A Semantic Approach to the Discovery of Workflow Activity Patterns in Event Logs. Diogo R. Ferreira. Lucinéia H. Thom
|
|
|
- Frederick Ramsey
- 8 years ago
- Views:
Transcription
1 This is an unedited version of an article published in IJBPIM, Vol. 6, No. 1, A Semantic Approach to the Discovery of Workflow Activity Patterns in Event Logs Diogo R. Ferreira IST Technical University of Lisbon, Avenida Prof. Dr. Cavaco Silva, Porto Salvo, Portugal diogo.ferreira@ist.utl.pt Lucinéia H. Thom Institute of Informatics, Universidade Federal do Rio Grande do Sul, Porto Alegre, RS, Brazil lucineia@inf.ufrgs.br Abstract: Workflow activity patterns represent a set of recurrent behaviours that can be found in a wide range of business processes. In this paper we address the problem of determining the presence of these patterns in process models. This is usually done manually by the analyst, who inspects the model and interprets its elements in terms of the semantics of those patterns. Here, we present an approach to perform this discovery based on the event log created during process execution. The approach makes use of an ontology and the semantic annotation of the event log in order to discover the patterns automatically by means of semantic reasoning. We illustrate the application of the proposed approach in a case study involving a purchase process implemented in a commercial workflow system. Keywords: Business Process Modelling, Workflow Activity Patterns, Process Mining, Ontology Engineering, Semantic Reasoning Reference to this paper should be made as follows: Ferreira, D.R. and Thom, L.H. (2012) A Semantic Approach to the Discovery of Workflow Activity Patterns in Event Logs, Int. J. Business Process Integration and Management, Vol. X, Nos. Y, pp Biographical notes: Diogo R. Ferreira is professor of information systems at the Technical University of Lisbon, and he is an active researcher in the field of business process management, particularly in the area of process mining. Lucinéia H. Thom is a post-doc researcher at the Institute of Informatics of the Federal University of Rio Grande do Sul, Brazil. Her research interests are in the area of business process management and information technology for healthcare and homecare. 1 Introduction Business processes can be seen as being composed of patterns, which have been thoroughly studied in the literature (van der Aalst et al., 2003a; ter Hofstede and Dietz, 2003). There have been also attempts at explaining business processes by means of a single pattern, such action-workflow (Medina-Mora et al., 1992) or a transaction pattern (Dietz, 2006). In any case, these patterns fulfil a double role of facilitating the understanding of processes on one hand, and on the other hand providing the building blocks from which new processes can be designed. Most of the previous work has therefore focused on identifying these building blocks and deciding which of them are most appropriate to capture common structures in business processes. Here we take a different viewpoint of assuming that these patterns have been already defined, and instead we focus on the problem of determining whether a given set of patterns is present in a given business process. In particular, we are interested in recognising the presence of patterns by making use of the semantics of the business process, i.e. we are looking not only at the structural behaviour of business processes, but especially at the meaning of the activities contained in a process. For example, if we know that a certain activity can be interpreted as an approval step, then it is possible that the process contains an approval pattern. We are dealing with the so-called Workflow Activity Patterns (WAPs) (Thom et al., 2009) which represent business functions that typically occur in every business process, such as activity execution; decision making; Copyright c 2012 Inderscience Enterprises Ltd.
2 2 D.R. Ferreira and L.H. Thom notification; approval; etc. These business functions cannot be identified solely by looking at the structure of a process; it is necessary to understand the purpose of each activity in order to decide whether it corresponds to a known business function. In addition, we cannot say that the process contains an approval pattern just because it has an approval step; all of the required elements of the approval pattern must be present in order to consider that the process contains such pattern. Section 2 provides a summary of these patterns. Discovering workflow activity patterns in business processes is typically done manually by the analyst, working over diagrams of the process model. Such analysis is non-trivial since the meaning and purpose of any given activity can be given different interpretations. Also, in addition to semantics, the analyst must be able to correctly interpret the control-flow in the model to ensure that the observed behaviour corresponds to the structure of the candidate patterns. Overall, this becomes a difficult and error-prone task. Our goal is to provide automated means to assist the analyst in the discovery of WAPs. Since, to a large extent, such discovery is based on semantics, we turn to an ontologybased approach, as described in Section 3. In addition, to facilitate the verification of the sequential behaviour in the control-flow, we make use of the event log generated during process execution, rather than original the process model, as explained in Section 4. Throughout the presentation we use the example of a travel booking process introduced in (Thom et al., 2009). An experimental evaluation of the proposed approach in a more realistic process is provided in Section 5. By describing the principles, implementation and applications of the proposed approach, the reader will get a sense for the potential of using ontologies and automated reasoning to address challenging problems in the area of Business Process Management, especially those which, like the problem addressed here, rely on semantics to a large extent. 2 Workflow Activity Patterns Workflow activity patterns (WAPs) (Thom et al., 2009) are common structures that can be found in a variety of business processes. These structures involve control-flow constructs as well as interactions between participants, and also the semantics of the activities being performed. Our starting point will be the seven WAPs as defined in (Thom et al., 2009). These comprise the following behaviors: 1. Approval: An object (e.g. a document) has to be approved by some organisational role. A requester sends the approval request to a reviewer, who performs the approval and returns a result. 2. Question-Answer: When performing a process, an actor might have a question before working on the process or on a particular activity. This pattern allows to formulate such question, to identify an organisational role who is able to answer it, to send the question to the respective actor filling this role, and to wait for response. 3. Unidirectional Performative: A sender requests the execution of a particular activity from a receiver (e.g., a human or a software agent) involved in the process. The sender continues execution of his part of the process immediately after having sent the request. 4. Bidirectional Performative: A sender requests the execution of a particular activity from another role (e.g., a human or a software agent) involved in the process. The sender waits for a notification from the receiver that the requested activity has been performed. 5. Notification: The status or result of an activity execution is communicated to one or more process participants. 6. Information Request: An actor requests certain information from a process participant. He continues process execution after having received the desired information. 7. Decision: During process enactment, the performance of an activity is requested. Depending on the result of the requested activity, the process continues execution with one or several branches. This pattern allows the inclusion of a decision activity which connects to different subsequent execution branches (each of them associated with a specific transition condition). Exactly those branches whose transition condition evaluates to true are selected for execution. Figure 1 provides a summary of these workflow activity patterns in graphical form. The patterns are composed of certain elements, namely signals (send and receive), activities (e.g. Perform approval ) and messages (e.g. Approval request ). For example, WAP1 begins by a send signal with an approval request message; then there is a receive signal for that same message; after, an activity to perform the approval; and finally the exchange of the approval result by another pair of send and receive signals. For simplicity, we have deliberately omitted some elements from these patterns. For example, WAP2 as originally defined in (Thom et al., 2009) contains additional activities before Send question, namely an activity Describe question and another activity Identify role habilities. These elements could be used, in effect, to distinguish WAP2 from other patterns. By omitting some elements, the patterns become very similar in terms of structure, as can be seen in Figure 1. However, there are some clear differences in purpose and semantics between them, and it is precisely these semantics, in addition to structure, that we will use to discover them in business processes.
3 A Semantic Approach to the Discovery of WAPs in Event Logs 3 WAP1: Approval WAP2: Question-Answer WAP3: Unidirectional Performative WAP4: Bidirectional Performative WAP5: Notification WAP6: Information Request WAP7: Decision Figure 1 Simplified versions of the seven WAPs defined in (Thom et al., 2009)
4 4 D.R. Ferreira and L.H. Thom 3 Semantics of Model Elements Figure 3 shows an example of a travel booking process that has been modelled using the same kind of elements that were used to define the seven workflow activity patterns. However, the process makes use of its own vocabulary, which is specific to this application domain. Our goal is to understand the semantics of each activity and to reason about these elements in order to determine which patterns are present in this process. Note that Figure 3 already includes an indication of the patterns that were found manually by an analyst. Our goal is to discover these patterns automatically, provided that the model elements have been appropriately annotated. 3.1 Defining the WAP Ontology In order to reason about concrete examples such as the one depicted in Figure 3, we need an ontology that provides a description of the patterns to be discovered, and we need to annotate the elements in the given process with the concepts defined in that ontology. For example, one should understand that the shape Send request for booking in Figure 3 is in effect a send signal with an activity request message as in WAP4; one should also realise that Authorize trip corresponds to a Perform approval activity as in WAP1; and so on. In order to do this, we introduce an ontology to specify these pattern elements. Figure 2 shows the class hierarchy for the WAP ontology that has been developed in this work, as it appears in Protégé 1. Basically, there are two toplevel classes, Element and Pattern, with Element being the superclass for the various pattern elements, and Pattern being the superclass for the definitions of the several WAPs. The rationale for this ontology can be summarized as follows: Each Pattern is defined as containing certain elements of the classes Signal and Activity. For this purpose, we define the object property haselement with domain Pattern and range Element. Example: PatternApproval haselement ActivityPerformApproval. Each Signal has a certain kind of Message and for this purpose we define the object property hasmessage with domain Signal and range Message. Example: PatternApproval haselement (SignalSend and (hasmessage MessageApprovalRequest)). Each subclass of Pattern is defined by an equivalent class expression, which specifies the elements that the pattern contains. For example, the definition for WAP1 can be written as follows: PatternApproval Pattern and haselement some (SignalSend and hasmessage some MessageApprovalRequest) and haselement some (SignalReceive and hasmessage some MessageApprovalRequest) and haselement some ActivityPerformApproval and haselement some (SignalSend and hasmessage some MessageApprovalResult) and haselement some (SignalReceive and hasmessage some MessageApprovalResult) Figure 2 Class hierarchy for the WAP ontology. In general, a process may contain many elements, with only some of them matching the elements of a given pattern. Therefore, we make use of the keyword some, meaning that it is necessary for a pattern/signal to have at least one element/message of that kind, but possibly more. The definitions for the remaining patterns are analogous, and they are omitted for brevity; those definitions are similar to the one above, but make use of different elements. In particular, the definitions for WAP3 and WAP5 are shorter, while WAP7 has an additional activity. We should mention that this is not the first time that an ontology for workflow activity patterns has been devised. In (Thom et al., 2008) the authors make use of a WAP ontology for the purpose of supporting process modelling; in this case the ontology describes the patterns and the relationships between them in order 1 Protégé is available at:
5 A Semantic Approach to the Discovery of WAPs in Event Logs 5 Figure 3 Travel booking example, adapted from (Thom et al., 2009)
