This is the author s version of a work that was submitted/accepted for publication in the following source:
|
|
|
- Jordan Jonah Lucas
- 8 years ago
- Views:
Transcription
1 This is the author s version of a work that was submitted/accepted for publication in the following source: Suriadi, Suriadi, Ouyang, Chun, van der Aalst, Wil M.P., & ter Hofstede, Arthur (2013) Root cause analysis with enriched process logs. Lecture Notes in Business Information Processing [Business Process Management Workshops: BPM 2012 International Workshops Revised Papers], 132, pp This file was downloaded from: c Copyright 2013 Springer-Verlag Berlin Heidelberg. Notice: Changes introduced as a result of publishing processes such as copy-editing and formatting may not be reflected in this document. For a definitive version of this work, please refer to the published source:
2 Root Cause Analysis with Enriched Process Logs S. Suriadi 1, C. Ouyang 1, W.M.P. van der Aalst 1,2, and A.H.M. ter Hofstede 1,2 1 Queensland University of Technology, Australia {s.suriadi,c.ouyang,a.terhofstede}@qut.edu.au 2 Eindhoven University of Technology, The Netherlands {w.m.p.v.d.aalst,a.h.m.ter.hofstede}@tue.nl Abstract. In the field of process mining, the exploitation of event logs for the purpose of root cause analysis is a relatively unexplored area. This paper proposes an approach to enrich and transform process-based logs for the purpose of root cause analysis through the application of classification techniques. This approach facilitites an objective identification of the root cause(s) of various incidents as it is grounded on what has actually happened, thus, minimizing the influence of subjective perceptions in the results. The approach proposed in this paper is formalized and its applicability has been validated using both self-generated logs and a publicly-available log. Topic classification: Mining of business processes Keywords: process mining, root cause analysis, event logs, business process management 1 Introduction A recent survey by Gartner shows that risk management is one of the top strategic business priorities for CEOs and senior executives [2]. A common way to mitigate risks is to remove or minimize the presence of key factors which are known to contribute to the occurrence of unwanted risk events. For example, it is well-established that pilot fatigue is one of the key factors contributing to airline safety issues [3]. Thus, measures to mitigate the chance of pilots being fatigued during working hours have routinely been implemented Root cause analysis (RCA) has been applied widely in organisations and many techniques have been developed, including the use of flow charts, spider charts, brainstorming, and others [1]. Through RCA, one aims to find an explanation of risk incidents, preferably an explanation involving a minimal number of factors. As many events are recorded in logs nowadays (e.g. by devices or software applications) one can exploit this data for the purpose of RCA with the added advantage that the data reflects reality and not a perception (e.g. in the form of a model) of reality. As we focus on operational rocesses in this paper, one can take post-execution event data as a starting point and compare features, recorded as attributes, of cases (i.e. process instances) that were classified as successful with those features of cases that were classified as unsuccessful.
3 2 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede This way we can define a classification problem whose results provide valuable input for RCA. The features which may be the root cause(s) of risk incidents may come from various context, including instance context, process context, social context, and environmental context [19]. However, raw data from post-execution logs (commonly known as event logs), may not readily contain the necessary information to explain the possible root cause(s) of risk incidents. In this paper, we propose an RCA approach that starts with an existing event log and enriches it with relevant contextual information for explaining possible root cause(s) of risk incidents. This enriched log can then be manipulated further such that it can be analyzed using established classification techniques. In other words, we transform a process mining problem, i.e. RCA based on event logs, into a standard classification problem. In this paper, we focus on the approach and not on the selection of variables (features). In fact, in order to illustrate our approach and also to scope our paper, we investigate the effect of workload on overtime (long-running) cases. Here we may draw on the Yerkes Dodson law [21, pp ] which captures the relationship between the stress level of resources and their performance. This relationship can be visualised as an inverted letter U in a diagram with performance on the y-axis and degree of stress level on the x-axis, indicating that both low and high stress levels are related to low performance. In the remainder of the paper, we first explain our approach in detail and present a formalisation. This is then followed by an application of the approach to RCA with workload-enriched logs. Finally the approach is validated with a publicly available log to demonstrate its applicability. 2 Approach In this section, we describe our approach to mining the root cause of risk incidents (such as budget overrun and long running/overtime cases) through the transformation of a process mining problem into a standard classification problem. Our approach starts with determining relevant information that is needed to explain the root cause of a risk incident, followed by the enrichment of the related event log with the necessary information to ensure that sufficient information for RCA is captured. Through the application of aggregation functions and other refinement procedures, we transform this enriched event log into a form that is suitable to be analysed by classification techniques. Fig. 1 depicts our approach - the details of which are explained in this section. RCA Data Requirements. As a requirement from classification techniques, RCA uses a response variable for the labelling of successful/unsuccessful cases. An example of a response variable can be seen as a feature in a log which states the outcome of a case as either being on-time or overtime. The features which may influence the occurrence of successful/unsuccessful cases are labelled as predic-
4 2 Approach 3 Raw Event Log Enrich Enriched Event Log Aggregate L L A'E AE Case Log Refine Classification-ready Log L* AC L* A'C informs informs contains Response / Predictor Variables Data Mining Analysis Fig. 1: Approach Diagram. tor variables. An example of a predictor variable can be specified by workload which may have impact on the occurrence of long-running (over-time) cases. Thus, the very first step of our approach is to determine the response variable capturing the risk incident we want to analyze, and the set of predictor variables which may contribute to the occurrence of such risk incident. The determination of these attributes must of course be informed by established management theories and studies as well as from a company s risk registries. In process mining, these variables may be taken from various context, including instance context (e.g. size of an insurance claim), process context (e.g. total number of resources involved), social context (e.g. stress level), and external context (e.g. weather) [19]. Enrich Raw Event Log. Once the predictor and response variables are determined, we need to verify if our raw event log contains sufficient information to captures those variables. It is possible that some information may not be readily available in the raw event log, but can be derived from the data in the raw event log. There are also situations when the required information needs to be obtained from external sources and be correlated to the raw event log. Once the above information is obtainable, we can then extend the raw event log with such information thus resulting in an enriched event log). Definition 1 (Event log). An event log consists of a set of events. Events are characterised by various attributes, e.g., an event may have a timestamp, correspond to an activity, etc. Let A E = {a 1,..., a n } be a set of event attributes. For each attribute a i A E (1 i n), D i = dom(a i ) (i.e. the domain of a i ), e.g., the domain of attribute timestamp is the set of all possible time values. L AE 2 D1... Dn is an event log based on the set of attributes A E. For any event e L and attribute a A E : # a (e) is the value of attribute a for event e. Definition 2 (Event log enrichment). Let L AE be an event log based on the set of attributes A E. Let A D be a set of derivable attributes whose value can be calculated from A E, i.e. for each attribute d A D, L AE {d} = δ d (L AE ) where δ d is a derivative function that computes the value of attribute d for all events in L AE. Let A K be a set of correlatable attributes whose value can be obtained from external sources based on some key attributes in A E, i.e. for each attribute k A E, L AE {k} = ω k (L AE ) where ω k is a correlative function that retrieves the value of attribute k for all events in L AE. L A E where A E = A E A D A K, is an enriched event log with a set of extended (derivable and correlatable) attributes.
5 4 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede From Event Log to Case Log. The next step is to transform the event log into a case log. This is necessary because RCA is normally performed at case level. Definition 3 (Case log). A case log comprises a set of cases. Cases, like events, have attributes, e.g., a case has a case identifier, corresponds to a trace (i.e. a sequence of events), etc. Let A C = {s 1,..., s m } be a set of case attributes, including a mandatory attribute named case id which uniquely identifies a case. For each s i A C (1 i m), D i = dom(s i ) where dom(case id) = C (i.e. the set of all possible case identifiers). L A C 2 D1...C...Dm is a case log based on the set of attributes A C. For any case c L A C and attribute s A C : # s (c) is the value of attribute s for case c. For any c 1, c 2 L A C, # case id (c 1 ) # case id (c 2 ). Definition 4 (Aggregation of event log to case log). Let L AE be an event log based on the set of event attributes A E where case id A E. A corresponding case log L A C based on the set of attributes A C can be generated from L AE as: (1) the set of case identifiers c L # case id (c) = A e L AE # case id (e); and (2) for C each case c L A C and attribute s A C \{case id}, # s (c) = α s (L AE, # case id (c)) where α s is an aggregation function that calculates the value of attribute s in case c from the relevant events in L AE. Get Case Log Ready for Classification. For classification techniques to work, there are often requirements imposed on the structure of the data. For example, most classification techniques require the response variable to be presented in a categorial (nominal) form. If our data is not already in the correct format, we need to further transform the attributes in a case log accordingly. Definition 5 (Classification-ready case log). Let L A C be a case log based on the set of (normal) attributes A C. Let A C be a set of classification attributes (e.g. capturing response variables) whose value is of categorial form and can be computed from the set of case attributes A C. L A where A C = A C A C, is C a classification-ready case log. For each case c L A and attribute q A C : C # q (c) = χ q (L A C, c) where χ q is a classification function that derives the value of attribute q in case c based on the corresponding case data in L A C. RCA with Classification Techniques. Through the process detailed so far, we have now transformed a raw event log into a case log in a format that is suitable for classification analysis. The enriched case log now has the values of both the response and predictor variables of interest. One can feed these data into various data mining algorithms to find the root cause(s) of a risk incident. 3 RCA with Workload-Enriched Logs In this section, we apply our approach to the analysis of overtime cases using event logs enriched with workload information. According to dictionary, workload is defined as the amount of work assigned to or expected from a person in a
