EA USA Online Data Protection Suite. Frequently Asked Questions
|
|
|
- Dwight Simon
- 7 years ago
- Views:
Transcription
1 EA USA Online Data Protection Suite Frequently Asked Questions
2 TABLE OF CONTENTS EA USA ONLINE DATA PROTECTION SUITE ABOUT THE ONLINE DATA PROTECTION SUITE... 3 What is included in the Online Data Protection Suite?... 3 What is the DataScrambler?... 3 What is PhishBlock?... 3 How does the Online Data Protection Suite compare to other security software?... 4 What are the benefits of the Online Data Protection Suite?... 5 COMMON TERMS... 6 What is phishing?... 6 What is keylogging?... 6 What is malware?... 6 USING THE ONLINE DATA PROTECTION SUITE... 7 How do I install the Online Data Protection Suite?... 7 How do I know if the Online Data Protection Suite is working?... 7 What happens if I go to a Phishing Site?... 7 Which web sites are protected against phishing?... 8 How do I know what version of the software I am running?... 8 How do I get updates for the software?... 8 What data is transmitted from the Online Data Protection Suite and my use of it to EA or other parties?... 8 Can I install the Online Data Protection on more than one PC?... 8 Can I re-install the Online Data Protection Suite after using up my 3 installations?... 8 How do I uninstall the Online Data Protection software?... 8 How do I renew my software?... 8 How do I use the Credit Monitor Tab?... 8 When I look at the Activity Report it does not show my personal data. How do I change this?... 9 I want to turn off my Activity Report or see it less frequently. How do I do this?... 9 I don t want to see the DataScrambler. Can I turn it off?
3 What am I agreeing to by checking "allow to provide anonymous information about detected threats" during installation? What happens if I do not select this box? TECHNICAL REQUIREMENTS What are the minimum system requirements to run the Online Data Protection software? What Internet browsers are supported? Will the software work with my anti-virus or any other security software? Do I need anti-virus software if I am running the Online Data Protection Suite? Can I use the software on my Apple/Mac? Can I install the EA USA Online Data Protection on my ipad or smart phone? TROUBLESHOOTING AND CUSTOMER SUPPORT I am having issues using my web conference service or screen sharing software Within certain web pages/services, I have some issues using my keyboard I have a problem with the software. How can I get help? The Online Data Protection Suite fails to install and I receive this message: Unable to connect to license server. Please check Internet connection The license fails to validate during installation I cannot see the DataScrambler I have misplaced my installation file and can no longer find the download link What happens if a warning appears on my computer that refers to the Online Data Protection Suite? I can t install the Online Data Protection from my gmail account. What should I do?
4 ABOUT THE ONLINE DATA PROTECTION SUITE WHAT IS INCLUDED IN THE ONLINE DATA PROTECTION SUITE? The Online Data Protection Suite is data and identity theft prevention software designed to protect your personal information while you surf the Internet. It includes two programs: DataScrambler antikeylogging software and PhishBlock anti-phishing software. You can always access information about the product by clicking on the Nationwide logo at the bottom right of your desktop or by clicking on the DataScrambler. It adds an extra, real-time layer of protection to whatever other anti-virus, anti-spyware or firewall software you have. WHAT IS THE DATASCRAMBLER? The DataScrambler is anti-keylogging software that is inserted into your browser and shows the actual keystrokes being replaced by alternate keystrokes, providing a visual display of how your information is being continuously protected. WHAT IS PHISHBLOCK? PhishBlock is anti-phishing software that is proactive and customized; detecting phishing sites the very first time they are loaded. We use proprietary methods to identify phishing sites that attempt to emulate major brands. PhishBlock can automatically identify a scam site and overlays a warning page to inform you. 3
5 HOW DOES THE ONLINE DATA PROTECTION SUITE COMPARE TO OTHER SECURITY SOFTWARE? A leading laboratory for the evaluation of security software (West Coast Labs) found the technology behind EA USA s Online Data Protection Suite thwarted a significantly higher number of keylogging and phishing attacks than conventional desktop solutions. Refer to the chart below for more details on how the Online Data Protection Suite offers additional protection that traditional anti-virus software does not. BENEFIT ONLINE & MOBILE DATA PROTECTION SUITE DESKTOP ANTI- VIRUS, ANTI- SPYWARE OR OTHER INTERNET SECURITY SUITES* Proactive protection against data entry into all websites Protection without needing to detect and eradicate malware Outperforms all other major desktop security packages in thwarting new spyware attacks Protects against phishing attacks in realtime outperforming all competitors Plug-and-Play no configuration required Secure portable browsing on any PC or Flash-based device USB, mobile phone, etc. *Refers to all major anti-virus products including Norton, McAfee, Kaspersky, AVG and also refers to anti-spyware solutions and combined desktop Internet security suites. 4
6 WHAT ARE THE BENEFITS OF THE ONLINE DATA PROTECTION SUITE? The Online Data Protection Suite is designed to provide real-time protection against electronic data theft and identity theft, allowing you to browse and use the Internet more safely. This solution is able to prevent illegal and unwanted data capture without needing to identify malware itself. Thus the software provides a complementary, yet more proactive, level of protection than that offered by conventional desktop security solutions. The Online Data Protection: protects every keystroke you type (passwords, credit cards, identity information) protects against malware that takes pictures of your data and steals it protects you against being lured to a fake (phishing) site that steals your data shows every keystroke you type being protected and displays a monthly report showing what data has been protected To see the protection the software has been providing, view the Activity Report in the software. This can be accessed by clicking on the DataScrambler or Nationwide logo to bring up the user interface, then selecting the Report tab to view your activity report. 5
7 COMMON TERMS WHAT IS PHISHING? Phishing (pronounced "fishing") is a type of online identity theft that involves the use of and fraudulent websites to steal personal data or information (such as credit card numbers, passwords, account data or other sensitive information). Con artists typically send millions of fraudulent messages with links to fraudulent websites that appear to come from brands you trust such as your bank or credit card company and request you provide personal information. Criminals can use this information for many different types of fraud, including stealing money from your account, opening new accounts in your name, or obtaining official documents using your identity. WHAT IS KEYLOGGING? Keystroke logging, which is often called keylogging, is the action of tracking the keys struck on a keyboard, typically in a covert manner so that the person using the keyboard is unaware his or her actions are being monitored. As a generic term, keylogging can also refer to taking pictures of a user s screen to steal data, also known as screen capture. Keylogging, or a keylogger, is a type of surveillance software or spyware that records every keystroke you make including instant messages, , and any information you type at any time using your keyboard and then transmits this information to an unknown third party. Those third parties now have access to confidential information such as bank account numbers typed into an online banking site, logins, passwords, etc. Some keyloggers allow not only keyboard keystrokes to be captured but also are often capable of collecting screen captures from the computer. WHAT IS MALWARE? Malware, or malicious software, is software designed by criminals to disrupt or deny computer operations, gather information that leads to loss of privacy or exploitation of a user, gain unauthorized access to system resources and/or steal other personal information. 6
