The Sample Policies for Information Security Measure for Universities. Tohoku University Hideaki Sone
|
|
|
- Owen York
- 8 years ago
- Views:
Transcription
1 The Sample Policies for Information Security Measure for Universities Tohoku University Hideaki Sone 1
2 Agenda Activities and Information Security Measure in universities Activities of Universities, Variety of information, Security incidents, Requests Sample policies for information security measures Background, WG Activities, Structure, Contents Structure of the Sample Policies Character, Assumption, System of the sample policies Usage of the sample policies in university Application, Example Measures for information security education in universities Education material, Three Choice Tutorial 2
3 Activities and Information Security Measure in universities 3
4 Activities of Universities Members Executive officers, personnel (office / technical / assistant), professors, temporary worker, contract worker Students (undergraduate, graduate, researcher) member?/ customer? TA/RA student? / personnel? Researchers (normal / visiting / contract / int l / - - -) rights / responsibilities Activities Education (for students) Research (together with students) Administration (Medical) 4
5 Varieties of information handled in universities Relationship with activities Education: Registration/score, course materials/coursework, e-learning Research: paper draft, data, technology/equipment, publication Administration: Personnel, finance,, press release Request for information security Information systems Confidential information(examination, paper/patent draft, management) Social responsibility Request about personal information protection, security export control, Academic freedom Education about information security 5
6 Security incidents in universities Reports from others on the internet Unauthorized access (scan attack, spam ) Virus (online/offline) Copyright infringement Thoughtlessness, less-education Network failure Backbone, external connection (route, abnormal traffic) Incidents on information control Software license control Information leakage 6
7 Requests on efforts of universities Establishment of information security policy Information security incident countermeasures Unauthorized access of/from internet Countermeasure against information leakage Prevention measure, user education, self-check Reference to the uniform criterion for government agency Although the criterion does not cover universities, it is a useful reference for information systems to promote increase of its information security level Establishment of system for information security essential requirement for national universities 7
8 Sample policies for information security measures 8
9 Background of establishment of information security policy of universities BG Urgent need for increase of information security level Policy, rules and regulations, educational materials Wide range of expert knowledge on relationship to education and research activities, management, etc. The uniform criterion for government agency, Private Information Protection Law, corporated national universities, increasing security level Request Sample policies to be used as templates Expert group from universities and engineers institute 9
10 Activities to establish sample policies for universities University computer centers and NII Research meeting for security policy of university Vision on information security policy of university (March, 2002) IEICE Network management guideline study working group Network management guideline for higher education institute (April, 2003) Increasing request for specific and effective sample policies Establishment of sample policies by NII and IEICE(since 2006) Response to new requests The uniform criterion for government agency (December, 2005) Standard and effective policies Working Group for Information Security Policy for National Universities and Institutions Sub groups: General field and structure, Network operation, Authentication operation, Clerical use, Users, Education and ethics Supports: National corporative computer centers, Informatization promotion association of national universities MEXT, NISC (National Information Security Center) Joint activity with IEICE Network management guideline study WG Establishment of sample policies and interpretation, and publishment
11 Sample policies referring the government criterion Target Uniform criterion for government agency (NISC) Ministries Government officers Network management guideline for higher education institute (IEICE) Universities, colleges Professors, students, Information systems Management by system section Internal use Web site (Official site only) Independent operation by departments and labs System for research/experiment Web site (many local sites, Web BBS, Blogs) Easy to control Balance between security control and academic freedom Education
12 General field Activity to establish the sample policies Agenda and structure Establishment of rules and manuals, referring comments and questions Public comments request (August 2007) Publication of The Sample Policies for Information Security Measure for Institutions of Higher Education (October 2007) Lectures at seminars and workshops to spread the results Operation and management Users(Usage,self-inspection Education(Users, Managers, Executive) Clerical use Authentication(Operation) 12
13 System of the sample policies Pocicies Fundamental Policy(1) Fundamental Rule(1) Rules(10) Gudeliens(33) 13
14 Structure of the sample policies Policy Rules and regulations Manuals and guidelines A1000 情 報 システム 運 用 基 本 方 針 A1001 情 報 システム 運 用 基 本 規 程 A2101 情 報 システム 運 用 管 理 規 程 A2102 情 報 システム 運 用 リスク 管 理 規 程 A2103 情 報 システム 非 常 時 行 動 計 画 に 関 する 規 程 A2104 情 報 格 付 け 規 程 A3100 情 報 システム 運 用 管 理 手 順 の 策 定 に 関 する 解 説 書 A3101 情 報 システムにおける 情 報 セキュリティ 対 策 実 施 規 程 A3102 例 外 措 置 手 順 書 ; A3103 インシデント 対 応 手 順 A3104 情 報 格 付 け 取 扱 手 順 ; A3105 情 報 システム 運 用 リスク 評 価 手 順 A3106 セキュリティホール 対 策 計 画 に 関 する 様 式 A3107 ウェブサーバ 設 定 確 認 実 施 手 順 A3108 メールサーバのセキュリティ 維 持 手 順 A3109 人 事 異 動 の 際 に 行 うべき 情 報 セキュリティ 対 策 実 施 規 程 A3110 機 器 等 の 購 入 における 情 報 セキュリティ 対 策 実 施 規 程 A3111 外 部 委 託 における 情 報 セキュリティ 対 策 実 施 手 順 A3112 ソフトウェア 開 発 における 情 報 セキュリティ 対 策 実 施 手 順 A3113 外 部 委 託 における 情 報 セキュリティ 対 策 に 関 する 評 価 手 順 A3114 情 報 システムの 構 築 等 におけるセキュリティ 要 件 及 びセキュリティ 機 能 の 検 討 に 関 する 解 説 書 (*) A3115 情 報 システムの 構 築 等 におけるST 評 価 ST 確 認 の 実 施 に 関 する 解 説 書 (*) A2201 情 報 システム 利 用 規 程 A3200 情 報 システム 利 用 者 向 け 文 書 の 策 定 に 関 する 解 説 書 A3201 PC 取 扱 いガイドライン A3202 電 子 メール 利 用 ガイドライン; A3203 ウェブブラウザ 利 用 ガイドライン A3204 ウェブ 公 開 ガイドライン; A3205 利 用 者 パスワードガイドライン A3211 学 外 情 報 セキュリティ 水 準 低 下 防 止 手 順 A3212 自 己 点 検 の 考 え 方 と 実 務 への 準 備 に 関 する 解 説 書 A2301 年 度 講 習 計 画 A3300 教 育 テキストの 策 定 に 関 する 解 説 書 A3301 教 育 テキスト 作 成 ガイドライン( 利 用 者 向 け) A3302 ( 部 局 管 理 者 向 け); A3303 (CIO/ 役 職 者 向 け) A2401 情 報 セキュリティ 監 査 規 程 A3401 情 報 セキュリティ 監 査 実 施 手 順 A2501 事 務 情 報 セキュリティ 対 策 基 準 A3500 各 種 マニュアル 類 の 策 定 に 関 する 解 説 書 ; A3501 各 種 マニュアル 類 (**) A3502 責 任 者 等 の 役 割 から 見 た 遵 守 事 項 A2601 証 明 書 ポリシー(*) A2602 認 証 実 施 規 程 (*) A3600 認 証 手 順 の 策 定 に 関 する 解 説 書 A3601 情 報 システムアカウント 取 得 手 順 は 策 定 手 引 書 (*) 外 部 文 書 の 参 照 のみ, (**) 各 大 学 にて 策 定 することを 想 定 14
15 Content of the sample policies (Total 45,586p) Policy A10xx (12p) General x0xx 2,12p Rules/Regulations A2xxx (200p) Manuals/Guidelines A3xxx (374p) Management x1xx 4, 47p 16,186p Usage x2xx 9,76p 1, 8p 8, 95p Education x3xx 1, 5p 4, 38p Audit x4xx 1, 4p 1, 24p Clerical use x5xx 1,134p 2, 24p Authentication x6xx 2, 2p 2, 7p 15