6 3 RCA with Workload-Enriched Logs 5 specified time period 1. In the context of business processes, workload has been defined and computed in different ways (e.g. [21, Chapter 11] [12]). In this paper, we consider workload as a list of work items that have been allocated to and/or started by a resource in a specified time period. Workload is usually not recorded directly in a raw event log but can be derived from a set of basic event attributes that capture the information about resource, activity, timestamp, and transaction type (which refers to the life-cycle of activities, e.g. start, complete) associated with each event. Below, we precisely define workload based on the information in a given event log of any process. Definition 6 (Workload). Let L be an event log based on the set of event attributes including {case id, resource, activity, time, trans}, where dom(trans) = {allocate, start, complete}. For any resource r {# resource (e) e L}, the workload of r in time period (t s, t e ), is defined as WLL (r) = WLts (r) WL(ts ts,te,te) L L (r). first of all, assume three short notations: L r,ts = {e L # resource (e) = r # time (e) < t s } L r,ts,te = {e L # resource (e) = r t s # time (e) t e } e L, wi(e) = (# activity (e), # case id (e)). Then: WL ts L (r) = {wi(e) e # Lr,ts trans (e) {allocate, start}} \ {wi(e) e L r,ts # trans (e) = complete}, i.e. the list of work items that have been allocated to and/or started but not yet completed by resource r at time t s ; and (ts,te) WL L (r) = {wi(e) e L r,ts,te # trans (e) {allocate, start}} \WL ts L (r), i.e. the list of additional work items that are allocated to and/or started by resource r within time period (t s, t e ). Consider a raw event log L AE with a set of existing event attributes A E. Following the approach in Sect. 2, we enrich log L AE with workload information. A derivable attribute res workload captures the workload of all resources in the log within certain time periods. Each time period is specified by referencing the timestamp of an individual event in L AE and using the average activity duration (AAD) of the process as the time duration. We assume an existing function AvgActDuration which takes an event log and returns the corresponding AAD 2. Algorithm 1 defines how to compute the value of attribute res workload based on the raw event log L AE. First, a relation R WL, i.e. a set of (time,res workload) tuples, is derived capturing the workload of all resources each time an event is recorded in L AE. By definition, an event log can be treated as a relation where the set of event attributes specify its relation scheme. Hence, in Algorithm 1 three relational algebra operators [10] are used to define certain log operations: the selection (σ) of a set of events that satifies specific conditions in the log; the projection (π) of all events in the log restricted to a set of attributes; and finally the natural join ( ) for combining all events in L AE and all tuples in R WL on their common attribute time to yield the workload-enriched log L AE {res workload} The underlying computation for such function is already supported by a number of log pre-processing tools, such as Nitro (see
7 6 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede Algorithm 1: Generation of workload-enriched event log based on an instantiation of derivative function γ in Definition 2. Input: an event log L AE and a derivable attribute res workload Output: a workload-enriched event log L AE {res workload} begin R WL := ; /* R WL is a relation of {time, res workload} */ R := {# resource(e) e L AE }; T := {# time(e) e L AE }; d h := AvgActDuration(L AE )/2; for t T do rwl := ; t s := t d h ; t e := t + d h ; for r R do L r := σ resource=r(l AE ); /* calculate allocated/started but not completed work items at time t s */ L r,ts := σ time<ts (L r ); for tr {allocate, start, complete} do L tr WI := π {case id,activity} (σ trans=tr (L r,ts )) rwl := rwl {(r, (L allocate WI L start WI ) \ L complete WI )}; /* calculate allocated/started work items within time period (t s, t e) */ r,ts,te LM := σ ts time te (L r ); for tr {allocate, start} do L tr WI := π {case id,activity} (σ trans=tr (L r,ts,te )) rwl := rwl {(r, (L allocate WI L start WI ))} R WL := R WL {(t, rwl)} L AE {res workload} = {time} (L AE, R WL) Now consider the set of event attributes A C = {case id, time start, time end, avg workload, resources} that are required for deriving the value of predictor and response variables in the next step. We generate case log L A C from (the above enriched) event log L AE {res workload}. For each case c L A C, we calculate: # time start (c) = Min(π {time} (σ case id=#case id (c)(l AE ))) # time end (c) = Max(π {time} (σ case id=#case id (c)(l AE ))) # resources (c) = {# resource (e) e σ case id=#case id (c)(l AE )} # avg workload (c) = {(r, ( e i L c A E workload(r, e i ) ) / L c A E ) r R} where R = {# resource (e) e L AE } is the set of all resources in L AE, L c A E = σ #time start (c) timestamp # time end (c)(l AE ) is the set of all events in L AE that occurred between the start and the end of case c, workload(r, e i ) is the workload of resource r at the time of event e i, which is specified in # res workload (e i ). Finally, two examples of classification-ready attributes are A C = {isovertime, isclerkinvolved}, where isovertime signals if a case (time) duration exceeds a specific threshold value, and isclerkinvolved indicates if resource named Clerk
8 4 Validation of Approach 7 is involved in a case. Both returns a value of boolean type (a valid categorial form). Hence, for each case c L A where A C = A C A C, C # isovertime (c) = ((# time end (c) # time start (c) > threshold) # isclerkinvolved (c) = (Clerk # resources (c)) 4 Validation of Approach Two rounds of approach validation were conducted. The first validation round was based on a self-generated synthetic log. It was conducted during the development of our approach (w.r.t the enrichment of event log with workload information) to facilitate step-by-step validation and refinement of our approach. The second evaluation round was conducted to demonstrate the general applicability of our approach in a less controlled environment by applying our approach to a log whose generation was beyond our control. The first validation round is briefly described in Sect. 4.1, while a more elaborate description of the second evaluation round is provided in Sect Log Quality. To derive workload information, we assume the existence of an event log of certain quality: (1) a minimum of 3-star log quality (as defined in the process mining manifesto [18]), (2) the existence of a number of open XES-equivalent attributes: (a) concept:name (at trace and event level), (b) lifecycle:transition, org:resource, time:timestamp (at event level), and (3) the recording of start (or assign) and complete transition of each activity. 4.1 Validation with Synthetic Log The first validation round was conducted using a Purchase Order scenario. A synthetic log was generated using a Coloured Petri Net (CPN) [9] model of the Purchase Order process through the application of the MXML-log-generator plug-in [11]. This log records the assign, start, and complete transitions for each activity. This log file was imported to a MySQL database such that relevant relational algebra operations can be performed. The workload derivation function and case log aggregation functions (as defined in Sect. 3) were implemented as a Java program which interacted with the database. The final classificationready case log was successfully fed into the WEKA data mining tool such that the root cause of overtime cases can be analyzed by the application of various classification algorithms (e.g. J48 [13] and JRip [4]). The classification analysis result from this log showed that average resources workload was a key factor in the occurence of overtime cases. This validation round confirms the applicability of our approach in performing an RCA through the enrichment and transformation of a process log such that root cause(s) of a risk incident can be identified by applying classification techniques. The details of this validation round are available in Appendix A.
9 8 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede 4.2 Validation with Public Log While the first validation round was necessary to confirm the applicability of our approach, it was weak as it was based on a log that we generated ourselves. To demonstrate the general applicability of our approach, we conducted a second validation round using an event log that was generated by other people and is available from the process mining website. 3 Equally important, while further refinement is still needed, the second validation round confirms the generalizability of the Java program developed in enriching and transforming event log with resources workload and involvement information. Thus, it is possible to automate and streamline (to a certain degree) the approach proposed in this paper. The log used in this validation round was generated from a telephone repair process. This log contains the necessary attributes as defined in M. There are four activities in this log: Analyze Defects, Repair (Complex), Repair (Simple), and Test Repair. There are 12 resources in the log: SolverC1, SolverC2, SolverC3, SolverS1, SolverS2, SolverS3, Tester1, Tester2,..., Tester6. There are more than 1100 cases (mostly completed cases). Log Enrichment with Workload The log used in this validation round meets the minimum log quality as stated earlier. Thus, we can proceed to enrich the log with workload information. This log was imported to a MySQL database table (called eventlog table) so that it could be manipulated using relational algebra operators (see Table 1 for a snippet of the table). caseid Activity eventtype timestamp resource 18 Analyze Defect start :36:00 Tester6 18 Analyze Defect complete :44:00 Tester6 15 Repair (Complex) start :29:00 SolverC Table 1: A snippet of the eventlog database table. The workload derivation function (Algorithm 1 from Sect. 3) was implemented in a Java program (which interacted with the eventlog through SQL queries). This program outputs a table called workloadstarted which captures the workload information of each resource (i.e. the realization of R W L relation). The average activity duration used is 450 seconds. The log used in our validation only contains the start and complete transition, thus, workloadstarted only reflects the work items that were still being executed by a particular resource at a point in time when an event was recorded in the log. A snippet of the workloadstarted table is provided in Table 2. The content of each field named after each resource identifier (e.g. SolverC1 and SolverC3) represents the workload of the corresponding resource at its corresponding timestamp. For example, using :37:00 as a reference time, resource SolverC1 had no work items being executed (or assigned to) between the period of :33:15 and :40:45, while resource SolverS3 had two work items that were either being executed or assigned (that is, the activity Repair 3
10 4 Validation of Approach 9 (Simple) for case number 70 and 34) over the same period. The workloadenriched event log (i.e. L A E ) is obtained by joining Table 2 and Table 1 on timestamp field. timestamp Workload SolverC1... Workload SolverC3 Workload SolverS :37:00 (empty)... (empty) (70:Repair (Simple)),... (34:Repair (Simple)) :10:00 (36:Repair (Complex))... (60:Repair (Complex)) (empty) Table 2: A snippet of the workloadstarted table (R W L ) Aggregation to Case Log The workload-enriched event log obtained so far contains the workload information of each resource at every timestamp in the log. Given that a case may consist of more than one event, we need to aggregate the workload information among all relevant events (that make up one case) in the log. We have implemented the necessary functions to obtain the # time start (c), # time end (c), # resources (c), and # avg workload (c) case attributes (defined in Sect. 3). In our implementation, the average workload for each resource (quantified as the number of work items) is stored in a separate field, each named using the following format: avgwl rx, where r x is a resource s identifier (see Table 3). The results of the application of these aggregation functions were stored in another table, called the caselog table (which is a manifestation of L A C ). Classification-ready Case Log Finally, we transformed caselog into a form that is ready for classification analysis. Currently, caselog does not contain a proper response variable: we know the start and end of each case; however, we still need to further refine this information to obtain the duration of the case and then to categorize each case to on-time or overtime. In other words, we need to implement a function to obtain the # isovertime(c) attribute (defined in Sect. 3). In our implementation, on-time cases were labeled with a 0 value, while overtime cases were labelled with a 1 value. The threshold value which determines if a case is overdue or not is set to 1 hour. 4 We have also implemented a function to obtain the # isrxinvolved(c) value (defined in Sect. 3) to ensure that the information regarding the involvement (or non-involvement) of each resource is presented as a distinct predictor variable. For n-number of resources, this function creates n new field, named as isinvolved rx (where r x is a resource s identifier). Each of these fields can now be labelled individually as a distinct predictor variable. We then extended the caselog table with the results of the application of these two functions. A snippet of the final classification-ready case log table is shown in Table 3. This table is a manifestation of L A C 4 This number is chosen based on the fact that most cases completed within 1 hour (of course, the assumption here is that the majority of cases do not run overtime).
