Exploiting Open Functionality in SMS- Capable Cellular Networks
|
|
|
- Arthur Perkins
- 8 years ago
- Views:
Transcription
1 i i Exploiting Open Functionality in SMS- Capable Cellular Networks Systems and Internet Infrastructure Security CSE InfraGard Pittsburgh Chapter General Meeting Wednesday March 29, Pittsburgh, PA William Enck, Patrick Traynor, Patrick McDaniel, and Thomas La Porta 1
2 Unintended Consequences The law of unintended consequences holds that almost all human actions have at least one unintended consequence. 2
3 Large Scale Attacks Past damaging attacks follow a pattern... Bad (or good) guys find the vulnerability... Somebody does some work... Then exploit it... Hence, an exploit evolves in the following way: 1. Recognition 2. Reconnaissance 3. Exploit 4. Recovery/Fix 3
4 Recognition: SMS Messaging What is SMS? Allows mobile phones and other devices to send small asynchronous messages containing text. Ubiquitous internationally (Europe, Asia) Often used in environments where voice calls are not appropriate or possible. On September 11th, SMS helped many people communicate even though call channels were full also observed anecdotally during recent hurricanes Can be delivered via Internet Web-pages (provider websites) , IM,... 4
5 Telecommunications Vocabulary Signaling System 7 (SS7): The phone network POTS: Plain-old telephone service Cellular network: Radio network and infrastructure used to support mobile communications (phones) Base Station (BS): Cellular towers for wireless delivery Channel: A frequency (carrier) over which cell phone communications are transmitted Sector: A cell region covered by fixed channels 5
6 SMS message delivery in 30 seconds... BS Base Station BS BS PSTN VLR MSC Mobile Switching Center HLR BS VLR Cell Network SMSC BS MSC Internet Short Messaging Service Center BS ESME External Short Messaging Entity 6
7 The air interface Traffic channels (TCH) used to deliver voice traffic to cell phones (yak yak...) Control Channel (CCH) used for signaling between base station and phones used to deliver SMS messages not originally designed for SMS CCH TCH 7
8 Call Setup/SMS Delivery SDCCH (Stand-alone Dedicated Control Channel) ( ) Call Setup/SMS Delivery( ) Ready( )
9 GSM as TDM GSM Analysis Each channel divided into 8 time-slots Each call transmits during its time-slot (TCH) Paging channel (PCH) and SDCCH are embedded in CCH BW: 762 bits/sec (96 bytes) per SDCCH Number of SDCCH is 2 * number of channels Number of channels averages 2-6 per sector (2/4/8/12/??) 4 5 Frame # Multiframe SDCCH 0 SDCCH 1 Channel Time Slot #
10 The vulnerability Once you fill the SDCCH channels with SMS traffic, call setup is blocked Voice X SMS SMS SMS SMS SMS SMS SMS SMS So, the goal of an adversary is to fill the cell network with SMS traffic Not as simple as you might think... 10
11 Reconnaissance: Gray-box Testing Standards documentation only tells half of the story Open Questions (Implementation Specific): How are messages stored? How do injection and delivery rates compare? What interface limitations currently exist? Cellular Network 11
12 Phone Capacity Methodology Determine phone capacity by slowly injecting messages while target phone is powered on Each phone in our sample set displayed the number of new messages Result: Low end phones observed message buffers High end phone drained power before max found (500+) Some phones were incapable of receiving new messages without user intervention 12
13 Delivery Discipline Methodology Determine network queuing policy by slowly injecting hundreds of (enumerated) messages while target phone is powered off Set of received messages indicates both the buffer size and eviction policy for each user at the SMSC Result: Buffer sizes varied by provider (range of 30 to a few hundred) Message eviction policy also varied (FIFO and LIFO observed) Internet 1 SMSC Cell Network We caused messages to be lost 13
14 Injection vs. Delivery Rate Methodology Find a bottleneck by comparing injection and delivery rates 7-8 second interarrival times observed on phones Experimentally finding maximum injection rate is dangerous Google found many websites selling bulk SMS sending Estimate hundreds to thousands of messages can be sent per second Faster Internet Slower Large imbalance between injection and delivery 14
15 Interface Regulation Methodology Determine limitations on provider web interfaces using automated scripts to inject messages at a moderate rate Recorded HTML response to each message sent Result: Rudimentary restrictions (IP-based, Session cookie) Unable to determine if messages dropped due to SPAM filtering Bulk senders advertise messages per second Some SMSC advertise up to 20,000 message/sec Multiple bulk senders can be used All observed interface regulations are trivially circumvented 15
16 Gray-box Testing Summary Not all messages injected will be delivered Messages can be injected orders of magnitude faster than they can be delivered Delivery time is multiple seconds Interfaces have trivial mass insertion countermeasures Result: An attack must be distributed and must target many users 16
17 Reconnaissance: Finding cell phones... North American Numbering Plan (NANP) NPA-NXX-XXXX Numbering Plan Area (Area code) Numbering Plan Exchange NPA/NXX prefixes are administered by a provider Phone number mobility may change this a little Mappings between providers and exchanges publicly documented and available on the web Implication: An adversary can identify the prefixes used in a target area (e.g., metropolitan area) 17
18 Web scraping Googling for phone numbers 865 numbers in SC 7,300 in NYC 6,184 in DC... in less than 5 seconds 18
19 Using the SMS interface While google may provide a good hit-list, it is advantageous to create a larger and fresher list Providers entry points into the SMS are available, e.g., , web, instant messaging Almost all provider web interfaces indicate whether the phone number is good or not (not just ability to deliver) Hence, web interface is an oracle for available phones 19
20 Exploit: Area Capacity Determining the capacity of an area is simple with the above observations. C = (sectors/area)*(sdcchs/sector)*(throughput/sdcch) Note that this is the capacity of the system. An attack would be aided by normal traffic. Model Data Channel Bandwidth: 3GPP TS v8.9.0 (GSM Standard) City profiles and SMS channel characteristics: National Communications System NCS TIB 03-2 City and population profiles: US Census