6 6 D.R. Ferreira and L.H. Thom to produce recommendations about the possible use of other patterns in the same model; ultimately, it is the user who decides whether a given pattern should be inserted in the model. Here, we have built a different ontology for the specific purpose of being able to infer which patterns are present in a given process model; we have therefore focused more on specifying the elements of these patterns, and on how these patterns are defined in terms of the elements they contain. 3.2 Semantic Annotation of Model Elements While the ontology above defines the classes, a given process model will contain the elements that can be seen as individuals of those classes. For example, the first shape Send request for booking in Figure 3 corresponds to two elements: a signal and a message. The signal is an individual of SignalSend and the message is an individual of MessageActivityRequest. We have therefore: Element1 : SignalSend Element2 : MessageActivityRequest Element1 hasmessage Element2 As another example, the shape Authorize trip is an individual of ActivityPerformApproval, so we could have: Element3 : ActivityPerformApproval Now, the whole process is represented as an individual of Pattern so that from the above we would have: Process1 : Pattern Process1 haselement Element1 Process1 haselement Element3 Note that there is no need to assert Process1 haselement Element2 since Element2 is a message and it is associated with Element1 via the haselement property. Once the shapes in the model have been annotated with the corresponding classes from the ontology, creating these individuals is straightforward and can be done automatically. Then a reasoner can be invoked to infer the patterns that the process contains. The critical point here is precisely in correctly annotating the elements, e.g. knowing that Send request for booking corresponds to two classes (SignalSend and MessageActivityRequest) and Authorize trip corresponds to ActivityPerformApproval. This annotation must be done manually by the analyst; in terms of effort, it is similar to other approaches that involve semantic annotation of business processes, e.g. (Born et al., 2007; Zouggar et al., 2008; Filipowska et al., 2009). Still, the annotation is made difficult by the fact that the shapes in a process model make use of a domain-specific vocabulary and are often labelled in different ways. To facilitate this task, it would be desirable to have the shapes in a process model labelled in a consistent way, such as using verb-object style, as recommended by (Mendling et al., 2010). For the process in Figure 3, we would have: Send request for booking :: SignalSend MessageActivityRequest Receive request for booking :: SignalReceive MessageActivityRequest Verify if there are available flights and book the trip :: ActivityExecute Send notification of flight booking :: SignalSend MessageActivityResult Receive notification of flight booking :: SignalReceive MessageActivityResult Send notification of no available flights :: SignalSend MessageNotify Receive notification of no available flights :: SignalReceive MessageNotify Submit booking for approval :: SignalSend MessageApprovalRequest Receive booking for approval :: SignalReceive MessageApprovalRequest Authorize trip :: ActivityPerformApproval Send notification with approval result :: SignalSend MessageApprovalResult Receive result of approval :: SignalReceive MessageApprovalResult Send notification trip not authorized :: SignalSend MessageNotify Receive notification :: SignalReceive MessageNotify Send request to buy tickets :: SignalSend MessageActivityRequest Receive request to buy tickets :: SignalReceive MessageActivityRequest Buy the tickets :: ActivityExecute Send notification of activity completed :: SignalSend MessageActivityResult Receive electronic ticket :: SignalReceive MessageActivityResult Send electronic ticket to requestor :: SignalSend MessageNotify Receive ticket :: SignalReceive MessageNotify
7 A Semantic Approach to the Discovery of WAPs in Event Logs 7 Provided with this annotation, the individuals and their properties can be generated automatically. For each class in the annotation, a new individual is created from that class. If the first class is a Signal and the second class is a Message, we add the property hasmessage which relates those two individuals. Finally, we create an individual of Pattern to represent the whole process, and we associate all signals and activities to the process via the property haselement. 3.3 Pattern Discovery through Reasoning Through the use of reasoning, it is possible to obtain additional statements that can be inferred from the available classes and individuals. The type of inference we will be most interested in is class membership. As explained above, each WAP is defined by an equivalent class expression that specifies the elements that the pattern contains. If a process has all the elements that satisfy a given pattern expression, then the process will become a member of that class (a subclass of Pattern). In general, a process may end up being a member of several classes, which means that one can find in that process all the elements required by those patterns. As an example, let us consider the following excerpt of the travel booking process: Submit booking for approval :: SignalSend MessageApprovalRequest Receive booking for approval :: SignalReceive MessageApprovalRequest Authorize trip :: ActivityPerformApproval Send notification with approval result :: SignalSend MessageApprovalResult Receive result of approval :: SignalReceive MessageApprovalResult These will result in the following individuals being created: Element1 : SignalSend Element2 : MessageApprovalRequest Element1 hasmessage Element2 Element3 : SignalReceive Element4 : MessageApprovalRequest Element3 hasmessage Element4 Element5 : ActivityPerformApproval Element6 : SignalSend Element7 : MessageApprovalResult Element6 hasmessage Element7 Element8 : SignalReceive Element9 : MessageApprovalResult Element8 hasmessage Element9 Process1 : Pattern Process1 haselement Element1 Process1 haselement Element3 Process1 haselement Element5 Process1 haselement Element6 Process1 haselement Element8 From the WAP ontology and the individuals above, a semantic reasoner is able to infer the following statements: Process1 rdf:type Thing Process1 rdf:type PatternApproval The process is a member of Thing since it is a Pattern and a Pattern is a subclass of Thing. The reasoner is also able to infer that the process is a member of PatternApproval since, by the elements it contains, it satisfies the expression for that class. It should be noted that even before the individuals are created, invoking a reasoner on the WAP ontology produces the following statements: PatternBidirectionalPerformative rdfs:subclassof PatternUnidirectionalPerformative PatternDecision rdfs:subclassof PatternBidirectionalPerformative This can be easily understood by inspection of Figure 1. In fact, WAP4 contains all the elements of WAP3 and therefore WAP4 satisfies the definition of WAP3. The same happens with WAP7 and WAP4; WAP7 extends WAP4 and therefore it fits the definition of WAP4. This means that any process that contains WAP4 will also be listed as containing WAP3, and any process containing WAP7 will contain WAP4, and therefore WAP3 as well. 3.4 Retrieving the Patterns with SPARQL From the WAP ontology and the individuals created from a given process, a reasoner is able to produce a large number of statements. Not all of these statements will be equally interesting. For example, knowing that a process is a Thing is trivial; also, if a process contains both WAP3 and WAP4, the most interesting statement is that it contains WAP4, since we know that any process that contains WAP4 also contains WAP3. In general, we are interested in class memberships that are closer to the leafs of the class hierarchy, as this represents more specific knowledge about the process and the patterns it contains. In order to retrieve the patterns that a process (e.g. Process1) contains, we use the following SPARQL query: 1: PREFIX wap:... 2: PREFIX rdf:... 3: PREFIX rdfs:...
8 8 D.R. Ferreira and L.H. Thom 4: SELECT?pattern WHERE {wap:process1 rdf:type?pattern. 5:?pattern rdfs:subclassof wap:pattern. 6: FILTER (?pattern!= wap:pattern). 7: OPTIONAL {?pattern2 rdfs:subclassof?pattern. 8: wap:process1 rdf:type?pattern2 } 9: FILTER (!bound(?pattern2)) } The query determines all class memberships of Process1 (line 4) where the class must be a subclass of Pattern (line 5). According to the OWL standard, a class is by definition a subclass of itself, so Pattern will also appear in the results; we exclude this case with the filter expression in line 6. In lines 7-9 we exclude the case when the result indicates that the process contains both a pattern and a subclass of that pattern (as in WAP3 and WAP4). Lines 7-8 check if there is a subclass (e.g. WAP4) of the pattern (e.g. WAP3) that the process also contains. If so, then we are interested in the subclass (WAP4) rather than in the original class (WAP3). Line 9 excludes the result when there is such case. Running this query on the travel booking example produces the following results: Process1 rdfs:subclassof PatternApproval Process1 rdfs:subclassof PatternBidirectionalPerformative Process1 rdfs:subclassof PatternNotification Note that PatternUnidirectionalPerformative is excluded by lines 7-9 since PatternBidirectionalPerformative is a subclass of PatternUnidirectionalPerformative. These results indicate that the process contains enough elements to satisfy the definition of three different patterns: WAP1, WAP4 and WAP5. However, when comparing these results with Figure 3, we note the absence of WAP7 and WAP3. This can be explained as follows: With regard to WAP7, this pattern is not detected since the process does not include an ActivityMakeDecision. The analyst considered that such activity is implicit in the diamond shape, and did not include it in the annotation. With regard to WAP3, that part of the process in Figure 3 is inferred as an instance of WAP5 rather than WAP3. This is because the message has been annotated as MessageNotify. However, it appears that the analyst originally thought that it was a MessageActivityRequest. 4 Capturing the Sequence of Events In the previous section we have shown how it is possible to discover, through the use of reasoning, the presence WAPs in a process model, provided that a suitable annotation of the model elements is available. In this section we address the problem of checking not only that the pattern elements are present, but also that they are present in the correct order, as specified in the original WAPs of Figure 1. For this purpose, and rather than analysing the control-flow of the process model, we resort to the sequence of events recorded during process execution. The use of event logs is very common in the area of process mining (van der Aalst et al., 2003b), for example to discover control-flow models (van der Aalst et al., 2004) and social networks (van der Aalst et al., 2005), or to study conformance (Rozinat and van der Aalst, 2008), among other issues. Here we use the event log as a means to retrieve the sequential behaviour of the process. 4.1 Translating the Event Log An event log is a list of recorded events, where each event typically contains a reference to an activity (task id) that has been performed, the process instance (case id) that the activity belongs to, the user (originator) who performed the activity, and the time and date (timestamp) of when the activity was completed (van der Aalst et al., 2007). Such event log is usually retrieved from the execution of a business process on a workflow system, but it can also be obtained by simulation of the given process (Medeiros and Günther, 2005). For our purpose, the event log needs to contain only the case id and task id, in chronological order. The sequence of tasks executed within a process instance, i.e. the sequence of task-ids associated with the same caseid, is called a trace (van der Aalst et al., 2004). A sample trace of the process in Figure 3 is as follows: Send request for booking Receive request for booking Verify if there are available flights and book the trip Send notification of flight booking Receive notification of flight booking Send notification of no available flights Receive notification of no available flights Provided with the mapping of Section 3.2, this trace can be translated into the following sequence: SignalSend MessageActivityRequest SignalReceive MessageActivityRequest ActivityExecute SignalSend MessageActivityResult SignalReceive MessageActivityResult SignalSend MessageNotify SignalReceive MessageNotify Since the control-flow in Figure 3 admits only 3 possible paths, there are a limited number of possible traces (the parallel execution of the branches beginning with Send notification trip not authorized may generate some additional traces). These traces can be translated in a similar way as above, and this translation can be done automatically for all traces based on the provided annotation of the model elements. For the trace above, the approach described in the previous section would detect the presence of WAP4 and
