Successful DB2 NETLOGON in LAB (Sniffer on LAB HUB)
|
|
|
- Marlene McCoy
- 9 years ago
- Views:
Transcription
1 Troubleshooting Analysis for Windows 2000 Active Directory Authentication Problem Overview Servers DB1 & DB2 are configured with clustering (DB1 is active and DB2 is backup). The PDC (server NT9) is connected to a different subnet, which is separated by two firewalls. The DB server clustering services depend on Active Directory Authentication. When the servers cannot authenticate, the clustering service cannot start. To initially start the clustering services on the DB servers, the work-around is to connect to the DB server via terminal services and to manually map a network drive from the DB server to the PDC server using a domain USERID. Once the drive is mapped, the clustering service can be successfully started and then the network drive map can be disconnected. Once the cluster service is up and running it continues to work fine even if the Active Directory authentication fails (until the clustering service has to be restarted again). Connectivity for the Production Environment DB1 backend ----> client-fw1 ----> utilfw2 ----> NT9 Connectivity for the LAB Environment DB2 backend ----> NT9 Source Trace Files Trace file "Filter for NT09 IP (Mar31pm-apr01am).cap" was obtained with port monitor configured for the DB1 server and shows all traffic between the production servers DB1 & NT9 from :01 to :13. Trace file " lab capture 02 DB2 communicating with NT9 ok.cap " shows all traffic on the LAB segment hub, including traffic between replica servers DB2 & NT9. Observations?? Switches and firewalls are not logging any drops between NT9 and the DB servers.?? Both DB servers are logging NETLOGON system authentication errors because they do not receive the responses to their RPC NETLOGON request packets submitted to TCP port 1026 on NT9 (NETLOGON UUID = abcd-ef cffb).?? The NETLOGON request packets seen in the LAB appear identical to those sent on the production network.?? DB1 can successfully communicate with the Directory Replication Interface via the same port 1026 on NT9 (NTDS UUID = e b06-11d1-ab04-00c04fc2dcd2).?? The NETLOGON response packets are being intercepted and RESET by utilfw2.?? utilfw2 runs Firewall-1 software on a Nokia platform. Revised on 14/05/2003 by Daniel Cayer Page 1 of 9
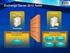
2 No. Time Successful DB2 NETLOGON in LAB (Sniffer on LAB HUB) NOTE: DB server and PDC are on the same local subnet. The traffic in the production network is identical to that in the LAB until the NETLOGON request, which is successfully acknowledged and answered in the LAB. This trace files contains all traffic from both servers since they were powered on. 1 Search for Domain Controller 1.1 DNS query for DC SRC DST Pro Info :27:51 DB2 NT9 DNS Standard query SRV _ldap._tcp.default-first-site-name._sites.dc._msdcs.cwh- OTTAWA.COM 1.2 DNS response: DC found :27:51 NT9 DB2 DNS Standard query response SRV cwh-ott-nt-009.cwh-ottawa.com 2 Determine if DC is closest one available 2.1 LDAP search request for matching host name, domain name, SID & GUID :27:51 DB2 NT9 LDAP MsgId=1 MsgType=Search Request 2.2 Successful LDAP response :27:51 NT9 DB2 LDAP MsgId=1 MsgType=Search Entry 3 Establishment of secured channel between DB2 & DC (NT09) 3.1 PORTMAPPER (EPM) request via RPC for Active Directory Logon :27:51 DB2 NT9 TCP 1103 > 135 [SYN] Seq= Ack=0 Win=16384 Len= :27:51 NT9 DB2 TCP 135 > 1103 [SYN, ACK] Seq= Ack= Win=17520 Len= :27:51 DB2 NT9 TCP 1103 > 135 [ACK] Seq= Ack= Win=17520 Len= :27:51 DB2 NT9 DCERPC Bind: call_id: 1 UUID: EPM :27:51 NT9 DB2 DCERPC Bind_ack: call_id: 1 accept max_xmit: 5840 max_recv: :27:51 DB2 NT9 EPM Map request 3.2 PORTMAPPER response (port = 1026) :27:51 NT9 DB2 EPM Map reply :27:51 DB2 NT9 TCP 1103 > 135 [FIN, ACK] Seq= Ack= Win=17132 Len=0 3.3 NETLOGON request :27:51 DB2 NT9 TCP 1104 > 1026 [SYN] Seq= Ack=0 Win=16384 Len= :27:51 NT9 DB2 TCP 1026 > 1104 [SYN, ACK] Seq= Ack= Win=17520 Len= :27:51 NT9 DB2 TCP 135 > 1103 [ACK] Seq= Ack= Win=17292 Len= :27:51 NT9 DB2 TCP 135 > 1103 [FIN, ACK] Seq= Ack= Win=17292 Len= :27:51 DB2 NT9 TCP 1104 > 1026 [ACK] Seq= Ack= Win=17520 Len= :27:51 DB2 NT9 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON :27:51 DB2 NT9 TCP 1103 > 135 [ACK] Seq= Ack= Win=17132 Len=0 3.4 NETLOGON request acknowledgement :27:51 NT9 DB2 DCERPC Bind_ack: call_id: 1 accept max_xmit: 5840 max_recv: NETLOGON server challenge request :27:51 DB2 NT9 RPC_NETLOGON ServerReqChallenge request, REBIZX-DB2 3.6 NETLOGON server challenge response :27:51 NT9 DB2 RPC_NETLOGON ServerReqChallenge reply 3.7 NETLOGON server authentication request :27:51 DB2 NT9 RPC_NETLOGON ServerAuthenticate3 request 3.8 NETLOGON server authentication response :27:51 NT9 DB2 RPC_NETLOGON ServerAuthenticate3 reply 3.9 New NETLOGON connection for Domain Info lookup :27:51 DB2 NT9 TCP 1105 > 1026 [SYN] Seq= Ack=0 Win=16384 Len= :27:51 NT9 DB2 TCP 1026 > 1105 [SYN, ACK] Seq= Ack= Win=17520 Len= :27:51 DB2 NT9 TCP 1105 > 1026 [ACK] Seq= Ack= Win=17520 Len= :27:51 DB2 NT9 DCERPC Bind: call_id: 3 UUID: RPC_NETLOGON :27:51 NT9 DB2 DCERPC Bind_ack: call_id: 3 accept max_xmit: 5840 max_recv: :27:51 DB2 NT9 RPC_NETLOGON NetrLogonGetDomainInfo request Revised on 14/05/2003 by Daniel Cayer Page 2 of 9
3 3.10 Domain Info response (encrypted payload) :27:51 NT9 DB2 RPC_NETLOGON NetrLogonGetDomainInfo reply 3.11 Establish SMB connection, authenticate with Kerberos, etc :27:51 DB2 NT9 ICMP Echo (ping) request :27:51 NT9 DB2 ICMP Echo (ping) reply :27:51 DB2 NT9 TCP 1106 > 445 [SYN] Seq= Ack=0 Win=16384 Len= :27:51 NT9 DB2 TCP 445 > 1106 [SYN, ACK] Seq= Ack= Win=17520 Len= :27:51 DB2 NT9 TCP 1106 > 445 [ACK] Seq= Ack= Win=17520 Len= :27:51 DB2 NT9 ICMP Echo (ping) request :27:51 NT9 DB2 ICMP Echo (ping) reply :27:51 DB2 NT9 SMB Negotiate Protocol Request :27:51 NT9 DB2 SMB Negotiate Protocol Response :27:51 DB2 NT9 KRB5 AS-REQ :27:51 NT9 DB2 KRB5 KRB-ERROR :27:51 DB2 NT9 KRB5 AS-REQ :27:51 NT9 DB2 KRB5 AS-REP :27:51 DB2 NT9 KRB5 TGS-REQ :27:51 NT9 DB2 KRB5 TGS-REP :27:51 DB2 NT9 KRB5 TGS-REQ :27:51 NT9 DB2 KRB5 TGS-REP :27:51 DB2 NT9 SMB Session Setup AndX Request[Unreassembled Packet] :27:51 DB2 NT9 NBSS NBSS Continuation Message :27:51 NT9 DB2 TCP 445 > 1106 [ACK] Seq= Ack= Win=17520 Len= :27:51 NT9 DB2 SMB Session Setup AndX Response, Error: STATUS_MORE_PROCESSING_REQUIRED :27:51 DB2 NT9 SMB Session Setup AndX Request[Unreassembled Packet] :27:51 DB2 NT9 NBSS NBSS Continuation Message :27:51 NT9 DB2 TCP 445 > 1106 [ACK] Seq= Ack= Win=17520 Len= :27:51 NT9 DB2 SMB Session Setup AndX Response :27:51 DB2 NT9 SMB Tree