SRA 6.0 User s Guide 1
|
|
|
- Baldric Richards
- 8 years ago
- Views:
Transcription
1 SRA 6.0 User s Guide 1
2 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage to hardware or loss of data if instructions are not followed. WARNING: A WARNING indicates a potential for property damage, personal injury, or death Dell Inc. Trademarks: Dell, the DELL logo, SonicWALL, SonicWALL GMS, SonicWALL ViewPoint, Aventail, Reassembly-Free Deep Packet Inspection, Dynamic Security for the Global Network, SonicWALL Aventail Advanced End Point Control (EPC ), SonicWALL Aventail Advanced Reporting, SonicWALL Aventail Connect Mobile, SonicWALL Aventail Connect, SonicWALL Aventail Native Access Modules, SonicWALL Aventail Policy Zones, SonicWALL Aventail Smart Access, SonicWALL Aventail Unified Policy, SonicWALL Aventail Advanced EPC, SonicWALL Clean VPN, SonicWALL Clean Wireless, SonicWALL Global Response Intelligent Defense (GRID) Network, SonicWALL Mobile Connect, SonicWALL SuperMassive E10000 Series, and all other SonicWALL product and service names and slogans are trademarks of Dell Inc P/N Rev. C 2 Dell SonicWALL SRA 6.0 User s Guide
3 Table of Contents Chapter 1. Using This Guide About this Guide Organization of this Guide Guide Conventions Current Documentation Quick Access Work Sheet Chapter 2. Virtual Office Overview Virtual Office Overview Accessing Virtual Office Resources Browser Requirements Web Management Interface Overview Certificates Chapter 3. Using Virtual Office Features Importing Certificates Using Two-Factor Authentication User Prerequisites User Configuration Tasks Using One-Time Passwords User Prerequisites User Configuration Tasks Verifying User One-Time Password Configuration Using NetExtender User Prerequisites User Configuration Tasks Installing NetExtender on Android Smartphones Using NetExtender on Android Smartphones Related Documents Using Secure Virtual Assist Understanding Secure Virtual Assist Installing and Launching Secure Virtual Assist Configuring Secure Virtual Assist Settings Selecting a Secure Virtual Assist Mode Launching a Secure Virtual Assist Technician Session Performing Secure Virtual Assist Technician Tasks Initiating a Secure Virtual Assist Session from the Customer View Using Secure Virtual Assist Using Secure Virtual Assist in Unattended Mode Enabling a System for Secure Virtual Access Using the Request Assistance Feature Using Secure Virtual Meeting Features Table of Contents 3
4 User Roles Coordinator Role Participant Role Using File Shares Using the File Shares Applet Using HTML-Based File Shares Managing Bookmarks Adding Bookmarks Editing Bookmarks Removing Bookmarks Using Bookmarks Using Remote Desktop Bookmarks Using VNC Bookmarks Using FTP Bookmarks Using Telnet Bookmarks Using SSHv1 Bookmarks Using SSHv2 Bookmarks Using Web Bookmarks Using File Share Bookmarks Using Citrix Bookmarks Global Bookmark Single Sign-On Options Per-Bookmark Single Sign-On Options Logging Out of the Virtual Office Appendix A. Support Information Contact Information GNU General Public License (GPL) Source Code Limited Hardware Warranty End User Licensing Agreement Dell SonicWALL SRA 6.0 User s Guide
5 Chapter 1 Using This Guide About this Guide Welcome to the Dell SonicWALL SRA User s Guide. This manual is a user's guide. It provides information on using the Dell SonicWALL SRA user portal called Virtual Office that allows you to create bookmarks and run services over the Dell SonicWALL SRA appliance. Always check for the latest version of this manual as well as other Dell SonicWALL products and services documentation. Organization of this Guide The Dell SonicWALL SRA User s Guide organization is structured into the following parts: Chapter 1 Using this Guide This chapter provides helpful information for using this guide. It.includes conventions used in this guide, information on how to obtain additional product information, and a Quick Access Worksheet that you should complete before using the SRA appliance. Chapter 2 Virtual Office Overview This chapter provides an overview of new Dell SonicWALL SRA appliance user features, NetExtender, File Shares, Secure Virtual Assist, Secure Virtual Access, Secure Virtual Meeting, services, sessions, bookmarks, and service tray menu options. Chapter 3 Using Virtual Office This chapter provides procedures on importing certificates, using Two-Factor authentication, using One-Time Passwords, using NetExtender, using Virtual Assist and Virtual Meeting, configuring bookmarks, and using file shares. Chapter 4 Support Information This chapter provides the Limited Hardware Warranty, End User Licensing Agreement, and Dell SonicWALL Support contact information. Using This Guide 5
6 Guide Conventions The following conventions used in this guide are as follows: Convention Bold Italic Use Highlights dialog box, window, and screen names. Also highlights buttons. Also used for file names and text or values you are being instructed to type into the interface. Indicates the name of a technical manual. Also indicates emphasis on certain words in a sentence. Sometimes indicates the first instance of a significant term or concept. Current Documentation Check the Dell SonicWALL documentation Web site for the latest versions of all Dell SonicWALL product documentation at Quick Access Work Sheet Use the Quick Access Work Sheet to collect important information that you will need and should be completed by your network administrator to allow remote users SSL VPN access. IP Address: User Name: Password: Domain: 6 Dell SonicWALL SRA 6.0 User s Guide
7 Chapter 2 Virtual Office Overview This chapter provides an overview of the Dell SonicWALL SSL VPN user portal. It also includes an introduction to the SRA appliance and its features and applications. This chapter contains the following sections: Virtual Office Overview section on page 7 Browser Requirements section on page 8 Web Management Interface Overview section on page 10 Virtual Office Overview Dell SonicWALL SSL VPN Virtual Office provides secure remote access to network resources, such as applications, files, intranet Web sites, and through Web access interface such as Microsoft Outlook Web Access (OWA). The underlying protocol used for these sessions is SSL. With SSL VPN, mobile workers, telecommuters, partners, and customers can access information and applications on your intranet or extranet. What information should be accessible to the user is determined by access policies configured by the Dell SonicWALL SSL VPN administrator. Accessing Virtual Office Resources Remote network resources can be accessed in the following ways: Using a standard Web browser - To access network resources, you must log into the SSL VPN portal. Once authenticated, you may access intranet HTTP and HTTPS sites, offloaded portals, Web-based applications, and Web-based . In addition, you may upload and download files using FTP or Windows Network File Sharing. All access is performed through a standard Web browser and does not require any client applications to be downloaded to remote users machines. Using Java thin-client access to corporate desktops and applications The Dell SonicWALL SRA security appliance includes several Java or ActiveX thin-client programs that can be launched from within the Dell SonicWALL SRA security appliance. Terminal Services and VNC Java clients allow remote users to access corporate servers and desktops, open files, edit and store data as if they were at the office. Terminal Services provides the ability to open individual applications and support remote sound and print services. In addition, users may access Telnet and SSH servers for SSH version 1 (SSHv1) and SSH version 2 (SSHv2), from the SSL VPN portal. Using the NetExtender SSL VPN client The Dell SonicWALL SSL VPN network extension client, NetExtender, is available through the SSL VPN Virtual Office portal via an ActiveX control or through stand-alone applications for Windows, Linux, MacOS, Windows Mobile, and Android smartphone platforms. To connect using the SSL VPN client, log into the portal, download the installer application and then launch the NetExtender connector to establish the SSL VPN tunnel. The NetExtender Android client has a different installation process, described in this guide. Once you have set up the SSL VPN tunnel, you can access network resources as if you were on the local network. Virtual Office Overview 7
