Security Vulnerability Assessment
|
|
|
- Miles Chapman
- 8 years ago
- Views:
Transcription
1 Security Vulnerability Assessment Deter, Detect, Delay, Respond the elements for minimizing your operational risk. A detailed SVA assists you to understand how best to do so.
2 Security Vulnerability Assessment The SVA methodology, when combined with our team of seasoned professionals, is the best risk-reduction approach available. In today s business environment, any impact to operations poses wide ranging consequences. A proper SVA will help companies understand their vulnerabilities and allow them to apply critical resources to help mitigate those risks. OSSI is pleased to offer a package service providing Security Vulnerability Assessments and related consultancy services to clients around the world. Our trained professionals have the experience and knowledge to assist in helping our clients better understand and protect against facility and process risks, as part of their organizational safety management system.
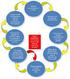
3 The Security Vulnerability Assessment A Security Vulnerability Assessment ( SVA ) is the identification and analysis of facility and/or operational vulnerabilities and threats. A systematic process, it analyses high-risk scenarios, characterizes the threat, and attempts to reduce the risk through the application of effective countermeasures. A quality SVA will determine the highest vulnerabilities, how successfully an adversary could exploit these vulnerabilities, and the resulting damage due to an attack. The client can then utilize this to make a determination on how best to protect against these attacks given the risk/reward scenarios. Types of Facilities OSSI Covers OSSI can provide SVAs for our clients across many industries. Whether your company owns oil refineries in Africa, mining operations in South America, construction projects in Afghanistan or terminal operations in Europe, OSSI s tailored SVA teams are uniquely qualified to assess and identify potential vulnerabilities. Based on that assessment, we will then suggest the best approach to mitigate against these scenarios. SVA Team Composition We have a team of trained SVA assessors with experience on military, government, and commercial facilities in high-threat areas throughout the world. Our team members have experience in military, maritime security, terminal and refining operations, construction engineering, and logistics activities. Methodology Step 1 Asset Characterization Step 2 Threat Assessment Step 3 Vulnerability Analysis Step 4 Risk Assessment Step 5 Countermeasures Analysis Upon completion of the SVA, OSSI will continue to assist the client with integrating new countermeasures into their overall operational processes. 2
4 Security Vulnerability Assessment Background Complete risk avoidance, while preferred, is very rarely achievable. We simply cannot establish operations within a bubble and expect to function properly. It is even more difficult when taking into account the complex operations and unique locations of our clients. As such, facilities, personnel, and operations are vulnerable to any number of threats, including geo-political tensions, environmental hazards, criminal activity, and terrorism. Today s business environment demands that leaders have a clear understanding of their operational environment and take the necessary steps to minimize any damage that might occur. The practice of identifying physical vulnerabilities is not new. Security managers have long placed emphasis on facility physical security while targeting perimeter security, material/equipment pilferage, equipment functionality, etc. But vulnerabilities are not just confined to the physical facilities and operational processes. With the increased reliance on automated equipment, IT professionals have diligently worked to keep systems fully operational and free from unauthorized access. HSE professionals continue to strive to foster safe work environments benefiting both their employees and the local communities. Given these numerous threats to companies today, the SVA methodology is focused on bringing all stakeholders together and forming a multidisciplinary team to identify and assess the operational environment. In general, this team identifies critical assets (human, physical, intellectual property, etc.), assigns a rank to each based on the risk potential verses consequences, and makes recommendations on how best to minimize against these consequences. Applications At the most basic level, any good risk assessment will attempt to minimize risk through deterrence, detection, delay, and response. The SVA takes these strategies and looks to apply them in a way that best utilizes the available resources. The SVA is designed with a methodology that can be tailored to numerous industries and specific segments within those industries. With respect to the petroleum and gas industry, OSSI can provide assessments for marine terminal operations, refineries, tank farms, pipelines, exploratory operations, transportation, and construction. 3
5 Assessment Team Our assessment team consists of seasoned security and industry specialists. The typical team will be composed of the following: 1. Team Leader has a clear understanding of the SVA approach and methodology with experience from performing many assessments across a number of industries. 2. Security Specialist fully knowledgeable on proper facility security methods, systems, and procedures. Typically will have a military/anti-terrorism background with unique knowledge of terrorism, weapons, insurgency/ guerilla warfare, and countermeasures. Able to utilize current industry practices to decrease threat risks and minimize damage. 3. Safety Representative fully knowledgeable on HSE requirements; including process hazards, safety procedures, methods, and systems. 4. Design Engineer (Petroleum/Gas or Construction) provides insight and guidance on the proper engineered design work incorporating the latest HSSE procedures into new facilities or existing facility updates. 5. Cyber Security / Technology Specialist (as required) knowledgeable on current cyber security practices and technologies. 4
6 Quantitative Analysis The importance of conducting a proper SVA can be boiled down to its core it presents a clear and concise determination of the likelihood of an adversary successfully exploiting a particular vulnerability, the impact of such an attack, and the best methods for decreasing both an attack s success and impact. It is a qualitative tool that presents to the organization the necessary information required to make key decisions. The team-based approach takes into account different experiences and skill-sets to provide a detailed synopsis of areas requiring additional emphasis. In doing so, it makes recommendations for general improvements across the facility/process while more specific security measures can be directed at those vulnerabilities that, as a result of attack likelihood or consequence, present the greatest needs. Key steps of the SVA are: 1. Asset Characterization a. Critical asset and infrastructure identification b. Current countermeasure evaluation c. Consequence impact evaluation 2. Threat Assessment a. Adversary identification b. Adversary characterization c. Target attractiveness determination 3. Vulnerability Analysis a. Scenario determination and consequence evaluation b. Existing security measures evaluation c. Vulnerability identification and rating 4. Risk Assessment a. Attack likelihood estimation b. Risk evaluation and need for additional countermeasures 5. Countermeasures Analysis a. Countermeasure options identification/evaluation b. Countermeasure prioritization The above methodology is a risk/performance-based approach. It is also only a snapshot in time and we recommend continuous improvement built upon the baseline assessment. 5
