GSM Sniffing. Karsten Nohl, Sylvain Munaut,
|
|
|
- Louise Little
- 9 years ago
- Views:
Transcription
1 GSM Sniffing Karsten Nohl, Sylvain Munaut,
2 GSM networks are victim and source of attacks on user privacy SS7 Phone Base station GSM backend network User database (HLR) Attack vectors GUI attacks, phishing Malware Weak encryption No network authentication Over-the-air software installation (security is optional) Access to private user data Focus of this talk
3 Source: GSMA press statement GSM intercept is an engineering challenge the GSM call has to be identified and recorded from the radio interface. * + we strongly suspect the team developing the intercept approach has underestimated its practical complexity. A hacker would need a radio receiver system and the signal processing software necessary to process the raw radio data. GSMA, Aug. 09 This talk introduces cheap tools for capturing, decrypting and analyzing GSM calls and SMS
4 We will demonstrate how to find phones and decrypt their calls Attack input: Phone number OsmocomBB phones Silent SMS Rainbow tables HLR lookups Outputs: 1. Target location 2. Decrypted calls and SMS
5 Agenda Locating a phone Sniffing air traffic Cracking A5/1
6 Telcos do not authenticate each other but leak private user data The global SS7 network Telco Send SMS to your subscriber x Telco Telco Where in the world is your subscriber y Telco HLR query can be abused All telcos trust each other on the global SS7 network SS7 is abused for security and privacy attacks; currently for SMS spam
7 Information leaked through SS7 network disclose user location Query Accessible to Location granularity HLR query Anytime interrogation Anybody on the Internet Network operators General region (rural) to city part (urban) Cell ID: precise location -location granularity accessible from the Internet-
8 Our target phone is currently in Berlin Starting point: Target phone number 1 Find city and IMSI through HLR 2 Find LAC and TMSI: Probe each location area through silent (or broken) SMSs Demo 3 Find cell: Probe each cell in location area through SMSs
9 Agenda Locating a phone Sniffing air traffic Cracking A5/1
10 GSM calls are transmitted encrypted over unpredictable frequencies Beacon channel Phone, are you here? Yes, I am Ok, switch channel Downlink Uplink Encrypted Control channel Start encryption You are being called Switch to hopping channels OK OK Traffic channel Voice Voice Unpredictable hopping Voice Voice Voice Voice Voice Voice
11 GSM spectrum is divided by operators and cells GSM 900 brand Operator allocation One cell allocation Channels of one call 960 MHz 925 MHz 915 MHz Downlink Uplink Cell allocations and hopping sequences should be spread over the available spectrum for noise resistance and increased sniffing costs 880 MHz
12 GSM debugging tools have vastly different sepctrum coverage GSM 900 band Channels of one call GSM debugging tools [sniffing bandwidth] OsmocomBB [200 khz] USRP-1 [8MHz] USRP-2 [20MHz] Frequency coverage Commercial FPGA board [50 MHz] Downlink Uplink Focus of this talk
13 Even reprogrammed cheap phones can intercept hopping calls Start with a EUR 10 phone from 2006 You get: Upgrade to an open source firmware Patch DSP code to ignore encryption Add faster USB cable Remove uplink filter Debugger for your own calls Single timeslot sniffer Demo Multi timeslot sniffer Uplink + downlink sniffer
14 Agenda Locating a phone Sniffing air traffic Cracking A5/1
15 GSM uses symmetric A5/1 session keys for call privacy Operator and phone share a master key to derive session keys Random nonce Master key Hash function Session key Random nonce and session key Random nonce Communication A5/1- Operator Home Location Register Base station encrypted with session key Cell phone We extract this session keys
16 A5/1 s 64-bit keys are vulnerable to timememory trade-off attacks Start End A5/1 keys can be cracked with rainbow tables in seconds on a PC (details: 26C3 s talk GSM SRLY? ) Second generation rainbow tables is available through Bittorrent Distinguished points: Last 12 bits are zero 15
17 GSM packets are expanded and spread over four frames 23 byte message Forward error correction 57 byte redundant user data 114 bit burst 114 bit burst 114 bit burst 114 bit burst encryption encryption encryption encryption
18 Lots of GSM traffic is predictable providing known key stream Assignment Frame with known or guessable plaintext Very early Early Late Known Channel Unknown Channel Timing known through 1. Empty Ack after Assignment complete Mobile terminated calls Network terminated calls 2. Empty Ack after Alerting 3. Connect Acknowledge 4. Idle filling on SDCCH (multiple frames) 5. System Information 5+6 (~1/sec) 6. LAPDm traffic 1. Empty Ack after Cipher mode complete 2. Call proceeding 3. Alerting 4. Idle filling (multiple frames) 5. Connect 6. System Information 5+6 (~1/sec) 7. LAPDm Stealing bits Counting Counting frames Stealing bits Counting Source:GSM standards 17
19 Two phones are enough for targeted intercept Demo Plaintext SI msg. Encrypted SI msg. Kraken A5/1 cracker Encryption key Kc Phone 1 records control messages for target TMSI(s) Phone 2 hops on the same frequencies as target phone, records voice calls
20 Randomized padding makes control messages unpredictable to mitigate attacks SDCCH trace d b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b e 02 ea 81 5c b 2b 2b d 9f 6d b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b a a e 0d 02 d b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b 2b Padding in GSM has traditionally been predictable (2B) Every byte of randomized padding increasing attack cost by two orders of magnitude! Randomization was specified in 2008 (TS44.006) and should be implemented with high priority Additionally needed: randomization of system information messages 19
21 GSM network wish list 1. SMS home routing 2. Randomized padding 3. Rekeying before each call and SMS 4. Frequent TMSI changes 5. Frequency hopping
22 GSM should currently be used as an untrusted network, just like the Internet Threat Investment Scope Fake base station Passive intercept of voice + SMS Passive intercept of data Phone virus / malware Phishing Low Low Currently not possible Medium to high High Local Local Large Large Mitigation Mutual authentication & trust anchor Trust anchor Cell phone networks do not provide state-of-the art security. Protection must be embedded in the phones and locked away from malware.
