NEEDLE STACKS & BIG DATA: USING EVENT STREAM PROCESSING FOR RISK, SURVEILLANCE & SECURITY ANALYTICS IN CAPITAL MARKETS
|
|
|
- Estella Dixon
- 10 years ago
- Views:
Transcription
1 NEEDLE STACKS & BIG DATA: USING PROCESSING FOR RISK, SURVEILLANCE & SECURITY ANALYTICS IN CAPITAL MARKETS JERRY BAULIER, DIRECTOR, PROCESSING DAVID M. WALLACE, GLOBAL FINANCIAL SERVICES MARKETING MANAGER
2 NEEDLE STACKS & BIG DATA AGENDA Big Data and the Three V s Event Stream Processing: Continuous Data Analysis Surveillance for Risk Reduction Roque trader surveillance Market portfolio risk Cyber security Wrap-up
3 NEEDLE STACKS BIG DATA: FINANCIAL SERVICES AT THE TOP Source: Dr. Robert Rubin, Wall Street & Technology, 2011: CEB TowerGroup, 2013
4 NEEDLE STACKS BIG DATA: GROWTH IN VOLUME AND VARIETY Source: CEB TowerGroup, Gain New Insight from Unstructured Data, 2013.
5 NEEDLE STACKS BIG DATA: GROWTH IN VOLUME AND VELOCITY Source: Options Price Reporting Authority, Data Recipient Notices
6 NEEDLE STACKS WHAT WE ASSUME WE WANT FROM BIG DATA ANALYTICS Find the needles in the haystacks
7 NEEDLE STACKS WHAT WE ACTUALLY NEED FROM BIG DATA ANALYTICS I need to collect the needles while the data is in motion
8 NEEDLE STACKS WHAT WE WANT TO FIND IN THE NEEDLE STACK Find me the golden needle right now!
9 NEEDLE STACKS WHAT DO YOU CALL IT? Real-Time Analytics Complex Event Processing Contextual Awareness Event Stream Processing Operational Intelligence CEP ESP Event Driven Architecture Data Stream Mining Continuous Intelligence Situational Awareness Real-Time Visualization Asynchronous Processing
10 COMPLEX PROCESSING CEP usually refers to event processing that assumes an event cloud as input, and therefore can make no assumptions about the arrival order of events. * Its been around for a long time (mostly in form of proprietary solutions) It s only the name and availability of commercial frameworks that s relatively new. What is complex the events or the processing? Two architectures: Rules-based, Continuous Query-based * This is the definition provided by the Event Processing Technical Society
11 PROCESSING (ESP) ESP is a subcategory of Complex Event Processing (CEP) focused on analyzing/processing events in motion called Event Streams.* * This is the definition provided by the Event Processing Technical Society
12 TYPICAL CHARACTERISTICS OF PROCESSING APPLICATIONS Continuous queries on data in motion (with incrementally updated results) Very low (max) event processing latencies (i.e., secsmsecs) High volumes (>100k events/sec) Derived event windows with retention policies Continuously reduce event streams into actionable intelligence for alerts Predetermined data mining, decision making, alerting, position management, scoring, profiling, Event out-of-order handling to ensure ordered source streams
13 PROCESSING ENGINE: -DRIVEN, FLOW-CENTRIC SOURCES/PUBLISHERS Venues & Instruments Databases Applications Applications PROCESSING ENGINE Publish / subscribe Inserts/updates/deletes Continuous queries Aggregate (group by) Correlate (join) Compute Filter Procedural User defined functions Retention windows Pattern matching Ad-hoc queries Command & control Security (Auth, Encrypt, AC) Persistence / recovery Fail-over Distributed services Model management SOURCES/PUBLISHERS MOBILE BI / BAM ALERTS WORKFLOWS
14 PROCESSING CONTINUOUS QUERIES DATA FLOW DIAGRAM SOURCES/PUBLISHERS PROCESSING ENGINE SOURCES/PUBLISHERS SOURCE WINDOW FILTER DERIVED WINDOW Venues & Instruments SOURCE WINDOW JOIN DERIVED WINDOW Databases Applications Applications SOURCE WINDOW PATTERN MATCH DERIVED WINDOW MOBILE BI / BAM ALERTS WORKFLOWS
15 HYBRID DATA ANALYTICS Data Sources Real-Time Analytics Event Stream Processing Advanced Predictive Analytics In-Memory Analytics Server Visualization, Alerts, Decision Management Visualization Risk Data Market Data Reference Data Trades Pattern Matching Correlation Aggregation Thresholding Profiling Risk Analytics Fraud Analytics Behavioral Analytics Decision Management Alert Management Persistence Store (Hadoop) Macro Orchestration (Event Stream Processing)
16 USE CASES
17 NEEDLE STACKS PROCESSING: RISK SURVEILLANCE METHODS Position monitoring Thresholding Profiling individual signatures, group signatures, fraud signatures, Pattern matching Event A followed by (time) Event B followed by (time) not Event C Neural networks Cognitive learning
18 TRADING SURVEILLANCE / FRAUD MANAGEMENT PROCESS FLOW Operational Data Sources Continuous Surveillance with Event Stream Processing Directed Alerts to ESP Fraud Data Staging Advanced Predictive Analytics and Alert Generation Process Business Rules Alert Administration Fraud Network Analysis Network Rules Transactions Analytics Anomaly Detection Network Analytics Entities Predictive Modeling Internal Data Directed Alerts from ESP Alert Management & Reporting Market Feeds X X X Intelligent Fraud Repository Learn and Improve Cycle Case Management Compliance Investigators Business Rules Update Process
19 ROGUE TRADER SURVEILLANCE USE CASE POST-TRADE ORDER PRACTICE & COMPLIANCE ALERTING Event Stream Sources/Publishers Trades Market Feeds Brokers Restricted Securities Venue Trade Windows Trades Brokers of Interest Restricted Securities Venues Trades Event Stream Processing Server Trades of Large Size (filter) Trades of Interest (join) Frontrunning Patterns (procedural) Restricted Sales (join) Marking Open/Close Patterns (procedural) Broker Alerts (aggregate) Broker Alerts: Broker aggregates for each alert type and total. Front running: broker buys securities for his own account before buying the same securities for his customer, then sells when the price rises; or broker sells securities out of his personal accounts prior to selling the same securities for his clients. Restricted Sale: sales of securities that have ownership restrictions. Front- Running Alert Restricted Sale Alert Open/Close Mark Alert Broker Alerts Case Management GUI Marking the Close: attempting to influence the closing price of a security by executing purchases at the close of normal trading hours. Marking the Open: attempting to influence the opening price of a security by making trades at the opening of normal trading hours.
