Understanding Secure Shell Host Keys
|
|
|
- Marilyn Skinner
- 10 years ago
- Views:
Transcription
1 Understanding Secure Shell Host Keys White Paper 4848 tramway ridge dr. ne suite 101 albuquerque, nm
2 Understanding Host Keys Think about the last time you faxed personal or company information to someone for the first time. Did you wonder if the number you were sending this information to was the right one? Unlike a phone call, where no personal information is exchanged until you have identified who you are speaking to, when you send a fax you might wonder where your information is ending up. When using the public network (internet), verifying that the server being connected to is the right number is taken for granted far too often. In this white paper, we will talk about the importance of knowing that the server you (or one of your end users) is connecting to is the right number and how Secure Shell server host keys are used to verify a server s identity. This paper assumes the reader has a general familiarity with the Secure Shell protocol. For more information, refer to our Secure Shell Overview white paper which can be read online or downloaded from our web site: Here is a brief excerpt from that white paper s introduction: Secure Shell (SSH) provides an open protocol for securing network communications which is less complex and expensive than hardware-based VPN solutions. Secure Shell client/server solutions provide command shell, file transfer, and data tunneling services for TCP/IP applications. SSH connections provide highly secure authentication, encryption, and data integrity to combat password theft and other security threats. Introduction Users and administrators turn to Secure Shell for many reasons. Some need to replace Telnet or FTP. Others are looking to move away from simple passwords to public-key, Kerberos, or keyboard-interactive authentication. Still others are looking for a low cost alternative to VPNs. Whatever the reason for using Secure Shell, every user and administrator of Secure Shell needs to understand host keys. Understanding what host keys are, how they work, and the security they provide can reduce confusion and possible frustration about administering and using this authentication tool for both administrators and end users. Failure to understand host keys can cause many problems. Some users may be frightened or confused by messages when a new or changed host key is encountered. This can result in additional and unnecessary support costs. Even worse, improper handling of host keys can lead to a compromised system. What vulnerabilities do host keys help address? Man-in-the middle attacks: When you connect to a remote host, if you cannot reliably verify that the host key is from the host you intend to connect to, you risk the possibility that an adversary has placed a server pretending to be the Secure Shell server between you and the final destination. The server you re actually connecting to is a man-in-the-middle. This man-in-themiddle is able to see both the username and password information you transmit as you attempt to authenticate. Once intercepted, a man-in-the-middle can use this information to establish a connection with the remote server and see all traffic between you and the remote server. Understanding Secure Shell Host Keys VanDyke Software, Inc.
3 Depending on your network topology, the risk of man-in-the-middle attack can vary widely. If users and administrators take some very basic steps, the risk of a man-in-the-middle attack can be significantly reduced. How web servers prevent man-in-the-middle attacks: This uncertainty about the authenticity of a remote host is not a unique problem. Most of us have connected to a secure web server at one time or another. We look down at the bottom corner of the browser and we see a little padlock. It gives us a warm fuzzy feeling that we know we have connected to a secure web server. So, how do secure web servers solve this problem? A secure web server uses a certificate issued by a trusted third-party Certificate Authority (CA) such as VeriSign and the client is responsible for checking that certificate upon connecting. In Internet Explorer and other browsers, you can review a list of certificate authorities that are deemed to be trusted. When you initially connect to the web server, the browser checks the certificate it receives from the remote server to see that it has been signed by one of the known trusted authorities. It also checks to see if the certificate has been revoked or expired. If a certificate has been revoked or expired, a dialogue will pop up indicating there is a problem with the certificate. You can also get a pop-up dialog if the certificate doesn t match the host you are connecting to. In general, Secure Shell servers don't have the same type of key infrastructure that web servers depend on. Most Secure Shell servers rely on host keys that are created automatically by the server after installation. And these host keys can't easily be verified the first time a client connects. What is the purpose of the host key? A host key is the server s public key. The host key is used by the client to decrypt an authentication message sent from the server when connecting. The basic purpose of the host key is to ensure that when you connect to a remote host, it is actually the host that you intended to connect to. Unfortunately, this presents something of a catch-22, as described in the following illustrations. If you've never connected to the host before, how do you know the host you are connecting to is the right one? In Secure Shell, host keys can be used for host-based authentication, but this paper will not be addressing host-based authentication since it is not widely used. Creating host keys Creating a host key for a Secure Shell server is usually done only once. The server software creates the host key automatically during installation and configuration. Less commonly, an administrator can elect to manually generate a host key and select the encryption algorithm and key length. For those of you familiar with Secure Shell's public-key authentication, the choice of algorithms (DSA or RSA) and the key length (usually between 1024 and 2048 bits long) is identical to the options for those user authentication keys. A host key consists of two components, a private and a public component. The public component is sent to the client when the client connects. The private component should be protected so that only the administrator and the Secure Shell server have access to it. This cannot be overemphasized. If an adversary acquires a copy of the private host key, it can be used to impersonate your server with complete impunity. Understanding Secure Shell Host Keys VanDyke Software, Inc.
4 Accepting a new host key The illustrations below describe how the client application and the host perform a host key exchange when connecting for the first time. Once the connection is established, the key exchange takes place before any personal data is sent by the client application. Understanding Secure Shell Host Keys VanDyke Software, Inc.
5 If the host key does not match an existing key in the client application s host key database, a challenge message is generated by the client application. An example text message and dialog box are shown below. The host key database does not contain an entry for the hostname myserver, which resolved to , port 22. It is recommended you verify your host key before accepting. Server's host key fingerprint (MD5 hash): 14:09:26:bc:13:24:31:5c:f7:6c:39:94:f7:4d:52:14 If you trust this host, enter y to add the key to the host key database and connect. If you do not trust this host, enter n to abandon the connection. Accept and save? (y/n) If you re using a Windows client, you may see a dialog such as: Many users, not understanding exactly what the text or dialog means, simply accept the new host key. Accepting the key is problematic if the user does not know for certain that the host key it has just accepted is actually from the server that the client believes it is connecting to. Understanding Secure Shell Host Keys VanDyke Software, Inc.