8 The NetExtender standalone applications are automatically installed on a client system the first time you click on the NetExtender link in the Virtual Office portal. The standalone client can be launched directly from users computers without requiring them to log in to the SSL VPN portal first. Using the Dell SonicWALL Mobile Connect app Dell SonicWALL Mobile Connect is an app for iphone and ipad that, like NetExtender, uses SSL VPN to enable secure, mobile connections to private networks protected by Dell SonicWALL security appliances. For information about installing and using Dell SonicWALL Mobile Connect, see the Dell SonicWALL Mobile Connect User s Guide available on at: For SSL VPN to work as described in this guide, the SonicWALL SRA security appliance must be installed and configured according to the directions provided in the SonicWALL SRA Getting Started Guide for your model. Browser Requirements The following Web browsers are supported for the SSL VPN Virtual Office portal: Internet Explorer 8.0+, 9.0+ Firefox Safari 5.0+ Chrome For administrator management interface Web browser compatibility, refer to the SonicWALL SSL VPN Administrator s Guide. 8 Dell SonicWALL SRA 6.0 User s Guide
9 The following table provides specific browser requirements. pplication Proxy How to read this table: eatures and Browser Requirements Windows XP Windows Vista Windows 7 Linux MacOS X NetExtender browser browser independent independent (Java 1.6.0_10+) (Java 1.6.0_10+) RDP5 (Java 1.6.0_10) RDP5 (ActiveX) Feature OS Platform Browser RDP5 (Java 1.6.0_10+) Minimum Recommended Browser Versions: VNC (Java 1.6.0_10+) Telnet (Java 1.6.0_10+) , SSHv2 (Java 1.6.0_10+) 8 16 P, HTTPS, FTP (Browser) File Sharing (Browser) Notes: 1 MacOS and Linux supports Virtual Assist on the clientside only. Technician must be running a supported version of Windows operating system. Sharing (Java 1.6.0_10+) Citrix (ActiveX) Citrix (Java 1.6.0_10+) Virtual Assist (Java not required) browser browser 1 1 independent independent (Java 1.6.0_10+) (Java 1.6.0_10+) To configure SonicOS SSL VPN firmware, an administrator must use a Web browser with JavaScript, cookies, and SSL enabled. Virtual Assist is fully supported on Windows platforms. Virtual Assist is certified to work on Windows 7, Windows Vista and Windows XP. Limited functionality is supported on Mac OS where customers can request for assistance via web-requests. Virtual Office Overview 9
10 Web Management Interface Overview From your workstation at your remote location, launch an approved Web browser and browse to your SRA appliance at the URL provided to you by your network administrator. Step 1 Step 2 Open a Web browser and enter (the default LAN management IP address) in the Location or Address field. A security warning may appear. Click the Yes button to continue. Step 3 The SonicWALL SSL VPN Management Interface displays and prompts you to enter your user name and password. As a default value, enter admin in the User Name field, password in the Password field, and select a domain from the Domain drop-down list and click the Login button. Only LocalDomain allows administrator privileges. Note that your administrator may have set up another login and password for you that has only user privileges. The default page displayed is the Virtual Office home page. The default version of this page shows a SonicWALL logo, although your company s system administrator may have customized this page to contain a logo and look and feel of your company. Go to the Virtual Office Overview, page 7 to learn more about the Virtual Office home page. From the Virtual Office portal home page, you cannot navigate to the administrator s environment. If you have administrator s privileges and want to enter the administrator environment, you need to go back to the login page and enter a username and password that 10 Dell SonicWALL SRA 6.0 User s Guide
11 have administrator privileges, and login again using the LocalDomain domain. Only the LocalDomain allows administrator access to the management interface. Also note that the domain is independent of the privileges set up for the user. Logging in as a user takes you directly to Virtual Office. The Virtual Office Home page displays as shown here. The Virtual Office content will vary based on the configuration of your network administrator. Some bookmarks and services described in the SonicWALL SSL VPN User s Guide may not be displayed when you log into the SonicWALL SRA security appliance. The Virtual Office consists of the nodes described in the following table. Node File Shares NetExtender Description Provides access to the File Shares utility, which gives remote users with a secure Web interface access to Microsoft File Shares using the CIFS (Common Internet File System) or SMB (Server Message Block) protocols. Using a Web interface similar in style to Microsoft s familiar Network Neighborhood or My Network Places, File Shares allow users with appropriate permissions to browse network shares, rename, delete, retrieve, and upload files, and to create bookmarks for later recall. Provides access to the NetExtender utility, a transparent SSL VPN client for Windows, MacOS, Linux, Windows Mobile, or Android smartphone users that allows you to run any application securely on the remote network. It acts as an IP-level mechanism provided by the virtual interface that negotiates the ActiveX component (on Windows with IE), using a Point-to-Point Protocol (PPP) adapter instance. On non- Windows platforms except Android, Java controls are used to automatically install NetExtender from the Virtual Office portal. After installation, NetExtender automatically launches and connects a virtual adapter for SSL secure NetExtender point-to-point access to permitted hosts and subnets on the internal network. Virtual Office Overview 11