9 A Semantic Approach to the Discovery of WAPs in Event Logs 9 WAP5 regardless of the order in which the elements appear in the trace. However, these patterns should only be detected if their elements appear in the correct order. For this purpose, we introduce the notion of an order relation, to be included in the WAP ontology. 4.2 Adding an Order Relation In the trace above, the events that belong to the same WAP were recorded not only in sequence, but also consecutively in the event log. In practice, this may not be the case, as the events may become interspersed with other activities, namely those originated by parallel branches. The order relation for pattern elements should therefore make use of the notion of weak (rather than strict) order. The notion of weak (vs. strict) order has already been used extensively to capture the behavioural profiles of business processes from the sequence of events recorded in an event log (Weidlich et al., 2011). In the present context, the definition of weak order applies to any pair of activities that follow one another, not necessarily in consecutive order. Formally, two activities a i and a j in a trace σ = a 1,..., a n are in weak order if and only if 1 i < j n. To express this relation, we introduce the object property followedby with domain Element and range Element, and we redefine the class expressions for the WAPs using this property. The definition for WAP1 becomes: PatternApproval Pattern and haselement some (SignalSend and hasmessage some MessageApprovalRequest and followedby some (SignalReceive and hasmessage some MessageApprovalRequest and followedby some (ActivityPerformApproval and followedby some (SignalSend and hasmessage some MessageApprovalResult and followedby some (SignalReceive and hasmessage some MessageApprovalResult ) ) ) ) ) The definitions for the remaining patterns are analogous. It should be noted that the property followedby is transitive, so that if A followedby B and B followedby C hold, then it can be inferred that A followedby C holds as well. Such transitivity facilitates the specification of the order relations in the event log, since it is necessary to specify only the order relation between consecutive events for the reasoner to infer the order relation between all pairs of events. 4.3 Creating the Individuals As before, in Section 3.3, the individuals can be created automatically from the event log. For example, the trace in Section 4.1 will result in the following individuals being created: Element01 : SignalSend Element02 : MessageApprovalRequest Element01 hasmessage Element02 Element03 : SignalReceive Element04 : MessageApprovalRequest Element03 hasmessage Element04 Element05 : ActivityPerformApproval Element06 : SignalSend Element07 : MessageApprovalResult Element06 hasmessage Element07 Element08 : SignalReceive Element09 : MessageApprovalResult Element08 hasmessage Element09 Element10 : SignalSend Element11 : MessageNotify Element10 hasmessage Element11 Element12 : SignalReceive Element13 : MessageNotify Element12 hasmessage Element13 Trace1 : Pattern Trace1 haselement Element01 Trace1 haselement Element03 Trace1 haselement Element05 Trace1 haselement Element06 Trace1 haselement Element08 Trace1 haselement Element010 Trace1 haselement Element012 Element01 followedby Element03 Element03 followedby Element05 Element05 followedby Element06 Element06 followedby Element08 Element08 followedby Element10 Element10 followedby Element12 Due to the transitivity of the property followedby, all order relations between non-consecutive elements will be inferred. Also, from these statements and the new class expressions, as defined in Section 4.2, the reasoner is able to infer: Trace1 rdfs:subclassof PatternBidirectionalPerformative Trace1 rdfs:subclassof PatternNotification Similar results can be obtained for other traces with additional patterns. The SPARQL query of Section 3.4 needs no modification other than replacing Process1 by Trace1. Now, however, changing the order of events in the event log leads to different order relations, and therefore
10 10 D.R. Ferreira and L.H. Thom different assertions involving the property followedby. A pattern will only appear in the result if the corresponding elements follow each other in the same order as defined in the class expression. 4.4 Implementation The WAP ontology was developed and tested in Protégé together with the Pellet Reasoner Plug-in 2. Using Java code, we load the ontology and create the individuals with the Jena framework 3. The Pellet reasoner 4 is invoked through Jena to perform reasoning over the ontology together with the individuals. The SPARQL query is also executed through Jena. Basically, using Jena we load the ontology file created with Protégé into an ontology model (a Java object implementing the OntModel interface). Then we read a text file containing the annotation of the process elements. For each class in the annotation, we retrieve a class reference (OntClass) from the ontology model, and create an individual of that class by invoking OntClass.createIndividual(). The relations between individuals are established by retrieving references to the appropriate object properties. Finally, using the Pellet reasoner, we create an inference model (InfModel) and then run the SPARQL query over this new model. Iterating through the results provides the subclasses of Pattern contained in the process. 5 Case Study: A Purchase Process The following case study is based on the purchase process of a Portuguese company, implemented in a commercial workflow system (BizAgi 5 ). The process is structured according to the following main stages: An employee fills out a requisition form for a certain product and sends it to the warehouse, which checks how many units are available in stock and returns the result. After receiving the result from the warehouse, the employee checks if there are enough units and, in that case, asks the warehouse to dispatch the product, receiving a confirmation in the end. However, in case the stock level is insufficient, the employee creates and submits a purchase request for approval by a manager. If approval is not granted, the process ends immediately. Otherwise, the process continues with the employee relaying a purchase order to the purchase department. The purchase department orders the product from a supplier and makes the warehouse aware of Figure 4 Event log for a trace of the purchase process the incoming merchandise. Once the warehouse receives the product, it notifies the employee and forwards the invoice to the purchase department. The purchase department takes care of paying to the supplier and, once this is finished, notifies the employee that the requisition can be closed. Upon receiving note that payment is done, the employee closes the requisition and notifies the manager that the purchase request that had been previously approved is now complete. For the purpose of this case study, the process has been augmented with additional activities in order to represent send and receive signals. The inclusion of these activities was necessary because the system event log does not record the exchange of messages between participants, only that some participant has performed some task. To make it easier to demonstrate the proposed approach, we modelled these exchanges explicitly. The send and receive signals are included as extra, donothing activities that do not affect the overall flow of the process, except for the fact that each user will visualise the same form for a second time, either after completing the current task (when sending the output to others) or before completing the current task (when receiving the input from others). Figure 5 and Figure 6 show the overall structure of the purchase process. Since the activity labels are in Portuguese, we will not delve further into it, and instead we just note that the first lane is the employee, the second one is the warehouse, the third one represents the manager, and the fourth stands for the purchase department. During this study we were able to collect two kinds of traces: one where the desired product was available in stock and was therefore dispatched immediately from the warehouse; and another where the product was not in stock and a purchase request was submitted, approved, and processed to the end (there were no instances of purchase requests that were not approved). Figure 4 shows a screenshot for a trace of the first kind, as recorded in the event log. Based on the process model, we established a mapping between the activity labels and the classes in the WAP ontology, which is effectively equivalent to a semantic annotation of those activities. Using such
11 A Semantic Approach to the Discovery of WAPs in Event Logs 11 Figure 5 Purchase process as implemented in BizAgi (part 1 of 2)
12 12 D.R. Ferreira and L.H. Thom Figure 6 Purchase process as implemented in BizAgi (part 2 of 2)
13 A Semantic Approach to the Discovery of WAPs in Event Logs 13 Figure 7 WAPs discovered in Trace1 of the purchase process Figure 8 WAPs discovered in Trace2 of the purchase process annotation, we translated the event logs mechanically, by replacing each event by its corresponding class or classes, as described in Section 4.1. Since only two kinds of traces were observed in the event log, we picked up one instance of each, which we denoted by Trace1 and Trace2. Figure 7 and Figure 8 highlight the path of each trace in the process model, and show the WAPs discovered in each of those traces. It should be noted that a different annotation of the model elements may lead to the discovery of different WAPs. For example, Figure 9 illustrates the effect of a different annotation for the part of the process where the warehouse receives a request to dispatch the product and then returns a confirmation that the product has been dispatched. If this confirmation is taken as a notification, then the annotation becomes: SignalSend MessageActivityRequest SignalReceive MessageActivityRequest ActivityExecute SignalSend MessageNotification SignalReceive MessageNotification The annotation above leads to the discovery of WAP3 and WAP5, as in the original trace depicted in Figure 7. The first three events become a unidirectional performative (WAP3) and the last two events are a notification pattern (WAP5). On the other hand, if the confirmation from the warehouse is interpreted as a result, the annotation becomes: SignalSend MessageActivityRequest (a) Original annotation Figure 9 (b) Alternative annotation WAPs discovered with different annotations SignalReceive MessageActivityRequest ActivityExecute SignalSend MessageActivityResult SignalReceive MessageActivityResult In this case, the five events fit into the definition of a bidirectional performative (WAP4), as shown in Figure 9(b). In practice, it is up to the analyst to decide which annotation is more correct. At the present stage, establishing the semantics of the activities in a process requires human interpretation, so different results may arise from the same process. In any case, the approach described here is able to discover the presence of WAPs in a way that is consistent with the provided annotation.
14 14 D.R. Ferreira and L.H. Thom 6 Conclusion In this work we have introduced an approach to automate the discovery of WAPs in business processes by means of reasoning over an ontology. In this ontology, the classes define the elements that each pattern contains, and the individuals represent the elements of the given process. These individuals can be generated automatically from an event log recorded during process execution. Both the semantics and the sequence of events are used to determine whether a given pattern is present in the process. In future work, we intend to focus on tool support for the semantic annotation of model elements, and in particular on facilitating the annotation of elements which have a mapping to ontology classes other than oneto-one, such as one-to-many or many-to-one. This would avoid the need to insert artificial activities in the process, as we did in the case study to represent signals. Another branch for future work is to support more elaborate versions of the same patterns, including the iterative and concurrent versions of certain WAPs. Acknowledgment We are grateful to the PNPD Program from the Brazilian Coordination for the Improvement of Graduated Students (CAPES). References Born, M., Dörr, F., and Weber, I. (2007). User-friendly semantic annotation in business process modeling. In Web Information Systems Engineering WISE 2007 Workshops, volume 4832 of LNCS, pages Springer. Dietz, J. L. (2006). The deep structure of business processes. Communications of the ACM, 49(5): Filipowska, A., Kaczmarek, M., and Stein, S. (2009). Semantically annotated EPC within semantic business process management. In Business Process Management Workshops, volume 17 of LNBIP, pages Springer. Medeiros, A. K. A. D. and Günther, C. W. (2005). Process mining: Using CPN tools to create test logs for mining algorithms. In Proceedings of the Sixth Workshop and Tutorial on Practical Use of Coloured Petri Nets and the CPN Tools, pages Medina-Mora, R., Winograd, T., Flores, R., and Flores, F. (1992). The action workflow approach to workflow management technology. In Proceedings of the 1992 ACM conference on Computer-Supported CooperativeWork, CSCW 92, pages ACM. Mendling, J., Reijers, H., and Recker, J. (2010). Activity labeling in process modeling: Empirical insights and recommendations. Information Systems, 35(4): Rozinat, A. and van der Aalst, W. M. P. (2008). Conformance checking of processes based on monitoring real behavior. Information Systems, 33(1): ter Hofstede, A. and Dietz, J. (2003). Generic recurrent patterns in business processes. In Weske, M., editor, Business Process Management, volume 2678 of LNCS, pages Springer Berlin / Heidelberg. Thom, L. H., Reichert, M., Chiao, C., Iochpe, C., and Hess, G. (2008). Inventing less, reusing more, and adding intelligence to business process modeling. In Database and Expert Systems Applications, volume 5181 of LNCS, pages Springer. Thom, L. H., Reichert, M., and Iochpe, C. (2009). Activity patterns in process-aware information systems: basic concepts and empirical evidence. International Journal of Business Process Integration and Management, 4(2): van der Aalst, W., ter Hofstede, A., and anda.p. Barros, B. K. (2003a). Workflow patterns. Distributed and Parallel Databases, 14(1):5 51. van der Aalst, W., van Dongen, B. F., Herbst, J., Maruster, L., Schimm, G., and Weijters, A. J. M. M. (2003b). Workflow mining: A survey of issues and approaches. Data and Knowledge Engineering, 47(2): van der Aalst, W., Weijters, T., and Maruster, L. (2004). Workflow mining: discovering process models from event logs. IEEE Transactions on Knowledge and Data Engineering, 16(9): van der Aalst, W. M. P., Reijers, H. A., and Song, M. (2005). Discovering social networks from event logs. Computer Supported Cooperative Work, 14(6): van der Aalst, W. M. P., Reijers, H. A., Weijters, A. J. M. M., van Dongen, B. F., Alves de Medeiros, A. K., Song, M., and Verbeek, H. M. W. (2007). Business process mining: An industrial application. Information Systems, 32(5): Weidlich, M., Polyvyanyy, A., Desai, N., Mendling, J., and Weske, M. (2011). Process compliance analysis based on behavioural profiles. Information Systems, 36(7): Zouggar, N., Vallespir, B., and Chen, D. (2008). Semantic enrichment of enterprise models by ontologies-based semantic annotations. In Proceedings of the 12th International EDOC Conference Workshops, pages IEEE Computer Society.
