SECURE INFORMATION FLOW AWARENESS for smart wireless ehealth systems
|
|
|
- Darcy Murphy
- 9 years ago
- Views:
Transcription
1 www. sec.org SECURE INFORMATION FLOW AWARENESS for smart wireless ehealth systems SSD 12 - SCI Chemnitz 2012 stefan pfeiffer, andreas lehmann, sebastian unger, dirk timmermann
2 Lab-on-a-Chip-Implants (Online Bio-Sensing) Remote Diagnosis Online Drugstores and Remote Drug Ordering Wireless Hospital Administration Online Health Monitoring Remote Patient Supervision
3 nurse nurse Primary Care Physician Primary Care Physician nurse
4 nurse nurse Primary Care Physician Primary Care Physician nurse
5 nurse nurse Primary Care Physician Primary Care Physician nurse
6 nurse nurse Primary Care Physician Primary Care Physician nurse
7 Reliable Secure?!?
8 Two-Layer-Approach
9 Two-Layer-Approach Technology Devices Users Network Technology
10 Two-Layer-Approach Technology Security Mechanisms Devices Cryptography Users Security Protocols Network Technology Security Architectures
11 Two-Layer-Approach Infrastructure Layer Technology Security Mechanisms Devices Cryptography Users Security Protocols Network Technology Security Architectures
12 Two-Layer-Approach Process Definition Layer (Workflows / Automation Processes) Infrastructure Layer Technology Security Mechanisms Devices Cryptography Users Security Protocols Network Technology Security Architectures
13 Process Definition Layer Security Information Flow Control Security Domain: Public (Low) Public Private Security Domain: Private (High)
14 Process Definition Layer Security Information Flow Control Security Domain: Public (Low) Information Flow: Low High Public Information Flow: High Low Private Security Domain: Private (High)
15 Example Process
16 Infrastructure Layer - Users Primary Care Physician Patient Emergency Physician
17 Infrastructure Layer - Devices Primary Care Physician Body Area Network Bluetooth Compliant 3G Smartphone Patient Sensor EHR Database Medical In-Car- Information-System Emergency Physician
18 Infrastructure Layer - Networking Primary Care Physician 3G Transmission Tower Body Area Network Internet Carrier Internet Gateway Forwarding Send / Receive Send / Receive Bluetooth Compliant 3G Smartphone Patient Sensor EHR Database Medical In-Car- Information-System Emergency Physician
19 Infrastructure Layer - Security Primary Care Physician 3G Transmission Tower Body Area Network Internet Carrier Internet Gateway Forwarding Send / Receive Send / Receive Bluetooth Compliant 3G Smartphone Patient Sensor EHR Database Medical In-Car- Information-System Emergency Physician
20 Process Definition Layer Process Security Policy: Only Primary Care Physician and Patient have access to the patients EHR database.
21 Process Definition Layer Process Security Policy: Only Primary Care Physician and Patient have access to the patients EHR database. Process Model (informal): FALL DETECTION sensor alarm patient fell to ground BLOOD PRESSURE sensor alarm drop in blood pressure
22 Process Definition Layer Process Security Policy: Only Primary Care Physician and Patient have access to the patients EHR database. Process Model (informal): FALL DETECTION sensor alarm patient fell to ground BLOOD PRESSURE sensor alarm drop in blood pressure EMERGENCY CALL sent autonomously (location, ID, )
23 Process Definition Layer Process Security Policy: Only Primary Care Physician and Patient have access to the patients EHR database. Process Model (informal): FALL DETECTION sensor alarm patient fell to ground BLOOD PRESSURE sensor alarm drop in blood pressure EMERGENCY CALL sent autonomously (location, ID, ) Emergency doctor receives call immediately STARTS DRIVING to location MEDICAL IN-CAR-INFORMATION-SYSTEM accesses the central EHR DATABASE requesting for: drug intolerances medicamentous specialities
24 Process Definition Layer Process Security Policy: Only Primary Care Physician and Patient have access to the patients EHR database. Process Model (informal): FALL DETECTION sensor alarm patient fell to ground BLOOD PRESSURE sensor alarm drop in blood pressure EMERGENCY CALL sent autonomously (location, ID, ) Emergency doctor receives call immediately STARTS DRIVING to location MEDICAL IN-CAR-INFORMATION-SYSTEM accesses the central EHR DATABASE requesting for: drug intolerances medicamentous specialities emergency doctor provides a PERSONALIZED EMERGENCY TREATMENT
25 Verification Framework
26 Verification Framework 1. Process Modeling w.r.t. Infrastructure Layer BPMN 2.0 Model: (ID)
27 Verification Framework 2. Security Annotation in Business Process Model w.r.t. Security Policy Annotated BPMN 2.0 Model: (ID)
28 Verification Framework 3. Transformation from Business Process Model to Formalism (here: Petri nets) Annotated BPMN 2.0 Model Petri net Model
29 Verification Framework 4. Fully Automated Verification of Process Definition Layer Security Properties Tool Support (Full Automation) ANICA secure?!? LoLA Information Flow Violations Witness Path
30 Verification Framework 5. Information Flow Violation BP-Model-Feedback (Witness Path) Petri net Model