23 Questions? GSM project supported by Rainbow tables, Airprobe, Kraken OsmocomBB firmware Karsten Nohl Sylvain Munaut srlabs.de osmocom.org
Karsten Nohl, [email protected]. Breaking GSM phone privacy
 arsten Nohl, [email protected] Breaking GSM phone privacy GSM is global, omnipresent and wants to be hacked 80% of mobile phone market 200+ countries 5 billion users! GSM encryption introduced in 1987
arsten Nohl, [email protected] Breaking GSM phone privacy GSM is global, omnipresent and wants to be hacked 80% of mobile phone market 200+ countries 5 billion users! GSM encryption introduced in 1987
Defending mobile phones. Karsten Nohl, [email protected] Luca Melette, [email protected]
 Defending mobile phones Karsten Nohl, [email protected] Luca Melette, [email protected] GSM networks provide the base for various attacks SS7 Phone Base station GSM backend network User database (HLR) Vulnerability
Defending mobile phones Karsten Nohl, [email protected] Luca Melette, [email protected] GSM networks provide the base for various attacks SS7 Phone Base station GSM backend network User database (HLR) Vulnerability
Evaluating GSM A5/1 security on hopping channels
 Evaluating GSM A5/1 security on hopping channels Bogdan Diaconescu v1.0 This paper is a practical approach on evaluating A5/1 stream cipher on a GSM hopping network air interface called Um. The end goal
Evaluating GSM A5/1 security on hopping channels Bogdan Diaconescu v1.0 This paper is a practical approach on evaluating A5/1 stream cipher on a GSM hopping network air interface called Um. The end goal
Mobile network security report: Poland
 Mobile network security report: Poland GSM Map Project [email protected] Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Poland GSM Map Project [email protected] Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Greece
 Mobile network security report: Greece GSM Map Project [email protected] Security Research Labs, Berlin October 2012 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Greece GSM Map Project [email protected] Security Research Labs, Berlin October 2012 Abstract. Mobile networks differ widely in their protection capabilities against common
GSM security country report: USA
 GSM security country report: USA GSM Map Project [email protected] Security Research Labs, Berlin August 2013 Abstract. GSM networks differ widely in their protection capabilities against common attacks.
GSM security country report: USA GSM Map Project [email protected] Security Research Labs, Berlin August 2013 Abstract. GSM networks differ widely in their protection capabilities against common attacks.
GSM security country report: Germany
 GSM security country report: Germany GSM Map Project [email protected] Security Research Labs, Berlin December 2013 Abstract. GSM networks differ widely in their protection capabilities against common attacks.
GSM security country report: Germany GSM Map Project [email protected] Security Research Labs, Berlin December 2013 Abstract. GSM networks differ widely in their protection capabilities against common attacks.
Mobile network security report: Belgium
 Mobile network security report: Belgium GSM Map Project [email protected] Security Research Labs, Berlin December 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Belgium GSM Map Project [email protected] Security Research Labs, Berlin December 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Germany
 Mobile network security report: Germany GSM Map Project [email protected] Security Research Labs, Berlin December 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Germany GSM Map Project [email protected] Security Research Labs, Berlin December 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Norway
 Mobile network security report: Norway GSM Map Project [email protected] Security Research Labs, Berlin August 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Norway GSM Map Project [email protected] Security Research Labs, Berlin August 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Karsten Nohl, Chris Paget 26C3, Berlin GSM SRSLY?
