{Governmental Client Training} June 20, 2016
|
|
|
- Damon Bridges
- 8 years ago
- Views:
Transcription
1 {Governmental Client Training} June 20, 2016
2 2 Online Banking Controls & Fraud Considerations Dan Block, CPA Rumzei Abdallah, CPA
3 Agenda 3 Online Banking Considerations What happened? 7 Controls Commonly Identified for Online Banking Fraud Examination vs Audit Fraud Case Study Things to look for Q&A
4 Online Banking Considerations 4 What happened? The complexities of cybersecurity have increased and become inherent in almost every organization causing these need to address these risks of fraud. The extent to which online and electronic banking transactions are used significantly increases the exposure to inappropriate and unauthorized transactions.
5 Online Banking Considerations 5 Examples of Internal Control failures that have led to fraud An external hacker obtained the password information to the bank account of a small community organization and withdrew small amounts that would likely be under approval thresholds. Fraudulent checks were created and cashed in the name of a midsize company. An internal staff circumvented controls and approved wire transfers to a personal account to the tune of millions of dollars. So now what?
6 Controls Commonly Identified for Online Banking Security 6 1. Access security 2. Volume limits 3. Limited payees and transfers 4. Positive Pay 5. Bank Reconciliations 6. Notification 7. Activity Logging
7 Pop Quiz 7 What is heartbleed? a) A computer virus that causes your computer to randomly shut down without saving changes, also known as the blue screen of death. b) An virus that sends all of your passwords to hackers, which they can then use to log into your bank accounts and withdraw funds. c) A security bug mistakenly written into security encryption that makes it possible for hackers to extract data from massive databases containing user names, passwords and other sensitive information. d) A Taylor Swift song about her most recent break-up
8 Pop Quiz 8 What is heartbleed? Answer: c) A security bug mistakenly written into security encryption that makes it possible for hackers to extract data from massive databases containing user names, passwords and other sensitive information.
9 Pop Quiz 9 Who was impacted?
10 1. Access Security 10 Accounts, IDs, and passwords should uniquely identify each employee. Significant passwords help protect against unauthorized hacking access. Changing passwords regularly helps both with employees who may share a password at one point in time as well as fighting against passwords that are compromised.
11 1. Access Security 11 Multifactor Authentication (MFA) Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the user's identity for a login or other transaction. SOMETHING YOU HAVE SOMETHING YOU KNOW LOGIN SUCCESS
12 2. Volume Limits 12 Limiting the amount of each transaction and the total transactions per day can protect against the potential loss if access is compromised. A logical limit would be to follow the tiered amounts typically prescribed in check signing policies.
13 3. Limited Payees and Transfers 13 Transfers: Written instructions with the financial institution should limit transfers to other accounts in the entity s name. Payees: Controls over adding payees should be commensurate with controls over adding vendors to AP software.
14 4. Positive Pay 14 Positive Pay was originally designed so that a company issuing checks would send a list of checks and the pertinent details (payee, amount, check number) to their bank. Then, when a check was presented on their account, the bank could confirm the details and thwart any bogus checks. Today, this service has expanded to include a variety of review points and options and remains an effective tool to mitigate fraud. The bank customer can have the option to review all unconfirmed checks presented online with defaults set to allow after 24 hours or deny. Positive Pay has been copied for ACH transactions and can be used in a similar fashion for electronic banking.
15 5. Bank Reconciliations 15 This may sound elementary, but MANY communities and businesses fail to include an online-only account in the same monthly reconciliation and closing processes as traditional bank accounts (i.e. a PayPal account).
16 6. Notification 16 Enforce a notification system that cannot be overridden by the person with the banking administrator login ID and password. For example, create an forwarding account that automatically notifies multiple employees (i.e. someone in accounting and someone in operations) whenever a payment is made or received.
17 7. Activity Logging 17 Many banks are providing access to activity logs for their online accounts. These can be used by management for routine reviews of employee activity. Additionally, internal and external auditors can develop data analysis techniques to comb these logs for unusual activity. Letting employees know that their activity is logged can provide a significant deterrent to fraudulent behavior. Electronic searches of the log files may confirm routine activities or expose anomalies worth investigating further.
18 Fraud Standards in an Audit 18 SAS 99 Misstatement arising from fraudulent financial reporting Misstatement arising from misappropriation of assets Fraud triangle Fraud Brainstorming Focus on direct and material impact on financial statements Valid A/R and revenue Adequate reserves for uncollectible accounts Adequate settlement estimates Risk for misappropriation due to: Lack of segregation of duties Lack of required approvals Inappropriate access/authorization to bank accounts Professional Skepticism
19 Audits v. Fraud Examinations 19
20 The Perfect Case Study Dixon, Illinois Population 15, Median household income - $38, Median house/condo value - $83, Total Primary Government Expenses of $15.6M
21 (Almost) Every Red Flag We Talked About 21 Long-term employee Started as in intern in high-school in 1970 Named Treasurer and Comptroller in 1983 Lack of internal controls Reconciled accounts Made deposits Requested funds Controlled the mail (PO Box) Embezzlement/index.php?cparticle=3&siarticle=2#artanc
22 Things to Look For Billing Schemes 22
23 Things to Look For Billing Schemes 23 Invoice Numbers Subtle changes Out of sequence Inconsistent Duplicate
24 Things to Look For Billing Schemes 24
25 Things to Look For Billing Schemes 25
26 Duplicates 26 Highlight your data Leave out employee at this point Go to conditional formatting Highlight Cells Rules Duplicate Values Click ok
27 Duplicates 27 All the duplicates will now be highlighted in the default color Sort your data by color
28 Duplicates 28 Manual Review More highlights = higher risk
29 Billing Out of Sequence 29 Invoice numbers out of sequence - (=IF(B4- B3>=0,"","OutSeq") 1) Sort the data by Invoice Number then Invoice Date B Invoice Invoice Invoice Invoice Invoice
30 Billing Out of Sequence 30 Invoice Invoice Invoice Out of Sequence Checks - (=IF(B4- B3>=0,"","OutSeq") 2) Insert a column next to the Invoice Date column. The column should be formatted as General 3) Start at the second row of data in your set. Insert the following formula: (=IF(B4-B3>=0,"","OutSeq") The B is replaced with whichever column the Invoice Date is in. The 4 and 3 is replaced with whichever rows are your second and first rows in your data set. 4) Highlight your new column and calculated formulas. Paste/Special values only so they don t change when you re-sort for any reason.
