Accountable Key Infrastructure (AKI): A Proposal for a Public-Key Validation Infrastructure
|
|
|
- Christal Riley
- 8 years ago
- Views:
Transcription
1 Accountable Key Infrastructure (AKI): A Proposal for a Public-Key Validation Infrastructure Tiffany Hyun-Jin Kim Lin-Shung Huang Adrian Perrig Collin Jackson Virgil Gligor CyLab / Carnegie Mellon University {hyunjin1,adrian,virgil}@ece.cmu.edu {linshung.huang,collin.jackson}@sv.cmu.edu ABSTRACT Recent trends in public-key infrastructure research explore the tradeoff between decreased trust in Certificate Authorities (CAs), resilience against attacks, communication overhead (bandwidth and latency) for setting up an SSL/TLS connection, and availability with respect to verifiability of public key information. In this paper, we propose AKI as a new public-key validation infrastructure, to reduce the level of trust in CAs. AKI integrates an architecture for key revocation of all entities (e.g., CAs, domains) with an architecture for accountability of all infrastructure parties through checks-and-balances. AKI efficiently handles common certification operations, and gracefully handles catastrophic events such as domain key loss or compromise. We propose AKI to make progress towards a public-key validation infrastructure with key revocation that reduces trust in any single entity. Categories and Subject Descriptors K.6.5 [MANAGEMENT OF COMPUTING AND INFORMA- TION SYSTEMS]: Security and Protection Authentication; C.2.0 [COMPUTER-COMMUNICATION NETWORKS]: General Security and protection Keywords Public-Key Infrastructure, SSL, TLS, certificate validation, public log servers, accountability. 1. INTRODUCTION Secure connection establishment on the Internet through SSL and TLS has been a tremendous success, as it is globally used for practically all secure web-based communication. Given that the security of the majority of network-based financial or commercial transactions relies on SSL/TLS, one would hope that its security is commensurate with its proliferation and importance. Unfortunately, numerous attack vectors against SSL/TLS exist and recently several high-profile attacks have demonstrated its vulnerability in practice. The main weakness lies in the fact that current browsers trust hundreds of root Certificate Authority (CA) certificates, and a security breach of a single CA can compromise the security of sites protected by any one of the other CAs, powerfully An earlier version of this paper was published as a technical report [18]. Copyright is held by the International World Wide Web Conference Committee (IW3C2). IW3C2 reserves the right to provide a hyperlink to the author s site if the Material is used in electronic media. WWW 2013, May 13 17, 2013, Rio de Janeiro, Brazil. ACM /13/05. illustrating the concept of weakest-link security. In fact, a maliciously issued certificate for a site can be used by an adversary to mount Man-in-the-Middle (MitM) attacks on connections to that site. To demonstrate the large extent of the SSL universe in which the weakest link could occur, EFF s SSL Observatory reports that Microsoft IE and Mozilla Firefox trust 1482 different CA public keys [13]. Since CAs are in the business of managing cryptographic keys, they are expected to have secure processes in place to protect their keys. Regrettably, recent events have highlighted the inability of several CAs to keep their keys and certificate issuance processes secure. We list a few high-profile cases that were recently discovered. In March 2011, in an attack on a Comodo reseller, fake certificates were issued for mail.google.com, login.yahoo.com, login.skype.com, login.live.com, and addons.mozilla.org [11, 27]. Comodo suggested that the attack originated from an Iranian IP address. In August 2011, news broke that DigiNotar, a Dutch CA, improperly issued a certificate for all Google domains to an external party [30]. It was claimed that as many as 250 false certificates for an unknown number of domains were released. It was reported that these certificates were used by the Iranian government to spy on Iranian citizens communications with Google during the month of August For the Stuxnet malware, two Taiwanese CAs private keys were compromised, which the Stuxnet developers used to sign their malware [14]. Since not all CA vulnerabilities become public, we expect that an even larger number of CA-breaches may have occurred. These examples demonstrate that CA breaches can result in realworld attacks. Besides CA-based attacks, SSL/TLS has other vulnerabilities, for example the fact that users click through browser warnings in case of self-signed certificates [12]. In Syria, such an attack was used to mount a MitM attack against Facebook [10], supposedly by the Syrian Telecom Ministry. Addressing these problems is very challenging, as several seemingly conflicting requirements need to be satisfied. On one hand, adversarial events such as CA private key compromise or domain private key compromise need to be addressed. On the other hand, legitimate events such as switching to different CAs or key recreation after private key loss need to be supported. For example, legitimate re-creation of a key pair and certificate after private-key loss may appear to be an impersonation attempt. Also, legitimately switching to a new CA to cease using a compromised CA that signs fraudulent certificates may also appear as a malicious event. Hence, we aim to create a certificate infrastructure that can prevent adversarial attacks yet gracefully handle legitimate key and certificate management events. We design a new certificate validation infrastructure to address these challenges. Our proposal is called Accountable Key Infras-
2 tructure (AKI), integrating an architecture for key revocation of all entities (e.g., CAs, domains) with an architecture for accountability of all infrastructure parties through checks-and-balances. AKI efficiently handles common certification operations and gracefully handles catastrophic events such as domain key loss or compromise. We propose AKI to make progress towards a public-key validation infrastructure with key revocation that reduces trust in any single entity. To accomplish these goals, we leverage globally visible directories (i.e., public log servers) that enable public integrity validation for certificate information. Such public validation provides accountability for CA s actions, and thus creates deterrence against fraudulent CA activities. To reduce the number of trusted CAs, a domain can define which and how many CAs are required to update the certificate. To enable recovery from unanticipated events, certificates can be updated through another set of CAs; however, the certificates become active after a domainspecified hold time. In case of fraudulent updates, legitimate domains can react during the hold time to have the fraudulent certificate removed. To evaluate the security, availability, and efficiency of our publickey validation infrastructure and to enable comparison between different systems, we propose a new set of metrics. Specifically, we propose Duration of Compromise (DoC), Duration of Unavailability (DoU), and several efficiency metrics. The DoC metrics provide insight into the security of a system, measuring the impact of a compromise or loss of various credentials, such as the private key of CAs or domains. The DoU metrics measure availability, again depending on various events such as key compromise or loss. Finally, the efficiency metrics measure the overhead of operating the public-key validation infrastructure and the overhead of secure session establishment. We present these metrics in detail in Section PROBLEM DEFINITION The core problem we aim to address is the design of a new public-key validation infrastructure that reduces the amount of trust placed in any one infrastructure component (e.g., CA), yet reduces the system s attack surface and single points of failure. Additional goals are efficiency and incentives for deployment for all associated parties. In this section, we first describe a list of desired properties, followed by assumptions and the adversary model. Detailed metrics for evaluation are described in Section Desired Properties Checks and balances: The infrastructure should limit trust in any single party, and limited trust should be distributed over multiple parties to prevent a single point of failure. Furthermore, parties can monitor each other to detect misbehavior. Brief compromise period: Given the compromise of a private key of any trusted party, the time during which an attacker can successfully attack a legitimate client should be brief. This includes the compromise of CAs, public log servers, or domains. Brief unavailability period: After various events (benign or adversarial), the time during which a legitimate client (who is not under an attack) cannot verify a domain s certificate should be brief. This includes when a domain s certificate is newly registered or updated, and when the CAs, log servers, and domains private keys are compromised. Trust agility: Users can decide which entities they trust to form their root of trust, and they can modify their trust decisions at any time [24]. Furthermore, such changes should be made without undue delay. We extend this notion of trust agility to domains, enabling domains to select their roots of trust and to modify their trust decisions at any time. Privacy: Clients should not reveal which entity/server they establish an SSL/TLS connection with. Efficiency: One of the most important efficiency requirements is to avoid increasing the latency of an SSL/TLS connection establishment in particular, avoiding any additional round-trips to external servers. Moreover, no additional infrastructure servers should be needed. 2.2 Assumptions In our approach of checks and balances, we assume a set of entities that do not collude: CAs, public log servers, and validators. We assume that these entities audit each others accountable operations and disseminate detected misbehavior. In the context of the current Internet, the Electronic Frontier Foundation (EFF) may be one entity that would play the role of a validator entity, for example. We assume that browsers store the authentic public keys of CAs, public log servers, and validators. We also assume that all parties are loosely time synchronized (up to a few minutes). 2.3 Adversary Model We consider an adversary whose main goal is to impersonate a victim web site that is using HTTPS. To achieve this goal, the adversary may compromise some infrastructure servers that the victim trusts. An adversary may be able to temporarily gain control of some infrastructure servers that the victim trusts, but can gain long-term control of infrastructure servers that the victim does not trust. Gaining control means access to private signing keys. 3. BACKGROUND Two main families of proposals to reduce trust in CAs exist that are related to our design: (1) certificate observatories and (2) timeline servers that provide public visibility into all certificate operations. We briefly provide an overview of these approaches. 3.1 Certificate Observatories The first type to reduce the trust in CAs and prevent many of the attacks discussed in Section 1 is to create a public repository of SSL/TLS server certificates and enable browsers to compare the key they have received (presumably from the server) with the observation of the observatory which is received over an integrityprotected connection. This integrity-protected connection is set up by embedding a root public key of the observatory system into the client, creating a PKI just to authenticate the relatively small number of observatory nodes. Perspectives. The Perspectives system [2, 33] has globally distributed notary servers that contact known SSL / TLS servers once a day to fetch the current server s certificate. These notary servers then store the history of observed certificates and support queries into their database. Perspectives offers a Firefox plugin, which contacts a random subset of notary servers after an HTTPS connection is opened, to compare the notary certificate observations with the received certificate. A configurable policy decides if the received certificate is presumed valid. Convergence. Convergence [1] enhances Perspectives in several dimensions, most notably providing privacy for certificate lookups by including a two-step onion routing approach, where the first Convergence server redirects the query to a second server, and the second server responds (the first server knows the identity of the querier, but not the web site queried, and the second server only knows the query but not the querier). SSL Observatory. EFF s SSL Observatory [13] also collects global certificate information. However, it does not frequently update the information nor support any online queries.
3 Discussion. The main advantage of these certificate observatories is that server operators need not be aware of this approach. Hence, no additional steps are necessary on their part. The approach even works to validate self-signed certificates. These systems are also effective to prevent numerous CA-based attacks, for example, all the attacks in Iran [11, 27] and Syria [10] would have been prevented, as the illegitimate certificates would have been detected as different from the legitimate server certificates. The main disadvantage of these systems is that they require additional connections to query the observatories, resulting in higher latency for establishing an HTTPS connection. Another disadvantage is a period of unavailability for new and updated certificates. However, this can be remedied with a scheme where a new certificate is offered ahead of time to the observation servers, but this approach negates one of the main advantages of these systems in that they do not require assistance from the server operators. 3.2 Certificate Log Servers Certificate Transparency [20 22] and Sovereign Keys [9] are two recent proposals that suggest a public log to record all certificate transactions. Certificate Transparency (CT). In CT [20 22], the authors construct an append-only log by using an append-only Merkle hash tree structure, enabling efficient validation of each certificate that was added to the log. More specifically, domains register their certificates and obtain a non-repudiable statement (audit proof) that their certificate has been added to the append-only log. Domain owners provide the audit proof along with the certificate such that clients can validate whether the certificate was included in the log. Sovereign Keys (SK). In the SK model, timeline servers act similar to timestamping servers [15]. In SK, the first registration of a certificate binds the key to the domain name, preventing any subsequent registrations for the same name. Only the legitimate owner of the certificate has the private key, enabling revocation and reregistration of the name with a new public key. The browser can contact the timeline server to inspect if the received server certificate is indeed the correct certificate registered in the timeline server s log. To reduce the load on timeline servers, distributed mirror servers store a copy of the timeline server database to efficiently disseminate information. Discussion. The public log proposed by CT and SK creates accountability for a CA s actions, an idea which we build on in this paper. The main advantage of the log is that it prevents the attacks mentioned in the introduction. For example, compelled certificates [28] are simply invalid in this framework, as the legitimate owner did not approve the newly generated key. Unfortunately, CT and SK have some shortcomings. CT and SK do not specify any revocation mechanism for audit proofs, which indicates that audit proofs are valid indefinitely. Instead, CT relies on other approaches such as Certificate Revocation Lists, Online Certificate Status Protocol, Revocation Transparency [19], etc. Thus, these approaches currently do not handle events such as private key loss or compromise of a domain. For SK, the browser needs to query a mirror server to download the server s certificate history, increasing latency, decreasing availability, and sacrificing privacy. In Section 9, we discuss these systems in more detail. 4. AKI: Accountable Key Infrastructure Before we describe the details of AKI, we first provide a highlevel overview. The main entities in our system are as follows. A Domain (server) represents a named entity with which clients desire to establish secure connections. CA 2 A.com 1 CA 1 2 (K A, K -1 ) A (K CA, K -1 ) CA ILS (K ILS, K -1 ) ILS Cert, {Root} Cert 1 = { A.com, K A } K -1 CA 1 Cert 2 = { A.com, K A } K -1 CA 2 Cert = {Cert 1 Cert 2 } K -1 ILS, h 1 1 Is {Root} K -1 the current root for ILS? ILS Browser Yes / No Verifies Cert and ILS verification information Verifies Cert Adds Cert to ILS Creates ILS proof: A.com Root {Root} K -1 ILS h = {Hash tree verification nodes} Validators Figure 1: AKI certificate registration process. This figure depicts A.com registering a certificate (signed by two CAs) to a single ILS, but the domain can acquire multiple certificates from multiple CAs and register to multiple ILSs. Dashed arrows represent occasional communications. A Client (browser) is an entity establishing TLS connections with domains (servers). A Certification Agency (CA) is similar to a current certificate authority that certifies domains public keys, but agency instead of authority indicates that CAs are not absolute authorities any more in AKI. In addition to current systems, Integrity Log Server (ILS) Operators (ILSO) are Internet services that operate ILSs that log domains certificates and make them publicly available. Each ILS maintains an Integrity Tree, which is a hash tree of all the registered certificates in lexicographic order. All ILS operations (i.e., log data entries such as registration, updates, and revocation) are digitally signed. We envision that large ISPs or widely available Internet-based corporations such as Amazon or Google will operate ILSs. Validators are entities that monitor ILS operations, by downloading the entire ILS data structure and performing consistency checks. Consistency checks include validation that certificate updates follow the certificate policy or that certificates do not suddenly disappear from the log. Non-governmental Internet governance organizations, such as the EFF, could serve as validators. In the case of ILSO misbehavior, validators disseminate incriminating information without requiring their own authentication information. Figure 1 depicts an overview of our AKI architecture. Alice owns domain A.com and wants to obtain an AKI-protected certificate, as she wants to protect herself against compromise of the CAs that signed her certificate and other rogue CAs, and protect her clients against compelled certificates. To define the security properties that she intends to achieve for her domain, Alice defines CAs and ILSOs that she trusts, the minimum number of CA signatures that she recommends her clients for validation, and rules for certificate revocation, replacement, and updates. Alice includes these parameters with her public key and contacts more than the minimum number of trusted CAs (according to her security policy) to sign her certificate. She then registers the certificate with one or multiple ILSs. Each ILS adds A.com to its database, by placing it in the Integrity Tree. The ILS then re-computes hash values over all stored certificates for updated verification information. Alice now supplements her certificate with the verification information that she downloads from every ILS, and sends it to browsers that connect to her web site via HTTPS. For certificate validation, the browser uses the trusted root-ca certificates as in current practice, and uses the pre-installed ILS public key(s) on her browser to validate ILS information.
