Digital Work Habits: Research Report
|
|
|
- Conrad Archibald Byrd
- 8 years ago
- Views:
Transcription
1 Digital Work Habits: Research Report Contents Executive Summary...2 Methodology...3 Findings: Who Responded...3 Work Styles...4 Risks...7 Other Digital Habits...8 Conclusions and Recommendations...9 Appendix...11
2 Executive Summary Back in 2010, Microsoft reported there were approximately one billion Outlook installations worldwide. i It s not news that is the hub of the digital work environment. However, it s easy to overlook that is a collaboration tool the go-to platform for communicating and coordinating with co-workers, partners, and customers. can be a powerful productivity booster, but it can also be a time sink, a source of embarrassment if misused, or at worst, a security risk. and other collaboration tools in the workplace are also a topic for serious study. One of the key findings in this area is that our ability to quickly connect with others has led to a new style of work. According to London School of Economics Professor of Sociology Judy Wajcman, work in the digital office could be characterized as highly interrupted. But as she delved more deeply she noticed that people have actually integrated all these technologies into their work processes and organized their work in particular ways. They didn t use the concept of interruptions. They just thought this is how they do their work now. ii In the spirit of Wajcman, we decided to learn about usage in the digital office. Not only did we survey metrics daily volumes, time spent managing s but we were also interested in understanding the user behaviors surrounding s. Our survey bears out Wajcman s overall assessment. Almost 45% of those surveyed are receiving between 50 and 300 s per day. While s are now an established part of our work, at some point even Wajcman understands they become an interruption. The survey shows that 20% are immersed in their inbox between 30 and 60 minutes, and another 16% are spending over an hour per day, or more than five hours per week, organizing s. Time spent searching, categorizing, and deleting on a daily basis is time taken away from the work that is supposed to be enabling. Has this interrupted work style led to an increase in communication mishaps more accidental reply-alls or internal s seen by clients or an meant for a coworker sent to the CEO? Our findings indicate that miscommunications are not an unusual occurrence: 62% reported some kind of damaging being sent. While the consequences varied, the most common result reported was embarrassment of the parties involved in exchange (64%). However, there were more serious outcomes, including job loss (12%) and even compliance violations (6%).
3 Methodology In September of 2012, Varonis published an 11-question survey, which was distributed to IT personnel and security staff. We received 127 responses from 92 different organizations. The survey was constructed to: Measure the daily volume employees receive Assess how workers manage their , and how much time they spend doing this Determine the frequency and severity of mistakes Understand how employees handle other digital distractions at work Findings: Who Responded In categorizing the responses, the sample was almost evenly split between small-to-medium sized businesses (typically defined to be fewer than 1000 employees) and the enterprise environment. We received a wide range of job titles from CEO to IT analysts and everything in between. To simplify our analysis we organized titles into three broad categories: C-level, Manager, and Employee. Not surprisingly, more than 90% of survey responders came from the Manager and Employee categories this should be kept in mind when reviewing the results.
4 Overall managers and employees are heavily engaged with their s. About 45% receive between 50 and 300 s per day and another 17% are in the message bucket. There s even an elite being bombarded with over 300 daily s. Our repsondents are also conscientous about reading their . About 14% claimed there are no unread s in their inbox. And another 23% have fewer than 10 unread s. How much time is all this taking? The largest segment, or 44%, are spending up to 30 minutes per day taming and managing their s. With this -centric sample, we re not surprised that over 20% are spending up to 1 hour and sizeable minority (16%) are focused on managing their inboxes more than one hour per day. Work Styles One question we wanted to look at is whether there is a relationship between job title and volumes. Wajcman has conjectured that our digital work habits have been influenced by a flattening in organizational structure so that both managers and their groups are tasked with greater workload and the s that come with this. To explore this, we categorized all the job titles into C-level, Manager, and Employee. We were especially interested in comparing Employees against Managers. Our results show the Employee s daily volume is skewed towards the higher end, with more than 25% receiving over 100 s per day. The Manager group is a little more even-keeled with a mere 6% experiencing over 100 s per day and a little over half dealing with a manageable A statistical test for independence between Employee and Manager indicates there s some evidence for saying these two groups have different patterns.
5 It is possible to interpret our results as validating Wajcman s insights about some non-managers having taken over tasks from other employees. volumes are a signature of their growing responsibilities as their network of contacts has expanded. C-levels are clearly immersed in their . Our sample size for this statistic is small, but over one-third reported receiving over 100 s per day. But it is not surprising that CEOs will see extremes: as the hub in an chain, a disproportionate number of s should naturally land in the CEO s inbox. We also tried to pin down the organizational habits of users. Respondents were asked to classify themselves as filers (they leave a clean inbox), hoarders (never delete, but file and tag), mixture (some filing and some hoarding), and out-of-control (given up on organizing). Over 34% of those surveyed the filers are emptying their on a daily basis (after reading them, of course). The hoarders make up 19% of the survey group. Around 40% are a hybrid of both patterns. And there was a small but telling niche of 6% that has admitted to completely giving up on managing their inboxes. We undertook an analysis comparing the time spent on s between the three derived job categories. After testing for independence, we are on firmer statistical ground in saying that Employees and Managers share similar time profiles. At the extreme end, between 13% and 20% of both groups report spending more than 1 hour managing their s. And they share similar percentages in the minute rate: 22% of Employees, and 25% of managers.
6 This suggests Wajcman s point that is simply part of the work culture, not just an interruption, even at the top of the corporate hierarchy. To validate this view, one only has to look at the C-level group. Although the sample size is small, it s still revealing that executive suite is reporting spending over 1 hour per day managing and organizing s. We also wanted to look at daily volumes against company size. We see similar profiles in the SMB range, and into the lower end of the enterprise space. It further validates that is as much a part of the office environment as cube walls and furniture. Another way to break down the time spent on is to view it through the lens of the different organizing classifications filers, hoarders, hybrids, and out-of-control. We compared these categories against the time spent on s. The most revealing pattern is in the group that has given up on their s. It s characterized by extremes: almost 30% spend over an hour managing and organizing, and approximately 60% spend under 5 minutes. Perhaps they spend a few minutes looking for a specific subject line and then give up, or else for an important , they spend hours searching? For the other categories it s clear that investing in some management pays off in terms of reducing time spent in the inbox.