31 Plante & Moran, PLLC 31
Application Intrusion Detection
 Application Intrusion Detection Drew Miller Black Hat Consulting Application Intrusion Detection Introduction Mitigating Exposures Monitoring Exposures Response Times Proactive Risk Analysis Summary Introduction
Application Intrusion Detection Drew Miller Black Hat Consulting Application Intrusion Detection Introduction Mitigating Exposures Monitoring Exposures Response Times Proactive Risk Analysis Summary Introduction
ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS
 $ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
$ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
THE ABC S OF DATA ANALYTICS
 THE ABC S OF DATA ANALYTICS ANGEL BUTLER MAY 23, 2013 HOUSTON AREA SCHOOL DISTRICT INTERNAL AUDITORS (HASDIA) AGENDA Data Analytics Overview Data Analytics Examples Compliance Purchasing and Accounts Payable
THE ABC S OF DATA ANALYTICS ANGEL BUTLER MAY 23, 2013 HOUSTON AREA SCHOOL DISTRICT INTERNAL AUDITORS (HASDIA) AGENDA Data Analytics Overview Data Analytics Examples Compliance Purchasing and Accounts Payable
Online Cash Management Security: Beyond the User Login
 Online Cash Management Security: Beyond the User Login Sonya Crites, CTP, SunTrust Anita Stevenson-Patterson, CTP, Manheim February 28, 2008 Agenda Industry Trends Government Regulations Payment Fraud
Online Cash Management Security: Beyond the User Login Sonya Crites, CTP, SunTrust Anita Stevenson-Patterson, CTP, Manheim February 28, 2008 Agenda Industry Trends Government Regulations Payment Fraud
Fighting Fraud with Data Mining & Analysis
 Fighting Fraud with Data Mining & Analysis Leonard W. Vona December 2008 Fraud Auditing, Inc. Phone: 518-784-2250 www.fraudauditing.net E-mail: leonard@leonardvona.com Copyright 2008 Leonard Vona and Fraud
Fighting Fraud with Data Mining & Analysis Leonard W. Vona December 2008 Fraud Auditing, Inc. Phone: 518-784-2250 www.fraudauditing.net E-mail: leonard@leonardvona.com Copyright 2008 Leonard Vona and Fraud
Detecting, Preventing, and Mitigating Identity Theft
 THE RED FLAGS RULE Detecting, Preventing, and Mitigating Identity Theft Training for Ball State University s Identity Theft Protection Program What is the Red Flag Rule? Congress passed the Fair and Accurate
THE RED FLAGS RULE Detecting, Preventing, and Mitigating Identity Theft Training for Ball State University s Identity Theft Protection Program What is the Red Flag Rule? Congress passed the Fair and Accurate
Business Online. Quick Reference Guide
 Business Online Quick Reference Guide . All rights reserved. This work is confidential and its use is strictly limited. Use is permitted only in accordance with the terms of the agreement under which it
Business Online Quick Reference Guide . All rights reserved. This work is confidential and its use is strictly limited. Use is permitted only in accordance with the terms of the agreement under which it
Personal Online Banking & Bill Pay. Guide to Getting Started
 Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
Personal Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Online Banking. Whether you re at home,
Basic ebusiness Banking User Guide
 Basic ebusiness Banking User Guide 1 Welcome: Welcome to Chemical Bank s ebusiness Banking system. With ebusiness Banking, you can access your accounts 24-hours a day, seven days a week; anywhere an Internet
Basic ebusiness Banking User Guide 1 Welcome: Welcome to Chemical Bank s ebusiness Banking system. With ebusiness Banking, you can access your accounts 24-hours a day, seven days a week; anywhere an Internet
Chapter 7 Trustee. Internal Control Questionnaire
 Chapter 7 Trustee Instructions for the trustee: The purpose of the (ICQ) is to provide the United States Trustee with an understanding of the internal controls and financial record keeping and reporting
Chapter 7 Trustee Instructions for the trustee: The purpose of the (ICQ) is to provide the United States Trustee with an understanding of the internal controls and financial record keeping and reporting
Business Online Banking & Bill Pay Guide to Getting Started
 Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Business Online Banking & Bill Pay Guide to Getting Started What s Inside Contents Security at Vectra Bank... 4 Getting Started Online... 5 Welcome to Vectra Bank Business Online Banking. Whether you re
Business ebanking Fraud Prevention Best Practices
 Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
THE CHANGING FACE OF CYBERCRIME AND WHAT IT MEANS FOR BANKS
 THE CHANGING FACE OF CYBERCRIME AND WHAT IT MEANS FOR BANKS David Glockner, Managing Director strozfriedberg.com Overview The big picture: what does cybercrime look like today and how is it evolving? What
THE CHANGING FACE OF CYBERCRIME AND WHAT IT MEANS FOR BANKS David Glockner, Managing Director strozfriedberg.com Overview The big picture: what does cybercrime look like today and how is it evolving? What
BUSINESS NETTELLER ONLINE BANKING USER GUIDE
 BUSINESS NETTELLER ONLINE BANKING USER GUIDE Revised 6.5.2013 TABLE OF CONTENTS Login Process...1 Cash Management User Login...2 Cash Management User Single Sign-on...3 Multi-Factor Authentication...4
BUSINESS NETTELLER ONLINE BANKING USER GUIDE Revised 6.5.2013 TABLE OF CONTENTS Login Process...1 Cash Management User Login...2 Cash Management User Single Sign-on...3 Multi-Factor Authentication...4
BANKOH BUSINESS CONNECTIONS WIRE TRANSFER GUIDE
 BANKOH BUSINESS CONNECTIONS WIRE TRANSFER GUIDE Revision 2/2013 1 of 35 Contents GENERAL INFORMATION... 3 Wire Transfers... 3 Types of Wires... 3 Wire Templates... 3 Bankoh Business Connections Wire Cut-off
BANKOH BUSINESS CONNECTIONS WIRE TRANSFER GUIDE Revision 2/2013 1 of 35 Contents GENERAL INFORMATION... 3 Wire Transfers... 3 Types of Wires... 3 Wire Templates... 3 Bankoh Business Connections Wire Cut-off
How do I contact someone if my question is not answered in this FAQ?