4 Before trusting the ILS information received from Alice, the client browser occasionally checks with validators to confirm that the ILSs current root hash values are valid. To reduce latency, we also describe later how the the web server can staple validator information during the HTTPS connection setup. 4.1 AKI Details We discuss the details of AKI based on the following stages: certificate creation, CA signature acquisition, ILS registration, browserbased validation, ILS tree update, certificate update, and certificate revocation and recovery. Certificate creation. AKI certificates contain several extensions over standard X.509 certificates and feature the following additional fields: Trusted CAs (CA_LIST): This field contains a list of trusted CAs for creating a new certificate. Trusted ILSs (ILS_LIST): This field contains a list of trusted ILSs where the certificate is registered. ILS validation proof timeout (ILS_TIMEOUT): This field indicates how long an ILS proof is acceptable to the browser after the proof creation time. The tradeoff is among efficiency, availability, and robustness to compromise. A long timeout requires fewer queries to the ILS for an updated proof, but increases the amount of time until a certificate can be revoked. This parameter typically varies from one hour to one day. Minimum number of CAs to generate an AKI certificate (CA_MIN): This field indicates the number of CA signatures required to initially register a certificate to ILS and to update a certificate. This parameter is typically set to 1 or 2. Threshold number of CAs for certificate re-establishment (CA_TH): This field indicates the minimum number of CA signatures needed to re-establish a certificate in case of a lost private key. In other words, this parameter indicates the number of different CA signatures that can activate the new key for the domain that lost its key. An attacker can register a certificate to an ILS for a domain who is unaware of AKI, and select CA_TH to be high such that the domain can never revoke the adversary s certificate. To prevent such an attack, we set CA_TH = CA_MIN + 1. Cool-off period for an unlinked certificate (COP_ UNLINKED): This field indicates the minimum cool-off period for a new certificate that is not linked to the old certificate (i.e., the new public key is not signed by the previous private key of the domain). In AKI, registering a new certificate does not automatically validate it:. Instead, AKI enforces a cool-off period until a new certificate becomes valid which will replace the previous certificate. This enables protection against an adversary who quickly registers a new key following a CA compromise, as the legitimate owner can revoke the new certificate during the cool-off period. An attacker can register a new key for a domain that is unaware of AKI and set COP_UNLINKED to be high to prevent the domain owner from re-acquiring the ILS entry. To prevent such an attack, an upper bound exists for COP_UNLINKED (e.g., 7 days). Cool-off period for a certificate from an untrusted CA (COP_UNTRUSTED): This field indicates the minimum cool-off period for a new certificate that is signed by a CA that is not inca_list. In case of a lost or compromised private key, an attacker can acquire a certificate signed by some CA (that the domain owner does not trust), and this parameter provides time to enable the legitimate owner to revoke the bogus certificate. We recommend that COP_UNTRUSTED is defined to be longer 2 hours ago 1 hour ago c.com b.com a.com Integrity Tree Now Root z.com y.com x.com Time Figure 2: AKI Integrity Tree structure. thancop_unlinked. For similar reasons as forcop_unlinked, COP_UNTRUSTED has an upper bound (e.g., 10 days). CA signature acquisition. After creating a certificate with AKI extensions, the domain contacts the CA_MIN number of CAs from CA_LIST to acquire CA signatures. In AKI, the combination of all the CAs and ILS signatures validates the domain s AKI certificate. Hence, care must be taken to include all the CAs serial numbers and timestamps, and the X.509 standard will need to be amended to enable such multi-signatures (discussed in Appendix A). ILS registration. The domain then contacts one or more of the trusted ILSs (fromils_list) to register the AKI certificate. The ILS data structure to store AKI certificates is based on a binary hash tree, called Integrity Tree, as depicted in Figure 2. All AKI certificates are placed at the leaf nodes of the binary hash tree, sorted in lexicographic order. AKI uses a sorted hash tree as opposed to a linear list as in previous work [9, 22] for the following reasons: 1) The hash tree efficiently represents the current state of all distinct names, and its height only depends on the number of different entries but not on time (i.e., it does not grow taller with revocations/re-establishments, thus removing a source of DoS). 2) The height is logarithmic in the number of entries. Hence, a validation of any leaf node can be efficiently represented based on an authenticated root node and a logarithmic number of nodes to re-compute the root node from the leaf node. 3) The sorting enables quick verification of the absence of an entry, whereas in a linear list, the entire list needs to be searched. As depicted in Figure 2, the Integrity Tree enables independent validators to check the integrity of the entire data structure. The hash chaining of the trees enables temporal re-construction of all operations, similar to a timestamping service or the timeline server data structure [9, 22]. When adding a new AKI certificate, the ILS first verifies whether an entry already exists in its Integrity Tree for the same domain name. (In Section 6 we discuss how an ILS checks other ILSs to ensure name uniqueness.) If the name is indeed new, the ILS schedules the AKI certificate to be added to the Integrity Tree. The ILS creates a registration confirmation of the successful addition through a digital signature with its private key, and returns it to the domain. The ILS registration confirmation contains a proof of absence that the name is not present in the Integrity Tree, preventing a malicious ILS from minting forged registration confirmations if the name is already registered. The domain also obtains a signed statement from validators that they have seen the registration confirmation, and the domain can use this ILS registration confirmation and validator statement to start using the new certificate for a limited time, until the ILS generates the next Integrity Tree which will include the new certificate as a leaf node. Figure 3 depicts the certificate registration process. The ILS update period (ILS_UP) is the interval between two tree updates; at every ILS_UP, an ILS finalizes and commits the
5 A.com requests to register its AKI certificate Is A.com a new entry in ILS? (A.com exists in ILS) N Is new key signed by old key? N Σ CA_TH? N Registration fails Y Y Y Σ CA_MIN? All CAs from CA_LIST? Y N Registration fails N All signed CAs from CA_LIST? Y N Wait for cool-off period (COP_UNTRUSTED) Wait for cool-off period (COP_UNLINKED) Y Register at next update time and send ILS confirmation Figure 3: Flowchart of ILS certificate registration, update, revocation and recovery. Upon receiving a certificate registration request from A.com, the ILS follows this flowchart and plans to add the certificates. Σ stands for the CA signatures that A.com obtained. next Integrity Tree. At this point, the domain contacts the ILS to request the signed root node ({Root} K 1 ) and the hash tree verification nodes (h) that are needed to validate its certificate as depicted ILS in Figure 2, where ILS_UP is set to one hour. In practice, ILS_UP is set to one or two hours, to enable quick certificate revocation. ILS verification information is combined with the AKI certificate to enable client browsers to validate the ILS information without the need to contact an ILS during the TLS connection setup. Browser-based validation. The browser receives the validator and ILS information together with the server/domain s AKI certificate during the second phase of the TLS protocol. 1 The CA signatures are validated using the browser s CA root certificates, and the ILS and validator information is validated using the ILS and validator public keys stored in the browser. The ILS_TIMEOUT field in the AKI certificate is validated to ensure that the ILS information is sufficiently recent depending on the domain s preferences specified in the certificate. In Section 6, we discuss incremental deployment issues, considering the actions an AKI-enabled browser should perform when presented with a legacy TLS certificate. ILS tree update. Periodically at a well-specified time, the ILS updates its Integrity Tree by purging AKI certificates that have been revoked or expired without renewal. The ILS also activates certificates that have passed their cool-off periods. We envision update intervals of an hour up to a day. Hourly updates enable more fine-grained certificate revocation but increase overhead, as servers/domains need to frequently query the new signed root value to ensure that their certificates remain unchanged. Certificate update. Before an AKI certificate expires, the domain creates a new private key, and requests the trusted CAs in CA_LIST to sign the new key. The domain also signs the new key with its previous private key. After gathering CA_MIN number of CA signatures, the domain combines all signatures and other relevant information into an AKI certificate. The domain then sends the AKI 1 To avoid additional latency and privacy leakage by the browser, the domain directly contacts relevant ILSs and validators, and passes the ILS and validator information to the browser. The browser would specify as part of the TLS handshake which CA/ILS/validator information it already has and which information it still seeks to receive. Note that the domain only needs to contact the ILS once every ILS_TIMEOUT time period and when the ILS switches to a new Integrity Tree (i.e., everyils_up). Then the domain can give that ILS information to the client browser. The validator needs to be contacted every ILS_UP time period to authenticate the ILS Integrity Tree root value. certificate with an update request to the ILS, which will readily accept the new AKI certificate since it is signed with the domain s old key and the update request is signed by both new and old keys. (Requiring a signature with the new key confirms possession of the new private key.) There is no cool-off period in this case, and the new AKI certificate is added when the ILS creates the next Integrity Tree. Hence, the new key can be readily used. Certificate revocation and recovery. In case a key needs to be prematurely removed, a certificate revocation message needs to be sent to the ILS. Either the private key corresponding to the certificate s public key is used to sign the revocation message, or a special revocation key can be used, for which the public key is included in the certificate. The point of using a different revocation key could speed up recovery for the case where the main private key is compromised, as a shorter cool-off period can be used if the new public key would be signed by the revocation key. The cool-off periods (COP_UNLINKED, COP_UNTRUSTED) in the AKI certificate specify the amount of time that needs to elapse before the new certificate becomes active. In case of private key compromise (and potentially private revocation key compromise), the COP_UNLINKED and COP_UNTRUSTED values enable the legitimate owner to react and revoke a fraudulent certificate that was potentially registered by the adversary. 2 Since some domains may not have the best key secrecy and availability practices in place, we need to consider the case of catastrophic key compromise and loss when only the adversary is in possession of all secrets. In that case, we need recovery mechanisms where the legitimate owner can re-gain control of its domain. By contacting CA_TH number of CAs and obtaining signatures on a fresh key, the legitimate owner can eventually re-gain control. However, the adversary will be able to use the key until a valid revocation message arrives. 4.2 Checks and Balances among Parties In this section, we describe how AKI achieves checks and balances among CAs, ILSs, validators, domain owners, and clients to reduce trust and prevent misbehavior by any party. Figure 4 illustrates what each party monitors and how each party reports. An important aspect of AKI is that all actions are digitally signed, such that any misbehavior can be demonstrated based on the entities signatures. Consequently, an accusation for misbehavior can be checked without trusting the accuser, ruling out slander attacks. Equivocation is an example for a misbehavior, where one party provides different answers to the same query for example an ILS server who would create two different Integrity Trees in a given time period and uses either tree to respond to different entities. Since only a single Integrity Tree can exist per ILS per time period, the demonstration of the two ILS-signed Integrity Trees demonstrates ILS misbehavior. Validation by CAs. Once the domain owner acquires signatures from trusted CAs for the certificate, the CAs monitor the ILS for any malicious changes in the domain s ILS entry. If the ILS makes a potentially invalid update (e.g., updated certificate without any of the trusted CAs signatures), the CAs immediately inform the domain owner. Validation by validators. Validators maintain a list of revoked ILSs that are detected for misbehavior. Validators disseminate the revoked ILSs, especially to the domain owners who are registered to those revoked ILSs, in which case the domain owners attempt to register with other valid ILSs. Thanks to the fact that all ILS operations are signed, the validator can easily demonstrate misbehavior 2 We envision that trusted CAs would sign these revocation messages.