Ontology-Based Discovery of Workflow Activity Patterns
 Ontology-Based Discovery of Workflow Activity Patterns Diogo R. Ferreira 1, Susana Alves 1, Lucinéia H. Thom 2 1 IST Technical University of Lisbon, Portugal {diogo.ferreira,susana.alves}@ist.utl.pt 2
Ontology-Based Discovery of Workflow Activity Patterns Diogo R. Ferreira 1, Susana Alves 1, Lucinéia H. Thom 2 1 IST Technical University of Lisbon, Portugal {diogo.ferreira,susana.alves}@ist.utl.pt 2
DISCOVERY AND ANALYSIS OF ACTIVITY PATTERN CO- OCCURRENCES IN BUSINESS PROCESS MODELS
 DISCOVERY AND ANALYSIS OF ACTIVITY PATTERN CO- OCCURRENCES IN BUSINESS PROCESS MODELS Jean Michel Lau, Cirano Iochpe Informatics Institute, Federal University of Rio Grande do Sul, 9500 Bento Gonçalves
DISCOVERY AND ANALYSIS OF ACTIVITY PATTERN CO- OCCURRENCES IN BUSINESS PROCESS MODELS Jean Michel Lau, Cirano Iochpe Informatics Institute, Federal University of Rio Grande do Sul, 9500 Bento Gonçalves
Towards an Intelligent Workflow Designer based on the Reuse of Workflow Patterns
 Towards an Intelligent Workflow Designer based on the Reuse of Workflow Patterns 1 Cirano Iochpe, Carolina Chiao 1, Guillermo Hess 1, Gleison Nascimento 1 Federal University of Rio Grande do Sul Institute
Towards an Intelligent Workflow Designer based on the Reuse of Workflow Patterns 1 Cirano Iochpe, Carolina Chiao 1, Guillermo Hess 1, Gleison Nascimento 1 Federal University of Rio Grande do Sul Institute
BPMN PATTERNS USED IN MANAGEMENT INFORMATION SYSTEMS
 BPMN PATTERNS USED IN MANAGEMENT INFORMATION SYSTEMS Gabriel Cozgarea 1 Adrian Cozgarea 2 ABSTRACT: Business Process Modeling Notation (BPMN) is a graphical standard in which controls and activities can
BPMN PATTERNS USED IN MANAGEMENT INFORMATION SYSTEMS Gabriel Cozgarea 1 Adrian Cozgarea 2 ABSTRACT: Business Process Modeling Notation (BPMN) is a graphical standard in which controls and activities can
Workflow Patterns for Business Process Modeling
 Workflow Patterns for Business Process Modeling Lucinéia Heloisa Thom 1, Cirano Iochpe 1,2, Manfred Reichert 3 1 Federal University of Rio Grande do Sul, Informatics Institute, Av. Bento Gonçalves, 9500,
Workflow Patterns for Business Process Modeling Lucinéia Heloisa Thom 1, Cirano Iochpe 1,2, Manfred Reichert 3 1 Federal University of Rio Grande do Sul, Informatics Institute, Av. Bento Gonçalves, 9500,
Business Process Modeling
 Business Process Concepts Process Mining Kelly Rosa Braghetto Instituto de Matemática e Estatística Universidade de São Paulo kellyrb@ime.usp.br January 30, 2009 1 / 41 Business Process Concepts Process
Business Process Concepts Process Mining Kelly Rosa Braghetto Instituto de Matemática e Estatística Universidade de São Paulo kellyrb@ime.usp.br January 30, 2009 1 / 41 Business Process Concepts Process
A METHOD FOR REWRITING LEGACY SYSTEMS USING BUSINESS PROCESS MANAGEMENT TECHNOLOGY
 A METHOD FOR REWRITING LEGACY SYSTEMS USING BUSINESS PROCESS MANAGEMENT TECHNOLOGY Gleison Samuel do Nascimento, Cirano Iochpe Institute of Informatics, Federal University of Rio Grande do Sul, Porto Alegre,
A METHOD FOR REWRITING LEGACY SYSTEMS USING BUSINESS PROCESS MANAGEMENT TECHNOLOGY Gleison Samuel do Nascimento, Cirano Iochpe Institute of Informatics, Federal University of Rio Grande do Sul, Porto Alegre,
An Ontology-based Framework for Enriching Event-log Data
 An Ontology-based Framework for Enriching Event-log Data Thanh Tran Thi Kim, Hannes Werthner e-commerce group Institute of Software Technology and Interactive Systems, Vienna, Austria Email: kimthanh@ec.tuwien.ac.at,
An Ontology-based Framework for Enriching Event-log Data Thanh Tran Thi Kim, Hannes Werthner e-commerce group Institute of Software Technology and Interactive Systems, Vienna, Austria Email: kimthanh@ec.tuwien.ac.at,
A Meta-model of Business Interaction for Assisting Intelligent Workflow Systems
 A Meta-model of Business Interaction for Assisting Intelligent Workflow Systems Areti Manataki and Yun-Heh Chen-Burger Centre for Intelligent Systems and their Applications, School of Informatics, The
A Meta-model of Business Interaction for Assisting Intelligent Workflow Systems Areti Manataki and Yun-Heh Chen-Burger Centre for Intelligent Systems and their Applications, School of Informatics, The
Modeling Workflow Patterns
 Modeling Workflow Patterns Bizagi Suite Workflow Patterns 1 Table of Contents Modeling workflow patterns... 4 Implementing the patterns... 4 Basic control flow patterns... 4 WCP 1- Sequence... 4 WCP 2-
Modeling Workflow Patterns Bizagi Suite Workflow Patterns 1 Table of Contents Modeling workflow patterns... 4 Implementing the patterns... 4 Basic control flow patterns... 4 WCP 1- Sequence... 4 WCP 2-
Dotted Chart and Control-Flow Analysis for a Loan Application Process
 Dotted Chart and Control-Flow Analysis for a Loan Application Process Thomas Molka 1,2, Wasif Gilani 1 and Xiao-Jun Zeng 2 Business Intelligence Practice, SAP Research, Belfast, UK The University of Manchester,
Dotted Chart and Control-Flow Analysis for a Loan Application Process Thomas Molka 1,2, Wasif Gilani 1 and Xiao-Jun Zeng 2 Business Intelligence Practice, SAP Research, Belfast, UK The University of Manchester,
Mercy Health System. St. Louis, MO. Process Mining of Clinical Workflows for Quality and Process Improvement
 Mercy Health System St. Louis, MO Process Mining of Clinical Workflows for Quality and Process Improvement Paul Helmering, Executive Director, Enterprise Architecture Pete Harrison, Data Analyst, Mercy
Mercy Health System St. Louis, MO Process Mining of Clinical Workflows for Quality and Process Improvement Paul Helmering, Executive Director, Enterprise Architecture Pete Harrison, Data Analyst, Mercy
Discovering User Communities in Large Event Logs
 Discovering User Communities in Large Event Logs Diogo R. Ferreira, Cláudia Alves IST Technical University of Lisbon, Portugal {diogo.ferreira,claudia.alves}@ist.utl.pt Abstract. The organizational perspective
Discovering User Communities in Large Event Logs Diogo R. Ferreira, Cláudia Alves IST Technical University of Lisbon, Portugal {diogo.ferreira,claudia.alves}@ist.utl.pt Abstract. The organizational perspective
Generation of a Set of Event Logs with Noise
 Generation of a Set of Event Logs with Noise Ivan Shugurov International Laboratory of Process-Aware Information Systems National Research University Higher School of Economics 33 Kirpichnaya Str., Moscow,
Generation of a Set of Event Logs with Noise Ivan Shugurov International Laboratory of Process-Aware Information Systems National Research University Higher School of Economics 33 Kirpichnaya Str., Moscow,
Conformance Checking of RBAC Policies in Process-Aware Information Systems
 Conformance Checking of RBAC Policies in Process-Aware Information Systems Anne Baumgrass 1, Thomas Baier 2, Jan Mendling 2, and Mark Strembeck 1 1 Institute of Information Systems and New Media Vienna
Conformance Checking of RBAC Policies in Process-Aware Information Systems Anne Baumgrass 1, Thomas Baier 2, Jan Mendling 2, and Mark Strembeck 1 1 Institute of Information Systems and New Media Vienna
Process Mining and Monitoring Processes and Services: Workshop Report
 Process Mining and Monitoring Processes and Services: Workshop Report Wil van der Aalst (editor) Eindhoven University of Technology, P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. w.m.p.v.d.aalst@tm.tue.nl
Process Mining and Monitoring Processes and Services: Workshop Report Wil van der Aalst (editor) Eindhoven University of Technology, P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. w.m.p.v.d.aalst@tm.tue.nl
Improving Business Process Models with Agent-based Simulation and Process Mining
 Improving Business Process Models with Agent-based Simulation and Process Mining Fernando Szimanski 1, Célia G. Ralha 1, Gerd Wagner 2, and Diogo R. Ferreira 3 1 University of Brasília, Brazil fszimanski@gmail.com,
Improving Business Process Models with Agent-based Simulation and Process Mining Fernando Szimanski 1, Célia G. Ralha 1, Gerd Wagner 2, and Diogo R. Ferreira 3 1 University of Brasília, Brazil fszimanski@gmail.com,
Decision Mining in Business Processes