8 USING THE ONLINE DATA PROTECTION SUITE HOW DO I INSTALL THE ONLINE DATA PROTECTION SUITE? 1. Click on the download link available in your program confirmation Download the Online Data Protection installation package. Select either Run from the available options or save the file to your desktop and double-click to run the software from there. 3. Follow the instructions/prompts in the software. 4. The installation package will copy the necessary files and license to your computer. 5. At the end of the installation, you will be required to reboot your computer to activate the software. HOW DO I KNOW IF THE ONLINE DATA PROTECTION SUITE IS WORKING? If you are running the Online Data Protection Suite, you will see the DataScrambler located in the top right of your browser, as shown below: Each time you type into a web page, you will notice that the keystroke you type into a field is replaced by an alternate random character in the DataScrambler. It is these alternate keystrokes not what you type that would be picked up by any hackers trying to monitor your keystrokes. WHAT HAPPENS IF I GO TO A PHISHING SITE? If you navigate to a phishing site, your browser will automatically display a warning page to prevent you from entering your personal details. If you choose to, you can ignore the warning and proceed to the site but this is not recommended. 7
9 WHICH WEB SITES ARE PROTECTED AGAINST PHISHING? There are a large number of sites (over 800) that you are automatically protected against, which cover all the main categories of the web such as banking and finance, payment processing, auction sites, utilities, entertainment, social networking sites and more. The list of protected sites is continuously growing and your software will automatically update itself with these new sites. HOW DO I KNOW WHAT VERSION OF THE SOFTWARE I AM RUNNING? Go to the Options tab by clicking on the DataScrambler or double-clicking on the nationwide logo at the bottom right of your desktop and you will see the version number at the bottom of the window. HOW DO I GET UPDATES FOR THE SOFTWARE? The software automatically checks each day for new updates. If available, it downloads updates automatically in the background while you use your PC, just like anti-virus software. WHAT DATA IS TRANSMITTED FROM THE ONLINE DATA PROTECTION SUITE AND MY USE OF IT TO EA OR OTHER PARTIES? All data submitted from the software (with permission) is anonymous and consists only of counts (e.g. numbers of web sites visited) and profile data (details of operating system, default browser, etc). None of the collected or transmitted data is personal nor is it traceable to an individual user of the software. CAN I INSTALL THE ONLINE DATA PROTECTION ON MORE THAN ONE PC? Your license for the Online Data Protection Suite allows you to install the software on up to 3 different computers. CAN I RE-INSTALL THE ONLINE DATA PROTECTION SUITE AFTER USING UP MY 3 INSTALLATIONS? You can re-install the Online Data Protection Suite on the same computer as many times as necessary. However, if you have already installed the software on three computers and need to install it on one more machine, you will not be able to complete the installation. The Online Data Protection Suite license allows installation on up to 3 machines only. HOW DO I UNINSTALL THE ONLINE DATA PROTECTION SOFTWARE? Go to the Start Menu on your computer, select Control Panel, select Uninstall a Program, highlight the Online Data Protection Suite, then click Uninstall and follow the prompts. HOW DO I RENEW MY SOFTWARE? Depending on how you received the software, you may need to renew it once the license expires. You will be prompted by the software to renew near the end of your license period. Just click the renew button and this will automatically take you to the renewal page. HOW DO I USE THE CREDIT MONITOR TAB? If you have already enrolled in your credit monitoring service you can enter your policy/member number in the Credit Monitor Tab (accessed from the DataScrambler or by double-clicking on the Nationwide logo in the tray icon) and proceed to log in to check your credit report. The Credit Monitor Tab also contains your identity theft program s contact information if you ever need support from EA 8
10 USA s identity theft resolution specialists about your credit monitoring benefits, your credit report or in case of identity theft. WHEN I LOOK AT THE ACTIVITY REPORT IT DOES NOT SHOW MY PERSONAL DATA. HOW DO I CHANGE THIS? Go to the Options tab (accessed by clicking on the DataScrambler or double-clicking the Nationwide logo in the tray icon at bottom right of your desktop) and choose the setting to give permission to share your security statistics. Note: only Firefox and Internet Explorer users can receive report data at this time. I WANT TO TURN OFF MY ACTIVITY REPORT OR SEE IT LESS FREQUENTLY. HOW DO I DO THIS? Go to the Options tab, accessed by clicking on the DataScrambler or double-clicking the Nationwide logo in the tray icon at the bottom right of your desktop, and then choose what frequency to display the report. You can also choose Never if you prefer to not have the Activity Report automatically appear. In this case, you can still manually access it by clicking on the DataScrambler or doubleclicking the Nationwide logo in the tray icon at the bottom right of your desktop. I DON T WANT TO SEE THE DATASCRAMBLER. CAN I TURN IT OFF? Yes. To prevent the DataScrambler from showing within the browser, click on the DataScrambler (or double-click the Nationwide logo on the tray icon at the bottom right of your desktop), then select the Options tab. The Display Keystroke Substitution option will have a green check mark next to it. Click on the green check mark to change it to a red X. This will disable the DataScrambler from displaying within your browser the next time you open your browser. 9
11 WHAT AM I AGREEING TO BY CHECKING ALLOW TO PROVIDE ANONYMOUS INFORMATION ABOUT DETECTED THREATS DURING THE INSTALLATION? WHAT HAPPENS IF I DO NOT SELECT THIS BOX? When you agree to provide anonymous information about detected threats, this will allow us to collect statistical data that contributes to the Reports Tab section on the malware you are being protected from. This information is statistical and anonymous in nature; no personal information or browsing habits are being collected. If you do not agree to provide anonymous information about detected threats, the Report Tab will not be able to show your statistics. 10