20 RISK DATA AGGREGATION USE CASE TRADING SYSTEMS CALCULATION ENGINES ENTERPRISE DATA ANALYTICS & VISUALIZATION Front Office Data Fabric MARKET DATA Sources DQ & Value Add Market Data Fabric REFERENCE DATA Risk Engine Pricing Lib Risk Engine Pricing Lib Risk Engine Pricing Lib Risk Engine Pricing Lib Enterprise Service Bus PROCESSING Continuous Data Integration P & L Workflow Limits Persistence Store In-Memory Risk & Analytics Engine Aggregation, Analytics, Exploration Persistence & History Store (Hadoop) Reporting Layers Senior Management Head of Risk Risk Managers Visualization Exploration
21 CYBER SURVEILLANCE USING HYBRID ANALYTICS Data Sources Real-Time Analytics Event Stream Processing Advanced Predictive Analytics In-Memory Analytics Server Visualization, Alerts, Decision Mgt. Visualization Syslogs SIEM (Security Info & Event Mgmt) Reference Data Network Monitors Pattern matching Trending Individual signatures Known threat signatures Consolidated views Causality Predictive analytics Decision trees Neural networks Gradient boosting Case management Alert management Rule effectivity Prevention Causality Persistence Store (Hadoop) Case Management GRC Macro Orchestration (Event Stream Processing)
22 NEEDLE STACKS ADVANTAGES OF PROCESSING Much lower latencies for action, hence new opportunities Big data analytics ability to deal with the growing huge data volumes & reduce to knowledge Move back-end analytics to continuous analytics with a working resultant set Reduced storage requirements Reduced computational requirements Focused on action and new patterns of interest Hybrid analytics = closed loop analytics ESP front-ends advanced predictive analytics Knowledge based analytics can be applied to many problems
23 NEEDLE STACKS FINDING THE RIGHT NEEDLE IN THE STACK Continuous Event Stream Processing + Advanced Predictive Analytics Delivers the Gold!
24 THANK YOU! QUESTIONS? CONTACT:
25 ROBUST ARCHITECTURE REQUIRES ENTERPRISE ARCHITECTURE APPROACH DATA SOURCES ENTERPRISE ANALYTICAL FRAMEWORK DATA SERVICES EDW ADW FOUNDATIONAL ENTERPRISE & ANALYTICAL DATA WAREHOUSE BUILT FOR PURPOSE ANALYTICAL DATA STORES ANALYTICS SERVICES ANALYTICAL INSIGHTS OPERATIONAL DECISIONS
26 MARKET RISK MANAGEMENT USE CASE Data Sources Real-Time Risk Analysis Analytics Data Visualization Data Integration In-Memory Analytics Server Visualization Risk Data Market Data Reference Data Event Stream Processing In-Memory Risk Analytics Other Reporting Trades Positions & Limits Monitoring Valuation Aggregation Stress Testing Macro Orchestration (Event Stream Processing)
Big Data and Advanced Analytics Technologies for the Smart Grid
 1 Big Data and Advanced Analytics Technologies for the Smart Grid Arnie de Castro, PhD SAS Institute IEEE PES 2014 General Meeting July 27-31, 2014 Panel Session: Using Smart Grid Data to Improve Planning,
1 Big Data and Advanced Analytics Technologies for the Smart Grid Arnie de Castro, PhD SAS Institute IEEE PES 2014 General Meeting July 27-31, 2014 Panel Session: Using Smart Grid Data to Improve Planning,
White Paper. How Streaming Data Analytics Enables Real-Time Decisions
 White Paper How Streaming Data Analytics Enables Real-Time Decisions Contents Introduction... 1 What Is Streaming Analytics?... 1 How Does SAS Event Stream Processing Work?... 2 Overview...2 Event Stream
White Paper How Streaming Data Analytics Enables Real-Time Decisions Contents Introduction... 1 What Is Streaming Analytics?... 1 How Does SAS Event Stream Processing Work?... 2 Overview...2 Event Stream
Getting Real Real Time Data Integration Patterns and Architectures
 Getting Real Real Time Data Integration Patterns and Architectures Nelson Petracek Senior Director, Enterprise Technology Architecture Informatica Digital Government Institute s Enterprise Architecture
Getting Real Real Time Data Integration Patterns and Architectures Nelson Petracek Senior Director, Enterprise Technology Architecture Informatica Digital Government Institute s Enterprise Architecture
A New Era Of Analytic
 Penang egovernment Seminar 2014 A New Era Of Analytic Megat Anuar Idris Head, Project Delivery, Business Analytics & Big Data Agenda Overview of Big Data Case Studies on Big Data Big Data Technology Readiness
Penang egovernment Seminar 2014 A New Era Of Analytic Megat Anuar Idris Head, Project Delivery, Business Analytics & Big Data Agenda Overview of Big Data Case Studies on Big Data Big Data Technology Readiness
WHITE PAPER. Enabling predictive analysis in service oriented BPM solutions.