 Decision Mining in Business Processes A. Rozinat and W.M.P. van der Aalst Department of Technology Management, Eindhoven University of Technology P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands {a.rozinat,w.m.p.v.d.aalst}@tm.tue.nl
Decision Mining in Business Processes A. Rozinat and W.M.P. van der Aalst Department of Technology Management, Eindhoven University of Technology P.O. Box 513, NL-5600 MB, Eindhoven, The Netherlands {a.rozinat,w.m.p.v.d.aalst}@tm.tue.nl
Eventifier: Extracting Process Execution Logs from Operational Databases
 Eventifier: Extracting Process Execution Logs from Operational Databases Carlos Rodríguez 1, Robert Engel 2, Galena Kostoska 1, Florian Daniel 1, Fabio Casati 1, and Marco Aimar 3 1 University of Trento,
Eventifier: Extracting Process Execution Logs from Operational Databases Carlos Rodríguez 1, Robert Engel 2, Galena Kostoska 1, Florian Daniel 1, Fabio Casati 1, and Marco Aimar 3 1 University of Trento,
EXTENDING BUSINESS PROCESS MODELING TOOLS WITH WORKFLOW PATTERN REUSE
 EXTENDING BUSINESS PROCESS MODELING TOOLS WITH WORKFLOW PATTERN REUSE Lucinéia Heloisa Thom 1, Jean Michael Lau 1, Cirano Iochpe 1,2, Jan Mendling 3 1 Institute of Informatics, Federal University of Rio
EXTENDING BUSINESS PROCESS MODELING TOOLS WITH WORKFLOW PATTERN REUSE Lucinéia Heloisa Thom 1, Jean Michael Lau 1, Cirano Iochpe 1,2, Jan Mendling 3 1 Institute of Informatics, Federal University of Rio
Model Discovery from Motor Claim Process Using Process Mining Technique
 International Journal of Scientific and Research Publications, Volume 3, Issue 1, January 2013 1 Model Discovery from Motor Claim Process Using Process Mining Technique P.V.Kumaraguru *, Dr.S.P.Rajagopalan
International Journal of Scientific and Research Publications, Volume 3, Issue 1, January 2013 1 Model Discovery from Motor Claim Process Using Process Mining Technique P.V.Kumaraguru *, Dr.S.P.Rajagopalan
Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop
 Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop Sergio Hernández 1, S.J. van Zelst 2, Joaquín Ezpeleta 1, and Wil M.P. van der Aalst 2 1 Department of Computer Science and Systems Engineering
Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop Sergio Hernández 1, S.J. van Zelst 2, Joaquín Ezpeleta 1, and Wil M.P. van der Aalst 2 1 Department of Computer Science and Systems Engineering
Process Modelling from Insurance Event Log
 Process Modelling from Insurance Event Log P.V. Kumaraguru Research scholar, Dr.M.G.R Educational and Research Institute University Chennai- 600 095 India Dr. S.P. Rajagopalan Professor Emeritus, Dr. M.G.R
Process Modelling from Insurance Event Log P.V. Kumaraguru Research scholar, Dr.M.G.R Educational and Research Institute University Chennai- 600 095 India Dr. S.P. Rajagopalan Professor Emeritus, Dr. M.G.R
EFFECTIVE CONSTRUCTIVE MODELS OF IMPLICIT SELECTION IN BUSINESS PROCESSES. Nataliya Golyan, Vera Golyan, Olga Kalynychenko
 380 International Journal Information Theories and Applications, Vol. 18, Number 4, 2011 EFFECTIVE CONSTRUCTIVE MODELS OF IMPLICIT SELECTION IN BUSINESS PROCESSES Nataliya Golyan, Vera Golyan, Olga Kalynychenko
380 International Journal Information Theories and Applications, Vol. 18, Number 4, 2011 EFFECTIVE CONSTRUCTIVE MODELS OF IMPLICIT SELECTION IN BUSINESS PROCESSES Nataliya Golyan, Vera Golyan, Olga Kalynychenko
Managing and Tracing the Traversal of Process Clouds with Templates, Agendas and Artifacts
 Managing and Tracing the Traversal of Process Clouds with Templates, Agendas and Artifacts Marian Benner, Matthias Book, Tobias Brückmann, Volker Gruhn, Thomas Richter, Sema Seyhan paluno The Ruhr Institute
Managing and Tracing the Traversal of Process Clouds with Templates, Agendas and Artifacts Marian Benner, Matthias Book, Tobias Brückmann, Volker Gruhn, Thomas Richter, Sema Seyhan paluno The Ruhr Institute
CHAPTER 1 INTRODUCTION
 CHAPTER 1 INTRODUCTION 1.1 Research Motivation In today s modern digital environment with or without our notice we are leaving our digital footprints in various data repositories through our daily activities,
CHAPTER 1 INTRODUCTION 1.1 Research Motivation In today s modern digital environment with or without our notice we are leaving our digital footprints in various data repositories through our daily activities,
FlowSpy: : exploring Activity-Execution Patterns from Business Processes
 FlowSpy: : exploring Activity-Execution Patterns from Business Processes Cristian Tristão 1, Duncan D. Ruiz 2, Karin Becker 3 ctristaobr@gmail.com, duncan@pucrs.br, kbeckerbr@gmail.com 1 Departamento de
FlowSpy: : exploring Activity-Execution Patterns from Business Processes Cristian Tristão 1, Duncan D. Ruiz 2, Karin Becker 3 ctristaobr@gmail.com, duncan@pucrs.br, kbeckerbr@gmail.com 1 Departamento de
Activity Mining for Discovering Software Process Models
 Activity Mining for Discovering Software Process Models Ekkart Kindler, Vladimir Rubin, Wilhelm Schäfer Software Engineering Group, University of Paderborn, Germany [kindler, vroubine, wilhelm]@uni-paderborn.de
Activity Mining for Discovering Software Process Models Ekkart Kindler, Vladimir Rubin, Wilhelm Schäfer Software Engineering Group, University of Paderborn, Germany [kindler, vroubine, wilhelm]@uni-paderborn.de
BIS 3106: Business Process Management. Lecture Two: Modelling the Control-flow Perspective
 BIS 3106: Business Process Management Lecture Two: Modelling the Control-flow Perspective Makerere University School of Computing and Informatics Technology Department of Computer Science SEM I 2015/2016
BIS 3106: Business Process Management Lecture Two: Modelling the Control-flow Perspective Makerere University School of Computing and Informatics Technology Department of Computer Science SEM I 2015/2016
Process mining challenges in hospital information systems
 Proceedings of the Federated Conference on Computer Science and Information Systems pp. 1135 1140 ISBN 978-83-60810-51-4 Process mining challenges in hospital information systems Payam Homayounfar Wrocław
Proceedings of the Federated Conference on Computer Science and Information Systems pp. 1135 1140 ISBN 978-83-60810-51-4 Process mining challenges in hospital information systems Payam Homayounfar Wrocław
Business Process Quality Metrics: Log-based Complexity of Workflow Patterns
 Business Process Quality Metrics: Log-based Complexity of Workflow Patterns Jorge Cardoso Department of Mathematics and Engineering, University of Madeira, Funchal, Portugal jcardoso@uma.pt Abstract. We
Business Process Quality Metrics: Log-based Complexity of Workflow Patterns Jorge Cardoso Department of Mathematics and Engineering, University of Madeira, Funchal, Portugal jcardoso@uma.pt Abstract. We
Semantic Analysis of Flow Patterns in Business Process Modeling
 Semantic Analysis of Flow Patterns in Business Process Modeling Pnina Soffer 1, Yair Wand 2, and Maya Kaner 3 1 University of Haifa, Carmel Mountain 31905, Haifa 31905, Israel 2 Sauder School of Business,
Semantic Analysis of Flow Patterns in Business Process Modeling Pnina Soffer 1, Yair Wand 2, and Maya Kaner 3 1 University of Haifa, Carmel Mountain 31905, Haifa 31905, Israel 2 Sauder School of Business,
Supporting the BPM lifecycle with FileNet
 Supporting the BPM lifecycle with FileNet Mariska Netjes Hajo A. Reijers Wil. M.P. van der Aalst Outline Introduction Evaluation approach Evaluation of FileNet Conclusions Business Process Management Supporting
Supporting the BPM lifecycle with FileNet Mariska Netjes Hajo A. Reijers Wil. M.P. van der Aalst Outline Introduction Evaluation approach Evaluation of FileNet Conclusions Business Process Management Supporting
BPMN by example. Bizagi Suite. Copyright 2014 Bizagi
 BPMN by example Bizagi Suite Recruitment and Selection 1 Table of Contents Scope... 2 BPMN 2.0 Business Process Modeling Notation... 2 Why Is It Important To Model With Bpmn?... 2 Introduction to BPMN...
BPMN by example Bizagi Suite Recruitment and Selection 1 Table of Contents Scope... 2 BPMN 2.0 Business Process Modeling Notation... 2 Why Is It Important To Model With Bpmn?... 2 Introduction to BPMN...
