Microsoft Vista: Serious Challenges for Digital Investigations
|
|
|
- Logan Cook
- 8 years ago
- Views:
Transcription
1 Proceedings of Student-Faculty Research Day, CSIS, Pace University, May 2 nd, 2008 Microsoft Vista: Serious Challenges for Digital Investigations Darren R. Hayes and Shareq Qureshi Seidenberg School of CSIS, Pace University, New York {dhayes@pace.edu, sq05639n@pace.edu} ABSTRACT Microsoft s Vista ( Vista ) can be seen as a dramatic departure from previous versions of the vendor s operating systems, in terms of security and file systems. This vendor s technical advances in security have created problems for law enforcement and other computer forensics investigators. This paper will illustrate how changes to Vista s file systems will impede the retrieval of inculpatory evidence by prosecutors; the discovery of digital evidence on a system is more problematic in a Vista environment. The successful conviction of a defendant is reliant upon a prosecutor effectively demonstrating control, ownership and intent relating to the data found on the perpetrator s computer. However, a machine running Vista is likely to negatively impact these findings. This paper will seek to guide the forensics investigator through the plethora of Vista operating system changes and provide suggestions for alternative methods of data discovery. Keywords Vista, BitLocker, Encryption, Operating Systems, Computer Forensics I. INTRODUCTION The paper will detail the findings of scientific experiments, conducted in the Seidenberg School s Computer Forensics Laboratory. Through collaboration with the Manhattan District Attorney s Office, the computer forensics research group was able to research key files types that are of interest to prosecutors of criminal investigations. Subsequently, this research has provided information about the challenges expected to be encountered within a Vista environment and ultimately provide helpful recommendations to investigators. The research herein merely highlights some of the results, which pertain to files, especially in regards to defragmentation, restoration, metadata, event logs, indexing and storage. A. Defragmentation and Restore The defragmentation program on Vista is different to the one on previous versions of Windows as there is no longer a graphical display of the process. Most importantly, defragmentation in Vista is set to automatically run once a week. We know from Carrier that some defragmentation occurs periodically in previous versions of Windows unbeknownst to us. However, defragmentation is run automatically in A3.1
2 Vista (Carrier B., 2005). A defragmentation can also be executed manually in Vista if necessary. Either way, it works in the background at a low priority without a graphical display. Defragmentation can also run from an administrative command prompt. To perform this, click on the start orb and type 'cmd' in the search box. Do not press enter. Instead, hold down 'Ctrl', 'Shift' and then press enter. After providing administrative credentials, you will be at the command prompt. If you do this correctly, the prompt will read 'C:\Windows\system32>'. At this prompt, type 'defrag /?' for a full list of the defragmentation commands together with a few examples. To get a detailed report of the fragmentation status, enter 'defrag C: -a -v'. To perform a full defragmentation, enter 'defrag C: -w' or 'defrag C: -w -f' to force a defragmentation if you have low disk space. Note that in both cases you can add the switches '-a' and '-v' if you want more detailed output. Why is this important? Its importance stems from the fact that with the advent of automatic defragmentation, computer forensics investigators will face a significant decrease in evidentiary data (Microsoft, Description of the Microsoft Windows Registry, 2007). Figure 1. Screen shot of defragmentation in Vista Figure 2. Screen shot of defragmentation in Windows XP A3.2
3 B. Event Logs Windows event logs have changed dramatically in Vista. A new XML file format is being used for the event logs and a new extension of EVTX is now used. The files are now located in: C:\Windows\System32\winevt\Logs\ There are now approximately 30 different event logs that Windows Vista reports events to. Currently these logs can only be read by the native Windows Vista Event Viewer (eventvwr), although an EnCase EnScript is under development. Below is the screen shot of Event Log of Vista (Lance, 2007). Figure 3. Vista Event log WinHex and X-Ways Forensics have confirmed that if a file in an NTFS volume has only been partially filled with data then these files are marked with "partial init." (partial initialization) in the Attribute column. The size of the actually initialized/defined portion of the file is now displayed in the Details Panel when opening such a file or when looking at it in File mode, labeled as "Valid data length", and the affected uninitialized range will be displayed in a different color. Search hits in the uninitialized portion of a file will be marked as search hits in "slack etc. The fact that a file has been partially initialized only will also be remembered by containers. All of that is meant to help a skillful forensic examiner to avoid drawing inaccurate conclusions. This risk exists because data that is stored in the A3.3
4 allocated clusters of a file may be old data that was present on the disk before the clusters were allocated to that file, if the clusters have never been actually overwritten with new data. In other words, there may be data that has nothing to do with the file, although according to the logical file size it is part of it (Carvey, 2006). File types that are not always fully initialized can include Windows Registry and Windows Event Log (.evtx). Event logs are important to investigators who may try to build up a portrait of a suspect s behavior. For example, viewing the event logs for a computer would be critical for a case involving Internet Chat, especially when trying to prove that an individual was communicating at certain times. The event logs would also be important to determine if a suspect had attempted to secret information or tamper with evidence. C. Windows Search Engine (Indexing) Windows Vista includes a new search engine and indexing feature. Indexing has been available since Windows 2000 but it was turned off by default (Carrier B., 2005). In Windows Vista, it is enabled by default. The new search feature is accessible from the Start Menu or any Windows Explorer window (Lance, 2007). Users can now save their searches and review the results in real-time as the search results are updated as new files are added to the system. Saved searches are placed under the user s profile: C:\Users\<username>\Searches The indexing service is used to quickly locate files by indexing the file s metadata and contents (some file types). Microsoft Mail is included in the types of data that is indexed and available for searches. These indexes are located in the following location: C:\ProgramData\Microsoft\Search\Data\Appliations\Windows\Projects\systemIndex\Indexer\Ci Files Vista maintains several index files in this directory and these can be searched for keywords using the keyword search feature in EnCase. When extracting messages and attachments, attachments now become child objects of their respective parent messages. That makes it very easy to find the attachments for a given message, or to find the message that contains a given attachment. Because of this parent-child relationship, one can now conveniently include the containing message when copying attachments to evidence file container, or include the attachments when copying the message. Tagging an message will also tag its attachments. Tagging an attachment will at least partially tag the containing message (Garfinkel, Febraury 2006). The logs for Refine Volume Snapshot, Logical Search, and Indexing, which contain the internal IDs of processed files to identify the offending file in case of a crash, are no longer stored in separate log files and no longer in the evidence object metadata directories. Instead, a single file "VS.log" is now created in the directory from where X-Ways Forensics is run, and it is overwritten each time a new operation is started. This means you no longer have to search for the correct log file for the last operation, and it also saves drive space. As before, the last line in such a file specifies the internal ID of the last file that was processed. Unlike many other aspects of Vista, the new default settings for indexing are a boon to investigators trying to ascertain ownership, intent and control by a suspect. A3.4