 WHITE PAPER Enabling predictive analysis in service oriented BPM solutions. Summary Complex Event Processing (CEP) is a real time event analysis, correlation and processing mechanism that fits in seamlessly
WHITE PAPER Enabling predictive analysis in service oriented BPM solutions. Summary Complex Event Processing (CEP) is a real time event analysis, correlation and processing mechanism that fits in seamlessly
Operational Intelligence: Real-Time Business Analytics for Big Data Philip Russom
 Operational Intelligence: Real-Time Business Analytics for Big Data Philip Russom TDWI Research Director for Data Management August 14, 2012 Sponsor Speakers Philip Russom Research Director, Data Management,
Operational Intelligence: Real-Time Business Analytics for Big Data Philip Russom TDWI Research Director for Data Management August 14, 2012 Sponsor Speakers Philip Russom Research Director, Data Management,
Big data platform for IoT Cloud Analytics. Chen Admati, Advanced Analytics, Intel
 Big data platform for IoT Cloud Analytics Chen Admati, Advanced Analytics, Intel Agenda IoT @ Intel End-to-End offering Analytics vision Big data platform for IoT Cloud Analytics Platform Capabilities
Big data platform for IoT Cloud Analytics Chen Admati, Advanced Analytics, Intel Agenda IoT @ Intel End-to-End offering Analytics vision Big data platform for IoT Cloud Analytics Platform Capabilities
Software AG Product Strategy Vision & Strategie Das Digitale Unternehmen
 Software AG Product Strategy Vision & Strategie Das Digitale Unternehmen Dr. Wolfram Jost CTO Agenda 1 2 3 Positioning Product Portfolio Key Innovation Areas What does digitization mean? more than automation,
Software AG Product Strategy Vision & Strategie Das Digitale Unternehmen Dr. Wolfram Jost CTO Agenda 1 2 3 Positioning Product Portfolio Key Innovation Areas What does digitization mean? more than automation,
Traditional BI vs. Business Data Lake A comparison
 Traditional BI vs. Business Data Lake A comparison The need for new thinking around data storage and analysis Traditional Business Intelligence (BI) systems provide various levels and kinds of analyses
Traditional BI vs. Business Data Lake A comparison The need for new thinking around data storage and analysis Traditional Business Intelligence (BI) systems provide various levels and kinds of analyses
Embracing the Cloud, Mobile, Social & Big Data
 Embracing the Cloud, Mobile, Social & Big Data Introducing ARIS 9.0 and webmethods 9.0 Dr. Wolfram Jost CTO Software AG 2010-2013 2 Positioning 3 2013 Software 2013 AG. Software All rights AG. reserved.
Embracing the Cloud, Mobile, Social & Big Data Introducing ARIS 9.0 and webmethods 9.0 Dr. Wolfram Jost CTO Software AG 2010-2013 2 Positioning 3 2013 Software 2013 AG. Software All rights AG. reserved.
Complex Event Processing (CEP) Why and How. Richard Hallgren BUGS 2013-05-30
 Complex Event Processing (CEP) Why and How Richard Hallgren BUGS 2013-05-30 Objectives Understand why and how CEP is important for modern business processes Concepts within a CEP solution Overview of StreamInsight
Complex Event Processing (CEP) Why and How Richard Hallgren BUGS 2013-05-30 Objectives Understand why and how CEP is important for modern business processes Concepts within a CEP solution Overview of StreamInsight
MASTER DATA MANAGEMENT IN THE AGE OF BIG DATA
 MASTER DATA MANAGEMENT IN THE AGE OF BIG DATA PRESENTED TO IRMAC MAY 15, 2013 STEVE PAPAGIANNIS [email protected] 416 307 4620 DEFINITIONS WHAT ARE MASTER AND BIG DATA??? Master data is information
MASTER DATA MANAGEMENT IN THE AGE OF BIG DATA PRESENTED TO IRMAC MAY 15, 2013 STEVE PAPAGIANNIS [email protected] 416 307 4620 DEFINITIONS WHAT ARE MASTER AND BIG DATA??? Master data is information
How To Make Data Streaming A Real Time Intelligence
 REAL-TIME OPERATIONAL INTELLIGENCE Competitive advantage from unstructured, high-velocity log and machine Big Data 2 SQLstream: Our s-streaming products unlock the value of high-velocity unstructured log
REAL-TIME OPERATIONAL INTELLIGENCE Competitive advantage from unstructured, high-velocity log and machine Big Data 2 SQLstream: Our s-streaming products unlock the value of high-velocity unstructured log
Find the Hidden Signal in Market Data Noise
 Find the Hidden Signal in Market Data Noise Revolution Analytics Webinar, 13 March 2013 Andrie de Vries Business Services Director (Europe) @RevoAndrie [email protected] Agenda Find the Hidden
Find the Hidden Signal in Market Data Noise Revolution Analytics Webinar, 13 March 2013 Andrie de Vries Business Services Director (Europe) @RevoAndrie [email protected] Agenda Find the Hidden
Embedded inside the database. No need for Hadoop or customcode. True real-time analytics done per transaction and in aggregate. On-the-fly linking IP
 Operates more like a search engine than a database Scoring and ranking IP allows for fuzzy searching Best-result candidate sets returned Contextual analytics to correctly disambiguate entities Embedded
Operates more like a search engine than a database Scoring and ranking IP allows for fuzzy searching Best-result candidate sets returned Contextual analytics to correctly disambiguate entities Embedded
Metrics that Matter Security Risk Analytics
 Metrics that Matter Security Risk Analytics Rich Skinner, CISSP Director Security Risk Analytics & Big Data Brinqa [email protected] April 1 st, 2014. Agenda Challenges in Enterprise Security, Risk
Metrics that Matter Security Risk Analytics Rich Skinner, CISSP Director Security Risk Analytics & Big Data Brinqa [email protected] April 1 st, 2014. Agenda Challenges in Enterprise Security, Risk
Simplifying Big Data Analytics: Unifying Batch and Stream Processing. John Fanelli,! VP Product! In-Memory Compute Summit! June 30, 2015!!