21 dedicate ns. H is used itment to CHs, on which on h has apltiframe, ent. Acttleneck. s bottleidth. As secutive nnel unit ndwidth, the enbe transl session esting in rving no p to 900 the total l to twice hannels. onstrated The Exploit (Metro) Capacity to the greater = sectors population density, * SDCCH/sector we assume 12 SDCCHs * msgs/hour are used = kb/sec Comparison: of SDCCHs. cable modem ~= 768 kb/sec on multi-send interface What happens when we have broadcast SMS? 240 msgs/sec Manhattan is smaller in area at 31.1 mi 2. Assuming the same sector distribution as Washington D.C., there are 55 sectors. Due per sector. Sectors in Manhattan SDCCHs per sector C 12 SDCCH (55 sectors) 1 sector 594, 000 msg/hr 165 msg/sec Messages per SDCCH per hour «900 msg/hr 1 SDCCH 165 Given msgs/sec that SMSCs * 1500 in use bybytes service providers (max message in 2000 were capa- length) ble of processing 2500 msgs/sec [59], such volumes are achievable even in the hypothetical case of a sector having twice this number Using a source transmission size of 1500 bytes as described in Section 3.1 to submit an SMS from the Internet, Table 3 shows the bandwidth required at the source to saturate the control channels, thereby incapacitating legitimate voice and text messaging services for Washington D.C. and Manhattan. The adversary s bandwidth requirements can be reduced by an order of magnitude when attacking providers including Verizon and Cingular Wireless due to «21
22 Regional Service How much bandwidth is needed to prevent access to all cell phones in the United States? About 3.8 Gbps or 2 OC-48s (5.0 Gbps) 22
23 Recovery/Fix: The solutions (today) Solution 1: separate Internet from cell network pros: essentially eliminates attacks (from Internet) cons: infeasible, loss of important functionality Solution 2: resource over-provisioning pros: allows a mitigation strategy without re-architecting cons: costly, just raises the bar on the attackers 23
24 The solutions (tomorrow) Solution 3: Queuing Separate queues for control vs. SMS Control messaging should preempt with priority Cons: complex to do correctly Solution 4: Rate limitation Control the aggregate input into a network/sector Cons: complex to do correctly Solution 5: Next generation networks 3G networks will logically separate data and voice Thus, Internet -based DOS attacks will affect data only Cons: available when? 24
25 The Reality Attacks occur accidentally Celebration Messages Overload SMS Network (Oman) Mobile Networks Facing Overload (Russia) Will Success Spoil SMS? (Europe and Asia) In-place tools may prevent trivial exploits message filtering, over-provisioning Sophisticated adversaries could likely exploit this vulnerability without additional counter-measures Many possible entry points into the network Zombie networks Little network internal control of SMS messaging Note: Edge solutions are unlikely to be successful 25
26 Recommendations Short term: reduce number of SMS gateways and regulate input flow into cell phone network Remove any feedback on the availability of cell phones or success of message delivery Implement an emergency shutdown procedure Disconnect from Internet during crisis Only allow emergency services during crisis Seek solutions from equipment manufacturers Separate control traffic from SMS messaging Advanced cell networks 26
27 A cautionary tale... Attaching the Internet to any critical infrastructure is inherently dangerous... because of the unintended consequences Will/have been felt in other areas electrical grids emergency services banking and finance and many more... 27
28 Thank you More info: Contact: 28
Exploiting open functionality in SMS-capable cellular networks
 Journal of Computer Security 16 (2008) 713 742 713 DOI 10.3233/JCS-2007-0308 IOS Press Exploiting open functionality in SMS-capable cellular networks Patrick Traynor, William Enck, Patrick McDaniel and
Journal of Computer Security 16 (2008) 713 742 713 DOI 10.3233/JCS-2007-0308 IOS Press Exploiting open functionality in SMS-capable cellular networks Patrick Traynor, William Enck, Patrick McDaniel and
Exploiting Open Functionality in SMS-Capable Cellular Networks
 Exploiting Open Functionality in SMS-Capable Cellular Networks William Enck, Patrick Traynor, Patrick McDaniel, and Thomas La Porta Systems and Internet Infrastructure Security Laboratory Department of
Exploiting Open Functionality in SMS-Capable Cellular Networks William Enck, Patrick Traynor, Patrick McDaniel, and Thomas La Porta Systems and Internet Infrastructure Security Laboratory Department of
Exploiting Vulnerabilities and Security Mechanisms in Internet based SMS capable Cellular network
 280 Exploiting Vulnerabilities and Security Mechanisms in Internet based SMS capable Cellular network Akramul Azim 1, Anwarul Azim 2, Tarikul Alam Khan Sabbir 3,Ashequl Qadir 4 1 Faculty of Comp. science
280 Exploiting Vulnerabilities and Security Mechanisms in Internet based SMS capable Cellular network Akramul Azim 1, Anwarul Azim 2, Tarikul Alam Khan Sabbir 3,Ashequl Qadir 4 1 Faculty of Comp. science
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail
 CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
GSM LOGICAL CHANNELS
 GSM LOGICAL CHANNELS There are two types of GSM logical channels 1. Traffic Channels (TCHs) 2. Control Channels (CCHs) Traffic channels carry digitally encoded user speech or user data and have identical
GSM LOGICAL CHANNELS There are two types of GSM logical channels 1. Traffic Channels (TCHs) 2. Control Channels (CCHs) Traffic channels carry digitally encoded user speech or user data and have identical
Vulnerability of South African Mobile Networks to Network Warfare Attacks
 Vulnerability of South African Mobile Networks to Network Warfare Attacks Brett van Niekerk and Manoj Maharaj School of Management, IT, and Governance University of KwaZulu-Natal Westville, South Africa
Vulnerability of South African Mobile Networks to Network Warfare Attacks Brett van Niekerk and Manoj Maharaj School of Management, IT, and Governance University of KwaZulu-Natal Westville, South Africa
www.ijreat.org Published by: PIONEER RESEARCH & DEVELOPMENT GROUP (www.prdg.org) 1
 Emergency Alert System using Android L.Hariprasath 1, R.Dhivya 2, S.Adithya 3 1 Assistant professor, Department of IT, Anand Institute of Higher Technology Kazhipattur, Chennai, Tamilnadu, India 2&3 UG-Student,
Emergency Alert System using Android L.Hariprasath 1, R.Dhivya 2, S.Adithya 3 1 Assistant professor, Department of IT, Anand Institute of Higher Technology Kazhipattur, Chennai, Tamilnadu, India 2&3 UG-Student,
Mobile Wireless Overview
 Mobile Wireless Overview A fast-paced technological transition is occurring today in the world of internetworking. This transition is marked by the convergence of the telecommunications infrastructure
Mobile Wireless Overview A fast-paced technological transition is occurring today in the world of internetworking. This transition is marked by the convergence of the telecommunications infrastructure
