Popular Android Exploits
|
|
|
- Peter McKinney
- 9 years ago
- Views:
Transcription
1 20-CS-6053 Network Security Spring, 2016 An Introduction To Popular Android Exploits and what makes them possible April, 2016
2 Questions Can a benign service call a dangerous service without the user knowing? Can Google Play determine whether code has security holes and prevent it from being added to the market? Can code that has security holes be exploited by a third party? Does proguard prevent repackaging attacks?
3 Obfuscation Proguard: Proguard makes it a bit harder to Reverse Engineer, but it will still be possible (and the APKtool gives you the possibility to debug). Moreover, you cannot use all of proguard optimization because you will not be able to convert classes to dex. In fact, you can only use shrink and agressive overloading. Bottom line: proguard lets you shrink you code about 30% but it will not make your application hackproof
4 What follows is from: Reference Execute This! Analyzing Unsafe and Malicious Dynamic Code Loading in Android Applications Sebastian Poeplau, Yanick Fratantonio, Antonio Bianchi, Christopher Kruegel, and Giovanni Vigna Network and Distributed Sysytem Symposium February, 2014
5 Google Bouncer Bouncer quietly and automatically scans apps (both new and previously uploaded ones) and developer accounts in Google Play with its reputation engine and cloud infrastructure. But 1. Bouncer can be fingerprinted - an app can know that it is being scanned by the Bouncer 2. External code can be added to a running app that was downloaded from the Play store 3. Android does not enforce security checks on such code 4. Numerous benign apps add external code routinely 5. Developers of many benign apps are unaware of or do not properly implement protection mechanisms
6 Android OS Environment Additional considerations 1. External code can come from anywhere, including other app stores such as Amazon s App Store 2. Android OS treats the store that the device manufacturer prefers differently from others: To install APKs from other stores users enable the sideloading setting, otherwise the OS rejects apps that do not originate from the preferred store. 3. Users may be forced to accept external code (assumed benign - and most are) otherwise their app won t have some desired feature or may not update 4. Android OS does not check the integrity of class files & applications are run without checking signatures
7 Common Exploits Malware escapes offline analysis Once an application has been approved by Google Bouncer, admitted to the store and installed by users, it can download and execute additional code that could be malware Malware is injected into benign apps Attacker can replace the original code with malicious code because Android OS does not enforce security checks Attacker runs the malicious code with the original permissions of the app!
8 Class Loaders Instruments Allow programs to load additional classes Used by Android programs to load classes from arbitrary files Android class loader accepts apk, dex, jar formats No restrictions on location or source of a class App may download an apk file from the internet and use DexClassLoader to load the contained classes then the methods of those classes can be invoked to run malware
9 DexClassLoader Instruments A class loader that loads classes from.jar and.apk files containing a classes.dex entry. This can be used to execute code not installed as part of an application. This class loader requires an application-private, writable directory to cache optimized classes. Use: File dexoutputdir = context.getdir("dex", 0); to create such a directory From class Context: Use 0 or MODE PRIVATE as default, mode: MODE WORLD READABLE and MODE WORLD WRITEABLE control permissions (dangerous and deprecated)
10 Package Contexts Instruments A Context object is associated with an app on load The object provides access to the app s resource Android OS provides createpackagecontext to create contexts for other installed apps - just need to know their package name This allows an app to access resources of another app, & create a class loader for loading classes of that app If flags CONTEXT INCLUDE CODE and CONTEXT IGNORE SECURITY are set when calling createpackagecontext the OS does not verify that the app originates from the same developer or that the app to be loaded satisfies any criteria So, an app can load and execute code from any app
11 Package Contexts Instruments Many applications use CONTEXT IGNORE SECURITY If an attacker manages to install a package with the same name as an app that is careless about checking integrity and authenticating then the attacker s code can be executed with the app s permissions
12 Context Instruments Interface to global information about an application environment. Allows access to application-specific resources and classes, as well as up-calls for application-level operations such as launching activities, broadcasting and receiving intents, etc. Constants: CONTEXT IGNORE SECURITY: ignore any security restrictions on the Context being requested, allowing it to always be loaded. CONTEXT INCLUDE CODE: include the application code with the context. createpackagecontext(string name, int flags): The returned Context is the same as what the named application gets when it is launched, containing the same resources and class loader
13 Native Code Instruments Apps are allowed to run native code via JNI Android OS makes some checks on resource access for example, creating a network socket, an op done by root, is not allowed directly for the native code but is allowed with permission But an attacker can run native code in several different ways, without the burden of conforming to a well-defined API Native code can be downloaded and executed at runtime Only need app to have internet permission All current root exploits are native code - added after app installation
14 Runtime.exec Instruments Allows apps to execute arbitrary binaries Gives an app access to a bash shell No check is made on the binary to be executed An attacker can use system calls to execute arbitrary binaries
15 APK installation Instruments The Package Manager can be used by an owner to install and uninstall apps The PM prompts to have owner accept permissions The PM requires a signed certificate to install But it does not check anything about the certificate It is only used to determine whether two apps have the same source If an attacker can replace the apk that a benign app tries to install, the app does not detect the switch unless it implements a custom verification mechanism
16 Sideloading An owner has to enable sideloading in the system settings to install apps from any source other than the preferred store of the device manufacturer But any user who wants to use an alternative application store has to do the same To assist users in the process of setting up their devices, providers of such application stores usually offer detailed instructions on how to find the sideloading settings, often without warning about potential security implications. Thus, it is reasonable to assume that sideloading is enabled on a considerable fraction of Android devices Facebook has used direct updates instead of going through Google Play in the past
17 Why is Loading External Code Allowed? There are legitmate reasons for loading external code Until recently, developers did beta testing on a subset of users via external apk loading. Apps can be extended by installing additional modules. But such apps are on their own in checking whether the add-ons are legitimate Framework developers use external apk loading to auto-update their frameworks to all users Unfortunately, implementations of such auto-updaters can be flawed and vulnerable to injection attacks
18 Exploiting External Code Loading Evasion of the Bouncer Benign code that does the following: 1. uses permission to visit the internet 2. uses permission to write files to external storage 3. Activity contains a single button - when pressed, code is downloaded from a site and the user sees a browser (to hide the download) 4. The downloaded code is executed Bouncer did not detect the potential to download and execute malicious code Bouncer did not even request the download Same results for available anti-virus apps
19 Exploiting External Code Loading Code substitution Android OS directs responsibility for checking the integrity and authenticity of external code to the app or framework developers Some apps download external code via http and are subject to man-in-the-middle attacks Some apps download external code to storage that is write-accessible to other apps
20 Exploiting External Code Loading Improper package name usage The same package name can be used by several different applications as long as they are not installed on the same device An attacker can write malicious code in a package with a well-known name If the package is downloaded and installed, all apps using the package will be affected.
