E-commerce in Your Inbox: Product Recommendations at Scale
|
|
|
- Samson Walters
- 10 years ago
- Views:
Transcription
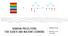
1 E-commerce in Your Inbox: Product Recommendations at Scale Mihajlo Grbovic, Vladan Radosavljevic, Nemanja Djuric, Narayan Bhamidipati Yahoo Labs 701 First Avenue, Sunnyvale, USA {mihajlo, vladan, nemanja, Jaikit Savla, Varun Bhagwan, Doug Sharp Yahoo, Inc. 701 First Avenue, Sunnyvale, USA {jaikit, vbhagwan, ABSTRACT In recent years online advertising has become increasingly ubiquitous and effective. Advertisements shown to visitors fund sites and apps that publish digital content, manage social networks, and operate services. Given such large variety of internet resources, determining an appropriate type of advertising for a given platform has become critical to financial success. Native advertisements, namely ads that are similar in look and feel to content, have had great success in news and social feeds. However, to date there has not been a winning formula for ads in clients. In this paper we describe a system that leverages user purchase history determined from receipts to deliver highly personalized product ads to Yahoo Mail users. We propose to use a novel neural language-based algorithm specifically tailored for delivering effective product recommendations, which was evaluated against baselines that included showing popular products and products predicted based on cooccurrence. We conducted rigorous offline testing using a large-scale product purchase data set, covering purchases of more than 29 million users from 172 e-commerce websites. Ads in the form of product recommendations were successfully tested on online traffic, where we observed a steady 9% lift in click-through rates over other ad formats in mail, as well as comparable lift in conversion rates. Following successful tests, the system was launched into production during the holiday season of Categories and Subject Descriptors H.2.8 [Database applications]: Data Mining Keywords Data mining; computational advertising; audience modeling Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. Copyrights for components of this work owned by others than ACM must be honored. Abstracting with credit is permitted. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. Request permissions from [email protected]. KDD 15, August 10-13, 2015, Sydney, NSW, Australia c 2015 ACM. ISBN /15/08...$15.00 DOI: 1. INTRODUCTION Hundreds of millions of people around the world visit their inboxes daily, mostly to communicate with their contacts, although a significant fraction of time is spent checking utility bills, reading newsletters, and tracking purchases. To monetize this overwhelming amount of traffic, clients typically show display ads in a form of images alongside native content. Convincing users to exit the mode, characterized by a relentless focus on the task of dealing with their mail, in order to enter a mode where they are willing to click on ads is a challenging task. Effective personalization and targeting [11], where the goal is to find the best matching ads to be displayed for each individual user, is essential to tackling this problem, as ads need to be highly relevant to overcome user s inclination to focus narrowly on the task. In addition to financial gains for online businesses [26], proactively tailoring advertisements to the tastes of each individual consumer also leads to an improved user experience, and can help with increasing user loyalty and retention [2]. Inbound s are still insufficiently explored and exploited for the purposes of ad targeting, while arguably representing a treasure trove of monetizable data. A recent study [13] showed that only 10% of inbound volume represents human-generated s. Furthermore, out of the remaining 90% of traffic more than 22% represents s related to online shopping. Given that a significant percentage of overall traffic has commercial intent, a popular form of targeted advertising is mail retargeting (MRT), where advertisers target users who previously received s from certain commercial web domains. These s present a strong signal useful for targeting campaigns, as they give a broad picture about each customer s interests and relationship with commercial domains. A recent paper [14] proposed to make use of this vast potential and presented a clustering method to generate MRT rules, showing that such rules are more accurate than the ones generated by human experts. However, in order to go beyond MRT rules that utilize only the fact that users and e-commerce sites communicated, advertisers require more detailed data such as purchased product name and price that are often part of body. clients have been working with e-commerce and travel domains to standardize how s are formatted, resulting in schemas maintained by the schema.org com-
2 Figure 1: Product recommendations in Yahoo Mail munity 1. With more and more e-commerce sites using standard schemas, clients can provide more personalized user notifications, such as package tracking 2 and flight details 3. In addition, receipt extraction brings monetization opportunity through product advertising to users based on their individual purchase history. Availability of purchase data from multiple commercial domains puts the provider in the unique position to be able to build better recommendation systems than those based on any one commercial domain alone. In particular, unlike e-commerce websites that make recommendations of type: Customers who bought X also bought Y, providers can make recommendations of type: Customers who bought X from vendor V 1 also bought Y from vendor V 2, allowing much more powerful and effective targeting solutions. In this paper we tell the story of an end-to-end development of product ads for Yahoo Mail. The effort included developing a product-level purchase prediction algorithm, capable of scaling to millions of users and products. To this end, we propose an approach that embeds products into real-valued, low-dimensional vector space using a neural language model applied to a time series of user purchases. As a result, products with similar contexts (i.e., their surrounding purchases) are mapped to vectors that are nearby in the embedding space. To be able to make meaningful and diverse suggestions about the next product to be purchased, we further cluster the product vectors and model transition probabilities between clusters. The closest products in the embedding space from the most probable clusters are used to form final recommendations for a product. The product prediction model was trained using a largescale purchase data set, comprising more than 280 million purchases made by 29 million users, involving 2.1 million unique products. The model was evaluated on a held-out month, where we tested the effectiveness of recommendations in terms of yield rate. In addition, we evaluated several baseline approaches, including showing popular products to all users, showing popular products in various user groups (called cohorts, specified by user s gender, age, and location), as well as showing products that are historically frequently purchased after the product a user most recently bought. To mitigate the cold start problem, popular products in user s cohort were used as back-fill recommendations for users without earlier purchases. 1 accessed June yahoomail.tumblr.com/post/ /track-yourpackages-now-in-the-yahoo-mail-app, accessed June venturebeat.com/2014/10/22/yahoo-mail-now-tells-youabout-upcoming-flights-and-events, accessed June 2015 Empirical results show that the proposed product-level model is able to more accurately predict purchases than baseline approaches. In the experimental section we also share results of bucket tests on live traffic, where we compared the performance of the baselines in the same ad slot. Our method substantially improves key business metrics, measured in terms of clicks and conversions. Moreover, our product-prediction technique was successfully implemented at large scale, tested in live buckets, and finally launched in production. The system is able to make near-real-time product recommendations with latency of less than 200ms. In Figure 1 we show an example of our product recommender, where an offer from walmart.com is suggested after related purchase was made on amazon.com (marked with red). 2. RELATED WORK In this section we describe related work in mail-based advertising, as well as neural language models that motivated our product recommendation approach. 2.1 Leveraging data in advertising Web environment provides content publishers with a means to track user behavior in much greater detail than in an offline settings, including capturing user s registered information and activity logs of user s clicks, page views, searches, website visits, social activities, and interactions with ads. This allows for targeting of users based on their behavior, which is typically referred to as ad targeting [1]. With the rise of big data applications and platforms, machine learning approaches are heavily leveraged to automate the ad targeting process. Within the past several years, there has been a plethora of research papers that explored different aspects of online advertising, each with the goal of maximizing the benefits for advertisers, content publishers, and users. For any machine learning technique, features used to train a model typically have a critical influence on the performance of the deployed algorithm. Features derived from user events collected by publishers are often used in predicting the user s propensity to click or purchase [9]. However, these features represent only a weak proxy to what publishers and advertisers are actually interested in, namely, user s purchase intent. On the other hand, commercial s in the form of promotions and purchase receipts convey a strong, very direct purchase intent signal that can enable advertisers to reach a high-quality audience. According to the Direct Marketing Association s National Client Report 4, an user has been identified as having over 10% more value than the average online customer. Despite these 4 accessed June 2015
3 encouraging facts, limited work has been done to analyze the potential of features derived from commercial s. A recent work [14] was among the first attempts to investigate the value of commercial data. The authors applied Sparse Principal Component Analysis (SPCA) on the counts of received s in order to cluster commercial domains, demonstrating significant promise of data source. Outside of the domain, information about user s purchase history is extensively used by e-commerce websites to recommend relevant products to their users [22]. Recommendation systems predict which products a user will most likely be interested in either by exploiting purchase behavior of users with similar interests (referred to as collaborative filtering [22]) or by using user s historical interaction with other products (i.e., context-based recommendation [29]). Unlike these studies, we are not limited to the data from a single website, as purchases extracted from s enable us to gather information from hundreds of different e-commerce websites that can be exploited to learn better product predictions. To the best of our knowledge, this work represents the first study that offers a comprehensive empirical analysis and evaluation of product predictors using data of such scale and nature. 2.2 Neural language models In a number of Natural Language Processing (NLP) applications, including information retrieval, part-of-speech tagging, chunking, and many others, specific objectives can all be generalized to the task of assigning a probability value to a sequence of words. To this end, language models have been developed, defining a mathematical model to capture statistical properties of words and the dependencies among them [3, 20]. Traditionally, language model approaches represent each word as a feature vector using a one-hot representation, where a word vector has the same length as the size of a vocabulary, and the position that corresponds to the observed word is equal to 1, and 0 otherwise. However, this approach often exhibits significant limitations in practical tasks, suffering from high dimensionality of the problem and severe data sparsity, resulting in suboptimal performance. Neural language models have been proposed to address these issues, inducing low-dimensional, distributed embeddings of words by means of neural networks [5, 8, 28]. Such approaches take advantage of the word order in text documents, explicitly modeling the assumption that closer words in the word sequence are statistically more dependent. Historically, inefficient training of the neural network-based models has been an obstacle to their wider applicability, given that the vocabulary size may grow to several millions in practical tasks. However, this issue has been successfully addressed by recent advances in the field, particularly with the development of highly scalable continuous bag-of-words (CBOW) and skip-gram (SG) language models [23, 24] for learning word representations. These powerful, efficient models have shown very promising results in capturing both syntactic and semantic relationships between words in largescale text corpora, obtaining state-of-the-art results on a plethora of NLP tasks. More recently, the concept of distributed representations has been extended beyond word representations to sentences and paragraphs [10, 21], relational entities [6, 27], general text-based attributes [19], descriptive text of images [18], nodes in graph structure [25], and other applications. pi"c$ purchases)of)user)un$)) " " pi"1$ pi+1$ pi+c$ Projec.on) pi$ i1th)product) Figure 2: prod2vec skip-gram model 3. PROPOSED APPROACH In this section we describe the proposed methodology for the task of product recommendations, which leverages information about prior purchases determined from receipts. To address this task we propose to learn representation of products in low-dimensional space from historical logs using neural language models. Product recommendation can then be performed in the learned embedding space through simple nearest neighbor search. More specifically, given a set S of receipt logs obtained from N users, where user s log s = (e 1,..., e M ) S is defined as an uninterupted sequence of M receipts, and each receipt e m = (p m1, p m2,... p mtm ) consists of T m purchased products, our objective is to find D-dimensional real-valued representation v p R D of each product p such that similar products lie nearby in the vector space. We propose several approaches for learning product representations that address specifics of the recommendations from receipts. We first propose prod2vec method that considers all purchased products independently. We then propose novel bagged-prod2vec method that takes into account that some products are listed as purchased together in receipts, which results in better, more useful product representations. Finally, we present product-to-product and user-to-product recommendation models that make use of the learned representations. 