Mining Business Topics in Source Code using Latent Dirichlet Allocation
|
|
|
- Alaina Carter
- 8 years ago
- Views:
Transcription
1 Mining Business Topics in Source Code using Latent Dirichlet Allocation ABSTRACT Girish Maskeri, Santonu Sarkar SETLabs, Infosys Technologies Limited Bangalore , India One of the difficulties in maintaining a large software system is the absence of documented business domain topics and correlation between these domain topics and source code. Without such a correlation, people without any prior application knowledge would find it hard to comprehend the functionality of the system. Latent Dirichlet Allocation (LDA), a statistical model, has emerged as a popular technique for discovering topics in large text document corpus. But its applicability in extracting business domain topics from source code has not been explored so far. This paper investigates LDA in the context of comprehending large software systems and proposes a human assisted approach based on LDA for extracting domain topics from source code. This method has been applied on a number of open source and proprietary systems. Preliminary results indicate that LDA is able to identify some of the domain topics and is a satisfactory starting point for further manual refinement of topics. Categories and Subject Descriptors D.2.7 [Software Engineering]: Distribution, Maintenance, and Enhancement Restructuring, reverse engineering, and reengineering; General terms Theory,Algorithms,Experimentation Keywords Maintenance, Program comprehension, LDA 1. INTRODUCTION Large legacy software systems often exist in a state of disorganization with poor or no documentation. Adding new features and fixing bugs in such a system is highly error prone and time consuming since the original authors of the Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. ISEC 08, February 19-22, 2008, Hyderabad, India. Copyright 2008 ACM /08/ $5.00. Kenneth Heafield California Institute of Technology CA USA kpu@kheafield.com system are generally no longer available. Moreover, the people maintaining the code-base do not comprehend the functional purpose of different program elements (functions, files, classes, data structures etc.) and the roles they play to fulfill various functional services offered by the system. When a software system is small, one can understand its functional architecture by manually browsing the source code. For large systems, practitioners often rely on program analysis techniques such as call graph, control and data flow and slicing [2].Though this is very helpful to understand the structural intricacies of the system, it helps a little to comprehend the functional intent of the system. The reason is not difficult to understand. Structural analysis techniques work on the structural information derived from a set of program source code. The structural information is at a very low level of granularity- such as files, functions, datastructures, variable usage dependencies, function calls and so on. This information hardly reveals any underlying functional purpose. For a large system, this information becomes overwhelmingly large for a maintainer to manually derive any functional intent out of it. Moreover, for a system with millions of lines of code, the memory requirement to hold the structural information and perform various analysis often becomes a bottleneck. An important step to comprehend the functional intent of the system (or the intended functional architecture) is to identify the business topics that exist in the system, around which the high level components (or modules) have been implemented. For example consider a large banking application that deals with customers, bank accounts, credit cards, interest and so on. A maintainer without any application knowledge will find it difficult to add a new interest calculation logic. However, if it is possible to extract the business topics such as customer, interest from the source code and establish an association between interest with various program elements, it would be of immense help to the maintainer to identify the related functions, files, classes and data structures and carry out the required changes for interest calculation. This in turn can make a novice programmer much more productive in maintaining a system, specially when the software is in the order of millions of lines of code with little documentation. A plausible technique to identify such topics is to derive semantic information by extracting and analyzing various important keywords from the source code text [13]. It is often the case that the original authors of the code leave hints to the meaning of program elements in the form of keywords in files, functions, data type names and so on. For
2 instance, it is highly common to use keywords like proxy, http while implementing an http-proxy functionality. Similarly, for a banking application one would surely like to use a keyword like interest in implementing functions, classes and data structures pertaining to interest calculation. Assuming that the meaningful keywords do exist in program elements, is it possible to semantically correlate these keywords to meaningful clusters where each meaningful cluster of keywords can be interpreted as a Topic? For instance, is it possible to group all proxy related keywords together into one cluster and identify it as proxy topic and authentication related keywords into another cluster forming the authentication topic? If this is possible, one can subsequently establish association between the topic proxy and various program elements (files, functions or data structures) pertaining to proxy. This paper addresses the above problem and proposes a human assisted approach based on the Latent Dirichlet Allocation (LDA) [7] for identifying topics in source code. LDA has been quite popular in the realm of text document classification and identifying topics from text documents. To the best of our knowledge, This is the first attempt at applying LDA in the context of source code analysis. The paper is organized as follows: In the next section we provide a brief review of the literature relevant to our work and the necessary background information on LDA. Section 3 discusses the applicability of LDA for extracting domain topics from source code and provides an interpretation of the LDA model in the context of source code. A detailed description of extracting domain topics from source code using LDA is presented in section 4. We have applied LDA on a number of open source and proprietary systems. Section 5 presents the results obtained. Advantages and disadvantages of the presented LDA based method and some of the interesting observations made during our experimentation are presented in Section 6. Finally, Section 7 discusses the future research directions and concludes the paper. 2. BACKGROUND AND RELATED WORK Researchers have long recognized the importance of linguistic information such as identifier names and comments in program comprehension. For instance, Biggerstaff et al. [5] have suggested assignment of domain concepts as an approach to program comprehension. Tonella et al. [8] have proposed function names and signatures to obtain domain specific information. Anquetil et al.[3] have suggested that the information obtained from the name of file often carry the functional intent of the source code specified in the file. Wilde et al.[24] have also suggested usage of linguistic information to identify the functional intent of the system. Since then, linguistic information has been used in various program analysis and maintenance tasks such as traceability between external documentation and source code [4, 16], feature location 1 [17, 21, 25], identifying high level conceptual clones [15] and so on. Recently, linguistic information has also been used to identify topics in source code and subsequently used for software clustering [13] and software categorization [11]. Kuhn et al.[13] have used Latent Semantic Analysis (LSA) [9] based approach for identifying topics in source code by 1 Feature location is sometimes referred to as concept location semantically clustering software artifacts such as methods, files or packages based on identifier names and comments. Our approach differs from that of Kuhn et al. in two ways. Firstly, and most importantly, our interpretation of a topic is different from that of Kuhn. Kuhn interprets semantically clustered software artifacts (like methods, files etc.) as topics whereas we interpret a set of semantically related linguistic terms derived from identifier names and comments as a topic. Another important difference is in the approach used for semantic clustering. While Kuhn et al. have adopted LSA to cluster a set of meaningful software artifacts, our approach of clustering linguistic terms is based on the Latent Dirichlet Allocation. Kawaguchi et al. [11] uses linguistic information in source code for automatically identifying categories and categorizing open source repositories. A cluster of related identifiers is considered as a category. In our case, we consider a cluster of terms derived from identifiers as a topic ; thus a topic can certainly be considered synonymous to a category. However, our approach of clustering semantically related identifier terms differs from the approach suggested by Kawaguchi et al. [11]. Kawaguchi et al. first uses LSA to derive pairwise similarity between the terms and then apply a clustering algorithm to cluster similar terms together. The LDA based approach we have adopted alleviates the need of having two steps. Since LDA is essentially a topic modeling technique, it not only discovers similarity between terms, it also creates a cluster of similar terms to form a topic. In the rest of this section, we provide a brief description of LDA and its use in extracting topics from text documents. 2.1 LDA Latent Dirichlet Allocation (LDA) [7] is a statistical model, specifically a topic model, originally used in the area of natural langauge processing for representing text documents. The basic idea of LDA is that a document can be considered as a mixture of a limited number of topics and each meaningful word in the document can be associated with one of these topics. Given a corpus of documents, LDA attempts to discover the following: It identifies a set of topics It associates a set of words with a topic It defines a specific mixture of these topics for each document in the corpus. LDA has been applied to extract topics from text documents. For instance, Newman et al.[19] applied LDA to derive 400 topics such as September 11 attacks, Harry Potter, Basketball and Holidays from a corpus of New York Times news articles and represent each news article as a mixture of these topics. LDA has also been applied for identification of topics in a number of different areas. For instance, LDA has been used to find scientific topics from abstracts of papers published in the proceedings of the national academy of sciences [10]. McCallum et al. [18] have proposed LDA to extract topics from social networks and apply it to a collection of 250,000 Enron s. A variation on LDA has also been used by Steyvers et al. [22] to analyze 160,000 abstracts from the citeseer computer science collection. Recently, Zheng et al. [6] have applied LDA to obtain various biological concepts from a protein related corpus.