21 Exploiting External Code Loading Self-update of an advertising framework A game that includes an advertising framework that can update itself via http Framework checks for updates upon game start Update is downloaded and started via DexClassLoader Connection was taken over and malicious file plus an MD5 hash was served The MD5 hash was checked for file integrity but no authentication was done The app expects a particular class name and a method to execute. These can be determined from decoding via apktool
22 Exploiting External Code Loading Bootstrapping mechanism of a shared framework Framework allows developers to create apps for several platforms Device-specific framework runtime runs the code Android version is an app that can be started by any app that is based on it Code loading the framework runtime into an app is generated automatically for the developer Uses createpackagecontext with hard-coded package name Loading code does not verify the integrity of the loaded app so any package with the right name is accepted
23 Exploiting External Code Loading Bootstrapping mechanism of a shared framework If attacker can install bogus code with the same package name and required class, when an app based on the framework is launched, the bogus code will run
24 Intent Spoofing Intent: main method of interprocess communication used to start activities and services and notify broadcast receivers Component can be configured to accept intents from components of other apps with android:exported="true" in the manifest Registering an implicit intent makes it exported automatically Example: am start \ -a android.intent.action.sendto \ -d mailto:[email protected] \ --es com.paypal.android.p2pmobile.amount 9.99 \ --ei com.paypal.android.p2pmobile.paramtype 42 \ -n com.paypal.android.p2pmobile/.activity.sendmoneyactivity see
25 Intent Interception A malicious app receives an intent that was not intended for it. Can cause a leak of sensitive information Can result in the malicious component being activated instead of the legitimate component. However, a broadcast may be secured with a permission - then a component will not receive that intent unless it has that permission Example: id=uk.co.ashtonbrsc.android.intentintercept
26 Android Malware Examples Millions of phones have bitcoin mining malware Adware problems Virus Shield: fake app Android.bankun: banking malware Android.koler: drive-by-download: Premium SMS messages Dendroid: remote access trojan
Execute This! Analyzing Unsafe and Malicious Dynamic Code Loading in Android Applications
 Execute This! Analyzing Unsafe and Malicious Dynamic Code Loading in Android Applications Sebastian Poeplau, Yanick Fratantonio, Antonio Bianchi, Christopher Kruegel, Giovanni Vigna UC Santa Barbara Santa
Execute This! Analyzing Unsafe and Malicious Dynamic Code Loading in Android Applications Sebastian Poeplau, Yanick Fratantonio, Antonio Bianchi, Christopher Kruegel, Giovanni Vigna UC Santa Barbara Santa
Defending Behind The Device Mobile Application Risks
 Defending Behind The Device Mobile Application Risks Tyler Shields Product Manager and Strategist Veracode, Inc Session ID: MBS-301 Session Classification: Advanced Agenda The What The Problem Mobile Ecosystem
Defending Behind The Device Mobile Application Risks Tyler Shields Product Manager and Strategist Veracode, Inc Session ID: MBS-301 Session Classification: Advanced Agenda The What The Problem Mobile Ecosystem
Hacking your Droid ADITYA GUPTA
 Hacking your Droid ADITYA GUPTA adityagupta1991 [at] gmail [dot] com facebook[dot]com/aditya1391 Twitter : @adi1391 INTRODUCTION After the recent developments in the smart phones, they are no longer used
Hacking your Droid ADITYA GUPTA adityagupta1991 [at] gmail [dot] com facebook[dot]com/aditya1391 Twitter : @adi1391 INTRODUCTION After the recent developments in the smart phones, they are no longer used
APPLICATION SECURITY: FROM WEB TO MOBILE. DIFFERENT VECTORS AND NEW ATTACK
 APPLICATION SECURITY: FROM WEB TO MOBILE. DIFFERENT VECTORS AND NEW ATTACK John T Lounsbury Vice President Professional Services, Asia Pacific INTEGRALIS Session ID: MBS-W01 Session Classification: Advanced
APPLICATION SECURITY: FROM WEB TO MOBILE. DIFFERENT VECTORS AND NEW ATTACK John T Lounsbury Vice President Professional Services, Asia Pacific INTEGRALIS Session ID: MBS-W01 Session Classification: Advanced
Malware detection methods for fixed and mobile networks
 Malware detection methods for fixed and mobile networks Gavin McWilliams January 2013 [email protected] Academic Centre of Excellence in Cyber Security Research Presentation Outline Malware detection
Malware detection methods for fixed and mobile networks Gavin McWilliams January 2013 [email protected] Academic Centre of Excellence in Cyber Security Research Presentation Outline Malware detection
HP AppPulse Mobile. Adding HP AppPulse Mobile to Your Android App
 HP AppPulse Mobile Adding HP AppPulse Mobile to Your Android App Document Release Date: April 2015 How to Add HP AppPulse Mobile to Your Android App How to Add HP AppPulse Mobile to Your Android App For
HP AppPulse Mobile Adding HP AppPulse Mobile to Your Android App Document Release Date: April 2015 How to Add HP AppPulse Mobile to Your Android App How to Add HP AppPulse Mobile to Your Android App For
Android Security Joshua Hodosh and Tim Leek
 Android Security Joshua Hodosh and Tim Leek This work is sponsored under Air Force contract FA8721-05-C-0002. Opinions, interpretations, conclusions, and recommendations are those of the authors and are
