Gizmo, a lightweight open source web proxy Rachel Engel : June, 2009
|
|
|
- Shanna Sims
- 8 years ago
- Views:
Transcription
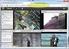
1 isec Partners, Inc. Gizmo, a lightweight open source web proxy Rachel Engel : June, 2009 The world needs a small, fast, cross-platform graphical web proxy. People spend a lot of time debugging web applications, and often they do so with complex tools that attempt to solve highly domain specific problems (like finding weak session identifiers, improperly used cookies, etc). Web technologies have diverse enough technical representations that it's often a thorny issue to detect every vulnerability in an automatable, generic way. Even if one can generate vulnerabilities and bugs automatically, a truly thorough web security analysis needs a human performing the analysis to understand the corner cases, new technologies, and business logic vulnerabilities that an automated scanner may not find. With this in mind, gizmo is a tool for people who are doing non-automated web security analysis and want a small, concise tool with which to do so. The goal is to be a concise http editing pocket knife. The decomposition of the process of website analysis into its constituent parts is the domain of a great many security tools, and applications attempt to attack this problem in different ways. If the website is viewed as a series of vulnerabilities, and the web security tool as an application that helps the user browse the attack surface s vulnerabilities, then a GUI tool with heavyweight analysis features is ideal. This approach works well for what it does, but it doesn t find every vulnerability, and it doesn t serve every need. For programmers, an approach that lets them treat the web session as data to be operated on is slightly more natural. Web technologies change constantly, and someone fluent with the protocols and languages involved is often going to want to work as directly with the protocol or language as possible. Languages, protocols, and technologies change over time, making automated tools in need of repair and updating. A programmer will likely prefer to infer the model from the data themselves, and test the properties of the model by interacting with it directly. For web application security analysis, this often means the programmer will want to work directly with the http traffic, having tools with a set of features targeted at letting them view and edit http traffic. This is gizmo s approach. Gizmo provides functionality for viewing, manipulating, searching, and sending http requests. It does no automated analysis. A short introduction follows to give the give the reader a flavor of a typical gizmo session. Java 1.6 is gizmo s only prerequisite. To install gizmo, unzip gizmo.zip into a directory of your choice, then click on gizmo.jar in the resulting directory. At this point, a small window like the one below appears:
2 The title bar at the top is used for information about the state of gizmo. In the image above, gizmo is listening on port 8080 (on localhost), and is not intercepting. The port can be altered by selecting File->Config and entering a port. The title bar will be updated to reflect the new port setting. The user then sets their web browsers proxy to use localhost:8080. Browsing the web at this point will cause http requests to show up in gizmo in the tab marked 'summary'. The display in this tab represents each http message that passes through gizmo with the status line of the message. The status line is considered a sort of 'minimized' state of display. If the user wants to see the full size of the request (maybe to further identify it), they can scroll down to the request (using the arrow keys, j/k, home/end or G/H) and hit <enter> to expand it. At this point the request will expand to its full size. One issue that gizmo handles slightly differently than other tools is the issue of handling different request encodings. A common tactic is to decode the request automatically or in a user-invokable way in the GUI. As a tool, gizmo deals primarily with text, and pictures or hex editors look awkward embedded in a text display. There are a number of external tools that will display pictures or provide hex
3 editing much better than a web proxy will. Gizmo makes it very easy to interoperate with other tools, leaving the user to decide how to process requests. Gizmo provides an editor/terminal that lets the user process requests via external programs (python scripts, shell scripts, hex editors, image viewers, etc). The integration is done in a way that should allow any program that takes command line arguments to interoperate nicely with gizmo s command shell mode. To use editing mode, scroll down to a request you'd like to process and hit 'e'. A window like the following is displayed: The current request is copied into the upper pane in this window after the user invokes editing mode. The request can be edited manually. When the window is closed (either by clicking it closed or hitting escape), the contents of the upper pane get placed in the summary tab of the main window as a new request. The request can then be sent by typing s. This editor window can also be used as a terminal to modify the request via external programs, interpreted languages, or shell scripting environments. The terminal mode is built around a java s exec function (java.lang.runtime getruntime().exec(string[] cmdarray, String[] envp). Any time the user hits enter at the command line in the editor window, the strings in the default shell field and in the command line field are concatenated and run. If the default shell field were blank, and the user types: cmd.exe /c echo hello on the command line, the command would be run. After the command is run, stdout and stderr of the resulting process are be displayed in the grey area at the bottom. If the defaults hell window had cmd.exe /c echo and the user typed hello on the command line, you would see the same result. The default shell field is where the user enters the shell prefix needed to invoke their commands ( sh c, cmd /c, python c, etc). This is provided as a typing convenience to save the user from retyping their shell constantly.
4 The actual integration with gizmo comes in the form of an environment variable. Before the command is executed, the request is serialized to a temporary file, and the filename is stored in the BUF environment variable. Pass %BUF% or $BUF to your script, and your script can work directly with the contents of the request. After the command is finished executing, the contents of the file are re-read and used to replace the current contents of the editor window. The flow for programmably manipulating requests like this is: 1. Select request for editing 2. Pass request to script ( script.py $BUF ) 3. Tweak results by hand in the editing pane 4. Close editing window 5. Send Composing multiple decodings is easy to do with a few small scripts. For example, the user could write one small script that base64 decodes a request (base64d below), and another that URL decodes it (urld). The user can compose the two scripts to base64 decode and URL decode a request by running the command: base64d %BUF% && urld %BUF% Adding esoteric decodings using this method is as simple as adding another step to the pipeline or modifying existing scripts. This feature can also be used on smaller pieces of the full HTTP message. If a piece of text is selected in the request editor when the user hits enter, gizmo uses that selection as the contents of %BUF% instead of the full request. When the command finishes executing, the selection will be replaced by the new contents of %BUF%. This allows you to apply encodings selectively to different parts of the request. Basic editing flows like this highlight the intended minimalistic experience. Gizmo includes features for searching requests, manipulating requests, and sending requests. Intercepting Requests: The proxy is either intercepting requests, or it s not. This mode can be toggled by clicking the radio button in the lower right or pressing <CTRL>-I. In normal operation, requests go straight to the summary tab without user intervention. In intercept mode, requests are put into a holding state in the intercept tab. Requests in the intercept tab have not been sent to the server. Once the user hits s on a request, the request is sent and moved over to the summary tab.