 Karsten Nohl, Chris Paget 26C3, Berlin GSM SRSLY? Summary: GSM Encryption needs to be shown insecure GSM is constantly under attack: A5/1 cipher shown insecure repeatedly Lack of network authentication
Karsten Nohl, Chris Paget 26C3, Berlin GSM SRSLY? Summary: GSM Encryption needs to be shown insecure GSM is constantly under attack: A5/1 cipher shown insecure repeatedly Lack of network authentication
GSM Research. Chair in Communication Systems Department of Applied Sciences University of Freiburg 2010
 Chair in Communication Systems Department of Applied Sciences University of Freiburg 2010 Dennis Wehrle, Konrad Meier, Dirk von Suchodoletz, Klaus Rechert, Gerhard Schneider Overview 1. GSM Infrastructure
Chair in Communication Systems Department of Applied Sciences University of Freiburg 2010 Dennis Wehrle, Konrad Meier, Dirk von Suchodoletz, Klaus Rechert, Gerhard Schneider Overview 1. GSM Infrastructure
Mobile network security report: Netherlands
 Mobile network security report: Netherlands GSM Map Project [email protected] Security Research Labs, Berlin July 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Netherlands GSM Map Project [email protected] Security Research Labs, Berlin July 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Poland
 Mobile network security report: Poland GSM Map Project [email protected] Security Research Labs, Berlin October 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Poland GSM Map Project [email protected] Security Research Labs, Berlin October 2014 Abstract. Mobile networks differ widely in their protection capabilities against common
Security of phone communications
 Security of phone communications Authentication, identification and mobile security Matej Kovačič (CC) 2015 This work is published under Creative Commons licence: AttributionNonCommercial-ShareAlike 2.5
Security of phone communications Authentication, identification and mobile security Matej Kovačič (CC) 2015 This work is published under Creative Commons licence: AttributionNonCommercial-ShareAlike 2.5
Mobile Security. Practical attacks using cheap equipment. Business France. Presented the 07/06/2016. For. By Sébastien Dudek
 Mobile Security Practical attacks using cheap equipment Presented the 07/06/2016 Business France By Sébastien Dudek For Content Security measures Recent publications in the hacking community Practical
Mobile Security Practical attacks using cheap equipment Presented the 07/06/2016 Business France By Sébastien Dudek For Content Security measures Recent publications in the hacking community Practical
GSM Channels. Physical & Logical Channels. Traffic and Control Mutltiframing. Frame Structure
 GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
Ch 2.3.3 GSM PENN. Magda El Zarki - Tcom 510 - Spring 98
 Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
SPYTEC 3000 The system for GSM communication monitoring
 SPYTEC 3000 The system for GSM communication monitoring The SPYTEC 3000 system is intended for passive (if system encryption is absent of if A5.2 encryption is used) or semi-active (if A5.1 encryption
SPYTEC 3000 The system for GSM communication monitoring The SPYTEC 3000 system is intended for passive (if system encryption is absent of if A5.2 encryption is used) or semi-active (if A5.1 encryption
Wireless Phone GSM tracking. Denis Foo Kune, John Koelndorfer, Nick Hopper, Yongdae Kim
 Wireless Phone GSM tracking Denis Foo Kune, John Koelndorfer, Nick Hopper, Yongdae Kim Can someone track your phone? GPS Need access to phone Cell network trilateration/triangulation Multiple base stations
Wireless Phone GSM tracking Denis Foo Kune, John Koelndorfer, Nick Hopper, Yongdae Kim Can someone track your phone? GPS Need access to phone Cell network trilateration/triangulation Multiple base stations
GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving
 GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving 1 Space Division Multiple Access of the signals from the MSs A BTS with n directed antennae covers mobile stations
GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving 1 Space Division Multiple Access of the signals from the MSs A BTS with n directed antennae covers mobile stations
GSM: PHYSICAL & LOGICAL CHANNELS
 GSM: PHYSICAL & LOGICAL CHANNELS AN OVERVIEW Prepared by Learntelecom.com 1. GSM: PHYSICAL AND LOGICAL CHANNELS GSM uses a mix of Frequency Division Multiple Access (FDMA) and Time Division Multiple Access
GSM: PHYSICAL & LOGICAL CHANNELS AN OVERVIEW Prepared by Learntelecom.com 1. GSM: PHYSICAL AND LOGICAL CHANNELS GSM uses a mix of Frequency Division Multiple Access (FDMA) and Time Division Multiple Access
Using TEMS Pocket. Johan Montelius
 Using TEMS Pocket Johan Montelius Introduction In this laboration you will get acquainted with the TEMS Pocket tool. You will examine both the Monaco network and a commercial network. Since this is your
Using TEMS Pocket Johan Montelius Introduction In this laboration you will get acquainted with the TEMS Pocket tool. You will examine both the Monaco network and a commercial network. Since this is your
GSM Databases. Virginia Location Area HLR Vienna Cell Virginia BSC. Virginia MSC VLR
 Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
Mobile self- defense. Karsten Nohl <[email protected]> SRLabs Template v12
 Mobile self- defense Karsten Nohl SRLabs Template v12 Agenda SS7 a0acks 3G security Self- defense opfons 2 SS7 network enables exchange of SMS and cryptographic keys Mobile operator Exchange
Mobile self- defense Karsten Nohl SRLabs Template v12 Agenda SS7 a0acks 3G security Self- defense opfons 2 SS7 network enables exchange of SMS and cryptographic keys Mobile operator Exchange
The GSM and GPRS network T-110.300/301
 The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
RADIUS. Brief brochure. Product Purpose
 Product Purpose The Product is designed for searching, intercepting, registering and analyzing of communication sessions as well as service information circulating in cellular GSM networks without encryption
Product Purpose The Product is designed for searching, intercepting, registering and analyzing of communication sessions as well as service information circulating in cellular GSM networks without encryption
GSM System. Global System for Mobile Communications
 GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
GSM Risks and Countermeasures
 GSM Risks and Countermeasures STI Group Discussion and Written Project Authors: Advisor: Johannes Ullrich Accepted: February 1, 2010 Abstract Recent research has shown that GSM encryption can be cracked
GSM Risks and Countermeasures STI Group Discussion and Written Project Authors: Advisor: Johannes Ullrich Accepted: February 1, 2010 Abstract Recent research has shown that GSM encryption can be cracked
Appendix C GSM System and Modulation Description
 C1 Appendix C GSM System and Modulation Description C1. Parameters included in the modelling In the modelling the number of mobiles and their positioning with respect to the wired device needs to be taken
C1 Appendix C GSM System and Modulation Description C1. Parameters included in the modelling In the modelling the number of mobiles and their positioning with respect to the wired device needs to be taken
12/3/08. Security in Wireless LANs and Mobile Networks. Wireless Magnifies Exposure Vulnerability. Mobility Makes it Difficult to Establish Trust
 Security in Wireless LANs and Mobile Networks Wireless Magnifies Exposure Vulnerability Information going across the wireless link is exposed to anyone within radio range RF may extend beyond a room or
Security in Wireless LANs and Mobile Networks Wireless Magnifies Exposure Vulnerability Information going across the wireless link is exposed to anyone within radio range RF may extend beyond a room or
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail
 CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
Frequency [MHz] ! " # $ %& &'( " Use top & bottom as additional guard. guard band. Giuseppe Bianchi DOWNLINK BS MS 890.4 UPLINK MS BS 890.2.