31 Verification Framework 5. Information Flow Violation BP-Model-Feedback (Witness Path) BPMN 2.0 Model Petri net Model
32 Conclusion 1. Detect ALL Information Leaks in mhealth workflows 2. Reliable Secure Workflows in mhealth Applications
33 Thank you for your attention! For further information and details, don t hesitate to ask... Stefan Pfeiffer Andreas Lehmann... or visit our websites... www. sec.org
34 Backup Slides
35 ehealth Information Flow Violations 1. Emergency Information Flow Violation 2. Untrusted / Not Certified System Components 3. Information Flow Policy Violation by Design
36 Verification Framework
37 Security The Ancient Way Security Mechanisms: guarded single entry point guarded walls built upon hills ALARM in-castle information system
38 Security The Ancient Way
Health Care 2.0: How Technology is Transforming Health Care
 Health Care 2.0: How Technology is Transforming Health Care Matthew Kaiser, CEBS, SPHR Director, HR Technology and Outsourcing Lockton Kansas City, Missouri The opinions expressed in this presentation
Health Care 2.0: How Technology is Transforming Health Care Matthew Kaiser, CEBS, SPHR Director, HR Technology and Outsourcing Lockton Kansas City, Missouri The opinions expressed in this presentation
Healthcare Delivery. Transforming. through Mobility Solutions. A Solution White Paper - version 1.0
 Transforming Healthcare Delivery through Mobility Solutions A Solution White Paper - version 1.0 HTC Global Services HTC Towers, No. 41, GST Road, Guindy, Chennai - 600 032, India. Ph: +91 44 4345 3500
Transforming Healthcare Delivery through Mobility Solutions A Solution White Paper - version 1.0 HTC Global Services HTC Towers, No. 41, GST Road, Guindy, Chennai - 600 032, India. Ph: +91 44 4345 3500
Mobile Health. Architecture, Applications, Security. Capt Farell FOLLY, Ir. June 20th, Lusaka - ZAMBIA. Africa Internet Summit 2013
 1 Mobile Health, Applications, Capt Farell FOLLY, Ir Africa Internet Summit 2013 June 20th, Lusaka - ZAMBIA 2 Sommaire 1 2 3 3 m-services 1 m-services 2 Use cases for 3 Description Interactions 4 m-services
1 Mobile Health, Applications, Capt Farell FOLLY, Ir Africa Internet Summit 2013 June 20th, Lusaka - ZAMBIA 2 Sommaire 1 2 3 3 m-services 1 m-services 2 Use cases for 3 Description Interactions 4 m-services
HIC 2009 Workshop Introduction to Health Informatics
 HIC 2009 Workshop Introduction to Health Informatics Part 2: Knowledge Domain & Educational Options Professor Anthony Maeder University of Western Sydney Health Informatics Knowledge Domain Perspectives
HIC 2009 Workshop Introduction to Health Informatics Part 2: Knowledge Domain & Educational Options Professor Anthony Maeder University of Western Sydney Health Informatics Knowledge Domain Perspectives
The HYDRA project. Personal health monitoring
 The HYDRA project A middleware platform for personal health monitoring Peter Rosengren, Technical Coordinator [email protected] IST-2005-034891 Personal health monitoring Patient has some medical
The HYDRA project A middleware platform for personal health monitoring Peter Rosengren, Technical Coordinator [email protected] IST-2005-034891 Personal health monitoring Patient has some medical
A Study of the Design of Wireless Medical Sensor Network based u- Healthcare System
 , pp.91-96 http://dx.doi.org/10.14257/ijbsbt.2014.6.3.11 A Study of the Design of Wireless Medical Sensor Network based u- Healthcare System Ronnie D. Caytiles and Sungwon Park 1* 1 Hannam University 133
, pp.91-96 http://dx.doi.org/10.14257/ijbsbt.2014.6.3.11 A Study of the Design of Wireless Medical Sensor Network based u- Healthcare System Ronnie D. Caytiles and Sungwon Park 1* 1 Hannam University 133
Internet of things (IOT) applications covering industrial domain. Dev Bhattacharya [email protected]
 Internet of things (IOT) applications covering industrial domain Dev Bhattacharya [email protected] Outline Internet of things What is Internet of things (IOT) Simplified IOT System Architecture
Internet of things (IOT) applications covering industrial domain Dev Bhattacharya [email protected] Outline Internet of things What is Internet of things (IOT) Simplified IOT System Architecture
Internet of Things on HealthCare and Chinese Wearable Medical Devices
 Internet of Things on HealthCare and Chinese Wearable Medical Devices Xia Wenhuan Director, Greater China Region Business Development TIP Group [email protected] BD Internal INTERNET OF THINGS
Internet of Things on HealthCare and Chinese Wearable Medical Devices Xia Wenhuan Director, Greater China Region Business Development TIP Group [email protected] BD Internal INTERNET OF THINGS
Cryptography and Network Security Chapter 1
 Cryptography and Network Security Chapter 1 Acknowledgments Lecture slides are based on the slides created by Lawrie Brown Chapter 1 Introduction The art of war teaches us to rely not on the likelihood
Cryptography and Network Security Chapter 1 Acknowledgments Lecture slides are based on the slides created by Lawrie Brown Chapter 1 Introduction The art of war teaches us to rely not on the likelihood