6 CA Unknown changes in domain s entry? Report ILS misbehavior Created bogus certificate? Consistent certificate for domain in multiple ILSs? Bogus entry exists for domain? ILSs Domain Equivocation exists for domain? Report ILS behavior Correct operation? Report ILS misbehavior Current root value? Validators Provide list of revoked ILS Report CA misbehavior Current root for ILS? Client Report ILS misbehavior Monitoring Reporting Figure 4: Checks and balances among AKI entities. In AKI, each entity monitors other entity for misbehavior detection and reports to other entities. in case the signed records are inconsistent with the ILS s state. In the absence of a compromised ILS private key, a validator cannot perform a slander attack, as it cannot forge signatures that would incriminate the ILS for malicious behavior. Validation by domain owners. Prior to initial registration of a certificate to an ILS, the domain first ensures that a CA has not created a bogus certificate for that domain by checking the ILS as follows: the domain owner queries the ILS for entries that are lexicographically adjacent to its entry in the Integrity Tree. After confirming that no entry exists for the domain, the domain owner registers its certificate with the ILS. Validation by clients. A client browser obtains ILS and validator information from the domain s web server. The browser may also check ILSs and validators directly. In case of any inconsistent information, the client will report such misbehavior to validators for further dissemination. 5. SECURITY ANALYSIS In this paper, we provide an informal analysis of the AKI architecture. We are working on a formal analysis, which we will publish in a paper currently under preparation. The main security property we aim to achieve is the prevention of successful impersonation of a victim server. More concretely, given a domain S with a certificate C S, an adversary M attempts to impersonate S to a client C during the TLS connection establishment. The attack succeeds if C has a connection with M while believing that the connection is with S. We assume that S uses an AKI certificate, and that C uses an AKI-enabled browser. We argue that AKI is resilient against attackers that compromise different entities private keys. M compromises S s private key. Assuming S detects the compromise, it can immediately revoke the key. However, M can use the key until time t 0 +ILS_TIMEOUT period, where t 0 is the time when the certificate had been revoked at the ILS. The domain s selection of ILS_TIMEOUT depends on its choice of tradeoff between availability, overhead, and duration of impersonation after compromise. To re-instantiate a key after compromise, there is an unavailability period (COP_UNLINKED as specified in the certificate) in case the domain lost access to its private key. However, if the domain owner still has access to the private key, it can obtain trusted CA signatures for its new key, sign it with its old key, and immediately obtain an ILS confirmation that will enable use of the new key. M compromises CAs private keys. As long as fewer thanca_th keys of trusted CAs in CA_LIST are compromised, there is no impact on browsers who contact the trusted ILSs. The CA_LIST evicts untrusted CAs from the set of potential weak links. Given a small well-selected list of trusted CAs, it is highly unlikely that more than a threshold number are compromised. Even in case more than the CA_TH number of CAs are compromised, a newly registered key will have to cool off during the prolonged period (CA_UNLINKED) as the fraudulent certificate is not linked to the previous one (as we assume that S s private key was not compromised in this case). Such an extended time should leave sufficient time for S to detect and react to the impersonation attempt, without suffering any compromise (thanks to trusted CAs who watch out for ILS entry changes). If S s private key was compromised in addition, M can impersonate S during the entire CA_UNLINKED period. However, this case is exceedingly unlikely, as several well-selected CAs and the domain s private key all need to be compromised at the same time. An adversary can also contact a different ILS to register an AKI certificate for a victim domain whose AKI certificate is already registered at a legitimate ILS. If ILSs coordinate their name spaces, as we discuss in Section 6, this attack is prevented. M compromises ILSs private keys. We consider three attacks: equivocation with multiple Integrity Trees, fake entries for S.com in same Integrity Tree, and forged ILS confirmations. As we argue in the following analysis, a compromised ILS is not sufficient to perform a MitM attack on a server with an existing AKI certificate. If M attempts to perform equivocation (i.e., create a shadow Integrity Tree with malicious entries and then answer queries from either tree depending on the querier), validators can readily detect this since they need to sign off the Integrity Tree root value in each time period for clients to accept the ILS information. If an ILS provides different information to different validators, then domains can detect this as they contact different validators and disseminate the information amongst validators. Since ILSs need to sign off the Integrity Tree root value, all the operations performed since the previous Integrity Tree need to be correct, thus, the ILS has very limited opportunity to manipulate the tree, e.g., removal and introduction of a fake certificate would not be possible unless it follows the correct policy of the certificate. The fact that the Integrity Tree root value prevents equivocation even helps in the case when M compromises CAs private keys in addition to the ILS s. If M attempts to re-register a new key, S can detect this behavior (as we discuss in Section 4.1) and raise an alarm. If M attempts to provide different answers to S s queries, it would need to create different Integrity Trees within one time period, which can be detected as described in the previous paragraph. Another attack for M would be to attempt to create two different entries for S.com at different places in the Integrity Tree, one for the legitimate S.com and the other for a fraudulent S.com. In this scenario, M would provide the legitimate response to S s queries, and a fraudulent certificate for other queries. Fortunately, this case is easily detectable by the validators, as the leaf nodes would not be in sorted order. Placing the two leaf nodes next to each other will be detected by S, when it also queries for the leaf nodes that are adjacent to its certificate in the Integrity Tree. Another case is where M misuses the ILS s compromised private key to sign fake ILS registration confirmations, which would enable a freshly generated and initially registered AKI certificate to be immediately used and trusted by AKI-enabled browsers. The proof of absence that is part of the registration confirmation though prevents the ILS from creating such confirmations for names that are already registered. Since domains register the ILS registration confirmation with validators, the absence of the name in the next Integrity Tree can be detected.
7 6. DISCUSSION Censorship resilience. Corporations/governments may want to eavesdrop on all employees /citizens communication. More specifically, corporations/governments can set up their own CA and ILS that create fake certificates. In such a case, users can opt out by installing legitimate CAs and ILSs as roots of trust. Moreover, malicious behavior can be easily collected and demonstrated to the world. Absence of ILS information during incremental deployment. Similar to Extended Validation (EV) certificates, absence of ILS information may not raise any suspicions. To prevent an attack where a non-aki certificate is used to attack a domain that is using an AKI-certificate, we require browsers to contact ILSs trusted by the browser to validate the absence of AKI information. 3 In the absence of an ILS response, the browser needs to abort the connection. Note that no additional latency is required for deploying sites, since they provide the ILS information during the SSL handshake; only legacy domains and attackers have additional latency. Hence, this additional latency provides a positive incentive for adoption at domains. In some legitimate environments, ILSs may not be reachable, for example paywalls at airports or hotels do not permit any external connections until the user has authenticated, paid, or accepted the terms of service. A challenge then is: how can the browser verify the non-aki certificate of the paywall service without access to the ILSs? In this case, geographically-linked certificates [17] can be used, or the paywall obtains an AKI-certificate. In case of legacy certificates, a browser would need to contact several ILSs and could only proceed when receiving a negative response from all ILSs, which would increase latency considerably, deterring initial AKI adopters. To speed up this process, ILSs could sign a Bloom Filter representing the set of entities in its Integrity Tree. Browsers would then only contact an ILS if the entity is in the ILS s Bloom Filter. Since Bloom Filters have a tunable falsepositive rate, the browser may unnecessarily contact the ILS for a small fraction of legacy domains. Unfortunately, freshly registered certificates are not yet part of the Integrity Tree, thus they would not be part of the Bloom Filter either (unless the Bloom Filter is generated and distributed frequently), so a malicious legacy certificate could be used to impersonate a site until it is properly added to the Integrity Tree. Since such Bloom Filters would only be needed during initial phases of AKI adoption, we feel that the efficiency-security tradeoff is worthwhile, especially for short ILS update periods. Globally consistent registration. Ideally, all global ILSs coordinate registration and provide one global name space, preventing the same name to be registered at different ILSs with different certificates. However, global coordination is challenging to implement in practice, as different global entities mutually distrust each other. An example is where a rogue CA issues a bogus certificate for A.com, presumably the CA and the requester of A.com are in a different legal region from the legitimate owner of A.com preventing the conflict to be locally resolved through legal means. In such cases of inconsistent registrations, the CAs local to the registered name of A.com obtain precedence in determining the correct certificate. If the foreign ILS does not unregister the conflicting entry, it loses its credibility and will be subsequently ignored. It is the 3 In AKI, ILSs can provide proofs of non-existence by providing the authenticated Integrity Tree leaf nodes before and after the point where the domain in question would be located at (since all the nodes are sorted in lexicographic order). task of the validators to document, store, and disseminate such incriminating ILS information. The SCION architecture [34] offers isolation among Trust Domains with uniform legal environments. By defining trusted CAs, ILSs, and validators within each Trust Domain, and by binding DNS name spaces to Trust Domains, SCION greatly simplifies consistency issues, as it is clear which CAs, ILSs, and validators are responsible for the certificate validation. Within a Trust Domain, these entities can coordinate to prevent registration of rogue certificates. Usability. Prior work has shown that users ignore and click through certificate warnings [31]. However, AKI can identify real attacks and completely block users from proceeding without an option to click through. Interaction with HSTS. AKI does not address SSL stripping [23] attacks where an adversary actively rewrites HTTPS links to HTTP links while eavesdropping HTTP traffic. Against such attacks, websites can force clients to always use HTTPS by declaring the HTTP Strict Transport Security (HSTS) header [16]. Furthermore, HSTS treats certificate warnings as fatal errors as does AKI. AKI extends HSTS by requiring valid ILS information for AKI certificates. 7. REALIZATION IN PRACTICE To demonstrate the feasibility of AKI in a real-world setting, we built a prototype as a proof-of-concept system. For testing, we created a CA with OpenSSL. We pre-installed the CA and ILS root certificates on our servers and clients. We implemented an ILS server in Python that maintains an AKI Integrity Tree. The Integrity Tree node hashes were computed with SHA-256, and the root node was signed with RSA We used Coordinated Universal Time (UTC) to define precedence for domain to key mappings and to audit timeline integrity. We configured a stock Nginx HTTP server to serve our AKI-certificates, which are basically X.509 certificates with custom AKI extension fields (described in Section 4.1). We implemented our AKI client in the Chromium web browser. ILS proof stapling. To deliver fresh ILS proofs for AKI-certificates to clients, we explored the following options. One option is to let CAs embed the ILS proof in the certificate itself, by inserting it into a certificate extension. However, once the certificate file is updated with a time-bounded ILS proof, the hash of the updated certificate would not match the original certificate recorded in the ILS Integrity Tree. To avoid this issue, another option is to let servers send the ILS proofs over the TLS handshake, utilizing a TLS extension. An alternative is to provide the ILS proof in a separate dummy certificate, appended to the leaf of the server s certificate chain. In our prototype, we sent ILS proofs via TLS extensions, given that Nginx currently supports the TLS Certificate Status Request extension (primarily used for OCSP stapling). This allows our server to deliver ILS proofs as a stapled response over the TLS handshake to clients without modifying Nginx. The server could use a side-loaded script to periodically fetch fresh ILS proofs and load them into Nginx. We modified the Chromium browser to extract the embedded ILS proofs via the TLSCertificate Status Request extension, and validate the ILS proofs. Performance cost. AKI induces no round trip latencies (no extra network requests) to the TLS handshake. However, AKI increases the TLS handshake message size by roughly a kilobyte due to ILS proof stapling (assuming millions of domain names registered to the ILS). The ILS proof is composed from the following constituents: a list of authentication node hashes (32 bytes per node), a timestamp (4 bytes), and a root node signature (256 bytes). Further, the server s certificate size is slightly increased (by roughly 40 bytes) due to the additional custom X.509 extension.