 Simplifying Big Data Analytics: Unifying Batch and Stream Processing John Fanelli,! VP Product! In-Memory Compute Summit! June 30, 2015!! Streaming Analy.cs S S S Scale- up Database Data And Compute Grid
Simplifying Big Data Analytics: Unifying Batch and Stream Processing John Fanelli,! VP Product! In-Memory Compute Summit! June 30, 2015!! Streaming Analy.cs S S S Scale- up Database Data And Compute Grid
SAS Fraud Framework for Banking
 SAS Fraud Framework for Banking Including Social Network Analysis John C. Brocklebank, Ph.D. Vice President, SAS Solutions OnDemand Advanced Analytics Lab SAS Fraud Framework for Banking Agenda Introduction
SAS Fraud Framework for Banking Including Social Network Analysis John C. Brocklebank, Ph.D. Vice President, SAS Solutions OnDemand Advanced Analytics Lab SAS Fraud Framework for Banking Agenda Introduction
YOU VS THE SENSORS. Six Requirements for Visualizing the Internet of Things. Dan Potter Chief Marketing Officer, Datawatch Corporation
 YOU VS THE SENSORS Six Requirements for Visualizing the Internet of Things Dan Potter Chief Marketing Officer, Datawatch Corporation About Datawatch NASDAQ: DWCH Pioneer in real-time visual data discovery
YOU VS THE SENSORS Six Requirements for Visualizing the Internet of Things Dan Potter Chief Marketing Officer, Datawatch Corporation About Datawatch NASDAQ: DWCH Pioneer in real-time visual data discovery
What s New in Security Analytics 10.4. Be the Hunter.. Not the Hunted
 What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
What s New in Security Analytics 10.4 Be the Hunter.. Not the Hunted Attackers Are Outpacing Detection Attacker Capabilities Time To Discovery Source: VERIZON 2014 DATA BREACH INVESTIGATIONS REPORT 2 TRANSFORM
Big Data Volume, Velocity, Variability
 Big Fast Data Anwendungen und Lösungen der Software AG Big Data Volume, Velocity, Variability Dr. Jürgen Krämer VP Product Strategy IBO & Product Management Apama 20.02.2014 the time window to analyze
Big Fast Data Anwendungen und Lösungen der Software AG Big Data Volume, Velocity, Variability Dr. Jürgen Krämer VP Product Strategy IBO & Product Management Apama 20.02.2014 the time window to analyze
Data Warehousing and Data Mining in Business Applications
 133 Data Warehousing and Data Mining in Business Applications Eesha Goel CSE Deptt. GZS-PTU Campus, Bathinda. Abstract Information technology is now required in all aspect of our lives that helps in business
133 Data Warehousing and Data Mining in Business Applications Eesha Goel CSE Deptt. GZS-PTU Campus, Bathinda. Abstract Information technology is now required in all aspect of our lives that helps in business
SAP Predictive Analysis: Strategy, Value Proposition
 September 10-13, 2012 Orlando, Florida SAP Predictive Analysis: Strategy, Value Proposition Thomas B Kuruvilla, Solution Management, SAP Business Intelligence Scott Leaver, Solution Management, SAP Business
September 10-13, 2012 Orlando, Florida SAP Predictive Analysis: Strategy, Value Proposition Thomas B Kuruvilla, Solution Management, SAP Business Intelligence Scott Leaver, Solution Management, SAP Business
locuz.com Big Data Services
 locuz.com Big Data Services Big Data At Locuz, we help the enterprise move from being a data-limited to a data-driven one, thereby enabling smarter, faster decisions that result in better business outcome.
locuz.com Big Data Services Big Data At Locuz, we help the enterprise move from being a data-limited to a data-driven one, thereby enabling smarter, faster decisions that result in better business outcome.
Big Data Use Case Deep Dive 5 Game Changing Use Cases for Big Data
 Big Data Use Case Deep Dive 5 Game Changing Use Cases for Big Data Disruptive forces impact long standing business models across industries Pressure to do more with less Shift of power to the consumer
Big Data Use Case Deep Dive 5 Game Changing Use Cases for Big Data Disruptive forces impact long standing business models across industries Pressure to do more with less Shift of power to the consumer
Managing Data in Motion
 Managing Data in Motion Data Integration Best Practice Techniques and Technologies April Reeve ELSEVIER AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY
Managing Data in Motion Data Integration Best Practice Techniques and Technologies April Reeve ELSEVIER AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY
The Synergy of SOA, Event-Driven Architecture (EDA), and Complex Event Processing (CEP)
 The Synergy of SOA, Event-Driven Architecture (EDA), and Complex Event Processing (CEP) Gerhard Bayer Senior Consultant International Systems Group, Inc. [email protected] http://www.isg-inc.com Table
The Synergy of SOA, Event-Driven Architecture (EDA), and Complex Event Processing (CEP) Gerhard Bayer Senior Consultant International Systems Group, Inc. [email protected] http://www.isg-inc.com Table
SAP SE - Legal Requirements and Requirements
 Finding the signals in the noise Niklas Packendorff @packendorff Solution Expert Analytics & Data Platform Legal disclaimer The information in this presentation is confidential and proprietary to SAP and
Finding the signals in the noise Niklas Packendorff @packendorff Solution Expert Analytics & Data Platform Legal disclaimer The information in this presentation is confidential and proprietary to SAP and
IBM Big Data in Government
 IBM Big in Government Turning big data into smarter decisions Deepak Mohapatra Sr. Consultant Government IBM Software Group [email protected] The Big Paradigm Shift 2 Big Creates A Challenge And an
IBM Big in Government Turning big data into smarter decisions Deepak Mohapatra Sr. Consultant Government IBM Software Group [email protected] The Big Paradigm Shift 2 Big Creates A Challenge And an
High-Performance Analytics
 High-Performance Analytics David Pope January 2012 Principal Solutions Architect High Performance Analytics Practice Saturday, April 21, 2012 Agenda Who Is SAS / SAS Technology Evolution Current Trends
High-Performance Analytics David Pope January 2012 Principal Solutions Architect High Performance Analytics Practice Saturday, April 21, 2012 Agenda Who Is SAS / SAS Technology Evolution Current Trends
Big Data & Analytics for Semiconductor Manufacturing
 Big Data & Analytics for Semiconductor Manufacturing 半 導 体 生 産 におけるビッグデータ 活 用 Ryuichiro Hattori 服 部 隆 一 郎 Intelligent SCM and MFG solution Leader Global CoC (Center of Competence) Electronics team General
Big Data & Analytics for Semiconductor Manufacturing 半 導 体 生 産 におけるビッグデータ 活 用 Ryuichiro Hattori 服 部 隆 一 郎 Intelligent SCM and MFG solution Leader Global CoC (Center of Competence) Electronics team General
Big Data in the Nordics 2012
 Big Data in the Nordics 2012 A survey about increasing data volumes and Big Data analysis among private and governmental organizations in Sweden, Norway, Denmark and Finland. Unexplored Big Data Potential