Android Security Joshua Hodosh and Tim Leek This work is sponsored under Air Force contract FA8721-05-C-0002. Opinions, interpretations, conclusions, and recommendations are those of the authors and are
Pentesting Android Apps. Sneha Rajguru (@Sneharajguru)
 Pentesting Android Apps Sneha Rajguru (@Sneharajguru) About Me Penetration Tester Web, Mobile and Infrastructure applications, Secure coding ( part time do secure code analysis), CTF challenge writer (at
Pentesting Android Apps Sneha Rajguru (@Sneharajguru) About Me Penetration Tester Web, Mobile and Infrastructure applications, Secure coding ( part time do secure code analysis), CTF challenge writer (at
Enterprise Apps: Bypassing the Gatekeeper
 Enterprise Apps: Bypassing the Gatekeeper By Avi Bashan and Ohad Bobrov Executive Summary The Apple App Store is a major part of the ios security paradigm, offering a central distribution process that
Enterprise Apps: Bypassing the Gatekeeper By Avi Bashan and Ohad Bobrov Executive Summary The Apple App Store is a major part of the ios security paradigm, offering a central distribution process that
Introduction to Android
 Introduction to Android 26 October 2015 Lecture 1 26 October 2015 SE 435: Development in the Android Environment 1 Topics for Today What is Android? Terminology and Technical Terms Ownership, Distribution,
Introduction to Android 26 October 2015 Lecture 1 26 October 2015 SE 435: Development in the Android Environment 1 Topics for Today What is Android? Terminology and Technical Terms Ownership, Distribution,
Analysis of advanced issues in mobile security in android operating system
 Available online atwww.scholarsresearchlibrary.com Archives of Applied Science Research, 2015, 7 (2):34-38 (http://scholarsresearchlibrary.com/archive.html) ISSN 0975-508X CODEN (USA) AASRC9 Analysis of
Available online atwww.scholarsresearchlibrary.com Archives of Applied Science Research, 2015, 7 (2):34-38 (http://scholarsresearchlibrary.com/archive.html) ISSN 0975-508X CODEN (USA) AASRC9 Analysis of
Tushar Dalvi Sr. Security Engineer at LinkedIn Penetration Tester. Responsible for securing a large suite mobile apps
 Tony Trummer Staff Engineer, Information Security at LinkedIn Penetration tester and mobile security enthusiast #3 in Android Security Acknowledgements Tushar Dalvi Sr. Security Engineer at LinkedIn Penetration
Tony Trummer Staff Engineer, Information Security at LinkedIn Penetration tester and mobile security enthusiast #3 in Android Security Acknowledgements Tushar Dalvi Sr. Security Engineer at LinkedIn Penetration
Security in Android apps
 Security in Android apps Falco Peijnenburg (3749002) August 16, 2013 Abstract Apps can be released on the Google Play store through the Google Developer Console. The Google Play store only allows apps
Security in Android apps Falco Peijnenburg (3749002) August 16, 2013 Abstract Apps can be released on the Google Play store through the Google Developer Console. The Google Play store only allows apps
Kaspersky Fraud Prevention: a Comprehensive Protection Solution for Online and Mobile Banking
 Kaspersky Fraud Prevention: a Comprehensive Protection Solution for Online and Mobile Banking Today s bank customers can perform most of their financial activities online. According to a global survey
Kaspersky Fraud Prevention: a Comprehensive Protection Solution for Online and Mobile Banking Today s bank customers can perform most of their financial activities online. According to a global survey
Security Guide. BlackBerry Enterprise Service 12. for ios, Android, and Windows Phone. Version 12.0
 Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Android Security Evaluation Framework
 INTRODUCING... A S E F Android Security Evaluation Framework - Parth Patel $ whoami_ Agenda Manual Research Automation - A S E F Let s solve problems Conclusion Android OS Open Source Security Evaluation
INTRODUCING... A S E F Android Security Evaluation Framework - Parth Patel $ whoami_ Agenda Manual Research Automation - A S E F Let s solve problems Conclusion Android OS Open Source Security Evaluation
CompTIA Mobile App Security+ Certification Exam (Android Edition) Live exam ADR-001 Beta Exam AD1-001
 CompTIA Mobile App Security+ Certification Exam (Android Edition) Live exam ADR-001 Beta Exam AD1-001 INTRODUCTION This exam will certify that the successful candidate has the knowledge and skills required
CompTIA Mobile App Security+ Certification Exam (Android Edition) Live exam ADR-001 Beta Exam AD1-001 INTRODUCTION This exam will certify that the successful candidate has the knowledge and skills required
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
TOTAL DEFENSE MOBILE SECURITY USER S GUIDE
 TOTAL DEFENSE MOBILE SECURITY USER S GUIDE Publication date 2015.04.09 Copyright 2015 Total Defense Mobile Security LEGAL NOTICE All rights reserved. No part of this book may be reproduced or transmitted
TOTAL DEFENSE MOBILE SECURITY USER S GUIDE Publication date 2015.04.09 Copyright 2015 Total Defense Mobile Security LEGAL NOTICE All rights reserved. No part of this book may be reproduced or transmitted
Mercury User Guide v1.1
 Mercury User Guide v1.1 Tyrone Erasmus 2012-09-03 Index Index 1. Introduction... 3 2. Getting started... 4 2.1. Recommended requirements... 4 2.2. Download locations... 4 2.3. Setting it up... 4 2.3.1.
Mercury User Guide v1.1 Tyrone Erasmus 2012-09-03 Index Index 1. Introduction... 3 2. Getting started... 4 2.1. Recommended requirements... 4 2.2. Download locations... 4 2.3. Setting it up... 4 2.3.1.
