Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses
|
|
|
- Stanley Francis
- 9 years ago
- Views:
Transcription
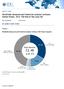
1 Market Share Worldwide Specialized Threat Analysis and Protection Market Shares, 2014: Rapidly Evolving Security Defenses Robert Westervelt Rob Ayoub Pete Lindstrom Elizabeth Corr IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Specialized Threat Analysis and Protection 2014 Share Snapshot Note: 2014 Share (%), Growth (%), and Revenue ($M) Source: IDC, 2015 October 2015, IDC #259667
2 EXECUTIVE SUMMARY The specialized threat analysis and protection (STAP) market continued to gain traction in 2014 with widespread adoption of SaaS and on-premises sandboxes and a renewed focus on emerging endpoint security technologies. Organizations are also increasingly evaluating network inspection solutions designed to detect attacker movement to sensitive resources. Significant STAP trends are: Vendors converting proof of concepts (POCs). Security vendors converted a significant number of STAP proof of concepts in IDC estimates that the market in 2014 had revenue of $930 million. It is forecast to grow to over $3 billion by 2019, with a total market CAGR of 27.6%. Identifying attacker movement. High-profile attacks, data breaches, and critical vulnerabilities in 2013 and 2014 drove interest in NetFlow and other products designed to detect lateral movement within a corporate network. FireEye, Lancope, IBM, and Bit9-Carbon Black were the top 4 security vendors selling STAP solutions in Calling for incident response (IR) support. Early adopters of STAP solutions sought incident response expertise, increasing demand for digital forensics specialists, data breach support, and other professional services. Vendors responded by adding or bolstering their services offerings in IDC believes that emerging endpoint solutions designed to detect advanced threats will gain momentum. Vendors are combining monitoring with behavioral analytics with other non-signaturebased detection capabilities to identify zero days. There is some evidence that end customers are beginning to shed standard antivirus in favor of some endpoint STAP solutions. The STAP market will continue to evolve with established security vendors adding STAP features to their portfolio organically or acquiring emerging STAP solutions. In 2014, Palo Alto Networks acquired Israeli start-up Cyvera for an estimated $200 million and, later in the year, introduced Traps, a STAP endpoint product that integrates with its WildFire file sandboxing service. Cisco Systems acquired ThreatGRID, adding suspicious file analysis sandboxing capabilities to its portfolio. FireEye further built out its portfolio with the acquisition of npulse Technologies to support forensics and threat remediation activities. This IDC study examines the competitive market for this specialized security technology. It aims to identify the market leaders and significant trends that will impact the broader market for security products and services. Security vendor products that fit into the STAP market must be sold as a dedicated product and purchased from customers to specifically address the problem of identifying custom malware. "The specialized threat analysis and protection market is rapidly evolving, with established vendors adding STAP offerings that compete against a growing cadre of security start-ups. The innovative security technologies in this market modernize many of the outdated approaches that attackers are easily bypassing today. Organizations are showing significant interest and adoption of STAP products to address the growing need for advanced threat detection." Robert Westervelt, research manager, Security Products, IDC 2015 IDC #
3 ADVICE FOR TECHNOLOGY SUPPLIERS The specialized threat analysis and protection market continues to be challenging for vendors, buyers, and sales channel resellers. The competitive market continues to evolve with STAP security products often overlapping a variety of adjacent security technology areas. Security vendor products that fit into the STAP market must be sold as a dedicated product and purchased from customers to specifically address the problem of identifying custom malware, sophisticated attack techniques, and other activity associated with advanced persistent threats. The products must not be signature based. Buyers are seeking to bolster their existing security infrastructure by making an investment in products designed to detect advanced threats from each of the three STAP submarkets: endpoint, boundary, and internal network analysis. Some vendor solutions provide functionality from each of the submarkets, integrating emulation products designed to analyze suspicious files with behavioral analysis to identify function calls and suspicious file activity on the endpoint, and network analysis to detect attacker reconnaissance activity and lateral movement within the network. Endpoint STAP products use behavioral analysis of memory and application operations. It primarily consists of an agent or sensor on devices that monitor system processes and files for signs of anomalous behavior or attempt to prevent suspicious files from executing. IDC anticipates future consolidation of the endpoint STAP submarket, with traditional endpoint security vendors adding STAP endpoint capabilities to their platforms. Boundary STAP products consist mainly of virtual sandboxing/emulation and behavioral analysis technologies. These safe zones are used to detonate and monitor the behavior of suspicious files, which are designed to evade signature-based defenses. Buyers have increasingly purchased SaaSbased sandboxing services, but on-premises and hybrid deployments are also common with enterprise customers. Internal network analysis STAP products monitor network flow to detect indications of attacker reconnaissance activity, malware movement, and botnet or malware command and control activity. Products should be equipped to help responders pinpoint endpoint infections and interrupt command and control communication provide context to incident responders. The strongest STAP solutions appear to come from vendors that have created strong technology partnerships, and IDC has determined that a security vendor's technology partner ecosystem is being examined thoroughly in product evaluations. To remain competitive, security vendors should also consider the following recommendations: Strike key differentiators: Product evaluations are becoming a significant challenge for buyers planning to adopt STAP technology. Channel resellers are also strained when attempting to determine if a STAP product can fit in their portfolio without conflicting with top-tier technology partners. Make clear all differentiating management features and capabilities against competitive solutions. Expand deployment options: A key buying requirement is the ability to integrate products with existing security infrastructure. This requirement may result in the need for full SaaS, onpremises, or a mixture of SaaS and on-premises solutions. While usability and effortless deployment are advantageous, buyers are also choosing STAP solutions with flexible deployment models IDC #
4 Create services offerings: An analysis of early adopter buying behaviors found that vendor services offerings are not a primary buying requirement; however, a second inquiry with customers identified a significant need for follow-up services engagements. The services requirement was prompted by a lack of routine maintenance, deficient incident response processes, and poorly configured deployments. Develop risk scoring models: Buying trends suggest the addition of a configurable risk scoring methodology to assist responders in prioritizing alerts captures the attention of C-suite executives during sales engagements. Despite the growing number of risk-based scoring capabilities incorporated into security products, STAP vendors can use risk scoring as a product differentiator. It could also foster the comfort level required to prompt organizations to embrace automated response and remediation features. MARKET SHARE The worldwide STAP security market rose to $930 million in 2014, an increase of 126.3% from FireEye remains the STAP market leader, with 37.9% share of the market in It saw its share of the market decline 5.2% based on additional market entrants and widespread availability of competing sandboxing solutions. A notable competitor is Palo Alto Networks and the rapid adoption of its subscription-based WildFire sandboxing service in Table 1 displays worldwide revenue and market share for the STAP security market. Tables 2 4 display 2014 revenue and market shares for the top vendors in each submarket. STAP boundary is the largest market segment, with FireEye continuing to be the sole dominating vendor. Sandboxing technologies have quickly come to market from network security competitors and security start-ups. Boundary STAP includes products from Check Point, Cyphort, iboss, Fortinet, Intel Security, Proofpoint, Symantec, and others. It also includes a share of sandboxing components that exist within standalone vendor advanced threat defense solutions (see Table 3). STAP endpoint is the fastest-growing market segment and one that is quickly evolving as endpoint security vendors, including Symantec and Intel Security, add endpoint advanced threat detection capabilities to their platforms to meet their established customer requirements. Lancope has gained significant adoption of its advanced threat detection solution, leveraging its close relationship with Cisco Systems. RSA and Blue Coat are each transforming their network packet capturing appliances, which had been focused for digital forensics investigations, into breach detection and analysis platforms (see Table 4) IDC #