12 Node Secure Virtual Assist Secure Virtual Meeting Secure Virtual Access (if configured by administrator Bookmarks Options Online Help Tips/Help Logout Description Provides access to Virtual Assist, an easy to use tool that allows Sonic- WALL SSL VPN users to remotely support customers by taking control of their computers while the customer observes. Virtual Assist is a lightweight, thin client that installs automatically using Java from the Sonic- WALL SSL VPN Virtual Office without requiring the installation of any external software. For computers that do not support Java, Virtual Assist can be manually installed by downloading an executable file from the Virtual Office. Provides access to Virtual Meeting, which allows multiple users to view a desktop and interactively participate in a meeting from virtually anywhere with an Internet connection. Virtual Meeting is similar to the oneto-one desktop sharing provided by Virtual Assist except multiple users can share a desktop. Secure Virtual Access allows technicians to gain access to systems outside the LAN of the SRA appliance. After downloading and installing the thin client for Secure Virtual Access mode, the system will appear only on that technician s Virtual Assist support queue, within the SRA s management interface. Provides a list of available bookmarks which are objects that enable you to connect to a location or application conveniently and quickly. Provides the option to change user password and use single sign-on, if enabled by the administrator. Launches online help for Virtual Office. Provides a short list of common questions and tips about the Virtual Office. Logs you out of the Virtual Office environment. The Home page provides customized content and links to network resources. The Home Page may contain support contact information, VPN instructions, company news, or technical updates. Only a Web browser is required to access intranet Web sites, File Shares, and FTP sites. VNC, Telnet and SSHv1 require Java. SSHv2 provides stronger encryption than SSHv1, requires SUN JRE 1.4 or above and can only connect to servers that support SSHv2. Terminal Services requires either Java or ActiveX on the client machine. As examples of tasks you can perform and environments you can reach through Virtual Office, you can connect to: Intranet Web or HTTPS sites If your organization supports Web-based , such as Outlook Web Access, you can also access Web-based The entire network by launching the NetExtender client FTP servers for uploading and downloading files The corporate network neighborhood for file sharing Telnet and SSH servers Desktops and desktop applications using Terminal Services or VNC. servers via the NetExtender client. The administrator determines what resources are available to users from the SonicWALL SSL VPN Virtual Office. The administrator can create user, group, and global policies that disable access to certain machines or applications on the corporate network. The administrator may also define bookmarks, or preconfigured links, to Web sites or computers on the intranet. Additional bookmarks may be defined by the end user. 12 Dell SonicWALL SRA 6.0 User s Guide
13 SonicWALL NetExtender is a software application that enables remote users to securely connect to the remote network. With NetExtender, remote users can virtually join the remote network. Users can mount network drives, upload and download files, and access resources in the same way as if they were on the local network. Certificates If the SRA appliance uses a self-signed SSL certificate for HTTPS authentication, then it is recommended to install the certificate before establishing a NetExtender connection. If you are unsure whether the certificate is self-signed or generated by a trusted root Certificate Authority, SonicWALL recommends that you import the certificate. The easiest way to import the certificate is to click the Import Certificate button at the bottom of the Virtual Office home page. If the certificate is not issued by an authorized organization, a message is displayed warning users of the risk. A user can then view detailed information and choose to continue or end the connection. Virtual Office Overview 13
14 14 Dell SonicWALL SRA 6.0 User s Guide
15 Chapter 3 Using Virtual Office Features This chapter provides details on how to use the features in the Dell SonicWALL SSL VPN user portal, including NetExtender, configuring bookmarks, accessing services, and using file shares. This chapter contains the following sections: Importing Certificates section on page 15 Using Two-Factor Authentication section on page 16 Using One-Time Passwords section on page 20 Using NetExtender section on page 22 Using Secure Virtual Assist section on page 77 Using Secure Virtual Meeting section on page 104 Using File Shares section on page 119 Managing Bookmarks section on page 132 Using Bookmarks section on page 139 Logging Out of the Virtual Office section on page 157 Importing Certificates If the SSL VPN gateway uses a self-signed SSL certificate for HTTPS authentication, then it is recommended to install the certificate before establishing a NetExtender connection. If you are unsure whether the certificate is self-signed or generated by a trusted root Certificate Authority, Dell SonicWALL recommends that you import the certificate. If using Internet Explorer, the easiest way to import the certificate is to click the Import Certificate button at the bottom of the Virtual Office home page. The following warning messages may be displayed: Click Yes. The certificate will be imported. Note Certificates can only be imported through this method if you are using Internet Explorer. Certificates for other browsers such as Chrome or Firefox must be imported manually. Using Virtual Office Features 15
16 Using Two-Factor Authentication The following sections describe how to log in to the SSL VPN Virtual Office portal using twofactor authentication: User Prerequisites on page 16 User Configuration Tasks on page 16 User Prerequisites Before you can log in using two-factor authentication, you must meet the following prerequisites: Your administrator has created your user account. You have an account with a two-factor authentication server that conforms to the RFC standard. User Configuration Tasks The following sections describe how users log in to the Dell SonicWALL SRA appliance using the two types of two-factor authentication: RSA Two-Factor User Authentication Process on page 16 VASCO Two-Factor User Authentication Process on page 18 Other RADIUS Server Two-Factor Authentication Process on page 19 RSA Two-Factor User Authentication Process The following sections describe user tasks when using RSA two-factor authentication to log in to the Dell SonicWALL SSL VPN Virtual Office: Logging into the SSL VPN Virtual Office Using RSA Two-Factor Authentication on page 16 Creating a New PIN on page 17 Waiting for the Next Token Mode on page 18 Logging into the SSL VPN Virtual Office Using RSA Two-Factor Authentication To log in to the Dell SonicWALL SSL VPN Virtual Office using RSA two-factor authentication, perform the following steps. 16 Dell SonicWALL SRA 6.0 User s Guide
17 Step 1 Enter the IP address of the SRA appliance in your computers browser. The authentication window is displayed. Step 2 Step 3 Enter your username in the Username field. The first time you log in to the Virtual office, your entry in the password field depends on whether your system requires a PIN: If you already have a PIN, enter the passcode in the Password field. The passcode is the user PIN and the SecurID token code. For example, if the user s PIN is 8675 and the token code is , then the passcode is If a PIN is required, but you do not yet have a PIN, enter the SecurID token code in the Password field. You will be prompted to create a PIN. If the RSA server does not require a PIN, simply enter the SecurID token code. Note Consult with your network administrator to determine if your configuration requires a PIN. Step 4 Step 5 Select the appropriate Domain. If manually entering the Domain, it is case-sensitive. Click Login. Creating a New PIN The RSA Authentication Manager automatically determines when users are required to create a new PIN. will determines that user associated with a particular token requires a new PIN. The SRA appliance prompts the user to enter new PIN. Using Virtual Office Features 17