16 Publication of the sample policies Publication on the Internet 31 October, 2007 Also link from "The Sample Policies for Information Security Measure for Institutions of Higher Education PDF file, text file FAQ and news Result of request for public comments (August, 2007) Other materials Old versions Vision on information security policy of university (March, 2002) 16
17 Working Group for Promoting Information Security Policy in Institutions of Higher Education Promotion of information security policy to universities Development of promotional materials for use of the sample policies Development of educational materials Information on usage of the sample policies Support for study at each university Lectures Response to questions/requests on the sample policies Preparation for further revision Survey on changing circumstances and new requests Revision of the governmental criterion, progress of technology/services Since December,
18 Structure of the Sample Policies 18
19 Character of the sample policies Established as sample policies for universities Standard and effective information security policies To be customized at each university/institute Reference to the government criterion Especially, on clerical information systems Reference to other standards and orders ISO, and other information security standres 19
20 Assumption in the sample policies A hypothetical A University Two Faculties of Letters and Science 1,000 students(250 each grade) Information Media Center Campus network and information systems One of vice-president is posted as CIO (and CISO) Effective reference for each university Reference to the government criterion to the extent possible Also reference to Network management guideline study working group (2003) to consider conditions in universities Extension to information systems to include information asset security 20
21 Information system management structure in A University University general director Information security advisor Board University IS management committeedecision University management director Auditor Professors IS management committee IS management committee IS management committee IS management committee Audit Genaral Director Genaral Director Genaral Director Genaral Director External reports Technical director Technical director Technical director Technical director Technical Staff Technical Staff Technical Staff Technical Staff Backbone Internet users Users Bureau Users Letters Science Information Media Center 21
22 Usage of the sample policies in university 22
23 Application to policies of each university The sample policies were established for a virtual university Referring the sample, appropriate adjustment (alteration and change) is needed Selection of necessary rules, adjustment, and establishment by a commettee of the university (Some universities made no changes... ) Matching with the university s management policy, systems, and existing rules and regulations Network Information systems Total information security Matching with document handling rules for paper 23
24 An example of application in a university Range and policy of discussion Range Same as the sample for clerical department; Depending on rating for research results, etc. Is a measurement equipment an information system? Rule a general criterion, and discuss at department committee for more details Matching with document handling rules Notice on matching of rating and handling; Papers are governed by existing rules. Fundamental policy, rules and standards Revision by referring the sample policies Rules and regulations for management Retain consistency with existing rules User rules Consistency with rules for existing systems 24
25 Measures for information security education in universities 25
26 Enlightenment for students and members Education for fresh members Entrance guidance(before class registration) Class of information processing exercise(after some experience) Education for staffs On recruitment Periodical development, and evaluation? Education materials for students and members Textbook for information processing exercise Textbook for information security/ethics education 26
27 An example of education material for information security and ethics Tohoku University Computer network guideline for security and ethical conduct (13 pages, 1 st ver. 1999) Precautions for security and ethical conduct, which must be followed by students and staffs when using the computer network. 1.Network community and rules 2.The Basic Concept The freedom of speech and academic freedom Protecting the life, security and property of everyone Respecting everyone s privacy Following the laws, rules and regulations 3.Network Security ID, password, unauthorized access/monitoring, protection, etc. 4.Network Citizenship 5.Cooperating with the net, Using more effectively 27
28 Development of material for information security education Hikari & Tsubasa s Information Security Three Choice Tutorial Fundamental of the sample policies and recent topics Target on university students 14 lessons Easy to self-learn Anime of conversations between students Three choice quiz + friendly tutorial Extension learning Tutorial + Study points + Columns + Self-check Textbook (4 pages description) 28
29 Three Choice Tutorial - Index 1. Virus 2. Phishing 3. Anonymous BBS 4. USB memory 5. SNS 6. Malware 7. Fraud bill 8. Copyright 9. Attached file 10. Wireless LAN 11. Password management 12. OS update 13. Net-shopping 14. Before dispose a PC 29
Teacher Training and Certificate System
 Teacher Training and Certificate System 1. Teacher Training Teacher training in Japan started with the establishment of normal schools (schools for teacher training) in 1872. In 1886, a higher normal school
Teacher Training and Certificate System 1. Teacher Training Teacher training in Japan started with the establishment of normal schools (schools for teacher training) in 1872. In 1886, a higher normal school
Internet Services / Educational Computer System (ECS) at Osaka University
 Internet Services / Educational Computer System (ECS) at Osaka University Fall, 2014 Cybermedia Center Osaka University http://www.cmc.osaka-u.ac.jp/ Osaka University Personal ID (OUPID) Osaka University
Internet Services / Educational Computer System (ECS) at Osaka University Fall, 2014 Cybermedia Center Osaka University http://www.cmc.osaka-u.ac.jp/ Osaka University Personal ID (OUPID) Osaka University
Public Financial Assistance for Formal Education in Japan
 Public Financial Assistance for Formal Education in Japan In Japan, households bear a particularly high proportion of the costs of pre-primary and tertiary education compared with other OECD countries
Public Financial Assistance for Formal Education in Japan In Japan, households bear a particularly high proportion of the costs of pre-primary and tertiary education compared with other OECD countries
TS-3GB-S.R0125-505-0v1.0 VoIP Supplementary Services Descriptions: Call Forwarding - Unconditional
 TS-GB-S.R0--0v.0 VoIP Supplementary Services Descriptions: Call Forwarding - Unconditional 0 年 月 日 制 定 社 団 法 人 情 報 通 信 技 術 委 員 会 THE TELECOMMUNICATION TECHNOLOGY COMMITTEE 本 書 は ( 社 ) 情 報 通 信 技 術 委 員 会
TS-GB-S.R0--0v.0 VoIP Supplementary Services Descriptions: Call Forwarding - Unconditional 0 年 月 日 制 定 社 団 法 人 情 報 通 信 技 術 委 員 会 THE TELECOMMUNICATION TECHNOLOGY COMMITTEE 本 書 は ( 社 ) 情 報 通 信 技 術 委 員 会
Document and entity information
 Company information Company information FASF member mark Document name Document and entity information Aug 2015 第 3 四 半 期 決 算 短 信 日 本 基 準 ( 連 結 ) Filing date 20150710 Company name TRANSACTION CO., Ltd.
Company information Company information FASF member mark Document name Document and entity information Aug 2015 第 3 四 半 期 決 算 短 信 日 本 基 準 ( 連 結 ) Filing date 20150710 Company name TRANSACTION CO., Ltd.