 Help Where may I find the answers to my Internet Banking questions? How do I contact someone if my question is not answered in this FAQ? Enrolling How do I enroll in Internet Banking? Logging In How do
Help Where may I find the answers to my Internet Banking questions? How do I contact someone if my question is not answered in this FAQ? Enrolling How do I enroll in Internet Banking? Logging In How do
Fraud Detection and Prevention. Timothy P. Minahan Vice President Government Banking TD Bank
 Fraud Detection and Prevention Timothy P. Minahan Vice President Government Banking TD Bank Prevention vs. Detection Prevention controls are designed to keep fraud from occurring Detection controls are
Fraud Detection and Prevention Timothy P. Minahan Vice President Government Banking TD Bank Prevention vs. Detection Prevention controls are designed to keep fraud from occurring Detection controls are
University of Nebraska - Lincoln Identity Theft Prevention Program
 I. Purpose & Scope This program was developed pursuant to the Federal Trade Commission s (FTC) Red Flag Rules promulgated pursuant to the Fair and Accurate Credit Transactions Act (the FACT Act). The University
I. Purpose & Scope This program was developed pursuant to the Federal Trade Commission s (FTC) Red Flag Rules promulgated pursuant to the Fair and Accurate Credit Transactions Act (the FACT Act). The University
CITY OF MARQUETTE, MICHIGAN CITY COMMISSION POLICY
 CITY OF MARQUETTE, MICHIGAN CITY COMMISSION POLICY Policy Number: 2008-02 Date Adopted: October 27, 2008 Department: Administrative SUBJECT: IDENTITY THEFT PREVENTION PROGRAM I. OBJECTIVE: A. To protect
CITY OF MARQUETTE, MICHIGAN CITY COMMISSION POLICY Policy Number: 2008-02 Date Adopted: October 27, 2008 Department: Administrative SUBJECT: IDENTITY THEFT PREVENTION PROGRAM I. OBJECTIVE: A. To protect
Interagency Guidelines on Identity Theft Detection, Prevention, and Mitigation
 Guidelines to FTC Red Flag Rule(reformatted) Appendix A to Part 681 Interagency Guidelines on Identity Theft Detection, Prevention, and Mitigation Section 681.2 of this part requires each financial institution
Guidelines to FTC Red Flag Rule(reformatted) Appendix A to Part 681 Interagency Guidelines on Identity Theft Detection, Prevention, and Mitigation Section 681.2 of this part requires each financial institution
Cathay Business Online Banking
 Cathay Business Online Banking A QUICK GUIDE TO CATHAY BUSINESS ONLINE BANKING R6119 CATHAY 8_5x11 Cover V2.indd 1 6/11/13 5:50 PM Welcome Welcome to Cathay Business Online Banking (formerly known as Cathay
Cathay Business Online Banking A QUICK GUIDE TO CATHAY BUSINESS ONLINE BANKING R6119 CATHAY 8_5x11 Cover V2.indd 1 6/11/13 5:50 PM Welcome Welcome to Cathay Business Online Banking (formerly known as Cathay
Performance Audit City s Payment Process
 Performance Audit City s Payment Process January 2013 City Auditor s Office City of Kansas City, Missouri 18-2011 Office of the City Auditor 21 st Floor, City Hall 414 East 12 th Street (816) 513-3300
Performance Audit City s Payment Process January 2013 City Auditor s Office City of Kansas City, Missouri 18-2011 Office of the City Auditor 21 st Floor, City Hall 414 East 12 th Street (816) 513-3300
Target Security Breach
 Target Security Breach Lessons Learned for Retailers and Consumers 2014 Pointe Solutions, Inc. PO Box 41, Exton, PA 19341 USA +1 610 524 1230 Background In the aftermath of the Target breach that affected
Target Security Breach Lessons Learned for Retailers and Consumers 2014 Pointe Solutions, Inc. PO Box 41, Exton, PA 19341 USA +1 610 524 1230 Background In the aftermath of the Target breach that affected
Reliance Bank Fraud Prevention Best Practices
 Reliance Bank Fraud Prevention Best Practices May 2013 User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters and numbers.
Reliance Bank Fraud Prevention Best Practices May 2013 User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters and numbers.
by: Scott Baranowski, CIA
 Community Bank Auditors Group A/P, Procurement and Credit Card Internal Controls June 4, 2014 by: Scott Baranowski, CIA MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2013 Wolf
Community Bank Auditors Group A/P, Procurement and Credit Card Internal Controls June 4, 2014 by: Scott Baranowski, CIA MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2013 Wolf
FFIEC CONSUMER GUIDANCE
 FFIEC CONSUMER GUIDANCE Important Facts About Your Account Authentication Online Banking & Multi-factor authentication and layered security are helping assure safe Internet transactions for banks and their
FFIEC CONSUMER GUIDANCE Important Facts About Your Account Authentication Online Banking & Multi-factor authentication and layered security are helping assure safe Internet transactions for banks and their
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
P-Card Fraud Controls. Introduction
 Introduction According to 2013 Association of Financial Professionals (AFP) Payments Fraud and Survey, the second most targeted payment type for fraud was corporate/commercial purchasing cards. 29% of
Introduction According to 2013 Association of Financial Professionals (AFP) Payments Fraud and Survey, the second most targeted payment type for fraud was corporate/commercial purchasing cards. 29% of
Identity Theft Prevention Program
 -- Sample Policy -- Identity Theft Prevention Program Purpose To establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection with the opening of
-- Sample Policy -- Identity Theft Prevention Program Purpose To establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection with the opening of
Bank Account Reconciliation, Bank Account Access and Automated Clearing House (ACH) Transactions Review
 Internal Audit Department 350 South 5th Street, Suite 302 Minneapolis, MN 55415-1316 (612) 673-2056 Audit Team on the Engagement: Kelcie Brady, Student Intern Jacob L. Claeys Lauren Heir, Student Intern
Internal Audit Department 350 South 5th Street, Suite 302 Minneapolis, MN 55415-1316 (612) 673-2056 Audit Team on the Engagement: Kelcie Brady, Student Intern Jacob L. Claeys Lauren Heir, Student Intern
Orange County Department of Education Vendor Portal Vendor Guide
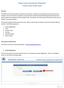 Orange County Department of Education Vendor Portal Vendor Guide Overview The OCDE Vendor Portal provides an interface for businesses, individuals, and employees who provide services to Orange County school
Orange County Department of Education Vendor Portal Vendor Guide Overview The OCDE Vendor Portal provides an interface for businesses, individuals, and employees who provide services to Orange County school
How To Prevent Fraud On A Credit Card
 Fraud Detection and Prevention Financial Management Advisory Council August 28, 2014 Sarah Mahugh, CPA, MBA Financial Audit Audit Manager Overview Fraud trends Fraud Risks and internal controls Case Studies
Fraud Detection and Prevention Financial Management Advisory Council August 28, 2014 Sarah Mahugh, CPA, MBA Financial Audit Audit Manager Overview Fraud trends Fraud Risks and internal controls Case Studies
Need help? The Accounts Payable Help Documentation is designed to make your Accounts Payable experience as efficient as possible.