ENGN4536 Mobile Communications
 ENGN4536 Mobile Communications Dr Thushara Abhayapala Department of Engineering Faculty of Engineering & Information Technology Australian National University thushara@faceng.anu.edu.au http://www.webct.anu.edu.au
ENGN4536 Mobile Communications Dr Thushara Abhayapala Department of Engineering Faculty of Engineering & Information Technology Australian National University thushara@faceng.anu.edu.au http://www.webct.anu.edu.au
GSM Channels. Physical & Logical Channels. Traffic and Control Mutltiframing. Frame Structure
 GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
GSM: PHYSICAL & LOGICAL CHANNELS
 GSM: PHYSICAL & LOGICAL CHANNELS AN OVERVIEW Prepared by Learntelecom.com 1. GSM: PHYSICAL AND LOGICAL CHANNELS GSM uses a mix of Frequency Division Multiple Access (FDMA) and Time Division Multiple Access
GSM: PHYSICAL & LOGICAL CHANNELS AN OVERVIEW Prepared by Learntelecom.com 1. GSM: PHYSICAL AND LOGICAL CHANNELS GSM uses a mix of Frequency Division Multiple Access (FDMA) and Time Division Multiple Access
Wireless Cellular Networks: 1G and 2G
 Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
GSM System. Global System for Mobile Communications
 GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
GSM v. CDMA: Technical Comparison of M2M Technologies
 GSM v. CDMA: Technical Comparison of M2M Technologies Introduction Aeris provides network and data analytics services for Machine-to- Machine ( M2M ) and Internet of Things ( IoT ) applications using multiple
GSM v. CDMA: Technical Comparison of M2M Technologies Introduction Aeris provides network and data analytics services for Machine-to- Machine ( M2M ) and Internet of Things ( IoT ) applications using multiple
Multiplexing on Wireline Telephone Systems
 Multiplexing on Wireline Telephone Systems Isha Batra, Divya Raheja Information Technology, Dronacharya College of Engineering Farrukh Nagar, Gurgaon, India ABSTRACT- This Paper Outlines a research multiplexing
Multiplexing on Wireline Telephone Systems Isha Batra, Divya Raheja Information Technology, Dronacharya College of Engineering Farrukh Nagar, Gurgaon, India ABSTRACT- This Paper Outlines a research multiplexing
CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface
 CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface Hank Carter Professor Patrick Traynor 10/4/2012 UMTS and CDMA 3G technology - major change from GSM (TDMA) Based on techniques originally
CS 8803 - Cellular and Mobile Network Security: CDMA/UMTS Air Interface Hank Carter Professor Patrick Traynor 10/4/2012 UMTS and CDMA 3G technology - major change from GSM (TDMA) Based on techniques originally
Ch 2.3.3 GSM PENN. Magda El Zarki - Tcom 510 - Spring 98
 Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
Global System for Mobile Communication Technology
 Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
Locating Mobile Phones using Signalling System #7. Tobias Engel <tobias@ccc.de> twitter: @2b_as
 Locating Mobile Phones using Signalling System #7 Tobias Engel twitter: @2b_as What is Signalling System #7? protocol suite used by most telecommunications operators throughout the world
Locating Mobile Phones using Signalling System #7 Tobias Engel twitter: @2b_as What is Signalling System #7? protocol suite used by most telecommunications operators throughout the world
On Cellular Botnets: Measuring the Impact of Malicious Devices on a Cellular Network Core
 On Cellular Botnets: Measuring the Impact of Malicious Devices on a Cellular Network Core ABSTRACT Patrick Traynor Georgia Tech Information Security Center (GTISC) School of Computer Science Georgia Institute
On Cellular Botnets: Measuring the Impact of Malicious Devices on a Cellular Network Core ABSTRACT Patrick Traynor Georgia Tech Information Security Center (GTISC) School of Computer Science Georgia Institute
How To Understand How Satellite Links Fit In Gsm Over Satellite Links
 Application Note: Paradise Datacom connecting GSM networks via Satellite Presented by Paradise Datacom Limited February 2008 Proprietary and Confidential Paradise Datacom provides this information in good
Application Note: Paradise Datacom connecting GSM networks via Satellite Presented by Paradise Datacom Limited February 2008 Proprietary and Confidential Paradise Datacom provides this information in good
MAP/C SEND ROUTING INFO FOR SM. Destination Mobile Number. Obtain the SS7 address of the MSC VLR currently serving the specified Mobile Number
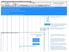 In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
Lecture overview. History of cellular systems (1G) GSM introduction. Basic architecture of GSM system. Basic radio transmission parameters of GSM
 Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
Administrivia. CSMA/CA: Recap. Mobility Management. Mobility Management. Channel Partitioning, Random Access and Scheduling
 Administrivia No lecture on Thurs. Last work will be out this week (not due, covers wireless) Extra office hours for next week and the week after. Channel Partitioning, Random Access and Scheduling Channel
Administrivia No lecture on Thurs. Last work will be out this week (not due, covers wireless) Extra office hours for next week and the week after. Channel Partitioning, Random Access and Scheduling Channel
On Attack Causality in Internet-Connected Cellular Networks
 On Attack Causality in Internet-Connected Cellular Networks Patrick Traynor, Patrick McDaniel and Thomas La Porta Systems and Internet Infrastructure Security Laboratory Networking and Security Research
On Attack Causality in Internet-Connected Cellular Networks Patrick Traynor, Patrick McDaniel and Thomas La Porta Systems and Internet Infrastructure Security Laboratory Networking and Security Research
Dimensioning and Deployment of GSM Networks
 Case Study: Dimensioning and Deployment of GSM Networks Acknowledgement: some of these slides are based on originals and information kindly provided by Ian O Shea of Altobridge Ltd. 2011 1 GSM System Architecture
Case Study: Dimensioning and Deployment of GSM Networks Acknowledgement: some of these slides are based on originals and information kindly provided by Ian O Shea of Altobridge Ltd. 2011 1 GSM System Architecture
How To Understand The Gsm And Mts Mobile Network Evolution
 Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Wireless Mobile Telephony
 Wireless Mobile Telephony The Ohio State University Columbus, OH 43210 Durresi@cis.ohio-state.edu http://www.cis.ohio-state.edu/~durresi/ 1 Overview Why wireless mobile telephony? First Generation, Analog