Healthcare Services - education and research - developed in the INSEED project
 Healthcare Services - education and research - developed in the INSEED project Radu DOBRESCU Universitatea Politehnica din Bucureşti Program Strategic pentru Promovarea Inovarii în Servicii prin Educaţie
Healthcare Services - education and research - developed in the INSEED project Radu DOBRESCU Universitatea Politehnica din Bucureşti Program Strategic pentru Promovarea Inovarii în Servicii prin Educaţie
A Study on Design of Health Device for U-Health System
 , pp.79-86 http://dx.doi.org/10.14257/ijbsbt.2015.7.2.08 A Study on Design of Health Device for U-Health System Am-Suk Oh Dept. of Media Engineering, Tongmyong University, Busan, Korea [email protected] Abstract
, pp.79-86 http://dx.doi.org/10.14257/ijbsbt.2015.7.2.08 A Study on Design of Health Device for U-Health System Am-Suk Oh Dept. of Media Engineering, Tongmyong University, Busan, Korea [email protected] Abstract
Patient Centricity and the Changing Landscape of Healthcare
 Patient Centricity and the Changing Landscape of Healthcare Andrea Cotter Director Healthcare Marketing IBM Corporation IBM Healthcare and Life Sciences Patient Centricity and the Changing Landscape of
Patient Centricity and the Changing Landscape of Healthcare Andrea Cotter Director Healthcare Marketing IBM Corporation IBM Healthcare and Life Sciences Patient Centricity and the Changing Landscape of
Spok Template v2 7/8/2015
 COMMUNICATION TOOLS TO COMPLEMENT THE EHR Brian Edds, Vice President Product Strategy at Spok, Inc. ABOUT SPOK Decades of experience managing healthcare communications 98% customer satisfaction scores
COMMUNICATION TOOLS TO COMPLEMENT THE EHR Brian Edds, Vice President Product Strategy at Spok, Inc. ABOUT SPOK Decades of experience managing healthcare communications 98% customer satisfaction scores
ehealth, HIS, etc ehealth All information about health HMIS mhealth HIS Statistical IS Credited: Karl Brown, Rockefeller Foundation
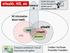 ehealth, HIS, etc Statistical IS Health Informatics: Formal discipline that studies use of information in health All information about health HIS HMIS ehealth mhealth Tele-medicine Enterprise architecture:
ehealth, HIS, etc Statistical IS Health Informatics: Formal discipline that studies use of information in health All information about health HIS HMIS ehealth mhealth Tele-medicine Enterprise architecture:
The Total Telehealth Solution
 The Total Telehealth Solution Overview of Telehealth Module 1 Overview of Telehealth/Telemedicine Telemedicine began over 40 years ago. Formally defined; telemedicine is the use of medical information,
The Total Telehealth Solution Overview of Telehealth Module 1 Overview of Telehealth/Telemedicine Telemedicine began over 40 years ago. Formally defined; telemedicine is the use of medical information,
Activating Standardization Bodies Around Medical Apps
 Activating Standardization Bodies Around Medical Apps Michael J. Ackerman, Ph.D. Assistant Director High Performance Computing and Communications U.S. National Library of Medicine The views and opinions
Activating Standardization Bodies Around Medical Apps Michael J. Ackerman, Ph.D. Assistant Director High Performance Computing and Communications U.S. National Library of Medicine The views and opinions
Cryptography and Network Security
 Cryptography and Network Security Third Edition by William Stallings Lecture slides by Shinu Mathew John http://shinu.info/ Chapter 1 Introduction http://shinu.info/ 2 Background Information Security requirements
Cryptography and Network Security Third Edition by William Stallings Lecture slides by Shinu Mathew John http://shinu.info/ Chapter 1 Introduction http://shinu.info/ 2 Background Information Security requirements
e-health Initiative Lina Abou Mrad MBA, PMP Director, National E-Health Program Health Insight 4 -March 2014
 e-health Initiative Lina Abou Mrad MBA, PMP Director, National E-Health Program Health Insight 4 -March 2014 What is E-Health? The term e-health was barely in use before 1999 Terms such as medical informatics,
e-health Initiative Lina Abou Mrad MBA, PMP Director, National E-Health Program Health Insight 4 -March 2014 What is E-Health? The term e-health was barely in use before 1999 Terms such as medical informatics,
Evolution of Information Society. after the Mobile Information Society. the emergence of Personal Information Services
 Mobile Health Akihisa KODATE, Dr.-Eng. Visiting Associate Professor Global Information and Telecommunication Institute Waseda University, Japan E-mail : [email protected] Images of Hertz Handy of Vita phone,
Mobile Health Akihisa KODATE, Dr.-Eng. Visiting Associate Professor Global Information and Telecommunication Institute Waseda University, Japan E-mail : [email protected] Images of Hertz Handy of Vita phone,
Cyber Security Management for Utility Operations by Dennis K. Holstein (Opus Publishing) and Jose Diaz (Thales esecurity)