 Need help? The Accounts Payable Help Documentation is designed to make your Accounts Payable experience as efficient as possible. All you have to do to navigate through this document is simply use the
Need help? The Accounts Payable Help Documentation is designed to make your Accounts Payable experience as efficient as possible. All you have to do to navigate through this document is simply use the
Your security is our priority
 Your security is our priority Welcome to our Cash Management newsletter for businesses. You will find valuable information about how to limit your company s risk for fraud. We offer a wide variety of products
Your security is our priority Welcome to our Cash Management newsletter for businesses. You will find valuable information about how to limit your company s risk for fraud. We offer a wide variety of products
IT Security Risks & Trends
 IT Security Risks & Trends Key Threats to All Businesses 1 1 What do the following have in common? Catholic church parish Hospice Collection agency Main Street newspaper stand Electrical contractor Health
IT Security Risks & Trends Key Threats to All Businesses 1 1 What do the following have in common? Catholic church parish Hospice Collection agency Main Street newspaper stand Electrical contractor Health
Business Online Banking Quick Users Guide
 Business Online Banking Quick Users Guide Business Online Banking Quick Users Guide Table of Contents Overview 2 First Time Login 2 Security 4 Contact Points 4 Registering your Browser / Computer 5 Adding,
Business Online Banking Quick Users Guide Business Online Banking Quick Users Guide Table of Contents Overview 2 First Time Login 2 Security 4 Contact Points 4 Registering your Browser / Computer 5 Adding,
ACCG Identity Theft Prevention Program. ACCG 50 Hurt Plaza, Suite 1000 Atlanta, Georgia 30303 (404)522-5022 (404)525-2477 www.accg.
 ACCG Identity Theft Prevention Program ACCG 50 Hurt Plaza, Suite 1000 Atlanta, Georgia 30303 (404)522-5022 (404)525-2477 www.accg.org July 2009 Contents Summary of ACCG Identity Theft Prevention Program...
ACCG Identity Theft Prevention Program ACCG 50 Hurt Plaza, Suite 1000 Atlanta, Georgia 30303 (404)522-5022 (404)525-2477 www.accg.org July 2009 Contents Summary of ACCG Identity Theft Prevention Program...
Red Flag Rules and Aging Services: What You Need to Know
 Red Flag Rules and Aging Services: What You Need to Know Late in 2007, six federal agencies, including the Federal Trade Commission ( FTC ), jointly issued final rules and accompanying guidelines to implement
Red Flag Rules and Aging Services: What You Need to Know Late in 2007, six federal agencies, including the Federal Trade Commission ( FTC ), jointly issued final rules and accompanying guidelines to implement
Identification of Red Flags, Detecting Red Flags, and Preventing and Mitigating Identity Theft
 George Mason University Identity Theft Prevention Program - Procedures Revised September 30, 2012 Identification of, ing, and Preventing and Mitigating Identity Theft IDENTIFICATION OF COVERED ACCOUNT
George Mason University Identity Theft Prevention Program - Procedures Revised September 30, 2012 Identification of, ing, and Preventing and Mitigating Identity Theft IDENTIFICATION OF COVERED ACCOUNT
Broker Registration Guide for TrustFunds Authentication A- B- C Registration Steps 1-2- 3-4
 Broker Registration Guide for TrustFunds Authentication A- B- C Registration Steps 1-2- 3-4 Broker Authentication 1. From the TrustFunds website homepage, click Get Started Now to begin your Authentication
Broker Registration Guide for TrustFunds Authentication A- B- C Registration Steps 1-2- 3-4 Broker Authentication 1. From the TrustFunds website homepage, click Get Started Now to begin your Authentication
Here are two informational brochures that disclose ways that we protect your accounts and tips you can use to be safer online.
 Here are two informational brochures that disclose ways that we protect your accounts and tips you can use to be safer online. FFIEC BUSINESS ACCOUNT GUIDANCE New financial standards will assist credit
Here are two informational brochures that disclose ways that we protect your accounts and tips you can use to be safer online. FFIEC BUSINESS ACCOUNT GUIDANCE New financial standards will assist credit
FINANCE COMMITTEE PROCEDURES. Audit Process. Cash Handling
 1 FINANCE COMMITTEE PROCEDURES Audit Process 1. Internal audits are conducted once a year. 2. The bookkeeper will provide the following information: bank statements, prior year vouchers, and access to
1 FINANCE COMMITTEE PROCEDURES Audit Process 1. Internal audits are conducted once a year. 2. The bookkeeper will provide the following information: bank statements, prior year vouchers, and access to
Approved by the Audit Committee of the Board of Trustees, effective February 3, 2009.
 Red Flag Identity Theft Policy 1.) Policy and Program Rationale: Messiah College ( College ) has developed the Identity Theft Policy ( Policy) and Prevention Program ( Program ) pursuant to the Federal
Red Flag Identity Theft Policy 1.) Policy and Program Rationale: Messiah College ( College ) has developed the Identity Theft Policy ( Policy) and Prevention Program ( Program ) pursuant to the Federal
Red Flags Identity Theft Training Program. Fall 2015
 Red Flags Identity Theft Training Program Fall 2015 Background In 2003, U.S. Congress enacted the Fair and Accurate Credit Transactions Act of 2003 (FACTA). FACTA requires creditors to adopt policies and
Red Flags Identity Theft Training Program Fall 2015 Background In 2003, U.S. Congress enacted the Fair and Accurate Credit Transactions Act of 2003 (FACTA). FACTA requires creditors to adopt policies and
Identity Theft Prevention Program Red Flag Rules Policy P093.00 Issued: May 2009
 Identity Theft Prevention Program Red Flag Rules Policy P093.00 Issued: May 2009 The Federal Trade Commission has issued a final rule (the Red Flag Rule) under the Fair and Accurate Credit Transactions
Identity Theft Prevention Program Red Flag Rules Policy P093.00 Issued: May 2009 The Federal Trade Commission has issued a final rule (the Red Flag Rule) under the Fair and Accurate Credit Transactions
By: Gerald Gagne. Community Bank Auditors Group Cybersecurity What you need to do now. June 9, 2015
 Community Bank Auditors Group Cybersecurity What you need to do now June 9, 2015 By: Gerald Gagne MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2015 Wolf & Company, P.C. Cybersecurity
Community Bank Auditors Group Cybersecurity What you need to do now June 9, 2015 By: Gerald Gagne MEMBER OF PKF NORTH AMERICA, AN ASSOCIATION OF LEGALLY INDEPENDENT FIRMS 2015 Wolf & Company, P.C. Cybersecurity
Covered Areas: Those EVMS departments that have activities with Covered Accounts.