Mobile App Reputation
 Mobile App Reputation A Webroot Security Intelligence Service Timur Kovalev and Darren Niller April 2013 2012 Webroot Inc. All rights reserved. Contents Rise of the Malicious App Machine... 3 Webroot App
Mobile App Reputation A Webroot Security Intelligence Service Timur Kovalev and Darren Niller April 2013 2012 Webroot Inc. All rights reserved. Contents Rise of the Malicious App Machine... 3 Webroot App
Smartphone Pentest Framework v0.1. User Guide
 Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
Smartphone Pentest Framework v0.1 User Guide 1 Introduction: The Smartphone Pentest Framework (SPF) is an open source tool designed to allow users to assess the security posture of the smartphones deployed
Beginners Guide to Android Reverse Engineering
 (W)ORK-SH/OP: Beginners Guide to Android Reverse Engineering (W)ORK-SH/OP: [email protected] Hall[14], Day 3 11:00h Agenda Purpose Recommended or needed tools (De)construction of Android apps Obtaining APKs Decompiling
(W)ORK-SH/OP: Beginners Guide to Android Reverse Engineering (W)ORK-SH/OP: [email protected] Hall[14], Day 3 11:00h Agenda Purpose Recommended or needed tools (De)construction of Android apps Obtaining APKs Decompiling
Advanced Endpoint Protection Overview
 Advanced Endpoint Protection Overview Advanced Endpoint Protection is a solution that prevents Advanced Persistent Threats (APTs) and Zero-Day attacks and enables protection of your endpoints by blocking
Advanced Endpoint Protection Overview Advanced Endpoint Protection is a solution that prevents Advanced Persistent Threats (APTs) and Zero-Day attacks and enables protection of your endpoints by blocking
ANDROID SECURITY ATTACKS AND DEFENSES ABHISHEK DUBEY I ANMOL MISRA. ( r öc) CRC Press VV J Taylor & Francis Group ^ "^ Boca Raton London New York
 ANDROID SECURITY ATTACKS AND DEFENSES ABHISHEK DUBEY I ANMOL MISRA ( r öc) CRC Press VV J Taylor & Francis Group ^ "^ Boca Raton London New York CRC Press is an imprint of the Taylor & Francis Croup, an
ANDROID SECURITY ATTACKS AND DEFENSES ABHISHEK DUBEY I ANMOL MISRA ( r öc) CRC Press VV J Taylor & Francis Group ^ "^ Boca Raton London New York CRC Press is an imprint of the Taylor & Francis Croup, an
Patterns for Secure Boot and Secure Storage in Computer Systems
 Patterns for Secure Boot and Secure Storage in Computer Systems Hans Löhr, Ahmad-Reza Sadeghi, Marcel Winandy Horst Görtz Institute for IT Security, Ruhr-University Bochum, Germany {hans.loehr,ahmad.sadeghi,marcel.winandy}@trust.rub.de
Patterns for Secure Boot and Secure Storage in Computer Systems Hans Löhr, Ahmad-Reza Sadeghi, Marcel Winandy Horst Görtz Institute for IT Security, Ruhr-University Bochum, Germany {hans.loehr,ahmad.sadeghi,marcel.winandy}@trust.rub.de
Click Start > Control Panel > System icon to open System Properties dialog box. Click Advanced > Environment Variables.
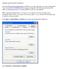 Configure Java environment on Windows After installing Java Development Kit on Windows, you may still need to do some configuration to get Java ready for compiling and executing Java programs. The following
Configure Java environment on Windows After installing Java Development Kit on Windows, you may still need to do some configuration to get Java ready for compiling and executing Java programs. The following
Messing with the Android Runtime
 Northeastern University Systems Security Lab Messing with the Android Runtime Collin Mulliner, April 26th 2013, Singapore crm[at]ccs.neu.edu SyScan Singapore 2013 $ finger [email protected] 'postdoc'
Northeastern University Systems Security Lab Messing with the Android Runtime Collin Mulliner, April 26th 2013, Singapore crm[at]ccs.neu.edu SyScan Singapore 2013 $ finger [email protected] 'postdoc'
Android Security. Giovanni Russello [email protected]
 Android Security Giovanni Russello [email protected] N-Degree of Separation Applications can be thought as composed by Main Functionality Several Non-functional Concerns Security is a non-functional
Android Security Giovanni Russello [email protected] N-Degree of Separation Applications can be thought as composed by Main Functionality Several Non-functional Concerns Security is a non-functional
Administering Jive for Outlook
 Administering Jive for Outlook TOC 2 Contents Administering Jive for Outlook...3 System Requirements...3 Installing the Plugin... 3 Installing the Plugin... 3 Client Installation... 4 Resetting the Binaries...4
Administering Jive for Outlook TOC 2 Contents Administering Jive for Outlook...3 System Requirements...3 Installing the Plugin... 3 Installing the Plugin... 3 Client Installation... 4 Resetting the Binaries...4
Tutorial on Smartphone Security
 Tutorial on Smartphone Security Wenliang (Kevin) Du Professor [email protected] Smartphone Usage Smartphone Applications Overview» Built-in Protections (ios and Android)» Jailbreaking and Rooting» Security
Tutorial on Smartphone Security Wenliang (Kevin) Du Professor [email protected] Smartphone Usage Smartphone Applications Overview» Built-in Protections (ios and Android)» Jailbreaking and Rooting» Security
Configuring WildFire. Version 1.0 PAN-OS 5.0.1. Johan Loos. [email protected]
 Configuring WildFire Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] WildFire Overview WildFire is a cloud based malware detection service. Basically is the idea when the user downloads a file,
Configuring WildFire Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] WildFire Overview WildFire is a cloud based malware detection service. Basically is the idea when the user downloads a file,
Novell Filr 1.0.x Mobile App Quick Start
 Novell Filr 1.0.x Mobile App Quick Start February 2014 Novell Quick Start Novell Filr allows you to easily access all your files and folders from your desktop, browser, or a mobile device. In addition,