 Cyber Security Management for Utility Operations by Dennis K. Holstein (Opus Publishing) and Jose Diaz (Thales esecurity) Abstract Strong identity management enforced with digital authentication mechanisms
Cyber Security Management for Utility Operations by Dennis K. Holstein (Opus Publishing) and Jose Diaz (Thales esecurity) Abstract Strong identity management enforced with digital authentication mechanisms
Copyright 2005-2010 Soleran, Inc. esalestrack On-Demand CRM. Trademarks and all rights reserved. esalestrack is a Soleran product Privacy Statement

The Internet of Things: Opportunities & Challenges
 The Internet of Things: Opportunities & Challenges What is the IoT? Things, people and cloud services getting connected via the Internet to enable new use cases and business models Cloud Services How is
The Internet of Things: Opportunities & Challenges What is the IoT? Things, people and cloud services getting connected via the Internet to enable new use cases and business models Cloud Services How is
PCI Requirements Coverage Summary Table
 StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table January 2013 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table January 2013 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
Health Information Technology & Management Chapter 2 HEALTH INFORMATION SYSTEMS
 Health Information Technology & Management Chapter 2 HEALTH INFORMATION SYSTEMS INFORMATION SYSTEM *Use of computer hardware and software to process data into information. *Healthcare information system
Health Information Technology & Management Chapter 2 HEALTH INFORMATION SYSTEMS INFORMATION SYSTEM *Use of computer hardware and software to process data into information. *Healthcare information system
Iknaia Asset and Personnel Tracking Management System for the Healthcare Industry
 Iknaia Asset and Personnel Tracking Management System for the Healthcare Industry July 2014 Introduction Trying to find your way around a large hospital or locating a high-value medical device such as
Iknaia Asset and Personnel Tracking Management System for the Healthcare Industry July 2014 Introduction Trying to find your way around a large hospital or locating a high-value medical device such as
Overview of ehr Development. Slide - 1
 Overview of ehr Development Slide - 1 Where are we today? Hospital Authority 8 million patient records 800 million laboratory results 340 million prescribed drugs 34 million Xray images 33 million transactions
Overview of ehr Development Slide - 1 Where are we today? Hospital Authority 8 million patient records 800 million laboratory results 340 million prescribed drugs 34 million Xray images 33 million transactions
Domonial, le Sucre. Easy to Use Intruder Detection Systems
 Domonial, le Sucre Easy to Use Intruder Detection Systems Domonial Brief description With over a million installed sites, Domonial is one of the most popular remotely monitored wireless security systems
Domonial, le Sucre Easy to Use Intruder Detection Systems Domonial Brief description With over a million installed sites, Domonial is one of the most popular remotely monitored wireless security systems
Wireless and Mobile Technologies for Healthcare: Ensuring Privacy, Security, and Availability
 Wireless and Mobile Technologies for Healthcare: Ensuring Privacy, Security, and Availability T. Jepsen, N. Buckley, D. Witters, K. Stine INTRODUCTION The IEEE-USA Medical Technology Policy Committee sponsored
Wireless and Mobile Technologies for Healthcare: Ensuring Privacy, Security, and Availability T. Jepsen, N. Buckley, D. Witters, K. Stine INTRODUCTION The IEEE-USA Medical Technology Policy Committee sponsored
PCI DSS Policies Outline. PCI DSS Policies. All Rights Reserved. ecfirst. 2010. Page 1 of 7 www.ecfirst.com
 Policy/Procedure Description PCI DSS Policies Install and Maintain a Firewall Configuration to Protect Cardholder Data Establish Firewall and Router Configuration Standards Build a Firewall Configuration
Policy/Procedure Description PCI DSS Policies Install and Maintain a Firewall Configuration to Protect Cardholder Data Establish Firewall and Router Configuration Standards Build a Firewall Configuration
Access is power. Access management may be an untapped element in a hospital s cybersecurity plan. January 2016. kpmg.com
 Access is power Access management may be an untapped element in a hospital s cybersecurity plan January 2016 kpmg.com Introduction Patient data is a valuable asset. Having timely access is critical for
Access is power Access management may be an untapped element in a hospital s cybersecurity plan January 2016 kpmg.com Introduction Patient data is a valuable asset. Having timely access is critical for
BI en Salud: Registro de Salud Electrónico, Estado del Arte!
 BI en Salud: Registro de Salud Electrónico, Estado del Arte! Manuel Graña Romay! ENGINE Centre, Wrocław University of Technology! Grupo de Inteligencia Computacional (GIC); UPV/EHU; www.ehu.es/ ccwintco!
BI en Salud: Registro de Salud Electrónico, Estado del Arte! Manuel Graña Romay! ENGINE Centre, Wrocław University of Technology! Grupo de Inteligencia Computacional (GIC); UPV/EHU; www.ehu.es/ ccwintco!