6 Before accepting the new host keys, the user should use a secure method to verify that the host key corresponds to the actual server. When a Secure Shell server host key is created, a unique fingerprint is also generated. This fingerprint is a human-readable cryptographic hash that can be used to verify the authenticity of the key being presented by the server to the client. Methods for verifying host keys, including using the host key s fingerprint, are discussed below. Handling a changed host key After a host key has been accepted and saved, the user should not see this message again. However, if the host key presented by the server on a subsequent connection is different from the one saved on the user s local system, a second message will be displayed. Here is an example: The host key sent by the server is different from the host key stored in the host key database for myserver ( ), port 22. This may mean that a hostile party has "hijacked" your connection and you are not connected to the server you specified. It is recommended you verify your host key before accepting. Server's host key fingerprint (MD5 hash): 14:09:26:bc:13:24:31:5c:f7:6c:39:94:f7:4d:52:14 If you trust this host, enter y to add the key to the host key database and connect. If you do not trust this host, enter n to abandon the connection. Accept and save? (y/n) As you can see from the text of the message, a user seeing words such as hijacked might get very nervous. There are several scenarios that could cause this situation. The first is that the Understanding Secure Shell Host Keys VanDyke Software, Inc.
7 server has been compromised or you are experiencing a man-in-the-middle attack. However, this is not usually the case. Here are a few more likely senarios. 1. It s possible that the administrator changed the host key. 2. The machine the user is connecting to actually has more than one Secure Shell server running and the client is not keeping track of the different host keys for the different servers running on the same machine. 3. The adminstrator rebuilt the server and did not preserve the host keys. As with a new host key, before accepting the changed host key, the user should use a secure method to verify the host key being presented corresponds to the actual server. Here are a few methods to address this question of host authenticity. Known hosts After the client connects to the server for the first time and accepts and saves the host key, it is stored in a local database. One solution for eliminating the need to manually verify the host key is for the administrator to pre-populate the database of known hosts on each of the client machines. Where host keys are stored and the exact format they are stored in is usually client specific. For example, in SecureCRT or SecureFX, host keys are stored in the user's application data area and can be viewed, imported, or deleted using the Global Options dialog. For VanDyke's Linux and UNIX servers, they are stored in the user's home directory under ~/.vshell/known_hosts. In addition, most clients also look in a common location. For example, under Linux or UNIX, a common set of known host keys can be found in /usr/local/etc/known_hosts. Verifying host keys Calling the system administrator and verifying the host key over the phone is a simple solution to making sure the host key is correct and that the client is not vulnerable to a man-in-the-middle attack. However, in many situations this is not a practical solution. There may be too many servers. There may be too many clients. Or, the administrator may not be available when the user first connects. There are a number of other methods that can be used to distribute host keys or fingerprints: An ISP or network administrator might distribute host key fingerprints on a secure web page that all customers or users have access to. The host key fingerprint can be sent by to end users so they have it readily available to compare to the fingerprint displayed in the challenge message. For enterprises that already use a system such as SMS to push files out to client systems, host keys could also be distributed through this system. Organizations using Kerberos could take advantage of Secure Shell's GSSAPI key exchange which doesn't require hosts keys and instead leverages Kerberos host verification. Recently, an IETF draft has been released that specifies a method of checking host key fingerprints using secure DNS (DNSSEC). Secure Shell solutions implementing this new mechanism are not yet widely available. Understanding Secure Shell Host Keys VanDyke Software, Inc.
8 Backup your host keys As with any critical data, backing up your host keys is a good idea. If you should ever need to rebuild your Secure Shell server or migrate it to a new machine, these backups will be invaluable in effecting a smooth and transparent transition for your users. The need for policy With any security solution, there is a need for policy. As part of a company's security awareness training, users should be educated about the value of host keys and made aware of a company's procedure for checking host keys. Clearly communicating this policy can alleviate a lot of the fear, uncertainty, and doubt that accompany users decision-making when a new host key is presented. Administrators should understand that changing host keys could have a ripple effect. In the case where a host key must be changed, the change should, if at all possible, be communicated to users of the service in advance of making it. By doing so, much of the help desk grief can be eliminated. Summary Turning off Telnet and FTP and moving to Secure Shell makes sense and protects both passwords and data from being sent in the clear. In addition to encryption, Secure Shell provides a way to authenticate both the end user and host. This document has illustrated how host keys play an integral role in establishing this trusted connection. In order to maintain the security and integrity of the system, users and administrators need to understand host keys and the correct method for verifying them. Understanding Secure Shell Host Keys VanDyke Software, Inc.
