Using Static Program Analysis to Aid Intrusion Detection
|
|
|
- Brent Jones
- 8 years ago
- Views:
Transcription
1 Using Static Program to Aid Intrusion Detection M. Egele M. Szydlowski E. Kirda C. Kruegel Secure Systems Lab Vienna University of Technology SIG SIDAR Conference on Detection of Intrusions and Malware & Vulnerability Assessment, 2006
2 outline 1 Motivation 2 3 How We Evaluated Our Results Results Results Comparison with Log Data
3 what we want to do and why PHP is arguably the most prominent language to develop web-based applications Many exploits for vulnerabilities in PHP-applications exist User/attacker can influence the application mainly via its parameters We employ interprocedural dataflow analysis to gain knowledge about used parameters Especially types and possible values of parameters are interesting
4 what we want to do and why PHP is arguably the most prominent language to develop web-based applications Many exploits for vulnerabilities in PHP-applications exist User/attacker can influence the application mainly via its parameters We employ interprocedural dataflow analysis to gain knowledge about used parameters Especially types and possible values of parameters are interesting
5 what we want to do and why PHP is arguably the most prominent language to develop web-based applications Many exploits for vulnerabilities in PHP-applications exist User/attacker can influence the application mainly via its parameters We employ interprocedural dataflow analysis to gain knowledge about used parameters Especially types and possible values of parameters are interesting
6 what we want to do and why PHP is arguably the most prominent language to develop web-based applications Many exploits for vulnerabilities in PHP-applications exist User/attacker can influence the application mainly via its parameters We employ interprocedural dataflow analysis to gain knowledge about used parameters Especially types and possible values of parameters are interesting
7 what we want to do and why PHP is arguably the most prominent language to develop web-based applications Many exploits for vulnerabilities in PHP-applications exist User/attacker can influence the application mainly via its parameters We employ interprocedural dataflow analysis to gain knowledge about used parameters Especially types and possible values of parameters are interesting
8 existing intrusion detection system MAID tries to characterize web-requests through different models: Learning based intrusion detection system developed at the Secure Systems Lab TU Vienna. models include parameter presence/absence model, structural inference, token finder models... No a priori knowledge of applications it protects learning is basically done via logfile analysis In some cases unnecessary imprecision leads to many false positives this is what we want to improve
9 existing intrusion detection system MAID tries to characterize web-requests through different models: Learning based intrusion detection system developed at the Secure Systems Lab TU Vienna. models include parameter presence/absence model, structural inference, token finder models... No a priori knowledge of applications it protects learning is basically done via logfile analysis In some cases unnecessary imprecision leads to many false positives this is what we want to improve
10 existing intrusion detection system MAID tries to characterize web-requests through different models: Learning based intrusion detection system developed at the Secure Systems Lab TU Vienna. models include parameter presence/absence model, structural inference, token finder models... No a priori knowledge of applications it protects learning is basically done via logfile analysis In some cases unnecessary imprecision leads to many false positives this is what we want to improve
11 existing intrusion detection system MAID tries to characterize web-requests through different models: Learning based intrusion detection system developed at the Secure Systems Lab TU Vienna. models include parameter presence/absence model, structural inference, token finder models... No a priori knowledge of applications it protects learning is basically done via logfile analysis In some cases unnecessary imprecision leads to many false positives this is what we want to improve
12 mode of operation Motivation Input: PHP Source File Parse File and Includes Abstract Represen tation Identify Interesting Parameters Action performed Output: Parameter Info Link Parameters and Usage Track Variable Values Variable Type Inference parse the application source code
13 mode of operation Motivation Input: PHP Source File Output: Parameter Info Parse File and Includes Link Parameters and Usage Abstract Represen tation Track Variable Values Identify Interesting Parameters Variable Type Inference Action performed identify the parameters the application accepts
14 mode of operation Motivation Input: PHP Source File Parse File and Includes Abstract Represen tation Identify Interesting Parameters Action performed Output: Parameter Info Link Parameters and Usage Track Variable Values Variable Type Inference type inference on variables
15 mode of operation Motivation Input: PHP Source File Parse File and Includes Abstract Represen tation Identify Interesting Parameters Action performed Output: Parameter Info Link Parameters and Usage Track Variable Values Variable Type Inference variables values are tracked
16 mode of operation Motivation Input: PHP Source File Parse File and Includes Abstract Represen tation Identify Interesting Parameters Action performed Output: Parameter Info Link Parameters and Usage Track Variable Values Variable Type Inference parameter usage is examined
17 parsing Motivation Original Zend language parser was used Includes are resolved (constant expressions) Variables and functions are identified
18 parsing Motivation Original Zend language parser was used Includes are resolved (constant expressions) Variables and functions are identified
19 parsing Motivation Original Zend language parser was used Includes are resolved (constant expressions) Variables and functions are identified
20 how parameters can be accessed in PHP Parameter name is index into a parameter array e.g., $_GET, $_POST superglobals Via register_globals risky
21 how parameters can be accessed in PHP Parameter name is index into a parameter array e.g., $_GET, $_POST superglobals Via register_globals risky
22 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
23 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
24 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
25 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
26 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
27 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
28 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
29 example on accessing parameters 1 class Util { 2 function getget($var, $default = null) { 3 return (isset($_get[$var])) 4? Util::dispelMagicQuotes($_GET[$var]) 5 : $default; 6 } 7 function getformdata($arg, $default = null) { 8 return (($val = Util::getPost($arg))!== null) 9? $val 10 : Util::getGet($arg, $default); 11 } 12 } $actionid = Util::getFormData( actionid )
30 how we find the parameter names 1 Dataflow analysis at procedural level 2 Interprocedural analysis for function calls (recursive) 3 This information can be used for the parameter presence/absence model of our IDS
31 how we find the parameter names 1 Dataflow analysis at procedural level 2 Interprocedural analysis for function calls (recursive) 3 This information can be used for the parameter presence/absence model of our IDS
32 how we find the parameter names 1 Dataflow analysis at procedural level 2 Interprocedural analysis for function calls (recursive) 3 This information can be used for the parameter presence/absence model of our IDS
33 parameter types - valuable information Very useful for the IDS (e.g., integers {-}?[0-9]+) PHP only has dynamic types (e.g., no int $x) and every value is dynamically typecast to whatever type expected by a given operation Type inference through applied operations via type matrix, special cases include: &&,,xor,! always return boolean. always returns string &,,ˆ string iff operands are string - integer otherwise
34 parameter types - valuable information Very useful for the IDS (e.g., integers {-}?[0-9]+) PHP only has dynamic types (e.g., no int $x) and every value is dynamically typecast to whatever type expected by a given operation Type inference through applied operations via type matrix, special cases include: &&,,xor,! always return boolean. always returns string &,,ˆ string iff operands are string - integer otherwise
35 parameter types - valuable information Very useful for the IDS (e.g., integers {-}?[0-9]+) PHP only has dynamic types (e.g., no int $x) and every value is dynamically typecast to whatever type expected by a given operation Type inference through applied operations via type matrix, special cases include: &&,,xor,! always return boolean. always returns string &,,ˆ string iff operands are string - integer otherwise