5 TABLE 1 Worldwide Specialized Threat Analysis and Protection Revenue by Segment, ($M) CAGR (%) Boundary , , , , , Endpoint Internal network analysis Total , , , , , Source: IDC, 2015 TABLE 2 Worldwide Specialized Threat Analysis and Protection Revenue of Boundary Segment by Vendor, 2014 Revenue ($M) FireEye 353 AhnLab 25 Trend Micro 25 Cisco 25 Fidelis 23 Websense 23 IBM 20 Lastline 20 Palo Alto Networks 17 Other Source: IDC, IDC #
6 TABLE 3 Worldwide Specialized Threat Analysis and Protection Revenue of Endpoint Segment by Vendor, 2014 Revenue ($M) Bit9-CB 38.0 Cylance 13.0 Bromium 13.0 CrowdStrike 12.0 Invincea 12.0 Other 13.8 Source: IDC, 2015 TABLE 4 Worldwide Specialized Threat Analysis and Protection Revenue of Internal Network Analysis Segment by Vendor, 2014 Revenue ($M) Lancope 50.0 IBM 15.0 Damballa 15.0 Blue Coat 13.0 RSA 13.0 Other 12.4 Source: IDC, IDC #
7 WHO SHAPED THE YEAR Bit9 acquired Carbon Black at the beginning of 2014 and was able to highlight the effectiveness of its modern whitelisting approach with Carbon Black's endpoint forensics capabilities. Carbon Black had been tremendously successful with its approach prior to the acquisition gaining adoption with SOC personnel and incident response teams for its ability to take a complete inventory of every file on an endpoint system and monitor for system changes. The acquisition shifted attention on ways organizations can modernize their endpoint security solutions. FireEye gained attention with the launch of its Endpoint Security (HX Series) appliance in This product uses Mandiant's proprietary technology for incident responders to monitor endpoints for threat indicators and alert the security operations center team about possible compromised endpoints. Engineers are working on embedding Mandiant's MIR functionality into the HX Series, enabling responders to rapidly investigate potential threats. The appliance can be purchased separately or be integrated with the FireEye NX Series appliances. Palo Alto Networks acquired Morta and Cyvera in 2014 to add endpoint visibility to its portfolio. The resulting endpoint STAP product called Traps is designed to block attacker exploitation techniques. Traps integrates with WildFire, Palo Alto's SaaS-based sandboxing service. Cisco Systems acquired ThreatGRID, adding a sandbox for cloud-based suspicious file analysis. The company also showed progress in extending the Advanced Malware Protection component of its Sourcefire acquisition as an add-on to its ASA UTM appliances. Lancope leveraged its existing partnership with Cisco Systems to gain traction in the STAP market with its StealthWatch System for advanced threat detection. Lancope competes against other vendors in the internal network analysis submarket, which is designed to identify lateral movement within tracking network reconnaissance, internal malware propagation, command and control traffic, and data exfiltration. A Note on Symantec and Intel Security Intel Security is making gains with its Advanced Threat Defense offering, which consists of a standalone appliance, designed to integrate with other products in its portfolio. Intel Security uses a local blacklist to detect known malware and a virtual sandbox environment for suspicious file analysis. It connects to Intel Security's cloud-based Global Threat Intelligence for further protection. Symantec announced that it would split into separate security and information management businesses in The company also announced plans to invest in its portfolio of security products and enter the STAP market with an Advanced Threat Protection product that integrates its existing , networking, and endpoint solutions with file inspection technology called Symantec Cynic, a cloud-based sandbox environment for file inspection. Symantec also leverages a technology it calls Synapse to correlate event information between the network, endpoints, and to provide context to alerts for incident responders. MARKET CONTEXT The STAP market gained considerable traction in 2014 as end users increased security spending to stem the ever-increasing number of data breaches. The Target breach in particular raised the stakes for security accountability as the CEO was forced to resign in part as a result of the massive data 2015 IDC #
8 breach. STAP products are representing the first significant shift in the security stack in some time, and IDC predicts that organizations will continue to deploy these products either through on-premises devices, through endpoint clients, or via the cloud. The three STAP subsegments that IDC is tracking boundary, internal network, and endpoint have strong enterprise interest and adoption. However, these reasons vary based on each segment: Boundary. The interest in boundary devices has been prompted primarily by the success of FireEye and others to deliver sandboxing and other identification techniques on the network. Many security administrators are very comfortable with adding security devices to the network and as a result these devices fit easily into the day-to-day security operations function. Internal network. Internal network STAP products are primarily focused on botnet detection and determining if malware has infected the network. Instead of trying to evaluate the traffic flowing through the network boundaries, internal network STAP products rely on user behavior, flow traffic, and DNS traffic to determine whether there is malicious behavior on the network. One key advantage touted by internal network STAP products over boundary products is a reduction in the amount of false positives. Endpoint. Endpoint STAP products are being heralded as the next generation of endpoint security. As enterprises have become more disillusioned with legacy endpoint security products, the interest in solutions that are faster and more accurate has increased. Endpoint STAP vendors are approaching endpoint security using a wide variety of methods to improve the detection and prevention capabilities of malware on the endpoint. Other endpoint STAP products are more focused on analytics collection and visibility into the endpoint and then coordinate that data with network-based products. IDC does not believe that any single approach or product will solve an organization's security challenges, but by using a combination of STAP products with traditional security products, that many blind spots can be eliminated. Significant Market Developments Security vendor FireEye's continued success has resulted in an influx of advanced threat defense offerings that use virtual sandboxes to analyze suspicious files and identify advanced threats. The solutions, which first appealed to large enterprises, have experienced growth by capturing a broader segment of the market, which quickly embraced cloud-based sandboxing services. A variety of pureplay vendors with sandboxing offerings continue to make the boundary submarket extremely large compared with endpoint and internal network analysis. Bit9's acquisition of Carbon Black has helped fuel interest in modernizing endpoint defenses, which have been relying heavily on signature-based technology to detect malware. New concepts are being introduced that incorporate endpoint agent or sensor technology to increase visibility and give incident responders more context into alerts and control over infected systems. Endpoint STAP is rapidly evolving. The attention given to pure-play vendors has prompted established security vendors to add similar specialized threat analysis and protection capabilities. The root of many of these emerging technologies is in host-based intrusion prevention and digital forensics capabilities that identify threats in underlying system memory, abnormal application function calls, and other signs of unusual system behavior. IDC is aware of AccessData, FireEye MIR, Guidance Software Encase, RSA ECAT, and other forensics tools that help responders gain visibility while investigating the scope of an infection. IDC 2015 IDC #