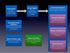
3 These applications of LDA seem to indicate that the technique can be effective in identifying latent topics and summarizing large corpus of text documents LDA Model For the sake of completeness, we briefly introduce the LDA model. A thorough and complete description of the LDA model can be found in [7]. The vocabulary for describing the LDA model is as follows: word A word is a basic unit defined to be an item from a vocabulary of size W. document A document is a sequence of N words denoted by d = (w 1,, w N ) where w n is the nth word in the sequence. corpus A corpus is a collection of M documents denoted by D = {d 1,, d M }. In the statistical natural language processing, it is common to model each document d as a multinomial distribution θ (d) over T topics, and each topic z j, j = 1 T as a multinomial distribution φ (j) over the set of words W. In order to discover the set of topics used and the distribution of these topics in each document in a corpus of documents D, we need to obtain an estimate of φ and θ. Blei et al. [7] have shown that the existing techniques of estimating φ and θ are slow to converge and propose a new model- LDA. The LDA based model assumes a prior Dirichlet distribution on θ, thus allowing the estimation of φ without requiring the estimation of θ. LDA assumes a generative process for creating a document [7] as presented below. 1. choose N P oisson(ξ) : Select the number of words N 2. θ Dir(α) : Select θ from the dirichlet distribution parameterized by α. 3. For each w n w do (a) Choose a topic z n Multinomial(θ) (b) Choose a word w n from p(w n z n, β), a multinomial probability φ zn In this model, various distributions namely, the set of topics, topic distribution for each of the documents and word probabilities for each of the topics are in general intractable for exact inference [7]. Hence a wide variety of approximate algorithms are considered for LDA. These algorithms attempt to maximize likelihood of the corpus given the model. A few algorithms have been proposed for fitting the LDA model to a text corpus such as variational Bayes [7], expectation propagation [14], and Gibbs sampling [10]. 3. APPLYING LDA TO SOURCE CODE Given that LDA has been successfully applied to large corpus of text data (as discussed in Section 2.1), it is interesting to explore i) how applicable it is in the context of source code ii) how effective the technique is in identifying business topics in a large software system. To apply LDA in source code, we consider a software system to be a collection of source code files and the software system is associated with a set of business domain concepts (or topics). For instance, the Apache web server implements functionality associated with http-proxy, authentication, server, caching and so on. Similarly, a database server like Postgresql implements functionality related to storage management. Moreover, there exists a many-many relationship between these topics like authentication, storage management and the source code files that implement these topics. Thus a source code file can be thought of as a mixture of these domain topics. Applying LDA to the source code now reduces to mapping source code entities of a software system to the LDA model, described in Table 1. Given this mapping, applica- LDA Model word document corpus Source Code Entities We define domain specific keywords extracted from names of program elements such as functions, files, data structures and comments to be the vocabulary set with cardinality V. A word w is an item from this vocabulary. A source code file becomes a document in LDA parlance. For our purpose, we represent a document f d = (w 1, w 2,..., w N ) to be a sequence of N domain specific keywords. The software system S = {f 1, f 2,..., f M } having M source code files forms the corpus. Table 1: Mapping LDA to Source Code tion of LDA to source code corpus is not difficult. Given a software system consisting of a set of source code files, domain related words are extracted from each of the source code files. Using this, a source code file-word matrix is constructed where source code files form the rows, domain words form the columns and each cell represents the weighted occurrence of the word, representing the column, in the source code file representing the row. This source code file-word matrix is provided as input to LDA. The result of LDA is a set of topics and a distribution of these topics in each source code file. A topic is a collection of domain words along with the importance of each word to the topic represented as a numeric fraction. 4. IMPLEMENTATION We have implemented a tool for static analysis of code. Figure 1 shows a part of this tool that specifically deals with topic extraction, topic location identification[5, 24], visualization of the topic distribution and a modularity analysis based on domain topics. The main input of LDA based topic extraction is a documentword matrix wd[w, f d ] = η where η is a value indicating the importance of the word w in the file f d. We will shortly describe an approach to compute η based on the number and the place of occurrences of w in f d. Our current implementation uses the Gibbs sampling method [10] that uses a markov chain monte carlo method to converge to the target
4 Figure 1: Tool Block diagram distributions in an iterative manner. The detailed description of this method is not in scope of this paper. Input Parameters. Our tool, based on the LDA approach, takes two parameters α and β (as described in Section 2.1.1) and creates the distribution φ of words over topics and the distribution θ of topics over documents. In addition to the parameters α and β the tool also requires the number of iterations. Recall that LDA defines a topic as a probability distribution of over all the terms in the corpus. We have defined an user specified cut-off value Ψ which is used to discern the most important words for each topic. 4.1 Keyword Extraction In order to create a document-word matrix for LDA, it is extremely important to find out meaningful domain related words in the source code. Approaches that apply LDA to linguistic text documents consider each word in the document for this purpose. However, unlike a plain text document a source code file is a structured document and it is definitely not appropriate to assume that each word in the file would be domain related. Firstly, a large percentage of words in source code files constitute the programming language syntax, such as for, if, class, return, while and so on. Moreover, domain keywords are often embedded inside identifier names as subwords and identifier names need to be split appropriately to extract the relevant subwords. Given this observation we propose the following steps to extract meaningful keywords from source code files: 1. Fact Extraction. 2. Splitting of identifiers and comments into keywords. 3. Stemming the keywords into their respective common roots. 4. Filtering of keywords to eliminate keywords that do not indicate any business concept. Fact Extraction. Fact extraction is the process of parsing source code documents and extracting meta-data of interest such as files, functions, function dependencies, data structures etc. We have used source navigator[1] for extracting facts from source code. Identifier Splitting. Splitting of identifiers into meaningful subwords is essential because unlike a natural language text where each word is independent and can be found in a dictionary, source code identifier names are generally not independent words but a sequence of meaningful chunks of letters and acronyms delimited by some character or through some naming convention. For instance a function named add auth info in httpd source code constitutes of three meaningful chunks of letters add, auth and info delimited by. The vocabulary we use for such meaningful chunks of letters is keyword. Each identifier is split into a set of keywords. In order to perform this splitting it is essential to know how the identifier names are delimited. There are a number of schemes such as underscore, hyphen, or through capitalization of specific letters (camel case) as in getloan- Details. We have implemented a regular expression based identifier splitting program in Perl. Stemming. Generally keywords in source code are used both singularly as well as in plural. For example loan and loans. In our analysis it is not necessary to consider them as two different keywords. Hence we unify all such keywords by stemming them to their common root. Also, It is a common practice[23, 12] to stem terms in order to improve the results of analysis. We have used the Porter s stemming algorithm [20] for stemming all words into a common root. Filtering. Not all keywords are indicators of topics in the domain. For instance keywords such as get and set are very generic and a stop-words list is employed to filter out such terms. 4.2 File Keyword Mapping Having identified a set of unique keywords for a given software system, we now compute the wd matrix. For this purpose, we compute a weighted sum of the number of occurrences of a word w in a file f d as follows: 1. We define a heuristic weightage λ : {lt} ℵ that assigns a user-defined positive integer to a locationtype lt. A location-type lt denotes the structural part of a source code file such as file name, function name, formal parameter names, comment, data-structure name and so on from which a keyword has been obtained. The weightage given to a word obtained from a function name would be different from a word obtained from a data structure name. 2. The importance factor wd[w, f d ] for a word w occurring in the file f d is computed by the weighted sum of the frequency of occurrences of w for each location type lt i in a source code file f d. That is, wd[w, f d ] = X lt i λ(lt i) ν(w, f d, lt i) where ν(w, f d, lt i) denotes the frequency of occurrence of the word w in the location type lt i of the source file f d. In order to illustrate the calculation of the importance factor wd consider the following code snippet from the file OrderDetails.java.
5 public class OrderDetails implements java.io.serializable { private String orderid; private String userid; private String orderdate; private float ordervalue; private String orderstatus; } public String getorderstatus() { return(orderstatus); } As discussed in section 4.1, identifier names are split to get meaningful domain words and importance factor calculated for each of the words. One such word that is extracted from the above code snippet is Order which occurs in comments and names of different type of identifiers such as in class name, attribute name and method name. These different types of sources for words constitute our set of location types lt. Generally, in an object oriented system, classes represent domain objects and their names are more likely to yield domain words that are important for that class. Hence, λ(class) generally is assigned higher value by domain experts than λ(attribute). Let us assume that in this particular example λ(class) equals 2, λ(attribute) equals 1 and λ(method) equals 1. The importance factor of the word Order in the above code snippet as calculated according to the formula given above is 7. wd[order, OrderDetails.java] = = 7 Similarly, weighted occurrence is calculated for other words such as details, user and status. 4.3 Topic labeling LDA could not satisfactorily derive a human understandable label for an identified topic. In most of the cases, the terms from which a label can be derived are abbreviations of business concepts or acronyms. As a result it becomes hard to create a meaningful label for a topic automatically. In the current version of the tool, identified topics have been labeled manually. 5. CASE STUDIES We have tested our approach on a number of open source and proprietary systems. In the rest of this section we discuss the results obtained using some of the topics as examples. 5.1 Topic Extraction for Apache We extracted 30 topics for Apache. For the sake of brevity we list only two topics, namely SSL and Logging. Table 1(a) lists the top keywords for topic SSL and their corresponding probability of occurrence when a random keyword is generated from the topic SSL. Our tool is able to extract not just the domain topics, but also infrastructure-level topics and cross cutting topics. For instance, logging is a topic that cuts across files and modules. Our tool, based on LDA, is able to cluster together all logging related keywords together as shown in table 1(b) that lists the top keywords for topic Logging and their corresponding probability values. (a) Topic labeled as SSL ssl expr init engine var ctx ptemp mctx lookup modssl ca (b) Topic labeled as Logging log request mod config name headers autoindex format cmd header add Table 2: Sample Topics extracted from Apache source code 5.2 Topic Extraction For Petstore In order to investigate the effect of naming on topic extraction results we considered Petstore, a J2EE blueprint implementation by Sun Microsystems. Being a reference J2EE implementation, it has followed good java naming conventions and a large number of identifiers have meaningful names. (a) Topic labeled as Contact Information info contact address family given telephone by (b) Topic labeled as Address Information address street city code country zip name state name end add Table 3: Sample Topics extracted from petstore source code As shown in table 2(a) we are able to successfully group all contact information related terms together. However, what is more significant in this example is that the top keywords info, contact are meaningful and indicative of the probable name of the topic. For example if we concatenate these two keywords into info contact it can be considered as a valid label for the contact information topic. Similarly, even in the case of address information topic, shown in table 2(b), the concatenation of the top keywords address and street can be used to label the address information topic. It can be observed from the sample topics extracted that good naming convention yields more meaningful names thereby simplifying the process of labeling the topics. 5.3 Synonymy and Polysemy resolution One of the key factors in extracting coherent topics and grouping semantically related keywords together is the abil-
6 ity of the algorithm employed to resolve synonymy-different words having the same meaning. We have observed that our tool is able to satisfactorily resolve synonymy to a good extent since LDA models topics in a file and words in a topic using multinomial probability distributions. For instance consider the topic labeled as transaction in PostgreSQL shown in table 5.3. LDA has identified that transaction and xact are synonymous and grouped them together in a single cluster as shown below. transaction namespace commit xact visible current abort names command start path Table 4: Transaction and Xact Synonymy resolution by LDA What s more interesting is the fact that our tool has been able to resolve polysemy-same words having different meaning in source code. A polyseme can appear in multiple domain topics depending on the context. The reason for our tool to be able to identify polyseme is not difficult to understand. Note that LDA models a topic as a distribution of terms; therefore it is perfectly valid for a term to appear in two topics with different probability values. Furthermore, LDA tries to infer a topic for a given term with the knowledge of the context of the word, i.e. the document where the word is appearing. For instance, in Linux-kernel source code we observed that the term volume has been used in the context of sound control as well as in the context of file systems. LDA is able to differentiate between these different uses of the term and has grouped the same term in different topics. 6. DISCUSSION In this section we discuss various factors that impact the results obtained. Subsequently we will discuss benefits and limitations of our approach. 6.1 Effect of number of Topics Our approach for topic extraction accepts the number of topics to be extracted as an input from the user. We have observed that varying the number of topics has a significant impact on polysemy resolution. For instance, consider the example of polysemy resolution of the keyword volume in Linux-kernel, discussed in subsection 5.3. We have conducted our experiment on Linux-kernel source code twice. In both the times we have kept all the parameters, namely α, β the number of iterations and the cut-off threshold Ψ same except for the number of topics. In the first experiment the number of topics T was set to 50 and in the second experiment T was set to 60. In both these experiments, of the total topics extracted two topics were sound related topics and one topic for file systems. Table 6.1 lists the probabilities of keyword volume in sound and file systems topic for both the experiments. Topic type Sound topic 1 Sound topic 2 file systems topic Volume probability Volume probability for Experiment1 for Experiment2 with T=50 with T= < Table 5: Effect of number of topics on polysemy resolution in Linux-kernel In our experiments we have used a value of the threshold Ψ to be for determining whether a keyword belongs to a topic or not. If the probability of a keyword associated with a topic is less than then we do not consider that keyword as indicator of that topic. In view of this, it can be observed from the table 6.1 that in experiment 1 the keyword volume has a probability of less than for topic file systems. Hence volume is associated with only the two sound related topics and not with the file systems topic. However, in experiment 2 when the number of topics was increased to 60, the probability of volume for topic file systems is This probability is greater than our threshold and hence volume is also considered as an indicator for file systems topic apart from the sound related topics. The polysemy in the keyword volume is revealed only in the second experiment with 60 topics. 6.2 Discovering optimal number of Topics The problem of identifying optimal number of topics is not specific to source code alone. Topic extraction from text documents faces a very similar problem. Griffiths and Steyvers recommend trying different numbers of topics T and suggest using the maximum likelihood method on P (w T ) [10]. Applying this technique to extract topics from Linux suggests that the optimal number of topics in the case of Linux is 270 as shown in figure 2. Figure 2: Linux Inferring optimum number of topics for However, automatically inferring the number of topics by maximizing the likelihood is not without problems.
