3M Cogent, Inc. White Paper. Facial Recognition. Biometric Technology. a 3M Company
|
|
|
- Dwight Fowler
- 7 years ago
- Views:
Transcription
1 3M Cogent, Inc. White Paper Facial Recognition Biometric Technology a 3M Company
2 Automated Facial Recognition: Turning Promise Into Reality Once the province of fiction, automated facial recognition has in just a few years emerged as more than a promise, but a distinct, doable reality. Over millions of years, the brain has evolved to immediately identify and focus on faces, distinguish features, and search our brain s database to match what we see with memories of previous faces. Teaching cameras and computers to process faces is the foundation of facial recognition technology: NIST Multiple Biometric Grand Challenge Identification and authentication can be made across a variety of contexts. As a no-touch system, all it requires for identification or authentication is that a person shows up. Existing monitoring and surveillance systems can be enhanced to automatically identify individuals. Unlike other biometrics, facial recognition is an ability all humans have, so operators can easily verify questionable matches. In December, 2008, just four years after it was released, the 3M Cogent Facial Recognition System squared off against the nine other industry-leading products in the National Institute of Standards and Technology Still Face Challenge Problem at the Multiple Biometric Grand Challenge (MBGC). 3M Cogent facial recognition software led in measured accuracy against all other vendors for both controlled and uncontrolled facial image comparisons. Even in adverse lighting, image, and pose conditions, the 3M Cogent algorithms consistently scored in the top tier for high accuracy (90+%) at a low false accept rate (.001%). Inherent Challenges Our brains find, process, and store face information with so little effort or attention that the sheer complexity of the task is hard to imagine. Translating that task into something a computer can do poses formidable obstacles: Faces have too much information human faces are highly complex patterns that differ in subtle ways, even more so than other biometrics, such as fingerprints and irises. Face information is too volatile our faces do not stay the same over time, altered as they are by age, weight, hairstyle, cosmetics, facial hair, paraphernalia, and transitory facial expressions. The information is a moving target images don t always capture the same face. Camera angle, lighting conditions, image quality, background, resolution, and partial images all produce different information sets, even for the same exact face. In recent NIST studies of facial recognition algorithms, most were easily overcome by these hurdles. Some software delivered false-reject rates of up to 43 percent using photos of subjects taken just 18 months apart. And a 45 degree angle rendered nearly all facial recognition systems helpless. If simply ducking one s head or making a face or just getting older is enough to frustrate the system, then facial recognition technology will require dramatic innovations to become reality. Making It Real The computational task is truly daunting. However, algorithms and software engineering are only half the problem. Facial Recognition Systems are also systems. They exist in the real world and, as such, they must: Integrate into existing information technology, security, and access control systems Work with legacy data and databases Adapt to meet the unique and evolving needs of disparate organizations Interface effectively with human operators Making automated facial recognition into a reality is more than just an abstract engineering problem ( can the system work? ), but a systems problem ( can the system work for us? ). 3M Cogent Facial Recognition Systems (FRS) 3M Cogent has leveraged more than 20 years of biometrics systems engineering to invent unique computational solutions that can match faces with unprecedented accuracy, in spite of a wide range of conditions and variations. The 3M Cogent FRS does not need perfect imaging conditions, but quickly adjusts and adapts to face or image changes without losing accuracy. 3M Cogent s Facial Recognition System involves more than just industry-leading facial recognition algorithms, but incorporates lessons from customizing biometric identification systems for all levels of government worldwide. 3M Cogent develops and builds the entire FRS system from algorithms to system integration to meet the unique requirements of each customer. Accurate, scalable, customizable, usable 3M Cogent s Facial Recognition Systems are turnkey solutions that allow organizations to focus resources on their core mission.
3 Seeing Faces The human brain brings millions of years of evolution to the task of seeing and identifying a face. Computers were engineered to see and process information in vastly different ways than the brain. For computers to see and identify human faces, several computational steps, each with unique and challenging obstacles, have to be successfully completed. Errors introduced in any stage accumulate, reducing the dependability of the final result. Step 1: Finding the Face Systems process numbers, so the first step in identifying and authenticating faces is to teach the computer to find the face in an image, a task much thornier than it sounds. Dark pigmentation, poor lighting, low resolution, facial paraphernalia, and camera angles can all hide a face mathematically. Where a person sees a face, a computer may see numbers indistinguishable from the background, unless sophisticated algorithms can compensate. Finding a face also means separating the face from the rest of the image and, in the case of video, tracking the face as it moves and changes from frame to frame. 3M Cogent technology employs sophisticated face-finding algorithms, able to accurately discover and isolate a face no matter what the person s race, camera angle, lighting, and other facehiding distractions. The software can then evaluate several images of the same face to find the most useful image for processing and matching. Step 2: Normalizing the Face Before any matching can take place, faces must be adjusted to present a common data set as defined in international (NIST) standards. To a human observer, this data set looks like a straighton, well-illuminated image of a forward-looking face, both eyes open, and undistorted by facial expressions or hidden by facial paraphernalia. Since not all face images are quite this perfect, the software must normalize the image. four steps to Seeing a Face Four Major Steps of Facial Recognition Step 4: Matching Faces The recognition part of automated facial recognition involves comparing the extracted data of an unknown face with the extracted data of known faces. The face data sets are compared, differences in data are identified, and, when the data are similar, a probability (score) is assigned that the data do, in fact, show the same face. The sophistication and accuracy of the earlier algorithms are critical to providing correct and comparable data. The completeness of the statistical analysis determines how dependable the final match really is. 3M Cogent facial matching algorithms have evolved from two decades of biometric sampling and matching research and development. 3M Cogent matching software uses unique statistical comparison and testing models from other proven biometric comparison products that achieve industry-leading accuracy in the final score. Step 3: Extracting Information Faces, even after normalization, are a mountain of data, but not all that data is necessary to correctly match face images. Feature extraction is the signal processing mathematics that 3M Cogent algorithms use to find and isolate the most useful numerical information in a face, information that best accounts for the variation between faces. Global, Local, and Point-Based Features 3M Cogent algorithms graph facial features across three data sets: 3M Cogent algorithms then perform mathematical transforms to translate the information into a set of relationships that can be most accurately and quickly compared with other face data sets. Once all images, including images in a database, have passed through these first three steps, the system is ready to match faces. Each of these three comparisons generates likely matches with similar images in the database. The 3M Cogent scoring algorithms are constantly refined through training the system both true and impostor results help teach the system by fine-tuning the scoring mechanism. Global as a graph mesh Local as groups of reference points Individual characteristic points Facial Recognition System Searching Workflow Score Fusion Using proprietary statistical models with lengthy and ongoing training with real-world results, the 3M Cogent algorithms calculate the overall likelihood that an individual face match can be made using the three sets of data. By remapping global, local, and point-based comparisons into a final matching score, score fusion powerfully reduces the deleterious effects of poor quality images, bad lighting, and the myriad of other variations that frustrate digital facial matching. Matching Modes 3M Cogent systems provide three modes for matching faces: 1:1 Matching Used primarily in access control or other security situations, 1:1 matching mode compares two face images to determine if the person in both images is the same person. 1:Few Matching Used to allow or disallow access, 1:Few matching uses a Watchlist module to compare a face image to a limited number of face images predetermined for identification. 1:N Matching The 1: N matching mode compares a face image against all images in a database. It allows for a centralized agency or inter-agency search and is fully scalable to meet an organization s evolving requirements.