7 ABOUT US Overseas Security & Strategic Information, Inc. ( OSSI ) is an international security company providing risk mitigation, intelligence, and physical security services to multinational corporations, governments, aid organizations and private individuals. Operating throughout the world on security and logistics projects for over a decade, we offer a dynamic and responsive security partner, allowing our clients to best achieve their objectives. To date, OSSI has served our clients in 22 countries across Asia, Africa, South America, North America, Europe and the Middle East. International Experience OSSI has provided security services globally since Throughout our years of operation, our cadre of experienced, culturally adept professionals have refined and improved their techniques and procedures to ensure that we provide the most contemporary approach to operate in any environment. We have built exceptional capabilities to operate in the United States, Middle East, South Asia, Africa and South America, and have experience in Europe and Asia. We believe in engaging the local community to build regional partnerships to augment our operational capabilities and national connections. Security Professionals OSSI distinguishes itself from other security providers by employing the highest caliber security management personnel. Our seasoned professionals are experienced, mature operators and have generally worked with OSSI for multiple years. Our people tend to be pragmatic, low profile and responsive, and they strive to facilitate our clients operations in a calm and controlled manner. At the same time, they have the experience, operational knowledge and capability to take control of the situation, should a security incident occur. Social Responsibility OSSI prides itself on maintaining a sensitive cultural awareness and Code of Conduct to ensure that we reflect a positive image on both OSSI and our clients operations. Our personnel have extensive experience working remotely in a variety of foreign countries, collaborating and integrating with the local community to facilitate our operations in an appropriate and respectful manner, while at all times remaining acutely aware of regional security threats. OSSI is a founding signatory of the Swiss Government initiated International Code of Conduct for Private Security Service Providers and a member of the International Stability Operations Association. 6
8 Overseas Security and Strategic Information, Inc. PO Box , Miami, FL USA tel: +1 (305)
October 2004. Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries, Second Edition
 October 2004 Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries, Second Edition October 2004 Security Vulnerability Assessment Methodology for the Petroleum and
October 2004 Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries, Second Edition October 2004 Security Vulnerability Assessment Methodology for the Petroleum and
DEVELOPMENT OF A RISK ASSESSMENT PROGRAM AGAINST TERRORISM IN REPUBLIC KOREA
 DEVELOPMENT OF A RISK ASSESSMENT PROGRAM AGAINST TERRORISM IN REPUBLIC KOREA Younghee Lee, Jinkyung Kim and Il Moon Department of Chemical Engineering, Yonsei University, 134 Sinchon-dong, Seodaemun-gu,
DEVELOPMENT OF A RISK ASSESSMENT PROGRAM AGAINST TERRORISM IN REPUBLIC KOREA Younghee Lee, Jinkyung Kim and Il Moon Department of Chemical Engineering, Yonsei University, 134 Sinchon-dong, Seodaemun-gu,
Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries. May 2003
 Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries May 2003 May 2003 Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries
Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries May 2003 May 2003 Security Vulnerability Assessment Methodology for the Petroleum and Petrochemical Industries
Oil & Gas Industry Towards Global Security. A Holistic Security Risk Management Approach. www.thalesgroup.com/security-services
 Oil & Gas Industry Towards Global Security A Holistic Security Risk Management Approach www.thalesgroup.com/security-services Oil & Gas Industry Towards Global Security This white paper discusses current
Oil & Gas Industry Towards Global Security A Holistic Security Risk Management Approach www.thalesgroup.com/security-services Oil & Gas Industry Towards Global Security This white paper discusses current
MAJOR PROJECTS CONSTRUCTION SAFETY STANDARD HS-09 Revision 0
 MAJOR PROJECTS CONSTRUCTION SAFETY SECURITY MANAGEMENT PROGRAM STANDARD HS-09 Document Owner(s) Tom Munro Project/Organization Role Supervisor, Major Projects Safety & Security (Canada) Version Control:
MAJOR PROJECTS CONSTRUCTION SAFETY SECURITY MANAGEMENT PROGRAM STANDARD HS-09 Document Owner(s) Tom Munro Project/Organization Role Supervisor, Major Projects Safety & Security (Canada) Version Control:
Relationship to National Response Plan Emergency Support Function (ESF)/Annex
 RISK MANAGEMENT Capability Definition Risk Management is defined by the Government Accountability Office (GAO) as A continuous process of managing through a series of mitigating actions that permeate an
RISK MANAGEMENT Capability Definition Risk Management is defined by the Government Accountability Office (GAO) as A continuous process of managing through a series of mitigating actions that permeate an
Security Awareness Training Solutions
 DATA SHEET Security Awareness Training Solutions A guide to available Dell SecureWorks services At Dell SecureWorks, we strive to be a trusted security advisor to our clients. Part of building this trust
DATA SHEET Security Awareness Training Solutions A guide to available Dell SecureWorks services At Dell SecureWorks, we strive to be a trusted security advisor to our clients. Part of building this trust
National Infrastructure Protection Center
 National Infrastructure Protection Center Risk Management: An Essential Guide to Protecting Critical Assets November 2002 Summary As organizations increase security measures and attempt to identify vulnerabilities
National Infrastructure Protection Center Risk Management: An Essential Guide to Protecting Critical Assets November 2002 Summary As organizations increase security measures and attempt to identify vulnerabilities
Security Guidelines. for the Petroleum Industry. Third Edition. Petroleum Refineries. Liquid Petroleum Pipelines
 Third Edition Petroleum Refineries Liquid Petroleum Pipelines Security Guidelines for the Petroleum Industry Petroleum Products Distribution and Marketing Oil and Natural Gas Production Operations Marine
Third Edition Petroleum Refineries Liquid Petroleum Pipelines Security Guidelines for the Petroleum Industry Petroleum Products Distribution and Marketing Oil and Natural Gas Production Operations Marine
Oil and Gas Industry A Comprehensive Security Risk Management Approach. www.riskwatch.com
 Oil and Gas Industry A Comprehensive Security Risk Management Approach www.riskwatch.com Introduction This white paper explores the key security challenges facing the oil and gas industry and suggests
Oil and Gas Industry A Comprehensive Security Risk Management Approach www.riskwatch.com Introduction This white paper explores the key security challenges facing the oil and gas industry and suggests
Building Blocks of a Cyber Resilience Program. Monika Josi monika.josi@safis.ch
 Building Blocks of a Cyber Resilience Program Monika Josi monika.josi@safis.ch About me Chief Security Advisor for Microsoft Europe, Middle East and Africa providing support to Governments and CIIP until
Building Blocks of a Cyber Resilience Program Monika Josi monika.josi@safis.ch About me Chief Security Advisor for Microsoft Europe, Middle East and Africa providing support to Governments and CIIP until
Support across the value chain. Expertise for Offshore Renewables Projects. rpsgroup.com/downstream
 Downstream Consultancy Support across the value chain Expertise for Offshore Renewables Projects rpsgroup.com/downstream 2 Downstream Consultancy RPS Energy a global energy consultancy n RPS Energy is
Downstream Consultancy Support across the value chain Expertise for Offshore Renewables Projects rpsgroup.com/downstream 2 Downstream Consultancy RPS Energy a global energy consultancy n RPS Energy is
Crisis Prevention and Response Services. NYA International. Crisis Prevention and Response Services. Crisis Prevention and Response Services
 NYA International B Effective risk management begins with a comprehensive understanding of the threat and an organisation s vulnerability, and the application of appropriate mitigation measures. Operating
NYA International B Effective risk management begins with a comprehensive understanding of the threat and an organisation s vulnerability, and the application of appropriate mitigation measures. Operating
INTELLIGENCE. RISK MITIGATION. RESPONSE. CONSULTANCY.