7 Number of Topics:. As discussed in section 6.2, the log-likelihood method for estimating the number of topics is not always appropriate and in a number of cases the number of topics is better supplied by domain experts and architects of the system. During our experiments we have observed that one needs to try different number of topics and repeat the topic extraction process to get a set of topics of acceptable quality. Figure 3: log-likelihood graph for our proprietary system We applied our tool to extract topics for a very large proprietary business application having multi-million lines of C code. The number of topics predicted using the likelihood method was much larger than what the architects and domain experts of the proprietary system considered reasonable. As shown in figure 3, likelihood peaked at T = 600 suggesting that the optimal number of topics for our system was 600. However, the architects and domain experts felt that the resonable number of topics to be around Effect of α and β As discussed in section 2.1.1, the LDA model accepts two parameters α and β. α controls the division of documents into topics and β controls division of topics into words. Larger values of β yield coarser topics and larger values of α yields coarser distribution of document into topics. Hence the right value of α and β is needed to derive good quality topics and assignment of topics to documents. Some of the implementations of LDA estimate these values on-the-fly while other implementations rely on the user to provide appropriate values. In our implementation the values of α and β needs to be provided by the user. 6.4 Human Intervention Even though LDA based topic extraction presented in this paper is automatic and unsupervised, we believe that human intervention is necessary in a number of aspects to achieve results of acceptable quality. In this subsection we point out areas of our method which would be helped by human intervention. Expert delineated Keyword Filtering:. Both keyword extraction and subsequent filtering has impact on the quality of the results obtained. The vocabulary of source code is much smaller than that of natural language text corpus and hence the effect of missing or incorrect terms is much stronger. Also, in the context of keyword extraction from identifiers in the program, we have observed that not all identifiers are equally good indicators of the business topics. For this purpose we have introduced the weighing scheme λ as described in Section 4.2 where an expert, for instance, can assign more weight to file names over say comments in the program. Human intervention can also improve the filtering of keywords by identifying infrastructure and domain specific stop words. For instance EJB, get, set are some of the common keywords which needs to be filtered out. Topic validation and labeling:. In our experience topic extraction has been an iterative process. Topics extracted initially are evaluated and based on the results keyword extraction and filtering heuristics are updated and the α and β parameters varied to extract better topics. It is difficult to automatically evaluate the quality of topics obtained. We needed a domain expert who can manually examine the cluster of terms and check if it truly represents a domain topic. Moreover, when a domain topic has been identified labeling has to be done manually. 7. CONCLUSION AND FUTURE WORK In this paper we have investigated the applicability of LDA in the context of program comprehension and proposed an approach based on LDA for topic extraction from source code. Experiments on several open source and proprietary systems revealed that our tool is able to satisfactorily extract some of the domain topics but not all. We also made an observation that certain human input is needed in order to improve the quality of topics extracted. One disadvantage of LDA is that it does not derive any interrelationship between the extracted topics nor identify topics at various level of granularity. As part of our future work we plan to investigate approaches to extract topics at various levels of granularity and identify various relations between them. we also intend to compare other approaches to topics extraction based on LSA to the LDA based approach presented here. Finally, We believe that the proposed approach based on LDA for business topic extraction is promising and warrants further research and validation. 8. REFERENCES [1] Source navigator [2] P. Anderson and M. Zarins. The codesurfer software understanding platform. In IWPC, pages IEEE Computer Society, [3] N. Anquetil and T. C. Lethbridge. Recovering software architecture from the names of source files. Journal of Software Maintenance: Research and Practice, 11: , [4] G. Antoniol, G. Canfora, G. Casazza, A. D. Lucia, and E. Merlo. Recovering traceability links between code and documentation. IEEE Transactions in Software Engineering, 28(10): , [5] T. J. Biggerstaff, B. G. Mitbander, and D. Webster. Program understanding and the concept assignment problem. Communications of the ACM, 37(5):72 83, May [6] Z. Bin, M. David, and L. Xinghua. Identifying biological concepts from a protein-related corpus with a probabilistic topic model. BMC Bioinformatics, 7, 2006.
8 [7] D. Blei, A. Ng, and M. Jordan. Latent dirichlet allocation. Journal of Machine Learning Research, 3: , [8] B. Caprile and P. Tonella. Nomen est omen: Analyzing the language of function identifiers. In Proceedings of the Sixth Working Conference on Reverse Engineering, [9] S. Deerwester, S. T. Dumais, G. W. Furnas, and T. K. Landauer. Indexing by latent semantic analysis. Journal of the American Society for Information Science, 41: , [10] T. Griffiths and M. Steyvers. Finding scientific topics. In Proceedings of the National Academy of Sciences, pages , [11] S. Kawaguchi, P. K. Garg, M. Matsushita, and K. Inoue. MUDABlue: An automatic categorization system for open source repositories. In APSEC, pages IEEE Computer Society, [12] A. Kuhn. Semantic clustering: Making use of linguistic information to reveal concepts in source code. Master s thesis, University of Bern, [13] A. Kuhn, S. Ducasse, and T. Gîrba. Semantic clustering: Identifying topics in source code. IST, To appear. [14] J. Lafferty and T. Minka. Expectation-propagation for the generative aspect model. In Proceedings of the 18th Conference on Uncertainty in Artificial Intelligence, [15] A. Marcus and J. I. Maletic. Identification of high-level concept clones in source code. In Proceedings of the 16th International Conference on Automated Software Engineering (ASE 2001), pages , Nov [16] A. Marcus and J. I. Maletic. Recovering documentation-to-source-code traceability links using latent semantic indexing. In International Conference on Software Engineering, pages IEEE Computer Society Press, may [17] A. Marcus, A. Sergeyev, V. Rajlich, and J. Maletic. An information retrieval approach to concept location in source code. In Proceedings of the 11th Working Conference on Reverse Engineering (WCRE 2004), pages , Nov [18] A. McCallum, A. Corrada-Emmanuel, and X. Wang. Topic and role discovery in social networks. In L. P. Kaelbling and A. Saffiotti, editors, IJCAI, pages Professional Book Center, [19] D. Newman, C. Chemudugunta, P. Smyth, and M. Steyvers. Analyzing entities and topics in news articles using statistical topic models. In Lecture Notes on Computer Science. Springer-Verlag, [20] M. F. Porter. An algorithm for suffix stripping. Morgan Kaufmann Publishers Inc., San Francisco, CA, USA, [21] D. Poshyvanyk and A. Marcus. Combining formal concept analysis with information retrieval for concept location in source code. In ICPC, pages IEEE Computer Society, [22] M. Steyvers, P. Smyth, M. Rosen-Zvi, and T. L. Griffiths. Probabilistic author-topic models for information discovery. In W. Kim, R. Kohavi, J. Gehrke, and W. DuMouchel, editors, KDD, pages ACM, [23] S. Ugurel, R. Krovetz, C. L. Giles, D. M. Pennock, E. J. Glover, and H. Zha. What s the code? automatic classification of source code archives. In Proceedings of the eigth ACM SIGKDD international conference on Knowledge discovery and data mining, pages , [24] N. Wilde, M. Buckellew, H. Page, V. Rajlich, and L. Pounds. A comparison of methods for locating features in legacy software. Journal of Systems and Software, 65(2): , [25] W. Zhao, L. Zhang, Y. Liu, J. Sun, and F. Yang. Sniafl: Towards a static noninteractive approach to feature location. ACM Transactions on Software Engineering and Methodology, 15(2): , April 2006.