9 analysts examine these products closely to determine whether there is real-time monitoring and alerting capabilities and the customer requirements and use cases that the products fulfill. METHODOLOGY This IDC software market sizing and forecast is presented in terms of packaged software and appliance revenue. IDC uses the term packaged software to distinguish commercially available software from custom software, not to imply that the software must be shrink-wrapped or otherwise provided via physical media. Packaged software is programs or codesets of any type commercially available through sale, lease, or rental, or as a service. Packaged software revenue typically includes fees for initial and continued right-to-use packaged software licenses. These fees may include, as part of the license contract, access to product support and/or other services that are inseparable from the right-to-use license fee structure, or this support may be priced separately. Upgrades may be included in the continuing right of use or may be priced separately. All of these are counted by IDC as packaged software revenue. Appliances are defined as a combination of hardware, operating environment, and application software where they are provided as a single product. Packaged software revenue excludes service revenue derived from training, consulting, and systems integration that is separate (or unbundled) from the right-to-use license but does include the implicit value of the product included in a service that offers software functionality by a different pricing scheme. It is the total product revenue that is further allocated to markets, geographic areas, and operating environments. The market forecast and analysis methodology incorporates information from five different but interrelated sources, as follows: Reported and observed trends and financial activity. This study incorporates reported and observed trends and financial activity in 2014 as of the end of September IDC's Software Census interviews. IDC interviews all significant market participants to determine product revenue, revenue demographics, pricing, and other relevant information. Product briefings, press releases, and other publicly available information. IDC's software analysts around the world meet with hundreds of software vendors each year. These briefings provide an opportunity to review current and future business and product strategies, revenue, shipments, customer bases, target markets, and other key product and competitive information. Vendor financial statements and related filings. Although many software vendors are privately held and choose to limit financial disclosures, information from publicly held companies provides a significant benchmark for assessing informal market estimates from private companies. IDC also builds detailed information related to private companies through in-depth analyst relationships and maintains an extensive library of financial and corporate information focused on the IT industry. We further maintain detailed revenue by product area models on more than 1,000 worldwide vendors. IDC demand-side research. This includes thousands of interviews with business users of software solutions annually and provides a powerful fifth perspective for assessing competitive performance and market dynamics. IDC's user strategy databases offer a compelling and consistent time-series view of industry trends and developments. Direct conversations with technology buyers provide an invaluable complement to the broader survey-based results IDC #
10 Ultimately, the data presented in this study represents IDC's best estimates based on these data sources as well as reported and observed activity by vendors and further modeling of data that we believe to be true to fill in any information gaps. The data in this study is derived from all these sources and entered into IDC's Software Market Forecaster database, which is then updated on a continuous basis as new information regarding software vendor revenue becomes available. Note: All numbers in this document may not be exact due to rounding. MARKET DEFINITION The specialized threat analysis and protection market overlaps the endpoint, messaging, network, and Web functional markets. The products help protect enterprises from new malware attacks that cannot be detected by traditional signature-based techniques. The STAP products use a variety of nonsignature-based protection methods including, but not limited to, sandboxing, behavioral analysis, file integrity monitoring, telemetric heuristics, containerization, netflow analysis, and threat intelligence, which can detect a malware attack or compromise by identifying attacker activity or subtle system process changes. Some of the products only detect and alert, while others may contain malware to prevent it from causing damage. Although these features may appear in other products, this category is only for dedicated STAP solutions. The STAP market is made up of distinguishable products as opposed to embedded features within a product. The ability to find and prevent advanced malware ultimately requires dedicated activities, and in this way, it is possible to measure the extent that enterprises are consciously taking actions to deal with advanced malware. The STAP market is a competitive market that overlaps other logical security products markets (e.g., IAM, network, endpoint, messaging, Web, SVM, and "other" security products). The STAP market must be reported separately and, furthermore, not added to the seven logical security products markets, otherwise the total security products market figure will be incorrect. RELATED RESEARCH IDC's Forecast Scenario Assumptions for the ICT Markets and Historical Market Values and Exchange Rates, Version 3, 2015 (IDC #259115, September 2015) Worldwide Specialized Threat Analysis and Protection Forecast, : Defending Against the Unknown (IDC #256354, May 2015) Market Analysis Perspective: Worldwide Security Products, 2014 (IDC #252908, December 2014) Worldwide IT Security Products Forecast and 2013 Vendor Shares: Comprehensive Security Product Review (IDC #253371, December 2014) IDC's Worldwide Security Products Taxonomy, 2014 (IDC #250802, September 2014) Worldwide Specialized Threat Analysis and Protection Forecast and 2012 Vendor Shares (IDC #242346, August 2013) 2015 IDC #
11 About IDC International Data Corporation (IDC) is the premier global provider of market intelligence, advisory services, and events for the information technology, telecommunications and consumer technology markets. IDC helps IT professionals, business executives, and the investment community make factbased decisions on technology purchases and business strategy. More than 1,100 IDC analysts provide global, regional, and local expertise on technology and industry opportunities and trends in over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology media, research, and events company. Global Headquarters 5 Speen Street Framingham, MA USA idc-insights-community.com Copyright Notice This IDC research document was published as part of an IDC continuous intelligence service, providing written research, analyst interactions, telebriefings, and conferences. Visit to learn more about IDC subscription and consulting services. To view a list of IDC offices worldwide, visit Please contact the IDC Hotline at , ext (or ) or [email protected] for information on applying the price of this document toward the purchase of an IDC service or for information on additional copies or Web rights. [trademark] Copyright 2015 IDC. Reproduction is forbidden unless authorized. All rights reserved.
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T W o r l d w i d e W e b S e c u r i t y 2 0 1 1-2 0 1 5 F o r e c a s t a n d 2 0 1
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T W o r l d w i d e W e b S e c u r i t y 2 0 1 1-2 0 1 5 F o r e c a s t a n d 2 0 1
Worldwide Problem Management Software Market Shares, 2014: 3rd Platform Technologies and Delivery Models Drive Growth
 MARKET SHARE Worldwide Problem Management Software Market Shares, 2014: 3rd Platform Technologies and Delivery Models Drive Growth Robert Young IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Problem Management
MARKET SHARE Worldwide Problem Management Software Market Shares, 2014: 3rd Platform Technologies and Delivery Models Drive Growth Robert Young IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Problem Management
Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail
 MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
Worldwide Datacenter Automation Software Market Shares, 2014: Year of Cloud and DevOps
 MARKET SHARE Worldwide Datacenter Automation Software Market Shares, 2014: Year of Cloud and DevOps Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Datacenter Automation Software 2014 Share
MARKET SHARE Worldwide Datacenter Automation Software Market Shares, 2014: Year of Cloud and DevOps Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Datacenter Automation Software 2014 Share
Worldwide Business Rules Management Systems 2011 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Business Rules Management Systems 2011 Vendor Shares Al Hilwa Stephen D. Hendrick IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200
COMPETITIVE ANALYSIS Worldwide Business Rules Management Systems 2011 Vendor Shares Al Hilwa Stephen D. Hendrick IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200
Worldwide Security and Vulnerability Management Market Shares, 2014: The Need for Improved Incident Response Driving Higher Growth Across the Market
 MARKET SHARE Worldwide Security and Vulnerability Management Market Shares, 2014: The Need for Improved Incident Response Driving Higher Growth Across the Market Robert Ayoub Elizabeth Corr Christian A.