Novell Filr 1.0.x Mobile App Quick Start February 2014 Novell Quick Start Novell Filr allows you to easily access all your files and folders from your desktop, browser, or a mobile device. In addition,
Security Evaluation CLX.Sentinel
 Security Evaluation CLX.Sentinel October 15th, 2009 Walter Sprenger [email protected] Compass Security AG Glärnischstrasse 7 Postfach 1628 CH-8640 Rapperswil Tel.+41 55-214 41 60 Fax+41 55-214 41
Security Evaluation CLX.Sentinel October 15th, 2009 Walter Sprenger [email protected] Compass Security AG Glärnischstrasse 7 Postfach 1628 CH-8640 Rapperswil Tel.+41 55-214 41 60 Fax+41 55-214 41
App Operating Instructions Manual ES File Explorer
 App Operating Instructions Manual ES File Explorer 2013/5 ES File Explorer (for Android only) In addition to managing local / shared / FTP / and Bluetooth file folders, you can also directly manage a variety
App Operating Instructions Manual ES File Explorer 2013/5 ES File Explorer (for Android only) In addition to managing local / shared / FTP / and Bluetooth file folders, you can also directly manage a variety
Full System Emulation:
 Full System Emulation: Achieving Successful Automated Dynamic Analysis of Evasive Malware Christopher Kruegel Lastline, Inc. [email protected] 1 Introduction Automated malware analysis systems (or sandboxes)
Full System Emulation: Achieving Successful Automated Dynamic Analysis of Evasive Malware Christopher Kruegel Lastline, Inc. [email protected] 1 Introduction Automated malware analysis systems (or sandboxes)
How to break in. Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering
 How to break in Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering Time Agenda Agenda Item 9:30 10:00 Introduction 10:00 10:45 Web Application Penetration
How to break in Tecniche avanzate di pen testing in ambito Web Application, Internal Network and Social Engineering Time Agenda Agenda Item 9:30 10:00 Introduction 10:00 10:45 Web Application Penetration
Lecture 17: Mobile Computing Platforms: Android. Mythili Vutukuru CS 653 Spring 2014 March 24, Monday
 Lecture 17: Mobile Computing Platforms: Android Mythili Vutukuru CS 653 Spring 2014 March 24, Monday Mobile applications vs. traditional applications Traditional model of computing: an OS (Linux / Windows),
Lecture 17: Mobile Computing Platforms: Android Mythili Vutukuru CS 653 Spring 2014 March 24, Monday Mobile applications vs. traditional applications Traditional model of computing: an OS (Linux / Windows),
BYPASSING THE ios GATEKEEPER
 BYPASSING THE ios GATEKEEPER AVI BASHAN Technology Leader Check Point Software Technologies, Ltd. OHAD BOBROV Director, Mobile Threat Prevention Check Point Software Technologies, Ltd. EXECUTIVE SUMMARY
BYPASSING THE ios GATEKEEPER AVI BASHAN Technology Leader Check Point Software Technologies, Ltd. OHAD BOBROV Director, Mobile Threat Prevention Check Point Software Technologies, Ltd. EXECUTIVE SUMMARY
SPYWARE & MALWARE. ComputerFixed.co.uk Page: 1 Email: [email protected]. How do you get infected? Will Anti-virus software protect me?
 ComputerFixed.co.uk Page: 1 Email: [email protected] SPYWARE & MALWARE How do you get infected? You can get infected by malware (malicious Software) in several ways. Malware often comes bundled
ComputerFixed.co.uk Page: 1 Email: [email protected] SPYWARE & MALWARE How do you get infected? You can get infected by malware (malicious Software) in several ways. Malware often comes bundled
6WRUP:DWFK. Policies for Dedicated IIS Web Servers Group. V2.1 policy module to restrict ALL network access
 OKENA 71 Second Ave., 3 rd Floor Waltham, MA 02451 Phone 781 209 3200 Fax 781 209 3199 6WRUP:DWFK Policies for Dedicated IIS Web Servers Group The policies shipped with StormWatch address both application-specific
OKENA 71 Second Ave., 3 rd Floor Waltham, MA 02451 Phone 781 209 3200 Fax 781 209 3199 6WRUP:DWFK Policies for Dedicated IIS Web Servers Group The policies shipped with StormWatch address both application-specific
Technical White Paper: Running Applications Under CrossOver: An Analysis of Security Risks
 Technical White Paper: Running Applications Under CrossOver: An Analysis of Security Risks Wine, Viruses, and Methods of Achieving Security Running Windows software via CrossOver is, on average, much safer
Technical White Paper: Running Applications Under CrossOver: An Analysis of Security Risks Wine, Viruses, and Methods of Achieving Security Running Windows software via CrossOver is, on average, much safer
Android Security - Common attack vectors
 Institute of Computer Science 4 Communication and Distributed Systems Rheinische Friedrich-Wilhelms-Universität Bonn, Germany Lab Course: Selected Topics in Communication Management Android Security -
Institute of Computer Science 4 Communication and Distributed Systems Rheinische Friedrich-Wilhelms-Universität Bonn, Germany Lab Course: Selected Topics in Communication Management Android Security -
International Journal of Advance Research in Computer Science and Management Studies
 Volume 3, Issue 3, March 2015 ISSN: 2321 7782 (Online) International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
Volume 3, Issue 3, March 2015 ISSN: 2321 7782 (Online) International Journal of Advance Research in Computer Science and Management Studies Research Article / Survey Paper / Case Study Available online
ESET MOBILE SECURITY FOR ANDROID
 ESET MOBILE SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security 1.1 Installation...3
ESET MOBILE SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security 1.1 Installation...3
Homework 9 Android App for Weather Forecast
 1. Objectives Homework 9 Android App for Weather Forecast Become familiar with Android Studio, Android App development and Facebook SDK for Android. Build a good-looking Android app using the Android SDK.
1. Objectives Homework 9 Android App for Weather Forecast Become familiar with Android Studio, Android App development and Facebook SDK for Android. Build a good-looking Android app using the Android SDK.