7 In trying to understand whether employees were applying any technologies to help organize and manage s, we asked about the use of automatic rules. The results were not encouraging: more than 80% had few or no automatic procedures to handle their inbox. management for most remains a time-intensive and hands-on activity. Finally, we were curious about who was in the Inbox Zero club i.e., those reporting fewer than 10 unread s in their inbox. Again, we re not surprised that the Employee and Manager categories share a similar profile. The -focused C-level group, however, did reveal there were a few CEOs who couldn t keep up with their daily volumes. Risks With now a permanent part of our work routines, there s always a danger of misuse and other risks. We asked what was the most damaging someone from your company has sent by mistake? The answers came back in free form text. For anyone who has ever hit reply-all by accident most of us, I suspect many of the answers will not be surprising. Here are a few representative responses: Inappropriate jokes intended for one person sent to another Internal communications accidentally sent to clients Long cc list of addresses that should have been placed in bcc
8 As we might expect based on our own experiences, mistakes with addressing and other messaging mishaps are not uncommon. About 62% of our sample responded with a story about an accident. And as we also might have guessed, the consequences were typically limited to embarrassment: 64% reporting that one or more parties were embarrassed by an errant . There were more serious outcomes, however, including job loss (even at the CEO level), confidentially breaches, compliance issues, and even an incident of a corporate fine. Other Digital Habits As a final question, we wanted to briefly explore how workers are using their internet connection for non-worked related activities. Almost one-third reported they had no such use for the web; 43% scan web sites for news; 8.5% reported being addicted to Facebook; and 2% reported downloading or streaming music from web sites. The survey conforms with the popular cultural view of the Web as an on-line meeting and entertainment resource the digital equivalent of a virtual coffee break with on-line friends. For some, it is an additional source of interruption.
9 Conclusions and Recommendations We agree with Professor Wajcman s view that has become a vital part of the way we work. But it s clear that at some point high volumes can affect productivity, and mistakes can lead to potential legal and compliance issues affecting the entire organization. The survey reveals that large daily incoming traffic is a pattern seen across different sized companies and different job categories -- there s no escaping the onslaught. The bigger challenge is how to best to use and manage s, and reduce risks associated with correspondence. Some could simply decide not to keep pace with since it is, for many, a losing race. For those who do run this race, queuing theory has bad news: unless you can service s in less time than the inter-arrival periods on average, you ll end up with a very, very long queue of backlogged messages. For practical purposes, assuming you re one of the 17% in the 100 per day club, you ll have to run a below-five minute sprint per . A different viewpoint comes to us by way of the call center world. They ve had a global writable inbox, called an 800 number, for far longer than addresses have been around. But the telecom industry has evolved and developed different techniques, some of them transferable to the data messaging environment, to speed overall throughput while also improving the waiting experience. Wajcman s ideas on filtering are especially relevant here. Call centers use skills-based or expert routing to direct incoming connections to the appropriate resource. A similar routing concept could be applied to s, guiding messages to the right endpoint based on scanning content and subject lines. In fact, this is an approach taken by help and support desk ticketing software. The question is whether these specialized routing techniques will migrate into general enterprise platforms. Perhaps with even more sophisticated intelligence, a real-time dashboard could be embedded in the client app, display the delay time for sendees to expect based on their current unanswered s, schedules, and to-do tasks. In other words, servers may need to provide the equivalent of a call center s message-on-hold perhaps showing their position numbers after employees hit the send key. There are short-term solutions that have been taken up by some companies. Employees can broadcast an bankruptcy notice to force co-workers to resend what is likely the most important content. Other organizations have been experimenting with an blackout one day a week, wherein workers communicate using other means either phone calls or perhaps an antiquated house call.
10 Finally, here are a few quick tips that may help your experience today: Before clicking on send, create and follow a checklist especially if the is in any way sensitive Verify contact in the to:, cc:, and bcc: fields Check the subject line for errors and typos (spell check doesn t always work there) Verify that attachments are the documents you wish others to read Do you really want to hit send? If you re not using automatic rules to filter and route s, you should be Learn Outlook s query syntax to narrow down searches. For example, to:jane lists all s sent to Jane Experiment with turning off audible and visible notifications, or limiting them to VIPs, and then check on your own schedule i About that 1 billion Microsoft Office figure, ZDNet (2010) ii Executive Leadership and Innovation Interview: Professor Judy Wajcman Discusses the Sociology of Technology and the Work-Life Balance, Gartner, Inc. (2011)
11 Appendix The following charts show the survey results for questions not presented in the body of the report:
12 ABOUT VARONIS SYSTEMS Varonis is the leader in unstructured and semi-structured data governance software. Based on patented technology and a highly accurate analytics engine, Varonis solutions give organizations total visibility and control over their data, ensuring that only the right users have access to the right data at all times from all devices, all use is monitored, and abuse is flagged. Varonis makes digital collaboration secure, effortless and efficient so that people can create and share content easily with whom they must, and organizations can be confident their content is protected and managed efficiently. Voted one of the «Fast 50 Reader Favorites» on FastCompany.com, and winner of the SC Magazine Innovation, Product or Service of the Year, and Best Network Security Awards, Varonis has more than 4,500 installations worldwide and is headquartered in New York, with regional offices in Europe, Asia and Latin America. Varonis, the Varonis logo, DatAdvantage, DataPrivilege and the IDU Classification Framework are registered trademarks of Varonis Systems in the United States and/or other countries and Metadata Framework, DatAnywhere, and Data Transport Engine are under a registration process in the United States and/or other countries. All other product and company names and marks mentioned in this document are the property of their respective owners and are mentioned for identification purposes only. WORLDWIDE HEADQUARTERS 1250 Broadway, 31st Floor New York, NY Phone: sales@varonis.com EUROPE, MIDDLE EAST AND AFRICA 55 Old Broad Street London, United Kingdom EC2M 1RX Phone: +44(0) sales-europe@varonis.com
10 Things IT Should be Doing (But Isn t)
 Contents Overview...1 Top Ten Things IT Should be Doing...2 Audit Data Access... 2 Inventory Permissions and Directory Services Group Objects... 2 Prioritize Which Data Should Be Addressed... 2 Remove
Contents Overview...1 Top Ten Things IT Should be Doing...2 Audit Data Access... 2 Inventory Permissions and Directory Services Group Objects... 2 Prioritize Which Data Should Be Addressed... 2 Remove
Big Data and Infosecurity: Research Report
 Big Data and Infosecurity: Research Report Contents Big Data and Infosecurity: Research Report... 1 Table of Contents... 1 Executive Summary... 2 Methodology... 2 Findings... 3 Who responded?... 3 What
Big Data and Infosecurity: Research Report Contents Big Data and Infosecurity: Research Report... 1 Table of Contents... 1 Executive Summary... 2 Methodology... 2 Findings... 3 Who responded?... 3 What
VARONIS WHITEPAPER Next Generation Enterprise Search
 VARONIS WHITEPAPER Next Generation Enterprise Search CONTENTS OVERVIEW 3 SEARCHING FOR SEARCH 4 A NEW APPROACH 5 Better results 5 Faster Results 5 Secure Results 5 Convenient Results 5 2 NEXT GENERATION
VARONIS WHITEPAPER Next Generation Enterprise Search CONTENTS OVERVIEW 3 SEARCHING FOR SEARCH 4 A NEW APPROACH 5 Better results 5 Faster Results 5 Secure Results 5 Convenient Results 5 2 NEXT GENERATION
Varonis: Secure Enterprise Collaboration and File Sharing Date: June 2015 Author: Terri McClure, Senior Analyst; and Leah Matuson, Research Analyst
 ESG Brief Varonis: Secure Enterprise Collaboration and File Sharing Date: June 2015 Author: Terri McClure, Senior Analyst; and Leah Matuson, Research Analyst Abstract: With the burgeoning workplace mobility
ESG Brief Varonis: Secure Enterprise Collaboration and File Sharing Date: June 2015 Author: Terri McClure, Senior Analyst; and Leah Matuson, Research Analyst Abstract: With the burgeoning workplace mobility
Accelerating Audits with Automation: Who s Accessing Your Unstructured Data?