Cost Accounting 1. B r e a k e v e n A n a l y s i s. S t r a t e g y I m p l e m e n t a t i o n B a l a n c e d S c o r e c a r d s
 Cost Accounting 1 B r e a k e v e n A n a l y s i s S t r a t e g y I m p l e m e n t a t i o n B a l a n c e d S c o r e c a r d s S t r a t e g y M o n i t o r i n g R e s p o n s i b i l i t y S e g
Cost Accounting 1 B r e a k e v e n A n a l y s i s S t r a t e g y I m p l e m e n t a t i o n B a l a n c e d S c o r e c a r d s S t r a t e g y M o n i t o r i n g R e s p o n s i b i l i t y S e g
Graduate Program in Japanese Language and Culture (Master s Program) Application Instructions
 Graduate Program in Japanese Language and Culture (Master s Program) Application Instructions For FY 2016 1. Objectives This program is designed to provide teachers of the Japanese-language working abroad
Graduate Program in Japanese Language and Culture (Master s Program) Application Instructions For FY 2016 1. Objectives This program is designed to provide teachers of the Japanese-language working abroad
Chiba Institute of Technology Graduate School
 Academic Year 2015 Chiba Institute of Technology Graduate School Fall Enrollment: September Examination International Student Admission Examination Application Guidelines Graduate School of Engineering
Academic Year 2015 Chiba Institute of Technology Graduate School Fall Enrollment: September Examination International Student Admission Examination Application Guidelines Graduate School of Engineering
How To Run A Server On A Microsoft Cloud Server (For A Small Amount Of Money)
 1SoftLayer 2WindowsServer2003 0 2013 8 t-sasaki@bit-surf.co.jp t-sasaki@bit-isle.co.jp BOE SoftLayer ID desktomo --- --- IT ISPDC CC ADSL3 SIer DC 5 ERP 2015 1 IT IT idc IT 200 140-0002 2-2-28 T 8F TEL
1SoftLayer 2WindowsServer2003 0 2013 8 t-sasaki@bit-surf.co.jp t-sasaki@bit-isle.co.jp BOE SoftLayer ID desktomo --- --- IT ISPDC CC ADSL3 SIer DC 5 ERP 2015 1 IT IT idc IT 200 140-0002 2-2-28 T 8F TEL
育 デジ (Iku-Digi) Promoting further evolution of digital promotion
 育 デジ (Iku-Digi) Promoting further evolution of digital promotion Abstract Digital promotion has established its presence and become a commodity in the pharmaceutical industry. In the last few years, use
育 デジ (Iku-Digi) Promoting further evolution of digital promotion Abstract Digital promotion has established its presence and become a commodity in the pharmaceutical industry. In the last few years, use
Security Threats. Information Security White Paper 2009 Part 2. Attacking Techniques Become More and More Sophisticated
 Information Security White Paper 2009 Part 2 10 M a j o r Security Threats Attacking Techniques Become More and More Sophisticated & Appendix D Information Security Overview for FY 2008 (10 Topics) June
Information Security White Paper 2009 Part 2 10 M a j o r Security Threats Attacking Techniques Become More and More Sophisticated & Appendix D Information Security Overview for FY 2008 (10 Topics) June
Hokkaido University Single Sign-on System User Guide
 Hokkaido University Single Sign-on System User Guide Translation of 北 海 道 大 学 シングルサインオンシステム 利 用 マニュアル ICT Promotion Division, ICT Promotion Office June 23, 2014 Note: This translation is provided solely
Hokkaido University Single Sign-on System User Guide Translation of 北 海 道 大 学 シングルサインオンシステム 利 用 マニュアル ICT Promotion Division, ICT Promotion Office June 23, 2014 Note: This translation is provided solely
第 9 回 仮 想 政 府 セミナー Introduction Shared Servicesを 考 える ~Old but New Challenge~ 東 京 大 学 公 共 政 策 大 学 院 奥 村 裕 一 2014 年 2 月 21 日
 第 9 回 仮 想 政 府 セミナー Introduction Shared Servicesを 考 える ~Old but New Challenge~ 東 京 大 学 公 共 政 策 大 学 院 奥 村 裕 一 2014 年 2 月 21 日 シェアードサービス(SS) ~Definition( 定 義 )~ 複 数 部 門 で 行 っている 同 類 の 業 務 を 一 つの 部 門 に 集 約
第 9 回 仮 想 政 府 セミナー Introduction Shared Servicesを 考 える ~Old but New Challenge~ 東 京 大 学 公 共 政 策 大 学 院 奥 村 裕 一 2014 年 2 月 21 日 シェアードサービス(SS) ~Definition( 定 義 )~ 複 数 部 門 で 行 っている 同 類 の 業 務 を 一 つの 部 門 に 集 約
Direct Marketing Production Printing & Value-Added Services: A strategy for growth
 2015 年 12 月 Direct Marketing Production Printing & Value-Added Services: A strategy for growth 完 成 のご 案 内 ダイレクトマーケティングにおける 印 刷 物 & 付 加 価 値 サービス : 成 長 への 戦 略 とは? 印 刷 物 を 活 用 したダイレクトマーケティングが 成 長 しており デジタル
2015 年 12 月 Direct Marketing Production Printing & Value-Added Services: A strategy for growth 完 成 のご 案 内 ダイレクトマーケティングにおける 印 刷 物 & 付 加 価 値 サービス : 成 長 への 戦 略 とは? 印 刷 物 を 活 用 したダイレクトマーケティングが 成 長 しており デジタル
EDB-Report. 最 新 Web 脆 弱 性 トレンドレポート(2014.11) 2014.11.01~2014.11.30 Exploit-DB(http://exploit-db.com)より 公 開 されている 内 容 に 基 づいた 脆 弱 性 トレンド 情 報 です
 04. 最 新 Web トレンドレポート(04.) 04..0~04..30 Exploit-DB(http://exploit-db.com)より 公 開 されている 内 容 に 基 づいた トレンド 情 報 です サマリー ペンタセキュリティシステムズ 株 式 会 社 R&Dセンター データセキュリティチーム 04 年 月 は Exploit-DBより 公 開 されている の 中 SQLインジェクション(SQL
04. 最 新 Web トレンドレポート(04.) 04..0~04..30 Exploit-DB(http://exploit-db.com)より 公 開 されている 内 容 に 基 づいた トレンド 情 報 です サマリー ペンタセキュリティシステムズ 株 式 会 社 R&Dセンター データセキュリティチーム 04 年 月 は Exploit-DBより 公 開 されている の 中 SQLインジェクション(SQL
レッドハット 製 品 プライスリスト Red Hat Enterprise Linux2013 新 製 品 (ベースサブスクリプション) 更 新 :2015 年 4 22
 Red Hat Enterprise Linux2013 新 製 品 (ベースサブスクリプション) 更 新 :2015 年 4 22 薄 紫 :3 年 型 番 :5 年 型 番 字 : 新 規 追 加 変 更 新 規 新 規 SKU 製 品 名 ソケット ゲストOS サポート 期 間 標 準 価 格 備 考 Server RH00001 Red Hat Enterprise Linux for Virtual
Red Hat Enterprise Linux2013 新 製 品 (ベースサブスクリプション) 更 新 :2015 年 4 22 薄 紫 :3 年 型 番 :5 年 型 番 字 : 新 規 追 加 変 更 新 規 新 規 SKU 製 品 名 ソケット ゲストOS サポート 期 間 標 準 価 格 備 考 Server RH00001 Red Hat Enterprise Linux for Virtual
Procedures to apply for Doctoral Degree
 Procedures to apply for Doctoral Degree Partly revised on March 5, 2015 Graduate School of Global Information and Telecommunication Studies, Waseda University 1. Doctorate Requirements The requirements
Procedures to apply for Doctoral Degree Partly revised on March 5, 2015 Graduate School of Global Information and Telecommunication Studies, Waseda University 1. Doctorate Requirements The requirements
AUTOMOBILE LIABILITY SECURITY ACT
 AUTOMOBILE LIABILITY SECURITY ACT & RELATED CABINET ORDER, MINISTERIAL ORDINANCE AND NOTIFICATION Including: Policy Conditions for Automobile Liability Insurance As of May 2, 2011 Translated and published
AUTOMOBILE LIABILITY SECURITY ACT & RELATED CABINET ORDER, MINISTERIAL ORDINANCE AND NOTIFICATION Including: Policy Conditions for Automobile Liability Insurance As of May 2, 2011 Translated and published
 DC DC φ φ DC φ φ AC φ φ φ φ φ φ φ 24V DC Class2 This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1 ) this device may not cause harmful interference,and
DC DC φ φ DC φ φ AC φ φ φ φ φ φ φ 24V DC Class2 This device complies with Part 15 of the FCC Rules. Operation is subject to the following two conditions: (1 ) this device may not cause harmful interference,and
Upper Secondary Education in Japan
 Upper Secondary Education in Japan The role of upper secondary education in Japan is to provide higher general education and specialized education according to students mental and physical development
Upper Secondary Education in Japan The role of upper secondary education in Japan is to provide higher general education and specialized education according to students mental and physical development
アジアにおける 保 険 研 究 の 動 向