4 Does it Work for You? Integration 3M Cogent systems are built using standardized languages and tools Service Oriented Architecture (SOA),.NET framework, and Oracle 11g database management to allow for efficient integration with existing systems, programs, and databases. With SOA, the 3M Cogent FRS can process ISO or ANSI/NIST-compliant transactions to/from existing, legacy biometric systems, including legacy facial recognition systems. Proven Biometric Solution The ultimate test of any Facial Recognition System is its usability as a complete solution. Just as the software must recognize variable and constantly changing faces, so the system has to be deployed across different organizations with disparate and ever-evolving requirements. 3M Cogent is continuously pushing the frontiers of facial recognition technology with innovative and customized products: Facial recognition-enabled mugshot management Available as part of a complete or standalone system, 3M Cogent s Mugshot System allows law enforcement personnel to securely access the mugshot database from a desk or crime scene and find mugshot matches using simple descriptions or digital images of the perpetrator. The 3M Cogent solution enables cost-effective and efficient integration with existing systems, high performance, adaptability, and ready usability by human operators and administrators. 3M Cogent biometric systems are designed to fit, adapt, and evolve to the needs of government and commercial organizations. In both software and hardware, 3M Cogent biometric systems scale linearly with the biometric matching and computing needs of the organization. 3M Cogent s Workflow Manager allows for rapid administrator customization of the system s workflow. Administrators can easily adapt the system to new business rules while maintaining legacy connectivity, thus minimizing risk and cost to the organization. ID document issuance For driver s licenses and other forms of government and commercial identification, 3M Cogent provides immediate face image capture, normalization, and 1:1 and 1:N identification. Personal PC facial recognition-enabled login 3M Cogent s BioTrust replaces unwieldy PC and Web password management with fingerprint or facial recognition biometrics. Using a PC s camera, BioTrust can store passwords and match the user s face to a predetermined image to log the user in to a computer or Web site. Built on two decades of innovative multiple biometrics systems experience, research, and industry leadership in everything from biometric input devices to software to the design and installation of distributed biometrics systems for business, government, and law enforcement agencies. 3M Cogent s facial recognition aces the ultimate test the real world test.
5 Security Systems Division 3M Cogent, Inc. 639 North Rosemead Boulevard Pasadena, CA U.S.A Please recycle. Printed in the U.S.A. 3M is a trademark of 3M. Cogent logo is a trademark of 3M Cogent. 3M Cogent, Inc v.πy All rights reserved. a 3M Company
SURVEILLANCE ENHANCED FACE RECOGNITION
 SURVEILLANCE ENHANCED FACE RECOGNITION BIOMETRICS Face Recognition Biometrics technology has matured rapidly over recent years, and the use of it for security and authentication purposes has become increasingly
SURVEILLANCE ENHANCED FACE RECOGNITION BIOMETRICS Face Recognition Biometrics technology has matured rapidly over recent years, and the use of it for security and authentication purposes has become increasingly
3M Cogent, Inc. White Paper. Beyond. Wiegand: Access Control. in the 21st Century. a 3M Company
 3M Cogent, Inc. White Paper Beyond Wiegand: Access Control in the 21st Century a 3M Company Unprecedented security features & capabilities Why Wiegand? The Problem with Wiegand In 1970, John Wiegand invented
3M Cogent, Inc. White Paper Beyond Wiegand: Access Control in the 21st Century a 3M Company Unprecedented security features & capabilities Why Wiegand? The Problem with Wiegand In 1970, John Wiegand invented
PRIME IDENTITY MANAGEMENT CORE
 PRIME IDENTITY MANAGEMENT CORE For secure enrollment applications processing and workflow management. PRIME Identity Management Core provides the foundation for any biometric identification platform. It
PRIME IDENTITY MANAGEMENT CORE For secure enrollment applications processing and workflow management. PRIME Identity Management Core provides the foundation for any biometric identification platform. It
Moving Service Management to SaaS Key Challenges and How Nimsoft Service Desk Helps Address Them
 Moving Service Management to SaaS Key Challenges and How Nimsoft Service Desk Helps Address Them Table of Contents Executive Summary... 3 Introduction: Opportunities of SaaS... 3 Introducing Nimsoft Service
Moving Service Management to SaaS Key Challenges and How Nimsoft Service Desk Helps Address Them Table of Contents Executive Summary... 3 Introduction: Opportunities of SaaS... 3 Introducing Nimsoft Service
Face Recognition: Some Challenges in Forensics. Anil K. Jain, Brendan Klare, and Unsang Park
 Face Recognition: Some Challenges in Forensics Anil K. Jain, Brendan Klare, and Unsang Park Forensic Identification Apply A l science i tto analyze data for identification Traditionally: Latent FP, DNA,
Face Recognition: Some Challenges in Forensics Anil K. Jain, Brendan Klare, and Unsang Park Forensic Identification Apply A l science i tto analyze data for identification Traditionally: Latent FP, DNA,
Multimodal Biometrics R&D Efforts to Exploit Biometric Transaction Management Systems
 Multimodal Biometrics R&D Efforts to Exploit Biometric Transaction Management Systems Erik J Bowman Principal Technologist Advanced Technology Group 24 September 2009 Agenda Problem Statements Research
Multimodal Biometrics R&D Efforts to Exploit Biometric Transaction Management Systems Erik J Bowman Principal Technologist Advanced Technology Group 24 September 2009 Agenda Problem Statements Research
Digital Identity & Authentication Directions Biometric Applications Who is doing what? Academia, Industry, Government
 Digital Identity & Authentication Directions Biometric Applications Who is doing what? Academia, Industry, Government Briefing W. Frisch 1 Outline Digital Identity Management Identity Theft Management
Digital Identity & Authentication Directions Biometric Applications Who is doing what? Academia, Industry, Government Briefing W. Frisch 1 Outline Digital Identity Management Identity Theft Management
RSA Adaptive Authentication For ecommerce
 RSA Adaptive Authentication For ecommerce Risk-based 3D Secure for Credit Card Issuers SOLUTION BRIEF RSA FRAUD & RISK INTELLIGENCE The Threat of ecommerce Fraud ecommerce fraud is a threat to both issuers
RSA Adaptive Authentication For ecommerce Risk-based 3D Secure for Credit Card Issuers SOLUTION BRIEF RSA FRAUD & RISK INTELLIGENCE The Threat of ecommerce Fraud ecommerce fraud is a threat to both issuers
Two-Factor Authentication over Mobile: Simplifying Security and Authentication
 SAP Thought Leadership Paper SAP Mobile Services Two-Factor Authentication over Mobile: Simplifying Security and Authentication Controlling Fraud and Validating End Users Easily and Cost-Effectively Table