 I. POLICY Eastern Virginia Medical School (EVMS) establishes the following identity theft program ( Program ) to detect, identify, and mitigate identity theft in its Covered Accounts in accordance with
I. POLICY Eastern Virginia Medical School (EVMS) establishes the following identity theft program ( Program ) to detect, identify, and mitigate identity theft in its Covered Accounts in accordance with
Northeast Technology Center Board Policy 2110 Page 1 IDENTITY THEFT PREVENTION (MANY COVERED ACCOUNTS)
 Page 1 IDENTITY THEFT PREVENTION (MANY COVERED ACCOUNTS) This Policy is adopted to ensure compliance with the Fair and Accurate Credit Transaction Act, 15 U.S.C. 1601 et seq. and the Federal Trade Commission
Page 1 IDENTITY THEFT PREVENTION (MANY COVERED ACCOUNTS) This Policy is adopted to ensure compliance with the Fair and Accurate Credit Transaction Act, 15 U.S.C. 1601 et seq. and the Federal Trade Commission
FAQ's. Introduction. Frequently asked questions about Epay Manager. For more information, please call 800.240.1824.
 FAQ's Frequently asked questions about Epay Manager. For more information, please call 800.240.1824. Introduction This document was created to help you answer a few of the more common questions about Epay
FAQ's Frequently asked questions about Epay Manager. For more information, please call 800.240.1824. Introduction This document was created to help you answer a few of the more common questions about Epay
Directions for the AP Invoice Upload Spreadsheet
 Directions for the AP Invoice Upload Spreadsheet The AP Invoice Upload Spreadsheet is used to enter Accounts Payable historical invoices (only, no GL Entry) to the OGSQL system. This spreadsheet is designed
Directions for the AP Invoice Upload Spreadsheet The AP Invoice Upload Spreadsheet is used to enter Accounts Payable historical invoices (only, no GL Entry) to the OGSQL system. This spreadsheet is designed
Red Flag Rules Information and Training
 Red Flag Rules Information and Training What are Red Flag Rules? The Red Flag Rules: - Are enforced by the Federal Trade Commission (FTC), the federal bank regulatory agencies, and the National Credit
Red Flag Rules Information and Training What are Red Flag Rules? The Red Flag Rules: - Are enforced by the Federal Trade Commission (FTC), the federal bank regulatory agencies, and the National Credit
Premium ebusiness Banking User Guide
 Premium ebusiness Banking User Guide Welcome: Welcome to Chemical Bank s ebusiness Banking system. With ebusiness Banking, you can access your accounts 24-hours a day, seven days a week; anywhere an Internet
Premium ebusiness Banking User Guide Welcome: Welcome to Chemical Bank s ebusiness Banking system. With ebusiness Banking, you can access your accounts 24-hours a day, seven days a week; anywhere an Internet
CHAPTER 101: IDENTITY THEFT PREVENTION PROGRAM
 CHAPTER 101: IDENTITY THEFT PREVENTION PROGRAM Section 101.01 Purpose 101.02 Definitions 101.03 Program established 101.04 Administration of program 101.05 Identification of relevant red flags 101.06 Detection
CHAPTER 101: IDENTITY THEFT PREVENTION PROGRAM Section 101.01 Purpose 101.02 Definitions 101.03 Program established 101.04 Administration of program 101.05 Identification of relevant red flags 101.06 Detection
ACHieve Access 4.3 User Guide for Corporate Customers
 ACHieve Access 4.3 User Guide for Corporate Customers January 2015 Citizens Bank 1 February 2015 Table of Contents SECTION 1: OVERVIEW... 4 Chapter 1: Introduction... 5 How to Use This Manual... 5 Overview
ACHieve Access 4.3 User Guide for Corporate Customers January 2015 Citizens Bank 1 February 2015 Table of Contents SECTION 1: OVERVIEW... 4 Chapter 1: Introduction... 5 How to Use This Manual... 5 Overview
WHEREAS the Federal Trade Commission regulations include utility companies in the definition of creditor;
 CITY OF STATE OF GEORGIA ORDINANCE NO: AN ORDINANCE TO AMEND THE CODE OF ORDINANCES, CITY OF, GEORGIA TO PROVIDE A NEW ARTICLE, IDENTITY THEFT PREVENTION PROGRAM; TO COMPLY WITH FEDERAL REGULATIONS RELATING
CITY OF STATE OF GEORGIA ORDINANCE NO: AN ORDINANCE TO AMEND THE CODE OF ORDINANCES, CITY OF, GEORGIA TO PROVIDE A NEW ARTICLE, IDENTITY THEFT PREVENTION PROGRAM; TO COMPLY WITH FEDERAL REGULATIONS RELATING
Generate Electronic Payments in Accounts Payable
 Generate Electronic Payments in Accounts Payable IMPORTANT NOTICE This document and the Sage 300 Construction and Real Estate software may be used only in accordance with the Sage 300 Construction and
Generate Electronic Payments in Accounts Payable IMPORTANT NOTICE This document and the Sage 300 Construction and Real Estate software may be used only in accordance with the Sage 300 Construction and
Trust Safety Update. Central Alberta Bar Society Red Deer June 3, 2015
 Trust Safety Update Central Alberta Bar Society Red Deer June 3, 2015 Today s Presentation Fraud Schemes & Lawyer s Trust Accounts Risk Mitigation strategies Examples etransactions and Trust Accounts Trust
Trust Safety Update Central Alberta Bar Society Red Deer June 3, 2015 Today s Presentation Fraud Schemes & Lawyer s Trust Accounts Risk Mitigation strategies Examples etransactions and Trust Accounts Trust
STATE OF NEW YORK OFFICE OF THE STATE COMPTROLLER 110 STATE STREET ALBANY, NEW YORK 12236. February 25, 2011
 THOMAS P. DiNAPOLI COMPTROLLER STATE OF NEW YORK OFFICE OF THE STATE COMPTROLLER 110 STATE STREET ALBANY, NEW YORK 12236 STEVEN J. HANCOX DEPUTY COMPTROLLER DIVISION OF LOCAL GOVERNMENT AND SCHOOL ACCOUNTABILITY
THOMAS P. DiNAPOLI COMPTROLLER STATE OF NEW YORK OFFICE OF THE STATE COMPTROLLER 110 STATE STREET ALBANY, NEW YORK 12236 STEVEN J. HANCOX DEPUTY COMPTROLLER DIVISION OF LOCAL GOVERNMENT AND SCHOOL ACCOUNTABILITY
NORTHEAST COMMUNITY COLLEGE ADMINISTRATIVE PROCEDURE NUMBER: AP-3250.0 FOR POLICY NUMBER: BP 3250 IDENITY THEFT PREVENTION PROGRAM PROCEDURES
 NORTHEAST COMMUNITY COLLEGE ADMINISTRATIVE PROCEDURE NUMBER: AP-3250.0 FOR POLICY NUMBER: BP 3250 IDENITY THEFT PREVENTION PROGRAM PROCEDURES 1. PROCEDURE SUMMARY STATMENT The purpose of this procedure
NORTHEAST COMMUNITY COLLEGE ADMINISTRATIVE PROCEDURE NUMBER: AP-3250.0 FOR POLICY NUMBER: BP 3250 IDENITY THEFT PREVENTION PROGRAM PROCEDURES 1. PROCEDURE SUMMARY STATMENT The purpose of this procedure
Knowledge Base. Table of Contents. Customers How Do I?
