State of California California Technology Agency. Software Management Plan Guidelines
|
|
|
- Michael Roberts
- 8 years ago
- Views:
Transcription
1 State f Califrnia Califrnia Technlgy Agency Sftware Management Plan Guidelines Revised April 2011
2 Sectin Overview INTRODUCTION TO SOFTWARE MANAGEMENT PLANNING The State Administrative Manual (SAM) Sectin describes the state s plicy regarding sftware management. Specifically, Sectin 4846 states as fllws: Each agency shall establish and maintain apprpriate cmputer sftware management practices and ensure that cmputer sftware they use and/r have purchased with state funds is legally prcured and is used in cmpliance with licenses, cntract terms, and applicable cpyright laws. Each agency shall develp and implement plicies and prcedures t ensure that all staff understand and adhere t prper sftware management plicies. Sftware piracy refers t the installatin r use f unlicensed r unauthrized cpies f sftware. This can ccur thrugh using ne licensed cpy t install a prgram n multiple cmputers r taking advantage f sftware upgrade ffers withut having a legal cpy f the versin t be upgraded. Piracy includes having the number f simultaneus users n the netwrk exceeding the number f available client licenses fr a netwrked prgram, unauthrized dwnlading f sftware frm the Internet, r illegally duplicating and using cpyrighted materials such as cunterfeit cpies f CD's, diskettes and related manuals and materials. The Califrnia Technlgy Agency (Technlgy Agency) permits the use f Open Surce Sftware (OSS). Cnsistent with ther sftware, use f OSS is subject t the sftware management licensing and security practices included in e SAM, Sectins 4846, , 5310 Item 2 and Item 5, Subsectin (f), and Rles and Respnsibilities Califrnia Technlgy Agency: The Technlgy Agency is the principal gvernment department respnsible fr imprving executive agency practices regarding the acquisitin and use f cmputer sftware, mnitring and eliminating the use f unauthrized cmputer sftware. The Technlgy Agency will utilize apprpriate versight mechanisms t mnitr and audit expenditures by state agencies t fster state agency cmpliance with the plicies set frth in SAM Sectin 4846 and with established plicies and guidelines. Department f General Services: The Department f General Services will develp apprpriate language fr inclusin in State cntracts t require cmpliance with sftware licenses and applicable cpyright laws when State funds are used t acquire, perate, r maintain cmputer sftware. Califrnia Technlgy Agency 2 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
3 State Agencies: State agencies shall develp, implement, and maintain specific plans, prcedures, and prcesses t ensure cmpliance with the established requirements. State cntractrs and recipients f state grants and state lan guarantee assistance shall have apprpriate systems and cntrls in place t ensure state funds are nt used t acquire, perate, r maintain cmputer sftware in vilatin f applicable cpyright laws. Each state agency shall designate an apprpriate psitin r unit t be respnsible fr ensuring cmpliance. Each state agency s cmpliance prgram shall be dcumented with sufficient specificity t meet the audit requirements by its internal auditrs and Infrmatin Security Officer. 1.2 Intrductin t the Guidelines These guidelines have been issued t assist state agencies in develping r cntinually administering a sftware management prgram t prevent sftware piracy and prmte gd sftware management practices. The guidelines are als intended t assist agencies in preparing a Sftware Management Plan (SMP) as required by SAM Sectin The absence f an effective SMP expses an rganizatin t a variety f tangible and intangible risks including: damage t the rganizatin's reputatin fines frm civil damages fr cpyright infringement denial f prduct supprt r warranty service the pssibility f civil and criminal charges against the directrs and managers f an rganizatin fund in vilatin f cpyright The benefits f an effective sftware management prgram are many. These include: the ability t determine actual sftware csts the ability t btain technical supprt fr installed sftware prducts access t infrmatin relating t upgrade issues the ability t plan future expenditures mre accurately the knwledge that licensing f installed sftware is accurately dcumented by the current sftware inventry and listed n the agency's supprted sftware list. 1.3 Practices That Supprt Gd Sftware Management T manage sftware prperly, the fllwing practices shuld be fllwed: Have and maintain a cmprehensive inventry f all installed sftware including micrcmputers, mid-range, and mainframe envirnments and maintain cmplete and accurate recrds f all licenses, certificatins and sftware purchase transactins, string these in a secure repsitry. Peridically review installed sftware and accmpanying licenses t ensure nly legal and supprted sftware are in use and t ensure nging cmpliance with the Sftware Management Plicy. Califrnia Technlgy Agency 3 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
4 Be familiar with the U.S. Cpyright Act fund in Title 17 f the U.S. cde in rder t understand the cnsequences f infringement f cpyright laws including the penalties and liabilities fr damages. Be familiar with the licensing agreements fr each individual sftware vendr in rder t understand the limitatins, such as transferring f licenses, expiratin f licenses, when supprt ends fr licenses, when upgrades will be needed, requirements fr patches, whether r nt sftware can be installed n hme cmputers, hw t terminate a license, etc. Have and maintain a sftware management prgram and train management and staff n the plicies and prcedures assciated with that prgram t ensure the use f best practices in sftware management and cmpliance with the plicy. Have and maintain a list f supprted sftware t guide what new sftware will be apprved fr purchase and what current sftware shuld be retained n the desktps, servers and ther prcessing devices. Remve all unlicensed sftware and sftware nt n the supprted sftware list, sftware n lnger in use frm individual cmputers, and nn-authrized sftware t make sure all sftware is legal and supprted and t free the hard drive space f unused sftware. Purchase sftware nly in the name f the state agency; nt in individuals' names. T the extent that the use f freeware and OSS is allwed by plicy within the department, make sure that such usage is apprved n a case by case basis and that apprpriate cntrls and prcesses are in place t ensure that sftware is used in accrdance with any cnditins r agreements prescribed by the manufacturer. T the extent that sftware purchased by end users is allwed by plicy t be installed n a department s cmputers, make sure that such usage is apprved n a case by case basis, that apprpriate cntrls and prcesses are in place t ensure that prper licensing is secured, and that the sftware is used in accrdance with the licensing agreements. D nt allw state licensed sftware t be installed n nn-state equipment except as specified in a service cntract r ther legal dcument that requires the parties t adhere t the agency's Sftware Management Plicy. Transfer and dispse f sftware accrding t license agreements t ensure prper dispsitin. Wipe r scrub hard drives f all sftware when cmputer devices are recycled r salvaged as necessary t cmply with the terms f the licensing agreement and t prtect any cnfidential r sensitive data. Require that sftware be acquired thrugh a frmal acquisitin prcess t ensure prper apprvals are btained, and that prper stck receipt, registratin and inventry recrds are created and maintained. Califrnia Technlgy Agency 4 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