36 parameter types - valuable information Very useful for the IDS (e.g., integers {-}?[0-9]+) PHP only has dynamic types (e.g., no int $x) and every value is dynamically typecast to whatever type expected by a given operation Type inference through applied operations via type matrix, special cases include: &&,,xor,! always return boolean. always returns string &,,ˆ string iff operands are string - integer otherwise
37 parameter types - valuable information Very useful for the IDS (e.g., integers {-}?[0-9]+) PHP only has dynamic types (e.g., no int $x) and every value is dynamically typecast to whatever type expected by a given operation Type inference through applied operations via type matrix, special cases include: &&,,xor,! always return boolean. always returns string &,,ˆ string iff operands are string - integer otherwise
38 parameter types - valuable information Very useful for the IDS (e.g., integers {-}?[0-9]+) PHP only has dynamic types (e.g., no int $x) and every value is dynamically typecast to whatever type expected by a given operation Type inference through applied operations via type matrix, special cases include: &&,,xor,! always return boolean. always returns string &,,ˆ string iff operands are string - integer otherwise
39 parameter types Motivation 1 Try to infer as many variables as possible via the operator-type matrix 2 If a parameter is linked to a variable, assume the parameter has the same type as the variable. 1 $x = $_GET[ THE_X ]; 2 if ($x == 42) 3 echo x is 42 ; 4 else 5 echo error x is not 42 3 Use the more general type if there is a conflict
40 parameter types Motivation 1 Try to infer as many variables as possible via the operator-type matrix 2 If a parameter is linked to a variable, assume the parameter has the same type as the variable. 1 $x = $_GET[ THE_X ]; 2 if ($x == 42) 3 echo x is 42 ; 4 else 5 echo error x is not 42 3 Use the more general type if there is a conflict
41 parameter types Motivation 1 Try to infer as many variables as possible via the operator-type matrix 2 If a parameter is linked to a variable, assume the parameter has the same type as the variable. 1 $x = $_GET[ THE_X ]; 2 if ($x == 42) 3 echo x is 42 ; 4 else 5 echo error x is not 42 3 Use the more general type if there is a conflict
42 possible value sets Motivation 1 Direct comparison via literal 2 Indirect comparison via switch-case construct 3 sanitation code (e.g., regexp, built-in functions) annotations possible 4 This information can be used for the structural models and character distribution models of our IDS
43 possible value sets Motivation 1 Direct comparison via literal 2 Indirect comparison via switch-case construct 3 sanitation code (e.g., regexp, built-in functions) annotations possible 4 This information can be used for the structural models and character distribution models of our IDS
44 possible value sets Motivation 1 Direct comparison via literal 2 Indirect comparison via switch-case construct 3 sanitation code (e.g., regexp, built-in functions) annotations possible 4 This information can be used for the structural models and character distribution models of our IDS
45 possible value sets Motivation 1 Direct comparison via literal 2 Indirect comparison via switch-case construct 3 sanitation code (e.g., regexp, built-in functions) annotations possible 4 This information can be used for the structural models and character distribution models of our IDS
46 the annotation used for SquirrelMail SquirrelMail uses the sqgetglobalvar function to retrieve its parameters. first argument: name of the parameter second argument: reference to the variable that should receive the value annotation: sqgetglobalvar:1:2 code: sqgetglobalvar( THE_X, &$x) now the analyzer knows that $x holds the value of the parameter THE_X
47 the annotation used for SquirrelMail SquirrelMail uses the sqgetglobalvar function to retrieve its parameters. first argument: name of the parameter second argument: reference to the variable that should receive the value annotation: sqgetglobalvar:1:2 code: sqgetglobalvar( THE_X, &$x) now the analyzer knows that $x holds the value of the parameter THE_X
48 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
49 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
50 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
51 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
52 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
53 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
54 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
55 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
56 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
57 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
58 1 $otherparam = Util::getFormData("otherparam"); 2 $param = array( 3 "name" => "pizzaman", 4 "value" => Util::getFormData("param"), 5 "info" => "something boring"); 6 $thirdparam = do_something($_post["thirdparam"]); 7 8 $strippedparam = stripslashes($param["value"]); 9 if ($strippedparam == "something") switch ($otherparam) { 12 case "something else": } 15 preg_match("/^([0-9]4).*", $thirdparam, $number);
59 How We Evaluated Our Results Results Results Comparison with Log Data how we evaluated our results is divided into two parts: Standalone of five real world web-applications Crosscheck of some of these results with actual log data only GET requests, since POST requests not logged We were able to find all parameters that actually appeared in the logs
60 How We Evaluated Our Results Results Results Comparison with Log Data how we evaluated our results is divided into two parts: Standalone of five real world web-applications Crosscheck of some of these results with actual log data only GET requests, since POST requests not logged We were able to find all parameters that actually appeared in the logs
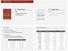
61 How We Evaluated Our Results Results Results Comparison with Log Data web applications under examination We analyzed the following popular web applications Application Parameters Details Percentage Horde2/IMP % Squirrelmail rc % phpbb % Horde3/IMP % PHP icalendar %
62 How We Evaluated Our Results Results Results Comparison with Log Data info on parameters found Examples of our findings Details for parameters 35% information for IDS Horde2: actionid TYPE_INT values: 0,1,101,102,... Horde3: actionid TYPE_STRING values: add_address, add_attachment,... icalendar: getdate TYPE_STRING preg_match("/([0-9]4)([0-9]2)([0-9]2)/")
63 How We Evaluated Our Results Results Results Comparison with Log Data info on parameters found Examples of our findings Details for parameters 35% information for IDS Horde2: actionid TYPE_INT values: 0,1,101,102,... Horde3: actionid TYPE_STRING values: add_address, add_attachment,... icalendar: getdate TYPE_STRING preg_match("/([0-9]4)([0-9]2)([0-9]2)/")
64 How We Evaluated Our Results Results Results Comparison with Log Data info on parameters found Examples of our findings Details for parameters 35% information for IDS Horde2: actionid TYPE_INT values: 0,1,101,102,... Horde3: actionid TYPE_STRING values: add_address, add_attachment,... icalendar: getdate TYPE_STRING preg_match("/([0-9]4)([0-9]2)([0-9]2)/")
65 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data Results for Horde2/IMP 3.1 Timeframe: three months, accesses name: reason type: TYPE_STRING values: failed, logout, session exact matches to, cc, bcc only information TYPE_STRING f filename to download-dialog (relict) replaced by MIME-Header parsing
66 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data Results for Horde2/IMP 3.1 Timeframe: three months, accesses name: reason type: TYPE_STRING values: failed, logout, session exact matches to, cc, bcc only information TYPE_STRING f filename to download-dialog (relict) replaced by MIME-Header parsing
67 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data Results for Horde2/IMP 3.1 Timeframe: three months, accesses name: reason type: TYPE_STRING values: failed, logout, session exact matches to, cc, bcc only information TYPE_STRING f filename to download-dialog (relict) replaced by MIME-Header parsing
68 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data Results for Horde2/IMP 3.1 Timeframe: three months, accesses name: reason type: TYPE_STRING values: failed, logout, session exact matches to, cc, bcc only information TYPE_STRING f filename to download-dialog (relict) replaced by MIME-Header parsing
69 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data Results for Squirrelmail Timeframe: three weeks, accesses name: smaction type: TYPE_STRING values: draft, edit_as_new, forward, forward_as_attachment, reply, reply_all exact matches what, where type: TYPE_STRING dynamic search parameters
70 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data Results for Squirrelmail Timeframe: three weeks, accesses name: smaction type: TYPE_STRING values: draft, edit_as_new, forward, forward_as_attachment, reply, reply_all exact matches what, where type: TYPE_STRING dynamic search parameters