8 We measured the client validation processing time in Chromium on a machine with 2.26 GHz dual-core CPU and 4 GB RAM, tested with a million domains registered at the ILS. The overall AKI processing time averaged 990 µs (median = 936 µs). Specifically, the RSA verification step averaged 880 µs (median = 831 µs), while the Merkle verification step only averaged 95 µs (median = 87 µs). The overall AKI processing time is relatively small, especially compared to other approaches, such as Perspectives and Sovereign Keys that require several network round-trips to communicate with servers. 4 Another advantage of using Integrity Trees that are relatively infrequently updated means that RSA verifications on the client side are amortized, as we envision that many domains will use the same set of ILSs, hence the root of the Integrity Tree will remain the same for numerous sites. Consequently, clients mostly only perform efficient hash tree verifications and only rarely perform signature verifications. 8. RELATED WORK Several proposals to detect malicious key changes have been proposed, such as Monkeysphere Web-of-Trust for SSL [3], the EFF s SSL observatory [13], and Certificate Patrol [4]. These proposals make it easy to detect key changes, but it is difficult to distinguish legitimate key changes from attacks. Langley et al. [5] implemented a public key pinning mechanism in Google Chrome. The browser vendor maintains a list of trustworthy public key(s) associated with each site. Public key pinning provides similar security benefits to AKI by preventing certificates signed by rogue CA from being accepted by the browser. Typically the keys of trusted CAs are pinned, allowing for an orderly transition from one certificate to the next. To address the scalability challenges of a browser vendor maintained database, the Public Key Pinning Extension for HTTP [6] generalizes this mechanism to an HTTP header that allows a server to declare the keys that can be used in the future for that domain name. Choosing a pin duration that is too long risks a lengthy period of unavailability for the site. Furthermore, if the user is visiting the site for the first time on a device or the pin has expired, no protection is provided. By contrast, AKI provides protection on the first visit to the site. Marlinspike and Perrin propose Trust Assertions for Certificate Keys (TACK) which pins public keys generated by the domain owners themselves [25]. More specifically, a server generates a TACK key pair, and use the TACK private key to sign the TLS public key. The TACK public key and the signature form the TACK, which clients can see in the TLS extension field, and clients pin the domain s TACK public key after observing the consistent TACK multiple times. Although TACK aims at removing complete trust in CAs, TACK relies on frequent visit patterns by clients to pin the domain s public key, resulting in a long initial unavailability period for every site. Furthermore, if a certificate becomes compromised and the pin is still inactive, the client must delete the observed TACK information. In contrast, AKI provides no initial unavailability period for any site, providing protection on the first visit to the site. Short-lived certificates [32] in conjunction with browser vendor maintained Certificate Revocation Lists (CRLs) can reduce the impact of key compromise. This requires servers to provide certificates with a short validity lifetime and update them from the CA on a daily basis. Short-lived certificates provide similar security benefits to OCSP while eliminating the need for an online check 4 A previous study indicates that round-trip latencies for OCSP lookups cost a mean of 497 ms with a median of 291 ms in realworld deployments [29]. during the HTTPS handshake. However, unlike AKI, they rely on browser vendors to somehow detect certificates that are issued by compromised CAs and block them using a browser vendor maintained blacklist. DNS-based Authentication of Named Entities (DANE) securely binds certificates with domain names using Domain Name System Security Extensions (DNSSEC), enabling domain holders to assert certificates without reference to CAs [8]. However, the security of DANE heavily relies on the security of DNS operators. In the following section, we perform an in-depth comparison of all the closely related certificate validation infrastructures. 9. THEORETICAL COMPARISON In this section, we compare AKI with other proposals with respect to security, availability, and efficiency metrics. One of the contributions of this paper is to establish a set of metrics for comparison, which we present in the following subsection. 9.1 Evaluation Metrics for Comparison Security metrics. The main security metric is Duration of Compromise (DoC): given the compromise of a private key, 5 for how long can a domain be impersonated? This metric can be specified with respect to the following cases: DoC after a trusted CA s private key compromise: This case also covers compelled certificates [28]. DoC after untrusted CA s private key compromise: This case is important for AKI, where a domain defines trusted and untrusted CAs. DoC after trusted public log server s private key compromise: To avoid a proliferation of cases, we do not consider untrusted log server s private key compromise, as it is a strictly weaker attack scenario. DoC after domain s private key compromise: This metric measures the DoC, for how long an adversary can misuse the captured private key. We define the DoC as the duration during which a key is revoked or the domain bootstraps a new key which invalidates the old key, whichever is earlier. Security guarantees of new systems can sometimes be circumvented due to required compatibility issues with legacy systems. For example, Extended Validation (EV) certificates or OCSP information in a certificate are both optional extensions, and their absence does not raise any suspicions. Therefore, even if an entity obtains an EV certificate and uses OCSP, an adversary can still obtain a fraudulent non-ev certificate without OCSP extensions that will enable MitM attacks. To measure the security of public key validation infrastructures during incremental deployment, we propose the following metric: Protection during incremental deployment: This is a binary measure to characterize whether any security is offered while compatibility with legacy systems needs to be ensured. Finally, we measure privacy of client requests. Connection privacy: information about a client is not leaked to entities other than the contacted domain. Availability Metrics. The main availability metric we use is Duration of Unavailability (DoU) of a domain s certificate after various 5 In a private key compromise, the key is disclosed to the adversary. Depending on the attack, the legitimate owner may still possess the key.
9 Table 1: Comparison of different public-key validation infrastructures based on the security, availability, and efficiency metrics. Entries in bold red font indicate major disadvantages of the corresponding scheme. Server stands for the ILS, DNS, Notary, or OCSP responder server, depending on which scheme is used. U corresponds to the public log servers update interval, which is in practice on the order of one hour. Section 9.2 describes our methodology for filling in the entries. CA+CRL CA+OCSP SLC Security Trusted CA compromise (compelled certificate) DoC days days days days N/A hours Untrusted CA key compromise DoC days days days 0 N/A Trusted Server key compromise DoC N/A 0 N/A N/A N/A days days days days 0 Domain key compromise DoC hours min days days <month hours day min ILS_TIMEOUT Protection during incremental deployment N/A N N Y N N Y Y Y Y Connection privacy Y N Y Y Y Y N/Y N Y Y Availability Initial registration DoU days hours days Planned key update DoU days hours Unplanned key update DoU days hours days CA compromise DoU days days days days N/A days Server compromise DoU days days N/A N/A N/A days days days days up to 1 day Domain compromise DoU min min min min <month hours days 0 U COP_UNLINKED Efficiency Number of additional servers required 0 O(C) O(D) O(C) O(C) O(D) O(D) Additional latency for TLS connection setup 0 RTT RTT RTT 0 0 Additional bandwidth for TLS connection setup 0 0.1KB KB 0.1KB 10KB 1KB 1KB 1KB Key Pinning TACK DANE Perspectives Convergence SK CT AKI system events. The shorter the DoU, the more available the system. We do not consider DDoS attacks in this paper; thus, we assume the general availability of all servers and communication networks. DoU after initial registration: This metric measures the time duration until the registered certificate becomes valid. DoU after planned key update: This metric measures the duration when an updated key becomes valid, which was planned to replace the current key. DoU after unplanned key update: In case of unplanned events such as losing a domain s private and backup keys, this metric measures the time duration when the updated key becomes valid. DoU after trusted CA s private key compromise: After a trusted CA s key becomes compromised, a domain s certificate may also become invalid. This metric measures the time to acquire a new certificate using the CA s new key. DoU after a trusted log server s private key compromise: A log server s public key compromise leads to invalid log entries. This metric measures the time to recover a log server s private key. DoU after domain s private key compromise: This metric measures the time until the domain s certificate becomes available with a new private key. Efficiency Metrics. Below is a list of metrics to measure the efficiency of certificate infrastructures: Number of additional servers required: This metric measures how many additional infrastructure servers are required, expressed as an order in the number of new connections established. For example, if C connections are established to D different domains, would we require O(C) +O(D) additional servers, O(D), or even O(1)? Additional latency to establish a secure connection: Compared to standard TLS, what additional latency would be required for a secure connection with the proposed scheme? Communication overhead: This metric measures the additional network overhead incurred for establishing a secure connection. In addition, we will evaluate schemes based on their ability for domains to select their trust perimeter (with respect to CAs and public log servers), as well as providing flexibility for certificate policies, such as specification to achieve different tradeoffs between availability and security metrics as defined above. 9.2 Comparison of Approaches Based on our metrics, Table 1 compares AKI with the following proposals: CA + CRL [7], CA + OCSP [26], Short-Lived Certificates (SLC) [32], Key Pinning [5], TACK [25], DANE [8], Perspectives (P) [33], Convergence (C) [1], Sovereign Keys (SK) [9], and Certificate Transparency (CT) [21]. We now discuss the methodology we used to fill in the table. For many of the catastrophic failures, such as compromise of a trusted CA or ILS private key, we assume that a software update is required to revoke the old key and setup a new key. We assume that such a software update is secure, and can be completed within a few days for most users. Security. For the Trusted CA compromise (compelled certificate) DoC metric, we assume that it will take days to push out a CA root certificate revocation message through a browser update, which was the method used to revoke DigiNotar s certificate after the compromise [30]. While some browsers use CRLs to revoke CA keys (e.g., Google Chrome), most browsers still require a software update. OCSP unfortunately does not help in this case, since CAs do not use OCSP to validate their root certificates. Similarly in the case of SLC and DANE, a browser update is required to revoke the CA key. Also in the case of Key Pinning, a browser update is required to remove the pin. Since P/C/CC, and TACK do not rely on CAs, the DoC is 0. Audit-log based schemes also protect from this case, preventing even a trusted CA from registering a new bogus certificate (the security analysis in Section 5 presents this case in more detail for AKI). For the following properties, we explain the metrics in a less verbose manner. For the Untrusted CA key compromise DoC metric, the impact is less than in the previous case. In particular for DANE, the adversary cannot impersonate the domain which was possible in the trusted case. For the Trusted Server key compromise DoC, we consider that the ILS/DNS/Notary/OCSP responder server s private key is compromised, resulting in a severe disruption for several approaches. Since no additional third parties exist in CA + CRL, SLC, and Key Pinning, this case is N/A for those schemes. Since a compromised
10 OCSP server s private key does not enable creation of a fake key, DoC is 0. On the other hand, if the TACK key is compromised, recovery can take up to 30 days, depending on the domain s parameter setting. In the case of a compromised notary key in P/C/CC, we assume that a software update would require days to be fully deployed, during which time attacks are feasible. SK and CT would also require a software update, requiring days for full deployment. In AKI, a malicious ILS or malicious validator alone is insufficient to mount an attack, as we discuss in Section 5. For the Domain key compromise DoC metric, we assume that browsers download CRLs every few hours; thus, the DoC for CA + CRL is on the order of hours. For SLC, it may take a few days for the certificate to expire. In TACK, it may require up to a month to have clients switch to a new key. For DANE, it may require hours until DNS entries time out and get replaced by new entries with the updated key information. In P/C/CC, depending on the client configuration, it can take days for an updated key to be consistently observed. Although the online validation of SK revocation is very fast, CT will require more time since stale validation information may be served by the adversary. For AKI, validation information is valid during domain-selected time ILS_TIMEOUT, which is on the order of several hours to one day, until the key is revoked. For Protection during incremental deployment, OCSP, and SLC offer no security, since an adversary can create a legacy certificate without any of these extensions which clients would accept. In TACK, a rollback to a compromised certificate attack is possible at the onset, when the TACK pin is not yet set up. For DANE, DNS responses may be rolled back to non-signed DNS replies. P/C/CC, SK, CT, and AKI all perform an online lookup for the case of a legacy certificate, which will reveal the legacy certificate. Connection privacy is not provided by OCSP, Perspectives, and SK, as the client performs an online lookup for each certificate. Convergence, however, uses a blinding step during lookup. Availability. Initial registration DoU requires several days for TACK and P/C/CC to confidently learn a new entry. In DANE, the current DNS entry needs to time out for the updated DNS entry to become available, which we estimate to take hours in the common case. For Planned key update DoU, we consider an optimization we discuss in Section 3, where domains pre-register a key with the notary servers, thus avoiding activation latency. For Unplanned key update DoU, we assume that P/C/CC use a configured policy where a key has to have been consistently observed for several days for clients to trust the key. For CA compromise DoU and Server compromise DoU, we assume that several days are required to recover and roll out new root keys. In key pinning, we assume that one day is required to push out a new software version with a new key. Domain compromise DoU indicates the delay required to register a new key. Efficiency. For the metric Number of additional servers required, we specify D for the number of domains and C for the number of connections established per day. For example, O(D) indicates that the number of additional servers needs to be proportional to the number of domains. For the metric Additional latency for TLS connection setup, we denote a round-trip time to a server by RTT, which includes server processing time. Since P/C/CC, SK, and OCSP also involve additional external connections, they can have a significant time overhead. For Additional bandwidth for TLS connection setup, we list the order of magnitude of additional bandwidth required to set up a TLS connection. For the case of SK, CT, and AKI, we assume that extra signatures are on the order of 256 Bytes, hash tree values are on the order of 32 Bytes, and that a hash tree has about 30 levels, resulting in about 2 KBytes of additional information, which is on the order of 1KB as listed in the table. 