SAP Thought Leadership Paper SAP Mobile Services Two-Factor Authentication over Mobile: Simplifying Security and Authentication Controlling Fraud and Validating End Users Easily and Cost-Effectively Table
Business-driven Policy Administration Transformation
 in collaboration with Business-driven Policy Administration Transformation Cost per policy analysis can help drive decisions for transforming policy administration systems Contents 1 Introduction 3 2 Challenges
in collaboration with Business-driven Policy Administration Transformation Cost per policy analysis can help drive decisions for transforming policy administration systems Contents 1 Introduction 3 2 Challenges
CA SiteMinder SSO Agents for ERP Systems
 PRODUCT SHEET: CA SITEMINDER SSO AGENTS FOR ERP SYSTEMS CA SiteMinder SSO Agents for ERP Systems CA SiteMinder SSO Agents for ERP Systems help organizations minimize sign-on requirements and increase security
PRODUCT SHEET: CA SITEMINDER SSO AGENTS FOR ERP SYSTEMS CA SiteMinder SSO Agents for ERP Systems CA SiteMinder SSO Agents for ERP Systems help organizations minimize sign-on requirements and increase security
Simply Sophisticated. Information Security and Compliance
 Simply Sophisticated Information Security and Compliance Simple Sophistication Welcome to Your New Strategic Advantage As technology evolves at an accelerating rate, risk-based information security concerns
Simply Sophisticated Information Security and Compliance Simple Sophistication Welcome to Your New Strategic Advantage As technology evolves at an accelerating rate, risk-based information security concerns
Setting the Record Straight About Cloud-Based Contact Centers
 Setting the Record Straight About Cloud-Based Contact Centers September 2012 Sponsored by: - 1-2012 DMG Consulting LLC Table of Contents Introduction... 1 Cloud-Based Solutions Are Secure... 1 Cloud-Based
Setting the Record Straight About Cloud-Based Contact Centers September 2012 Sponsored by: - 1-2012 DMG Consulting LLC Table of Contents Introduction... 1 Cloud-Based Solutions Are Secure... 1 Cloud-Based
White Paper Think BIG
 White Paper Think BIG Fusion of Biometric and Biographic Data In Large-Scale Identification Projects WCC is a global leader in search and match technology with a market leading platform for identification
White Paper Think BIG Fusion of Biometric and Biographic Data In Large-Scale Identification Projects WCC is a global leader in search and match technology with a market leading platform for identification
Benefits of Standardizing the Video Security System
 SALIENT SYSTEMS WHITE PAPER Benefits of Standardizing the Video Security System Salient Systems Corp. 10801 N. MoPac Exp. Building 3, Suite 700 Austin, TX 78759 Phone: (512) 617-4800 For a variety of reasons
SALIENT SYSTEMS WHITE PAPER Benefits of Standardizing the Video Security System Salient Systems Corp. 10801 N. MoPac Exp. Building 3, Suite 700 Austin, TX 78759 Phone: (512) 617-4800 For a variety of reasons
MORPHO CRIMINAL JUSTICE SUITE
 MORPHO CRIMINAL JUSTICE SUITE FULL RANGE OF PRODUCTS DEDICATED TO CRIMINAL JUSTICE MISSIONS 2 1 3 Morpho provides law enforcement with a wide range of products to support criminal investigation, background
MORPHO CRIMINAL JUSTICE SUITE FULL RANGE OF PRODUCTS DEDICATED TO CRIMINAL JUSTICE MISSIONS 2 1 3 Morpho provides law enforcement with a wide range of products to support criminal investigation, background
Reduce Medical Loss Ratio by Straight-Through-Processing with Oracle Health Insurance Components ORACLE WHITE PAPER JULY 2015
 Reduce Medical Loss Ratio by Straight-Through-Processing with Oracle Health Insurance Components ORACLE WHITE PAPER JULY 2015 Table of Contents Introduction 1 Business Agility 2 Risk-Based Intervention
Reduce Medical Loss Ratio by Straight-Through-Processing with Oracle Health Insurance Components ORACLE WHITE PAPER JULY 2015 Table of Contents Introduction 1 Business Agility 2 Risk-Based Intervention
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE
 IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
Select the right configuration management database to establish a platform for effective service management.
 Service management solutions Buyer s guide: purchasing criteria Select the right configuration management database to establish a platform for effective service management. All business activities rely
Service management solutions Buyer s guide: purchasing criteria Select the right configuration management database to establish a platform for effective service management. All business activities rely
EMC CAPTIVA SOLUTIONS FOR HEALTHCARE
 EMC CAPTIVA SOLUTIONS FOR HEALTHCARE Major advances in medical technology within the last several years have led members of an aging population to significantly raise expectations for the quality of care
EMC CAPTIVA SOLUTIONS FOR HEALTHCARE Major advances in medical technology within the last several years have led members of an aging population to significantly raise expectations for the quality of care
The Hidden Value of Enterprise Content Management Deliver business value by leveraging information
 The Hidden Value of Enterprise Content Management Deliver business value by leveraging information Introduction Enterprise Content Management (ECM) provides new information management tools, strategies
The Hidden Value of Enterprise Content Management Deliver business value by leveraging information Introduction Enterprise Content Management (ECM) provides new information management tools, strategies
Long Term Evolution (LTE) for Public Safety
 S T R A T E G I C W H I T E P A P E R Long Term Evolution (LTE) for Public Safety Enabling Flexible Business Models To provide seamless data communication during emergencies, public safety practitioners
S T R A T E G I C W H I T E P A P E R Long Term Evolution (LTE) for Public Safety Enabling Flexible Business Models To provide seamless data communication during emergencies, public safety practitioners
Data Discovery, Analytics, and the Enterprise Data Hub
 Data Discovery, Analytics, and the Enterprise Data Hub Version: 101 Table of Contents Summary 3 Used Data and Limitations of Legacy Analytic Architecture 3 The Meaning of Data Discovery & Analytics 4 Machine
Data Discovery, Analytics, and the Enterprise Data Hub Version: 101 Table of Contents Summary 3 Used Data and Limitations of Legacy Analytic Architecture 3 The Meaning of Data Discovery & Analytics 4 Machine
How To Create An Insight Analysis For Cyber Security
 IBM i2 Enterprise Insight Analysis for Cyber Analysis Protect your organization with cyber intelligence Highlights Quickly identify threats, threat actors and hidden connections with multidimensional analytics
IBM i2 Enterprise Insight Analysis for Cyber Analysis Protect your organization with cyber intelligence Highlights Quickly identify threats, threat actors and hidden connections with multidimensional analytics
WHITE PAPER OCTOBER 2014. Unified Monitoring. A Business Perspective
 WHITE PAPER OCTOBER 2014 Unified Monitoring A Business Perspective 2 WHITE PAPER: UNIFIED MONITORING ca.com Table of Contents Introduction 3 Section 1: Today s Emerging Computing Environments 4 Section