5 2.0 Overview Sectin 2 STEPS FOR PREPARATION OF SOFTWARE MANAGEMENT PLANS The Sftware Management Plicy requires the identificatin f the sftware management rles and respnsibilities within the rganizatin and the submittal f a supprted sftware list by each department. Mst agencies have designated sftware management rles and respnsibilities t staff within their rganizatin. The same persn may perfrm multiple rles; hwever, ne individual needs t be designated as ultimately respnsible fr each specific sftware management task. In additin, agencies shuld have and maintain a list f apprved and supprted sftware. The bjective f the fllwing guidelines is t assist state agencies in develping their Sftware Management Plans. T prepare fr develping the plan, state agencies shuld: 2.1 Have A Sftware Management Team As resurces allw, have a Sftware Management Team that will be respnsible fr develping and implementing the sftware management prgram as well as preparing the SMP. The team shuld cnsist f: A Sftware Assets Manager r ther jb title whse rles and respnsibilities are: Understanding general licensing prcedures and specific requirements f sftware, including pen surce, used within the rganizatin and knwing the particular limitatins f the agreements. Maintaining a list f apprved sftware fr use in the acquisitin prcess and the prcess f identifying unlicensed and unsupprted sftware. Maintaining a baseline inventry f all sftware residing within the agency t serve as the fundatin fr the sftware management prgram. Perfrming nging inventries fr asset management and cmpliance purpses. Selecting and securing an autmated tl t be used in cnducting the baseline and nging inventries, shuld the state agency decide t acquire/use such a tl. Making sure that all sftware is registered, and that the recrds f licenses and renewals are prperly maintained. Ensuring all unlicensed sftware is remved frm cmputers, servers and ther prcessing devices. Ensuring there is a secure repsitry fr all sftware licenses and sftware media t prevent lss, misuse and theft. Ensuring that prper checkut prcedures are develped and fllwed fr lading sftware nt the agency's cmputers. Califrnia Technlgy Agency 5 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
6 Maintaining a sftware lg t recrd when sftware is checked ut f the repsitry, wh checked ut the sftware, why the sftware was required, and when the sftware is returned t the repsitry. Ensuring that prper educatin n sftware management practices is available within the rganizatin and that training thrugh new emplyee rientatins, etc., is administered t all levels f staff including users, acquisitin supprt, technical, management and executives. Staff need t be aware f cpyrights prtecting cmputer sftware and the plicies and prcedures adpted by the agency t hnr thse cpyrights. Ensuring the required Sftware Management Plan and certificatins are develped and maintained accrding t the schedule utlined in the State Infrmatin Management Manual Sectin 05A. Mnitring the use f sftware n state wned desktps and mbile cmputers, which includes thse used in the hme envirnment t accmplish state wrk. Ensuring crrective actin is taken in terms f crrecting any license agreement breaches and ensuring the plicy and prcedural flws that led t failures f cmpliance are mdified t prevent further prblems. An Acquisitin Manager r ther jb title whse rles and respnsibilities are: Understanding general licensing prcedures and specific requirements f sftware used within the rganizatin including the limitatins f the agreements. Ensuring that prper sftware prcurement practices are in place and fllwed. Ensuring prper educatin f acquisitin staff in sftware prcurement practices. Ensuring language is included in state cntracts requiring vendrs t certify that they have apprpriate systems and cntrls in place t ensure that state funds are nt used t acquire, perate r maintain cmputer sftware in a manner that des nt cmply with applicable cpyrights. A Desktp and Mbile Cmputing Crdinatr whse rles and respnsibilities are: Reviewing sftware acquisitin requests that are being purchased thrugh the Desktp and Mbile Cmputing Plicy t ensure purchases are in cncert with the agency's supprted sftware standards. Reviewing exceptin requests fr purchases f sftware nt n the agency's supprted list and making recmmendatins t the Sftware Manager as t the apprpriateness f these purchases and the additin f the sftware items t the supprted sftware list. A Sftware Administratr r ther jb title, fr mainframe and mid-range cmputing systems, whse rles and respnsibilities are t manage sftware assets: NOTE: This is als desirable in netwrk installatins and desktp and mbile cmputing. Ensuring prper licensing n installed hardware is in accrdance with cntractual requirements. Califrnia Technlgy Agency 6 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
7 Negtiating the terms and cnditins f sftware usage with apprpriate vendrs, departmental prcurement staff, and/r the Department f General Services. Managing the physical inventry f sftware rders and maintaining a sftware inventry database f departmental sftware assets. Mnitring all installed and distributed cpies t ensure sftware cpyright prtectin. Acquiring new sftware, upgrades and fixes as necessary. Keeping abreast f all new and existing licensing requirements. Internal Auditrs whse rles and respnsibilities are: Perfrming internal audits as necessary t evaluate the existence and effectiveness f the SMP. Taking steps t verify that recmmended crrective actins are taken and ensuring that the apprpriate management is ntified when vilatins ccur. 2.2 Have And Maintain A Methdlgy T Cnduct A Full Sftware Inventry Each state agency must regularly cnduct a full sftware inventry applying the practices utlined abve. State agencies are advised t research alternatives fr cnducting a full inventry f all sftware residing n the agency's infrmatin technlgy systems. Alternatives can include acquiring an autmated tl, preparing an inventry thrugh manual prcedures, r cntracting fr an inventry service. Autmated tls are available that can inventry cmputer sftware thrugh a variety f techniques. In selecting an autmated tl, cnsider: Ease f use, requiring minimal training fr IT staff Accuracy Flexibility Cmpleteness Extensibility, enabling the tl t be used n multiple platfrms A manual inventry can be cnducted by individually accessing each cmputer and listing the sftware n each machine. Cntract services are available fr cnducting a sftware inventry as well as prviding additinal services such as training, auditing, and develping sftware management plans. 