 Knowledge Base Table of Contents Customers How Do I? Set up a Customer?...2 Record a payment received from a customer?...5 Allocate the customer s payment to an order?...6 Deposit the customers payments?...8
Knowledge Base Table of Contents Customers How Do I? Set up a Customer?...2 Record a payment received from a customer?...5 Allocate the customer s payment to an order?...6 Deposit the customers payments?...8
Payment Fraud and Risk Management
 Payment Fraud and Risk Management Act Today! 1. Help protect your computer against viruses and spyware by using anti-virus and anti-spyware software and automatic updates. Scan your computer regularly
Payment Fraud and Risk Management Act Today! 1. Help protect your computer against viruses and spyware by using anti-virus and anti-spyware software and automatic updates. Scan your computer regularly
Financial Transactions and Fraud Schemes
 Financial Transactions and Fraud Schemes Asset Misappropriation: Fraudulent Disbursements Fraudulent Disbursement Schemes Register disbursement schemes Check tampering schemes Payroll schemes Billing schemes
Financial Transactions and Fraud Schemes Asset Misappropriation: Fraudulent Disbursements Fraudulent Disbursement Schemes Register disbursement schemes Check tampering schemes Payroll schemes Billing schemes
Enhanced Login Security Frequently Asked Questions
 Enhanced Login Security Frequently Asked Questions Below are Frequently Asked Questions to assist you and you can also contact Customer Service at 903-657-8525 or 800-962-1610. Q: What is Enhanced Login
Enhanced Login Security Frequently Asked Questions Below are Frequently Asked Questions to assist you and you can also contact Customer Service at 903-657-8525 or 800-962-1610. Q: What is Enhanced Login
3344-19-01 Identity theft prevention program and red flag compliance policy.
 3344-19-01 Identity theft prevention program and red flag compliance policy. (A) Program adoption Cleveland state university has developed this identity theft prevention program ( program ) pursuant to
3344-19-01 Identity theft prevention program and red flag compliance policy. (A) Program adoption Cleveland state university has developed this identity theft prevention program ( program ) pursuant to
Internal Controls, Fraud Detection and ERP
 Internal Controls, Fraud Detection and ERP Recently the SEC adopted Section 404 of the Sarbanes Oxley Act. This law requires each annual report of a company to contain 1. A statement of management's responsibility
Internal Controls, Fraud Detection and ERP Recently the SEC adopted Section 404 of the Sarbanes Oxley Act. This law requires each annual report of a company to contain 1. A statement of management's responsibility
FRAUD PREVENTION STRATEGIES FOR HEALTH CARE A FORENSIC ACCOUNTANT S PERSPECTIVE
 FRAUD PREVENTION STRATEGIES FOR HEALTH CARE A FORENSIC ACCOUNTANT S PERSPECTIVE CPAs & ADVISORS experience reach // S. Todd Burchett, CPA, ABV, ASA, CFF, CFE Partner tburchett@bkd.com 210.268.1932 AGENDA
FRAUD PREVENTION STRATEGIES FOR HEALTH CARE A FORENSIC ACCOUNTANT S PERSPECTIVE CPAs & ADVISORS experience reach // S. Todd Burchett, CPA, ABV, ASA, CFF, CFE Partner tburchett@bkd.com 210.268.1932 AGENDA
White Paper. The E-Sign Act. Use and enforceability of identifiers, passwords and personal identification numbers as signatures
 White Paper The E-Sign Act Use and enforceability of identifiers, passwords and personal identification numbers as signatures 1 Table of Contents Introduction 2 The Audit Confirmation Process 2 The Confirm
White Paper The E-Sign Act Use and enforceability of identifiers, passwords and personal identification numbers as signatures 1 Table of Contents Introduction 2 The Audit Confirmation Process 2 The Confirm
Facts About FACTA Red Flag Identity Theft Prevention Program
 FACTA Red Flag Identity Theft Prevention Program FACTA Red Flag Policy Program, page 1 of 6 Contents Overview 3 Definition of Terms 3 Covered Accounts..3 List of Red Flags 3 Suspicious Documents...4 Suspicious
FACTA Red Flag Identity Theft Prevention Program FACTA Red Flag Policy Program, page 1 of 6 Contents Overview 3 Definition of Terms 3 Covered Accounts..3 List of Red Flags 3 Suspicious Documents...4 Suspicious
Accounts Payable: Invoice Processing Invoice Certification
 Accounts Payable: Invoice Processing Invoice Certification Note: The application is most effective in the latest version of Mozilla for Windows users and the latest version of Safari for Mac users. In
Accounts Payable: Invoice Processing Invoice Certification Note: The application is most effective in the latest version of Mozilla for Windows users and the latest version of Safari for Mac users. In
QuickBooks Credit Card Merchant Service May 18, 2015 revised
 May 18, 2015 revised Security Awareness link http://bblearn.missouri.edu Other resources: Signup for Swipe Reader Guidelines for Credit Card Swipe Reader What is the Merchant Service? The Merchant Service
May 18, 2015 revised Security Awareness link http://bblearn.missouri.edu Other resources: Signup for Swipe Reader Guidelines for Credit Card Swipe Reader What is the Merchant Service? The Merchant Service
Business Internet Banking / Cash Management Fraud Prevention Best Practices
 Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
A Performance Audit of the State s Purchasing Card Program
 REPORT TO THE UTAH LEGISLATURE Number 2006-09 A Performance Audit of the State s Purchasing Card Program September 2006 Audit Performed By: Audit Manager Audit Supervisor Audit Staff Rick Coleman Susan