18 Enter the PIN in the New PIN field and again in the Confirm PIN field and click OK. The PIN must be between 4 and 8 characters long. Step 6 The RSA Authentication Manager verifies that the new PIN is an acceptable PIN. If the PIN is accepted, the user is prompted to log in with the new passcode. Waiting for the Next Token Mode If user authentication fails three consecutive times, the RSA server requires the user to generate and enter a new token. To complete authentication, the user is prompted to wait for the token to change and enter the next token. VASCO Two-Factor User Authentication Process The following sections describe user tasks when using RSA two-factor authentication: Logging into the SSL VPN Virtual Office Using VASCO Two-Factor Authentication on page 18 Creating a New PIN on page 17 Logging into the SSL VPN Virtual Office Using VASCO Two-Factor Authentication To log in to the Dell SonicWALL SSL VPN Virtual Office using VASCO two-factor authentication, perform the following steps: 18 Dell SonicWALL SRA 6.0 User s Guide
19 Step 1 Step 2 Step 3 Enter the IP address of the SRA appliance in your computer s browser. The authentication window is displayed. Enter your username in the Username field. Enter the passcode in the Password field. Your entry in the password field depends on whether your system requires a PIN: If you already have a PIN, enter the passcode in the Password field. The passcode is the user PIN and the VASCO Digipass token code. For example, if the user s PIN is 8675 and the token code is , then the passcode is If a PIN is required, but you do not yet have a PIN, enter the VASCO Digipass code in the Password field. You will be prompted to create a PIN. If the RSA server does not require a PIN, simply enter the VASCO Digipass code. Note Consult with your network administrator to determine if your configuration requires a PIN. Step 4 Step 5 Select the appropriate Domain. If manually entering the Domain, it is case-sensitive. Click Login. Other RADIUS Server Two-Factor Authentication Process To log in to the Virtual Office using another type of RADIUS server for two-factor authentication, perform the following steps: Step 1 Enter the IP address of the SRA appliance in your computers browser. The authentication window is displayed. Step 2 Step 3 Step 4 Step 5 Step 6 Enter your username in the Username field. Enter your password in the Password field. Select the appropriate Domain. If manually entering the Domain, it is case-sensitive. Click Login. You will be prompted to enter additional information, the details of which will depend on the type of RADIUS server used. The example below shows an M.ID RADIUS server, which first prompts you to Please enter the M.ID PIN. Enter the PIN in the Challenge field and click OK. Using Virtual Office Features 19
20 Step 7 You will then be prompted to Please enter the M.ID Passcode. Enter the passcode received through or text message in the Challenge field and click OK. Using One-Time Passwords The following sections describe how to use one-time passwords: User Prerequisites, page 20 User Configuration Tasks, page 20 Verifying User One-Time Password Configuration, page 22 Using NetExtender, page 22 User Prerequisites Users must have a user account enabled in the SSL VPN management interface. Only users enabled by the administrator to use the One-Time Password feature will need to perform the following configuration tasks. The administrator must enable a correct address that is accessible by the user. Users cannot enable the One-Time Password feature and they must be able to access the SSL VPN Virtual Office portal. User Configuration Tasks To use the One-Time Password feature, perform the following steps: 20 Dell SonicWALL SRA 6.0 User s Guide
21 Step 1 Step 2 If you are not logged into the SSL VPN Virtual Office user interface, open a Web browser and type the Virtual Office interface URL in the Location or Address bar and press Enter. Type in your user name in the User Name field and your password in the Password field, then select the appropriate domain from the Domain drop-down menu. Click Login. The prompt A temporary password has been sent to user@ .com will appear, displaying your pre-configured account. Step 3 Step 4 Step 5 Login to your account to retrieve the one-time password. Type or paste the one-time password into the Password: field where prompted and click Login. You will be logged in to the Virtual Office. Note One-time passwords are immediately deleted after a successful login, and cannot be used again. Unused one-time passwords will expire according to each user s timeout policy. Configuring One-Time Passwords for SMS-Capable Phones One-Time Passwords can be configured to be sent via directly to SMS-capable phones. Contact your cell phone service provider for further information about enabling SMS. Below is a list of SMS formats for selected major carriers, where represents a 10-digit telephone number and area code. Note These SMS formats are for reference only. These formats are subject to change and may vary. You may need additional service or information from your provider before using SMS. Contact the SMS provider directly to verify these formats and for further information on SMS services, options, and capabilities. Verizon: @vtext.com Sprint: @messaging.sprintpcs.com AT&T: @mobile.att.net Cingular: @mobile.mycingular.com T-Mobile: @tmomail.net Nextel: @messaging.nextel.com Virgin Mobile: @vmobl.com Qwest: @qwestmp.com For a more complete list, see the Dell SonicWALL SSL VPN Administrator's Guide. Using Virtual Office Features 21
SonicWALL SSL VPN 5.0 User s Guide
 COMPREHENSIVE INTERNET SECURITY SonicWALL Secure Remote Access Appliances SonicWALL SSL VPN 5.0 User s Guide Table of Contents Using This Guide About this Guide......................................................
COMPREHENSIVE INTERNET SECURITY SonicWALL Secure Remote Access Appliances SonicWALL SSL VPN 5.0 User s Guide Table of Contents Using This Guide About this Guide......................................................
How To Use The Sonicwall Sra User Guide
 SonicWALL Secure Remote Access Appliances SonicWALL SRA 6.0 User s Guide Table of Contents Using This Guide About this Guide...................................................... 7 Organization of this
SonicWALL Secure Remote Access Appliances SonicWALL SRA 6.0 User s Guide Table of Contents Using This Guide About this Guide...................................................... 7 Organization of this
SonicWALL SSL VPN 3.5 User s Guide
 COMPREHENSIVE INTERNET SECURITY SonicWALL Internet Security Appliances SonicWALL SSL VPN 3.5 User s Guide Table of Contents Using This Guide About this Guide......................................................
COMPREHENSIVE INTERNET SECURITY SonicWALL Internet Security Appliances SonicWALL SSL VPN 3.5 User s Guide Table of Contents Using This Guide About this Guide......................................................