3.1 Low-dimensional product embeddings prod2vec. The prod2vec model involves learning vector representations of products from receipt logs by using a notion of a purchase sequence as a sentence and products within the sequence as words, borrowing the terminology from the NLP domain (see Figure 2 for graphical representation of the model). More specifically, prod2vec learns product representations using the skip-gram model [24] by maximizing the objective function over the entire set S of receipt logs, defined as follows L = log P(p i+j p i), (3.1) s S p i s c j c,j 0 where products from the same receipt are ordered arbitrarily. Probability P(p i+j p i) of observing a neighboring product p i+j given the current product p i is defined using the soft-max function, P(p i+j p i) = exp(v p i v p i+j ) P p=1 exp(v p i v p), (3.2)
4 where v p and v p are the input and output vector representations of product p, c is the length of the context for product sequences, and P is the number of unique products in the vocabulary. From equations (3.1) and (3.2) we see that prod2vec models context of product sequence, where products with similar contexts (i.e., with similar neighboring purchases) will have similar vector representations. However, prod2vec does not explicitly take into account that receipt may contain multiple products purchased at the same time, which we address by introducing a bagged version of prod2vec described below. bagged-prod2vec. In order to account for the fact that multiple products may be purchased at the same time, we propose a modified skip-gram model that introduces a notion of a shopping bag. As depicted in Figure 3, the model operates at the level of receipts instead at the level of products. Product vector representations are learned by maximizing a modified objective function over sequences s, defined as follows L = log P(e m+j p mk ). (3.3) s S e m s k=1,...,t m n j n,j 0 Probability P(e m+j p mk ) of observing products from neighboring receipt e m+j, e m+j = (p m+j,1... p m+j,tm ), given the k-th product from m-th receipt reduces to a product of probabilities P(e m+j p mk ) = P(p m+j,1 p mk )... P(p m+j,tm p mk ), each defined using soft-max (3.2). Note that the third sum in (3.3) goes over receipts, so the items from the same receipt do not predict each other during training. In addition, in order to capture temporal aspects of product purchases we propose to use the directed language model, where as context we only use future products [12]. The modification allows us to learn product embeddings capable of predicting future purchases. Learning. The models were optimized using stochastic gradient ascent, suitable for large-scale problems. However, computation of gradients L in (3.1) and (3.3) are proportional to the vocabulary size P, which is computationally expensive in practical tasks as P could easily reach millions of products. As an alternative, we used negative sampling approach proposed in [24], which significantly reduces the computational complexity. 3.2 Product-to-product predictive models Having learned low-dimensional product representations, we considered several possibilities for predicting the next product to be purchased. prod2vec-topk. Given a purchased product, the method calculates cosine similarities to all other products in the vocabulary and recommends the top K most similar products. prod2vec-cluster. To be able to make more diverse recommendations, we considered grouping similar products into clusters and recommending products from a cluster that is related to the cluster of previously purchased product. We applied K-means clustering algorithm implemented on the top of Hadoop distributed system where we grouped products based on cosine similarity between their low-dimensional representations. We assume that purchasing a product from any of the C clusters after a purchase from cluster c i follows a multinomial distribution Mu(θ i1, θ i2,... θ ic), where θ ij is the probability that a purchase from cluster c i is followed by a purchase from cluster c j. In order to estimate parameters θ ij, for each i and j, we adopted a maximum likelihood p 1 m- b s of user un e m- b e m- 1 e m+1 e m+b p 1 m p 1 m- 1 p1 m+1 p1 m+b Projec4on e m p K m m- th p 1 m- b s of user un e m- b e m- 1 e m+1 e m+b p 1 m p 1 m- 1 p1 m+1 p1 m+b Projec4on e m p K m m- th Figure 3: bagged-prod2vec model updates un user pi- c pi Projec'on pi- 1 pi+1 pi+c purchases of user un Figure 4: User embeddings for user to product predictions approach, ˆθ ij = # of times ci purchase was followed by cj. (3.4) count of c i purchases In order to recommend a new product given a purchased product p, we first identify which cluster p belongs to (e.g., p c i). Next, we rank all clusters c j, j = 1,..., C, by the value of θ ij and consider the top ones as top-related clusters to cluster c i. Finally, products from the top clusters are sorted by their cosine similarity to p, and we use the top K products as recommendations. 3.3 User-to-product predictive models In addition to product-to-product predictions [16, 17], most recommendation engines allow user-to-product predictions as well [15, 30]. Recommendation for a user are typically made considering historical purchases and/or interests inferred using other data sources such as user s online behavior [15], social contacts [30], and others. In this section we propose a novel approach to simultaneously learn vector representations of products and users such that, given a user, recommendations can be performed by finding K nearest products in the joint embedding space. user2vec. The user2vec model simultaneously learns vector representations of products and users by considering the user as a global context, motivated by paragraph2vec algorithm [21]. The architecture of such model is illustrated in Figure 4. The training data set was derived from user purchase sequences S, which comprised users u n and their purchased products ordered by the time of purchase, u n = (p n1, p n2,... p nun ), where U n denotes number of items purchased by user u n. During training, user vectors are updated to predict the products from their receipts, while product vectors are learned to predict other products in their context. For simplicity of presentation and w.l.o.g.
5 in the following we present non-bagged version of the language model, however we note that it is straightforward to extend the presented methodology to use the bagged version. More specifically, objective of user2vec is to maximize the log-likelihood over the set S of all purchase sequences, L = ( log P(u n p n1 : p nun ) s S u n s + ) (3.5) log P(p ni p n,i c : p n,i+c, u n) p ni u n where c is the length of the context for products in purchase sequence of the n-th user. The probability P(p ni p n,i c : p n,i+c, u n) is defined using a soft-max function, P(p ni p n,i c : p n,i+c, u n) = exp( v v p ni ) V p=1 exp( v v p), (3.6) where v p ni is the output vector representation of p ni, and v is averaged vector representation of the product context including corresponding u n, defined as v = 1 2c + 1 (vun + v pn,i+j ), (3.7) c j c,j 0 where v p is the input vector representation of p. Similarly, the probability P(u n p n1 : p nun ) is defined as P(u n p n1 : p nun ) = exp( v n v u n ) V p=1 exp( v n v p), (3.8) where v u n is the output vector representation of u n, and v n is averaged input vector representation of all the products purchased by user u n, v n = 1 U n U n v pni. (3.9) One of the main advantages of the user2vec model is that the product recommendations are specifically tailored for that user based on his purchase history. However, disadvantage is that the model would need to be updated very frequently. Unlike product-to-product recommendations, which may be relevant for longer time periods, user-to-product recommendations need to change often to account for the most recent user purchases. 4. EXPERIMENTS The experimental section is organized as follows. We first describe data set used in development of our product-toproduct and user-to-product predictors. Next we present valuable insights regarding purchase behavior of different age and gender groups in different US states. This information can be leveraged to improve demo- and geo-targeting of user groups. This is followed by a section on effectiveness of recommendation of popular products in different user cohorts, including age, gender, and US state. Finally, we show comparative results of various baseline recommendation algorithms. We conclude with the description of the system implementation at a large scale and bucket results that preceded our product launch. 4.1 Data set Our data sets included receipts sent to users who voluntarily opted-in for such studies, where we anonymized i=1 Percentage Male users Female users Age buckets (a) Percentage of purchasing users among all online users Average product price Male users Female users Age buckets (b) Average product price Figure 5: Purchasing habits for different demographics user IDs. Message bodies were analyzed by automated systems. Product names and prices were extracted from messages using an in-house extraction tool. Training data set collected for purposes of developing product prediction models comprised of more than million purchases made by N = 29 million users from 172 commercial websites. The product vocabulary included P = 2.1 million most frequently purchased products priced over $5. More formally, data set D p = {(u n, s n), n = 1,..., N} was derived by forming receipt sequences s n for each user u n, along with their timestamps. Specifically, s n = {(e n1, t n1),..., (e nmn, t nmn )}, where e nm is a receipt comprising one or more purchased products, and t nm is receipt timestamp. Predictions were evaluated on a held-out month of user purchases Dp ts, formed in the same manner as D p. We measured the effectiveness of recommendations using prediction accuracy. In particular, we measured the number of product purchases that were correctly predicted, divided by the total number of purchases. For all models, the accuracy was measured separately on each day, based on the recommendations calculated using prior days. We set a daily budget of distinct recommendations each algorithm is allowed to make for a user to K = 20, based on an estimate of optimal number of ads users can effectively perceive daily [7]. 4.2 Insights from purchase data To get deeper insights into behavior of online users based on their demographic background and geographic location, we segregated users into cohorts based on their age, gender, and location, and looked at their purchasing habits. Such information can be very valuable to marketers when considering how and where to spend their campaign budget. We only considered users from the US, and computed statistics per each state separately. First, we were interested in differences between male and female shopping behavior for different age ranges. In addition, we were interested in the following aspects of purchasing behavior: 1) percentage of online users who shop online; 2) average number of products bought; 4) average spent per user; and 4) average price of a bought item. Figures 5 and 6 illustrate the results. In Figure 5 for each gender and age group we show the percentage of online users who shop online, as well as the average prices of bought items. Expectedly, we see that male and female demographics exhibit different shopping patterns. Throughout the different age buckets percentage of female shoppers is consistently higher than for males, peaking in the age range. On the other hand, percentage of male shoppers reaches its maximum in the 21-24