An Overview of the Secure Shell (SSH)
 White Paper An Overview of the Secure Shell (SSH) 4848 tramway ridge dr. ne suite 101 albuquerque, nm 87111 505-332 -5700 www.vandyke.com Overview of Secure Shell... 2 Introduction to Secure Shell... 2
White Paper An Overview of the Secure Shell (SSH) 4848 tramway ridge dr. ne suite 101 albuquerque, nm 87111 505-332 -5700 www.vandyke.com Overview of Secure Shell... 2 Introduction to Secure Shell... 2
TELE 301 Network Management. Lecture 16: Remote Terminal Services
 TELE 301 Network Management Lecture 16: Remote Terminal Services Haibo Zhang Computer Science, University of Otago TELE301 Lecture 16: Remote Terminal Services 1 Today s Focus Remote Terminal Services
TELE 301 Network Management Lecture 16: Remote Terminal Services Haibo Zhang Computer Science, University of Otago TELE301 Lecture 16: Remote Terminal Services 1 Today s Focus Remote Terminal Services
DRAFT Standard Statement Encryption
 DRAFT Standard Statement Encryption Title: Encryption Standard Document Number: SS-70-006 Effective Date: x/x/2010 Published by: Department of Information Systems 1. Purpose Sensitive information held
DRAFT Standard Statement Encryption Title: Encryption Standard Document Number: SS-70-006 Effective Date: x/x/2010 Published by: Department of Information Systems 1. Purpose Sensitive information held
Chapter 17. Transport-Level Security
 Chapter 17 Transport-Level Security Web Security Considerations The World Wide Web is fundamentally a client/server application running over the Internet and TCP/IP intranets The following characteristics
Chapter 17 Transport-Level Security Web Security Considerations The World Wide Web is fundamentally a client/server application running over the Internet and TCP/IP intranets The following characteristics
LoadMaster SSL Certificate Quickstart Guide
 LoadMaster SSL Certificate Quickstart Guide for the LM-1500, LM-2460, LM-2860, LM-3620, SM-1020 This guide serves as a complement to the LoadMaster documentation, and is not a replacement for the full
LoadMaster SSL Certificate Quickstart Guide for the LM-1500, LM-2460, LM-2860, LM-3620, SM-1020 This guide serves as a complement to the LoadMaster documentation, and is not a replacement for the full
2 Advanced Session... Properties 3 Session profile... wizard. 5 Application... preferences. 3 ASCII / Binary... Transfer
 Contents I Table of Contents Foreword 0 Part I SecEx Overview 3 1 What is SecEx...? 3 2 Quick start... 4 Part II Configuring SecEx 5 1 Session Profiles... 5 2 Advanced Session... Properties 6 3 Session
Contents I Table of Contents Foreword 0 Part I SecEx Overview 3 1 What is SecEx...? 3 2 Quick start... 4 Part II Configuring SecEx 5 1 Session Profiles... 5 2 Advanced Session... Properties 6 3 Session
Security Policy Revision Date: 23 April 2009
 Security Policy Revision Date: 23 April 2009 Remote Desktop Support Version 3.2.1 or later for Windows Version 3.1.2 or later for Linux and Mac 4 ISL Light Security Policy This section describes the procedure
Security Policy Revision Date: 23 April 2009 Remote Desktop Support Version 3.2.1 or later for Windows Version 3.1.2 or later for Linux and Mac 4 ISL Light Security Policy This section describes the procedure
Network-Enabled Devices, AOS v.5.x.x. Content and Purpose of This Guide...1 User Management...2 Types of user accounts2
 Contents Introduction--1 Content and Purpose of This Guide...........................1 User Management.........................................2 Types of user accounts2 Security--3 Security Features.........................................3
Contents Introduction--1 Content and Purpose of This Guide...........................1 User Management.........................................2 Types of user accounts2 Security--3 Security Features.........................................3
How To Understand And Understand The Security Of A Key Infrastructure
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 12 Applying Cryptography Objectives Define digital certificates List the various types of digital certificates and how they are used
Chapter 7 Transport-Level Security
 Cryptography and Network Security Chapter 7 Transport-Level Security Lectured by Nguyễn Đức Thái Outline Web Security Issues Security Socket Layer (SSL) Transport Layer Security (TLS) HTTPS Secure Shell
Cryptography and Network Security Chapter 7 Transport-Level Security Lectured by Nguyễn Đức Thái Outline Web Security Issues Security Socket Layer (SSL) Transport Layer Security (TLS) HTTPS Secure Shell
Cornerstones of Security
 Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Using Entrust certificates with VPN
 Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Understanding the Cisco VPN Client
 Understanding the Cisco VPN Client The Cisco VPN Client for Windows (referred to in this user guide as VPN Client) is a software program that runs on a Microsoft Windows -based PC. The VPN Client on a
Understanding the Cisco VPN Client The Cisco VPN Client for Windows (referred to in this user guide as VPN Client) is a software program that runs on a Microsoft Windows -based PC. The VPN Client on a
This chapter describes how to set up and manage VPN service in Mac OS X Server.
 6 Working with VPN Service 6 This chapter describes how to set up and manage VPN service in Mac OS X Server. By configuring a Virtual Private Network (VPN) on your server you can give users a more secure
6 Working with VPN Service 6 This chapter describes how to set up and manage VPN service in Mac OS X Server. By configuring a Virtual Private Network (VPN) on your server you can give users a more secure
Secure File Transfer with SSH
 White Paper Secure File Transfer with SSH 4848 tramway ridge dr. ne suite 101 albuquerque, nm 87111 505-332 -5700 www.vandyke.com Data delivery over the Internet can be simple, convenient, and costeffective
White Paper Secure File Transfer with SSH 4848 tramway ridge dr. ne suite 101 albuquerque, nm 87111 505-332 -5700 www.vandyke.com Data delivery over the Internet can be simple, convenient, and costeffective
Case Study for Layer 3 Authentication and Encryption
 CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
CHAPTER 2 Case Study for Layer 3 Authentication and Encryption This chapter explains the basic tasks for configuring a multi-service, extranet Virtual Private Network (VPN) between a Cisco Secure VPN Client
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
File Transfer Protocol (FTP) & SSH
 http://xkcd.com/949/ File Transfer Protocol (FTP) & SSH Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Some materials copyright 1996-2012 Addison-Wesley J.F Kurose and K.W.
http://xkcd.com/949/ File Transfer Protocol (FTP) & SSH Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Some materials copyright 1996-2012 Addison-Wesley J.F Kurose and K.W.