MARKET SHARE Worldwide Security and Vulnerability Management Market Shares, 2014: The Need for Improved Incident Response Driving Higher Growth Across the Market Robert Ayoub Elizabeth Corr Christian A.
Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares
 Market Analysis Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares Charles J. Kolodgy IN THIS EXCERPT The content for this excerpt was taken directly from IDC Market
Market Analysis Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares Charles J. Kolodgy IN THIS EXCERPT The content for this excerpt was taken directly from IDC Market
Worldwide Cloud Systems Management Software 2013 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide cloud systems management software competitive market showed very
COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide cloud systems management software competitive market showed very
Worldwide Workload Management Software 2013 Vendor Shares
 EXCERPT Worldwide Workload Management Software 2013 Vendor Shares Mary Johnston Turner IN THIS EXCERPT The content for this paper is excerpted from the IDC Competitive Analysis Report, Worldwide Workload
EXCERPT Worldwide Workload Management Software 2013 Vendor Shares Mary Johnston Turner IN THIS EXCERPT The content for this paper is excerpted from the IDC Competitive Analysis Report, Worldwide Workload
Worldwide Datacenter Automation Software 2013 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
COMPETITIVE ANALYSIS Worldwide Datacenter Automation Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide datacenter automation software submarket of the workload scheduling
Sluggish Incident Response: Next-Generation Security Problems and Solutions
 CUSTOMER NEEDS AND STRATEGIES Sluggish Incident Response: Next-Generation Security Problems and Solutions Christian A. Christiansen Christina Richmond Robert Westervelt IDC OPINION The rush to adopt technologies
CUSTOMER NEEDS AND STRATEGIES Sluggish Incident Response: Next-Generation Security Problems and Solutions Christian A. Christiansen Christina Richmond Robert Westervelt IDC OPINION The rush to adopt technologies
COMPETITIVE ANALYSIS. Worldwide RDBMS 2006 Vendor Shares: Preliminary Results for the Top 5 Vendors IDC OPINION. Carl W. Olofson
 COMPETITIVE ANALYSIS Worldwide RDBMS 2006 Vendor Shares: Preliminary Results for the Top 5 Vendors Carl W. Olofson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200
COMPETITIVE ANALYSIS Worldwide RDBMS 2006 Vendor Shares: Preliminary Results for the Top 5 Vendors Carl W. Olofson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200
The Cyber Threat Landscape
 The Cyber Threat Landscape Oliver Rochford Research Director Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without
The Cyber Threat Landscape Oliver Rochford Research Director Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without
Worldwide Security and Vulnerability Management 2009 2013 Forecast and 2008 Vendor Shares
 EXCERPT Worldwide Security and Vulnerability Management 2009 2013 Forecast and 2008 Vendor Shares IN THIS EXCERPT Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
EXCERPT Worldwide Security and Vulnerability Management 2009 2013 Forecast and 2008 Vendor Shares IN THIS EXCERPT Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES EMERSON NETWORK POWER IDC MARKETSCAPE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Datacenter Infrastructure Management 2015 Vendor Assessment Jennifer Koppy THIS IDC MARKETSCAPE EXCERPT FEATURES EMERSON NETWORK POWER IDC MARKETSCAPE FIGURE
IDC MarketScape: Worldwide Cloud Professional Services 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2016 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: NTT DATA IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Cloud Professional Services 2016 Vendor Assessment Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: NTT DATA IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Worldwide Application Performance Management Software 2012 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Application Performance Management Software 2012 Vendor Shares Mary Johnston Turner Tim Grieser Melinda-Carol Ballou Rohit Mehra IDC OPINION Global Headquarters: 5 Speen
COMPETITIVE ANALYSIS Worldwide Application Performance Management Software 2012 Vendor Shares Mary Johnston Turner Tim Grieser Melinda-Carol Ballou Rohit Mehra IDC OPINION Global Headquarters: 5 Speen
Worldwide Datacenter Automation Software Market Shares, 2015: Year of Suite Success
 Market Share Worldwide Datacenter Automation Software Market Shares, 2015: Year of Suite Success Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Datacenter Automation Software 2015 Share
Market Share Worldwide Datacenter Automation Software Market Shares, 2015: Year of Suite Success Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Datacenter Automation Software 2015 Share
Worldwide Application Performance Management Software 2013 Vendor Shares
 Competitive Analysis Worldwide Application Performance Management Software 2013 Vendor Shares Melinda-Carol Ballou Rohit Mehra Tim Grieser Mary Johnston Turner IDC OPINION The worldwide application performance
Competitive Analysis Worldwide Application Performance Management Software 2013 Vendor Shares Melinda-Carol Ballou Rohit Mehra Tim Grieser Mary Johnston Turner IDC OPINION The worldwide application performance
Market Guide for Network Sandboxing
 G00271317 Market Guide for Network Sandboxing Published: 2 March 2015 Analyst(s): Lawrence Orans, Jeremy D'Hoinne Choosing a network sandboxing solution is challenging due to the wide array of options
G00271317 Market Guide for Network Sandboxing Published: 2 March 2015 Analyst(s): Lawrence Orans, Jeremy D'Hoinne Choosing a network sandboxing solution is challenging due to the wide array of options
Worldwide Cloud Systems Management Software 2012 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2012 Vendor Shares Mary Johnston Turner IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2012 Vendor Shares Mary Johnston Turner IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
I D C M a r k e t S c a p e : W o r l d w i d e M e s s a g i n g S e c u r i t y 2 0 1 3 2 0 1 4 V e n d o r A s s e s s m e n t
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e M e s s a g
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e M e s s a g
I D C A N A L Y S T C O N N E C T I O N
 I D C A N A L Y S T C O N N E C T I O N Robert Westervelt Research Manager, Security Products T h e R o l e a nd Value of Continuous Security M o nitoring August 2015 Continuous security monitoring (CSM)
I D C A N A L Y S T C O N N E C T I O N Robert Westervelt Research Manager, Security Products T h e R o l e a nd Value of Continuous Security M o nitoring August 2015 Continuous security monitoring (CSM)
Converged and Integrated Datacenter Systems: Creating Operational Efficiencies
 Insight Converged and Integrated Datacenter Systems: Creating Operational Efficiencies Rob Brothers IDC OPINION Enterprise IT has moved away from siloed servers, storage, information, and processes and