Business Process Management: A personal view
 Business Process Management: A personal view W.M.P. van der Aalst Department of Technology Management Eindhoven University of Technology, The Netherlands w.m.p.v.d.aalst@tm.tue.nl 1 Introduction Business
Business Process Management: A personal view W.M.P. van der Aalst Department of Technology Management Eindhoven University of Technology, The Netherlands w.m.p.v.d.aalst@tm.tue.nl 1 Introduction Business
Analysis of Service Level Agreements using Process Mining techniques
 Analysis of Service Level Agreements using Process Mining techniques CHRISTIAN MAGER University of Applied Sciences Wuerzburg-Schweinfurt Process Mining offers powerful methods to extract knowledge from
Analysis of Service Level Agreements using Process Mining techniques CHRISTIAN MAGER University of Applied Sciences Wuerzburg-Schweinfurt Process Mining offers powerful methods to extract knowledge from
Approaching Process Mining with Sequence Clustering: Experiments and Findings
 Approaching Process Mining with Sequence Clustering: Experiments and Findings Diogo Ferreira 1,3, Marielba Zacarias 2,3, Miguel Malheiros 3, Pedro Ferreira 3 1 IST Technical University of Lisbon, Taguspark,
Approaching Process Mining with Sequence Clustering: Experiments and Findings Diogo Ferreira 1,3, Marielba Zacarias 2,3, Miguel Malheiros 3, Pedro Ferreira 3 1 IST Technical University of Lisbon, Taguspark,
Change Propagation in Process Models using Behavioural Profiles
 Change Propagation in Process Models using Behavioural Profiles Matthias Weidlich, Mathias Weske Hasso-Plattner-Institute, Potsdam, Germany Email: {matthias.weidlich,weske}@hpi.uni-potsdam.de Jan Mendling
Change Propagation in Process Models using Behavioural Profiles Matthias Weidlich, Mathias Weske Hasso-Plattner-Institute, Potsdam, Germany Email: {matthias.weidlich,weske}@hpi.uni-potsdam.de Jan Mendling
A Software Framework for Risk-Aware Business Process Management
 A Software Framework for Risk-Aware Business Management Raffaele Conforti 1, Marcello La Rosa 1,2, Arthur H.M. ter Hofstede 1,4, Giancarlo Fortino 3, Massimiliano de Leoni 4, Wil M.P. van der Aalst 4,1,
A Software Framework for Risk-Aware Business Management Raffaele Conforti 1, Marcello La Rosa 1,2, Arthur H.M. ter Hofstede 1,4, Giancarlo Fortino 3, Massimiliano de Leoni 4, Wil M.P. van der Aalst 4,1,
Supporting the BPM life-cycle with FileNet
 Supporting the BPM life-cycle with FileNet Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven,
Supporting the BPM life-cycle with FileNet Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven,
Understanding Web personalization with Web Usage Mining and its Application: Recommender System
 Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
Towards Cross-Organizational Process Mining in Collections of Process Models and their Executions
 Towards Cross-Organizational Process Mining in Collections of Process Models and their Executions J.C.A.M. Buijs, B.F. van Dongen, W.M.P. van der Aalst Department of Mathematics and Computer Science, Eindhoven
Towards Cross-Organizational Process Mining in Collections of Process Models and their Executions J.C.A.M. Buijs, B.F. van Dongen, W.M.P. van der Aalst Department of Mathematics and Computer Science, Eindhoven
Application of Process Mining in Healthcare A Case Study in a Dutch Hospital
 Application of Process Mining in Healthcare A Case Study in a Dutch Hospital R.S. Mans 1, M.H. Schonenberg 1, M. Song 1, W.M.P. van der Aalst 1, and P.J.M. Bakker 2 1 Department of Information Systems
Application of Process Mining in Healthcare A Case Study in a Dutch Hospital R.S. Mans 1, M.H. Schonenberg 1, M. Song 1, W.M.P. van der Aalst 1, and P.J.M. Bakker 2 1 Department of Information Systems
Configuring IBM WebSphere Monitor for Process Mining
 Configuring IBM WebSphere Monitor for Process Mining H.M.W. Verbeek and W.M.P. van der Aalst Technische Universiteit Eindhoven Department of Mathematics and Computer Science P.O. Box 513, 5600 MB Eindhoven,
Configuring IBM WebSphere Monitor for Process Mining H.M.W. Verbeek and W.M.P. van der Aalst Technische Universiteit Eindhoven Department of Mathematics and Computer Science P.O. Box 513, 5600 MB Eindhoven,
USING PROCESS MINING FOR ITIL ASSESSMENT: A CASE STUDY WITH INCIDENT MANAGEMENT
 USING PROCESS MINING FOR ITIL ASSESSMENT: A CASE STUDY WITH INCIDENT MANAGEMENT Diogo R. Ferreira 1,2, Miguel Mira da Silva 1,3 1 IST Technical University of Lisbon, Portugal 2 Organizational Engineering
USING PROCESS MINING FOR ITIL ASSESSMENT: A CASE STUDY WITH INCIDENT MANAGEMENT Diogo R. Ferreira 1,2, Miguel Mira da Silva 1,3 1 IST Technical University of Lisbon, Portugal 2 Organizational Engineering
Towards a Software Framework for Automatic Business Process Redesign Marwa M.Essam 1, Selma Limam Mansar 2 1
 ACEEE Int. J. on Communication, Vol. 02, No. 03, Nov 2011 Towards a Software Framework for Automatic Business Process Redesign Marwa M.Essam 1, Selma Limam Mansar 2 1 Faculty of Information and Computer
ACEEE Int. J. on Communication, Vol. 02, No. 03, Nov 2011 Towards a Software Framework for Automatic Business Process Redesign Marwa M.Essam 1, Selma Limam Mansar 2 1 Faculty of Information and Computer
FileNet s BPM life-cycle support
 FileNet s BPM life-cycle support Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven, The Netherlands
FileNet s BPM life-cycle support Mariska Netjes, Hajo A. Reijers, Wil M.P. van der Aalst Eindhoven University of Technology, Department of Technology Management, PO Box 513, NL-5600 MB Eindhoven, The Netherlands
Feature. Applications of Business Process Analytics and Mining for Internal Control. World
 Feature Filip Caron is a doctoral researcher in the Department of Decision Sciences and Information Management, Information Systems Group, at the Katholieke Universiteit Leuven (Flanders, Belgium). Jan
Feature Filip Caron is a doctoral researcher in the Department of Decision Sciences and Information Management, Information Systems Group, at the Katholieke Universiteit Leuven (Flanders, Belgium). Jan
Business Process Measurement in small enterprises after the installation of an ERP software.
 Business Process Measurement in small enterprises after the installation of an ERP software. Stefano Siccardi and Claudia Sebastiani CQ Creativiquadrati snc, via Tadino 60, Milano, Italy http://www.creativiquadrati.it
Business Process Measurement in small enterprises after the installation of an ERP software. Stefano Siccardi and Claudia Sebastiani CQ Creativiquadrati snc, via Tadino 60, Milano, Italy http://www.creativiquadrati.it
ProM 6 Tutorial. H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.
 ProM 6 Tutorial H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.nl August 2010 1 Introduction This document shows how to use ProM 6 to
ProM 6 Tutorial H.M.W. (Eric) Verbeek mailto:h.m.w.verbeek@tue.nl R. P. Jagadeesh Chandra Bose mailto:j.c.b.rantham.prabhakara@tue.nl August 2010 1 Introduction This document shows how to use ProM 6 to
Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach
 Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach Santiago Aguirre, Carlos Parra, and Jorge Alvarado Industrial Engineering Department, Pontificia
Combination of Process Mining and Simulation Techniques for Business Process Redesign: A Methodological Approach Santiago Aguirre, Carlos Parra, and Jorge Alvarado Industrial Engineering Department, Pontificia
Process Mining Online Assessment Data
 Process Mining Online Assessment Data Mykola Pechenizkiy, Nikola Trčka, Ekaterina Vasilyeva, Wil van der Aalst, Paul De Bra {m.pechenizkiy, e.vasilyeva, n.trcka, w.m.p.v.d.aalst}@tue.nl, debra@win.tue.nl
Process Mining Online Assessment Data Mykola Pechenizkiy, Nikola Trčka, Ekaterina Vasilyeva, Wil van der Aalst, Paul De Bra {m.pechenizkiy, e.vasilyeva, n.trcka, w.m.p.v.d.aalst}@tue.nl, debra@win.tue.nl
WoPeD - An Educational Tool for Workflow Nets
 WoPeD - An Educational Tool for Workflow Nets Thomas Freytag, Cooperative State University (DHBW) Karlsruhe, Germany freytag@dhbw-karlsruhe.de Martin Sänger, 1&1 Internet AG, Karlsruhe, Germany m.saenger09@web.de
WoPeD - An Educational Tool for Workflow Nets Thomas Freytag, Cooperative State University (DHBW) Karlsruhe, Germany freytag@dhbw-karlsruhe.de Martin Sänger, 1&1 Internet AG, Karlsruhe, Germany m.saenger09@web.de
Towards an Evaluation Framework for Process Mining Algorithms
 Towards an Evaluation Framework for Process Mining Algorithms A. Rozinat, A.K. Alves de Medeiros, C.W. Günther, A.J.M.M. Weijters, and W.M.P. van der Aalst Eindhoven University of Technology P.O. Box 513,
Towards an Evaluation Framework for Process Mining Algorithms A. Rozinat, A.K. Alves de Medeiros, C.W. Günther, A.J.M.M. Weijters, and W.M.P. van der Aalst Eindhoven University of Technology P.O. Box 513,
IMPROVING BUSINESS PROCESS MODELING USING RECOMMENDATION METHOD
 Journal homepage: www.mjret.in ISSN:2348-6953 IMPROVING BUSINESS PROCESS MODELING USING RECOMMENDATION METHOD Deepak Ramchandara Lad 1, Soumitra S. Das 2 Computer Dept. 12 Dr. D. Y. Patil School of Engineering,(Affiliated
Journal homepage: www.mjret.in ISSN:2348-6953 IMPROVING BUSINESS PROCESS MODELING USING RECOMMENDATION METHOD Deepak Ramchandara Lad 1, Soumitra S. Das 2 Computer Dept. 12 Dr. D. Y. Patil School of Engineering,(Affiliated
Context-driven Business Process Modelling
 Context-driven Business Process Modelling Matthias Born 1, Jens Kirchner 1, and Jörg P. Müller 2 1 SAP Research, Karlsruhe, Vincenz-Priessnitz-Strasse 1, 76131 Karlsruhe {mat.born, jens.kirchner}@sap.com
Context-driven Business Process Modelling Matthias Born 1, Jens Kirchner 1, and Jörg P. Müller 2 1 SAP Research, Karlsruhe, Vincenz-Priessnitz-Strasse 1, 76131 Karlsruhe {mat.born, jens.kirchner}@sap.com
A Tool for Searching the Semantic Web for Supplies Matching Demands
 A Tool for Searching the Semantic Web for Supplies Matching Demands Zuzana Halanová, Pavol Návrat, Viera Rozinajová Abstract: We propose a model of searching semantic web that allows incorporating data
A Tool for Searching the Semantic Web for Supplies Matching Demands Zuzana Halanová, Pavol Návrat, Viera Rozinajová Abstract: We propose a model of searching semantic web that allows incorporating data
Towards a Framework for the Agile Mining of Business Processes
 Towards a Framework for the Agile Mining of Business Processes Barbara Weber 1, Manfred Reichert 2, Stefanie Rinderle 3, and Werner Wild 4 1 Quality Engineering Research Group, University of Innsbruck,
Towards a Framework for the Agile Mining of Business Processes Barbara Weber 1, Manfred Reichert 2, Stefanie Rinderle 3, and Werner Wild 4 1 Quality Engineering Research Group, University of Innsbruck,
How To Find The Model Of A Process From The Run Time
 Discovering Process Models from Unlabelled Event Logs Diogo R. Ferreira 1 and Daniel Gillblad 2 1 IST Technical University of Lisbon 2 Swedish Institute of Computer Science (SICS) diogo.ferreira@ist.utl.pt,
Discovering Process Models from Unlabelled Event Logs Diogo R. Ferreira 1 and Daniel Gillblad 2 1 IST Technical University of Lisbon 2 Swedish Institute of Computer Science (SICS) diogo.ferreira@ist.utl.pt,
CS 565 Business Process & Workflow Management Systems
 CS 565 Business Process & Workflow Management Systems Professor & Researcher Department of Computer Science, University of Crete & ICS-FORTH E-mail: dp@csd.uoc.gr, kritikos@ics.forth.gr Office: K.307,