131-1. Adding New Level in KDD to Make the Web Usage Mining More Efficient. Abstract. 1. Introduction [1]. 1/10
![131-1. Adding New Level in KDD to Make the Web Usage Mining More Efficient. Abstract. 1. Introduction [1]. 1/10 131-1. Adding New Level in KDD to Make the Web Usage Mining More Efficient. Abstract. 1. Introduction [1]. 1/10](/thumbs/25/4963058.jpg) 1/10 131-1 Adding New Level in KDD to Make the Web Usage Mining More Efficient Mohammad Ala a AL_Hamami PHD Student, Lecturer m_ah_1@yahoocom Soukaena Hassan Hashem PHD Student, Lecturer soukaena_hassan@yahoocom
1/10 131-1 Adding New Level in KDD to Make the Web Usage Mining More Efficient Mohammad Ala a AL_Hamami PHD Student, Lecturer m_ah_1@yahoocom Soukaena Hassan Hashem PHD Student, Lecturer soukaena_hassan@yahoocom
Latent Dirichlet Markov Allocation for Sentiment Analysis
 Latent Dirichlet Markov Allocation for Sentiment Analysis Ayoub Bagheri Isfahan University of Technology, Isfahan, Iran Intelligent Database, Data Mining and Bioinformatics Lab, Electrical and Computer
Latent Dirichlet Markov Allocation for Sentiment Analysis Ayoub Bagheri Isfahan University of Technology, Isfahan, Iran Intelligent Database, Data Mining and Bioinformatics Lab, Electrical and Computer
Verifying Business Processes Extracted from E-Commerce Systems Using Dynamic Analysis
 Verifying Business Processes Extracted from E-Commerce Systems Using Dynamic Analysis Derek Foo 1, Jin Guo 2 and Ying Zou 1 Department of Electrical and Computer Engineering 1 School of Computing 2 Queen
Verifying Business Processes Extracted from E-Commerce Systems Using Dynamic Analysis Derek Foo 1, Jin Guo 2 and Ying Zou 1 Department of Electrical and Computer Engineering 1 School of Computing 2 Queen
TRENDS IN AN INTERNATIONAL INDUSTRIAL ENGINEERING RESEARCH JOURNAL: A TEXTUAL INFORMATION ANALYSIS PERSPECTIVE. wernervanzyl@sun.ac.
 TRENDS IN AN INTERNATIONAL INDUSTRIAL ENGINEERING RESEARCH JOURNAL: A TEXTUAL INFORMATION ANALYSIS PERSPECTIVE J.W. Uys 1 *, C.S.L. Schutte 2 and W.D. Van Zyl 3 1 Indutech (Pty) Ltd., Stellenbosch, South
TRENDS IN AN INTERNATIONAL INDUSTRIAL ENGINEERING RESEARCH JOURNAL: A TEXTUAL INFORMATION ANALYSIS PERSPECTIVE J.W. Uys 1 *, C.S.L. Schutte 2 and W.D. Van Zyl 3 1 Indutech (Pty) Ltd., Stellenbosch, South
Component visualization methods for large legacy software in C/C++
 Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
Annales Mathematicae et Informaticae 44 (2015) pp. 23 33 http://ami.ektf.hu Component visualization methods for large legacy software in C/C++ Máté Cserép a, Dániel Krupp b a Eötvös Loránd University mcserep@caesar.elte.hu
Using Library Dependencies for Clustering
 Using Library Dependencies for Clustering Jochen Quante Software Engineering Group, FB03 Informatik, Universität Bremen quante@informatik.uni-bremen.de Abstract: Software clustering is an established approach
Using Library Dependencies for Clustering Jochen Quante Software Engineering Group, FB03 Informatik, Universität Bremen quante@informatik.uni-bremen.de Abstract: Software clustering is an established approach
Source Code Retrieval for Bug Localization using Latent Dirichlet Allocation
 2008 15th Working Conference on Reverse Engineering Source Code Retrieval for Bug Localization using Latent Dirichlet Allocation Stacy K. Lukins Univ. of Alabama in Huntsville slukins@cs.uah.edu Nicholas
2008 15th Working Conference on Reverse Engineering Source Code Retrieval for Bug Localization using Latent Dirichlet Allocation Stacy K. Lukins Univ. of Alabama in Huntsville slukins@cs.uah.edu Nicholas
Data Mining in Web Search Engine Optimization and User Assisted Rank Results
 Data Mining in Web Search Engine Optimization and User Assisted Rank Results Minky Jindal Institute of Technology and Management Gurgaon 122017, Haryana, India Nisha kharb Institute of Technology and Management
Data Mining in Web Search Engine Optimization and User Assisted Rank Results Minky Jindal Institute of Technology and Management Gurgaon 122017, Haryana, India Nisha kharb Institute of Technology and Management
Search Result Optimization using Annotators
 Search Result Optimization using Annotators Vishal A. Kamble 1, Amit B. Chougule 2 1 Department of Computer Science and Engineering, D Y Patil College of engineering, Kolhapur, Maharashtra, India 2 Professor,
Search Result Optimization using Annotators Vishal A. Kamble 1, Amit B. Chougule 2 1 Department of Computer Science and Engineering, D Y Patil College of engineering, Kolhapur, Maharashtra, India 2 Professor,
Topic models for Sentiment analysis: A Literature Survey
 Topic models for Sentiment analysis: A Literature Survey Nikhilkumar Jadhav 123050033 June 26, 2014 In this report, we present the work done so far in the field of sentiment analysis using topic models.
Topic models for Sentiment analysis: A Literature Survey Nikhilkumar Jadhav 123050033 June 26, 2014 In this report, we present the work done so far in the field of sentiment analysis using topic models.
Using LSI for Implementing Document Management Systems Turning unstructured data from a liability to an asset.
 White Paper Using LSI for Implementing Document Management Systems Turning unstructured data from a liability to an asset. Using LSI for Implementing Document Management Systems By Mike Harrison, Director,
White Paper Using LSI for Implementing Document Management Systems Turning unstructured data from a liability to an asset. Using LSI for Implementing Document Management Systems By Mike Harrison, Director,
Data Mining Yelp Data - Predicting rating stars from review text
 Data Mining Yelp Data - Predicting rating stars from review text Rakesh Chada Stony Brook University rchada@cs.stonybrook.edu Chetan Naik Stony Brook University cnaik@cs.stonybrook.edu ABSTRACT The majority
Data Mining Yelp Data - Predicting rating stars from review text Rakesh Chada Stony Brook University rchada@cs.stonybrook.edu Chetan Naik Stony Brook University cnaik@cs.stonybrook.edu ABSTRACT The majority
Clustering Technique in Data Mining for Text Documents
 Clustering Technique in Data Mining for Text Documents Ms.J.Sathya Priya Assistant Professor Dept Of Information Technology. Velammal Engineering College. Chennai. Ms.S.Priyadharshini Assistant Professor
Clustering Technique in Data Mining for Text Documents Ms.J.Sathya Priya Assistant Professor Dept Of Information Technology. Velammal Engineering College. Chennai. Ms.S.Priyadharshini Assistant Professor
Towards a Visually Enhanced Medical Search Engine
 Towards a Visually Enhanced Medical Search Engine Lavish Lalwani 1,2, Guido Zuccon 1, Mohamed Sharaf 2, Anthony Nguyen 1 1 The Australian e-health Research Centre, Brisbane, Queensland, Australia; 2 The
Towards a Visually Enhanced Medical Search Engine Lavish Lalwani 1,2, Guido Zuccon 1, Mohamed Sharaf 2, Anthony Nguyen 1 1 The Australian e-health Research Centre, Brisbane, Queensland, Australia; 2 The
Interactive Recovery of Requirements Traceability Links Using User Feedback and Configuration Management Logs
 Interactive Recovery of Requirements Traceability Links Using User Feedback and Configuration Management Logs Ryosuke Tsuchiya 1, Hironori Washizaki 1, Yoshiaki Fukazawa 1, Keishi Oshima 2, and Ryota Mibe
Interactive Recovery of Requirements Traceability Links Using User Feedback and Configuration Management Logs Ryosuke Tsuchiya 1, Hironori Washizaki 1, Yoshiaki Fukazawa 1, Keishi Oshima 2, and Ryota Mibe
Online Courses Recommendation based on LDA
 Online Courses Recommendation based on LDA Rel Guzman Apaza, Elizabeth Vera Cervantes, Laura Cruz Quispe, José Ochoa Luna National University of St. Agustin Arequipa - Perú {r.guzmanap,elizavvc,lvcruzq,eduardo.ol}@gmail.com
Online Courses Recommendation based on LDA Rel Guzman Apaza, Elizabeth Vera Cervantes, Laura Cruz Quispe, José Ochoa Luna National University of St. Agustin Arequipa - Perú {r.guzmanap,elizavvc,lvcruzq,eduardo.ol}@gmail.com
IT services for analyses of various data samples
 IT services for analyses of various data samples Ján Paralič, František Babič, Martin Sarnovský, Peter Butka, Cecília Havrilová, Miroslava Muchová, Michal Puheim, Martin Mikula, Gabriel Tutoky Technical
IT services for analyses of various data samples Ján Paralič, František Babič, Martin Sarnovský, Peter Butka, Cecília Havrilová, Miroslava Muchová, Michal Puheim, Martin Mikula, Gabriel Tutoky Technical
CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS
 66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
66 CHAPTER 5 INTELLIGENT TECHNIQUES TO PREVENT SQL INJECTION ATTACKS 5.1 INTRODUCTION In this research work, two new techniques have been proposed for addressing the problem of SQL injection attacks, one
MapReduce Approach to Collective Classification for Networks
 MapReduce Approach to Collective Classification for Networks Wojciech Indyk 1, Tomasz Kajdanowicz 1, Przemyslaw Kazienko 1, and Slawomir Plamowski 1 Wroclaw University of Technology, Wroclaw, Poland Faculty
MapReduce Approach to Collective Classification for Networks Wojciech Indyk 1, Tomasz Kajdanowicz 1, Przemyslaw Kazienko 1, and Slawomir Plamowski 1 Wroclaw University of Technology, Wroclaw, Poland Faculty