Insight Converged and Integrated Datacenter Systems: Creating Operational Efficiencies Rob Brothers IDC OPINION Enterprise IT has moved away from siloed servers, storage, information, and processes and
Worldwide Cloud Systems Management Software Market Shares, 2015: Year of Continued Expansion
 Market Share Worldwide Cloud Systems Management Software Market Shares, 2015: Year of Continued Expansion Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Cloud Systems Management Software
Market Share Worldwide Cloud Systems Management Software Market Shares, 2015: Year of Continued Expansion Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Cloud Systems Management Software
IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: SERVICENOW IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: SERVICENOW IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
Worldwide DDI Market Update
 Update Worldwide DDI Market Update Nolan Greene Petr Jirovsky IN THIS UPDATE This IDC update reviews the revenue and shipments of the worldwide DDI (DNS, DHCP, and IP address management [IPAM]) solutions
Update Worldwide DDI Market Update Nolan Greene Petr Jirovsky IN THIS UPDATE This IDC update reviews the revenue and shipments of the worldwide DDI (DNS, DHCP, and IP address management [IPAM]) solutions
Cirba Targets Software-Defined Infrastructure Control with Workload-Aware Predictive Analytics
 Vendor Profile Cirba Targets Software-Defined Infrastructure Control with Workload-Aware Predictive Analytics Mary Johnston Turner David Immerman IDC OPINION Software-defined infrastructure (SDI) enables
Vendor Profile Cirba Targets Software-Defined Infrastructure Control with Workload-Aware Predictive Analytics Mary Johnston Turner David Immerman IDC OPINION Software-defined infrastructure (SDI) enables
Worldwide Managed File Transfer Software 2013 Vendor Shares
 Competitive Analysis Worldwide Managed File Transfer Software 2013 Vendor Shares Chandana Gopal IDC OPINION Managed file transfer (MFT) software posted 5.1% growth in 2013 to $794.3 million. The Americas
Competitive Analysis Worldwide Managed File Transfer Software 2013 Vendor Shares Chandana Gopal IDC OPINION Managed file transfer (MFT) software posted 5.1% growth in 2013 to $794.3 million. The Americas
COMPETITIVE ANALYSIS. Worldwide Business Intelligence Tools 2010 Vendor Shares IDC OPINION. Dan Vesset
 COMPETITIVE ANALYSIS Worldwide Business Intelligence Tools 2010 Vendor Shares Dan Vesset IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
COMPETITIVE ANALYSIS Worldwide Business Intelligence Tools 2010 Vendor Shares Dan Vesset IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis
 IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: CHERWELL SOFTWARE IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Service Desk Management Software 2014 Vendor Analysis Robert Young THIS IDC MARKETSCAPE EXCERPT FEATURES: CHERWELL SOFTWARE IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Symantec Advanced Threat Protection: Network
 Symantec Advanced Threat Protection: Network DR150218C April 2015 Miercom www.miercom.com Contents 1.0 Executive Summary... 3 2.0 Overview... 4 2.1 Products Tested... 4 2.2. Malware Samples... 5 3.0 How
Symantec Advanced Threat Protection: Network DR150218C April 2015 Miercom www.miercom.com Contents 1.0 Executive Summary... 3 2.0 Overview... 4 2.1 Products Tested... 4 2.2. Malware Samples... 5 3.0 How
IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era
 Customer Needs and Strategies IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era Mary Johnston Turner IDC OPINION IT as a service (ITaaS) represents a fundamentally
Customer Needs and Strategies IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era Mary Johnston Turner IDC OPINION IT as a service (ITaaS) represents a fundamentally
ScienceLogic Offers Unified Infrastructure Monitoring and Analytics for Hybrid IT
 VENDOR PROFILE ScienceLogic Offers Unified Infrastructure Monitoring and Analytics for Hybrid IT Mary Johnston Turner David Immerman IDC OPINION Enterprise datacenter infrastructure environments are becoming
VENDOR PROFILE ScienceLogic Offers Unified Infrastructure Monitoring and Analytics for Hybrid IT Mary Johnston Turner David Immerman IDC OPINION Enterprise datacenter infrastructure environments are becoming
Worldwide Relational Database Management Systems 2007 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Relational Database Management Systems 2007 Vendor Shares Carl W. Olofson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
COMPETITIVE ANALYSIS Worldwide Relational Database Management Systems 2007 Vendor Shares Carl W. Olofson IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production
 Buyer Case Study SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production Brian McDonough IDC OPINION The goal of decision
Buyer Case Study SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production Brian McDonough IDC OPINION The goal of decision
Worldwide Cloud Systems Management Software Market Shares, 2014: Year of Hybrid Cloud
 MARKET SHARE Worldwide Cloud Systems Management Software Market Shares, 2014: Year of Hybrid Cloud Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Cloud Systems Management Software 2014
MARKET SHARE Worldwide Cloud Systems Management Software Market Shares, 2014: Year of Hybrid Cloud Mary Johnston Turner IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Cloud Systems Management Software 2014
Cisco Advanced Malware Protection for Endpoints
 Data Sheet Cisco Advanced Malware Protection for Endpoints Product Overview With today s sophisticated malware, you have to protect endpoints before, during, and after attacks. Cisco Advanced Malware Protection
Data Sheet Cisco Advanced Malware Protection for Endpoints Product Overview With today s sophisticated malware, you have to protect endpoints before, during, and after attacks. Cisco Advanced Malware Protection
IDC MarketScape: Worldwide Big Data Consulting and Systems Integration Services 2016 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Big Data Consulting and Systems Integration Services 2016 Vendor Assessment Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES HCL IDC MARKETSCAPE FIGURE FIGURE
IDC MarketScape IDC MarketScape: Worldwide Big Data Consulting and Systems Integration Services 2016 Vendor Assessment Ali Zaidi THIS IDC MARKETSCAPE EXCERPT FEATURES HCL IDC MARKETSCAPE FIGURE FIGURE
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E XCERPT M A R K E T A N A L Y S I S W o r l d w i d e S e c u r i t y a n d V u l n e r a b i l i
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E XCERPT M A R K E T A N A L Y S I S W o r l d w i d e S e c u r i t y a n d V u l n e r a b i l i
IDC MarketScape Excerpt: Worldwide HR BPO 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape Excerpt: Worldwide HR BPO 2014 Vendor Assessment Lisa Rowan THIS IDC MARKETSCAPE EXCERPT FEATURES: ADP IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape HR Business Process