9.3 Observations As is evident from Table 1, all the newer Certificate Validation Infrastructures handle the case of untrusted CAs or CA key compromise, dramatically increasing the security over the current certificate validation infrastructure. For practical deployment, it is critical that the TLS connection establishment does not incur any additional latency. Consequently, the additional RTT incurred by OCSP, P/C/CC, and SK is problematic. Moreover, any system requiring O(C) additional server infrastructure load is likely to incur excessive cost. Performing an online per-connection lookup to an external server also challenges privacy, as it may leak information about the connection to a thirdparty server. Another important factor is that certificates become immediately usable after initial registration. However, TACK, and P/C/CC do not support this feature. Overall, CT and AKI emerge with many desirable features. Compared to CT, the overhead of AKI is lower due to the different hash tree structure, AKI can tolerate compromise of an ILS or validator server, and AKI can rapidly validate the absence of an entry. Moreover, AKI supports key revocation and re-establishment, which is a desirable feature for a public-key validation infrastructure. 10. CONCLUSION Protecting current PKIs against CA root key compromises is becoming a topic of critical importance, as the weakest-link security model of the current PKI system is clearly too weak to provide meaningful security for critical web communication. To improve the resilience of public-key validation infrastructures to attacks, we design the Accountable Key Infrastructure (AKI), which combines an accountability infrastructure (providing checksand-balances on server operations and misbehavior dissemination) with key revocation mechanisms. Our AKI architecture offers flexibility for entities to select a security policy for their certificates, enabling a tradeoff between availability and security. AKI also provides tangible deployment incentives that we anticipate will help to drive adoption. 11. ACKNOWLEDGMENTS We would like to thank Cristina Basescu, Emilia Kasper, Ben Laurie, and Steve Matsumoto for their feedback on this paper and for insightful technical discussions. This research was supported by CyLab at Carnegie Mellon, and by support from NSF under awards CCF and CNS REFERENCES [1] Convergence. [2] Perspectives Project. [3] The Monkeysphere Project [4] Certificate Patrol. US/firefox/addon/certificate-patrol/, [5] Public Key Pinning. May [6] Public Key Pinning Extension for HTTP. Dec
11 [7] D. Cooper, S. Santesson, S. Farrell, S. Boeyen, R. Housley, and W. Polk. Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. Technical report, RFC 5280 (Proposed Standard) Internet Engineering Task Force, [8] M. M. Correia and M. Tok. DNS-based Authentication of Named Entities (DANE). Technical report, Universidade do Porto, [9] P. Eckersley. Sovereign Key Cryptography for Internet Domains. git;a=blob;f=sovereign-key-design.txt;hb=head. [10] P. Eckersley. A Syrian Man-In-The-Middle Attack against Facebook. May [11] P. Eckersley. Iranian hackers obtain fraudulent HTTPS certificates: How close to a Web security meltdown did we get? Mar [12] S. Egelman, L. F. Cranor, and J. Hong. You ve Been Warned: An Empirical Study of the Effectiveness of Web Browser Phishing Warnings. In Proceedings of the SIGCHI conference on Human factors in computing systems (CHI), [13] Electronic Frontier Foundation. SSL Observatory. [14] N. Falliere, L. O. Murchu, and E. Chien. W32.Stuxnet Dossier. Technical report, Symantec Corporation, [15] S. Haber and W. S. Stornetta. How to time-stamp a digital document. In Advances in Cryptology, CRYPTO, [16] J. Hodges, C. Jackson, and A. Barth. HTTP Strict Transport Security (HSTS). RFC 6797 (Proposed Standard), Nov [17] T. H.-J. Kim, V. Gligor, and A. Perrig. GeoPKI: Converting Spatial Trust into Certificate Trust. In Proceedings of the 9 th European PKI Workshop (EuroPKI), Sep [18] T. H.-J. Kim, L.-S. Huang, A. Perrig, C. Jackson, and V. Gligor. Transparent Key Integrity (TKI): A Proposal for a Public-Key Validation Infrastructure. Technical Report CMU-CyLab , Carnegie Mellon University, July [19] B. Laurie and E. Kasper. Revocation Transparency. RevocationTransparency.pdf. [20] B. Laurie and A. Langley. Certificate Authority Transparency and Auditability. CertificateAuthorityTransparencyandAuditability. pdf, [21] B. Laurie, A. Langley, and E. Kasper. Certificate Transparency certificate-transparency-draft. Mar [22] B. Laurie, A. Langley, and E. Kasper. Certificate Transparency. Jan [23] M. Marlinspike. More Tricks For Defeating SSL In Practice. In Blackhat, [24] M. Marlinspike. SSL And The Future Of Authenticity. Apr [25] M. Marlinspike and T. Perrin. Trust Assertions for Certificiate Keys. May [26] M. Myers, R. Ankney, A. Malpani, S. Galperin, and C. Adams. X.509 Internet Public Key Infrastructure Online Certificate Status Protocol - OCSP. Technical report, RFC 2560 (Proposed Standard) Internet Engineering Task Force, [27] P. Roberts. Phony SSL Certificates issued for Google, Yahoo, Skype, Others. Mar [28] C. Soghoian and S. Stamm. Certified Lies: Detecting and Defeating Government Interception Attacks against SSL [29] E. Stark, L.-S. Huang, D. Israni, C. Jackson, and D. Boneh. The case for prefetching and prevalidating TLS server certificates. In Proceedings of the 19th Network and Distributed System Security Symposium, [30] T. Sterling. Second firm warns of concern after Dutch hack [31] J. Sunshine, S. Egelman, H. Almuhimedi, N. Atri, and L. F. Cranor. Crying Wolf: An Empirical Study of SSL Warning Effectiveness. In Proceedings of the USENIX Security Symposium, [32] E. Topalovic, B. Saeta, L.-S. Huang, C. Jackson, and D. Boneh. Towards Short-Lived Certificates. In Web 2.0 Security and Privacy, May [33] D. Wendlandt, D. G. Andersen, and A. Perrig. Perspectives: Improving SSH-style Host Authentication with Multi-Path Probing. In Proceedings of USENIX Annual Technical Conference, June [34] X. Zhang, H.-C. Hsiao, G. Hasker, H. Chan, A. Perrig, and D. Andersen. SCION: Scalability, control, and isolation on next-generation networks. In Proceedings of IEEE Symposium on Security and Privacy, May APPENDIX A. MULTIPLE CA SIGNATURES The X.509 certificate format was specified to contain exactly one CA signature. We discuss below two approaches to support multiple signatures for X.509 certificates. Insert signatures into X.509 extensions. In X.509, the signature is computed from all fields in the certificate, except the signature algorithm identifier and the signature value itself. Therefore, we cannot simply inject X.509 extensions into a signed certificate, since the existing signature would not match. Suppose that we want a total of N different CA signatures. A workaround is to (1) get N 1 CAs to independently compute signatures from the original certificate, (2) insert the N 1 signatures along with the additional signer information into custom X.509 extensions (instead of the signature field) of the original certificate, and then (3) get the last CA to sign the updated certificate (including N 1 signatures) and put the final signature into the signature field. Send a dummy certificate over the TLS handshake. Without changing X.509 or existing CAs, the server can get signed certificates from each CA independently. However, sending multiple certificates for the same public key (signed by different CAs) is highly redundant. This overhead can be reduced if we extract the signatures along with the signer information, signature algorithm, etc., and store them into custom extension fields in an empty certificate at the end of an original certificate chain. An AKI-enabled browser can parse this dummy certificate for multiple signatures, while legacy SSL clients may ignore the dummy certificate and still be able to validate the certificate chain with a single CA signature.
ARPKI: Attack Resilient Public-Key Infrastructure
 ARPKI: Attack Resilient Public-Key Infrastructure David Basin, Cas Cremers, Tiffany Hyun-Jin Kim, Adrian Perrig, Ralf Sasse, Pawel Szalachowski ETH Zurich, University of Oxford, CMU 1 PUBLIC KEYS AND CERTIFICATES
ARPKI: Attack Resilient Public-Key Infrastructure David Basin, Cas Cremers, Tiffany Hyun-Jin Kim, Adrian Perrig, Ralf Sasse, Pawel Szalachowski ETH Zurich, University of Oxford, CMU 1 PUBLIC KEYS AND CERTIFICATES
SSL and Browsers: The Pillars of Broken Security
 SSL and Browsers: The Pillars of Broken Security Ivan Ristic Wolfgang Kandek Qualys, Inc. Session ID: TECH-403 Session Classification: Intermediate SSL, TLS, And PKI SSL (or TLS, if you prefer) is the
SSL and Browsers: The Pillars of Broken Security Ivan Ristic Wolfgang Kandek Qualys, Inc. Session ID: TECH-403 Session Classification: Intermediate SSL, TLS, And PKI SSL (or TLS, if you prefer) is the
Securing the SSL/TLS channel against man-in-the-middle attacks: Future technologies - HTTP Strict Transport Security and Pinning of Certs
 OWASP AppSec APAC 2012 The OWASP Foundation http://www.owasp.org Securing the SSL/TLS channel against man-in-the-middle attacks: Future technologies - HTTP Strict Transport Security and Pinning of Certs
OWASP AppSec APAC 2012 The OWASP Foundation http://www.owasp.org Securing the SSL/TLS channel against man-in-the-middle attacks: Future technologies - HTTP Strict Transport Security and Pinning of Certs
SSL/TLS: The Ugly Truth
 SSL/TLS: The Ugly Truth Examining the flaws in SSL/TLS protocols, and the use of certificate authorities. Adrian Hayter CNS Hut 3 Team adrian.hayter@cnsuk.co.uk Contents Introduction to SSL/TLS Cryptography
SSL/TLS: The Ugly Truth Examining the flaws in SSL/TLS protocols, and the use of certificate authorities. Adrian Hayter CNS Hut 3 Team adrian.hayter@cnsuk.co.uk Contents Introduction to SSL/TLS Cryptography
Attacks against certification service providers and their ramifications
 Federal IT Steering Unit FITSU Federal Intelligence Service FIS Reporting and Analysis Centre for Information Assurance MELANI www.melani.admin.ch Technological consideration Attacks against certification
Federal IT Steering Unit FITSU Federal Intelligence Service FIS Reporting and Analysis Centre for Information Assurance MELANI www.melani.admin.ch Technological consideration Attacks against certification
Securing End-to-End Internet communications using DANE protocol
 Securing End-to-End Internet communications using DANE protocol Today, the Internet is used by nearly.5 billion people to communicate, provide/get information. When the communication involves sensitive
Securing End-to-End Internet communications using DANE protocol Today, the Internet is used by nearly.5 billion people to communicate, provide/get information. When the communication involves sensitive
ALTERNATIVES TO CERTIFICATION AUTHORITIES FOR A SECURE WEB
 ALTERNATIVES TO CERTIFICATION AUTHORITIES FOR A SECURE WEB Scott Rea DigiCert, Inc. Session ID: SEC-T02 Session Classification: Intermediate BACKGROUND: WHAT IS A CERTIFICATION AUTHORITY? What is a certification
ALTERNATIVES TO CERTIFICATION AUTHORITIES FOR A SECURE WEB Scott Rea DigiCert, Inc. Session ID: SEC-T02 Session Classification: Intermediate BACKGROUND: WHAT IS A CERTIFICATION AUTHORITY? What is a certification
Contents. Identity Assurance (Scott Rea Dartmouth College) IdM Workshop, Brisbane Australia, August 19, 2008
 Identity Assurance (Scott Rea Dartmouth College) IdM Workshop, Brisbane Australia, August 19, 2008 Contents Authentication and Identity Assurance The Identity Assurance continuum Plain Password Authentication
Identity Assurance (Scott Rea Dartmouth College) IdM Workshop, Brisbane Australia, August 19, 2008 Contents Authentication and Identity Assurance The Identity Assurance continuum Plain Password Authentication
Public Key Infrastructure (PKI)
 Public Key Infrastructure (PKI) In this video you will learn the quite a bit about Public Key Infrastructure and how it is used to authenticate clients and servers. The purpose of Public Key Infrastructure
Public Key Infrastructure (PKI) In this video you will learn the quite a bit about Public Key Infrastructure and how it is used to authenticate clients and servers. The purpose of Public Key Infrastructure
SSL BEST PRACTICES OVERVIEW
 SSL BEST PRACTICES OVERVIEW THESE PROBLEMS ARE PERVASIVE 77.9% 5.2% 19.2% 42.3% 77.9% of sites are HTTP 5.2% have an incomplete chain 19.2% support weak/insecure cipher suites 42.3% support SSL 3.0 83.1%
SSL BEST PRACTICES OVERVIEW THESE PROBLEMS ARE PERVASIVE 77.9% 5.2% 19.2% 42.3% 77.9% of sites are HTTP 5.2% have an incomplete chain 19.2% support weak/insecure cipher suites 42.3% support SSL 3.0 83.1%
Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University
 Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University October 2015 1 List of Figures Contents 1 Introduction 1 2 History 2 3 Public Key Infrastructure (PKI) 3 3.1 Certificate
Digital Certificates (Public Key Infrastructure) Reshma Afshar Indiana State University October 2015 1 List of Figures Contents 1 Introduction 1 2 History 2 3 Public Key Infrastructure (PKI) 3 3.1 Certificate
E-commerce Design and Implementation of PoliCert
 PoliCert: Secure and Flexible TLS Certificate Management Pawel Szalachowski Inst. of Information Security Dept. of Computer Science ETH Zurich, Switzerland psz@inf.ethz.ch Stephanos Matsumoto CMU, United
PoliCert: Secure and Flexible TLS Certificate Management Pawel Szalachowski Inst. of Information Security Dept. of Computer Science ETH Zurich, Switzerland psz@inf.ethz.ch Stephanos Matsumoto CMU, United
Installation and usage of SSL certificates: Your guide to getting it right
 Installation and usage of SSL certificates: Your guide to getting it right So, you ve bought your SSL Certificate(s). Buying your certificate is only the first of many steps involved in securing your website.