2.3 Have And Maintain A List Of Supprted Sftware T standardize n the purchase and usage f sftware fr desktps and netwrks, have and maintain a list f supprted sftware. The list will facilitate prcurement as well as assist when auditing fr sftware management cmpliance. Fr a supprted sftware list: Califrnia Technlgy Agency 7 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
8 Identify with specificity the sftware supprted within the rganizatin. The list shuld cntain the fllwing infrmatin: Class f sftware (perating system, wrd prcessr, spreadsheet, database, , utilities, graphics, netwrk) Name and versin f sftware (Office 2007, Adbe Acrbat 9, Windws XP Service Pack 3, McAfee, etc.). Sub-class f sftware (OS390, Windws, Wrd, Excel, Access, ADABAS, IDMS, DB2, Grupwise, Outlk, WinZip, Nrtn, Crel Draw, Nvell, Unix) Type f license (enterprise r standalne), Apprpriate user base (clerical supprt, technical, management, executive) 2.4 Have And Maintain A Sftware Prcurement Prcess It is essential that the purchasing f sftware be a standard prcedure cnsistent with the acquisitin f ther critical department assets. All sftware purchases shuld prceed thrugh the state agency's nrmal purchasing prcess, requiring requisitins and management apprval. Cmpnents f a sftware prcurement prgram and prcess that will prmte prper sftware acquisitin may include: Educating and training prcurement staff n sftware licensing and cpyright laws. Centralizing all sftware purchases t prmte adherence t standardized sftware prcurement prcesses. Establishing a signature prcess t ensure respnsible parties are aware f and apprve each sftware acquisitin. Requiring that all sftware purchases be accmpanied by prper licenses and receipts, evidencing legal acquisitin and use. Requiring that all sftware purchases be made thrugh reputable, authrized resellers t prevent purchasing cunterfeit prgrams. Obtaining licenses and receipts fr each purchase. Ensuring that purchased sftware is registered with the manufacturer, if required. Ensuring sftware cannt be dwnladed and purchased frm the Internet withut apprval. Ensuring that purchased sftware is listed n a cmprehensive sftware lg. 2.5 Have And Maintain Recrd Keeping Standards Maintaining cmplete and accurate recrds is essential fr a gd sftware management prgram. T ensure that a sftware cmpliance prgram is ultimately successful, have and maintain gd recrd keeping standards t assist internal auditrs and ther audit fficers in cnducting a cmprehensive examinatin f sftware cmpliance. Califrnia Technlgy Agency 8 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
9 Prper recrd keeping shuld include: Maintaining sftware purchase recrds (purchase rder, invices, receipts, cpies f cancelled checks, if apprpriate). Maintaining a repsitry f sftware media, dcumentatin, prduct licenses, license agreements, manuals, and registratin cards. Stre sftware media, licenses and registratin cards in a secure area t prevent theft, lss r misuse. Maintaining a sftware lg including prduct and versin, publisher, sftware serial number purchase date, user name, user lcatin, hardware serial number and cmments. Maintaining recrds f staff wh have attended training in sftware management practices r have been intrduced t sftware cpyright requirements and apprpriate sftware usage thrugh ther educatinal pprtunities such as emplyee rientatin. Califrnia Technlgy Agency 9 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
10 Sectin 3 SOFTWARE MANAGEMENT PLAN 3.0 Overview Sftware management is an imprtant cmpnent f a State agency's verall resurce and cmpliance management prcess. The Sftware Management Plan (SMP) enables agencies t lay ut the framewrk fr a sftware management prgram t ensure that all State agencies meet the requirements f the Califrnia Sftware Management Plicy as stated in SAM Sectins These guidelines have been prepared t assist state agencies in develping the required SMP. T the extent that agencies have existing dcuments that have been develped thrugh the administratin f the Desktp and Mbile Cmputing Plicy r ther internal department effrts and that these dcuments will meet the requirements f the SMP, they can be submitted in lieu f creating new dcumentatin. The SMP shuld include the fllwing infrmatin t indicate hw the state agency plans t address the required sftware management prgram activities t cme in full cmpliance with the state IT plicy r hw the state agency is already accmplishing these activities and will cntinue with the administratin f a sftware management prgram. 3.1 Baseline Inventry Methdlgy It is essential that a baseline inventry be cnducted in rder t knw what sftware exists within an agency s that it can be prperly managed. An inventry cnsists f determining all sftware physically residing n an agency's cmputers and inventrying all riginal licenses fr the sftware. The SMP must address: Wh is invlved in cnducting the inventry (rganizatin/classificatin); What inventry methdlgy is used (e.g. autmated tls, manual prcesses, cntract services); Hw the inventry prcess is rganized; What infrmatin is gathered; Hw the infrmatin is reprted (e.g. frm, summary reprt); Wh receives the inventry infrmatin (sftware management team members, CIO, agency directr); and The baseline inventry cmpletin date. Califrnia Technlgy Agency 10 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