The dramatic growth in mobile device malware. continues to escalate at an ever-accelerating. pace. These threats continue to become more
 The dramatic growth in mobile device malware continues to escalate at an ever-accelerating pace. These threats continue to become more sophisticated while the barrier to entry remains low. As specific
The dramatic growth in mobile device malware continues to escalate at an ever-accelerating pace. These threats continue to become more sophisticated while the barrier to entry remains low. As specific
elearning for Secure Application Development
 elearning for Secure Application Development Curriculum Application Security Awareness Series 1-2 Secure Software Development Series 2-8 Secure Architectures and Threat Modeling Series 9 Application Security
elearning for Secure Application Development Curriculum Application Security Awareness Series 1-2 Secure Software Development Series 2-8 Secure Architectures and Threat Modeling Series 9 Application Security
Xerox Mobile Link 2.0 Frequently Asked Questions (FAQ) - Android
 Xerox Mobile Link 2.0 Frequently Asked Questions (FAQ) - Android Xerox Mobile Link is a personal productivity app that connects your mobile phone and tablet to a Xerox Multifunction Printer (MFP). You
Xerox Mobile Link 2.0 Frequently Asked Questions (FAQ) - Android Xerox Mobile Link is a personal productivity app that connects your mobile phone and tablet to a Xerox Multifunction Printer (MFP). You
Adobe Flash Player and Adobe AIR security
 Adobe Flash Player and Adobe AIR security Both Adobe Flash Platform runtimes Flash Player and AIR include built-in security and privacy features to provide strong protection for your data and privacy,
Adobe Flash Player and Adobe AIR security Both Adobe Flash Platform runtimes Flash Player and AIR include built-in security and privacy features to provide strong protection for your data and privacy,
Defense Media Activity Guide To Keeping Your Social Media Accounts Secure
 Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
Trend Micro Incorporated Research Paper 2012. Adding Android and Mac OS X Malware to the APT Toolbox
 Trend Micro Incorporated Research Paper 2012 Adding Android and Mac OS X Malware to the APT Toolbox Contents Abstract... 1 Introduction... 1 Technical Analysis... 2 Remote Access Trojan Functionality...
Trend Micro Incorporated Research Paper 2012 Adding Android and Mac OS X Malware to the APT Toolbox Contents Abstract... 1 Introduction... 1 Technical Analysis... 2 Remote Access Trojan Functionality...
U.S. Cellular Mobile Data Security. User Guide Version 00.01
 U.S. Cellular Mobile Data Security User Guide Version 00.01 Table of Contents Install U.S. Cellular Mobile Data Security...3 Activate U.S. Cellular Mobile Data Security...3 Main Interface...3 Checkup...4
U.S. Cellular Mobile Data Security User Guide Version 00.01 Table of Contents Install U.S. Cellular Mobile Data Security...3 Activate U.S. Cellular Mobile Data Security...3 Main Interface...3 Checkup...4
Mobile Malware and Spyware: Working Through the Bugs. Detective Cindy Murphy 608-267-8824 [email protected]
 Mobile Malware and Spyware: Working Through the Bugs Detective Cindy Murphy 608-267-8824 [email protected] The Mobile Malware Threat 155% increase in mobile malware from 2010 to 2011 614% increase
Mobile Malware and Spyware: Working Through the Bugs Detective Cindy Murphy 608-267-8824 [email protected] The Mobile Malware Threat 155% increase in mobile malware from 2010 to 2011 614% increase
The Behavioral Analysis of Android Malware
 , pp.41-47 http://dx.doi.org/10.14257/astl.2014.63.09 The Behavioral Analysis of Android Malware Fan Yuhui, Xu Ning Department of Computer and Information Engineering, Huainan Normal University, Huainan,
, pp.41-47 http://dx.doi.org/10.14257/astl.2014.63.09 The Behavioral Analysis of Android Malware Fan Yuhui, Xu Ning Department of Computer and Information Engineering, Huainan Normal University, Huainan,
"EZHACK" POPULAR SMART TV DONGLE REMOTE CODE EXECUTION
 "EZHACK" POPULAR SMART TV DONGLE REMOTE CODE EXECUTION CHECK POINT ALERTED EZCAST THAT ITS SMART TV DONGLE, WHICH IS USED BY APPROXIMATELY 5 MILLION USERS, IS EXPOSED TO SEVERE REMOTE CODE EXECUTION VULNERABILITIES
"EZHACK" POPULAR SMART TV DONGLE REMOTE CODE EXECUTION CHECK POINT ALERTED EZCAST THAT ITS SMART TV DONGLE, WHICH IS USED BY APPROXIMATELY 5 MILLION USERS, IS EXPOSED TO SEVERE REMOTE CODE EXECUTION VULNERABILITIES
Contents Release Notes... ... 3 System Requirements... ... 4 Administering Jive for Office... ... 5
 Jive for Office TOC 2 Contents Release Notes...3 System Requirements... 4 Administering Jive for Office... 5 Getting Set Up...5 Installing the Extended API JAR File... 5 Updating Client Binaries...5 Client
Jive for Office TOC 2 Contents Release Notes...3 System Requirements... 4 Administering Jive for Office... 5 Getting Set Up...5 Installing the Extended API JAR File... 5 Updating Client Binaries...5 Client
Now SMS/MMS Android Modem Quick Start Guide
 Now SMS/MMS Android Modem Quick Start Guide Using a GSM modem, or an Android phone as a modem, is a quick and efficient way to get started with SMS and/or MMS applications. No special service provider
Now SMS/MMS Android Modem Quick Start Guide Using a GSM modem, or an Android phone as a modem, is a quick and efficient way to get started with SMS and/or MMS applications. No special service provider
FAKE ANTIVIRUS MALWARE This information has come from http://www.bleepingcomputer.com/ - a very useful resource if you are having computer issues.
 FAKE ANTIVIRUS MALWARE This information has come from http://www.bleepingcomputer.com/ - a very useful resource if you are having computer issues. The latest tactic currently being used by malware creators
FAKE ANTIVIRUS MALWARE This information has come from http://www.bleepingcomputer.com/ - a very useful resource if you are having computer issues. The latest tactic currently being used by malware creators
AppUse - Android Pentest Platform Unified
 AppUse - Android Pentest Platform Unified Standalone Environment AppUse is designed to be a weaponized environment for Android application penetration testing. It is a unique, free, and rich platform aimed
AppUse - Android Pentest Platform Unified Standalone Environment AppUse is designed to be a weaponized environment for Android application penetration testing. It is a unique, free, and rich platform aimed
Comodo Mobile Security for Android Software Version 3.0
 Comodo Mobile Security for Android Software Version 3.0 User Guide Guide Version 3.0.042115 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Mobile
Comodo Mobile Security for Android Software Version 3.0 User Guide Guide Version 3.0.042115 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Mobile
Spyware and Viruses. There is a distinct difference between spyware and viruses.