5 Universal Commands: The following commands work identically whether or not gizmo is in intercept mode. j, <down> moves the cursor down one request k, <up> - moves the cursor up one request G, <end> - moves to the last request H, <home> - moves to the first request <enter> - toggles the expanded/contracted view of a request e - opens up the editor mode <ctrl>- i - toggles intercept mode (can also be done via the radio button in the lower right) Context-Dependant: The behavior of these commands depends on whether or not gizmo is intercepting requests. d s - deletes an intercepted request, sending a proxy error message to the client - s exists whether or not gizmo is intercepting. If gizmo is in intercept mode, it removes the sent request from the intercept tab and places it and the associated response in the summary tab. If gizmo is not intercepting, it sends the request and places the response right below its associated request in the summary pane. Gizmo is an open source tool that s under active development, with current development focused on: - adding new means of manipulating requests in gizmo with a focus on a keyboard-driven command interface - expanding shell manipulation mode Gizmo releases and source can be found on the web at
6 isec Partners, Inc. Appendix A: About isec Partners, Inc. isec Partners is a proven full-service security consulting firm, dedicated to making Software Secure. Our focus areas include: Mobile Application Security Web Application Security Client/Server Security Continuous Web Application Scanning (Automated/Manual) Published Books Notable Presentations Whitepaper, Tools, Advisories, & SDL Products 11 Published Whitepapers o Including the first whitepaper on CSRF 32 Free Security Tools o Application, Infrastructure, Mobile, VoIP, & Storage 8 Advisories o Including products from Apple, Adobe, and Lenovo Free SDL Products o SecurityQA Toolbar (Automated Web Application Testing) o Code Coach (Secure Code Enforcement and Scanning) o Computer Based Training (Java & WebApp Security)
Apache JMeter HTTP(S) Test Script Recorder
 Apache JMeter HTTP(S) Test Script Recorder This tutorial attempts to explain the exact steps for recording HTTP/HTTPS. For those new to JMeter, one easy way to create a test plan is to use the Recorder.
Apache JMeter HTTP(S) Test Script Recorder This tutorial attempts to explain the exact steps for recording HTTP/HTTPS. For those new to JMeter, one easy way to create a test plan is to use the Recorder.
Secure Web Development Teaching Modules 1. Security Testing. 1.1 Security Practices for Software Verification
 Secure Web Development Teaching Modules 1 Security Testing Contents 1 Concepts... 1 1.1 Security Practices for Software Verification... 1 1.2 Software Security Testing... 2 2 Labs Objectives... 2 3 Lab
Secure Web Development Teaching Modules 1 Security Testing Contents 1 Concepts... 1 1.1 Security Practices for Software Verification... 1 1.2 Software Security Testing... 2 2 Labs Objectives... 2 3 Lab
USING STUFFIT DELUXE THE STUFFIT START PAGE CREATING ARCHIVES (COMPRESSED FILES)
 USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
USING STUFFIT DELUXE StuffIt Deluxe provides many ways for you to create zipped file or archives. The benefit of using the New Archive Wizard is that it provides a way to access some of the more powerful
Generating lesson plans with. Adobe Acrobat
 Generating lesson plans with Adobe Acrobat Introduction Being a teacher requires so many non-teaching administrative tasks that sometimes just teaching gets lost in the paper shuffle. You can automate
Generating lesson plans with Adobe Acrobat Introduction Being a teacher requires so many non-teaching administrative tasks that sometimes just teaching gets lost in the paper shuffle. You can automate
+27O.557+! RM Auditor Additions - Web Monitor. Contents
 RM Auditor Additions - Web Monitor Contents RM Auditor Additions - Web Monitor... 1 Introduction... 2 Installing Web Monitor... 2 Overview... 2 Pre-requisites for installation... 2 Server installation...
RM Auditor Additions - Web Monitor Contents RM Auditor Additions - Web Monitor... 1 Introduction... 2 Installing Web Monitor... 2 Overview... 2 Pre-requisites for installation... 2 Server installation...
Internet Explorer Browser Clean-up
 Follow the steps below to determine your Internet Explorer version number and access browser clean-up procedures specific to your version. 1. From Internet Explorer, click the Help menu and choose About
Follow the steps below to determine your Internet Explorer version number and access browser clean-up procedures specific to your version. 1. From Internet Explorer, click the Help menu and choose About
Web Application Vulnerability Testing with Nessus
 The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP rikjones@computer.org Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP rikjones@computer.org Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
How to test and debug an ASP.NET application
 Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
Chapter 4 How to test and debug an ASP.NET application 113 4 How to test and debug an ASP.NET application If you ve done much programming, you know that testing and debugging are often the most difficult
Building and Using Web Services With JDeveloper 11g
 Building and Using Web Services With JDeveloper 11g Purpose In this tutorial, you create a series of simple web service scenarios in JDeveloper. This is intended as a light introduction to some of the
Building and Using Web Services With JDeveloper 11g Purpose In this tutorial, you create a series of simple web service scenarios in JDeveloper. This is intended as a light introduction to some of the
Hypercosm. Studio. www.hypercosm.com
 Hypercosm Studio www.hypercosm.com Hypercosm Studio Guide 3 Revision: November 2005 Copyright 2005 Hypercosm LLC All rights reserved. Hypercosm, OMAR, Hypercosm 3D Player, and Hypercosm Studio are trademarks
Hypercosm Studio www.hypercosm.com Hypercosm Studio Guide 3 Revision: November 2005 Copyright 2005 Hypercosm LLC All rights reserved. Hypercosm, OMAR, Hypercosm 3D Player, and Hypercosm Studio are trademarks
SonicWALL GMS Custom Reports
 SonicWALL GMS Custom Reports Document Scope This document describes how to configure and use the SonicWALL GMS 6.0 Custom Reports feature. This document contains the following sections: Feature Overview
SonicWALL GMS Custom Reports Document Scope This document describes how to configure and use the SonicWALL GMS 6.0 Custom Reports feature. This document contains the following sections: Feature Overview
Adding Links to Resources
 Adding Links to Resources Use the following instructions to add resource links to your Moodle course. If you have any questions, please contact the helpdesk at. Adding URL links 1. Log into your Moodle