IDC MarketScape IDC MarketScape Excerpt: Worldwide HR BPO 2014 Vendor Assessment Lisa Rowan THIS IDC MARKETSCAPE EXCERPT FEATURES: ADP IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape HR Business Process
Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research
 INSIGHT Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research David Schubmehl IDC OPINION Organizations are looking for better ways to perform
INSIGHT Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research David Schubmehl IDC OPINION Organizations are looking for better ways to perform
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE
 IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
IMPLEMENTING A SECURITY ANALYTICS ARCHITECTURE Solution Brief SUMMARY New security threats demand a new approach to security management. Security teams need a security analytics architecture that can handle
Carbon Black and Palo Alto Networks
 Carbon Black and Palo Alto Networks Bring Together Next-Generation Endpoint and Network Security Solutions Endpoints and Servers in the Crosshairs of According to a 2013 study, 70 percent of businesses
Carbon Black and Palo Alto Networks Bring Together Next-Generation Endpoint and Network Security Solutions Endpoints and Servers in the Crosshairs of According to a 2013 study, 70 percent of businesses
IDC MarketScape: Worldwide Supply Chain Management Business Consulting Services 2014 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Supply Chain Management Business Consulting Services 2014 Vendor Assessment Cushing Anderson Simon Ellis THIS IDC MARKETSCAPE EXCERPT FEATURES EY IDC MARKETSCAPE
IDC MARKETSCAPE IDC MarketScape: Worldwide Supply Chain Management Business Consulting Services 2014 Vendor Assessment Cushing Anderson Simon Ellis THIS IDC MARKETSCAPE EXCERPT FEATURES EY IDC MARKETSCAPE
2014 Human Capital Management Survey: HCM Buyer Actions and Plans
 Survey 2014 Human Capital Management Survey: HCM Buyer Actions and Plans Lisa Rowan IDC OPINION This study provides human capital management (HCM) applications buying behavior findings drawn from an IDC
Survey 2014 Human Capital Management Survey: HCM Buyer Actions and Plans Lisa Rowan IDC OPINION This study provides human capital management (HCM) applications buying behavior findings drawn from an IDC
IDC MarketScape: Worldwide Business Consulting Strategy for Digital Operations 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Business Consulting Strategy for Digital Operations 2015 Vendor Assessment Michael Versace Cushing Anderson THIS IDC MARKETSCAPE EXCERPT FEATURES KPMG IDC MARKETSCAPE
IDC MarketScape IDC MarketScape: Worldwide Business Consulting Strategy for Digital Operations 2015 Vendor Assessment Michael Versace Cushing Anderson THIS IDC MARKETSCAPE EXCERPT FEATURES KPMG IDC MARKETSCAPE
IDC MarketScape: Worldwide Oracle Implementation Services Ecosystem 2014 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Oracle Implementation Services Ecosystem 2014 Vendor Assessment Ali Zaidi Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE
IDC MARKETSCAPE IDC MarketScape: Worldwide Oracle Implementation Services Ecosystem 2014 Vendor Assessment Ali Zaidi Gard Little Chad Huston THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE
IDC MarketScape: Worldwide Digital Enterprise Strategy Consulting Services 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Digital Enterprise Strategy Consulting Services 2015 Vendor Assessment Cushing Anderson Mette Ahorlu THIS IDC MARKETSCAPE EXCERPT FEATURES PWC IDC MARKETSCAPE
IDC MarketScape IDC MarketScape: Worldwide Digital Enterprise Strategy Consulting Services 2015 Vendor Assessment Cushing Anderson Mette Ahorlu THIS IDC MARKETSCAPE EXCERPT FEATURES PWC IDC MARKETSCAPE
Worldwide Business Analytics Software Market Shares, 2014: Line of Business Drives Cloud and Visual Discovery Adoption
 MARKET SHARE Worldwide Business Analytics Software Market Shares, 2014: Line of Business Drives Cloud and Visual Discovery Adoption Dan Vesset David Schubmehl Alys Woodward Brian McDonough Carl W. Olofson
MARKET SHARE Worldwide Business Analytics Software Market Shares, 2014: Line of Business Drives Cloud and Visual Discovery Adoption Dan Vesset David Schubmehl Alys Woodward Brian McDonough Carl W. Olofson
Assessing the Business Value of the Secured Datacenter
 IDC SOLUTION BRIEF Assessing the Business Value of the Secured Datacenter Sponsored by: Cisco Pete Lindstrom Matthew Marden December 2014 Richard L. Villars OVERVIEW The world of IT is in the midst of
IDC SOLUTION BRIEF Assessing the Business Value of the Secured Datacenter Sponsored by: Cisco Pete Lindstrom Matthew Marden December 2014 Richard L. Villars OVERVIEW The world of IT is in the midst of
Understanding the Business Value of Migrating to Windows Server 2012
 WHITE PAPER Understanding the Business Value of Migrating to Windows Server 2012 Sponsored by: Microsoft and Intel Simon Piff February 2015 EXECUTIVE SUMMARY In December 2014, IDC Asia/Pacific undertook
WHITE PAPER Understanding the Business Value of Migrating to Windows Server 2012 Sponsored by: Microsoft and Intel Simon Piff February 2015 EXECUTIVE SUMMARY In December 2014, IDC Asia/Pacific undertook
IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment Jill Feblowitz THIS IDC MARKETSCAPE EXCERPT FEATURES: TIETO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MARKETSCAPE IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment Jill Feblowitz THIS IDC MARKETSCAPE EXCERPT FEATURES: TIETO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
How To Understand Cloud Economics
 WHITE PAPER Cloud Economics: A Financial Analysis of Information Management IT Delivery Models Sponsored by: Viewpointe LLC Michael Versace October 2013 Randy Perry IDC OPINION Executive Summary Cost optimization
WHITE PAPER Cloud Economics: A Financial Analysis of Information Management IT Delivery Models Sponsored by: Viewpointe LLC Michael Versace October 2013 Randy Perry IDC OPINION Executive Summary Cost optimization
DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified
 Insight DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified Stephen Elliot IDC OPINION Based on a research survey conducted during October and November of 2014 across multiple
Insight DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified Stephen Elliot IDC OPINION Based on a research survey conducted during October and November of 2014 across multiple
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 B U Y E R C A S E S T U D Y U. S. B a n k i n g I n s t i t u t i o n I m p l e m e n t s V a r o n i s t o G a i n C o n t r o l o f U n s t r u c t u r e d F i l e S e r v e r D a t a Laura DuBois I
B U Y E R C A S E S T U D Y U. S. B a n k i n g I n s t i t u t i o n I m p l e m e n t s V a r o n i s t o G a i n C o n t r o l o f U n s t r u c t u r e d F i l e S e r v e r D a t a Laura DuBois I
Unified Security, ATP and more
 SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