6 (a) ages (b) ages (c) ages (d) ages (e) ages (f) ages (g) ages (h) ages Figure 6: Purchasing behavior for different cohorts, dark color encodes higher values: (a, b) Percentage of shoppers among online users; (c, d) Average number of purchases per user; (e, f) Average amount spent per user; (g, h) Average product price bucket, and from there drops steadily. In addition, we observe that male users buy more expensive items on average. Furthermore, in Figure 6 we show per-state results, where darker color indicates higher values. Note that we only show results for different locations and age ranges, as we did not see significant differences between male and female purchasing behavior across states. First, in Figures 6(a) and 6(b) we show the percent of online shoppers in each state, for younger (18-20) and medium-age (40-44) populations, where we can see there exist significant differences between the states. In Figures 6(c) and 6(d) we show the average number of purchased products per state. Here, for both age buckets we see that the southern states purchase the least number of items. However, there is a significant difference between younger and older populations, as in northern states younger populations purchase more products, while in the northeast and the western states this holds true for the older populations. If we take a look at Figures 6(e) and 6(f) where we compare the average amount of money spent per capita, we can observe similar patterns, where in states like Alaska and North Dakota younger populations spend more money than peers from other states, and for older populations states with highest spending per user are California, Washington, and again Alaska. Interestingly, users from Alaska are the biggest spenders, irrespective of the age or metric used. Similar holds when we consider average price of a purchased item, shown in Figures 6(g) and 6(h). 4.3 Recommending popular products In this section we evaluate predictive properties of popular products. Recommending popular products to global population is a common baseline due to its strong performance, especially during holidays (e.g., Christmas, Thanksgiving). Such recommendations are intuitive, easy to calculate and implement, and may serve in a cold start scenarios for newly registered users when we have limited information. We considered how far back we need to look when calculating popularity and how long popular products stay relevant. Accuracy (%) Lookback of 5 days Lookback of 10 days Lookback of 20 days Lookback of 30 days Lookahead days Figure 7: Prediction accuracy and longevity of popular products with different lookbacks In Figure 7 we give results for popular products calculated in the previous 5, 10, 20, and 30 days of training data D p, evaluated on the first 1, 3, 7, 15, and 30 days of test data Dp ts. To account for ever-changing user purchase tastes, the results indicate that popular products need to be recalculated at least every 3 days with lookback of at most 5 days. Next, we evaluated the prediction accuracy of popular products computed for different user cohorts, and compared to the accuracy of globally popular products. In Figure 8 we compare accuracies of popular products in different user cohorts, with the lookback fixed at 5 days. We can observe that popular products in gender cohorts give bigger lift in prediction accuracy than popular products in age or state cohorts. Further, jointly considering age and gender when calculating popular products outperforms the popular gender products. Finally, including geographic dimension contributes to further accuracy lift. Overall, the results indicate that in the cold start scenario the best choice of which popular products to recommend are the ones from the user s (age,
7 Accuracy (%) Global Gender Age Age + gender State State + age + gender accuracy Accuracy (%),=1,=0.9,=0.7,= Lookahead days Figure 8: Prediction accuracy of popular products for different user cohorts gender, location) cohort. The results also suggest that popular products should be recalculated often to avoid decrease in accuracy with every passing day. 4.4 Recommending predicted products In this section we experiment with recommending products to users based on neural language models described in Section 3. Specifically, we compare the following algorithms: 1) prod2vec-topk was trained using data set D p, where product vectors were learned by maximizing log-likelihood of observing other products from sequences s, as proposed in (3.1). Recommendations for a given product p i were given by selecting the top K most similar products based on the cosine similarity in the resulting vector space. 2) bagged-prod2vec-topk was trained using D p, where product vectors were learned by maximizing log-likelihood of observing other products from sequences s as proposed in (3.3). Recommendations for a given product p i were given by selecting the top K most similar products based on the cosine similarity in the resulting vector space. 3) bagged-prod2vec-cluster was trained similarly to the bagged-prod2vec model, followed by clustering the product vectors into C clusters and calculating transition probabilities between them. After identifying which cluster p i belongs to (e.g., p i c i), we rank all clusters by their transition probabilities with respect to c i. Then, the products from top clusters are sorted by cosine similarity to p i, where top K c from each cluster are used as recommendations ( K c = K). Example predictions of bagged-prod2vec-cluster compared to predictions of bagged-prod2vec are shown in Table 2. It can be observed that predictions based on the clustering approach are more diverse. 4) user2vec was trained using data set D p where product vectors and user vectors were learned by maximizing log-likelihood proposed in (3.5) (see Figure 4). Recommendations for a given user u n were given by calculating cosine similarity between the user vector u n and all product vectors, and retrieving the top K nearest products. 5) co-purchase. For each product pair (p i, p j) we calculated frequency F (pi,p j ), i = 1,..., P, j = 1,..., P, with which product p j was purchased immediately after product p i. Then, recommendations for a product p i were given by sorting the frequencies F (pi,p j ), j = 1,..., P, and retrieving the top K products lookahead Lookahead days Figure 9: prod2vec accuracy with different decay values Since user u n may have multiple products purchased prior to day t d, separate predictions need to reach a consensus in order to choose the best K products to be shown on that day. To achieve this we propose time-decayed scoring of recommendations, followed by choice of top K products with the highest score. More specifically, given user s products purchased prior to t d along with their timestamps, {(p 1, t 1),... (p Un, t Un )}, for each product we retrieve top K recommendations along with their similarity scores, resulting in the set {(p j, sim j), j = 1,..., KU n}, where sim denotes cosine similarity. Next, we calculate a decayed score for every recommended product, d j = sim j α (t d t i ), (4.1) where (t d t i) is a difference in days between current day t d and the purchase time of product that led to recommendation of p j, and α is a decay factor. Finally, the decayed scores are sorted in descending order and the top K products are chosen as recommendations for day t d. Training details. Neural language models were trained using a machine with 96GB of RAM memory and 24 cores. Dimensionality of the embedding space was set to d = 300, context neighborhood size for all models was set to 5. Finally, we used 10 negative samples in each vector update. Similarly to the approach in [24], most frequent products and users were subsampled during training. To illustrate the performance of the language models, in Table 1 we give examples of product-to-product recommendations computed using bagged-prod2vec, where we see that the neighboring products are highly relevant to the query product (e.g., for despicable me the model retrieved similar cartoons). Evaluation details. Similarly to how popular product accuracy was measured, we assumed a daily budget of K = 20 distinct product recommendations per user. Predictions for day t d are based on prior purchases from previous days, and we did not consider updating predictions for day t d using purchases that happened during that day. Results. In the first set of experiments we evaluated performance of prod2vec for different values of decay factors. In Figure 9 we show prediction accuracy on test data Dp ts when looking 1, 3, 7, 15, and 30 days ahead. Initial prod2vec predictions were based on the last user purchase in the training data set D p. The results show that discounting of old predictions leads to improved recommendation accuracy, with decay factor of α = 0.9 being an optimal choice.
8 Table 1: Examples of product recommendations made by the bagged-prod2vec model despicable me first aid for the usmle step 1 disney frozen lunch napkins monsters university usmle step 1 secrets 3e disneys frozen party 9 square lunchdinner plates the croods first aid basic sciences 2e disneys frozen party 9oz hotcold cups turbo usmle step 1 qbook disneys frozen party 7x7 square cakedessert plates cloudy with a chance of meatballs brs physiology disneys frozen party printed plastic tablecover hotel transylvania rapid review pathology with student consult disneys frozen party 7 square cakedessert plates brave lippincotts microcards microbiology flash cards disney frozen beverage napkins birthday party supplies the smurfs first aid cases for the usmle step 2 disney frozen 9 oz paper cups wreckit ralph highyield neuroanatomy frozen invitation and thank you card planes lange pharmacology flash cards third edition disneys frozen party treat bags Table 2: Product recommendations for product cressi supernova dry snorkel bagged-prod2vec-topk bagged-prod2vec-cluster cluster ID jaws quick spit antifog 1 ounce cressi neoprene mask strap cressi neoprene mask strap cressi frameless mask cluster 1 cressi frameless mask cressi scuba diving snorkeling freediving mask snorkel set akona 2 mm neoprene low cut socks akona 2 mm neoprene low cut socks tilos neoprene fin socks tilos neoprene fin socks cluster 2 cressi scuba diving snorkeling freediving mask snorkel set mares equator 2mm dive boots mares cruise mesh duffle bag jaws quick spit antifog 1 ounce us divers island dry snorkel aqua sphere kayenne goggle with clear lens clear black regular cluster 3 us divers trek travel fin aqua sphere kayenne goggle with clear lens black regular us divers proflex ii diving fins nikon coolpix aw mp wi-fi and waterproof digital camera mares cruise backpack mesh bag olympus stylus tg ihs digital camera with 5x optical zoom cluster 4 water gear fin socks nikon coolpix aw110 wi fi and waterproof digital camera with gps Table 3: Results from live A/B testing of product recommendations on Yahoo Mail Accuracy (%) bag prod2vec clust bag prod2vec prod2vec co-purchase user2vec popular s-a-g Lookahead days Figure 10: Prediction accuracy of different algorithms Next, we evaluate different product-to-product and userto-product methods and compared them to the popular products approach found in Figure 8 to perform the best, namely recommending popular products computed separately for each (state, age, gender) cohort. Results are summarized in Figure 10. We can observe that all neural-based prediction algorithms outperformed method that recommends popular products. Further, even though user2vec model had the best overall accuracy on day 1, its prediction power quickly drops after 3 days. On the other hand, variants of the prod2vec model did not exhibit such behavior, and their performance remained steady across the first 7 days. Of all prod2vec models, the bagged-prod2vec-cluster model achieved the best performance, indicating that diversity in predictions leads to better results. Finally, predictions based on co-purchases did not perform as well as neural language models, supporting the don t count, predict claim from [4] where the authors suggest that simple co-occurence approaches are suboptimal. Control Popular Predicted Metric (5% traffic) (5% traffic) (5% traffic) CTR % % YR % 4.5 Bucket results Following offline evaluation of different product prediction methods, we conducted additional A/B testing experiments on live Yahoo Mail traffic. We ran two buckets with two different recommendation techniques, both on 5% of Yahoo Mail users. In the first bucket, for users with prior purchases the recommendations were based on the bagged-prod2veccluster model, while for users without prior purchases they were based on globally popular products. In the second bucket all users were recommended globally popular products. For purposes of a fair bucket test, both models were retrained and refreshed with the same frequency of 7 days. Both test buckets were evaluated against a control bucket in which products ads were replaced with standard ads from Yahoo Ad serving platform. All three buckets had significant amount of users with prior purchases. Evaluation was done based on the click-through rate (CTR) computed as #clicks #impressions CTR =. In particular, we measured the number of clicks on product ads that occurred after the targeted recommendation, divided by the total number of shown (or impressed) product ads. In the control bucket, we computed the same metric for standard ads. For the two product ad buckets we additionally measured the yield rate, calculated as YR = #conversions, where conversion refers to an actual #impressions purchase of the recommended product. Conversions were attributed to impression for up to 48 hours since the time users clicked or observed a product ad.