ProxyCap Help. Table of contents. Configuring ProxyCap. 2015 Proxy Labs
 ProxyCap Help 2015 Proxy Labs Table of contents Configuring ProxyCap The Ruleset panel Loading and saving rulesets Delegating ruleset management The Proxies panel The proxy list view Adding, removing and
ProxyCap Help 2015 Proxy Labs Table of contents Configuring ProxyCap The Ruleset panel Loading and saving rulesets Delegating ruleset management The Proxies panel The proxy list view Adding, removing and
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding
 Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Chapter 6 Configuring the SSL VPN Tunnel Client and Port Forwarding This chapter describes the configuration for the SSL VPN Tunnel Client and for Port Forwarding. When a remote user accesses the SSL VPN
Lab 8.3.1.2 Configure Basic AP Security through IOS CLI
 Lab 8.3.1.2 Configure Basic AP Security through IOS CLI Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn the following
Lab 8.3.1.2 Configure Basic AP Security through IOS CLI Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn the following
File transfer clients manual File Delivery Services
 File transfer clients manual File Delivery Services Publisher Post CH Ltd Information Technology Webergutstrasse 12 CH-3030 Berne (Zollikofen) Contact Post CH Ltd Information Technology Webergutstrasse
File transfer clients manual File Delivery Services Publisher Post CH Ltd Information Technology Webergutstrasse 12 CH-3030 Berne (Zollikofen) Contact Post CH Ltd Information Technology Webergutstrasse
Using sftp in Informatica PowerCenter
 Using sftp in Informatica PowerCenter Applies to: Informatica PowerCenter Summary This article briefs about how to push/pull files using SFTP program in Informatica PowerCenter. Author Bio Author(s): Sukumar
Using sftp in Informatica PowerCenter Applies to: Informatica PowerCenter Summary This article briefs about how to push/pull files using SFTP program in Informatica PowerCenter. Author Bio Author(s): Sukumar
Network Security Essentials Chapter 5
 Network Security Essentials Chapter 5 Fourth Edition by William Stallings Lecture slides by Lawrie Brown Chapter 5 Transport-Level Security Use your mentality Wake up to reality From the song, "I've Got
Network Security Essentials Chapter 5 Fourth Edition by William Stallings Lecture slides by Lawrie Brown Chapter 5 Transport-Level Security Use your mentality Wake up to reality From the song, "I've Got
Directory and File Transfer Services. Chapter 7
 Directory and File Transfer Services Chapter 7 Learning Objectives Explain benefits offered by centralized enterprise directory services such as LDAP over traditional authentication systems Identify major
Directory and File Transfer Services Chapter 7 Learning Objectives Explain benefits offered by centralized enterprise directory services such as LDAP over traditional authentication systems Identify major
Digital certificates and SSL
 Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Digital certificates and SSL 20 out of 33 rated this helpful Applies to: Exchange Server 2013 Topic Last Modified: 2013-08-26 Secure Sockets Layer (SSL) is a method for securing communications between
Guideline for setting up a functional VPN
 Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Sync Security and Privacy Brief
 Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
RSA SecurID Token User Guide February 12, 2015
 RSA SecurID Token User Guide Page i Table of Contents Section I How to request an RSA SecurID token... 1 Section II Setting your RSA SecurID PIN... 6 Section III Setting up PuTTY on your Windows workstation
RSA SecurID Token User Guide Page i Table of Contents Section I How to request an RSA SecurID token... 1 Section II Setting your RSA SecurID PIN... 6 Section III Setting up PuTTY on your Windows workstation
Configuring SSH and Telnet
 This chapter describes how to configure Secure Shell Protocol (SSH) and Telnet on Cisco NX-OS devices. This chapter includes the following sections: Finding Feature Information, page 1 Information About
This chapter describes how to configure Secure Shell Protocol (SSH) and Telnet on Cisco NX-OS devices. This chapter includes the following sections: Finding Feature Information, page 1 Information About
SSL Tunnels. Introduction
 SSL Tunnels Introduction As you probably know, SSL protects data communications by encrypting all data exchanged between a client and a server using cryptographic algorithms. This makes it very difficult,
SSL Tunnels Introduction As you probably know, SSL protects data communications by encrypting all data exchanged between a client and a server using cryptographic algorithms. This makes it very difficult,
Exam Questions SY0-401
 Exam Questions SY0-401 CompTIA Security+ Certification http://www.2passeasy.com/dumps/sy0-401/ 1. A company has implemented PPTP as a VPN solution. Which of the following ports would need to be opened
Exam Questions SY0-401 CompTIA Security+ Certification http://www.2passeasy.com/dumps/sy0-401/ 1. A company has implemented PPTP as a VPN solution. Which of the following ports would need to be opened
ERserver. iseries. Secure Sockets Layer (SSL)
 ERserver iseries Secure Sockets Layer (SSL) ERserver iseries Secure Sockets Layer (SSL) Copyright International Business Machines Corporation 2000, 2002. All rights reserved. US Government Users Restricted
ERserver iseries Secure Sockets Layer (SSL) ERserver iseries Secure Sockets Layer (SSL) Copyright International Business Machines Corporation 2000, 2002. All rights reserved. US Government Users Restricted
7.1. Remote Access Connection
 7.1. Remote Access Connection When a client uses a dial up connection, it connects to the remote access server across the telephone system. Windows client and server operating systems use the Point to
7.1. Remote Access Connection When a client uses a dial up connection, it connects to the remote access server across the telephone system. Windows client and server operating systems use the Point to
How to Connect SSTP VPN from Windows Server 2008/Vista to Vigor2950
 How to Connect SSTP VPN from Windows Server 2008/Vista to Vigor2950 Requirements Windows Server 2008, or Windows Vista SP1 Local Certificate (a online CA server on the Internet is required for some situation
How to Connect SSTP VPN from Windows Server 2008/Vista to Vigor2950 Requirements Windows Server 2008, or Windows Vista SP1 Local Certificate (a online CA server on the Internet is required for some situation
Introduction to Mobile Access Gateway Installation
 Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
Introduction to Mobile Access Gateway Installation This document describes the installation process for the Mobile Access Gateway (MAG), which is an enterprise integration component that provides a secure
DiamondStream Data Security Policy Summary
 DiamondStream Data Security Policy Summary Overview This document describes DiamondStream s standard security policy for accessing and interacting with proprietary and third-party client data. This covers