11 10 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede caseid start end isoverdue avgwl SolverC1... avgwl T ester6 isinvolved SolverC :58: false :22: false... Table 3: A snippet of a classifier-ready case log (L A ). C RCA with Classification Techniques We fed the classification-ready case log into WEKA [23]. WEKA supports classification algorithms, such as J.48 [13], JRip [4], and many others. We started the analysis by just using the average workload of all resources as predictor variables. An example of the results of the decision tree learning analysis (using the J.48 algorithm [13] under 10-fold cross validation mode [17, Chapter 3]) is shown in Fig. 2 (top part). For example, line 3 in Fig. 2 shows that if the average workload of resource SolverS1 is equal or less than and the average workload for Tester4 is equal to or less than (line 5), then the rules generated by the algorithm say that all 248 cases which fulfill these criteria should be classified as on-time (represented as 0 ). While the records in the log show that this rule misclassified 42 cases, this rule is correct in the majority of cases (202 cases out of 248). However, the accuracy of the classification result is rather low. For example, for on-time cases, the true positive (TP) rate (that is, the proportion of all on-time cases which were correctly classified as on-time ) is 70% ; however, the false positive (FP) rate (that is, the proportion of all overtime cases which were incorrectly classified as on-time ) is as high as 51%. For overtime cases, the TP rate (that is, the percentage of overtime cases which were correctly classified as overtime ) is 48%, while the FP rate is as high as 29%. Fig. 3 shows the full accuracy metrics. This analysis result suggests that the average workload for a number of resources seem to have an influence the occurrence of long-running cases, however, the correlation seems rather weak. Beyond Workload - Adding Another Predictor Variable We decided to include another predictor variable in our analysis, namely the resource involvement information (recall that this information was already calculated in our classificationready case log). The same J.48 algorithm was executed, except that this time, we used both workload and resource involvement information as predictor variables. The result obtained was much more accurate: 92% TP rate/ 14% FP rate (for on-time cases), and 85% TP rate/7% FP rate (for overtime cases). Both predictor variables were used in the generated classification tree; however, the complexity of the generated classification tree is high - this may suggest an overfitting model (the decision tree is not shown in this paper). We also applied a rule-based classification algorithm to the same data set, namely, the JRip algorithm. The result obtained was much simpler than the one obtained from J.48 algorithm (only 4 rules - see Fig. 2 bottom part). For example, the rule in line 28 states that all 201 cases in which SolverC3 is involved will run overtime (in reality, this rule only misclassified 6 cases). More interestingly, however, is that the generated rules do not include resources workload as a factor in lovertime cases (although they were included in the analysis). The accuracy of the result was also comparable: 92%/14% (TP/FP rate) for on-
12 4 Validation of Approach 1 J.48 Classification Tree - Predictor Variables: only average workload for all resources 11 2 ======================================================================================= 3 avgwl_solvers1 <= avgwl_tester4 <= avgwl_tester4 <= : 0 (248.0/42.0) 6 avgwl_tester4 > : 1 (67.0/24.0) 7 avgwl_tester4 > avgwl_tester4 <= : 0 (204.0/50.0) 9 avgwl_tester4 > avgwl_tester1 <= : 1 (6.0) 11 avgwl_tester1 > avgwl_tester2 <= : 1 (3.0) 13 avgwl_tester2 > avgwl_tester3 <= 0.9: 0 (8.0) 15 avgwl_tester3 > avgwl_solverc1 <= : 0 (3.0) 17 avgwl_solverc1 > : 1 (4.0) 18 avgwl_solvers1 > avgwl_tester4 <= avgwl_solvers2 <= : 0 (174.0/65.0) 21 avgwl_solvers2 > avgwl_tester2 <= : 0 (2.0) 23 avgwl_tester2 > : 1 (9.0) 24 avgwl_tester4 > : 1 (376.0/155.0) JRip Algorithm - Predictor Variables: average workload and resources involvement 27 ================================================================================== 28 (isinvolved_solverc3 = 1) => isoverdue=1 (201.0/6.0) 29 (isinvolved_solvers1 = 1) => isoverdue=1 (206.0/41.0) 30 (isinvolved_solverc2 = 1) and (isinvolved_solverc1 = 1) => isoverdue=1 (22.0/3.0) 31 => isoverdue=0 (675.0/64.0) Fig. 2: J.48 Classification Tree - Analysis Results 1 Full Accuracy Metrics 2 ===================== 3 Correctly Classified Instances % 4 Incorrectly Classified Instances % 5 Kappa statistic Mean absolute error Root mean squared error Relative absolute error % 9 Root relative squared error % 10 Total Number of Instances === Detailed Accuracy By Class === TP Rate FP Rate Precision Recall F-Measure ROC Area Class Weighted Avg === Confusion Matrix === a b <-- classified as a = b = 1 24 Fig. 3: Full Accuracy Metrics for the J.48 Classification Tree (from Fig. 2 - top part) time cases, and 85%/7% (TP/FP rate) for overtime cases. Fig. 4 shows the full accuracy metrics of the JRrip rules.
13 12 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede 1 Full Accuracy Metrics 2 ===================== 3 Correctly Classified Instances % 4 Incorrectly Classified Instances % 5 Kappa statistic Mean absolute error Root mean squared error Relative absolute error % 9 Root relative squared error % 10 Total Number of Instances === Detailed Accuracy By Class === TP Rate FP Rate Precision Recall F-Measure ROC Area Class Weighted Avg === Confusion Matrix === a b <-- classified as a = b = 1 Fig. 4: Full Accuracy Metrics for the JRip Rules (from Fig. 2 - bottom part) By comparing these results, we may say that both workload and resource involvement may be the root causes of overtime cases in our log; however, the nature of resource involvement alone may already be sufficient to explain the occurrence of overtime cases in most instances. 5 Related Work Traditional RCA techniques have been frequently applied in the domain of business and risk management (e.g. Andersen and Fagerhaug [1] and Wilson et al. [22]), as well as manufacturing industries (e.g. Horev [8]). Similarly, the use of data mining techniques in business domain has also been heavily studied and applied (e.g. Cao et al. [5]). However, the use of data mining techniques to systematically perform an RCA of business process-related issues is still a relatively unexplored area in the field of process mining (and business process management in general), although a limited number of related studies have started to emerge. For example, Heravizadeh et al [7] proposed a technique to understand the root cause of business processes based on business process models and augmented it with concepts from requirement engineering - this is in contrast with our approach which is based on post-execution data. Rozinat and van der Aalst [16] proposed the use of classification technique to find the correlation between data attributes and the routing choices made in business processes. This approach is different from ours in that our approach focuses on the enrichment and transformation of event logs to classification-ready log for the purpose of RCA. Of course, the classification-ready log can always
14 References 13 be used to find the root cause of various routing decisions; however, it is not limited to such cases only. Furthermore, in the work by Nakatumba and van der Aalst [12], a form of RCA which seeked to study the correlation between resources workload and their performance were performed using process mining techniques and data mining technique (linear regression). Similarly, in the work by Rozinat et al. [15], the results obtained from a process mining exercise were used to explain the root cause of the occurence of idle times in a manufacturing test process. Nevertheless, the focus of both approaches was on the RCA itself, instead of the approach taken to facilitate such an analysis. The approach proposed in this paper attempts to fill this gap. 6 Conclusions We have presented and formalized an approach to enrich and transform event log into a form that allows an RCA based on classification techniques. The applicability of our approach to facilitate RCA of risk incidents has been validated using both self-generated synthetic log and publicly available log. Future work include the validation of our approach using real-life log, as well as the packaging of our approach as a plug-in to the process mining tool (ProM). The application of optimization techniques to select the best set of features as the root cause(s) of a risk incident will also be considered. References 1. Bjorn Andersen and Tom Fagerhaug. Root Cause Analysis: Simplified Tools and Techniques. ASQ Quality Press, 2nd edition, ISBN French Caldwell. CEO survey 2012: CIOs must link risk management and compliance to business priorities. Gartner, (G ), March Stephanie Chen. Pilot fatigue is like having too much to drink. CNN News, May William W. Cohen. Fast effective rule induction. In Proceedings of 12th International Conference on Machine Learning, pages Morgan Kaufmann, Longbing Cao et al., editor. Data Mining for Business Applications. Springer, Christian W. Günther and Wil M. P. van der Aalst. A generic import framework for process event logs. In BPM Workshops on Business Process Intelligence, volume LNCS, Mitra Heravizadeh et al. Root cause analysis in business processes. Technical report, Queensland University of Technology, Menachem Horev. Root Cause Analysis in Process-Based Industries. Trafford Publishing, Kurt Jensen and Lars M. Kristensen. Coloured Petri Nets - Modelling and Validation of Concurrent Systems. Springer, David Maier. The Theory of Relational Databases. Computer Science Press, 1983.
15 14 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede 11. Ana K.A. De Medeiros and Christian W. Günther. Process mining: Using CPN tools to create test logs for mining algorithms. In 6th Workshop and Tutorial on Practical Use of Coloured Petri Nets and the CPN Tools, pages , Joyce Nakatumba and Wil M. P. van der Aalst. Analyzing resource behavior using process mining. In Stefanie Rinderle-Ma et al., editor, BPM Workshops, volume 43 of LNBIP, pages Springer, John R. Quinlan. C4.5: programs for machine learning. Morgan Kaufmann Publishers Inc., San Francisco, CA, USA, Anne Ratzer et al. CPN tools for editing, simulating, and analysing coloured petri nets. In ICATPN 2003, volume 2679 of LNCS, pages Springer, Anne Rozinat et al. Process mining applied to the test process of wafer scanners in ASML. IEEE Transactions on Systems, Man, and Cybernetics, Part C: Applications and Reviews, 39(4): , Anne Rozinat and Wil M. P. van der Aalst. Decision mining in ProM. In Business Process Management, volume 4102 of LNCS, pages Springer, Wil M. P. van der Aalst. Process Mining - Discovery, Conformance and Enhancement of Business Processes. Springer, Wil M. P. van der Aalst et al. Process mining manifesto. In Florian Daniel et al., editor, BPM Workshops (1), volume 99 of LNBIP, pages Springer, Wil M.P. van der Aalst and Schahram Dustdar. Process mining put into context. IEEE Internet Computing, 16:82 86, Voluntary Inter-Industry Commerce Solutions Association. Voluntary Inter- Industry Commerce Standard (VICS). Last accessed: 22 May Christopher D. Wickens and Justin G. Hollands. Engineering Psychology and Human Performance. Prentice-Hall Inc., New Jersey, 3rd edition, Paul F. Wilson et al. Root Cause Analysis: A Tool for Total Quality Management. ASQ Quality Press, Ian H. Witten et al. Weka: Practical machine learning tools and techniques with java implementations, A Validation with Synthetic Log We use the case study of a Purchase Order process based on the Voluntary Inter-industry Commerce Solutions (VICS) (Voluntary Inter-industry Commerce Solutions) industry reference model [20]. The risk incident whose root cause(s) are to be mined is the deadline expiry event (i.e. the response variable), using a derivable predictor variable, namely the resources workload information detailed in Section 3. A synthetic log was generated from the corresponding model of the Purchase Order process (modelled using the formal language of Coloured Petri Nets (CPN) [9] and aided by the CPN Tools [14]). The MXML-log-generator plug-in [11] was used to generate an MXML-formatted log file that we used to evaluate our approach to root cause mining. The details of the approach validation are provided in the remainder of this section. A.1 Purchase Order Scenario - CPN Model and MXML Logs Figure 5 shows the CPN model from which the synthetic log (used for the validation of our approach) was generated. This process consists of four manual
16 A Validation with Synthetic Log 15 activities: create purchase order (CREATE ), approve purchase order (APPROVE ), modify purchase order (Modify ), and confirm purchase order (CONFIRM ). This process also consists of two automated activities: order timeout (ORDER TIMEOUT) and process termination activity (TERMINATE ORDER PROCESS (see Figure 5). Since they are automated, the model assumes that they are completed as soon as they are assigned. When a transition representing a process activity (those transitions with thicker border in Figure 5) is fired, a corresponding code-region code is executed to add relevant event log entry to the log file (for example, see the code region for the transition TERMINATE ORDER PROCESS in bottom-right of Figure 5). Figure 6 shows the details of the manual activity model (the same model is instantiated for all manual activities in the model). This model captures three activity lifecycle events: the assignment/allocation of an activity to a resource, the start of the activity execution by the assigned resource, and the completion of the activity by the resource. The model logs the occurrence of each of these events in the code region (not shown in Figure 6) of the corresponding activities ( ALLOCATE TASK, START TASK, COMPLETE TASK ). A resource can be allocated with an activity at any time, regardless of whether the resource is busy or free. As the resource starts to execute an activity, its status is set to busy and it cannot execute other assigned activities. Upon the completion of the activity, the resource s status is set to free again. The duration of the execution of each manual activity is set to follow a normal distribution pattern. These rules are collectively expressed in the arc inscriptions and transition guards shown in Figure 6. We configured our model to simulate the execution of 129 process instances. At the end of the simulation, 129 log files were generated (one for each process instance). We then used the ProM Import Framework tool [6] to merge those files into a single MXML file to be used for our subsequent analysis. A.2 Enriching Event Log with Workload We have implemented the log enrichment process using the synthetically-generated log. Firstly, we transformed the generated MXML file (from the CPN model) into a form that is suitable for relational algebra transformation, such as SQL queries. To this end, a raw event log table (called eventlog table) was created using the MySQL database system and the MXML log file was then imported into the table. A snippet of the MySQL table is shown in Table 4. Once the log data was in a proper form, we applied the worklist derivation functions (defined in Section 3). The generated workload table is shown in Table 5.