![Frequency [MHz] ! # $ %& &'( Use top & bottom as additional guard. guard band. Giuseppe Bianchi DOWNLINK BS MS 890.4 UPLINK MS BS 890.2. Frequency [MHz] ! # $ %& &'( Use top & bottom as additional guard. guard band. Giuseppe Bianchi DOWNLINK BS MS 890.4 UPLINK MS BS 890.2.](/thumbs/18/697237.jpg) Frequency [MHz] 960 DOWNLINK BS MS 935 915 UPLINK MS BS 890 890.4 890.2 guard band Use top & bottom as additional guard! " # $ %& &'( " 1 2 3 4 5 6 7 8 F F uplink dwlink ( n) = [ 890.2 + 0.2( n 1) ] (
Frequency [MHz] 960 DOWNLINK BS MS 935 915 UPLINK MS BS 890 890.4 890.2 guard band Use top & bottom as additional guard! " # $ %& &'( " 1 2 3 4 5 6 7 8 F F uplink dwlink ( n) = [ 890.2 + 0.2( n 1) ] (
How To Understand The Gsm And Mts Mobile Network Evolution
 Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Global System for Mobile Communications (GSM)
 Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE [email protected] UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE [email protected] UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Introduction to WiFi Security. Frank Sweetser WPI Network Operations and Security [email protected]
 Introduction to WiFi Security Frank Sweetser WPI Network Operations and Security [email protected] Why should I care? Or, more formally what are the risks? Unauthorized connections Stealing bandwidth Attacks
Introduction to WiFi Security Frank Sweetser WPI Network Operations and Security [email protected] Why should I care? Or, more formally what are the risks? Unauthorized connections Stealing bandwidth Attacks
Global System for Mobile Communication (GSM)
 Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
GSM - Global System for Mobile Communications
 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
CS263: Wireless Communications and Sensor Networks
 CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 4: Medium Access Control October 5, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Medium Access Control Schemes: FDMA TDMA
CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 4: Medium Access Control October 5, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Medium Access Control Schemes: FDMA TDMA
MAP/C SEND ROUTING INFO FOR SM. Destination Mobile Number. Obtain the SS7 address of the MSC VLR currently serving the specified Mobile Number
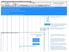 In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
Lecture Objectives. Lecture 8 Mobile Networks: Security in Wireless LANs and Mobile Networks. Agenda. References
 Lecture Objectives Wireless Networks and Mobile Systems Lecture 8 Mobile Networks: Security in Wireless LANs and Mobile Networks Introduce security vulnerabilities and defenses Describe security functions
Lecture Objectives Wireless Networks and Mobile Systems Lecture 8 Mobile Networks: Security in Wireless LANs and Mobile Networks Introduce security vulnerabilities and defenses Describe security functions
Chapter 6 Bandwidth Utilization: Multiplexing and Spreading 6.1
 Chapter 6 Bandwidth Utilization: Multiplexing and Spreading 6.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Note Bandwidth utilization is the wise use of
Chapter 6 Bandwidth Utilization: Multiplexing and Spreading 6.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. Note Bandwidth utilization is the wise use of
INTRODUCTION... 3 FREQUENCY HOPPING SPREAD SPECTRUM... 4 SECURED WIRELESS COMMUNICATION WITH AES ENCRYPTION... 6
 Technology Overview CONTENTS INTRODUCTION... 3 FREQUENCY HOPPING SPREAD SPECTRUM... 4 FULL TWO-WAY SYNCHRONIZED TDMA COMMUNICATION... 5 SECURED WIRELESS COMMUNICATION WITH AES ENCRYPTION... 6 UNMATCHED
Technology Overview CONTENTS INTRODUCTION... 3 FREQUENCY HOPPING SPREAD SPECTRUM... 4 FULL TWO-WAY SYNCHRONIZED TDMA COMMUNICATION... 5 SECURED WIRELESS COMMUNICATION WITH AES ENCRYPTION... 6 UNMATCHED
Worldwide attacks on SS7 network
 Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin ([email protected]) Alexandre De Oliveira ([email protected]) Agenda Overall telecom architecture Architecture
Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin ([email protected]) Alexandre De Oliveira ([email protected]) Agenda Overall telecom architecture Architecture
2G/3G Mobile Communication Systems
 2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