Connect AndX Request,Path: \\CWH-OTT-NT-009.CWH-OTTAWA.COM\IPC$ :27:51 NT9 DB2 SMB Tree Connect AndX Response :27:51 DB2 NT9 SMB NT Create AndX Request, Path: \lsarpc :27:51 NT9 DB2 SMB NT Create AndX Response, FID: 0x :27:51 DB2 NT9 DCERPC Bind: call_id: 1 UUID: LSA :27:51 NT9 DB2 DCERPC Bind_ack: call_id: 1 accept max_xmit: 4280 max_recv: :27:51 DB2 NT9 LSA OpenPolicy2 request, \\cwh-ott-nt-009.cwh-ottawa.com :27:51 NT9 DB2 SMB Write AndX Response, FID: 0x4000, 140 bytes :27:51 DB2 NT9 SMB Read AndX Request, FID: 0x4000, 1024 bytes at offset :27:51 NT9 DB2 LSA OpenPolicy2 reply :27:51 DB2 NT9 SMB NT Create AndX Request, Path: \lsarpc :27:51 NT9 DB2 SMB NT Create AndX Response, FID: 0x :27:51 DB2 NT9 DCERPC Bind: call_id: 2 UUID: LSA :27:51 NT9 DB2 DCERPC Bind_ack: call_id: 2 accept max_xmit: 4280 max_recv: :27:51 DB2 NT9 LSA QueryInfoPolicy request, Primary Domain Information :27:51 NT9 DB2 SMB Write AndX Response, FID: 0x4001, 96 bytes :27:51 DB2 NT9 SMB Read AndX Request, FID: 0x4001, 1024 bytes at offset :27:51 NT9 DB2 LSA QueryInfoPolicy reply :27:51 DB2 NT9 LSA QueryInfoPolicy request, Account Domain Information :27:51 NT9 DB2 SMB Write AndX Response, FID: 0x4001, 96 bytes :27:51 DB2 NT9 SMB Read AndX Request, FID: 0x4001, 1024 bytes at offset :27:51 NT9 DB2 LSA QueryInfoPolicy reply :27:51 DB2 NT9 LSA LookupSIDs2 request :27:51 NT9 DB2 SMB Write AndX Response, FID: 0x4001, 240 bytes :27:51 DB2 NT9 SMB Read AndX Request, FID: 0x4001, 1024 bytes at offset :27:51 NT9 DB2 LSA LookupSIDs2 reply :27:51 DB2 NT9 LSA Close request :27:51 NT9 DB2 SMB Write AndX Response, FID: 0x4001, 96 bytes :27:51 DB2 NT9 SMB Read AndX Request, FID: 0x4001, 1024 bytes at offset :27:51 NT9 DB2 LSA Close reply :27:51 DB2 NT9 SMB Close Request, FID: 0x :27:51 NT9 DB2 SMB Close Response :27:51 DB2 NT9 SMB Close Request, FID: 0x :27:51 NT9 DB2 SMB Close Response :27:51 DB2 NT9 TCP 1105 > 1026 [ACK] Seq= Ack= Win=16752 Len= :27:51 DB2 NT9 TCP 1104 > 1026 [ACK] Seq= Ack= Win=17380 Len= :27:51 DB2 NT9 TCP 1106 > 445 [ACK] Seq= Ack= Win=16066 Len=0 Revised on 14/05/2003 by Daniel Cayer Page 3 of 9
4 No. Time Failed DB1 NETLOGON on Production LAN (Sniffer next to DB1) 1 Search for Domain Controller SRC DST Proto Info :14:24 DB1 NT09 DNS Standard query SRV _ldap._tcp.pdc._msdcs.rebizx-db :14:24 NT09 DB1 DNS Standard query response, No such name :14:26 DB1 NT09 DNS Standard query SRV _ldap._tcp.default-first-site- Name._sites.dc._msdcs.rebizx-db :14:26 NT09 DB1 DNS Standard query response, No such name :14:26 DB1 NT09 DNS Standard query SRV _ldap._tcp.dc._msdcs.rebizx-db :14:26 NT09 DB1 DNS Standard query response, No such name :17:22 DB1 NT09 DNS Standard query SRV _ldap._tcp.default-first-site- Name._sites.dc._msdcs.CWH-OTTAWA.COM :17:22 NT09 DB1 DNS Standard query response SRV cwh-ott-nt-009.cwh-ottawa.com 2 Determine if DC is closest one available :17:22 DB1 NT09 LDAP MsgId=3743 MsgType=Search Request :17:22 NT09 DB1 LDAP MsgId=3743 MsgType=Search Entry 3 Establishment of secured channel between DB1 & DC (NT09) 3.1 PORTMAPPER (EPM) request via RPC for Active Directory Logon :17:22 DB1 NT09 TCP 1673 > epmap [SYN] Seq= Ack=0 Win=16384 Len= :17:22 NT09 DB1 TCP epmap > 1673 [SYN, ACK] Seq= Ack= Win=17520 Len= :17:22 DB1 NT09 TCP 1673 > epmap [ACK] Seq= Ack= Win=17520 Len= :17:22 DB1 NT09 DCERPC Bind: call_id: 1 UUID: EPM :17:22 NT09 DB1 DCERPC Bind_ack: call_id: 1 accept max_xmit: 5840 max_recv: :17:22 DB1 NT09 EPM Map request 3.2 PORTMAPPER response (port = 1026) :17:22 NT09 DB1 EPM Map reply :17:22 DB1 NT09 TCP 1673 > epmap [FIN, ACK] Seq= Ack= Win=17308 Len= :17:22 DB1 NT09 TCP 1674 > 1026 [SYN] Seq= Ack=0 Win=16384 Len= :17:22 NT09 DB1 TCP epmap > 1673 [ACK] Seq= Ack= Win=17292 Len= :17:22 NT09 DB1 TCP epmap > 1673 [FIN, ACK] Seq= Ack= Win=17292 Len= :17:22 DB1 NT09 TCP 1673 > epmap [ACK] Seq= Ack= Win=17308 Len=0 3.3 NETLOGON request :17:22 NT09 DB1 TCP 1026 > 1674 [SYN, ACK] Seq= Ack= Win=17520 Len= :17:22 DB1 NT09 TCP 1674 > 1026 [ACK] Seq= Ack= Win=17520 Len= :17:22 DB1 NT09 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON Retransmission of NETLOGON request (3-second timeoute) :17:26 DB1 NT09 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON NETLOGON error (NT09 reset of the TCP connection) :17:26 NT09 DB1 TCP 1026 > 1674 [RST] Seq= Ack= Win=0 Len= RETRY NETLOGON (2nd attempt, from a different source port) :17:26 DB1 NT09 TCP 1675 > 1026 [SYN] Seq= Ack=0 Win=16384 Len= :17:26 NT09 DB1 TCP 1026 > 1675 [SYN, ACK] Seq= Ack= Win=17520 Len= :17:26 DB1 NT09 TCP 1675 > 1026 [ACK] Seq= Ack= Win=17520 Len= :17:26 DB1 NT09 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON Retransmission of NETLOGON request (3-second timeoute) :17:29 DB1 NT09 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON NETLOGON error (NT09 reset of the TCP connection) :17:29 NT09 DB1 TCP 1026 > 1675 [RST] Seq= Ack= Win=0 Len=0 Revised on 14/05/2003 by Daniel Cayer Page 4 of 9
5 NOTE: Other successful TCP connections are seen on NT09 port 1026 for another UUID: No. Time SRC DST Proto Info :25:57 DB1 NT09 TCP 3927 > 1026 [SYN] Seq= Ack=0 Win=16384 Len= :25:57 NT09 DB1 TCP 1026 > 3927 [SYN, ACK] Seq= Ack= Win=17520 Len= :25:57 DB1 NT09 TCP 3927 > 1026 [ACK] Seq= Ack= Win=17520 Len= :25:57 DB1 NT09 DCERPC Bind: call_id: 1 UUID: e b06-11d1-ab04-00c04fc2dcd2 ver :25:57 DB1 NT09 TCP 3927 > 1026 [PSH,ACK] Seq= Ack= Win=17520 Len= :25:57 NT09 DB1 TCP 1026 > 3927 [ACK] Seq= Ack= Win=17520 Len= :25:57 NT09 DB1 DCERPC Bind_ack: call_id: 1 accept max_xmit: 5840 max_recv: :25:57 DB1 NT09 DCERPC Alter_context: call_id: 1 UUID: e b06-11d1-ab04-00c04fc2dcd2 ver :25:57 NT09 DB1 DCERPC Alter_context_resp: call_id: 1 accept max_xmit: 5840 max_recv: :25:57 DB1 NT09 DCERPC Request: call_id: 1 opnum: 0 ctx_id: :25:57 NT09 DB1 DCERPC Response: call_id: 1 ctx_id: :25:57 DB1 NT09 DCERPC Request: call_id: 2 opnum: 12 ctx_id: :25:57 NT09 DB1 DCERPC Response: call_id: 2 ctx_id: :25:57 DB1 NT09 DCERPC Request: call_id: 3 opnum: 12 ctx_id: :25:57 NT09 DB1 DCERPC Response: call_id: 3 ctx_id: :25:57 DB1 NT09 DCERPC Request: call_id: 4 opnum: 1 ctx_id: :25:57 NT09 DB1 DCERPC Response: call_id: 4 ctx_id: :25:57 DB1 NT09 TCP 3927 > 1026 [FIN, ACK] Seq= Ack= Win=16337 Len= :25:57 NT09 DB1 TCP 1026 > 3927 [ACK] Seq= Ack= Win=16683 Len= :25:57 NT09 DB1 TCP 1026 > 3927 [FIN, ACK] Seq= Ack= Win=16683 Len= :25:57 DB1 NT09 TCP 3927 > 1026 [ACK] Seq= Ack= Win=16337 Len=0 Kerberos Errors From DB1 to NT9 (Sniffer next to DB1) Trace file " DB1 kereberos failed to NT9.cap " shows that DB1 is using the wrong name to authenticate with Kerberos. In fact DB1 uses LDAP1's IP address instead of its own FQDN!!! These Kerberos errors are occurring at a regular 40-minute interval. NOTE: Sniffer does not decode Kerberos Use Ethereal instead! Frame 5 (1373 bytes on wire, 1373 bytes captured) Arrival Time: Mar 28, :02: Ethernet II, Src: 00:02:a5:6b:8d:96, Dst: 00:00:5e:00:01:04 Internet Protocol, Src Addr: ( ), Dst Addr: ( ) User Datagram Protocol, Src Port: 2729 (2729), Dst Port: 88 (88) Kerberos Version: 5 MSG Type: TGS-REQ Pre-Authentication Type: PA-TGS-REQ Value: 6E A A Request Options: Realm: CWH-OTTAWA.COM Server Name: HOST Type: Service and Instance Name: HOST Name: End Time: :48:05 (Z) Random Number: Encryption Types Type: rc4-hmac This should be a qualified domain such as "cwh-ott- nt-009.cwh- OTTAWA.COM"!!! Revised on 14/05/2003 by Daniel Cayer Page 5 of 9