12 TECHNICAL REQUIREMENTS WHAT ARE THE MINIMUM SYSTEM REQUIREMENTS TO RUN THE ONLINE DATA PROTECTION SOFTWARE? The minimum system requirements are: Windows XP (SP3), Windows Vista (SP2), Windows 7, Windows 8, Windows 8.1 and Windows 10. At least 512 MB RAM, a 233 MHz processor or higher 32/64 bit operating system For browsers, the software supports Internet Explorer 7.0 and above, Firefox 15 and above, and Google Chrome 35 and above. WHAT INTERNET BROWSERS ARE SUPPORTED? If you install the Online Data Protection Suite on your PC/laptop, Internet Explorer 7.0 and above, Firefox 15 and above and Google Chrome 35 and above are supported. WILL THE SOFTWARE WORK WITH MY ANTI-VIRUS OR ANY OTHER SECURITY SOFTWARE? Yes. The Online Data Protection Suite is designed to work alongside all other security suites and software providing you with an extra, real-time layer of protection against data and identity theft. DO I NEED ANTI-VIRUS SOFTWARE IF I AM RUNNING THE ONLINE DATA PROTECTION SUITE? While you now do not need anti-virus to protect against sensitive data being stolen when you use the Internet, anti-virus protects your PC from threats in other areas of your system and has the ability to remove viruses. For this reason we recommend all users install anti-virus and keep it up-to-date. CAN I USE THE SOFTWARE ON MY APPLE/MAC? No. The Online Data Protection Suite currently only operates on the Windows operating system. If you have a Windows partition on your Mac, then you can use the software but it is not supported under OS X operating systems. CAN I INSTALL THE EA USA ONLINE DATA PROTECTION ON MY IPAD OR SMART PHONE? No. The Online Data Protection was specifically designed for the use on a personal computer. Because your smart phone or ipad runs on a mobile operating system, you will not be able to install the Online Data Protection Suite. 11
13 TROUBLESHOOTING AND CUSTOMER SUPPORT I AM HAVING ISSUES USING MY WEB CONFERENCE SERVICE OR SCREEN SHARING SOFTWARE. While the Online Data Protection Suite supports many such services, the screen capture protection can prevent screen sharing with some solutions. To disable this protection and allow the sharing of your screen, click on the DataScrambler (or double-click the Nationwide logo at the bottom right of your desktop), then select the Options tab. The Prevent Screen Capture option will have a green check mark next to it. Click on the green check mark to change the option to a red X. This disables the protection. We recommend you restart this protection once you have completed your web conference or screen sharing activity. WITHIN CERTAIN WEB PAGES/SERVICES, I HAVE SOME ISSUES USING MY KEYBOARD. Some services prevent the Online Data Protection Suite key entry protection from working optimally. Restarting your browser or rebooting your computer will generally resolve 99% of these issues. 12
14 I HAVE A PROBLEM WITH THE SOFTWARE. HOW CAN I GET HELP? If you are experiencing a technical issue or a problem with the software, you can contact EA by using the Help link located on the Options window of the Report Tab which can be accessed by clicking on the DataScrambler (or double-clicking the Nationwide logo at the bottom right of your desktop). THE ONLINE DATA PROTECTION SUITE FAILS TO INSTALL AND I RECEIVE THIS MESSAGE: UNABLE TO CONNECT TO LICENSE SERVER. PLEASE CHECK INTERNET CONNECTION. When the software is unable to connect to the license server, this could mean one of several things. Check the following first: Is your computer connected to the Internet? Can you open a website via your browser? Do you have a local firewall that could be blocking the connection? If so, please disable this for the installation. Your connection may be blocked if you are located on a corporate LAN or in cases where network firewalls, IDP systems and content scanners exist. You should contact your network administrator for further information. THE LICENSE FAILS TO VALIDATE DURING INSTALLATION. If the license fails to validate during installation check the following: Is your computer connected to the Internet? For the installation to succeed, an Internet connection is required. Do you have a local firewall that could be blocking the connection? If so, please disable this for the installation. If you are still experiencing a problem, contact EA at DataProtectionSupport@europassistanceusa.com. 13
15 I CANNOT SEE THE DATASCRAMBLER. If you are unable to see the DataScrambler located in the top right-hand corner of your Internet browser, check the following: Have you installed the Online Data Protection Suite and can you see the Nationwide logo in the top-right hand corner of the browser? Did you reboot your computer after installation? If not, please restart your computer as this is a required process to complete the installation. Try to minimize and maximize the browser, which sometimes brings the DataScrambler into focus. Try to close and re-open the browser. Check to make sure that the browser you are using is supported. View the list of supported browsers Check to make sure that the browser is the active application. I HAVE MISPLACED MY INSTALLATION FILE AND CAN NO LONGER FIND THE DOWNLOAD LINK. If you no longer have the download link, please contact EA at DataProtectionSupport@europassistance-usa.com and we will send you a copy of your confirmation with the link. WHAT HAPPENS IF A WARNING APPEARS ON MY COMPUTER THAT REFERS TO THE ONLINE DATA PROTECTION SUITE? Sometimes you may get a warning screen from your firewall, Windows or anti-virus software about the actions of the Online Data Protection Suite. This is because the software is performing actions needed to protect you that can flag the attention of other software. In most cases you can ignore these warnings and carry on with the use of your computer. The following file names are related to the Online Data Protection Suite: DPS.exe, EP.exe, Data Protection Suite, PL.exe. If none of these are mentioned in the message, then the message likely does not relate to the software. If you are ever unsure, you can contact EA customer support by using the Help link located on the Options window of the Report Tab, which can be accessed by clicking on the DataScrambler (or double-clicking the Nationwide logo at the bottom right of your desktop) or contacting us at DataProtectionSupport@europassistance-usa.com. Please include a screenshot of any warning and a description of the situation in which it arose. I CAN T INSTALL THE ONLINE DATA PROTECTION FROM MY GMAIL ACCOUNT. WHAT SHOULD I DO? Sometimes clicking on a link in gmail to open an attachment will open a new window or tab in the browser before starting the download. This sometimes means the download process did not function properly due to your settings in gmail. You should be able to save the file first and then Run it from your downloaded folder. If you are having difficulties saving the file you can right click on the Online Data Protection Suite link in your confirmation , select Copy Hyperlink and then paste it in a new browser to begin installation. You can also try to turn off popup blocker or add mail.google.com to the allow list. One of these will normally sort out the issue. 14
FAKE ANTIVIRUS MALWARE This information has come from http://www.bleepingcomputer.com/ - a very useful resource if you are having computer issues.
 FAKE ANTIVIRUS MALWARE This information has come from http://www.bleepingcomputer.com/ - a very useful resource if you are having computer issues. The latest tactic currently being used by malware creators
FAKE ANTIVIRUS MALWARE This information has come from http://www.bleepingcomputer.com/ - a very useful resource if you are having computer issues. The latest tactic currently being used by malware creators
Antivirus. Quick Start Guide. Antivirus
 Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Quick Start Guide. www. K7Computing.com
 Quick Start Guide Table of Contents Before you install the Product... 3 Installing the program... 3 Quick Installation... 4 Custom Installation... 4 Installation... 7 Activation... 8 Offline Activation...