Wireless Mobile Telephony The Ohio State University Columbus, OH 43210 Durresi@cis.ohio-state.edu http://www.cis.ohio-state.edu/~durresi/ 1 Overview Why wireless mobile telephony? First Generation, Analog
GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving
 GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving 1 Space Division Multiple Access of the signals from the MSs A BTS with n directed antennae covers mobile stations
GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving 1 Space Division Multiple Access of the signals from the MSs A BTS with n directed antennae covers mobile stations
GSM GPRS. Course requirements: Understanding Telecommunications book by Ericsson (Part D PLMN) + supporting material (= these slides)
 GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
QUARTER ONE (Q1) 2015 QUALITY OF SERVICE REPORT FOR MOBILE NETWORK OPERATORS (TNM/AIRTEL)
 QUARTER ONE (Q1) 2015 QUALITY OF SERVICE REPORT FOR MOBILE NETWORK OPERATORS (TNM/AIRTEL) 1.0 INTRODUCTION The 2015 quarter one report analyses the key Performance Indicators which have been achieved by
QUARTER ONE (Q1) 2015 QUALITY OF SERVICE REPORT FOR MOBILE NETWORK OPERATORS (TNM/AIRTEL) 1.0 INTRODUCTION The 2015 quarter one report analyses the key Performance Indicators which have been achieved by
SHORT MESSAGE SERVICE SECURITY
 SHORT MESSAGE SERVICE SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
SHORT MESSAGE SERVICE SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
Indian Journal of Advances in Computer & Information Engineering Volume.1 Number.1 January-June 2013, pp.1-5 @ Academic Research Journals.
 Cellular System Rajat Chugh, Parag Jasoria, Tushar Arora, Nitin Ginotra and Vivek Anand V Semester, Department of Computer Science and Engineering, Dronacharya College of Engineering, Khentawas, Farukhnagar,
Cellular System Rajat Chugh, Parag Jasoria, Tushar Arora, Nitin Ginotra and Vivek Anand V Semester, Department of Computer Science and Engineering, Dronacharya College of Engineering, Khentawas, Farukhnagar,
Mobile Communications
 October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
The GSM and GPRS network T-110.300/301
 The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
GSM - Global System for Mobile Communications
 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
On Cellular Botnets: Impact of Malicious Devices on a Cellular Network Core
 On Cellular Botnets: Impact of Malicious Devices on a Cellular Network Core Loreto Felipe Sánchez-Infante Seminar Security in Telecommunications WinterSemester 2009/2010 Technische Universität Berlin (TU
On Cellular Botnets: Impact of Malicious Devices on a Cellular Network Core Loreto Felipe Sánchez-Infante Seminar Security in Telecommunications WinterSemester 2009/2010 Technische Universität Berlin (TU
Cellular Networks: Background and Classical Vulnerabilities
 Cellular Networks: Background and Classical Vulnerabilities Patrick Traynor CSE 545 1 Cellular Networks Provide communications infrastructure for an estimated 2.6 billion users daily. The Internet connects
Cellular Networks: Background and Classical Vulnerabilities Patrick Traynor CSE 545 1 Cellular Networks Provide communications infrastructure for an estimated 2.6 billion users daily. The Internet connects
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu
 Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
CS 8803 - Cellular and Mobile Network Security: Cellular Networking
 CS 8803 - Cellular and Mobile Network Security: Cellular Networking Professor Patrick Traynor 9/13/2012 The Big Picture Details create the big picture. -Sanford I. Weill 2 Overview Evolution Architecture
CS 8803 - Cellular and Mobile Network Security: Cellular Networking Professor Patrick Traynor 9/13/2012 The Big Picture Details create the big picture. -Sanford I. Weill 2 Overview Evolution Architecture
Monitoring mobile communication network, how does it work? How to prevent such thing about that?
 Monitoring mobile communication network, how does it work? How to prevent such thing about that? 潘 維 亞 周 明 哲 劉 子 揚 (P78017058) (P48027049) (N96011156) 1 Contents How mobile communications work Why monitoring?
Monitoring mobile communication network, how does it work? How to prevent such thing about that? 潘 維 亞 周 明 哲 劉 子 揚 (P78017058) (P48027049) (N96011156) 1 Contents How mobile communications work Why monitoring?
Understanding Mobile Wireless Backhaul
 Understanding Mobile Wireless Backhaul Understanding Mobile Wireless Backhaul 1 Introduction Wireless networks are evolving from voice-only traffic to networks supporting both voice and high-speed data
Understanding Mobile Wireless Backhaul Understanding Mobile Wireless Backhaul 1 Introduction Wireless networks are evolving from voice-only traffic to networks supporting both voice and high-speed data
Module 5. Broadcast Communication Networks. Version 2 CSE IIT, Kharagpur
 Module 5 Broadcast Communication Networks Lesson 9 Cellular Telephone Networks Specific Instructional Objectives At the end of this lesson, the student will be able to: Explain the operation of Cellular
Module 5 Broadcast Communication Networks Lesson 9 Cellular Telephone Networks Specific Instructional Objectives At the end of this lesson, the student will be able to: Explain the operation of Cellular
Emergency Alert System using Android Text Message Service ABSTRACT:
 Emergency Alert System using Android Text Message Service ABSTRACT: Cellular text messaging services are increasingly being relied upon to disseminate critical information during emergencies. Accordingly,
Emergency Alert System using Android Text Message Service ABSTRACT: Cellular text messaging services are increasingly being relied upon to disseminate critical information during emergencies. Accordingly,
Security Alarm Systems
 Security Alarm Systems Monitored alarm systems offer clients peace of mind as they activate on intrusion or tampering at the property and ensure any security alarm will have an appropriate response. However,
Security Alarm Systems Monitored alarm systems offer clients peace of mind as they activate on intrusion or tampering at the property and ensure any security alarm will have an appropriate response. However,
Global System for Mobile Communication (GSM)
 Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
Chapter 6 Wireless and Mobile Networks
 Chapter 6 Wireless and Mobile Networks A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
Chapter 6 Wireless and Mobile Networks A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations;
CHAPTER - 4 CHANNEL ALLOCATION BASED WIMAX TOPOLOGY
 CHAPTER - 4 CHANNEL ALLOCATION BASED WIMAX TOPOLOGY 4.1. INTRODUCTION In recent years, the rapid growth of wireless communication technology has improved the transmission data rate and communication distance.