6 Type: Unknown encryption type 0xff7b Type: Unknown encryption type 0x80 Type: des-cbc-md5 Type: des-cbc-crc Type: rc4-hmac-exp Type: Unknown encryption type 0xff79 Frame 6 (150 bytes on wire, 150 bytes captured) Arrival Time: Mar 28, :02: Ethernet II, Src: 00:a0:8e:32:ba:53, Dst: 00:02:a5:6b:8d:96 Internet Protocol, Src Addr: ( ), Dst Addr: ( ) User Datagram Protocol, Src Port: 88 (88), Dst Port: 2729 (2729) Kerberos Version: 5 MSG Type: KRB-ERROR stime: :01:20 (Z) susec: Error Code: KRB5KDC_ERR_S_PRINCIPAL_UNKNOWN realm: CWH-OTTAWA.COM sname: krbtgt Type: Service and Instance Name: krbtgt Name: CWH-OTTAWA.COM Failed NETLOGON on Production LAN (Sniffer next to NT9) NOTE: Span a port on switch connected to NT9 for the Sniffer. Trace file shows NETLOGON request from DB1 is reaching NT9 and NT9 is acknowledging!!! No. Time SRC DST Pro Info :17:54 DB1 NT9 TCP 1280 > 1026 [SYN] Seq= Ack=0 Win=16384 Len= :17:54 NT9 DB1 TCP 1026 > 1280 [SYN, ACK] Seq= Ack= Win=17520 Len= :17:54 DB1 NT9 TCP 1280 > 1026 [ACK] Seq= Ack= Win=17520 Len= :17:54 DB1 NT9 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON :17:54 NT9 DB1 DCERPC Bind_ack: call_id: 1 accept max_xmit: 5840 max_recv: :17:54 DB1 NT9 TCP 1280 > 1026 [RST] Seq= Ack=0 Win=0 Len= :17:58 DB1 NT9 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON :17:58 NT9 DB1 TCP 1026 > 1280 [RST] Seq= Ack= Win=0 Len=0 Where are these packets dropped and who is sending the RST on behalf of the DB servers??? obtain trace file from segment between 2 firewalls Failed NETLOGON on Production LAN (Trace from utilfw2 interface facing the other firewall) Packet 7906 above (NETLOGON response) is intercepted by utilfw2 and packet 7907 is originated from this same utilfw2 because both packets do not show up on the other side of this firewall: No. Time SRC DST Pro Info :45:00 DB1 NT9 TCP 4447 > 1026 [SYN] Seq= Ack=0 Win=16384 Len= :45:00 NT9 DB1 TCP 1026 > 4447 [SYN, ACK] Seq= Ack= Win=17520 Len=0 Revised on 14/05/2003 by Daniel Cayer Page 6 of 9
7 :45:00 DB1 NT9 TCP 4447 > 1026 [ACK] Seq= Ack= Win=17520 Len= :45:00 DB1 NT9 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON :45:03 DB1 NT9 DCERPC Bind: call_id: 1 UUID: RPC_NETLOGON :45:03 NT9 DB1 TCP 1026 > 4447 [RST] Seq= Ack= Win=0 Len=0 Revised on 14/05/2003 by Daniel Cayer Page 7 of 9
8 Questions 1. Is there any way to determine the correctness of the NETLOGON requests from DB1 (i.e.: is DB1 attempting to logon to NT09 correctly)? ANSWER: YES! The packets in the LAB are identical! 2. Is there any way to determine why NT09 does not even acknowledge these NETLOGON requests at the TCP layer? ANSWER: YES! NT09 DOES acknowledge the packets. The firewall is intercepting and dropping the response, which includes the TCP ACK!!! 3. Is NT09 supposed to be listening on port 1026 for both NETLOGON and NTDS UUIDs (e b06-11d1-ab04-00c04fc2dcd2 & abcd-ef cffb)? ANSWER: YES! This is a normal behavior for Win2K. 4. Are the Kerberos errors the cause of the NETLOGON failures? ANSWER: NO! NETLOGON fails because of the firewall. 5. What is the root cause of the Kerberos errors? 6. What are the dependencies between Kerberos and Active Directory Authentication? Suggestions 1. Fix Firewall 2. Fix Kerberos problem (Windows patch???) Microsoft Knowledge Base Articles: Troubleshooting Common Active Directory Setup Issues in Windows How to Enable Diagnostic Event Logging for Active Directory Services Using Uppercase Letters for Kerberos Realm Names HOW TO: Enable Kerberos Event Logging Kerberos Support on Windows 2000-Based Server Clusters XCCC: Exchange 2000 Windows 2000 Connectivity Through Firewalls A Missing Service Principal Name May Prevent Domain Controllers from Replicating Revised on 14/05/2003 by Daniel Cayer Page 8 of 9
9 Conclusion Once we were able to identify the failed NETLOGON requests in the trace files (corresponding to the NETLOGON errors on the DB servers), we then moved the Sniffer next to the PDC server and confirmed that the NETLOGON requests were indeed being answered. Additional traces from the firewalls allowed us to determine that the NETLOGON responses from the PDC were being blocked by the utilfw2 firewall. Upon reception of the NETLOGON response packet from NT9, utilfw2 would immediately send back a TCP RST to NT9. A support call was made to the firewall vendor (Check-Point) who confirmed that they did not support Microsoft Active Directory on this version of the firewall-1 software (version 4.x). Their recommendation was to upgrade the firewall software to a more recent version. Lessons Learned?? How Windows 2000 Active Directory Authentication works?? What Windows 2000 Active Directory Authentication looks like "on-the-wire". Revised on 14/05/2003 by Daniel Cayer Page 9 of 9
Active Directory network protocols and traffic
 HERVÉ SCHAUER CONSULTANTS Cabinet de Consultants en Sécurité Informatique depuis 1989 Spécialisé sur Unix, Windows, TCP/IP et Internet Windows Security OSSIR group 13th September S 2004 Active Directory
HERVÉ SCHAUER CONSULTANTS Cabinet de Consultants en Sécurité Informatique depuis 1989 Spécialisé sur Unix, Windows, TCP/IP et Internet Windows Security OSSIR group 13th September S 2004 Active Directory
Active Directory network protocols and traffic
 samba experience 2005 Göttingen, Germany 4 th May 2005 Active Directory network protocols and traffic Jean-Baptiste Marchand Jean-Baptiste Marchand Introduction Agenda Active
samba experience 2005 Göttingen, Germany 4 th May 2005 Active Directory network protocols and traffic Jean-Baptiste Marchand Jean-Baptiste Marchand Introduction Agenda Active
Colubris TechNote. Testing and Troubleshooting Active- Directory. Revision 1.3 Mar. 2008 Author: Dave Leger
 Colubris TechNote Testing and Troubleshooting Active- Directory Revision 1.3 Mar. 2008 Author: Dave Leger Colubris Networks 200 West St. Suite 300 Waltham, MA 02451 www.colubris.com Page 1 Contents OBJECTIVE...