Adding Links to Resources Use the following instructions to add resource links to your Moodle course. If you have any questions, please contact the helpdesk at. Adding URL links 1. Log into your Moodle
QR Code Functionality for Wildland Fire Mapping Jarl Moreland USFS GIS Specialist Albuquerque, NM R3RO
 QR Code Functionality for Wildland Fire Mapping Jarl Moreland USFS GIS Specialist Albuquerque, NM R3RO Mobile GIS applications for iphones, ipads, and other smart devices are a new and progressive way
QR Code Functionality for Wildland Fire Mapping Jarl Moreland USFS GIS Specialist Albuquerque, NM R3RO Mobile GIS applications for iphones, ipads, and other smart devices are a new and progressive way
Adobe Acrobat: Creating Interactive Forms
 Adobe Acrobat: Creating Interactive Forms This document provides information regarding creating interactive forms in Adobe Acrobat. Please note that creating forms requires the professional version (not
Adobe Acrobat: Creating Interactive Forms This document provides information regarding creating interactive forms in Adobe Acrobat. Please note that creating forms requires the professional version (not
ITP 101 Project 3 - Dreamweaver
 ITP 101 Project 3 - Dreamweaver Project Objectives You will also learn how to make a website outlining your company s products, location, and contact info. Project Details USC provides its students with
ITP 101 Project 3 - Dreamweaver Project Objectives You will also learn how to make a website outlining your company s products, location, and contact info. Project Details USC provides its students with
DiskPulse DISK CHANGE MONITOR
 DiskPulse DISK CHANGE MONITOR User Manual Version 7.9 Oct 2015 www.diskpulse.com info@flexense.com 1 1 DiskPulse Overview...3 2 DiskPulse Product Versions...5 3 Using Desktop Product Version...6 3.1 Product
DiskPulse DISK CHANGE MONITOR User Manual Version 7.9 Oct 2015 www.diskpulse.com info@flexense.com 1 1 DiskPulse Overview...3 2 DiskPulse Product Versions...5 3 Using Desktop Product Version...6 3.1 Product
TIBCO ActiveMatrix BPM Integration with Content Management Systems Software Release 2.2.0 September 2013
 TIBCO ActiveMatrix BPM Integration with Content Management Systems Software Release 2.2.0 September 2013 Two-Second Advantage Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE.
TIBCO ActiveMatrix BPM Integration with Content Management Systems Software Release 2.2.0 September 2013 Two-Second Advantage Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE.
IBM Security QRadar Vulnerability Manager Version 7.2.1. User Guide
 IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
enicq 5 System Administrator s Guide
 Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Application. 1.1 About This Tutorial. 1.1.1 Tutorial Requirements. 1.1.2 Provided Files
 About This Tutorial 1Creating an End-to-End HL7 Over MLLP Application 1.1 About This Tutorial 1.1.1 Tutorial Requirements 1.1.2 Provided Files This tutorial takes you through the steps of creating an end-to-end
About This Tutorial 1Creating an End-to-End HL7 Over MLLP Application 1.1 About This Tutorial 1.1.1 Tutorial Requirements 1.1.2 Provided Files This tutorial takes you through the steps of creating an end-to-end
TIBCO ActiveMatrix BPM - Integration with Content Management Systems
 TIBCO ActiveMatrix BPM - Integration with Content Management Systems Software Release 3.0 May 2014 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE.
TIBCO ActiveMatrix BPM - Integration with Content Management Systems Software Release 3.0 May 2014 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE.
Adobe Acrobat X Pro Forms
 Adobe Acrobat X Pro Forms Course objectives: Create interactive forms Manage form fields and properties Use forms in Adobe Reader Use PDF Actions Digital Signatures This course does not cover LiveCycle.
Adobe Acrobat X Pro Forms Course objectives: Create interactive forms Manage form fields and properties Use forms in Adobe Reader Use PDF Actions Digital Signatures This course does not cover LiveCycle.
ImageNow Interact for Microsoft SharePoint Installation, Setup, and User Guide
 ImageNow Interact for Microsoft SharePoint Installation, Setup, and User Guide Version: 6.6.x Written by: Product Documentation, R&D Date: March 2012 ImageNow and CaptureNow are registered trademarks of
ImageNow Interact for Microsoft SharePoint Installation, Setup, and User Guide Version: 6.6.x Written by: Product Documentation, R&D Date: March 2012 ImageNow and CaptureNow are registered trademarks of
SAM XFile. Trial Installation Guide Linux. Snell OD is in the process of being rebranded SAM XFile
 SAM XFile Trial Installation Guide Linux Snell OD is in the process of being rebranded SAM XFile Version History Table 1: Version Table Date Version Released by Reason for Change 10/07/2014 1.0 Andy Gingell
SAM XFile Trial Installation Guide Linux Snell OD is in the process of being rebranded SAM XFile Version History Table 1: Version Table Date Version Released by Reason for Change 10/07/2014 1.0 Andy Gingell
Secure Web Development Teaching Modules 1. Threat Assessment
 Secure Web Development Teaching Modules 1 Threat Assessment Contents 1 Concepts... 1 1.1 Software Assurance Maturity Model... 1 1.2 Security practices for construction... 3 1.3 Web application security
Secure Web Development Teaching Modules 1 Threat Assessment Contents 1 Concepts... 1 1.1 Software Assurance Maturity Model... 1 1.2 Security practices for construction... 3 1.3 Web application security
NASA Workflow Tool. User Guide. September 29, 2010
 NASA Workflow Tool User Guide September 29, 2010 NASA Workflow Tool User Guide 1. Overview 2. Getting Started Preparing the Environment 3. Using the NED Client Common Terminology Workflow Configuration
NASA Workflow Tool User Guide September 29, 2010 NASA Workflow Tool User Guide 1. Overview 2. Getting Started Preparing the Environment 3. Using the NED Client Common Terminology Workflow Configuration
SecuraLive ULTIMATE SECURITY
 SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
Introduction to dobe Acrobat XI Pro
 Introduction to dobe Acrobat XI Pro Introduction to Adobe Acrobat XI Pro is licensed under the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License. To view a copy of this
Introduction to dobe Acrobat XI Pro Introduction to Adobe Acrobat XI Pro is licensed under the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License. To view a copy of this
Integrating with BarTender Integration Builder
 Integrating with BarTender Integration Builder WHITE PAPER Contents Overview 3 Understanding BarTender's Native Integration Platform 4 Integration Builder 4 Administration Console 5 BarTender Integration
Integrating with BarTender Integration Builder WHITE PAPER Contents Overview 3 Understanding BarTender's Native Integration Platform 4 Integration Builder 4 Administration Console 5 BarTender Integration
DEPLOYMENT GUIDE Version 1.1. Deploying F5 with Oracle Application Server 10g