REPORT TO THE UTAH LEGISLATURE Number 2006-09 A Performance Audit of the State s Purchasing Card Program September 2006 Audit Performed By: Audit Manager Audit Supervisor Audit Staff Rick Coleman Susan
AGA Kansas City Chapter Data Analytics & Continuous Monitoring
 AGA Kansas City Chapter Data Analytics & Continuous Monitoring Agenda Market Overview & Drivers for Change Key challenges that organizations face Data Analytics What is data analytics and how can it help
AGA Kansas City Chapter Data Analytics & Continuous Monitoring Agenda Market Overview & Drivers for Change Key challenges that organizations face Data Analytics What is data analytics and how can it help
Number of Pages: 5 Number of Forms: 0 Saved As: X:/Policies & Procedures/13. JCAHO STD s (if applicable): N/A
 15.05 Identity Theft Prevention Program Policy: Identity Theft Prevention Program Effective Date: Manual: RFHC Clinical Policies and Procedures Revision Date: Number of Pages: 5 Number of Forms: 0 Saved
15.05 Identity Theft Prevention Program Policy: Identity Theft Prevention Program Effective Date: Manual: RFHC Clinical Policies and Procedures Revision Date: Number of Pages: 5 Number of Forms: 0 Saved
Fraud: Real Stories, Real People, Real Impact
 Fraud: Real Stories, Real People, Real Impact Chris Harper, CPA, MBA Senior Manager Types of Fraud Asset misappropriation Fraudulent financial reporting Identity theft Detection Skills The Fraud Triangle
Fraud: Real Stories, Real People, Real Impact Chris Harper, CPA, MBA Senior Manager Types of Fraud Asset misappropriation Fraudulent financial reporting Identity theft Detection Skills The Fraud Triangle
Internal Controls and Fraud Detection & Prevention. Harold Monk and Jennifer Christensen
 Internal Controls and Fraud Detection & Prevention Harold Monk and Jennifer Christensen 1 Common Fraud Statements Everyone in government has an honest and charitable heart. It may happen other places,
Internal Controls and Fraud Detection & Prevention Harold Monk and Jennifer Christensen 1 Common Fraud Statements Everyone in government has an honest and charitable heart. It may happen other places,
3) The client side of the Service Fee Bookings MUST be closed with FOP of CC (Not CC Merchant)
 Sabre Card Services The Sabre Card Services reconciliation option allows TBO users to daily close individual items in TBO that reconcile to the customer's Sabre Card Services' file by transaction, and
Sabre Card Services The Sabre Card Services reconciliation option allows TBO users to daily close individual items in TBO that reconcile to the customer's Sabre Card Services' file by transaction, and
Sharon Kurek, CPA, CFE Director of Internal Audit
 Sharon Kurek, CPA, CFE Director of Internal Audit What You Will Take Aware With You Definition of Internal Auditing Scope of Audit Activities Risk and Control Process Common Audit Topics Fraud Awareness
Sharon Kurek, CPA, CFE Director of Internal Audit What You Will Take Aware With You Definition of Internal Auditing Scope of Audit Activities Risk and Control Process Common Audit Topics Fraud Awareness
Treasury Management Services Product Terms and Conditions
 Treasury Management Services Product Thank you for choosing M&T Bank for your treasury management service needs. We appreciate the opportunity to serve you. If you have any questions about this Product
Treasury Management Services Product Thank you for choosing M&T Bank for your treasury management service needs. We appreciate the opportunity to serve you. If you have any questions about this Product
HUNTINGTON BUSINESS SECURITY SUITE USER GUIDE
 HUNTINGTON BUSINESS SECURITY SUITE USER GUIDE CONTENTS WELCOME 3 SECTION 1: GETTING STARTED LOGGING IN 5 SECTION 2: ACH POSITIVE PAY OVERVIEW 7 FILTERS 8 MANAGING EXCEPTIONS 11 WAREHOUSE 14 APPROVALS 15
HUNTINGTON BUSINESS SECURITY SUITE USER GUIDE CONTENTS WELCOME 3 SECTION 1: GETTING STARTED LOGGING IN 5 SECTION 2: ACH POSITIVE PAY OVERVIEW 7 FILTERS 8 MANAGING EXCEPTIONS 11 WAREHOUSE 14 APPROVALS 15
Admin Reference Guide. PinPoint Document Management System
 Admin Reference Guide PinPoint Document Management System 1 Contents Introduction... 2 Managing Departments... 3 Managing Languages... 4 Managing Users... 5 Managing User Groups... 7 Managing Tags... 9
Admin Reference Guide PinPoint Document Management System 1 Contents Introduction... 2 Managing Departments... 3 Managing Languages... 4 Managing Users... 5 Managing User Groups... 7 Managing Tags... 9
TITLE XVIII: IDENTITY THEFT PREVENTION PROGRAM
 River Bend Identity Theft Program 1 TITLE XVIII: IDENTITY THEFT PREVENTION PROGRAM Chapter 18.01. IDENTITY THEFT PREVENTION PROGRAM 2 Identity Theft Prevention Program SECTION Chapter 18.01: IDENTITY THEFT
River Bend Identity Theft Program 1 TITLE XVIII: IDENTITY THEFT PREVENTION PROGRAM Chapter 18.01. IDENTITY THEFT PREVENTION PROGRAM 2 Identity Theft Prevention Program SECTION Chapter 18.01: IDENTITY THEFT
Cash Management. Getting Started Guide
 Cash Management Getting Started Guide Table of Contents Accessing Cash Management Online... 3 Multifactor Authentication... 3 Navigation... 5 Administration... 5 Manage Users... 6 User Activity Reports...
Cash Management Getting Started Guide Table of Contents Accessing Cash Management Online... 3 Multifactor Authentication... 3 Navigation... 5 Administration... 5 Manage Users... 6 User Activity Reports...