17 16 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede 70 START LOG INT GENERATE input (id); LOG FILE output (); action (createcasefile(id)); initiate(id) id CREATE TASK 11`"Create " CREATE NAME STRING CREATE TASK LIFECYCLE APPROVE CREATED 1`"Approve " APPROVE NAME STRING APPROVE TASK LIFECYCLE RESOURCE 10 RESOURCE Modify TASK LIFECYCLE 1`"Modify " MODIFY NAME STRING [(#approved(po))] po PURCHASE ORDER APPROVAL po PROCESS APPROVAL STATUS po 1`"Confirm " CONFIRM NAME STRING APPROVED [istimedout( #timeout(po))] CONFIRM TASK LIFECYCLE po ORDER TIMEOUT po END ORDERING [not (#approved( po))] TERMINATE ORDER PROCESS po input (po); output (); action (addate((#orderid(po)), "Terminate Order Process", ["complete"], calculatetimestamp(), "automated", [])); Fig. 5: CPN Model of a Purchase Order Process A.3 Transforming Enriched Event Log to Classification-ready Case Log The aggregation functions to derive the start time of a case, the end time of a case, the resources involved in a case, as well as the average workload of each resource as defined in Section 3 have also been implemented. For a classification algorithm to work, the response variable must also be properly expressed in a categorical format. Therefore, we have also implemented the getisoverdue function (defined in Section 3). The threshold
18 A Validation with Synthetic Log 17 taskname In [selectallocatetaskguard( resource,taskname,po)] TASK CREATED po ALLOCATE TASK allocateresource(taskname, resource,po) resource po STRING TASK ALLOCATED TASK NAME In [selectstarttaskguard( resource,taskname,po)] 1 1`"Create " taskname po START resource setbusyresource( resource) 10 RESOURCE I/O RESOURCE selectaction(po,taskname) TASK IN PROGRESS [needallocated( resource,taskname, po) andalso po (#isbusy(resource))] taskname COMPLETE TASK resource freeresource(resource,taskname,po) po TASK COMPLETED Out Fig. 6: CPN Model of Purchase Order Manual activity Lifecycle value is set to 30 hours in this case study. Similarly, the involvement or noninvolvment of each resource should be presented as a distinct predictor variable in the classification-ready case log. Therefore, we have also implemented the getisresourceinvolved function defined in Section 3. A snippet of the final classification-ready case log is provided in Table 6 A.4 RCA with Classification Techniques Theoretically, by following the event log transformation process described so far, the data that reside in Table 6 should now be usable for various decision tree
19 18 S. Suriadi, C. Ouyang, W.M.P. van der Aalst, and A.H.M. ter Hofstede caseid activity eventtype timestamp resource 1 Create assign :14: Create start :31: Create complete :22: Approve assign :22: Approve start :22: Approve complete :30: Modify assign :40: Table 4: A snippet of imported MXML log into the eventlog MySQL database timestamp r1... r2 r :39:00 (103:Confirm ),(3:Modify ),... (54:Approve ) (104:Create )... (56:Confirm ),(126:Create ) Table 5: A snippet of the workloadstarted table caseid start end isoverdue isinvolved r1... avgwl r1 avgwl r :38: false :38: false Table 6: A snippet of a classifier-ready case log. learning algorithms. As expected, the data imported data from the classificationready caselog table into the data mining tool (called WEKA [23]) tool can be used to perform many classification analysis, including J.48, LADTree, Simple- Cart, and many others. A representative example of the results of the decision tree learning analysis (using the J.48 decision tree learning algorithm [13] over 10-fold cross validation mode) is shown in Figure 7 (top part). In the beginning, we only used the average resource workload of each resource as the predictor variables. The accuracy of the result obtained is quite high: 86% true positive (TP) rate for on-time cases (that is, the proportion of all on-time cases that were correctly classified as on-time ), and 13% false positive rate for the on-time class (that is, the proportion of all overtime cases which were incorrectly classified as on-time ). Table 8 shows the full accuracy measures of the generated J.48 classification tree. This result may suggest that there were some significant correlation between average workload of resources and the occurence of overtime /long-running cases. Next, we included the information regarding the involvement (or non-involvement) of every resource in the analysis. Nevertheless, the result obtained (through the application of the same J.48 algorithm) is similar to the previous one (see Figure 7 - bottom part). Most importantly, the accuracy of the result is only slightly better. Finally, we excluded the average workload information to see if the information regarding the involvement/non-involvement of resources is enough to explain long running cases. Using the same algorithm, the result obtained was
20 A Validation with Synthetic Log 19 J.48 Classification Tree - CPN Log - only average workload - 10 fold cross validation ===================================================================================== avgwl_r8 <= avgwl_r6 <= avgwl_r10 <= : 1 (3.0) avgwl_r10 > avgwl_r1 <= : 0 (12.0) avgwl_r1 > avgwl_r1 <= : 1 (3.0) avgwl_r1 > avgwl_r10 <= : 1 (4.0/1.0) avgwl_r10 > : 0 (16.0/2.0) avgwl_r6 > : 1 (47.0/6.0) avgwl_r8 > : 0 (44.0) J.48 Classification Tree - CPN Log - average workload + resource involvement 10-fold cross validation ============================================================================ avgwl_r8 <= avgwl_r6 <= resource7 = 0 avgwl_r8 <= : 1 (3.0/1.0) avgwl_r8 > : 0 (17.0) resource7 = 1 resource6 = 0 resource8 = 1: 1 (4.0) resource8 = 0 resource2 = 0 avgwl_r1 <= : 0 (6.0/1.0) avgwl_r1 > : 1 (2.0) resource2 = 1: 1 (2.0) resource6 = 1: 0 (4.0) avgwl_r6 > avgwl_r3 <= : 1 (45.0/4.0) avgwl_r3 > : 0 (2.0) avgwl_r8 > : 0 (44.0) Fig. 7: J.48 Classification Tree - Analysis Results much poorer: 68% TP rate (on average), with false positive rate going up to 37% (on average). Figure 9 shows the generated classification tree and the full accuracy metrics. Based on these analysis results, we may say that workload is the main root cause for explaining long running cases. By showing the details of our validation process, we have thus demonstrated the applicability of our approach in transforming a process mining problem into a problem that can be solved using a relatively rich and matured classification techniques from the field of data mining.
Supporting the Workflow Management System Development Process with YAWL
 Supporting the Workflow Management System Development Process with YAWL R.S. Mans 1, W.M.P. van der Aalst 1 Department of Mathematics and Computer Science, Eindhoven University of Technology, P.O. ox 513,
Supporting the Workflow Management System Development Process with YAWL R.S. Mans 1, W.M.P. van der Aalst 1 Department of Mathematics and Computer Science, Eindhoven University of Technology, P.O. ox 513,
A Software Framework for Risk-Aware Business Process Management
 A Software Framework for Risk-Aware Business Management Raffaele Conforti 1, Marcello La Rosa 1,2, Arthur H.M. ter Hofstede 1,4, Giancarlo Fortino 3, Massimiliano de Leoni 4, Wil M.P. van der Aalst 4,1,
A Software Framework for Risk-Aware Business Management Raffaele Conforti 1, Marcello La Rosa 1,2, Arthur H.M. ter Hofstede 1,4, Giancarlo Fortino 3, Massimiliano de Leoni 4, Wil M.P. van der Aalst 4,1,
Business Process Modeling
 Business Process Concepts Process Mining Kelly Rosa Braghetto Instituto de Matemática e Estatística Universidade de São Paulo kellyrb@ime.usp.br January 30, 2009 1 / 41 Business Process Concepts Process
Business Process Concepts Process Mining Kelly Rosa Braghetto Instituto de Matemática e Estatística Universidade de São Paulo kellyrb@ime.usp.br January 30, 2009 1 / 41 Business Process Concepts Process
Process Modelling from Insurance Event Log
 Process Modelling from Insurance Event Log P.V. Kumaraguru Research scholar, Dr.M.G.R Educational and Research Institute University Chennai- 600 095 India Dr. S.P. Rajagopalan Professor Emeritus, Dr. M.G.R
Process Modelling from Insurance Event Log P.V. Kumaraguru Research scholar, Dr.M.G.R Educational and Research Institute University Chennai- 600 095 India Dr. S.P. Rajagopalan Professor Emeritus, Dr. M.G.R
Decision Mining in Business Processes
 Decision Mining in Business Processes A. Rozinat and W.M.P. van der Aalst Department of Technology Management, Eindhoven University of Technology P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands {a.rozinat,w.m.p.v.d.aalst}@tm.tue.nl
Decision Mining in Business Processes A. Rozinat and W.M.P. van der Aalst Department of Technology Management, Eindhoven University of Technology P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands {a.rozinat,w.m.p.v.d.aalst}@tm.tue.nl
Mercy Health System. St. Louis, MO. Process Mining of Clinical Workflows for Quality and Process Improvement
 Mercy Health System St. Louis, MO Process Mining of Clinical Workflows for Quality and Process Improvement Paul Helmering, Executive Director, Enterprise Architecture Pete Harrison, Data Analyst, Mercy
Mercy Health System St. Louis, MO Process Mining of Clinical Workflows for Quality and Process Improvement Paul Helmering, Executive Director, Enterprise Architecture Pete Harrison, Data Analyst, Mercy
Supporting the BPM lifecycle with FileNet
 Supporting the BPM lifecycle with FileNet Mariska Netjes Hajo A. Reijers Wil. M.P. van der Aalst Outline Introduction Evaluation approach Evaluation of FileNet Conclusions Business Process Management Supporting
Supporting the BPM lifecycle with FileNet Mariska Netjes Hajo A. Reijers Wil. M.P. van der Aalst Outline Introduction Evaluation approach Evaluation of FileNet Conclusions Business Process Management Supporting
Dotted Chart and Control-Flow Analysis for a Loan Application Process
 Dotted Chart and Control-Flow Analysis for a Loan Application Process Thomas Molka 1,2, Wasif Gilani 1 and Xiao-Jun Zeng 2 Business Intelligence Practice, SAP Research, Belfast, UK The University of Manchester,