CHAPTER - 4 CHANNEL ALLOCATION BASED WIMAX TOPOLOGY 4.1. INTRODUCTION In recent years, the rapid growth of wireless communication technology has improved the transmission data rate and communication distance.
Cellular Network Organization. Cellular Wireless Networks. Approaches to Cope with Increasing Capacity. Frequency Reuse
 Cellular Network Organization Cellular Wireless Networks Use multiple low-power transmitters (100 W or less) Areas divided into cells Each served by its own antenna Served by base station consisting of
Cellular Network Organization Cellular Wireless Networks Use multiple low-power transmitters (100 W or less) Areas divided into cells Each served by its own antenna Served by base station consisting of
CS263: Wireless Communications and Sensor Networks
 CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 4: Medium Access Control October 5, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Medium Access Control Schemes: FDMA TDMA
CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 4: Medium Access Control October 5, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Medium Access Control Schemes: FDMA TDMA
Implementation of Mobile Measurement-based Frequency Planning in GSM
 Implementation of Mobile Measurement-based Frequency Planning in GSM Comp.Eng. Serkan Kayacan (*), Prof. Levent Toker (**) (*): Ege University, The Institute of Science, Computer Engineering, M.S. Student
Implementation of Mobile Measurement-based Frequency Planning in GSM Comp.Eng. Serkan Kayacan (*), Prof. Levent Toker (**) (*): Ege University, The Institute of Science, Computer Engineering, M.S. Student
Title: Telecommunications Internetworking Author: P.J. Louis Publisher: McGraw-Hill ISBN: 0071356541
 FURTHER READING As a preview for further reading, the following reference has been provided from the pages of the book below: Title: Telecommunications Internetworking Author: P.J. Louis Publisher: McGraw-Hill
FURTHER READING As a preview for further reading, the following reference has been provided from the pages of the book below: Title: Telecommunications Internetworking Author: P.J. Louis Publisher: McGraw-Hill
Latency on a Switched Ethernet Network
 Application Note 8 Latency on a Switched Ethernet Network Introduction: This document serves to explain the sources of latency on a switched Ethernet network and describe how to calculate cumulative latency
Application Note 8 Latency on a Switched Ethernet Network Introduction: This document serves to explain the sources of latency on a switched Ethernet network and describe how to calculate cumulative latency
TS-3GB-S.R0103-0v1.0 Network Firewall Configuration and Control (NFCC) - Stage 1 Requirements
 TS-3GB-S.R0103-0v1.0 Network Firewall Configuration and Control (NFCC) - Stage 1 Requirements Mar 3,2005 THE TELECOMMUNICATION TECHNOLOGY COMMITTEE TS-3GB-S.R0103-0v1.0 Network Firewall Configuration and
TS-3GB-S.R0103-0v1.0 Network Firewall Configuration and Control (NFCC) - Stage 1 Requirements Mar 3,2005 THE TELECOMMUNICATION TECHNOLOGY COMMITTEE TS-3GB-S.R0103-0v1.0 Network Firewall Configuration and
R2. The word protocol is often used to describe diplomatic relations. How does Wikipedia describe diplomatic protocol?
 Chapter 1 Review Questions R1. What is the difference between a host and an end system? List several different types of end systems. Is a Web server an end system? 1. There is no difference. Throughout
Chapter 1 Review Questions R1. What is the difference between a host and an end system? List several different types of end systems. Is a Web server an end system? 1. There is no difference. Throughout
What You Should Know About Free Text Messaging Services
 What You Should Know About Free Text Messaging Services An educational description of text messaging services including the positives and negatives about true SMS messaging as compared to free services
What You Should Know About Free Text Messaging Services An educational description of text messaging services including the positives and negatives about true SMS messaging as compared to free services
29.09.2015. Digital Communications Exploring SS7 signaling fraud that threatens mobile network security and subscriber privacy
 29.09.2015 Digital Communications Exploring SS7 signaling fraud that threatens mobile Mobile communications is a prime target for hackers who desire to penetrate critical infrastructures and businesses
29.09.2015 Digital Communications Exploring SS7 signaling fraud that threatens mobile Mobile communications is a prime target for hackers who desire to penetrate critical infrastructures and businesses
Wireless LANs vs. Wireless WANs
 White Paper Wireless LANs vs. Wireless WANs White Paper 2130273 Revision 1.0 Date 2002 November 18 Subject Supported Products Comparing Wireless LANs and Wireless WANs Wireless data cards and modules,
White Paper Wireless LANs vs. Wireless WANs White Paper 2130273 Revision 1.0 Date 2002 November 18 Subject Supported Products Comparing Wireless LANs and Wireless WANs Wireless data cards and modules,
Mobile Communications TCS 455
 Mobile Communications TCS 455 Dr. Prapun Suksompong prapun@siit.tu.ac.th Lecture 26 1 Office Hours: BKD 3601-7 Tuesday 14:00-16:00 Thursday 9:30-11:30 Announcements Read the following from the SIIT online
Mobile Communications TCS 455 Dr. Prapun Suksompong prapun@siit.tu.ac.th Lecture 26 1 Office Hours: BKD 3601-7 Tuesday 14:00-16:00 Thursday 9:30-11:30 Announcements Read the following from the SIIT online
Geographic Routing of Toll Free Services
 Introduction Routing calls based on the caller s location is an important aspect of many toll free services, whether a call originates from a wireline, wireless, or VOIP caller. For example, a toll free
Introduction Routing calls based on the caller s location is an important aspect of many toll free services, whether a call originates from a wireline, wireless, or VOIP caller. For example, a toll free
The Advantages and Disadvantages of Emergency Text Messaging
 Characterizing the Security Implications of Third-Party Emergency Alert Systems Over Cellular Text Messaging Services Patrick Traynor Georgia Institute of Technology traynor@cc.gatech.edu Abstract. Cellular