Big Data in the Nordics 2012 A survey about increasing data volumes and Big Data analysis among private and governmental organizations in Sweden, Norway, Denmark and Finland. Unexplored Big Data Potential
Aligning Your Strategic Initiatives with a Realistic Big Data Analytics Roadmap
 Aligning Your Strategic Initiatives with a Realistic Big Data Analytics Roadmap 3 key strategic advantages, and a realistic roadmap for what you really need, and when 2012, Cognizant Topics to be discussed
Aligning Your Strategic Initiatives with a Realistic Big Data Analytics Roadmap 3 key strategic advantages, and a realistic roadmap for what you really need, and when 2012, Cognizant Topics to be discussed
Practical Considerations for Real-Time Business Intelligence. Donovan Schneider Yahoo! September 11, 2006
 Practical Considerations for Real-Time Business Intelligence Donovan Schneider Yahoo! September 11, 2006 Outline Business Intelligence (BI) Background Real-Time Business Intelligence Examples Two Requirements
Practical Considerations for Real-Time Business Intelligence Donovan Schneider Yahoo! September 11, 2006 Outline Business Intelligence (BI) Background Real-Time Business Intelligence Examples Two Requirements
FINANCIAL SERVICES: FRAUD MANAGEMENT A solution showcase
 FINANCIAL SERVICES: FRAUD MANAGEMENT A solution showcase TECHNOLOGY OVERVIEW FRAUD MANAGE- MENT REFERENCE ARCHITECTURE This technology overview describes a complete infrastructure and application re-architecture
FINANCIAL SERVICES: FRAUD MANAGEMENT A solution showcase TECHNOLOGY OVERVIEW FRAUD MANAGE- MENT REFERENCE ARCHITECTURE This technology overview describes a complete infrastructure and application re-architecture
Hunting for the Undefined Threat: Advanced Analytics & Visualization
 SESSION ID: ANF-W04 Hunting for the Undefined Threat: Advanced Analytics & Visualization Joshua Stevens Enterprise Security Architect Hewlett-Packard Cyber Security Technology Office Defining the Hunt
SESSION ID: ANF-W04 Hunting for the Undefined Threat: Advanced Analytics & Visualization Joshua Stevens Enterprise Security Architect Hewlett-Packard Cyber Security Technology Office Defining the Hunt
Big Data overview. Livio Ventura. SICS Software week, Sept 23-25 Cloud and Big Data Day
 Big Data overview SICS Software week, Sept 23-25 Cloud and Big Data Day Livio Ventura Big Data European Industry Leader for Telco, Energy and Utilities and Digital Media Agenda some data on Data Big Data
Big Data overview SICS Software week, Sept 23-25 Cloud and Big Data Day Livio Ventura Big Data European Industry Leader for Telco, Energy and Utilities and Digital Media Agenda some data on Data Big Data
The Purview Solution Integration With Splunk
 The Purview Solution Integration With Splunk Integrating Application Management and Business Analytics With Other IT Management Systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview Integration
The Purview Solution Integration With Splunk Integrating Application Management and Business Analytics With Other IT Management Systems A SOLUTION WHITE PAPER WHITE PAPER Introduction Purview Integration
Towards Smart and Intelligent SDN Controller
 Towards Smart and Intelligent SDN Controller - Through the Generic, Extensible, and Elastic Time Series Data Repository (TSDR) YuLing Chen, Dell Inc. Rajesh Narayanan, Dell Inc. Sharon Aicler, Cisco Systems
Towards Smart and Intelligent SDN Controller - Through the Generic, Extensible, and Elastic Time Series Data Repository (TSDR) YuLing Chen, Dell Inc. Rajesh Narayanan, Dell Inc. Sharon Aicler, Cisco Systems
Cloud Integration and the Big Data Journey - Common Use-Case Patterns
 Cloud Integration and the Big Data Journey - Common Use-Case Patterns A White Paper August, 2014 Corporate Technologies Business Intelligence Group OVERVIEW The advent of cloud and hybrid architectures
Cloud Integration and the Big Data Journey - Common Use-Case Patterns A White Paper August, 2014 Corporate Technologies Business Intelligence Group OVERVIEW The advent of cloud and hybrid architectures
Three steps to put Predictive Analytics to Work
 Three steps to put Predictive Analytics to Work The most powerful examples of analytic success use Decision Management to deploy analytic insight in day to day operations helping organizations make more
Three steps to put Predictive Analytics to Work The most powerful examples of analytic success use Decision Management to deploy analytic insight in day to day operations helping organizations make more
Intelligent Business Operations
 Intelligent Business Operations Echtzeit-Datenanalyse und Aktionen im Zusammenspiel Dr. Jürgen Krämer VP Product Strategy IBO & Product Management Apama 23.06.2014 Helping Organizations Transform into
Intelligent Business Operations Echtzeit-Datenanalyse und Aktionen im Zusammenspiel Dr. Jürgen Krämer VP Product Strategy IBO & Product Management Apama 23.06.2014 Helping Organizations Transform into
Big Data and Analytics in Government
 Big Data and Analytics in Government Nov 29, 2012 Mark Johnson Director, Engineered Systems Program 2 Agenda What Big Data Is Government Big Data Use Cases Building a Complete Information Solution Conclusion
Big Data and Analytics in Government Nov 29, 2012 Mark Johnson Director, Engineered Systems Program 2 Agenda What Big Data Is Government Big Data Use Cases Building a Complete Information Solution Conclusion
Intelligent Business Operations and Big Data. 2014 Software AG. All rights reserved.
 Intelligent Business Operations and Big Data 1 What is Big Data? Big data is a popular term used to acknowledge the exponential growth, availability and use of information in the data-rich landscape of
Intelligent Business Operations and Big Data 1 What is Big Data? Big data is a popular term used to acknowledge the exponential growth, availability and use of information in the data-rich landscape of
IRMAC SAS INFORMATION MANAGEMENT, TRANSFORMING AN ANALYTICS CULTURE. Copyright 2012, SAS Institute Inc. All rights reserved.
 IRMAC SAS INFORMATION MANAGEMENT, TRANSFORMING AN ANALYTICS CULTURE ABOUT THE PRESENTER Marc has been with SAS for 10 years and leads the information management practice for canada. Marc s area of specialty
IRMAC SAS INFORMATION MANAGEMENT, TRANSFORMING AN ANALYTICS CULTURE ABOUT THE PRESENTER Marc has been with SAS for 10 years and leads the information management practice for canada. Marc s area of specialty
Klarna Tech Talk: Mind the Data! Jeff Pollock InfoSphere Information Integration & Governance
 Klarna Tech Talk: Mind the Data! Jeff Pollock InfoSphere Information Integration & Governance IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice
Klarna Tech Talk: Mind the Data! Jeff Pollock InfoSphere Information Integration & Governance IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice
What is Security Intelligence?