Colubris TechNote Testing and Troubleshooting Active- Directory Revision 1.3 Mar. 2008 Author: Dave Leger Colubris Networks 200 West St. Suite 300 Waltham, MA 02451 www.colubris.com Page 1 Contents OBJECTIVE...
Customer Tips. Basic E-mail Configuration and Troubleshooting. for the user. Overview. Basic Configuration. Xerox Multifunction Devices.
 Xerox Multifunction Devices Customer Tips November 24, 2003 This document applies to these Xerox products: x WC Pro 32/40 Color x WC Pro 65/75/90 x WC Pro 35/45/55 WC M35/M45/M55 x DC 555/545/535 x DC
Xerox Multifunction Devices Customer Tips November 24, 2003 This document applies to these Xerox products: x WC Pro 32/40 Color x WC Pro 65/75/90 x WC Pro 35/45/55 WC M35/M45/M55 x DC 555/545/535 x DC
Network layer: Overview. Network layer functions IP Routing and forwarding
 Network layer: Overview Network layer functions IP Routing and forwarding 1 Network layer functions Transport packet from sending to receiving hosts Network layer protocols in every host, router application
Network layer: Overview Network layer functions IP Routing and forwarding 1 Network layer functions Transport packet from sending to receiving hosts Network layer protocols in every host, router application
Samba as an Active Directory Domain Controller
 Samba as an Active Directory Domain Controller Gregory Havens II Texas A&M University [email protected] Anthony Liguori Rutgers University [email protected] C. Donour Sizemore University of Chicago
Samba as an Active Directory Domain Controller Gregory Havens II Texas A&M University [email protected] Anthony Liguori Rutgers University [email protected] C. Donour Sizemore University of Chicago
Visualizations and Correlations in Troubleshooting
 Visualizations and Correlations in Troubleshooting Kevin Burns Comcast [email protected] 1 Comcast Technology Groups Cable CMTS, Modem, Edge Services Backbone Transport, Routing Converged Regional
Visualizations and Correlations in Troubleshooting Kevin Burns Comcast [email protected] 1 Comcast Technology Groups Cable CMTS, Modem, Edge Services Backbone Transport, Routing Converged Regional
SKV PROPOSAL TO CLT FOR ACTIVE DIRECTORY AND DNS IMPLEMENTATION
 SKV PROPOSAL TO CLT FOR ACTIVE DIRECTORY AND DNS IMPLEMENTATION Date: April 22,2013 Prepared by: Sainath K.E.V Microsoft Most Valuable Professional Introduction: SKV Consulting is a Premier Consulting
SKV PROPOSAL TO CLT FOR ACTIVE DIRECTORY AND DNS IMPLEMENTATION Date: April 22,2013 Prepared by: Sainath K.E.V Microsoft Most Valuable Professional Introduction: SKV Consulting is a Premier Consulting
Understanding and Configuring NAT Tech Note PAN-OS 4.1
 Understanding and Configuring NAT Tech Note PAN-OS 4.1 Revision C 2012, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Scope... 3 Design Consideration... 3 Software requirement...
Understanding and Configuring NAT Tech Note PAN-OS 4.1 Revision C 2012, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Scope... 3 Design Consideration... 3 Software requirement...
Websense Support Webinar: Questions and Answers
 Websense Support Webinar: Questions and Answers Configuring Websense Web Security v7 with Your Directory Service Can updating to Native Mode from Active Directory (AD) Mixed Mode affect transparent user
Websense Support Webinar: Questions and Answers Configuring Websense Web Security v7 with Your Directory Service Can updating to Native Mode from Active Directory (AD) Mixed Mode affect transparent user
TECHNICAL NOTE. Technical Note P/N 300-999-649 REV 03. EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.
 TECHNICAL NOTE EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.0 and later Technical Note P/N 300-999-649 REV 03 February 6, 2014 This technical note describes how to configure
TECHNICAL NOTE EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.0 and later Technical Note P/N 300-999-649 REV 03 February 6, 2014 This technical note describes how to configure
Windows Server Firewall Configuration
 Windows Server Firewall, page 1 Cisco Firewall Configuration Utility Prerequisites, page 2 Run Cisco Firewall Configuration Utility, page 2 Verify New Windows Firewall Settings, page 3 Windows Server Firewall
Windows Server Firewall, page 1 Cisco Firewall Configuration Utility Prerequisites, page 2 Run Cisco Firewall Configuration Utility, page 2 Verify New Windows Firewall Settings, page 3 Windows Server Firewall
CYBER ATTACKS EXPLAINED: PACKET CRAFTING
 CYBER ATTACKS EXPLAINED: PACKET CRAFTING Protect your FOSS-based IT infrastructure from packet crafting by learning more about it. In the previous articles in this series, we explored common infrastructure
CYBER ATTACKS EXPLAINED: PACKET CRAFTING Protect your FOSS-based IT infrastructure from packet crafting by learning more about it. In the previous articles in this series, we explored common infrastructure
Network Security. Chapter 3. Cornelius Diekmann. Version: October 21, 2015. Lehrstuhl für Netzarchitekturen und Netzdienste Institut für Informatik
 Network Security Chapter 3 Cornelius Diekmann Lehrstuhl für Netzarchitekturen und Netzdienste Institut für Informatik Version: October 21, 2015 IN2101, WS 15/16, Network Security 1 Security Policies and
Network Security Chapter 3 Cornelius Diekmann Lehrstuhl für Netzarchitekturen und Netzdienste Institut für Informatik Version: October 21, 2015 IN2101, WS 15/16, Network Security 1 Security Policies and
Technical Support Information Belkin internal use only
 The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
The fundamentals of TCP/IP networking TCP/IP (Transmission Control Protocol / Internet Protocols) is a set of networking protocols that is used for communication on the Internet and on many other networks.
Active Directory. By: Kishor Datar 10/25/2007
 Active Directory By: Kishor Datar 10/25/2007 What is a directory service? Directory Collection of related objects Files, Printers, Fax servers etc. Directory Service Information needed to use and manage
Active Directory By: Kishor Datar 10/25/2007 What is a directory service? Directory Collection of related objects Files, Printers, Fax servers etc. Directory Service Information needed to use and manage
Univention Corporate Server. Operation of a Samba domain based on Windows NT domain services
 Univention Corporate Server Operation of a Samba domain based on Windows NT domain services 2 Table of Contents 1. Components of a Samba domain... 4 2. Installation... 5 3. Services of a Samba domain...
Univention Corporate Server Operation of a Samba domain based on Windows NT domain services 2 Table of Contents 1. Components of a Samba domain... 4 2. Installation... 5 3. Services of a Samba domain...