 DEPLOYMENT GUIDE Version 1.1 Deploying F5 with Oracle Application Server 10g Table of Contents Table of Contents Introducing the F5 and Oracle 10g configuration Prerequisites and configuration notes...1-1
DEPLOYMENT GUIDE Version 1.1 Deploying F5 with Oracle Application Server 10g Table of Contents Table of Contents Introducing the F5 and Oracle 10g configuration Prerequisites and configuration notes...1-1
Microsoft Windows Installation and Troubleshooting Guide
 Remote Access Services Microsoft Windows - Installation and Troubleshooting Guide Version 2.1 February 19, 2013 1 P age TABLE OF CONTENTS 1 MICROSOFT WINDOWS XP INSTALLATION PROCEDURES... 3 2 MICROSOFT
Remote Access Services Microsoft Windows - Installation and Troubleshooting Guide Version 2.1 February 19, 2013 1 P age TABLE OF CONTENTS 1 MICROSOFT WINDOWS XP INSTALLATION PROCEDURES... 3 2 MICROSOFT
ADOBE ACROBAT 7.0 CREATING FORMS
 ADOBE ACROBAT 7.0 CREATING FORMS ADOBE ACROBAT 7.0: CREATING FORMS ADOBE ACROBAT 7.0: CREATING FORMS...2 Getting Started...2 Creating the Adobe Form...3 To insert a Text Field...3 To insert a Check Box/Radio
ADOBE ACROBAT 7.0 CREATING FORMS ADOBE ACROBAT 7.0: CREATING FORMS ADOBE ACROBAT 7.0: CREATING FORMS...2 Getting Started...2 Creating the Adobe Form...3 To insert a Text Field...3 To insert a Check Box/Radio
Streaming Media System Requirements and Troubleshooting Assistance
 Test Your System Streaming Media System Requirements and Troubleshooting Assistance Test your system to determine if you can receive streaming media. This may help identify why you are having problems,
Test Your System Streaming Media System Requirements and Troubleshooting Assistance Test your system to determine if you can receive streaming media. This may help identify why you are having problems,
WordCom, Inc. Secure File Transfer Web Application
 WordCom, Inc. Secure File Transfer Web Application Table of Contents 1. Introduction 2. Logging into WordCom s File Transfer Web Client 3. Toolbar buttons 4. Sending a package in Enhanced Mode (If installed
WordCom, Inc. Secure File Transfer Web Application Table of Contents 1. Introduction 2. Logging into WordCom s File Transfer Web Client 3. Toolbar buttons 4. Sending a package in Enhanced Mode (If installed
WebLOAD IDE User's Guide Version 8.0
 WebLOAD IDE User's Guide Version 8.0 RadView Software The software supplied with this document is the property of RadView Software and is furnished under a licensing agreement. Neither the software nor
WebLOAD IDE User's Guide Version 8.0 RadView Software The software supplied with this document is the property of RadView Software and is furnished under a licensing agreement. Neither the software nor
Load testing with. WAPT Cloud. Quick Start Guide
 Load testing with WAPT Cloud Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. 2007-2015 SoftLogica
Load testing with WAPT Cloud Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. 2007-2015 SoftLogica
VMware Software Manager - Download Service User's Guide
 VMware Software Manager - Download Service User's Guide VMware Software Manager 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is
VMware Software Manager - Download Service User's Guide VMware Software Manager 1.1 This document supports the version of each product listed and supports all subsequent versions until the document is
1. Tutorial Overview
 RDz Web Services Tutorial 02 Web Services Abteilung Technische Informatik, Institut für Informatik, Universität Leipzig Abteilung Technische Informatik, Wilhelm Schickard Institut für Informatik, Universität
RDz Web Services Tutorial 02 Web Services Abteilung Technische Informatik, Institut für Informatik, Universität Leipzig Abteilung Technische Informatik, Wilhelm Schickard Institut für Informatik, Universität
Deploying the BIG-IP System v10 with Oracle Application Server 10g R2
 DEPLOYMENT GUIDE Deploying the BIG-IP System v10 with Oracle Application Server 10g R2 Version 1.1 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Oracle s Application Server 10g
DEPLOYMENT GUIDE Deploying the BIG-IP System v10 with Oracle Application Server 10g R2 Version 1.1 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Oracle s Application Server 10g
DataPA OpenAnalytics End User Training
 DataPA OpenAnalytics End User Training DataPA End User Training Lesson 1 Course Overview DataPA Chapter 1 Course Overview Introduction This course covers the skills required to use DataPA OpenAnalytics
DataPA OpenAnalytics End User Training DataPA End User Training Lesson 1 Course Overview DataPA Chapter 1 Course Overview Introduction This course covers the skills required to use DataPA OpenAnalytics
vtcommander Installing and Starting vtcommander
 vtcommander vtcommander provides a local graphical user interface (GUI) to manage Hyper-V R2 server. It supports Hyper-V technology on full and core installations of Windows Server 2008 R2 as well as on
vtcommander vtcommander provides a local graphical user interface (GUI) to manage Hyper-V R2 server. It supports Hyper-V technology on full and core installations of Windows Server 2008 R2 as well as on
Shellshock Security Patch for X86
 Shellshock Security Patch for X86 Guide for Using the FFPS Update Manager October 2014 Version 1.0. Page 1 Page 2 This page is intentionally blank Table of Contents 1.0 OVERVIEW - SHELLSHOCK/BASH SHELL
Shellshock Security Patch for X86 Guide for Using the FFPS Update Manager October 2014 Version 1.0. Page 1 Page 2 This page is intentionally blank Table of Contents 1.0 OVERVIEW - SHELLSHOCK/BASH SHELL
Weston Public Schools Virtual Desktop Access Instructions
 Instructions for connecting to the Weston Schools Virtual Desktop Environment Notes: You will have to have administrator permission on your computer in order to install a VMWare Client application which
Instructions for connecting to the Weston Schools Virtual Desktop Environment Notes: You will have to have administrator permission on your computer in order to install a VMWare Client application which
5nine Hyper-V Commander
 5nine Hyper-V Commander 5nine Hyper-V Commander provides a local graphical user interface (GUI), and a Framework to manage Hyper-V R2 server and various functions such as Backup/DR, HA and P2V/V2V. It
5nine Hyper-V Commander 5nine Hyper-V Commander provides a local graphical user interface (GUI), and a Framework to manage Hyper-V R2 server and various functions such as Backup/DR, HA and P2V/V2V. It
MyOra 3.0. User Guide. SQL Tool for Oracle. Jayam Systems, LLC
 MyOra 3.0 SQL Tool for Oracle User Guide Jayam Systems, LLC Contents Features... 4 Connecting to the Database... 5 Login... 5 Login History... 6 Connection Indicator... 6 Closing the Connection... 7 SQL
MyOra 3.0 SQL Tool for Oracle User Guide Jayam Systems, LLC Contents Features... 4 Connecting to the Database... 5 Login... 5 Login History... 6 Connection Indicator... 6 Closing the Connection... 7 SQL
Creating Forms With Adobe LiveCycle Designer 8.2