 2 What is Security Intelligence? Security Intelligence --noun 1. the real-time collection, normalization, and analytics of the data generated by users, applications and infrastructure that impacts the
2 What is Security Intelligence? Security Intelligence --noun 1. the real-time collection, normalization, and analytics of the data generated by users, applications and infrastructure that impacts the
Detecting Anomalous Behavior with the Business Data Lake. Reference Architecture and Enterprise Approaches.
 Detecting Anomalous Behavior with the Business Data Lake Reference Architecture and Enterprise Approaches. 2 Detecting Anomalous Behavior with the Business Data Lake Pivotal the way we see it Reference
Detecting Anomalous Behavior with the Business Data Lake Reference Architecture and Enterprise Approaches. 2 Detecting Anomalous Behavior with the Business Data Lake Pivotal the way we see it Reference
IBM Security. 2013 IBM Corporation. 2013 IBM Corporation
 IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
IBM Security Security Intelligence What is Security Intelligence? Security Intelligence --noun 1.the real-time collection, normalization and analytics of the data generated by users, applications and infrastructure
Streaming Analytics A Framework for Innovation
 Streaming Analytics A Framework for Innovation Jan Humble Solutions Architect 1 Volume and Scale of Sensing Data Can you TURN IT ON? Can you Identify Insights in REAL-TIME? Can you REACT and ENGAGE in
Streaming Analytics A Framework for Innovation Jan Humble Solutions Architect 1 Volume and Scale of Sensing Data Can you TURN IT ON? Can you Identify Insights in REAL-TIME? Can you REACT and ENGAGE in
IBM: An Early Leader across the Big Data Security Analytics Continuum Date: June 2013 Author: Jon Oltsik, Senior Principal Analyst
 ESG Brief IBM: An Early Leader across the Big Data Security Analytics Continuum Date: June 2013 Author: Jon Oltsik, Senior Principal Analyst Abstract: Many enterprise organizations claim that they already
ESG Brief IBM: An Early Leader across the Big Data Security Analytics Continuum Date: June 2013 Author: Jon Oltsik, Senior Principal Analyst Abstract: Many enterprise organizations claim that they already
SIEM 2.0: AN IANS INTERACTIVE PHONE CONFERENCE INTEGRATING FIVE KEY REQUIREMENTS MISSING IN 1ST GEN SOLUTIONS SUMMARY OF FINDINGS
 SIEM 2.0: INTEGRATING FIVE KEY REQUIREMENTS MISSING IN 1ST GEN SOLUTIONS AN IANS INTERACTIVE PHONE CONFERENCE SUMMARY OF FINDINGS OCTOBER 2009 Chris Peterson, LogRhythm CTO, Founder Chris brings a unique
SIEM 2.0: INTEGRATING FIVE KEY REQUIREMENTS MISSING IN 1ST GEN SOLUTIONS AN IANS INTERACTIVE PHONE CONFERENCE SUMMARY OF FINDINGS OCTOBER 2009 Chris Peterson, LogRhythm CTO, Founder Chris brings a unique
SAP Predictive Analysis: Strategy, Value Proposition
 September 10-13, 2012 Orlando, Florida SAP Predictive Analysis: Strategy, Value Proposition Charles Gadalla, Solution Management, SAP Business Intelligence Manavendra Misra, Chief Knowledge Officer, Cognilytics
September 10-13, 2012 Orlando, Florida SAP Predictive Analysis: Strategy, Value Proposition Charles Gadalla, Solution Management, SAP Business Intelligence Manavendra Misra, Chief Knowledge Officer, Cognilytics
Leveraging Machine Data to Deliver New Insights for Business Analytics
 Copyright 2015 Splunk Inc. Leveraging Machine Data to Deliver New Insights for Business Analytics Rahul Deshmukh Director, Solutions Marketing Jason Fedota Regional Sales Manager Safe Harbor Statement
Copyright 2015 Splunk Inc. Leveraging Machine Data to Deliver New Insights for Business Analytics Rahul Deshmukh Director, Solutions Marketing Jason Fedota Regional Sales Manager Safe Harbor Statement
Information Technology Policy
 Information Technology Policy Security Information and Event Management Policy ITP Number Effective Date ITP-SEC021 October 10, 2006 Category Supersedes Recommended Policy Contact Scheduled Review [email protected]
Information Technology Policy Security Information and Event Management Policy ITP Number Effective Date ITP-SEC021 October 10, 2006 Category Supersedes Recommended Policy Contact Scheduled Review [email protected]
Detect & Investigate Threats. OVERVIEW
 Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
Detect & Investigate Threats. OVERVIEW HIGHLIGHTS Introducing RSA Security Analytics, Providing: Security monitoring Incident investigation Compliance reporting Providing Big Data Security Analytics Enterprise-wide
Are You Ready for Big Data?
 Are You Ready for Big Data? Jim Gallo National Director, Business Analytics April 10, 2013 Agenda What is Big Data? How do you leverage Big Data in your company? How do you prepare for a Big Data initiative?
Are You Ready for Big Data? Jim Gallo National Director, Business Analytics April 10, 2013 Agenda What is Big Data? How do you leverage Big Data in your company? How do you prepare for a Big Data initiative?