Configuring LDAP Directory Search on SPA SIP IP Phones
 Application Note EDCS-711822 Updated January 2009 Configuring LDAP Directory Search on SPA SIP IP Phones 2009 Cisco Systems, Inc. All rights reserved. This document is Cisco Proprietary Information. Page
Application Note EDCS-711822 Updated January 2009 Configuring LDAP Directory Search on SPA SIP IP Phones 2009 Cisco Systems, Inc. All rights reserved. This document is Cisco Proprietary Information. Page
TheGreenBow IPsec VPN Client. Configuration Guide Cisco RV325 v1. Website: www.thegreenbow.com Contact: [email protected]
 TheGreenBow IPsec VPN Client Configuration Guide Cisco RV325 v1 Website: www.thegreenbow.com Contact: [email protected] Table of Contents 1 Introduction... 3 1.1 Goal of this document... 3 1.2 VPN
TheGreenBow IPsec VPN Client Configuration Guide Cisco RV325 v1 Website: www.thegreenbow.com Contact: [email protected] Table of Contents 1 Introduction... 3 1.1 Goal of this document... 3 1.2 VPN
Network Traffic Analysis
 2013 Network Traffic Analysis Gerben Kleijn and Terence Nicholls 6/21/2013 Contents Introduction... 3 Lab 1 - Installing the Operating System (OS)... 3 Lab 2 Working with TCPDump... 4 Lab 3 - Installing
2013 Network Traffic Analysis Gerben Kleijn and Terence Nicholls 6/21/2013 Contents Introduction... 3 Lab 1 - Installing the Operating System (OS)... 3 Lab 2 Working with TCPDump... 4 Lab 3 - Installing
Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP
 Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP Deployment Guide Cisco VCS X8.1 D14465.06 December 2013 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration
Cisco TelePresence Authenticating Cisco VCS Accounts Using LDAP Deployment Guide Cisco VCS X8.1 D14465.06 December 2013 Contents Introduction 3 Process summary 3 LDAP accessible authentication server configuration
SUSE Manager 1.2.x ADS Authentication
 Best Practice www.suse.com SUSE Manager 1.2.x ADS Authentication How to use MS-ADS authentiction (Version 0.7 / March 2 nd 2012) P r e f a c e This paper should help to integrate SUSE Manager to an existing
Best Practice www.suse.com SUSE Manager 1.2.x ADS Authentication How to use MS-ADS authentiction (Version 0.7 / March 2 nd 2012) P r e f a c e This paper should help to integrate SUSE Manager to an existing
Cisco Configuring Commonly Used IP ACLs
 Table of Contents Configuring Commonly Used IP ACLs...1 Introduction...1 Prerequisites...2 Hardware and Software Versions...3 Configuration Examples...3 Allow a Select Host to Access the Network...3 Allow
Table of Contents Configuring Commonly Used IP ACLs...1 Introduction...1 Prerequisites...2 Hardware and Software Versions...3 Configuration Examples...3 Allow a Select Host to Access the Network...3 Allow
VLAN und MPLS, Firewall und NAT,
 Internet-Technologien (CS262) VLAN und MPLS, Firewall und NAT, 15.4.2015 Christian Tschudin Departement Mathematik und Informatik, Universität Basel 6-1 Wiederholung Unterschied CSMA/CD und CSMA/CA? Was
Internet-Technologien (CS262) VLAN und MPLS, Firewall und NAT, 15.4.2015 Christian Tschudin Departement Mathematik und Informatik, Universität Basel 6-1 Wiederholung Unterschied CSMA/CD und CSMA/CA? Was
Borderware MXtreme. Secure Email Gateway QuickStart Guide. Copyright 2005 CRYPTOCard Corporation All Rights Reserved
 Borderware MXtreme Secure Email Gateway QuickStart Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview MXtreme is a hardened appliance with a highly robust
Borderware MXtreme Secure Email Gateway QuickStart Guide Copyright 2005 CRYPTOCard Corporation All Rights Reserved http://www.cryptocard.com Overview MXtreme is a hardened appliance with a highly robust
Policy Based Forwarding
 Policy Based Forwarding Tech Note PAN-OS 4.1 Revision A 2012, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Security... 3 Performance... 3 Symmetric Routing... 3 Service Versus
Policy Based Forwarding Tech Note PAN-OS 4.1 Revision A 2012, Palo Alto Networks, Inc. www.paloaltonetworks.com Contents Overview... 3 Security... 3 Performance... 3 Symmetric Routing... 3 Service Versus
SSSD DNS Improvements in AD Environment
 FreeIPA 3.3 Training Series SSSD DNS Improvements in AD Environment Lukáš Slebodník 2014-March-12 Content Preconditions and assumed setup Dynamic DNS updates DNS site discovery Troubleshooting 2 FreeIPA
FreeIPA 3.3 Training Series SSSD DNS Improvements in AD Environment Lukáš Slebodník 2014-March-12 Content Preconditions and assumed setup Dynamic DNS updates DNS site discovery Troubleshooting 2 FreeIPA
Outline. CSc 466/566. Computer Security. 18 : Network Security Introduction. Network Topology. Network Topology. Christian Collberg
 Outline Network Topology CSc 466/566 Computer Security 18 : Network Security Introduction Version: 2012/05/03 13:59:29 Department of Computer Science University of Arizona [email protected] Copyright
Outline Network Topology CSc 466/566 Computer Security 18 : Network Security Introduction Version: 2012/05/03 13:59:29 Department of Computer Science University of Arizona [email protected] Copyright
Networks: IP and TCP. Internet Protocol
 Networks: IP and TCP 11/1/2010 Networks: IP and TCP 1 Internet Protocol Connectionless Each packet is transported independently from other packets Unreliable Delivery on a best effort basis No acknowledgments
Networks: IP and TCP 11/1/2010 Networks: IP and TCP 1 Internet Protocol Connectionless Each packet is transported independently from other packets Unreliable Delivery on a best effort basis No acknowledgments
How do I get to www.randomsite.com?
 Networking Primer* *caveat: this is just a brief and incomplete introduction to networking to help students without a networking background learn Network Security. How do I get to www.randomsite.com? Local
Networking Primer* *caveat: this is just a brief and incomplete introduction to networking to help students without a networking background learn Network Security. How do I get to www.randomsite.com? Local
WatchGuard Mobile User VPN Guide
 WatchGuard Mobile User VPN Guide Mobile User VPN establishes a secure connection between an unsecured remote host and a protected network over an unsecured network using Internet Protocol Security (IPSec).
WatchGuard Mobile User VPN Guide Mobile User VPN establishes a secure connection between an unsecured remote host and a protected network over an unsecured network using Internet Protocol Security (IPSec).
Deploying the BIG-IP System v11 with Microsoft Exchange 2010 and 2013 Client Access Servers
 Deployment Guide Deploying the BIG-IP System v11 with Microsoft Exchange 2010 and 2013 Client Access Servers Welcome to the F5 and Microsoft Exchange 2010 and 2013 Client Access Server deployment guide.
Deployment Guide Deploying the BIG-IP System v11 with Microsoft Exchange 2010 and 2013 Client Access Servers Welcome to the F5 and Microsoft Exchange 2010 and 2013 Client Access Server deployment guide.
GlobalSCAPE DMZ Gateway, v1. User Guide
 GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
SonicWALL DHCP Server Enhancements in SonicOS Enhanced 4.0
 SonicWALL DHCP Server Enhancements in SonicOS Enhanced 4.0 Document Scope This document describes the DHCP enhancements in SonicOS Enhanced 4.0, including DHCP server options and DHCP server persistence.
SonicWALL DHCP Server Enhancements in SonicOS Enhanced 4.0 Document Scope This document describes the DHCP enhancements in SonicOS Enhanced 4.0, including DHCP server options and DHCP server persistence.
OSBRiDGE 5XLi. Configuration Manual. Firmware 3.10R
 OSBRiDGE 5XLi Configuration Manual Firmware 3.10R 1. Initial setup and configuration. OSBRiDGE 5XLi devices are configurable via WWW interface. Each device uses following default settings: IP Address:
OSBRiDGE 5XLi Configuration Manual Firmware 3.10R 1. Initial setup and configuration. OSBRiDGE 5XLi devices are configurable via WWW interface. Each device uses following default settings: IP Address:
Network Monitoring. By: Delbert Thompson Network & Network Security Supervisor Basin Electric Power Cooperative
 Network Monitoring By: Delbert Thompson Network & Network Security Supervisor Basin Electric Power Cooperative Overview of network Logical network view Goals of Network Monitoring Determine overall health
Network Monitoring By: Delbert Thompson Network & Network Security Supervisor Basin Electric Power Cooperative Overview of network Logical network view Goals of Network Monitoring Determine overall health
Firewalls. Chapter 3
 Firewalls Chapter 3 1 Border Firewall Passed Packet (Ingress) Passed Packet (Egress) Attack Packet Hardened Client PC Internet (Not Trusted) Hardened Server Dropped Packet (Ingress) Log File Internet Border
Firewalls Chapter 3 1 Border Firewall Passed Packet (Ingress) Passed Packet (Egress) Attack Packet Hardened Client PC Internet (Not Trusted) Hardened Server Dropped Packet (Ingress) Log File Internet Border
Procedure: You can find the problem sheet on Drive D: of the lab PCs. 1. IP address for this host computer 2. Subnet mask 3. Default gateway address
 Objectives University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 Lab.4 Basic Network Operation and Troubleshooting 1. To become familiar
Objectives University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 Lab.4 Basic Network Operation and Troubleshooting 1. To become familiar
CET442L Lab #2. IP Configuration and Network Traffic Analysis Lab
 CET442L Lab #2 IP Configuration and Network Traffic Analysis Lab Goals: In this lab you will plan and implement the IP configuration for the Windows server computers on your group s network. You will use
CET442L Lab #2 IP Configuration and Network Traffic Analysis Lab Goals: In this lab you will plan and implement the IP configuration for the Windows server computers on your group s network. You will use
Chapter 8 Security Pt 2
 Chapter 8 Security Pt 2 IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 All material copyright 1996-2012 J.F Kurose and K.W. Ross,
Chapter 8 Security Pt 2 IC322 Fall 2014 Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 All material copyright 1996-2012 J.F Kurose and K.W. Ross,
Guideline for setting up a functional VPN
 Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Upgrading User-ID. Tech Note PAN-OS 4.1. 2011, Palo Alto Networks, Inc.