 アジアにおける 保 険 研 究 の 動 向 神 谷 信 一 南 洋 理 工 大 学 Nanyang Technological University Singapore 2015 年 11 月 20 日 東 京 内 容 NTU Insurance Risk and Finance Research Centre (IRFRC) Taiwan Risk and Insurance Association
アジアにおける 保 険 研 究 の 動 向 神 谷 信 一 南 洋 理 工 大 学 Nanyang Technological University Singapore 2015 年 11 月 20 日 東 京 内 容 NTU Insurance Risk and Finance Research Centre (IRFRC) Taiwan Risk and Insurance Association
オープンソース NFV プラットフォーム の 取 り 組 み
 オープンソース NFV プラットフォーム の 取 り 組 み 平 成 27 年 4 月 レッドハット アジア 太 平 洋 地 域 事 業 開 発 戦 略 本 部 テレコム & NFV チーフ テクノロジスト 杉 山 秀 次 自 己 紹 介 ネットワーク 業 界 歴 27 年 現 在 レッドハットアジア 太 平 洋 地 域 において NFVチーフテクノロジストとして 活 動 前 職 はジュニパーネットワークスにてR&Dサポート
オープンソース NFV プラットフォーム の 取 り 組 み 平 成 27 年 4 月 レッドハット アジア 太 平 洋 地 域 事 業 開 発 戦 略 本 部 テレコム & NFV チーフ テクノロジスト 杉 山 秀 次 自 己 紹 介 ネットワーク 業 界 歴 27 年 現 在 レッドハットアジア 太 平 洋 地 域 において NFVチーフテクノロジストとして 活 動 前 職 はジュニパーネットワークスにてR&Dサポート
医 学 生 物 学 一 般 問 題 ( 問 題 用 紙 1 枚 解 答 用 紙 2 枚 )
 平 成 26 年 度 大 学 院 医 学 研 究 科 博 士 課 程 入 学 試 験 (1 回 目 ) 医 学 生 物 学 一 般 問 題 ( 問 題 用 紙 1 枚 解 答 用 紙 2 枚 ) 以 下 の 問 題 1 問 題 4のうち 二 つの 問 題 を 選 択 して 解 答 しなさい 一 つの 問 題 につき1 枚 の 解 答 用 紙 を 使 用 しなさい 紙 面 不 足 の 場 合 は 裏
平 成 26 年 度 大 学 院 医 学 研 究 科 博 士 課 程 入 学 試 験 (1 回 目 ) 医 学 生 物 学 一 般 問 題 ( 問 題 用 紙 1 枚 解 答 用 紙 2 枚 ) 以 下 の 問 題 1 問 題 4のうち 二 つの 問 題 を 選 択 して 解 答 しなさい 一 つの 問 題 につき1 枚 の 解 答 用 紙 を 使 用 しなさい 紙 面 不 足 の 場 合 は 裏
Abbreviations. Learning Goals and Objectives 学 習 到 達 目 標. Structure of Presentation
 Learning Goals and Objectives 学 習 到 達 目 標 Accrediting Medical Schools: Lessons learned from Liaison Committee on Medical Education (LCME) process in the United States 医 学 部 の 認 証 評 価 : 米 国 LCMEの 認 証 評
Learning Goals and Objectives 学 習 到 達 目 標 Accrediting Medical Schools: Lessons learned from Liaison Committee on Medical Education (LCME) process in the United States 医 学 部 の 認 証 評 価 : 米 国 LCMEの 認 証 評
Advanced Training Program for Teachers of the Japanese-Language Application Instructions For FY 2016
 Advanced Training Program for Teachers of the Japanese-Language Application Instructions For FY 2016 1. Objectives The Advanced Training Program at the Japan Foundation Japanese-Language Institute, Urawa
Advanced Training Program for Teachers of the Japanese-Language Application Instructions For FY 2016 1. Objectives The Advanced Training Program at the Japan Foundation Japanese-Language Institute, Urawa
Chiba Institute of Technology Graduate School
 Academic Year 2016 Chiba Institute of Technology Graduate School Spring Enrollment: September and March International Student Admission Application Guidelines Graduate School of Engineering Graduate School
Academic Year 2016 Chiba Institute of Technology Graduate School Spring Enrollment: September and March International Student Admission Application Guidelines Graduate School of Engineering Graduate School
7 myths about cars and free trade agreements
 ECIPE PRESENTATION» 7 myths about cars and free trade agreements Hosuk Lee-Makiyama Co-Director, European Centre for International Political Economy (ECIPE) Myth #1 作 り 話 #1 Mythe #1 Foreign imports are
ECIPE PRESENTATION» 7 myths about cars and free trade agreements Hosuk Lee-Makiyama Co-Director, European Centre for International Political Economy (ECIPE) Myth #1 作 り 話 #1 Mythe #1 Foreign imports are
Electronic Health Record (EHR) for use and
 Electronic Health Record (EHR) for use and development in developing countries Professor KANO Sadahiko Waseda University Graduate School of Asia Pacific Studies Workshop on Global Medicine and Local Culture:
Electronic Health Record (EHR) for use and development in developing countries Professor KANO Sadahiko Waseda University Graduate School of Asia Pacific Studies Workshop on Global Medicine and Local Culture:
EFL Information Gap Activities for Architecture Majors
 東 洋 大 学 人 間 科 学 総 合 研 究 所 紀 要 第 10 号 (2009) 11-20 11 EFL Information Gap Activities for Architecture Majors Michael SCHULMAN * A large body of literature supports the notion that information gap activities,
東 洋 大 学 人 間 科 学 総 合 研 究 所 紀 要 第 10 号 (2009) 11-20 11 EFL Information Gap Activities for Architecture Majors Michael SCHULMAN * A large body of literature supports the notion that information gap activities,
Current Situation of Research Nurse Education and Future Perspectives in Japan
 Current Situation of Research Nurse Education and Future Perspectives in Japan Eriko Aotani Clinical Trials Coordinating Center The Kitasato Institute 1 Who are involved in Clinical Trials? Patients. Others
Current Situation of Research Nurse Education and Future Perspectives in Japan Eriko Aotani Clinical Trials Coordinating Center The Kitasato Institute 1 Who are involved in Clinical Trials? Patients. Others
Information Security Policy
 Information Security Policy Touro College/University ( Touro ) is committed to information security. Information security is defined as protection of data, applications, networks, and computer systems
Information Security Policy Touro College/University ( Touro ) is committed to information security. Information security is defined as protection of data, applications, networks, and computer systems
gehr Project: Nation-wide EHR Implementation in JAPAN
 Kyoto Smart city Expo. 2016.06.01 Kyoto University University of Miyazaki gehr Project: Nation-wide EHR Implementation in JAPAN YOSHIHARA Hiroyuki, MD/Ph.D Emeritus professor of Kyoto University and University
Kyoto Smart city Expo. 2016.06.01 Kyoto University University of Miyazaki gehr Project: Nation-wide EHR Implementation in JAPAN YOSHIHARA Hiroyuki, MD/Ph.D Emeritus professor of Kyoto University and University
Green Solution with Simegy
 要 旨 オフィス 環 境 における 複 合 機 やプリンターの 消 費 電 力 の 見 える 化 や 消 費 電 力 の 削 減 のためのグリーン ソリューションが 近 年 強 く 求 められている 富 士 ゼ ロックスは 複 合 機 やプリンターを 管 理 / 活 用 するた めの ApeosWare Management Suite のようなソフ トウェアに 対 して ゼロックスの Simegy
要 旨 オフィス 環 境 における 複 合 機 やプリンターの 消 費 電 力 の 見 える 化 や 消 費 電 力 の 削 減 のためのグリーン ソリューションが 近 年 強 く 求 められている 富 士 ゼ ロックスは 複 合 機 やプリンターを 管 理 / 活 用 するた めの ApeosWare Management Suite のようなソフ トウェアに 対 して ゼロックスの Simegy
Utilization & Promotion Activities of Cloud in Japan
 CloudAsia Utilization & Promotion Activities of Cloud in Japan 28th, October, 2015 ASP-SaaS-Cloud Consortium (ASPIC) http://www.aspicjapan.org/en/index.html 1 Agenda Current situation in Japan Cloud promotion
CloudAsia Utilization & Promotion Activities of Cloud in Japan 28th, October, 2015 ASP-SaaS-Cloud Consortium (ASPIC) http://www.aspicjapan.org/en/index.html 1 Agenda Current situation in Japan Cloud promotion
Countermeasures against Information Leakage
 (5) Countermeasures against Information Leakage Seven Rules for People Working in Business Enterprises!! Information-technology Promotion Agency IT Security Center http://www.ipa.go.jp/security/ July 1,
(5) Countermeasures against Information Leakage Seven Rules for People Working in Business Enterprises!! Information-technology Promotion Agency IT Security Center http://www.ipa.go.jp/security/ July 1,
NTP Reflection DDoS Attack Explanatory Document
 NTP Reflection DDoS Attack Explanatory Document 3/13/2015 Edition 1 JANOG NTP Information Exchange WG ntp-talk-wg@janog.gr.jp Translation Contributed by SEIKO Solutions Inc. 1 2 Table of Contents 1. Overview...
NTP Reflection DDoS Attack Explanatory Document 3/13/2015 Edition 1 JANOG NTP Information Exchange WG ntp-talk-wg@janog.gr.jp Translation Contributed by SEIKO Solutions Inc. 1 2 Table of Contents 1. Overview...