VCU-TSA at Semeval-2016 Task 4: Sentiment Analysis in Twitter
 VCU-TSA at Semeval-2016 Task 4: Sentiment Analysis in Twitter Gerard Briones and Kasun Amarasinghe and Bridget T. McInnes, PhD. Department of Computer Science Virginia Commonwealth University Richmond,
VCU-TSA at Semeval-2016 Task 4: Sentiment Analysis in Twitter Gerard Briones and Kasun Amarasinghe and Bridget T. McInnes, PhD. Department of Computer Science Virginia Commonwealth University Richmond,
JRefleX: Towards Supporting Small Student Software Teams
 JRefleX: Towards Supporting Small Student Software Teams Kenny Wong, Warren Blanchet, Ying Liu, Curtis Schofield, Eleni Stroulia, Zhenchang Xing Department of Computing Science University of Alberta {kenw,blanchet,yingl,schofiel,stroulia,xing}@cs.ualberta.ca
JRefleX: Towards Supporting Small Student Software Teams Kenny Wong, Warren Blanchet, Ying Liu, Curtis Schofield, Eleni Stroulia, Zhenchang Xing Department of Computing Science University of Alberta {kenw,blanchet,yingl,schofiel,stroulia,xing}@cs.ualberta.ca
Using Topic Models to Support Software Maintenance
 Using Topic Models to Support Software Maintenance Scott Grant School of Computing Queen s University Kingston, Ontario, Canada Email: scott@cs.queensu.ca James R. Cordy School of Computing Queen s University
Using Topic Models to Support Software Maintenance Scott Grant School of Computing Queen s University Kingston, Ontario, Canada Email: scott@cs.queensu.ca James R. Cordy School of Computing Queen s University
VISUALIZATION APPROACH FOR SOFTWARE PROJECTS
 Canadian Journal of Pure and Applied Sciences Vol. 9, No. 2, pp. 3431-3439, June 2015 Online ISSN: 1920-3853; Print ISSN: 1715-9997 Available online at www.cjpas.net VISUALIZATION APPROACH FOR SOFTWARE
Canadian Journal of Pure and Applied Sciences Vol. 9, No. 2, pp. 3431-3439, June 2015 Online ISSN: 1920-3853; Print ISSN: 1715-9997 Available online at www.cjpas.net VISUALIZATION APPROACH FOR SOFTWARE
SPATIAL DATA CLASSIFICATION AND DATA MINING
 , pp.-40-44. Available online at http://www. bioinfo. in/contents. php?id=42 SPATIAL DATA CLASSIFICATION AND DATA MINING RATHI J.B. * AND PATIL A.D. Department of Computer Science & Engineering, Jawaharlal
, pp.-40-44. Available online at http://www. bioinfo. in/contents. php?id=42 SPATIAL DATA CLASSIFICATION AND DATA MINING RATHI J.B. * AND PATIL A.D. Department of Computer Science & Engineering, Jawaharlal
AN EFFICIENT APPROACH TO PERFORM PRE-PROCESSING
 AN EFFIIENT APPROAH TO PERFORM PRE-PROESSING S. Prince Mary Research Scholar, Sathyabama University, hennai- 119 princemary26@gmail.com E. Baburaj Department of omputer Science & Engineering, Sun Engineering
AN EFFIIENT APPROAH TO PERFORM PRE-PROESSING S. Prince Mary Research Scholar, Sathyabama University, hennai- 119 princemary26@gmail.com E. Baburaj Department of omputer Science & Engineering, Sun Engineering
Cloud Storage-based Intelligent Document Archiving for the Management of Big Data
 Cloud Storage-based Intelligent Document Archiving for the Management of Big Data Keedong Yoo Dept. of Management Information Systems Dankook University Cheonan, Republic of Korea Abstract : The cloud
Cloud Storage-based Intelligent Document Archiving for the Management of Big Data Keedong Yoo Dept. of Management Information Systems Dankook University Cheonan, Republic of Korea Abstract : The cloud
Towards an Evaluation Framework for Topic Extraction Systems for Online Reputation Management
 Towards an Evaluation Framework for Topic Extraction Systems for Online Reputation Management Enrique Amigó 1, Damiano Spina 1, Bernardino Beotas 2, and Julio Gonzalo 1 1 Departamento de Lenguajes y Sistemas
Towards an Evaluation Framework for Topic Extraction Systems for Online Reputation Management Enrique Amigó 1, Damiano Spina 1, Bernardino Beotas 2, and Julio Gonzalo 1 1 Departamento de Lenguajes y Sistemas
A Statistical Text Mining Method for Patent Analysis
 A Statistical Text Mining Method for Patent Analysis Department of Statistics Cheongju University, shjun@cju.ac.kr Abstract Most text data from diverse document databases are unsuitable for analytical
A Statistical Text Mining Method for Patent Analysis Department of Statistics Cheongju University, shjun@cju.ac.kr Abstract Most text data from diverse document databases are unsuitable for analytical
An Empirical Study on Requirements Traceability Using Eye-Tracking
 An Empirical Study on Requirements Traceability Using Eye-Tracking Nasir Ali 1,2, Zohreh Sharafi 1,2, Yann-Gaël Guéhéneuc 1, and Giuliano Antoniol 2 1 Ptidej Team, 2 SOCCER Lab, DGIGL, École Polytechnique
An Empirical Study on Requirements Traceability Using Eye-Tracking Nasir Ali 1,2, Zohreh Sharafi 1,2, Yann-Gaël Guéhéneuc 1, and Giuliano Antoniol 2 1 Ptidej Team, 2 SOCCER Lab, DGIGL, École Polytechnique
Topic Matching Based Change Impact Analysis from Feature on User Interface of Mobile Apps
 Topic Matching Based Change Impact Analysis from Feature on User Interface of Mobile Apps Qiwen Zou 1, Xiangping Chen 2,, Yuan Huang 1,3 1 School of Information Science and Technology, Sun Yat-sen University,
Topic Matching Based Change Impact Analysis from Feature on User Interface of Mobile Apps Qiwen Zou 1, Xiangping Chen 2,, Yuan Huang 1,3 1 School of Information Science and Technology, Sun Yat-sen University,
An Eclipse Plug-In for Visualizing Java Code Dependencies on Relational Databases
 An Eclipse Plug-In for Visualizing Java Code Dependencies on Relational Databases Paul L. Bergstein, Priyanka Gariba, Vaibhavi Pisolkar, and Sheetal Subbanwad Dept. of Computer and Information Science,
An Eclipse Plug-In for Visualizing Java Code Dependencies on Relational Databases Paul L. Bergstein, Priyanka Gariba, Vaibhavi Pisolkar, and Sheetal Subbanwad Dept. of Computer and Information Science,
Flattening Enterprise Knowledge
 Flattening Enterprise Knowledge Do you Control Your Content or Does Your Content Control You? 1 Executive Summary: Enterprise Content Management (ECM) is a common buzz term and every IT manager knows it
Flattening Enterprise Knowledge Do you Control Your Content or Does Your Content Control You? 1 Executive Summary: Enterprise Content Management (ECM) is a common buzz term and every IT manager knows it
Using Data Mining Methods to Predict Personally Identifiable Information in Emails
 Using Data Mining Methods to Predict Personally Identifiable Information in Emails Liqiang Geng 1, Larry Korba 1, Xin Wang, Yunli Wang 1, Hongyu Liu 1, Yonghua You 1 1 Institute of Information Technology,
Using Data Mining Methods to Predict Personally Identifiable Information in Emails Liqiang Geng 1, Larry Korba 1, Xin Wang, Yunli Wang 1, Hongyu Liu 1, Yonghua You 1 1 Institute of Information Technology,
Model-Based Cluster Analysis for Web Users Sessions
 Model-Based Cluster Analysis for Web Users Sessions George Pallis, Lefteris Angelis, and Athena Vakali Department of Informatics, Aristotle University of Thessaloniki, 54124, Thessaloniki, Greece gpallis@ccf.auth.gr
Model-Based Cluster Analysis for Web Users Sessions George Pallis, Lefteris Angelis, and Athena Vakali Department of Informatics, Aristotle University of Thessaloniki, 54124, Thessaloniki, Greece gpallis@ccf.auth.gr
COURSE RECOMMENDER SYSTEM IN E-LEARNING
 International Journal of Computer Science and Communication Vol. 3, No. 1, January-June 2012, pp. 159-164 COURSE RECOMMENDER SYSTEM IN E-LEARNING Sunita B Aher 1, Lobo L.M.R.J. 2 1 M.E. (CSE)-II, Walchand
International Journal of Computer Science and Communication Vol. 3, No. 1, January-June 2012, pp. 159-164 COURSE RECOMMENDER SYSTEM IN E-LEARNING Sunita B Aher 1, Lobo L.M.R.J. 2 1 M.E. (CSE)-II, Walchand
dm106 TEXT MINING FOR CUSTOMER RELATIONSHIP MANAGEMENT: AN APPROACH BASED ON LATENT SEMANTIC ANALYSIS AND FUZZY CLUSTERING
 dm106 TEXT MINING FOR CUSTOMER RELATIONSHIP MANAGEMENT: AN APPROACH BASED ON LATENT SEMANTIC ANALYSIS AND FUZZY CLUSTERING ABSTRACT In most CRM (Customer Relationship Management) systems, information on
dm106 TEXT MINING FOR CUSTOMER RELATIONSHIP MANAGEMENT: AN APPROACH BASED ON LATENT SEMANTIC ANALYSIS AND FUZZY CLUSTERING ABSTRACT In most CRM (Customer Relationship Management) systems, information on
Understanding Web personalization with Web Usage Mining and its Application: Recommender System
 Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
Understanding Web personalization with Web Usage Mining and its Application: Recommender System Manoj Swami 1, Prof. Manasi Kulkarni 2 1 M.Tech (Computer-NIMS), VJTI, Mumbai. 2 Department of Computer Technology,
BUSINESS RULES AND GAP ANALYSIS
 Leading the Evolution WHITE PAPER BUSINESS RULES AND GAP ANALYSIS Discovery and management of business rules avoids business disruptions WHITE PAPER BUSINESS RULES AND GAP ANALYSIS Business Situation More
Leading the Evolution WHITE PAPER BUSINESS RULES AND GAP ANALYSIS Discovery and management of business rules avoids business disruptions WHITE PAPER BUSINESS RULES AND GAP ANALYSIS Business Situation More
Bayesian networks - Time-series models - Apache Spark & Scala