Karsten Nohl University of Virginia. Henryk Plötz HU Berlin
 Karsten Nohl University of Virginia Henryk Plötz HU Berlin Radio Frequency IDentification Tiny computer chips Passively Powered Karsten Nohl, Henryk Plötz - RFID Security 2 Constant monitoring is already
Karsten Nohl University of Virginia Henryk Plötz HU Berlin Radio Frequency IDentification Tiny computer chips Passively Powered Karsten Nohl, Henryk Plötz - RFID Security 2 Constant monitoring is already
Wireless LAN Security: Securing Your Access Point
 IJCSNS International Journal of Computer Science and Network Security, VOL.6 No.5B, May 2006 173 Wireless LAN Security: Securing Your Access Point Sia Sie Tung, Nurul Nadia Ahmad, Tan Kim Geok Faculty
IJCSNS International Journal of Computer Science and Network Security, VOL.6 No.5B, May 2006 173 Wireless LAN Security: Securing Your Access Point Sia Sie Tung, Nurul Nadia Ahmad, Tan Kim Geok Faculty
Wireless LANs vs. Wireless WANs
 White Paper Wireless LANs vs. Wireless WANs White Paper 2130273 Revision 1.0 Date 2002 November 18 Subject Supported Products Comparing Wireless LANs and Wireless WANs Wireless data cards and modules,
White Paper Wireless LANs vs. Wireless WANs White Paper 2130273 Revision 1.0 Date 2002 November 18 Subject Supported Products Comparing Wireless LANs and Wireless WANs Wireless data cards and modules,
GSM Network and Services
 GSM Network and Services GPRS - sharing of resources 1 What is the problem? Many data applications are very bursty in its traffic pattern: http, smtp, pop, telnet,... Why reserve physical resources at
GSM Network and Services GPRS - sharing of resources 1 What is the problem? Many data applications are very bursty in its traffic pattern: http, smtp, pop, telnet,... Why reserve physical resources at
Wireless Cellular Networks: 1G and 2G
 Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
Verint GI2. Gi2 Features. 2010 Verint Systems Inc. All rights reserved.
 Verint GI2 Gi2 Features 2010 Verint Systems Inc. All rights reserved. Channelyser Function The Channelyser allows the user to interrogate the local networks and display the Broadcast information. This
Verint GI2 Gi2 Features 2010 Verint Systems Inc. All rights reserved. Channelyser Function The Channelyser allows the user to interrogate the local networks and display the Broadcast information. This
WHITE PAPER. WEP Cloaking for Legacy Encryption Protection
 WHITE PAPER WEP Cloaking for Legacy TM Encryption Protection Introduction Wired Equivalent Privacy (WEP) is the encryption protocol defined in the original IEEE 802.11 standard for Wireless Local Area
WHITE PAPER WEP Cloaking for Legacy TM Encryption Protection Introduction Wired Equivalent Privacy (WEP) is the encryption protocol defined in the original IEEE 802.11 standard for Wireless Local Area
Authentication in WLAN
 Authentication in WLAN Flaws in WEP (Wired Equivalent Privacy) Wi-Fi Protected Access (WPA) Based on draft 3 of the IEEE 802.11i. Provides stronger data encryption and user authentication (largely missing
Authentication in WLAN Flaws in WEP (Wired Equivalent Privacy) Wi-Fi Protected Access (WPA) Based on draft 3 of the IEEE 802.11i. Provides stronger data encryption and user authentication (largely missing
Mobile Phone Network Security
 Mobile Phone Network Security Internet Security [1] VU Adrian Dabrowski, Markus Kammerstetter, Georg Merzdovnik, Stefan Riegler and Aljosha Judmayer [email protected] Mobile phone networks 1G
Mobile Phone Network Security Internet Security [1] VU Adrian Dabrowski, Markus Kammerstetter, Georg Merzdovnik, Stefan Riegler and Aljosha Judmayer [email protected] Mobile phone networks 1G
introduction to femtocells
 .. introduction to femtocells Kévin Redon Technische Universität Berlin, Security in Telecommunications [email protected] OsmoDevCon 2012, Berlin, 24th March 2012 UMTS architecture SecT
.. introduction to femtocells Kévin Redon Technische Universität Berlin, Security in Telecommunications [email protected] OsmoDevCon 2012, Berlin, 24th March 2012 UMTS architecture SecT
Lecture overview. History of cellular systems (1G) GSM introduction. Basic architecture of GSM system. Basic radio transmission parameters of GSM
 Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
Monitoring mobile communication network, how does it work? How to prevent such thing about that?