レッドハット 製 品 プライスリスト 標 準 価 格. Red Hat Enterprise Linux 製 品 (RHEL Server)
 レッドハット 製 品 プライスリスト Red Hat Enterprise Linux 製 品 (RHEL Server) 新 価 格 は6 月 1 日 から 適 用 開 始 と 致 します 薄 紫 :3 年 型 番 水 色 :5 年 型 番 赤 文 字 : 新 規 追 加 変 更 当 価 格 表 は 予 告 なしに 変 更 する 場 合 がございますので ご 了 承 ください 税 込 価 格 は
レッドハット 製 品 プライスリスト Red Hat Enterprise Linux 製 品 (RHEL Server) 新 価 格 は6 月 1 日 から 適 用 開 始 と 致 します 薄 紫 :3 年 型 番 水 色 :5 年 型 番 赤 文 字 : 新 規 追 加 変 更 当 価 格 表 は 予 告 なしに 変 更 する 場 合 がございますので ご 了 承 ください 税 込 価 格 は
Marist College. Information Security Policy
 Marist College Information Security Policy February 2005 INTRODUCTION... 3 PURPOSE OF INFORMATION SECURITY POLICY... 3 INFORMATION SECURITY - DEFINITION... 4 APPLICABILITY... 4 ROLES AND RESPONSIBILITIES...
Marist College Information Security Policy February 2005 INTRODUCTION... 3 PURPOSE OF INFORMATION SECURITY POLICY... 3 INFORMATION SECURITY - DEFINITION... 4 APPLICABILITY... 4 ROLES AND RESPONSIBILITIES...
レッドハット 製 品 プライスリスト Red Hat Enterprise Linux 製 品 (RHEL for HPC) 更 新 :2015 年 4 22
 レッドハット 製 品 プライスリスト Red Hat Enterprise Linux 製 品 (RHEL for HPC) 更 新 :2015 年 4 22 薄 紫 :3 年 型 番 :5 年 型 番 字 : 新 規 追 加 変 更 当 価 格 表 は 予 告 なしに 変 更 する 場 合 がございますので ご 了 承 ください 価 格 は 全 て 税 抜 きでの 掲 載 となっております 新 規
レッドハット 製 品 プライスリスト Red Hat Enterprise Linux 製 品 (RHEL for HPC) 更 新 :2015 年 4 22 薄 紫 :3 年 型 番 :5 年 型 番 字 : 新 規 追 加 変 更 当 価 格 表 は 予 告 なしに 変 更 する 場 合 がございますので ご 了 承 ください 価 格 は 全 て 税 抜 きでの 掲 載 となっております 新 規
When a student leaves this intensive 5 day class they will have hands on understanding and experience in Ethical Hacking.
 Ethical Hacking and Countermeasures Course Description: This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems.
Ethical Hacking and Countermeasures Course Description: This class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems.
What legal aspects are needed to address specific ICT related issues?
 What legal aspects are needed to address specific ICT related issues? Belhassen ZOUARI CEO, National Agency for Computer Security, Tunisia Head of the Tunisian Cert (tuncert), E-mail : b.zouari@ansi.tn
What legal aspects are needed to address specific ICT related issues? Belhassen ZOUARI CEO, National Agency for Computer Security, Tunisia Head of the Tunisian Cert (tuncert), E-mail : b.zouari@ansi.tn
Addressing Japan s Healthcare Challenges with Information Technology
 a report of the csis global health policy center Addressing Japan s Healthcare Challenges with Information Technology recommendations from the u.s. experience Author John D. Halamka August 2011 a report
a report of the csis global health policy center Addressing Japan s Healthcare Challenges with Information Technology recommendations from the u.s. experience Author John D. Halamka August 2011 a report
PRACTICE. Field Trial against Cyber-attacks through International Collaboration ISPs Effort to Establish Quick Response Scheme. September 24th, 2013
 PRACTICE Field Trial against Cyber-attacks through International Collaboration ISPs Effort to Establish Quick Response Scheme September 24th, 2013 Satoshi NORITAKE NTT Communications / Telecom-ISAC Japan
PRACTICE Field Trial against Cyber-attacks through International Collaboration ISPs Effort to Establish Quick Response Scheme September 24th, 2013 Satoshi NORITAKE NTT Communications / Telecom-ISAC Japan
Information Security Policies in the Telecommunications Field
 Inmation Security Policies in the Telecommunications Field ~ Toward the Construction Safe and Secure Network Foundations~ Ministry Internal Affairs and Communications, JAPAN September 29th 2004 0 1 Contents
Inmation Security Policies in the Telecommunications Field ~ Toward the Construction Safe and Secure Network Foundations~ Ministry Internal Affairs and Communications, JAPAN September 29th 2004 0 1 Contents
How To Manage Security On A Networked Computer System
 Unified Security Reduce the Cost of Compliance Introduction In an effort to achieve a consistent and reliable security program, many organizations have adopted the standard as a key compliance strategy
Unified Security Reduce the Cost of Compliance Introduction In an effort to achieve a consistent and reliable security program, many organizations have adopted the standard as a key compliance strategy
GRADUATE SCHOOL OF INTERNATIONAL RELATIONS
 GRADUATE SCHOOL OF INTERNATIONAL RELATIONS INTERNATIONAL UNIVERSITY OF JAPAN HANDBOOK for 1-year Program Students who enrolled in THE ACADEMIC YEAR 2014-2015 CALENDAR OF THE ACADEMIC YEAR 2014-2015 FALL
GRADUATE SCHOOL OF INTERNATIONAL RELATIONS INTERNATIONAL UNIVERSITY OF JAPAN HANDBOOK for 1-year Program Students who enrolled in THE ACADEMIC YEAR 2014-2015 CALENDAR OF THE ACADEMIC YEAR 2014-2015 FALL
Biological Sciences Computer Systems
 Biological Sciences Computer Systems Summary of Acceptable Use Policies There are several policies that users must adhere to when using the Life Sciences Network. Most are derived from federal and state
Biological Sciences Computer Systems Summary of Acceptable Use Policies There are several policies that users must adhere to when using the Life Sciences Network. Most are derived from federal and state
この 外 国 弁 護 士 による 法 律 事 務 の 取 扱 いに 関 する 特 別 措 置 法 施 行 規 則 の 翻 訳 は 平
 この 外 国 弁 護 士 による 法 律 事 務 の 取 扱 いに 関 する 特 別 措 置 法 施 行 規 則 の 翻 訳 は 平 成 十 六 年 法 務 省 令 第 6 号 までの 改 正 ( 平 成 16 年 4 月 1 日 施 行 )について 法 令 用 語 日 英 標 準 対 訳 辞 書 ( 平 成 18 年 3 月 版 )に 準 拠 して 作 成 したものです なお この 法 令 の 翻
この 外 国 弁 護 士 による 法 律 事 務 の 取 扱 いに 関 する 特 別 措 置 法 施 行 規 則 の 翻 訳 は 平 成 十 六 年 法 務 省 令 第 6 号 までの 改 正 ( 平 成 16 年 4 月 1 日 施 行 )について 法 令 用 語 日 英 標 準 対 訳 辞 書 ( 平 成 18 年 3 月 版 )に 準 拠 して 作 成 したものです なお この 法 令 の 翻
Introduction to Computing @ WSU
 Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
Tokyo Tech Education Reform
 Tokyo Tech Education Reform For current s continuing degree programs in 2016 Program Overview Main points of education reform Q & A 1 Goal of Education Reform 国 立 大 学 法 人 東 京 工 業 大 学 教 育 改 革 のお 知 らせ We
Tokyo Tech Education Reform For current s continuing degree programs in 2016 Program Overview Main points of education reform Q & A 1 Goal of Education Reform 国 立 大 学 法 人 東 京 工 業 大 学 教 育 改 革 のお 知 らせ We
Research on Support for Persons with Mental Disability to Make Transition to Regular Employment
 Research on Support for Persons with Mental Disability to Make Transition to Regular Employment (Research Report No.108) Summary Key Words Persons with Mental Disabilities, Step-Up Employment Program for
Research on Support for Persons with Mental Disability to Make Transition to Regular Employment (Research Report No.108) Summary Key Words Persons with Mental Disabilities, Step-Up Employment Program for
Responsible Administrative Unit: Computing, Communications & Information Technologies. Information Technology Appropriate Use Policy
 1.0 BACKGROUND AND PURPOSE Information Technology ( IT ) includes a vast and growing array of computing, electronic and voice communications facilities and services. At the Colorado School of Mines ( Mines
1.0 BACKGROUND AND PURPOSE Information Technology ( IT ) includes a vast and growing array of computing, electronic and voice communications facilities and services. At the Colorado School of Mines ( Mines
POLICIES AND REGULATIONS Policy #78
 Peel District School Board POLICIES AND REGULATIONS Policy #78 DIGITAL CITIZENSHIP Digital Citizenship Digital citizenship is defined as the norms of responsible behaviour related to the appropriate use
Peel District School Board POLICIES AND REGULATIONS Policy #78 DIGITAL CITIZENSHIP Digital Citizenship Digital citizenship is defined as the norms of responsible behaviour related to the appropriate use
Ritsumeikan University Global 30 Project AY 2012 Follow-up