11 3.2 Unlicensed/Unauthrized Sftware Identificatin Methdlgy The identificatin f unlicensed and unauthrized sftware is accmplished by: 1) cmparing the results f the physical inventry with the license agreements, and 2) cmparing the results f the physical inventry t the list f sftware authrized by the rganizatin. The SMP must address: Wh is invlved in the identificatin f the unlicensed and unauthrized sftware (rganizatin/classificatin); Hw cmparisns are perfrmed t identify legal versus unlicensed and unauthrized sftware; Hw unlicensed and/r unauthrized sftware is reprted; Wh receives the reprts f unlicensed and unauthrized sftware; and Hw unlicensed and unauthrized sftware is remved frm cmputers. 3.3 Secure Repsitry A secure and prtected repsitry prevents lss, theft and unauthrized use f sftware, licenses and dcumentatin. T the extent pssible, repsitries shuld be kept in a centralized strage area within each facility. The SMP must address: What physical repsitries are used (e.g. file cabinet, lcked rm) and their lcatins (e.g. centralized, decentralized); Wh has access t the repsitries (rganizatin/classificatin); and What check ut prcedures are used t remve and return sftware and dcumentatin t the repsitries. 3.4 Onging Inventry And Cntrl Methdlgy Once the sftware base is examined in the initial "baseline" inventry, nging cntrl prcesses and prcedures must be in place t ensure that the inventry recrds are updated and remain cmplete and accurate. New sftware acquisitins must be added t the inventry and remved sftware must be deleted. In additin, peridic inventries shuld be cnducted t verify sftware recrds and mnitr nging cmpliance with the Sftware Management Plicy. Fr these subsequent inventries, it may nt be practical t include all cmputers. A sample f cmputers may be inspected. The SMP must address: Wh is respnsible fr develping, implementing and maintaining the nging inventry cntrl prcesses and prcedures; What nging inventry cntrl prcesses and prcedures are used t address receipt and installatin f sftware, remval, and dispsal f sftware and change cntrl; Califrnia Technlgy Agency 11 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
12 Wh is respnsible fr ensuring the inventry cntrl prcesses and prcedures are cntinuusly fllwed; Wh cnducts the nging inventries (rganizatin/classificatin); What prcesses/prcedures are in place t ensure the nging inventries ccur and wh is respnsible fr them; What methdlgy is used t sample the inventry (e.g. by sub-unit, by gegraphical lcatin); Hw is the sample size determined; and Hw ften will sample inventries ccur (e.g. mnthly, quarterly, every six mnths). 3.5 Internal Audits Effective sftware management is a cntinual prcess and includes audits. The bjective f the nging audits is t determine the nging cmpliance with sftware license agreements. These peridic spt checks will identify if unlicensed sftware has been deliberately r inadvertently installed n an agency's cmputers. The audit prgram shuld als examine the agency's sftware prcurement and recrd maintenance prcesses as well as the means by which staff are infrmed f apprpriate sftware usage. The SMP must identify: Wh perfrms these audits (rganizatin/classificatin); Wh is ntified f the results f the audit; and Hw results are cmmunicated (e.g. frms, reprts, presentatins). 3.6 Crrective Actins Crrective actin must be taken when unauthrized use f sftware is identified. Crrective actin is needed 1) when there is a breach f cpyright law r the terms f a sftware license, r 2) when inventry reveals unlicensed cpies f sftware. If either situatin is identified, the sftware prgrams must be deleted immediately. If nging use f the sftware is needed, immediate actin shuld be taken t crrect the licensing breach with the manufacturer. The SMP must address: Wh is respnsible fr crrective actins (rganizatin/classificatin); Hw crrective actins are accmplished; Wh is ntified f the crrectins; and Hw infractins are kept frm reccurring (e.g. educatin, changes in prcess, mre mnitring, up-dating the list f supprted sftware, re-evaluating the need fr additinal sftware licenses). Califrnia Technlgy Agency 12 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
13 3.7 Cntractrs' Certificatin The Sftware Management Plicy requires that state cntractrs certify they have apprpriate systems and cntrls in place t ensure that state funds will nt be used in the perfrmance f a cntract fr the acquisitin, peratin r maintenance f cmputer sftware in vilatin f cpyright laws. These requirements are t be incrprated as standard language in cntracts awarded by the state. The SMP must address: Wh ensures that certificatin has ccurred (rganizatin/classificatin); Hw the respnsible individual receives certificatin f cmpliance (e.g. written statement frm cntractr, written clause in a cntract); What cntrls are in place t ensure apprpriate measures are being taken t ensure cmpliance; and What measures are taken if cntractrs d nt cmply. 3.8 Dispsal Of Hardware And Sftware All hardware and sftware that is n lnger t be used in state service shall be dispsed f in an apprpriate manner. Sftware shuld be destryed t ensure that it cannt be re-used. Hardware can be recycled, except fr thse cmpnents which must have a license. Hard drives shuld be wiped r scrubbed t remve sftware as necessary t cmply with terms f the sftware licenses. The SMP must address: Wh is respnsible fr dispsal f sftware and hardware cmpnents (rganizatin/classificatin); and The prcedures in place t ensure sftware and hardware are dispsed f prperly. 4.0 Rles And Respnsibilities Fr The Administratin Of The Sftware Management Prgram Rles and respnsibilities fr the administratin f the sftware management prgram and the develpment f the SMP need t be defined within each state agency. The SMP must identify: What are the rles and respnsibilities f the department's executive staff? What are the rles and respnsibilities f department management? What are the rles and respnsibilities f user's f cmputer resurces? What are the rles and respnsibilities f the Sftware Management Team? Califrnia Technlgy Agency 13 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
14 5.0 Actin Plan The SMP must include an actin plan which lists thse activities that are in alignment with SAM Sectin If the department is currently cmpliant thrugh administratin f the Desktp and Mbile Cmputing Plicy r ther internal effrts, it can demnstrate that cmpliance thrugh the submissin f current sftware management dcumentatin. If nt currently in full cmpliance, the department must include an actin plan fr achieving cmpliance as part f the Sftware Management Plan. Include in the actin plan thse steps needed t: Obtain and maintain a current full sftware inventry; Detect any unlicensed and unauthrized sftware; Prvide the secure repsitry fr all sftware media and licenses; Maintain a prcess fr nging inventry cntrl; Establish and maintain a sftware management audit prgram and institute that prgram as an nging effrt; Establish and maintain the respnsibility and prcesses fr taking crrective actins when sftware breaches are identified; Maintain a means t ensure the cntractr certifies t apprpriate sftware usage; and Maintain a cnsistent and structured prcess fr dispsal f sftware and hardware. The actin plan shuld als identify thse steps fr the preparatin f the fllw-up sftware management reprt t be submitted t the Technlgy Agency. 6.0 Timeline The SMP must include a timeline that identifies when thse tasks listed in the actin plan discussed abve will be cmpleted. If the department can demnstrate cmpliance with the Executive SAM Sectins thrugh current dcumentatin, it will nt be required t prvide a timeline in the SMP. 7.0 Authrized Sftware List A current list f authrized sftware will assist in guiding what sftware is apprpriate and legal fr each rganizatin. The list shuld shw all classes and subclasses f sftware necessary t meet the agencies business needs and, within each class and subclass, which prducts and prduct versins will be supprted and the categry f emplyees using the prduct. The SMP must include a cpy f the agency's mst current authrized sftware list. 8.0 Sftware Management Educatin It is essential t have an educatin effrt s that all staff can receive training in the legal use f sftware and gd sftware management practices. Emplyee educatin shuld Califrnia Technlgy Agency 14 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