DiamondStream Data Security Policy Summary Overview This document describes DiamondStream s standard security policy for accessing and interacting with proprietary and third-party client data. This covers
Secure Use of the New NHS Network (N3): Good Practice Guidelines
 Programme NPFIT Document Record ID Key Sub-Prog / Project Information Governance NPFIT-FNT-TO-IG-GPG-0003.01 Prog. Director Mark Ferrar Status Approved Owner Tim Davis Version 1.0 Author Phil Benn Version
Programme NPFIT Document Record ID Key Sub-Prog / Project Information Governance NPFIT-FNT-TO-IG-GPG-0003.01 Prog. Director Mark Ferrar Status Approved Owner Tim Davis Version 1.0 Author Phil Benn Version
Security. Contents. S-72.3240 Wireless Personal, Local, Metropolitan, and Wide Area Networks 1
 Contents Security requirements Public key cryptography Key agreement/transport schemes Man-in-the-middle attack vulnerability Encryption. digital signature, hash, certification Complete security solutions
Contents Security requirements Public key cryptography Key agreement/transport schemes Man-in-the-middle attack vulnerability Encryption. digital signature, hash, certification Complete security solutions
Security + Certification (ITSY 1076) Syllabus
 Security + Certification (ITSY 1076) Syllabus Course: ITSY 1076 Security+ 40 hours Course Description: This course is targeted toward an Information Technology (IT) professional who has networking and
Security + Certification (ITSY 1076) Syllabus Course: ITSY 1076 Security+ 40 hours Course Description: This course is targeted toward an Information Technology (IT) professional who has networking and
How to Configure Captive Portal
 How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
How to Configure Captive Portal Captive portal is one of the user identification methods available on the Palo Alto Networks firewall. Unknown users sending HTTP or HTTPS 1 traffic will be authenticated,
SSL VPN vs. IPSec VPN
 SSL VPN vs. IPSec VPN White Paper 254 E. Hacienda Avenue Campbell, CA 95008 www.arraynetworks.net (408) 378-6800 1 SSL VPN vs. IPSec VPN Copyright 2002 Array Networks, Inc. SSL VPN vs. IPSec VPN White
SSL VPN vs. IPSec VPN White Paper 254 E. Hacienda Avenue Campbell, CA 95008 www.arraynetworks.net (408) 378-6800 1 SSL VPN vs. IPSec VPN Copyright 2002 Array Networks, Inc. SSL VPN vs. IPSec VPN White
Security Digital Certificate Manager
 System i Security Digital Certificate Manager Version 5 Release 4 System i Security Digital Certificate Manager Version 5 Release 4 Note Before using this information and the product it supports, be sure
System i Security Digital Certificate Manager Version 5 Release 4 System i Security Digital Certificate Manager Version 5 Release 4 Note Before using this information and the product it supports, be sure
F-Secure SSH. for Windows. User s Guide
 F-Secure SSH for Windows User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks or registered
F-Secure SSH for Windows User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks or registered
Topics in Network Security
 Topics in Network Security Jem Berkes MASc. ECE, University of Waterloo B.Sc. ECE, University of Manitoba www.berkes.ca February, 2009 Ver. 2 In this presentation Wi-Fi security (802.11) Protecting insecure
Topics in Network Security Jem Berkes MASc. ECE, University of Waterloo B.Sc. ECE, University of Manitoba www.berkes.ca February, 2009 Ver. 2 In this presentation Wi-Fi security (802.11) Protecting insecure
RemotelyAnywhere Getting Started Guide
 April 2007 About RemotelyAnywhere... 2 About RemotelyAnywhere... 2 About this Guide... 2 Installation of RemotelyAnywhere... 2 Software Activation...3 Accessing RemotelyAnywhere... 4 About Dynamic IP Addresses...
April 2007 About RemotelyAnywhere... 2 About RemotelyAnywhere... 2 About this Guide... 2 Installation of RemotelyAnywhere... 2 Software Activation...3 Accessing RemotelyAnywhere... 4 About Dynamic IP Addresses...
Testing New Applications In The DMZ Using VMware ESX. Ivan Dell Era Software Engineer IBM
 Testing New Applications In The DMZ Using VMware ESX Ivan Dell Era Software Engineer IBM Agenda Problem definition Traditional solution The solution with VMware VI Remote control through the firewall Problem
Testing New Applications In The DMZ Using VMware ESX Ivan Dell Era Software Engineer IBM Agenda Problem definition Traditional solution The solution with VMware VI Remote control through the firewall Problem
TS-800. Configuring SSH Client Software in UNIX and Windows Environments for Use with the SFTP Access Method in SAS 9.2, SAS 9.3, and SAS 9.
 TS-800 Configuring SSH Client Software in UNIX and Windows Environments for Use with the SFTP Access Method in SAS 9.2, SAS 9.3, and SAS 9.4 dsas Table of Contents Overview... 1 Configuring OpenSSH Software
TS-800 Configuring SSH Client Software in UNIX and Windows Environments for Use with the SFTP Access Method in SAS 9.2, SAS 9.3, and SAS 9.4 dsas Table of Contents Overview... 1 Configuring OpenSSH Software
ASX SFTP External User Guide
 ASX SFTP External User Guide Table of Contents 1. SOLUTION OVERVIEW... 3 1.1. BUSINESS CONTINUITY SOLUTION... 3 1.2. USER MANUAL AUDIENCE... 3 2. REQUESTING SFTP ACCESS... 4 2.1. SFTP ACCOUNTS... 4 2.2.
ASX SFTP External User Guide Table of Contents 1. SOLUTION OVERVIEW... 3 1.1. BUSINESS CONTINUITY SOLUTION... 3 1.2. USER MANUAL AUDIENCE... 3 2. REQUESTING SFTP ACCESS... 4 2.1. SFTP ACCOUNTS... 4 2.2.
CS 356 Lecture 28 Internet Authentication. Spring 2013
 CS 356 Lecture 28 Internet Authentication Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
CS 356 Lecture 28 Internet Authentication Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
Network Management Card Security Implementation
 [ APPLICATION NOTE #67 ] OFFER AT A GLANCE Offers Involved Network Management Card, APC Security Wizard Applications Configuration and monitoring of network managed devices Broad Customer Problem Secure
[ APPLICATION NOTE #67 ] OFFER AT A GLANCE Offers Involved Network Management Card, APC Security Wizard Applications Configuration and monitoring of network managed devices Broad Customer Problem Secure
Authentication Types. Password-based Authentication. Off-Line Password Guessing
 Authentication Types Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4:
Authentication Types Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4:
TABLE OF CONTENTS NETWORK SECURITY 2...1
 Network Security 2 This document is the exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
Network Security 2 This document is the exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
SSH and FTP on Ubuntu 9.04. WNYLUG Neal Chapman 09/09/2009
 SSH and FTP on Ubuntu 9.04 WNYLUG Neal Chapman 09/09/2009 SSH (Secure Shell) Secure Shell or SSH is a network protocol that allows data to be exchanged using a secure channel between two networked devices.