 Spyware and Viruses Spyware and viruses are getting to be the largest problem in the battle of keeping your computer running smoothly and being able to use your computer with any kind of efficiency. There
Spyware and Viruses Spyware and viruses are getting to be the largest problem in the battle of keeping your computer running smoothly and being able to use your computer with any kind of efficiency. There
Workday Mobile Security FAQ
 Workday Mobile Security FAQ Workday Mobile Security FAQ Contents The Workday Approach 2 Authentication 3 Session 3 Mobile Device Management (MDM) 3 Workday Applications 4 Web 4 Transport Security 5 Privacy
Workday Mobile Security FAQ Workday Mobile Security FAQ Contents The Workday Approach 2 Authentication 3 Session 3 Mobile Device Management (MDM) 3 Workday Applications 4 Web 4 Transport Security 5 Privacy
The SSL device also supports the 64-bit Internet Explorer with new ActiveX loaders for Assessment, Abolishment, and the Access Client.
 WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
WatchGuard SSL v3.2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 355419 Revision Date January 28, 2013 Introduction WatchGuard is pleased to announce the release of WatchGuard
3. Security. 3.1. Security center. Open the Settings app. Tap the Security option. Enable the option Unknown sources.
 G DATA Software 1. Introduction G DATA INTERNET SECURITY FOR ANDROID offers comprehensive protection against malware, intrusive apps and phishing attacks. Locate lost devices or wipe their content remotely
G DATA Software 1. Introduction G DATA INTERNET SECURITY FOR ANDROID offers comprehensive protection against malware, intrusive apps and phishing attacks. Locate lost devices or wipe their content remotely
Improve your mobile application security with IBM Worklight
 Improve your mobile application security with IBM Worklight Contents 1 Introduction 2 IBM Worklight overview 4 Enabling mobile security with IBM Worklight 6 Integrating IBM Worklight with enterprise security
Improve your mobile application security with IBM Worklight Contents 1 Introduction 2 IBM Worklight overview 4 Enabling mobile security with IBM Worklight 6 Integrating IBM Worklight with enterprise security
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Secure Web Application Coding Team Introductory Meeting December 1, 2005 1:00 2:00PM Bits & Pieces Room, Sansom West Room 306 Agenda
 Secure Web Application Coding Team Introductory Meeting December 1, 2005 1:00 2:00PM Bits & Pieces Room, Sansom West Room 306 Agenda 1. Introductions for new members (5 minutes) 2. Name of group 3. Current
Secure Web Application Coding Team Introductory Meeting December 1, 2005 1:00 2:00PM Bits & Pieces Room, Sansom West Room 306 Agenda 1. Introductions for new members (5 minutes) 2. Name of group 3. Current
2 Advanced Session... Properties 3 Session profile... wizard. 5 Application... preferences. 3 ASCII / Binary... Transfer
 Contents I Table of Contents Foreword 0 Part I SecEx Overview 3 1 What is SecEx...? 3 2 Quick start... 4 Part II Configuring SecEx 5 1 Session Profiles... 5 2 Advanced Session... Properties 6 3 Session
Contents I Table of Contents Foreword 0 Part I SecEx Overview 3 1 What is SecEx...? 3 2 Quick start... 4 Part II Configuring SecEx 5 1 Session Profiles... 5 2 Advanced Session... Properties 6 3 Session
User Documentation Web Traffic Security. University of Stavanger
 User Documentation Web Traffic Security University of Stavanger Table of content User Documentation... 1 Web Traffic Security... 1 University of Stavanger... 1 UiS Web Traffic Security... 3 Background...
User Documentation Web Traffic Security University of Stavanger Table of content User Documentation... 1 Web Traffic Security... 1 University of Stavanger... 1 UiS Web Traffic Security... 3 Background...
Authorize.net modules for oscommerce Online Merchant.
 Authorize.net Authorize.net modules for oscommerce Online Merchant. Chapters oscommerce Online Merchant v2.3 Copyright Copyright (c) 2014 oscommerce. All rights reserved. Content may be reproduced for
Authorize.net Authorize.net modules for oscommerce Online Merchant. Chapters oscommerce Online Merchant v2.3 Copyright Copyright (c) 2014 oscommerce. All rights reserved. Content may be reproduced for
Legal notices. Legal notices. For legal notices, see http://help.adobe.com/en_us/legalnotices/index.html.
 ADOBE AIR Security Legal notices Legal notices For legal notices, see http://help.adobe.com/en_us/legalnotices/index.html. iii Contents Installing and updating desktop applications...........................................................................
ADOBE AIR Security Legal notices Legal notices For legal notices, see http://help.adobe.com/en_us/legalnotices/index.html. iii Contents Installing and updating desktop applications...........................................................................
TECHNICAL NOTES BrightSign Network Security Statement BrightSign, LLC. 16795 Lark Ave., Suite 200 Los Gatos, CA 95032 408-852-9263 www.brightsign.
 TECHNICAL NOTES BrightSign Network Security Statement BrightSign, LLC. 16795 Lark Ave., Suite 200 Los Gatos, CA 95032 408-852-9263 www.brightsign.biz INTRODUCTION For a cloud-based content management and
TECHNICAL NOTES BrightSign Network Security Statement BrightSign, LLC. 16795 Lark Ave., Suite 200 Los Gatos, CA 95032 408-852-9263 www.brightsign.biz INTRODUCTION For a cloud-based content management and
AppConnect FAQ for MobileIron Technology Partners! AppConnect Overview
 AppConnect FAQ for MobileIron Technology Partners! AppConnect Overview What is AppConnect? AppConnect is a MobileIron product that secures and protects enterprise mobile apps. It manages the complete lifecycle
AppConnect FAQ for MobileIron Technology Partners! AppConnect Overview What is AppConnect? AppConnect is a MobileIron product that secures and protects enterprise mobile apps. It manages the complete lifecycle
This presentation introduces you to the new call home feature in IBM PureApplication System V2.0.