15 include the individual agency's plicies and prcedures relating t sftware management as well as statewide plicies. Training shuld be custmized t meet the specific audience needs (users, prcurement staff, management, technical staff, and executives). Sftware management educatin can be incrprated int nrmal emplyee rientatin and ther training pprtunities. The SMP must address hw the state agency will ensure that staff is made aware f sftware cpyright laws and gd sftware management practices. 9.0 Newly Established Agencies and Departments Newly established agencies and/r departments are required t submit an SMP in cnjunctin with their Desktp and Mbile Cmputing Plicy. Newly established state agencies and/r departments will submit t the Technlgy Agency a Sftware Management Reprt prpsing the plan the agency will implement in rder t cmply with the Sftware Management Plicy. The reprt shall include: 1. Prcedures n hw the agency and/r department will: a. Cnduct a 100 percent inventry f the agency s sftware t create a baseline and hw that baseline was cnducted; b. Detect and remve illegal and unlicensed sftware; c. Prvide fr a secure repsitry f sftware media, and licenses; d. Prvide nging inventry tracking and mnitring f new purchases and installatins; e. Perfrm peridic internal audits and ensure apprpriate crrective actins are taken when necessary; f. Receive certificatin frm its cntractrs and bidders that they have apprpriate systems and cntrls in place t ensure that state funds are nt used t acquire, perate, r maintain cmputer sftware in a manner that des nt cmply with applicable cpyrights; g. Ensure prper dispsal f hardware and sftware cnsistent with license requirements. 2. A statement f the rles and respnsibilities within the agency fr the administratin f the sftware management prgram and enfrcement f plicy; 3. An actin plan detailing the steps t full implementatin f the sftware management plicy; 4. A timeline fr full implementatin f the sftware management plicy; 5. A list f the agency s currently supprted sftware; 6. A plan fr emplyee rientatin and educatin Certificatin and Cmpliance Annually, each agency and/r department will submit t the CIO a certificatin reprt declaring they are in cmpliance with SAM Sectins Califrnia Technlgy Agency 15 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
16 State agencies shall retain within their rganizatin, fr three years, the annual certificatin in the frm f a Statement f Cmpliance (see SIMM Sectin 80) alng with the summary f updated inventries and audits cnducted by the agency as part f their nging sftware management practices. The certificatin, t be submitted t the agency CIO, must include the name f the agency representative respnsible fr ensuring agency cmpliance with the Sftware Management Plicy. In supprt f this certificate, each agency must maintain a detailed inventry reprt that must be made available t the Technlgy Agency and/r the Department f General Services upn request, per SAM Sectin Califrnia Technlgy Agency 16 Sftware Management Plan Guidelines SIMM Sectin 120 April 2011
Woodstock Multimedia, INC. Software/Hardware Usage Policy
 Wdstck Multimedia, INC. Sftware/Hardware Usage Plicy POLICY PURPOSE The purpse f the Wdstck Multimedia, INC. Sftware / Hardware Usage Plicy is t ensure that Wdstck Multimedia, INC. emplyees are prperly
Wdstck Multimedia, INC. Sftware/Hardware Usage Plicy POLICY PURPOSE The purpse f the Wdstck Multimedia, INC. Sftware / Hardware Usage Plicy is t ensure that Wdstck Multimedia, INC. emplyees are prperly
POLICY 1390 Information Technology Continuity of Business Planning Issued: June 4, 2009 Revised: June 12, 2014
 State f Michigan POLICY 1390 Infrmatin Technlgy Cntinuity f Business Planning Issued: June 4, 2009 Revised: June 12, 2014 SUBJECT: APPLICATION: PURPOSE: CONTACT AGENCY: Plicy fr Infrmatin Technlgy (IT)
State f Michigan POLICY 1390 Infrmatin Technlgy Cntinuity f Business Planning Issued: June 4, 2009 Revised: June 12, 2014 SUBJECT: APPLICATION: PURPOSE: CONTACT AGENCY: Plicy fr Infrmatin Technlgy (IT)
COPIES-F.Y.I., INC. Policies and Procedures Data Security Policy
 COPIES-F.Y.I., INC. Plicies and Prcedures Data Security Plicy Page 2 f 7 Preamble Mst f Cpies FYI, Incrprated financial, administrative, research, and clinical systems are accessible thrugh the campus
COPIES-F.Y.I., INC. Plicies and Prcedures Data Security Plicy Page 2 f 7 Preamble Mst f Cpies FYI, Incrprated financial, administrative, research, and clinical systems are accessible thrugh the campus
Request for Resume (RFR) CATS II Master Contract. All Master Contract Provisions Apply
 Sectin 1 General Infrmatin RFR Number: (Reference BPO Number) Functinal Area (Enter One Only) F50B3400026 7 Infrmatin System Security Labr Categry A single supprt resurce may be engaged fr a perid nt t
Sectin 1 General Infrmatin RFR Number: (Reference BPO Number) Functinal Area (Enter One Only) F50B3400026 7 Infrmatin System Security Labr Categry A single supprt resurce may be engaged fr a perid nt t
VCU Payment Card Policy
 VCU Payment Card Plicy Plicy Type: Administrative Respnsible Office: Treasury Services Initial Plicy Apprved: 12/05/2013 Current Revisin Apprved: 12/05/2013 Plicy Statement and Purpse The purpse f this
VCU Payment Card Plicy Plicy Type: Administrative Respnsible Office: Treasury Services Initial Plicy Apprved: 12/05/2013 Current Revisin Apprved: 12/05/2013 Plicy Statement and Purpse The purpse f this
GUIDANCE FOR BUSINESS ASSOCIATES
 GUIDANCE FOR BUSINESS ASSOCIATES This Guidance fr Business Assciates dcument is intended t verview UPMCs expectatins, as well as t prvide additinal resurces and infrmatin, t UPMC s HIPAA business assciates.
GUIDANCE FOR BUSINESS ASSOCIATES This Guidance fr Business Assciates dcument is intended t verview UPMCs expectatins, as well as t prvide additinal resurces and infrmatin, t UPMC s HIPAA business assciates.