Dotted Chart and Control-Flow Analysis for a Loan Application Process Thomas Molka 1,2, Wasif Gilani 1 and Xiao-Jun Zeng 2 Business Intelligence Practice, SAP Research, Belfast, UK The University of Manchester,
Towards Cross-Organizational Process Mining in Collections of Process Models and their Executions
 Towards Cross-Organizational Process Mining in Collections of Process Models and their Executions J.C.A.M. Buijs, B.F. van Dongen, W.M.P. van der Aalst Department of Mathematics and Computer Science, Eindhoven
Towards Cross-Organizational Process Mining in Collections of Process Models and their Executions J.C.A.M. Buijs, B.F. van Dongen, W.M.P. van der Aalst Department of Mathematics and Computer Science, Eindhoven
Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach
 Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach Santiago Aguirre, Carlos Parra, and Jorge Alvarado Industrial Engineering Department, Pontificia
Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach Santiago Aguirre, Carlos Parra, and Jorge Alvarado Industrial Engineering Department, Pontificia
An Extensible Framework for Analysing Resource Behaviour Using Event Logs
 An Extensible Framework for Analysing Resource Behaviour Using Event Logs A. Pika 1, M. T. Wynn 1, C. J. Fidge 1, A. H. M. ter Hofstede 1,2, M. Leyer 3, and W. M. P. van der Aalst 2,1 1 Queensland University
An Extensible Framework for Analysing Resource Behaviour Using Event Logs A. Pika 1, M. T. Wynn 1, C. J. Fidge 1, A. H. M. ter Hofstede 1,2, M. Leyer 3, and W. M. P. van der Aalst 2,1 1 Queensland University
Implementing Heuristic Miner for Different Types of Event Logs
 Implementing Heuristic Miner for Different Types of Event Logs Angelina Prima Kurniati 1, GunturPrabawa Kusuma 2, GedeAgungAry Wisudiawan 3 1,3 School of Compuing, Telkom University, Indonesia. 2 School
Implementing Heuristic Miner for Different Types of Event Logs Angelina Prima Kurniati 1, GunturPrabawa Kusuma 2, GedeAgungAry Wisudiawan 3 1,3 School of Compuing, Telkom University, Indonesia. 2 School
Relational XES: Data Management for Process Mining
 Relational XES: Data Management for Process Mining B.F. van Dongen and Sh. Shabani Department of Mathematics and Computer Science, Eindhoven University of Technology, The Netherlands. B.F.v.Dongen, S.Shabaninejad@tue.nl
Relational XES: Data Management for Process Mining B.F. van Dongen and Sh. Shabani Department of Mathematics and Computer Science, Eindhoven University of Technology, The Netherlands. B.F.v.Dongen, S.Shabaninejad@tue.nl
How To Understand The Impact Of A Computer On Organization
 International Journal of Research in Engineering & Technology (IJRET) Vol. 1, Issue 1, June 2013, 1-6 Impact Journals IMPACT OF COMPUTER ON ORGANIZATION A. D. BHOSALE 1 & MARATHE DAGADU MITHARAM 2 1 Department
International Journal of Research in Engineering & Technology (IJRET) Vol. 1, Issue 1, June 2013, 1-6 Impact Journals IMPACT OF COMPUTER ON ORGANIZATION A. D. BHOSALE 1 & MARATHE DAGADU MITHARAM 2 1 Department
Predicting Deadline Transgressions Using Event Logs
 Predicting Deadline Transgressions Using Event Logs Anastasiia Pika 1, Wil M. P. van der Aalst 2,1, Colin J. Fidge 1, Arthur H. M. ter Hofstede 1,2, and Moe T. Wynn 1 1 Queensland University of Technology,
Predicting Deadline Transgressions Using Event Logs Anastasiia Pika 1, Wil M. P. van der Aalst 2,1, Colin J. Fidge 1, Arthur H. M. ter Hofstede 1,2, and Moe T. Wynn 1 1 Queensland University of Technology,
Overview. Evaluation Connectionist and Statistical Language Processing. Test and Validation Set. Training and Test Set
 Overview Evaluation Connectionist and Statistical Language Processing Frank Keller keller@coli.uni-sb.de Computerlinguistik Universität des Saarlandes training set, validation set, test set holdout, stratification
Overview Evaluation Connectionist and Statistical Language Processing Frank Keller keller@coli.uni-sb.de Computerlinguistik Universität des Saarlandes training set, validation set, test set holdout, stratification
Towards a Software Framework for Automatic Business Process Redesign Marwa M.Essam 1, Selma Limam Mansar 2 1
 ACEEE Int. J. on Communication, Vol. 02, No. 03, Nov 2011 Towards a Software Framework for Automatic Business Process Redesign Marwa M.Essam 1, Selma Limam Mansar 2 1 Faculty of Information and Computer
ACEEE Int. J. on Communication, Vol. 02, No. 03, Nov 2011 Towards a Software Framework for Automatic Business Process Redesign Marwa M.Essam 1, Selma Limam Mansar 2 1 Faculty of Information and Computer
Process Mining and Monitoring Processes and Services: Workshop Report
 Process Mining and Monitoring Processes and Services: Workshop Report Wil van der Aalst (editor) Eindhoven University of Technology, P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. w.m.p.v.d.aalst@tm.tue.nl
Process Mining and Monitoring Processes and Services: Workshop Report Wil van der Aalst (editor) Eindhoven University of Technology, P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. w.m.p.v.d.aalst@tm.tue.nl
Experiments in Web Page Classification for Semantic Web
 Experiments in Web Page Classification for Semantic Web Asad Satti, Nick Cercone, Vlado Kešelj Faculty of Computer Science, Dalhousie University E-mail: {rashid,nick,vlado}@cs.dal.ca Abstract We address
Experiments in Web Page Classification for Semantic Web Asad Satti, Nick Cercone, Vlado Kešelj Faculty of Computer Science, Dalhousie University E-mail: {rashid,nick,vlado}@cs.dal.ca Abstract We address
Profiling Event Logs to Configure Risk Indicators for Process Delays
 Profiling Event Logs to Configure Risk Indicators for Process Delays Anastasiia Pika 1, Wil M. P. van der Aalst 2,1, Colin J. Fidge 1, Arthur H. M. ter Hofstede 1,2, and Moe T. Wynn 1 1 Queensland University
Profiling Event Logs to Configure Risk Indicators for Process Delays Anastasiia Pika 1, Wil M. P. van der Aalst 2,1, Colin J. Fidge 1, Arthur H. M. ter Hofstede 1,2, and Moe T. Wynn 1 1 Queensland University
Facilitating Business Process Discovery using Email Analysis
 Facilitating Business Process Discovery using Email Analysis Matin Mavaddat Matin.Mavaddat@live.uwe.ac.uk Stewart Green Stewart.Green Ian Beeson Ian.Beeson Jin Sa Jin.Sa Abstract Extracting business process
Facilitating Business Process Discovery using Email Analysis Matin Mavaddat Matin.Mavaddat@live.uwe.ac.uk Stewart Green Stewart.Green Ian Beeson Ian.Beeson Jin Sa Jin.Sa Abstract Extracting business process
Financial Trading System using Combination of Textual and Numerical Data
 Financial Trading System using Combination of Textual and Numerical Data Shital N. Dange Computer Science Department, Walchand Institute of Rajesh V. Argiddi Assistant Prof. Computer Science Department,
Financial Trading System using Combination of Textual and Numerical Data Shital N. Dange Computer Science Department, Walchand Institute of Rajesh V. Argiddi Assistant Prof. Computer Science Department,
Generation of a Set of Event Logs with Noise
 Generation of a Set of Event Logs with Noise Ivan Shugurov International Laboratory of Process-Aware Information Systems National Research University Higher School of Economics 33 Kirpichnaya Str., Moscow,
Generation of a Set of Event Logs with Noise Ivan Shugurov International Laboratory of Process-Aware Information Systems National Research University Higher School of Economics 33 Kirpichnaya Str., Moscow,
Mining the Software Change Repository of a Legacy Telephony System
 Mining the Software Change Repository of a Legacy Telephony System Jelber Sayyad Shirabad, Timothy C. Lethbridge, Stan Matwin School of Information Technology and Engineering University of Ottawa, Ottawa,
Mining the Software Change Repository of a Legacy Telephony System Jelber Sayyad Shirabad, Timothy C. Lethbridge, Stan Matwin School of Information Technology and Engineering University of Ottawa, Ottawa,
BPIC 2014: Insights from the Analysis of Rabobank Service Desk Processes
 BPIC 2014: Insights from the Analysis of Rabobank Service Desk Processes Bruna Christina P. Brandão, Guilherme Neves Lopes, Pedro Henrique P. Richetti Department of Applied Informatics - Federal University
BPIC 2014: Insights from the Analysis of Rabobank Service Desk Processes Bruna Christina P. Brandão, Guilherme Neves Lopes, Pedro Henrique P. Richetti Department of Applied Informatics - Federal University
Discovering process models from empirical data
 Discovering process models from empirical data Laura Măruşter (l.maruster@tm.tue.nl), Ton Weijters (a.j.m.m.weijters@tm.tue.nl) and Wil van der Aalst (w.m.p.aalst@tm.tue.nl) Eindhoven University of Technology,
Discovering process models from empirical data Laura Măruşter (l.maruster@tm.tue.nl), Ton Weijters (a.j.m.m.weijters@tm.tue.nl) and Wil van der Aalst (w.m.p.aalst@tm.tue.nl) Eindhoven University of Technology,
Online Compliance Monitoring of Service Landscapes
 Online Compliance Monitoring of Service Landscapes J.M.E.M. van der Werf 1 and H.M.W. Verbeek 2 1 Department of Information and Computing Science, Utrecht University, The Netherlands J.M.E.M.vanderWerf@UU.nl
Online Compliance Monitoring of Service Landscapes J.M.E.M. van der Werf 1 and H.M.W. Verbeek 2 1 Department of Information and Computing Science, Utrecht University, The Netherlands J.M.E.M.vanderWerf@UU.nl
Formal Modeling and Analysis by Simulation of Data Paths in Digital Document Printers
 Formal Modeling and Analysis by Simulation of Data Paths in Digital Document Printers Venkatesh Kannan, Wil M.P. van der Aalst, and Marc Voorhoeve Department of Mathematics and Computer Science, Eindhoven
Formal Modeling and Analysis by Simulation of Data Paths in Digital Document Printers Venkatesh Kannan, Wil M.P. van der Aalst, and Marc Voorhoeve Department of Mathematics and Computer Science, Eindhoven
ProM 6 Tutorial. H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.