Characterizing the Security Implications of Third-Party Emergency Alert Systems Over Cellular Text Messaging Services Patrick Traynor Georgia Institute of Technology traynor@cc.gatech.edu Abstract. Cellular
How To Get A Phone In The United States
 Telephone Systems COMP476 Home Telephones Plain Old Telephone Service (POTS) provides a twisted pair connection from your phone to the central office. You own your home wiring and the telephone company
Telephone Systems COMP476 Home Telephones Plain Old Telephone Service (POTS) provides a twisted pair connection from your phone to the central office. You own your home wiring and the telephone company
LTE Overview October 6, 2011
 LTE Overview October 6, 2011 Robert Barringer Enterprise Architect AT&T Proprietary (Internal Use Only) Not for use or disclosure outside the AT&T companies except under written agreement LTE Long Term
LTE Overview October 6, 2011 Robert Barringer Enterprise Architect AT&T Proprietary (Internal Use Only) Not for use or disclosure outside the AT&T companies except under written agreement LTE Long Term
Mobility and cellular networks
 Mobility and cellular s Wireless WANs Cellular radio and PCS s Wireless data s Satellite links and s Mobility, etc.- 2 Cellular s First generation: initially debuted in Japan in 1979, analog transmission
Mobility and cellular s Wireless WANs Cellular radio and PCS s Wireless data s Satellite links and s Mobility, etc.- 2 Cellular s First generation: initially debuted in Japan in 1979, analog transmission
2. Bulk SMS Software: Custom Desktop Software application using our API.
 What is Bulk SMS? In marketing industry SMS stands for Smart Marketing Services. The charges for SMS on mobile phones is very high especially when sending multiple messages and exorbitant when sending
What is Bulk SMS? In marketing industry SMS stands for Smart Marketing Services. The charges for SMS on mobile phones is very high especially when sending multiple messages and exorbitant when sending
GSM Radio Part 1: Physical Channel Structure
 GSM Radio Part 1: Physical Channel Structure 1 FREQUENCY BANDS AND CHANNELS...2 2 GSM TDMA...4 3 TDMA FRAME HIERARCHY...6 4 BURST STRUCTURE...7 5 TDMA MULTIFRAME STRUCTURE...9 5.1 Traffic Multiframe (26-Multiframe)...10
GSM Radio Part 1: Physical Channel Structure 1 FREQUENCY BANDS AND CHANNELS...2 2 GSM TDMA...4 3 TDMA FRAME HIERARCHY...6 4 BURST STRUCTURE...7 5 TDMA MULTIFRAME STRUCTURE...9 5.1 Traffic Multiframe (26-Multiframe)...10
How to deal with a thousand nodes: M2M communication over cellular networks. A. Maeder NEC Laboratories Europe andreas.maeder@neclab.
 How to deal with a thousand nodes: M2M communication over cellular networks A. Maeder NEC Laboratories Europe andreas.maeder@neclab.eu Outline Introduction to M2M communications The M2M use case landscape
How to deal with a thousand nodes: M2M communication over cellular networks A. Maeder NEC Laboratories Europe andreas.maeder@neclab.eu Outline Introduction to M2M communications The M2M use case landscape
Acquia Cloud Edge Protect Powered by CloudFlare
 Acquia Cloud Edge Protect Powered by CloudFlare Denial-of-service (DoS) Attacks Are on the Rise and Have Evolved into Complex and Overwhelming Security Challenges TECHNICAL GUIDE TABLE OF CONTENTS Introduction....
Acquia Cloud Edge Protect Powered by CloudFlare Denial-of-service (DoS) Attacks Are on the Rise and Have Evolved into Complex and Overwhelming Security Challenges TECHNICAL GUIDE TABLE OF CONTENTS Introduction....
Analysis of TCP Performance Over Asymmetric Wireless Links
 Virginia Tech ECPE 6504: Wireless Networks and Mobile Computing Analysis of TCP Performance Over Asymmetric Kaustubh S. Phanse (kphanse@vt.edu) Outline Project Goal Notions of Asymmetry in Wireless Networks
Virginia Tech ECPE 6504: Wireless Networks and Mobile Computing Analysis of TCP Performance Over Asymmetric Kaustubh S. Phanse (kphanse@vt.edu) Outline Project Goal Notions of Asymmetry in Wireless Networks
Telecommunications and the Information Age ET108B. Cell Phone Network
 Telecommunications and the Information Age ET108B Cell Phone Network The Cellular Telephone Network Cellular Telephone Features Carrying Data Across the Cellular Network Satellite Telephone Service Cellular
Telecommunications and the Information Age ET108B Cell Phone Network The Cellular Telephone Network Cellular Telephone Features Carrying Data Across the Cellular Network Satellite Telephone Service Cellular
CloudFlare advanced DDoS protection
 CloudFlare advanced DDoS protection Denial-of-service (DoS) attacks are on the rise and have evolved into complex and overwhelming security challenges. 1 888 99 FLARE enterprise@cloudflare.com www.cloudflare.com
CloudFlare advanced DDoS protection Denial-of-service (DoS) attacks are on the rise and have evolved into complex and overwhelming security challenges. 1 888 99 FLARE enterprise@cloudflare.com www.cloudflare.com
Chapter 13: Internet Connectivity
 Chapter 13: Internet Connectivity Complete CompTIA A+ Guide to PCs, 6e To configure an internal external modem To explain basic handshaking between a DTE device and a DCE device To use Windows tools when
Chapter 13: Internet Connectivity Complete CompTIA A+ Guide to PCs, 6e To configure an internal external modem To explain basic handshaking between a DTE device and a DCE device To use Windows tools when
GSM Risks and Countermeasures
 GSM Risks and Countermeasures STI Group Discussion and Written Project Authors: Advisor: Johannes Ullrich Accepted: February 1, 2010 Abstract Recent research has shown that GSM encryption can be cracked
GSM Risks and Countermeasures STI Group Discussion and Written Project Authors: Advisor: Johannes Ullrich Accepted: February 1, 2010 Abstract Recent research has shown that GSM encryption can be cracked
GSM BASICS GSM HISTORY:
 GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
Chapter 9. Communications and Networks. McGraw-Hill/Irwin. Copyright 2008 by The McGraw-Hill Companies, Inc. All rights reserved.