 INTELLIGENCE. RISK MITIGATION. RESPONSE. CONSULTANCY. 23 Grafton Street London W1S 4EY UK Main Tel: +44 (0) 207 887 2699 ABOUT PGI PGI is a privately owned UK business offering integrated, intelligence-led
INTELLIGENCE. RISK MITIGATION. RESPONSE. CONSULTANCY. 23 Grafton Street London W1S 4EY UK Main Tel: +44 (0) 207 887 2699 ABOUT PGI PGI is a privately owned UK business offering integrated, intelligence-led
Cyber threat intelligence and the lessons from law enforcement. kpmg.com/cybersecurity
 Cyber threat intelligence and the lessons from law enforcement kpmg.com/cybersecurity Introduction Cyber security breaches are rarely out of the media s eye. As adversary sophistication increases, many
Cyber threat intelligence and the lessons from law enforcement kpmg.com/cybersecurity Introduction Cyber security breaches are rarely out of the media s eye. As adversary sophistication increases, many
Cyber Risk to Help Shape Industry Trends in 2014
 Cyber Risk to Help Shape Industry Trends in 2014 Rigzone Staff 12/18/2013 URL: http://www.rigzone.com/news/oil_gas/a/130621/cyber_risk_to_help_shape_industry_trends_i n_2014 The oil and gas industry s
Cyber Risk to Help Shape Industry Trends in 2014 Rigzone Staff 12/18/2013 URL: http://www.rigzone.com/news/oil_gas/a/130621/cyber_risk_to_help_shape_industry_trends_i n_2014 The oil and gas industry s
Enabling Mission Success
 Enabling Mission Success Challenging Work in Challenging Places Implementing complex programs in remote or high-risk locations demands effective planning, rapid response and value-added solutions. Triple
Enabling Mission Success Challenging Work in Challenging Places Implementing complex programs in remote or high-risk locations demands effective planning, rapid response and value-added solutions. Triple
LNG and Petrochemical Security Risk Assessment and Management
 LNG and Petrochemical Security Risk Assessment and Management American Association of Port Authorities Port Security Seminar Seattle, WA July 20, 2006 David A. Moore, PE, CSP AcuTech Consulting Group 2001
LNG and Petrochemical Security Risk Assessment and Management American Association of Port Authorities Port Security Seminar Seattle, WA July 20, 2006 David A. Moore, PE, CSP AcuTech Consulting Group 2001
Subject: Critical Infrastructure Identification, Prioritization, and Protection
 For Immediate Release Office of the Press Secretary The White House December 17, 2003 Homeland Security Presidential Directive / HSPD-7 Subject: Critical Infrastructure Identification, Prioritization,
For Immediate Release Office of the Press Secretary The White House December 17, 2003 Homeland Security Presidential Directive / HSPD-7 Subject: Critical Infrastructure Identification, Prioritization,
Ten Tips for Completing a Site Security Plan
 TRANSPORTATION LOGISTICS PETROCHEMICal Commercial Industrial Retail Federal Systems Banking Ten Tips for Completing a Site Security Plan Introduction The Chemical Facility Anti-Terrorism Standards (CFATS)
TRANSPORTATION LOGISTICS PETROCHEMICal Commercial Industrial Retail Federal Systems Banking Ten Tips for Completing a Site Security Plan Introduction The Chemical Facility Anti-Terrorism Standards (CFATS)
Cyber Threat Intelligence and Incident Coordination Center (C 3 ) Protecting the Healthcare Industry from Cyber Attacks
 Cyber Threat Intelligence and Incident Coordination Center (C 3 ) Protecting the Healthcare Industry from Cyber Attacks July 2014 Cyber Threat Intelligence and Incident Coordination Center: Protecting
Cyber Threat Intelligence and Incident Coordination Center (C 3 ) Protecting the Healthcare Industry from Cyber Attacks July 2014 Cyber Threat Intelligence and Incident Coordination Center: Protecting
December 17, 2003 Homeland Security Presidential Directive/Hspd-7
 For Immediate Release Office of the Press Secretary December 17, 2003 December 17, 2003 Homeland Security Presidential Directive/Hspd-7 Subject: Critical Infrastructure Identification, Prioritization,
For Immediate Release Office of the Press Secretary December 17, 2003 December 17, 2003 Homeland Security Presidential Directive/Hspd-7 Subject: Critical Infrastructure Identification, Prioritization,
PASTA Abstract. Process for Attack S imulation & Threat Assessment Abstract. VerSprite, LLC Copyright 2013
 2013 PASTA Abstract Process for Attack S imulation & Threat Assessment Abstract VerSprite, LLC Copyright 2013 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
2013 PASTA Abstract Process for Attack S imulation & Threat Assessment Abstract VerSprite, LLC Copyright 2013 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Terrorist Protection Planning Using a Relative Risk Reduction Approach*
 BNL-71383-2003-CP Terrorist Protection Planning Using a Relative Risk Reduction Approach* Session VIII: Technology Forum Focus Groups Dr. Joseph P. Indusi Nonproliferation and National Security Department
BNL-71383-2003-CP Terrorist Protection Planning Using a Relative Risk Reduction Approach* Session VIII: Technology Forum Focus Groups Dr. Joseph P. Indusi Nonproliferation and National Security Department
How To Write A Book On Risk Management
 National Center for Risk and Economic Analysis of Terrorism Events CREATE FY2015 (Year 11) Call for White Papers CREATE, the DHS-sponsored Center of Excellence at the University of Southern California,
National Center for Risk and Economic Analysis of Terrorism Events CREATE FY2015 (Year 11) Call for White Papers CREATE, the DHS-sponsored Center of Excellence at the University of Southern California,
ENISA s Study on the Evolving Threat Landscape. European Network and Information Security Agency
 ENISA s Study on the Evolving Threat Landscape European Network and Information Security Agency Agenda Introduction to ENISA Preliminary remarks The ENISA report Major findings Conclusions 2 ENISA The
ENISA s Study on the Evolving Threat Landscape European Network and Information Security Agency Agenda Introduction to ENISA Preliminary remarks The ENISA report Major findings Conclusions 2 ENISA The
Cyber- Attacks: The New Frontier for Fraudsters. Daniel Wanjohi, Technology Security Specialist
 Cyber- Attacks: The New Frontier for Fraudsters Daniel Wanjohi, Technology Security Specialist What is it All about The Cyber Security Agenda ; Protecting computers, networks, programs and data from unintended
Cyber- Attacks: The New Frontier for Fraudsters Daniel Wanjohi, Technology Security Specialist What is it All about The Cyber Security Agenda ; Protecting computers, networks, programs and data from unintended
www.pwc.com The data breach lifecycle: From prevention to response IAPP global privacy summit March 6, 2014 (4:30-5:30) Draft v8 2-25-14
 www.pwc.com The data breach lifecycle: From prevention to response IAPP global privacy summit (4:30-5:30) Draft v8 2-25-14 Common Myths 1. You have not been hacked. 2. Cyber security is about keeping the
www.pwc.com The data breach lifecycle: From prevention to response IAPP global privacy summit (4:30-5:30) Draft v8 2-25-14 Common Myths 1. You have not been hacked. 2. Cyber security is about keeping the
FREQUENTLY ASKED QUESTIONS
 FREQUENTLY ASKED QUESTIONS Continuous Monitoring 1. What is continuous monitoring? Continuous monitoring is one of six steps in the Risk Management Framework (RMF) described in NIST Special Publication
FREQUENTLY ASKED QUESTIONS Continuous Monitoring 1. What is continuous monitoring? Continuous monitoring is one of six steps in the Risk Management Framework (RMF) described in NIST Special Publication
Experience the commitment WHITE PAPER. Information Security Continuous Monitoring. Charting the Right Course. cgi.com 2014 CGI GROUP INC.