 Bayesian networks - Time-series models - Apache Spark & Scala Dr John Sandiford, CTO Bayes Server Data Science London Meetup - November 2014 1 Contents Introduction Bayesian networks Latent variables Anomaly
Bayesian networks - Time-series models - Apache Spark & Scala Dr John Sandiford, CTO Bayes Server Data Science London Meetup - November 2014 1 Contents Introduction Bayesian networks Latent variables Anomaly
International Journal of Computer Science Trends and Technology (IJCST) Volume 2 Issue 3, May-Jun 2014
 RESEARCH ARTICLE OPEN ACCESS A Survey of Data Mining: Concepts with Applications and its Future Scope Dr. Zubair Khan 1, Ashish Kumar 2, Sunny Kumar 3 M.Tech Research Scholar 2. Department of Computer
RESEARCH ARTICLE OPEN ACCESS A Survey of Data Mining: Concepts with Applications and its Future Scope Dr. Zubair Khan 1, Ashish Kumar 2, Sunny Kumar 3 M.Tech Research Scholar 2. Department of Computer
International Journal of Scientific & Engineering Research, Volume 4, Issue 11, November-2013 5 ISSN 2229-5518
 International Journal of Scientific & Engineering Research, Volume 4, Issue 11, November-2013 5 INTELLIGENT MULTIDIMENSIONAL DATABASE INTERFACE Mona Gharib Mohamed Reda Zahraa E. Mohamed Faculty of Science,
International Journal of Scientific & Engineering Research, Volume 4, Issue 11, November-2013 5 INTELLIGENT MULTIDIMENSIONAL DATABASE INTERFACE Mona Gharib Mohamed Reda Zahraa E. Mohamed Faculty of Science,
A Vague Improved Markov Model Approach for Web Page Prediction
 A Vague Improved Markov Model Approach for Web Page Prediction ABSTRACT Priya Bajaj and Supriya Raheja Department of Computer Science & Engineering, ITM University Gurgaon, Haryana 122001, India Today
A Vague Improved Markov Model Approach for Web Page Prediction ABSTRACT Priya Bajaj and Supriya Raheja Department of Computer Science & Engineering, ITM University Gurgaon, Haryana 122001, India Today
Explanation-Oriented Association Mining Using a Combination of Unsupervised and Supervised Learning Algorithms
 Explanation-Oriented Association Mining Using a Combination of Unsupervised and Supervised Learning Algorithms Y.Y. Yao, Y. Zhao, R.B. Maguire Department of Computer Science, University of Regina Regina,
Explanation-Oriented Association Mining Using a Combination of Unsupervised and Supervised Learning Algorithms Y.Y. Yao, Y. Zhao, R.B. Maguire Department of Computer Science, University of Regina Regina,
EMC Documentum Content Services for SAP iviews for Related Content
 EMC Documentum Content Services for SAP iviews for Related Content Version 6.0 Administration Guide P/N 300 005 446 Rev A01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748 9103 1 508 435 1000
EMC Documentum Content Services for SAP iviews for Related Content Version 6.0 Administration Guide P/N 300 005 446 Rev A01 EMC Corporation Corporate Headquarters: Hopkinton, MA 01748 9103 1 508 435 1000
MIRACLE at VideoCLEF 2008: Classification of Multilingual Speech Transcripts
 MIRACLE at VideoCLEF 2008: Classification of Multilingual Speech Transcripts Julio Villena-Román 1,3, Sara Lana-Serrano 2,3 1 Universidad Carlos III de Madrid 2 Universidad Politécnica de Madrid 3 DAEDALUS
MIRACLE at VideoCLEF 2008: Classification of Multilingual Speech Transcripts Julio Villena-Román 1,3, Sara Lana-Serrano 2,3 1 Universidad Carlos III de Madrid 2 Universidad Politécnica de Madrid 3 DAEDALUS
Introduction to Data Mining
 Introduction to Data Mining Jay Urbain Credits: Nazli Goharian & David Grossman @ IIT Outline Introduction Data Pre-processing Data Mining Algorithms Naïve Bayes Decision Tree Neural Network Association
Introduction to Data Mining Jay Urbain Credits: Nazli Goharian & David Grossman @ IIT Outline Introduction Data Pre-processing Data Mining Algorithms Naïve Bayes Decision Tree Neural Network Association
SERG. Reconstructing Requirements Traceability in Design and Test Using Latent Semantic Indexing
 Delft University of Technology Software Engineering Research Group Technical Report Series Reconstructing Requirements Traceability in Design and Test Using Latent Semantic Indexing Marco Lormans and Arie
Delft University of Technology Software Engineering Research Group Technical Report Series Reconstructing Requirements Traceability in Design and Test Using Latent Semantic Indexing Marco Lormans and Arie
Clustering Connectionist and Statistical Language Processing
 Clustering Connectionist and Statistical Language Processing Frank Keller keller@coli.uni-sb.de Computerlinguistik Universität des Saarlandes Clustering p.1/21 Overview clustering vs. classification supervised
Clustering Connectionist and Statistical Language Processing Frank Keller keller@coli.uni-sb.de Computerlinguistik Universität des Saarlandes Clustering p.1/21 Overview clustering vs. classification supervised
CiteSeer x in the Cloud
 Published in the 2nd USENIX Workshop on Hot Topics in Cloud Computing 2010 CiteSeer x in the Cloud Pradeep B. Teregowda Pennsylvania State University C. Lee Giles Pennsylvania State University Bhuvan Urgaonkar
Published in the 2nd USENIX Workshop on Hot Topics in Cloud Computing 2010 CiteSeer x in the Cloud Pradeep B. Teregowda Pennsylvania State University C. Lee Giles Pennsylvania State University Bhuvan Urgaonkar
An Integrated Approach to Learning Object Sequencing
 An Integrated Approach to Learning Object Sequencing Battur Tugsgerel 1, Rachid Anane 2 and Georgios Theodoropoulos 1 1 School of Computer Science, University of Birmingham, UK. {b.tugsgerel, g.k.theodoropoulos}@cs.bham.ac.uk
An Integrated Approach to Learning Object Sequencing Battur Tugsgerel 1, Rachid Anane 2 and Georgios Theodoropoulos 1 1 School of Computer Science, University of Birmingham, UK. {b.tugsgerel, g.k.theodoropoulos}@cs.bham.ac.uk
Technical Report. The KNIME Text Processing Feature:
 Technical Report The KNIME Text Processing Feature: An Introduction Dr. Killian Thiel Dr. Michael Berthold Killian.Thiel@uni-konstanz.de Michael.Berthold@uni-konstanz.de Copyright 2012 by KNIME.com AG
Technical Report The KNIME Text Processing Feature: An Introduction Dr. Killian Thiel Dr. Michael Berthold Killian.Thiel@uni-konstanz.de Michael.Berthold@uni-konstanz.de Copyright 2012 by KNIME.com AG
Incorporating Evidence in Bayesian networks with the Select Operator
 Incorporating Evidence in Bayesian networks with the Select Operator C.J. Butz and F. Fang Department of Computer Science, University of Regina Regina, Saskatchewan, Canada SAS 0A2 {butz, fang11fa}@cs.uregina.ca
Incorporating Evidence in Bayesian networks with the Select Operator C.J. Butz and F. Fang Department of Computer Science, University of Regina Regina, Saskatchewan, Canada SAS 0A2 {butz, fang11fa}@cs.uregina.ca
Data Mining Approach For Subscription-Fraud. Detection in Telecommunication Sector
 Contemporary Engineering Sciences, Vol. 7, 2014, no. 11, 515-522 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ces.2014.4431 Data Mining Approach For Subscription-Fraud Detection in Telecommunication
Contemporary Engineering Sciences, Vol. 7, 2014, no. 11, 515-522 HIKARI Ltd, www.m-hikari.com http://dx.doi.org/10.12988/ces.2014.4431 Data Mining Approach For Subscription-Fraud Detection in Telecommunication
Learning outcomes. Knowledge and understanding. Competence and skills
 Syllabus Master s Programme in Statistics and Data Mining 120 ECTS Credits Aim The rapid growth of databases provides scientists and business people with vast new resources. This programme meets the challenges
Syllabus Master s Programme in Statistics and Data Mining 120 ECTS Credits Aim The rapid growth of databases provides scientists and business people with vast new resources. This programme meets the challenges
An Analysis of the Transitions between Mobile Application Usages based on Markov Chains
 An Analysis of the Transitions between Mobile Application Usages based on Markov Chains Charles Gouin-Vallerand LICEF Research Center, Télé- Université du Québec 5800 St-Denis Boul. Montreal, QC H2S 3L5
An Analysis of the Transitions between Mobile Application Usages based on Markov Chains Charles Gouin-Vallerand LICEF Research Center, Télé- Université du Québec 5800 St-Denis Boul. Montreal, QC H2S 3L5
Management of Very Large Security Event Logs
 Management of Very Large Security Event Logs Balasubramanian Ramaiah Myungsook Klassen Computer Science Department, California Lutheran University 60 West Olsen Rd, Thousand Oaks, CA 91360, USA Abstract
Management of Very Large Security Event Logs Balasubramanian Ramaiah Myungsook Klassen Computer Science Department, California Lutheran University 60 West Olsen Rd, Thousand Oaks, CA 91360, USA Abstract
Automatic Annotation Wrapper Generation and Mining Web Database Search Result
 Automatic Annotation Wrapper Generation and Mining Web Database Search Result V.Yogam 1, K.Umamaheswari 2 1 PG student, ME Software Engineering, Anna University (BIT campus), Trichy, Tamil nadu, India
Automatic Annotation Wrapper Generation and Mining Web Database Search Result V.Yogam 1, K.Umamaheswari 2 1 PG student, ME Software Engineering, Anna University (BIT campus), Trichy, Tamil nadu, India
In this presentation, you will be introduced to data mining and the relationship with meaningful use.