 Chapter 9 Communications and Networks McGraw-Hill/Irwin Copyright 2008 by The McGraw-Hill Companies, Inc. All rights reserved. Competencies (Page 1 of 2) Discuss connectivity, the wireless revolution,
Chapter 9 Communications and Networks McGraw-Hill/Irwin Copyright 2008 by The McGraw-Hill Companies, Inc. All rights reserved. Competencies (Page 1 of 2) Discuss connectivity, the wireless revolution,
Chapter 3 Cellular Networks. Wireless Network and Mobile Computing Professor: Dr. Patrick D. Cerna
 Chapter 3 Cellular Networks Wireless Network and Mobile Computing Professor: Dr. Patrick D. Cerna Objectives! Understand Cellular Phone Technology! Know the evolution of evolution network! Distinguish
Chapter 3 Cellular Networks Wireless Network and Mobile Computing Professor: Dr. Patrick D. Cerna Objectives! Understand Cellular Phone Technology! Know the evolution of evolution network! Distinguish
WIRELESS IN THE METRO PACKET MICROWAVE EXPLAINED
 WIRELESS IN THE METRO PACKET MICROWAVE EXPLAINED RAJESH KUMAR SUNDARARAJAN Assistant Vice President - Product Management, Aricent Group WIRELESS IN THE METRO PACKET MICROWAVE EXPLAINED This whitepaper
WIRELESS IN THE METRO PACKET MICROWAVE EXPLAINED RAJESH KUMAR SUNDARARAJAN Assistant Vice President - Product Management, Aricent Group WIRELESS IN THE METRO PACKET MICROWAVE EXPLAINED This whitepaper
Introduction Chapter 1. Uses of Computer Networks
 Introduction Chapter 1 Uses of Computer Networks Network Hardware Network Software Reference Models Example Networks Network Standardization Metric Units Revised: August 2011 Uses of Computer Networks
Introduction Chapter 1 Uses of Computer Networks Network Hardware Network Software Reference Models Example Networks Network Standardization Metric Units Revised: August 2011 Uses of Computer Networks
SERVICE PROVIDER ACCESS IN MOBILE NETWORKS. March 2003
 Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT) SERVICE PROVIDER ACCESS IN MOBILE NETWORKS March 2003 Page 2 EXECUTIVE SUMMARY
Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT) SERVICE PROVIDER ACCESS IN MOBILE NETWORKS March 2003 Page 2 EXECUTIVE SUMMARY
2G/3G Mobile Communication Systems
 2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
GSM System Architecture
 Intersystem Operation and Mobility Management David Tipper Associate Professor Graduate Program in Telecommunications and Networking University it of Pittsburgh Telcom 2700 Slides 6 http://www.tele.pitt.edu/tipper.html
Intersystem Operation and Mobility Management David Tipper Associate Professor Graduate Program in Telecommunications and Networking University it of Pittsburgh Telcom 2700 Slides 6 http://www.tele.pitt.edu/tipper.html
Review of Cell Phone Technology
 Review of Cell Phone Technology Types of Cell Technology - CDMA - GSM - iden - TDMA CDMA Code Division Multiple Access (CDMA) CDMA Code Division Multiple Access. In reality it is cdmaone (2G) or CDMA2000
Review of Cell Phone Technology Types of Cell Technology - CDMA - GSM - iden - TDMA CDMA Code Division Multiple Access (CDMA) CDMA Code Division Multiple Access. In reality it is cdmaone (2G) or CDMA2000
Wireless Phone GSM tracking. Denis Foo Kune, John Koelndorfer, Nick Hopper, Yongdae Kim
 Wireless Phone GSM tracking Denis Foo Kune, John Koelndorfer, Nick Hopper, Yongdae Kim Can someone track your phone? GPS Need access to phone Cell network trilateration/triangulation Multiple base stations
Wireless Phone GSM tracking Denis Foo Kune, John Koelndorfer, Nick Hopper, Yongdae Kim Can someone track your phone? GPS Need access to phone Cell network trilateration/triangulation Multiple base stations
Global System for Mobile Communications (GSM)
 Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE Thi-Mai-Trang.Nguyen@lip6.fr UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE Thi-Mai-Trang.Nguyen@lip6.fr UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Lecture 15: Congestion Control. CSE 123: Computer Networks Stefan Savage
 Lecture 15: Congestion Control CSE 123: Computer Networks Stefan Savage Overview Yesterday: TCP & UDP overview Connection setup Flow control: resource exhaustion at end node Today: Congestion control Resource
Lecture 15: Congestion Control CSE 123: Computer Networks Stefan Savage Overview Yesterday: TCP & UDP overview Connection setup Flow control: resource exhaustion at end node Today: Congestion control Resource
Multi-vendor Penetration Testing in the Advanced Metering Infrastructure: Future Challenges
 Multi-vendor Penetration Testing in the Advanced ing Infrastructure: Future Challenges DIMACS Workshop on Algorithmic Decision Theory for the Smart Grid Stephen McLaughlin - Penn State University 1 Data
Multi-vendor Penetration Testing in the Advanced ing Infrastructure: Future Challenges DIMACS Workshop on Algorithmic Decision Theory for the Smart Grid Stephen McLaughlin - Penn State University 1 Data
Packet Synchronization in Cellular Backhaul Networks By Patrick Diamond, PhD, Semtech Corporation
 Packet Synchronization in Cellular Backhaul Networks By Patrick Diamond, PhD, Semtech Corporation (Semtech White Paper October 2008) INTRODUCTION For carriers to leverage cost-effective IP networks to
Packet Synchronization in Cellular Backhaul Networks By Patrick Diamond, PhD, Semtech Corporation (Semtech White Paper October 2008) INTRODUCTION For carriers to leverage cost-effective IP networks to
Overview of WAN Connections Module 1
 Overview of WAN Connections Module 1 Objectives This module introduces the basic elements of WAN connections and describes the role each element plays in creating that connection. After completing this
Overview of WAN Connections Module 1 Objectives This module introduces the basic elements of WAN connections and describes the role each element plays in creating that connection. After completing this