71 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data Results for Squirrelmail Timeframe: three weeks, accesses name: smaction type: TYPE_STRING values: draft, edit_as_new, forward, forward_as_attachment, reply, reply_all exact matches what, where type: TYPE_STRING dynamic search parameters
72 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data shows that we were able to find all parameters in the sourcecode that are actually used For about 35%, detailed information on these parameters could be deduced by our analyzer This additional information can be used to improve the precision of our IDS
73 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data shows that we were able to find all parameters in the sourcecode that are actually used For about 35%, detailed information on these parameters could be deduced by our analyzer This additional information can be used to improve the precision of our IDS
74 How We Evaluated Our Results Results Results Comparison with Log Data crosscheck with real log data shows that we were able to find all parameters in the sourcecode that are actually used For about 35%, detailed information on these parameters could be deduced by our analyzer This additional information can be used to improve the precision of our IDS
75 How We Evaluated Our Results Results Results Comparison with Log Data details on phpbb Scenario: December 2005 mass defacement of phpbb Exploit modifies the GLOBALS array via: profile.php?globals[...] Parameter presence and absence model GLOBALS not a parameter of the web-application
76 How We Evaluated Our Results Results Results Comparison with Log Data details on phpbb Scenario: December 2005 mass defacement of phpbb Exploit modifies the GLOBALS array via: profile.php?globals[...] Parameter presence and absence model GLOBALS not a parameter of the web-application
77 How We Evaluated Our Results Results Results Comparison with Log Data details on phpbb Scenario: December 2005 mass defacement of phpbb Exploit modifies the GLOBALS array via: profile.php?globals[...] Parameter presence and absence model GLOBALS not a parameter of the web-application
78 Parameter name detection via inter-procedural dataflow analysis Determine types and possible values of parameters based on their use by the application Would have been able to detect real-world exploit
Static Program Analysis of PHP and request Parameters in Network Marketing
 Using Static Program Analysis to Aid Intrusion Detection Manuel Egele, Martin Szydlowski, Engin Kirda, and Christopher Kruegel Secure Systems Lab, Technical University Vienna {pizzaman,msz,ek,chris}@seclab.tuwien.ac.at
Using Static Program Analysis to Aid Intrusion Detection Manuel Egele, Martin Szydlowski, Engin Kirda, and Christopher Kruegel Secure Systems Lab, Technical University Vienna {pizzaman,msz,ek,chris}@seclab.tuwien.ac.at
PHP Integration Kit. Version 2.5.1. User Guide
 PHP Integration Kit Version 2.5.1 User Guide 2012 Ping Identity Corporation. All rights reserved. PingFederate PHP Integration Kit User Guide Version 2.5.1 December, 2012 Ping Identity Corporation 1001
PHP Integration Kit Version 2.5.1 User Guide 2012 Ping Identity Corporation. All rights reserved. PingFederate PHP Integration Kit User Guide Version 2.5.1 December, 2012 Ping Identity Corporation 1001
RIPS - A static source code analyser for vulnerabilities in PHP scripts
 RIPS - A static source code analyser for vulnerabilities in PHP scripts Johannes Dahse 1 Introduction The amount of websites have increased rapidly during the last years. While websites consisted mostly
RIPS - A static source code analyser for vulnerabilities in PHP scripts Johannes Dahse 1 Introduction The amount of websites have increased rapidly during the last years. While websites consisted mostly
ICT. PHP coding. Universityy. in any
 Information Technology Services Division ICT Volume 3 : Application Standards ICT 3.2.1.1-2011 PHP Coding Standards Abstract This document defines the standards applicable to PHP coding. Copyright Deakin
Information Technology Services Division ICT Volume 3 : Application Standards ICT 3.2.1.1-2011 PHP Coding Standards Abstract This document defines the standards applicable to PHP coding. Copyright Deakin
The C Programming Language course syllabus associate level
 TECHNOLOGIES The C Programming Language course syllabus associate level Course description The course fully covers the basics of programming in the C programming language and demonstrates fundamental programming
TECHNOLOGIES The C Programming Language course syllabus associate level Course description The course fully covers the basics of programming in the C programming language and demonstrates fundamental programming
PHP Magic Tricks: Type Juggling. PHP Magic Tricks: Type Juggling
 Who Am I Chris Smith (@chrismsnz) Previously: Polyglot Developer - Python, PHP, Go + more Linux Sysadmin Currently: Pentester, Consultant at Insomnia Security Little bit of research Insomnia Security Group
Who Am I Chris Smith (@chrismsnz) Previously: Polyglot Developer - Python, PHP, Go + more Linux Sysadmin Currently: Pentester, Consultant at Insomnia Security Little bit of research Insomnia Security Group
CLC Server Command Line Tools USER MANUAL
 CLC Server Command Line Tools USER MANUAL Manual for CLC Server Command Line Tools 2.5 Windows, Mac OS X and Linux September 4, 2015 This software is for research purposes only. QIAGEN Aarhus A/S Silkeborgvej
CLC Server Command Line Tools USER MANUAL Manual for CLC Server Command Line Tools 2.5 Windows, Mac OS X and Linux September 4, 2015 This software is for research purposes only. QIAGEN Aarhus A/S Silkeborgvej
Facebook Twitter YouTube Google Plus Website Email
 PHP MySQL COURSE WITH OOP COURSE COVERS: PHP MySQL OBJECT ORIENTED PROGRAMMING WITH PHP SYLLABUS PHP 1. Writing PHP scripts- Writing PHP scripts, learn about PHP code structure, how to write and execute
PHP MySQL COURSE WITH OOP COURSE COVERS: PHP MySQL OBJECT ORIENTED PROGRAMMING WITH PHP SYLLABUS PHP 1. Writing PHP scripts- Writing PHP scripts, learn about PHP code structure, how to write and execute
Manage cloud infrastructures using Zend Framework
 Manage cloud infrastructures using Zend Framework by Enrico Zimuel (enrico@zend.com) Senior Software Engineer Zend Framework Core Team Zend Technologies Ltd About me Email: enrico@zend.com Twitter: @ezimuel
Manage cloud infrastructures using Zend Framework by Enrico Zimuel (enrico@zend.com) Senior Software Engineer Zend Framework Core Team Zend Technologies Ltd About me Email: enrico@zend.com Twitter: @ezimuel
Certified PHP/MySQL Web Developer Course
 Course Duration : 3 Months (120 Hours) Day 1 Introduction to PHP 1.PHP web architecture 2.PHP wamp server installation 3.First PHP program 4.HTML with php 5.Comments and PHP manual usage Day 2 Variables,
Course Duration : 3 Months (120 Hours) Day 1 Introduction to PHP 1.PHP web architecture 2.PHP wamp server installation 3.First PHP program 4.HTML with php 5.Comments and PHP manual usage Day 2 Variables,
Webapps Vulnerability Report
 Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
Tuesday, May 1, 2012 Webapps Vulnerability Report Introduction This report provides detailed information of every vulnerability that was found and successfully exploited by CORE Impact Professional during
DocStore: Document Database for MySQL at Facebook. Peng Tian, Tian Xia 04/14/2015
 DocStore: Document Database for MySQL at Facebook Peng Tian, Tian Xia 04/14/2015 Agenda Overview of DocStore Document: A new column type to store JSON New Built-in JSON functions Document Path: A intuitive
DocStore: Document Database for MySQL at Facebook Peng Tian, Tian Xia 04/14/2015 Agenda Overview of DocStore Document: A new column type to store JSON New Built-in JSON functions Document Path: A intuitive
First Java Programs. V. Paúl Pauca. CSC 111D Fall, 2015. Department of Computer Science Wake Forest University. Introduction to Computer Science
 First Java Programs V. Paúl Pauca Department of Computer Science Wake Forest University CSC 111D Fall, 2015 Hello World revisited / 8/23/15 The f i r s t o b l i g a t o r y Java program @author Paul Pauca
First Java Programs V. Paúl Pauca Department of Computer Science Wake Forest University CSC 111D Fall, 2015 Hello World revisited / 8/23/15 The f i r s t o b l i g a t o r y Java program @author Paul Pauca
Web Presentation Layer Architecture
 Chapter 4 Web Presentation Layer Architecture In this chapter we provide a discussion of important current approaches to web interface programming based on the Model 2 architecture [59]. From the results
Chapter 4 Web Presentation Layer Architecture In this chapter we provide a discussion of important current approaches to web interface programming based on the Model 2 architecture [59]. From the results
Introduction to Lex. General Description Input file Output file How matching is done Regular expressions Local names Using Lex
 Introduction to Lex General Description Input file Output file How matching is done Regular expressions Local names Using Lex General Description Lex is a program that automatically generates code for
