand firewall technology and the various approaches to firewall implementation Identify the various approaches to remote and dial-up
MailMarshal SMTP 2006 Anti-Spam Technology
 MailMarshal SMTP 2006 Anti-Spam Technology August, 2006 Contents Introduction 2 Multi-layered spam detection and management 2 SpamCensor: Marshal s unique heuristic filter 2 URLCensor: Live URL blacklist
MailMarshal SMTP 2006 Anti-Spam Technology August, 2006 Contents Introduction 2 Multi-layered spam detection and management 2 SpamCensor: Marshal s unique heuristic filter 2 URLCensor: Live URL blacklist
Deployment Guide. For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php
 Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
TEAL: Transparent Email Archiving Library
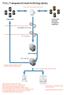 TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
TEAL: Transparent Email Archiving Library 1. Users send & receive email as per normal 2. Existing customer filters remove spam & viruses Filters (Spam, Anti-Virus) 3. Interceptor agent takes a copy of
SPAMfighter Mail Gateway
 SPAMfighter Mail Gateway User Manual Copyright (c) 2009 SPAMfighter ApS Revised 2009-05-19 1 Table of contents 1. Introduction...3 2. Basic idea...4 2.1 Detect-and-remove...4 2.2 Power-through-simplicity...4
SPAMfighter Mail Gateway User Manual Copyright (c) 2009 SPAMfighter ApS Revised 2009-05-19 1 Table of contents 1. Introduction...3 2. Basic idea...4 2.1 Detect-and-remove...4 2.2 Power-through-simplicity...4
Firewalls and VPNs. Principles of Information Security, 5th Edition 1
 Firewalls and VPNs Principles of Information Security, 5th Edition 1 Learning Objectives Upon completion of this material, you should be able to: Understand firewall technology and the various approaches
Firewalls and VPNs Principles of Information Security, 5th Edition 1 Learning Objectives Upon completion of this material, you should be able to: Understand firewall technology and the various approaches
Technical White Paper
 Instant APN Technical White Paper Introduction AccessMyLan Instant APN is a hosted service that provides access to a company network via an Access Point Name (APN) on the AT&T mobile network. Any device
Instant APN Technical White Paper Introduction AccessMyLan Instant APN is a hosted service that provides access to a company network via an Access Point Name (APN) on the AT&T mobile network. Any device
ALABAMA CENTRALIZED E-MAIL (ACE) PROJECT SUMMARY
 ALABAMA CENTRALIZED E-MAIL (ACE) PROJECT SUMMARY E-mail is a mission-critical application that business and government organizations expect to be secure, reliable and available at all times. The State
ALABAMA CENTRALIZED E-MAIL (ACE) PROJECT SUMMARY E-mail is a mission-critical application that business and government organizations expect to be secure, reliable and available at all times. The State
BlackBerry Enterprise Service 10. Version: 10.2. Configuration Guide
 BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
Configuring SMTP in Microsoft Exchange 2000 Server. Patricia Anderson Simon Attwell
 Configuring SMTP in Microsoft Exchange 2000 Server Patricia Anderson Simon Attwell Configuring SMTP in Microsoft Exchange 2000 Server Patricia Anderson Simon Attwell Copyright Information in this document,
Configuring SMTP in Microsoft Exchange 2000 Server Patricia Anderson Simon Attwell Configuring SMTP in Microsoft Exchange 2000 Server Patricia Anderson Simon Attwell Copyright Information in this document,
MCSA Objectives. Exam 70-236: TS:Exchange Server 2007, Configuring
 MCSA Objectives Exam 70-236: TS:Exchange Server 2007, Configuring Installing and Configuring Microsoft Exchange Servers Prepare the infrastructure for Exchange installation. Prepare the servers for Exchange
MCSA Objectives Exam 70-236: TS:Exchange Server 2007, Configuring Installing and Configuring Microsoft Exchange Servers Prepare the infrastructure for Exchange installation. Prepare the servers for Exchange