SSH and FTP on Ubuntu 9.04 WNYLUG Neal Chapman 09/09/2009 SSH (Secure Shell) Secure Shell or SSH is a network protocol that allows data to be exchanged using a secure channel between two networked devices.
How to make a VPN connection to our servers from Windows 7
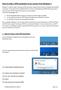 How to make a VPN connection to our servers from Windows 7 Windows 7 is able to make a new type of VPN connection called a Secure Socket Tunnelling Protocol (SSTP) connection. This works just like a traditional
How to make a VPN connection to our servers from Windows 7 Windows 7 is able to make a new type of VPN connection called a Secure Socket Tunnelling Protocol (SSTP) connection. This works just like a traditional
SECUR IN MIRTH CONNECT. Best Practices and Vulnerabilities of Mirth Connect. Author: Jeff Campbell Technical Consultant, Galen Healthcare Solutions
 SECUR Y IN MIRTH CONNECT Best Practices and Vulnerabilities of Mirth Connect Author: Jeff Campbell Technical Consultant, Galen Healthcare Solutions Date: May 15, 2015 galenhealthcare.com 2015. All rights
SECUR Y IN MIRTH CONNECT Best Practices and Vulnerabilities of Mirth Connect Author: Jeff Campbell Technical Consultant, Galen Healthcare Solutions Date: May 15, 2015 galenhealthcare.com 2015. All rights
Scenario: IPsec Remote-Access VPN Configuration
 CHAPTER 3 Scenario: IPsec Remote-Access VPN Configuration This chapter describes how to use the security appliance to accept remote-access IPsec VPN connections. A remote-access VPN enables you to create
CHAPTER 3 Scenario: IPsec Remote-Access VPN Configuration This chapter describes how to use the security appliance to accept remote-access IPsec VPN connections. A remote-access VPN enables you to create
McAfee Firewall Enterprise 8.2.1
 Configuration Guide FIPS 140 2 Revision A McAfee Firewall Enterprise 8.2.1 The McAfee Firewall Enterprise FIPS 140 2 Configuration Guide, version 8.2.1, provides instructions for setting up McAfee Firewall
Configuration Guide FIPS 140 2 Revision A McAfee Firewall Enterprise 8.2.1 The McAfee Firewall Enterprise FIPS 140 2 Configuration Guide, version 8.2.1, provides instructions for setting up McAfee Firewall
HTTPS is Fast and Hassle-free with CloudFlare
 HTTPS is Fast and Hassle-free with CloudFlare 1 888 99 FLARE [email protected] www.cloudflare.com In the past, organizations had to choose between performance and security when encrypting their
HTTPS is Fast and Hassle-free with CloudFlare 1 888 99 FLARE [email protected] www.cloudflare.com In the past, organizations had to choose between performance and security when encrypting their
Fig. 4.2.1: Packet Filtering
 4.2 Types of Firewalls /DKo98/ FIREWALL CHARACTERISTICS 1. All traffic from inside to outside, and vice versa, must pass through the firewall. This is achieved by physically blocking all access to the
4.2 Types of Firewalls /DKo98/ FIREWALL CHARACTERISTICS 1. All traffic from inside to outside, and vice versa, must pass through the firewall. This is achieved by physically blocking all access to the
Global Client Access Managed Communications Solutions. JPMorgan - Global Client Access. Managed Internet Solutions (EC Gateway)
 Managed Communications JPMorgan - Global Client Access Managed Internet (EC Gateway) Managed Communications Overview JPMorgan offers a variety of electronic communications services that are reliable and
Managed Communications JPMorgan - Global Client Access Managed Internet (EC Gateway) Managed Communications Overview JPMorgan offers a variety of electronic communications services that are reliable and
A host-based firewall can be used in addition to a network-based firewall to provide multiple layers of protection.
 A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
Cisco ASA. Administrators
 Cisco ASA for Accidental Administrators Version 1.1 Corrected Table of Contents i Contents PRELUDE CHAPTER 1: Understanding Firewall Fundamentals What Do Firewalls Do? 5 Types of Firewalls 6 Classification
Cisco ASA for Accidental Administrators Version 1.1 Corrected Table of Contents i Contents PRELUDE CHAPTER 1: Understanding Firewall Fundamentals What Do Firewalls Do? 5 Types of Firewalls 6 Classification
Certificate Management. PAN-OS Administrator s Guide. Version 7.0
 Certificate Management PAN-OS Administrator s Guide Version 7.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Certificate Management PAN-OS Administrator s Guide Version 7.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
information security and its Describe what drives the need for information security.
 Computer Information Systems (Forensics Classes) Objectives for Course Challenges CIS 200 Intro to Info Security: Includes managerial and Describe information security and its critical role in business.
Computer Information Systems (Forensics Classes) Objectives for Course Challenges CIS 200 Intro to Info Security: Includes managerial and Describe information security and its critical role in business.