 Contents of This Paper Available Tools... 2 The Solution... 2 A Closer Look... 2 Accessing Folders... 3 Who s Authorizing Users... 4 Tracking Key Files... 5 Tracking the Last User of a File... 5 Matching
Contents of This Paper Available Tools... 2 The Solution... 2 A Closer Look... 2 Accessing Folders... 3 Who s Authorizing Users... 4 Tracking Key Files... 5 Tracking the Last User of a File... 5 Matching
Dynamics CRM for Outlook Basics
 Dynamics CRM for Outlook Basics Microsoft Dynamics CRM April, 2015 Contents Welcome to the CRM for Outlook Basics guide... 1 Meet CRM for Outlook.... 2 A new, but comfortably familiar face................................................................
Dynamics CRM for Outlook Basics Microsoft Dynamics CRM April, 2015 Contents Welcome to the CRM for Outlook Basics guide... 1 Meet CRM for Outlook.... 2 A new, but comfortably familiar face................................................................
VARONIS CASE STUDY. Heemskerk Municipality
 VARONIS CASE STUDY We are using DatAdvantage to determine the people who own a lot of data so we can then speak to them about their requirements. Using the reports we can show them how much space they
VARONIS CASE STUDY We are using DatAdvantage to determine the people who own a lot of data so we can then speak to them about their requirements. Using the reports we can show them how much space they
VARONIS CASE STUDY Children's Hospital of Wisconsin
 VARONIS CASE STUDY Children's Hospital of Wisconsin As a security professional, DatAdvantage fills a very important need for me. I have not seen another product that can do what DatAdvantage does. Without
VARONIS CASE STUDY Children's Hospital of Wisconsin As a security professional, DatAdvantage fills a very important need for me. I have not seen another product that can do what DatAdvantage does. Without
Guide. Email is vital - but it s not your business!
 Email is vital - but it s not your business! Businesses around the world send around 100 billion emails every day and the volume shows no sign of abating any time soon. Indeed, according to research from
Email is vital - but it s not your business! Businesses around the world send around 100 billion emails every day and the volume shows no sign of abating any time soon. Indeed, according to research from
VARONIS RESEARCH PAPER. Information Entropy. Information Entropy
 VARONIS RESEARCH PAPER 1 CONTENTS EXECUTIVE SUMMARY 3 METHODOLOGY 5 WHO RESPONDED 5 PROTECTING IP AND NDAS 6 DATA LEAKAGE AND ENTROPY 8 NDAS AND ENTROPY 9 GAUGING THE SIZE OF LIKELY LEAKERS 10 IP LEAKAGE
VARONIS RESEARCH PAPER 1 CONTENTS EXECUTIVE SUMMARY 3 METHODOLOGY 5 WHO RESPONDED 5 PROTECTING IP AND NDAS 6 DATA LEAKAGE AND ENTROPY 8 NDAS AND ENTROPY 9 GAUGING THE SIZE OF LIKELY LEAKERS 10 IP LEAKAGE
This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet Web site references, may
 This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet Web site references, may change without notice. Some examples depicted herein are
This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet Web site references, may change without notice. Some examples depicted herein are
VARONIS WHITEPAPER. Mastering the Information Explosion
 VARONIS WHITEPAPER CONTENTS INTRODUCTION 3 UNSTRUCTURED DATA 4 80% of Your Data is Unstructured 4 Unstructured Data Growth Is Exponential 4 A Greater Portion of it Needs to be Managed and Secured 4 Complexity
VARONIS WHITEPAPER CONTENTS INTRODUCTION 3 UNSTRUCTURED DATA 4 80% of Your Data is Unstructured 4 Unstructured Data Growth Is Exponential 4 A Greater Portion of it Needs to be Managed and Secured 4 Complexity
VARONIS CASE STUDY. HIT Entertainment
 VARONIS CASE STUDY Once we deployed Varonis DatAdvantage, we were able to identify excessive permissions within seconds; previously, this process took days or even, in some cases, weeks. James Herbert
VARONIS CASE STUDY Once we deployed Varonis DatAdvantage, we were able to identify excessive permissions within seconds; previously, this process took days or even, in some cases, weeks. James Herbert
Managing Agile Projects in TestTrack GUIDE
 Managing Agile Projects in TestTrack GUIDE Table of Contents Introduction...1 Automatic Traceability...2 Setting Up TestTrack for Agile...6 Plan Your Folder Structure... 10 Building Your Product Backlog...
Managing Agile Projects in TestTrack GUIDE Table of Contents Introduction...1 Automatic Traceability...2 Setting Up TestTrack for Agile...6 Plan Your Folder Structure... 10 Building Your Product Backlog...
The 5-Minute Guide to Customer Support
 Tame the Email Monster Moving Customer Support from Email to a Help Desk to Boost Efficiency July 2011 Table of Contents Executive Summary... 3 The Global Inbox... 4 Does Email Scale As Your Business Grows?...
Tame the Email Monster Moving Customer Support from Email to a Help Desk to Boost Efficiency July 2011 Table of Contents Executive Summary... 3 The Global Inbox... 4 Does Email Scale As Your Business Grows?...