 ProM 6 Tutorial H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.nl August 2010 1 Introduction This document shows how to use ProM 6 to
ProM 6 Tutorial H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.nl August 2010 1 Introduction This document shows how to use ProM 6 to
Process Aware Host-based Intrusion Detection Model
 Process Aware Host-based Intrusion Detection Model Hanieh Jalali 1, Ahmad Baraani 1 1 University of Isfahan, Computer Department, Isfahan, Iran {jalali, ahmadb}@eng.ui.ac.ir 117 Abstract: Nowadays, many
Process Aware Host-based Intrusion Detection Model Hanieh Jalali 1, Ahmad Baraani 1 1 University of Isfahan, Computer Department, Isfahan, Iran {jalali, ahmadb}@eng.ui.ac.ir 117 Abstract: Nowadays, many
Chapter 6. The stacking ensemble approach
 82 This chapter proposes the stacking ensemble approach for combining different data mining classifiers to get better performance. Other combination techniques like voting, bagging etc are also described
82 This chapter proposes the stacking ensemble approach for combining different data mining classifiers to get better performance. Other combination techniques like voting, bagging etc are also described
Process Mining Online Assessment Data
 Process Mining Online Assessment Data Mykola Pechenizkiy, Nikola Trčka, Ekaterina Vasilyeva, Wil van der Aalst, Paul De Bra {m.pechenizkiy, e.vasilyeva, n.trcka, w.m.p.v.d.aalst}@tue.nl, debra@win.tue.nl
Process Mining Online Assessment Data Mykola Pechenizkiy, Nikola Trčka, Ekaterina Vasilyeva, Wil van der Aalst, Paul De Bra {m.pechenizkiy, e.vasilyeva, n.trcka, w.m.p.v.d.aalst}@tue.nl, debra@win.tue.nl
Analysis of WEKA Data Mining Algorithm REPTree, Simple Cart and RandomTree for Classification of Indian News
 Analysis of WEKA Data Mining Algorithm REPTree, Simple Cart and RandomTree for Classification of Indian News Sushilkumar Kalmegh Associate Professor, Department of Computer Science, Sant Gadge Baba Amravati
Analysis of WEKA Data Mining Algorithm REPTree, Simple Cart and RandomTree for Classification of Indian News Sushilkumar Kalmegh Associate Professor, Department of Computer Science, Sant Gadge Baba Amravati
Supporting the BPM life-cycle with FileNet
 Supporting the BPM life-cycle with FileNet Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven,
Supporting the BPM life-cycle with FileNet Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven,
Separating Compliance Management and Business Process Management
 Separating Compliance Management and Business Process Management Elham Ramezani 1, Dirk Fahland 2, Jan Martijn van der Werf 2, and Peter Mattheis 1 1 Hochschule Furtwangen, Germany (ramezani Peter.Mattheis)@hs-furtwangen.de
Separating Compliance Management and Business Process Management Elham Ramezani 1, Dirk Fahland 2, Jan Martijn van der Werf 2, and Peter Mattheis 1 1 Hochschule Furtwangen, Germany (ramezani Peter.Mattheis)@hs-furtwangen.de
Evaluation & Validation: Credibility: Evaluating what has been learned
 Evaluation & Validation: Credibility: Evaluating what has been learned How predictive is a learned model? How can we evaluate a model Test the model Statistical tests Considerations in evaluating a Model
Evaluation & Validation: Credibility: Evaluating what has been learned How predictive is a learned model? How can we evaluate a model Test the model Statistical tests Considerations in evaluating a Model
ProM Framework Tutorial
 ProM Framework Tutorial Authors: Ana Karla Alves de Medeiros (a.k.medeiros@.tue.nl) A.J.M.M. (Ton) Weijters (a.j.m.m.weijters@tue.nl) Technische Universiteit Eindhoven Eindhoven, The Netherlands February
ProM Framework Tutorial Authors: Ana Karla Alves de Medeiros (a.k.medeiros@.tue.nl) A.J.M.M. (Ton) Weijters (a.j.m.m.weijters@tue.nl) Technische Universiteit Eindhoven Eindhoven, The Netherlands February
Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop
 Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop Sergio Hernández 1, S.J. van Zelst 2, Joaquín Ezpeleta 1, and Wil M.P. van der Aalst 2 1 Department of Computer Science and Systems Engineering
Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop Sergio Hernández 1, S.J. van Zelst 2, Joaquín Ezpeleta 1, and Wil M.P. van der Aalst 2 1 Department of Computer Science and Systems Engineering
FileNet s BPM life-cycle support
 FileNet s BPM life-cycle support Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven, The Netherlands
FileNet s BPM life-cycle support Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven, The Netherlands
Using Process Mining to Bridge the Gap between BI and BPM
 Using Process Mining to Bridge the Gap between BI and BPM Wil van der alst Eindhoven University of Technology, The Netherlands Process mining techniques enable process-centric analytics through automated
Using Process Mining to Bridge the Gap between BI and BPM Wil van der alst Eindhoven University of Technology, The Netherlands Process mining techniques enable process-centric analytics through automated
Summary and Outlook. Business Process Intelligence Course Lecture 8. prof.dr.ir. Wil van der Aalst. www.processmining.org
 Business Process Intelligence Course Lecture 8 Summary and Outlook prof.dr.ir. Wil van der Aalst www.processmining.org Overview Chapter 1 Introduction Part I: Preliminaries Chapter 2 Process Modeling and
Business Process Intelligence Course Lecture 8 Summary and Outlook prof.dr.ir. Wil van der Aalst www.processmining.org Overview Chapter 1 Introduction Part I: Preliminaries Chapter 2 Process Modeling and
Data Quality Mining: Employing Classifiers for Assuring consistent Datasets
 Data Quality Mining: Employing Classifiers for Assuring consistent Datasets Fabian Grüning Carl von Ossietzky Universität Oldenburg, Germany, fabian.gruening@informatik.uni-oldenburg.de Abstract: Independent
Data Quality Mining: Employing Classifiers for Assuring consistent Datasets Fabian Grüning Carl von Ossietzky Universität Oldenburg, Germany, fabian.gruening@informatik.uni-oldenburg.de Abstract: Independent
IDENTIFIC ATION OF SOFTWARE EROSION USING LOGISTIC REGRESSION
 http:// IDENTIFIC ATION OF SOFTWARE EROSION USING LOGISTIC REGRESSION Harinder Kaur 1, Raveen Bajwa 2 1 PG Student., CSE., Baba Banda Singh Bahadur Engg. College, Fatehgarh Sahib, (India) 2 Asstt. Prof.,
http:// IDENTIFIC ATION OF SOFTWARE EROSION USING LOGISTIC REGRESSION Harinder Kaur 1, Raveen Bajwa 2 1 PG Student., CSE., Baba Banda Singh Bahadur Engg. College, Fatehgarh Sahib, (India) 2 Asstt. Prof.,
Analysis of Service Level Agreements using Process Mining techniques
 Analysis of Service Level Agreements using Process Mining techniques CHRISTIAN MAGER University of Applied Sciences Wuerzburg-Schweinfurt Process Mining offers powerful methods to extract knowledge from
Analysis of Service Level Agreements using Process Mining techniques CHRISTIAN MAGER University of Applied Sciences Wuerzburg-Schweinfurt Process Mining offers powerful methods to extract knowledge from
Customer Classification And Prediction Based On Data Mining Technique
 Customer Classification And Prediction Based On Data Mining Technique Ms. Neethu Baby 1, Mrs. Priyanka L.T 2 1 M.E CSE, Sri Shakthi Institute of Engineering and Technology, Coimbatore 2 Assistant Professor
Customer Classification And Prediction Based On Data Mining Technique Ms. Neethu Baby 1, Mrs. Priyanka L.T 2 1 M.E CSE, Sri Shakthi Institute of Engineering and Technology, Coimbatore 2 Assistant Professor
FRAUD DETECTION IN ELECTRIC POWER DISTRIBUTION NETWORKS USING AN ANN-BASED KNOWLEDGE-DISCOVERY PROCESS
 FRAUD DETECTION IN ELECTRIC POWER DISTRIBUTION NETWORKS USING AN ANN-BASED KNOWLEDGE-DISCOVERY PROCESS Breno C. Costa, Bruno. L. A. Alberto, André M. Portela, W. Maduro, Esdras O. Eler PDITec, Belo Horizonte,
FRAUD DETECTION IN ELECTRIC POWER DISTRIBUTION NETWORKS USING AN ANN-BASED KNOWLEDGE-DISCOVERY PROCESS Breno C. Costa, Bruno. L. A. Alberto, André M. Portela, W. Maduro, Esdras O. Eler PDITec, Belo Horizonte,
Rabobank: Incident and change process analysis
 Rabobank: Incident and change process analysis Michael Arias 1, Mauricio Arriagada 1, Eric Rojas 1, Cecilia Sant-Pierre 1, Marcos Sepúlveda 1 1 Pontificia Universidad Católica de Chile, Av. Vicuña Mackenna
Rabobank: Incident and change process analysis Michael Arias 1, Mauricio Arriagada 1, Eric Rojas 1, Cecilia Sant-Pierre 1, Marcos Sepúlveda 1 1 Pontificia Universidad Católica de Chile, Av. Vicuña Mackenna
A Meta-model of Business Interaction for Assisting Intelligent Workflow Systems
 A Meta-model of Business Interaction for Assisting Intelligent Workflow Systems Areti Manataki and Yun-Heh Chen-Burger Centre for Intelligent Systems and their Applications, School of Informatics, The
A Meta-model of Business Interaction for Assisting Intelligent Workflow Systems Areti Manataki and Yun-Heh Chen-Burger Centre for Intelligent Systems and their Applications, School of Informatics, The
Performance Measures in Data Mining
 Performance Measures in Data Mining Common Performance Measures used in Data Mining and Machine Learning Approaches L. Richter J.M. Cejuela Department of Computer Science Technische Universität München
Performance Measures in Data Mining Common Performance Measures used in Data Mining and Machine Learning Approaches L. Richter J.M. Cejuela Department of Computer Science Technische Universität München
Classification of Titanic Passenger Data and Chances of Surviving the Disaster Data Mining with Weka and Kaggle Competition Data
 Proceedings of Student-Faculty Research Day, CSIS, Pace University, May 2 nd, 2014 Classification of Titanic Passenger Data and Chances of Surviving the Disaster Data Mining with Weka and Kaggle Competition
Proceedings of Student-Faculty Research Day, CSIS, Pace University, May 2 nd, 2014 Classification of Titanic Passenger Data and Chances of Surviving the Disaster Data Mining with Weka and Kaggle Competition
Model Discovery from Motor Claim Process Using Process Mining Technique
 International Journal of Scientific and Research Publications, Volume 3, Issue 1, January 2013 1 Model Discovery from Motor Claim Process Using Process Mining Technique P.V.Kumaraguru *, Dr.S.P.Rajagopalan
International Journal of Scientific and Research Publications, Volume 3, Issue 1, January 2013 1 Model Discovery from Motor Claim Process Using Process Mining Technique P.V.Kumaraguru *, Dr.S.P.Rajagopalan
Merging Event Logs with Many to Many Relationships
 Merging vent Logs with Many to Many Relationships Lihi Raichelson and Pnina Soffer Department of Information Systems, University of Haifa, Haifa 31905, Israel LihiRaOs@gmail.com, Spnina@is.haifa.ac.il
Merging vent Logs with Many to Many Relationships Lihi Raichelson and Pnina Soffer Department of Information Systems, University of Haifa, Haifa 31905, Israel LihiRaOs@gmail.com, Spnina@is.haifa.ac.il
DATA MINING, DIRTY DATA, AND COSTS (Research-in-Progress)
 DATA MINING, DIRTY DATA, AND COSTS (Research-in-Progress) Leo Pipino University of Massachusetts Lowell Leo_Pipino@UML.edu David Kopcso Babson College Kopcso@Babson.edu Abstract: A series of simulations
DATA MINING, DIRTY DATA, AND COSTS (Research-in-Progress) Leo Pipino University of Massachusetts Lowell Leo_Pipino@UML.edu David Kopcso Babson College Kopcso@Babson.edu Abstract: A series of simulations
An Ontology-based Framework for Enriching Event-log Data
 An Ontology-based Framework for Enriching Event-log Data Thanh Tran Thi Kim, Hannes Werthner e-commerce group Institute of Software Technology and Interactive Systems, Vienna, Austria Email: kimthanh@ec.tuwien.ac.at,
An Ontology-based Framework for Enriching Event-log Data Thanh Tran Thi Kim, Hannes Werthner e-commerce group Institute of Software Technology and Interactive Systems, Vienna, Austria Email: kimthanh@ec.tuwien.ac.at,