CS 565 Business Process & Workflow Management Systems Professor & Researcher Department of Computer Science, University of Crete & ICS-FORTH E-mail: dp@csd.uoc.gr, kritikos@ics.forth.gr Office: K.307,
Implementing Heuristic Miner for Different Types of Event Logs
 Implementing Heuristic Miner for Different Types of Event Logs Angelina Prima Kurniati 1, GunturPrabawa Kusuma 2, GedeAgungAry Wisudiawan 3 1,3 School of Compuing, Telkom University, Indonesia. 2 School
Implementing Heuristic Miner for Different Types of Event Logs Angelina Prima Kurniati 1, GunturPrabawa Kusuma 2, GedeAgungAry Wisudiawan 3 1,3 School of Compuing, Telkom University, Indonesia. 2 School
Verifying Business Processes Extracted from E-Commerce Systems Using Dynamic Analysis
 Verifying Business Processes Extracted from E-Commerce Systems Using Dynamic Analysis Derek Foo 1, Jin Guo 2 and Ying Zou 1 Department of Electrical and Computer Engineering 1 School of Computing 2 Queen
Verifying Business Processes Extracted from E-Commerce Systems Using Dynamic Analysis Derek Foo 1, Jin Guo 2 and Ying Zou 1 Department of Electrical and Computer Engineering 1 School of Computing 2 Queen
On Global Completeness of Event Logs
 On Global Completeness of Event Logs Hedong Yang 1, Arthur HM ter Hofstede 2,3, B.F. van Dongen 3, Moe T. Wynn 2, and Jianmin Wang 1 1 Tsinghua University, Beijing, China, 10084 yanghd06@mails.tsinghua.edu.cn,jimwang@tsinghua.edu.cn
On Global Completeness of Event Logs Hedong Yang 1, Arthur HM ter Hofstede 2,3, B.F. van Dongen 3, Moe T. Wynn 2, and Jianmin Wang 1 1 Tsinghua University, Beijing, China, 10084 yanghd06@mails.tsinghua.edu.cn,jimwang@tsinghua.edu.cn
Merging Event Logs with Many to Many Relationships
 Merging vent Logs with Many to Many Relationships Lihi Raichelson and Pnina Soffer Department of Information Systems, University of Haifa, Haifa 31905, Israel LihiRaOs@gmail.com, Spnina@is.haifa.ac.il
Merging vent Logs with Many to Many Relationships Lihi Raichelson and Pnina Soffer Department of Information Systems, University of Haifa, Haifa 31905, Israel LihiRaOs@gmail.com, Spnina@is.haifa.ac.il
Dynamic Business Process Management based on Process Change Patterns
 2007 International Conference on Convergence Information Technology Dynamic Business Process Management based on Process Change Patterns Dongsoo Kim 1, Minsoo Kim 2, Hoontae Kim 3 1 Department of Industrial
2007 International Conference on Convergence Information Technology Dynamic Business Process Management based on Process Change Patterns Dongsoo Kim 1, Minsoo Kim 2, Hoontae Kim 3 1 Department of Industrial
MEASURING SOFTWARE FUNCTIONAL SIZE FROM BUSINESS PROCESS MODELS
 International Journal of Software Engineering and Knowledge Engineering World Scientific Publishing Company MEASURING SOFTWARE FUNCTIONAL SIZE FROM BUSINESS PROCESS MODELS CARLOS MONSALVE CIDIS-FIEC, Escuela
International Journal of Software Engineering and Knowledge Engineering World Scientific Publishing Company MEASURING SOFTWARE FUNCTIONAL SIZE FROM BUSINESS PROCESS MODELS CARLOS MONSALVE CIDIS-FIEC, Escuela
Relational XES: Data Management for Process Mining
 Relational XES: Data Management for Process Mining B.F. van Dongen and Sh. Shabani Department of Mathematics and Computer Science, Eindhoven University of Technology, The Netherlands. B.F.v.Dongen, S.Shabaninejad@tue.nl
Relational XES: Data Management for Process Mining B.F. van Dongen and Sh. Shabani Department of Mathematics and Computer Science, Eindhoven University of Technology, The Netherlands. B.F.v.Dongen, S.Shabaninejad@tue.nl
An Outlook on Semantic Business Process Mining and Monitoring
 An Outlook on Semantic Business Process Mining and Monitoring A.K. Alves de Medeiros 1,C.Pedrinaci 2, W.M.P. van der Aalst 1, J. Domingue 2,M.Song 1,A.Rozinat 1,B.Norton 2, and L. Cabral 2 1 Eindhoven
An Outlook on Semantic Business Process Mining and Monitoring A.K. Alves de Medeiros 1,C.Pedrinaci 2, W.M.P. van der Aalst 1, J. Domingue 2,M.Song 1,A.Rozinat 1,B.Norton 2, and L. Cabral 2 1 Eindhoven
PLG: a Framework for the Generation of Business Process Models and their Execution Logs
 PLG: a Framework for the Generation of Business Process Models and their Execution Logs Andrea Burattin and Alessandro Sperduti Department of Pure and Applied Mathematics University of Padua, Italy {burattin,sperduti}@math.unipd.it
PLG: a Framework for the Generation of Business Process Models and their Execution Logs Andrea Burattin and Alessandro Sperduti Department of Pure and Applied Mathematics University of Padua, Italy {burattin,sperduti}@math.unipd.it
Process Mining for Electronic Data Interchange
 Process Mining for Electronic Data Interchange R. Engel 1, W. Krathu 1, C. Pichler 2, W. M. P. van der Aalst 3, H. Werthner 1, and M. Zapletal 1 1 Vienna University of Technology, Austria Institute for
Process Mining for Electronic Data Interchange R. Engel 1, W. Krathu 1, C. Pichler 2, W. M. P. van der Aalst 3, H. Werthner 1, and M. Zapletal 1 1 Vienna University of Technology, Austria Institute for
Personalization of Web Search With Protected Privacy
 Personalization of Web Search With Protected Privacy S.S DIVYA, R.RUBINI,P.EZHIL Final year, Information Technology,KarpagaVinayaga College Engineering and Technology, Kanchipuram [D.t] Final year, Information
Personalization of Web Search With Protected Privacy S.S DIVYA, R.RUBINI,P.EZHIL Final year, Information Technology,KarpagaVinayaga College Engineering and Technology, Kanchipuram [D.t] Final year, Information
EDIminer: A Toolset for Process Mining from EDI Messages
 EDIminer: A Toolset for Process Mining from EDI Messages Robert Engel 1, R. P. Jagadeesh Chandra Bose 2, Christian Pichler 1, Marco Zapletal 1, and Hannes Werthner 1 1 Vienna University of Technology,
EDIminer: A Toolset for Process Mining from EDI Messages Robert Engel 1, R. P. Jagadeesh Chandra Bose 2, Christian Pichler 1, Marco Zapletal 1, and Hannes Werthner 1 1 Vienna University of Technology,
08 BPMN/1. Software Technology 2. MSc in Communication Sciences 2009-10 Program in Technologies for Human Communication Davide Eynard
 MSc in Communication Sciences 2009-10 Program in Technologies for Human Communication Davide Eynard Software Technology 2 08 BPMN/1 2 ntro Sequence of (three?) lessons on BPMN and technologies related
MSc in Communication Sciences 2009-10 Program in Technologies for Human Communication Davide Eynard Software Technology 2 08 BPMN/1 2 ntro Sequence of (three?) lessons on BPMN and technologies related
The Analysis Method about Change Domain of Business Process Model Based on the Behavior Profile of Petri Net
 Appl. Math. Inf. Sci. 6-3S, No. 3, 943-949 (2012) 943 Applied Mathematics & Information Sciences An International Journal The Analysis Method about Change Domain of Business Process Model Based on the
Appl. Math. Inf. Sci. 6-3S, No. 3, 943-949 (2012) 943 Applied Mathematics & Information Sciences An International Journal The Analysis Method about Change Domain of Business Process Model Based on the
Optimised Realistic Test Input Generation
 Optimised Realistic Test Input Generation Mustafa Bozkurt and Mark Harman {m.bozkurt,m.harman}@cs.ucl.ac.uk CREST Centre, Department of Computer Science, University College London. Malet Place, London
Optimised Realistic Test Input Generation Mustafa Bozkurt and Mark Harman {m.bozkurt,m.harman}@cs.ucl.ac.uk CREST Centre, Department of Computer Science, University College London. Malet Place, London
Using Event Logs to Derive Role Engineering Artifacts
 Using Logs to Derive Role Engineering Artifacts Abstract Process-aware information systems are used to execute business processes to reach the operational goals of an organization. In this context, access
Using Logs to Derive Role Engineering Artifacts Abstract Process-aware information systems are used to execute business processes to reach the operational goals of an organization. In this context, access
An Ontology Based Method to Solve Query Identifier Heterogeneity in Post- Genomic Clinical Trials
 ehealth Beyond the Horizon Get IT There S.K. Andersen et al. (Eds.) IOS Press, 2008 2008 Organizing Committee of MIE 2008. All rights reserved. 3 An Ontology Based Method to Solve Query Identifier Heterogeneity
ehealth Beyond the Horizon Get IT There S.K. Andersen et al. (Eds.) IOS Press, 2008 2008 Organizing Committee of MIE 2008. All rights reserved. 3 An Ontology Based Method to Solve Query Identifier Heterogeneity
IDENTIFYING PATTERNS OF WORKFLOW DESIGN RELYING ON ORGANIZATIONAL STRUCTURE ASPECTS
 IDENTIFYING PATTERNS OF WORKFLOW DESIGN RELYING ON ORGANIZATIONAL STRUCTURE ASPECTS Lucinéia Heloisa Thom, Cirano Iochpe Instituto de Informática, Universidade Federal do Rio Grande do Sul, Av.Bento Conçalves,
IDENTIFYING PATTERNS OF WORKFLOW DESIGN RELYING ON ORGANIZATIONAL STRUCTURE ASPECTS Lucinéia Heloisa Thom, Cirano Iochpe Instituto de Informática, Universidade Federal do Rio Grande do Sul, Av.Bento Conçalves,
CPN Tools 4: A Process Modeling Tool Combining Declarative and Imperative Paradigms
 CPN Tools 4: A Process Modeling Tool Combining Declarative and Imperative Paradigms Michael Westergaard 1,2 and Tijs Slaats 3,4 1 Department of Mathematics and Computer Science, Eindhoven University of
CPN Tools 4: A Process Modeling Tool Combining Declarative and Imperative Paradigms Michael Westergaard 1,2 and Tijs Slaats 3,4 1 Department of Mathematics and Computer Science, Eindhoven University of
Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg
 Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Impressum ( 5 TMG) Herausgeber: Otto-von-Guericke-Universität Magdeburg
Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Nr.: Fakultät für Informatik Otto-von-Guericke-Universität Magdeburg Impressum ( 5 TMG) Herausgeber: Otto-von-Guericke-Universität Magdeburg
Discovering process models from empirical data
 Discovering process models from empirical data Laura Măruşter (l.maruster@tm.tue.nl), Ton Weijters (a.j.m.m.weijters@tm.tue.nl) and Wil van der Aalst (w.m.p.aalst@tm.tue.nl) Eindhoven University of Technology,
Discovering process models from empirical data Laura Măruşter (l.maruster@tm.tue.nl), Ton Weijters (a.j.m.m.weijters@tm.tue.nl) and Wil van der Aalst (w.m.p.aalst@tm.tue.nl) Eindhoven University of Technology,
From Business World to Software World: Deriving Class Diagrams from Business Process Models
 From Business World to Software World: Deriving Class Diagrams from Business Process Models WARARAT RUNGWORAWUT 1 AND TWITTIE SENIVONGSE 2 Department of Computer Engineering, Chulalongkorn University 254
From Business World to Software World: Deriving Class Diagrams from Business Process Models WARARAT RUNGWORAWUT 1 AND TWITTIE SENIVONGSE 2 Department of Computer Engineering, Chulalongkorn University 254
Online Compliance Monitoring of Service Landscapes
 Online Compliance Monitoring of Service Landscapes J.M.E.M. van der Werf 1 and H.M.W. Verbeek 2 1 Department of Information and Computing Science, Utrecht University, The Netherlands J.M.E.M.vanderWerf@UU.nl
Online Compliance Monitoring of Service Landscapes J.M.E.M. van der Werf 1 and H.M.W. Verbeek 2 1 Department of Information and Computing Science, Utrecht University, The Netherlands J.M.E.M.vanderWerf@UU.nl
of Business Process Modelling at Suncorp
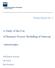 Project Report No. 1 A Study of the Use of Business Process Modelling at Suncorp - Initial Insights - Naif Hassan Alzubidi Jan Recker Eike Bernhard A Study of the Use of Business Process Modelling at Suncorp.