SonicWALL SSL-VPN 2.1 User s Guide
 COMPREHENSIVE INTERNET SECURITY SonicWALL Internet Security Appliances SonicWALL SSL-VPN 2.1 User s Guide Using This Guide About this Guide...................................................... 5 Organization
COMPREHENSIVE INTERNET SECURITY SonicWALL Internet Security Appliances SonicWALL SSL-VPN 2.1 User s Guide Using This Guide About this Guide...................................................... 5 Organization
SonicWALL SSL-VPN 2.5: NetExtender
 SonicWALL SSL-VPN 2.5: NetExtender Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the
SonicWALL SSL-VPN 2.5: NetExtender Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the
SonicWALL SSL VPN 5.0: NetExtender
 SonicWALL SSL VPN 5.0: NetExtender Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL VPN Environment. This document contains the
SonicWALL SSL VPN 5.0: NetExtender Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL VPN Environment. This document contains the
Dell SonicWALL Aventail 10.6.5 Connect Tunnel User Guide
 Dell SonicWALL Aventail 10.6.5 Connect Tunnel User Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates
Dell SonicWALL Aventail 10.6.5 Connect Tunnel User Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates
Dell SonicWALL SRA 7.5 Citrix Access
 Dell SonicWALL SRA 7.5 Citrix Access Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through Dell SonicWALL SRA 7.5. It also includes information about
Dell SonicWALL SRA 7.5 Citrix Access Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through Dell SonicWALL SRA 7.5. It also includes information about
VPN Web Portal Usage Guide
 VPN Web Portal Usage Guide Table of Contents WHAT IS VPN WEB CLIENT 4 SUPPORTED WEB BROWSERS 4 LOGGING INTO VPN WEB CLIENT 5 ESTABLISHING A VPN CONNECTION 6 KNOWN ISSUES WITH MAC COMPUTERS 6 ACCESS INTRANET
VPN Web Portal Usage Guide Table of Contents WHAT IS VPN WEB CLIENT 4 SUPPORTED WEB BROWSERS 4 LOGGING INTO VPN WEB CLIENT 5 ESTABLISHING A VPN CONNECTION 6 KNOWN ISSUES WITH MAC COMPUTERS 6 ACCESS INTRANET
Windows and MAC User Handbook Remote and Secure Connection Version 1.01 09/19/2013. User Handbook
 Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
Hosted Email Security Quick Start Guide
 Hosted Email Security Quick Start Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Hosted Email Security Quick Start Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Citrix Access on SonicWALL SSL VPN
 Citrix Access on SonicWALL SSL VPN Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through SonicWALL SSL VPN 5.0. It also includes information about configuring
Citrix Access on SonicWALL SSL VPN Document Scope This document describes how to configure and use Citrix bookmarks to access Citrix through SonicWALL SSL VPN 5.0. It also includes information about configuring
SonicWALL Mobile Connect. Mobile Connect for OS X 3.0. User Guide
 SonicWALL Mobile Connect Mobile Connect for OS X 3.0 User Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
SonicWALL Mobile Connect Mobile Connect for OS X 3.0 User Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
Clientless SSL VPN Users
 Manage Passwords, page 1 Username and Password Requirements, page 3 Communicate Security Tips, page 3 Configure Remote Systems to Use Clientless SSL VPN Features, page 3 Manage Passwords Optionally, you
Manage Passwords, page 1 Username and Password Requirements, page 3 Communicate Security Tips, page 3 Configure Remote Systems to Use Clientless SSL VPN Features, page 3 Manage Passwords Optionally, you
Global VPN Client Getting Started Guide
 Global VPN Client Getting Started Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Global VPN Client Getting Started Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential
Citrix Access Gateway Plug-in for Windows User Guide
 Citrix Access Gateway Plug-in for Windows User Guide Access Gateway 9.2, Enterprise Edition Copyright and Trademark Notice Use of the product documented in this guide is subject to your prior acceptance
Citrix Access Gateway Plug-in for Windows User Guide Access Gateway 9.2, Enterprise Edition Copyright and Trademark Notice Use of the product documented in this guide is subject to your prior acceptance
SSL-VPN 200 Getting Started Guide
 Secure Remote Access Solutions APPLIANCES SonicWALL SSL-VPN Series SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide Thank you for your purchase of the SonicWALL SSL-VPN
Secure Remote Access Solutions APPLIANCES SonicWALL SSL-VPN Series SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide Thank you for your purchase of the SonicWALL SSL-VPN
How To Use Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
CONNECT-TO-CHOP USER GUIDE
 CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
The SSL device also supports the 64-bit Internet Explorer with new ActiveX loaders for Assessment, Abolishment, and the Access Client.
 WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
ZyWALL SSL 10. User s Guide. Integrated SSL-VPN Appliance. www.zyxel.com. Version 2.00 12/2008 Edition 1
 ZyWALL SSL 10 Integrated SSL-VPN Appliance User s Guide Version 2.00 12/2008 Edition 1 www.zyxel.com About This User's Guide About This User's Guide Intended Audience This manual is intended for people
ZyWALL SSL 10 Integrated SSL-VPN Appliance User s Guide Version 2.00 12/2008 Edition 1 www.zyxel.com About This User's Guide About This User's Guide Intended Audience This manual is intended for people
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources
 Akin Gump Strauss Hauer & Feld LLP Remote Access Resources Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2013 Akin Gump Strauss Hauer & Feld LLP Checkpoint VPN (Firm
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2013 Akin Gump Strauss Hauer & Feld LLP Checkpoint VPN (Firm
SonicWALL SSL VPN 3.5: Virtual Assist
 SonicWALL SSL VPN 3.5: Virtual Assist Document Scope This document describes how to use the SonicWALL Virtual Assist add-on for SonicWALL SSL VPN security appliances. This document contains the following
SonicWALL SSL VPN 3.5: Virtual Assist Document Scope This document describes how to use the SonicWALL Virtual Assist add-on for SonicWALL SSL VPN security appliances. This document contains the following
WatchGuard SSL v3.2 Update 1 Release Notes. Introduction. Windows 8 and 64-bit Internet Explorer Support. Supported Devices SSL 100 and 560
 WatchGuard SSL v3.2 Update 1 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 445469 Revision Date 3 April 2014 Introduction WatchGuard is pleased to announce the release of WatchGuard
WatchGuard SSL v3.2 Update 1 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 445469 Revision Date 3 April 2014 Introduction WatchGuard is pleased to announce the release of WatchGuard
ReadyNAS Remote. User Manual. June 2013 202-11078-03. 350 East Plumeria Drive San Jose, CA 95134 USA
 User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
VPN: Virtual Private Network Setup Instructions
 VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
Initial Access and Basic IPv4 Internet Configuration
 Initial Access and Basic IPv4 Internet Configuration This quick start guide provides initial and basic Internet (WAN) configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N
Initial Access and Basic IPv4 Internet Configuration This quick start guide provides initial and basic Internet (WAN) configuration information for the ProSafe Wireless-N 8-Port Gigabit VPN Firewall FVS318N
Network Connect Installation and Usage Guide
 Network Connect Installation and Usage Guide I. Installing the Network Connect Client..2 II. Launching Network Connect from the Desktop.. 9 III. Launching Network Connect Pre-Windows Login 11 IV. Installing
Network Connect Installation and Usage Guide I. Installing the Network Connect Client..2 II. Launching Network Connect from the Desktop.. 9 III. Launching Network Connect Pre-Windows Login 11 IV. Installing
Dell SonicWALL SRA 7.5 Secure Virtual Meeting and Secure Virtual Assist
 Dell SonicWALL SRA 7.5 Secure Virtual Meeting and Secure Virtual Assist Document Scope This document describes how to configure and use the Dell SonicWALL SRA Secure Virtual Meeting feature and the Dell
Dell SonicWALL SRA 7.5 Secure Virtual Meeting and Secure Virtual Assist Document Scope This document describes how to configure and use the Dell SonicWALL SRA Secure Virtual Meeting feature and the Dell
Instructions for Configuring Your Browser Settings and Online Security FAQ s. ios8 Settings for iphone and ipad app
 Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Verizon Remote Access User Guide
 Version 17.12 Last Updated: August 2012 2012 Verizon. All Rights Reserved. The Verizon names and logos and all other names, logos, and slogans identifying Verizon s products and services are trademarks
Version 17.12 Last Updated: August 2012 2012 Verizon. All Rights Reserved. The Verizon names and logos and all other names, logos, and slogans identifying Verizon s products and services are trademarks
For more information refer: UTM - FAQ: What are the basics of SSLVPN setup on Gen5 UTM appliances running SonicOS Enhanced 5.2?