 Ritsumeikan University Global 30 Project AY 2012 Follow-up Kiyofumi Kawaguchi President, Ritsumeikan University 1 Table of Contents Global 30 Project Achievements and Related Results Achievements and Goals,
Ritsumeikan University Global 30 Project AY 2012 Follow-up Kiyofumi Kawaguchi President, Ritsumeikan University 1 Table of Contents Global 30 Project Achievements and Related Results Achievements and Goals,
Data Sciences Program 2015 (DSP2015)
 データ 科 学 を 実 践 する 社 会 生 命 環 境 基 盤 構 築 人 材 の 育 成 プログラム Development of Human Resource Creating Social, Life, and Environmental Foundations Data Sciences Program 2015 (DSP2015) GUIDANCE FOR ENTRANCE EXAMINATION
データ 科 学 を 実 践 する 社 会 生 命 環 境 基 盤 構 築 人 材 の 育 成 プログラム Development of Human Resource Creating Social, Life, and Environmental Foundations Data Sciences Program 2015 (DSP2015) GUIDANCE FOR ENTRANCE EXAMINATION
Most EFL teachers in Japan find that there are groups of verbs which consistently
 Results of a Corpus Study of LOOK, SEE, and WATCH Gregory C. Anthony Hachinohe University Reference Data: Anthony, G. C. (2012). Results of a Corpus Study of LOOK, SEE, and WATCH. In A. Stewart & N. Sonda
Results of a Corpus Study of LOOK, SEE, and WATCH Gregory C. Anthony Hachinohe University Reference Data: Anthony, G. C. (2012). Results of a Corpus Study of LOOK, SEE, and WATCH. In A. Stewart & N. Sonda
NIPISSING UNIVERSITY DIRECTORY OF RECORDS
 NIPISSING UNIVERSITY DIRECTORY OF RECORDS PERSONAL INFORMATION BANKS Personal Information Bank (PIB) - a collection of personal information that is organized and can be retrieved by an individual's name
NIPISSING UNIVERSITY DIRECTORY OF RECORDS PERSONAL INFORMATION BANKS Personal Information Bank (PIB) - a collection of personal information that is organized and can be retrieved by an individual's name
Changing Views on Motivation in a Globalizing World
 32 The Language Teacher READERS FORUM Changing Views on Motivation in a Globalizing World Elizabeth Wadell Diablo Valley College, California April Shandor English Center, Oakland, California Given that
32 The Language Teacher READERS FORUM Changing Views on Motivation in a Globalizing World Elizabeth Wadell Diablo Valley College, California April Shandor English Center, Oakland, California Given that
Tokyo Tech Education Reform
 Tokyo Tech Education Reform For prospective graduate s Program Overview Main points of education reform Q & A 1 Goal of Education Reform 国 立 大 学 法 人 東 京 工 業 大 学 教 育 改 革 のお 知 らせ We will cultivate s with
Tokyo Tech Education Reform For prospective graduate s Program Overview Main points of education reform Q & A 1 Goal of Education Reform 国 立 大 学 法 人 東 京 工 業 大 学 教 育 改 革 のお 知 らせ We will cultivate s with
*The above quota includes the quotas for the other programs in the Accounting School.
 Tohoku University Accounting School 2016 Academic Year Program in International Accounting Policy Application Guidelines for Student Screening (April Entrance) The Tohoku University Accounting School will
Tohoku University Accounting School 2016 Academic Year Program in International Accounting Policy Application Guidelines for Student Screening (April Entrance) The Tohoku University Accounting School will
Primary Schools in Japan
 Primary Schools in Japan Overview Japanese primary school lasts for six years. In Japan, the school system is generally called the 6-3-3-4 year system, which expressly places primary school education as
Primary Schools in Japan Overview Japanese primary school lasts for six years. In Japan, the school system is generally called the 6-3-3-4 year system, which expressly places primary school education as
ใบสม ครเข าร วมโครงการน ส ตแลกเปล ยนมหาว ทยาล ยเกษตรศาสตร
 ใบสม ครเข าร วมโครงการน ส ตแลกเปล ยนมหาว ทยาล ยเกษตรศาสตร ส วนท 1 รายละเอ ยดโครงการแลกเปล ยน มหาว ทยาล ยค ส ญญาท สม ครเข าร วมโครงการแลกเปล ยน...ประเทศ... ภาคการศ กษาท สม คร เมษายน 2557 ก นยายน 2557 ต
ใบสม ครเข าร วมโครงการน ส ตแลกเปล ยนมหาว ทยาล ยเกษตรศาสตร ส วนท 1 รายละเอ ยดโครงการแลกเปล ยน มหาว ทยาล ยค ส ญญาท สม ครเข าร วมโครงการแลกเปล ยน...ประเทศ... ภาคการศ กษาท สม คร เมษายน 2557 ก นยายน 2557 ต
Data Mining for Risk Management in Hospital Information Systems
 Data Mining for Risk Management in Hospital Information Systems Shusaku Tsumoto and Shoji Hirano Department of Medical Informatics, Shimane University, School of Medicine, 89-1 Enya-cho, Izumo 693-8501
Data Mining for Risk Management in Hospital Information Systems Shusaku Tsumoto and Shoji Hirano Department of Medical Informatics, Shimane University, School of Medicine, 89-1 Enya-cho, Izumo 693-8501
Joint Universities Computer Centre Limited ( JUCC ) Information Security Awareness Training - Session One
 Joint Universities Computer Centre Limited ( JUCC ) Information Security Awareness Training - Session One End User Security, IS Control Evaluation & Self- Assessment Information Security Trends and Countermeasures
Joint Universities Computer Centre Limited ( JUCC ) Information Security Awareness Training - Session One End User Security, IS Control Evaluation & Self- Assessment Information Security Trends and Countermeasures
社 会 と 健 康 Diploma Program
 北 海 道 大 学 環 境 健 康 科 学 研 究 教 育 センター Hokkaido University Center for and Sciences (CEHS) 社 会 と 健 康 Diploma Program 履 修 の 手 引 き, Environment Diploma Program Course Guide 平 成 7 年 度 (FY015) 015.7 Program Objective
北 海 道 大 学 環 境 健 康 科 学 研 究 教 育 センター Hokkaido University Center for and Sciences (CEHS) 社 会 と 健 康 Diploma Program 履 修 の 手 引 き, Environment Diploma Program Course Guide 平 成 7 年 度 (FY015) 015.7 Program Objective
さくらインターネット 研 究 所 上 級 研 究 員 日 本 Vyattaユーザー 会 運 営 委 員 松 本 直 人
 2011 年 08 月 18 日 さくらインターネット 研 究 所 上 級 研 究 員 日 本 Vyattaユーザー 会 運 営 委 員 松 本 直 人 (C)Copyright 1996-2010 SAKURA Internet Inc. 現 在 起 こっているコト 従 来 のコンピューティング クラウド コンピューティング パブリック プライベートの 区 別 なくクラウドへ 移 行 中 仮 想
2011 年 08 月 18 日 さくらインターネット 研 究 所 上 級 研 究 員 日 本 Vyattaユーザー 会 運 営 委 員 松 本 直 人 (C)Copyright 1996-2010 SAKURA Internet Inc. 現 在 起 こっているコト 従 来 のコンピューティング クラウド コンピューティング パブリック プライベートの 区 別 なくクラウドへ 移 行 中 仮 想
Educational Administration in Japan
 Educational Administration in Japan This article presents an overview of the development of educational administration in Japan since the introduction of a modern education system, and shows how the system
Educational Administration in Japan This article presents an overview of the development of educational administration in Japan since the introduction of a modern education system, and shows how the system
My experience of Ruby Education in Taiwan
 My experience of Ruby Education in Taiwan ~ 台 湾 にRuby 教 育 で 得 た 知 見 Mu-Fan Teng(@ryudoawaru) Ruby World Conference はじめに 発 表 する 機 会 をいただき ありがとうございます 自 己 紹 介 鄧 慕 凡 (Mu-Fan Teng) a.k.a: 竜 堂 終 両 方 どもある 小 説
My experience of Ruby Education in Taiwan ~ 台 湾 にRuby 教 育 で 得 た 知 見 Mu-Fan Teng(@ryudoawaru) Ruby World Conference はじめに 発 表 する 機 会 をいただき ありがとうございます 自 己 紹 介 鄧 慕 凡 (Mu-Fan Teng) a.k.a: 竜 堂 終 両 方 どもある 小 説
Acceptable Use of Computing and Information Technology Resources
 Acceptable Use of Computing and Information Technology Resources Version 1.0, February2, 2010 General Statement As part of its educational mission, Hocking College acquires, develops, and maintains computers,
Acceptable Use of Computing and Information Technology Resources Version 1.0, February2, 2010 General Statement As part of its educational mission, Hocking College acquires, develops, and maintains computers,
Managing HKU author reputations, enhancing HKU's reputation. Creative Commons: Attribution 3.0 Hong Kong License
 Title Managing HKU author reputations, enhancing HKU's reputation Author(s) Palmer, DT Citation The World 100 Conference: Managing University Reputation in a Competitive World, Hong Kong, 22-23 June 2010.