SYMANTEC Unified Security, ATP and more TAKE THE NEXT STEP Martin Werner PreSales Consultant, Symantec Switzerland AG MEET SWISS INFOSEC! 27.01.2016 Unified Security 2 Symantec Enterprise Security Users
WHITE PAPER SPLUNK SOFTWARE AS A SIEM
 SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
SPLUNK SOFTWARE AS A SIEM Improve your security posture by using Splunk as your SIEM HIGHLIGHTS Splunk software can be used to operate security operations centers (SOC) of any size (large, med, small)
Integrating MSS, SEP and NGFW to catch targeted APTs
 #SymVisionEmea #SymVisionEmea Integrating MSS, SEP and NGFW to catch targeted APTs Tom Davison Information Security Practice Manager, UK&I Antonio Forzieri EMEA Solution Lead, Cyber Security 2 Information
#SymVisionEmea #SymVisionEmea Integrating MSS, SEP and NGFW to catch targeted APTs Tom Davison Information Security Practice Manager, UK&I Antonio Forzieri EMEA Solution Lead, Cyber Security 2 Information
I D C V E N D O R S P O T L I G H T
 I D C V E N D O R S P O T L I G H T S u p p o r t i n g Softw a re Business Transformation w ith Sys t e m s D e s i g n e d for the Task November 2014 Adapted from Managing Business Model Transitions
I D C V E N D O R S P O T L I G H T S u p p o r t i n g Softw a re Business Transformation w ith Sys t e m s D e s i g n e d for the Task November 2014 Adapted from Managing Business Model Transitions
Cisco Advanced Malware Protection
 Solution Overview Cisco Advanced Malware Protection Breach Prevention, Detection, Response, and Remediation for the Real World BENEFITS Gain unmatched global threat intelligence to strengthen front-line
Solution Overview Cisco Advanced Malware Protection Breach Prevention, Detection, Response, and Remediation for the Real World BENEFITS Gain unmatched global threat intelligence to strengthen front-line
Business Networks: The Next Wave of Innovation
 White Paper Business Networks: The Next Wave of Innovation Sponsored by: Ariba Michael Fauscette November 2014 In This White Paper The business network is forming a new framework for productivity and value
White Paper Business Networks: The Next Wave of Innovation Sponsored by: Ariba Michael Fauscette November 2014 In This White Paper The business network is forming a new framework for productivity and value
STRATEGIC ADVANTAGE: CONSULTING & ISIGHT INTELLIGENCE
 ANALYST DAY STRATEGIC ADVANTAGE: CONSULTING & ISIGHT INTELLIGENCE TRAVIS REESE, PRESIDENT, MANDIANT CONSULTING AND ISIGHT INTELLIGENCE COPYRIGHT 2016, FIREEYE, INC. ALL RIGHTS RESERVED. INTELLIGENCE- LED
ANALYST DAY STRATEGIC ADVANTAGE: CONSULTING & ISIGHT INTELLIGENCE TRAVIS REESE, PRESIDENT, MANDIANT CONSULTING AND ISIGHT INTELLIGENCE COPYRIGHT 2016, FIREEYE, INC. ALL RIGHTS RESERVED. INTELLIGENCE- LED
DNS Server Security Survey
 EXECUTIVE BRIEF DNS Server Security Survey Sponsored by: EfficientIP Romain Fouchereau June 2014 INTRODUCTION With most organizations having some business linked to and more importantly relying on an online
EXECUTIVE BRIEF DNS Server Security Survey Sponsored by: EfficientIP Romain Fouchereau June 2014 INTRODUCTION With most organizations having some business linked to and more importantly relying on an online
Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption
 INDUSTRY DEVELOPMENTS AND MODELS Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption Christopher Chute IDC OPINION Office 365 is Microsoft's next-generation email and
INDUSTRY DEVELOPMENTS AND MODELS Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption Christopher Chute IDC OPINION Office 365 is Microsoft's next-generation email and
Cisco Cyber Threat Defense - Visibility and Network Prevention
 White Paper Advanced Threat Detection: Gain Network Visibility and Stop Malware What You Will Learn The Cisco Cyber Threat Defense (CTD) solution brings visibility to all the points of your extended network,
White Paper Advanced Threat Detection: Gain Network Visibility and Stop Malware What You Will Learn The Cisco Cyber Threat Defense (CTD) solution brings visibility to all the points of your extended network,
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T N i n e S t a r t - U p s a n d I n n o v a t o r s E x t e n d t h e C l o u d S y
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com E X C E R P T N i n e S t a r t - U p s a n d I n n o v a t o r s E x t e n d t h e C l o u d S y
I D C T E C H N O L O G Y S P O T L I G H T. S e r ve r S e c u rity: N o t W h a t It U s e d t o Be!
 I D C T E C H N O L O G Y S P O T L I G H T S e r ve r S e c u rity: N o t W h a t It U s e d t o Be! December 2014 Adapted from Worldwide Endpoint Security 2013 2017 Forecast and 2012 Vendor Shares by
I D C T E C H N O L O G Y S P O T L I G H T S e r ve r S e c u rity: N o t W h a t It U s e d t o Be! December 2014 Adapted from Worldwide Endpoint Security 2013 2017 Forecast and 2012 Vendor Shares by
I D C M a r k e t S c a p e : W o r l d w i d e B u s i n e s s A n a l y t i c s B P O S e r v i c e s 2 0 1 2 V e n d o r A n a l y s i s
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e B u s i n e
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com C O M P E T I T I V E A N A L Y S I S I D C M a r k e t S c a p e : W o r l d w i d e B u s i n e
W o r l d w i d e a n d U. S. M a n a g e d M o b i l i t y 2 0 1 3 2 0 1 7 F o r e c a s t : U n i t e d S t a t e s L e a d s i n A d o p t i o n
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com M A R K E T A N A L Y S I S W o r l d w i d e a n d U. S. M a n a g e d M o b i l i t y 2 0 1 3 2
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com M A R K E T A N A L Y S I S W o r l d w i d e a n d U. S. M a n a g e d M o b i l i t y 2 0 1 3 2
Addressing the SANS Top 20 Critical Security Controls for Effective Cyber Defense
 A Trend Micro Whitepaper I February 2016 Addressing the SANS Top 20 Critical Security Controls for Effective Cyber Defense How Trend Micro Deep Security Can Help: A Mapping to the SANS Top 20 Critical
A Trend Micro Whitepaper I February 2016 Addressing the SANS Top 20 Critical Security Controls for Effective Cyber Defense How Trend Micro Deep Security Can Help: A Mapping to the SANS Top 20 Critical
Perspective: Cloud Solutions and Deployment for Healthcare Payers in 2014
 Perspective Perspective: Cloud Solutions and Deployment for Healthcare Payers in 2014 Lynne A. Dunbrack Judy Hanover IN THIS PERSPECTIVE This IDC Health Insights Perspective examines the current status
Perspective Perspective: Cloud Solutions and Deployment for Healthcare Payers in 2014 Lynne A. Dunbrack Judy Hanover IN THIS PERSPECTIVE This IDC Health Insights Perspective examines the current status
Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure
 EXECUTIVE BRIEF Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure Sponsored by: Symantec Carla Arend December 2014 Andrew Buss IDC Opinion Microsoft will be ending Extended Support
EXECUTIVE BRIEF Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure Sponsored by: Symantec Carla Arend December 2014 Andrew Buss IDC Opinion Microsoft will be ending Extended Support