 Monitoring mobile communication network, how does it work? How to prevent such thing about that? 潘 維 亞 周 明 哲 劉 子 揚 (P78017058) (P48027049) (N96011156) 1 Contents How mobile communications work Why monitoring?
Monitoring mobile communication network, how does it work? How to prevent such thing about that? 潘 維 亞 周 明 哲 劉 子 揚 (P78017058) (P48027049) (N96011156) 1 Contents How mobile communications work Why monitoring?
Attenuation (amplitude of the wave loses strength thereby the signal power) Refraction Reflection Shadowing Scattering Diffraction
 Wireless Physical Layer Q1. Is it possible to transmit a digital signal, e.g., coded as square wave as used inside a computer, using radio transmission without any loss? Why? It is not possible to transmit
Wireless Physical Layer Q1. Is it possible to transmit a digital signal, e.g., coded as square wave as used inside a computer, using radio transmission without any loss? Why? It is not possible to transmit
Mobile Communications TCS 455
 Mobile Communications TCS 455 Dr. Prapun Suksompong [email protected] Lecture 26 1 Office Hours: BKD 3601-7 Tuesday 14:00-16:00 Thursday 9:30-11:30 Announcements Read the following from the SIIT online
Mobile Communications TCS 455 Dr. Prapun Suksompong [email protected] Lecture 26 1 Office Hours: BKD 3601-7 Tuesday 14:00-16:00 Thursday 9:30-11:30 Announcements Read the following from the SIIT online
(U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks
 (U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks Christos Xenakis, Christoforos Ntantogian, Orestis Panos Department of Digital Systems, University of Piraeus Piraeus, Greece
(U)SimMonitor: A Mobile Application for Security Evaluation of Cellular Networks Christos Xenakis, Christoforos Ntantogian, Orestis Panos Department of Digital Systems, University of Piraeus Piraeus, Greece
How to hack your way out of home detention
 How to hack your way out of home detention About me William @Amm0nRa Turner @Assurance Disclaimer: I own this system (and 0wn it) The following information is for academic purposes only Don t use this
How to hack your way out of home detention About me William @Amm0nRa Turner @Assurance Disclaimer: I own this system (and 0wn it) The following information is for academic purposes only Don t use this
Module 5. Broadcast Communication Networks. Version 2 CSE IIT, Kharagpur
 Module 5 Broadcast Communication Networks Lesson 9 Cellular Telephone Networks Specific Instructional Objectives At the end of this lesson, the student will be able to: Explain the operation of Cellular
Module 5 Broadcast Communication Networks Lesson 9 Cellular Telephone Networks Specific Instructional Objectives At the end of this lesson, the student will be able to: Explain the operation of Cellular
UMTS security. Helsinki University of Technology S-38.153 Security of Communication Protocols [email protected] 15.4.2003
 UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols [email protected] 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols [email protected] 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
Your 802.11 Wireless Network has No Clothes
 Your 802.11 Wireless Network has No Clothes William A. Arbaugh Narendar Shankar Y.C. Justin Wan Department of Computer Science University of Maryland College Park, Maryland 20742 March 30, 2001 Abstract
Your 802.11 Wireless Network has No Clothes William A. Arbaugh Narendar Shankar Y.C. Justin Wan Department of Computer Science University of Maryland College Park, Maryland 20742 March 30, 2001 Abstract
CSE331: Introduction to Networks and Security. Lecture 6 Fall 2006
 CSE331: Introduction to Networks and Security Lecture 6 Fall 2006 Open Systems Interconnection (OSI) End Host Application Reference model not actual implementation. Transmits messages (e.g. FTP or HTTP)
CSE331: Introduction to Networks and Security Lecture 6 Fall 2006 Open Systems Interconnection (OSI) End Host Application Reference model not actual implementation. Transmits messages (e.g. FTP or HTTP)
Security in IEEE 802.11 WLANs
 Security in IEEE 802.11 WLANs 1 IEEE 802.11 Architecture Extended Service Set (ESS) Distribution System LAN Segment AP 3 AP 1 AP 2 MS MS Basic Service Set (BSS) Courtesy: Prashant Krishnamurthy, Univ Pittsburgh
Security in IEEE 802.11 WLANs 1 IEEE 802.11 Architecture Extended Service Set (ESS) Distribution System LAN Segment AP 3 AP 1 AP 2 MS MS Basic Service Set (BSS) Courtesy: Prashant Krishnamurthy, Univ Pittsburgh
Theory and Practice. IT-Security: GSM Location System Syslog XP 3.7. Mobile Communication. December 18, 2001. GSM Location System Syslog XP 3.
 Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke [email protected] Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke [email protected] Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
9.1 Introduction. 9.2 Roaming
 9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
802.11 Security (WEP, WPA\WPA2) 19/05/2009. Giulio Rossetti Unipi [email protected]
 802.11 Security (WEP, WPA\WPA2) 19/05/2009 Giulio Rossetti Unipi [email protected] 802.11 Security Standard: WEP Wired Equivalent Privacy The packets are encrypted, before sent, with a Secret Key
802.11 Security (WEP, WPA\WPA2) 19/05/2009 Giulio Rossetti Unipi [email protected] 802.11 Security Standard: WEP Wired Equivalent Privacy The packets are encrypted, before sent, with a Secret Key
Authentication and Security in Mobile Phones
 Authentication and Security in Mobile Phones Greg Rose QUALCOMM Australia [email protected] ABSTRACT Mobile telephone systems have a checkered reputation regarding security and authentication features after
Authentication and Security in Mobile Phones Greg Rose QUALCOMM Australia [email protected] ABSTRACT Mobile telephone systems have a checkered reputation regarding security and authentication features after
Mobile Phone Security. Hoang Vo Billy Ngo
 Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
Chapter 6 CDMA/802.11i
 Chapter 6 CDMA/802.11i IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Some material copyright 1996-2012 J.F Kurose and K.W. Ross,
Chapter 6 CDMA/802.11i IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Some material copyright 1996-2012 J.F Kurose and K.W. Ross,
Provides a communication link between MS and MSC; Manages DB for MS location. Controls user connection. Transmission.
 Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
Key Hopping A Security Enhancement Scheme for IEEE 802.11 WEP Standards
 White Paper Key Hopping A Security Enhancement Scheme for IEEE 802.11 WEP Standards By Dr. Wen-Ping Ying, Director of Software Development, February 2002 Introduction Wireless LAN networking allows the
White Paper Key Hopping A Security Enhancement Scheme for IEEE 802.11 WEP Standards By Dr. Wen-Ping Ying, Director of Software Development, February 2002 Introduction Wireless LAN networking allows the
3GPP Wireless Standard
 3GPP Wireless Standard Shishir Pandey School of Technology and Computer Science TIFR, Mumbai April 10, 2009 Shishir Pandey (TIFR) 3GPP Wireless Standard April 10, 2009 1 / 23 3GPP Overview 3GPP : 3rd Generation
3GPP Wireless Standard Shishir Pandey School of Technology and Computer Science TIFR, Mumbai April 10, 2009 Shishir Pandey (TIFR) 3GPP Wireless Standard April 10, 2009 1 / 23 3GPP Overview 3GPP : 3rd Generation
SHORT MESSAGE SERVICE SECURITY
 SHORT MESSAGE SERVICE SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
SHORT MESSAGE SERVICE SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
GSM BASICS GSM HISTORY:
 GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
PwC. Outline. The case for wireless networking. Access points and network cards. Introduction: OSI layers and 802 structure
 PwC Outline Wireless LAN Security: Attacks and Countermeasures 1. Introduction 2. Problems with 802.11 security 3. Attacks on and risks to Wireless Networks 4. Defending wireless networks ISACA Hong Kong
PwC Outline Wireless LAN Security: Attacks and Countermeasures 1. Introduction 2. Problems with 802.11 security 3. Attacks on and risks to Wireless Networks 4. Defending wireless networks ISACA Hong Kong
LoRaWAN. What is it? A technical overview of LoRa and LoRaWAN. Technical Marketing Workgroup 1.0
 LoRaWAN What is it? A technical overview of LoRa and LoRaWAN Technical Marketing Workgroup 1.0 November 2015 TABLE OF CONTENTS 1. INTRODUCTION... 3 What is LoRa?... 3 Long Range (LoRa )... 3 2. Where does
LoRaWAN What is it? A technical overview of LoRa and LoRaWAN Technical Marketing Workgroup 1.0 November 2015 TABLE OF CONTENTS 1. INTRODUCTION... 3 What is LoRa?... 3 Long Range (LoRa )... 3 2. Where does
Content Teaching Academy at James Madison University
 Content Teaching Academy at James Madison University 1 2 The Battle Field: Computers, LANs & Internetworks 3 Definitions Computer Security - generic name for the collection of tools designed to protect
Content Teaching Academy at James Madison University 1 2 The Battle Field: Computers, LANs & Internetworks 3 Definitions Computer Security - generic name for the collection of tools designed to protect
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 6. Wireless Network Security
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 6 Wireless Network Security Objectives Overview of IEEE 802.11 wireless security Define vulnerabilities of Open System Authentication,
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 6 Wireless Network Security Objectives Overview of IEEE 802.11 wireless security Define vulnerabilities of Open System Authentication,
Wireless LAN Security Mechanisms
 Wireless LAN Security Mechanisms Jingan Xu, Andreas Mitschele-Thiel Technical University of Ilmenau, Integrated Hard- and Software Systems Group [email protected], [email protected] Abstract.
Wireless LAN Security Mechanisms Jingan Xu, Andreas Mitschele-Thiel Technical University of Ilmenau, Integrated Hard- and Software Systems Group [email protected], [email protected] Abstract.