5 D. ReadyBoost and Physical Memory ReadyBoost is a Microsoft feature which allows a user to add virtual memory by using a removable flash drive. This memory is then cached and used as an extension to installed physical memory. Flash memory is much faster than paging data to the pagefile on a hard disk and is therefore a cheap alternative to adding memory to a system. Data that is written to the removable flash disk is encrypted using AES-128 encryption before being written to the flash disk. Therefore an examiner who recovers a flash disk used for ReadyBoost will not be able to decipher the data. Accessing physical memory using DD is a common way of collecting volatile data (contents of RAM) before a system is shutdown and/or imaged. This procedure works in Windows 2000 and Windows XP but does not in Windows 2003 and Windows Vista. This is because the \\.\PhysicalMemory Pipe is not accessible even from an administrator account. Therefore, it is currently not possible to collect physical memory using the standard version of win32 DD.EXE. ReadyBoost is an important feature for an examiner to be cognizant of, especially because USB memory has become so pervasive in recent times and it can now be used as an extension of a system s volatile memory and the file footprint for a USB drive has changed with Vista. E. File Metadata The last access dates in Windows Vista are no longer updated when a file is accessed. Microsoft explains that with all the new file system transactional journaling, it was somewhat of a performance hit, so they have disabled them by default. Figure 4. File Metadata Represented in Vista In Windows Vista, this feature is enabled by default. This feature can be turned off via a registry key. This default setting obviously has a severe impact on how some types of cases are analyzed and examiners should take great care when using these date stamps as part of their analysis (Disabling last access time in windows vista to improve ntfs performance, 2006). A reduction in file metadata is a serious blow to criminal investigations. For example, it is not enough to simply find contraband images stored on a suspect s computer, facing child endangerment charges. Intent must also be demonstrated, by the prosecution, with accurate information pertaining to file access times. F. Volume Shadow Services The Volume Shadow Service was first introduced in Windows XP in a limited way and then further enhanced in Windows 2003 Server. Its goal was to create copies of important files that could then be A3.5
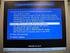
6 safely backed up without having file locking issues. It was off by default and only a limited number of files or directories could be shadowed in Windows Figure 5. Volume Shadow Copy Program in Vista The block level changes that are saved by the previous version feature are stored in the System Volume Information folder as part of a restore point. This data is not encrypted (absent BitLocker) and can be easily searched using the EnCase search feature. In the root of the System Volume Information folder, several files can be seen with GUIDs as the filename (Lance, 2007). Figure 6. Saved Block Level Changes in Vista II. CHANGES IN EVIDENCE Log files are generally an important source of information in a forensic examination. The new log file format consists of a small file header, which is followed by a series of chunks. The chunks are selfcontained. No event record will extend over the boundary between two chunks. Thus, for every event log only the current chunk (64 KB) and the file header (4 KB) have to be mapped into memory. Events are in XML but are encoded in BXML. A practical test was conducted in the forensics laboratory, at Pace University, on Windows XP and Vista. The experiment hypothesized that a person wanted to change the system time after committing the crime. It was possible in both operating systems but the nature of the evidence is different in Vista s Event Viewer compared to that of Windows XP. The Vista Event Viewer A3.6
7 clearly shows that the system clock was manipulated while The XP Event Viewer showed no record of the system clock being changed. This experiment was important because accurately determining a series of events in a criminal investigation can be critical. Thus, Windows Vista Event Viewer can potentially provide better evidence to a forensics investigator than previous versions of Windows. Below is the screen shot from Vista and it is compared with XP. Figure 7. Windows Vista Event Viewer Figure 8. Windows XP Event Viewer A3.7
8 III. CONCLUSION Windows Vista can be viewed as more problematic for investigations involving the use of digital evidence. The problems encountered are mainly as a result of enhancements made to encryption, through Vista s Encrypted File System (EFS), BitLocker Drive Encryption with Trusted Platform Module (TPM) and electronic mail encryption in Windows Mail (Hayes & Qureshi, 2008). For the purposes of this paper, it appears evident that Microsoft has sought to remove the user from many housekeeping tasks associated with operating systems, such as file restoration and defragmentation. On the one hand, Shadow Copy and file restoration features will be beneficial to examiners. On the other hand the introduction of automatic defragmentation poses new problems for data recovery. Vista is dramatically different and computer forensics investigators will need to adapt to changes in the nature of evidence, its value as well as new methods of retrieval. REFERENCES A. Andreas, S. (2007, August). A parser to transform vista event log files into plain text. Retrieved from evtx_parser.html B. Baryamureeba, V. a. (2007, November). The Enhanced Digital Investigation Process Model. Retrieved from C. Berghel, H. (2007). Hiding Data, Forensics and Anti-Forensics. D. Carrier, B. (2005). File System Forensic analysis. Upper Saddle River,NJ 07458: Addison-Wesley. E. Carrier, B. (2005). File System Forensics Analysis. Addison Wesley. F. Carvey, H. (2006). Windows Forensics and Incident Recovery. Addison-Wesley. G. Disabling last access time in windows vista to improve ntfs performance. (2006). blogs.technet.com/filecab/archive/2006/11/07. H. File Extensions. (2005, September). Retrieved from I. Garfinkel, S. (Febraury 2006). AFF: A New Format for Storing Hard Drive Images. J. Hayes, D. R., & Qureshi, S. (2008). A Framework for Computer Forensics Investigations Involving Microsoft Vista. LISAT. Farmingdale: IEEE. K. John, M. (2007, October 23). Finding the user setting in Vista. Retrieved February 3, 2008, from L. Lance, M. (2007). Basic Investigations of Windows Vista. M. Microsoft. (2007, September). Description of the Microsoft Windows Registry. Retrieved from N. Microsoft. (2007). Microsoft's Windows OS global market share. Retrieved from O. Microsoft. (2002, November 2). MSDN. Retrieved January 2008, from A3.8
TZWorks Windows Event Log Viewer (evtx_view) Users Guide
 TZWorks Windows Event Log Viewer (evtx_view) Users Guide Abstract evtx_view is a standalone, GUI tool used to extract and parse Event Logs and display their internals. The tool allows one to export all
TZWorks Windows Event Log Viewer (evtx_view) Users Guide Abstract evtx_view is a standalone, GUI tool used to extract and parse Event Logs and display their internals. The tool allows one to export all
Determining VHD s in Windows 7 Dustin Hurlbut
 Introduction Windows 7 has the ability to create and mount virtual machines based upon launching a single file. The Virtual Hard Disk (VHD) format permits creation of virtual drives that can be used for
Introduction Windows 7 has the ability to create and mount virtual machines based upon launching a single file. The Virtual Hard Disk (VHD) format permits creation of virtual drives that can be used for
Fall. Forensic Examination of Encrypted Systems Matthew Postinger COSC 374
 Fall 2011 Forensic Examination of Encrypted Systems Matthew Postinger COSC 374 Table of Contents Abstract... 3 File System Encryption... 3 Windows EFS... 3 Apple FileVault... 4 Full Disk Encryption...
Fall 2011 Forensic Examination of Encrypted Systems Matthew Postinger COSC 374 Table of Contents Abstract... 3 File System Encryption... 3 Windows EFS... 3 Apple FileVault... 4 Full Disk Encryption...
Forensically Determining the Presence and Use of Virtual Machines in Windows 7
 Forensically Determining the Presence and Use of Virtual Machines in Windows 7 Introduction Dustin Hurlbut Windows 7 has the ability to create and mount virtual machines based upon launching a single file.
Forensically Determining the Presence and Use of Virtual Machines in Windows 7 Introduction Dustin Hurlbut Windows 7 has the ability to create and mount virtual machines based upon launching a single file.