Find the Information That Matters. Visualize Your Data, Your Way. Scalable, Flexible, Global Enterprise Ready
 Real-Time IoT Platform Solutions for Wireless Sensor Networks Find the Information That Matters ViZix is a scalable, secure, high-capacity platform for Internet of Things (IoT) business solutions that
Real-Time IoT Platform Solutions for Wireless Sensor Networks Find the Information That Matters ViZix is a scalable, secure, high-capacity platform for Internet of Things (IoT) business solutions that
Big Data and Trusted Information
 Dr. Oliver Adamczak Big Data and Trusted Information CAS Single Point of Truth 7. Mai 2012 The Hype Big Data: The next frontier for innovation, competition and productivity McKinsey Global Institute 2012
Dr. Oliver Adamczak Big Data and Trusted Information CAS Single Point of Truth 7. Mai 2012 The Hype Big Data: The next frontier for innovation, competition and productivity McKinsey Global Institute 2012
A Guide Through the BPM Maze
 A Guide Through the BPM Maze WHAT TO LOOK FOR IN A COMPLETE BPM SOLUTION With multiple vendors, evolving standards, and ever-changing requirements, it becomes difficult to recognize what meets your BPM
A Guide Through the BPM Maze WHAT TO LOOK FOR IN A COMPLETE BPM SOLUTION With multiple vendors, evolving standards, and ever-changing requirements, it becomes difficult to recognize what meets your BPM
Converging Technologies: Real-Time Business Intelligence and Big Data
 Have 40 Converging Technologies: Real-Time Business Intelligence and Big Data Claudia Imhoff, Intelligent Solutions, Inc Colin White, BI Research September 2013 Sponsored by Vitria Technologies, Inc. Converging
Have 40 Converging Technologies: Real-Time Business Intelligence and Big Data Claudia Imhoff, Intelligent Solutions, Inc Colin White, BI Research September 2013 Sponsored by Vitria Technologies, Inc. Converging
Opportunities with Predictive Analytics. Greg Leflar, Vice President [email protected]
 Opportunities with Predictive Analytics Greg Leflar, Vice President [email protected] Opportunities for Predictive Analytics We help you separate the Value from the Hype The field of predictive
Opportunities with Predictive Analytics Greg Leflar, Vice President [email protected] Opportunities for Predictive Analytics We help you separate the Value from the Hype The field of predictive
How In-Memory Data Grids Can Analyze Fast-Changing Data in Real Time
 SCALEOUT SOFTWARE How In-Memory Data Grids Can Analyze Fast-Changing Data in Real Time by Dr. William Bain and Dr. Mikhail Sobolev, ScaleOut Software, Inc. 2012 ScaleOut Software, Inc. 12/27/2012 T wenty-first
SCALEOUT SOFTWARE How In-Memory Data Grids Can Analyze Fast-Changing Data in Real Time by Dr. William Bain and Dr. Mikhail Sobolev, ScaleOut Software, Inc. 2012 ScaleOut Software, Inc. 12/27/2012 T wenty-first
WHITE PAPER SPLUNK SOFTWARE AS A SIEM
 SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
Industry Impact of Big Data in the Cloud: An IBM Perspective
 Industry Impact of Big Data in the Cloud: An IBM Perspective Inhi Cho Suh IBM Software Group, Information Management Vice President, Product Management and Strategy email: [email protected] twitter: @inhicho
Industry Impact of Big Data in the Cloud: An IBM Perspective Inhi Cho Suh IBM Software Group, Information Management Vice President, Product Management and Strategy email: [email protected] twitter: @inhicho
The Lab and The Factory
 The Lab and The Factory Architecting for Big Data Management April Reeve DAMA Wisconsin March 11 2014 1 A good speech should be like a woman's skirt: long enough to cover the subject and short enough to
The Lab and The Factory Architecting for Big Data Management April Reeve DAMA Wisconsin March 11 2014 1 A good speech should be like a woman's skirt: long enough to cover the subject and short enough to
High Performance Data Management Use of Standards in Commercial Product Development
 v2 High Performance Data Management Use of Standards in Commercial Product Development Jay Hollingsworth: Director Oil & Gas Business Unit Standards Leadership Council Forum 28 June 2012 1 The following
v2 High Performance Data Management Use of Standards in Commercial Product Development Jay Hollingsworth: Director Oil & Gas Business Unit Standards Leadership Council Forum 28 June 2012 1 The following
Q1 Labs Corporate Overview
 Q1 Labs Corporate Overview The Security Intelligence Leader Who we are: Innovative Security Intelligence software company One of the largest and most successful SIEM vendors Leader in Gartner 2011, 2010,
Q1 Labs Corporate Overview The Security Intelligence Leader Who we are: Innovative Security Intelligence software company One of the largest and most successful SIEM vendors Leader in Gartner 2011, 2010,
Five Technology Trends for Improved Business Intelligence Performance
 TechTarget Enterprise Applications Media E-Book Five Technology Trends for Improved Business Intelligence Performance The demand for business intelligence data only continues to increase, putting BI vendors
TechTarget Enterprise Applications Media E-Book Five Technology Trends for Improved Business Intelligence Performance The demand for business intelligence data only continues to increase, putting BI vendors
Augmented Search for Web Applications. New frontier in big log data analysis and application intelligence
 Augmented Search for Web Applications New frontier in big log data analysis and application intelligence Business white paper May 2015 Web applications are the most common business applications today.
Augmented Search for Web Applications New frontier in big log data analysis and application intelligence Business white paper May 2015 Web applications are the most common business applications today.
An Integrated Big Data & Analytics Infrastructure June 14, 2012 Robert Stackowiak, VP Oracle ESG Data Systems Architecture
 An Integrated Big Data & Analytics Infrastructure June 14, 2012 Robert Stackowiak, VP ESG Data Systems Architecture Big Data & Analytics as a Service Components Unstructured Data / Sparse Data of Value
An Integrated Big Data & Analytics Infrastructure June 14, 2012 Robert Stackowiak, VP ESG Data Systems Architecture Big Data & Analytics as a Service Components Unstructured Data / Sparse Data of Value
SQLstream 4 Product Brief. CHANGING THE ECONOMICS OF BIG DATA SQLstream 4.0 product brief
 SQLstream 4 Product Brief CHANGING THE ECONOMICS OF BIG DATA SQLstream 4.0 product brief 2 Latest: The latest release of SQlstream s award winning s-streaming Product Portfolio, SQLstream 4, is changing
SQLstream 4 Product Brief CHANGING THE ECONOMICS OF BIG DATA SQLstream 4.0 product brief 2 Latest: The latest release of SQlstream s award winning s-streaming Product Portfolio, SQLstream 4, is changing
Big Data: Key Concepts The three Vs
 Big Data: Key Concepts The three Vs Big data in general has context in three Vs: Sheer quantity of data Speed with which data is produced, processed, and digested Diversity of sources inside and outside.
Big Data: Key Concepts The three Vs Big data in general has context in three Vs: Sheer quantity of data Speed with which data is produced, processed, and digested Diversity of sources inside and outside.
Smarter Analytics Leadership Summit Big Data. Real Solutions. Big Results.