SIMULATION STANDARD FOR BUSINESS PROCESS MANAGEMENT. 15 New England Executive Park The Oaks, Clews Road
 Proceedings of the 2011 Winter Simulation Conference S. Jain, R.R. Creasey, J. Himmelspach, K.P. White, and M. Fu, eds. SIMULATION STANDARD FOR BUSINESS PROCESS MANAGEMENT John Januszczak Geoff Hook Meta
Proceedings of the 2011 Winter Simulation Conference S. Jain, R.R. Creasey, J. Himmelspach, K.P. White, and M. Fu, eds. SIMULATION STANDARD FOR BUSINESS PROCESS MANAGEMENT John Januszczak Geoff Hook Meta
Impact of Boolean factorization as preprocessing methods for classification of Boolean data
 Impact of Boolean factorization as preprocessing methods for classification of Boolean data Radim Belohlavek, Jan Outrata, Martin Trnecka Data Analysis and Modeling Lab (DAMOL) Dept. Computer Science,
Impact of Boolean factorization as preprocessing methods for classification of Boolean data Radim Belohlavek, Jan Outrata, Martin Trnecka Data Analysis and Modeling Lab (DAMOL) Dept. Computer Science,
Process-Family-Points
 Process-Family-Points Sebastian Kiebusch 1, Bogdan Franczyk 1, and Andreas Speck 2 1 University of Leipzig, Faculty of Economics and Management, Information Systems Institute, Germany kiebusch@wifa.uni-leipzig.de,
Process-Family-Points Sebastian Kiebusch 1, Bogdan Franczyk 1, and Andreas Speck 2 1 University of Leipzig, Faculty of Economics and Management, Information Systems Institute, Germany kiebusch@wifa.uni-leipzig.de,
Eventifier: Extracting Process Execution Logs from Operational Databases
 Eventifier: Extracting Process Execution Logs from Operational Databases Carlos Rodríguez 1, Robert Engel 2, Galena Kostoska 1, Florian Daniel 1, Fabio Casati 1, and Marco Aimar 3 1 University of Trento,
Eventifier: Extracting Process Execution Logs from Operational Databases Carlos Rodríguez 1, Robert Engel 2, Galena Kostoska 1, Florian Daniel 1, Fabio Casati 1, and Marco Aimar 3 1 University of Trento,
Process Mining-based Understanding and Analysis of Volvo IT s Incident and Problem Management Processes The BPI Challenge 2013
 Process Mining-based Understanding and Analysis of Volvo IT s Incident and Problem Management Processes The BPI Challenge 2013 Chang Jae Kang 2, Young Sik Kang *,1, Yeong Shin Lee 1, Seonkyu Noh, Hyeong
Process Mining-based Understanding and Analysis of Volvo IT s Incident and Problem Management Processes The BPI Challenge 2013 Chang Jae Kang 2, Young Sik Kang *,1, Yeong Shin Lee 1, Seonkyu Noh, Hyeong
Predictive Modeling for Collections of Accounts Receivable Sai Zeng IBM T.J. Watson Research Center Hawthorne, NY, 10523. Abstract
 Paper Submission for ACM SIGKDD Workshop on Domain Driven Data Mining (DDDM2007) Predictive Modeling for Collections of Accounts Receivable Sai Zeng saizeng@us.ibm.com Prem Melville Yorktown Heights, NY,
Paper Submission for ACM SIGKDD Workshop on Domain Driven Data Mining (DDDM2007) Predictive Modeling for Collections of Accounts Receivable Sai Zeng saizeng@us.ibm.com Prem Melville Yorktown Heights, NY,
CPN Tools 4: A Process Modeling Tool Combining Declarative and Imperative Paradigms
 CPN Tools 4: A Process Modeling Tool Combining Declarative and Imperative Paradigms Michael Westergaard 1,2 and Tijs Slaats 3,4 1 Department of Mathematics and Computer Science, Eindhoven University of
CPN Tools 4: A Process Modeling Tool Combining Declarative and Imperative Paradigms Michael Westergaard 1,2 and Tijs Slaats 3,4 1 Department of Mathematics and Computer Science, Eindhoven University of
EMiT: A process mining tool
 EMiT: A process mining tool B.F. van Dongen and W.M.P. van der Aalst Department of Technology Management, Eindhoven University of Technology P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands. b.f.v.dongen@tue.nl
EMiT: A process mining tool B.F. van Dongen and W.M.P. van der Aalst Department of Technology Management, Eindhoven University of Technology P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands. b.f.v.dongen@tue.nl
CHAPTER 1 INTRODUCTION
 CHAPTER 1 INTRODUCTION 1.1 Research Motivation In today s modern digital environment with or without our notice we are leaving our digital footprints in various data repositories through our daily activities,
CHAPTER 1 INTRODUCTION 1.1 Research Motivation In today s modern digital environment with or without our notice we are leaving our digital footprints in various data repositories through our daily activities,
PLG: a Framework for the Generation of Business Process Models and their Execution Logs
 PLG: a Framework for the Generation of Business Process Models and their Execution Logs Andrea Burattin and Alessandro Sperduti Department of Pure and Applied Mathematics University of Padua, Italy {burattin,sperduti}@math.unipd.it
PLG: a Framework for the Generation of Business Process Models and their Execution Logs Andrea Burattin and Alessandro Sperduti Department of Pure and Applied Mathematics University of Padua, Italy {burattin,sperduti}@math.unipd.it
The Optimality of Naive Bayes
 The Optimality of Naive Bayes Harry Zhang Faculty of Computer Science University of New Brunswick Fredericton, New Brunswick, Canada email: hzhang@unbca E3B 5A3 Abstract Naive Bayes is one of the most
The Optimality of Naive Bayes Harry Zhang Faculty of Computer Science University of New Brunswick Fredericton, New Brunswick, Canada email: hzhang@unbca E3B 5A3 Abstract Naive Bayes is one of the most
IDENTIFYING BANK FRAUDS USING CRISP-DM AND DECISION TREES
 IDENTIFYING BANK FRAUDS USING CRISP-DM AND DECISION TREES Bruno Carneiro da Rocha 1,2 and Rafael Timóteo de Sousa Júnior 2 1 Bank of Brazil, Brasília-DF, Brazil brunorocha_33@hotmail.com 2 Network Engineering
IDENTIFYING BANK FRAUDS USING CRISP-DM AND DECISION TREES Bruno Carneiro da Rocha 1,2 and Rafael Timóteo de Sousa Júnior 2 1 Bank of Brazil, Brasília-DF, Brazil brunorocha_33@hotmail.com 2 Network Engineering
Predicting the Risk of Heart Attacks using Neural Network and Decision Tree
 Predicting the Risk of Heart Attacks using Neural Network and Decision Tree S.Florence 1, N.G.Bhuvaneswari Amma 2, G.Annapoorani 3, K.Malathi 4 PG Scholar, Indian Institute of Information Technology, Srirangam,
Predicting the Risk of Heart Attacks using Neural Network and Decision Tree S.Florence 1, N.G.Bhuvaneswari Amma 2, G.Annapoorani 3, K.Malathi 4 PG Scholar, Indian Institute of Information Technology, Srirangam,
EDIminer: A Toolset for Process Mining from EDI Messages
 EDIminer: A Toolset for Process Mining from EDI Messages Robert Engel 1, R. P. Jagadeesh Chandra Bose 2, Christian Pichler 1, Marco Zapletal 1, and Hannes Werthner 1 1 Vienna University of Technology,
EDIminer: A Toolset for Process Mining from EDI Messages Robert Engel 1, R. P. Jagadeesh Chandra Bose 2, Christian Pichler 1, Marco Zapletal 1, and Hannes Werthner 1 1 Vienna University of Technology,
Supply chain management by means of FLM-rules
 Supply chain management by means of FLM-rules Nicolas Le Normand, Julien Boissière, Nicolas Méger, Lionel Valet LISTIC Laboratory - Polytech Savoie Université de Savoie B.P. 80439 F-74944 Annecy-Le-Vieux,
Supply chain management by means of FLM-rules Nicolas Le Normand, Julien Boissière, Nicolas Méger, Lionel Valet LISTIC Laboratory - Polytech Savoie Université de Savoie B.P. 80439 F-74944 Annecy-Le-Vieux,
BUsiness process mining, or process mining in a short
 , July 2-4, 2014, London, U.K. A Process Mining Approach in Software Development and Testing Process: A Case Study Rabia Saylam, Ozgur Koray Sahingoz Abstract Process mining is a relatively new and emerging
, July 2-4, 2014, London, U.K. A Process Mining Approach in Software Development and Testing Process: A Case Study Rabia Saylam, Ozgur Koray Sahingoz Abstract Process mining is a relatively new and emerging
Preprocessing and Content/Navigational Pages Identification as Premises for an Extended Web Usage Mining Model Development
 Informatica Economică vol. 13, no. 4/2009 168 Preprocessing and Content/Navigational Pages Identification as Premises for an Extended Web Usage Mining Model Development Daniel MICAN, Dan-Andrei SITAR-TAUT
Informatica Economică vol. 13, no. 4/2009 168 Preprocessing and Content/Navigational Pages Identification as Premises for an Extended Web Usage Mining Model Development Daniel MICAN, Dan-Andrei SITAR-TAUT
BPMN PATTERNS USED IN MANAGEMENT INFORMATION SYSTEMS
 BPMN PATTERNS USED IN MANAGEMENT INFORMATION SYSTEMS Gabriel Cozgarea 1 Adrian Cozgarea 2 ABSTRACT: Business Process Modeling Notation (BPMN) is a graphical standard in which controls and activities can
BPMN PATTERNS USED IN MANAGEMENT INFORMATION SYSTEMS Gabriel Cozgarea 1 Adrian Cozgarea 2 ABSTRACT: Business Process Modeling Notation (BPMN) is a graphical standard in which controls and activities can
Application of Process Mining in Healthcare A Case Study in a Dutch Hospital
 Application of Process Mining in Healthcare A Case Study in a Dutch Hospital R.S. Mans 1, M.H. Schonenberg 1, M. Song 1, W.M.P. van der Aalst 1, and P.J.M. Bakker 2 1 Department of Information Systems
Application of Process Mining in Healthcare A Case Study in a Dutch Hospital R.S. Mans 1, M.H. Schonenberg 1, M. Song 1, W.M.P. van der Aalst 1, and P.J.M. Bakker 2 1 Department of Information Systems
Activity Mining for Discovering Software Process Models
 Activity Mining for Discovering Software Process Models Ekkart Kindler, Vladimir Rubin, Wilhelm Schäfer Software Engineering Group, University of Paderborn, Germany [kindler, vroubine, wilhelm]@uni-paderborn.de
Activity Mining for Discovering Software Process Models Ekkart Kindler, Vladimir Rubin, Wilhelm Schäfer Software Engineering Group, University of Paderborn, Germany [kindler, vroubine, wilhelm]@uni-paderborn.de
Process Mining Tools: A Comparative Analysis
 EINDHOVEN UNIVERSITY OF TECHNOLOGY Department of Mathematics and Computer Science Process Mining Tools: A Comparative Analysis Irina-Maria Ailenei in partial fulfillment of the requirements for the degree
EINDHOVEN UNIVERSITY OF TECHNOLOGY Department of Mathematics and Computer Science Process Mining Tools: A Comparative Analysis Irina-Maria Ailenei in partial fulfillment of the requirements for the degree
VCU-TSA at Semeval-2016 Task 4: Sentiment Analysis in Twitter
 VCU-TSA at Semeval-2016 Task 4: Sentiment Analysis in Twitter Gerard Briones and Kasun Amarasinghe and Bridget T. McInnes, PhD. Department of Computer Science Virginia Commonwealth University Richmond,
VCU-TSA at Semeval-2016 Task 4: Sentiment Analysis in Twitter Gerard Briones and Kasun Amarasinghe and Bridget T. McInnes, PhD. Department of Computer Science Virginia Commonwealth University Richmond,
Advanced analytics at your hands
 2.3 Advanced analytics at your hands Neural Designer is the most powerful predictive analytics software. It uses innovative neural networks techniques to provide data scientists with results in a way previously
2.3 Advanced analytics at your hands Neural Designer is the most powerful predictive analytics software. It uses innovative neural networks techniques to provide data scientists with results in a way previously
Towards an Evaluation Framework for Process Mining Algorithms
 Towards an Evaluation Framework for Process Mining Algorithms A. Rozinat, A.K. Alves de Medeiros, C.W. Günther, A.J.M.M. Weijters, and W.M.P. van der Aalst Eindhoven University of Technology P.O. Box 513,
Towards an Evaluation Framework for Process Mining Algorithms A. Rozinat, A.K. Alves de Medeiros, C.W. Günther, A.J.M.M. Weijters, and W.M.P. van der Aalst Eindhoven University of Technology P.O. Box 513,
Keywords Data mining, Classification Algorithm, Decision tree, J48, Random forest, Random tree, LMT, WEKA 3.7. Fig.1. Data mining techniques.