 TM SSL-VPN: How to setup SSL-VPN feature (NetExtender Access)... of 6 1/12/2013 11:46 PM Question/Title UTM SSL-VPN: How to setup SSL-VPN feature (NetExtender Access) on SonicOS Enhanced (SonicOS 5.6 and
TM SSL-VPN: How to setup SSL-VPN feature (NetExtender Access)... of 6 1/12/2013 11:46 PM Question/Title UTM SSL-VPN: How to setup SSL-VPN feature (NetExtender Access) on SonicOS Enhanced (SonicOS 5.6 and
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.7.0 1996-2006 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.7.0 1996-2006 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
EURECOM VPN SSL for students User s guide
 EURECOM VPN SSL for students User s guide Table of Contents Introduction... 2 Login process... 2 Portail main page... 2 Prerequisite... 2 RSA SecurId software token... 3 First usage of RSA SecurID token...
EURECOM VPN SSL for students User s guide Table of Contents Introduction... 2 Login process... 2 Portail main page... 2 Prerequisite... 2 RSA SecurId software token... 3 First usage of RSA SecurID token...
Juniper SSL VPN Notes Page 1
 Juniper SSL VPN Notes Page 1 The Juniper SSL VPN is a full-featured appliance using SSL protocol to allow remote computers to securely access our organization s resources with a standard browser. The types
Juniper SSL VPN Notes Page 1 The Juniper SSL VPN is a full-featured appliance using SSL protocol to allow remote computers to securely access our organization s resources with a standard browser. The types
Two Factor Authentication in SonicOS
 Two Factor Authentication in SonicOS 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage
Two Factor Authentication in SonicOS 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources (DUO)
 Akin Gump Strauss Hauer & Feld LLP Remote Access Resources (DUO) Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2015 Akin Gump Strauss Hauer & Feld LLP Check Point
Akin Gump Strauss Hauer & Feld LLP Remote Access Resources (DUO) Firm Laptop Windows Home PC Mac Computer Apple ipad Android Devices Exit akingump.com 2015 Akin Gump Strauss Hauer & Feld LLP Check Point
Analyzer 7.1 Administrator s Guide
 Analyzer 7.1 Administrator s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage
Analyzer 7.1 Administrator s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage
Access to applications and the network depends on whether or not you are using personal equipment or a Firm-issued laptop or desktop.
 Overview of Help & Tips The new System allows authorized users to log in and access the Firm s network through either Citrix or VPN (also known as Stonegate IPSec VPN). This system incorporates additional
Overview of Help & Tips The new System allows authorized users to log in and access the Firm s network through either Citrix or VPN (also known as Stonegate IPSec VPN). This system incorporates additional
Requirements on terminals and network Telia Secure Remote User, TSRU (version 7.1 R4)
 Requirements on terminals and network Telia Secure Remote User, TSRU (version 7.1 R4) Content Page Introduction 2 Platform support 2 Cross Platform support 2 Web and file browsing 2 Client-side Applets
Requirements on terminals and network Telia Secure Remote User, TSRU (version 7.1 R4) Content Page Introduction 2 Platform support 2 Cross Platform support 2 Web and file browsing 2 Client-side Applets
Clientless SSL VPN End User Set-up
 37 CHAPTER This ections is for the system administrator who sets up Clientless (browser-based) SSL VPN for end users. It summarizes configuration requirements and tasks for the user remote system. It also
37 CHAPTER This ections is for the system administrator who sets up Clientless (browser-based) SSL VPN for end users. It summarizes configuration requirements and tasks for the user remote system. It also
www.novell.com/documentation SSL VPN User Guide Access Manager 3.1 SP5 January 2013
 www.novell.com/documentation SSL VPN User Guide Access Manager 3.1 SP5 January 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation SSL VPN User Guide Access Manager 3.1 SP5 January 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
CommandCenter Secure Gateway User Guide Release 6.0
 CommandCenter Secure Gateway User Guide Release 6.0 Copyright 2014 Raritan, Inc. CC-0X-v6.0-E April 2014 255-80-3100-00 This document contains proprietary information that is protected by copyright. All
CommandCenter Secure Gateway User Guide Release 6.0 Copyright 2014 Raritan, Inc. CC-0X-v6.0-E April 2014 255-80-3100-00 This document contains proprietary information that is protected by copyright. All
Sharp Remote Device Manager (SRDM) Server Software Setup Guide
 Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
Sharp Remote Device Manager (SRDM) Server Software Setup Guide This Guide explains how to install the software which is required in order to use Sharp Remote Device Manager (SRDM). SRDM is a web-based
TechNote. Contents. Introduction. System Requirements. SRA Two-factor Authentication with Quest Defender. Secure Remote Access.
 Secure Remote Access SRA Two-factor Authentication with Quest Defender SonicOS Contents Introduction... 1 System Requirements... 1 Defender Configuration... 2 Dell SonicWALL SRA Configuration... 18 Two-factor
Secure Remote Access SRA Two-factor Authentication with Quest Defender SonicOS Contents Introduction... 1 System Requirements... 1 Defender Configuration... 2 Dell SonicWALL SRA Configuration... 18 Two-factor
UP L18 Enhanced MDM and Updated Email Protection Hands-On Lab
 UP L18 Enhanced MDM and Updated Email Protection Hands-On Lab Description The Symantec App Center platform continues to expand it s offering with new enhanced support for native agent based device management
UP L18 Enhanced MDM and Updated Email Protection Hands-On Lab Description The Symantec App Center platform continues to expand it s offering with new enhanced support for native agent based device management
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Installing Management Applications on VNX for File
 EMC VNX Series Release 8.1 Installing Management Applications on VNX for File P/N 300-015-111 Rev 01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748-9103 1-508-435-1000 www.emc.com Copyright
EMC VNX Series Release 8.1 Installing Management Applications on VNX for File P/N 300-015-111 Rev 01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748-9103 1-508-435-1000 www.emc.com Copyright
Remote Application Server Version 14. Last updated: 25-02-15
 Remote Application Server Version 14 Last updated: 25-02-15 Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise
Remote Application Server Version 14 Last updated: 25-02-15 Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise
Content Filtering Client Policy & Reporting Administrator s Guide
 Content Filtering Client Policy & Reporting Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
Content Filtering Client Policy & Reporting Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
IBM Remote Lab Platform Citrix Setup Guide
 Citrix Setup Guide Version 1.8.2 Trademarks IBM is a registered trademark of International Business Machines Corporation. The following are trademarks of International Business Machines Corporation in
Citrix Setup Guide Version 1.8.2 Trademarks IBM is a registered trademark of International Business Machines Corporation. The following are trademarks of International Business Machines Corporation in