Whitepaper Enhancing BitLocker Deployment and Management with SimplySecure. Addressing the Concerns of the IT Professional Rob Weber February 2015
 Whitepaper Enhancing BitLocker Deployment and Management with SimplySecure Addressing the Concerns of the IT Professional Rob Weber February 2015 Page 2 Table of Contents What is BitLocker?... 3 What is
Whitepaper Enhancing BitLocker Deployment and Management with SimplySecure Addressing the Concerns of the IT Professional Rob Weber February 2015 Page 2 Table of Contents What is BitLocker?... 3 What is
CYBER FORENSICS. KRISHNA SASTRY PENDYALA Cyber Forensic Division Central Forensic Science Laboratory Hyderabad.
 CYBER FORENSICS KRISHNA SASTRY PENDYALA Cyber Forensic Division Central Forensic Science Laboratory Hyderabad. 11 DIGITAL EVIDENCE? Cyber crimes Digital evidence Digital evidence is any information of
CYBER FORENSICS KRISHNA SASTRY PENDYALA Cyber Forensic Division Central Forensic Science Laboratory Hyderabad. 11 DIGITAL EVIDENCE? Cyber crimes Digital evidence Digital evidence is any information of
Introduction to BitLocker FVE
 Introduction to BitLocker FVE (Understanding the Steps Required to enable BitLocker) Exploration of Windows 7 Advanced Forensic Topics Day 3 What is BitLocker? BitLocker Drive Encryption is a full disk
Introduction to BitLocker FVE (Understanding the Steps Required to enable BitLocker) Exploration of Windows 7 Advanced Forensic Topics Day 3 What is BitLocker? BitLocker Drive Encryption is a full disk
Just EnCase. Presented By Larry Russell CalCPA State Technology Committee May 18, 2012
 Just EnCase Presented By Larry Russell CalCPA State Technology Committee May 18, 2012 What is e-discovery Electronically Stored Information (ESI) Discover or Monitor for Fraudulent Activity Tools used
Just EnCase Presented By Larry Russell CalCPA State Technology Committee May 18, 2012 What is e-discovery Electronically Stored Information (ESI) Discover or Monitor for Fraudulent Activity Tools used
Digital Forensics. Tom Pigg Executive Director Tennessee CSEC
 Digital Forensics Tom Pigg Executive Director Tennessee CSEC Definitions Digital forensics Involves obtaining and analyzing digital information as evidence in civil, criminal, or administrative cases Analyze
Digital Forensics Tom Pigg Executive Director Tennessee CSEC Definitions Digital forensics Involves obtaining and analyzing digital information as evidence in civil, criminal, or administrative cases Analyze
Windows BitLocker Drive Encryption Step-by-Step Guide
 Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
Windows BitLocker Drive Encryption Step-by-Step Guide Microsoft Corporation Published: September 2006 Abstract Microsoft Windows BitLocker Drive Encryption is a new hardware-enhanced feature in the Microsoft
RECOVERING FROM SHAMOON
 Executive Summary Fidelis Threat Advisory #1007 RECOVERING FROM SHAMOON November 1, 2012 Document Status: FINAL Last Revised: 2012-11-01 The Shamoon malware has received considerable coverage in the past
Executive Summary Fidelis Threat Advisory #1007 RECOVERING FROM SHAMOON November 1, 2012 Document Status: FINAL Last Revised: 2012-11-01 The Shamoon malware has received considerable coverage in the past
TPM. (Trusted Platform Module) Installation Guide V3.3.0. for Windows Vista
 TPM (Trusted Platform Module) Installation Guide V3.3.0 for Windows Vista Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM...
TPM (Trusted Platform Module) Installation Guide V3.3.0 for Windows Vista Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM...
DISK DEFRAG Professional
 auslogics DISK DEFRAG Professional Help Manual www.auslogics.com / Contents Introduction... 5 Installing the Program... 7 System Requirements... 7 Installation... 7 Registering the Program... 9 Uninstalling
auslogics DISK DEFRAG Professional Help Manual www.auslogics.com / Contents Introduction... 5 Installing the Program... 7 System Requirements... 7 Installation... 7 Registering the Program... 9 Uninstalling
Alternate Data Streams in Forensic Investigations of File Systems Backups
 Alternate Data Streams in Forensic Investigations of File Systems Backups Derek Bem and Ewa Z. Huebner School of Computing and Mathematics University of Western Sydney d.bem@cit.uws.edu.au and e.huebner@cit.uws.edu.au
Alternate Data Streams in Forensic Investigations of File Systems Backups Derek Bem and Ewa Z. Huebner School of Computing and Mathematics University of Western Sydney d.bem@cit.uws.edu.au and e.huebner@cit.uws.edu.au
Encrypting with BitLocker for disk volumes under Windows 7
 Encrypting with BitLocker for disk volumes under Windows 7 Summary of the contents 1 Introduction 2 Hardware requirements for BitLocker Driver Encryption 3 Encrypting drive 3.1 Operating System Drive 3.1.1
Encrypting with BitLocker for disk volumes under Windows 7 Summary of the contents 1 Introduction 2 Hardware requirements for BitLocker Driver Encryption 3 Encrypting drive 3.1 Operating System Drive 3.1.1
Can Computer Investigations Survive Windows XP?
 Can Computer Investigations Survive? An Examination of Microsoft and its Effect on Computer Forensics December 2001 by Kimberly Stone and Richard Keightley 2001 Guidance Software All Rights Reserved Executive
Can Computer Investigations Survive? An Examination of Microsoft and its Effect on Computer Forensics December 2001 by Kimberly Stone and Richard Keightley 2001 Guidance Software All Rights Reserved Executive
Help System. Table of Contents
 Help System Table of Contents 1 INTRODUCTION...1 2 GETTING STARTED!... 2 2.1 Installation...2 2.2 Wizard...3 2.3 Browse Method:...7 2.4 Search Method:...7 2.5 Surface Scan Method:... 8 3 RECOVERING DELETED
Help System Table of Contents 1 INTRODUCTION...1 2 GETTING STARTED!... 2 2.1 Installation...2 2.2 Wizard...3 2.3 Browse Method:...7 2.4 Search Method:...7 2.5 Surface Scan Method:... 8 3 RECOVERING DELETED
IT Essentials v4.1 LI 11.4.5 Upgrade and configure storage devices and hard drives. IT Essentials v4.1 LI 12.1.3 Windows OS directory structures
 IT Essentials v4.1 LI 11.4.5 Upgrade and configure storage devices and hard drives 2.3 Disk management tools In Windows Vista and Windows 7, use the following path: Start > Start Search > type diskmgmt.msc
IT Essentials v4.1 LI 11.4.5 Upgrade and configure storage devices and hard drives 2.3 Disk management tools In Windows Vista and Windows 7, use the following path: Start > Start Search > type diskmgmt.msc
Table of Contents. TPM Configuration Procedure... 2. 1. Configuring the System BIOS... 2
 Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Table of Contents TPM Configuration Procedure... 2 1. Configuring the System BIOS... 2 2. Installing the Infineon TPM Driver and the GIGABYTE Ultra TPM Utility... 3 3. Initializing the TPM Chip... 4 3.1.