Version: Modified By: Date: Approved By: Date: 1.0 Michael Hawkins October 29, 2013 Dan Bowden November 2013
 Versin: Mdified By: Date: Apprved By: Date: 1.0 Michael Hawkins Octber 29, 2013 Dan Bwden Nvember 2013 Rule 4-004J Payment Card Industry (PCI) Patch Management (prpsed) 01.1 Purpse The purpse f the Patch
Versin: Mdified By: Date: Apprved By: Date: 1.0 Michael Hawkins Octber 29, 2013 Dan Bwden Nvember 2013 Rule 4-004J Payment Card Industry (PCI) Patch Management (prpsed) 01.1 Purpse The purpse f the Patch
How To Write An Ehsms Training, Awareness And Competency Procedure
 Envirnmental, Health & Safety Management System (EHSMS) Dcument Number: 00122 Issue Date: 05/07/2014 Training, Awareness and Cmpetency Prcedure Revisin Number: 7 Prepared By: Stalcup, Bryce Apprved By:
Envirnmental, Health & Safety Management System (EHSMS) Dcument Number: 00122 Issue Date: 05/07/2014 Training, Awareness and Cmpetency Prcedure Revisin Number: 7 Prepared By: Stalcup, Bryce Apprved By:
Electronic and Information Resources Accessibility Compliance Plan
 Electrnic and Infrmatin Resurces Accessibility Cmpliance Plan Intrductin The University f Nrth Texas at Dallas (UNTD) is cmmitted t prviding a wrk envirnment that affrds equal access and pprtunity t therwise
Electrnic and Infrmatin Resurces Accessibility Cmpliance Plan Intrductin The University f Nrth Texas at Dallas (UNTD) is cmmitted t prviding a wrk envirnment that affrds equal access and pprtunity t therwise
Chapter 7 Business Continuity and Risk Management
 Chapter 7 Business Cntinuity and Risk Management Sectin 01 Business Cntinuity Management 070101 Initiating the Business Cntinuity Plan (BCP) Purpse: T establish the apprpriate level f business cntinuity
Chapter 7 Business Cntinuity and Risk Management Sectin 01 Business Cntinuity Management 070101 Initiating the Business Cntinuity Plan (BCP) Purpse: T establish the apprpriate level f business cntinuity
University of Texas at Dallas Policy for Accepting Credit Card and Electronic Payments
 University f Texas at Dallas Plicy fr Accepting Credit Card and Electrnic Payments Cntents: Purpse Applicability Plicy Statement Respnsibilities f a Merchant Department Prcess t Becme a Merchant Department
University f Texas at Dallas Plicy fr Accepting Credit Card and Electrnic Payments Cntents: Purpse Applicability Plicy Statement Respnsibilities f a Merchant Department Prcess t Becme a Merchant Department
THIRD PARTY PROCUREMENT PROCEDURES
 ADDENDUM #1 THIRD PARTY PROCUREMENT PROCEDURES NORTH CENTRAL TEXAS COUNCIL OF GOVERNMENTS TRANSPORTATION DEPARTMENT JUNE 2011 OVERVIEW These prcedures establish standards and guidelines fr the Nrth Central
ADDENDUM #1 THIRD PARTY PROCUREMENT PROCEDURES NORTH CENTRAL TEXAS COUNCIL OF GOVERNMENTS TRANSPORTATION DEPARTMENT JUNE 2011 OVERVIEW These prcedures establish standards and guidelines fr the Nrth Central
Wire Transfer Request
 Wire Transfer Request Requirements and Instructins OFFICE OF DISBURSEMENTS Categry: Dcument Name: Payment Prcessing Wire Transfer Request - Requirements and Instructins Respnsible Department: Office f
Wire Transfer Request Requirements and Instructins OFFICE OF DISBURSEMENTS Categry: Dcument Name: Payment Prcessing Wire Transfer Request - Requirements and Instructins Respnsible Department: Office f
RUTGERS POLICY. Responsible Executive: Vice President for Information Technology and Chief Information Officer
 RUTGERS POLICY Sectin: 70.1.1 Sectin Title: Infrmatin Technlgy Plicy Name: Acceptable Use Plicy fr Infrmatin Technlgy Resurces Frmerly Bk: N/A Apprval Authrity: Senir Vice President fr Administratin Respnsible
RUTGERS POLICY Sectin: 70.1.1 Sectin Title: Infrmatin Technlgy Plicy Name: Acceptable Use Plicy fr Infrmatin Technlgy Resurces Frmerly Bk: N/A Apprval Authrity: Senir Vice President fr Administratin Respnsible
PENETRATION TEST OF THE INDIAN HEALTH SERVICE S COMPUTER NETWORK
 Department f Health and Human Services OFFICE OF INSPECTOR GENERAL PENETRATION TEST OF THE INDIAN HEALTH SERVICE S COMPUTER NETWORK Inquiries abut this reprt may be addressed t the Office f Public Affairs
Department f Health and Human Services OFFICE OF INSPECTOR GENERAL PENETRATION TEST OF THE INDIAN HEALTH SERVICE S COMPUTER NETWORK Inquiries abut this reprt may be addressed t the Office f Public Affairs
State Fleet Card Oversight Usage and Responsibilities
 State Fleet Card Oversight Usage and Respnsibilities Intrductin The Department f General Services (DGS), Office f Fleet and Asset Management (OFAM) administers a statewide ne-prvider payment system cntract
State Fleet Card Oversight Usage and Respnsibilities Intrductin The Department f General Services (DGS), Office f Fleet and Asset Management (OFAM) administers a statewide ne-prvider payment system cntract
Multi-Year Accessibility Policy and Plan for NSF Canada and NSF International Strategic Registrations Canada Company, 2014-2021
 Multi-Year Accessibility Plicy and Plan fr NSF Canada and NSF Internatinal Strategic Registratins Canada Cmpany, 2014-2021 This 2014-21 accessibility plan utlines the plicies and actins that NSF Canada
Multi-Year Accessibility Plicy and Plan fr NSF Canada and NSF Internatinal Strategic Registratins Canada Cmpany, 2014-2021 This 2014-21 accessibility plan utlines the plicies and actins that NSF Canada