Monitoring solar PV output
 Monitoring solar PV output Introduction Monitoring of your solar PV output is useful to see the actual outputs. This can be measured from the inverter and/or mains using current clamps or pulse meters
Monitoring solar PV output Introduction Monitoring of your solar PV output is useful to see the actual outputs. This can be measured from the inverter and/or mains using current clamps or pulse meters
Cloud Based Telehealth
 Cloud Based Telehealth ewave MD Healthcare Everywhere! Talor Sax VP Business Development ewave MD [email protected] March 2012 Key events in ewave MD s history n Centralized Web- Based EHR (1,500 physicians)
Cloud Based Telehealth ewave MD Healthcare Everywhere! Talor Sax VP Business Development ewave MD [email protected] March 2012 Key events in ewave MD s history n Centralized Web- Based EHR (1,500 physicians)
The State of Health Data Exchange: The Impact on Healthcare Operations
 The State of Health Data Exchange: The Impact on Healthcare Operations Healthcare Financial Management Association Kentucky HFMA Chapter Louisville, KY January 22, 2015 Gary W. Ozanich, Ph.D. Northern
The State of Health Data Exchange: The Impact on Healthcare Operations Healthcare Financial Management Association Kentucky HFMA Chapter Louisville, KY January 22, 2015 Gary W. Ozanich, Ph.D. Northern
www.opentheredbox.com Charlie Mountain Top Nowak Senior Director Public Sector Healthcare Solutions cnowak@extensionhealthcare.
 www.opentheredbox.com Charlie Mountain Top Nowak Senior Director Public Sector Healthcare Solutions [email protected] 919-607-8124 Important considerations for Alarm Management Equipment How
www.opentheredbox.com Charlie Mountain Top Nowak Senior Director Public Sector Healthcare Solutions [email protected] 919-607-8124 Important considerations for Alarm Management Equipment How
Privacy Policy Version 1.0, 1 st of May 2016
 Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
Privacy Policy Version 1.0, 1 st of May 2016 THIS PRIVACY POLICY APPLIES TO PERSONAL INFORMATION COLLECTED BY GOCIETY SOLUTIONS FROM USERS OF THE GOCIETY SOLUTIONS APPLICATIONS (GoLivePhone and GoLiveAssist)
INSTRUCTIONS FOR USE: OA-RX
 P a g e 1 INSTRUCTIONS FOR USE: OA-RX Welcome to Office Ally s Electronic Prescription module, called OA-Rx. This web-based program has been designed to integrate into Office Ally s Practice Mate and EHR
P a g e 1 INSTRUCTIONS FOR USE: OA-RX Welcome to Office Ally s Electronic Prescription module, called OA-Rx. This web-based program has been designed to integrate into Office Ally s Practice Mate and EHR
How To Understand The Difference Between Terminology And Ontology
 Terminology and Ontology in Semantic Interoperability of Electronic Health Records Dr. W. Ceusters Saarland University Semantic Interoperability Working definition: Two information systems are semantically
Terminology and Ontology in Semantic Interoperability of Electronic Health Records Dr. W. Ceusters Saarland University Semantic Interoperability Working definition: Two information systems are semantically
Wireless Infusion Pumps: Securing Hospitals Most Ubiquitous Medical Device
 Wireless Infusion Pumps: Securing Hospitals Most Ubiquitous Medical Device The Healthcare Sector at the NCCoE MARCH, 3 2016 THE NATIONAL CYBERSECURITY LAB HELPS SECURE HIT 1. About Us: The National Cybersecurity
Wireless Infusion Pumps: Securing Hospitals Most Ubiquitous Medical Device The Healthcare Sector at the NCCoE MARCH, 3 2016 THE NATIONAL CYBERSECURITY LAB HELPS SECURE HIT 1. About Us: The National Cybersecurity
Clinical Workflow Solutions EXTENSION HealthAlert
 Clinical Workflow Solutions EXTENSION HealthAlert NEC Corporation of America necam.com EXTENSION s suite of solutions unites the various clinical information systems in a medical environment to deliver
Clinical Workflow Solutions EXTENSION HealthAlert NEC Corporation of America necam.com EXTENSION s suite of solutions unites the various clinical information systems in a medical environment to deliver
Healthcare: Network and infrastructure solutions for an evolving industry. Healthcare Solutions
 Healthcare: Network and infrastructure solutions for an evolving industry Healthcare Solutions The business of healthcare is evolving faster than ever. Are your network and data center infrastructure up
Healthcare: Network and infrastructure solutions for an evolving industry Healthcare Solutions The business of healthcare is evolving faster than ever. Are your network and data center infrastructure up
SCADA Compliance Tools For NERC-CIP. The Right Tools for Bringing Your Organization in Line with the Latest Standards
 SCADA Compliance Tools For NERC-CIP The Right Tools for Bringing Your Organization in Line with the Latest Standards OVERVIEW Electrical utilities are responsible for defining critical cyber assets which
SCADA Compliance Tools For NERC-CIP The Right Tools for Bringing Your Organization in Line with the Latest Standards OVERVIEW Electrical utilities are responsible for defining critical cyber assets which
Table of Contents. Introduction. Audience. At Course Completion
 Table of Contents Introduction Audience At Course Completion Prerequisites Certified Professional Exams Student Materials Course Outline Introduction This four-day, instructor-led course provides students
Table of Contents Introduction Audience At Course Completion Prerequisites Certified Professional Exams Student Materials Course Outline Introduction This four-day, instructor-led course provides students
ehealth and Health Information Exchange in Minnesota
 ehealth and Health Information Exchange in Minnesota Connecting Minnesota Providers at the Point of Care Lisa Moon, RN Director Privacy Security and HIE Oversight Program Office of Health Information Technology
ehealth and Health Information Exchange in Minnesota Connecting Minnesota Providers at the Point of Care Lisa Moon, RN Director Privacy Security and HIE Oversight Program Office of Health Information Technology