 International Journal of Emerging Research in Management &Technology Research Article October 2015 Comparative Study of Various Decision Tree Classification Algorithm Using WEKA Purva Sewaiwar, Kamal Kant
International Journal of Emerging Research in Management &Technology Research Article October 2015 Comparative Study of Various Decision Tree Classification Algorithm Using WEKA Purva Sewaiwar, Kamal Kant
DECISION TREE INDUCTION FOR FINANCIAL FRAUD DETECTION USING ENSEMBLE LEARNING TECHNIQUES
 DECISION TREE INDUCTION FOR FINANCIAL FRAUD DETECTION USING ENSEMBLE LEARNING TECHNIQUES Vijayalakshmi Mahanra Rao 1, Yashwant Prasad Singh 2 Multimedia University, Cyberjaya, MALAYSIA 1 lakshmi.mahanra@gmail.com
DECISION TREE INDUCTION FOR FINANCIAL FRAUD DETECTION USING ENSEMBLE LEARNING TECHNIQUES Vijayalakshmi Mahanra Rao 1, Yashwant Prasad Singh 2 Multimedia University, Cyberjaya, MALAYSIA 1 lakshmi.mahanra@gmail.com
DATA MINING TECHNOLOGY. Keywords: data mining, data warehouse, knowledge discovery, OLAP, OLAM.
 DATA MINING TECHNOLOGY Georgiana Marin 1 Abstract In terms of data processing, classical statistical models are restrictive; it requires hypotheses, the knowledge and experience of specialists, equations,
DATA MINING TECHNOLOGY Georgiana Marin 1 Abstract In terms of data processing, classical statistical models are restrictive; it requires hypotheses, the knowledge and experience of specialists, equations,
EFFECTIVE CONSTRUCTIVE MODELS OF IMPLICIT SELECTION IN BUSINESS PROCESSES. Nataliya Golyan, Vera Golyan, Olga Kalynychenko
 380 International Journal Information Theories and Applications, Vol. 18, Number 4, 2011 EFFECTIVE CONSTRUCTIVE MODELS OF IMPLICIT SELECTION IN BUSINESS PROCESSES Nataliya Golyan, Vera Golyan, Olga Kalynychenko
380 International Journal Information Theories and Applications, Vol. 18, Number 4, 2011 EFFECTIVE CONSTRUCTIVE MODELS OF IMPLICIT SELECTION IN BUSINESS PROCESSES Nataliya Golyan, Vera Golyan, Olga Kalynychenko
Conformance Checking of Interacting Processes With Overlapping Instances
 Conformance Checking of Interacting Processes With Overlapping Instances Dirk Fahland, Massimiliano de Leoni, Boudewijn F. van Dongen, and Wil M.P. van der Aalst Eindhoven University of Technology, The
Conformance Checking of Interacting Processes With Overlapping Instances Dirk Fahland, Massimiliano de Leoni, Boudewijn F. van Dongen, and Wil M.P. van der Aalst Eindhoven University of Technology, The
ProM 6 Exercises. J.C.A.M. (Joos) Buijs and J.J.C.L. (Jan) Vogelaar {j.c.a.m.buijs,j.j.c.l.vogelaar}@tue.nl. August 2010
 ProM 6 Exercises J.C.A.M. (Joos) Buijs and J.J.C.L. (Jan) Vogelaar {j.c.a.m.buijs,j.j.c.l.vogelaar}@tue.nl August 2010 The exercises provided in this section are meant to become more familiar with ProM
ProM 6 Exercises J.C.A.M. (Joos) Buijs and J.J.C.L. (Jan) Vogelaar {j.c.a.m.buijs,j.j.c.l.vogelaar}@tue.nl August 2010 The exercises provided in this section are meant to become more familiar with ProM
Analyzing a TCP/IP-Protocol with Process Mining Techniques
 Analyzing a TCP/IP-Protocol with Process Mining Techniques Christian Wakup 1 and Jörg Desel 2 1 rubecon information technologies GmbH, Germany 2 Fakultät für Mathematik und Informatik, FernUniversität
Analyzing a TCP/IP-Protocol with Process Mining Techniques Christian Wakup 1 and Jörg Desel 2 1 rubecon information technologies GmbH, Germany 2 Fakultät für Mathematik und Informatik, FernUniversität
Example: Credit card default, we may be more interested in predicting the probabilty of a default than classifying individuals as default or not.
 Statistical Learning: Chapter 4 Classification 4.1 Introduction Supervised learning with a categorical (Qualitative) response Notation: - Feature vector X, - qualitative response Y, taking values in C
Statistical Learning: Chapter 4 Classification 4.1 Introduction Supervised learning with a categorical (Qualitative) response Notation: - Feature vector X, - qualitative response Y, taking values in C
Data Mining Application in Direct Marketing: Identifying Hot Prospects for Banking Product
 Data Mining Application in Direct Marketing: Identifying Hot Prospects for Banking Product Sagarika Prusty Web Data Mining (ECT 584),Spring 2013 DePaul University,Chicago sagarikaprusty@gmail.com Keywords:
Data Mining Application in Direct Marketing: Identifying Hot Prospects for Banking Product Sagarika Prusty Web Data Mining (ECT 584),Spring 2013 DePaul University,Chicago sagarikaprusty@gmail.com Keywords:
Process Mining: Using CPN Tools to Create Test Logs for Mining Algorithms
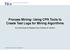 Mining: Using CPN Tools to Create Test Logs for Mining Algorithms Ana Karla Alves de Medeiros and Christian W. Günther 2 Outline Introduction Mining The need for synthetic logs MXML format Using the Logging
Mining: Using CPN Tools to Create Test Logs for Mining Algorithms Ana Karla Alves de Medeiros and Christian W. Günther 2 Outline Introduction Mining The need for synthetic logs MXML format Using the Logging
COMP3420: Advanced Databases and Data Mining. Classification and prediction: Introduction and Decision Tree Induction
 COMP3420: Advanced Databases and Data Mining Classification and prediction: Introduction and Decision Tree Induction Lecture outline Classification versus prediction Classification A two step process Supervised
COMP3420: Advanced Databases and Data Mining Classification and prediction: Introduction and Decision Tree Induction Lecture outline Classification versus prediction Classification A two step process Supervised
Lluis Belanche + Alfredo Vellido. Intelligent Data Analysis and Data Mining. Data Analysis and Knowledge Discovery
 Lluis Belanche + Alfredo Vellido Intelligent Data Analysis and Data Mining or Data Analysis and Knowledge Discovery a.k.a. Data Mining II An insider s view Geoff Holmes: WEKA founder Process Mining
Lluis Belanche + Alfredo Vellido Intelligent Data Analysis and Data Mining or Data Analysis and Knowledge Discovery a.k.a. Data Mining II An insider s view Geoff Holmes: WEKA founder Process Mining
Extension of Decision Tree Algorithm for Stream Data Mining Using Real Data
 Fifth International Workshop on Computational Intelligence & Applications IEEE SMC Hiroshima Chapter, Hiroshima University, Japan, November 10, 11 & 12, 2009 Extension of Decision Tree Algorithm for Stream
Fifth International Workshop on Computational Intelligence & Applications IEEE SMC Hiroshima Chapter, Hiroshima University, Japan, November 10, 11 & 12, 2009 Extension of Decision Tree Algorithm for Stream
Feature. Applications of Business Process Analytics and Mining for Internal Control. World
 Feature Filip Caron is a doctoral researcher in the Department of Decision Sciences and Information Management, Information Systems Group, at the Katholieke Universiteit Leuven (Flanders, Belgium). Jan
Feature Filip Caron is a doctoral researcher in the Department of Decision Sciences and Information Management, Information Systems Group, at the Katholieke Universiteit Leuven (Flanders, Belgium). Jan
Performance Analysis of Naive Bayes and J48 Classification Algorithm for Data Classification
 Performance Analysis of Naive Bayes and J48 Classification Algorithm for Data Classification Tina R. Patil, Mrs. S. S. Sherekar Sant Gadgebaba Amravati University, Amravati tnpatil2@gmail.com, ss_sherekar@rediffmail.com
Performance Analysis of Naive Bayes and J48 Classification Algorithm for Data Classification Tina R. Patil, Mrs. S. S. Sherekar Sant Gadgebaba Amravati University, Amravati tnpatil2@gmail.com, ss_sherekar@rediffmail.com
Process Mining Using BPMN: Relating Event Logs and Process Models
 Noname manuscript No. (will be inserted by the editor) Process Mining Using BPMN: Relating Event Logs and Process Models Anna A. Kalenkova W. M. P. van der Aalst Irina A. Lomazova Vladimir A. Rubin Received:
Noname manuscript No. (will be inserted by the editor) Process Mining Using BPMN: Relating Event Logs and Process Models Anna A. Kalenkova W. M. P. van der Aalst Irina A. Lomazova Vladimir A. Rubin Received:
Method of Fault Detection in Cloud Computing Systems
 , pp.205-212 http://dx.doi.org/10.14257/ijgdc.2014.7.3.21 Method of Fault Detection in Cloud Computing Systems Ying Jiang, Jie Huang, Jiaman Ding and Yingli Liu Yunnan Key Lab of Computer Technology Application,
, pp.205-212 http://dx.doi.org/10.14257/ijgdc.2014.7.3.21 Method of Fault Detection in Cloud Computing Systems Ying Jiang, Jie Huang, Jiaman Ding and Yingli Liu Yunnan Key Lab of Computer Technology Application,
Comparative Analysis of Classification Algorithms on Different Datasets using WEKA
 Volume 54 No13, September 2012 Comparative Analysis of Classification Algorithms on Different Datasets using WEKA Rohit Arora MTech CSE Deptt Hindu College of Engineering Sonepat, Haryana, India Suman
Volume 54 No13, September 2012 Comparative Analysis of Classification Algorithms on Different Datasets using WEKA Rohit Arora MTech CSE Deptt Hindu College of Engineering Sonepat, Haryana, India Suman
Process Mining. ^J Springer. Discovery, Conformance and Enhancement of Business Processes. Wil M.R van der Aalst Q UNIVERS1TAT.
 Wil M.R van der Aalst Process Mining Discovery, Conformance and Enhancement of Business Processes Q UNIVERS1TAT m LIECHTENSTEIN Bibliothek ^J Springer Contents 1 Introduction I 1.1 Data Explosion I 1.2
Wil M.R van der Aalst Process Mining Discovery, Conformance and Enhancement of Business Processes Q UNIVERS1TAT m LIECHTENSTEIN Bibliothek ^J Springer Contents 1 Introduction I 1.1 Data Explosion I 1.2
Workflow Automation and Management Services in Web 2.0: An Object-Based Approach to Distributed Workflow Enactment
 Workflow Automation and Management Services in Web 2.0: An Object-Based Approach to Distributed Workflow Enactment Peter Y. Wu wu@rmu.edu Department of Computer & Information Systems Robert Morris University
Workflow Automation and Management Services in Web 2.0: An Object-Based Approach to Distributed Workflow Enactment Peter Y. Wu wu@rmu.edu Department of Computer & Information Systems Robert Morris University
Another Look at Sensitivity of Bayesian Networks to Imprecise Probabilities
 Another Look at Sensitivity of Bayesian Networks to Imprecise Probabilities Oscar Kipersztok Mathematics and Computing Technology Phantom Works, The Boeing Company P.O.Box 3707, MC: 7L-44 Seattle, WA 98124
Another Look at Sensitivity of Bayesian Networks to Imprecise Probabilities Oscar Kipersztok Mathematics and Computing Technology Phantom Works, The Boeing Company P.O.Box 3707, MC: 7L-44 Seattle, WA 98124
Open-Source Machine Learning: R Meets Weka
 Open-Source Machine Learning: R Meets Weka Kurt Hornik Christian Buchta Achim Zeileis Weka? Weka is not only a flightless endemic bird of New Zealand (Gallirallus australis, picture from Wekapedia) but
Open-Source Machine Learning: R Meets Weka Kurt Hornik Christian Buchta Achim Zeileis Weka? Weka is not only a flightless endemic bird of New Zealand (Gallirallus australis, picture from Wekapedia) but