IDC MarketScape: Worldwide Telecom Service Provider 2013 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Telecom Service Provider 2013 Vendor Assessment Courtney Munroe Melanie Posey THIS IDC MARKETSCAPE EXCERPT FEATURES: BT GLOBAL SERVICES IDC MARKETSCAPE FIGURE
IDC MARKETSCAPE IDC MarketScape: Worldwide Telecom Service Provider 2013 Vendor Assessment Courtney Munroe Melanie Posey THIS IDC MARKETSCAPE EXCERPT FEATURES: BT GLOBAL SERVICES IDC MARKETSCAPE FIGURE
The Hillstone and Trend Micro Joint Solution
 The Hillstone and Trend Micro Joint Solution Advanced Threat Defense Platform Overview Hillstone and Trend Micro offer a joint solution the Advanced Threat Defense Platform by integrating the industry
The Hillstone and Trend Micro Joint Solution Advanced Threat Defense Platform Overview Hillstone and Trend Micro offer a joint solution the Advanced Threat Defense Platform by integrating the industry
SANS Top 20 Critical Controls for Effective Cyber Defense
 WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
WHITEPAPER SANS Top 20 Critical Controls for Cyber Defense SANS Top 20 Critical Controls for Effective Cyber Defense JANUARY 2014 SANS Top 20 Critical Controls for Effective Cyber Defense Summary In a
Advanced Threat Protection with Dell SecureWorks Security Services
 Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Symantec Advanced Threat Protection: Network
 Symantec Advanced Threat Protection: Network Data Sheet: Advanced Threat Protection The Problem Today s advanced attacks hide themselves on legitimate websites, leverage new and unknown vulnerabilities,
Symantec Advanced Threat Protection: Network Data Sheet: Advanced Threat Protection The Problem Today s advanced attacks hide themselves on legitimate websites, leverage new and unknown vulnerabilities,
Fighting Advanced Threats
 Fighting Advanced Threats With FortiOS 5 Introduction In recent years, cybercriminals have repeatedly demonstrated the ability to circumvent network security and cause significant damages to enterprises.
Fighting Advanced Threats With FortiOS 5 Introduction In recent years, cybercriminals have repeatedly demonstrated the ability to circumvent network security and cause significant damages to enterprises.
Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments
 BUYER CASE STUDY Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments Iris Feng Eric Sheppard IDC OPINION Today's datacenter is dominated by virtualized workloads
BUYER CASE STUDY Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments Iris Feng Eric Sheppard IDC OPINION Today's datacenter is dominated by virtualized workloads
Western European Organizations Turn to the Cloud for UCaaS
 IDC TOP LINE Western European Organizations Turn to the Cloud for UCaaS Commissioned by: Verizon and Cisco Jason Andersson July 2015 INTRODUCTION Unified communications as a service (UCaaS) is a fast-growing
IDC TOP LINE Western European Organizations Turn to the Cloud for UCaaS Commissioned by: Verizon and Cisco Jason Andersson July 2015 INTRODUCTION Unified communications as a service (UCaaS) is a fast-growing
Combating a new generation of cybercriminal with in-depth security monitoring. 1 st Advanced Data Analysis Security Operation Center
 Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored. It takes an average
Combating a new generation of cybercriminal with in-depth security monitoring 1 st Advanced Data Analysis Security Operation Center The Challenge Don t leave your systems unmonitored. It takes an average
The State of Mobility in the Enterprise in 2014: An IDC Survey of Devices, Platforms, Decisions, and Deployments
 Survey The State of Mobility in the Enterprise in 2014: An IDC Survey of Devices, Platforms, Decisions, and Deployments Ben Hoffman IDC OPINION IDC recently fielded results for its Enterprise Mobile Device
Survey The State of Mobility in the Enterprise in 2014: An IDC Survey of Devices, Platforms, Decisions, and Deployments Ben Hoffman IDC OPINION IDC recently fielded results for its Enterprise Mobile Device
"Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona
 Buyer Case Study "Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona Dan Vesset IDC OPINION Investment in analytics, business intelligence, and big data technologies
Buyer Case Study "Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona Dan Vesset IDC OPINION Investment in analytics, business intelligence, and big data technologies
Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats
 Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats Executive Summary Palo Alto Networks strategic partnership with Splunk brings the power of our next generation
Palo Alto Networks and Splunk: Combining Next-generation Solutions to Defeat Advanced Threats Executive Summary Palo Alto Networks strategic partnership with Splunk brings the power of our next generation
Data Management: Foundational Technologies for Health Insurance Exchange Success
 INDUSTRY BRIEF Data Management: Foundational Technologies for Health Insurance Exchange Success Sponsored by: Informatica Janice W. Young November 2013 IN THIS INDUSTRY BRIEF U.S. health plans have been
INDUSTRY BRIEF Data Management: Foundational Technologies for Health Insurance Exchange Success Sponsored by: Informatica Janice W. Young November 2013 IN THIS INDUSTRY BRIEF U.S. health plans have been
WHITE PAPER Cloud-Based, Automated Breach Detection. The Seculert Platform
 WHITE PAPER Cloud-Based, Automated Breach Detection The Seculert Platform Table of Contents Introduction 3 Automatic Traffic Log Analysis 4 Elastic Sandbox 5 Botnet Interception 7 Speed and Precision 9
WHITE PAPER Cloud-Based, Automated Breach Detection The Seculert Platform Table of Contents Introduction 3 Automatic Traffic Log Analysis 4 Elastic Sandbox 5 Botnet Interception 7 Speed and Precision 9
Why a Network-based Security Solution is Better than Using Point Solutions Architectures
 Why a Network-based Security Solution is Better than Using Point Solutions Architectures In This Paper Many threats today rely on newly discovered vulnerabilities or exploits CPE-based solutions alone
Why a Network-based Security Solution is Better than Using Point Solutions Architectures In This Paper Many threats today rely on newly discovered vulnerabilities or exploits CPE-based solutions alone
REVOLUTIONIZING ADVANCED THREAT PROTECTION
 REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
REVOLUTIONIZING ADVANCED THREAT PROTECTION A NEW, MODERN APPROACH Blue Coat Advanced Threat Protection Group GRANT ASPLUND Senior Technology Evangelist 1 WHY DO I STAND ON MY DESK? "...I stand upon my
White Paper. Why Next-Generation Firewalls Don t Stop Advanced Malware and Targeted APT Attacks
 White Paper Why Next-Generation Firewalls Don t Stop Advanced Malware and Targeted APT Attacks White Paper Executive Summary Around the world, organizations are investing massive amounts of their budgets
White Paper Why Next-Generation Firewalls Don t Stop Advanced Malware and Targeted APT Attacks White Paper Executive Summary Around the world, organizations are investing massive amounts of their budgets