 Experience the commitment WHITE PAPER Information Security Continuous Monitoring Charting the Right Course May 2014 cgi.com 2014 CGI GROUP INC. During the last few months of 2013, six federal agencies
Experience the commitment WHITE PAPER Information Security Continuous Monitoring Charting the Right Course May 2014 cgi.com 2014 CGI GROUP INC. During the last few months of 2013, six federal agencies
GAO. Information Security Risk Assessment Practices of Leading Organizations. Accounting and Information Management Division
 GAO United States General Accounting Office Accounting and Information Management Division November 1999 Information Security Risk Assessment Practices of Leading Organizations A Supplement to GAO s May
GAO United States General Accounting Office Accounting and Information Management Division November 1999 Information Security Risk Assessment Practices of Leading Organizations A Supplement to GAO s May
www.pwc.co.uk Cyber security Building confidence in your digital future
 www.pwc.co.uk Cyber security Building confidence in your digital future November 2013 Contents 1 Confidence in your digital future 2 Our point of view 3 Building confidence 4 Our services Confidence in
www.pwc.co.uk Cyber security Building confidence in your digital future November 2013 Contents 1 Confidence in your digital future 2 Our point of view 3 Building confidence 4 Our services Confidence in
CYBER SECURITY, A GROWING CIO PRIORITY
 www.wipro.com CYBER SECURITY, A GROWING CIO PRIORITY Bivin John Verghese, Practitioner - Managed Security Services, Wipro Ltd. Contents 03 ------------------------------------- Abstract 03 -------------------------------------
www.wipro.com CYBER SECURITY, A GROWING CIO PRIORITY Bivin John Verghese, Practitioner - Managed Security Services, Wipro Ltd. Contents 03 ------------------------------------- Abstract 03 -------------------------------------
Address C-level Cybersecurity issues to enable and secure Digital transformation
 Home Overview Challenges Global Resource Growth Impacting Industries Address C-level Cybersecurity issues to enable and secure Digital transformation We support cybersecurity transformations with assessments,
Home Overview Challenges Global Resource Growth Impacting Industries Address C-level Cybersecurity issues to enable and secure Digital transformation We support cybersecurity transformations with assessments,
NIST Cybersecurity Initiatives. ARC World Industry Forum 2014
 NIST Cybersecurity Initiatives Keith Stouffer and Vicky Pillitteri NIST ARC World Industry Forum 2014 February 10-13, 2014 Orlando, FL National Institute of Standards and Technology (NIST) NIST s mission
NIST Cybersecurity Initiatives Keith Stouffer and Vicky Pillitteri NIST ARC World Industry Forum 2014 February 10-13, 2014 Orlando, FL National Institute of Standards and Technology (NIST) NIST s mission
Digital Infrastructure - A Model For Success
 Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES Session 6 : Securing Your Fortress Best practices, standards, techniques and technologies secure your organization from cyber criminals.
Organizer: BRIDGING BARRIERS: LEGAL AND TECHNICAL OF CYBERCRIME CASES Session 6 : Securing Your Fortress Best practices, standards, techniques and technologies secure your organization from cyber criminals.
AT A HEARING ENTITLED THREATS TO THE HOMELAND
 STATEMENT OF JAMES B. COMEY DIRECTOR FEDERAL BUREAU OF INVESTIGATION BEFORE THE COMMITTEE ON HOMELAND SECURITY AND GOVERNMENTAL AFFAIRS UNITED STATES SENATE AT A HEARING ENTITLED THREATS TO THE HOMELAND
STATEMENT OF JAMES B. COMEY DIRECTOR FEDERAL BUREAU OF INVESTIGATION BEFORE THE COMMITTEE ON HOMELAND SECURITY AND GOVERNMENTAL AFFAIRS UNITED STATES SENATE AT A HEARING ENTITLED THREATS TO THE HOMELAND
PROTECTING CRITICAL CONTROL AND SCADA SYSTEMS WITH A CYBER SECURITY MANAGEMENT SYSTEM
 PROTECTING CRITICAL CONTROL AND SCADA SYSTEMS WITH A CYBER SECURITY MANAGEMENT SYSTEM Don Dickinson Phoenix Contact USA P.O. Box 4100 Harrisburg, PA 17111 ABSTRACT Presidential Executive Order 13636 Improving
PROTECTING CRITICAL CONTROL AND SCADA SYSTEMS WITH A CYBER SECURITY MANAGEMENT SYSTEM Don Dickinson Phoenix Contact USA P.O. Box 4100 Harrisburg, PA 17111 ABSTRACT Presidential Executive Order 13636 Improving
Industrial Control Systems Security Guide
 Industrial Control Systems Security Guide Keith Stouffer, Engineering Lab National Institute of Standards and Technology NIST SP 800-82, Rev 2 and ICS Cybersecurity Testbed Keith Stouffer Project Leader,
Industrial Control Systems Security Guide Keith Stouffer, Engineering Lab National Institute of Standards and Technology NIST SP 800-82, Rev 2 and ICS Cybersecurity Testbed Keith Stouffer Project Leader,
CLOUD MANAGED SERVICES FRAMEWORK E-BOOK
 CLOUD MANAGED SERVICES FRAMEWORK E-BOOK TABLE OF CONTENTS 1 Introduction 2 2 Operational Insight 3 3 Cloud Management Process Control 4 4 Infrastructure, Application & Data Security 5 5 Continuous Improvement
CLOUD MANAGED SERVICES FRAMEWORK E-BOOK TABLE OF CONTENTS 1 Introduction 2 2 Operational Insight 3 3 Cloud Management Process Control 4 4 Infrastructure, Application & Data Security 5 5 Continuous Improvement
PHYSICAL SECURITY. A Primer and a Story of Why it s Necessary
 PHYSICAL SECURITY A Primer and a Story of Why it s Necessary 1 What Is PhySec? Physical Security consists of physical, logical and design measures which protect people, physical property and other assets
PHYSICAL SECURITY A Primer and a Story of Why it s Necessary 1 What Is PhySec? Physical Security consists of physical, logical and design measures which protect people, physical property and other assets
Risk Management Handbook
 Risk Management Handbook 1999 Introduction Risk management is the process of selecting and implementing countermeasures to achieve an acceptable level of risk at an acceptable cost. The analytical risk
Risk Management Handbook 1999 Introduction Risk management is the process of selecting and implementing countermeasures to achieve an acceptable level of risk at an acceptable cost. The analytical risk
USING SECURITY METRICS TO ASSESS RISK MANAGEMENT CAPABILITIES
 Christina Kormos National Agency Phone: (410)854-6094 Fax: (410)854-4661 ckormos@radium.ncsc.mil Lisa A. Gallagher (POC) Arca Systems, Inc. Phone: (410)309-1780 Fax: (410)309-1781 gallagher@arca.com USING