Sage HRMS 2012 Sage Employee Self Service. Technical Installation Guide for Windows Server 2003 and Windows Server 2008
 Sage HRMS 2012 Sage Employee Self Service Technical Installation Guide for Windows Server 2003 and Windows Server 2008 2011 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product
Sage HRMS 2012 Sage Employee Self Service Technical Installation Guide for Windows Server 2003 and Windows Server 2008 2011 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product
Example - Barracuda Network Access Client Configuration
 Example - Barracuda Network Access Client Configuration Introducing an active Barracuda Network Access Client environment involves several components, such as global objects, trustzone settings, Access
Example - Barracuda Network Access Client Configuration Introducing an active Barracuda Network Access Client environment involves several components, such as global objects, trustzone settings, Access
Fundamentals of Windows Server 2008 Network and Applications Infrastructure
 Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
Fundamentals of Windows Server 2008 Network and Applications Infrastructure MOC6420 About this Course This five-day instructor-led course introduces students to network and applications infrastructure
From SPAMfighter SMTP Anti Spam Server to SPAMfighter Mail Gateway
 From SPAMfighter SMTP Anti Spam Server to SPAMfighter Mail Gateway This guide will assist you in going from the SPAMfighter SMTP Anti Spam Server to the SPAMfighter Mail Gateway. It is strongly advised
From SPAMfighter SMTP Anti Spam Server to SPAMfighter Mail Gateway This guide will assist you in going from the SPAMfighter SMTP Anti Spam Server to the SPAMfighter Mail Gateway. It is strongly advised
CA Mobile Device Management 2014 Q1 Getting Started
 CA Mobile Device Management 2014 Q1 Getting Started This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is
CA Mobile Device Management 2014 Q1 Getting Started This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation ) is
Password Reset PRO INSTALLATION GUIDE
 Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
Netwrix Auditor. Administrator's Guide. Version: 7.1 10/30/2015
 Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
Netwrix Auditor Administrator's Guide Version: 7.1 10/30/2015 Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from Netwrix Corporation
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2. Administration Guide
 BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Administration Guide Published: 2010-06-16 SWDT487521-1041691-0616023638-001 Contents 1 Overview: BlackBerry Enterprise
BlackBerry Enterprise Server for Microsoft Exchange Version: 5.0 Service Pack: 2 Administration Guide Published: 2010-06-16 SWDT487521-1041691-0616023638-001 Contents 1 Overview: BlackBerry Enterprise
Panda Cloud Email Protection
 Panda Cloud Email Protection 1. Introduction a) What is spam? Spam is the term used to describe unsolicited messages or messages sent from unknown senders. They are usually sent in large (even massive)
Panda Cloud Email Protection 1. Introduction a) What is spam? Spam is the term used to describe unsolicited messages or messages sent from unknown senders. They are usually sent in large (even massive)
Introduction to the Mobile Access Gateway
 Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
msuite5 & mdesign Installation Prerequisites
 CommonTime Limited msuite5 & mdesign Installation Prerequisites Administration considerations prior to installing msuite5 and mdesign. 7/7/2011 Version 2.4 Overview... 1 msuite version... 1 SQL credentials...
CommonTime Limited msuite5 & mdesign Installation Prerequisites Administration considerations prior to installing msuite5 and mdesign. 7/7/2011 Version 2.4 Overview... 1 msuite version... 1 SQL credentials...