Introduction to Lex General Description Input file Output file How matching is done Regular expressions Local names Using Lex General Description Lex is a program that automatically generates code for
Swaddler: An Approach for the Anomaly-based Detection of State Violations in Web Applications
 Swaddler: An Approach for the Anomaly-based Detection of State Violations in Web Applications Marco Cova, Davide Balzarotti, Viktoria Felmetsger, and Giovanni Vigna Department of Computer Science, University
Swaddler: An Approach for the Anomaly-based Detection of State Violations in Web Applications Marco Cova, Davide Balzarotti, Viktoria Felmetsger, and Giovanni Vigna Department of Computer Science, University
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Fall 2005 Handout 7 Scanner Parser Project Wednesday, September 7 DUE: Wednesday, September 21 This
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Fall 2005 Handout 7 Scanner Parser Project Wednesday, September 7 DUE: Wednesday, September 21 This
Working with forms in PHP
 2002-6-29 Synopsis In this tutorial, you will learn how to use forms with PHP. Page 1 Forms and PHP One of the most popular ways to make a web site interactive is the use of forms. With forms you can have
2002-6-29 Synopsis In this tutorial, you will learn how to use forms with PHP. Page 1 Forms and PHP One of the most popular ways to make a web site interactive is the use of forms. With forms you can have
Security Awareness For Website Administrators. State of Illinois Central Management Services Security and Compliance Solutions
 Security Awareness For Website Administrators State of Illinois Central Management Services Security and Compliance Solutions Common Myths Myths I m a small target My data is not important enough We ve
Security Awareness For Website Administrators State of Illinois Central Management Services Security and Compliance Solutions Common Myths Myths I m a small target My data is not important enough We ve
Package retrosheet. April 13, 2015
 Type Package Package retrosheet April 13, 2015 Title Import Professional Baseball Data from 'Retrosheet' Version 1.0.2 Date 2015-03-17 Maintainer Richard Scriven A collection of tools
Type Package Package retrosheet April 13, 2015 Title Import Professional Baseball Data from 'Retrosheet' Version 1.0.2 Date 2015-03-17 Maintainer Richard Scriven A collection of tools
Form Validation. Server-side Web Development and Programming. What to Validate. Error Prevention. Lecture 7: Input Validation and Error Handling
 Form Validation Server-side Web Development and Programming Lecture 7: Input Validation and Error Handling Detecting user error Invalid form information Inconsistencies of forms to other entities Enter
Form Validation Server-side Web Development and Programming Lecture 7: Input Validation and Error Handling Detecting user error Invalid form information Inconsistencies of forms to other entities Enter
Web Application Security
 Web Application Security Richard A. Kemmerer Reliable Software Group Computer Science Department University of California Santa Barbara, CA 93106, USA http://www.cs.ucsb.edu/~rsg www.cs.ucsb.edu/~rsg/
Web Application Security Richard A. Kemmerer Reliable Software Group Computer Science Department University of California Santa Barbara, CA 93106, USA http://www.cs.ucsb.edu/~rsg www.cs.ucsb.edu/~rsg/
Web Service Facade for PHP5. Andreas Meyer, Sebastian Böttner, Stefan Marr
 Web Service Facade for PHP5 Andreas Meyer, Sebastian Böttner, Stefan Marr Agenda Objectives and Status Architecture Framework Features WSD Generator PHP5 eflection API Security Aspects used approach planned
Web Service Facade for PHP5 Andreas Meyer, Sebastian Böttner, Stefan Marr Agenda Objectives and Status Architecture Framework Features WSD Generator PHP5 eflection API Security Aspects used approach planned
LabVIEW Internet Toolkit User Guide
 LabVIEW Internet Toolkit User Guide Version 6.0 Contents The LabVIEW Internet Toolkit provides you with the ability to incorporate Internet capabilities into VIs. You can use LabVIEW to work with XML documents,
LabVIEW Internet Toolkit User Guide Version 6.0 Contents The LabVIEW Internet Toolkit provides you with the ability to incorporate Internet capabilities into VIs. You can use LabVIEW to work with XML documents,
C Compiler Targeting the Java Virtual Machine
 C Compiler Targeting the Java Virtual Machine Jack Pien Senior Honors Thesis (Advisor: Javed A. Aslam) Dartmouth College Computer Science Technical Report PCS-TR98-334 May 30, 1998 Abstract One of the
C Compiler Targeting the Java Virtual Machine Jack Pien Senior Honors Thesis (Advisor: Javed A. Aslam) Dartmouth College Computer Science Technical Report PCS-TR98-334 May 30, 1998 Abstract One of the
CSE 308. Coding Conventions. Reference
 CSE 308 Coding Conventions Reference Java Coding Conventions googlestyleguide.googlecode.com/svn/trunk/javaguide.html Java Naming Conventions www.ibm.com/developerworks/library/ws-tipnamingconv.html 2
CSE 308 Coding Conventions Reference Java Coding Conventions googlestyleguide.googlecode.com/svn/trunk/javaguide.html Java Naming Conventions www.ibm.com/developerworks/library/ws-tipnamingconv.html 2
RIPS - A static source code analyser for vulnerabilities in PHP scripts
 RIPS - A static source code analyser for vulnerabilities in PHP scripts Johannes Dahse Seminar Work at Chair for Network and Data Security Prof. Dr. Jörg Schwenk advised through Dominik Birk 23.08.2010
RIPS - A static source code analyser for vulnerabilities in PHP scripts Johannes Dahse Seminar Work at Chair for Network and Data Security Prof. Dr. Jörg Schwenk advised through Dominik Birk 23.08.2010
ARC: appmosphere RDF Classes for PHP Developers
 ARC: appmosphere RDF Classes for PHP Developers Benjamin Nowack appmosphere web applications, Kruppstr. 100, 45145 Essen, Germany bnowack@appmosphere.com Abstract. ARC is an open source collection of lightweight
ARC: appmosphere RDF Classes for PHP Developers Benjamin Nowack appmosphere web applications, Kruppstr. 100, 45145 Essen, Germany bnowack@appmosphere.com Abstract. ARC is an open source collection of lightweight
Spring Security CAS Plugin - Reference Documentation. Burt Beckwith. Version 3.0.0.M1
 Spring Security CAS Plugin - Reference Documentation Burt Beckwith Version 3.0.0.M1 Table of Contents 1. Introduction to the Spring Security CAS Plugin.................................................
Spring Security CAS Plugin - Reference Documentation Burt Beckwith Version 3.0.0.M1 Table of Contents 1. Introduction to the Spring Security CAS Plugin.................................................
SRFax Fax API Web Services Documentation
 SRFax Fax API Web Services Documentation Revision Date: July 2015 The materials and sample code are provided only for the purpose of an existing or potential customer evaluating or implementing a programmatic
SRFax Fax API Web Services Documentation Revision Date: July 2015 The materials and sample code are provided only for the purpose of an existing or potential customer evaluating or implementing a programmatic
Software documentation systems
 Software documentation systems Basic introduction to various user-oriented and developer-oriented software documentation systems. Ondrej Holotnak Ondrej Jombik Software documentation systems: Basic introduction
Software documentation systems Basic introduction to various user-oriented and developer-oriented software documentation systems. Ondrej Holotnak Ondrej Jombik Software documentation systems: Basic introduction
1 Introduction. 2 An Interpreter. 2.1 Handling Source Code
 1 Introduction The purpose of this assignment is to write an interpreter for a small subset of the Lisp programming language. The interpreter should be able to perform simple arithmetic and comparisons
1 Introduction The purpose of this assignment is to write an interpreter for a small subset of the Lisp programming language. The interpreter should be able to perform simple arithmetic and comparisons
Moving from CS 61A Scheme to CS 61B Java
 Moving from CS 61A Scheme to CS 61B Java Introduction Java is an object-oriented language. This document describes some of the differences between object-oriented programming in Scheme (which we hope you
Moving from CS 61A Scheme to CS 61B Java Introduction Java is an object-oriented language. This document describes some of the differences between object-oriented programming in Scheme (which we hope you
Compiler Construction
 Compiler Construction Regular expressions Scanning Görel Hedin Reviderad 2013 01 23.a 2013 Compiler Construction 2013 F02-1 Compiler overview source code lexical analysis tokens intermediate code generation
Compiler Construction Regular expressions Scanning Görel Hedin Reviderad 2013 01 23.a 2013 Compiler Construction 2013 F02-1 Compiler overview source code lexical analysis tokens intermediate code generation
Microsoft Windows PowerShell v2 For Administrators
 Course 50414B: Microsoft Windows PowerShell v2 For Administrators Course Details Course Outline Module 1: Introduction to PowerShell the Basics This module explains how to install and configure PowerShell.