EHR Software Feature Comparison
 EHR Comparison ELECTRONIC MEDICAL RECORDS Patient demographics Manages the input and maintenance of patient information including demographics, insurance, contacts, referrals, notes and more. Consents
EHR Comparison ELECTRONIC MEDICAL RECORDS Patient demographics Manages the input and maintenance of patient information including demographics, insurance, contacts, referrals, notes and more. Consents
Summer projects for Dept. of IT students in the summer 2015
 Summer projects for Dept. of IT students in the summer 2015 Here are 7 possible summer project topics for students. If you are interested in any of them, contact the person associated with the project
Summer projects for Dept. of IT students in the summer 2015 Here are 7 possible summer project topics for students. If you are interested in any of them, contact the person associated with the project
CMS & ehr - An Update
 Health Informatics in Hong Kong CMS & ehr - An Update Dr NT Cheung HA Convention 2010 CMS / epr is essential in the HA Each Day... 12,000 users 90,000 patients 8M CMS transactions 700,000 epr views In
Health Informatics in Hong Kong CMS & ehr - An Update Dr NT Cheung HA Convention 2010 CMS / epr is essential in the HA Each Day... 12,000 users 90,000 patients 8M CMS transactions 700,000 epr views In
A Review of the Components and Best Practices in Using Electronic Health Records
 A Review of the Components and Best Practices in Using Electronic Health Records Thomas Andrews, RN-BC, MS Director, Acute Care Informatics Presence Health Webinar: November 27, 2012 Polling Question Have
A Review of the Components and Best Practices in Using Electronic Health Records Thomas Andrews, RN-BC, MS Director, Acute Care Informatics Presence Health Webinar: November 27, 2012 Polling Question Have
Aligning Meaningful Use CQM and PQRS Reporting for 2015
 Aligning Meaningful Use CQM and PQRS Reporting for 2015 August 19, 2015 Introductions Marni Anderson Project Specialist, MetaStar [email protected] 608-441-8253 Laura Sawyer Clinical Application Coordinator,
Aligning Meaningful Use CQM and PQRS Reporting for 2015 August 19, 2015 Introductions Marni Anderson Project Specialist, MetaStar [email protected] 608-441-8253 Laura Sawyer Clinical Application Coordinator,
In the pursuit of becoming smart
 WHITE PAPER In the pursuit of becoming smart The business insight into Comarch IoT Platform Introduction Businesses around the world are seeking the direction for the future, trying to find the right solution
WHITE PAPER In the pursuit of becoming smart The business insight into Comarch IoT Platform Introduction Businesses around the world are seeking the direction for the future, trying to find the right solution
WHITEPAPER MOBILE REMOTE PATIENT MONITORING. Author: Arif Nasim Head of Mobility Practice
 WHITEPAPER MOBILE REMOTE PATIENT MONITORING Author: Arif Nasim Head of Mobility Practice 1 INTRODUCTION With the growing elderly population and the increase in diseases along with the rising treatment
WHITEPAPER MOBILE REMOTE PATIENT MONITORING Author: Arif Nasim Head of Mobility Practice 1 INTRODUCTION With the growing elderly population and the increase in diseases along with the rising treatment
Regulation of Mobile Medical Apps
 Regulation of Mobile Medical Apps May 30, 2014 Copyright 2014 Software Quality Consulting Inc. Slide 1 Speaker Bio Steven R. Rakitin has over 35 years experience as a software engineer and 25 years in
Regulation of Mobile Medical Apps May 30, 2014 Copyright 2014 Software Quality Consulting Inc. Slide 1 Speaker Bio Steven R. Rakitin has over 35 years experience as a software engineer and 25 years in
Pharmaceutical Industry
 Application of Mobility in Pharmaceutical Industry for Field Sales Force A Solution White Paper - version 1.0 HTC Global Services HTC Towers, No.41, GST Road, Guindy, Chennai - 600 032, INDIA. Ph: +91
Application of Mobility in Pharmaceutical Industry for Field Sales Force A Solution White Paper - version 1.0 HTC Global Services HTC Towers, No.41, GST Road, Guindy, Chennai - 600 032, INDIA. Ph: +91
ONTARIO S EHR CONNECTIVITY STRATEGY IMPROVING PRIMARY TO SPECIALIST REFERRAL THROUGH INTEGRATION. Peter Bascom Chief Architect, ehealth Ontario
 ONTARIO S EHR CONNECTIVITY STRATEGY IMPROVING PRIMARY TO SPECIALIST REFERRAL THROUGH INTEGRATION Peter Bascom Chief Architect, ehealth Ontario Cindy Hollister Director, Professional Practice, Canada Health
ONTARIO S EHR CONNECTIVITY STRATEGY IMPROVING PRIMARY TO SPECIALIST REFERRAL THROUGH INTEGRATION Peter Bascom Chief Architect, ehealth Ontario Cindy Hollister Director, Professional Practice, Canada Health
WHITE PAPER Usher Mobile Identity Platform
 WHITE PAPER Usher Mobile Identity Platform Security Architecture For more information, visit Usher.com [email protected] Toll Free (US ONLY): 1 888.656.4464 Direct Dial: 703.848.8710 Table of contents Introduction
WHITE PAPER Usher Mobile Identity Platform Security Architecture For more information, visit Usher.com [email protected] Toll Free (US ONLY): 1 888.656.4464 Direct Dial: 703.848.8710 Table of contents Introduction
A MEDICAL HEALTH CARE SYSTEM WITH HIGH SECURITY USING ANDROID APPLICATION
 A MEDICAL HEALTH CARE SYSTEM WITH HIGH SECURITY USING ANDROID APPLICATION Mr. T.CHANDRA SEKHAR RAO PROFESSOR and HEAD T.SREEDHAR M.TECH DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING LOYOLA INSTITUTE
A MEDICAL HEALTH CARE SYSTEM WITH HIGH SECURITY USING ANDROID APPLICATION Mr. T.CHANDRA SEKHAR RAO PROFESSOR and HEAD T.SREEDHAR M.TECH DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING LOYOLA INSTITUTE
Emerson s Smart Wireless and WIB Requirements
 Emerson s Smart Wireless and WIB Requirements Acronyms.................................................................. page 2 Overview..................................................................