How to make a VPN connection to our servers from Windows 8
 How to make a VPN connection to our servers from Windows 8 Windows 8 is able to make a newer type of VPN connection called a Secure Socket Tunnelling Protocol (SSTP) connection. This works just like a
How to make a VPN connection to our servers from Windows 8 Windows 8 is able to make a newer type of VPN connection called a Secure Socket Tunnelling Protocol (SSTP) connection. This works just like a
Credit Card Security
 Credit Card Security Created 16 Apr 2014 Revised 16 Apr 2014 Reviewed 16 Apr 2014 Purpose This policy is intended to ensure customer personal information, particularly credit card information and primary
Credit Card Security Created 16 Apr 2014 Revised 16 Apr 2014 Reviewed 16 Apr 2014 Purpose This policy is intended to ensure customer personal information, particularly credit card information and primary
Security Configuration Guide P/N 300-010-493 Rev A05
 EMC VPLEX Security Configuration Guide P/N 300-010-493 Rev A05 June 7, 2011 This guide provides an overview of VPLEX security configuration settings, including secure deployment and usage settings needed
EMC VPLEX Security Configuration Guide P/N 300-010-493 Rev A05 June 7, 2011 This guide provides an overview of VPLEX security configuration settings, including secure deployment and usage settings needed
REPORT ON AUDIT OF LOCAL AREA NETWORK OF C-STAR LAB
 REPORT ON AUDIT OF LOCAL AREA NETWORK OF C-STAR LAB Conducted: 29 th March 5 th April 2007 Prepared By: Pankaj Kohli (200607011) Chandan Kumar (200607003) Aamil Farooq (200505001) Network Audit Table of
REPORT ON AUDIT OF LOCAL AREA NETWORK OF C-STAR LAB Conducted: 29 th March 5 th April 2007 Prepared By: Pankaj Kohli (200607011) Chandan Kumar (200607003) Aamil Farooq (200505001) Network Audit Table of
Transport Level Security
 Transport Level Security Overview Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
Transport Level Security Overview Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
AnzioWin FTP Dialog. AnzioWin version 15.0 and later
 AnzioWin FTP Dialog AnzioWin version 15.0 and later With AnzioWin version 15.0, we have included an enhanced interactive FTP dialog that operates similar to Windows Explorer. The FTP dialog, shown below,
AnzioWin FTP Dialog AnzioWin version 15.0 and later With AnzioWin version 15.0, we have included an enhanced interactive FTP dialog that operates similar to Windows Explorer. The FTP dialog, shown below,
SSL Guide. (Secure Socket Layer)
 SSL Guide (Secure Socket Layer) To find basic information about network and advanced network features of your Brother machine: uu Network User's Guide. To download the latest manual, please visit the Brother
SSL Guide (Secure Socket Layer) To find basic information about network and advanced network features of your Brother machine: uu Network User's Guide. To download the latest manual, please visit the Brother
2.4: Authentication Authentication types Authentication schemes: RSA, Lamport s Hash Mutual Authentication Session Keys Trusted Intermediaries
 Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application
Chapter 2: Security Techniques Background Secret Key Cryptography Public Key Cryptography Hash Functions Authentication Chapter 3: Security on Network and Transport Layer Chapter 4: Security on the Application
Introduction to Securing Data in Transit
 Introduction to Securing Data in Transit Jennifer Vesperman [email protected] 2002 02 24 Revision History Revision 0.1 2002 02 17 Revised by: MEG Converted from text file. Modified wording. Revision 0.2
Introduction to Securing Data in Transit Jennifer Vesperman [email protected] 2002 02 24 Revision History Revision 0.1 2002 02 17 Revised by: MEG Converted from text file. Modified wording. Revision 0.2
Brazosport College VPN Connection Installation and Setup Instructions. Draft 2 March 24, 2005
 Brazosport College VPN Connection Installation and Setup Instructions Draft 2 March 24, 2005 Introduction This is an initial draft of these instructions. These instructions have been tested by the IT department
Brazosport College VPN Connection Installation and Setup Instructions Draft 2 March 24, 2005 Introduction This is an initial draft of these instructions. These instructions have been tested by the IT department
What IT Auditors Need to Know About Secure Shell. SSH Communications Security
 What IT Auditors Need to Know About Secure Shell SSH Communications Security Agenda Secure Shell Basics Security Risks Compliance Requirements Methods, Tools, Resources What is Secure Shell? A cryptographic
What IT Auditors Need to Know About Secure Shell SSH Communications Security Agenda Secure Shell Basics Security Risks Compliance Requirements Methods, Tools, Resources What is Secure Shell? A cryptographic
How do I load balance FTP on NetScaler?
 How do I load balance FTP on NetScaler? Introduction: File transfer protocol is a standard for the exchange of files across a network. It is based on a client/server model with an FTP client on a user
How do I load balance FTP on NetScaler? Introduction: File transfer protocol is a standard for the exchange of files across a network. It is based on a client/server model with an FTP client on a user
File Protection using rsync. Setup guide
 File Protection using rsync Setup guide Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 Overview... 2 2. Rsync technology... 3 Terminology... 3 Implementation... 3 3. Rsync data hosts...
File Protection using rsync Setup guide Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 Overview... 2 2. Rsync technology... 3 Terminology... 3 Implementation... 3 3. Rsync data hosts...
Setting Up Scan to SMB on TaskALFA series MFP s.
 Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
Xerox DocuShare Security Features. Security White Paper
 Xerox DocuShare Security Features Security White Paper Xerox DocuShare Security Features Businesses are increasingly concerned with protecting the security of their networks. Any application added to a
Xerox DocuShare Security Features Security White Paper Xerox DocuShare Security Features Businesses are increasingly concerned with protecting the security of their networks. Any application added to a
Measurement of the Usage of Several Secure Internet Protocols from Internet Traces
 Measurement of the Usage of Several Secure Internet Protocols from Internet Traces Yunfeng Fei, John Jones, Kyriakos Lakkas, Yuhong Zheng Abstract: In recent years many common applications have been modified
Measurement of the Usage of Several Secure Internet Protocols from Internet Traces Yunfeng Fei, John Jones, Kyriakos Lakkas, Yuhong Zheng Abstract: In recent years many common applications have been modified
File Manager User Guide
 File Manager User Guide Please note: EasySiteOptimizer Version 1.6 is supplied with Web Hosting (IBP) and Advanced Web Hosting only. File Manager Introduction to File Manager To access File Manager, select
File Manager User Guide Please note: EasySiteOptimizer Version 1.6 is supplied with Web Hosting (IBP) and Advanced Web Hosting only. File Manager Introduction to File Manager To access File Manager, select
Remote Access VPN Solutions
 Remote Access VPN Solutions P/N 500187 June 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 3 Remote Access VPN Defined Page 3 Business Case Page 4 Key Requirements Page
Remote Access VPN Solutions P/N 500187 June 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 3 Remote Access VPN Defined Page 3 Business Case Page 4 Key Requirements Page
Overview of CSS SSL. SSL Cryptography Overview CHAPTER
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet, ensuring secure transactions such as the transmission of credit card numbers
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet, ensuring secure transactions such as the transmission of credit card numbers
Virtual Private Networks
 Virtual Private Networks ECE 4886 Internetwork Security Dr. Henry Owen Definition Virtual Private Network VPN! Virtual separation in protocol provides a virtual network using no new hardware! Private communication
Virtual Private Networks ECE 4886 Internetwork Security Dr. Henry Owen Definition Virtual Private Network VPN! Virtual separation in protocol provides a virtual network using no new hardware! Private communication
Certificate Management
 Certificate Management This guide provides information on...... Configuring the GO!Enterprise MDM server to use a Microsoft Active Directory Certificate Authority... Using Certificates from Outside Sources...