Title Managing HKU author reputations, enhancing HKU's reputation Author(s) Palmer, DT Citation The World 100 Conference: Managing University Reputation in a Competitive World, Hong Kong, 22-23 June 2010.
Odessa College Use of Computer Resources Policy Policy Date: November 2010
 Odessa College Use of Computer Resources Policy Policy Date: November 2010 1.0 Overview Odessa College acquires, develops, and utilizes computer resources as an important part of its physical and educational
Odessa College Use of Computer Resources Policy Policy Date: November 2010 1.0 Overview Odessa College acquires, develops, and utilizes computer resources as an important part of its physical and educational
Panasonic AC-DC Power Supply Design Support Service
 Panasonic AC-DC Power Supply Design Support Service The best solution to design your AC-DC power supply (how to design a switching power supply, order a transformer, prevent EMI, etc.) Panasonic s IPD
Panasonic AC-DC Power Supply Design Support Service The best solution to design your AC-DC power supply (how to design a switching power supply, order a transformer, prevent EMI, etc.) Panasonic s IPD
The Course of Study is the series of guidelines for subject
 The Language Teacher Feature Article 3 Behind MEXT s new Course of Study Guidelines Keywords Course of Study Guidelines, MEXT, Communicative Language Teaching (CLT) in Japan The new Course of Study Guidelines
The Language Teacher Feature Article 3 Behind MEXT s new Course of Study Guidelines Keywords Course of Study Guidelines, MEXT, Communicative Language Teaching (CLT) in Japan The new Course of Study Guidelines
Master of Tropical Medicine
 PROSPECTUS 2014-2015 Master of Tropical Medicine Graduate School of Biomedical Sciences, Nagasaki University Admission Policy Applicants for this school, designed to educate students who will lead the
PROSPECTUS 2014-2015 Master of Tropical Medicine Graduate School of Biomedical Sciences, Nagasaki University Admission Policy Applicants for this school, designed to educate students who will lead the
Information Security. Be Aware, Secure, and Vigilant. https://www.gosafeonline.sg/ Be vigilant about information security and enjoy using the internet
 Be Aware, Secure, and Vigilant Information Security Use the Internet with Confidence Be vigilant about information security and enjoy using the internet https://www.gosafeonline.sg/ The Smartphone Security
Be Aware, Secure, and Vigilant Information Security Use the Internet with Confidence Be vigilant about information security and enjoy using the internet https://www.gosafeonline.sg/ The Smartphone Security
TS-M2M-0002v0.6.2 onem2m Requirements Technical Specification
 TS-M2M-0002v0.6.2 onem2m Requirements Technical Specification 2014 年 1 月 17 日 制 定 一 般 社 団 法 人 情 報 通 信 技 術 委 員 会 THE TELECOMMUNICATION TECHNOLOGY COMMITTEE 本 書 は 一 般 社 団 法 人 情 報 通 信 技 術 委 員 会 が 著 作 権 を
TS-M2M-0002v0.6.2 onem2m Requirements Technical Specification 2014 年 1 月 17 日 制 定 一 般 社 団 法 人 情 報 通 信 技 術 委 員 会 THE TELECOMMUNICATION TECHNOLOGY COMMITTEE 本 書 は 一 般 社 団 法 人 情 報 通 信 技 術 委 員 会 が 著 作 権 を
Corporate Amazon Gift Certificate Instruction for Downloading the GC File
 Corporate Amazon Gift Certificate Instruction for Downloading the GC File August 2010 (rev1) Amazon Gift Cards Japan KK Thank you very much for ordering Corporate Amazon Gift Certificate. We deliver Corporate
Corporate Amazon Gift Certificate Instruction for Downloading the GC File August 2010 (rev1) Amazon Gift Cards Japan KK Thank you very much for ordering Corporate Amazon Gift Certificate. We deliver Corporate
The existence of credential effects in Canadian nursing education; Quebec versus the rest of Canada
 タイトル 著 者 The existence of credential effec nursing education : Quebec versus Canada Lee, Heyung-Jik 引 用 北 海 商 科 大 学 論 集, 2(1): 1-9 発 行 日 2013-02 The existence of credential effects in Canadian nursing
タイトル 著 者 The existence of credential effec nursing education : Quebec versus Canada Lee, Heyung-Jik 引 用 北 海 商 科 大 学 論 集, 2(1): 1-9 発 行 日 2013-02 The existence of credential effects in Canadian nursing
Introduction to FDS Entry Management System
 Introduction to FDS Entry Management System January 2015 Fit Design System Co., Ltd. http://www.fit-design.com : Feature and Function of Entry Management System Feature Wiring work
Introduction to FDS Entry Management System January 2015 Fit Design System Co., Ltd. http://www.fit-design.com : Feature and Function of Entry Management System Feature Wiring work
Effect of Captioning Lecture Videos For Learning in Foreign Language 外 国 語 ( 英 語 ) 講 義 映 像 に 対 する 字 幕 提 示 の 理 解 度 効 果
 Effect of Captioning Lecture Videos For Learning in Foreign Language VERI FERDIANSYAH 1 SEIICHI NAKAGAWA 1 Toyohashi University of Technology, Tenpaku-cho, Toyohashi 441-858 Japan E-mail: {veri, nakagawa}@slp.cs.tut.ac.jp
Effect of Captioning Lecture Videos For Learning in Foreign Language VERI FERDIANSYAH 1 SEIICHI NAKAGAWA 1 Toyohashi University of Technology, Tenpaku-cho, Toyohashi 441-858 Japan E-mail: {veri, nakagawa}@slp.cs.tut.ac.jp
PASS4TEST 専 門 IT 認 証 試 験 問 題 集 提 供 者
 PASS4TEST 専 門 IT 認 証 試 験 問 題 集 提 供 者 http://www.pass4test.jp 1 年 で 無 料 進 級 することに 提 供 する Exam : MB2-707 Title : Microsoft Dynamics CRM Customization and Configuration Vendor : Microsoft Version : DEMO 1
PASS4TEST 専 門 IT 認 証 試 験 問 題 集 提 供 者 http://www.pass4test.jp 1 年 で 無 料 進 級 することに 提 供 する Exam : MB2-707 Title : Microsoft Dynamics CRM Customization and Configuration Vendor : Microsoft Version : DEMO 1
Act on Special Measures Concerning Nuclear Emergency Preparedness (Act No. 156 of December 17, 1999)
 この 原 子 力 災 害 対 策 特 別 措 置 法 の 翻 訳 は 平 成 18 年 法 律 第 118 号 までの 改 正 ( 平 成 19 年 1 月 9 日 施 行 )について 法 令 用 語 日 英 標 準 対 訳 辞 書 ( 平 成 19 年 3 月 版 )に 準 拠 して 作 成 したものです なお この 法 令 の 翻 訳 は 公 定 訳 ではありません 法 的 効 力 を 有 するのは
この 原 子 力 災 害 対 策 特 別 措 置 法 の 翻 訳 は 平 成 18 年 法 律 第 118 号 までの 改 正 ( 平 成 19 年 1 月 9 日 施 行 )について 法 令 用 語 日 英 標 準 対 訳 辞 書 ( 平 成 19 年 3 月 版 )に 準 拠 して 作 成 したものです なお この 法 令 の 翻 訳 は 公 定 訳 ではありません 法 的 効 力 を 有 するのは
Preschool Education and Care in Japan
 Preschool Education and Care in Japan Preschool education is called pre-primary education in the ISCED (International Standard Classification of Education, designed by UNESCO) and classified as level 0.