Emerson s Smart Wireless and WIB Requirements Acronyms.................................................................. page 2 Overview..................................................................
The U.S. FDA s Regulation and Oversight of Mobile Medical Applications
 The U.S. FDA s Regulation and Oversight of Mobile Medical Applications The U.S. FDA s Regulation and Oversight of Mobile Medical Applications As smart phones and portable tablet computers become the preferred
The U.S. FDA s Regulation and Oversight of Mobile Medical Applications The U.S. FDA s Regulation and Oversight of Mobile Medical Applications As smart phones and portable tablet computers become the preferred
North Dakota Telepharmacy Project: An Update
 North Dakota Telepharmacy Project: An Update North Dakota Pharmacist Association Convention April 23-25, 2010, Minot, North Dakota Ann Rathke, North Dakota Telepharmacy Project NDSU College of Pharmacy,
North Dakota Telepharmacy Project: An Update North Dakota Pharmacist Association Convention April 23-25, 2010, Minot, North Dakota Ann Rathke, North Dakota Telepharmacy Project NDSU College of Pharmacy,
ehealth Pod Pilot Program Challenges I. Identifying Challenges for Providers Not Participating in the Pilot
 Pennsylvania s Department of Public Welfare s Office of Medical Assistance Programs (OMAP) developed the ehealth Pod Pilot Program to stimulate the use of health information technology by behavioral health
Pennsylvania s Department of Public Welfare s Office of Medical Assistance Programs (OMAP) developed the ehealth Pod Pilot Program to stimulate the use of health information technology by behavioral health
How To Use Zh Openemr
 ZHOpenEMR A Fully Integrated Certified EHR and Practice Management System Z&H Healthcare Solutions, LLC ZHOpenEMR ONC-ATB Ambulatory EHR 2011-2012 Certified Incentive Reporting No License fees Used in
ZHOpenEMR A Fully Integrated Certified EHR and Practice Management System Z&H Healthcare Solutions, LLC ZHOpenEMR ONC-ATB Ambulatory EHR 2011-2012 Certified Incentive Reporting No License fees Used in
70 299 Implementing and Administering Security in a Microsoft Windows Server 2003 Network
 70 299 Implementing and Administering Security in a Microsoft Windows Server 2003 Network Course Number: 70 299 Length: 1 Day(s) Course Overview This course is part of the MCSA training.. Prerequisites
70 299 Implementing and Administering Security in a Microsoft Windows Server 2003 Network Course Number: 70 299 Length: 1 Day(s) Course Overview This course is part of the MCSA training.. Prerequisites
Stefan Sjöström, SEABB, PAPI UGM Automation ABB Underground mining Mobile Integration. ABB Group May 18, 2015 Slide 1 3BSE081096-212
 Stefan Sjöström, SEABB, PAPI UGM Automation ABB Underground mining Mobile Integration May 18, 2015 Slide 1 Integrated Mine automation and electrification Mine Operation Center Substations GIS Substations
Stefan Sjöström, SEABB, PAPI UGM Automation ABB Underground mining Mobile Integration May 18, 2015 Slide 1 Integrated Mine automation and electrification Mine Operation Center Substations GIS Substations
Securing Unified Communications for Healthcare
 Securing Unified Communications for Healthcare Table of Contents Securing UC A Unique Process... 2 Fundamental Components of a Healthcare UC Security Architecture... 3 Making Unified Communications Secure
Securing Unified Communications for Healthcare Table of Contents Securing UC A Unique Process... 2 Fundamental Components of a Healthcare UC Security Architecture... 3 Making Unified Communications Secure
Start your adventure with SMART HOME.