Course 50414B: Microsoft Windows PowerShell v2 For Administrators Course Details Course Outline Module 1: Introduction to PowerShell the Basics This module explains how to install and configure PowerShell.
Comprehensive Static Analysis Using Polyspace Products. A Solution to Today s Embedded Software Verification Challenges WHITE PAPER
 Comprehensive Static Analysis Using Polyspace Products A Solution to Today s Embedded Software Verification Challenges WHITE PAPER Introduction Verification of embedded software is a difficult task, made
Comprehensive Static Analysis Using Polyspace Products A Solution to Today s Embedded Software Verification Challenges WHITE PAPER Introduction Verification of embedded software is a difficult task, made
WhatsApp monitoring for Fun and Stalking. by Flavio Giobergia
 WhatsApp monitoring for Fun and Stalking by Flavio Giobergia The idea behind the project If you have used WhatsApp at least once in your life, you know that there is a really lovely/shitty (deping on the
WhatsApp monitoring for Fun and Stalking by Flavio Giobergia The idea behind the project If you have used WhatsApp at least once in your life, you know that there is a really lovely/shitty (deping on the
High-Level Programming Languages. Nell Dale & John Lewis (adaptation by Michael Goldwasser)
 High-Level Programming Languages Nell Dale & John Lewis (adaptation by Michael Goldwasser) Low-Level Languages What are disadvantages of low-level languages? (e.g., machine code or assembly code) Programming
High-Level Programming Languages Nell Dale & John Lewis (adaptation by Michael Goldwasser) Low-Level Languages What are disadvantages of low-level languages? (e.g., machine code or assembly code) Programming
J a v a Quiz (Unit 3, Test 0 Practice)
 Computer Science S-111a: Intensive Introduction to Computer Science Using Java Handout #11 Your Name Teaching Fellow J a v a Quiz (Unit 3, Test 0 Practice) Multiple-choice questions are worth 2 points
Computer Science S-111a: Intensive Introduction to Computer Science Using Java Handout #11 Your Name Teaching Fellow J a v a Quiz (Unit 3, Test 0 Practice) Multiple-choice questions are worth 2 points
Enterprise Content Management System Monitor 5.1 Agent Debugging Guide Revision 1.3. 2014-11-05 CENIT AG Author: Stefan Bettighofer
 Enterprise Content Management System Monitor 5.1 Agent Debugging Guide Revision 1.3 2014-11-05 CENIT AG Author: Stefan Bettighofer 1 Table of Contents 1 Table of Contents... 2 2 Overview... 3 3 Definitions...
Enterprise Content Management System Monitor 5.1 Agent Debugging Guide Revision 1.3 2014-11-05 CENIT AG Author: Stefan Bettighofer 1 Table of Contents 1 Table of Contents... 2 2 Overview... 3 3 Definitions...
RIPS. A static source code analyser for vulnerabilities in PHP scripts. NDS Seminar. A static source code analyser for vulnerabilities in PHP scripts
 NDS Seminar 1 1.1 Motivation 1.2 PHP Vulnerabilities 1.3 Taint Analysis 1.4 Static VS Dynamic Code Analysis : RIPS 2.1 Configuration 2.2 The Tokenizer 2.3 Token Analysis 2.4 Webinterface 2.5 Results 2.6
NDS Seminar 1 1.1 Motivation 1.2 PHP Vulnerabilities 1.3 Taint Analysis 1.4 Static VS Dynamic Code Analysis : RIPS 2.1 Configuration 2.2 The Tokenizer 2.3 Token Analysis 2.4 Webinterface 2.5 Results 2.6
Tutorial on C Language Programming
 Tutorial on C Language Programming Teodor Rus rus@cs.uiowa.edu The University of Iowa, Department of Computer Science Introduction to System Software p.1/64 Tutorial on C programming C program structure:
Tutorial on C Language Programming Teodor Rus rus@cs.uiowa.edu The University of Iowa, Department of Computer Science Introduction to System Software p.1/64 Tutorial on C programming C program structure:
Pixy: A Static Analysis Tool for Detecting Web Application Vulnerabilities (Technical Report)
 Pixy: A Static Analysis Tool for Detecting Web Application Vulnerabilities (Technical Report) Nenad Jovanovic, Christopher Kruegel, Engin Kirda Secure Systems Lab Vienna University of Technology Abstract
Pixy: A Static Analysis Tool for Detecting Web Application Vulnerabilities (Technical Report) Nenad Jovanovic, Christopher Kruegel, Engin Kirda Secure Systems Lab Vienna University of Technology Abstract
How I hacked PacketStorm (1988-2000)
 Outline Recap Secure Programming Lecture 8++: SQL Injection David Aspinall, Informatics @ Edinburgh 13th February 2014 Overview Some past attacks Reminder: basics Classification Injection route and motive
Outline Recap Secure Programming Lecture 8++: SQL Injection David Aspinall, Informatics @ Edinburgh 13th February 2014 Overview Some past attacks Reminder: basics Classification Injection route and motive
SQL Injection Attack Lab
 Laboratory for Computer Security Education 1 SQL Injection Attack Lab Copyright c 2006-2010 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
Laboratory for Computer Security Education 1 SQL Injection Attack Lab Copyright c 2006-2010 Wenliang Du, Syracuse University. The development of this document is funded by the National Science Foundation
Introduction to Synoptic
 Introduction to Synoptic 1 Introduction Synoptic is a tool that summarizes log files. More exactly, Synoptic takes a set of log files, and some rules that tell it how to interpret lines in those logs,
Introduction to Synoptic 1 Introduction Synoptic is a tool that summarizes log files. More exactly, Synoptic takes a set of log files, and some rules that tell it how to interpret lines in those logs,
NEVER guess an e-mail address. Your mail will nearly always go to the wrong person.