Quick Start Guide Table of Contents Before you install the Product... 3 Installing the program... 3 Quick Installation... 4 Custom Installation... 4 Installation... 7 Activation... 8 Offline Activation...
Quick Start. Installing the software. for Webroot Internet Security Complete, Version 7.0
 Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
ESET SMART SECURITY 6
 ESET SMART SECURITY 6 Microsoft Windows 8 / 7 / Vista / XP / Home Server Quick Start Guide Click here to download the most recent version of this document ESET Smart Security provides state-of-the-art
ESET SMART SECURITY 6 Microsoft Windows 8 / 7 / Vista / XP / Home Server Quick Start Guide Click here to download the most recent version of this document ESET Smart Security provides state-of-the-art
ESET SMART SECURITY 9
 ESET SMART SECURITY 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security
ESET SMART SECURITY 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET Smart Security is all-in-one Internet security
Shaw Secure Powered by McAfee Registration and Installation
 OVERVIEW This document will guide you through the process of account registration, downloading, and installing Shaw Secure Powered by McAfee. If you experience any challenges with the software installation
OVERVIEW This document will guide you through the process of account registration, downloading, and installing Shaw Secure Powered by McAfee. If you experience any challenges with the software installation
Welcome to Cox Business Security Suite:
 Welcome to Cox Business Security Suite: Thank you for choosing Cox Business Security Suite Powered by McAfee. Cox Business Security Suite is a simple, efficient and reliable way to protect your business
Welcome to Cox Business Security Suite: Thank you for choosing Cox Business Security Suite Powered by McAfee. Cox Business Security Suite is a simple, efficient and reliable way to protect your business
ESET NOD32 ANTIVIRUS 8
 ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 ANTIVIRUS 8 Microsoft Windows 8.1 / 8 / 7 / Vista / XP / Home Server 2003 / Home Server 2011 Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus
ESET NOD32 Antivirus 4 for Linux Desktop. Quick Start Guide
 ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013
 Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
Welcome To The L.R.F.H.S. Computer Group Wednesday 27 th November 2013 BACKUP SECURITY AND THE CLOUD BACK UP ALWAYS BACK UP TO AN EXTERNAL DEVICE OR REMOVAL MEDIA- NEVER DIRECTLY ON TO YOUR COMPUTER IF
ESET NOD32 ANTIVIRUS 9
 ESET NOD32 ANTIVIRUS 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus provides state-of-the-art protection
ESET NOD32 ANTIVIRUS 9 Microsoft Windows 10 / 8.1 / 8 / 7 / Vista / XP Quick Start Guide Click here to download the most recent version of this document ESET NOD32 Antivirus provides state-of-the-art protection
FOR MAC. Quick Start Guide. Click here to download the most recent version of this document
 FOR MAC Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based on
FOR MAC Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against malicious code. Based on
avast! Free Antivirus 7.0 Quick Start Guide avast! Free Antivirus 7.0 Quick Start Guide
 avast! Free Antivirus 7.0 Quick Start Guide 1 Welcome to avast! Free Antivirus 7.0 The new avast! Antivirus 7.0 brings a range of new features and improvements which make it even faster and even less resource-hungry
avast! Free Antivirus 7.0 Quick Start Guide 1 Welcome to avast! Free Antivirus 7.0 The new avast! Antivirus 7.0 brings a range of new features and improvements which make it even faster and even less resource-hungry
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome
 Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software
Trusteer Rapport. User Guide. Version 3.5.1307 April 2014
 Trusteer Rapport User Guide Version 3.5.1307 April 2014 Contents About this Guide 1 Need More Information about Trusteer Rapport? 1 Sending us Feedback 1 1. What is Trusteer Rapport? 3 Antivirus: A False
Trusteer Rapport User Guide Version 3.5.1307 April 2014 Contents About this Guide 1 Need More Information about Trusteer Rapport? 1 Sending us Feedback 1 1. What is Trusteer Rapport? 3 Antivirus: A False
AT&T Internet Security Suite - powered by McAfee. Installation Guide (for Clean Machine with No Anti-Virus Installed)
 AT&T Internet Security Suite - powered by McAfee Installation Guide (for Clean Machine with No Anti-Virus Installed) Contents 2 Contents Introduction 3 Chapters 1. Start Download Manager...4 2. Select
AT&T Internet Security Suite - powered by McAfee Installation Guide (for Clean Machine with No Anti-Virus Installed) Contents 2 Contents Introduction 3 Chapters 1. Start Download Manager...4 2. Select
Passport Installation. Windows XP + Internet Explorer 8
 Passport Installation Windows XP + Internet Explorer 8 OS Version Windows XP System Type 32bit or 64bit Browser & version Internet Explorer 8 Before you begin.. Make sure you have Anti Virus software installed
Passport Installation Windows XP + Internet Explorer 8 OS Version Windows XP System Type 32bit or 64bit Browser & version Internet Explorer 8 Before you begin.. Make sure you have Anti Virus software installed
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Verizon Internet Security Suite Powered by McAfee. Installation Guide for Business Users
 Verizon Internet Security Suite Powered by McAfee Installation Guide for Business Users ii Contents Introduction 3 System requirements 5 Installing Verizon Internet Security Suite 7 Signing in to your
Verizon Internet Security Suite Powered by McAfee Installation Guide for Business Users ii Contents Introduction 3 System requirements 5 Installing Verizon Internet Security Suite 7 Signing in to your
Instructions for Accessing the Hodges University Virtual Lab
 Instructions for Accessing the Hodges University Virtual Lab Table of Contents Adding the VLAB as a Trusted Site... 3 Accessing the VLAB using Windows 8... 5 Using Internet Explorer and Windows 8 to Access
Instructions for Accessing the Hodges University Virtual Lab Table of Contents Adding the VLAB as a Trusted Site... 3 Accessing the VLAB using Windows 8... 5 Using Internet Explorer and Windows 8 to Access
User Guide for the Identity Shield
 User Guide for the Identity Shield Copyright Webroot SecureAnywhere User Guide for the Identity Shield January, 2013 2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and
User Guide for the Identity Shield Copyright Webroot SecureAnywhere User Guide for the Identity Shield January, 2013 2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and
FAQ. Safe Anywhere PC. Disclaimer:
 FAQ Safe Anywhere PC Version: 1.0 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch
FAQ Safe Anywhere PC Version: 1.0 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Contents. McAfee Internet Security 3
 User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
How to easily clean an infected computer (Malware Removal Guide)
 How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
Trend Micro Antivirus for Mac 2016
 H Trend Micro Antivirus for Mac 2016 Product Guide V1.0 Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
H Trend Micro Antivirus for Mac 2016 Product Guide V1.0 Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
ESET CYBER SECURITY PRO for Mac Quick Start Guide. Click here to download the most recent version of this document
 ESET CYBER SECURITY PRO for Mac Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against
ESET CYBER SECURITY PRO for Mac Quick Start Guide Click here to download the most recent version of this document ESET Cyber Security Pro provides state-of-the-art protection for your computer against
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
CougarTrack Troubleshooting - Internet Explorer 8
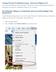 CougarTrack Troubleshooting - Internet Explorer 8 If you are having difficulty accessing pages in CougarTrack, please read through the following information and make any applicable changes to your computer.