 Start your adventure with SMART HOME. Your home can be smarter than you think. Explore the benefits of home automation with FIBARO STARTER KIT. Five intelligent devices together with Home Center Lite will
Start your adventure with SMART HOME. Your home can be smarter than you think. Explore the benefits of home automation with FIBARO STARTER KIT. Five intelligent devices together with Home Center Lite will
Smart Integration of Wireless Temperature Monitoring System with Building Automation System
 Smart Integration of Wireless Temperature Monitoring System with Building Automation System Case Study Area of engagement Solution to integrate wireless temperature monitoring system with BMS (Building
Smart Integration of Wireless Temperature Monitoring System with Building Automation System Case Study Area of engagement Solution to integrate wireless temperature monitoring system with BMS (Building
Data Management and Good Clinical Practice Patrick Murphy, Research Informatics, Family Health International
 Data Management and Good Clinical Practice Patrick Murphy,, Family Health International 1 What is GCP? Good Clinical Practice is an international ethical and scientific quality standard for designing,
Data Management and Good Clinical Practice Patrick Murphy,, Family Health International 1 What is GCP? Good Clinical Practice is an international ethical and scientific quality standard for designing,
PCI Requirements Coverage Summary Table
 StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table December 2011 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
StillSecure PCI Complete Managed PCI Compliance Solution PCI Requirements Coverage Summary Table December 2011 Table of Contents Introduction... 2 Coverage assumptions for PCI Complete deployments... 2
Physician Champions David C. Kibbe, MD, & Daniel Mongiardo, MD FAQ Responses
 Physician Champions David C. Kibbe, MD, & Daniel Mongiardo, MD FAQ Responses DR. KIBBE S RESPONSES What is health information exchange? How can health information exchange help my practice? Can I comply
Physician Champions David C. Kibbe, MD, & Daniel Mongiardo, MD FAQ Responses DR. KIBBE S RESPONSES What is health information exchange? How can health information exchange help my practice? Can I comply
The Internet of ANYthing
 The of ANYthing Abstract It is projected that by 2020 there will be 50 billion things connected to the. This presents both unprecedented opportunity and challenge. In the global network of things, new
The of ANYthing Abstract It is projected that by 2020 there will be 50 billion things connected to the. This presents both unprecedented opportunity and challenge. In the global network of things, new
Guide To Meaningful Use
 Guide To Meaningful Use Volume 1 Collecting the Data Contents INTRODUCTION... 3 CORE SET... 4 1. DEMOGRAPHICS... 5 2. VITAL SIGNS... 6 3. PROBLEM LIST... 8 4. MAINTAIN ACTIVE MEDICATIONS LIST... 9 5. MEDICATION
Guide To Meaningful Use Volume 1 Collecting the Data Contents INTRODUCTION... 3 CORE SET... 4 1. DEMOGRAPHICS... 5 2. VITAL SIGNS... 6 3. PROBLEM LIST... 8 4. MAINTAIN ACTIVE MEDICATIONS LIST... 9 5. MEDICATION
TELE HEALTH CASE STUDY: TELE RADIOLOGY
 TELE HEALTH 2 HealthFore Transforming Healthcare HealthFore Technologies Limited is a global healthcare IT solutions and advisory services company. Our B2B and B2C IT solutions help hospital chains, diagnostic
TELE HEALTH 2 HealthFore Transforming Healthcare HealthFore Technologies Limited is a global healthcare IT solutions and advisory services company. Our B2B and B2C IT solutions help hospital chains, diagnostic
Web of Things Architecture
 Web of Things Architecture 1. Introduction This document is an explanation about the architecture of Web Of Things (WoT). The purpose of this document is to provide (a) a guideline of the mapping between
Web of Things Architecture 1. Introduction This document is an explanation about the architecture of Web Of Things (WoT). The purpose of this document is to provide (a) a guideline of the mapping between
MEDIAWEB HEALTHCARE PATIENT MANAGEMENT SYSTEM CLINICAL DATA & PATIENT INFOTAINMENT
 MEDIAWEB HEALTHCARE PATIENT MANAGEMENT SYSTEM CLINICAL DATA & PATIENT INFOTAINMENT MODERN HEALTH STRUCTURES USE INTEGRATED SOLUTIONS, CLINICAL DATA (HEALTH MEDICAL) AND HOSPITALITY (PATIENT INFOTAINMENT
MEDIAWEB HEALTHCARE PATIENT MANAGEMENT SYSTEM CLINICAL DATA & PATIENT INFOTAINMENT MODERN HEALTH STRUCTURES USE INTEGRATED SOLUTIONS, CLINICAL DATA (HEALTH MEDICAL) AND HOSPITALITY (PATIENT INFOTAINMENT
The ELGA initiative: A plan for implementing a nationwide electronic health records system in Austria
 The ELGA initiative: A plan for implementing a nationwide electronic health records system in Austria Georg Duftschmid, Wolfgang Dorda, Walter Gall Core Unit of Medical Statistics and Informatics Section
The ELGA initiative: A plan for implementing a nationwide electronic health records system in Austria Georg Duftschmid, Wolfgang Dorda, Walter Gall Core Unit of Medical Statistics and Informatics Section
Technical Article. NFiC: a new, economical way to make a device NFC-compliant. Prashant Dekate
 Technical NFiC: a new, economical way to make a device NFC-compliant Prashant Dekate NFiC: a new, economical way to make a device NFC-compliant Prashant Dekate The installed base of devices with Near Field
Technical NFiC: a new, economical way to make a device NFC-compliant Prashant Dekate NFiC: a new, economical way to make a device NFC-compliant Prashant Dekate The installed base of devices with Near Field