Computer Forensics and Investigations Duration: 5 Days Courseware: CT 0619217065
 Computer Forensics and Investigations Duration: 5 Days Courseware: CT 0619217065 Introduction The Computer Forensics and Investigation course presents methods to properly conduct a computer forensics investigation
Computer Forensics and Investigations Duration: 5 Days Courseware: CT 0619217065 Introduction The Computer Forensics and Investigation course presents methods to properly conduct a computer forensics investigation
Server & Client Optimization
 Table of Contents: Farmers WIFE / Farmers WIFE Advanced Make sure your Server specification is within the requirements... 2 Operating System... 2 Hardware... 2 Processor Server... 2 Memory... 2 Hard disk
Table of Contents: Farmers WIFE / Farmers WIFE Advanced Make sure your Server specification is within the requirements... 2 Operating System... 2 Hardware... 2 Processor Server... 2 Memory... 2 Hard disk
Using Virtual PC 7.0 for Mac with GalleryPro
 Using Virtual PC 7.0 for Mac with GalleryPro Installing and Configuring What is Virtual PC for Mac? Virtual PC (VPC) is emulation software that simulates an actual (though virtual) Windows computer running
Using Virtual PC 7.0 for Mac with GalleryPro Installing and Configuring What is Virtual PC for Mac? Virtual PC (VPC) is emulation software that simulates an actual (though virtual) Windows computer running
Managing Applications, Services, Folders, and Libraries
 Lesson 4 Managing Applications, Services, Folders, and Libraries Learning Objectives Students will learn to: Understand Local versus Network Applications Remove or Uninstall an Application Understand Group
Lesson 4 Managing Applications, Services, Folders, and Libraries Learning Objectives Students will learn to: Understand Local versus Network Applications Remove or Uninstall an Application Understand Group
Technical Procedure for Evidence Search
 Technical Procedure for Evidence Search 1.0 Purpose - The purpose of this procedure is to provide a systematic means of searching digital evidence in order to find data sought by the search authorization.
Technical Procedure for Evidence Search 1.0 Purpose - The purpose of this procedure is to provide a systematic means of searching digital evidence in order to find data sought by the search authorization.
Corrupt and Shutdown Dirty EVTX Log Files: A Comparison of Recovery Using the Microsoft Event Viewer Versus Ipswitch's LogHealer Technology
 Corrupt and Shutdown Dirty EVTX Log Files: A Comparison of Recovery Using the Microsoft Event Viewer Versus Ipswitch's LogHealer Technology As the Microsoft Windows Vista, Windows Server 2008, and Windows
Corrupt and Shutdown Dirty EVTX Log Files: A Comparison of Recovery Using the Microsoft Event Viewer Versus Ipswitch's LogHealer Technology As the Microsoft Windows Vista, Windows Server 2008, and Windows
Using WMI Scripts with BitDefender Client Security
 Using WMI Scripts with BitDefender Client Security Whitepaper Copyright 2009 BitDefender; Table of Contents 1. Introduction... 3 2. Key Benefits... 4 3. Available WMI Script Templates... 5 4. Operation...
Using WMI Scripts with BitDefender Client Security Whitepaper Copyright 2009 BitDefender; Table of Contents 1. Introduction... 3 2. Key Benefits... 4 3. Available WMI Script Templates... 5 4. Operation...
Smart TPM. User's Manual. Rev. 1001 12MD-STPM-1001R
 Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
Smart TPM User's Manual Rev. 1001 12MD-STPM-1001R We recommend that you download the latest version of the Smart TPM utility from GIGABYTE's website. If you have installed Ultra TPM earlier, you can install
MSc Computer Security and Forensics. Examinations for 2009-2010 / Semester 1
 MSc Computer Security and Forensics Cohort: MCSF/09B/PT Examinations for 2009-2010 / Semester 1 MODULE: COMPUTER FORENSICS & CYBERCRIME MODULE CODE: SECU5101 Duration: 2 Hours Instructions to Candidates:
MSc Computer Security and Forensics Cohort: MCSF/09B/PT Examinations for 2009-2010 / Semester 1 MODULE: COMPUTER FORENSICS & CYBERCRIME MODULE CODE: SECU5101 Duration: 2 Hours Instructions to Candidates:
In order to enable BitLocker, your hard drive must be partitioned in a particular manner.
 ENABLE BITLOCKER ON WINDOWS VISTA - WITHOUT A TPM Requirements: You must be running Vista Enterprise or Vista Ultimate to enable BitLocker. Any other version of Vista is not compatible. It is recommended
ENABLE BITLOCKER ON WINDOWS VISTA - WITHOUT A TPM Requirements: You must be running Vista Enterprise or Vista Ultimate to enable BitLocker. Any other version of Vista is not compatible. It is recommended
{ecasey, gstellatos}@strozllc.com
 The Impact of Full Disk Encryption on Digital Forensics Eoghan Casey, Director of Training, Gerasimos J. Stellatos, Digital Forensic Examiner Stroz Friedberg, LLC 1150 Connecticut Ave, NW Washington, DC
The Impact of Full Disk Encryption on Digital Forensics Eoghan Casey, Director of Training, Gerasimos J. Stellatos, Digital Forensic Examiner Stroz Friedberg, LLC 1150 Connecticut Ave, NW Washington, DC
ICT Professional Optional Programmes
 ICT Professional Optional Programmes Skills Team are a Microsoft Academy with new training rooms and IT labs in our purpose built training centre in Ealing, West London. We offer a range of year-long qualifications
ICT Professional Optional Programmes Skills Team are a Microsoft Academy with new training rooms and IT labs in our purpose built training centre in Ealing, West London. We offer a range of year-long qualifications
User Manual. Copyright Rogev LTD
 User Manual Copyright Rogev LTD Introduction Thank you for choosing FIXER1. This User's Guide is provided to you to familiar yourself with the program. You can find a complete list of all the program's
User Manual Copyright Rogev LTD Introduction Thank you for choosing FIXER1. This User's Guide is provided to you to familiar yourself with the program. You can find a complete list of all the program's
Incident Response and Computer Forensics
 Incident Response and Computer Forensics James L. Antonakos WhiteHat Forensics Incident Response Topics Why does an organization need a CSIRT? Who s on the team? Initial Steps Detailed Project Plan Incident
Incident Response and Computer Forensics James L. Antonakos WhiteHat Forensics Incident Response Topics Why does an organization need a CSIRT? Who s on the team? Initial Steps Detailed Project Plan Incident
File System Forensics FAT and NTFS. Copyright Priscilla Oppenheimer 1
 File System Forensics FAT and NTFS 1 FAT File Systems 2 File Allocation Table (FAT) File Systems Simple and common Primary file system for DOS and Windows 9x Can be used with Windows NT, 2000, and XP New
File System Forensics FAT and NTFS 1 FAT File Systems 2 File Allocation Table (FAT) File Systems Simple and common Primary file system for DOS and Windows 9x Can be used with Windows NT, 2000, and XP New
BitLocker To Go User Guide
 BitLocker To Go User Guide 1. Introduction BitLocker To Go a new feature of Windows 7 is a full-disk encryption protection technology for removable storage devices that are connected to one of the USB
BitLocker To Go User Guide 1. Introduction BitLocker To Go a new feature of Windows 7 is a full-disk encryption protection technology for removable storage devices that are connected to one of the USB
Impact of Digital Forensics Training on Computer Incident Response Techniques
 Impact of Digital Forensics Training on Computer Incident Response Techniques Valorie J. King, PhD Collegiate Associate Professor University of Maryland University College Presentation to AFCEA June 25,
Impact of Digital Forensics Training on Computer Incident Response Techniques Valorie J. King, PhD Collegiate Associate Professor University of Maryland University College Presentation to AFCEA June 25,
Managing and Supporting Windows XP Chapter #16
 Managing and Supporting Windows XP Chapter #16 Amy Hissom Key Terms Backup Operator A Windows 2000/XP user account that can back up and restore any files on the system regardless of its having access to
Managing and Supporting Windows XP Chapter #16 Amy Hissom Key Terms Backup Operator A Windows 2000/XP user account that can back up and restore any files on the system regardless of its having access to
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
EVALUATION OF REGISTRY DATA REMOVAL BY SHREDDER PROGRAMS
 Chapter 5 EVALUATION OF REGISTRY DATA REMOVAL BY SHREDDER PROGRAMS Harry Velupillai and Pontjho Mokhonoana Abstract Shredder programs attempt to overcome Window s inherent inability to erase data completely.