Certificate Management This guide provides information on...... Configuring the GO!Enterprise MDM server to use a Microsoft Active Directory Certificate Authority... Using Certificates from Outside Sources...
SSH, SCP, SFTP, Denyhosts. Süha TUNA Res. Assist.
 SSH, SCP, SFTP, Denyhosts Süha TUNA Res. Assist. Outline 1. What is Secure Shell? 2. ssh (Install and Configuration) 3. scp 4. sftp 5. X11 Forwarding 6. Generating Key Pairs 7. Disabling root Access 8.
SSH, SCP, SFTP, Denyhosts Süha TUNA Res. Assist. Outline 1. What is Secure Shell? 2. ssh (Install and Configuration) 3. scp 4. sftp 5. X11 Forwarding 6. Generating Key Pairs 7. Disabling root Access 8.
1 hours, 30 minutes, 38 seconds Heavy scan. All scanned network resources. Copyright 2001, FTP access obtained
 home Network Vulnerabilities Detail Report Grouped by Vulnerability Report Generated by: Symantec NetRecon 3.5 Licensed to: X Serial Number: 0182037567 Machine Scanned from: ZEUS (192.168.1.100) Scan Date:
home Network Vulnerabilities Detail Report Grouped by Vulnerability Report Generated by: Symantec NetRecon 3.5 Licensed to: X Serial Number: 0182037567 Machine Scanned from: ZEUS (192.168.1.100) Scan Date:
athenahealth Interface Connectivity SSH Implementation Guide
 athenahealth Interface Connectivity SSH Implementation Guide 1. OVERVIEW... 2 2. INTERFACE LOGICAL SCHEMATIC... 3 3. INTERFACE PHYSICAL SCHEMATIC... 4 4. SECURE SHELL... 5 5. NETWORK CONFIGURATION... 6
athenahealth Interface Connectivity SSH Implementation Guide 1. OVERVIEW... 2 2. INTERFACE LOGICAL SCHEMATIC... 3 3. INTERFACE PHYSICAL SCHEMATIC... 4 4. SECURE SHELL... 5 5. NETWORK CONFIGURATION... 6
Upgrading Redwood Engine Software. Version 2.0.x to 3.1.0
 Upgrading Redwood Engine Software Version 2.0.x to 3.1.0 December 2013 APP NOTE Table of Contents 1 Introduction... 3 1.1 Backing Up the Redwood Engine Configuration, Statistics, and Log Files... 3 2 Checking
Upgrading Redwood Engine Software Version 2.0.x to 3.1.0 December 2013 APP NOTE Table of Contents 1 Introduction... 3 1.1 Backing Up the Redwood Engine Configuration, Statistics, and Log Files... 3 2 Checking
Ciphire Mail. Abstract
 Ciphire Mail Technical Introduction Abstract Ciphire Mail is cryptographic software providing email encryption and digital signatures. The Ciphire Mail client resides on the user's computer between the
Ciphire Mail Technical Introduction Abstract Ciphire Mail is cryptographic software providing email encryption and digital signatures. The Ciphire Mail client resides on the user's computer between the
SSH and Basic Commands
 SSH and Basic Commands In this tutorial we'll introduce you to SSH - a tool that allows you to send remote commands to your Web server - and show you some simple UNIX commands to help you manage your website.
SSH and Basic Commands In this tutorial we'll introduce you to SSH - a tool that allows you to send remote commands to your Web server - and show you some simple UNIX commands to help you manage your website.
SBClient SSL. Ehab AbuShmais
 SBClient SSL Ehab AbuShmais Agenda SSL Background U2 SSL Support SBClient SSL 2 What Is SSL SSL (Secure Sockets Layer) Provides a secured channel between two communication endpoints Addresses all three
SBClient SSL Ehab AbuShmais Agenda SSL Background U2 SSL Support SBClient SSL 2 What Is SSL SSL (Secure Sockets Layer) Provides a secured channel between two communication endpoints Addresses all three
Secure Transport Service (STS) Certificate Update Information
 Secure Transport Service (STS) Certificate Update Information What is changing? The Experian Secure Transport Service (STS), Experian s file transfer application, is having the server certificate replaced
Secure Transport Service (STS) Certificate Update Information What is changing? The Experian Secure Transport Service (STS), Experian s file transfer application, is having the server certificate replaced
Compliance and Security Challenges with Remote Administration
 Sponsored by Netop Compliance and Security Challenges with Remote Administration A SANS Whitepaper January 2011 Written by Dave Shackleford Compliance Control Points Encryption Access Roles and Privileges
Sponsored by Netop Compliance and Security Challenges with Remote Administration A SANS Whitepaper January 2011 Written by Dave Shackleford Compliance Control Points Encryption Access Roles and Privileges
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 8 Authentication
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 8 Authentication Objectives Define authentication Describe the different types of authentication credentials List and explain the
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 8 Authentication Objectives Define authentication Describe the different types of authentication credentials List and explain the