 This presentation introduces you to the new call home feature in IBM PureApplication System V2.0. Page 1 of 19 This slide shows the agenda, which covers the process flow, user interface, commandline interface
This presentation introduces you to the new call home feature in IBM PureApplication System V2.0. Page 1 of 19 This slide shows the agenda, which covers the process flow, user interface, commandline interface
AGENDA. Background. The Attack Surface. Case Studies. Binary Protections. Bypasses. Conclusions
 MOBILE APPLICATIONS AGENDA Background The Attack Surface Case Studies Binary Protections Bypasses Conclusions BACKGROUND Mobile apps for everything == lots of interesting data Banking financial Social
MOBILE APPLICATIONS AGENDA Background The Attack Surface Case Studies Binary Protections Bypasses Conclusions BACKGROUND Mobile apps for everything == lots of interesting data Banking financial Social
ez Agent Administrator s Guide
 ez Agent Administrator s Guide Copyright This document is protected by the United States copyright laws, and is proprietary to Zscaler Inc. Copying, reproducing, integrating, translating, modifying, enhancing,
ez Agent Administrator s Guide Copyright This document is protected by the United States copyright laws, and is proprietary to Zscaler Inc. Copying, reproducing, integrating, translating, modifying, enhancing,
Norman Security Portal
 User Guide Norman Security Portal SECURITY PORTAL Features Cloud-based endpoint management Managed & unmanaged customers Generate client software Statistics & reports Security Module Antivirus & Antispyware
User Guide Norman Security Portal SECURITY PORTAL Features Cloud-based endpoint management Managed & unmanaged customers Generate client software Statistics & reports Security Module Antivirus & Antispyware
Security Solution for Android Application Assessment
 Security Solution for Android Application Assessment Aparna Bhonde 1, Madhumita Chatterjee 2 Department of IT, PIIT, New Panvel, Mumbai, India 1,2 Abstract: Android Operating System is dominating the share
Security Solution for Android Application Assessment Aparna Bhonde 1, Madhumita Chatterjee 2 Department of IT, PIIT, New Panvel, Mumbai, India 1,2 Abstract: Android Operating System is dominating the share
3. Broken Account and Session Management. 4. Cross-Site Scripting (XSS) Flaws. Web browsers execute code sent from websites. Account Management
 What is an? s Ten Most Critical Web Application Security Vulnerabilities Anthony LAI, CISSP, CISA Chapter Leader (Hong Kong) [email protected] Open Web Application Security Project http://www.owasp.org
What is an? s Ten Most Critical Web Application Security Vulnerabilities Anthony LAI, CISSP, CISA Chapter Leader (Hong Kong) [email protected] Open Web Application Security Project http://www.owasp.org
Google 2 factor authentication User Guide
 Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
How To Create A Bada App On Android 2.2.2 (Mainfest) On Android 3.5.2 And Get A Download Of Bada (For Android) On A Microsoft Gosu 2.5 (For Black
 I. bada... 3 1. Developer Site : Register application development information... 3 1) Registration procedure... 3 2) Standards for managing mainfest.xml depending on status of registration for bada application
I. bada... 3 1. Developer Site : Register application development information... 3 1) Registration procedure... 3 2) Standards for managing mainfest.xml depending on status of registration for bada application
ESET NOD32 Antivirus 4 for Linux Desktop. Quick Start Guide
 ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
End User Devices Security Guidance: Apple OS X 10.10
 GOV.UK Guidance End User Devices Security Guidance: Apple OS X 10.10 Published Contents 1. Changes since previous guidance 2. Usage scenario 3. Summary of platform security 4. How the platform can best
GOV.UK Guidance End User Devices Security Guidance: Apple OS X 10.10 Published Contents 1. Changes since previous guidance 2. Usage scenario 3. Summary of platform security 4. How the platform can best
How Attackers are Targeting Your Mobile Devices. Wade Williamson
 How Attackers are Targeting Your Mobile Devices Wade Williamson Today s Agenda Brief overview of mobile computing today Understanding the risks Analysis of recently discovered malware Protections and best
How Attackers are Targeting Your Mobile Devices Wade Williamson Today s Agenda Brief overview of mobile computing today Understanding the risks Analysis of recently discovered malware Protections and best
Mobile security, forensics & malware analysis with Santoku Linux. * Copyright 2013 viaforensics, LLC. Proprietary Information.
 Mobile security, forensics & malware analysis with Santoku Linux PRESENTER - ANDREW HOOG CEO/Co-founder of viaforensics Andrew is a published author, computer scientist, and mobile security & forensics
Mobile security, forensics & malware analysis with Santoku Linux PRESENTER - ANDREW HOOG CEO/Co-founder of viaforensics Andrew is a published author, computer scientist, and mobile security & forensics
... Mobile App Reputation Services THE RADICATI GROUP, INC.
 . The Radicati Group, Inc. 1900 Embarcadero Road, Suite 206 Palo Alto, CA 94303 Phone 650-322-8059 Fax 650-322-8061 http://www.radicati.com THE RADICATI GROUP, INC. Mobile App Reputation Services Understanding
. The Radicati Group, Inc. 1900 Embarcadero Road, Suite 206 Palo Alto, CA 94303 Phone 650-322-8059 Fax 650-322-8061 http://www.radicati.com THE RADICATI GROUP, INC. Mobile App Reputation Services Understanding
How to achieve PCI DSS Compliance with Checkmarx Source Code Analysis
 How to achieve PCI DSS Compliance with Checkmarx Source Code Analysis Document Scope This document aims to assist organizations comply with PCI DSS 3 when it comes to Application Security best practices.
How to achieve PCI DSS Compliance with Checkmarx Source Code Analysis Document Scope This document aims to assist organizations comply with PCI DSS 3 when it comes to Application Security best practices.