9 CTR Model Update Model Update Popular Predicted DAY Model Update Model Update Figure 11: CTR of predicted versus popular recommendations in live bucket test over time The results are presented in Table 3. We can make several observations. First, both popular and predicted bucket showed better CTR numbers than the control bucket, indicating that the users prefer product ads over standard ads. Second, the prediction bucket achieved slightly better CTR rates than the popular bucket. Finally, the prediction bucket achieved significantly better YR than the popular bucket. This indicates that many times users click on popular products out of curiosity and do not end up buying the product, whereas clicks on targeted products lead to more purchases as they better capture user interests. Overall, the presented results strongly suggest benefits of the proposed approach for the task of product recommendations. In addition, in Figure 11 we show how CTR rates change over time. Similarly to our offline experiments, it can be observed that popular recommendations become stale much faster than predicted recommendations, as indicated by the steeper CTR drop. They are also more susceptible to novelty bias following model updates, as seen by larger increase in CTR. Another useful finding was that 7 day updates are not sufficient, confirming findings from Figure SYSTEM DEPLOYMENT In this section we cover the details on our system implementation that led to final product deployment. 5.1 Implementation details Due to product requirements for near-real-time predictions, we chose to use product-to-product recommendations, with the bagged-prod2vec-cluster model. The model is updated every 5 days with the most recent purchase data. The product vectors are stored on Hadoop Distributed File System (HDFS), and updated via training procedure implemented on Hadoop 5, where we heavily leverage parallel processing with MapReduce. We form purchase sequences using the newest purchased products extracted from receipts, and incrementally update the product vectors instead of training them from scratch. Popular products were used as back-fill for users who do not have prior purchase history. Following the experimental results, we recalculated popular products every 3 days, with a lookback of 5 days. More specifically, we extracted 5 accessed June most frequently purchased products for every state-agegender cohort, and showed them in randomized order to users without purchase history. We implemented a multi-tier architecture in order to productionize product recommendation capability on Yahoo Mail. For data storage we used a custom, high-performance distributed key-value store (similar to Cassandra 6 ), which persists user profiles and product-to-product prediction model. The user profile store utilizes user identifier as a key and stores multiple columns representing user prior purchases as values. User profiles are updated hourly with new products, extracted from receipts. Each purchase record persists in memory with time-to-live (TTL) set to 60 days, after which period it is discarded. Product-to-product prediction model is stored in a similar key-value store, where purchased product is used as a key and values are multiple columns each representing predicted products ordered by score. Both user and product-toproduct stores are updated in batch without impacting real traffic. Separate process performs all processing of querying user purchases and asynchronously retrieves relevant predictions and offers. It then returns selected product ad back to presentation process implemented in JavaScript and HTML which renders it in the browser. The retrieval process is configured such that it can fetch offers from multiple e-commerce websites (affiliate partners). The system runs with a service-level agreement of 500ms and can be improved further by caching interactions with affiliate partners. Given predictions for a certain user, once the user logs into the client we show a new recommendation after every user action, including clicking on folders, composing , and searching the inbox. Recommendation are circled in the order of decayed prediction score, as described in Section 4.4. The product ads are implemented in the so-called pencil ad position, just above the first in the inbox (Figure 1). 6. CONCLUSIONS AND FUTURE WORK We presented the details of a large-scale product recommendation framework that was launched on Yahoo Mail in the form of product ads. We discussed the recommendation methodology, as well as the high-level implementation details behind our system. To perform recommendations, we described how we employed neural language models capable of learning product embeddings for product-to-product predictions, as well as user embeddings for user-to-products predictions. Several variants of the prediction models were tested offline and the best candidate was chosen for an online bucket test. Following the encouraging bucket test results, we launched the system in production. In our ongoing work, we plan to utilize implicit feedback available through ad views, ad clicks, and conversions to further improve the performance of our product recommendation system. 7. REFERENCES [1] A. Ahmed, Y. Low, M. Aly, V. Josifovski, and A. J. Smola. Scalable distributed inference of dynamic user interests for behavioral targeting. In KDD, pages , [2] J. Alba, J. Lynch, B. Weitz, C. Janiszewski, R. Lutz, A. Sawyer, and S. Wood. Interactive home shopping: 6 accessed June 2015
10 consumer, retailer, and manufacturer incentives to participate in electronic marketplaces. The Journal of Marketing, pages 38 53, [3] R. Baeza-Yates, B. Ribeiro-Neto, et al. Modern information retrieval, volume 463. ACM press New York, [4] M. Baroni, G. Dinu, and G. Kruszewski. DonÕt count, predict! a systematic comparison of context-counting vs. context-predicting semantic vectors. In Proceedings of the 52nd Annual Meeting of the Association for Computational Linguistics, volume 1, pages , [5] Y. Bengio, H. Schwenk, J.-S. Senécal, F. Morin, and J.-L. Gauvain. Neural probabilistic language models. In Innovations in Machine Learning, pages Springer, [6] A. Bordes, N. Usunier, A. Garcia-Duran, J. Weston, and O. Yakhnenko. Translating embeddings for modeling multi-relational data. In Advances in Neural Information Processing Systems, pages , [7] C.-H. Cho and H. J. Cheon. Why do people avoid advertising on the internet? Journal of advertising, 33(4):89 97, [8] R. Collobert, J. Weston, L. Bottou, M. Karlen, K. Kavukcuoglu, and P. Kuksa. Natural language processing (almost) from scratch. The Journal of Machine Learning Research, 12: , [9] N. Djuric, V. Radosavljevic, M. Grbovic, and N. Bhamidipati. Hidden conditional random fields with distributed user embeddings for ad targeting. In IEEE International Conference on Data Mining, Dec [10] N. Djuric, H. Wu, V. Radosavljevic, M. Grbovic, and N. Bhamidipati. Hierarchical neural language models for joint representation of streaming documents and their content. In International World Wide Web Conference (WWW), [11] D. Essex. Matchmaker, matchmaker. Communications of the ACM, 52(5):16 17, [12] M. Grbovic, N. Djuric, V. Radosavljevic, and N. Bhamidipati. Search retargeting using directed query embeddings. In International World Wide Web Conference (WWW), [13] M. Grbovic, G. Halawi, Z. Karnin, and Y. Maarek. How many folders do you really need?: Classifying into a handful of categories. In Proceedings of the 23rd ACM International Conference on Conference on Information and Knowledge Management, pages ACM, [14] M. Grbovic and S. Vucetic. Generating ad targeting rules using sparse principal component analysis with constraints. In international conference on World Wide Web, pages , [15] D. J. Hu, R. Hall, and J. Attenberg. Style in the long tail: discovering unique interests with latent variable models in large scale social e-commerce. In Proceedings of the 20th ACM SIGKDD international conference on Knowledge discovery and data mining, pages ACM, [16] J. Katukuri, T. Konik, R. Mukherjee, and S. Kolay. Recommending similar items in large-scale online marketplaces. In Big Data (Big Data), 2014 IEEE International Conference on, pages IEEE, [17] J. Katukuri, R. Mukherjee, and T. Konik. Large-scale recommendations in a dynamic marketplace. In Workshop on Large Scale Recommendation Systems at RecSys, volume 13, [18] R. Kiros, R. Zemel, and R. Salakhutdinov. Multimodal neural language models. In Proceedings of the 31th International Conference on Machine Learning, [19] R. Kiros, R. S. Zemel, and R. Salakhutdinov. A multiplicative model for learning distributed text-based attribute representations. arxiv preprint arxiv: , [20] V. Lavrenko and W. B. Croft. Relevance based language models. In SIGIR, pages ACM, [21] Q. V. Le and T. Mikolov. Distributed representations of sentences and documents. arxiv preprint arxiv: , [22] G. Linden, B. Smith, and J. York. Amazon.com recommendations: Item-to-item collaborative filtering. IEEE Internet Computing, 7(1):76 80, Jan [23] T. Mikolov, K. Chen, G. Corrado, and J. Dean. Efficient estimation of word representations in vector space. arxiv preprint arxiv: , [24] T. Mikolov, I. Sutskever, K. Chen, G. S. Corrado, and J. Dean. Distributed representations of words and phrases and their compositionality. In NIPS, pages , [25] B. Perozzi, R. Al-Rfou, and S. Skiena. Deepwalk: Online learning of social representations. arxiv preprint arxiv: , [26] D. Riecken. Personalized views of personalization. Communications of the ACM, 43(8):27 28, [27] R. Socher, D. Chen, C. D. Manning, and A. Ng. Reasoning with neural tensor networks for knowledge base completion. In Advances in Neural Information Processing Systems, pages , [28] J. Turian, L. Ratinov, and Y. Bengio. Word representations: a simple and general method for semi-supervised learning. In Proceedings of the 48th Annual Meeting of the Association for Computational Linguistics, pages Association for Computational Linguistics, [29] Y. Zhang and M. Pennacchiotti. Predicting purchase behaviors from social media. In WWW, pages , [30] X. W. Zhao, Y. Guo, Y. He, H. Jiang, Y. Wu, and X. Li. We know what you want to buy: a demographic-based system for product recommendation on microblogs. In Proceedings of the 20th ACM SIGKDD international conference on Knowledge discovery and data mining, pages ACM, 2014.