 16. WebMail (E-mail) E-mail is a mechanism for sending messages and information between computer users. Individuals are identified by their e-mail address, which is used in much the same way as a postal
16. WebMail (E-mail) E-mail is a mechanism for sending messages and information between computer users. Individuals are identified by their e-mail address, which is used in much the same way as a postal
JDK 1.5 Updates for Introduction to Java Programming with SUN ONE Studio 4
 JDK 1.5 Updates for Introduction to Java Programming with SUN ONE Studio 4 NOTE: SUN ONE Studio is almost identical with NetBeans. NetBeans is open source and can be downloaded from www.netbeans.org. I
JDK 1.5 Updates for Introduction to Java Programming with SUN ONE Studio 4 NOTE: SUN ONE Studio is almost identical with NetBeans. NetBeans is open source and can be downloaded from www.netbeans.org. I
CSCI110 Exercise 4: Database - MySQL
 CSCI110 Exercise 4: Database - MySQL The exercise This exercise is to be completed in the laboratory and your completed work is to be shown to the laboratory tutor. The work should be done in week-8 but
CSCI110 Exercise 4: Database - MySQL The exercise This exercise is to be completed in the laboratory and your completed work is to be shown to the laboratory tutor. The work should be done in week-8 but
Compiler Construction
 Compiler Construction Lecture 1 - An Overview 2003 Robert M. Siegfried All rights reserved A few basic definitions Translate - v, a.to turn into one s own language or another. b. to transform or turn from
Compiler Construction Lecture 1 - An Overview 2003 Robert M. Siegfried All rights reserved A few basic definitions Translate - v, a.to turn into one s own language or another. b. to transform or turn from
Fachgebiet Technische Informatik, Joachim Zumbrägel
 Computer Network Lab 2015 Fachgebiet Technische Informatik, Joachim Zumbrägel Overview Internet Internet Protocols Fundamentals about HTTP Communication HTTP-Server, mode of operation Static/Dynamic Webpages
Computer Network Lab 2015 Fachgebiet Technische Informatik, Joachim Zumbrägel Overview Internet Internet Protocols Fundamentals about HTTP Communication HTTP-Server, mode of operation Static/Dynamic Webpages
Concepts and terminology in the Simula Programming Language
 Concepts and terminology in the Simula Programming Language An introduction for new readers of Simula literature Stein Krogdahl Department of Informatics University of Oslo, Norway April 2010 Introduction
Concepts and terminology in the Simula Programming Language An introduction for new readers of Simula literature Stein Krogdahl Department of Informatics University of Oslo, Norway April 2010 Introduction
PHP Authentication Schemes
 7 PHP Authentication Schemes IN THIS CHAPTER Overview Generating Passwords Authenticating User Against Text Files Authenticating Users by IP Address Authenticating Users Using HTTP Authentication Authenticating
7 PHP Authentication Schemes IN THIS CHAPTER Overview Generating Passwords Authenticating User Against Text Files Authenticating Users by IP Address Authenticating Users Using HTTP Authentication Authenticating
A Brief Introduction to MySQL
 A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
A Brief Introduction to MySQL by Derek Schuurman Introduction to Databases A database is a structured collection of logically related data. One common type of database is the relational database, a term
Package GEOquery. August 18, 2015
 Type Package Package GEOquery August 18, 2015 Title Get data from NCBI Gene Expression Omnibus (GEO) Version 2.34.0 Date 2014-09-28 Author Maintainer BugReports
Type Package Package GEOquery August 18, 2015 Title Get data from NCBI Gene Expression Omnibus (GEO) Version 2.34.0 Date 2014-09-28 Author Maintainer BugReports
Web applications. Web security: web basics. HTTP requests. URLs. GET request. Myrto Arapinis School of Informatics University of Edinburgh
 Web applications Web security: web basics Myrto Arapinis School of Informatics University of Edinburgh HTTP March 19, 2015 Client Server Database (HTML, JavaScript) (PHP) (SQL) 1 / 24 2 / 24 URLs HTTP
Web applications Web security: web basics Myrto Arapinis School of Informatics University of Edinburgh HTTP March 19, 2015 Client Server Database (HTML, JavaScript) (PHP) (SQL) 1 / 24 2 / 24 URLs HTTP
Dove User Guide Copyright 2010-2011 Virgil Trasca
 Dove User Guide Dove User Guide Copyright 2010-2011 Virgil Trasca Table of Contents 1. Introduction... 1 2. Distribute reports and documents... 3 Email... 3 Messages and templates... 3 Which message is
Dove User Guide Dove User Guide Copyright 2010-2011 Virgil Trasca Table of Contents 1. Introduction... 1 2. Distribute reports and documents... 3 Email... 3 Messages and templates... 3 Which message is
http://algs4.cs.princeton.edu dictionary find definition word definition book index find relevant pages term list of page numbers
 ROBERT SEDGEWICK KEVI WAYE F O U R T H E D I T I O ROBERT SEDGEWICK KEVI WAYE ROBERT SEDGEWICK KEVI WAYE Symbol tables Symbol table applications Key-value pair abstraction. Insert a value with specified.
ROBERT SEDGEWICK KEVI WAYE F O U R T H E D I T I O ROBERT SEDGEWICK KEVI WAYE ROBERT SEDGEWICK KEVI WAYE Symbol tables Symbol table applications Key-value pair abstraction. Insert a value with specified.
INTRUSION PROTECTION AGAINST SQL INJECTION ATTACKS USING REVERSE PROXY
 INTRUSION PROTECTION AGAINST SQL INJECTION ATTACKS USING REVERSE PROXY Asst.Prof. S.N.Wandre Computer Engg. Dept. SIT,Lonavala University of Pune, snw.sit@sinhgad.edu Gitanjali Dabhade Monika Ghodake Gayatri
INTRUSION PROTECTION AGAINST SQL INJECTION ATTACKS USING REVERSE PROXY Asst.Prof. S.N.Wandre Computer Engg. Dept. SIT,Lonavala University of Pune, snw.sit@sinhgad.edu Gitanjali Dabhade Monika Ghodake Gayatri
Web Portal User Guide. Version 6.0
 Web Portal User Guide Version 6.0 2013 Pitney Bowes Software Inc. All rights reserved. This document may contain confidential and proprietary information belonging to Pitney Bowes Inc. and/or its subsidiaries
Web Portal User Guide Version 6.0 2013 Pitney Bowes Software Inc. All rights reserved. This document may contain confidential and proprietary information belonging to Pitney Bowes Inc. and/or its subsidiaries
CS 111 Classes I 1. Software Organization View to this point:
 CS 111 Classes I 1 Software Organization View to this point: Data Objects and primitive types Primitive types operators (+, /,,*, %). int, float, double, char, boolean Memory location holds the data Objects
CS 111 Classes I 1 Software Organization View to this point: Data Objects and primitive types Primitive types operators (+, /,,*, %). int, float, double, char, boolean Memory location holds the data Objects
Privilege Manager for Unix How To
 Privilege Manager for Unix How To Administer Event and Keystroke Logs Event and Keystroke Logs Quest One Privilege Manager for UNIX can record two different types of log information for audit purposes.
Privilege Manager for Unix How To Administer Event and Keystroke Logs Event and Keystroke Logs Quest One Privilege Manager for UNIX can record two different types of log information for audit purposes.
Object Oriented Software Design
 Object Oriented Software Design Introduction to Java - II Giuseppe Lipari http://retis.sssup.it/~lipari Scuola Superiore Sant Anna Pisa September 14, 2011 G. Lipari (Scuola Superiore Sant Anna) Introduction
Object Oriented Software Design Introduction to Java - II Giuseppe Lipari http://retis.sssup.it/~lipari Scuola Superiore Sant Anna Pisa September 14, 2011 G. Lipari (Scuola Superiore Sant Anna) Introduction
RoleCast: Finding Missing Security Checks When You Do Not Know What Checks Are
 RoleCast: Finding Missing Security Checks When You Do Not Know What Checks Are Sooel Son The University of Texas at Austin samuel@cs.utexas.edu Kathryn S. McKinley Microsoft Research and The University
RoleCast: Finding Missing Security Checks When You Do Not Know What Checks Are Sooel Son The University of Texas at Austin samuel@cs.utexas.edu Kathryn S. McKinley Microsoft Research and The University
Web Forensic Evidence of SQL Injection Analysis
 International Journal of Science and Engineering Vol.5 No.1(2015):157-162 157 Web Forensic Evidence of SQL Injection Analysis 針 對 SQL Injection 攻 擊 鑑 識 之 分 析 Chinyang Henry Tseng 1 National Taipei University
International Journal of Science and Engineering Vol.5 No.1(2015):157-162 157 Web Forensic Evidence of SQL Injection Analysis 針 對 SQL Injection 攻 擊 鑑 識 之 分 析 Chinyang Henry Tseng 1 National Taipei University
A binary search tree or BST is a binary tree that is either empty or in which the data element of each node has a key, and:
 Binary Search Trees 1 The general binary tree shown in the previous chapter is not terribly useful in practice. The chief use of binary trees is for providing rapid access to data (indexing, if you will)
Binary Search Trees 1 The general binary tree shown in the previous chapter is not terribly useful in practice. The chief use of binary trees is for providing rapid access to data (indexing, if you will)
PART-A Questions. 2. How does an enumerated statement differ from a typedef statement?