FAYETTEVILLE STATE UNIVERSITY
 FAYETTEVILLE STATE UNIVERSITY IDENTITY THEFT PREVENTION (RED FLAGS RULE) Authrity: Categry: Issued by the Fayetteville State University Bard f Trustees. University-Wide Applies t: Administratrs Faculty
FAYETTEVILLE STATE UNIVERSITY IDENTITY THEFT PREVENTION (RED FLAGS RULE) Authrity: Categry: Issued by the Fayetteville State University Bard f Trustees. University-Wide Applies t: Administratrs Faculty
Audit Committee Charter
 Audit Cmmittee Charter Membership The Audit Cmmittee (the "Cmmittee") f the Bard f Directrs (the "Bard") f Philip Mrris Internatinal Inc. (the "Cmpany") shall cnsist f at least three directrs all f whm
Audit Cmmittee Charter Membership The Audit Cmmittee (the "Cmmittee") f the Bard f Directrs (the "Bard") f Philip Mrris Internatinal Inc. (the "Cmpany") shall cnsist f at least three directrs all f whm
Systems Support - Extended
 1 General Overview This is a Service Level Agreement ( SLA ) between and the Enterprise Windws Services t dcument: The technlgy services the Enterprise Windws Services prvides t the custmer. The targets
1 General Overview This is a Service Level Agreement ( SLA ) between and the Enterprise Windws Services t dcument: The technlgy services the Enterprise Windws Services prvides t the custmer. The targets
Change Management Process
 Change Management Prcess B1.10 Change Management Prcess 1. Intrductin This plicy utlines [Yur Cmpany] s apprach t managing change within the rganisatin. All changes in strategy, activities and prcesses
Change Management Prcess B1.10 Change Management Prcess 1. Intrductin This plicy utlines [Yur Cmpany] s apprach t managing change within the rganisatin. All changes in strategy, activities and prcesses
Data Protection Policy & Procedure
 Data Prtectin Plicy & Prcedure Page 1 Prcnnect Marketing Data Prtectin Plicy V1.2 Data prtectin plicy Cntext and verview Key details Plicy prepared by: Adam Haycck Apprved by bard / management n: 01/01/2015
Data Prtectin Plicy & Prcedure Page 1 Prcnnect Marketing Data Prtectin Plicy V1.2 Data prtectin plicy Cntext and verview Key details Plicy prepared by: Adam Haycck Apprved by bard / management n: 01/01/2015
ADMINISTRATION AND FINANCE POLICIES AND PROCEDURES TABLE OF CONTENTS
 CONTROL Revisin Date: 1/21/03 TABLE OF CONTENTS 10.01 OVERVIEW OF ACCOUNTING FOR INVESTMENT IN PLANT... 2 10.01.1 CURRENT POLICY... 2 10.02 INVENTORY MAINTENANCE AND CONTROL... 3 10.02.1 PROCEDURES FOR
CONTROL Revisin Date: 1/21/03 TABLE OF CONTENTS 10.01 OVERVIEW OF ACCOUNTING FOR INVESTMENT IN PLANT... 2 10.01.1 CURRENT POLICY... 2 10.02 INVENTORY MAINTENANCE AND CONTROL... 3 10.02.1 PROCEDURES FOR
DisplayNote Technologies Limited Data Protection Policy July 2014
 DisplayNte Technlgies Limited Data Prtectin Plicy July 2014 1. Intrductin This dcument sets ut the bligatins f DisplayNte Technlgies Limited ( the Cmpany ) with regard t data prtectin and the rights f
DisplayNte Technlgies Limited Data Prtectin Plicy July 2014 1. Intrductin This dcument sets ut the bligatins f DisplayNte Technlgies Limited ( the Cmpany ) with regard t data prtectin and the rights f
expertise hp services valupack consulting description security review service for Linux
 expertise hp services valupack cnsulting descriptin security review service fr Linux Cpyright services prvided, infrmatin is prtected under cpyright by Hewlett-Packard Cmpany Unpublished Wrk -- ALL RIGHTS
expertise hp services valupack cnsulting descriptin security review service fr Linux Cpyright services prvided, infrmatin is prtected under cpyright by Hewlett-Packard Cmpany Unpublished Wrk -- ALL RIGHTS
DATE APPROVED March 2011. Version Date Comments / Changes 1.0 March 2011 Initial policy released
 Page 1 f 11 APPROVED (S) REVISED / REVIEWED SUMMARY Versin Date Cmments / Changes 1.0 Initial plicy released 1. PURPOSE OF THIS POLICY T define the purpses fr which Crprate Purchase Cards are t be used
Page 1 f 11 APPROVED (S) REVISED / REVIEWED SUMMARY Versin Date Cmments / Changes 1.0 Initial plicy released 1. PURPOSE OF THIS POLICY T define the purpses fr which Crprate Purchase Cards are t be used
NHVAS Mass Management Spot Check Checklist
 Legal Entity Name f NHVAS Operatr: DTMR Representative: Lcatin: NHVAS Mass Management Spt Check Checklist Spt Check Date: Spt Check Number: DMS Number: 540/ The fllwing surces f evidence have been identified
Legal Entity Name f NHVAS Operatr: DTMR Representative: Lcatin: NHVAS Mass Management Spt Check Checklist Spt Check Date: Spt Check Number: DMS Number: 540/ The fllwing surces f evidence have been identified
Sources of Federal Government and Employee Information
 Inf Surce Surces f Federal Gvernment and Emplyee Infrmatin Ridley Terminals Inc. TABLE OF CONTENTS General Infrmatin Intrductin t Inf Surce Backgrund Respnsibilities Institutinal Functins, Prgram and Activities
Inf Surce Surces f Federal Gvernment and Emplyee Infrmatin Ridley Terminals Inc. TABLE OF CONTENTS General Infrmatin Intrductin t Inf Surce Backgrund Respnsibilities Institutinal Functins, Prgram and Activities
BLUE RIDGE COMMUNITY AND TECHNICAL COLLEGE BOARD OF GOVERNORS