Installation and usage of SSL certificates: Your guide to getting it right So, you ve bought your SSL Certificate(s). Buying your certificate is only the first of many steps involved in securing your website.
Search for Trust: An Analysis and Comparison of CA System Alternatives and Enhancements
 1 Search for Trust: An Analysis and Comparison of CA System Alternatives and Enhancements Alexandra C. Grant Senior Honors Thesis Advisor: Charles C. Palmer Dartmouth Computer Science Technical Report
1 Search for Trust: An Analysis and Comparison of CA System Alternatives and Enhancements Alexandra C. Grant Senior Honors Thesis Advisor: Charles C. Palmer Dartmouth Computer Science Technical Report
Secure Sockets Layer (SSL) / Transport Layer Security (TLS)
 Secure Sockets Layer (SSL) / Transport Layer Security (TLS) Brad Karp UCL Computer Science CS GZ03 / M030 19 th November 2014 What Problems Do SSL/TLS Solve? Two parties, client and server, not previously
Secure Sockets Layer (SSL) / Transport Layer Security (TLS) Brad Karp UCL Computer Science CS GZ03 / M030 19 th November 2014 What Problems Do SSL/TLS Solve? Two parties, client and server, not previously
HTTPS Inspection with Cisco CWS
 White Paper HTTPS Inspection with Cisco CWS What is HTTPS? Hyper Text Transfer Protocol Secure (HTTPS) is a secure version of the Hyper Text Transfer Protocol (HTTP). It is a combination of HTTP and a
White Paper HTTPS Inspection with Cisco CWS What is HTTPS? Hyper Text Transfer Protocol Secure (HTTPS) is a secure version of the Hyper Text Transfer Protocol (HTTP). It is a combination of HTTP and a
Analyzing DANE's Response to Known DNSsec Vulnerabilities
 Analyzing DANE's Response to Known DNSsec Vulnerabilities Matthew Henry Joseph Kirik Emily Scheerer UMBC UMBC UMBC henmatt1@umbc.edu joskir1@umbc.edu semily1@umbc.edu May 9, 2014 Abstract: SSL/TLS is currently
Analyzing DANE's Response to Known DNSsec Vulnerabilities Matthew Henry Joseph Kirik Emily Scheerer UMBC UMBC UMBC henmatt1@umbc.edu joskir1@umbc.edu semily1@umbc.edu May 9, 2014 Abstract: SSL/TLS is currently
Should You Trust the Padlock? Web Security and the HTTPS Value Chain. Keeping Current 20 November 2013 Ken Calvert
 Should You Trust the Padlock? Web Security and the HTTPS Value Chain Keeping Current 20 November 2013 Ken Calvert Outline 1. What are we afraid of? 2. Countermeasures: Securing the Web 3. Public-key Crypto
Should You Trust the Padlock? Web Security and the HTTPS Value Chain Keeping Current 20 November 2013 Ken Calvert Outline 1. What are we afraid of? 2. Countermeasures: Securing the Web 3. Public-key Crypto
Running head: SSL CERTIFICATE AUTHORITY ISSUES 1. Investigating Implementations Designed. to Resolve SSL Certificate Authority Issues.
 Running head: SSL CERTIFICATE AUTHORITY ISSUES 1 Investigating Implementations Designed to Resolve SSL Certificate Authority Issues Michael Ham Stefani Kokel Josh Stroschein Dakota State University SSL
Running head: SSL CERTIFICATE AUTHORITY ISSUES 1 Investigating Implementations Designed to Resolve SSL Certificate Authority Issues Michael Ham Stefani Kokel Josh Stroschein Dakota State University SSL
Certificate Management. PAN-OS Administrator s Guide. Version 7.0
 Certificate Management PAN-OS Administrator s Guide Version 7.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Certificate Management PAN-OS Administrator s Guide Version 7.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Websense Content Gateway HTTPS Configuration
 Websense Content Gateway HTTPS Configuration web security data security email security Support Webinars 2010 Websense, Inc. All rights reserved. Webinar Presenter Title: Sr. Tech Support Specialist Cisco
Websense Content Gateway HTTPS Configuration web security data security email security Support Webinars 2010 Websense, Inc. All rights reserved. Webinar Presenter Title: Sr. Tech Support Specialist Cisco
Alternatives and Enhancements to CAs for a Secure Web
 Alternatives and Enhancements to CAs for a Secure Web Ben Wilson Digicert, Inc. - CA/Browser Forum Eran Messeri Google Session Classification: Intermediate Current Web PKI System OS / Browsers have Managed
Alternatives and Enhancements to CAs for a Secure Web Ben Wilson Digicert, Inc. - CA/Browser Forum Eran Messeri Google Session Classification: Intermediate Current Web PKI System OS / Browsers have Managed
ADDITIONAL Information Security Review, 3b/2011. 28 November 2011 On vulnerabilities in the certificate system
 ADDITIONAL Information Security Review, 3b/2011 28 November 2011 On vulnerabilities in the certificate system 1 CERT-FI Information Security Review 3b/2011 On vulnerabilities in the certificate system
ADDITIONAL Information Security Review, 3b/2011 28 November 2011 On vulnerabilities in the certificate system 1 CERT-FI Information Security Review 3b/2011 On vulnerabilities in the certificate system
Public Key Infrastructures
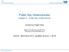 Public Key Infrastructures Chapter 5 Public Key Infrastructures Content by Ralph Holz Network Architectures and Services Version: November 2014, updated January 7, 2016 IN2101, Network Security 1 Public
Public Key Infrastructures Chapter 5 Public Key Infrastructures Content by Ralph Holz Network Architectures and Services Version: November 2014, updated January 7, 2016 IN2101, Network Security 1 Public
Towards Short-Lived Certificates
 Towards Short-Lived Certificates Emin Topalovic, Brennan Saeta, Lin-Shung Huang, Collin Jackson and Dan Boneh Stanford University, {emint, saeta, dabo}@cs.stanford.edu Carnegie Mellon University, {linshung.huang,
Towards Short-Lived Certificates Emin Topalovic, Brennan Saeta, Lin-Shung Huang, Collin Jackson and Dan Boneh Stanford University, {emint, saeta, dabo}@cs.stanford.edu Carnegie Mellon University, {linshung.huang,
Project X Mass interception of encrypted connections
 Project X Mass interception of encrypted connections What? SSL/TLS interception TOR interception ...a thorny path Common Issues Public Key Pinning avoids rogue CA to sign certs Common Issues Google and
Project X Mass interception of encrypted connections What? SSL/TLS interception TOR interception ...a thorny path Common Issues Public Key Pinning avoids rogue CA to sign certs Common Issues Google and
ITL BULLETIN FOR JULY 2012. Preparing for and Responding to Certification Authority Compromise and Fraudulent Certificate Issuance
 ITL BULLETIN FOR JULY 2012 Preparing for and Responding to Certification Authority Compromise and Fraudulent Certificate Issuance Paul Turner, Venafi William Polk, Computer Security Division, Information
ITL BULLETIN FOR JULY 2012 Preparing for and Responding to Certification Authority Compromise and Fraudulent Certificate Issuance Paul Turner, Venafi William Polk, Computer Security Division, Information
Electronic Contract Signing without Using Trusted Third Party
 Electronic Contract Signing without Using Trusted Third Party Zhiguo Wan 1, Robert H. Deng 2 and David Lee 1 Sim Kim Boon Institute for Financial Economics 1, School of Information Science 2, Singapore
Electronic Contract Signing without Using Trusted Third Party Zhiguo Wan 1, Robert H. Deng 2 and David Lee 1 Sim Kim Boon Institute for Financial Economics 1, School of Information Science 2, Singapore
KEY DISTRIBUTION: PKI and SESSION-KEY EXCHANGE. Mihir Bellare UCSD 1
 KEY DISTRIBUTION: PKI and SESSION-KEY EXCHANGE Mihir Bellare UCSD 1 The public key setting Alice M D sk[a] (C) Bob pk[a] C C $ E pk[a] (M) σ $ S sk[a] (M) M, σ Vpk[A] (M, σ) Bob can: send encrypted data
KEY DISTRIBUTION: PKI and SESSION-KEY EXCHANGE Mihir Bellare UCSD 1 The public key setting Alice M D sk[a] (C) Bob pk[a] C C $ E pk[a] (M) σ $ S sk[a] (M) M, σ Vpk[A] (M, σ) Bob can: send encrypted data
Internal Server Names and IP Address Requirements for SSL:
 Internal Server Names and IP Address Requirements for SSL: Guidance on the Deprecation of Internal Server Names and Reserved IP Addresses provided by the CA/Browser Forum June 2012, Version 1.0 Introduction
Internal Server Names and IP Address Requirements for SSL: Guidance on the Deprecation of Internal Server Names and Reserved IP Addresses provided by the CA/Browser Forum June 2012, Version 1.0 Introduction
Lesson 10: Attacks to the SSL Protocol
 Lesson 10: Attacks to the SSL Protocol Luciano Bello - luciano@debian.org Chalmers University Dr. Alfonso Muñoz - amunoz@diatel.upm.es T>SIC Group. Universidad Politécnica de Madrid Security of the SSL
Lesson 10: Attacks to the SSL Protocol Luciano Bello - luciano@debian.org Chalmers University Dr. Alfonso Muñoz - amunoz@diatel.upm.es T>SIC Group. Universidad Politécnica de Madrid Security of the SSL
User Guide Supplement. S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series
 User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
Merkle Hash Trees for Distributed Audit Logs
 Merkle Hash Trees for Distributed Audit Logs Subject proposed by Karthikeyan Bhargavan Karthikeyan.Bhargavan@inria.fr April 7, 2015 Modern distributed systems spread their databases across a large number
Merkle Hash Trees for Distributed Audit Logs Subject proposed by Karthikeyan Bhargavan Karthikeyan.Bhargavan@inria.fr April 7, 2015 Modern distributed systems spread their databases across a large number
Securing Your Software for the Mobile Application Market
 WHITE PAPER: SECURING YOUR SOFTWARE FOR THE MOBILE APPLICATION MARKET White Paper Securing Your Software for the Mobile Application Market The Latest Code Signing Technology Securing Your Software for
WHITE PAPER: SECURING YOUR SOFTWARE FOR THE MOBILE APPLICATION MARKET White Paper Securing Your Software for the Mobile Application Market The Latest Code Signing Technology Securing Your Software for
Introduction to Network Security Key Management and Distribution
 Introduction to Network Security Key Management and Distribution Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University of Science and Technology cetinkayae@mst.edu http://web.mst.edu/~cetinkayae/teaching/cpe5420fall2015
Introduction to Network Security Key Management and Distribution Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University of Science and Technology cetinkayae@mst.edu http://web.mst.edu/~cetinkayae/teaching/cpe5420fall2015
Complete Website Security
 Symantec TM Complete Website Security Symantec is the world s leading provider of Internet trust, authentication and security solutions. Symantec TM Complete Website Security offers you SSL management
Symantec TM Complete Website Security Symantec is the world s leading provider of Internet trust, authentication and security solutions. Symantec TM Complete Website Security offers you SSL management
Certificate technology on Pulse Secure Access
 Certificate technology on Pulse Secure Access How-to Guide Published Date July 2015 Contents Introduction: 3 Creating a Certificate signing request (CSR): 3 Import Intermediate CAs: 5 Using Trusted Client
Certificate technology on Pulse Secure Access How-to Guide Published Date July 2015 Contents Introduction: 3 Creating a Certificate signing request (CSR): 3 Import Intermediate CAs: 5 Using Trusted Client
NIST ITL July 2012 CA Compromise
 NIST ITL July 2012 CA Compromise Prepared for: Intelligent People paul.turner@venafi.com 1 NIST ITL Bulletin on CA Compromise http://csrc.nist.gov/publications/nistbul/july-2012_itl-bulletin.pdf These
NIST ITL July 2012 CA Compromise Prepared for: Intelligent People paul.turner@venafi.com 1 NIST ITL Bulletin on CA Compromise http://csrc.nist.gov/publications/nistbul/july-2012_itl-bulletin.pdf These
You Won t Be Needing These Any More: On Removing Unused Certificates From Trust Stores
 You Won t Be Needing These Any More: On Removing Unused Certificates From Trust Stores Henning Perl 1, Sascha Fahl 1, and Matthew Smith 2 1 Leibniz University Hannover, Germany, {perl, fahl}@dcsec.uni-hannover.de
You Won t Be Needing These Any More: On Removing Unused Certificates From Trust Stores Henning Perl 1, Sascha Fahl 1, and Matthew Smith 2 1 Leibniz University Hannover, Germany, {perl, fahl}@dcsec.uni-hannover.de
Using Entrust certificates with VPN
 Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Certificate technology on Junos Pulse Secure Access
 Certificate technology on Junos Pulse Secure Access How-to Introduction:... 1 Creating a Certificate signing request (CSR):... 1 Import Intermediate CAs: 3 Using Trusted Client CA on Juno Pulse Secure
Certificate technology on Junos Pulse Secure Access How-to Introduction:... 1 Creating a Certificate signing request (CSR):... 1 Import Intermediate CAs: 3 Using Trusted Client CA on Juno Pulse Secure
Secure Web Appliance. SSL Intercept
 Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Secure cloud access system using JAR ABSTRACT:
 Secure cloud access system using JAR ABSTRACT: Cloud computing enables highly scalable services to be easily consumed over the Internet on an as-needed basis. A major feature of the cloud services is that
Secure cloud access system using JAR ABSTRACT: Cloud computing enables highly scalable services to be easily consumed over the Internet on an as-needed basis. A major feature of the cloud services is that
[SMO-SFO-ICO-PE-046-GU-
 Presentation This module contains all the SSL definitions. See also the SSL Security Guidance Introduction The package SSL is a static library which implements an API to use the dynamic SSL library. It
Presentation This module contains all the SSL definitions. See also the SSL Security Guidance Introduction The package SSL is a static library which implements an API to use the dynamic SSL library. It
BUSINESS GUIDE SECURING YOUR SOFTWARE FOR THE MOBILE APPLICATION MARKET THE LATEST CODE SIGNING TECHNOLOGY
 SECURING YOUR SOFTWARE FOR THE MOBILE APPLICATION MARKET THE LATEST CODE SIGNING TECHNOLOGY Now from CONTENTS 1 THE CHALLENGE 1 A BRIEF REVIEW OF CODE SIGNING 2 THE SOLUTION 2 HOW THE CODE SIGNING PORTAL
SECURING YOUR SOFTWARE FOR THE MOBILE APPLICATION MARKET THE LATEST CODE SIGNING TECHNOLOGY Now from CONTENTS 1 THE CHALLENGE 1 A BRIEF REVIEW OF CODE SIGNING 2 THE SOLUTION 2 HOW THE CODE SIGNING PORTAL
Server Certificates based on DNSSEC
 Server Certificates based on DNSSEC Audun Jøsang and Kashif Sana Dar University of Oslo josang@mn.uio.no and kashifd@ifi.uio.no Abstract. Globally unique domain names and IP addresses that are provided
Server Certificates based on DNSSEC Audun Jøsang and Kashif Sana Dar University of Oslo josang@mn.uio.no and kashifd@ifi.uio.no Abstract. Globally unique domain names and IP addresses that are provided
CSC574 - Computer and Network Security Module: Public Key Infrastructure
 CSC574 - Computer and Network Security Module: Public Key Infrastructure Prof. William Enck Spring 2013 1 Meeting Someone New Anywhere in the Internet 2 What is a certificate? A certificate makes an association
CSC574 - Computer and Network Security Module: Public Key Infrastructure Prof. William Enck Spring 2013 1 Meeting Someone New Anywhere in the Internet 2 What is a certificate? A certificate makes an association
Lecture slides by Lawrie Brown for Cryptography and Network Security, 5/e, by William Stallings, Chapter 14 Key Management and Distribution.