CougarTrack Troubleshooting - Internet Explorer 8 If you are having difficulty accessing pages in CougarTrack, please read through the following information and make any applicable changes to your computer.
Contents. VPN Instructions. VPN Instructions... 1
 VPN Instructions Contents VPN Instructions... 1 Download & Install Check Point VPN Software... 2 Connect to FPUA by VPN... 6 Connect to Your Computer... 8 Determine Your Machine Type... 10 Identify 32-bit
VPN Instructions Contents VPN Instructions... 1 Download & Install Check Point VPN Software... 2 Connect to FPUA by VPN... 6 Connect to Your Computer... 8 Determine Your Machine Type... 10 Identify 32-bit
Software. Webroot. Spy Sweeper. User Guide. for. Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com. Version 6.
 Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
Get Started Guide - PC Tools Internet Security
 Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Kaspersky Internet Security User Guide
 Kaspersky Internet Security User Guide APPLICATION VERSION: 15.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Kaspersky Internet Security User Guide APPLICATION VERSION: 15.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Citrix Receiver 11.8 for Macintosh OS X
 1. Document Control Record Document title Document Owner Citrix Receiver 11.8 for Macintosh OS X Rayna McKinley 2. Issue and Amendment Record Issue Date Revised by Comments 1 8/15/2013 Rayna McKinley Original
1. Document Control Record Document title Document Owner Citrix Receiver 11.8 for Macintosh OS X Rayna McKinley 2. Issue and Amendment Record Issue Date Revised by Comments 1 8/15/2013 Rayna McKinley Original
F-Secure Anti-Virus for Mac 2015
 F-Secure Anti-Virus for Mac 2015 TOC F-Secure Anti-Virus for Mac 2015 Contents Chapter 1: Getting started...3 1.1 Manage subscription...4 1.2 How to make sure that my computer is protected...4 1.2.1 Protection
F-Secure Anti-Virus for Mac 2015 TOC F-Secure Anti-Virus for Mac 2015 Contents Chapter 1: Getting started...3 1.1 Manage subscription...4 1.2 How to make sure that my computer is protected...4 1.2.1 Protection
avast! Free Antivirus for Mac Quick Start Guide avast! Free Antivirus for Mac Quick Start Guide
 avast! Free Antivirus for Mac Quick Start Guide 1 Introduction Welcome to avast! Free Antivirus for Mac. avast! Free Antivirus for Mac contains the same ICSA Certified scan engine as all avast! antivirus
avast! Free Antivirus for Mac Quick Start Guide 1 Introduction Welcome to avast! Free Antivirus for Mac. avast! Free Antivirus for Mac contains the same ICSA Certified scan engine as all avast! antivirus
avast! Free Antivirus 8.0 Quick Start Guide avast! Free Antivirus 8.0 Quick Start Guide
 avast! Free Antivirus 8.0 Quick Start Guide 1 Contents Welcome to avast! Antivirus 8.0... 3 How to install avast! Free Antivirus 8.0... 4 Protection Status... 9 More about the real-time shields... 10 Cloud
avast! Free Antivirus 8.0 Quick Start Guide 1 Contents Welcome to avast! Antivirus 8.0... 3 How to install avast! Free Antivirus 8.0... 4 Protection Status... 9 More about the real-time shields... 10 Cloud
How To Use Secureanything On A Mac Or Ipad (For A Mac)
 User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
Security and Protection in Real-Time
 Security and Protection in Real-Time Product White Paper Aug 29, 2006 ParetoLogic Anti-Spyware offers an advanced set of tools designed to protect your computer from spyware threats. There are two lines
Security and Protection in Real-Time Product White Paper Aug 29, 2006 ParetoLogic Anti-Spyware offers an advanced set of tools designed to protect your computer from spyware threats. There are two lines
Kaspersky Internet Security
 Kaspersky Internet Security User Guide APPLICATION VERSION: 16.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Kaspersky Internet Security User Guide APPLICATION VERSION: 16.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
AT&T Internet Security Suite - powered by McAfee. Installation Guide (for Customers with Existing Security Software)
 AT&T Internet Security Suite - powered by McAfee Installation Guide (for Customers with Existing Security Software) Contents 2 Contents Introduction 3 Chapters 1. Start Download Manager...4 2. Remove Incompatible
AT&T Internet Security Suite - powered by McAfee Installation Guide (for Customers with Existing Security Software) Contents 2 Contents Introduction 3 Chapters 1. Start Download Manager...4 2. Remove Incompatible
Kaspersky Small Office Security User Guide
 Kaspersky Small Office Security User Guide APPLICATION VERSION: 4.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Kaspersky Small Office Security User Guide APPLICATION VERSION: 4.0 Dear User, Thank you for choosing our product. We hope that this document will help you in your work and will provide answers regarding
Installing VPN for PC v1.3
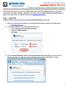 Follow these instructions to access your Public/Private folders from home. Please Note: If you are having connectivity issues after installing or upgrading VPN, please refer to Troubleshooting Connectivity
Follow these instructions to access your Public/Private folders from home. Please Note: If you are having connectivity issues after installing or upgrading VPN, please refer to Troubleshooting Connectivity
Remote Access to Niagara Wheatfield s Computer Network
 Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
PC Troubleshooting Steps
 PC Troubleshooting Steps This FAQ is designed to help PC users to go through various troubleshooting steps to allow them to view the FerrisConnect Learn/Vista sites appropriately. Compatible Browsers Check
PC Troubleshooting Steps This FAQ is designed to help PC users to go through various troubleshooting steps to allow them to view the FerrisConnect Learn/Vista sites appropriately. Compatible Browsers Check
DataTraveler Locker+ User Manual
 DataTraveler Locker+ User Manual Document No. 48008071-001.A02 DataTraveler Locker+ Page 1 of 22 Table of Contents About This Manual... 3 System Requirements... 3 Recommendations... 3 Setup (Windows Environment)...
DataTraveler Locker+ User Manual Document No. 48008071-001.A02 DataTraveler Locker+ Page 1 of 22 Table of Contents About This Manual... 3 System Requirements... 3 Recommendations... 3 Setup (Windows Environment)...