Christina Kormos National Agency Phone: (410)854-6094 Fax: (410)854-4661 ckormos@radium.ncsc.mil Lisa A. Gallagher (POC) Arca Systems, Inc. Phone: (410)309-1780 Fax: (410)309-1781 gallagher@arca.com USING
Cyber security: it s not just about technology
 Cyber security: it s not just about technology The five most common mistakes kpmg.com b Cyber security: it s not just about technology Contents Preface 1 01 Understanding the cyber risk 3 02 The five most
Cyber security: it s not just about technology The five most common mistakes kpmg.com b Cyber security: it s not just about technology Contents Preface 1 01 Understanding the cyber risk 3 02 The five most
ICBA Summary of FFIEC Cybersecurity Assessment Tool
 ICBA Summary of FFIEC Cybersecurity Assessment Tool July 2015 Contact: Jeremy Dalpiaz Assistant Vice President Cyber Security and Data Security Policy Jeremy.Dalpiaz@icba.org www.icba.org ICBA Summary
ICBA Summary of FFIEC Cybersecurity Assessment Tool July 2015 Contact: Jeremy Dalpiaz Assistant Vice President Cyber Security and Data Security Policy Jeremy.Dalpiaz@icba.org www.icba.org ICBA Summary
SCOPE. September 25, 2014, 0930 EDT
 National Protection and Programs Directorate Office of Cyber and Infrastructure Analysis (OCIA) Critical Infrastructure Security and Resilience Note Critical Infrastructure Security and Resilience Note:
National Protection and Programs Directorate Office of Cyber and Infrastructure Analysis (OCIA) Critical Infrastructure Security and Resilience Note Critical Infrastructure Security and Resilience Note:
EEI Business Continuity. Threat Scenario Project (TSP) April 4, 2012. EEI Threat Scenario Project
 EEI Business Continuity Conference Threat Scenario (TSP) April 4, 2012 EEI Threat Scenario 1 Background EEI, working with a group of CIOs and Subject Matter Experts, conducted a survey with member companies
EEI Business Continuity Conference Threat Scenario (TSP) April 4, 2012 EEI Threat Scenario 1 Background EEI, working with a group of CIOs and Subject Matter Experts, conducted a survey with member companies
High Level Cyber Security Assessment 2/1/2012. Assessor: J. Doe
 2/1/2012 Assessor: J. Doe Disclaimer This report is provided as is for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information
2/1/2012 Assessor: J. Doe Disclaimer This report is provided as is for informational purposes only. The Department of Homeland Security (DHS) does not provide any warranties of any kind regarding any information
Industrial Cyber Security Risk Manager. Proactively Monitor, Measure and Manage Cyber Security Risk
 Industrial Cyber Security Risk Manager Proactively Monitor, Measure and Manage Cyber Security Risk With Today s Cyber Threats, How Secure is Your Control System? Today, industrial organizations are faced
Industrial Cyber Security Risk Manager Proactively Monitor, Measure and Manage Cyber Security Risk With Today s Cyber Threats, How Secure is Your Control System? Today, industrial organizations are faced
APICS INSIGHTS AND INNOVATIONS SUPPLY CHAIN RISK CHALLENGES AND PRACTICES
 APICS INSIGHTS AND INNOVATIONS SUPPLY CHAIN RISK CHALLENGES AND PRACTICES APICS INSIGHTS AND INNOVATIONS ABOUT THIS REPORT This report examines the role that supply chain risk management plays in organizations
APICS INSIGHTS AND INNOVATIONS SUPPLY CHAIN RISK CHALLENGES AND PRACTICES APICS INSIGHTS AND INNOVATIONS ABOUT THIS REPORT This report examines the role that supply chain risk management plays in organizations
Appendix A: Gap Analysis Spreadsheet. Competency and Skill List. Critical Thinking
 Appendix A: Gap Analysis Spreadsheet Competency and Skill List Competency Critical Thinking Data Collection & Examination Communication & Collaboration Technical Exploitation Information Security Computing
Appendix A: Gap Analysis Spreadsheet Competency and Skill List Competency Critical Thinking Data Collection & Examination Communication & Collaboration Technical Exploitation Information Security Computing
Fundamentals of Energy Infrastructure Security: Risk Mitigation in the International Environment
 Brochure More information from http://www.researchandmarkets.com/reports/306049/ Fundamentals of Energy Infrastructure Security: Risk Mitigation in the International Environment Description: The world's
Brochure More information from http://www.researchandmarkets.com/reports/306049/ Fundamentals of Energy Infrastructure Security: Risk Mitigation in the International Environment Description: The world's
C DIG COMMITTED TO EXCELLENCE IN CYBER DEFENCE. ONE MISSION. ONE GROUP. CSCSS / DEFENCE INTELLIGENCE GROUP
 C DIG CSCSS / DEFENCE INTELLIGENCE GROUP COMMITTED TO EXCELLENCE IN CYBER DEFENCE. ONE MISSION. ONE GROUP. CENTRE FOR STRATEGIC CSCSS CYBERSPACE + SECURITY SCIENCE C DIG CSCSS / DEFENCE INTELLIGENCE GROUP
C DIG CSCSS / DEFENCE INTELLIGENCE GROUP COMMITTED TO EXCELLENCE IN CYBER DEFENCE. ONE MISSION. ONE GROUP. CENTRE FOR STRATEGIC CSCSS CYBERSPACE + SECURITY SCIENCE C DIG CSCSS / DEFENCE INTELLIGENCE GROUP
Below are the module descriptions for all modules currently taught on our BA (Hons) Accounting and Finance course.
 BA (Hons) Accounting and Finance module descriptions Below are the module descriptions for all modules currently taught on our BA (Hons) Accounting and Finance course. Year One Core Modules Economics for
BA (Hons) Accounting and Finance module descriptions Below are the module descriptions for all modules currently taught on our BA (Hons) Accounting and Finance course. Year One Core Modules Economics for
Internet Safety and Security: Strategies for Building an Internet Safety Wall
 Internet Safety and Security: Strategies for Building an Internet Safety Wall Sylvanus A. EHIKIOYA, PhD Director, New Media & Information Security Nigerian Communications Commission Abuja, NIGERIA Internet
Internet Safety and Security: Strategies for Building an Internet Safety Wall Sylvanus A. EHIKIOYA, PhD Director, New Media & Information Security Nigerian Communications Commission Abuja, NIGERIA Internet
Time Is Not On Our Side!
 An audit sets the baseline. Restricting The next steps Authenticating help prevent, Tracking detect, and User Access? respond. It is rare for a few days to pass without news of a security breach affecting
An audit sets the baseline. Restricting The next steps Authenticating help prevent, Tracking detect, and User Access? respond. It is rare for a few days to pass without news of a security breach affecting
Increase insight. Reduce risk. Feel confident.