Project Report No. 1 A Study of the Use of Business Process Modelling at Suncorp - Initial Insights - Naif Hassan Alzubidi Jan Recker Eike Bernhard A Study of the Use of Business Process Modelling at Suncorp.
Using Semantic Lifting for improving Process Mining: a Data Loss Prevention System case study
 Using Semantic Lifting for improving Process Mining: a Data Loss Prevention System case study Antonia Azzini, Chiara Braghin, Ernesto Damiani, Francesco Zavatarelli Dipartimento di Informatica Università
Using Semantic Lifting for improving Process Mining: a Data Loss Prevention System case study Antonia Azzini, Chiara Braghin, Ernesto Damiani, Francesco Zavatarelli Dipartimento di Informatica Università
Structural Detection of Deadlocks in Business Process Models
 Structural Detection of Deadlocks in Business Process Models Ahmed Awad and Frank Puhlmann Business Process Technology Group Hasso Plattner Institut University of Potsdam, Germany (ahmed.awad,frank.puhlmann)@hpi.uni-potsdam.de
Structural Detection of Deadlocks in Business Process Models Ahmed Awad and Frank Puhlmann Business Process Technology Group Hasso Plattner Institut University of Potsdam, Germany (ahmed.awad,frank.puhlmann)@hpi.uni-potsdam.de
Trace Clustering in Process Mining
 Trace Clustering in Process Mining M. Song, C.W. Günther, and W.M.P. van der Aalst Eindhoven University of Technology P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. {m.s.song,c.w.gunther,w.m.p.v.d.aalst}@tue.nl
Trace Clustering in Process Mining M. Song, C.W. Günther, and W.M.P. van der Aalst Eindhoven University of Technology P.O.Box 513, NL-5600 MB, Eindhoven, The Netherlands. {m.s.song,c.w.gunther,w.m.p.v.d.aalst}@tue.nl
EXPLOITING FOLKSONOMIES AND ONTOLOGIES IN AN E-BUSINESS APPLICATION
 EXPLOITING FOLKSONOMIES AND ONTOLOGIES IN AN E-BUSINESS APPLICATION Anna Goy and Diego Magro Dipartimento di Informatica, Università di Torino C. Svizzera, 185, I-10149 Italy ABSTRACT This paper proposes
EXPLOITING FOLKSONOMIES AND ONTOLOGIES IN AN E-BUSINESS APPLICATION Anna Goy and Diego Magro Dipartimento di Informatica, Università di Torino C. Svizzera, 185, I-10149 Italy ABSTRACT This paper proposes
A business process metamodel for Enterprise Information Systems automatic generation
 A business process metamodel for Enterprise Information Systems automatic generation Luiz Fernando Batista Loja 1, Valdemar Vicente Graciano Neto 1, Sofia Larissa da Costa 1, Juliano Lopes de Oliveira
A business process metamodel for Enterprise Information Systems automatic generation Luiz Fernando Batista Loja 1, Valdemar Vicente Graciano Neto 1, Sofia Larissa da Costa 1, Juliano Lopes de Oliveira
AMFIBIA: A Meta-Model for the Integration of Business Process Modelling Aspects
 AMFIBIA: A Meta-Model for the Integration of Business Process Modelling Aspects Björn Axenath, Ekkart Kindler, Vladimir Rubin Software Engineering Group, University of Paderborn, Warburger Str. 100, D-33098
AMFIBIA: A Meta-Model for the Integration of Business Process Modelling Aspects Björn Axenath, Ekkart Kindler, Vladimir Rubin Software Engineering Group, University of Paderborn, Warburger Str. 100, D-33098
Building Ontology Networks: How to Obtain a Particular Ontology Network Life Cycle?
 See discussions, stats, and author profiles for this publication at: http://www.researchgate.net/publication/47901002 Building Ontology Networks: How to Obtain a Particular Ontology Network Life Cycle?
See discussions, stats, and author profiles for this publication at: http://www.researchgate.net/publication/47901002 Building Ontology Networks: How to Obtain a Particular Ontology Network Life Cycle?
Process Mining Framework for Software Processes
 Process Mining Framework for Software Processes Vladimir Rubin 1,2, Christian W. Günther 1, Wil M.P. van der Aalst 1, Ekkart Kindler 2, Boudewijn F. van Dongen 1, and Wilhelm Schäfer 2 1 Eindhoven University
Process Mining Framework for Software Processes Vladimir Rubin 1,2, Christian W. Günther 1, Wil M.P. van der Aalst 1, Ekkart Kindler 2, Boudewijn F. van Dongen 1, and Wilhelm Schäfer 2 1 Eindhoven University
A Research Article on Data Mining in Addition to Process Mining: Similarities and Dissimilarities
 A Research Article on Data Mining in Addition to Process Mining: Similarities and Dissimilarities S. Sowjanya Chintalapati 1, Ch.G.V.N.Prasad 2, J. Sowjanya 3, R.Vineela 4 1, 3, 4 Assistant Professor,
A Research Article on Data Mining in Addition to Process Mining: Similarities and Dissimilarities S. Sowjanya Chintalapati 1, Ch.G.V.N.Prasad 2, J. Sowjanya 3, R.Vineela 4 1, 3, 4 Assistant Professor,
Separating Compliance Management and Business Process Management
 Separating Compliance Management and Business Process Management Elham Ramezani 1, Dirk Fahland 2, Jan Martijn van der Werf 2, and Peter Mattheis 1 1 Hochschule Furtwangen, Germany (ramezani Peter.Mattheis)@hs-furtwangen.de
Separating Compliance Management and Business Process Management Elham Ramezani 1, Dirk Fahland 2, Jan Martijn van der Werf 2, and Peter Mattheis 1 1 Hochschule Furtwangen, Germany (ramezani Peter.Mattheis)@hs-furtwangen.de
Generating Web Applications from Process Models
 Generating Web Applications from Process Models Jan Schulz-Hofen, Silvan Golega Hasso-Plattner-Institute for Software Systems Engineering Prof.-Dr.-Helmert-Str. 2-3 D-14482 Potsdam, Germany {jan.schulz-hofen,
Generating Web Applications from Process Models Jan Schulz-Hofen, Silvan Golega Hasso-Plattner-Institute for Software Systems Engineering Prof.-Dr.-Helmert-Str. 2-3 D-14482 Potsdam, Germany {jan.schulz-hofen,
The Ontology and Architecture for an Academic Social Network
 www.ijcsi.org 22 The Ontology and Architecture for an Academic Social Network Moharram Challenger Computer Engineering Department, Islamic Azad University Shabestar Branch, Shabestar, East Azerbaijan,
www.ijcsi.org 22 The Ontology and Architecture for an Academic Social Network Moharram Challenger Computer Engineering Department, Islamic Azad University Shabestar Branch, Shabestar, East Azerbaijan,
Process Mining by Measuring Process Block Similarity
 Process Mining by Measuring Process Block Similarity Joonsoo Bae, James Caverlee 2, Ling Liu 2, Bill Rouse 2, Hua Yan 2 Dept of Industrial & Sys Eng, Chonbuk National Univ, South Korea jsbae@chonbukackr
Process Mining by Measuring Process Block Similarity Joonsoo Bae, James Caverlee 2, Ling Liu 2, Bill Rouse 2, Hua Yan 2 Dept of Industrial & Sys Eng, Chonbuk National Univ, South Korea jsbae@chonbukackr
Linking BPMN, ArchiMate, and BWW: Perfect Match for Complete and Lawful Business Process Models?
 Linking BPMN, ArchiMate, and BWW: Perfect Match for Complete and Lawful Business Process Models? Ludmila Penicina Institute of Applied Computer Systems, Riga Technical University, 1 Kalku, Riga, LV-1658,
Linking BPMN, ArchiMate, and BWW: Perfect Match for Complete and Lawful Business Process Models? Ludmila Penicina Institute of Applied Computer Systems, Riga Technical University, 1 Kalku, Riga, LV-1658,
Chapter XXI Business Process Intelligence
 467 Chapter XXI Business Process Intelligence M. Castellanos Hewlett-Packard Laboratories, USA A. K. Alves de Medeiros Eindhoven University of Technology, The Netherlands J. Mendling Queensland University
467 Chapter XXI Business Process Intelligence M. Castellanos Hewlett-Packard Laboratories, USA A. K. Alves de Medeiros Eindhoven University of Technology, The Netherlands J. Mendling Queensland University
Business Independent Model of Mobile Workforce Management
 Business Independent Model of Mobile Workforce Management Volker Gruhn and Thomas Richter Chair of Applied Telematics / e-business, University of Leipzig Klostergasse 3, 04109 Leipzig, Germany {gruhn,richter}@ebus.informatik.uni-leipzig.de
Business Independent Model of Mobile Workforce Management Volker Gruhn and Thomas Richter Chair of Applied Telematics / e-business, University of Leipzig Klostergasse 3, 04109 Leipzig, Germany {gruhn,richter}@ebus.informatik.uni-leipzig.de