 In this presentation, you will be introduced to data mining and the relationship with meaningful use. Data mining refers to the art and science of intelligent data analysis. It is the application of machine
In this presentation, you will be introduced to data mining and the relationship with meaningful use. Data mining refers to the art and science of intelligent data analysis. It is the application of machine
Rotorcraft Health Management System (RHMS)
 AIAC-11 Eleventh Australian International Aerospace Congress Rotorcraft Health Management System (RHMS) Robab Safa-Bakhsh 1, Dmitry Cherkassky 2 1 The Boeing Company, Phantom Works Philadelphia Center
AIAC-11 Eleventh Australian International Aerospace Congress Rotorcraft Health Management System (RHMS) Robab Safa-Bakhsh 1, Dmitry Cherkassky 2 1 The Boeing Company, Phantom Works Philadelphia Center
Experiments in Web Page Classification for Semantic Web
 Experiments in Web Page Classification for Semantic Web Asad Satti, Nick Cercone, Vlado Kešelj Faculty of Computer Science, Dalhousie University E-mail: {rashid,nick,vlado}@cs.dal.ca Abstract We address
Experiments in Web Page Classification for Semantic Web Asad Satti, Nick Cercone, Vlado Kešelj Faculty of Computer Science, Dalhousie University E-mail: {rashid,nick,vlado}@cs.dal.ca Abstract We address
Comparing Methods to Identify Defect Reports in a Change Management Database
 Comparing Methods to Identify Defect Reports in a Change Management Database Elaine J. Weyuker, Thomas J. Ostrand AT&T Labs - Research 180 Park Avenue Florham Park, NJ 07932 (weyuker,ostrand)@research.att.com
Comparing Methods to Identify Defect Reports in a Change Management Database Elaine J. Weyuker, Thomas J. Ostrand AT&T Labs - Research 180 Park Avenue Florham Park, NJ 07932 (weyuker,ostrand)@research.att.com
Intelligent Search for Answering Clinical Questions Coronado Group, Ltd. Innovation Initiatives
 Intelligent Search for Answering Clinical Questions Coronado Group, Ltd. Innovation Initiatives Search The Way You Think Copyright 2009 Coronado, Ltd. All rights reserved. All other product names and logos
Intelligent Search for Answering Clinical Questions Coronado Group, Ltd. Innovation Initiatives Search The Way You Think Copyright 2009 Coronado, Ltd. All rights reserved. All other product names and logos
Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop
 Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop Sergio Hernández 1, S.J. van Zelst 2, Joaquín Ezpeleta 1, and Wil M.P. van der Aalst 2 1 Department of Computer Science and Systems Engineering
Handling Big(ger) Logs: Connecting ProM 6 to Apache Hadoop Sergio Hernández 1, S.J. van Zelst 2, Joaquín Ezpeleta 1, and Wil M.P. van der Aalst 2 1 Department of Computer Science and Systems Engineering
Semantic Concept Based Retrieval of Software Bug Report with Feedback
 Semantic Concept Based Retrieval of Software Bug Report with Feedback Tao Zhang, Byungjeong Lee, Hanjoon Kim, Jaeho Lee, Sooyong Kang, and Ilhoon Shin Abstract Mining software bugs provides a way to develop
Semantic Concept Based Retrieval of Software Bug Report with Feedback Tao Zhang, Byungjeong Lee, Hanjoon Kim, Jaeho Lee, Sooyong Kang, and Ilhoon Shin Abstract Mining software bugs provides a way to develop
Programs are Knowledge Bases
 Programs are Knowledge Bases Daniel Ratiu and Florian Deissenboeck Institut für Informatik, Technische Universität München Boltzmannstr. 3, D-85748 Garching b. München, Germany {ratiu deissenb}@in.tum.de
Programs are Knowledge Bases Daniel Ratiu and Florian Deissenboeck Institut für Informatik, Technische Universität München Boltzmannstr. 3, D-85748 Garching b. München, Germany {ratiu deissenb}@in.tum.de
Data, Measurements, Features
 Data, Measurements, Features Middle East Technical University Dep. of Computer Engineering 2009 compiled by V. Atalay What do you think of when someone says Data? We might abstract the idea that data are
Data, Measurements, Features Middle East Technical University Dep. of Computer Engineering 2009 compiled by V. Atalay What do you think of when someone says Data? We might abstract the idea that data are
Simple Language Models for Spam Detection
 Simple Language Models for Spam Detection Egidio Terra Faculty of Informatics PUC/RS - Brazil Abstract For this year s Spam track we used classifiers based on language models. These models are used to
Simple Language Models for Spam Detection Egidio Terra Faculty of Informatics PUC/RS - Brazil Abstract For this year s Spam track we used classifiers based on language models. These models are used to
REST Client Pattern. [Draft] Bhim P. Upadhyaya ABSTRACT
![REST Client Pattern. [Draft] Bhim P. Upadhyaya ABSTRACT REST Client Pattern. [Draft] Bhim P. Upadhyaya ABSTRACT](/thumbs/37/17683249.jpg) REST Client Pattern [Draft] Bhim P. Upadhyaya EqualInformation Chicago, USA bpupadhyaya@gmail.com ABSTRACT Service oriented architecture (SOA) is a common architectural practice in large enterprises. There
REST Client Pattern [Draft] Bhim P. Upadhyaya EqualInformation Chicago, USA bpupadhyaya@gmail.com ABSTRACT Service oriented architecture (SOA) is a common architectural practice in large enterprises. There
A Scheme for Automation of Telecom Data Processing for Business Application
 A Scheme for Automation of Telecom Data Processing for Business Application 1 T.R.Gopalakrishnan Nair, 2 Vithal. J. Sampagar, 3 Suma V, 4 Ezhilarasan Maharajan 1, 3 Research and Industry Incubation Center,
A Scheme for Automation of Telecom Data Processing for Business Application 1 T.R.Gopalakrishnan Nair, 2 Vithal. J. Sampagar, 3 Suma V, 4 Ezhilarasan Maharajan 1, 3 Research and Industry Incubation Center,
The Missing Link - A Probabilistic Model of Document Content and Hypertext Connectivity
 The Missing Link - A Probabilistic Model of Document Content and Hypertext Connectivity David Cohn Burning Glass Technologies 201 South Craig St, Suite 2W Pittsburgh, PA 15213 david.cohn@burning-glass.com
The Missing Link - A Probabilistic Model of Document Content and Hypertext Connectivity David Cohn Burning Glass Technologies 201 South Craig St, Suite 2W Pittsburgh, PA 15213 david.cohn@burning-glass.com
AN SQL EXTENSION FOR LATENT SEMANTIC ANALYSIS
 Advances in Information Mining ISSN: 0975 3265 & E-ISSN: 0975 9093, Vol. 3, Issue 1, 2011, pp-19-25 Available online at http://www.bioinfo.in/contents.php?id=32 AN SQL EXTENSION FOR LATENT SEMANTIC ANALYSIS
Advances in Information Mining ISSN: 0975 3265 & E-ISSN: 0975 9093, Vol. 3, Issue 1, 2011, pp-19-25 Available online at http://www.bioinfo.in/contents.php?id=32 AN SQL EXTENSION FOR LATENT SEMANTIC ANALYSIS
Sheeba J.I1, Vivekanandan K2
 IMPROVED UNSUPERVISED FRAMEWORK FOR SOLVING SYNONYM, HOMONYM, HYPONYMY & POLYSEMY PROBLEMS FROM EXTRACTED KEYWORDS AND IDENTIFY TOPICS IN MEETING TRANSCRIPTS Sheeba J.I1, Vivekanandan K2 1 Assistant Professor,sheeba@pec.edu
IMPROVED UNSUPERVISED FRAMEWORK FOR SOLVING SYNONYM, HOMONYM, HYPONYMY & POLYSEMY PROBLEMS FROM EXTRACTED KEYWORDS AND IDENTIFY TOPICS IN MEETING TRANSCRIPTS Sheeba J.I1, Vivekanandan K2 1 Assistant Professor,sheeba@pec.edu
Training Management System for Aircraft Engineering: indexing and retrieval of Corporate Learning Object
 Training Management System for Aircraft Engineering: indexing and retrieval of Corporate Learning Object Anne Monceaux 1, Joanna Guss 1 1 EADS-CCR, Centreda 1, 4 Avenue Didier Daurat 31700 Blagnac France
Training Management System for Aircraft Engineering: indexing and retrieval of Corporate Learning Object Anne Monceaux 1, Joanna Guss 1 1 EADS-CCR, Centreda 1, 4 Avenue Didier Daurat 31700 Blagnac France
CHAPTER 1 INTRODUCTION
 1 CHAPTER 1 INTRODUCTION Exploration is a process of discovery. In the database exploration process, an analyst executes a sequence of transformations over a collection of data structures to discover useful
1 CHAPTER 1 INTRODUCTION Exploration is a process of discovery. In the database exploration process, an analyst executes a sequence of transformations over a collection of data structures to discover useful
Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2
 Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2 Department of Computer Engineering, YMCA University of Science & Technology, Faridabad,
Optimization of Search Results with Duplicate Page Elimination using Usage Data A. K. Sharma 1, Neelam Duhan 2 1, 2 Department of Computer Engineering, YMCA University of Science & Technology, Faridabad,
Chapter 5. Regression Testing of Web-Components
 Chapter 5 Regression Testing of Web-Components With emergence of services and information over the internet and intranet, Web sites have become complex. Web components and their underlying parts are evolving
Chapter 5 Regression Testing of Web-Components With emergence of services and information over the internet and intranet, Web sites have become complex. Web components and their underlying parts are evolving
Term extraction for user profiling: evaluation by the user
 Term extraction for user profiling: evaluation by the user Suzan Verberne 1, Maya Sappelli 1,2, Wessel Kraaij 1,2 1 Institute for Computing and Information Sciences, Radboud University Nijmegen 2 TNO,
Term extraction for user profiling: evaluation by the user Suzan Verberne 1, Maya Sappelli 1,2, Wessel Kraaij 1,2 1 Institute for Computing and Information Sciences, Radboud University Nijmegen 2 TNO,
Mining Signatures in Healthcare Data Based on Event Sequences and its Applications
 Mining Signatures in Healthcare Data Based on Event Sequences and its Applications Siddhanth Gokarapu 1, J. Laxmi Narayana 2 1 Student, Computer Science & Engineering-Department, JNTU Hyderabad India 1
Mining Signatures in Healthcare Data Based on Event Sequences and its Applications Siddhanth Gokarapu 1, J. Laxmi Narayana 2 1 Student, Computer Science & Engineering-Department, JNTU Hyderabad India 1
Test Run Analysis Interpretation (AI) Made Easy with OpenLoad
 Test Run Analysis Interpretation (AI) Made Easy with OpenLoad OpenDemand Systems, Inc. Abstract / Executive Summary As Web applications and services become more complex, it becomes increasingly difficult
Test Run Analysis Interpretation (AI) Made Easy with OpenLoad OpenDemand Systems, Inc. Abstract / Executive Summary As Web applications and services become more complex, it becomes increasingly difficult
ECE 578 Term Paper Network Security through IP packet Filtering
 ECE 578 Term Paper Network Security through IP packet Filtering Cheedu Venugopal Reddy Dept of Electrical Eng and Comp science Oregon State University Bin Cao Dept of electrical Eng and Comp science Oregon
ECE 578 Term Paper Network Security through IP packet Filtering Cheedu Venugopal Reddy Dept of Electrical Eng and Comp science Oregon State University Bin Cao Dept of electrical Eng and Comp science Oregon
APPLICATION OF DATA MINING TECHNIQUES FOR BUILDING SIMULATION PERFORMANCE PREDICTION ANALYSIS. email paul@esru.strath.ac.uk
 Eighth International IBPSA Conference Eindhoven, Netherlands August -4, 2003 APPLICATION OF DATA MINING TECHNIQUES FOR BUILDING SIMULATION PERFORMANCE PREDICTION Christoph Morbitzer, Paul Strachan 2 and
Eighth International IBPSA Conference Eindhoven, Netherlands August -4, 2003 APPLICATION OF DATA MINING TECHNIQUES FOR BUILDING SIMULATION PERFORMANCE PREDICTION Christoph Morbitzer, Paul Strachan 2 and
Mobile Storage and Search Engine of Information Oriented to Food Cloud
 Advance Journal of Food Science and Technology 5(10): 1331-1336, 2013 ISSN: 2042-4868; e-issn: 2042-4876 Maxwell Scientific Organization, 2013 Submitted: May 29, 2013 Accepted: July 04, 2013 Published:
Advance Journal of Food Science and Technology 5(10): 1331-1336, 2013 ISSN: 2042-4868; e-issn: 2042-4876 Maxwell Scientific Organization, 2013 Submitted: May 29, 2013 Accepted: July 04, 2013 Published:
EDIminer: A Toolset for Process Mining from EDI Messages
 EDIminer: A Toolset for Process Mining from EDI Messages Robert Engel 1, R. P. Jagadeesh Chandra Bose 2, Christian Pichler 1, Marco Zapletal 1, and Hannes Werthner 1 1 Vienna University of Technology,
EDIminer: A Toolset for Process Mining from EDI Messages Robert Engel 1, R. P. Jagadeesh Chandra Bose 2, Christian Pichler 1, Marco Zapletal 1, and Hannes Werthner 1 1 Vienna University of Technology,
Keywords: Regression testing, database applications, and impact analysis. Abstract. 1 Introduction
 Regression Testing of Database Applications Bassel Daou, Ramzi A. Haraty, Nash at Mansour Lebanese American University P.O. Box 13-5053 Beirut, Lebanon Email: rharaty, nmansour@lau.edu.lb Keywords: Regression
Regression Testing of Database Applications Bassel Daou, Ramzi A. Haraty, Nash at Mansour Lebanese American University P.O. Box 13-5053 Beirut, Lebanon Email: rharaty, nmansour@lau.edu.lb Keywords: Regression
Comparative Analysis of EM Clustering Algorithm and Density Based Clustering Algorithm Using WEKA tool.