Wake Forest University. Identity Theft Prevention Program. Effective May 1, 2009
 Wake Forest University Identity Theft Prevention Program Effective May 1, 2009 I. GENERAL It is the policy of Wake Forest University ( University ) to comply with the Federal Trade Commission's ( FTC )
Wake Forest University Identity Theft Prevention Program Effective May 1, 2009 I. GENERAL It is the policy of Wake Forest University ( University ) to comply with the Federal Trade Commission's ( FTC )
Keep Your Business Banking
 Keep Your Business Banking Safe in the Digital Age By Erin Fonté As a business executive, you have many choices in conducting banking activities, including online and mobile banking options. But with increasing
Keep Your Business Banking Safe in the Digital Age By Erin Fonté As a business executive, you have many choices in conducting banking activities, including online and mobile banking options. But with increasing
Online Banking Fraud Prevention Recommendations and Best Practices
 Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Is There Anyway to Prevent Fraud? Bill Gady, CGA CPA Partner
 Is There Anyway to Prevent Fraud? Bill Gady, CGA CPA Partner Learning Objectives: Understand how fraud can occur Learn procedures you can implement to prevent fraud Learn how to detect fraud Common Situations
Is There Anyway to Prevent Fraud? Bill Gady, CGA CPA Partner Learning Objectives: Understand how fraud can occur Learn procedures you can implement to prevent fraud Learn how to detect fraud Common Situations
BUSINESS ONLINE BANKING AGREEMENT
 BUSINESS ONLINE BANKING AGREEMENT This Business Online Banking Agreement ("Agreement") establishes the terms and conditions for Business Online Banking Services ( Service(s) ) provided by Mechanics Bank
BUSINESS ONLINE BANKING AGREEMENT This Business Online Banking Agreement ("Agreement") establishes the terms and conditions for Business Online Banking Services ( Service(s) ) provided by Mechanics Bank
University Identity Theft and Detection Program (NEW) All Campuses and All Service Providers Subject to the Red Flags Rule
 NUMBER: BUSF 4.12 SECTION: SUBJECT: Finance and Planning University Identity Theft and Detection Program (NEW) DATE: March 3, 2011 Policy for: Procedure for: Authorized by: Issued by: All Campuses and
NUMBER: BUSF 4.12 SECTION: SUBJECT: Finance and Planning University Identity Theft and Detection Program (NEW) DATE: March 3, 2011 Policy for: Procedure for: Authorized by: Issued by: All Campuses and
Don t Fall Victim to Cybercrime:
 Don t Fall Victim to Cybercrime: Best Practices to Safeguard Your Business Agenda Cybercrime Overview Corporate Account Takeover Computer Hacking, Phishing, Malware Breach Statistics Internet Security
Don t Fall Victim to Cybercrime: Best Practices to Safeguard Your Business Agenda Cybercrime Overview Corporate Account Takeover Computer Hacking, Phishing, Malware Breach Statistics Internet Security
This Agreement shall be governed by and construed in accordance with the laws of the State of Wyoming.
 Online Agreement: Online Banking Agreement. By submitting this form, you agree that you have read and agree to all terms herein. If you would like to talk with us about your enrollment, please call 307-732-BOJH
Online Agreement: Online Banking Agreement. By submitting this form, you agree that you have read and agree to all terms herein. If you would like to talk with us about your enrollment, please call 307-732-BOJH
A8.700 TREASURY. This directive applies to all campuses of the University of Hawai i.
 Prepared by Treasury Office. This amends A8.710 dated July 2001. A8.710 April 2005 A8.700 TREASURY P 1 of 5 A8.710 Credit Card Program 1. Purpose To provide uniform procedures for the processing of credit
Prepared by Treasury Office. This amends A8.710 dated July 2001. A8.710 April 2005 A8.700 TREASURY P 1 of 5 A8.710 Credit Card Program 1. Purpose To provide uniform procedures for the processing of credit
Carleton College IDENTITY THEFT PREVENTION PROGRAM POLICY STATEMENT
 Program Adoption Carleton College developed this Identity Theft Prevention Program ( Program ) pursuant to the Federal Trade Commission s (FTC) Red Flags Rule, set forth in Part 681 of Title 16 of the
Program Adoption Carleton College developed this Identity Theft Prevention Program ( Program ) pursuant to the Federal Trade Commission s (FTC) Red Flags Rule, set forth in Part 681 of Title 16 of the
Contract and Procurement Fraud. Vendor Management
 Contract and Procurement Fraud Vendor Management Introduction Organizations must take steps to reduce vendor fraud, including: Conducting vendor due diligence Managing vendor risks via contracts Ensuring
Contract and Procurement Fraud Vendor Management Introduction Organizations must take steps to reduce vendor fraud, including: Conducting vendor due diligence Managing vendor risks via contracts Ensuring
Identity Theft Prevention Program. Approved by the Arizona Board of Regents on May 1, 2009
 Identity Theft Prevention Program Approved by the Arizona Board of Regents on May 1, 2009 I. Purpose & Scope This Program was developed pursuant to the Federal Trade Commission s ( FTC ) Red Flag Rules
Identity Theft Prevention Program Approved by the Arizona Board of Regents on May 1, 2009 I. Purpose & Scope This Program was developed pursuant to the Federal Trade Commission s ( FTC ) Red Flag Rules
City of Caro Identity Theft Prevention Policy
 City of Caro Identity Theft Prevention Policy Purpose The purpose of this policy is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection
City of Caro Identity Theft Prevention Policy Purpose The purpose of this policy is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection
Administering the Customer Platform
 Administering the Customer Platform Business Banking Certification Training Section Objectives By the end of this section, you will know how to: access the Customer Platform support your business users
Administering the Customer Platform Business Banking Certification Training Section Objectives By the end of this section, you will know how to: access the Customer Platform support your business users
McLennan Community College
 McLennan Community College POLICIES AND PROCEDURES Subject: Identity Theft Prevention Program Reference: E-XXVIII-f Source: Board of Trustees Eff. Date: November 27, 2012 Approval Auth: Board of Trustees
McLennan Community College POLICIES AND PROCEDURES Subject: Identity Theft Prevention Program Reference: E-XXVIII-f Source: Board of Trustees Eff. Date: November 27, 2012 Approval Auth: Board of Trustees
A Business Signer who has the Manage Users feature assigned to them can create other users on the User Management page in DFCU OnLine.
 MANAGING USERS A Business Signer who has the Manage Users feature assigned to them can create other users on the User Management page in DFCU OnLine. To add a user and configure rights: 1. In the Menu,
MANAGING USERS A Business Signer who has the Manage Users feature assigned to them can create other users on the User Management page in DFCU OnLine. To add a user and configure rights: 1. In the Menu,
policy All terms used in this policy that are defined in 16 C.F.R. 681.2 shall have the same meaning provided in that section.
 Name of Policy: Identity theft detection, prevention, and mitigation. Policy Number: 3364-15-12 Approving Officer: President Responsible Agent: Compliance Officer Scope: All University of Toledo Campuses
Name of Policy: Identity theft detection, prevention, and mitigation. Policy Number: 3364-15-12 Approving Officer: President Responsible Agent: Compliance Officer Scope: All University of Toledo Campuses