Invited Applications Paper
 Invited Applications Paper - - Thore Graepel Joaquin Quiñonero Candela Thomas Borchert Ralf Herbrich Microsoft Research Ltd., 7 J J Thomson Avenue, Cambridge CB3 0FB, UK [email protected] [email protected]
Invited Applications Paper - - Thore Graepel Joaquin Quiñonero Candela Thomas Borchert Ralf Herbrich Microsoft Research Ltd., 7 J J Thomson Avenue, Cambridge CB3 0FB, UK [email protected] [email protected]
Online Content Optimization Using Hadoop. Jyoti Ahuja Dec 20 2011
 Online Content Optimization Using Hadoop Jyoti Ahuja Dec 20 2011 What do we do? Deliver right CONTENT to the right USER at the right TIME o Effectively and pro-actively learn from user interactions with
Online Content Optimization Using Hadoop Jyoti Ahuja Dec 20 2011 What do we do? Deliver right CONTENT to the right USER at the right TIME o Effectively and pro-actively learn from user interactions with
Tensor Factorization for Multi-Relational Learning
 Tensor Factorization for Multi-Relational Learning Maximilian Nickel 1 and Volker Tresp 2 1 Ludwig Maximilian University, Oettingenstr. 67, Munich, Germany [email protected] 2 Siemens AG, Corporate
Tensor Factorization for Multi-Relational Learning Maximilian Nickel 1 and Volker Tresp 2 1 Ludwig Maximilian University, Oettingenstr. 67, Munich, Germany [email protected] 2 Siemens AG, Corporate
The Need for Training in Big Data: Experiences and Case Studies
 The Need for Training in Big Data: Experiences and Case Studies Guy Lebanon Amazon Background and Disclaimer All opinions are mine; other perspectives are legitimate. Based on my experience as a professor
The Need for Training in Big Data: Experiences and Case Studies Guy Lebanon Amazon Background and Disclaimer All opinions are mine; other perspectives are legitimate. Based on my experience as a professor
Linear programming approach for online advertising
 Linear programming approach for online advertising Igor Trajkovski Faculty of Computer Science and Engineering, Ss. Cyril and Methodius University in Skopje, Rugjer Boshkovikj 16, P.O. Box 393, 1000 Skopje,
Linear programming approach for online advertising Igor Trajkovski Faculty of Computer Science and Engineering, Ss. Cyril and Methodius University in Skopje, Rugjer Boshkovikj 16, P.O. Box 393, 1000 Skopje,
A survey on click modeling in web search
 A survey on click modeling in web search Lianghao Li Hong Kong University of Science and Technology Outline 1 An overview of web search marketing 2 An overview of click modeling 3 A survey on click models
A survey on click modeling in web search Lianghao Li Hong Kong University of Science and Technology Outline 1 An overview of web search marketing 2 An overview of click modeling 3 A survey on click models
A Near Real-Time Personalization for ecommerce Platform Amit Rustagi [email protected]
 A Near Real-Time Personalization for ecommerce Platform Amit Rustagi [email protected] Abstract. In today's competitive environment, you only have a few seconds to help site visitors understand that you
A Near Real-Time Personalization for ecommerce Platform Amit Rustagi [email protected] Abstract. In today's competitive environment, you only have a few seconds to help site visitors understand that you
The multilayer sentiment analysis model based on Random forest Wei Liu1, Jie Zhang2
 2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2016) The multilayer sentiment analysis model based on Random forest Wei Liu1, Jie Zhang2 1 School of
2nd International Conference on Advances in Mechanical Engineering and Industrial Informatics (AMEII 2016) The multilayer sentiment analysis model based on Random forest Wei Liu1, Jie Zhang2 1 School of
Driving Results with. Dynamic Creative
 Driving Results with Dynamic Creative Introduction In the world of digital advertising, reaching people is no longer the number one problem brands face when they plan a campaign. Ad networks and servers,
Driving Results with Dynamic Creative Introduction In the world of digital advertising, reaching people is no longer the number one problem brands face when they plan a campaign. Ad networks and servers,
How To Cluster On A Search Engine
 Volume 2, Issue 2, February 2012 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: A REVIEW ON QUERY CLUSTERING
Volume 2, Issue 2, February 2012 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: A REVIEW ON QUERY CLUSTERING
Web Analytics Definitions Approved August 16, 2007
 Web Analytics Definitions Approved August 16, 2007 Web Analytics Association 2300 M Street, Suite 800 Washington DC 20037 [email protected] 1-800-349-1070 Licensed under a Creative
Web Analytics Definitions Approved August 16, 2007 Web Analytics Association 2300 M Street, Suite 800 Washington DC 20037 [email protected] 1-800-349-1070 Licensed under a Creative
Search Result Optimization using Annotators
 Search Result Optimization using Annotators Vishal A. Kamble 1, Amit B. Chougule 2 1 Department of Computer Science and Engineering, D Y Patil College of engineering, Kolhapur, Maharashtra, India 2 Professor,
Search Result Optimization using Annotators Vishal A. Kamble 1, Amit B. Chougule 2 1 Department of Computer Science and Engineering, D Y Patil College of engineering, Kolhapur, Maharashtra, India 2 Professor,
Driving Results with. Dynamic Creative Optimization
 Driving Results with Dynamic Creative Optimization Introduction In the world of digital advertising, reaching people is no longer the number one problem brands face when they plan a campaign. Ad networks
Driving Results with Dynamic Creative Optimization Introduction In the world of digital advertising, reaching people is no longer the number one problem brands face when they plan a campaign. Ad networks
Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2
 Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2 Department of Computer Engineering, YMCA University of Science & Technology, Faridabad,
Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2 Department of Computer Engineering, YMCA University of Science & Technology, Faridabad,
Figure 1. The cloud scales: Amazon EC2 growth [2].
![Figure 1. The cloud scales: Amazon EC2 growth [2]. Figure 1. The cloud scales: Amazon EC2 growth [2].](/thumbs/26/9133435.jpg) - Chung-Cheng Li and Kuochen Wang Department of Computer Science National Chiao Tung University Hsinchu, Taiwan 300 [email protected], [email protected] Abstract One of the most important issues
- Chung-Cheng Li and Kuochen Wang Department of Computer Science National Chiao Tung University Hsinchu, Taiwan 300 [email protected], [email protected] Abstract One of the most important issues
Adaptive Tolerance Algorithm for Distributed Top-K Monitoring with Bandwidth Constraints
 Adaptive Tolerance Algorithm for Distributed Top-K Monitoring with Bandwidth Constraints Michael Bauer, Srinivasan Ravichandran University of Wisconsin-Madison Department of Computer Sciences {bauer, srini}@cs.wisc.edu
Adaptive Tolerance Algorithm for Distributed Top-K Monitoring with Bandwidth Constraints Michael Bauer, Srinivasan Ravichandran University of Wisconsin-Madison Department of Computer Sciences {bauer, srini}@cs.wisc.edu
Nine Common Types of Data Mining Techniques Used in Predictive Analytics
 1 Nine Common Types of Data Mining Techniques Used in Predictive Analytics By Laura Patterson, President, VisionEdge Marketing Predictive analytics enable you to develop mathematical models to help better
1 Nine Common Types of Data Mining Techniques Used in Predictive Analytics By Laura Patterson, President, VisionEdge Marketing Predictive analytics enable you to develop mathematical models to help better
So today we shall continue our discussion on the search engines and web crawlers. (Refer Slide Time: 01:02)
 Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #39 Search Engines and Web Crawler :: Part 2 So today we
Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #39 Search Engines and Web Crawler :: Part 2 So today we
Similarity Search in a Very Large Scale Using Hadoop and HBase
 Similarity Search in a Very Large Scale Using Hadoop and HBase Stanislav Barton, Vlastislav Dohnal, Philippe Rigaux LAMSADE - Universite Paris Dauphine, France Internet Memory Foundation, Paris, France
Similarity Search in a Very Large Scale Using Hadoop and HBase Stanislav Barton, Vlastislav Dohnal, Philippe Rigaux LAMSADE - Universite Paris Dauphine, France Internet Memory Foundation, Paris, France
Mining Signatures in Healthcare Data Based on Event Sequences and its Applications
 Mining Signatures in Healthcare Data Based on Event Sequences and its Applications Siddhanth Gokarapu 1, J. Laxmi Narayana 2 1 Student, Computer Science & Engineering-Department, JNTU Hyderabad India 1
Mining Signatures in Healthcare Data Based on Event Sequences and its Applications Siddhanth Gokarapu 1, J. Laxmi Narayana 2 1 Student, Computer Science & Engineering-Department, JNTU Hyderabad India 1
Importance of Online Product Reviews from a Consumer s Perspective
 Advances in Economics and Business 1(1): 1-5, 2013 DOI: 10.13189/aeb.2013.010101 http://www.hrpub.org Importance of Online Product Reviews from a Consumer s Perspective Georg Lackermair 1,2, Daniel Kailer
Advances in Economics and Business 1(1): 1-5, 2013 DOI: 10.13189/aeb.2013.010101 http://www.hrpub.org Importance of Online Product Reviews from a Consumer s Perspective Georg Lackermair 1,2, Daniel Kailer
Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus
 Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus 1. Introduction Facebook is a social networking website with an open platform that enables developers to extract and utilize user information
Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus 1. Introduction Facebook is a social networking website with an open platform that enables developers to extract and utilize user information
Text Analytics. A business guide
 Text Analytics A business guide February 2014 Contents 3 The Business Value of Text Analytics 4 What is Text Analytics? 6 Text Analytics Methods 8 Unstructured Meets Structured Data 9 Business Application
Text Analytics A business guide February 2014 Contents 3 The Business Value of Text Analytics 4 What is Text Analytics? 6 Text Analytics Methods 8 Unstructured Meets Structured Data 9 Business Application
Web Advertising Personalization using Web Content Mining and Web Usage Mining Combination
 8 Web Advertising Personalization using Web Content Mining and Web Usage Mining Combination Ketul B. Patel 1, Dr. A.R. Patel 2, Natvar S. Patel 3 1 Research Scholar, Hemchandracharya North Gujarat University,
8 Web Advertising Personalization using Web Content Mining and Web Usage Mining Combination Ketul B. Patel 1, Dr. A.R. Patel 2, Natvar S. Patel 3 1 Research Scholar, Hemchandracharya North Gujarat University,
Data Mining Applications in Higher Education
 Executive report Data Mining Applications in Higher Education Jing Luan, PhD Chief Planning and Research Officer, Cabrillo College Founder, Knowledge Discovery Laboratories Table of contents Introduction..............................................................2
Executive report Data Mining Applications in Higher Education Jing Luan, PhD Chief Planning and Research Officer, Cabrillo College Founder, Knowledge Discovery Laboratories Table of contents Introduction..............................................................2
Product recommendations and promotions (couponing and discounts) Cross-sell and Upsell strategies
 WHITEPAPER Today, leading companies are looking to improve business performance via faster, better decision making by applying advanced predictive modeling to their vast and growing volumes of data. Business
WHITEPAPER Today, leading companies are looking to improve business performance via faster, better decision making by applying advanced predictive modeling to their vast and growing volumes of data. Business
Parallel Data Mining. Team 2 Flash Coders Team Research Investigation Presentation 2. Foundations of Parallel Computing Oct 2014
 Parallel Data Mining Team 2 Flash Coders Team Research Investigation Presentation 2 Foundations of Parallel Computing Oct 2014 Agenda Overview of topic Analysis of research papers Software design Overview
Parallel Data Mining Team 2 Flash Coders Team Research Investigation Presentation 2 Foundations of Parallel Computing Oct 2014 Agenda Overview of topic Analysis of research papers Software design Overview
Introduction. A. Bellaachia Page: 1
 Introduction 1. Objectives... 3 2. What is Data Mining?... 4 3. Knowledge Discovery Process... 5 4. KD Process Example... 7 5. Typical Data Mining Architecture... 8 6. Database vs. Data Mining... 9 7.