 Smarter Analytics Leadership Summit Big Data. Real Solutions. Big Results. 5 Game Changing Use Cases for Big Data Inhi Cho Suh Vice President Product Management & Strategy Information Management IBM Software
Smarter Analytics Leadership Summit Big Data. Real Solutions. Big Results. 5 Game Changing Use Cases for Big Data Inhi Cho Suh Vice President Product Management & Strategy Information Management IBM Software
OPEN MODERN DATA ARCHITECTURE FOR FINANCIAL SERVICES RISK MANAGEMENT
 WHITEPAPER OPEN MODERN DATA ARCHITECTURE FOR FINANCIAL SERVICES RISK MANAGEMENT A top-tier global bank s end-of-day risk analysis jobs didn t complete in time for the next start of trading day. To solve
WHITEPAPER OPEN MODERN DATA ARCHITECTURE FOR FINANCIAL SERVICES RISK MANAGEMENT A top-tier global bank s end-of-day risk analysis jobs didn t complete in time for the next start of trading day. To solve
Enterprise Operational SQL on Hadoop Trafodion Overview
 Enterprise Operational SQL on Hadoop Trafodion Overview Rohit Jain Distinguished & Chief Technologist Strategic & Emerging Technologies Enterprise Database Solutions Copyright 2012 Hewlett-Packard Development
Enterprise Operational SQL on Hadoop Trafodion Overview Rohit Jain Distinguished & Chief Technologist Strategic & Emerging Technologies Enterprise Database Solutions Copyright 2012 Hewlett-Packard Development
Find the needle in the security haystack
 Find the needle in the security haystack Gunnar Kristian Kopperud Principal Presales Consultant Security & Endpoint Management Technology Day Oslo 1 Find the needle in the security haystack Manually deep
Find the needle in the security haystack Gunnar Kristian Kopperud Principal Presales Consultant Security & Endpoint Management Technology Day Oslo 1 Find the needle in the security haystack Manually deep
IoT Analytics: Four Key Essentials and Four Target Industries
 IoT Analytics: Four Key Essentials and Four Target Industries 1 Introduction Analysts and IT personnel across all industries seek technology to better engage and manage data generated by the Internet of
IoT Analytics: Four Key Essentials and Four Target Industries 1 Introduction Analysts and IT personnel across all industries seek technology to better engage and manage data generated by the Internet of
Testing Big data is one of the biggest
 Infosys Labs Briefings VOL 11 NO 1 2013 Big Data: Testing Approach to Overcome Quality Challenges By Mahesh Gudipati, Shanthi Rao, Naju D. Mohan and Naveen Kumar Gajja Validate data quality by employing
Infosys Labs Briefings VOL 11 NO 1 2013 Big Data: Testing Approach to Overcome Quality Challenges By Mahesh Gudipati, Shanthi Rao, Naju D. Mohan and Naveen Kumar Gajja Validate data quality by employing
IBM AND NEXT GENERATION ARCHITECTURE FOR BIG DATA & ANALYTICS!
 The Bloor Group IBM AND NEXT GENERATION ARCHITECTURE FOR BIG DATA & ANALYTICS VENDOR PROFILE The IBM Big Data Landscape IBM can legitimately claim to have been involved in Big Data and to have a much broader
The Bloor Group IBM AND NEXT GENERATION ARCHITECTURE FOR BIG DATA & ANALYTICS VENDOR PROFILE The IBM Big Data Landscape IBM can legitimately claim to have been involved in Big Data and to have a much broader
FRAUD & SECURITY INTELLIGENCE
 FRAUD & SECURITY INTELLIGENCE STU BRADLEY, SR. DIRECTOR SECURITY INTELLIGENCE PRACTICE APRIL 16, 2015 2015 TRENDS MOBILE IS HERE TO STAY 2015 TRENDS INTERNET OF THINGS CREATING VULNERABILITIES 2015 TRENDS
FRAUD & SECURITY INTELLIGENCE STU BRADLEY, SR. DIRECTOR SECURITY INTELLIGENCE PRACTICE APRIL 16, 2015 2015 TRENDS MOBILE IS HERE TO STAY 2015 TRENDS INTERNET OF THINGS CREATING VULNERABILITIES 2015 TRENDS
Big Data & Analytics. Counterparty Credit Risk Management. Big Data in Risk Analytics
 Deniz Kural, Senior Risk Expert BeLux Patrick Billens, Big Data Solutions Leader Big Data & Analytics Counterparty Credit Risk Management Challenges for the Counterparty Credit Risk Manager Regulatory
Deniz Kural, Senior Risk Expert BeLux Patrick Billens, Big Data Solutions Leader Big Data & Analytics Counterparty Credit Risk Management Challenges for the Counterparty Credit Risk Manager Regulatory
RESEARCH REPORT. The State of Streaming Big Data Analytics: 2014 Survey Results
 RESEARCH REPORT The State of Streaming Big Data Analytics: 2014 Survey Results April 2014 Executive Summary As the speed of business accelerates, organizations produce increasingly vast volumes of high
RESEARCH REPORT The State of Streaming Big Data Analytics: 2014 Survey Results April 2014 Executive Summary As the speed of business accelerates, organizations produce increasingly vast volumes of high
Providing real-time, built-in analytics with S/4HANA. Jürgen Thielemans, SAP Enterprise Architect SAP Belgium&Luxembourg
 Providing real-time, built-in analytics with S/4HANA Jürgen Thielemans, SAP Enterprise Architect SAP Belgium&Luxembourg SAP HANA Analytics Vision Situation today: OLTP and OLAP separated, one-way streets
Providing real-time, built-in analytics with S/4HANA Jürgen Thielemans, SAP Enterprise Architect SAP Belgium&Luxembourg SAP HANA Analytics Vision Situation today: OLTP and OLAP separated, one-way streets
Evolving Data Warehouse Architectures
 Evolving Data Warehouse Architectures In the Age of Big Data Philip Russom April 15, 2014 TDWI would like to thank the following companies for sponsoring the 2014 TDWI Best Practices research report: Evolving
Evolving Data Warehouse Architectures In the Age of Big Data Philip Russom April 15, 2014 TDWI would like to thank the following companies for sponsoring the 2014 TDWI Best Practices research report: Evolving
Security Analytics Topology
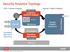 Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
Security Analytics Topology CEP = Stream Analytics Hadoop = Batch Analytics Months to years LOGS PKTS Correlation with Live in Real Time Meta, logs, select payload Decoder Long-term, intensive analysis