 Lecture slides by Lawrie Brown for Cryptography and Network Security, 5/e, by William Stallings, Chapter 14 Key Management and Distribution. 1 Opening quote. 2 The topics of cryptographic key management
Lecture slides by Lawrie Brown for Cryptography and Network Security, 5/e, by William Stallings, Chapter 14 Key Management and Distribution. 1 Opening quote. 2 The topics of cryptographic key management
SSL: Paved With Good Intentions. Richard Moore rich@westpoint.ltd.uk
 SSL: Paved With Good Intentions Richard Moore rich@westpoint.ltd.uk Why do we need SSL? Privacy Online shopping Online banking Identity Protection Data Integrity Early SSL First public version was SSLv2
SSL: Paved With Good Intentions Richard Moore rich@westpoint.ltd.uk Why do we need SSL? Privacy Online shopping Online banking Identity Protection Data Integrity Early SSL First public version was SSLv2
Securing LAN Connected Devices in Industrial Sites with TLS and Multicast DNS
 Securing LAN Connected Devices in Industrial Sites with TLS and Multicast DNS Tero Keski-Valkama May 28, 2015 Version 1.0 Abstract This whitepaper outlines a more flexible and more secure user interface
Securing LAN Connected Devices in Industrial Sites with TLS and Multicast DNS Tero Keski-Valkama May 28, 2015 Version 1.0 Abstract This whitepaper outlines a more flexible and more secure user interface
Key Management Interoperability Protocol (KMIP)
 (KMIP) Addressing the Need for Standardization in Enterprise Key Management Version 1.0, May 20, 2009 Copyright 2009 by the Organization for the Advancement of Structured Information Standards (OASIS).
(KMIP) Addressing the Need for Standardization in Enterprise Key Management Version 1.0, May 20, 2009 Copyright 2009 by the Organization for the Advancement of Structured Information Standards (OASIS).
Cleaning Encrypted Traffic
 Optenet Documentation Cleaning Encrypted Traffic Troubleshooting Guide iii Version History Doc Version Product Date Summary of Changes V6 OST-6.4.300 01/02/2015 English editing Optenet Documentation
Optenet Documentation Cleaning Encrypted Traffic Troubleshooting Guide iii Version History Doc Version Product Date Summary of Changes V6 OST-6.4.300 01/02/2015 English editing Optenet Documentation
Certificate Management
 Certificate Management Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Certificate Management Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Is Your SSL Website and Mobile App Really Secure?
 Is Your SSL Website and Mobile App Really Secure? Agenda What is SSL / TLS SSL Vulnerabilities PC/Server Mobile Advice to the Public Hong Kong Computer Emergency Response Team Coordination Centre 香 港 電
Is Your SSL Website and Mobile App Really Secure? Agenda What is SSL / TLS SSL Vulnerabilities PC/Server Mobile Advice to the Public Hong Kong Computer Emergency Response Team Coordination Centre 香 港 電
Certification Practice Statement
 Certification Practice Statement Revision R1 2013-01-09 1 Copyright Printed: January 9, 2013 This work is the intellectual property of Salzburger Banken Software. Reproduction and distribution require
Certification Practice Statement Revision R1 2013-01-09 1 Copyright Printed: January 9, 2013 This work is the intellectual property of Salzburger Banken Software. Reproduction and distribution require
Asymmetric cryptosystems fundamental problem: authentication of public keys
 Network security Part 2: protocols and systems (a) Authentication of public keys Università degli Studi di Brescia Dipartimento di Ingegneria dell Informazione 2014/2015 Asymmetric cryptosystems fundamental
Network security Part 2: protocols and systems (a) Authentication of public keys Università degli Studi di Brescia Dipartimento di Ingegneria dell Informazione 2014/2015 Asymmetric cryptosystems fundamental
Computer and Network Security. Outline
 Computer and Network Security Lecture 10 Certificates and Revocation Outline Key Distribution Certification Authorities Certificate revocation 1 Key Distribution K A, K B E KA ( K AB, E KB (KAB) ) K A
Computer and Network Security Lecture 10 Certificates and Revocation Outline Key Distribution Certification Authorities Certificate revocation 1 Key Distribution K A, K B E KA ( K AB, E KB (KAB) ) K A
How to configure HTTPS proxying in Zorp 5
 How to configure HTTPS proxying in Zorp 5 June 24, 2014 This tutorial describes how to configure Zorp to proxy HTTPS traffic Copyright 1996-2014 BalaBit IT Security Ltd. Table of Contents 1. Preface...
How to configure HTTPS proxying in Zorp 5 June 24, 2014 This tutorial describes how to configure Zorp to proxy HTTPS traffic Copyright 1996-2014 BalaBit IT Security Ltd. Table of Contents 1. Preface...
Overview Most of the documentation out there on the transition from SHA-1 certificates to SHA-2 certificates will tell you three things:
 SHA-1 Versus SHA-2 Overview Most of the documentation out there on the transition from SHA-1 certificates to SHA-2 certificates will tell you three things: - Breaking SHA-1 is not yet practical but will
SHA-1 Versus SHA-2 Overview Most of the documentation out there on the transition from SHA-1 certificates to SHA-2 certificates will tell you three things: - Breaking SHA-1 is not yet practical but will
A PKI approach targeting the provision of a minimum security level within Internet
 A PKI approach targeting the provision of a minimum security level within Internet Maryline Laurent-Maknavicius CNRS Samovar UMR 5157, GET/INT/LOR Maryline.Maknavicius@int-evry.fr Abstract After decades
A PKI approach targeting the provision of a minimum security level within Internet Maryline Laurent-Maknavicius CNRS Samovar UMR 5157, GET/INT/LOR Maryline.Maknavicius@int-evry.fr Abstract After decades
Author: Kai Engert, kaie at redhat dot com or kaie at kuix dot de For updates to this document, please check http://kuix.
 Spam Salt aka Message Salt An invention against email abuse (Spam), introducing an email sender authentication mechanism. Author: Kai Engert, kaie at redhat dot com or kaie at kuix dot de For updates to
Spam Salt aka Message Salt An invention against email abuse (Spam), introducing an email sender authentication mechanism. Author: Kai Engert, kaie at redhat dot com or kaie at kuix dot de For updates to
How To Ensure Correctness Of Data In The Cloud
 Ensuring Data Storage Security in Cloud Computing ABSTRACT Cloud computing has been envisioned as the next-generation architecture of IT enterprise. In contrast to traditional solutions, where the IT services
Ensuring Data Storage Security in Cloud Computing ABSTRACT Cloud computing has been envisioned as the next-generation architecture of IT enterprise. In contrast to traditional solutions, where the IT services
PKI : state of the art and future trends
 PKI : state of the art and future trends David Chadwick d.w.chadwick@truetrust.co.uk 25 Sept 2013 2010-13 TrueTrust Ltd 1 Contents Review of X.509 state of the art to date What is new in X.509 (2016) What
PKI : state of the art and future trends David Chadwick d.w.chadwick@truetrust.co.uk 25 Sept 2013 2010-13 TrueTrust Ltd 1 Contents Review of X.509 state of the art to date What is new in X.509 (2016) What
18-731 Midterm. Name: Andrew user id:
 18-731 Midterm 6 March 2008 Name: Andrew user id: Scores: Problem 0 (10 points): Problem 1 (10 points): Problem 2 (15 points): Problem 3 (10 points): Problem 4 (20 points): Problem 5 (10 points): Problem
18-731 Midterm 6 March 2008 Name: Andrew user id: Scores: Problem 0 (10 points): Problem 1 (10 points): Problem 2 (15 points): Problem 3 (10 points): Problem 4 (20 points): Problem 5 (10 points): Problem
Security Digital Certificate Manager
 System i Security Digital Certificate Manager Version 5 Release 4 System i Security Digital Certificate Manager Version 5 Release 4 Note Before using this information and the product it supports, be sure
System i Security Digital Certificate Manager Version 5 Release 4 System i Security Digital Certificate Manager Version 5 Release 4 Note Before using this information and the product it supports, be sure
Wildcard and SAN: Understanding Multi-Use SSL Certificates
 Wildcard and SAN: Understanding Multi-Use SSL Certificates LEVERAGING MULTI-USE DIGITAL CERTIFICATES TO SIMPLIFY CERTIFICATE MANAGEMENT AND REDUCE COSTS Wildcard and SAN: Understanding Multi-Use SSL Certificates
Wildcard and SAN: Understanding Multi-Use SSL Certificates LEVERAGING MULTI-USE DIGITAL CERTIFICATES TO SIMPLIFY CERTIFICATE MANAGEMENT AND REDUCE COSTS Wildcard and SAN: Understanding Multi-Use SSL Certificates
Using EMC Unisphere in a Web Browsing Environment: Browser and Security Settings to Improve the Experience
 Using EMC Unisphere in a Web Browsing Environment: Browser and Security Settings to Improve the Experience Applied Technology Abstract The Web-based approach to system management taken by EMC Unisphere
Using EMC Unisphere in a Web Browsing Environment: Browser and Security Settings to Improve the Experience Applied Technology Abstract The Web-based approach to system management taken by EMC Unisphere
How SSL-Encrypted Web Connections are Intercepted
 Web Connections are Web Connections Are When an encrypted web connection is intercepted, it could be by an enterprise for a lawful reason. But what should be done when the interception is illegal and caused
Web Connections are Web Connections Are When an encrypted web connection is intercepted, it could be by an enterprise for a lawful reason. But what should be done when the interception is illegal and caused
Authentication Application
 Authentication Application KERBEROS In an open distributed environment servers to be able to restrict access to authorized users to be able to authenticate requests for service a workstation cannot be
Authentication Application KERBEROS In an open distributed environment servers to be able to restrict access to authorized users to be able to authenticate requests for service a workstation cannot be
MD5 Considered Harmful Today
 MD5 Considered Harmful Today Creating a rogue CA certificate Alexander Sotirov Marc Stevens Jacob Appelbaum Arjen Lenstra David Molnar Dag Arne Osvik Benne de Weger New York, USA CWI, Netherlands Noisebridge/Tor,
MD5 Considered Harmful Today Creating a rogue CA certificate Alexander Sotirov Marc Stevens Jacob Appelbaum Arjen Lenstra David Molnar Dag Arne Osvik Benne de Weger New York, USA CWI, Netherlands Noisebridge/Tor,
How to configure SSL proxying in Zorp 3 F5
 How to configure SSL proxying in Zorp 3 F5 June 14, 2013 This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2013 BalaBit IT Security Ltd. Table of Contents 1. Preface...