Installing GFI MailSecurity
 Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
Setting up Microsoft Office 365
 Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Setup Guide Revision F Using McAfee SaaS Email Protection to Secure Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
SKV PROPOSAL TO CLT FOR ACTIVE DIRECTORY AND DNS IMPLEMENTATION
 SKV PROPOSAL TO CLT FOR ACTIVE DIRECTORY AND DNS IMPLEMENTATION Date: April 22,2013 Prepared by: Sainath K.E.V Microsoft Most Valuable Professional Introduction: SKV Consulting is a Premier Consulting
SKV PROPOSAL TO CLT FOR ACTIVE DIRECTORY AND DNS IMPLEMENTATION Date: April 22,2013 Prepared by: Sainath K.E.V Microsoft Most Valuable Professional Introduction: SKV Consulting is a Premier Consulting
Setting up Microsoft Office 365
 Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding
 Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Introduction to the EIS Guide
 Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
XIA Configuration Server
 XIA Configuration Server XIA Configuration Server v7 Installation Quick Start Guide Monday, 05 January 2015 1 P a g e X I A C o n f i g u r a t i o n S e r v e r Contents Requirements... 3 XIA Configuration
XIA Configuration Server XIA Configuration Server v7 Installation Quick Start Guide Monday, 05 January 2015 1 P a g e X I A C o n f i g u r a t i o n S e r v e r Contents Requirements... 3 XIA Configuration
Figure 41-1 IP Filter Rules
 41. Firewall / IP Filter This function allows user to enable the functionality of IP filter. Both inside and outside packets through router could be decided to allow or drop by supervisor. Figure 41-1
41. Firewall / IP Filter This function allows user to enable the functionality of IP filter. Both inside and outside packets through router could be decided to allow or drop by supervisor. Figure 41-1
Dell - Secure Exchange Reference Architecture Dell White Paper
 Dell - Secure Exchange Reference Architecture Dell White Paper By Sumankumar Singh & Bharath Vasudevan 1 Summary Email has become a vital communication tool for most businesses. Whether in the office or
Dell - Secure Exchange Reference Architecture Dell White Paper By Sumankumar Singh & Bharath Vasudevan 1 Summary Email has become a vital communication tool for most businesses. Whether in the office or
MCSE SYLLABUS. Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003:
 MCSE SYLLABUS Course Contents : Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003: Managing Users, Computers and Groups. Configure access to shared folders. Managing and Maintaining
MCSE SYLLABUS Course Contents : Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003: Managing Users, Computers and Groups. Configure access to shared folders. Managing and Maintaining
E-mail Filter. SurfControl E-mail Filter 5.0 for SMTP Getting Started Guide. www.surfcontrol.com. The World s #1 Web & E-mail Filtering Company
 E-mail Filter SurfControl E-mail Filter 5.0 for SMTP Getting Started Guide www.surfcontrol.com The World s #1 Web & E-mail Filtering Company CONTENTS CONTENTS INTRODUCTION About This Document...2 Product
E-mail Filter SurfControl E-mail Filter 5.0 for SMTP Getting Started Guide www.surfcontrol.com The World s #1 Web & E-mail Filtering Company CONTENTS CONTENTS INTRODUCTION About This Document...2 Product
Microsoft Windows Server System White Paper
 Introduction to Network Access Protection Microsoft Corporation Published: June 2004, Updated: May 2006 Abstract Network Access Protection, a platform for Microsoft Windows Server "Longhorn" (now in beta
Introduction to Network Access Protection Microsoft Corporation Published: June 2004, Updated: May 2006 Abstract Network Access Protection, a platform for Microsoft Windows Server "Longhorn" (now in beta
F-Secure Internet Gatekeeper
 F-Secure Internet Gatekeeper TOC F-Secure Internet Gatekeeper Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper...5 1.1 Features...6 Chapter 2: Deployment...8 2.1 System requirements...9 2.2
F-Secure Internet Gatekeeper TOC F-Secure Internet Gatekeeper Contents Chapter 1: Welcome to F-Secure Internet Gatekeeper...5 1.1 Features...6 Chapter 2: Deployment...8 2.1 System requirements...9 2.2
PowerLink Bandwidth Aggregation Redundant WAN Link and VPN Fail-Over Solutions
 Bandwidth Aggregation Redundant WAN Link and VPN Fail-Over Solutions Find your network example: 1. Basic network with and 2 WAN lines - click here 2. Add a web server to the LAN - click here 3. Add a web,
Bandwidth Aggregation Redundant WAN Link and VPN Fail-Over Solutions Find your network example: 1. Basic network with and 2 WAN lines - click here 2. Add a web server to the LAN - click here 3. Add a web,
DeltaV System Health Monitoring Networking and Security
 DeltaV Distributed Control System White Paper DeltaV System Health Monitoring Networking and Security Introduction Emerson Process Management s DeltaV System Health Monitoring service enables you to proactively
DeltaV Distributed Control System White Paper DeltaV System Health Monitoring Networking and Security Introduction Emerson Process Management s DeltaV System Health Monitoring service enables you to proactively