 Creating Forms With Adobe LiveCycle Designer 8.2 Instructional Media Center HCC Version 2 Modified Date 1/20/10 Learning Objectives: At the end of this training session the student will be able to use
Creating Forms With Adobe LiveCycle Designer 8.2 Instructional Media Center HCC Version 2 Modified Date 1/20/10 Learning Objectives: At the end of this training session the student will be able to use
DEPLOYMENT GUIDE Version 1.2. Deploying F5 with Oracle E-Business Suite 12
 DEPLOYMENT GUIDE Version 1.2 Deploying F5 with Oracle E-Business Suite 12 Table of Contents Table of Contents Introducing the BIG-IP LTM Oracle E-Business Suite 12 configuration Prerequisites and configuration
DEPLOYMENT GUIDE Version 1.2 Deploying F5 with Oracle E-Business Suite 12 Table of Contents Table of Contents Introducing the BIG-IP LTM Oracle E-Business Suite 12 configuration Prerequisites and configuration
PHP Debugging. Draft: March 19, 2013 2013 Christopher Vickery
 PHP Debugging Draft: March 19, 2013 2013 Christopher Vickery Introduction Debugging is the art of locating errors in your code. There are three types of errors to deal with: 1. Syntax errors: When code
PHP Debugging Draft: March 19, 2013 2013 Christopher Vickery Introduction Debugging is the art of locating errors in your code. There are three types of errors to deal with: 1. Syntax errors: When code
Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services
 Deployment Guide Deploying the BIG-IP System with Microsoft Windows Server 2003 Terminal Services Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services Welcome to the BIG-IP
Deployment Guide Deploying the BIG-IP System with Microsoft Windows Server 2003 Terminal Services Deploying the BIG-IP LTM system and Microsoft Windows Server 2003 Terminal Services Welcome to the BIG-IP
ViRobot Desktop 5.5. User s Guide
 ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
(These instructions are only meant to get you started. They do not include advanced features.)
 FrontPage XP/2003 HOW DO I GET STARTED CREATING A WEB PAGE? Previously, the process of creating a page on the World Wide Web was complicated. Hypertext Markup Language (HTML) is a relatively simple computer
FrontPage XP/2003 HOW DO I GET STARTED CREATING A WEB PAGE? Previously, the process of creating a page on the World Wide Web was complicated. Hypertext Markup Language (HTML) is a relatively simple computer
Legal Notes. Regarding Trademarks. 2012 KYOCERA Document Solutions Inc.
 Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
How To Test Your Web Site On Wapt On A Pc Or Mac Or Mac (Or Mac) On A Mac Or Ipad Or Ipa (Or Ipa) On Pc Or Ipam (Or Pc Or Pc) On An Ip
 Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
Load testing with WAPT: Quick Start Guide This document describes step by step how to create a simple typical test for a web application, execute it and interpret the results. A brief insight is provided
NDSU Technology Learning & Media Center. Introduction to Google Sites
 NDSU Technology Learning & Media Center QBB 150C 231-5130 www.ndsu.edu/its/tlmc Introduction to Google Sites Get Help at the TLMC 1. Get help with class projects on a walk-in basis; student learning assistants
NDSU Technology Learning & Media Center QBB 150C 231-5130 www.ndsu.edu/its/tlmc Introduction to Google Sites Get Help at the TLMC 1. Get help with class projects on a walk-in basis; student learning assistants
Securing Adobe connect Server and CQ Server
 Securing Adobe connect Server and CQ Server To Enable SSL on Connect Server and CQ server (Index) Configure custom.ini File Uncomment the SSL TAGs in Server.xml file. Configure the Four components of connect
Securing Adobe connect Server and CQ Server To Enable SSL on Connect Server and CQ server (Index) Configure custom.ini File Uncomment the SSL TAGs in Server.xml file. Configure the Four components of connect
Connecting to LUA s webmail
 Connecting to LUA s webmail Effective immediately, the Company has enhanced employee remote access to email (Outlook). By utilizing almost any browser you will have access to your Company e-mail as well
Connecting to LUA s webmail Effective immediately, the Company has enhanced employee remote access to email (Outlook). By utilizing almost any browser you will have access to your Company e-mail as well
Configure Your Computer to Work With Microsoft Word - Windows Vista
 COMPUTER CONFIGURATION INSTRUCTIONS CENTER FOR THE DEVELOPMENT OF SECURITY EXCELLENCE May 2013 The purpose of this document is to provide step-by-step instructions to students on how to configure their
COMPUTER CONFIGURATION INSTRUCTIONS CENTER FOR THE DEVELOPMENT OF SECURITY EXCELLENCE May 2013 The purpose of this document is to provide step-by-step instructions to students on how to configure their
Distributing forms and compiling forms data
 Distributing forms and compiling forms data Recent versions of Acrobat have allowed forms to be created which the end user can fill in with the free Adobe Reader and save what has been entered. The form
Distributing forms and compiling forms data Recent versions of Acrobat have allowed forms to be created which the end user can fill in with the free Adobe Reader and save what has been entered. The form
Installation and Operation Manual Portable Device Manager, Windows version
 Installation and Operation Manual version version About this document This document is intended as a guide for installation, maintenance and troubleshooting of Portable Device Manager (PDM) and is relevant
Installation and Operation Manual version version About this document This document is intended as a guide for installation, maintenance and troubleshooting of Portable Device Manager (PDM) and is relevant
Appendix A How to create a data-sharing lab
 Appendix A How to create a data-sharing lab Creating a lab involves completing five major steps: creating lists, then graphs, then the page for lab instructions, then adding forms to the lab instructions,
Appendix A How to create a data-sharing lab Creating a lab involves completing five major steps: creating lists, then graphs, then the page for lab instructions, then adding forms to the lab instructions,
WS_FTP Professional 12
 WS_FTP Professional 12 Tools Guide Contents CHAPTER 1 Introduction Ways to Automate Regular File Transfers...5 Check Transfer Status and Logs...6 Building a List of Files for Transfer...6 Transfer Files
WS_FTP Professional 12 Tools Guide Contents CHAPTER 1 Introduction Ways to Automate Regular File Transfers...5 Check Transfer Status and Logs...6 Building a List of Files for Transfer...6 Transfer Files
r-one Python Setup 1 Setup 2 Using IDLE 3 Using IDLE with your Robot ENGI 128: Introduction to Engineering Systems Fall, 2014
 r-one Python Setup 1 Setup The files needed are available in the Resources page of http://www.clear.rice.edu/engi128. You will need to setup two files: Python 2.7.8 and PySerial 1. Download Python 2.7.8.