Introduction 1. Objectives... 3 2. What is Data Mining?... 4 3. Knowledge Discovery Process... 5 4. KD Process Example... 7 5. Typical Data Mining Architecture... 8 6. Database vs. Data Mining... 9 7.
Web Browsing Quality of Experience Score
 Web Browsing Quality of Experience Score A Sandvine Technology Showcase Contents Executive Summary... 1 Introduction to Web QoE... 2 Sandvine s Web Browsing QoE Metric... 3 Maintaining a Web Page Library...
Web Browsing Quality of Experience Score A Sandvine Technology Showcase Contents Executive Summary... 1 Introduction to Web QoE... 2 Sandvine s Web Browsing QoE Metric... 3 Maintaining a Web Page Library...
A/B SPLIT TESTING GUIDE How to Best Test for Conversion Success
 A/B SPLIT TESTING GUIDE How to Best Test for Conversion Success CONVERSION OPTIMIZATION WHITE PAPER BY STEELHOUSE Q2 2012 TABLE OF CONTENTS Executive Summary...3 Importance of Conversion...4 What is A/B
A/B SPLIT TESTING GUIDE How to Best Test for Conversion Success CONVERSION OPTIMIZATION WHITE PAPER BY STEELHOUSE Q2 2012 TABLE OF CONTENTS Executive Summary...3 Importance of Conversion...4 What is A/B
Recommendations in Mobile Environments. Professor Hui Xiong Rutgers Business School Rutgers University. Rutgers, the State University of New Jersey
 1 Recommendations in Mobile Environments Professor Hui Xiong Rutgers Business School Rutgers University ADMA-2014 Rutgers, the State University of New Jersey Big Data 3 Big Data Application Requirements
1 Recommendations in Mobile Environments Professor Hui Xiong Rutgers Business School Rutgers University ADMA-2014 Rutgers, the State University of New Jersey Big Data 3 Big Data Application Requirements
Big Data Big Deal? Salford Systems www.salford-systems.com
 Big Data Big Deal? Salford Systems www.salford-systems.com 2015 Copyright Salford Systems 2010-2015 Big Data Is The New In Thing Google trends as of September 24, 2015 Difficult to read trade press without
Big Data Big Deal? Salford Systems www.salford-systems.com 2015 Copyright Salford Systems 2010-2015 Big Data Is The New In Thing Google trends as of September 24, 2015 Difficult to read trade press without
Understanding Web personalization with Web Usage Mining and its Application: Recommender System
 Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
Oracle Real Time Decisions
 A Product Review James Taylor CEO CONTENTS Introducing Decision Management Systems Oracle Real Time Decisions Product Architecture Key Features Availability Conclusion Oracle Real Time Decisions (RTD)
A Product Review James Taylor CEO CONTENTS Introducing Decision Management Systems Oracle Real Time Decisions Product Architecture Key Features Availability Conclusion Oracle Real Time Decisions (RTD)
Machine Learning using MapReduce
 Machine Learning using MapReduce What is Machine Learning Machine learning is a subfield of artificial intelligence concerned with techniques that allow computers to improve their outputs based on previous
Machine Learning using MapReduce What is Machine Learning Machine learning is a subfield of artificial intelligence concerned with techniques that allow computers to improve their outputs based on previous
Comparison of K-means and Backpropagation Data Mining Algorithms
 Comparison of K-means and Backpropagation Data Mining Algorithms Nitu Mathuriya, Dr. Ashish Bansal Abstract Data mining has got more and more mature as a field of basic research in computer science and
Comparison of K-means and Backpropagation Data Mining Algorithms Nitu Mathuriya, Dr. Ashish Bansal Abstract Data mining has got more and more mature as a field of basic research in computer science and
RANDOM PROJECTIONS FOR SEARCH AND MACHINE LEARNING
 = + RANDOM PROJECTIONS FOR SEARCH AND MACHINE LEARNING Stefan Savev Berlin Buzzwords June 2015 KEYWORD-BASED SEARCH Document Data 300 unique words per document 300 000 words in vocabulary Data sparsity:
= + RANDOM PROJECTIONS FOR SEARCH AND MACHINE LEARNING Stefan Savev Berlin Buzzwords June 2015 KEYWORD-BASED SEARCH Document Data 300 unique words per document 300 000 words in vocabulary Data sparsity:
BUY. Mobile Retargeting for Retailers: Recapturing Customers Cross-Platform. February 2014. 1.877.AMPUSH.1 [email protected]
 BUY Mobile Retargeting for Retailers: Recapturing Customers Cross-Platform February 2014 1.877.AMPUSH.1 [email protected] TABLE OF CONTENTS Executive Summary 3 The Mobile Advertising Opportunity 4 E-Commerce
BUY Mobile Retargeting for Retailers: Recapturing Customers Cross-Platform February 2014 1.877.AMPUSH.1 [email protected] TABLE OF CONTENTS Executive Summary 3 The Mobile Advertising Opportunity 4 E-Commerce
Successful Steps and Simple Ideas to Maximise your Direct Marketing Return On Investment
 Successful Steps and Simple Ideas to Maximise your Direct Marketing Return On Investment By German Sacristan, X1 Head of Marketing and Customer Experience, UK and author of The Digital & Direct Marketing
Successful Steps and Simple Ideas to Maximise your Direct Marketing Return On Investment By German Sacristan, X1 Head of Marketing and Customer Experience, UK and author of The Digital & Direct Marketing
Text Mining Approach for Big Data Analysis Using Clustering and Classification Methodologies
 Text Mining Approach for Big Data Analysis Using Clustering and Classification Methodologies Somesh S Chavadi 1, Dr. Asha T 2 1 PG Student, 2 Professor, Department of Computer Science and Engineering,
Text Mining Approach for Big Data Analysis Using Clustering and Classification Methodologies Somesh S Chavadi 1, Dr. Asha T 2 1 PG Student, 2 Professor, Department of Computer Science and Engineering,
Microblog Sentiment Analysis with Emoticon Space Model
 Microblog Sentiment Analysis with Emoticon Space Model Fei Jiang, Yiqun Liu, Huanbo Luan, Min Zhang, and Shaoping Ma State Key Laboratory of Intelligent Technology and Systems, Tsinghua National Laboratory
Microblog Sentiment Analysis with Emoticon Space Model Fei Jiang, Yiqun Liu, Huanbo Luan, Min Zhang, and Shaoping Ma State Key Laboratory of Intelligent Technology and Systems, Tsinghua National Laboratory
Data Mining Yelp Data - Predicting rating stars from review text
 Data Mining Yelp Data - Predicting rating stars from review text Rakesh Chada Stony Brook University [email protected] Chetan Naik Stony Brook University [email protected] ABSTRACT The majority
Data Mining Yelp Data - Predicting rating stars from review text Rakesh Chada Stony Brook University [email protected] Chetan Naik Stony Brook University [email protected] ABSTRACT The majority
Automated Collaborative Filtering Applications for Online Recruitment Services
 Automated Collaborative Filtering Applications for Online Recruitment Services Rachael Rafter, Keith Bradley, Barry Smyth Smart Media Institute, Department of Computer Science, University College Dublin,
Automated Collaborative Filtering Applications for Online Recruitment Services Rachael Rafter, Keith Bradley, Barry Smyth Smart Media Institute, Department of Computer Science, University College Dublin,
Mobile Real-Time Bidding and Predictive
 Mobile Real-Time Bidding and Predictive Targeting AdTheorent s Real-Time Learning Machine : An Intelligent Solution FOR Mobile Advertising Marketing and media companies must move beyond basic data analysis
Mobile Real-Time Bidding and Predictive Targeting AdTheorent s Real-Time Learning Machine : An Intelligent Solution FOR Mobile Advertising Marketing and media companies must move beyond basic data analysis
Predict the Popularity of YouTube Videos Using Early View Data
 000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
A QoS-Aware Web Service Selection Based on Clustering
 International Journal of Scientific and Research Publications, Volume 4, Issue 2, February 2014 1 A QoS-Aware Web Service Selection Based on Clustering R.Karthiban PG scholar, Computer Science and Engineering,
International Journal of Scientific and Research Publications, Volume 4, Issue 2, February 2014 1 A QoS-Aware Web Service Selection Based on Clustering R.Karthiban PG scholar, Computer Science and Engineering,
Achieve Better Ranking Accuracy Using CloudRank Framework for Cloud Services
 Achieve Better Ranking Accuracy Using CloudRank Framework for Cloud Services Ms. M. Subha #1, Mr. K. Saravanan *2 # Student, * Assistant Professor Department of Computer Science and Engineering Regional
Achieve Better Ranking Accuracy Using CloudRank Framework for Cloud Services Ms. M. Subha #1, Mr. K. Saravanan *2 # Student, * Assistant Professor Department of Computer Science and Engineering Regional
Profile Based Personalized Web Search and Download Blocker
 Profile Based Personalized Web Search and Download Blocker 1 K.Sheeba, 2 G.Kalaiarasi Dhanalakshmi Srinivasan College of Engineering and Technology, Mamallapuram, Chennai, Tamil nadu, India Email: 1 [email protected],
Profile Based Personalized Web Search and Download Blocker 1 K.Sheeba, 2 G.Kalaiarasi Dhanalakshmi Srinivasan College of Engineering and Technology, Mamallapuram, Chennai, Tamil nadu, India Email: 1 [email protected],
Big Data Analytics of Multi-Relationship Online Social Network Based on Multi-Subnet Composited Complex Network
 , pp.273-284 http://dx.doi.org/10.14257/ijdta.2015.8.5.24 Big Data Analytics of Multi-Relationship Online Social Network Based on Multi-Subnet Composited Complex Network Gengxin Sun 1, Sheng Bin 2 and
, pp.273-284 http://dx.doi.org/10.14257/ijdta.2015.8.5.24 Big Data Analytics of Multi-Relationship Online Social Network Based on Multi-Subnet Composited Complex Network Gengxin Sun 1, Sheng Bin 2 and
IJCSES Vol.7 No.4 October 2013 pp.165-168 Serials Publications BEHAVIOR PERDITION VIA MINING SOCIAL DIMENSIONS
 IJCSES Vol.7 No.4 October 2013 pp.165-168 Serials Publications BEHAVIOR PERDITION VIA MINING SOCIAL DIMENSIONS V.Sudhakar 1 and G. Draksha 2 Abstract:- Collective behavior refers to the behaviors of individuals
IJCSES Vol.7 No.4 October 2013 pp.165-168 Serials Publications BEHAVIOR PERDITION VIA MINING SOCIAL DIMENSIONS V.Sudhakar 1 and G. Draksha 2 Abstract:- Collective behavior refers to the behaviors of individuals
Computational Advertising Andrei Broder Yahoo! Research. SCECR, May 30, 2009
 Computational Advertising Andrei Broder Yahoo! Research SCECR, May 30, 2009 Disclaimers This talk presents the opinions of the author. It does not necessarily reflect the views of Yahoo! Inc or any other
Computational Advertising Andrei Broder Yahoo! Research SCECR, May 30, 2009 Disclaimers This talk presents the opinions of the author. It does not necessarily reflect the views of Yahoo! Inc or any other
Distributed forests for MapReduce-based machine learning
 Distributed forests for MapReduce-based machine learning Ryoji Wakayama, Ryuei Murata, Akisato Kimura, Takayoshi Yamashita, Yuji Yamauchi, Hironobu Fujiyoshi Chubu University, Japan. NTT Communication
Distributed forests for MapReduce-based machine learning Ryoji Wakayama, Ryuei Murata, Akisato Kimura, Takayoshi Yamashita, Yuji Yamauchi, Hironobu Fujiyoshi Chubu University, Japan. NTT Communication
Analyzing Big Data with AWS
 Analyzing Big Data with AWS Peter Sirota, General Manager, Amazon Elastic MapReduce @petersirota What is Big Data? Computer generated data Application server logs (web sites, games) Sensor data (weather,
Analyzing Big Data with AWS Peter Sirota, General Manager, Amazon Elastic MapReduce @petersirota What is Big Data? Computer generated data Application server logs (web sites, games) Sensor data (weather,
Business Intelligence Solutions for Gaming and Hospitality
 Business Intelligence Solutions for Gaming and Hospitality Prepared by: Mario Perkins Qualex Consulting Services, Inc. Suzanne Fiero SAS Objective Summary 2 Objective Summary The rise in popularity and
Business Intelligence Solutions for Gaming and Hospitality Prepared by: Mario Perkins Qualex Consulting Services, Inc. Suzanne Fiero SAS Objective Summary 2 Objective Summary The rise in popularity and
Dynamical Clustering of Personalized Web Search Results
 Dynamical Clustering of Personalized Web Search Results Xuehua Shen CS Dept, UIUC [email protected] Hong Cheng CS Dept, UIUC [email protected] Abstract Most current search engines present the user a ranked
Dynamical Clustering of Personalized Web Search Results Xuehua Shen CS Dept, UIUC [email protected] Hong Cheng CS Dept, UIUC [email protected] Abstract Most current search engines present the user a ranked
SPATIAL DATA CLASSIFICATION AND DATA MINING
 , pp.-40-44. Available online at http://www. bioinfo. in/contents. php?id=42 SPATIAL DATA CLASSIFICATION AND DATA MINING RATHI J.B. * AND PATIL A.D. Department of Computer Science & Engineering, Jawaharlal
, pp.-40-44. Available online at http://www. bioinfo. in/contents. php?id=42 SPATIAL DATA CLASSIFICATION AND DATA MINING RATHI J.B. * AND PATIL A.D. Department of Computer Science & Engineering, Jawaharlal
Overcoming basket abandonment through effective implementation of real-time communications services.