 International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 9, Issue 8 (January 2014), PP. 19-24 Comparative Analysis of EM Clustering Algorithm
International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 9, Issue 8 (January 2014), PP. 19-24 Comparative Analysis of EM Clustering Algorithm
ALIAS: A Tool for Disambiguating Authors in Microsoft Academic Search
 Project for Michael Pitts Course TCSS 702A University of Washington Tacoma Institute of Technology ALIAS: A Tool for Disambiguating Authors in Microsoft Academic Search Under supervision of : Dr. Senjuti
Project for Michael Pitts Course TCSS 702A University of Washington Tacoma Institute of Technology ALIAS: A Tool for Disambiguating Authors in Microsoft Academic Search Under supervision of : Dr. Senjuti
Ensembles and PMML in KNIME
 Ensembles and PMML in KNIME Alexander Fillbrunn 1, Iris Adä 1, Thomas R. Gabriel 2 and Michael R. Berthold 1,2 1 Department of Computer and Information Science Universität Konstanz Konstanz, Germany First.Last@Uni-Konstanz.De
Ensembles and PMML in KNIME Alexander Fillbrunn 1, Iris Adä 1, Thomas R. Gabriel 2 and Michael R. Berthold 1,2 1 Department of Computer and Information Science Universität Konstanz Konstanz, Germany First.Last@Uni-Konstanz.De
VMware vcenter Log Insight User's Guide
 VMware vcenter Log Insight User's Guide vcenter Log Insight 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
VMware vcenter Log Insight User's Guide vcenter Log Insight 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Software Design Document (SDD) Template
 (SDD) Template Software design is a process by which the software requirements are translated into a representation of software components, interfaces, and data necessary for the implementation phase.
(SDD) Template Software design is a process by which the software requirements are translated into a representation of software components, interfaces, and data necessary for the implementation phase.
Prediction of Heart Disease Using Naïve Bayes Algorithm
 Prediction of Heart Disease Using Naïve Bayes Algorithm R.Karthiyayini 1, S.Chithaara 2 Assistant Professor, Department of computer Applications, Anna University, BIT campus, Tiruchirapalli, Tamilnadu,
Prediction of Heart Disease Using Naïve Bayes Algorithm R.Karthiyayini 1, S.Chithaara 2 Assistant Professor, Department of computer Applications, Anna University, BIT campus, Tiruchirapalli, Tamilnadu,
A FUZZY BASED APPROACH TO TEXT MINING AND DOCUMENT CLUSTERING
 A FUZZY BASED APPROACH TO TEXT MINING AND DOCUMENT CLUSTERING Sumit Goswami 1 and Mayank Singh Shishodia 2 1 Indian Institute of Technology-Kharagpur, Kharagpur, India sumit_13@yahoo.com 2 School of Computer
A FUZZY BASED APPROACH TO TEXT MINING AND DOCUMENT CLUSTERING Sumit Goswami 1 and Mayank Singh Shishodia 2 1 Indian Institute of Technology-Kharagpur, Kharagpur, India sumit_13@yahoo.com 2 School of Computer
Enhancing Requirement Traceability Link Using User's Updating Activity
 ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Special Issue 3, March 2014 2014 International Conference
ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Special Issue 3, March 2014 2014 International Conference
Context Capture in Software Development
 Context Capture in Software Development Bruno Antunes, Francisco Correia and Paulo Gomes Knowledge and Intelligent Systems Laboratory Cognitive and Media Systems Group Centre for Informatics and Systems
Context Capture in Software Development Bruno Antunes, Francisco Correia and Paulo Gomes Knowledge and Intelligent Systems Laboratory Cognitive and Media Systems Group Centre for Informatics and Systems
Probabilistic topic models for sentiment analysis on the Web
 University of Exeter Department of Computer Science Probabilistic topic models for sentiment analysis on the Web Chenghua Lin September 2011 Submitted by Chenghua Lin, to the the University of Exeter as
University of Exeter Department of Computer Science Probabilistic topic models for sentiment analysis on the Web Chenghua Lin September 2011 Submitted by Chenghua Lin, to the the University of Exeter as
KNOWLEDGE DISCOVERY FOR SUPPLY CHAIN MANAGEMENT SYSTEMS: A SCHEMA COMPOSITION APPROACH
 KNOWLEDGE DISCOVERY FOR SUPPLY CHAIN MANAGEMENT SYSTEMS: A SCHEMA COMPOSITION APPROACH Shi-Ming Huang and Tsuei-Chun Hu* Department of Accounting and Information Technology *Department of Information Management
KNOWLEDGE DISCOVERY FOR SUPPLY CHAIN MANAGEMENT SYSTEMS: A SCHEMA COMPOSITION APPROACH Shi-Ming Huang and Tsuei-Chun Hu* Department of Accounting and Information Technology *Department of Information Management
Fraud Detection in Online Banking Using HMM
 2012 International Conference on Information and Network Technology (ICINT 2012) IPCSIT vol. 37 (2012) (2012) IACSIT Press, Singapore Fraud Detection in Online Banking Using HMM Sunil Mhamane + and L.M.R.J
2012 International Conference on Information and Network Technology (ICINT 2012) IPCSIT vol. 37 (2012) (2012) IACSIT Press, Singapore Fraud Detection in Online Banking Using HMM Sunil Mhamane + and L.M.R.J
Self Organizing Maps for Visualization of Categories
 Self Organizing Maps for Visualization of Categories Julian Szymański 1 and Włodzisław Duch 2,3 1 Department of Computer Systems Architecture, Gdańsk University of Technology, Poland, julian.szymanski@eti.pg.gda.pl
Self Organizing Maps for Visualization of Categories Julian Szymański 1 and Włodzisław Duch 2,3 1 Department of Computer Systems Architecture, Gdańsk University of Technology, Poland, julian.szymanski@eti.pg.gda.pl
Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus
 Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus 1. Introduction Facebook is a social networking website with an open platform that enables developers to extract and utilize user information
Facebook Friend Suggestion Eytan Daniyalzade and Tim Lipus 1. Introduction Facebook is a social networking website with an open platform that enables developers to extract and utilize user information
A Survey on Product Aspect Ranking
 A Survey on Product Aspect Ranking Charushila Patil 1, Prof. P. M. Chawan 2, Priyamvada Chauhan 3, Sonali Wankhede 4 M. Tech Student, Department of Computer Engineering and IT, VJTI College, Mumbai, Maharashtra,
A Survey on Product Aspect Ranking Charushila Patil 1, Prof. P. M. Chawan 2, Priyamvada Chauhan 3, Sonali Wankhede 4 M. Tech Student, Department of Computer Engineering and IT, VJTI College, Mumbai, Maharashtra,
ASSOCIATION RULE MINING ON WEB LOGS FOR EXTRACTING INTERESTING PATTERNS THROUGH WEKA TOOL
 International Journal Of Advanced Technology In Engineering And Science Www.Ijates.Com Volume No 03, Special Issue No. 01, February 2015 ISSN (Online): 2348 7550 ASSOCIATION RULE MINING ON WEB LOGS FOR
International Journal Of Advanced Technology In Engineering And Science Www.Ijates.Com Volume No 03, Special Issue No. 01, February 2015 ISSN (Online): 2348 7550 ASSOCIATION RULE MINING ON WEB LOGS FOR