r-one Python Setup 1 Setup The files needed are available in the Resources page of http://www.clear.rice.edu/engi128. You will need to setup two files: Python 2.7.8 and PySerial 1. Download Python 2.7.8.
Adobe Acrobat 9 Pro Accessibility Guide: Creating Accessible Forms
 Adobe Acrobat 9 Pro Accessibility Guide: Creating Accessible Forms Adobe, the Adobe logo, Acrobat, Acrobat Connect, the Adobe PDF logo, Creative Suite, LiveCycle, and Reader are either registered trademarks
Adobe Acrobat 9 Pro Accessibility Guide: Creating Accessible Forms Adobe, the Adobe logo, Acrobat, Acrobat Connect, the Adobe PDF logo, Creative Suite, LiveCycle, and Reader are either registered trademarks
Using J-ISIS in a Local Network
 23 December 2012 Author: Jean-Claude Dauphin jc.dauphin@gmail.com Status:draft Using J-ISIS in a Local Network 1. Introduction J-ISIS uses TCP/IP protocol to communicate between computers. TCP/IP like
23 December 2012 Author: Jean-Claude Dauphin jc.dauphin@gmail.com Status:draft Using J-ISIS in a Local Network 1. Introduction J-ISIS uses TCP/IP protocol to communicate between computers. TCP/IP like
Delegated Administration Quick Start
 Delegated Administration Quick Start Topic 50200 Delegated Administration Quick Start Updated 22-Oct-2013 Applies to: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere,
Delegated Administration Quick Start Topic 50200 Delegated Administration Quick Start Updated 22-Oct-2013 Applies to: Web Filter, Web Security, Web Security Gateway, and Web Security Gateway Anywhere,
MyReports Recommended Browser Settings MYR-200a
 MyReports Recommended Browser Settings MYR-200a Note: If you have installed an additional Tool Bar on your browser, such as Yahoo Tool Bar or Google Tool Bar, be sure that it is also configured to allow
MyReports Recommended Browser Settings MYR-200a Note: If you have installed an additional Tool Bar on your browser, such as Yahoo Tool Bar or Google Tool Bar, be sure that it is also configured to allow
Toad for Oracle 8.6 SQL Tuning
 Quick User Guide for Toad for Oracle 8.6 SQL Tuning SQL Tuning Version 6.1.1 SQL Tuning definitively solves SQL bottlenecks through a unique methodology that scans code, without executing programs, to
Quick User Guide for Toad for Oracle 8.6 SQL Tuning SQL Tuning Version 6.1.1 SQL Tuning definitively solves SQL bottlenecks through a unique methodology that scans code, without executing programs, to
Using SSH Secure Shell Client for FTP
 Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
DEPLOYMENT GUIDE Version 1.0. Deploying F5 with the Oracle Fusion Middleware SOA Suite 11gR1
 DEPLOYMENT GUIDE Version 1.0 Deploying F5 with the Oracle Fusion Middleware SOA Suite 11gR1 Introducing the F5 and Oracle Fusion Middleware SOA Suite configuration Welcome to the F5 and Oracle Fusion Middleware
DEPLOYMENT GUIDE Version 1.0 Deploying F5 with the Oracle Fusion Middleware SOA Suite 11gR1 Introducing the F5 and Oracle Fusion Middleware SOA Suite configuration Welcome to the F5 and Oracle Fusion Middleware
TIBCO Spotfire Automation Services 6.5. Installation and Deployment Manual
 TIBCO Spotfire Automation Services 6.5 Installation and Deployment Manual Revision date: 17 April 2014 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED
TIBCO Spotfire Automation Services 6.5 Installation and Deployment Manual Revision date: 17 April 2014 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES OTHER TIBCO SOFTWARE. USE OF SUCH EMBEDDED
Apple Applications > Safari 2008-10-15
 Safari User Guide for Web Developers Apple Applications > Safari 2008-10-15 Apple Inc. 2008 Apple Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system,
Safari User Guide for Web Developers Apple Applications > Safari 2008-10-15 Apple Inc. 2008 Apple Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system,
Configuring Security for FTP Traffic
 2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
2 Configuring Security for FTP Traffic Securing FTP traffic Creating a security profile for FTP traffic Configuring a local traffic FTP profile Assigning an FTP security profile to a local traffic FTP
Acrobat XI Pro Accessible Forms and Interactive Documents
 Contents 2 Types of interactive PDF Form Fields 2 Automatic Field Detection using the Acrobat Form Wizard 5 Creating a Form without the Forms Wizard 6 Forms Editing Mode 6 Selecting a New Form Field to
Contents 2 Types of interactive PDF Form Fields 2 Automatic Field Detection using the Acrobat Form Wizard 5 Creating a Form without the Forms Wizard 6 Forms Editing Mode 6 Selecting a New Form Field to
P&WC Portal Settings. 1) Portal Language Setting:
 P&WC Portal Settings In order to set your Internet Explorer Browser and to resolve a few specific issues that users of the P&WC Portal might have, we recommend that you change a few settings in your browser.