SecuraLive ULTIMATE SECURITY
 SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
Passport installation Windows 8 + Firefox
 Passport installation Windows 8 + Firefox OS Version Windows 8 System Type 32-bit and 64-bit Browser name & version Firefox 23 Before you begin Check you have Anti Virus software installed on your computer
Passport installation Windows 8 + Firefox OS Version Windows 8 System Type 32-bit and 64-bit Browser name & version Firefox 23 Before you begin Check you have Anti Virus software installed on your computer
MacScan. MacScan User Guide. Detect, Isolate and Remove Spyware
 MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
MacScan MacScan User Guide Detect, Isolate and Remove Spyware Part 1 1.1 Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files
What's the difference between spyware and a virus? What is Scareware?
 What's the difference between spyware and a virus? What is Scareware? Spyware and viruses are both forms of unwanted or malicious software, sometimes called "malware." You can use Microsoft Security Essentials
What's the difference between spyware and a virus? What is Scareware? Spyware and viruses are both forms of unwanted or malicious software, sometimes called "malware." You can use Microsoft Security Essentials
Cyber Security: Software Security and Hard Drive Encryption
 Links in this document have been set for a desktop computer with the resolution set to 1920 x 1080 pixels. Cyber Security: Software Security and Hard Drive Encryption 301-1497, Rev A September 2012 Copyright
Links in this document have been set for a desktop computer with the resolution set to 1920 x 1080 pixels. Cyber Security: Software Security and Hard Drive Encryption 301-1497, Rev A September 2012 Copyright
The current case DNSChanger what computer users can do now
 The current case DNSChanger what computer users can do now Content What happened so far? 2 What is going to happen on 8 March 2012? 2 How can I test my Internet settings? 2 On the PC 3 On the router 5
The current case DNSChanger what computer users can do now Content What happened so far? 2 What is going to happen on 8 March 2012? 2 How can I test my Internet settings? 2 On the PC 3 On the router 5
Using desktop ANYWHERE
 Using desktop ANYWHERE A facility for students and staff which provides access to University IT facilities from most computers which have a connection to the Internet. Using a web browser you can access:
Using desktop ANYWHERE A facility for students and staff which provides access to University IT facilities from most computers which have a connection to the Internet. Using a web browser you can access:
DOE VPN Client Installation and Setup Guide March 2011
 DOE VPN Client Installation and Setup Guide March 2011 Table of Contents Introduction... 3 System Requirements... 3 Microsoft Windows... 3 Mac OS X... 4 Windows... 4 Installation for the Cisco AnyConnect
DOE VPN Client Installation and Setup Guide March 2011 Table of Contents Introduction... 3 System Requirements... 3 Microsoft Windows... 3 Mac OS X... 4 Windows... 4 Installation for the Cisco AnyConnect
avast! Internet Security 7.0 Quick Start Guide avast! Internet Security 7.0 Quick Start Guide
 avast! Internet Security 7.0 Quick Start Guide 1 Welcome to avast! Internet Security 7.0 The new avast! Antivirus 7.0 brings a range of new features and improvements which make it even faster and even
avast! Internet Security 7.0 Quick Start Guide 1 Welcome to avast! Internet Security 7.0 The new avast! Antivirus 7.0 brings a range of new features and improvements which make it even faster and even
Kaseya 2. User Guide. Version 1.1
 Kaseya 2 AntiMalware User Guide Version 1.1 September 30, 2013 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULA as updated
Kaseya 2 AntiMalware User Guide Version 1.1 September 30, 2013 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULA as updated
User Guide. Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved.
 Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved. Table of Contents Getting Started... 4 New Features... 4 System Requirements... 4 Configuring Microsoft Internet Explorer... 4 Configuring
Copyright 2003 Networks Associates Technology, Inc. All Rights Reserved. Table of Contents Getting Started... 4 New Features... 4 System Requirements... 4 Configuring Microsoft Internet Explorer... 4 Configuring
Optimal Browser Settings for Internet Explorer Running on Microsoft Windows
 Optimal Browser Settings for Internet Explorer Running on Microsoft Windows If you have Internet Explorer 7 or 8: Each time you log in to our web site, it evaluates whether you are using the same computer
Optimal Browser Settings for Internet Explorer Running on Microsoft Windows If you have Internet Explorer 7 or 8: Each time you log in to our web site, it evaluates whether you are using the same computer
Safe internet: Getting Started Guide
 Safe internet: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial Configuration
Safe internet: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial Configuration
How to Install Windows 7 software
 Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Installation & Licensing Guide. AquiferTest Pro. An Easy-to-Use Pumping Test and Slug Test Data Analysis Package
 Installation & Licensing Guide AquiferTest Pro An Easy-to-Use Pumping Test and Slug Test Data Analysis Package Table of Contents Software Maintenance and Support... 3 How to Contact SWS... 3 System Requirements...
Installation & Licensing Guide AquiferTest Pro An Easy-to-Use Pumping Test and Slug Test Data Analysis Package Table of Contents Software Maintenance and Support... 3 How to Contact SWS... 3 System Requirements...
Kaspersky Security 9.0 for Microsoft SharePoint Server Administrator's Guide
 Kaspersky Security 9.0 for Microsoft SharePoint Server Administrator's Guide APPLICATION VERSION: 9.0 Dear User! Thank you for choosing our product. We hope that this document will help you in your work
Kaspersky Security 9.0 for Microsoft SharePoint Server Administrator's Guide APPLICATION VERSION: 9.0 Dear User! Thank you for choosing our product. We hope that this document will help you in your work
avast! Pro Antivirus 7.0 Quick Start Guide avast! Pro Antivirus 7.0 Quick Start Guide
 avast! Pro Antivirus 7.0 Quick Start Guide 1 Welcome to avast! Pro Antivirus 7.0 The new avast! Antivirus 7.0 brings a range of new features and improvements which make it even faster and even less resource-hungry
avast! Pro Antivirus 7.0 Quick Start Guide 1 Welcome to avast! Pro Antivirus 7.0 The new avast! Antivirus 7.0 brings a range of new features and improvements which make it even faster and even less resource-hungry
Kaspersky Internet Security 2014: Reviewer s Guide
 Kaspersky Internet Security 2014: Reviewer s Guide Index 1 Introduction... 3 2 Key Benefits... 3 2.1 Real-time protection against all Internet threats 3 2.2 Secure online banking and shopping 4 2.3 Proactive
Kaspersky Internet Security 2014: Reviewer s Guide Index 1 Introduction... 3 2 Key Benefits... 3 2.1 Real-time protection against all Internet threats 3 2.2 Secure online banking and shopping 4 2.3 Proactive
MiraCosta College now offers two ways to access your student virtual desktop.
 MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access
 Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
Downloading, Installing, and Updating Sophos Anti-Virus
 Downloading, Installing, and Updating Sophos Anti-Virus Part 1: Downloading Sophos Anti-Virus 1) Open your Internet browser and go to www.bol.ucla.edu. *Only use Chrome or Firefox to download this installation.
Downloading, Installing, and Updating Sophos Anti-Virus Part 1: Downloading Sophos Anti-Virus 1) Open your Internet browser and go to www.bol.ucla.edu. *Only use Chrome or Firefox to download this installation.
Ad-Aware Antivirus Overview
 Contents Ad-Aware Antivirus Overview... 3 What is Ad-Aware Antivirus?... 3 Ad-Aware Antivirus Features... 4 System Requirements... 6 Getting Started... 7 Ad-Aware Install... 7 Using Ad-Aware Free 30 day
Contents Ad-Aware Antivirus Overview... 3 What is Ad-Aware Antivirus?... 3 Ad-Aware Antivirus Features... 4 System Requirements... 6 Getting Started... 7 Ad-Aware Install... 7 Using Ad-Aware Free 30 day
Fiery E100 Color Server. Welcome
 Fiery E100 Color Server Welcome 2011 Electronics For Imaging, Inc. The information in this publication is covered under Legal Notices for this product. 45098226 27 June 2011 WELCOME 3 WELCOME This Welcome
Fiery E100 Color Server Welcome 2011 Electronics For Imaging, Inc. The information in this publication is covered under Legal Notices for this product. 45098226 27 June 2011 WELCOME 3 WELCOME This Welcome
2. PMP New Computer Installation. & Networking Instructions
 ONTARIO CHIROPRACTIC ASSOCIATION PATIENT MANAGEMENT PROGRAM PUTTING EXPERIENCE INTO PRACTICE PMP New Computer Installation & Networking Instructions This document provides installation instructions for
ONTARIO CHIROPRACTIC ASSOCIATION PATIENT MANAGEMENT PROGRAM PUTTING EXPERIENCE INTO PRACTICE PMP New Computer Installation & Networking Instructions This document provides installation instructions for
Parallels Transporter Agent
 Parallels Transporter Agent User's Guide Copyright 1999-2015 Parallels IP Holdings GmbH and its affiliates. All rights reserved. Parallels IP Holdings GmbH Vordergasse 59 8200 Schaffhausen Switzerland
Parallels Transporter Agent User's Guide Copyright 1999-2015 Parallels IP Holdings GmbH and its affiliates. All rights reserved. Parallels IP Holdings GmbH Vordergasse 59 8200 Schaffhausen Switzerland
Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
2013 ACT Special Study Learn to Administer the ACT Aspire Online Test
 2013 ACT Special Study Learn to Administer the ACT Aspire Online Test Page 1 of 16 Learn to Administer the ACT Aspire Online Test If you are a Test Supervisor, you will be able to do everything listed
2013 ACT Special Study Learn to Administer the ACT Aspire Online Test Page 1 of 16 Learn to Administer the ACT Aspire Online Test If you are a Test Supervisor, you will be able to do everything listed
Charter Business Desktop Security Administrator's Guide
 Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
Verizon Internet Security Suite Multi-Device Powered by McAfee. Installation Guide for Multi Devices for Residential Users
 Verizon Internet Security Suite Multi-Device Powered by McAfee Installation Guide for Multi Devices for Residential Users Contents Introduction 3 System requirements 4 Installing Verizon Internet Security
Verizon Internet Security Suite Multi-Device Powered by McAfee Installation Guide for Multi Devices for Residential Users Contents Introduction 3 System requirements 4 Installing Verizon Internet Security
Contents. Hardware Configuration... 27 Uninstalling Shortcuts Black...29
 Contents Getting Started...1 Check your Computer meets the Minimum Requirements... 1 Ensure your Computer is Running in Normal Sized Fonts... 7 Ensure your Regional Settings are Correct... 9 Reboot your
Contents Getting Started...1 Check your Computer meets the Minimum Requirements... 1 Ensure your Computer is Running in Normal Sized Fonts... 7 Ensure your Regional Settings are Correct... 9 Reboot your
1. Any email requesting personal information, or asking you to verify an account, is usually a scam... even if it looks authentic.
 Your identity is one of the most valuable things you own. It s important to keep your identity from being stolen by someone who can potentially harm your good name and financial well-being. Identity theft
Your identity is one of the most valuable things you own. It s important to keep your identity from being stolen by someone who can potentially harm your good name and financial well-being. Identity theft
Installing VinNOW Client Computers
 Installing VinNOW Client Computers Please review this entire document prior to proceeding Client computers must use UNC path for database connection and can t be connected using a mapped network drive.
Installing VinNOW Client Computers Please review this entire document prior to proceeding Client computers must use UNC path for database connection and can t be connected using a mapped network drive.
AVG AntiVirus Free Edition 2015
 AVG AntiVirus Free Edition 2015 User Manual Document revision 2015.18 (3.2.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
AVG AntiVirus Free Edition 2015 User Manual Document revision 2015.18 (3.2.2015) C opyright AVG Technologies C Z, s.r.o. All rights reserved. All other trademarks are the property of their respective owners.