WHITE PAPER OCTOBER 2014 Unified Monitoring A Business Perspective 2 WHITE PAPER: UNIFIED MONITORING ca.com Table of Contents Introduction 3 Section 1: Today s Emerging Computing Environments 4 Section
Usable Multi-Factor Authentication and Risk- Based Authorization
 CYBER SECURITY DIVISION 2014 R&D SHOWCASE AND TECHNICAL WORKSHOP Usable Multi-Factor Authentication and Risk- Based Authorization IBM T.J. Watson Research Center Larry Koved December 18, 2014 Team Profile
CYBER SECURITY DIVISION 2014 R&D SHOWCASE AND TECHNICAL WORKSHOP Usable Multi-Factor Authentication and Risk- Based Authorization IBM T.J. Watson Research Center Larry Koved December 18, 2014 Team Profile
Security, Reliability, Scalability
 AT&T enterprise hosting services AT&T Enterprise Hosting Services Security, Reliability, Scalability and Global Reach For Mission Critical and Resource-Intensive e-business Applications Benefits Flexible
AT&T enterprise hosting services AT&T Enterprise Hosting Services Security, Reliability, Scalability and Global Reach For Mission Critical and Resource-Intensive e-business Applications Benefits Flexible
Adopting Agile Testing
 Adopting Agile Testing A Borland Agile Testing White Paper August 2012 Executive Summary More and more companies are adopting Agile methods as a flexible way to introduce new software products. An important
Adopting Agile Testing A Borland Agile Testing White Paper August 2012 Executive Summary More and more companies are adopting Agile methods as a flexible way to introduce new software products. An important
Biometrics in Physical Access Control Issues, Status and Trends White Paper
 Biometrics in Physical Access Control Issues, Status and Trends White Paper Authored and Presented by: Bill Spence, Recognition Systems, Inc. SIA Biometrics Industry Group Vice-Chair & SIA Biometrics Industry
Biometrics in Physical Access Control Issues, Status and Trends White Paper Authored and Presented by: Bill Spence, Recognition Systems, Inc. SIA Biometrics Industry Group Vice-Chair & SIA Biometrics Industry
Accenture Duck Creek Driving efficiency and high performance through Property & Casualty insurance software
 Driving efficiency and high performance through Property & Casualty insurance software World-class software is a critical component to business success for high performing companies. Finding the best software
Driving efficiency and high performance through Property & Casualty insurance software World-class software is a critical component to business success for high performing companies. Finding the best software
Relational Databases in the Cloud
 Contact Information: February 2011 zimory scale White Paper Relational Databases in the Cloud Target audience CIO/CTOs/Architects with medium to large IT installations looking to reduce IT costs by creating
Contact Information: February 2011 zimory scale White Paper Relational Databases in the Cloud Target audience CIO/CTOs/Architects with medium to large IT installations looking to reduce IT costs by creating
W.A.R.N. Passive Biometric ID Card Solution
 W.A.R.N. Passive Biometric ID Card Solution Updated November, 2007 Biometric technology has advanced so quickly in the last decade that questions and facts about its cost, use, and accuracy are often confused
W.A.R.N. Passive Biometric ID Card Solution Updated November, 2007 Biometric technology has advanced so quickly in the last decade that questions and facts about its cost, use, and accuracy are often confused
Data Center Fabrics and Their Role in Managing the Big Data Trend
 Data Center Fabrics and Their Role in Managing the Big Data Trend The emergence of Big Data as a critical technology initiative is one of the driving factors forcing IT decision-makers to explore new alternatives
Data Center Fabrics and Their Role in Managing the Big Data Trend The emergence of Big Data as a critical technology initiative is one of the driving factors forcing IT decision-makers to explore new alternatives
Facial Comparison and FBI Identification Training
 Facial Comparison and FBI Identification Training Module 1: Introduction to the FBI Face Training Program This work product is solely the product of the FBI. It was created for educational purposes only.
Facial Comparison and FBI Identification Training Module 1: Introduction to the FBI Face Training Program This work product is solely the product of the FBI. It was created for educational purposes only.
Leveraging innovative security solutions for government. Helping to protect government IT infrastructure, meet compliance demands and reduce costs
 IBM Global Technology Services Leveraging innovative security solutions for government. Helping to protect government IT infrastructure, meet compliance demands and reduce costs Achieving a secure government
IBM Global Technology Services Leveraging innovative security solutions for government. Helping to protect government IT infrastructure, meet compliance demands and reduce costs Achieving a secure government
How can Content Aware Identity and Access Management give me the control I need to confidently move my business forward?
 SOLUTION BRIEF Content Aware Identity and Access Management May 2010 How can Content Aware Identity and Access Management give me the control I need to confidently move my business forward? we can CA Content
SOLUTION BRIEF Content Aware Identity and Access Management May 2010 How can Content Aware Identity and Access Management give me the control I need to confidently move my business forward? we can CA Content
Is Your Identity Management Program Protecting Your Federal Systems?
 Is Your Identity Management Program Protecting Your Federal Systems? With the increase in integrated, cloud and remote technologies, it is more challenging than ever for federal government agencies to
Is Your Identity Management Program Protecting Your Federal Systems? With the increase in integrated, cloud and remote technologies, it is more challenging than ever for federal government agencies to
Insurance Technology Solutions. Mindteck. Maximizing Business Value with Efficient IT Services
 Mindteck Maximizing Business Value with Efficient IT Services 1 The Insurance business environment is characterized by the ability of a company to adapt and keep pace with market changes and technological
Mindteck Maximizing Business Value with Efficient IT Services 1 The Insurance business environment is characterized by the ability of a company to adapt and keep pace with market changes and technological
Two-Factor Authentication
 Two-Factor Authentication A Total Cost of Ownership Viewpoint CONTENTS + Two-Factor Authentication 3 A Total Cost of Ownership Viewpoint + Introduction 3 + Defining Total Cost of Ownership 3 + VeriSign
Two-Factor Authentication A Total Cost of Ownership Viewpoint CONTENTS + Two-Factor Authentication 3 A Total Cost of Ownership Viewpoint + Introduction 3 + Defining Total Cost of Ownership 3 + VeriSign
How can Identity and Access Management help me to improve compliance and drive business performance?