 Overcoming basket abandonment through effective implementation of real-time communications services. The benefits of real-time customer engagement For the vast majority of online retailers, converting
Overcoming basket abandonment through effective implementation of real-time communications services. The benefits of real-time customer engagement For the vast majority of online retailers, converting
Using In-Memory Computing to Simplify Big Data Analytics
 SCALEOUT SOFTWARE Using In-Memory Computing to Simplify Big Data Analytics by Dr. William Bain, ScaleOut Software, Inc. 2012 ScaleOut Software, Inc. 12/27/2012 T he big data revolution is upon us, fed
SCALEOUT SOFTWARE Using In-Memory Computing to Simplify Big Data Analytics by Dr. William Bain, ScaleOut Software, Inc. 2012 ScaleOut Software, Inc. 12/27/2012 T he big data revolution is upon us, fed
Distributed Framework for Data Mining As a Service on Private Cloud
 RESEARCH ARTICLE OPEN ACCESS Distributed Framework for Data Mining As a Service on Private Cloud Shraddha Masih *, Sanjay Tanwani** *Research Scholar & Associate Professor, School of Computer Science &
RESEARCH ARTICLE OPEN ACCESS Distributed Framework for Data Mining As a Service on Private Cloud Shraddha Masih *, Sanjay Tanwani** *Research Scholar & Associate Professor, School of Computer Science &
STATISTICA. Financial Institutions. Case Study: Credit Scoring. and
 Financial Institutions and STATISTICA Case Study: Credit Scoring STATISTICA Solutions for Business Intelligence, Data Mining, Quality Control, and Web-based Analytics Table of Contents INTRODUCTION: WHAT
Financial Institutions and STATISTICA Case Study: Credit Scoring STATISTICA Solutions for Business Intelligence, Data Mining, Quality Control, and Web-based Analytics Table of Contents INTRODUCTION: WHAT
Our SEO services use only ethical search engine optimization techniques. We use only practices that turn out into lasting results in search engines.
 Scope of work We will bring the information about your services to the target audience. We provide the fullest possible range of web promotion services like search engine optimization, PPC management,
Scope of work We will bring the information about your services to the target audience. We provide the fullest possible range of web promotion services like search engine optimization, PPC management,
User Data Analytics and Recommender System for Discovery Engine
 User Data Analytics and Recommender System for Discovery Engine Yu Wang Master of Science Thesis Stockholm, Sweden 2013 TRITA- ICT- EX- 2013: 88 User Data Analytics and Recommender System for Discovery
User Data Analytics and Recommender System for Discovery Engine Yu Wang Master of Science Thesis Stockholm, Sweden 2013 TRITA- ICT- EX- 2013: 88 User Data Analytics and Recommender System for Discovery
Towards a Transparent Proactive User Interface for a Shopping Assistant
 Towards a Transparent Proactive User Interface for a Shopping Assistant Michael Schneider Department of Computer Science, Saarland University, Stuhlsatzenhausweg, Bau 36.1, 66123 Saarbrücken, Germany [email protected]
Towards a Transparent Proactive User Interface for a Shopping Assistant Michael Schneider Department of Computer Science, Saarland University, Stuhlsatzenhausweg, Bau 36.1, 66123 Saarbrücken, Germany [email protected]
Paper AA-08-2015. Get the highest bangs for your marketing bucks using Incremental Response Models in SAS Enterprise Miner TM
 Paper AA-08-2015 Get the highest bangs for your marketing bucks using Incremental Response Models in SAS Enterprise Miner TM Delali Agbenyegah, Alliance Data Systems, Columbus, Ohio 0.0 ABSTRACT Traditional
Paper AA-08-2015 Get the highest bangs for your marketing bucks using Incremental Response Models in SAS Enterprise Miner TM Delali Agbenyegah, Alliance Data Systems, Columbus, Ohio 0.0 ABSTRACT Traditional
WEB SITE OPTIMIZATION THROUGH MINING USER NAVIGATIONAL PATTERNS
 WEB SITE OPTIMIZATION THROUGH MINING USER NAVIGATIONAL PATTERNS Biswajit Biswal Oracle Corporation [email protected] ABSTRACT With the World Wide Web (www) s ubiquity increase and the rapid development
WEB SITE OPTIMIZATION THROUGH MINING USER NAVIGATIONAL PATTERNS Biswajit Biswal Oracle Corporation [email protected] ABSTRACT With the World Wide Web (www) s ubiquity increase and the rapid development
Accelerating Hadoop MapReduce Using an In-Memory Data Grid
 Accelerating Hadoop MapReduce Using an In-Memory Data Grid By David L. Brinker and William L. Bain, ScaleOut Software, Inc. 2013 ScaleOut Software, Inc. 12/27/2012 H adoop has been widely embraced for
Accelerating Hadoop MapReduce Using an In-Memory Data Grid By David L. Brinker and William L. Bain, ScaleOut Software, Inc. 2013 ScaleOut Software, Inc. 12/27/2012 H adoop has been widely embraced for
Concept and Project Objectives
 3.1 Publishable summary Concept and Project Objectives Proactive and dynamic QoS management, network intrusion detection and early detection of network congestion problems among other applications in the
3.1 Publishable summary Concept and Project Objectives Proactive and dynamic QoS management, network intrusion detection and early detection of network congestion problems among other applications in the
Large-Scale Data Sets Clustering Based on MapReduce and Hadoop
 Journal of Computational Information Systems 7: 16 (2011) 5956-5963 Available at http://www.jofcis.com Large-Scale Data Sets Clustering Based on MapReduce and Hadoop Ping ZHOU, Jingsheng LEI, Wenjun YE
Journal of Computational Information Systems 7: 16 (2011) 5956-5963 Available at http://www.jofcis.com Large-Scale Data Sets Clustering Based on MapReduce and Hadoop Ping ZHOU, Jingsheng LEI, Wenjun YE
Model-Based Cluster Analysis for Web Users Sessions
 Model-Based Cluster Analysis for Web Users Sessions George Pallis, Lefteris Angelis, and Athena Vakali Department of Informatics, Aristotle University of Thessaloniki, 54124, Thessaloniki, Greece [email protected]
Model-Based Cluster Analysis for Web Users Sessions George Pallis, Lefteris Angelis, and Athena Vakali Department of Informatics, Aristotle University of Thessaloniki, 54124, Thessaloniki, Greece [email protected]
InfiniteGraph: The Distributed Graph Database
 A Performance and Distributed Performance Benchmark of InfiniteGraph and a Leading Open Source Graph Database Using Synthetic Data Objectivity, Inc. 640 West California Ave. Suite 240 Sunnyvale, CA 94086
A Performance and Distributed Performance Benchmark of InfiniteGraph and a Leading Open Source Graph Database Using Synthetic Data Objectivity, Inc. 640 West California Ave. Suite 240 Sunnyvale, CA 94086
Statistical Models in Data Mining
 Statistical Models in Data Mining Sargur N. Srihari University at Buffalo The State University of New York Department of Computer Science and Engineering Department of Biostatistics 1 Srihari Flood of
Statistical Models in Data Mining Sargur N. Srihari University at Buffalo The State University of New York Department of Computer Science and Engineering Department of Biostatistics 1 Srihari Flood of
A Platform for Supporting Data Analytics on Twitter: Challenges and Objectives 1
 A Platform for Supporting Data Analytics on Twitter: Challenges and Objectives 1 Yannis Stavrakas Vassilis Plachouras IMIS / RC ATHENA Athens, Greece {yannis, vplachouras}@imis.athena-innovation.gr Abstract.