 Upgrading User-ID Tech Note PAN-OS 4.1 Revision B 2011, Palo Alto Networks, Inc. Overview PAN-OS 4.1 introduces significant improvements in the User-ID feature by adding support for multiple user directories,
Upgrading User-ID Tech Note PAN-OS 4.1 Revision B 2011, Palo Alto Networks, Inc. Overview PAN-OS 4.1 introduces significant improvements in the User-ID feature by adding support for multiple user directories,
PktFilter A Win32 service to control the IPv4 filtering driver of Windows 2000/XP/Server 2003 http://sourceforge.net/projects/pktfilter/
 PktFilter A Win32 service to control the IPv4 filtering driver of Windows 2000/XP/Server 2003 http://sourceforge.net/projects/pktfilter/ Jean-Baptiste Marchand [email protected] Contents 1
PktFilter A Win32 service to control the IPv4 filtering driver of Windows 2000/XP/Server 2003 http://sourceforge.net/projects/pktfilter/ Jean-Baptiste Marchand [email protected] Contents 1
Transport server data paths
 1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
Chapter 8 Monitoring and Logging
 Chapter 8 Monitoring and Logging This chapter describes the SSL VPN Concentrator status information, logging, alerting and reporting features. It describes: SSL VPN Concentrator Status Active Users Event
Chapter 8 Monitoring and Logging This chapter describes the SSL VPN Concentrator status information, logging, alerting and reporting features. It describes: SSL VPN Concentrator Status Active Users Event
Network layer" 1DT066! Distributed Information Systems!! Chapter 4" Network Layer!! goals: "
 1DT066! Distributed Information Systems!! Chapter 4" Network Layer!! Network layer" goals: "! understand principles behind layer services:" " layer service models" " forwarding versus routing" " how a
1DT066! Distributed Information Systems!! Chapter 4" Network Layer!! Network layer" goals: "! understand principles behind layer services:" " layer service models" " forwarding versus routing" " how a
Configuring Active Directory Single Sign-On (AD SSO)
 9 CHAPTER Configuring Active Directory Single Sign-On (AD SSO) This chapter describes how to configure Active Directory (AD) Single Sign-On (SSO) for the Cisco NAC Appliance. Topics include: Overview,
9 CHAPTER Configuring Active Directory Single Sign-On (AD SSO) This chapter describes how to configure Active Directory (AD) Single Sign-On (SSO) for the Cisco NAC Appliance. Topics include: Overview,
Nokia Siemens Networks. CPEi-lte 7212. User Manual
 Nokia Siemens Networks CPEi-lte 7212 User Manual Contents Chapter 1: CPEi-lte 7212 User Guide Overview... 1-1 Powerful Features in a Single Unit... 1-2 Front of the CPEi-lte 7212... 1-2 Back of the CPEi-lte
Nokia Siemens Networks CPEi-lte 7212 User Manual Contents Chapter 1: CPEi-lte 7212 User Guide Overview... 1-1 Powerful Features in a Single Unit... 1-2 Front of the CPEi-lte 7212... 1-2 Back of the CPEi-lte
Lesson Plans Managing a Windows 2003 Network Infrastructure
 Lesson Plans Managing a Windows 2003 Network Infrastructure (Exam 70-291) Table of Contents Course Overview... 2 Section 0.1: Introduction... 3 Section 1.1: Client Configuration... 4 Section 1.2: IP Addressing...
Lesson Plans Managing a Windows 2003 Network Infrastructure (Exam 70-291) Table of Contents Course Overview... 2 Section 0.1: Introduction... 3 Section 1.1: Client Configuration... 4 Section 1.2: IP Addressing...
Network Security. Marcus Bendtsen Institutionen för Datavetenskap (IDA) Avdelningen för Databas- och Informationsteknik (ADIT)
 Network Security ICMP, TCP, DNS, Scanning Marcus Bendtsen Institutionen för Datavetenskap (IDA) Avdelningen för Databas- och Informationsteknik (ADIT) Agenda A couple of examples of network protocols that
Network Security ICMP, TCP, DNS, Scanning Marcus Bendtsen Institutionen för Datavetenskap (IDA) Avdelningen för Databas- och Informationsteknik (ADIT) Agenda A couple of examples of network protocols that
CS 326e F2002 Lab 1. Basic Network Setup & Ethereal Time: 2 hrs
 CS 326e F2002 Lab 1. Basic Network Setup & Ethereal Time: 2 hrs Tasks: 1 (10 min) Verify that TCP/IP is installed on each of the computers 2 (10 min) Connect the computers together via a switch 3 (10 min)
CS 326e F2002 Lab 1. Basic Network Setup & Ethereal Time: 2 hrs Tasks: 1 (10 min) Verify that TCP/IP is installed on each of the computers 2 (10 min) Connect the computers together via a switch 3 (10 min)
Module 10: Maintaining Active Directory
 Module 10: Maintaining Active Directory! Lesson: Backing Up Active Directory Topic: How to Back Up Active Directory! Lesson: Restoring Active Directory Topic: How to Perform a Primary Restore! Lesson:
Module 10: Maintaining Active Directory! Lesson: Backing Up Active Directory Topic: How to Back Up Active Directory! Lesson: Restoring Active Directory Topic: How to Perform a Primary Restore! Lesson:
TCP Performance Management for Dummies
 TCP Performance Management for Dummies Nalini Elkins Inside Products, Inc. Monday, August 8, 2011 Session Number 9285 Our SHARE Sessions Orlando 9285: TCP/IP Performance Management for Dummies Monday,
TCP Performance Management for Dummies Nalini Elkins Inside Products, Inc. Monday, August 8, 2011 Session Number 9285 Our SHARE Sessions Orlando 9285: TCP/IP Performance Management for Dummies Monday,
IP network tools & troubleshooting. AFCHIX 2010 Nairobi, Kenya October 2010
 IP network tools & troubleshooting AFCHIX 2010 Nairobi, Kenya October 2010 Network configuration Reminder, configure your network in /etc/ rc.conf ( x = your IP, from.10 to...) ifconfig_bge0= 41.215.76.x/24
IP network tools & troubleshooting AFCHIX 2010 Nairobi, Kenya October 2010 Network configuration Reminder, configure your network in /etc/ rc.conf ( x = your IP, from.10 to...) ifconfig_bge0= 41.215.76.x/24
BASIC ANALYSIS OF TCP/IP NETWORKS
 BASIC ANALYSIS OF TCP/IP NETWORKS INTRODUCTION Communication analysis provides powerful tool for maintenance, performance monitoring, attack detection, and problems fixing in computer networks. Today networks
BASIC ANALYSIS OF TCP/IP NETWORKS INTRODUCTION Communication analysis provides powerful tool for maintenance, performance monitoring, attack detection, and problems fixing in computer networks. Today networks
qliqdirect Active Directory Guide
 qliqdirect Active Directory Guide qliqdirect is a Windows Service with Active Directory Interface. qliqdirect resides in your network/server and communicates with qliqsoft cloud servers securely. qliqdirect
qliqdirect Active Directory Guide qliqdirect is a Windows Service with Active Directory Interface. qliqdirect resides in your network/server and communicates with qliqsoft cloud servers securely. qliqdirect
Configuring SSL VPN on the Cisco ISA500 Security Appliance
 Application Note Configuring SSL VPN on the Cisco ISA500 Security Appliance This application note describes how to configure SSL VPN on the Cisco ISA500 security appliance. This document includes these
Application Note Configuring SSL VPN on the Cisco ISA500 Security Appliance This application note describes how to configure SSL VPN on the Cisco ISA500 security appliance. This document includes these
A1.1.1.11.1.1.2 1.1.1.3S B
 CS Computer 640: Network AdityaAkella Lecture Introduction Networks Security 25 to Security DoS Firewalls and The D-DoS Vulnerabilities Road Ahead Security Attacks Protocol IP ICMP Routing TCP Security
CS Computer 640: Network AdityaAkella Lecture Introduction Networks Security 25 to Security DoS Firewalls and The D-DoS Vulnerabilities Road Ahead Security Attacks Protocol IP ICMP Routing TCP Security
FortiOS Handbook - Load Balancing VERSION 5.2.2
 FortiOS Handbook - Load Balancing VERSION 5.2.2 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE
FortiOS Handbook - Load Balancing VERSION 5.2.2 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET BLOG https://blog.fortinet.com CUSTOMER SERVICE
Unix System Administration
 Unix System Administration Chris Schenk Lecture 08 Tuesday Feb 13 CSCI 4113, Spring 2007 ARP Review Host A 128.138.202.50 00:0B:DB:A6:76:18 Host B 128.138.202.53 00:11:43:70:45:81 Switch Host C 128.138.202.71
Unix System Administration Chris Schenk Lecture 08 Tuesday Feb 13 CSCI 4113, Spring 2007 ARP Review Host A 128.138.202.50 00:0B:DB:A6:76:18 Host B 128.138.202.53 00:11:43:70:45:81 Switch Host C 128.138.202.71
Non-intrusive, complete network protocol decoding with plain mnemonics in English
 The Triple Play Analysis Suite - DATA The Triple Play Analysis Suite - Data are meant for emulating the client s application such as FTP downloading or Web Browser testing at the termination point of DSL
The Triple Play Analysis Suite - DATA The Triple Play Analysis Suite - Data are meant for emulating the client s application such as FTP downloading or Web Browser testing at the termination point of DSL
PineApp Surf-SeCure Quick
 PineApp Surf-SeCure Quick Installation Guide September 2010 WEB BASED INSTALLATION SURF-SECURE AS PROXY 1. Once logged in, set the appliance s clock: a. Click on the Edit link under Time-Zone section.