 SOLUTION BRIEF: IDENTITY AND ACCESS MANAGEMENT (IAM) How can Identity and Access Management help me to improve compliance and drive business performance? CA Identity and Access Management automates the
SOLUTION BRIEF: IDENTITY AND ACCESS MANAGEMENT (IAM) How can Identity and Access Management help me to improve compliance and drive business performance? CA Identity and Access Management automates the
Driving the Business Forward with Human Capital Management. Five key points to consider before you invest
 Driving the Business Forward with Human Capital Management Five key points to consider before you invest For HR leaders to contribute to the business successfully, they need HR solutions with the right
Driving the Business Forward with Human Capital Management Five key points to consider before you invest For HR leaders to contribute to the business successfully, they need HR solutions with the right
An Oracle White Paper December 2010. Leveraging Oracle Enterprise Single Sign-On Suite Plus to Achieve HIPAA Compliance
 An Oracle White Paper December 2010 Leveraging Oracle Enterprise Single Sign-On Suite Plus to Achieve HIPAA Compliance Executive Overview... 1 Health Information Portability and Accountability Act Security
An Oracle White Paper December 2010 Leveraging Oracle Enterprise Single Sign-On Suite Plus to Achieve HIPAA Compliance Executive Overview... 1 Health Information Portability and Accountability Act Security
Line of Business Solutions Complement Large Scale Postmodern ERP Deployment Strategies by Cultura Technologies
 Line of Business Solutions Complement Large Scale Postmodern ERP Deployment Strategies by Cultura Technologies Executive Summary Highly specialized Line of Business (LOB) solutions, such as AGRIS and CINCH,
Line of Business Solutions Complement Large Scale Postmodern ERP Deployment Strategies by Cultura Technologies Executive Summary Highly specialized Line of Business (LOB) solutions, such as AGRIS and CINCH,
Oracle Data Integrator and Oracle Warehouse Builder Statement of Direction
 First Published January 2010 Updated May 2011 Oracle Data Integrator and Oracle Warehouse Builder Statement of Direction Disclaimer This document in any form, software or printed matter, contains proprietary
First Published January 2010 Updated May 2011 Oracle Data Integrator and Oracle Warehouse Builder Statement of Direction Disclaimer This document in any form, software or printed matter, contains proprietary
WHITE PAPER. Five Steps to Better Application Monitoring and Troubleshooting
 WHITE PAPER Five Steps to Better Application Monitoring and Troubleshooting There is no doubt that application monitoring and troubleshooting will evolve with the shift to modern applications. The only
WHITE PAPER Five Steps to Better Application Monitoring and Troubleshooting There is no doubt that application monitoring and troubleshooting will evolve with the shift to modern applications. The only
An Introduction to Cryptography and Digital Signatures
 An Introduction to Cryptography and Digital Signatures Author: Ian Curry March 2001 Version 2.0 Copyright 2001-2003 Entrust. All rights reserved. Cryptography The concept of securing messages through
An Introduction to Cryptography and Digital Signatures Author: Ian Curry March 2001 Version 2.0 Copyright 2001-2003 Entrust. All rights reserved. Cryptography The concept of securing messages through
ITIL V3: Making Business Services Serve the Business
 ITIL V3: Making Business Services Serve the Business An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for ASG October 2008 IT Management Research, Industry Analysis, and Consulting Table
ITIL V3: Making Business Services Serve the Business An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for ASG October 2008 IT Management Research, Industry Analysis, and Consulting Table
Unified Communications-as-a-Service (UCaaS) for Video Conferencing
 Unified Communications-as-a-Service (UCaaS) for Video Conferencing The proliferation of technology at a consumer level has been empowering. Laptops, tablets and smart phones now come equipped with extensive
Unified Communications-as-a-Service (UCaaS) for Video Conferencing The proliferation of technology at a consumer level has been empowering. Laptops, tablets and smart phones now come equipped with extensive
ONE PLATFORM FOR ALL YOUR PRINT, SCAN, AND DEVICE MANAGEMENT
 ONE PLATFORM FOR ALL YOUR PRINT, SCAN, AND DEVICE MANAGEMENT MANAGE ALL PRINTING & SCANNING WITH ONE SINGLE PLATFORM Incorporating uniflow into your document processes will lead to real improvements in
ONE PLATFORM FOR ALL YOUR PRINT, SCAN, AND DEVICE MANAGEMENT MANAGE ALL PRINTING & SCANNING WITH ONE SINGLE PLATFORM Incorporating uniflow into your document processes will lead to real improvements in
Revolutionize Testing With Agile Design Environment
 Revolutionize Testing With Agile Design Environment GAIN OPERATIONAL EFFICIENCY WITH CASTLE WORLDWIDE S ITEM AUTHORING AND MANAGEMENT PLATFORM Copyright 2011 Castle Worldwide Inc. All Rights Reserved.
Revolutionize Testing With Agile Design Environment GAIN OPERATIONAL EFFICIENCY WITH CASTLE WORLDWIDE S ITEM AUTHORING AND MANAGEMENT PLATFORM Copyright 2011 Castle Worldwide Inc. All Rights Reserved.