Chapter 5 EVALUATION OF REGISTRY DATA REMOVAL BY SHREDDER PROGRAMS Harry Velupillai and Pontjho Mokhonoana Abstract Shredder programs attempt to overcome Window s inherent inability to erase data completely.
NovaBACKUP. User Manual. NovaStor / November 2011
 NovaBACKUP User Manual NovaStor / November 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without
NovaBACKUP User Manual NovaStor / November 2011 2011 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without
Computer Forensic Capabilities
 Computer Forensic Capabilities Agenda What is computer forensics? Where to find computer evidence Forensic imaging Forensic analysis What is Computer Forensics? The preservation, identification, extraction,
Computer Forensic Capabilities Agenda What is computer forensics? Where to find computer evidence Forensic imaging Forensic analysis What is Computer Forensics? The preservation, identification, extraction,
Advanced Methods and Techniques
 2013 CTIN Digital Forensics Conference Advanced Methods and Techniques Brett Shavers 2013 CTIN Digital Forensics Conference The XWF Book Not done yet Eric Zimmerman (FBI) is the coauthor Jimmy Weg is the
2013 CTIN Digital Forensics Conference Advanced Methods and Techniques Brett Shavers 2013 CTIN Digital Forensics Conference The XWF Book Not done yet Eric Zimmerman (FBI) is the coauthor Jimmy Weg is the
DIGIPASS CertiID. Getting Started 3.1.0
 DIGIPASS CertiID Getting Started 3.1.0 Disclaimer Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without any other warranties, or conditions, express
DIGIPASS CertiID Getting Started 3.1.0 Disclaimer Disclaimer of Warranties and Limitations of Liabilities The Product is provided on an 'as is' basis, without any other warranties, or conditions, express
Digital Forensics Tutorials Acquiring an Image with FTK Imager
 Digital Forensics Tutorials Acquiring an Image with FTK Imager Explanation Section Digital Forensics Definition The use of scientifically derived and proven methods toward the preservation, collection,
Digital Forensics Tutorials Acquiring an Image with FTK Imager Explanation Section Digital Forensics Definition The use of scientifically derived and proven methods toward the preservation, collection,
(b) slack file space.
 Hidden Files A Computer Forensics Case Study Question Paper 1. Outline the meaning of the following terms: (a) cookie, [2 marks] A cookie is data stored locally that is used by some websites for data that
Hidden Files A Computer Forensics Case Study Question Paper 1. Outline the meaning of the following terms: (a) cookie, [2 marks] A cookie is data stored locally that is used by some websites for data that
Gladinet Cloud Backup V3.0 User Guide
 Gladinet Cloud Backup V3.0 User Guide Foreword The Gladinet User Guide gives step-by-step instructions for end users. Revision History Gladinet User Guide Date Description Version 8/20/2010 Draft Gladinet
Gladinet Cloud Backup V3.0 User Guide Foreword The Gladinet User Guide gives step-by-step instructions for end users. Revision History Gladinet User Guide Date Description Version 8/20/2010 Draft Gladinet
BackupAssist v6 quickstart guide
 Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Using the new features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 2 Backing up VSS applications... 2 Restoring VSS applications... 3 System State backup and restore...
Windows Offline Files
 Windows Offline Files 1. Description: Windows Offline Files or Client Side Caching (CSC) allows files and folders stored on any Server Message Block (SMB) network share to be available offline. To further
Windows Offline Files 1. Description: Windows Offline Files or Client Side Caching (CSC) allows files and folders stored on any Server Message Block (SMB) network share to be available offline. To further
How to Encrypt your Windows 7 SDS Machine with Bitlocker
 How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
How to Encrypt your Windows 7 SDS Machine with Bitlocker ************************************ IMPORTANT ******************************************* Before encrypting your SDS Windows 7 Machine it is highly
Microsoft Diagnostics and Recovery Toolset 7 Evaluation Guide
 Microsoft Diagnostics and Recovery Toolset 7 Evaluation Guide White Paper Descriptor This document provides administrators with information and steps-by-step technique for deploying Microsoft Diagnostics
Microsoft Diagnostics and Recovery Toolset 7 Evaluation Guide White Paper Descriptor This document provides administrators with information and steps-by-step technique for deploying Microsoft Diagnostics
Cautions When Using BitLocker Drive Encryption on PRIMERGY
 Cautions When Using BitLocker Drive Encryption on PRIMERGY July 2008 Fujitsu Limited Table of Contents Preface...3 1 Recovery mode...4 2 Changes in hardware configurations...5 3 Prior to hardware maintenance
Cautions When Using BitLocker Drive Encryption on PRIMERGY July 2008 Fujitsu Limited Table of Contents Preface...3 1 Recovery mode...4 2 Changes in hardware configurations...5 3 Prior to hardware maintenance
Retrieving Internet chat history with the same ease as a squirrel cracks nuts
 Retrieving Internet chat history with the same ease as a squirrel Yuri Gubanov CEO, Belkasoft http://belkasoft.com SANS Forensic Summit September 21, 2011 London, Great Britain What is Instant Messenger!
Retrieving Internet chat history with the same ease as a squirrel Yuri Gubanov CEO, Belkasoft http://belkasoft.com SANS Forensic Summit September 21, 2011 London, Great Britain What is Instant Messenger!
Operating Systems Forensics
 Operating Systems Forensics Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2015 Nuno Santos Summary! Windows boot sequence! Relevant Windows data structures!
Operating Systems Forensics Section II. Basic Forensic Techniques and Tools CSF: Forensics Cyber-Security MSIDC, Spring 2015 Nuno Santos Summary! Windows boot sequence! Relevant Windows data structures!