P&WC Portal Settings In order to set your Internet Explorer Browser and to resolve a few specific issues that users of the P&WC Portal might have, we recommend that you change a few settings in your browser.
UH CMS Basics. Cascade CMS Basics Class. UH CMS Basics Updated: June,2011! Page 1
 UH CMS Basics Cascade CMS Basics Class UH CMS Basics Updated: June,2011! Page 1 Introduction I. What is a CMS?! A CMS or Content Management System is a web based piece of software used to create web content,
UH CMS Basics Cascade CMS Basics Class UH CMS Basics Updated: June,2011! Page 1 Introduction I. What is a CMS?! A CMS or Content Management System is a web based piece of software used to create web content,
Tutorial: Load Testing with CLIF
 Tutorial: Load Testing with CLIF Bruno Dillenseger, Orange Labs Learning the basic concepts and manipulation of the CLIF load testing platform. Focus on the Eclipse-based GUI. Menu Introduction about Load
Tutorial: Load Testing with CLIF Bruno Dillenseger, Orange Labs Learning the basic concepts and manipulation of the CLIF load testing platform. Focus on the Eclipse-based GUI. Menu Introduction about Load
Check list for web developers
 Check list for web developers Requirement Yes No Remarks 1. Input Validation 1.1) Have you done input validation for all the user inputs using white listing and/or sanitization? 1.2) Does the input validation
Check list for web developers Requirement Yes No Remarks 1. Input Validation 1.1) Have you done input validation for all the user inputs using white listing and/or sanitization? 1.2) Does the input validation
InfoView User s Guide. BusinessObjects Enterprise XI Release 2
 BusinessObjects Enterprise XI Release 2 InfoView User s Guide BusinessObjects Enterprise XI Release 2 Patents Trademarks Copyright Third-party contributors Business Objects owns the following U.S. patents,
BusinessObjects Enterprise XI Release 2 InfoView User s Guide BusinessObjects Enterprise XI Release 2 Patents Trademarks Copyright Third-party contributors Business Objects owns the following U.S. patents,
Outlook 2003 User Guide. April 15, 2004
 Outlook 2003 User Guide April 15, 2004 PURPOSE OF THE DOCUMENT... 2 NAVIGATE OUTLOOK...3 Toolbars... 3 Menu Toolbar... 4 Standard Toolbar... 5 Outlook Bar... 6 Navigation Pane... 7 USING THE MAIL OPTION...
Outlook 2003 User Guide April 15, 2004 PURPOSE OF THE DOCUMENT... 2 NAVIGATE OUTLOOK...3 Toolbars... 3 Menu Toolbar... 4 Standard Toolbar... 5 Outlook Bar... 6 Navigation Pane... 7 USING THE MAIL OPTION...
Immersion Day. Creating an Elastic Load Balancer. Rev 2015-01
 Rev 2015-01 Table of Contents Overview...3 Launch a Second Web Server...4 Create an ELB...6 Copyright 2015, Amazon Web Services, All Rights Reserved Page 2 Overview This lab will walk the user through
Rev 2015-01 Table of Contents Overview...3 Launch a Second Web Server...4 Create an ELB...6 Copyright 2015, Amazon Web Services, All Rights Reserved Page 2 Overview This lab will walk the user through
Outlook Web Access (OWA) User Guide
 Outlook Web Access (OWA) User Guide September 2010 TABLE OF CONTENTS TABLE OF CONTENTS... 2 1.0 INTRODUCTION... 4 1.1 OUTLOOK WEB ACCESS SECURITY CONSIDERATIONS... 4 2.0 GETTING STARTED... 5 2.1 LOGGING
Outlook Web Access (OWA) User Guide September 2010 TABLE OF CONTENTS TABLE OF CONTENTS... 2 1.0 INTRODUCTION... 4 1.1 OUTLOOK WEB ACCESS SECURITY CONSIDERATIONS... 4 2.0 GETTING STARTED... 5 2.1 LOGGING
Firewalls and Software Updates
 Firewalls and Software Updates License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents General
Firewalls and Software Updates License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License. Contents General
ithenticate User Manual
 ithenticate User Manual Version: 2.0.8 Updated February 4, 2014 Contents Introduction 4 New Users 4 Logging In 4 Resetting Your Password 5 Changing Your Password or Username 6 The ithenticate Account Homepage
ithenticate User Manual Version: 2.0.8 Updated February 4, 2014 Contents Introduction 4 New Users 4 Logging In 4 Resetting Your Password 5 Changing Your Password or Username 6 The ithenticate Account Homepage
Deploying the BIG-IP LTM with the Cacti Open Source Network Monitoring System
 DEPLOYMENT GUIDE Deploying the BIG-IP LTM with the Cacti Open Source Network Monitoring System Version 1.0 Deploying F5 with Cacti Open Source Network Monitoring System Welcome to the F5 and Cacti deployment
DEPLOYMENT GUIDE Deploying the BIG-IP LTM with the Cacti Open Source Network Monitoring System Version 1.0 Deploying F5 with Cacti Open Source Network Monitoring System Welcome to the F5 and Cacti deployment
WebSphere Business Monitor V6.2 Business space dashboards
 Copyright IBM Corporation 2009 All rights reserved IBM WEBSPHERE BUSINESS MONITOR 6.2 LAB EXERCISE WebSphere Business Monitor V6.2 What this exercise is about... 2 Lab requirements... 2 What you should
Copyright IBM Corporation 2009 All rights reserved IBM WEBSPHERE BUSINESS MONITOR 6.2 LAB EXERCISE WebSphere Business Monitor V6.2 What this exercise is about... 2 Lab requirements... 2 What you should
Outlook Web Access E-mail
 Outlook Web Access E-mail A. Accessing the mailbox via the Internet 1. Open your browser Firebox or Internet Explorer 2. In the URL address location box, key mail.asbury.edu for students and mail2.asbury.edu
Outlook Web Access E-mail A. Accessing the mailbox via the Internet 1. Open your browser Firebox or Internet Explorer 2. In the URL address location box, key mail.asbury.edu for students and mail2.asbury.edu
Detecting and Exploiting XSS with Xenotix XSS Exploit Framework
 Detecting and Exploiting XSS with Xenotix XSS Exploit Framework ajin25@gmail.com keralacyberforce.in Introduction Cross Site Scripting or XSS vulnerabilities have been reported and exploited since 1990s.