PineApp Surf-SeCure Quick Installation Guide September 2010 WEB BASED INSTALLATION SURF-SECURE AS PROXY 1. Once logged in, set the appliance s clock: a. Click on the Edit link under Time-Zone section.
Apliware firewall. TheGreenBow IPSec VPN Client. Configuration Guide. http://www.thegreenbow.com [email protected]
 TheGreenBow IPSec VPN Client Configuration Guide Apliware firewall WebSite: Contact: http://www.thegreenbow.com [email protected] Table of contents 1 Introduction... 0 1.1 Goal of this document...
TheGreenBow IPSec VPN Client Configuration Guide Apliware firewall WebSite: Contact: http://www.thegreenbow.com [email protected] Table of contents 1 Introduction... 0 1.1 Goal of this document...
Symantec Firewall/VPN 200
 TheGreenBow IPSec VPN Client Configuration Guide Symantec Firewall/VPN 200 WebSite: Contact: http://www.thegreenbow.com [email protected] Table of contents 1 Introduction... 0 1.1 Goal of this document...
TheGreenBow IPSec VPN Client Configuration Guide Symantec Firewall/VPN 200 WebSite: Contact: http://www.thegreenbow.com [email protected] Table of contents 1 Introduction... 0 1.1 Goal of this document...
Chapter 10 Troubleshooting
 Chapter 10 Troubleshooting This chapter provides troubleshooting tips and information for your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. After each problem description, instructions are provided
Chapter 10 Troubleshooting This chapter provides troubleshooting tips and information for your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. After each problem description, instructions are provided
Ingate Firewall. TheGreenBow IPSec VPN Client Configuration Guide. http://www.thegreenbow.com [email protected]
 TheGreenBow IPSec VPN Client Configuration Guide Ingate Firewall WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow Sistech SA -
TheGreenBow IPSec VPN Client Configuration Guide Ingate Firewall WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow Sistech SA -
Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop
 Deployment Guide Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop Welcome to the F5 deployment guide for Citrix VDI applications, including XenApp and XenDesktop with the BIG-IP v11.2
Deployment Guide Deploying the BIG-IP LTM and APM with Citrix XenApp or XenDesktop Welcome to the F5 deployment guide for Citrix VDI applications, including XenApp and XenDesktop with the BIG-IP v11.2
UNCLASSIFIED. BlackBerry Enterprise Server Isolation in a Microsoft Exchange Environment (ITSG-23)
 BlackBerry Enterprise Server Isolation in a Microsoft Exchange Environment (ITSG-23) March 2007 This page intentionally left blank. March 2007 Foreword The BlackBerry Enterprise Server Isolation in a Microsoft
BlackBerry Enterprise Server Isolation in a Microsoft Exchange Environment (ITSG-23) March 2007 This page intentionally left blank. March 2007 Foreword The BlackBerry Enterprise Server Isolation in a Microsoft
Load Balancing. FortiOS Handbook v3 for FortiOS 4.0 MR3
 Load Balancing FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook Load Balancing v3 8 February 2012 01-431-99686-20120208 Copyright 2012 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, and
Load Balancing FortiOS Handbook v3 for FortiOS 4.0 MR3 FortiOS Handbook Load Balancing v3 8 February 2012 01-431-99686-20120208 Copyright 2012 Fortinet, Inc. All rights reserved. Fortinet, FortiGate, and
Micronet SP881. TheGreenBow IPSec VPN Client Configuration Guide. http://www.thegreenbow.com [email protected]
 TheGreenBow IPSec VPN Client Configuration Guide Micronet SP881 WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow Sistech SA -
TheGreenBow IPSec VPN Client Configuration Guide Micronet SP881 WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow Sistech SA -
Host Fingerprinting and Firewalking With hping
 Host Fingerprinting and Firewalking With hping Naveed Afzal National University Of Computer and Emerging Sciences, Lahore, Pakistan Email: [email protected] Naveedafzal gmail.com Abstract: The purpose
Host Fingerprinting and Firewalking With hping Naveed Afzal National University Of Computer and Emerging Sciences, Lahore, Pakistan Email: [email protected] Naveedafzal gmail.com Abstract: The purpose
Application. Transport. Network. Data Link. Physical. Network Layers. Goal
 Layers Goal Understand how application processes set up a connection and exchange messages. Understand how addresses are determined 1 2 Data Exchange Between Processes TCP Connection-Setup Between Processes
Layers Goal Understand how application processes set up a connection and exchange messages. Understand how addresses are determined 1 2 Data Exchange Between Processes TCP Connection-Setup Between Processes
Using DC Agent for Transparent User Identification
 Using DC Agent for Transparent User Identification Using DC Agent Web Security Solutions v7.7, 7.8 If your organization uses Microsoft Windows Active Directory, you can use Websense DC Agent to identify
Using DC Agent for Transparent User Identification Using DC Agent Web Security Solutions v7.7, 7.8 If your organization uses Microsoft Windows Active Directory, you can use Websense DC Agent to identify
Smart Tips. Enabling WAN Load Balancing. Key Features. Network Diagram. Overview. Featured Products. WAN Failover. Enabling WAN Load Balancing Page 1
 Smart Tips Enabling WAN Load Balancing Overview Many small businesses today use broadband links such as DSL or Cable, favoring them over the traditional link such as T1/E1 or leased lines because of the
Smart Tips Enabling WAN Load Balancing Overview Many small businesses today use broadband links such as DSL or Cable, favoring them over the traditional link such as T1/E1 or leased lines because of the
Catalyst Layer 3 Switch for Wake On LAN Support Across VLANs Configuration Example
 Catalyst Layer 3 Switch for Wake On LAN Support Across VLANs Configuration Example Document ID: 91672 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information
Catalyst Layer 3 Switch for Wake On LAN Support Across VLANs Configuration Example Document ID: 91672 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information
Deploying ModusGate with Exchange Server. (Version 4.0+)
 Deploying ModusGate with Exchange Server (Version 4.0+) Active Directory and LDAP: Overview... 3 ModusGate/Exchange Server Deployment Strategies... 4 Basic Requirements for ModusGate & Exchange Server
Deploying ModusGate with Exchange Server (Version 4.0+) Active Directory and LDAP: Overview... 3 ModusGate/Exchange Server Deployment Strategies... 4 Basic Requirements for ModusGate & Exchange Server
Cisco SA 500 Series Security Appliance
 TheGreenBow IPSec VPN Client Configuration Guide Cisco SA 500 Series Security Appliance This guide applies to the following models: Cisco SA 520 Cisco SA 520W Cisco SA 540 WebSite: Contact: http://www.thegreenbow.de
TheGreenBow IPSec VPN Client Configuration Guide Cisco SA 500 Series Security Appliance This guide applies to the following models: Cisco SA 520 Cisco SA 520W Cisco SA 540 WebSite: Contact: http://www.thegreenbow.de
Planet CS-1000. TheGreenBow IPSec VPN Client. Configuration Guide. http://www.thegreenbow.com [email protected]
 TheGreenBow IPSec VPN Client Configuration Guide Planet CS-1000 WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow Sistech SA -
TheGreenBow IPSec VPN Client Configuration Guide Planet CS-1000 WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow Sistech SA -
Linksys RV042. TheGreenBow IPSec VPN Client. Configuration Guide. http://www.thegreenbow.com [email protected]
 TheGreenBow IPSec VPN Client Configuration Guide Linksys RV042 WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: TheGreenBow Support Team Company:
TheGreenBow IPSec VPN Client Configuration Guide Linksys RV042 WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: TheGreenBow Support Team Company:
What is a DoS attack?