The Meaning. Linkfiles In Forensic Examinations
 The Meaning of Linkfiles In Forensic Examinations A look at the practical value to forensic examinations of dates and times, and object identifiers in Windows shortcut files. Harry Parsonage September
The Meaning of Linkfiles In Forensic Examinations A look at the practical value to forensic examinations of dates and times, and object identifiers in Windows shortcut files. Harry Parsonage September
COMPUTER FORENSICS. DAVORY: : DATA RECOVERY
 COMPUTER FORENSICS. DAVORY: : DATA RECOVERY Supervised By: Dr. Lo ai Tawalbeh New York Institute of Technology (NYIT)-Amman-2006 TOPICS Definition Recovery from what?? Davory SOFTWARE. Restore Software.
COMPUTER FORENSICS. DAVORY: : DATA RECOVERY Supervised By: Dr. Lo ai Tawalbeh New York Institute of Technology (NYIT)-Amman-2006 TOPICS Definition Recovery from what?? Davory SOFTWARE. Restore Software.
Encrypting the Private Files on Your Computer Presentation by Eric Moore, CUGG June 12, 2010
 Encrypting the Private Files on Your Computer Presentation by Eric Moore, CUGG June 12, 2010 I. File Encryption Basics A. Encryption replaces data within a file with ciphertext which resembles random data
Encrypting the Private Files on Your Computer Presentation by Eric Moore, CUGG June 12, 2010 I. File Encryption Basics A. Encryption replaces data within a file with ciphertext which resembles random data
Advanced Event Viewer Manual
 Advanced Event Viewer Manual Document version: 2.2944.01 Download Advanced Event Viewer at: http://www.advancedeventviewer.com Page 1 Introduction Advanced Event Viewer is an award winning application
Advanced Event Viewer Manual Document version: 2.2944.01 Download Advanced Event Viewer at: http://www.advancedeventviewer.com Page 1 Introduction Advanced Event Viewer is an award winning application
Digital Forensics. Larry Daniel
 Digital Forensics Larry Daniel Introduction A recent research report from The Yankee Group found that 67.6 percent of US households in 2002 contained at least one PC The investigators foresee three-quarters
Digital Forensics Larry Daniel Introduction A recent research report from The Yankee Group found that 67.6 percent of US households in 2002 contained at least one PC The investigators foresee three-quarters
Events Forensic Tools for Microsoft Windows
 Events Forensic Tools for Microsoft Windows Professional forensic tools Events Forensic Tools for Windows Easy Events Log Management Events Forensic Tools (EFT) is a fast, easy to use and very effective
Events Forensic Tools for Microsoft Windows Professional forensic tools Events Forensic Tools for Windows Easy Events Log Management Events Forensic Tools (EFT) is a fast, easy to use and very effective
ADMINISTERING WINDOWS VISTA SECURITY: THE BIG SURPRISES
 ADMINISTERING WINDOWS VISTA SECURITY: THE BIG SURPRISES Introduction. Chapter 1 Administering Vista Security: The Little Surprises. Restoring the Administrator. Making Your Own Administrator. Activating
ADMINISTERING WINDOWS VISTA SECURITY: THE BIG SURPRISES Introduction. Chapter 1 Administering Vista Security: The Little Surprises. Restoring the Administrator. Making Your Own Administrator. Activating
Backup and Disaster Recovery Restoration Guide
 Backup and Disaster Recovery Restoration Guide Page 1 Table of Contents Table of Contents...2 Terms of Use...3 BDR...4 Creating Point-in-Time Restoration Volumes...4 Mounting a Restoration Volume...4 Dismounting
Backup and Disaster Recovery Restoration Guide Page 1 Table of Contents Table of Contents...2 Terms of Use...3 BDR...4 Creating Point-in-Time Restoration Volumes...4 Mounting a Restoration Volume...4 Dismounting
DataCove. Installation Instructions for Search Plug-in for Microsoft Outlook 2007 & 2010 (All Users)
 Installation Instructions for Search Plug-in for Microsoft Outlook 2007 & 2010 (All Users) System Requirements: Windows XP, Vista or 7 Outlook 2007 or 2010 32 bit Editions 1GB of RAM Microsoft.NET Framework
Installation Instructions for Search Plug-in for Microsoft Outlook 2007 & 2010 (All Users) System Requirements: Windows XP, Vista or 7 Outlook 2007 or 2010 32 bit Editions 1GB of RAM Microsoft.NET Framework
Using Bitlocker to Encrypt your Flash Drive Information Technology Services July 27, 2012
 Using Bitlocker to Encrypt your Flash Drive Information Technology Services July 27, 2012 Contact the ITS Helpdesk at 402-559-7700 or helpdesk@unmc.edu with questions. How it works Basically, BitLocker
Using Bitlocker to Encrypt your Flash Drive Information Technology Services July 27, 2012 Contact the ITS Helpdesk at 402-559-7700 or helpdesk@unmc.edu with questions. How it works Basically, BitLocker
Basic ShadowProtect Troubleshooting
 Level 11, 53 Walker Street North Sydney NSW 2060 Australia t +61 2 9929 9770 f +61 2 9929 9771 w www.storagecraft.com.au Basic ShadowProtect Synopsis This article describes basic ShadowProtect troubleshooting
Level 11, 53 Walker Street North Sydney NSW 2060 Australia t +61 2 9929 9770 f +61 2 9929 9771 w www.storagecraft.com.au Basic ShadowProtect Synopsis This article describes basic ShadowProtect troubleshooting
HW 07: Ch 12 Investigating Windows
 1 of 7 5/15/2015 2:40 AM HW 07: Ch 12 Investigating Windows Click 'check' on each question or your score will not be recorded. resources: windows special folders ntfs.com Windows cmdline ref how ntfs works
1 of 7 5/15/2015 2:40 AM HW 07: Ch 12 Investigating Windows Click 'check' on each question or your score will not be recorded. resources: windows special folders ntfs.com Windows cmdline ref how ntfs works
RecoverIt Frequently Asked Questions
 RecoverIt Frequently Asked Questions Windows Recovery FAQs When can I use Windows Recovery application? This application is used to recover the deleted files from internal or external storage devices with
RecoverIt Frequently Asked Questions Windows Recovery FAQs When can I use Windows Recovery application? This application is used to recover the deleted files from internal or external storage devices with
StarWind iscsi SAN Software: Implementation of Enhanced Data Protection Using StarWind Continuous Data Protection
 StarWind iscsi SAN Software: Implementation of Enhanced Data Protection Using StarWind Continuous Data Protection www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright
StarWind iscsi SAN Software: Implementation of Enhanced Data Protection Using StarWind Continuous Data Protection www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright
How to enable Disk Encryption on a laptop
 How to enable Disk Encryption on a laptop Skills and pre-requisites Intermediate IT skills required. You need to: have access to, and know how to change settings in the BIOS be confident that your data