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE
 CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
WHITE PAPER. Creating your Intranet Checklist
 WHITE PAPER Creating your Intranet Checklist About this guide It can be overwhelming to run and manage an Intranet project. As a provider of Intranet software and services to small, medium and large organizations,
WHITE PAPER Creating your Intranet Checklist About this guide It can be overwhelming to run and manage an Intranet project. As a provider of Intranet software and services to small, medium and large organizations,
T 410 585 9505 E TMcDonough@AInfoSys.com W www.ainfosys.com VARONIS DATA GOVERNANCE SUITE
 T 410 585 9505 E TMcDonough@AInfoSys.com W www.ainfosys.com VARONIS DATA GOVERNANCE SUITE VARONIS DATA GOVERNANCE SUITE Features and Benefits FULLY INTEGRATED SOLUTIONS Varonis DatAdvantage for Windows
T 410 585 9505 E TMcDonough@AInfoSys.com W www.ainfosys.com VARONIS DATA GOVERNANCE SUITE VARONIS DATA GOVERNANCE SUITE Features and Benefits FULLY INTEGRATED SOLUTIONS Varonis DatAdvantage for Windows
WEBSENSE TRITON SOLUTIONS
 WEBSENSE TRITON SOLUTIONS INNOVATIVE SECURITY FOR WEB, EMAIL, DATA AND MOBILE TRITON STOPS MORE THREATS. WE CAN PROVE IT. PROTECTION AS ADVANCED AND DYNAMIC AS THE THREATS THEMSELVES The security threats
WEBSENSE TRITON SOLUTIONS INNOVATIVE SECURITY FOR WEB, EMAIL, DATA AND MOBILE TRITON STOPS MORE THREATS. WE CAN PROVE IT. PROTECTION AS ADVANCED AND DYNAMIC AS THE THREATS THEMSELVES The security threats
Microsoft Outlook 2010 Hints & Tips
 IT Services Microsoft Outlook 2010 Hints & Tips Contents Introduction... 1 What Outlook Starts Up In... 1 Sending Email Hints... 2 Tracking a Message... 2 Saving a Sent Item... 3 Delay Delivery of a Single
IT Services Microsoft Outlook 2010 Hints & Tips Contents Introduction... 1 What Outlook Starts Up In... 1 Sending Email Hints... 2 Tracking a Message... 2 Saving a Sent Item... 3 Delay Delivery of a Single
The Business Case for Data Governance
 Contents of This White Paper Data Governance...1 Why Today s Solutions Fall Short...2 Use Cases...3 Reviewing Data Permissions... 3 Reviewing Data Permissions with Varonis... 3 Reviewing User and Group
Contents of This White Paper Data Governance...1 Why Today s Solutions Fall Short...2 Use Cases...3 Reviewing Data Permissions... 3 Reviewing Data Permissions with Varonis... 3 Reviewing User and Group
VARONIS CASE STUDY THE HAGADONE CORPORATION
 VARONIS CASE STUDY THE HAGADONE CORPORATION Having the information available to bring to each company or their data holder and say, You guys don t actually need this access and you can get rid of this
VARONIS CASE STUDY THE HAGADONE CORPORATION Having the information available to bring to each company or their data holder and say, You guys don t actually need this access and you can get rid of this
v1.5, updated 05 September 2012 IHS-IT Workshop Outlook 2010 Ilse Herzinger / Daniela Rader, June 2012
 v1.5, updated 05 September 2012 IHS-IT Workshop Outlook 2010 Ilse Herzinger / Daniela Rader, June 2012 Warning IHS-IT will never ever ask for your password! E-Mails asking for some kind of account verification
v1.5, updated 05 September 2012 IHS-IT Workshop Outlook 2010 Ilse Herzinger / Daniela Rader, June 2012 Warning IHS-IT will never ever ask for your password! E-Mails asking for some kind of account verification
A RE YOU SUFFERING FROM A DATA PROBLEM?
 June 2012 A RE YOU SUFFERING FROM A DATA PROBLEM? DO YOU NEED A DATA MANAGEMENT STRATEGY? Most businesses today suffer from a data problem. Yet many don t even know it. How do you know if you have a data
June 2012 A RE YOU SUFFERING FROM A DATA PROBLEM? DO YOU NEED A DATA MANAGEMENT STRATEGY? Most businesses today suffer from a data problem. Yet many don t even know it. How do you know if you have a data
MICROSOFT OUTLOOK 2010
 MICROSOFT OUTLOOK 2010 George W. Rumsey Computer Resource Center 1525 East 53rd, Suite 906 Chicago, IL 60615 (773) 955-4455 www.computer-resource.com gwrumsey@att.net What Is Outlook?... 1 Folders... 2
MICROSOFT OUTLOOK 2010 George W. Rumsey Computer Resource Center 1525 East 53rd, Suite 906 Chicago, IL 60615 (773) 955-4455 www.computer-resource.com gwrumsey@att.net What Is Outlook?... 1 Folders... 2
Mothernode CRM ENTERPRISE (ERP) EDITION
 Mothernode CRM ENTERPRISE (ERP) EDITION Everything you need to run your business from sales to order fulfillment, inventory management to invoicing, and much more. Mothernode CRM The easiest way to run
Mothernode CRM ENTERPRISE (ERP) EDITION Everything you need to run your business from sales to order fulfillment, inventory management to invoicing, and much more. Mothernode CRM The easiest way to run
SOCIAL MEDIA ADVERTISING STRATEGIES THAT WORK
 SOCIAL MEDIA ADVERTISING STRATEGIES THAT WORK ABSTRACT» Social media advertising is a new and fast growing part of digital advertising. In this White Paper I'll present social media advertising trends,
SOCIAL MEDIA ADVERTISING STRATEGIES THAT WORK ABSTRACT» Social media advertising is a new and fast growing part of digital advertising. In this White Paper I'll present social media advertising trends,
Module One: Getting Started... 6. Opening Outlook... 6. Setting Up Outlook for the First Time... 7. Understanding the Interface...
 2 CONTENTS Module One: Getting Started... 6 Opening Outlook... 6 Setting Up Outlook for the First Time... 7 Understanding the Interface...12 Using Backstage View...14 Viewing Your Inbox...15 Closing Outlook...17
2 CONTENTS Module One: Getting Started... 6 Opening Outlook... 6 Setting Up Outlook for the First Time... 7 Understanding the Interface...12 Using Backstage View...14 Viewing Your Inbox...15 Closing Outlook...17
The Guide to: Email Marketing Analytics"
 The Guide to: Email Marketing Analytics" This guide has been lovingly created by Sign-Up.to we provide email marketing, mobile marketing and social media tools and services to organisations of all shapes
The Guide to: Email Marketing Analytics" This guide has been lovingly created by Sign-Up.to we provide email marketing, mobile marketing and social media tools and services to organisations of all shapes
National Cyber Security Month 2015: Daily Security Awareness Tips
 National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
A journey to effective travel expense administration
 A journey to effective travel expense administration Lexmark integrated Perceptive Content with SAP to streamline the management of travel expenses and gain greater control of costs Like most global organizations,
A journey to effective travel expense administration Lexmark integrated Perceptive Content with SAP to streamline the management of travel expenses and gain greater control of costs Like most global organizations,
VARONIS CASE STUDY. Matanuska Telephone Association (MTA)
 VARONIS CASE STUDY On a regular basis, DatAdvantage gives me insight into our day-to-day operations. Finn Rye, Information Security Officer, MTA 2 THE CUSTOMER LOCATION Palmer, Alaska INDUSTRY Telecommunications
VARONIS CASE STUDY On a regular basis, DatAdvantage gives me insight into our day-to-day operations. Finn Rye, Information Security Officer, MTA 2 THE CUSTOMER LOCATION Palmer, Alaska INDUSTRY Telecommunications
Email at Bradford - Outlook
 This document provides guidance for staff using Office 365 with Microsoft Outlook 2010 for email at the University of Bradford. The University of Bradford retains copyright for this material, which may
This document provides guidance for staff using Office 365 with Microsoft Outlook 2010 for email at the University of Bradford. The University of Bradford retains copyright for this material, which may
E-MAIL DEFENDER SERVICES
 E-MAIL DEFENDER SERVICES Email Defender User Guide 2015-02-12 What does E-Mail Defender do? Anti-Virus testing to eliminate known and suspected viruses. Blacklist services check distributed lists for fingerprints
E-MAIL DEFENDER SERVICES Email Defender User Guide 2015-02-12 What does E-Mail Defender do? Anti-Virus testing to eliminate known and suspected viruses. Blacklist services check distributed lists for fingerprints
E-Mail Management First Edition
 Assessment E-Mail Management First Edition The objectives of this book are to help the user: Take control of incoming e-mail to reduce inbox clutter and increase efficiency Learn about Microsoft Outlook
Assessment E-Mail Management First Edition The objectives of this book are to help the user: Take control of incoming e-mail to reduce inbox clutter and increase efficiency Learn about Microsoft Outlook
Copyright 2011 Smart VA Ltd All Rights Reserved.
 Copyright 2011 Smart VA Ltd All Rights Reserved. No part of this guide may be reproduced or transmitted in any form whatsoever, electronic, or mechanical, including photocopying, recording, or by any informational
Copyright 2011 Smart VA Ltd All Rights Reserved. No part of this guide may be reproduced or transmitted in any form whatsoever, electronic, or mechanical, including photocopying, recording, or by any informational
EMAIL QUICK START GUIDE
 IT Services Microsoft Outlook 2010 EMAIL QUICK START GUIDE Contents What is Outlook?...2 Quick Guide to Email...2 Create a new e-mail message...2 Forward or reply to an e-mail message...2 Creating new
IT Services Microsoft Outlook 2010 EMAIL QUICK START GUIDE Contents What is Outlook?...2 Quick Guide to Email...2 Create a new e-mail message...2 Forward or reply to an e-mail message...2 Creating new
Microsoft Outlook 2010
 Microsoft Outlook 2010 Prepared by Computing Services at the Eastman School of Music July 2010 Contents Microsoft Office Interface... 4 File Ribbon Tab... 5 Microsoft Office Quick Access Toolbar... 6 Appearance
Microsoft Outlook 2010 Prepared by Computing Services at the Eastman School of Music July 2010 Contents Microsoft Office Interface... 4 File Ribbon Tab... 5 Microsoft Office Quick Access Toolbar... 6 Appearance
GUIDE TO POSITIONLY. Everything you need to know to start your first SEO campaign with Positionly!
 GUIDE TO POSITIONLY Everything you need to know to start your first SEO campaign with Positionly! 1 Introduction In this guide, you'll learn everything you need to get started with Positionly. We'll walk
GUIDE TO POSITIONLY Everything you need to know to start your first SEO campaign with Positionly! 1 Introduction In this guide, you'll learn everything you need to get started with Positionly. We'll walk
Matter Management for Legal Departments Essential Features to Maximize Your Return on Investment
 White Paper Matter Management for Legal Departments Essential Features to Maximize Your Return on Investment Author: Matt Ryan, Senior Consultant Contents Introduction...1 System Scalability and Reliability...2
White Paper Matter Management for Legal Departments Essential Features to Maximize Your Return on Investment Author: Matt Ryan, Senior Consultant Contents Introduction...1 System Scalability and Reliability...2
Customer Service Strategy Guide: Customer Experience for the Millennial Generation
 Customer Service Strategy Guide: Customer Experience for the Millennial Generation Introduction The millennials are coming, and few businesses are prepared. For the purposes of this paper, the millennial
Customer Service Strategy Guide: Customer Experience for the Millennial Generation Introduction The millennials are coming, and few businesses are prepared. For the purposes of this paper, the millennial
Real Madrid brings the stadium closer to 450 million fans around the globe, with the Microsoft Cloud
 Customer Solution Story Real Madrid brings the stadium closer to 450 million fans around the globe, with the Microsoft Cloud We can create a one-to-one relationship with fans around the planet with the
Customer Solution Story Real Madrid brings the stadium closer to 450 million fans around the globe, with the Microsoft Cloud We can create a one-to-one relationship with fans around the planet with the
Acronis Digital Assets Research Findings: Unveiling Backup & Recovery Practices across Europe
 Acronis Digital Assets Research Findings: Unveiling Backup & Recovery Practices across Europe March 2010 Contents - Executive Summary: Count the cost of a lost day - Methodology - Research Finding 1: Companies
Acronis Digital Assets Research Findings: Unveiling Backup & Recovery Practices across Europe March 2010 Contents - Executive Summary: Count the cost of a lost day - Methodology - Research Finding 1: Companies
THE 2014 THREAT DETECTION CHECKLIST. Six ways to tell a criminal from a customer.
 THE 2014 THREAT DETECTION CHECKLIST Six ways to tell a criminal from a customer. Telling criminals from customers online isn t getting any easier. Attackers target the entire online user lifecycle from
THE 2014 THREAT DETECTION CHECKLIST Six ways to tell a criminal from a customer. Telling criminals from customers online isn t getting any easier. Attackers target the entire online user lifecycle from
1 P age. Outlook Set Up Options
 Outlook Set Up Options 1. Layout: Six Main Areas On The Main Screen: Menus, Toolbars, Navigation Pane/Folder List, Information Viewer, Reading Pane, To-Do Bar/Pane 2. Interface: Once an Item Is Opened
Outlook Set Up Options 1. Layout: Six Main Areas On The Main Screen: Menus, Toolbars, Navigation Pane/Folder List, Information Viewer, Reading Pane, To-Do Bar/Pane 2. Interface: Once an Item Is Opened
Case Management for the Medium to Large Law Firm Essential Features to Maximize Your Return on Investment
 White Paper Case Management for the Medium to Large Law Firm Essential Features to Maximize Your Return on Investment Author: Matt Ryan, Senior Consultant Contents Introduction...1 System Scalability and
White Paper Case Management for the Medium to Large Law Firm Essential Features to Maximize Your Return on Investment Author: Matt Ryan, Senior Consultant Contents Introduction...1 System Scalability and
4 Keys to Successful Project Collaboration & Execution
 4 Keys to Successful Project Collaboration & Execution: Page 1 of 7 4 Keys to Successful Project Collaboration & Execution BY MANGOSPRING, INC. 4 Keys to Successful Project Collaboration & Execution: Page
4 Keys to Successful Project Collaboration & Execution: Page 1 of 7 4 Keys to Successful Project Collaboration & Execution BY MANGOSPRING, INC. 4 Keys to Successful Project Collaboration & Execution: Page
Help Your Book to Sell through Social Media
 Help Your Book to Sell through Social Media Social networking sites and blogging have revolutionised the way consumers find out about products and talk about them. Social media is usually free to use,
Help Your Book to Sell through Social Media Social networking sites and blogging have revolutionised the way consumers find out about products and talk about them. Social media is usually free to use,
UNSW Social Media communication guidelines
 \ UNSW Social Media communication guidelines UNSW Marketing Services CONTENTS: 1. Purpose... 2 2. Definition of social media... 2 3. Risks associated with social media... 3 4. Social media branding...
\ UNSW Social Media communication guidelines UNSW Marketing Services CONTENTS: 1. Purpose... 2 2. Definition of social media... 2 3. Risks associated with social media... 3 4. Social media branding...
Life after Microsoft Outlook Google Apps
 Welcome Welcome to Gmail! Now that you ve switched from Microsoft Outlook to, here are some tips on beginning to use Gmail. Google Apps What s Different? Here are some of the differences you ll notice
Welcome Welcome to Gmail! Now that you ve switched from Microsoft Outlook to, here are some tips on beginning to use Gmail. Google Apps What s Different? Here are some of the differences you ll notice
How To Make Internet Available For Free
 Is Connectivity A Human Right? For almost ten years, Facebook has been on a mission to make the world more open and connected. For us, that means the entire world not just the richest, most developed countries.
Is Connectivity A Human Right? For almost ten years, Facebook has been on a mission to make the world more open and connected. For us, that means the entire world not just the richest, most developed countries.
The Business Value of Call Accounting
 WHITE PAPER The Business Value of Call Accounting How Call Accounting Software Helps Reduce Business Expenses and Improve Productivity Introduction Call accounting software has been available for more
WHITE PAPER The Business Value of Call Accounting How Call Accounting Software Helps Reduce Business Expenses and Improve Productivity Introduction Call accounting software has been available for more
1 P a g e. Copyright 2013. CRMKnowledge.
 1 P a g e Contents Introduction... 3 An overview of Queues in Microsoft Dynamics CRM... 3 How are Queues created in CRM... 4 How are Queues made visible to users?... 4 What can be put into a Queue?...
1 P a g e Contents Introduction... 3 An overview of Queues in Microsoft Dynamics CRM... 3 How are Queues created in CRM... 4 How are Queues made visible to users?... 4 What can be put into a Queue?...
VARONIS CASE STUDY. Philip Morris International (PMI)
 VARONIS CASE STUDY We chose Varonis following standard procurement processes in our company as well as technical evaluations within our IT lab. The technical evaluations were very important to determine
VARONIS CASE STUDY We chose Varonis following standard procurement processes in our company as well as technical evaluations within our IT lab. The technical evaluations were very important to determine
Top 5 best practices for creating effective dashboards. and the 7 mistakes you don t want to make
 Top 5 best practices for creating effective dashboards and the 7 mistakes you don t want to make p2 Financial services professionals are buried in data that measure and track: relationships and processes,
Top 5 best practices for creating effective dashboards and the 7 mistakes you don t want to make p2 Financial services professionals are buried in data that measure and track: relationships and processes,
Acceptable Use of ICT Policy For Staff
 Policy Document Acceptable Use of ICT Policy For Staff Acceptable Use of ICT Policy For Staff Policy Implementation Date Review Date and Frequency January 2012 Every two Years Rev 1: 26 January 2014 Policy
Policy Document Acceptable Use of ICT Policy For Staff Acceptable Use of ICT Policy For Staff Policy Implementation Date Review Date and Frequency January 2012 Every two Years Rev 1: 26 January 2014 Policy
Why Buy GoldMine Premium Edition 9.2?
 Why Buy GoldMine Premium Edition 9.2? The Top Reasons Why to Buy GoldMine Premium Edition with New Items in Version 9.2 GoldMine is a leading provider of relationship management solutions for small businesses
Why Buy GoldMine Premium Edition 9.2? The Top Reasons Why to Buy GoldMine Premium Edition with New Items in Version 9.2 GoldMine is a leading provider of relationship management solutions for small businesses
Code of Practice for E-mail Users
 Code of Practice for E-mail Users Page 1 of 7 May11/ver02 1. Be concise and to the point Do not make an e-mail longer than it needs to be. Remember that reading an e-mail is harder than reading printed
Code of Practice for E-mail Users Page 1 of 7 May11/ver02 1. Be concise and to the point Do not make an e-mail longer than it needs to be. Remember that reading an e-mail is harder than reading printed
Compliance and Security Solutions
 Content-aware Compliance and Security Solutions for Microsoft SharePoint SharePoint and the ECM Challenge The numbers tell the story. According to the consulting firm Doculabs, 80 percent of the information
Content-aware Compliance and Security Solutions for Microsoft SharePoint SharePoint and the ECM Challenge The numbers tell the story. According to the consulting firm Doculabs, 80 percent of the information
WHITE PAPER. Data Center Fabrics. Why the Right Choice is so Important to Your Business
 WHITE PAPER Data Center Fabrics Why the Right Choice is so Important to Your Business Introduction Data center fabrics are emerging as the preferred architecture for next-generation virtualized data centers,
WHITE PAPER Data Center Fabrics Why the Right Choice is so Important to Your Business Introduction Data center fabrics are emerging as the preferred architecture for next-generation virtualized data centers,
The 2015 email data quality trends report. How organizations today are managing and using email
 The 2015 email data quality trends report How organizations today are managing and using email CONTENTS Summary...1 Research methodology...1 Key findings...2 Email collection and database maintenance challenges...2
The 2015 email data quality trends report How organizations today are managing and using email CONTENTS Summary...1 Research methodology...1 Key findings...2 Email collection and database maintenance challenges...2
THE TOP 5 RECRUITMENT KPIs
 BETTER DATA, BETTER BUSINESS: THE TOP 5 RECRUITMENT KPIs Jointly written by: COPYRIGHT 2012, BULLHORN + INSIGHTSQUARED, ALL RIGHTS RESERVED. Companies today are increasingly competing in a data-centric
BETTER DATA, BETTER BUSINESS: THE TOP 5 RECRUITMENT KPIs Jointly written by: COPYRIGHT 2012, BULLHORN + INSIGHTSQUARED, ALL RIGHTS RESERVED. Companies today are increasingly competing in a data-centric
Google Lead Generation for Attorneys
 1 Google Lead Generation For Attorneys Leverage The Power Of AdWords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
1 Google Lead Generation For Attorneys Leverage The Power Of AdWords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
RingCentral Office@Hand from AT&T Desktop App for Windows & Mac. User Guide
 RingCentral Office@Hand from AT&T Desktop App for Windows & Mac User Guide RingCentral Office@Hand from AT&T User Guide Table of Contents 2 Table of Contents 3 Welcome 4 Download and install the app 5
RingCentral Office@Hand from AT&T Desktop App for Windows & Mac User Guide RingCentral Office@Hand from AT&T User Guide Table of Contents 2 Table of Contents 3 Welcome 4 Download and install the app 5
Measuring the Success of Your Mobile Strategy
 WHITEPAPER / MOBILE ANALYTICS Measuring the Success of Your Mobile Strategy Applying the lessons learned over the past 15 years, digital marketers now use web analytics to measure what matters to their
WHITEPAPER / MOBILE ANALYTICS Measuring the Success of Your Mobile Strategy Applying the lessons learned over the past 15 years, digital marketers now use web analytics to measure what matters to their
Outlook 2010 Email Computer Training Solutions Student Guide Version Revision Date Course Length
 Outlook 2010 Email Computer Training Solutions Version 0.3 Revision Date Course Length 2013-Mar-05 3.5 hours Table of Contents Quick Reference... 3 Outlook 2010 Main Window... 3 Icons in the Guide...
Outlook 2010 Email Computer Training Solutions Version 0.3 Revision Date Course Length 2013-Mar-05 3.5 hours Table of Contents Quick Reference... 3 Outlook 2010 Main Window... 3 Icons in the Guide...
HIPAA Privacy and Security. Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012
 HIPAA Privacy and Security Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012 Goals and Objectives Course Goal: To introduce the staff of Munson Healthcare to the concepts
HIPAA Privacy and Security Rochelle Steimel, HIPAA Privacy Official Judy Smith, Staff Development January 2012 Goals and Objectives Course Goal: To introduce the staff of Munson Healthcare to the concepts
FAMILY GUIDE TO. Mobile Safety. How to keep your children safe and connected in today s mobile world SPONSORED BY:
 FAMILY GUIDE TO Mobile Safety How to keep your children safe and connected in today s mobile world SPONSORED BY: Is Your Child Ready for a Mobile Phone? MOBILE PHONES ARE PART OF OUR LIVES. They re powerful
FAMILY GUIDE TO Mobile Safety How to keep your children safe and connected in today s mobile world SPONSORED BY: Is Your Child Ready for a Mobile Phone? MOBILE PHONES ARE PART OF OUR LIVES. They re powerful
WhitePaper. The Business Value of Call Accounting Software How Call Accounting Helps Reduce Telecom Expenses and Improve Productivity
 The Business Value of Call Accounting Software How Call Accounting Helps Reduce Telecom Expenses and Improve Productivity WhitePaper We innovate. You benefit. The Business Value of Call Accounting Software
The Business Value of Call Accounting Software How Call Accounting Helps Reduce Telecom Expenses and Improve Productivity WhitePaper We innovate. You benefit. The Business Value of Call Accounting Software
1.877.896.3611 www.infrascale.com
 White Paper Making the Upgrade: From Backup Vendor to Data Protection Platform nfrascaletm Simplify Your Business and Offer Customers Complete Data Protection Your customers are ready to explore data protection
White Paper Making the Upgrade: From Backup Vendor to Data Protection Platform nfrascaletm Simplify Your Business and Offer Customers Complete Data Protection Your customers are ready to explore data protection
Google Lead Generation For Attorneys - Leverage The Power Of Adwords To Grow Your Law Business FAST. The Foundation of Google AdWords
 Google Lead Generation For Attorneys - Leverage The Power Of Adwords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
Google Lead Generation For Attorneys - Leverage The Power Of Adwords To Grow Your Law Business FAST You re about to discover the secrets of fast legal practice success with Google AdWords. Google AdWords
Faxing: A Healthcare Disaster. 10 Ways Faxing is Holding Back Your Business
 Faxing: A Healthcare Disaster 10 Ways Faxing is Holding Back Your Business December 2015 We Need A Fax Revolution Faxing is one of the most common forms of communication in healthcare. It s a point-to-point
Faxing: A Healthcare Disaster 10 Ways Faxing is Holding Back Your Business December 2015 We Need A Fax Revolution Faxing is one of the most common forms of communication in healthcare. It s a point-to-point
1. Understanding Big Data
 Big Data and its Real Impact on Your Security & Privacy Framework: A Pragmatic Overview Erik Luysterborg Partner, Deloitte EMEA Data Protection & Privacy leader Prague, SCCE, March 22 nd 2016 1. 2016 Deloitte
Big Data and its Real Impact on Your Security & Privacy Framework: A Pragmatic Overview Erik Luysterborg Partner, Deloitte EMEA Data Protection & Privacy leader Prague, SCCE, March 22 nd 2016 1. 2016 Deloitte
Outlook 2010 Desk Reference Guide
 Outlook 2010 Desk Reference Guide Version 1.0 Developed by OR/WA IRM Please remember to print back-to-back. July 12, 2011 Microsoft Outlook 2010 This document has been developed by OR/WA IRM staff to provide
Outlook 2010 Desk Reference Guide Version 1.0 Developed by OR/WA IRM Please remember to print back-to-back. July 12, 2011 Microsoft Outlook 2010 This document has been developed by OR/WA IRM staff to provide
Focus On echalk Email. Introduction. In This Guide. Contents:
 Focus On echalk Email Introduction Email can be very useful in a school setting. For instance, instead of writing out a memo and delivering it to everyone s mailbox in the main office, you can simply send
Focus On echalk Email Introduction Email can be very useful in a school setting. For instance, instead of writing out a memo and delivering it to everyone s mailbox in the main office, you can simply send
A Simple Guide to Churn Analysis
 A Simple Guide to Churn Analysis A Publication by Evergage Introduction Thank you for downloading A Simple Guide to Churn Analysis. The goal of this guide is to make analyzing churn easy, meaning you wont
A Simple Guide to Churn Analysis A Publication by Evergage Introduction Thank you for downloading A Simple Guide to Churn Analysis. The goal of this guide is to make analyzing churn easy, meaning you wont
10 Building Blocks for Securing File Data
 hite Paper 10 Building Blocks for Securing File Data Introduction Securing file data has never been more important or more challenging for organizations. Files dominate the data center, with analyst firm
hite Paper 10 Building Blocks for Securing File Data Introduction Securing file data has never been more important or more challenging for organizations. Files dominate the data center, with analyst firm
QLIKVIEW DEPLOYMENT FOR BIG DATA ANALYTICS AT KING.COM
 QLIKVIEW DEPLOYMENT FOR BIG DATA ANALYTICS AT KING.COM QlikView Technical Case Study Series Big Data June 2012 qlikview.com Introduction This QlikView technical case study focuses on the QlikView deployment
QLIKVIEW DEPLOYMENT FOR BIG DATA ANALYTICS AT KING.COM QlikView Technical Case Study Series Big Data June 2012 qlikview.com Introduction This QlikView technical case study focuses on the QlikView deployment
Outlook Web App (OWA) To create a new message:
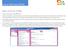 What you ll see in Mail 1. Create a new message by clicking New mail. 2. Folder list. The folder list includes the folders in your mailbox. It may include other folders, such as Favorites and archive folders.
What you ll see in Mail 1. Create a new message by clicking New mail. 2. Folder list. The folder list includes the folders in your mailbox. It may include other folders, such as Favorites and archive folders.
Service Overview. KANA Express. Introduction. Good experiences. On brand. On budget.
 KANA Express Service Overview Introduction KANA Express provides a complete suite of integrated multi channel contact and knowledge management capabilities, proven to enable significant improvements in
KANA Express Service Overview Introduction KANA Express provides a complete suite of integrated multi channel contact and knowledge management capabilities, proven to enable significant improvements in
Crisis Management Guide
 Crisis Management Guide The Crisis Management Guide has been designed to help your company effectively respond to a crisis situation. Crises, large and small can be minimized if a thorough Crisis Management
Crisis Management Guide The Crisis Management Guide has been designed to help your company effectively respond to a crisis situation. Crises, large and small can be minimized if a thorough Crisis Management
CORRALLING THE WILD, WILD WEST OF SOCIAL MEDIA INTELLIGENCE
 CORRALLING THE WILD, WILD WEST OF SOCIAL MEDIA INTELLIGENCE Michael Diederich, Microsoft CMG Research & Insights Introduction The rise of social media platforms like Facebook and Twitter has created new
CORRALLING THE WILD, WILD WEST OF SOCIAL MEDIA INTELLIGENCE Michael Diederich, Microsoft CMG Research & Insights Introduction The rise of social media platforms like Facebook and Twitter has created new
Microsoft Outlook 2010. Reference Guide for Lotus Notes Users
 Microsoft Outlook 2010 Reference Guide for Lotus Notes Users ContentsWelcome to Office Outlook 2010... 2 Mail... 3 Viewing Messages... 4 Working with Messages... 7 Responding to Messages... 11 Organizing
Microsoft Outlook 2010 Reference Guide for Lotus Notes Users ContentsWelcome to Office Outlook 2010... 2 Mail... 3 Viewing Messages... 4 Working with Messages... 7 Responding to Messages... 11 Organizing
Streamline your supply chain with data. How visual analysis helps eliminate operational waste
 Streamline your supply chain with data How visual analysis helps eliminate operational waste emagazine October 2011 contents 3 Create a data-driven supply chain: 4 paths to insight 4 National Motor Club
Streamline your supply chain with data How visual analysis helps eliminate operational waste emagazine October 2011 contents 3 Create a data-driven supply chain: 4 paths to insight 4 National Motor Club
How To Use Microsoft Dynamics Crm For Customer Service
 Customer Service with Microsoft Dynamics CRM Improve customer satisfaction and service effectiveness with Microsoft Dynamics CRM for Customer Service Deliver customer information, case management, service
Customer Service with Microsoft Dynamics CRM Improve customer satisfaction and service effectiveness with Microsoft Dynamics CRM for Customer Service Deliver customer information, case management, service
HiSoftware Policy Sheriff. SP HiSoftware Security Sheriff SP. Content-aware. Compliance and Security Solutions for. Microsoft SharePoint
 HiSoftware Policy Sheriff SP HiSoftware Security Sheriff SP Content-aware Compliance and Security Solutions for Microsoft SharePoint SharePoint and the ECM Challenge The numbers tell the story. According
HiSoftware Policy Sheriff SP HiSoftware Security Sheriff SP Content-aware Compliance and Security Solutions for Microsoft SharePoint SharePoint and the ECM Challenge The numbers tell the story. According
Streamlining Web and Email Security
 How to Protect Your Business from Malware, Phishing, and Cybercrime The SMB Security Series Streamlining Web and Email Security sponsored by Introduction to Realtime Publishers by Don Jones, Series Editor
How to Protect Your Business from Malware, Phishing, and Cybercrime The SMB Security Series Streamlining Web and Email Security sponsored by Introduction to Realtime Publishers by Don Jones, Series Editor
Best Practices for Growing your Mobile App Business. Proven ways to increase your ROI and get your app in the hands of loyal users
 Best Practices for Growing your Mobile App Business Proven ways to increase your ROI and get your app in the hands of loyal users Competing For Users With more than a million mobile apps competing for
Best Practices for Growing your Mobile App Business Proven ways to increase your ROI and get your app in the hands of loyal users Competing For Users With more than a million mobile apps competing for
Outlook Web App McKinney ISD 5/27/2011
 Outlook Web App McKinney ISD 5/27/2011 Outlook Web App Tutorial Outlook Web Access allows you to gain access to your messages, calendars, contacts, tasks and public folders from any computer with internet
Outlook Web App McKinney ISD 5/27/2011 Outlook Web App Tutorial Outlook Web Access allows you to gain access to your messages, calendars, contacts, tasks and public folders from any computer with internet
IT Service Management Metrics that Matter. Reason to Improve: Unintended Consequences of Low Performance
 WHITE paper Four Key Benchmarks for Improving IT Performance page 2 page 3 page 4 page 5 page 6 page 6 Mean Time to Repair First Fix Rate Change Success Rate Server to System Administration Ratio Reason
WHITE paper Four Key Benchmarks for Improving IT Performance page 2 page 3 page 4 page 5 page 6 page 6 Mean Time to Repair First Fix Rate Change Success Rate Server to System Administration Ratio Reason
Netskope Cloud Report. Report Highlights. cloud report. Three of the top 10 cloud apps are Storage, and enterprises use an average of 26 such apps
 cloud report JAN 2014 Netskope Cloud Report In the second Netskope Cloud Report, we ve compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the
cloud report JAN 2014 Netskope Cloud Report In the second Netskope Cloud Report, we ve compiled the most interesting trends on cloud app adoption and usage based on aggregated, anonymized data from the
BIG DATA IN THE FINANCIAL WORLD
 BIG DATA IN THE FINANCIAL WORLD Predictive and real-time analytics are essential to big data operation in the financial world Big Data Republic and Dell teamed up to survey financial organizations regarding
BIG DATA IN THE FINANCIAL WORLD Predictive and real-time analytics are essential to big data operation in the financial world Big Data Republic and Dell teamed up to survey financial organizations regarding
The 9 Ugliest Mistakes Made with Data Backup and How to Avoid Them
 The 9 Ugliest Mistakes Made with Data Backup and How to Avoid Them If your data is important to your business and you cannot afford to have your operations halted for days even weeks due to data loss or
The 9 Ugliest Mistakes Made with Data Backup and How to Avoid Them If your data is important to your business and you cannot afford to have your operations halted for days even weeks due to data loss or
BMC Track-It! Key Benefits
 PRODUCT SOLUTION DATASHEET BMC Track-It! BMC Track-It! is the leader in the small to mid-sized business help desk market and gives you the ability to immediately take control of your Help Desk and IT Management
PRODUCT SOLUTION DATASHEET BMC Track-It! BMC Track-It! is the leader in the small to mid-sized business help desk market and gives you the ability to immediately take control of your Help Desk and IT Management
Sorting out SIEM strategy Five step guide to full security information visibility and controlled threat management
 Sorting out SIEM strategy Five step guide to full security information visibility and controlled threat management This guide will show you how a properly implemented and managed SIEM solution can solve
Sorting out SIEM strategy Five step guide to full security information visibility and controlled threat management This guide will show you how a properly implemented and managed SIEM solution can solve
Numara Track-It! 10.5. Product Family Overview. www.numarasoftware.com
 Numara Track-It! 10.5 Product Family Overview www.numarasoftware.com Introduction The Numara Track-It! family of IT Management solutions gives you the ability to immediately take control of your Help Desk
Numara Track-It! 10.5 Product Family Overview www.numarasoftware.com Introduction The Numara Track-It! family of IT Management solutions gives you the ability to immediately take control of your Help Desk
IDERA WHITEPAPER. The paper will cover the following ten areas: Monitoring Management. WRITTEN BY Greg Robidoux
 WRITTEN BY Greg Robidoux Top SQL Server Backup Mistakes and How to Avoid Them INTRODUCTION Backing up SQL Server databases is one of the most important tasks DBAs perform in their SQL Server environments
WRITTEN BY Greg Robidoux Top SQL Server Backup Mistakes and How to Avoid Them INTRODUCTION Backing up SQL Server databases is one of the most important tasks DBAs perform in their SQL Server environments
VARONIS CASE STUDY. Greenhill & Co.
 VARONIS CASE STUDY We liked DatAdvantage because it told us right away the access rights that certain folders had, which people had access to those folders, where the content was moving to, and if that
VARONIS CASE STUDY We liked DatAdvantage because it told us right away the access rights that certain folders had, which people had access to those folders, where the content was moving to, and if that
Six Signs. you are ready for BI WHITE PAPER
 Six Signs you are ready for BI WHITE PAPER LET S TAKE A LOOK AT THE WAY YOU MIGHT BE MONITORING AND MEASURING YOUR COMPANY About the auther You re managing information from a number of different data sources.
Six Signs you are ready for BI WHITE PAPER LET S TAKE A LOOK AT THE WAY YOU MIGHT BE MONITORING AND MEASURING YOUR COMPANY About the auther You re managing information from a number of different data sources.