Preschool Education and Care in Japan Preschool education is called pre-primary education in the ISCED (International Standard Classification of Education, designed by UNESCO) and classified as level 0.
Student Tech Security Training. ITS Security Office
 Student Tech Security Training ITS Security Office ITS Security Office Total Security is an illusion security will always be slightly broken. Find strategies for living with it. Monitor our Network with
Student Tech Security Training ITS Security Office ITS Security Office Total Security is an illusion security will always be slightly broken. Find strategies for living with it. Monitor our Network with
Using the Moodle Reader Module to Facilitate an Extensive. Reading Program
 RESEARCH NOTE 41 Using the Moodle Reader Module to Facilitate an Extensive Reading Program Wayne Pennington Introduction Early attempts to incorporate Extensive Reading as a teaching technique can be traced
RESEARCH NOTE 41 Using the Moodle Reader Module to Facilitate an Extensive Reading Program Wayne Pennington Introduction Early attempts to incorporate Extensive Reading as a teaching technique can be traced
Audit and Risk Management Committee. IT Security Update
 Audit and Risk Management Committee 26 th February 2015 IT Security Update Description of paper 1. The purpose of this paper is to update the Committee on current security issues and what steps are being
Audit and Risk Management Committee 26 th February 2015 IT Security Update Description of paper 1. The purpose of this paper is to update the Committee on current security issues and what steps are being
For victims of traffic accidents
 For victims of traffic accidents 交 通 事 故 に 遭 われた 方 へ (Guideline for victims) ( 被 害 者 の 手 引 ) Name( 名 前 ) Police Station( 警 察 署 ) Contact( 担 当 者 ) Telephone Number( 電 話 番 号 ) Preface This leaflet has been
For victims of traffic accidents 交 通 事 故 に 遭 われた 方 へ (Guideline for victims) ( 被 害 者 の 手 引 ) Name( 名 前 ) Police Station( 警 察 署 ) Contact( 担 当 者 ) Telephone Number( 電 話 番 号 ) Preface This leaflet has been
How To Teach English At Kumon
 English Education at Kumon 1 Running Head: ENGLISH EDUCATION AT KUMON English Education at KUMON ~ A Case Study of Two Children and their Mothers ~ by Yukiko Kawabata A graduation thesis submitted to the
English Education at Kumon 1 Running Head: ENGLISH EDUCATION AT KUMON English Education at KUMON ~ A Case Study of Two Children and their Mothers ~ by Yukiko Kawabata A graduation thesis submitted to the
Caldwell Community College and Technical Institute
 Caldwell Community College and Technical Institute Student Computer Usage Policies and Procedures I. Campus Computer Usage Overview: The purpose of this document is to define the policies and procedures
Caldwell Community College and Technical Institute Student Computer Usage Policies and Procedures I. Campus Computer Usage Overview: The purpose of this document is to define the policies and procedures
Result of the Attitude Survey on Information Security
 Presentation Result of the Attitude Survey on Information Security Conducted toward the companies Operating in Thailand February, 2009 Center of the International Cooperation for Computerization of Japan
Presentation Result of the Attitude Survey on Information Security Conducted toward the companies Operating in Thailand February, 2009 Center of the International Cooperation for Computerization of Japan
Ibaraki University. Graduate School of Agriculture. (Master s Program)
 Ibaraki University 茨 城 大 学 Graduate School of Agriculture 大 学 院 農 学 研 究 科 (Master s Program) 修 士 課 程 Application Guidelines for Academic Year 2015 平 成 27 年 度 学 生 募 集 要 項 (October Admissions) 10 月 入 学 Special
Ibaraki University 茨 城 大 学 Graduate School of Agriculture 大 学 院 農 学 研 究 科 (Master s Program) 修 士 課 程 Application Guidelines for Academic Year 2015 平 成 27 年 度 学 生 募 集 要 項 (October Admissions) 10 月 入 学 Special
MPLS Configration 事 例
 MPLS Configration 事 例 JANOG6 MPLSパネル グローバルワン 株 式 会 社 06/16/2000 JANOG6 MPLS Pannel 1 MPLS Configration なにが 必 要?(Ciscoしかわかりません) IOSは12.0(7) T 以 上 がいい PEは3600, 4500, 7200, and 7500 PはCisco LS1010, 7200,
MPLS Configration 事 例 JANOG6 MPLSパネル グローバルワン 株 式 会 社 06/16/2000 JANOG6 MPLS Pannel 1 MPLS Configration なにが 必 要?(Ciscoしかわかりません) IOSは12.0(7) T 以 上 がいい PEは3600, 4500, 7200, and 7500 PはCisco LS1010, 7200,
Studying Security Weaknesses of Android System
 , pp. 7-12 http://dx.doi.org/10.14257/ijsia.2015.9.3.02 Studying Security Weaknesses of Android System Jae-Kyung Park* and Sang-Yong Choi** *Chief researcher at Cyber Security Research Center, Korea Advanced
, pp. 7-12 http://dx.doi.org/10.14257/ijsia.2015.9.3.02 Studying Security Weaknesses of Android System Jae-Kyung Park* and Sang-Yong Choi** *Chief researcher at Cyber Security Research Center, Korea Advanced
原 子 力 規 制 委 員 会 のマネジメントシステム 体 系
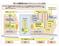 原 子 力 規 制 委 員 会 のマネジメントシステム 体 系 目 的 : 原 子 力 規 制 委 員 会 設 置 法 の 任 務 を 達 成 するため 原 子 力 規 制 委 員 会 の 業 務 の 品 質 を 維 持 向 上 すると もに 効 果 的 なリー ダーシップに 支 えられた 安 全 文 化 の 醸 成 をもたらす 統 合 マネジメントシステムを 構 築 し 実 施 することを 目 的
原 子 力 規 制 委 員 会 のマネジメントシステム 体 系 目 的 : 原 子 力 規 制 委 員 会 設 置 法 の 任 務 を 達 成 するため 原 子 力 規 制 委 員 会 の 業 務 の 品 質 を 維 持 向 上 すると もに 効 果 的 なリー ダーシップに 支 えられた 安 全 文 化 の 醸 成 をもたらす 統 合 マネジメントシステムを 構 築 し 実 施 することを 目 的
McAfee Firewall Enterprise
 Quick Start Guide Revision C McAfee Firewall Enterprise version 8.3.x This quick start guide provides high-level instructions for setting up McAfee Firewall Enterprise. 要 查 看 此 文 档 的 简 体 中 文 版 本, 请 访 问
Quick Start Guide Revision C McAfee Firewall Enterprise version 8.3.x This quick start guide provides high-level instructions for setting up McAfee Firewall Enterprise. 要 查 看 此 文 档 的 简 体 中 文 版 本, 请 访 问
FORBIDDEN - Ethical Hacking Workshop Duration
 Workshop Course Module FORBIDDEN - Ethical Hacking Workshop Duration Lecture and Demonstration : 15 Hours Security Challenge : 01 Hours Introduction Security can't be guaranteed. As Clint Eastwood once
Workshop Course Module FORBIDDEN - Ethical Hacking Workshop Duration Lecture and Demonstration : 15 Hours Security Challenge : 01 Hours Introduction Security can't be guaranteed. As Clint Eastwood once
A Content- Specific Task-Based Language Program for Online Business English Instruction
 A Content- Specific Task-Based Language Program for Online Business English Instruction M. Michael Hadas BBT Online University Reference Data: Hadas, M. M., (2014). A content-specific task-based language
A Content- Specific Task-Based Language Program for Online Business English Instruction M. Michael Hadas BBT Online University Reference Data: Hadas, M. M., (2014). A content-specific task-based language
End-user Security Analytics Strengthens Protection with ArcSight
 Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
Case Study for XY Bank End-user Security Analytics Strengthens Protection with ArcSight INTRODUCTION Detect and respond to advanced persistent threats (APT) in real-time with Nexthink End-user Security
The Ministry of Information & Communication Technology MICT
 The Ministry of Information & Communication Technology MICT Document Reference: ISGSN2012-10-01-Ver 1.0 Published Date: March 2014 1 P a g e Table of Contents Table of Contents... 2 Definitions... 3 1.
The Ministry of Information & Communication Technology MICT Document Reference: ISGSN2012-10-01-Ver 1.0 Published Date: March 2014 1 P a g e Table of Contents Table of Contents... 2 Definitions... 3 1.