How to configure SSL proxying in Zorp 3 F5 June 14, 2013 This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2013 BalaBit IT Security Ltd. Table of Contents 1. Preface...
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Securing VMware View Communication Channels with SSL Certificates TECHNICAL WHITE PAPER
 Securing VMware View Communication Channels with SSL Certificates TECHNICAL WHITE PAPER Table of Contents About VMware View.... 3 Changes in VMware View 5.1.... 3 SSL Authentication Mechanism.... 4 X.509
Securing VMware View Communication Channels with SSL Certificates TECHNICAL WHITE PAPER Table of Contents About VMware View.... 3 Changes in VMware View 5.1.... 3 SSL Authentication Mechanism.... 4 X.509
The Case for Prefetching and Prevalidating TLS Server Certificates
 The Case for Prefetching and Prevalidating TLS Server Certificates Emily Stark Massachusetts Institute of Technology estark@mit.edu Dinesh Israni Carnegie Mellon University ddi@andrew.cmu.edu Collin Jackson
The Case for Prefetching and Prevalidating TLS Server Certificates Emily Stark Massachusetts Institute of Technology estark@mit.edu Dinesh Israni Carnegie Mellon University ddi@andrew.cmu.edu Collin Jackson
SECURITY ANALYSIS OF A SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTER NETWORKS
 SECURITY ANALYSIS OF A SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTER NETWORKS Abstract: The Single sign-on (SSO) is a new authentication mechanism that enables a legal user with a single credential
SECURITY ANALYSIS OF A SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTER NETWORKS Abstract: The Single sign-on (SSO) is a new authentication mechanism that enables a legal user with a single credential
Chapter 7 Managing Users, Authentication, and Certificates
 Chapter 7 Managing Users, Authentication, and Certificates This chapter contains the following sections: Adding Authentication Domains, Groups, and Users Managing Certificates Adding Authentication Domains,
Chapter 7 Managing Users, Authentication, and Certificates This chapter contains the following sections: Adding Authentication Domains, Groups, and Users Managing Certificates Adding Authentication Domains,
Brocade Engineering. PKI Tutorial. Jim Kleinsteiber. February 6, 2002. Page 1
 PKI Tutorial Jim Kleinsteiber February 6, 2002 Page 1 Outline Public Key Cryptography Refresher Course Public / Private Key Pair Public-Key Is it really yours? Digital Certificate Certificate Authority
PKI Tutorial Jim Kleinsteiber February 6, 2002 Page 1 Outline Public Key Cryptography Refresher Course Public / Private Key Pair Public-Key Is it really yours? Digital Certificate Certificate Authority
VeriSign Code Signing Digital Certificates for Adobe AIR Technology
 VeriSign Code Signing Digital Certificates for Adobe AIR Technology Realizing the Possibilities of Internet Software Distribution Contents + What is Code Signing and Why is it Important? 3 + Who Needs
VeriSign Code Signing Digital Certificates for Adobe AIR Technology Realizing the Possibilities of Internet Software Distribution Contents + What is Code Signing and Why is it Important? 3 + Who Needs
Security Digital Certificate Manager
 IBM i Security Digital Certificate Manager 7.1 IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in Notices,
IBM i Security Digital Certificate Manager 7.1 IBM i Security Digital Certificate Manager 7.1 Note Before using this information and the product it supports, be sure to read the information in Notices,
White Paper: Managing Security on Mobile Phones
 White Paper: Managing Security on Mobile Phones April 2006 Managing Security on Mobile Phones April 2006 Table of Contents Abstract...2 Executive Summary...2 The Importance Of Managing Security On Mobile
White Paper: Managing Security on Mobile Phones April 2006 Managing Security on Mobile Phones April 2006 Table of Contents Abstract...2 Executive Summary...2 The Importance Of Managing Security On Mobile
The name of the Contract Signer (as hereinafter defined) duly authorized by the Applicant to bind the Applicant to this Agreement is.
 Trustwave Subscriber Agreement for Digital Certificates Ver. 11JUL14 PLEASE READ THIS AGREEMENT AND THE TRUSTWAVE CERTIFICATION PRACTICES STATEMENTS ( CPS ) CAREFULLY BEFORE USING THE CERTIFICATE ISSUED
Trustwave Subscriber Agreement for Digital Certificates Ver. 11JUL14 PLEASE READ THIS AGREEMENT AND THE TRUSTWAVE CERTIFICATION PRACTICES STATEMENTS ( CPS ) CAREFULLY BEFORE USING THE CERTIFICATE ISSUED
Den Gode Webservice - Security Analysis
 Den Gode Webservice - Security Analysis Cryptomathic A/S September, 2006 Executive Summary This report analyses the security mechanisms provided in Den Gode Web Service (DGWS). DGWS provides a framework
Den Gode Webservice - Security Analysis Cryptomathic A/S September, 2006 Executive Summary This report analyses the security mechanisms provided in Den Gode Web Service (DGWS). DGWS provides a framework
Part III-a. Universität Klagenfurt - IWAS Multimedia Kommunikation (VK) M. Euchner; Mai 2001. Siemens AG 2001, ICN M NT
 Part III-a Contents Part III-a Public-Key Infrastructure (PKI) Definition of a PKI and PKI components PKI Trust Models Digital Certificate, X.509 Certificate Management and Life Cycle Public Key Infrastructure
Part III-a Contents Part III-a Public-Key Infrastructure (PKI) Definition of a PKI and PKI components PKI Trust Models Digital Certificate, X.509 Certificate Management and Life Cycle Public Key Infrastructure
How to configure SSL proxying in Zorp 6
 How to configure SSL proxying in Zorp 6 April 17, 2015 Abstract This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2015 BalaBit IT Security Ltd. Table of Contents 1. Preface...
How to configure SSL proxying in Zorp 6 April 17, 2015 Abstract This tutorial describes how to configure Zorp to proxy SSL traffic Copyright 1996-2015 BalaBit IT Security Ltd. Table of Contents 1. Preface...
The Use of the Simple Certificate Enrollment Protocol (SCEP) and Untrusted Devices
 The Use of the Simple Certificate Enrollment Protocol (SCEP) and Untrusted Devices Essay Authors Ted Shorter, CTO, Certified Security Solutions, Inc. Wayne Harris, PKI Practice Lead, Certified Security
The Use of the Simple Certificate Enrollment Protocol (SCEP) and Untrusted Devices Essay Authors Ted Shorter, CTO, Certified Security Solutions, Inc. Wayne Harris, PKI Practice Lead, Certified Security
Neutralus Certification Practices Statement
 Neutralus Certification Practices Statement Version 2.8 April, 2013 INDEX INDEX...1 1.0 INTRODUCTION...3 1.1 Overview...3 1.2 Policy Identification...3 1.3 Community & Applicability...3 1.4 Contact Details...3
Neutralus Certification Practices Statement Version 2.8 April, 2013 INDEX INDEX...1 1.0 INTRODUCTION...3 1.1 Overview...3 1.2 Policy Identification...3 1.3 Community & Applicability...3 1.4 Contact Details...3
CS5008: Internet Computing
 CS5008: Internet Computing Lecture 22: Internet Security A. O Riordan, 2009, latest revision 2015 Internet Security When a computer connects to the Internet and begins communicating with others, it is
CS5008: Internet Computing Lecture 22: Internet Security A. O Riordan, 2009, latest revision 2015 Internet Security When a computer connects to the Internet and begins communicating with others, it is
How To Understand And Understand The Security Of A Key Infrastructure
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
Grandstream Networks, Inc. UCM6100 Security Manual
 Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Grandstream Networks, Inc. UCM6100 Security Manual Index Table of Contents OVERVIEW... 3 WEB UI ACCESS... 4 UCM6100 HTTP SERVER ACCESS... 4 PROTOCOL TYPE... 4 USER LOGIN... 4 LOGIN TIMEOUT... 5 TWO-LEVEL
Extended SSL Certificates
 Introduction Widespread usage of internet has led to the growth of awareness amongst users, who now associate green address bar with security. Though people are able to recognize the green bar, there is
Introduction Widespread usage of internet has led to the growth of awareness amongst users, who now associate green address bar with security. Though people are able to recognize the green bar, there is
CSE543 - Introduction to Computer and Network Security. Module: Public Key Infrastructure
 CSE543 - Introduction to Computer and Network Security Module: Public Key Infrastructure Professor Trent Jaeger 1 Meeting Someone New Anywhere in the Internet 2 What is a certificate? A certificate makes
CSE543 - Introduction to Computer and Network Security Module: Public Key Infrastructure Professor Trent Jaeger 1 Meeting Someone New Anywhere in the Internet 2 What is a certificate? A certificate makes
This chapter describes how to use the Junos Pulse Secure Access Service in a SAML single sign-on deployment. It includes the following sections:
 CHAPTER 1 SAML Single Sign-On This chapter describes how to use the Junos Pulse Secure Access Service in a SAML single sign-on deployment. It includes the following sections: Junos Pulse Secure Access
CHAPTER 1 SAML Single Sign-On This chapter describes how to use the Junos Pulse Secure Access Service in a SAML single sign-on deployment. It includes the following sections: Junos Pulse Secure Access
IoT Security Platform
 IoT Security Platform 2 Introduction Wars begin when the costs of attack are low, the benefits for a victor are high, and there is an inability to enforce law. The same is true in cyberwars. Today there
IoT Security Platform 2 Introduction Wars begin when the costs of attack are low, the benefits for a victor are high, and there is an inability to enforce law. The same is true in cyberwars. Today there
SSL/TLS and MITM attacks. A case study in Network Security By Lars Nybom & Alexander Wall
 SSL/TLS and MITM attacks A case study in Network Security By Lars Nybom & Alexander Wall SSL/TLS Background SSL/TLS Secure Socket Layer/Transport Layer Security (rfc 2246) SSL/TLS Background SSL/TLS Secure
SSL/TLS and MITM attacks A case study in Network Security By Lars Nybom & Alexander Wall SSL/TLS Background SSL/TLS Secure Socket Layer/Transport Layer Security (rfc 2246) SSL/TLS Background SSL/TLS Secure
Using etoken for SSL Web Authentication. SSL V3.0 Overview
 Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
Using etoken for SSL Web Authentication Lesson 12 April 2004 etoken Certification Course SSL V3.0 Overview Secure Sockets Layer protocol, version 3.0 Provides communication privacy over the internet. Prevents
X.509 Certificate Revisited
 X.509 Certificate Revisited Tohari Ahmad Informatics Department, Faculty of Information Technology - FTIF, ITS Surabaya Email: tohari@its-sby.edu Abstract A digital certificate is used for identifying
X.509 Certificate Revisited Tohari Ahmad Informatics Department, Faculty of Information Technology - FTIF, ITS Surabaya Email: tohari@its-sby.edu Abstract A digital certificate is used for identifying
SSL, PKI and Secure Communication
 SSL, PKI and Secure Communication Aditya Marella 20 th March, 2014 03/19/2014 Usable Privacy and Security 1 Secure Sockets Layer (SSL) Developed by Netscape Sits on top of TCP and below application level
SSL, PKI and Secure Communication Aditya Marella 20 th March, 2014 03/19/2014 Usable Privacy and Security 1 Secure Sockets Layer (SSL) Developed by Netscape Sits on top of TCP and below application level
Mobile OTPK Technology for Online Digital Signatures. Dec 15, 2015
 Mobile OTPK Technology for Online Digital Signatures Dec 15, 2015 Presentation Agenda The presentation will cover Background Traditional PKI What are the issued faced? Alternative technology Introduction
Mobile OTPK Technology for Online Digital Signatures Dec 15, 2015 Presentation Agenda The presentation will cover Background Traditional PKI What are the issued faced? Alternative technology Introduction
Reducing Certificate Revocation Cost using NPKI
 Reducing Certificate Revocation Cost using NPKI Albert Levi and Çetin Kaya Koç Oregon State University, Electrical and Computer Engineering Dept., Information Security Lab, Corvallis, Oregon, USA levi@ece.orst.edu
Reducing Certificate Revocation Cost using NPKI Albert Levi and Çetin Kaya Koç Oregon State University, Electrical and Computer Engineering Dept., Information Security Lab, Corvallis, Oregon, USA levi@ece.orst.edu
Lab Exercise SSL/TLS. Objective. Step 1: Open a Trace. Step 2: Inspect the Trace
 Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
Lab Exercise SSL/TLS Objective To observe SSL/TLS (Secure Sockets Layer / Transport Layer Security) in action. SSL/TLS is used to secure TCP connections, and it is widely used as part of the secure web:
