A Systems Approach to Safety Engineering
|
|
|
- Curtis Hines
- 7 years ago
- Views:
Transcription
1 A Systems Approach to Safety Engineering Nancy G. Leveson Aeronautics and Astronautics Engineering Systems MIT
2 The Problem
3 Why do we need a new approach? New causes of accidents in complex, softwareintensive systems Software does not fail, it usually issues unsafe commands Role of humans in systems is changing Traditional safety engineering approaches were developed for relatively simple electro-mechanical systems We need more effective techniques for these new systems and new causes
4 Accident with No Component Failures
5 Types of Accidents Component Failure Accidents Single or multiple component failures Usually assume random failure Component Interaction Accidents Arise in interactions among components Related to interactive complexity and use of computers Level of interactions has reached point where can no longer be thoroughly Planned Understood Anticipated Guarded against
6 It s still hungry and I ve been stuffing worms into it all day.
7 So What Do We Need to Do? Engineering a Safer World Expand our accident causation models Create new hazard analysis techniques Use new system design techniques Safety-driven design Improved system engineering Improve accident analysis and learning from events Improve control of safety during operations Improve management decision-making and safety culture
8 An Expanded View of Accident Causes
9 Accident Causality Models Explain why accidents occur Provide foundations for: Investigating and analyzing cause(s) of accidents Analyzing hazards Designing to prevent future losses Assessing risk Current ones are VERY old Created before computers and modern technology
10 Chain-of-Events Causation Models Assumption: Accidents are caused by chains of component failures Simple, direct relationship between events in chain Ignores non-linear relationships, feedback, etc. Events almost always involve component failure, human error, or energy-related event Forms the basis for most safety-engineering and reliability engineering analysis: e,g, FTA, PRA, FMECA, Event Trees, etc. and design: e.g., redundancy, over-design, safety margins,.
11 Limitations of Chain-of-Events Causation Models Oversimplifies causality Excludes or does not handle Component interaction accidents (vs. component failure accidents) Indirect or non-linear interactions among events Systemic factors in accidents Human errors Migration toward states of increasing risk
12 Software-Related Accidents Are usually caused by flawed requirements Incomplete or wrong assumptions about operation of controlled system or required operation of computer Unhandled controlled-system states and environmental conditions Merely trying to get the software correct or to make it reliable will not make it safer under these conditions.
13 Software-Related Accidents (2) Software may be highly reliable and correct and still be unsafe: Correctly implements requirements but specified behavior unsafe from a system perspective. Requirements do not specify some particular behavior required for system safety (incomplete) Software has unintended (and unsafe) behavior beyond what is specified in requirements.
14 Operator Error: Old View (Sidney Dekker, Jens Rasmussen) Operator error is cause of incidents and accidents So do something about operator involved (suspend, retrain, admonish) Or do something about operators in general Marginalize them by putting in more automation Rigidify their work by creating more rules and procedures
15 Operator Error: New View Operator error is a symptom, not a cause All behavior affected by context (system) in which occurs To do something about error, must look at system in which people work or operate machines: Design of equipment Usefulness of procedures Existence of goal conflicts and production pressures
16 Adaptation Systems are continually changing Systems and organizations migrate toward accidents (states of high risk) under cost and productivity pressures in an aggressive, competitive environment [Rasmussen] Need to include this in our causality models
17 STAMP A new accident causality model using Systems Theory (vs. Reliability Theory)
18 System s s Theoretic View of Safety Safety is a system property It is not a component property It can only be analyzed in the context of the whole Accidents arise from Interactions among system components (human, physical, social) That violate the constraints on safe component behavior and interactions Losses are the result of complex processes, not simply chains of failure events
19 STAMP (3) Systems can be viewed as hierarchical control structures Systems are viewed as interrelated components kept in a state of dynamic equilibrium by feedback loops of information and control Controllers imposes constraints upon the activity at a lower level of the hierarchy: safety constraints A change in emphasis: prevent failures enforce safety constraints on system behavior
20
21 Control processes operate between levels of control Controller Control Actions Model of Process Feedback Process models must contain: - Required relationship among process variables - Current state (values of process variables - The ways the process can change state Controlled Process
22
23 Relationship Between Safety and Process Models Accidents occur when models do not match process and Required control commands are not given Incorrect (unsafe) ones are given Correct commands given at wrong time (too early, too late) Control stops too soon Explains software errors, human errors, component interaction accidents
24
25 STAMP: System Theoretic Accident Model and Processes Treat safety as a dynamic control problem rather than a component failure problem. O-ring did not control propellant gas release by sealing gap in field joint of Challenger Space Shuttle Software did not adequately control descent speed of Mars Polar Lander Temperature in batch reactor not adequately controlled in system design Public health system did not adequately control contamination of the milk supply with melamine Financial system did not adequately control the use of financial instruments Events are the result of the inadequate control Result from lack of enforcement of safety constraints in system design and operations
26 Summary: Accident Causality Accidents occur when 1. Control structure or control actions do not enforce safety constraints a. Unhandled environmental disturbances or conditions b. Unhandled or uncontrolled component failures c. Dysfunctional (unsafe) interactions among components 2. Control actions inadequately coordinated among multiple controllers 3. Control structure degrades over time (slow migration of control structure toward a state of high-risk) Need to control and detect this migration
27 Uncoordinated Control Agents UNSAFE SAFE STATE BOTH TCAS TCAS ATC and ATC provides provide uncoordinated instructions & independent to to both planes instructions Control Agent (TCAS) Instructions Instructions No Coordination Instructions Instructions Control Agent (ATC)
28 Uses for STAMP Create new, more powerful hazard analysis techniques (STPA) Safety-driven design (physical, operational, organizational) More comprehensive accident/incident investigation and root cause analysis Organizational and cultural risk analysis Identifying physical and project risks Defining safety metrics and performance audits Designing and evaluating potential policy and structural improvements Identifying leading indicators of increasing risk New holistic approaches to security
29
30 Improved Hazard Analysis
31 STPA: System Theoretic Process Analysis A new hazard analysis technique that: Identifies safety constraints (system and component requirements) Identifies causes of hazards including Hardware failure Unsafe software behavior Unsafe human action and decision-making Organizational and Management structure flaws Operational flaws Safety Culture
32 5 Missing or wrong communication with another controller
33 Ballistic Missile Defense System (BMDS) Non-Advocate Safety Assessment using STPA A layered defense to defeat all ranges of threats in all phases of flight (boost, mid-course, and terminal) Made up of many existing systems (BMDS Element) Early warning radars Aegis Ground-Based Midcourse Defense (GMD) Command and Control Battle Management and Communications (C2BMC) Others MDA used STPA to evaluate (prior to deployment and test) the residual safety risk of inadvertent launch
34 Safety Control Structure Diagram for FMIS 8/2/
35 Results Deployment and testing of BMDS held up for 6 months because so many scenarios identified for inadvertent launch. In many of these scenarios: All components were operating exactly as intended Missing cases in software, obscure timing interactions Could not be found by fault trees or other standard techniques Complexity of component interactions led to unanticipated system behavior STPA also identified component failures that could cause inadvertent launch (most analysis techniques consider only these failure events)
36 Results (2) A lot of money spent to fix problems found Now being used proactively for upgrades As changes are made to the system, the differences are assessed by updating the control structure diagrams and assessment analysis templates.
37 HTV Joint research project between MIT and JAXA to determine feasibility and usefulness of STPA for JAXA projects Comparison between STPA and FTA for HTV
38 Comparison between STPA and FTA ISS component failures Crew mistakes in operation Crew process model inconsistent Activation missing/inappropriate Activation delayed HTV component failures HTV state changes over time Out of range radio disturbance Physical disturbance t, x feedback missing/inadequate t, x feedback delayed t, x feedback incorrect Flight Mode feedback missing/inadequate Flight Mode feedback incorrect Visual Monitoring missing/inadequate Identified by both (STPA and FTA) Identified by STPA only Wrong information/directive from JAXA/NASA GS
39 Additional Uses for STAMP Safety-driven design Instead of designing and then performing hazard analysis, use STPA to guide design process Integration of safety into system engineering Intent specifications Embed safety analysis and information within system engineering process and specifications CAST: Improved accident investigation and causal analysis Safety during operations Improved management decision-making and safety culture
40 Technical Does it work? Is it practical? Safety analysis of new missile defense system (MDA) Safety-driven design of new JPL outer planets explorer Safety analysis of the JAXA HTV (unmanned cargo spacecraft to ISS) Incorporating risk into early trade studies (NASA Constellation) Orion spacecraft (Space Shuttle replacement) Automobiles (Intelligent Cruise Control) NextGen (for NASA, just starting) Accident/incident analysis (aircraft, petrochemical plants, air traffic control, railway accident, )
41 Analysis of the management structure of the space shuttle program (post-columbia) Risk management in the development of NASA s new manned space program (Constellation) NASA Mission control re-planning and changing mission control procedures safely Food safety Does it work? Is it practical? Social and Managerial Safety in pharmaceutical drug development Risk analysis of outpatient GI surgery at Beth Israel Deaconess Hospital Analysis and prevention of corporate fraud
42 Conclusions Traditional safety engineering techniques are based on assumptions no longer true for the systems we are building Trying to add software and human error to traditional accident models and techniques is hopeless A new, more sophisticated causality model is needed to handle the new causes of accidents and the complexity in our modern systems Using STAMP, we can create much more powerful and effective safety engineering tools and techniques
43 Nancy Leveson, Engineering a Safer World (to be published by MIT Press, 2011)
CAST Analysis. 2013 John Thomas and Nancy Leveson. All rights reserved.
 CAST Analysis 1 CAST Process Identify the Accident (Loss) Identify the Hazards Identify the Safety Constraints Identify the Proximal Events Draw the Safety Control Structure Analyze each component 2 CAST
CAST Analysis 1 CAST Process Identify the Accident (Loss) Identify the Hazards Identify the Safety Constraints Identify the Proximal Events Draw the Safety Control Structure Analyze each component 2 CAST
DESPITE AN ENORMOUS amount
 Vviewpoints DOI:10.1145/2556938 William Young and Nancy G. Leveson Inside Risks An Integrated Approach to ty and Security Based on Systems Theory Applying a more powerful new safety methodology to security
Vviewpoints DOI:10.1145/2556938 William Young and Nancy G. Leveson Inside Risks An Integrated Approach to ty and Security Based on Systems Theory Applying a more powerful new safety methodology to security
THEORIES OF ACCIDENT CAUSATION
 THEORIES OF ACCIDENT CAUSATION You ve carefully thought out all the angles. You ve done it a thousand times. It comes naturally to you. You know what you re doing, it s what you ve been trained to do your
THEORIES OF ACCIDENT CAUSATION You ve carefully thought out all the angles. You ve done it a thousand times. It comes naturally to you. You know what you re doing, it s what you ve been trained to do your
ASSESSMENT OF THE ISO 26262 STANDARD, ROAD VEHICLES FUNCTIONAL SAFETY
 ASSESSMENT OF THE ISO 26262 STANDARD, ROAD VEHICLES FUNCTIONAL SAFETY Dr. Qi Van Eikema Hommes SAE 2012 Government/Industry Meeting January 25, 2012 1 Outline ISO 26262 Overview Scope of the Assessment
ASSESSMENT OF THE ISO 26262 STANDARD, ROAD VEHICLES FUNCTIONAL SAFETY Dr. Qi Van Eikema Hommes SAE 2012 Government/Industry Meeting January 25, 2012 1 Outline ISO 26262 Overview Scope of the Assessment
SYSTEMIC FACTORS IN SOFTWARE-RELATED SPACECRAFT ACCIDENTS
 SYSTEMIC FACTORS IN SOFTWARE-RELATED SPACECRAFT ACCIDENTS Prof. Nancy G. Leveson Aeronautics and Astronautics Dept. Massachusetts Institute of Technology leveson@mit.edu and http://sunnyday.mit.edu AIAA
SYSTEMIC FACTORS IN SOFTWARE-RELATED SPACECRAFT ACCIDENTS Prof. Nancy G. Leveson Aeronautics and Astronautics Dept. Massachusetts Institute of Technology leveson@mit.edu and http://sunnyday.mit.edu AIAA
Safety Driven Design with UML and STPA M. Rejzek, S. Krauss, Ch. Hilbes. Fourth STAMP Workshop, March 23-26, 2015, MIT Boston
 Safety Driven Design with UML and STPA M. Rejzek, S. Krauss, Ch. Hilbes System and Safety Engineering A typical situation: Safety Engineer System Engineer / Developer Safety Case Product 2 System and Safety
Safety Driven Design with UML and STPA M. Rejzek, S. Krauss, Ch. Hilbes System and Safety Engineering A typical situation: Safety Engineer System Engineer / Developer Safety Case Product 2 System and Safety
Introduction to system safety and risk management in complex systems. Dr. John Thomas Massachusetts Institute of Technology
 Introduction to system safety and risk management in complex systems Dr. John Thomas Massachusetts Institute of Technology Agenda Introduction to system safety Challenges for complex systems Goals System-theoretic
Introduction to system safety and risk management in complex systems Dr. John Thomas Massachusetts Institute of Technology Agenda Introduction to system safety Challenges for complex systems Goals System-theoretic
University of Paderborn Software Engineering Group II-25. Dr. Holger Giese. University of Paderborn Software Engineering Group. External facilities
 II.2 Life Cycle and Safety Safety Life Cycle: The necessary activities involving safety-related systems, occurring during a period of time that starts at the concept phase of a project and finishes when
II.2 Life Cycle and Safety Safety Life Cycle: The necessary activities involving safety-related systems, occurring during a period of time that starts at the concept phase of a project and finishes when
Mission Assurance for Unprecedented Missions
 Mission Assurance for Unprecedented Missions Aegis Standard Missile-3 Terminal High Altitude Area Defense US Ground-Based Interceptor Forward-Based Radar With Adjunct Sensor Lt Gen (ret) Trey Obering USAF
Mission Assurance for Unprecedented Missions Aegis Standard Missile-3 Terminal High Altitude Area Defense US Ground-Based Interceptor Forward-Based Radar With Adjunct Sensor Lt Gen (ret) Trey Obering USAF
Investigating Safety and Cybersecurity Design Tradespace for Manned-Unmanned Aerial Systems Integration Using Systems Theoretic Process Analysis
 Investigating Safety and Cybersecurity Design Tradespace for Manned-Unmanned Aerial Systems Integration Using Systems Theoretic Process Analysis Kip Johnson 1, Nancy Leveson 2 Department of Aeronautics
Investigating Safety and Cybersecurity Design Tradespace for Manned-Unmanned Aerial Systems Integration Using Systems Theoretic Process Analysis Kip Johnson 1, Nancy Leveson 2 Department of Aeronautics
System Theoretic Approach To Cybersecurity
 System Theoretic Approach To Cybersecurity Dr. Qi Van Eikema Hommes Lecturer and Research Affiliate Hamid Salim Stuart Madnick Professor IC3.mit.edu 1 Research Motivations Cyber to Physical Risks with
System Theoretic Approach To Cybersecurity Dr. Qi Van Eikema Hommes Lecturer and Research Affiliate Hamid Salim Stuart Madnick Professor IC3.mit.edu 1 Research Motivations Cyber to Physical Risks with
4. Critical success factors/objectives of the activity/proposal/project being risk assessed
 ARTC Risk Management Work Instruction 2: 1. Conduct Risk Assessment Workshop This Work Instruction provides general guidelines for conducting a generic Risk Assessment workshop. The instructions supplement
ARTC Risk Management Work Instruction 2: 1. Conduct Risk Assessment Workshop This Work Instruction provides general guidelines for conducting a generic Risk Assessment workshop. The instructions supplement
Accident Investigations -- ISRI Safety Council
 Accident Investigations -- Digging i for Root Causes ISRI Safety Council May 12, 2009 Getting Started Housekeeping Workshop Rules Zero Accident Consulting LLC Zero Accident Culture ZERO ACCIDENT CULTURE
Accident Investigations -- Digging i for Root Causes ISRI Safety Council May 12, 2009 Getting Started Housekeeping Workshop Rules Zero Accident Consulting LLC Zero Accident Culture ZERO ACCIDENT CULTURE
Part 2: The Use of Software in Safety Critical Systems
 Part 2: The Use of Software in Safety Critical Systems Software Design of Safety-Critical Systems There are three different concerns: Reliability. (Continuous operation. Absence of errors.) Safety. (Avoiding
Part 2: The Use of Software in Safety Critical Systems Software Design of Safety-Critical Systems There are three different concerns: Reliability. (Continuous operation. Absence of errors.) Safety. (Avoiding
Safety-Driven Model-Based System Engineering Methodology Part I: Methodology Description *
 Safety-Driven Model-Based System Engineering Methodology Part I: Methodology Description * December 16, 2007 Prepared by: Margaret Stringfellow Herring, MIT Brandon D. Owens, MIT Dr. Nancy Leveson, MIT
Safety-Driven Model-Based System Engineering Methodology Part I: Methodology Description * December 16, 2007 Prepared by: Margaret Stringfellow Herring, MIT Brandon D. Owens, MIT Dr. Nancy Leveson, MIT
Mauro Calvano. About Aviation Safety Management Systems
 Mauro Calvano About Aviation Safety Management Systems January 2003 1 INTRODUCTION In order to be aware of the factors that are driving the accident rate during the last decade, we must identify the hazards
Mauro Calvano About Aviation Safety Management Systems January 2003 1 INTRODUCTION In order to be aware of the factors that are driving the accident rate during the last decade, we must identify the hazards
Socio-Technical Systems
 Software Engineering Socio-Technical Systems Based on Software Engineering, 7 th Edition by Ian Sommerville Objectives To explain what a socio-technical system is and the distinction between this and a
Software Engineering Socio-Technical Systems Based on Software Engineering, 7 th Edition by Ian Sommerville Objectives To explain what a socio-technical system is and the distinction between this and a
Organizational Causes of the STS-107 Mishap
 Organizational Causes of the STS-107 Mishap ORGANIZATIONAL CAUSES: The organizational causes of this accident are rooted in the Space Shuttle Program s history and culture, including the original compromises
Organizational Causes of the STS-107 Mishap ORGANIZATIONAL CAUSES: The organizational causes of this accident are rooted in the Space Shuttle Program s history and culture, including the original compromises
Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks
 Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks Hamid Salim Stuart Madnick Working Paper CISL# 2014-12 September 2014 Composite Information Systems Laboratory
Cyber Safety: A Systems Thinking and Systems Theory Approach to Managing Cyber Security Risks Hamid Salim Stuart Madnick Working Paper CISL# 2014-12 September 2014 Composite Information Systems Laboratory
Safety and Security Driven Design. Unmanned Aircraft-National Airspace System Integration Case Study
 2 nd uropean STAMP Workshop, 2014 Safety and Security Driven Design. Unmanned Aircraft-National Airspace System Integration Case Study Kip Johnson Prof. Nancy eveson See accompanying abstract: Johnson,
2 nd uropean STAMP Workshop, 2014 Safety and Security Driven Design. Unmanned Aircraft-National Airspace System Integration Case Study Kip Johnson Prof. Nancy eveson See accompanying abstract: Johnson,
Manufacturers versus Component Part and Raw Material Suppliers: How to Prevent Liability By Kenneth Ross *
 Manufacturers versus Component Part and Raw Material Suppliers: How to Prevent Liability By Kenneth Ross * Introduction One of the more perplexing and potentially dangerous areas of product liability practice
Manufacturers versus Component Part and Raw Material Suppliers: How to Prevent Liability By Kenneth Ross * Introduction One of the more perplexing and potentially dangerous areas of product liability practice
Developing System-Based Leading Indicators for Proactive Risk Management in the Chemical Processing Industry. Ibrahim A. Khawaji
 Developing System-Based Leading Indicators for Proactive Risk Management in the Chemical Processing Industry by Ibrahim A. Khawaji B.S., Chemical Engineering, Colorado School of Mines, 2001 SUBMITTED TO
Developing System-Based Leading Indicators for Proactive Risk Management in the Chemical Processing Industry by Ibrahim A. Khawaji B.S., Chemical Engineering, Colorado School of Mines, 2001 SUBMITTED TO
SFTA, SFMECA AND STPA APPLIED TO BRAZILIAN SPACE SOFTWARE
 SFTA, SFMECA AND STPA APPLIED TO BRAZILIAN SPACE SOFTWARE Carlos H N Lahoz Instituto de Aeronautica e Espaco (IAE) Instituto Tecnologico da Aeronautica(ITA) BRAZIL STAMP/STAP Workshop 2014 25-27 March2014-MIT
SFTA, SFMECA AND STPA APPLIED TO BRAZILIAN SPACE SOFTWARE Carlos H N Lahoz Instituto de Aeronautica e Espaco (IAE) Instituto Tecnologico da Aeronautica(ITA) BRAZIL STAMP/STAP Workshop 2014 25-27 March2014-MIT
Risk. Risk Categories. Project Risk (aka Development Risk) Technical Risk Business Risk. Lecture 5, Part 1: Risk
 Risk Lecture 5, Part 1: Risk Jennifer Campbell CSC340 - Winter 2007 The possibility of suffering loss Risk involves uncertainty and loss: Uncertainty: The degree of certainty about whether the risk will
Risk Lecture 5, Part 1: Risk Jennifer Campbell CSC340 - Winter 2007 The possibility of suffering loss Risk involves uncertainty and loss: Uncertainty: The degree of certainty about whether the risk will
Using Incident Investigation Tools Proactively for Incident Prevention.
 Using Incident Investigation Tools Proactively for Incident Prevention. Joanne De Landre General Manager, Safety Wise Solutions ANZSASI 2006 - Melbourne Introduction Reducing Error Investigative Tools
Using Incident Investigation Tools Proactively for Incident Prevention. Joanne De Landre General Manager, Safety Wise Solutions ANZSASI 2006 - Melbourne Introduction Reducing Error Investigative Tools
Subject: CREW RESOURCE MANAGEMENT TRAINING PROGRAMME
 ADVISORY CIRCULAR FOR AIR OPERATORS Subject: CREW RESOURCE MANAGEMENT TRAINING PROGRAMME Date: xx.xx.2013 Initiated By: Republic of Korea AC No: 1. PURPOSE This advisory circular (AC) presents guidelines
ADVISORY CIRCULAR FOR AIR OPERATORS Subject: CREW RESOURCE MANAGEMENT TRAINING PROGRAMME Date: xx.xx.2013 Initiated By: Republic of Korea AC No: 1. PURPOSE This advisory circular (AC) presents guidelines
Managing Design Changes using Safety-Guided Design for a Safety Critical Automotive System
 Managing Design Changes using Safety-Guided Design for a Safety Critical Automotive System by John Sgueglia B.S. Electrical Engineering Rochester Institute of Technology, 2000 SUBMITTED TO THE SYSTEM DESIGN
Managing Design Changes using Safety-Guided Design for a Safety Critical Automotive System by John Sgueglia B.S. Electrical Engineering Rochester Institute of Technology, 2000 SUBMITTED TO THE SYSTEM DESIGN
Chapter 1: Health & Safety Management Systems (SMS) Leadership and Organisational Safety Culture
 Chapter 1: Health & Safety Management Systems (SMS) Leadership and Organisational Safety Culture 3 29 Safety Matters! A Guide to Health & Safety at Work Chapter outline Leadership and Organisational Safety
Chapter 1: Health & Safety Management Systems (SMS) Leadership and Organisational Safety Culture 3 29 Safety Matters! A Guide to Health & Safety at Work Chapter outline Leadership and Organisational Safety
APPLICATION OF CAST AND STPA TO RAILROAD SAFETY IN CHINA. Airong Dong
 APPLICATION OF CAST AND STPA TO RAILROAD SAFETY IN CHINA by Airong Dong Bachelor in Engineering, Communications and Information System, Dalian Maritime University (1997) Master in Engineering, Communications
APPLICATION OF CAST AND STPA TO RAILROAD SAFETY IN CHINA by Airong Dong Bachelor in Engineering, Communications and Information System, Dalian Maritime University (1997) Master in Engineering, Communications
Safety critical communication. Overview. Communication. Andy Brazier
 Safety critical communication Andy Brazier Tel: (+44) 01492 879813 Mob: (+44) 07984 284642 andy@abrisk.co.uk www.abrisk.co.uk 1 Overview Communication is a two way process Critical communication includes:
Safety critical communication Andy Brazier Tel: (+44) 01492 879813 Mob: (+44) 07984 284642 andy@abrisk.co.uk www.abrisk.co.uk 1 Overview Communication is a two way process Critical communication includes:
Safety in Management. 2013 John Thomas and Nancy Leveson. All rights reserved.
 Safety in Management 1 Major Ingredients of Effective Safety Management Commitment and leadership Corporate safety policy Risk awareness and communication channels Controls on system migration toward higher
Safety in Management 1 Major Ingredients of Effective Safety Management Commitment and leadership Corporate safety policy Risk awareness and communication channels Controls on system migration toward higher
Space Exploration. A Visual History. Philip Stooke
 Space Exploration A Visual History Philip Stooke It all began with Sputnik 4 th October 1957 It all began with Sputnik 4 th October 1957 It all began with Sputnik 4 th October 1957 and Laika Laika on the
Space Exploration A Visual History Philip Stooke It all began with Sputnik 4 th October 1957 It all began with Sputnik 4 th October 1957 It all began with Sputnik 4 th October 1957 and Laika Laika on the
PATRIOT MISSILE DEFENSE Software Problem Led to System Failure at Dhahran, Saudi Arabia
 --.- /Initcd Stdcs General Accounting Offiw Ikport to the Chairman, Subcommittee on Investigations and Oversight, Committee on Science, Space, and Technology, House of Rcprcsentativcs PATRIOT MISSILE DEFENSE
--.- /Initcd Stdcs General Accounting Offiw Ikport to the Chairman, Subcommittee on Investigations and Oversight, Committee on Science, Space, and Technology, House of Rcprcsentativcs PATRIOT MISSILE DEFENSE
Enterprise Security Tactical Plan
 Enterprise Security Tactical Plan Fiscal Years 2011 2012 (July 1, 2010 to June 30, 2012) Prepared By: State Chief Information Security Officer The Information Security Council State of Minnesota Enterprise
Enterprise Security Tactical Plan Fiscal Years 2011 2012 (July 1, 2010 to June 30, 2012) Prepared By: State Chief Information Security Officer The Information Security Council State of Minnesota Enterprise
Edwin Lindsay Principal Consultant. Compliance Solutions (Life Sciences) Ltd, Tel: + 44 (0) 7917134922 E-Mail: elindsay@blueyonder.co.
 Edwin Lindsay Principal Consultant, Tel: + 44 (0) 7917134922 E-Mail: elindsay@blueyonder.co.uk There were no guidelines/ regulations There was no training No Procedures No Inspectors Inform All staff of
Edwin Lindsay Principal Consultant, Tel: + 44 (0) 7917134922 E-Mail: elindsay@blueyonder.co.uk There were no guidelines/ regulations There was no training No Procedures No Inspectors Inform All staff of
Barriers To Team Success
 Barriers To Team Success When plans are inadequate Leaders without leadership skills When members have poor attitudes Training that doesn t train Communications breakdowns Team members don t get along
Barriers To Team Success When plans are inadequate Leaders without leadership skills When members have poor attitudes Training that doesn t train Communications breakdowns Team members don t get along
Beyond Normal Accidents and High Reliability Organizations: The Need for an Alternative Approach to Safety in Complex Systems
 Beyond Normal Accidents and High Reliability Organizations: The Need for an Alternative Approach to Safety in Complex Systems Karen Marais, Nicolas Dulac, and Nancy Leveson MIT 1 Introduction Organizational
Beyond Normal Accidents and High Reliability Organizations: The Need for an Alternative Approach to Safety in Complex Systems Karen Marais, Nicolas Dulac, and Nancy Leveson MIT 1 Introduction Organizational
Title & Image NATIONAL CIVIL AVIATION ADMINSTRATION. Advisory Circular
 Title & Image NATIONAL CIVIL AVIATION ADMINSTRATION Advisory Circular Subject: CREW RESOURCE MANAGEMENT TRAINING PROGRAMME Issuing Office: [Identity of Office of NCAA issuing ] Document No.: [NCAA AC #]
Title & Image NATIONAL CIVIL AVIATION ADMINSTRATION Advisory Circular Subject: CREW RESOURCE MANAGEMENT TRAINING PROGRAMME Issuing Office: [Identity of Office of NCAA issuing ] Document No.: [NCAA AC #]
Socio technical Systems. Ian Sommerville 2006 Software Engineering, 8th edition. Chapter 2 Slide 1
 Socio technical Systems Ian Sommerville 2006 Software Engineering, 8th edition. Chapter 2 Slide 1 Objectives To explain what a socio technical system is and the distinction between this and a computer
Socio technical Systems Ian Sommerville 2006 Software Engineering, 8th edition. Chapter 2 Slide 1 Objectives To explain what a socio technical system is and the distinction between this and a computer
Integrating gsix Sigma THINKING into Scrum-Based. Darian Rashid Agile Trainer and Coach darian@agileethos.com
 Integrating gsix Sigma THINKING into Scrum-Based Development Environments Darian Rashid Agile Trainer and Coach darian@agileethos.com Lean Six Sigma THINKING in Software Development What is Six Sigma Thinking
Integrating gsix Sigma THINKING into Scrum-Based Development Environments Darian Rashid Agile Trainer and Coach darian@agileethos.com Lean Six Sigma THINKING in Software Development What is Six Sigma Thinking
JOURNAL OF OBJECT TECHNOLOGY
 JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2006 Vol. 5. No. 8, November-December 2006 Requirements Engineering Tasks Donald Firesmith,
JOURNAL OF OBJECT TECHNOLOGY Online at www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2006 Vol. 5. No. 8, November-December 2006 Requirements Engineering Tasks Donald Firesmith,
Using STAMP/STPA to Chinese High Speed Railway Train Control System
 Using STAMP/STPA to Chinese High Speed Railway Train Control System Liu Jintao,Ph.D. candidate State Key Laboratory of Rail Traffic Control and Safety Beijing Jiaotong University Outline Background and
Using STAMP/STPA to Chinese High Speed Railway Train Control System Liu Jintao,Ph.D. candidate State Key Laboratory of Rail Traffic Control and Safety Beijing Jiaotong University Outline Background and
The Boeing Company Strategic Missile & Defense Systems
 The Boeing Company Strategic Missile & Defense Systems Brad Bruce November 8, 2011 Boeing Business Units How SM&DS Fits Organizationally Boeing BDS Network & Space Systems Boeing Defense, Space & Security
The Boeing Company Strategic Missile & Defense Systems Brad Bruce November 8, 2011 Boeing Business Units How SM&DS Fits Organizationally Boeing BDS Network & Space Systems Boeing Defense, Space & Security
2014 STAMP Conference MIT Partnership for a Systems Approach to Safety Using STAMP Principles in Risk Management of Large Scale Pipeline Projects
 2014 STAMP Conference MIT Partnership for a Systems Approach to Safety Using STAMP Principles in Risk Management of Large Scale Pipeline Projects Lorena Pelegrín 27/03/2014 Table of Contents Background
2014 STAMP Conference MIT Partnership for a Systems Approach to Safety Using STAMP Principles in Risk Management of Large Scale Pipeline Projects Lorena Pelegrín 27/03/2014 Table of Contents Background
PinkLINK July 2008. Pink Elephant. All rights reserved. Page 1 of 5 Learn more about ITIL by visiting: www.pinkelephant.com.
 Service Concepts Made Easy Part 2: Resources & Capabilities By Pierre Bernard, Manager, Product Portfolio Research & Development INTRODUCTION This is a continuation of articles exploring some of the concepts
Service Concepts Made Easy Part 2: Resources & Capabilities By Pierre Bernard, Manager, Product Portfolio Research & Development INTRODUCTION This is a continuation of articles exploring some of the concepts
Enhancing Human Spaceflight Safety Through Spacecraft Survivability Engineering
 AIAA SPACE 2009 Conference & Exposition 14-17 September 2009, Pasadena, California AIAA 2009-6523 Enhancing Human Spaceflight Safety Through Spacecraft Survivability Engineering Meghan S. Buchanan 1 and
AIAA SPACE 2009 Conference & Exposition 14-17 September 2009, Pasadena, California AIAA 2009-6523 Enhancing Human Spaceflight Safety Through Spacecraft Survivability Engineering Meghan S. Buchanan 1 and
A shift in responsibility. More parties involved Integration with other systems. 2
 EFFECTIVE SERVICE RELATIONSHIP MANAGEMENT ALSO INCLUES THE FOLLOWING ACTIVITIES: Today, organizations frequently elect to have certain services be provided by service vendors, also referred to as service
EFFECTIVE SERVICE RELATIONSHIP MANAGEMENT ALSO INCLUES THE FOLLOWING ACTIVITIES: Today, organizations frequently elect to have certain services be provided by service vendors, also referred to as service
Comparison of Risk Analysis Methodologies in an Electrical Grid. Svana Helen Björnsdóttir STAMP Workshop in Amsterdam October 4-6, 2015
 Comparison of Risk Analysis Methodologies in an Electrical Grid Svana Helen Björnsdóttir STAMP Workshop in Amsterdam October 4-6, 2015 INTRODUCTION S.H.Bjornsdottir Stiki/Reykjavik University 2 Aim of
Comparison of Risk Analysis Methodologies in an Electrical Grid Svana Helen Björnsdóttir STAMP Workshop in Amsterdam October 4-6, 2015 INTRODUCTION S.H.Bjornsdottir Stiki/Reykjavik University 2 Aim of
Functional Hazard Assessment (FHA) Report for Unmanned Aircraft Systems
 Distribution: EUROCONTROL Ebeni Holger Matthiesen Hayley Burdett Unmanned Aircraft System (UAS) Safety Case Development Chris Machin Joanne Stoker Don Harris Alan Simpson Functional Hazard Assessment (FHA)
Distribution: EUROCONTROL Ebeni Holger Matthiesen Hayley Burdett Unmanned Aircraft System (UAS) Safety Case Development Chris Machin Joanne Stoker Don Harris Alan Simpson Functional Hazard Assessment (FHA)
Flight Operations Briefing Notes
 Flight Operations Briefing Notes I Introduction This Flight Operations Briefing Note presents a definition of situational awareness. It explains the complex process of gaining and maintaining situational
Flight Operations Briefing Notes I Introduction This Flight Operations Briefing Note presents a definition of situational awareness. It explains the complex process of gaining and maintaining situational
Engineering Project Data Analysis
 Session 24C Engineering Project Data Analysis By: George Graw Stuart Simon Copyright 2014 Raytheon Company. All rights reserved. Customer Success Is Our Mission is a registered trademark of Raytheon Company.
Session 24C Engineering Project Data Analysis By: George Graw Stuart Simon Copyright 2014 Raytheon Company. All rights reserved. Customer Success Is Our Mission is a registered trademark of Raytheon Company.
Holistic Approach to Barrier Integrity: Managing an Effective Safeguarding Strategy. San Burnett
 Holistic Approach to Barrier Integrity: Managing an Effective Safeguarding Strategy San Burnett Holistic Approach to Barrier Integrity Managing an Effective Safeguarding Strategy San Burnett Principal
Holistic Approach to Barrier Integrity: Managing an Effective Safeguarding Strategy San Burnett Holistic Approach to Barrier Integrity Managing an Effective Safeguarding Strategy San Burnett Principal
Accident Causation. Presented by: Lance Hofmann Director of Environmental Health & Safety EagleMed LLC
 Accident Causation Presented by: Lance Hofmann Director of Environmental Health & Safety EagleMed LLC Agenda o Introduction o Industrial Revolution o Domino Theory o Heinrich s Theorems o Modern Causation
Accident Causation Presented by: Lance Hofmann Director of Environmental Health & Safety EagleMed LLC Agenda o Introduction o Industrial Revolution o Domino Theory o Heinrich s Theorems o Modern Causation
SUSAN HARWOOD GRANT OSHA SMALL BUSINESS ASSISTANCE RIT S OSHA OUTREACH CENTER TRAINING OUTLINE AND
 SUSAN HARWOOD GRANT OSHA SMALL BUSINESS ASSISTANCE AND RIT S OSHA OUTREACH CENTER TRAINING OUTLINE TOPIC: INTRODUCTION This section overviews the core elements, processes and steps needed to implement
SUSAN HARWOOD GRANT OSHA SMALL BUSINESS ASSISTANCE AND RIT S OSHA OUTREACH CENTER TRAINING OUTLINE TOPIC: INTRODUCTION This section overviews the core elements, processes and steps needed to implement
Requirements Management John Hrastar
 Requirements Management John Hrastar NASA Project Management Conference March 30-31, 2004 University of Maryland Conference Center Introduction Three aspects of requirements management Requirements in
Requirements Management John Hrastar NASA Project Management Conference March 30-31, 2004 University of Maryland Conference Center Introduction Three aspects of requirements management Requirements in
The Role of Software in Spacecraft Accidents
 The Role of Software in Spacecraft Accidents Nancy G. Leveson Aeronautics and Astronautics Department Massachusetts Institute of Technology Abstract: The first and most important step in solving any problem
The Role of Software in Spacecraft Accidents Nancy G. Leveson Aeronautics and Astronautics Department Massachusetts Institute of Technology Abstract: The first and most important step in solving any problem
March 21, 2011. Dear Ranking Member Costello:
 U.S. Department of The Inspector General Office of Inspector General Transportation Washington, DC 20590 Office of the Secretary of Transportation March 21, 2011 The Honorable Jerry F. Costello Ranking
U.S. Department of The Inspector General Office of Inspector General Transportation Washington, DC 20590 Office of the Secretary of Transportation March 21, 2011 The Honorable Jerry F. Costello Ranking
TOPO Trajectory Operations Officer
 ISS Live! was developed at NASA s Johnson Space Center (JSC) under NASA Contracts NNJ14RA02C and NNJ11HA14C wherein the U.S. Government retains certain rights. Console Handbook TOPO Trajectory Operations
ISS Live! was developed at NASA s Johnson Space Center (JSC) under NASA Contracts NNJ14RA02C and NNJ11HA14C wherein the U.S. Government retains certain rights. Console Handbook TOPO Trajectory Operations
FREQUENTLY ASKED QUESTIONS
 FREQUENTLY ASKED QUESTIONS Continuous Monitoring 1. What is continuous monitoring? Continuous monitoring is one of six steps in the Risk Management Framework (RMF) described in NIST Special Publication
FREQUENTLY ASKED QUESTIONS Continuous Monitoring 1. What is continuous monitoring? Continuous monitoring is one of six steps in the Risk Management Framework (RMF) described in NIST Special Publication
Beyond Minimums: The Pursuit of Aviation Professionalism and Organizational Excellence. Gordon Harwell Lead Check Airman/Human Factors Project Lead
 Beyond Minimums: The Pursuit of Aviation Professionalism and Organizational Excellence Gordon Harwell Lead Check Airman/Human Factors Project Lead Suggested Reading Beyond Minimums What are Minimums Do
Beyond Minimums: The Pursuit of Aviation Professionalism and Organizational Excellence Gordon Harwell Lead Check Airman/Human Factors Project Lead Suggested Reading Beyond Minimums What are Minimums Do
Quality Risk Management Tools Quality Risk Management Tool Selection When to Select FMEA: QRM Tool Selection Matrix
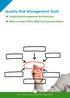 Quality Risk Management Tools Quality Risk Management Tool Selection When to Select FMEA: QRM Tool Selection Matrix 26 Quality Risk Management Tools The ICH Q9 guideline, Quality Risk Management, provides
Quality Risk Management Tools Quality Risk Management Tool Selection When to Select FMEA: QRM Tool Selection Matrix 26 Quality Risk Management Tools The ICH Q9 guideline, Quality Risk Management, provides
Independent Validation of Software Safety Requirements for System of Systems by S. Driskell, J. Murphy, J.B. Michael, M. Shing
 Independent Validation of Software Safety Requirements for System of Systems by S. Driskell, J. Murphy, J.B. Michael, M. Shing Presented by Stephen Driskell Stephen.Driskell@TASC.com Judy Murphy jmurphy@mpl.com
Independent Validation of Software Safety Requirements for System of Systems by S. Driskell, J. Murphy, J.B. Michael, M. Shing Presented by Stephen Driskell Stephen.Driskell@TASC.com Judy Murphy jmurphy@mpl.com
The Top 5 Software Capabilities for Ensuring Food Safety
 The Top 5 Software Capabilities for Ensuring Food Safety How can manufacturers minimize food safety risks? We ve all seen the headlines: Contaminated peanut butter. Metal fragments in cereal. Undeclared
The Top 5 Software Capabilities for Ensuring Food Safety How can manufacturers minimize food safety risks? We ve all seen the headlines: Contaminated peanut butter. Metal fragments in cereal. Undeclared
Effective Root Cause Analysis For Corrective and Preventive Action
 Effective Root Cause Analysis For Corrective and Preventive Action Manuel Marco Understanding Key Principles Requirement need or expectation that is stated, generally implied, or obligatory Generally implied
Effective Root Cause Analysis For Corrective and Preventive Action Manuel Marco Understanding Key Principles Requirement need or expectation that is stated, generally implied, or obligatory Generally implied
Failure Analysis Methods What, Why and How. MEEG 466 Special Topics in Design Jim Glancey Spring, 2006
 Failure Analysis Methods What, Why and How MEEG 466 Special Topics in Design Jim Glancey Spring, 2006 Failure Analysis Methods Every product or process has modes of failure. An analysis of potential failures
Failure Analysis Methods What, Why and How MEEG 466 Special Topics in Design Jim Glancey Spring, 2006 Failure Analysis Methods Every product or process has modes of failure. An analysis of potential failures
Proposed Competencies for Safety Certification Training Program
 SMS Leadership List the advantages of effective safety management and the benefits that FTA anticipates SMS adoption will bring the transit industry Categorize the activities performed by an Accountable
SMS Leadership List the advantages of effective safety management and the benefits that FTA anticipates SMS adoption will bring the transit industry Categorize the activities performed by an Accountable
with Managing RSA the Lifecycle of Key Manager RSA Streamlining Security Operations Data Loss Prevention Solutions RSA Solution Brief
 RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
RSA Solution Brief Streamlining Security Operations with Managing RSA the Lifecycle of Data Loss Prevention and Encryption RSA envision Keys with Solutions RSA Key Manager RSA Solution Brief 1 Who is asking
Who needs humans to run computers? Role of Big Data and Analytics in running Tomorrow s Computers illustrated with Today s Examples
 15 April 2015, COST ACROSS Workshop, Würzburg Who needs humans to run computers? Role of Big Data and Analytics in running Tomorrow s Computers illustrated with Today s Examples Maris van Sprang, 2015
15 April 2015, COST ACROSS Workshop, Würzburg Who needs humans to run computers? Role of Big Data and Analytics in running Tomorrow s Computers illustrated with Today s Examples Maris van Sprang, 2015
AEROSPACE ENGINEERING SERIES, GS-0861
 TS-124 May 1993 General Schedule Position Classification Flysheet AEROSPACE ENGINEERING SERIES, GS-0861 Theodore Roosevelt Building 1900 E Street, NW Washington, DC 20415-8330 Classification Programs Division
TS-124 May 1993 General Schedule Position Classification Flysheet AEROSPACE ENGINEERING SERIES, GS-0861 Theodore Roosevelt Building 1900 E Street, NW Washington, DC 20415-8330 Classification Programs Division
FAILURE MODES AND EFFECT ANALYSIS (FMEA)
 FAILURE MODES AND EFFECT ANALYSIS (FMEA) INTRODUCTION While defining the functions and desired standards of performance of an asset, the objectives of maintenance with respect to that asset are defined.
FAILURE MODES AND EFFECT ANALYSIS (FMEA) INTRODUCTION While defining the functions and desired standards of performance of an asset, the objectives of maintenance with respect to that asset are defined.
HUNTINGTON WOODS DEPARTMENT OF PUBLIC SAFETY GOALS AND OBJECTIVES PROGRAM DETAIL
 The following presents a detailed outline of goals and objectives of this Department organized by Department function. It is intended to provide a guideline for use in assessing progress in attaining the
The following presents a detailed outline of goals and objectives of this Department organized by Department function. It is intended to provide a guideline for use in assessing progress in attaining the
Generally Accepted Recordkeeping Principles
 Generally Accepted Recordkeeping Principles Information Governance Maturity Model Information is one of the most vital strategic assets any organization possesses. Organizations depend on information to
Generally Accepted Recordkeeping Principles Information Governance Maturity Model Information is one of the most vital strategic assets any organization possesses. Organizations depend on information to
ITIL Intermediate Lifecycle Stream:
 ITIL Intermediate Lifecycle Stream: SERVICE TRANSITION CERTIFICATE Sample Paper 1, version 6.1 Gradient Style, Complex Multiple Choice SCENARIO BOOKLET This booklet contains the scenarios upon which the
ITIL Intermediate Lifecycle Stream: SERVICE TRANSITION CERTIFICATE Sample Paper 1, version 6.1 Gradient Style, Complex Multiple Choice SCENARIO BOOKLET This booklet contains the scenarios upon which the
OSW TN002 - TMT GUIDELINES FOR SOFTWARE SAFETY TMT.SFT.TEC.11.022.REL07
 OSW TN002 - TMT GUIDELINES FOR SOFTWARE SAFETY TMT.SFT.TEC.11.022.REL07 August 22, 2012 TMT.SFT.TEC.11.022.REL07 PAGE 2 OF 15 TABLE OF CONTENTS 1 INTRODUCTION 3 1.1 Audience... 3 1.2 Scope... 3 1.3 OSW
OSW TN002 - TMT GUIDELINES FOR SOFTWARE SAFETY TMT.SFT.TEC.11.022.REL07 August 22, 2012 TMT.SFT.TEC.11.022.REL07 PAGE 2 OF 15 TABLE OF CONTENTS 1 INTRODUCTION 3 1.1 Audience... 3 1.2 Scope... 3 1.3 OSW
Systems Engineering. Designing, implementing, deploying and operating systems which include hardware, software and people
 Systems Engineering Designing, implementing, deploying and operating systems which include hardware, software and people Ian Sommerville 2000 Software Engineering, 6th edition. Chapter 2 Slide 1 Objectives
Systems Engineering Designing, implementing, deploying and operating systems which include hardware, software and people Ian Sommerville 2000 Software Engineering, 6th edition. Chapter 2 Slide 1 Objectives
Embracing Microsoft Vista for Enhanced Network Security
 Embracing Microsoft Vista for Enhanced Network Security Effective Implementation of Server & Domain Isolation Requires Complete Network Visibility throughout the OS Migration Process For questions on this
Embracing Microsoft Vista for Enhanced Network Security Effective Implementation of Server & Domain Isolation Requires Complete Network Visibility throughout the OS Migration Process For questions on this
Software Requirements Specification
 1 of 7 17.04.98 13:32 Software Requirements Specification The sub-sections : 1. What is a Software Requirements Specification 2. Why is a Software Requirement Specification Required 3. What is Contained
1 of 7 17.04.98 13:32 Software Requirements Specification The sub-sections : 1. What is a Software Requirements Specification 2. Why is a Software Requirement Specification Required 3. What is Contained
A Characterization Taxonomy for Integrated Management of Modeling and Simulation Tools
 A Characterization Taxonomy for Integrated Management of Modeling and Simulation Tools Bobby Hartway AEgis Technologies Group 631 Discovery Drive Huntsville, AL 35806 256-922-0802 bhartway@aegistg.com
A Characterization Taxonomy for Integrated Management of Modeling and Simulation Tools Bobby Hartway AEgis Technologies Group 631 Discovery Drive Huntsville, AL 35806 256-922-0802 bhartway@aegistg.com
2016 Charter School Application Evaluation Rubric. For applications submitted to The Louisiana Board of Elementary and Secondary Education
 2016 Charter School Application Evaluation Rubric For applications submitted to The Louisiana Board of Elementary and Secondary Education 2016 Charter School Application Evaluation Rubric The purpose of
2016 Charter School Application Evaluation Rubric For applications submitted to The Louisiana Board of Elementary and Secondary Education 2016 Charter School Application Evaluation Rubric The purpose of
Office Business Applications (OBA) for Healthcare Organizations. Make better decisions using the tools you already know
 Office Business Applications (OBA) for Healthcare Organizations Make better decisions using the tools you already know Page 1 A B S T R A C T Healthcare information is getting more and more difficult to
Office Business Applications (OBA) for Healthcare Organizations Make better decisions using the tools you already know Page 1 A B S T R A C T Healthcare information is getting more and more difficult to
Intelligent solutions for quantifying Operational Risk
 Intelligent solutions for quantifying Operational Risk Overview There is an increasingly urgent requirement for major organisations to quantify their operational risk in ways that can be audited, controlled,
Intelligent solutions for quantifying Operational Risk Overview There is an increasingly urgent requirement for major organisations to quantify their operational risk in ways that can be audited, controlled,
A blueprint for an Enterprise Information Security Assurance System. Acuity Risk Management LLP
 A blueprint for an Enterprise Information Security Assurance System Acuity Risk Management LLP Introduction The value of information as a business asset continues to grow and with it the need for effective
A blueprint for an Enterprise Information Security Assurance System Acuity Risk Management LLP Introduction The value of information as a business asset continues to grow and with it the need for effective
Maximizing return on plant assets
 Maximizing return on plant assets Manufacturers in nearly every process industry face the need to improve their return on large asset investments. Effectively managing assets, however, requires a wealth
Maximizing return on plant assets Manufacturers in nearly every process industry face the need to improve their return on large asset investments. Effectively managing assets, however, requires a wealth
Aviation Safety Policy. Aviation Safety (AVS) Safety Management System Requirements
 Aviation Safety Policy ORDER VS 8000.367A Effective Date: 11/30/2012 SUBJ: Aviation Safety (AVS) Safety Management System Requirements 1. This order provides requirements to be met by AVS and AVS services/offices
Aviation Safety Policy ORDER VS 8000.367A Effective Date: 11/30/2012 SUBJ: Aviation Safety (AVS) Safety Management System Requirements 1. This order provides requirements to be met by AVS and AVS services/offices
ACCIDENT ANALYSIS AND PREVENTION. Gavin McKellar International Conference on Ergonomics. Sao Paulo August 2011
 ACCIDENT ANALYSIS AND PREVENTION Gavin McKellar International Conference on Ergonomics. Sao Paulo August 2011 Tips for the next World Cup Lessons Learned Is Aviation Safe? Fatalities LEVELS OF RISK DRAWING
ACCIDENT ANALYSIS AND PREVENTION Gavin McKellar International Conference on Ergonomics. Sao Paulo August 2011 Tips for the next World Cup Lessons Learned Is Aviation Safe? Fatalities LEVELS OF RISK DRAWING
Karlene H. Roberts, PhD. Haas School of Business University of California Berkeley, CA 94720 USA E-mail: Karlene@haas.berkeley.edu
 Karlene H. Roberts, PhD. Haas School of Business University of California Berkeley, CA 94720 USA E-mail: Karlene@haas.berkeley.edu When anyone asks me how I can best describe my experience in nearly forty
Karlene H. Roberts, PhD. Haas School of Business University of California Berkeley, CA 94720 USA E-mail: Karlene@haas.berkeley.edu When anyone asks me how I can best describe my experience in nearly forty
CSC340: Information Systems Analysis and Design. About the Course
 CSC340: Information Systems Analysis and Design Professor Jennifer Campbell campbell@cs.toronto.edu http://www.cs.toronto.edu/~csc340h/ Acknowledgement: Material Provided by Professor Steve Easterbrook
CSC340: Information Systems Analysis and Design Professor Jennifer Campbell campbell@cs.toronto.edu http://www.cs.toronto.edu/~csc340h/ Acknowledgement: Material Provided by Professor Steve Easterbrook
The Software Process. The Unified Process (Cont.) The Unified Process (Cont.)
 The Software Process Xiaojun Qi 1 The Unified Process Until recently, three of the most successful object-oriented methodologies were Booch smethod Jacobson s Objectory Rumbaugh s OMT (Object Modeling
The Software Process Xiaojun Qi 1 The Unified Process Until recently, three of the most successful object-oriented methodologies were Booch smethod Jacobson s Objectory Rumbaugh s OMT (Object Modeling
Algorithms and optimization for search engine marketing
 Algorithms and optimization for search engine marketing Using portfolio optimization to achieve optimal performance of a search campaign and better forecast ROI Contents 1: The portfolio approach 3: Why
Algorithms and optimization for search engine marketing Using portfolio optimization to achieve optimal performance of a search campaign and better forecast ROI Contents 1: The portfolio approach 3: Why
Position Descriptions. Aerospace
 Position Descriptions Aerospace Aerospace Engineering? Aeromechanics / Flight Control / Flight Qualities Engineer Predict, analyze, and verify air vehicle flight dynamics including aircraft aerodynamics,
Position Descriptions Aerospace Aerospace Engineering? Aeromechanics / Flight Control / Flight Qualities Engineer Predict, analyze, and verify air vehicle flight dynamics including aircraft aerodynamics,
Lecture 9: Requirements Modelling
 A little refresher: What are we modelling? Lecture 9: Requirements Modelling Requirements; Systems; Systems Thinking Role of Modelling in RE Why modelling is important Limitations of modelling Brief overview
A little refresher: What are we modelling? Lecture 9: Requirements Modelling Requirements; Systems; Systems Thinking Role of Modelling in RE Why modelling is important Limitations of modelling Brief overview
Occupational safety risk management in Australian mining
 IN-DEPTH REVIEW Occupational Medicine 2004;54:311 315 doi:10.1093/occmed/kqh074 Occupational safety risk management in Australian mining J. Joy Abstract Key words In the past 15 years, there has been a
IN-DEPTH REVIEW Occupational Medicine 2004;54:311 315 doi:10.1093/occmed/kqh074 Occupational safety risk management in Australian mining J. Joy Abstract Key words In the past 15 years, there has been a
HUMAN ERROR COCKPIT VULNERABILITIES
 HUMAN ERROR COCKPIT VULNERABILITIES Oliver Ciuică*, Eduard Mihai* * Faculty of Aeronautical Management, Henri Coandă Air Force Academy, Braov, Romania Abstract: The present paper aims to underline the
HUMAN ERROR COCKPIT VULNERABILITIES Oliver Ciuică*, Eduard Mihai* * Faculty of Aeronautical Management, Henri Coandă Air Force Academy, Braov, Romania Abstract: The present paper aims to underline the
TEST MANAGEMENT SOLUTION Buyer s Guide WHITEPAPER. Real-Time Test Management
 TEST MANAGEMENT SOLUTION Buyer s Guide WHITEPAPER Real-Time Test Management How to Select the Best Test Management Vendor? The implementation of a Test Management system to automate business processes
TEST MANAGEMENT SOLUTION Buyer s Guide WHITEPAPER Real-Time Test Management How to Select the Best Test Management Vendor? The implementation of a Test Management system to automate business processes
Driving Reuse in the Supply Chain
 Driving Reuse in the Supply Chain The Cisco Systems Journey May 2014 2014 Perception Software. All rights reserved. 1 Contents Executive Summary The Cisco Challenge on Reuse 3 Why Reuse? 4 Cost, Quality
Driving Reuse in the Supply Chain The Cisco Systems Journey May 2014 2014 Perception Software. All rights reserved. 1 Contents Executive Summary The Cisco Challenge on Reuse 3 Why Reuse? 4 Cost, Quality
Procurement s Role in Plant Reliability and Safety. Reduce Instrumentation Costs Without Sacrificing Reliability and Safety
 Procurement s Role in Plant Reliability and Safety Reduce Instrumentation Costs Without Sacrificing Reliability and Safety TCO Gauges as Alarms MRO Spend ERP New Way Forward Contact Form Distributor Locator
Procurement s Role in Plant Reliability and Safety Reduce Instrumentation Costs Without Sacrificing Reliability and Safety TCO Gauges as Alarms MRO Spend ERP New Way Forward Contact Form Distributor Locator
The 7 th International Scientific Conference DEFENSE RESOURCES MANAGEMENT IN THE 21st CENTURY Braşov, November 15 th 2012
 The 7 th International Scientific Conference DEFENSE RESOURCES MANAGEMENT IN THE 21st CENTURY Braşov, November 15 th 2012 COMMUNICATION ISSUES OF UAV 1 INTEGRATION INTO NON 1 st. Lt. Gábor Pongrácz, ATM
The 7 th International Scientific Conference DEFENSE RESOURCES MANAGEMENT IN THE 21st CENTURY Braşov, November 15 th 2012 COMMUNICATION ISSUES OF UAV 1 INTEGRATION INTO NON 1 st. Lt. Gábor Pongrácz, ATM
A Systems Approach to Protecting the U.S. Air Traffic Control System Against Cyber-Terrorism
 A Systems Approach to Protecting the U.S. Air Traffic Control System Against Cyber-Terrorism Arthur Pyster Deputy Assistant Administrator for Information Services and Deputy Chief Information Officer arthur.pyster@faa.gov
A Systems Approach to Protecting the U.S. Air Traffic Control System Against Cyber-Terrorism Arthur Pyster Deputy Assistant Administrator for Information Services and Deputy Chief Information Officer arthur.pyster@faa.gov
Network-Wide Change Management Visibility with Route Analytics
 Network-Wide Change Management Visibility with Route Analytics Executive Summary Change management is a hot topic, and rightly so. Studies routinely report that a significant percentage of application
Network-Wide Change Management Visibility with Route Analytics Executive Summary Change management is a hot topic, and rightly so. Studies routinely report that a significant percentage of application
Flight Operations Briefing Notes
 Flight Operations Briefing Notes I Introduction Encountering wake turbulence in flight can be a surprising experience, both for crews and passengers. Wake turbulence occurs suddenly, and is usually accompanied
Flight Operations Briefing Notes I Introduction Encountering wake turbulence in flight can be a surprising experience, both for crews and passengers. Wake turbulence occurs suddenly, and is usually accompanied