 1. Distinguish & and && operators. PART-A Questions 2. How does an enumerated statement differ from a typedef statement? 3. What are the various members of a class? 4. Who can access the protected members
1. Distinguish & and && operators. PART-A Questions 2. How does an enumerated statement differ from a typedef statement? 3. What are the various members of a class? 4. Who can access the protected members
Setting up the integration between Oracle Social Engagement & Monitoring Cloud Service and Oracle RightNow Cloud Service
 An Oracle Best Practice Guide November 2013 Setting up the integration between Oracle Social Engagement & Monitoring Cloud Service and Oracle RightNow Cloud Service Introduction Creation of the custom
An Oracle Best Practice Guide November 2013 Setting up the integration between Oracle Social Engagement & Monitoring Cloud Service and Oracle RightNow Cloud Service Introduction Creation of the custom
Cross-Site Scripting Prevention with Dynamic Data Tainting and Static Analysis
 Cross-Site Scripting Prevention with Dynamic Data Tainting and Static Analysis Philipp Vogt, Florian Nentwich, Nenad Jovanovic, Engin Kirda, Christopher Kruegel, and Giovanni Vigna Secure Systems Lab Technical
Cross-Site Scripting Prevention with Dynamic Data Tainting and Static Analysis Philipp Vogt, Florian Nentwich, Nenad Jovanovic, Engin Kirda, Christopher Kruegel, and Giovanni Vigna Secure Systems Lab Technical
Cross-Site Scripting Prevention with Dynamic Data Tainting and Static Analysis
 Cross-Site Scripting Prevention with Dynamic Data Tainting and Static Analysis Philipp Vogt, Florian Nentwich, Nenad Jovanovic, Engin Kirda, Christopher Kruegel, and Giovanni Vigna Secure Systems Lab Technical
Cross-Site Scripting Prevention with Dynamic Data Tainting and Static Analysis Philipp Vogt, Florian Nentwich, Nenad Jovanovic, Engin Kirda, Christopher Kruegel, and Giovanni Vigna Secure Systems Lab Technical
Static vs. Dynamic. Lecture 10: Static Semantics Overview 1. Typical Semantic Errors: Java, C++ Typical Tasks of the Semantic Analyzer
 Lecture 10: Static Semantics Overview 1 Lexical analysis Produces tokens Detects & eliminates illegal tokens Parsing Produces trees Detects & eliminates ill-formed parse trees Static semantic analysis
Lecture 10: Static Semantics Overview 1 Lexical analysis Produces tokens Detects & eliminates illegal tokens Parsing Produces trees Detects & eliminates ill-formed parse trees Static semantic analysis
Unix Scripts and Job Scheduling
 Unix Scripts and Job Scheduling Michael B. Spring Department of Information Science and Telecommunications University of Pittsburgh spring@imap.pitt.edu http://www.sis.pitt.edu/~spring Overview Shell Scripts
Unix Scripts and Job Scheduling Michael B. Spring Department of Information Science and Telecommunications University of Pittsburgh spring@imap.pitt.edu http://www.sis.pitt.edu/~spring Overview Shell Scripts
X-ROAD 6 SIGNER CONSOLE USER GUIDE
 X-ROAD 6 SIGNER CONSOLE USER GUIDE 2.2 Signer Console User Guide Page 2 VERSION HISTORY Date Version Description 20.11.2014 0.1 First draft 20.11.2014 0.2 Some improvements done 1.12.2014 1.0 Minor corrections
X-ROAD 6 SIGNER CONSOLE USER GUIDE 2.2 Signer Console User Guide Page 2 VERSION HISTORY Date Version Description 20.11.2014 0.1 First draft 20.11.2014 0.2 Some improvements done 1.12.2014 1.0 Minor corrections
PRI-(BASIC2) Preliminary Reference Information Mod date 3. Jun. 2015
 PRI-(BASIC2) Table of content Introduction...2 New Comment...2 Long variable...2 Function definition...3 Function declaration...3 Function return value...3 Keyword return inside functions...4 Function
PRI-(BASIC2) Table of content Introduction...2 New Comment...2 Long variable...2 Function definition...3 Function declaration...3 Function return value...3 Keyword return inside functions...4 Function
Monday, April 8, 13. Creating Successful Magento ERP Integrations
 Creating Successful Magento ERP Integrations Happy Together Creating Successful Magento ERP Integrations David Alger CTO / Lead Engineer www.classyllama.com A Little About Me Exclusively focused on Magento
Creating Successful Magento ERP Integrations Happy Together Creating Successful Magento ERP Integrations David Alger CTO / Lead Engineer www.classyllama.com A Little About Me Exclusively focused on Magento
Document Structure Integrity: A Robust Basis for Cross-Site Scripting Defense
 Document Structure Integrity: A Robust Basis for Cross-Site Scripting Defense Yacin Nadji Illinois Institute Of Technology Prateek Saxena UC Berkeley Dawn Song UC Berkeley 1 A Cross-Site Scripting Attack
Document Structure Integrity: A Robust Basis for Cross-Site Scripting Defense Yacin Nadji Illinois Institute Of Technology Prateek Saxena UC Berkeley Dawn Song UC Berkeley 1 A Cross-Site Scripting Attack
Secure Application Development with the Zend Framework
 Secure Application Development with the Zend Framework By Stefan Esser Who? Stefan Esser from Cologne / Germany in IT security since 1998 PHP core developer since 2001 Month of PHP Bugs/Security and Suhosin
Secure Application Development with the Zend Framework By Stefan Esser Who? Stefan Esser from Cologne / Germany in IT security since 1998 PHP core developer since 2001 Month of PHP Bugs/Security and Suhosin
Tachyon: a Meta-circular Optimizing JavaScript Virtual Machine
 Tachyon: a Meta-circular Optimizing JavaScript Virtual Machine Maxime Chevalier-Boisvert Erick Lavoie Marc Feeley Bruno Dufour {chevalma, lavoeric, feeley, dufour}@iro.umontreal.ca DIRO - Université de
Tachyon: a Meta-circular Optimizing JavaScript Virtual Machine Maxime Chevalier-Boisvert Erick Lavoie Marc Feeley Bruno Dufour {chevalma, lavoeric, feeley, dufour}@iro.umontreal.ca DIRO - Université de
SQL injection: Not only AND 1=1. The OWASP Foundation. Bernardo Damele A. G. Penetration Tester Portcullis Computer Security Ltd
 SQL injection: Not only AND 1=1 Bernardo Damele A. G. Penetration Tester Portcullis Computer Security Ltd bernardo.damele@gmail.com +44 7788962949 Copyright Bernardo Damele Assumpcao Guimaraes Permission
SQL injection: Not only AND 1=1 Bernardo Damele A. G. Penetration Tester Portcullis Computer Security Ltd bernardo.damele@gmail.com +44 7788962949 Copyright Bernardo Damele Assumpcao Guimaraes Permission
Information and Computer Science Department ICS 324 Database Systems Lab#11 SQL-Basic Query
 Information and Computer Science Department ICS 324 Database Systems Lab#11 SQL-Basic Query Objectives The objective of this lab is to learn the query language of SQL. Outcomes After completing this Lab,
Information and Computer Science Department ICS 324 Database Systems Lab#11 SQL-Basic Query Objectives The objective of this lab is to learn the query language of SQL. Outcomes After completing this Lab,
Once logged in you will have two options to access your e mails
 How do I access Webmail? Webmail You can access web mail at:- http://stu.utt.edu.tt:2095 or https://stu.utt.edu.tt:2096 Enter email address i.e. user name (full email address needed eg. fn.ln@stu.utt.edu.tt
How do I access Webmail? Webmail You can access web mail at:- http://stu.utt.edu.tt:2095 or https://stu.utt.edu.tt:2096 Enter email address i.e. user name (full email address needed eg. fn.ln@stu.utt.edu.tt
SQL Server An Overview
 SQL Server An Overview SQL Server Microsoft SQL Server is designed to work effectively in a number of environments: As a two-tier or multi-tier client/server database system As a desktop database system
SQL Server An Overview SQL Server Microsoft SQL Server is designed to work effectively in a number of environments: As a two-tier or multi-tier client/server database system As a desktop database system
ODBC Client Driver Help. 2015 Kepware, Inc.