The Re-emergence of Data Capture Technology
 The Re-emergence of Data Capture Technology Understanding Today s Digital Capture Solutions Digital capture is a key enabling technology in a business world striving to balance the shifting advantages
The Re-emergence of Data Capture Technology Understanding Today s Digital Capture Solutions Digital capture is a key enabling technology in a business world striving to balance the shifting advantages
Mobile Driver s License Solution
 Mobile Driver s License Solution Secure, convenient and more efficient Improved identity protection through secure mobile driver s licenses The introduction of a mobile driver s license is a huge opportunity
Mobile Driver s License Solution Secure, convenient and more efficient Improved identity protection through secure mobile driver s licenses The introduction of a mobile driver s license is a huge opportunity
Increasing customer satisfaction and reducing costs in property and casualty insurance
 Increasing customer satisfaction and reducing costs in property and casualty insurance Contents: 1 Optimizing claim handling 2 Improve claim handling with real-time risk assessment 3 How do predictive
Increasing customer satisfaction and reducing costs in property and casualty insurance Contents: 1 Optimizing claim handling 2 Improve claim handling with real-time risk assessment 3 How do predictive
WHITE PAPER: STRATEGIC IMPACT PILLARS FOR EFFICIENT MIGRATION TO CLOUD COMPUTING IN GOVERNMENT
 WHITE PAPER: STRATEGIC IMPACT PILLARS FOR EFFICIENT MIGRATION TO CLOUD COMPUTING IN GOVERNMENT IntelliDyne, LLC MARCH 2012 STRATEGIC IMPACT PILLARS FOR EFFICIENT MIGRATION TO CLOUD COMPUTING IN GOVERNMENT
WHITE PAPER: STRATEGIC IMPACT PILLARS FOR EFFICIENT MIGRATION TO CLOUD COMPUTING IN GOVERNMENT IntelliDyne, LLC MARCH 2012 STRATEGIC IMPACT PILLARS FOR EFFICIENT MIGRATION TO CLOUD COMPUTING IN GOVERNMENT
Federation and a CMDB
 BEST PRACTICES WHITE PAPER Client Solutions BSM e: bsm@clients.ie t: 01 620 4000 w: www.clients.ie/bsm Federation and a CMDB Table of Contents EXECUTIVE SUMMARY...1 WHAT IS FEDERATION?...2 Federation and
BEST PRACTICES WHITE PAPER Client Solutions BSM e: bsm@clients.ie t: 01 620 4000 w: www.clients.ie/bsm Federation and a CMDB Table of Contents EXECUTIVE SUMMARY...1 WHAT IS FEDERATION?...2 Federation and
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA"
 GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
GETTING REAL ABOUT SECURITY MANAGEMENT AND "BIG DATA" A Roadmap for "Big Data" in Security Analytics ESSENTIALS This paper examines: Escalating complexity of the security management environment, from threats
GEOGRAPHIC INFORMATION SYSTEMS (GIS): THE BEDROCK OF NG9-1-1
 GEOGRAPHIC INFORMATION SYSTEMS (GIS): THE BEDROCK OF NG9-1-1 THE TIME IS NOW FOR PSAPS AND REGIONAL AGENCIES TO TAKE ADVANTAGE OF THE ACCURATE GEOSPATIAL DATABASES THAT WILL BE KEY TO NEXT GENERATION EMERGENCY
GEOGRAPHIC INFORMATION SYSTEMS (GIS): THE BEDROCK OF NG9-1-1 THE TIME IS NOW FOR PSAPS AND REGIONAL AGENCIES TO TAKE ADVANTAGE OF THE ACCURATE GEOSPATIAL DATABASES THAT WILL BE KEY TO NEXT GENERATION EMERGENCY
Measuring Success Service Desk Evaluation Guide for the Midsized Business: How to Choose the Right Service Desk Solution and Improve Your ROI
 BEST PRACTICES WHITE PAPER Measuring Success Service Desk Evaluation Guide for the Midsized Business: How to Choose the Right Service Desk Solution and Improve Your ROI Table of Contents INTRODUCTION...1
BEST PRACTICES WHITE PAPER Measuring Success Service Desk Evaluation Guide for the Midsized Business: How to Choose the Right Service Desk Solution and Improve Your ROI Table of Contents INTRODUCTION...1
Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail
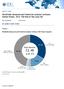 MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
Top 10 Anti-fraud Tips: The Cybersecurity Breach Aftermath
 ebook Top 10 Anti-fraud Tips: The Cybersecurity Breach Aftermath Protecting against downstream fraud attacks in the wake of large-scale security breaches. Digital companies can no longer trust static login
ebook Top 10 Anti-fraud Tips: The Cybersecurity Breach Aftermath Protecting against downstream fraud attacks in the wake of large-scale security breaches. Digital companies can no longer trust static login
TotalChrom. Chromatography Data Systems. Streamlining your laboratory workflow
 TotalChrom Chromatography Data Systems Streamlining your laboratory workflow maximize productivity with TotalChrom CDS Acquiring, processing, reporting, reviewing and approving data is a streamlined series
TotalChrom Chromatography Data Systems Streamlining your laboratory workflow maximize productivity with TotalChrom CDS Acquiring, processing, reporting, reviewing and approving data is a streamlined series
EXECUTIVE SUMMARY. Warehouse Management Systems. Technology for Global Supply Chain Performance. Authored By: Carla Reed. ChainLink Technology Series
 EXECUTIVE SUMMARY ChainLink Technology Series Warehouse Management Systems Technology for Global Supply Chain Performance Copyright ChainLink Research 2007 Authored By: Carla Reed June, 2007 About ChainLink
EXECUTIVE SUMMARY ChainLink Technology Series Warehouse Management Systems Technology for Global Supply Chain Performance Copyright ChainLink Research 2007 Authored By: Carla Reed June, 2007 About ChainLink
Preemptive security solutions for healthcare
 Helping to secure critical healthcare infrastructure from internal and external IT threats, ensuring business continuity and supporting compliance requirements. Preemptive security solutions for healthcare
Helping to secure critical healthcare infrastructure from internal and external IT threats, ensuring business continuity and supporting compliance requirements. Preemptive security solutions for healthcare
customer care solutions
 customer care solutions from Nuance white paper :: A Guide to Successful Intelligent Virtual Assistants Why Best-in-Class Technology Alone Is Not Enough NUANCE :: customer care solutions More than ever
customer care solutions from Nuance white paper :: A Guide to Successful Intelligent Virtual Assistants Why Best-in-Class Technology Alone Is Not Enough NUANCE :: customer care solutions More than ever
Windows Embedded Security and Surveillance Solutions
 Windows Embedded Security and Surveillance Solutions Windows Embedded 2010 Page 1 Copyright The information contained in this document represents the current view of Microsoft Corporation on the issues
Windows Embedded Security and Surveillance Solutions Windows Embedded 2010 Page 1 Copyright The information contained in this document represents the current view of Microsoft Corporation on the issues
Meeting the challenges of today s oil and gas exploration and production industry.
 Meeting the challenges of today s oil and gas exploration and production industry. Leveraging innovative technology to improve production and lower costs Executive Brief Executive overview The deep waters
Meeting the challenges of today s oil and gas exploration and production industry. Leveraging innovative technology to improve production and lower costs Executive Brief Executive overview The deep waters
ETPL Extract, Transform, Predict and Load
 ETPL Extract, Transform, Predict and Load An Oracle White Paper March 2006 ETPL Extract, Transform, Predict and Load. Executive summary... 2 Why Extract, transform, predict and load?... 4 Basic requirements
ETPL Extract, Transform, Predict and Load An Oracle White Paper March 2006 ETPL Extract, Transform, Predict and Load. Executive summary... 2 Why Extract, transform, predict and load?... 4 Basic requirements
Océ PRISMA software. Powerful technology, leading portfolio, a proven partner. Maximize potential
 Océ PRISMA software Powerful technology, leading portfolio, a proven partner Maximize potential The critical choice is yours Manage the demands and opportunities of today s document processes Why Océ PRISMA
Océ PRISMA software Powerful technology, leading portfolio, a proven partner Maximize potential The critical choice is yours Manage the demands and opportunities of today s document processes Why Océ PRISMA
Crash Data System - A new-generation software product approach and a move to improved national systems
 4 th IRTAD CONFERENCE 16-17 September, 2009, Seoul, Korea Crash Data System - A new-generation software product approach and a move to improved national systems Dr. Jim Jarvis & Subu Kamal Country: India
4 th IRTAD CONFERENCE 16-17 September, 2009, Seoul, Korea Crash Data System - A new-generation software product approach and a move to improved national systems Dr. Jim Jarvis & Subu Kamal Country: India
Enterprise content management solutions Better decisions, faster. Storing, finding and managing content in the digital enterprise.