Wireless Tools. Training materials for wireless trainers
 Wireless Tools Training materials for wireless trainers This talk covers tools that will show you a great deal of information about wireless networks, including network discovery, data logging, security
Wireless Tools Training materials for wireless trainers This talk covers tools that will show you a great deal of information about wireless networks, including network discovery, data logging, security
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu
 Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
SSL A discussion of the Secure Socket Layer
 www.harmonysecurity.com [email protected] SSL A discussion of the Secure Socket Layer By Stephen Fewer Contents 1 Introduction 2 2 Encryption Techniques 3 3 Protocol Overview 3 3.1 The SSL Record
www.harmonysecurity.com [email protected] SSL A discussion of the Secure Socket Layer By Stephen Fewer Contents 1 Introduction 2 2 Encryption Techniques 3 3 Protocol Overview 3 3.1 The SSL Record
Special Topics in Security and Privacy of Medical Information. Reminders. Medical device security. Sujata Garera
 Special Topics in Security and Privacy of Medical Information Sujata Garera Reminders Assignment due today Project part 1 due on next Tuesday Assignment 2 will be online today evening 2nd Discussion session
Special Topics in Security and Privacy of Medical Information Sujata Garera Reminders Assignment due today Project part 1 due on next Tuesday Assignment 2 will be online today evening 2nd Discussion session
Security in cellular-radio access networks
 Security in cellular-radio access networks Ravishankar Borgaonkar, Oxford University 5G Security Workshop Stockholm, Sweden 11 May 2016 Outline Radio Access Network Layered Security Emerging low cost attacks
Security in cellular-radio access networks Ravishankar Borgaonkar, Oxford University 5G Security Workshop Stockholm, Sweden 11 May 2016 Outline Radio Access Network Layered Security Emerging low cost attacks
Bluetooth voice and data performance in 802.11 DS WLAN environment
 1 (1) Bluetooth voice and data performance in 802.11 DS WLAN environment Abstract In this document, the impact of a 20dBm 802.11 Direct-Sequence WLAN system on a 0dBm Bluetooth link is studied. A typical
1 (1) Bluetooth voice and data performance in 802.11 DS WLAN environment Abstract In this document, the impact of a 20dBm 802.11 Direct-Sequence WLAN system on a 0dBm Bluetooth link is studied. A typical
EPL 657 Wireless Networks
 EPL 657 Wireless Networks Some fundamentals: Multiplexing / Multiple Access / Duplex Infrastructure vs Infrastructureless Panayiotis Kolios Recall: The big picture... Modulations: some basics 2 Multiplexing
EPL 657 Wireless Networks Some fundamentals: Multiplexing / Multiple Access / Duplex Infrastructure vs Infrastructureless Panayiotis Kolios Recall: The big picture... Modulations: some basics 2 Multiplexing
What is LOG Storm and what is it useful for?
 What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
Lab 7. Answer. Figure 1
 Lab 7 1. For each of the first 8 Ethernet frames, specify the source of the frame (client or server), determine the number of SSL records that are included in the frame, and list the SSL record types that
Lab 7 1. For each of the first 8 Ethernet frames, specify the source of the frame (client or server), determine the number of SSL records that are included in the frame, and list the SSL record types that
CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface
 CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface Hank Carter Professor Patrick Traynor 10/4/2012 UMTS and CDMA 3G technology - major change from GSM (TDMA) Based on techniques originally
CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface Hank Carter Professor Patrick Traynor 10/4/2012 UMTS and CDMA 3G technology - major change from GSM (TDMA) Based on techniques originally
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
HIPAA Security Considerations for Broadband Fixed Wireless Access Systems White Paper
 HIPAA Security Considerations for Broadband Fixed Wireless Access Systems White Paper Rev 1.0 HIPAA Security Considerations for Broadband Fixed Wireless Access Systems This white paper will investigate
HIPAA Security Considerations for Broadband Fixed Wireless Access Systems White Paper Rev 1.0 HIPAA Security Considerations for Broadband Fixed Wireless Access Systems This white paper will investigate
Forensic Identification of GSM Mobile Phones
 Forensic Identification of GSM Mobile Phones Jakob Hasse dence GmbH c/o Technische Universität Dresden [email protected] Thomas Gloe dence GmbH c/o Technische Universität Dresden [email protected]
Forensic Identification of GSM Mobile Phones Jakob Hasse dence GmbH c/o Technische Universität Dresden [email protected] Thomas Gloe dence GmbH c/o Technische Universität Dresden [email protected]
Attacking Automatic Wireless Network Selection. Dino A. Dai Zovi and Shane A. Macaulay {ddaizovi,smacaulay1}@bloomberg.com
 Attacking Automatic Wireless Network Selection Dino A. Dai Zovi and Shane A. Macaulay {ddaizovi,smacaulay1}@bloomberg.com We made Slashdot! Hackers, Meet Microsoft "The random chatter of several hundred
Attacking Automatic Wireless Network Selection Dino A. Dai Zovi and Shane A. Macaulay {ddaizovi,smacaulay1}@bloomberg.com We made Slashdot! Hackers, Meet Microsoft "The random chatter of several hundred
Network Security - ISA 656 Review
 Network Security - ISA 656 Review Angelos Stavrou December 4, 2007 Material Test Conditions 7:20pm - 9:30pm, Thursday, Dec 11th, in the Lab (STI-128) Same style of questions as the midterm I m not asking
Network Security - ISA 656 Review Angelos Stavrou December 4, 2007 Material Test Conditions 7:20pm - 9:30pm, Thursday, Dec 11th, in the Lab (STI-128) Same style of questions as the midterm I m not asking