Dexcom Portrait on the Web User Guide For Use with the Dexcom G4 PLATINUM Continuous Glucose Monitoring System
 Dexcom Portrait on the Web User Guide For Use with the Dexcom G4 PLATINUM Continuous Glucose Monitoring System LBL 0123491 Rev 10 Table of Contents 1 Introduction to Dexcom Portrait on the Web... 3 1.1
Dexcom Portrait on the Web User Guide For Use with the Dexcom G4 PLATINUM Continuous Glucose Monitoring System LBL 0123491 Rev 10 Table of Contents 1 Introduction to Dexcom Portrait on the Web... 3 1.1
Bitdefender Internet Security 2015 User's Guide
 USER'S GUIDE Bitdefender Internet Security 2015 User's Guide Publication date 10/16/2014 Copyright 2014 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
USER'S GUIDE Bitdefender Internet Security 2015 User's Guide Publication date 10/16/2014 Copyright 2014 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
User Guide for PCs. SecureAnywhere AntiVirus SecureAnywhere Internet Security Plus SecureAnywhere Complete Endpoint Protection
 User Guide for PCs SecureAnywhere AntiVirus SecureAnywhere Internet Security Plus SecureAnywhere Complete Endpoint Protection Copyright Webroot SecureAnywhere User Guide for PCs July, 2013 2013 Webroot
User Guide for PCs SecureAnywhere AntiVirus SecureAnywhere Internet Security Plus SecureAnywhere Complete Endpoint Protection Copyright Webroot SecureAnywhere User Guide for PCs July, 2013 2013 Webroot
System Use Requirements
 ProjectDox Component Customer Installation v. 8.3.8.8 System Use Requirements 4835 East Cactus Road Suite 420 Scottsdale, Arizona 85254 Phone: 602.714.9774 www.avolvesoftware.com Copyright 2015 Avolve
ProjectDox Component Customer Installation v. 8.3.8.8 System Use Requirements 4835 East Cactus Road Suite 420 Scottsdale, Arizona 85254 Phone: 602.714.9774 www.avolvesoftware.com Copyright 2015 Avolve
Table of Contents. FleetSoft Installation Guide
 FleetSoft Installation Guide Table of Contents FleetSoft Installation Guide... 1 Minimum System Requirements... 2 Installation Notes... 3 Frequently Asked Questions... 4 Deployment Overview... 6 Automating
FleetSoft Installation Guide Table of Contents FleetSoft Installation Guide... 1 Minimum System Requirements... 2 Installation Notes... 3 Frequently Asked Questions... 4 Deployment Overview... 6 Automating
formerly Help Desk Authority 9.1.3 Upgrade Guide
 formerly Help Desk Authority 9.1.3 Upgrade Guide 2 Contacting Quest Software Email: Mail: Web site: info@quest.com Quest Software, Inc. World Headquarters 5 Polaris Way Aliso Viejo, CA 92656 USA www.quest.com
formerly Help Desk Authority 9.1.3 Upgrade Guide 2 Contacting Quest Software Email: Mail: Web site: info@quest.com Quest Software, Inc. World Headquarters 5 Polaris Way Aliso Viejo, CA 92656 USA www.quest.com
Non-Employee VPN Quick Start Guide
 1. Computer Requirements Pentium-based personal computer Windows XP SP3: 128 MB RAM Windows Vista Windows 7 Home/Pro 10 MB hard disk space Microsoft Internet Explorer 6.0 or later or Mozilla Firefox 1.0
1. Computer Requirements Pentium-based personal computer Windows XP SP3: 128 MB RAM Windows Vista Windows 7 Home/Pro 10 MB hard disk space Microsoft Internet Explorer 6.0 or later or Mozilla Firefox 1.0
Student Getting Started Guide
 with with Student Getting Started Guide TABLE OF CONTENTS Table of Contents FIRST STEPS TO ENSURE SUCCESS... 3 Ensure System Requirements are met on Your Computer... 3 Find Out Which Operating System Is
with with Student Getting Started Guide TABLE OF CONTENTS Table of Contents FIRST STEPS TO ENSURE SUCCESS... 3 Ensure System Requirements are met on Your Computer... 3 Find Out Which Operating System Is
How To Use Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Cox Business Premium Security Service FAQs
 FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
Securing Your Business s Bank Account
 Commercial Banking Customers Securing Your Business s Bank Account Trusteer Rapport Resource Guide For Business Banking January 2014 Table of Contents 1. Introduction 3 Who is Trusteer? 3 2. What is Trusteer
Commercial Banking Customers Securing Your Business s Bank Account Trusteer Rapport Resource Guide For Business Banking January 2014 Table of Contents 1. Introduction 3 Who is Trusteer? 3 2. What is Trusteer
Using Spy Sweeper for Windows Author: Jocelyn Kasamoto
 WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
Section 1.0 Getting Started with the Vālant EMR. Contents
 Section 1.0 Getting Started with the Vālant EMR Contents Getting Started with the Valant EMR application:... 2 Hardware Requirements for the Vālant EMR:... 3 Software Requirements for the Vālant EMR:...
Section 1.0 Getting Started with the Vālant EMR Contents Getting Started with the Valant EMR application:... 2 Hardware Requirements for the Vālant EMR:... 3 Software Requirements for the Vālant EMR:...
McAfee.com Personal Firewall
 McAfee.com Personal Firewall 1 Table of Contents Table of Contents...2 Installing Personal Firewall...3 Configuring Personal Firewall and Completing the Installation...3 Configuring Personal Firewall...
McAfee.com Personal Firewall 1 Table of Contents Table of Contents...2 Installing Personal Firewall...3 Configuring Personal Firewall and Completing the Installation...3 Configuring Personal Firewall...
Payment Fraud and Risk Management
 Payment Fraud and Risk Management Act Today! 1. Help protect your computer against viruses and spyware by using anti-virus and anti-spyware software and automatic updates. Scan your computer regularly
Payment Fraud and Risk Management Act Today! 1. Help protect your computer against viruses and spyware by using anti-virus and anti-spyware software and automatic updates. Scan your computer regularly
VirtualXP Users Guide
 VirtualXP Users Guide Contents Chapter 1: Introduction... 2 Chapter 2: Install and Uninstall VirtualXP... 3 2.1 System Requirement... 3 2.2 Installing VirtualXP... 3 2.3 Uninstalling VirtualXP... 3 Chapter
VirtualXP Users Guide Contents Chapter 1: Introduction... 2 Chapter 2: Install and Uninstall VirtualXP... 3 2.1 System Requirement... 3 2.2 Installing VirtualXP... 3 2.3 Uninstalling VirtualXP... 3 Chapter
Kaspersky Password Manager
 Kaspersky Password Manager User Guide Dear User, Thank you for choosing our product. We hope that you will find this documentation useful and that it will provide answers to most questions that may arise.
Kaspersky Password Manager User Guide Dear User, Thank you for choosing our product. We hope that you will find this documentation useful and that it will provide answers to most questions that may arise.
Citrix : Remediation - MAC
 Citrix : Remediation - MAC Key Points: 1. 2. 3. 4. 5. 6. 7. Understanding End Point Scan Analysis Supported anti-virus and firewall products Configuring AVAST/SOPHOS and the Mac OS X Firewall Installing
Citrix : Remediation - MAC Key Points: 1. 2. 3. 4. 5. 6. 7. Understanding End Point Scan Analysis Supported anti-virus and firewall products Configuring AVAST/SOPHOS and the Mac OS X Firewall Installing
Technology Services Group Procedures. IH Anywhere guide. 0 P a g e
 VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
Verizon Remote Access User Guide
 Version 17.12 Last Updated: August 2012 2012 Verizon. All Rights Reserved. The Verizon names and logos and all other names, logos, and slogans identifying Verizon s products and services are trademarks
Version 17.12 Last Updated: August 2012 2012 Verizon. All Rights Reserved. The Verizon names and logos and all other names, logos, and slogans identifying Verizon s products and services are trademarks