How to enable Disk Encryption on a laptop Skills and pre-requisites Intermediate IT skills required. You need to: have access to, and know how to change settings in the BIOS be confident that your data
TPM. (Trusted Platform Module) Installation Guide V2.1
 TPM (Trusted Platform Module) Installation Guide V2.1 Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM... 6 2.2 Installing
TPM (Trusted Platform Module) Installation Guide V2.1 Table of contents 1 Introduction 1.1 Convention... 4 1.2 TPM - An Overview... 5 2 Using TPM for the first time 2.1 Enabling TPM... 6 2.2 Installing
Digital Forensic Tool for Decision Making in Computer Security Domain
 Digital Forensic Tool for Decision Making in Computer Security Domain S. K. Khode 1,V. N. Pahune 2 and M. R. Sayankar 3 1, 2, 3 Computer Engineering Department of Bapurao Deshmukh College of Engineering,
Digital Forensic Tool for Decision Making in Computer Security Domain S. K. Khode 1,V. N. Pahune 2 and M. R. Sayankar 3 1, 2, 3 Computer Engineering Department of Bapurao Deshmukh College of Engineering,
Recovers Lost or Deleted Pictures from: Any Memory Card Type Any Brand Using Any Mass Storage Reader
 Recovers Lost or Deleted Pictures from: Any Memory Card Type Any Brand Using Any Mass Storage Reader Reader and Media not included Image Recovery - Recovers lost or deleted image files (JPEG, TIFF and
Recovers Lost or Deleted Pictures from: Any Memory Card Type Any Brand Using Any Mass Storage Reader Reader and Media not included Image Recovery - Recovers lost or deleted image files (JPEG, TIFF and
Windows BitLocker and Paragon s Backup Solutions
 PARAGON Software GmbH Heinrich-von-Stephan-Str. 5c 79100 Freiburg, Germany Tel. +49 (0) 761 59018201 Fax +49 (0) 761 59018130 Internet www.paragon-software.com Email sales@paragon-software.com Windows
PARAGON Software GmbH Heinrich-von-Stephan-Str. 5c 79100 Freiburg, Germany Tel. +49 (0) 761 59018201 Fax +49 (0) 761 59018130 Internet www.paragon-software.com Email sales@paragon-software.com Windows
BackupAssist v6 quickstart guide
 New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
New features in BackupAssist v6... 2 VSS application backup (Exchange, SQL, SharePoint)... 3 System State backup... 3 Restore files, applications, System State and mailboxes... 4 Fully cloud ready Internet
Simnet Registry Repair 2011. User Guide. Edition 1.3
 Simnet Registry Repair 2011 User Guide Edition 1.3 1 Content Getting Started...3 System requirements...3 Minimum system requirements...3 Recomended system specifications...3 Program Overview...4 About
Simnet Registry Repair 2011 User Guide Edition 1.3 1 Content Getting Started...3 System requirements...3 Minimum system requirements...3 Recomended system specifications...3 Program Overview...4 About
Detection of Data Hiding in Computer Forensics. About Your Presenter
 Detection of Data Hiding in Computer Forensics NEbraskaCERT Conference August 22nd, 2008 James E. Martin CISSP, JD About Your Presenter 2008-Present: Security Engineer, West Corporation 2004-2008: Senior
Detection of Data Hiding in Computer Forensics NEbraskaCERT Conference August 22nd, 2008 James E. Martin CISSP, JD About Your Presenter 2008-Present: Security Engineer, West Corporation 2004-2008: Senior
Practice test 220-802 Domain-2 Security (Brought to you by RMRoberts.com)
 Practice test 220-802 Domain-2 Security (Brought to you by RMRoberts.com) 1. Which command is used to access the local group policy editor for Windows 7? A. poledit.exe B. gpedit.msc C. local.msc D. grplocal.exe
Practice test 220-802 Domain-2 Security (Brought to you by RMRoberts.com) 1. Which command is used to access the local group policy editor for Windows 7? A. poledit.exe B. gpedit.msc C. local.msc D. grplocal.exe
Table of Contents. Online backup Manager User s Guide
 Table of Contents Backup / Restore Windows System State... 2 Supported versions... 2 Requirements and recommendations... 2 1.1 Overview... 4 1.2 How to backup Windows System State... 5 1.2.1 For Windows
Table of Contents Backup / Restore Windows System State... 2 Supported versions... 2 Requirements and recommendations... 2 1.1 Overview... 4 1.2 How to backup Windows System State... 5 1.2.1 For Windows
Chapter Contents. Operating System Activities. Operating System Basics. Operating System Activities. Operating System Activities 25/03/2014
 Chapter Contents Operating Systems and File Management Section A: Operating System Basics Section B: Today s Operating Systems Section C: File Basics Section D: File Management Section E: Backup Security
Chapter Contents Operating Systems and File Management Section A: Operating System Basics Section B: Today s Operating Systems Section C: File Basics Section D: File Management Section E: Backup Security
Hyper-V backup implementation guide
 Hyper-V backup implementation guide A best practice guide for Hyper-V backup administrators. www.backup-assist.ca Contents 1. Planning a Hyper-V backup... 2 Hyper-V backup considerations... 2 2. Hyper-V
Hyper-V backup implementation guide A best practice guide for Hyper-V backup administrators. www.backup-assist.ca Contents 1. Planning a Hyper-V backup... 2 Hyper-V backup considerations... 2 2. Hyper-V
S m a r t M a s t e B T E C O R P O R A T I O N USER MANUAL
 S m a r t M a s t e rtm 2014 B T E C O R P O R A T I O N USER MANUAL S m a r t M a s t e r T M 2 0 1 4 U s e r M a n u a l P a g e 1 o f 2 3 Contents Contents...1 Introduction...2 Audience...2 SmartMaster
S m a r t M a s t e rtm 2014 B T E C O R P O R A T I O N USER MANUAL S m a r t M a s t e r T M 2 0 1 4 U s e r M a n u a l P a g e 1 o f 2 3 Contents Contents...1 Introduction...2 Audience...2 SmartMaster
Forensic Decryption of FAT BitLocker Volumes
 Forensic Decryption of FAT BitLocker Volumes P. Shabana Subair, C. Balan (&), S. Dija, and K.L. Thomas Centre for Development of Advanced Computing, PO Box 6520, Vellayambalam, Thiruvananthapuram 695033,
Forensic Decryption of FAT BitLocker Volumes P. Shabana Subair, C. Balan (&), S. Dija, and K.L. Thomas Centre for Development of Advanced Computing, PO Box 6520, Vellayambalam, Thiruvananthapuram 695033,
Hiva-network.com. Microsoft_70-680_v2011-06-22_Kat. Exam A
 Exam A Microsoft_70-680_v2011-06-22_Kat QUESTION 1 You have a computer that runs Windows 7. The computer has a single volume. You install 15 applications and customize the environment. You complete the
Exam A Microsoft_70-680_v2011-06-22_Kat QUESTION 1 You have a computer that runs Windows 7. The computer has a single volume. You install 15 applications and customize the environment. You complete the
Legal Notes. Regarding Trademarks. 2012 KYOCERA Document Solutions Inc.
 Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Chapter 4. Operating Systems and File Management
 Chapter 4 Operating Systems and File Management Chapter Contents Section A: Operating System Basics Section B: Today s Operating Systems Section C: File Basics Section D: File Management Section E: Backup
Chapter 4 Operating Systems and File Management Chapter Contents Section A: Operating System Basics Section B: Today s Operating Systems Section C: File Basics Section D: File Management Section E: Backup
Lenovo Online Data Backup User Guide Version 1.8.14
 Lenovo Online Data Backup User Guide Version 1.8.14 Contents Chapter 1: Installing Lenovo Online Data Backup...5 Downloading the Lenovo Online Data Backup Client...5 Installing the Lenovo Online Data
Lenovo Online Data Backup User Guide Version 1.8.14 Contents Chapter 1: Installing Lenovo Online Data Backup...5 Downloading the Lenovo Online Data Backup Client...5 Installing the Lenovo Online Data
How to Reinstall SQL Server 2005
 How to Reinstall SQL Server 2005 Sometimes a problem occurs during the installation of SQL Server and it needs to be completely reinstalled. This quick reference guide will help you reinstall SQL Server
How to Reinstall SQL Server 2005 Sometimes a problem occurs during the installation of SQL Server and it needs to be completely reinstalled. This quick reference guide will help you reinstall SQL Server
Understanding Backup and Recovery Methods
 Lesson 8 Understanding Backup and Recovery Methods Learning Objectives Students will learn to: Understand Local, Online, and Automated Backup Methods Understand Backup Options Understand System Restore
Lesson 8 Understanding Backup and Recovery Methods Learning Objectives Students will learn to: Understand Local, Online, and Automated Backup Methods Understand Backup Options Understand System Restore
Cleaning your Windows 7, Windows XP and Macintosh OSX Computers
 Cleaning your Windows 7, Windows XP and Macintosh OSX Computers A cleaning of your computer can help your computer run faster and make you more efficient. We have listed some tools and how to use these
Cleaning your Windows 7, Windows XP and Macintosh OSX Computers A cleaning of your computer can help your computer run faster and make you more efficient. We have listed some tools and how to use these
An Application Footprint Reference Set: Tracking the Lifetime of Software
 An Application Footprint Reference Set: Tracking the Lifetime of Software Mary Laamanen & John Tebbutt National Software Reference Library National Institute of Standards and Technology Motivation Gather
An Application Footprint Reference Set: Tracking the Lifetime of Software Mary Laamanen & John Tebbutt National Software Reference Library National Institute of Standards and Technology Motivation Gather
Upgrading Client Security and Policy Manager in 4 easy steps
 Page 1 of 13 F-Secure White Paper Upgrading Client Security and Policy Manager in 4 easy steps Purpose This white paper describes how to easily upgrade your existing environment running Client Security
Page 1 of 13 F-Secure White Paper Upgrading Client Security and Policy Manager in 4 easy steps Purpose This white paper describes how to easily upgrade your existing environment running Client Security
MapInfo License Server Utility
 MapInfo License Server Utility Version 2.0 PRODUCT GUIDE Information in this document is subject to change without notice and does not represent a commitment on the part of the vendor or its representatives.
MapInfo License Server Utility Version 2.0 PRODUCT GUIDE Information in this document is subject to change without notice and does not represent a commitment on the part of the vendor or its representatives.
RECOVERING DELETED DATA FROM FAT PARTITIONS WITHIN MOBILE PHONE HANDSETS USING TRADITIONAL IMAGING TECHNIQUES
 RECOVERING DELETED DATA FROM FAT PARTITIONS WITHIN MOBILE PHONE HANDSETS USING TRADITIONAL IMAGING TECHNIQUES KEVIN MANSELL CONTROL-F LTD. KEVIN.MANSELL@CONTROLF.CO.UK DARREN LOLE & FIONA LITCHFIELD SERVICE
RECOVERING DELETED DATA FROM FAT PARTITIONS WITHIN MOBILE PHONE HANDSETS USING TRADITIONAL IMAGING TECHNIQUES KEVIN MANSELL CONTROL-F LTD. KEVIN.MANSELL@CONTROLF.CO.UK DARREN LOLE & FIONA LITCHFIELD SERVICE
NetDocuments Local Document Service
 NetDocuments Local Document Service Overview The NetDocuments Local Document Service allows NetDocuments customers to maintain a complete, up-to-date copy of all their documents and document Profiles on
NetDocuments Local Document Service Overview The NetDocuments Local Document Service allows NetDocuments customers to maintain a complete, up-to-date copy of all their documents and document Profiles on
Active @ UNDELETE Users Guide
 Active @ UNDELETE Users Guide Contents 2 Contents Legal Statement...5 Active@ UNDELETE Overview... 6 Getting Started with Active@ UNDELETE... 7 Active@ UNDELETE Views And Windows... 7 Recovery Explorer
Active @ UNDELETE Users Guide Contents 2 Contents Legal Statement...5 Active@ UNDELETE Overview... 6 Getting Started with Active@ UNDELETE... 7 Active@ UNDELETE Views And Windows... 7 Recovery Explorer
Guidelines on use of encryption to protect person identifiable and sensitive information
 Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
Guidelines on use of encryption to protect person identifiable and sensitive information 1. Introduction David Nicholson, NHS Chief Executive, has directed that there should be no transfers of unencrypted
Paul McFedries. Home Server 2011 LEASHE. Third Edition. 800 East 96th Street, Indianapolis, Indiana 46240 USA
 Paul McFedries Microsoft Windows9 Home Server 2011 LEASHE Third Edition 800 East 96th Street, Indianapolis, Indiana 46240 USA Table of Contents Introduction 1 Part I Unleashing Windows Home Server Configuration
Paul McFedries Microsoft Windows9 Home Server 2011 LEASHE Third Edition 800 East 96th Street, Indianapolis, Indiana 46240 USA Table of Contents Introduction 1 Part I Unleashing Windows Home Server Configuration
HP Personal Workstations Step-By- Step Instructions for Upgrading Windows Vista or Windows XP Systems to Windows 7
 HP Personal Workstations Step-By- Step Instructions for Upgrading Windows Vista or Windows XP Systems to Windows 7 September 15, 2009 Introduction HP is committed to supporting our customer s operating
HP Personal Workstations Step-By- Step Instructions for Upgrading Windows Vista or Windows XP Systems to Windows 7 September 15, 2009 Introduction HP is committed to supporting our customer s operating
Advanced Diploma In Hardware, Networking & Server Configuration
 Advanced Diploma In Hardware, Networking & Server Configuration Who should do this course? This course is meant for those persons who have a dream of getting job based on Computer Hardware, Networking
Advanced Diploma In Hardware, Networking & Server Configuration Who should do this course? This course is meant for those persons who have a dream of getting job based on Computer Hardware, Networking
ENTERPRISE COMPUTER INCIDENT RESPONSE AND FORENSICS TRAINING
 ENTERPRISE COMPUTER INCIDENT RESPONSE AND FORENSICS TRAINING MODULE A INTRODUCTION TO COMPUTER FORENSICS AND NVESTIGATIONS A1.0 Explain concepts related to computer forensics. A1.1 This module is measured
ENTERPRISE COMPUTER INCIDENT RESPONSE AND FORENSICS TRAINING MODULE A INTRODUCTION TO COMPUTER FORENSICS AND NVESTIGATIONS A1.0 Explain concepts related to computer forensics. A1.1 This module is measured
Password Memory 6 User s Guide
 C O D E : A E R O T E C H N O L O G I E S Password Memory 6 User s Guide 2007-2015 by code:aero technologies Phone: +1 (321) 285.7447 E-mail: info@codeaero.com Table of Contents Password Memory 6... 1
C O D E : A E R O T E C H N O L O G I E S Password Memory 6 User s Guide 2007-2015 by code:aero technologies Phone: +1 (321) 285.7447 E-mail: info@codeaero.com Table of Contents Password Memory 6... 1