 CprE 592-YG Computer and Network Forensics Log-based Signature Analysis Denial of Service Attacks - from analyst s point of view Yong Guan 3216 Coover Tel: (515) 294-8378 Email: [email protected] October
CprE 592-YG Computer and Network Forensics Log-based Signature Analysis Denial of Service Attacks - from analyst s point of view Yong Guan 3216 Coover Tel: (515) 294-8378 Email: [email protected] October
1 hours, 30 minutes, 38 seconds Heavy scan. All scanned network resources. Copyright 2001, FTP access obtained
 home Network Vulnerabilities Detail Report Grouped by Vulnerability Report Generated by: Symantec NetRecon 3.5 Licensed to: X Serial Number: 0182037567 Machine Scanned from: ZEUS (192.168.1.100) Scan Date:
home Network Vulnerabilities Detail Report Grouped by Vulnerability Report Generated by: Symantec NetRecon 3.5 Licensed to: X Serial Number: 0182037567 Machine Scanned from: ZEUS (192.168.1.100) Scan Date:
Juniper NetScreen 5GT
 TheGreenBow IPSec VPN Client Configuration Guide Juniper NetScreen 5GT WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: Connected Team Company:
TheGreenBow IPSec VPN Client Configuration Guide Juniper NetScreen 5GT WebSite: Contact: http://www.thegreenbow.com [email protected] Configuration Guide written by: Writer: Connected Team Company:
Computer Networks. Chapter 5 Transport Protocols
 Computer Networks Chapter 5 Transport Protocols Transport Protocol Provides end-to-end transport Hides the network details Transport protocol or service (TS) offers: Different types of services QoS Data
Computer Networks Chapter 5 Transport Protocols Transport Protocol Provides end-to-end transport Hides the network details Transport protocol or service (TS) offers: Different types of services QoS Data
Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure
 Question Number (ID) : 1 (wmpmsp_mngnwi-121) You are an administrator for an organization that provides Internet connectivity to users from the corporate network. Several users complain that they cannot
Question Number (ID) : 1 (wmpmsp_mngnwi-121) You are an administrator for an organization that provides Internet connectivity to users from the corporate network. Several users complain that they cannot
Cisco RV 120W Wireless-N VPN Firewall
 TheGreenBow IPSec VPN Client Configuration Guide Cisco RV 120W Wireless-N VPN Firewall WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow
TheGreenBow IPSec VPN Client Configuration Guide Cisco RV 120W Wireless-N VPN Firewall WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow
ZyXEL ZyWALL P1 firmware V3.64
 TheGreenBow IPSec VPN Client Configuration Guide ZyXEL ZyWALL P1 firmware V3.64 WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow
TheGreenBow IPSec VPN Client Configuration Guide ZyXEL ZyWALL P1 firmware V3.64 WebSite: Contact: http://www.thegreenbow.com [email protected] IPSec VPN Router Configuration Property of TheGreenBow
Getting Started Guide
 Getting Started Guide CensorNet Professional Copyright CensorNet Limited, 2007-2011 This document is designed to provide information about the first time configuration and testing of the CensorNet Professional
Getting Started Guide CensorNet Professional Copyright CensorNet Limited, 2007-2011 This document is designed to provide information about the first time configuration and testing of the CensorNet Professional
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0
 Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Quick Note 53. Ethernet to W-WAN failover with logical Ethernet interface.
 Quick Note 53 Ethernet to W-WAN failover with logical Ethernet interface. Digi Support August 2015 1 Contents 1 Introduction... 2 1.1 Introduction... 2 1.2 Assumptions... 3 1.3 Corrections... 3 2 Version...
Quick Note 53 Ethernet to W-WAN failover with logical Ethernet interface. Digi Support August 2015 1 Contents 1 Introduction... 2 1.1 Introduction... 2 1.2 Assumptions... 3 1.3 Corrections... 3 2 Version...
Packet Capture. Document Scope. SonicOS Enhanced Packet Capture
 Packet Capture Document Scope This solutions document describes how to configure and use the packet capture feature in SonicOS Enhanced. This document contains the following sections: Feature Overview
Packet Capture Document Scope This solutions document describes how to configure and use the packet capture feature in SonicOS Enhanced. This document contains the following sections: Feature Overview
Implementing, Managing, and Maintaining a Microsoft Windows Server 2003 Network Infrastructure
 Question Number (ID) : 1 (jaamsp_mngnwi-025) Lisa would like to configure five of her 15 Web servers, which are running Microsoft Windows Server 2003, Web Edition, to always receive specific IP addresses
Question Number (ID) : 1 (jaamsp_mngnwi-025) Lisa would like to configure five of her 15 Web servers, which are running Microsoft Windows Server 2003, Web Edition, to always receive specific IP addresses
Minimal network traffic is the result of SiteAudit s design. The information below explains why network traffic is minimized.
 SiteAudit Knowledge Base Network Traffic March 2012 In This Article: SiteAudit s Traffic Impact How SiteAudit Discovery Works Why Traffic is Minimal How to Measure Traffic Minimal network traffic is the
SiteAudit Knowledge Base Network Traffic March 2012 In This Article: SiteAudit s Traffic Impact How SiteAudit Discovery Works Why Traffic is Minimal How to Measure Traffic Minimal network traffic is the
Firewall Implementation
 CS425: Computer Networks Firewall Implementation Ankit Kumar Y8088 Akshay Mittal Y8056 Ashish Gupta Y8410 Sayandeep Ghosh Y8465 October 31, 2010 under the guidance of Prof. Dheeraj Sanghi Department of
CS425: Computer Networks Firewall Implementation Ankit Kumar Y8088 Akshay Mittal Y8056 Ashish Gupta Y8410 Sayandeep Ghosh Y8465 October 31, 2010 under the guidance of Prof. Dheeraj Sanghi Department of
Denial Of Service. Types of attacks
 Denial Of Service The goal of a denial of service attack is to deny legitimate users access to a particular resource. An incident is considered an attack if a malicious user intentionally disrupts service
Denial Of Service The goal of a denial of service attack is to deny legitimate users access to a particular resource. An incident is considered an attack if a malicious user intentionally disrupts service
Client Server Networks
 Name: Date: Quiz 3: Load 2008 Server, LAN Setup, Driver Load, Windows Update, Windows Defender, Active Directory, Organizational Units, Groups, Password and Lockout Polices, Joining a Domain, Wireless
Name: Date: Quiz 3: Load 2008 Server, LAN Setup, Driver Load, Windows Update, Windows Defender, Active Directory, Organizational Units, Groups, Password and Lockout Polices, Joining a Domain, Wireless
Step-by-Step Guide for Creating and Testing Connection Manager Profiles in a Test Lab
 Step-by-Step Guide for Creating and Testing Connection Manager Profiles in a Test Lab Microsoft Corporation Published: May, 2005 Author: Microsoft Corporation Abstract This guide describes how to create
Step-by-Step Guide for Creating and Testing Connection Manager Profiles in a Test Lab Microsoft Corporation Published: May, 2005 Author: Microsoft Corporation Abstract This guide describes how to create
DNS: How it works. DNS: How it works (more or less ) DNS: How it Works. Technical Seminars Spring 2010 1. Paul Semple psemple@rm.
 DNS: How it works Paul Semple [email protected] DNS: How it works (more or less ) Paul Semple [email protected] 1 Objectives What DNS is and why we need it DNS on Windows Server networks / Community Connect
DNS: How it works Paul Semple [email protected] DNS: How it works (more or less ) Paul Semple [email protected] 1 Objectives What DNS is and why we need it DNS on Windows Server networks / Community Connect
Virtual Private Network VPN IPSec Testing: Functionality Interoperability and Performance
 Virtual Private Network VPN IPSec Testing: Functionality Interoperability and Performance Johnnie Chen Project Manager of Network Security Group Network Benchmarking Lab Network Benchmarking Laboratory
Virtual Private Network VPN IPSec Testing: Functionality Interoperability and Performance Johnnie Chen Project Manager of Network Security Group Network Benchmarking Lab Network Benchmarking Laboratory
SKV PROPOSAL TO TLC FOR ACTIVE DIRECTORY SITE IMPLEMENTATION
 SKV PROPOSAL TO TLC FOR ACTIVE DIRECTORY SITE IMPLEMENTATION Date: Jan 27,2014 Prepared by: Sainath K.E.V Microsoft Most Valuable Professional Introduction: SKV Consulting is a Premier Consulting providing
SKV PROPOSAL TO TLC FOR ACTIVE DIRECTORY SITE IMPLEMENTATION Date: Jan 27,2014 Prepared by: Sainath K.E.V Microsoft Most Valuable Professional Introduction: SKV Consulting is a Premier Consulting providing
Step-by-Step Guide for Setting Up VPN-based Remote Access in a Test Lab
 Página 1 de 54 Step-by-Step Guide for Setting Up VPN-based Remote Access in a Test Lab This guide provides detailed information about how you can use five computers to create a test lab with which to configure
Página 1 de 54 Step-by-Step Guide for Setting Up VPN-based Remote Access in a Test Lab This guide provides detailed information about how you can use five computers to create a test lab with which to configure