 Increase insight. Reduce risk. Feel confident. Define critical goals with enhanced visibility then enable security and compliance across your complex IT infrastructure. VIRTUALIZATION + CLOUD NETWORKING
Increase insight. Reduce risk. Feel confident. Define critical goals with enhanced visibility then enable security and compliance across your complex IT infrastructure. VIRTUALIZATION + CLOUD NETWORKING
U.S. DoD Physical Security Market
 U.S. DoD Physical Security Market Technologies Used for DoD Applications June 2011 Table of Contents Executive Summary 7 Introduction 8 Definitions and Scope 9-11 Percentage of FY 2010 Total Budget Request
U.S. DoD Physical Security Market Technologies Used for DoD Applications June 2011 Table of Contents Executive Summary 7 Introduction 8 Definitions and Scope 9-11 Percentage of FY 2010 Total Budget Request
THE DIGITAL AGE THE DEFINITIVE CYBERSECURITY GUIDE FOR DIRECTORS AND OFFICERS
 THE DIGITAL AGE THE DEFINITIVE CYBERSECURITY GUIDE FOR DIRECTORS AND OFFICERS Download the entire guide and follow the conversation at SecurityRoundtable.org Collaboration and communication between technical
THE DIGITAL AGE THE DEFINITIVE CYBERSECURITY GUIDE FOR DIRECTORS AND OFFICERS Download the entire guide and follow the conversation at SecurityRoundtable.org Collaboration and communication between technical
SECURITY METRICS: MEASUREMENTS TO SUPPORT THE CONTINUED DEVELOPMENT OF INFORMATION SECURITY TECHNOLOGY
 SECURITY METRICS: MEASUREMENTS TO SUPPORT THE CONTINUED DEVELOPMENT OF INFORMATION SECURITY TECHNOLOGY Shirley Radack, Editor Computer Security Division Information Technology Laboratory National Institute
SECURITY METRICS: MEASUREMENTS TO SUPPORT THE CONTINUED DEVELOPMENT OF INFORMATION SECURITY TECHNOLOGY Shirley Radack, Editor Computer Security Division Information Technology Laboratory National Institute
Cheryl Metzler 16-May-2006 AIHCE Chicago
 Global Global Incident Incident Reporting Reporting System System WMD WMD or or Sine The Best Qua Thing Non? Since Sliced Bread? Cheryl Metzler 16-May-2006 AIHCE Chicago BP Global Overview We operate in
Global Global Incident Incident Reporting Reporting System System WMD WMD or or Sine The Best Qua Thing Non? Since Sliced Bread? Cheryl Metzler 16-May-2006 AIHCE Chicago BP Global Overview We operate in
SECURITY SERVICES GROUP
 SECURITY SERVICES GROUP INTELLIGENCE SUPPORT SERVICES HUMANITARIAN RESPONSE ADVISORY www.security-s-group.com ABOUT US Security Services Group (SSG) is a boutique Global Advisory Firm based in Atlanta.
SECURITY SERVICES GROUP INTELLIGENCE SUPPORT SERVICES HUMANITARIAN RESPONSE ADVISORY www.security-s-group.com ABOUT US Security Services Group (SSG) is a boutique Global Advisory Firm based in Atlanta.
FFIEC Cybersecurity Assessment Tool Overview for Chief Executive Officers and Boards of Directors
 Overview for Chief Executive Officers and Boards of Directors In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council 1 (FFIEC) developed
Overview for Chief Executive Officers and Boards of Directors In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council 1 (FFIEC) developed
A Guide to the Cyber Essentials Scheme
 A Guide to the Cyber Essentials Scheme Published by: CREST Tel: 0845 686-5542 Email: admin@crest-approved.org Web: http://www.crest-approved.org/ Principal Author Jane Frankland, Managing Director, Jane
A Guide to the Cyber Essentials Scheme Published by: CREST Tel: 0845 686-5542 Email: admin@crest-approved.org Web: http://www.crest-approved.org/ Principal Author Jane Frankland, Managing Director, Jane
FFIEC Cybersecurity Assessment Tool
 Overview In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council 1 (FFIEC) developed the Cybersecurity Tool (), on behalf of its members,
Overview In light of the increasing volume and sophistication of cyber threats, the Federal Financial Institutions Examination Council 1 (FFIEC) developed the Cybersecurity Tool (), on behalf of its members,
Oil Spill Emergency Response. Oil Spill Emergency
 Oil Spill Emergency Response 1 Oil Spill Emergency Response We work to prevent incidents that may result in spills of hazardous substances. This means making sure our facilities are well designed, safely
Oil Spill Emergency Response 1 Oil Spill Emergency Response We work to prevent incidents that may result in spills of hazardous substances. This means making sure our facilities are well designed, safely
m a s t e r o f s c i e n c e i n
 m a s t e r o f s c i e n c e i n Global affairs The M.S. in Global Affairs is the flagship graduate program of the Center for Global Affairs (CGA), ranked by the Foreign Policy Association in 2010 and
m a s t e r o f s c i e n c e i n Global affairs The M.S. in Global Affairs is the flagship graduate program of the Center for Global Affairs (CGA), ranked by the Foreign Policy Association in 2010 and
Internal audit of cybersecurity. Presentation to the Atlanta IIA Chapter January 2015
 Internal audit of cybersecurity Presentation to the Atlanta IIA Chapter January 2015 Agenda Executive summary Why is this topic important? Cyber attacks: increasing complexity arket insights: What are
Internal audit of cybersecurity Presentation to the Atlanta IIA Chapter January 2015 Agenda Executive summary Why is this topic important? Cyber attacks: increasing complexity arket insights: What are
Cyber threat intelligence and the lessons from law enforcement. kpmg.com.au
 Cyber threat intelligence and the lessons from law enforcement kpmg.com.au Introduction Cyber security breaches are rarely out of the media s eye. As adversary sophistication increases, many organisations
Cyber threat intelligence and the lessons from law enforcement kpmg.com.au Introduction Cyber security breaches are rarely out of the media s eye. As adversary sophistication increases, many organisations
Integrated Risk Management Solutions
 Integrated Risk Management Solutions Our services 2 RPS Integrated Risk Management Solutions provides specialist HSE & Risk Management consultancy services to the energy industry and other major hazard
Integrated Risk Management Solutions Our services 2 RPS Integrated Risk Management Solutions provides specialist HSE & Risk Management consultancy services to the energy industry and other major hazard
Optimizing Network Vulnerability
 SOLUTION BRIEF Adding Real-World Exposure Awareness to Vulnerability and Risk Management Optimizing Network Vulnerability Management Using RedSeal november 2011 WHITE PAPER RedSeal Networks, Inc. 3965
SOLUTION BRIEF Adding Real-World Exposure Awareness to Vulnerability and Risk Management Optimizing Network Vulnerability Management Using RedSeal november 2011 WHITE PAPER RedSeal Networks, Inc. 3965
GAO. Information Security Risk Assessment. Practices of Leading Organizations. Exposure Draft. Accounting and Information Management Division
 GAO United States General Accounting Office Accounting and Information Management Division August 1999 Information Security Risk Assessment Practices of Leading Organizations Exposure Draft GAO/AIMD-99-139
GAO United States General Accounting Office Accounting and Information Management Division August 1999 Information Security Risk Assessment Practices of Leading Organizations Exposure Draft GAO/AIMD-99-139
Cyber security: Are consumer companies up to the challenge?