Dimensioning, configuration and deployment of Radio Access Networks. Lecture 2.1: Voice in GSM
 Dimensioning, configuration and deployment of Radio Access Networks. Lecture.: Voice in GSM GSM Specified by ETSI Frequency Division Duplex TDMA system Originally at 900MHz, but today also at 800, 800,
Dimensioning, configuration and deployment of Radio Access Networks. Lecture.: Voice in GSM GSM Specified by ETSI Frequency Division Duplex TDMA system Originally at 900MHz, but today also at 800, 800,
A Network Administrator s Guide to Web App Security
 A Network Administrator s Guide to Web App Security Speaker: Orion Cassetto, Product Marketing Manager, Incapsula Moderator: Rich Nass, OpenSystems Media Agenda Housekeeping Presentation Questions and
A Network Administrator s Guide to Web App Security Speaker: Orion Cassetto, Product Marketing Manager, Incapsula Moderator: Rich Nass, OpenSystems Media Agenda Housekeeping Presentation Questions and
ROUTER CONTROL MECHANISM FOR CONGESTION AVOIDANCE IN CDMA BASED IP NETWORK
 International Journal of Information Technology and Knowledge Management July-December 2010, Volume 2, No. 2, pp. 465-470 ROUTER CONTROL MECHANISM FOR CONGESTION AVOIDANCE IN CDMA BASED IP NETWORK V.Sumalatha1
International Journal of Information Technology and Knowledge Management July-December 2010, Volume 2, No. 2, pp. 465-470 ROUTER CONTROL MECHANISM FOR CONGESTION AVOIDANCE IN CDMA BASED IP NETWORK V.Sumalatha1
How To Make A Cell Phone Network More Efficient
 Cellular Network Planning and Optimization Part V: GSM Jyri Hämäläinen, Communications and Networking Department, TKK, 18.1.2008 GSM Briefly 2 General GSM was the first digital cellular system. GSM was
Cellular Network Planning and Optimization Part V: GSM Jyri Hämäläinen, Communications and Networking Department, TKK, 18.1.2008 GSM Briefly 2 General GSM was the first digital cellular system. GSM was
LTE Multimedia Broadcast Multicast Services (MBMS)
 LTE Multimedia Broadcast Multicast Services (MBMS) LTE is the technology of choice for mobile operators because it delivers significantly higher bandwidth with the lowest amount of spectral resources.
LTE Multimedia Broadcast Multicast Services (MBMS) LTE is the technology of choice for mobile operators because it delivers significantly higher bandwidth with the lowest amount of spectral resources.
1.264 Lecture 32. Telecom: Basic technology. Next class: Green chapter 4, 6, 7, 10. Exercise due before class
 1.264 Lecture 32 Telecom: Basic technology Next class: Green chapter 4, 6, 7, 10. Exercise due before class 1 Exercise 1 Communications at warehouse A warehouse scans its inventory with RFID readers that
1.264 Lecture 32 Telecom: Basic technology Next class: Green chapter 4, 6, 7, 10. Exercise due before class 1 Exercise 1 Communications at warehouse A warehouse scans its inventory with RFID readers that
Wireless Access of GSM
 Wireless Access of GSM Project Report FALL, 1999 Wireless Access of GSM Abstract: Global System for Mobile communications (GSM) started to be developed by Europeans when the removal of many European trade
Wireless Access of GSM Project Report FALL, 1999 Wireless Access of GSM Abstract: Global System for Mobile communications (GSM) started to be developed by Europeans when the removal of many European trade
CARLETON UNIVERSITY Department of Systems and Computer Engineering. SYSC4700 Telecommunications Engineering Winter 2014. Term Exam 13 February 2014
 CARLETON UNIVERSITY Department of Systems and Computer Engineering SYSC4700 Telecommunications Engineering Winter 2014 Term Exam 13 February 2014 Duration: 75 minutes Instructions: 1. Closed-book exam
CARLETON UNIVERSITY Department of Systems and Computer Engineering SYSC4700 Telecommunications Engineering Winter 2014 Term Exam 13 February 2014 Duration: 75 minutes Instructions: 1. Closed-book exam
Wireless Broadband Access
 Wireless Broadband Access (Brought to you by RMRoberts.com) Mobile wireless broadband is a term used to describe wireless connections based on mobile phone technology. Broadband is an electronics term
Wireless Broadband Access (Brought to you by RMRoberts.com) Mobile wireless broadband is a term used to describe wireless connections based on mobile phone technology. Broadband is an electronics term
Global System for Mobile Communication (GSM)
 Global System for Mobile Communication (GSM) Definition Global system for mobile communication (GSM) is a globally accepted standard for digital cellular communication. GSM is the name of a standardization
Global System for Mobile Communication (GSM) Definition Global system for mobile communication (GSM) is a globally accepted standard for digital cellular communication. GSM is the name of a standardization
Smartphone Botnets. Berlin Institute of Technology FG Security in Telecommunications SPRING 2010
 Berlin Institute of Technology FG Security in Telecommunications Smartphone Botnets SPRING 2010 Weiss Collin Mulliner, July 7 th 2010 collin@sec.t-labs.tu-berlin.de Agenda Introduction Motivation Project
Berlin Institute of Technology FG Security in Telecommunications Smartphone Botnets SPRING 2010 Weiss Collin Mulliner, July 7 th 2010 collin@sec.t-labs.tu-berlin.de Agenda Introduction Motivation Project
VoIP Glossary. Client (Softphone client): The software installed in the userâ s computer to make calls over the Internet.
 VoIP Glossary Analog audio signals: Analog audio signals are used to transmit voice data over telephone lines. This is done by varying or modulating the frequency of sound waves to accurately reflect the
VoIP Glossary Analog audio signals: Analog audio signals are used to transmit voice data over telephone lines. This is done by varying or modulating the frequency of sound waves to accurately reflect the