 Enterprise content management solutions Better decisions, faster Storing, finding and managing content in the digital enterprise. Streamlines the collection, protection, sharing and distribution of digital
Enterprise content management solutions Better decisions, faster Storing, finding and managing content in the digital enterprise. Streamlines the collection, protection, sharing and distribution of digital
SIMATIC PCS 7 takes you beyond the limits. SIMATIC PCS 7. Answers for industry.
 SIMATIC PCS 7 takes you beyond the limits. SIMATIC PCS 7 Answers for industry. Your benefits Performance Scalability Integration Safety & Security Innovation Modernization Global Network of Experts 2 The
SIMATIC PCS 7 takes you beyond the limits. SIMATIC PCS 7 Answers for industry. Your benefits Performance Scalability Integration Safety & Security Innovation Modernization Global Network of Experts 2 The
5 Steps to Choosing the Right BPM Suite
 5 Steps to Choosing the Right BPM Suite BPM Suites can deliver significant business benefits and a fast ROI but only if you choose the right one By Laura Mooney, Metastorm Copyright 2009, Metastorm Inc.
5 Steps to Choosing the Right BPM Suite BPM Suites can deliver significant business benefits and a fast ROI but only if you choose the right one By Laura Mooney, Metastorm Copyright 2009, Metastorm Inc.
One platform for all your print, scan and device management
 One platform for all your print, scan and device management Manage all Printing & Scanning with one single Platform. Incorporating uniflow into your document processes will lead to real improvements in
One platform for all your print, scan and device management Manage all Printing & Scanning with one single Platform. Incorporating uniflow into your document processes will lead to real improvements in
Unifying IT How Dell Is Using BMC
 Unifying IT Management: How Dell Is Using BMC Software to Implement ITIL ABSTRACT Companies are looking for ways to maximize the efficiency with which they plan, deliver, and manage technology services.
Unifying IT Management: How Dell Is Using BMC Software to Implement ITIL ABSTRACT Companies are looking for ways to maximize the efficiency with which they plan, deliver, and manage technology services.
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 VENDOR PROFILE Passlogix and Enterprise Secure Single Sign-On: A Success Story Sally Hudson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
VENDOR PROFILE Passlogix and Enterprise Secure Single Sign-On: A Success Story Sally Hudson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
Extend the value of your core business systems.
 Legacy systems renovation to SOA September 2006 Extend the value of your core business systems. Transforming legacy applications into an SOA framework Page 2 Contents 2 Unshackling your core business systems
Legacy systems renovation to SOA September 2006 Extend the value of your core business systems. Transforming legacy applications into an SOA framework Page 2 Contents 2 Unshackling your core business systems
Network Security and Vulnerability Assessment Solutions
 Network Security and Vulnerability Assessment Solutions Unified Vulnerability Management It s a known fact that the exponential growth and successful exploitation of vulnerabilities create increasingly
Network Security and Vulnerability Assessment Solutions Unified Vulnerability Management It s a known fact that the exponential growth and successful exploitation of vulnerabilities create increasingly
A European manufacturer
 A European manufacturer Saving nearly USD19 million through improved workplace management Overview The need Balance the pressure for growth against aggressive cost reduction targets. The solution The organization
A European manufacturer Saving nearly USD19 million through improved workplace management Overview The need Balance the pressure for growth against aggressive cost reduction targets. The solution The organization
Dell Mobile Clinical Computing
 Dell Mobile Clinical Computing Healthcare Technology Solutions that Deliver Greater Security, IT Productivity and Clinician Efficiency Today s healthcare environment relies heavily on the latest technology
Dell Mobile Clinical Computing Healthcare Technology Solutions that Deliver Greater Security, IT Productivity and Clinician Efficiency Today s healthcare environment relies heavily on the latest technology
turnkey clouds, turnkey profits
 WHITE PAPER Turnkey Clouds, Turnkey Profits March 2011 turnkey clouds, turnkey profits To meet customer demand and succeed, service providers need to build cloud services that are agile, secure, and profitable.
WHITE PAPER Turnkey Clouds, Turnkey Profits March 2011 turnkey clouds, turnkey profits To meet customer demand and succeed, service providers need to build cloud services that are agile, secure, and profitable.
secure user IDs and business processes Identity and Access Management solutions Your business technologists. Powering progress
 secure Identity and Access Management solutions user IDs and business processes Your business technologists. Powering progress 2 Protected identity through access management Cutting costs, increasing security
secure Identity and Access Management solutions user IDs and business processes Your business technologists. Powering progress 2 Protected identity through access management Cutting costs, increasing security
agility made possible
 SOLUTION BRIEF Flexibility and Choices in Infrastructure Management can IT live up to business expectations with soaring infrastructure complexity and challenging resource constraints? agility made possible
SOLUTION BRIEF Flexibility and Choices in Infrastructure Management can IT live up to business expectations with soaring infrastructure complexity and challenging resource constraints? agility made possible
EMPOWERING BUSINESSES WITH A UNIQUE DEVELOPMENT NEEDS WITH HIGH LEVEL OF
 EMPOWERING BUSINESSES WITH A UNIQUE TECHNOLOGY INFRASTRUCTURE TO ADDRESS CUSTOM APPLICATION DEVELOPMENT NEEDS WITH HIGH LEVEL OF AGILITY AND EASE Enterprise Business Application Infrastructure Everything
EMPOWERING BUSINESSES WITH A UNIQUE TECHNOLOGY INFRASTRUCTURE TO ADDRESS CUSTOM APPLICATION DEVELOPMENT NEEDS WITH HIGH LEVEL OF AGILITY AND EASE Enterprise Business Application Infrastructure Everything
Working Together More Efficiently:
 A White Paper by Exact Software Working Together More Efficiently: Mapping out the Company s Business Processes Business Unified A White Paper by Exact Software Executive Overview To embrace the collaborative
A White Paper by Exact Software Working Together More Efficiently: Mapping out the Company s Business Processes Business Unified A White Paper by Exact Software Executive Overview To embrace the collaborative
High-Performance Scorecards. Best practices to build a winning formula every time
 High-Performance Scorecards Best practices to build a winning formula every time Will your team win or lose? Scorecards drive financial decision making For decades, your organization has used the predictive
High-Performance Scorecards Best practices to build a winning formula every time Will your team win or lose? Scorecards drive financial decision making For decades, your organization has used the predictive
UPGRADE THE WAY YOU WORK
 WHITE PAPER UPGRADE THE WAY YOU WORK WHY WINDOWS 10 HELPS INCREASE PRODUCTIVITY AND REDUCE COMPLEXITY WHERE TO GO How Windows 10 Can Help Your Teams Perform Better 2 What to Consider Before Choosing to
WHITE PAPER UPGRADE THE WAY YOU WORK WHY WINDOWS 10 HELPS INCREASE PRODUCTIVITY AND REDUCE COMPLEXITY WHERE TO GO How Windows 10 Can Help Your Teams Perform Better 2 What to Consider Before Choosing to
NICE Systems and Avaya provide businesses with Insight from Interactions
 IP Telephony Contact Centers Mobility Services OVERVIEW NICE Systems and Avaya provide businesses with Insight from Interactions Supports Avaya Communication Manager Application Enablement Services (AES)
IP Telephony Contact Centers Mobility Services OVERVIEW NICE Systems and Avaya provide businesses with Insight from Interactions Supports Avaya Communication Manager Application Enablement Services (AES)
Simplify Your Windows Server Migration
 SOLUTION BRIEF: ENDPOINT MANAGEMENT........................................ Simplify Your Windows Server Migration Who should read this paper Windows Server 2003 customers looking to migrate to the latest
SOLUTION BRIEF: ENDPOINT MANAGEMENT........................................ Simplify Your Windows Server Migration Who should read this paper Windows Server 2003 customers looking to migrate to the latest
Autonomic computing: strengthening manageability for SOA implementations
 Autonomic computing Executive brief Autonomic computing: strengthening manageability for SOA implementations December 2006 First Edition Worldwide, CEOs are not bracing for change; instead, they are embracing
Autonomic computing Executive brief Autonomic computing: strengthening manageability for SOA implementations December 2006 First Edition Worldwide, CEOs are not bracing for change; instead, they are embracing
Easy. Modular. Universal. Laboratory automation with SIMATIC PCS 7 LAB SIMATIC PCS 7. Answers for industry.