 Cyber security: Are consumer companies up to the challenge? 1 Cyber security: Are consumer companies up to the challenge? A survey of webcast participants kpmg.com 1 Cyber security: Are consumer companies
Cyber security: Are consumer companies up to the challenge? 1 Cyber security: Are consumer companies up to the challenge? A survey of webcast participants kpmg.com 1 Cyber security: Are consumer companies
J. Gordon Consulting Engineers Ltd 1977-2012
 J. Gordon Consulting Engineers Ltd 1977-2012 Consulting, Design, Engineering and Project management of Security Systems All information, ideas, concepts, methods and technologies mentioned in this document
J. Gordon Consulting Engineers Ltd 1977-2012 Consulting, Design, Engineering and Project management of Security Systems All information, ideas, concepts, methods and technologies mentioned in this document
COUNTERINTELLIGENCE. Protecting Key Assets: A Corporate Counterintelligence Guide
 COUNTERINTELLIGENCE O F F I C E O F T H E N A T I O N A L C O U N T E R I N T E L L I G E N C E Protecting Key Assets: A Corporate Counterintelligence Guide E X E C U T I V E Counterintelligence for the
COUNTERINTELLIGENCE O F F I C E O F T H E N A T I O N A L C O U N T E R I N T E L L I G E N C E Protecting Key Assets: A Corporate Counterintelligence Guide E X E C U T I V E Counterintelligence for the
Cyber Security for audit committees
 AUDIT COMMITTEE INSTITUTE Cyber Security for audit committees An introduction kpmg.com/globalaci 2 Audit Committee Institute An introduction to cyber security for audit committees Audit committees have
AUDIT COMMITTEE INSTITUTE Cyber Security for audit committees An introduction kpmg.com/globalaci 2 Audit Committee Institute An introduction to cyber security for audit committees Audit committees have
Cyber Information-Sharing Models: An Overview
 PARTNERSHIP Cyber Information-Sharing Models: An Overview October 2012. The MITRE Corporation. All rights reserved. Approved for Public Release. Case Number 11-4486. Distribution Unlimited. Table of Contents
PARTNERSHIP Cyber Information-Sharing Models: An Overview October 2012. The MITRE Corporation. All rights reserved. Approved for Public Release. Case Number 11-4486. Distribution Unlimited. Table of Contents
C ETS C/ETS: CYBER INTELLIGENCE + ENTERPRISE SOLUTIONS CSCSS / ENTERPRISE TECHNOLOGY + SECURITY
 CSCSS / ENTERPRISE TECHNOLOGY + SECURITY C/ETS: CYBER INTELLIGENCE + ENTERPRISE SOLUTIONS CENTRE FOR STRATEGIC CSCSS CYBERSPACE + SECURITY SCIENCE CSCSS / ENTERPRISE TECHNOLOGY + SECURITY GROUP Information
CSCSS / ENTERPRISE TECHNOLOGY + SECURITY C/ETS: CYBER INTELLIGENCE + ENTERPRISE SOLUTIONS CENTRE FOR STRATEGIC CSCSS CYBERSPACE + SECURITY SCIENCE CSCSS / ENTERPRISE TECHNOLOGY + SECURITY GROUP Information
Strategic Risk Management for School Board Trustees
 Strategic Management for School Board Trustees A Management Process Framework May, 2012 Table of Contents Introduction Page I. Purpose....................................... 3 II. Applicability and Scope............................
Strategic Management for School Board Trustees A Management Process Framework May, 2012 Table of Contents Introduction Page I. Purpose....................................... 3 II. Applicability and Scope............................
NATIONAL STRATEGY FOR GLOBAL SUPPLY CHAIN SECURITY
 NATIONAL STRATEGY FOR GLOBAL SUPPLY CHAIN SECURITY JANUARY 2012 Table of Contents Executive Summary 1 Introduction 2 Our Strategic Goals 2 Our Strategic Approach 3 The Path Forward 5 Conclusion 6 Executive
NATIONAL STRATEGY FOR GLOBAL SUPPLY CHAIN SECURITY JANUARY 2012 Table of Contents Executive Summary 1 Introduction 2 Our Strategic Goals 2 Our Strategic Approach 3 The Path Forward 5 Conclusion 6 Executive
CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE LEADERSHIP. RESEARCH. DEFENCE.
 CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE LEADERSHIP. RESEARCH. DEFENCE. CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE The early 21st century has been defined by the Internet,
CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE LEADERSHIP. RESEARCH. DEFENCE. CSCSS CENTRE FOR STRATEGIC CYBERSPACE + SECURITY SCIENCE The early 21st century has been defined by the Internet,
Electronic Warfare - Emerging Trends, Approaches, Key issues and Investment Outlook. Reference code: DF4420PR Published: March 2015
 Electronic Warfare - Emerging Trends, Approaches, Key issues and Investment Outlook Reference code: DF4420PR Published: March 2015 1 AGENDA Methodology and sample size Change in occurrence of electronic
Electronic Warfare - Emerging Trends, Approaches, Key issues and Investment Outlook Reference code: DF4420PR Published: March 2015 1 AGENDA Methodology and sample size Change in occurrence of electronic
SCREENING FACILITIES FOR CYBER SECURITY RISK ANALYSIS. by Paul Baybutt Primatech Inc. paulb@primatech.com 614-841-9800 www.primatech.com.
 SCREENING FACILITIES FOR CYBER SECURITY RISK ANALYSIS by Paul Baybutt Primatech Inc. paulb@primatech.com 614-841-9800 www.primatech.com Abstract Many chemical companies have performed security vulnerability
SCREENING FACILITIES FOR CYBER SECURITY RISK ANALYSIS by Paul Baybutt Primatech Inc. paulb@primatech.com 614-841-9800 www.primatech.com Abstract Many chemical companies have performed security vulnerability
Solutions for Oil and Gas Protecting onshore, offshore and coastal assets and infrastructure. Improving safety, security, maintenance and operations.
 Solutions for Oil and Gas Protecting onshore, offshore and coastal assets and infrastructure. Improving safety, security, maintenance and operations. In a global economy heavily reliant on oil and gas,
Solutions for Oil and Gas Protecting onshore, offshore and coastal assets and infrastructure. Improving safety, security, maintenance and operations. In a global economy heavily reliant on oil and gas,
Human mobility and displacement tracking
 Human mobility and displacement tracking The importance of collective efforts to efficiently and ethically collect, analyse and disseminate information on the dynamics of human mobility in crises Mobility
Human mobility and displacement tracking The importance of collective efforts to efficiently and ethically collect, analyse and disseminate information on the dynamics of human mobility in crises Mobility
Agenda. Introduction to SCADA. Importance of SCADA security. Recommended steps
 Agenda Introduction to SCADA Importance of SCADA security Recommended steps SCADA systems are usually highly complex and SCADA systems are used to control complex industries Yet.SCADA systems are actually
Agenda Introduction to SCADA Importance of SCADA security Recommended steps SCADA systems are usually highly complex and SCADA systems are used to control complex industries Yet.SCADA systems are actually
VULNERABILITY ASSESSMENT AND SURVEY PROGRAM. Overview of Assessment Methodology. U.S. Department of Energy Office of Energy Assurance
 VULNERABILITY ASSESSMENT AND SURVEY PROGRAM Overview of Assessment Methodology U.S. Department of Energy Office of Energy Assurance September 28, 2001 CONTENTS 1 Introduction... 1 2 Assessment Methodology...