A Platform for Supporting Data Analytics on Twitter: Challenges and Objectives 1 Yannis Stavrakas Vassilis Plachouras IMIS / RC ATHENA Athens, Greece {yannis, vplachouras}@imis.athena-innovation.gr Abstract.
Customer Analytics. Turn Big Data into Big Value
 Turn Big Data into Big Value All Your Data Integrated in Just One Place BIRT Analytics lets you capture the value of Big Data that speeds right by most enterprises. It analyzes massive volumes of data
Turn Big Data into Big Value All Your Data Integrated in Just One Place BIRT Analytics lets you capture the value of Big Data that speeds right by most enterprises. It analyzes massive volumes of data
Analysing Large Web Log Files in a Hadoop Distributed Cluster Environment
 Analysing Large Files in a Hadoop Distributed Cluster Environment S Saravanan, B Uma Maheswari Department of Computer Science and Engineering, Amrita School of Engineering, Amrita Vishwa Vidyapeetham,
Analysing Large Files in a Hadoop Distributed Cluster Environment S Saravanan, B Uma Maheswari Department of Computer Science and Engineering, Amrita School of Engineering, Amrita Vishwa Vidyapeetham,
Example application (1) Telecommunication. Lecture 1: Data Mining Overview and Process. Example application (2) Health
 Lecture 1: Data Mining Overview and Process What is data mining? Example applications Definitions Multi disciplinary Techniques Major challenges The data mining process History of data mining Data mining
Lecture 1: Data Mining Overview and Process What is data mining? Example applications Definitions Multi disciplinary Techniques Major challenges The data mining process History of data mining Data mining
Chapter 6. Attracting Buyers with Search, Semantic, and Recommendation Technology
 Attracting Buyers with Search, Semantic, and Recommendation Technology Learning Objectives Using Search Technology for Business Success Organic Search and Search Engine Optimization Recommendation Engines
Attracting Buyers with Search, Semantic, and Recommendation Technology Learning Objectives Using Search Technology for Business Success Organic Search and Search Engine Optimization Recommendation Engines
Query Recommendation employing Query Logs in Search Optimization
 1917 Query Recommendation employing Query Logs in Search Optimization Neha Singh Department of Computer Science, Shri Siddhi Vinayak Group of Institutions, Bareilly Email: [email protected] Dr Manish
1917 Query Recommendation employing Query Logs in Search Optimization Neha Singh Department of Computer Science, Shri Siddhi Vinayak Group of Institutions, Bareilly Email: [email protected] Dr Manish
Network Big Data: Facing and Tackling the Complexities Xiaolong Jin
 Network Big Data: Facing and Tackling the Complexities Xiaolong Jin CAS Key Laboratory of Network Data Science & Technology Institute of Computing Technology Chinese Academy of Sciences (CAS) 2015-08-10
Network Big Data: Facing and Tackling the Complexities Xiaolong Jin CAS Key Laboratory of Network Data Science & Technology Institute of Computing Technology Chinese Academy of Sciences (CAS) 2015-08-10
It is clear the postal mail is still very relevant in today's marketing environment.
 Email and Mobile Digital channels have many strengths, but they also have weaknesses. For example, many companies routinely send out emails as a part of their marketing campaigns. But people receive hundreds
Email and Mobile Digital channels have many strengths, but they also have weaknesses. For example, many companies routinely send out emails as a part of their marketing campaigns. But people receive hundreds
A Study of Web Log Analysis Using Clustering Techniques
 A Study of Web Log Analysis Using Clustering Techniques Hemanshu Rana 1, Mayank Patel 2 Assistant Professor, Dept of CSE, M.G Institute of Technical Education, Gujarat India 1 Assistant Professor, Dept
A Study of Web Log Analysis Using Clustering Techniques Hemanshu Rana 1, Mayank Patel 2 Assistant Professor, Dept of CSE, M.G Institute of Technical Education, Gujarat India 1 Assistant Professor, Dept
International Journal of Engineering Research-Online A Peer Reviewed International Journal Articles available online http://www.ijoer.
 REVIEW ARTICLE ISSN: 2321-7758 UPS EFFICIENT SEARCH ENGINE BASED ON WEB-SNIPPET HIERARCHICAL CLUSTERING MS.MANISHA DESHMUKH, PROF. UMESH KULKARNI Department of Computer Engineering, ARMIET, Department
REVIEW ARTICLE ISSN: 2321-7758 UPS EFFICIENT SEARCH ENGINE BASED ON WEB-SNIPPET HIERARCHICAL CLUSTERING MS.MANISHA DESHMUKH, PROF. UMESH KULKARNI Department of Computer Engineering, ARMIET, Department
Augmented Search for Web Applications. New frontier in big log data analysis and application intelligence
 Augmented Search for Web Applications New frontier in big log data analysis and application intelligence Business white paper May 2015 Web applications are the most common business applications today.
Augmented Search for Web Applications New frontier in big log data analysis and application intelligence Business white paper May 2015 Web applications are the most common business applications today.
AdTheorent s. The Intelligent Solution for Real-time Predictive Technology in Mobile Advertising. The Intelligent Impression TM
 AdTheorent s Real-Time Learning Machine (RTLM) The Intelligent Solution for Real-time Predictive Technology in Mobile Advertising Worldwide mobile advertising revenue is forecast to reach $11.4 billion
AdTheorent s Real-Time Learning Machine (RTLM) The Intelligent Solution for Real-time Predictive Technology in Mobile Advertising Worldwide mobile advertising revenue is forecast to reach $11.4 billion
16.1 MAPREDUCE. For personal use only, not for distribution. 333
 For personal use only, not for distribution. 333 16.1 MAPREDUCE Initially designed by the Google labs and used internally by Google, the MAPREDUCE distributed programming model is now promoted by several
For personal use only, not for distribution. 333 16.1 MAPREDUCE Initially designed by the Google labs and used internally by Google, the MAPREDUCE distributed programming model is now promoted by several
Email Spam Detection Using Customized SimHash Function
 International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 1, Issue 8, December 2014, PP 35-40 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org Email
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 1, Issue 8, December 2014, PP 35-40 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org Email
Collaborative Filtering. Radek Pelánek
 Collaborative Filtering Radek Pelánek 2015 Collaborative Filtering assumption: users with similar taste in past will have similar taste in future requires only matrix of ratings applicable in many domains
Collaborative Filtering Radek Pelánek 2015 Collaborative Filtering assumption: users with similar taste in past will have similar taste in future requires only matrix of ratings applicable in many domains
Search Engine Optimisation workbook
 Search Engine Optimisation workbook Sub-title here Search Engine Optimisation workbook SEO: Getting Started When referring to SEO the focus is on organic search results not paid for traffic from Google
Search Engine Optimisation workbook Sub-title here Search Engine Optimisation workbook SEO: Getting Started When referring to SEO the focus is on organic search results not paid for traffic from Google
The Scientific Data Mining Process
 Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Chapter 4 The Scientific Data Mining Process When I use a word, Humpty Dumpty said, in rather a scornful tone, it means just what I choose it to mean neither more nor less. Lewis Carroll [87, p. 214] In
Search Taxonomy. Web Search. Search Engine Optimization. Information Retrieval
 Information Retrieval INFO 4300 / CS 4300! Retrieval models Older models» Boolean retrieval» Vector Space model Probabilistic Models» BM25» Language models Web search» Learning to Rank Search Taxonomy!
Information Retrieval INFO 4300 / CS 4300! Retrieval models Older models» Boolean retrieval» Vector Space model Probabilistic Models» BM25» Language models Web search» Learning to Rank Search Taxonomy!
Data Mining Analytics for Business Intelligence and Decision Support
 Data Mining Analytics for Business Intelligence and Decision Support Chid Apte, T.J. Watson Research Center, IBM Research Division Knowledge Discovery and Data Mining (KDD) techniques are used for analyzing
Data Mining Analytics for Business Intelligence and Decision Support Chid Apte, T.J. Watson Research Center, IBM Research Division Knowledge Discovery and Data Mining (KDD) techniques are used for analyzing
Benchmarking Hadoop & HBase on Violin
 Technical White Paper Report Technical Report Benchmarking Hadoop & HBase on Violin Harnessing Big Data Analytics at the Speed of Memory Version 1.0 Abstract The purpose of benchmarking is to show advantages
Technical White Paper Report Technical Report Benchmarking Hadoop & HBase on Violin Harnessing Big Data Analytics at the Speed of Memory Version 1.0 Abstract The purpose of benchmarking is to show advantages
Clustering Technique in Data Mining for Text Documents
 Clustering Technique in Data Mining for Text Documents Ms.J.Sathya Priya Assistant Professor Dept Of Information Technology. Velammal Engineering College. Chennai. Ms.S.Priyadharshini Assistant Professor
Clustering Technique in Data Mining for Text Documents Ms.J.Sathya Priya Assistant Professor Dept Of Information Technology. Velammal Engineering College. Chennai. Ms.S.Priyadharshini Assistant Professor
MARKETING ANALYTICS AS A SERVICE
 MARKETING ANALYTICS AS A SERVICE WEATHER BASED CONTENT PERSONALIZATION Joseph A. Marr, Ph.D. Senior Principal Data Scientist SYNTASA Kirk D. Borne, Ph.D. Advisory Board Member SYNTASA MAY 2014 INTRODUCTION:
MARKETING ANALYTICS AS A SERVICE WEATHER BASED CONTENT PERSONALIZATION Joseph A. Marr, Ph.D. Senior Principal Data Scientist SYNTASA Kirk D. Borne, Ph.D. Advisory Board Member SYNTASA MAY 2014 INTRODUCTION:
Knowledge Discovery from patents using KMX Text Analytics
 Knowledge Discovery from patents using KMX Text Analytics Dr. Anton Heijs [email protected] Treparel Abstract In this white paper we discuss how the KMX technology of Treparel can help searchers
Knowledge Discovery from patents using KMX Text Analytics Dr. Anton Heijs [email protected] Treparel Abstract In this white paper we discuss how the KMX technology of Treparel can help searchers
CiteSeer x in the Cloud
 Published in the 2nd USENIX Workshop on Hot Topics in Cloud Computing 2010 CiteSeer x in the Cloud Pradeep B. Teregowda Pennsylvania State University C. Lee Giles Pennsylvania State University Bhuvan Urgaonkar
Published in the 2nd USENIX Workshop on Hot Topics in Cloud Computing 2010 CiteSeer x in the Cloud Pradeep B. Teregowda Pennsylvania State University C. Lee Giles Pennsylvania State University Bhuvan Urgaonkar