 Easy. Modular. Universal. Laboratory automation with SIMATIC PCS 7 LAB SIMATIC PCS 7 Answers for industry. Greater efficiency in the laboratory SIMATIC ET 200pro I/O module Considerably less overhead Whether
Easy. Modular. Universal. Laboratory automation with SIMATIC PCS 7 LAB SIMATIC PCS 7 Answers for industry. Greater efficiency in the laboratory SIMATIC ET 200pro I/O module Considerably less overhead Whether
Mobile Voice Productivity & Automation. For Field Service Applications
 AccuSpeechMobile: Technical Overview Mobile Voice Productivity & Automation For Field Service Applications Mobile Inspections, Repair, Delivery & Asset Management Table of Contents Mobile Workforce Productivity
AccuSpeechMobile: Technical Overview Mobile Voice Productivity & Automation For Field Service Applications Mobile Inspections, Repair, Delivery & Asset Management Table of Contents Mobile Workforce Productivity
At the Heart of Improved Business Dexterity
 At the Heart of Improved Business Dexterity Be Nimble, Be Quick: Driving Agility in Insurance Abstract The insurance landscape is evolving rapidly and is fraught with challenges. Insurance providers are
At the Heart of Improved Business Dexterity Be Nimble, Be Quick: Driving Agility in Insurance Abstract The insurance landscape is evolving rapidly and is fraught with challenges. Insurance providers are
Critical Issues with Lotus Notes and Domino 8.5 Password Authentication, Security and Management
 Security Comparison Critical Issues with Lotus Notes and Domino 8.5 Password Authentication, Security and Management PistolStar, Inc. PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200 Fax: 603.546.2309
Security Comparison Critical Issues with Lotus Notes and Domino 8.5 Password Authentication, Security and Management PistolStar, Inc. PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200 Fax: 603.546.2309
Cybersecurity and Secure Authentication with SAP Single Sign-On
 Solution in Detail SAP NetWeaver SAP Single Sign-On Cybersecurity and Secure Authentication with SAP Single Sign-On Table of Contents 3 Quick Facts 4 Remember One Password Only 6 Log In Once to Handle
Solution in Detail SAP NetWeaver SAP Single Sign-On Cybersecurity and Secure Authentication with SAP Single Sign-On Table of Contents 3 Quick Facts 4 Remember One Password Only 6 Log In Once to Handle
Digital Persona Fingerprint Reader Installation
 Digital Persona Fingerprint Reader Installation The link to download the Fingerprint Reader Software for AXIS-ACH is http://corpcu.com/fingerprint-reader-software This will begin the download for the drivers.
Digital Persona Fingerprint Reader Installation The link to download the Fingerprint Reader Software for AXIS-ACH is http://corpcu.com/fingerprint-reader-software This will begin the download for the drivers.
Technology Brochure New Technology for the Digital Consumer
 Technology Brochure New Technology for the Digital Consumer Redefining how Service Providers deliver the Digital Experience 7 August 2014 New Technology for the Digital Consumer Consumer attitudes and
Technology Brochure New Technology for the Digital Consumer Redefining how Service Providers deliver the Digital Experience 7 August 2014 New Technology for the Digital Consumer Consumer attitudes and
PalmSecureID for the EDUCATION MARKETPLACE
 PalmSecureID for the EDUCATION MARKETPLACE with Student Identity Integrity With the continued effort to increase efficiencies in the world of education, PalmSecureID can be utilized in a variety of settings
PalmSecureID for the EDUCATION MARKETPLACE with Student Identity Integrity With the continued effort to increase efficiencies in the world of education, PalmSecureID can be utilized in a variety of settings
Simplify Software as a Service (SaaS) Integration
 Simplify Software as a Service (SaaS) Integration By Simon Peel December 2008 Introduction Fuelled by a fiercely competitive business environment that requires the pace of business and technology to accelerate,
Simplify Software as a Service (SaaS) Integration By Simon Peel December 2008 Introduction Fuelled by a fiercely competitive business environment that requires the pace of business and technology to accelerate,
Signature Verification Why xyzmo offers the leading solution.
 Dynamic (Biometric) Signature Verification The signature is the last remnant of the hand-written document in a digital world, and is considered an acceptable and trustworthy means of authenticating all
Dynamic (Biometric) Signature Verification The signature is the last remnant of the hand-written document in a digital world, and is considered an acceptable and trustworthy means of authenticating all
White Paper. What is an Identity Provider, and Why Should My Organization Become One?
 White Paper What is an Identity Provider, and Why Should My Organization Become One? May 2015 Executive Overview Tame Access Control Security Risks: Become an Identity Provider (IdP) Organizations today
White Paper What is an Identity Provider, and Why Should My Organization Become One? May 2015 Executive Overview Tame Access Control Security Risks: Become an Identity Provider (IdP) Organizations today