VULNERABILITY ASSESSMENT AND SURVEY PROGRAM Overview of Assessment Methodology U.S. Department of Energy Office of Energy Assurance September 28, 2001 CONTENTS 1 Introduction... 1 2 Assessment Methodology...
OVERVIEW OF THE ADMINISTRATION S FY 2005 REQUEST FOR HOMELAND SECURITY By Steven M. Kosiak
 March 22, 2004 OVERVIEW OF THE ADMINISTRATION S FY 2005 REQUEST FOR HOMELAND SECURITY By Steven M. Kosiak The Bush Administration s fiscal year (FY) 2005 budget request includes $47.4 billion for homeland
March 22, 2004 OVERVIEW OF THE ADMINISTRATION S FY 2005 REQUEST FOR HOMELAND SECURITY By Steven M. Kosiak The Bush Administration s fiscal year (FY) 2005 budget request includes $47.4 billion for homeland
CENTRALIZED CONTROL CENTERS FOR THE OIL & GAS INDUSTRY A detailed analysis on Business challenges and Technical adoption.
 WWW.WIPRO.COM CENTRALIZED CONTROL CENTERS FOR THE OIL & GAS INDUSTRY A detailed analysis on Business challenges and Technical adoption. Senthilvelan Umapathi Practice Lead Table of contents 02 Executive
WWW.WIPRO.COM CENTRALIZED CONTROL CENTERS FOR THE OIL & GAS INDUSTRY A detailed analysis on Business challenges and Technical adoption. Senthilvelan Umapathi Practice Lead Table of contents 02 Executive
SURVEY REPORT SPON. Identifying Critical Gaps in Database Security. Published April 2016. An Osterman Research Survey Report.
 SURVEY REPORT Gaps in Database An Osterman Research Survey Report sponsored by Published April 2016 SPON sponsored by Osterman Research, Inc. P.O. Box 1058 Black Diamond, Washington 98010-1058 USA Tel:
SURVEY REPORT Gaps in Database An Osterman Research Survey Report sponsored by Published April 2016 SPON sponsored by Osterman Research, Inc. P.O. Box 1058 Black Diamond, Washington 98010-1058 USA Tel:
Frost & Sullivan s. Aerospace, Defence & Security Practice. Global Industrial Cyber Security Trends
 Frost & Sullivan s Aerospace, Defence & Security Practice Global Industrial Cyber Security Trends Presented by Philipp Reuter Director Frost & Sullivan, Turkey 1 Worth over $ 50 Billion globally in 2014
Frost & Sullivan s Aerospace, Defence & Security Practice Global Industrial Cyber Security Trends Presented by Philipp Reuter Director Frost & Sullivan, Turkey 1 Worth over $ 50 Billion globally in 2014
Development of An Analysis Tool For Performing Civil Aviation Security Risk Assessment
 Development of An Analysis Tool For Performing Civil Aviation Security Risk Assessment Allan R. Hunt AKELA, Inc. 5276 Hollister Avenue, Suite 263 Santa Barbara, CA 93111 Karl F. Kellerman FAA Office of
Development of An Analysis Tool For Performing Civil Aviation Security Risk Assessment Allan R. Hunt AKELA, Inc. 5276 Hollister Avenue, Suite 263 Santa Barbara, CA 93111 Karl F. Kellerman FAA Office of
IT Insights. Managing Third Party Technology Risk
 IT Insights Managing Third Party Technology Risk According to a recent study by the Institute of Internal Auditors, more than 65 percent of organizations rely heavily on third parties, yet most allocate
IT Insights Managing Third Party Technology Risk According to a recent study by the Institute of Internal Auditors, more than 65 percent of organizations rely heavily on third parties, yet most allocate
Notice of Funding Opportunity (NOFO):
 Federal Program: State Homeland Security Program (SHSP): SHSP supports the implementation of risk driven, capabilities-based State Homeland Security Strategies to address capability targets set in State
Federal Program: State Homeland Security Program (SHSP): SHSP supports the implementation of risk driven, capabilities-based State Homeland Security Strategies to address capability targets set in State
SECURITY / INTELLIGENCE / CONSULTING
 SECURITY / INTELLIGENCE / CONSULTING Hayes Group International (HGI) is a global security and intelligence consulting and advisory firm specializing in emerging and frontier markets. Focused on development
SECURITY / INTELLIGENCE / CONSULTING Hayes Group International (HGI) is a global security and intelligence consulting and advisory firm specializing in emerging and frontier markets. Focused on development
Cybersecurity in the maritime and offshore industry
 Cybersecurity in the maritime and offshore industry Where do we stand today - and what is the pathway going forward? Tor E. Svensen, CEO Maritime 24 March 2015 1 DNV GL 24 March 2015 SAFER, SMARTER, GREENER
Cybersecurity in the maritime and offshore industry Where do we stand today - and what is the pathway going forward? Tor E. Svensen, CEO Maritime 24 March 2015 1 DNV GL 24 March 2015 SAFER, SMARTER, GREENER
Obtaining Enterprise Cybersituational
 SESSION ID: SPO-R06A Obtaining Enterprise Cybersituational Awareness Eric J. Eifert Sr. Vice President Managed Security Services DarkMatter Agenda My Background Key components of the Cyber Situational
SESSION ID: SPO-R06A Obtaining Enterprise Cybersituational Awareness Eric J. Eifert Sr. Vice President Managed Security Services DarkMatter Agenda My Background Key components of the Cyber Situational
CONSULTING IMAGE PLACEHOLDER
 CONSULTING IMAGE PLACEHOLDER KUDELSKI SECURITY CONSULTING SERVICES CYBERCRIME MACHINE LEARNING ECOSYSTEM & INTRUSION DETECTION: CYBERCRIME OR REALITY? ECOSYSTEM COSTS BENEFITS BIG BOSS Criminal Organization
CONSULTING IMAGE PLACEHOLDER KUDELSKI SECURITY CONSULTING SERVICES CYBERCRIME MACHINE LEARNING ECOSYSTEM & INTRUSION DETECTION: CYBERCRIME OR REALITY? ECOSYSTEM COSTS BENEFITS BIG BOSS Criminal Organization
Quantitative Risk. Global Expertise. Independent
 Quantitative Risk Global Expertise Independent The PRS Group: The global standard in country and political risk. We help our clients assess the impact of country and political risk on their assets in over
Quantitative Risk Global Expertise Independent The PRS Group: The global standard in country and political risk. We help our clients assess the impact of country and political risk on their assets in over