 2015 Kepware, Inc. 2 Table of Contents Table of Contents 2 4 Overview 4 External Dependencies 4 Driver Setup 5 Data Source Settings 5 Data Source Setup 6 Data Source Access Methods 13 Fixed Table 14 Table
2015 Kepware, Inc. 2 Table of Contents Table of Contents 2 4 Overview 4 External Dependencies 4 Driver Setup 5 Data Source Settings 5 Data Source Setup 6 Data Source Access Methods 13 Fixed Table 14 Table
CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS
 66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
Algorithms and Data Structures Written Exam Proposed SOLUTION
 Algorithms and Data Structures Written Exam Proposed SOLUTION 2005-01-07 from 09:00 to 13:00 Allowed tools: A standard calculator. Grading criteria: You can get at most 30 points. For an E, 15 points are
Algorithms and Data Structures Written Exam Proposed SOLUTION 2005-01-07 from 09:00 to 13:00 Allowed tools: A standard calculator. Grading criteria: You can get at most 30 points. For an E, 15 points are
The PHP 5.4 Features You Will Actually Use
 The PHP 5.4 Features You Will Actually Use About Me Lorna Jane Mitchell PHP Consultant/Developer Author of PHP Master (Sitepoint) and PHP Web Services (O Reilly) Twitter: @lornajane Website: http://lornajane.net
The PHP 5.4 Features You Will Actually Use About Me Lorna Jane Mitchell PHP Consultant/Developer Author of PHP Master (Sitepoint) and PHP Web Services (O Reilly) Twitter: @lornajane Website: http://lornajane.net
C++ INTERVIEW QUESTIONS
 C++ INTERVIEW QUESTIONS http://www.tutorialspoint.com/cplusplus/cpp_interview_questions.htm Copyright tutorialspoint.com Dear readers, these C++ Interview Questions have been designed specially to get
C++ INTERVIEW QUESTIONS http://www.tutorialspoint.com/cplusplus/cpp_interview_questions.htm Copyright tutorialspoint.com Dear readers, these C++ Interview Questions have been designed specially to get
Black Hat Briefings USA 2004 Cameron Hotchkies cameron@0x90.org
 Blind SQL Injection Automation Techniques Black Hat Briefings USA 2004 Cameron Hotchkies cameron@0x90.org What is SQL Injection? Client supplied data passed to an application without appropriate data validation
Blind SQL Injection Automation Techniques Black Hat Briefings USA 2004 Cameron Hotchkies cameron@0x90.org What is SQL Injection? Client supplied data passed to an application without appropriate data validation
Nintex Workflow 2013 Help
 Nintex Workflow 2013 Help Last updated: Wednesday, January 15, 2014 1 Workflow Actions... 7 1.1 Action Set... 7 1.2 Add User To AD Group... 8 1.3 Assign Flexi Task... 10 1.4 Assign To-Do Task... 25 1.5
Nintex Workflow 2013 Help Last updated: Wednesday, January 15, 2014 1 Workflow Actions... 7 1.1 Action Set... 7 1.2 Add User To AD Group... 8 1.3 Assign Flexi Task... 10 1.4 Assign To-Do Task... 25 1.5
Chapter 5 Names, Bindings, Type Checking, and Scopes
 Chapter 5 Names, Bindings, Type Checking, and Scopes Chapter 5 Topics Introduction Names Variables The Concept of Binding Type Checking Strong Typing Scope Scope and Lifetime Referencing Environments Named
Chapter 5 Names, Bindings, Type Checking, and Scopes Chapter 5 Topics Introduction Names Variables The Concept of Binding Type Checking Strong Typing Scope Scope and Lifetime Referencing Environments Named
Object Oriented Software Design
 Object Oriented Software Design Introduction to Java - II Giuseppe Lipari http://retis.sssup.it/~lipari Scuola Superiore Sant Anna Pisa October 28, 2010 G. Lipari (Scuola Superiore Sant Anna) Introduction
Object Oriented Software Design Introduction to Java - II Giuseppe Lipari http://retis.sssup.it/~lipari Scuola Superiore Sant Anna Pisa October 28, 2010 G. Lipari (Scuola Superiore Sant Anna) Introduction
Programming Assignment II Due Date: See online CISC 672 schedule Individual Assignment
 Programming Assignment II Due Date: See online CISC 672 schedule Individual Assignment 1 Overview Programming assignments II V will direct you to design and build a compiler for Cool. Each assignment will
Programming Assignment II Due Date: See online CISC 672 schedule Individual Assignment 1 Overview Programming assignments II V will direct you to design and build a compiler for Cool. Each assignment will
Detecting (and even preventing) SQL Injection Using the Percona Toolkit and Noinject!
 Detecting (and even preventing) SQL Injection Using the Percona Toolkit and Noinject! Justin Swanhart Percona Live, April 2013 INTRODUCTION 2 Introduction 3 Who am I? What do I do? Why am I here? The tools
Detecting (and even preventing) SQL Injection Using the Percona Toolkit and Noinject! Justin Swanhart Percona Live, April 2013 INTRODUCTION 2 Introduction 3 Who am I? What do I do? Why am I here? The tools
Static Taint-Analysis on Binary Executables
 Static Taint-Analysis on Binary Executables Sanjay Rawat, Laurent Mounier, Marie-Laure Potet VERIMAG University of Grenoble October 2011 Static Taint-Analysis on Binary Executables 1/29 Outline 1 Introduction
Static Taint-Analysis on Binary Executables Sanjay Rawat, Laurent Mounier, Marie-Laure Potet VERIMAG University of Grenoble October 2011 Static Taint-Analysis on Binary Executables 1/29 Outline 1 Introduction
Precisely Target the Right Audience
 Precisely Target the Right Audience With Upsight Segmentation, you can create custom user segments from any combination of the 11 dimensions where Upsight automatically collects data. These segments provide
Precisely Target the Right Audience With Upsight Segmentation, you can create custom user segments from any combination of the 11 dimensions where Upsight automatically collects data. These segments provide
cs2010: algorithms and data structures
 cs2010: algorithms and data structures Lecture 11: Symbol Table ADT. Vasileios Koutavas 28 Oct 2015 School of Computer Science and Statistics Trinity College Dublin Algorithms ROBERT SEDGEWICK KEVIN WAYNE
cs2010: algorithms and data structures Lecture 11: Symbol Table ADT. Vasileios Koutavas 28 Oct 2015 School of Computer Science and Statistics Trinity College Dublin Algorithms ROBERT SEDGEWICK KEVIN WAYNE
Introduction to Java
 Introduction to Java The HelloWorld program Primitive data types Assignment and arithmetic operations User input Conditional statements Looping Arrays CSA0011 Matthew Xuereb 2008 1 Java Overview A high
Introduction to Java The HelloWorld program Primitive data types Assignment and arithmetic operations User input Conditional statements Looping Arrays CSA0011 Matthew Xuereb 2008 1 Java Overview A high
RT Support Ticket System
 Table of Contents RT Self Service Panel Login... 1 Creating a New Ticket... 1 Reviewing the Ticket... 3 Reading a Thread... 3 Resolving a Ticket... 4 Re-opening a Ticket... 4 Note: At the time of purchase,
Table of Contents RT Self Service Panel Login... 1 Creating a New Ticket... 1 Reviewing the Ticket... 3 Reading a Thread... 3 Resolving a Ticket... 4 Re-opening a Ticket... 4 Note: At the time of purchase,
Automatic Creation of SQL Injection and Cross-Site Scripting Attacks Adam Kiezun, Philip J. Guo, Karthick Jayaraman, and Michael D.
 Computer Science and Artificial Intelligence Laboratory Technical Report MIT-CSAIL-TR-2008-054 September 10, 2008 Automatic Creation of SQL Injection and Cross-Site Scripting Attacks Adam Kiezun, Philip
Computer Science and Artificial Intelligence Laboratory Technical Report MIT-CSAIL-TR-2008-054 September 10, 2008 Automatic Creation of SQL Injection and Cross-Site Scripting Attacks Adam Kiezun, Philip
Intel Retail Client Manager Audience Analytics
 Intel Retail Client Manager Audience Analytics By using this document, in addition to any agreements you have with Intel, you accept the terms set forth below. You may not use or facilitate the use of
Intel Retail Client Manager Audience Analytics By using this document, in addition to any agreements you have with Intel, you accept the terms set forth below. You may not use or facilitate the use of