Citrix Access Gateway Enterprise Edition Citrix Access Gateway Plugin for Windows User Guide. Citrix Access Gateway 9.0, Enterprise Edition
 Citrix Access Gateway Enterprise Edition Citrix Access Gateway Plugin for Windows User Guide Citrix Access Gateway 9.0, Enterprise Edition Copyright and Trademark Notice Use of the product documented in
Citrix Access Gateway Enterprise Edition Citrix Access Gateway Plugin for Windows User Guide Citrix Access Gateway 9.0, Enterprise Edition Copyright and Trademark Notice Use of the product documented in
Requirements on terminals and network Telia Secure Remote User, TSRU (version 7.3 R6)
 Requirements on terminals and network Telia Secure Remote User, TSRU (version 7.3 R6) Content Page Introduction 2 Platform support 2 Cross Platform support 2 Web and file browsing 2 Client-side Applets
Requirements on terminals and network Telia Secure Remote User, TSRU (version 7.3 R6) Content Page Introduction 2 Platform support 2 Cross Platform support 2 Web and file browsing 2 Client-side Applets
Allianz Global Investors Remote Access Guide
 Allianz Global Investors Remote Access Guide Web Address: http://remote.allianzgi-us.com/ Page 1 of 34 pages Please contact the Service Desk at Table of Contents 1. Introduction to the Remote Access Page
Allianz Global Investors Remote Access Guide Web Address: http://remote.allianzgi-us.com/ Page 1 of 34 pages Please contact the Service Desk at Table of Contents 1. Introduction to the Remote Access Page
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client
 SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
SHC Client Remote Access User Guide for Citrix & F5 VPN Edge Client Version 1.1 1/15/2013 This remote access end user reference guide provides an overview of how to install Citrix receiver (a required
DIGIPASS Authentication for Sonicwall Aventail SSL VPN
 DIGIPASS Authentication for Sonicwall Aventail SSL VPN With VASCO IDENTIKEY Server 3.0 Integration Guideline 2009 Vasco Data Security. All rights reserved. PAGE 1 OF 52 Disclaimer Disclaimer of Warranties
DIGIPASS Authentication for Sonicwall Aventail SSL VPN With VASCO IDENTIKEY Server 3.0 Integration Guideline 2009 Vasco Data Security. All rights reserved. PAGE 1 OF 52 Disclaimer Disclaimer of Warranties
DIGIPASS Authentication for SonicWALL SSL-VPN
 DIGIPASS Authentication for SonicWALL SSL-VPN With VACMAN Middleware 3.0 2006 VASCO Data Security. All rights reserved. Page 1 of 53 Integration Guideline Disclaimer Disclaimer of Warranties and Limitations
DIGIPASS Authentication for SonicWALL SSL-VPN With VACMAN Middleware 3.0 2006 VASCO Data Security. All rights reserved. Page 1 of 53 Integration Guideline Disclaimer Disclaimer of Warranties and Limitations
Office of Information Technology Connecting to Microsoft Exchange User Guide
 OVERVIEW The Office of Information Technology is migrating its messaging infrastructure from Microsoft Exchange 2003 to Microsoft Exchange 2010. Moving to the latest technology will provide many enhancements
OVERVIEW The Office of Information Technology is migrating its messaging infrastructure from Microsoft Exchange 2003 to Microsoft Exchange 2010. Moving to the latest technology will provide many enhancements
ATTENTION: End users should take note that Main Line Health has not verified within a Citrix
 Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
Access to Webmail services via a Non Trust Computer
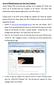 Access to Webmail services via a Non Trust Computer Aintree Outlook Web Access has been provided via the AppGate SSL Portal, this service can be accessed from any computer on the Internet. Two factor SMS
Access to Webmail services via a Non Trust Computer Aintree Outlook Web Access has been provided via the AppGate SSL Portal, this service can be accessed from any computer on the Internet. Two factor SMS
A Guide to New Features in Propalms OneGate 4.0
 A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
A Guide to New Features in Propalms OneGate 4.0 Propalms Ltd. Published April 2013 Overview This document covers the new features, enhancements and changes introduced in Propalms OneGate 4.0 Server (previously
Secure Access Using VPN
 Secure Access Using VPN WHAT IS CISCO SSL VPN? Cisco is the brand name of the VPN appliance (hardware). The SSL VPN stands for Secure Sockets Layer Virtual Private Network. SSL VPN is a service that allows
Secure Access Using VPN WHAT IS CISCO SSL VPN? Cisco is the brand name of the VPN appliance (hardware). The SSL VPN stands for Secure Sockets Layer Virtual Private Network. SSL VPN is a service that allows
Two-Factor Authentication
 Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
New Online Banking Guide for FIRST time Login
 New Online Banking Guide for FIRST time Login Step 1: Login Enter your existing Online Banking User ID and Password. Click Log-In. Step 2: Accepting terms and Conditions to Proceed Click on See the terms
New Online Banking Guide for FIRST time Login Step 1: Login Enter your existing Online Banking User ID and Password. Click Log-In. Step 2: Accepting terms and Conditions to Proceed Click on See the terms
Net 2. NetApp Electronic Library. User Guide for Net 2 Client Version 6.0a
 Net 2 NetApp Electronic Library User Guide for Net 2 Client Version 6.0a Table of Contents 1 INTRODUCTION AND KEY FEATURES... 3 SOME OF THE KEY FEATURES INCLUDE:... 3 INSTALLATION PREREQUISITES:... 3 2
Net 2 NetApp Electronic Library User Guide for Net 2 Client Version 6.0a Table of Contents 1 INTRODUCTION AND KEY FEATURES... 3 SOME OF THE KEY FEATURES INCLUDE:... 3 INSTALLATION PREREQUISITES:... 3 2
Remote Application Server Version 14. Last updated: 06-02-15
 Remote Application Server Version 14 Last updated: 06-02-15 Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise
Remote Application Server Version 14 Last updated: 06-02-15 Information in this document is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise
Installation and Setup Guide
 Installation and Setup Guide Contents 1. Introduction... 1 2. Before You Install... 3 3. Server Installation... 6 4. Configuring Print Audit Secure... 11 5. Licensing... 16 6. Printer Manager... 17 7.
Installation and Setup Guide Contents 1. Introduction... 1 2. Before You Install... 3 3. Server Installation... 6 4. Configuring Print Audit Secure... 11 5. Licensing... 16 6. Printer Manager... 17 7.
CTERA Agent for Linux
 User Guide CTERA Agent for Linux September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
User Guide CTERA Agent for Linux September 2013 Version 4.0 Copyright 2009-2013 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
Installation Guide for Pulse on Windows Server 2012
 MadCap Software Installation Guide for Pulse on Windows Server 2012 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2012 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
Users Guide. Wyse PocketCloud TM. Issue: 041911 PN: 883930-01 Rev. J
 Users Guide Wyse PocketCloud TM Issue: 041911 PN: 883930-01 Rev. J Copyright Notices 2011, Wyse Technology Inc. All rights reserved. This manual and the software and firmware described in it are copyrighted.
Users Guide Wyse PocketCloud TM Issue: 041911 PN: 883930-01 Rev. J Copyright Notices 2011, Wyse Technology Inc. All rights reserved. This manual and the software and firmware described in it are copyrighted.
Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Investment Management System. Connectivity Guide. IMS Connectivity Guide Page 1 of 11
 Investment Management System Connectivity Guide IMS Connectivity Guide Page 1 of 11 1. Introduction This document details the necessary steps and procedures required for organisations to access the Homes
Investment Management System Connectivity Guide IMS Connectivity Guide Page 1 of 11 1. Introduction This document details the necessary steps and procedures required for organisations to access the Homes
Campus VPN. Version 1.0 September 22, 2008
 Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
Campus VPN Version 1.0 September 22, 2008 University of North Texas 1 9/22/2008 Introduction This is a guide on the different ways to connect to the University of North Texas Campus VPN. There are several
CTERA Agent for Mac OS-X
 User Guide CTERA Agent for Mac OS-X June 2014 Version 4.1 Copyright 2009-2014 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
User Guide CTERA Agent for Mac OS-X June 2014 Version 4.1 Copyright 2009-2014 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
Technology Services Group Procedures. IH Anywhere guide. 0 P a g e
 VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
XenClient Enterprise Synchronizer Installation Guide
 XenClient Enterprise Synchronizer Installation Guide Version 5.1.0 March 26, 2014 Table of Contents About this Guide...3 Hardware, Software and Browser Requirements...3 BIOS Settings...4 Adding Hyper-V
XenClient Enterprise Synchronizer Installation Guide Version 5.1.0 March 26, 2014 Table of Contents About this Guide...3 Hardware, Software and Browser Requirements...3 BIOS Settings...4 Adding Hyper-V
mystanwell.com Installing Citrix Client Software Information and Business Systems
 mystanwell.com Installing Citrix Client Software Information and Business Systems Doc No: 020/12 Revision No: Revision Date: Page: 1 of 16 Contents Overview... 3 1. Microsoft Internet Explorer... 3 2.
mystanwell.com Installing Citrix Client Software Information and Business Systems Doc No: 020/12 Revision No: Revision Date: Page: 1 of 16 Contents Overview... 3 1. Microsoft Internet Explorer... 3 2.
Installation Guide for Pulse on Windows Server 2008R2
 MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
Dartmouth College Technical Support Document for Kronos PC version
 Dartmouth College Technical Support Document for Kronos PC version Contents How to Save the Kronos URL as a Favorite or Bookmark... 2 Internet Explorer... 2 Firefox... 4 Possible Problems When Logging
Dartmouth College Technical Support Document for Kronos PC version Contents How to Save the Kronos URL as a Favorite or Bookmark... 2 Internet Explorer... 2 Firefox... 4 Possible Problems When Logging
REMOTE ACCESS USER GUIDE
 REMOTE ACCESS USER GUIDE Document Released by the IT Department [21/11/2013] Content Summary 1. Remote Access User Guide Cover Page 2. Content Summary 3. Website/Portal Accessing 4. Method of Accessing
REMOTE ACCESS USER GUIDE Document Released by the IT Department [21/11/2013] Content Summary 1. Remote Access User Guide Cover Page 2. Content Summary 3. Website/Portal Accessing 4. Method of Accessing
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
How to use Mints@Home
 How to use Mints@Home Citrix Remote Access gives Mints users the ability to access University Of Cambridge and MINTS resources from any computer, anywhere in the world,. The service requires a high-speed
How to use Mints@Home Citrix Remote Access gives Mints users the ability to access University Of Cambridge and MINTS resources from any computer, anywhere in the world,. The service requires a high-speed
SRA 6.0 Administrator s Guide
 SRA 6.0 Administrator s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage to
SRA 6.0 Administrator s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION indicates potential damage to
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
1. Accessing the LONZA network from a private PC or Internet Café
 Using SSL VPN from non Lonza PCs 1. Accessing the LONZA network from a private PC or Internet Café To work at home with your private PC or from an Internet Café, you can use your browser to connect to
Using SSL VPN from non Lonza PCs 1. Accessing the LONZA network from a private PC or Internet Café To work at home with your private PC or from an Internet Café, you can use your browser to connect to
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access
 Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
Parallels Panel. Parallels Small Business Panel 10.2: User's Guide. Revision 1.0
 Parallels Panel Parallels Small Business Panel 10.2: User's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax:
Parallels Panel Parallels Small Business Panel 10.2: User's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax:
Using Access.Centegra.Com (Physician Access) Secure Remote Access from the Internet
 System Requirements These are the minimum requirements necessary to ensure the proper operation of Centegra Health System s Access.Centegra.Com. Administrative level access to the PC or other device used
System Requirements These are the minimum requirements necessary to ensure the proper operation of Centegra Health System s Access.Centegra.Com. Administrative level access to the PC or other device used
McAfee SMC Installation Guide 5.7. Security Management Center
 McAfee SMC Installation Guide 5.7 Security Management Center Legal Information The use of the products described in these materials is subject to the then current end-user license agreement, which can
McAfee SMC Installation Guide 5.7 Security Management Center Legal Information The use of the products described in these materials is subject to the then current end-user license agreement, which can
VMware Identity Manager Administration
 VMware Identity Manager Administration VMware Identity Manager 2.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware Identity Manager Administration VMware Identity Manager 2.4 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
SingTel VPN as a Service. Quick Start Guide
 SingTel VPN as a Service Quick Start Guide Document Control # Date of Release Version # 1 25 April 2014 PT_SN20_1.0 2 3 4 5 6 Page Affected Remarks 2/33 Table of Contents 1. SingTel VPN as a Service Administration...
SingTel VPN as a Service Quick Start Guide Document Control # Date of Release Version # 1 25 April 2014 PT_SN20_1.0 2 3 4 5 6 Page Affected Remarks 2/33 Table of Contents 1. SingTel VPN as a Service Administration...
Connecting Remotely via the Citrix Access Gateway (CAG)
 2011 Connecting Remotely via the Citrix Access Gateway (CAG) Version 2.0 *** The CAG is intended for users with OE equipment only. Users with GFE must still use RESCUE as their VPN solution. *** All VISN
2011 Connecting Remotely via the Citrix Access Gateway (CAG) Version 2.0 *** The CAG is intended for users with OE equipment only. Users with GFE must still use RESCUE as their VPN solution. *** All VISN
Sophos Mobile Control Installation guide. Product version: 3.5
 Sophos Mobile Control Installation guide Product version: 3.5 Document date: July 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...10 4 External
Sophos Mobile Control Installation guide Product version: 3.5 Document date: July 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...10 4 External
Remote VPN: Remote access for personal devices
 Remote VPN: Remote access for personal devices Documentation Team. March 2013. About Remote VPN Remote VPN 1 provides staff and students with secure, authenticated remote access to personal and shared
Remote VPN: Remote access for personal devices Documentation Team. March 2013. About Remote VPN Remote VPN 1 provides staff and students with secure, authenticated remote access to personal and shared
Remote Access Services Microsoft Windows - Installation Guide
 Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
Sophos UTM. Remote Access via SSL Configuring Remote Client
 Sophos UTM Remote Access via SSL Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
Sophos UTM Remote Access via SSL Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