Detecting and Exploiting XSS with Xenotix XSS Exploit Framework ajin25@gmail.com keralacyberforce.in Introduction Cross Site Scripting or XSS vulnerabilities have been reported and exploited since 1990s.
Digital Certificate IP Address Test Procedure
 Digital Certificate IP Address Test Procedure Testing Firewall Access to New CA IP Addresses May 11 th to 15 th Verizon is making some test servers with the new Certificate Authority (CA) system IP addresses
Digital Certificate IP Address Test Procedure Testing Firewall Access to New CA IP Addresses May 11 th to 15 th Verizon is making some test servers with the new Certificate Authority (CA) system IP addresses
OrgPublisher 11 Web Administration Installation for Windows 2008 Server
 OrgPublisher 11 Web Administration Installation for Windows 2008 Server Table of Contents Web Administration Installation Guide for Windows 2008 Server Installing IIS 7 on Server 2008... 4 Installing OrgPublisher
OrgPublisher 11 Web Administration Installation for Windows 2008 Server Table of Contents Web Administration Installation Guide for Windows 2008 Server Installing IIS 7 on Server 2008... 4 Installing OrgPublisher
MadCap Software. Upgrading Guide. Pulse
 MadCap Software Upgrading Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
MadCap Software Upgrading Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
CUNY TUMBLEWEED (SECURE TRANSPORT) USER GUIDE
 CUNY TUMBLEWEED (SECURE TRANSPORT) USER GUIDE INTRODUCTION Tumbleweed (Secure Transport) is used to provide secure file transfer of critical business files, financial transactions and sensitive data such
CUNY TUMBLEWEED (SECURE TRANSPORT) USER GUIDE INTRODUCTION Tumbleweed (Secure Transport) is used to provide secure file transfer of critical business files, financial transactions and sensitive data such
Working With Your FTP Site
 Working With Your FTP Site Welcome to your FTP Site! The UnlimitedFTP (UFTP) software will allow you to run from any web page using Netscape, Internet Explorer, Opera, Mozilla or Safari browsers. It can
Working With Your FTP Site Welcome to your FTP Site! The UnlimitedFTP (UFTP) software will allow you to run from any web page using Netscape, Internet Explorer, Opera, Mozilla or Safari browsers. It can
Chapter 3 ADDRESS BOOK, CONTACTS, AND DISTRIBUTION LISTS
 Chapter 3 ADDRESS BOOK, CONTACTS, AND DISTRIBUTION LISTS 03Archer.indd 71 8/4/05 9:13:59 AM Address Book 3.1 What Is the Address Book The Address Book in Outlook is actually a collection of address books
Chapter 3 ADDRESS BOOK, CONTACTS, AND DISTRIBUTION LISTS 03Archer.indd 71 8/4/05 9:13:59 AM Address Book 3.1 What Is the Address Book The Address Book in Outlook is actually a collection of address books
Deploying the BIG-IP System with Oracle E-Business Suite 11i
 Deploying the BIG-IP System with Oracle E-Business Suite 11i Introducing the BIG-IP and Oracle 11i configuration Configuring the BIG-IP system for deployment with Oracle 11i Configuring the BIG-IP system
Deploying the BIG-IP System with Oracle E-Business Suite 11i Introducing the BIG-IP and Oracle 11i configuration Configuring the BIG-IP system for deployment with Oracle 11i Configuring the BIG-IP system
MyOra 3.5. User Guide. SQL Tool for Oracle. Kris Murthy
 MyOra 3.5 SQL Tool for Oracle User Guide Kris Murthy Contents Features... 4 Connecting to the Database... 5 Login... 5 Login History... 6 Connection Indicator... 6 Closing the Connection... 7 SQL Editor...
MyOra 3.5 SQL Tool for Oracle User Guide Kris Murthy Contents Features... 4 Connecting to the Database... 5 Login... 5 Login History... 6 Connection Indicator... 6 Closing the Connection... 7 SQL Editor...
DEPLOYMENT GUIDE Version 1.1. DNS Traffic Management using the BIG-IP Local Traffic Manager
 DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
DEPLOYMENT GUIDE Version 1.1 DNS Traffic Management using the BIG-IP Local Traffic Manager Table of Contents Table of Contents Introducing DNS server traffic management with the BIG-IP LTM Prerequisites
How to Configure Windows 8.1 to run ereports on IE11
 How to Configure Windows 8.1 to run ereports on IE11 Description: Windows 8.1 ships with IE10, but can be updated to IE11. There is a special mode in IE11 called Enterprise Mode that can be used to emulate
How to Configure Windows 8.1 to run ereports on IE11 Description: Windows 8.1 ships with IE10, but can be updated to IE11. There is a special mode in IE11 called Enterprise Mode that can be used to emulate
QualysGuard WAS. Getting Started Guide Version 3.3. March 21, 2014
 QualysGuard WAS Getting Started Guide Version 3.3 March 21, 2014 Copyright 2011-2014 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
QualysGuard WAS Getting Started Guide Version 3.3 March 21, 2014 Copyright 2011-2014 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
HP WebInspect Tutorial
 HP WebInspect Tutorial Introduction: With the exponential increase in internet usage, companies around the world are now obsessed about having a web application of their own which would provide all the
HP WebInspect Tutorial Introduction: With the exponential increase in internet usage, companies around the world are now obsessed about having a web application of their own which would provide all the
A Tool for Evaluation and Optimization of Web Application Performance
 A Tool for Evaluation and Optimization of Web Application Performance Tomáš Černý 1 cernyto3@fel.cvut.cz Michael J. Donahoo 2 jeff_donahoo@baylor.edu Abstract: One of the main goals of web application
A Tool for Evaluation and Optimization of Web Application Performance Tomáš Černý 1 cernyto3@fel.cvut.cz Michael J. Donahoo 2 jeff_donahoo@baylor.edu Abstract: One of the main goals of web application