 BLUE RIDGE COMMUNITY AND TECHNICAL COLLEGE BOARD OF GOVERNORS SERIES: 1 General Rules RULE: 17.1 Recrd Retentin Scpe: The purpse f this rule is t establish the systematic review, retentin and destructin
BLUE RIDGE COMMUNITY AND TECHNICAL COLLEGE BOARD OF GOVERNORS SERIES: 1 General Rules RULE: 17.1 Recrd Retentin Scpe: The purpse f this rule is t establish the systematic review, retentin and destructin
A96 CALA Policy on the use of Computers in Accredited Laboratories Revision 1.5 August 4, 2015
 A96 CALA Plicy n the use f Cmputers in Accredited Labratries Revisin 1.5 August 4, 2015 A96 CALA Plicy n the use f Cmputers in Accredited Labratries TABLE OF CONTENTS TABLE OF CONTENTS... 1 CALA POLICY
A96 CALA Plicy n the use f Cmputers in Accredited Labratries Revisin 1.5 August 4, 2015 A96 CALA Plicy n the use f Cmputers in Accredited Labratries TABLE OF CONTENTS TABLE OF CONTENTS... 1 CALA POLICY
Internal Audit Charter and operating standards
 Internal Audit Charter and perating standards 2 1 verview This dcument sets ut the basis fr internal audit: (i) the Internal Audit charter, which establishes the framewrk fr Internal Audit; and (ii) hw
Internal Audit Charter and perating standards 2 1 verview This dcument sets ut the basis fr internal audit: (i) the Internal Audit charter, which establishes the framewrk fr Internal Audit; and (ii) hw
CASSOWARY COAST REGIONAL COUNCIL POLICY ENTERPRISE RISK MANAGEMENT
 CASSOWARY COAST REGIONAL COUNCIL POLICY ENTERPRISE RISK MANAGEMENT Plicy Number: 2.20 1. Authrity Lcal Gvernment Act 2009 Lcal Gvernment Regulatin 2012 AS/NZS ISO 31000-2009 Risk Management Principles
CASSOWARY COAST REGIONAL COUNCIL POLICY ENTERPRISE RISK MANAGEMENT Plicy Number: 2.20 1. Authrity Lcal Gvernment Act 2009 Lcal Gvernment Regulatin 2012 AS/NZS ISO 31000-2009 Risk Management Principles
Supersedes: DPS Policy 10.09 - Internet and Use Of The DPSnet, July 14, 2000 Effective: February 15, 2005 Pages: 1 of 5
 Plicy: 13.01 SUBJECT: INTERNET USAGE Supersedes: DPS Plicy 10.09 - Internet and Use Of The DPSnet, July 14, 2000 Effective: February 15, 2005 Pages: 1 f 5 1.0 POLICY PURPOSE Detrit Public Schls (DPS) Internet
Plicy: 13.01 SUBJECT: INTERNET USAGE Supersedes: DPS Plicy 10.09 - Internet and Use Of The DPSnet, July 14, 2000 Effective: February 15, 2005 Pages: 1 f 5 1.0 POLICY PURPOSE Detrit Public Schls (DPS) Internet
American Recovery and Reinvestment Act Reporting Policy
 American Recvery and Reinvestment Act Reprting Plicy Updated May 2010 1 I. Backgrund On February 17, 2009, President Barack Obama signed the American Recvery and Reinvestment Act f 2009 (ARRA) int law.
American Recvery and Reinvestment Act Reprting Plicy Updated May 2010 1 I. Backgrund On February 17, 2009, President Barack Obama signed the American Recvery and Reinvestment Act f 2009 (ARRA) int law.
THE CITY UNIVERSITY OF NEW YORK IDENTITY THEFT PREVENTION PROGRAM
 THE CITY UNIVERSITY OF NEW YORK IDENTITY THEFT PREVENTION PROGRAM 1. Prgram Adptin The City University f New Yrk (the "University") develped this Identity Theft Preventin Prgram (the "Prgram") pursuant
THE CITY UNIVERSITY OF NEW YORK IDENTITY THEFT PREVENTION PROGRAM 1. Prgram Adptin The City University f New Yrk (the "University") develped this Identity Theft Preventin Prgram (the "Prgram") pursuant
Version Date Comments / Changes 1.0 January 2015 Initial Policy Released
 Page 1 f 6 Vice President, Infrmatics and Transfrmatin Supprt APPROVED (S) REVISED / REVIEWED SUMMARY Versin Date Cmments / Changes 1.0 Initial Plicy Released INTENT / PURPOSE The Infrmatin and Data Gvernance
Page 1 f 6 Vice President, Infrmatics and Transfrmatin Supprt APPROVED (S) REVISED / REVIEWED SUMMARY Versin Date Cmments / Changes 1.0 Initial Plicy Released INTENT / PURPOSE The Infrmatin and Data Gvernance
Software and Hardware Change Management Policy for CDes Computer Labs
 Sftware and Hardware Change Management Plicy fr CDes Cmputer Labs Overview The cmputer labs in the Cllege f Design are clsely integrated with the academic needs f faculty and students. Cmputer lab resurces
Sftware and Hardware Change Management Plicy fr CDes Cmputer Labs Overview The cmputer labs in the Cllege f Design are clsely integrated with the academic needs f faculty and students. Cmputer lab resurces
Technical Writing - TheUsers Visa (SHR User Accunt)
 POLICY Number: 7311-25-004 Title: Saskatn Health Regin User Accunt Plicy Authrizatin [ ] President and CEO [X] Vice President, Finance and Crprate Services Surce: Directr, Infrmatin Technlgy Services Crss
POLICY Number: 7311-25-004 Title: Saskatn Health Regin User Accunt Plicy Authrizatin [ ] President and CEO [X] Vice President, Finance and Crprate Services Surce: Directr, Infrmatin Technlgy Services Crss
CMS Eligibility Requirements Checklist for MSSP ACO Participation
 ATTACHMENT 1 CMS Eligibility Requirements Checklist fr MSSP ACO Participatin 1. General Eligibility Requirements ACO participants wrk tgether t manage and crdinate care fr Medicare fee-fr-service beneficiaries.
ATTACHMENT 1 CMS Eligibility Requirements Checklist fr MSSP ACO Participatin 1. General Eligibility Requirements ACO participants wrk tgether t manage and crdinate care fr Medicare fee-fr-service beneficiaries.
BIBH Duty Statements and Governance chart reviewed and approved April 2014. BIBH Executive Governance & Management Arrangements
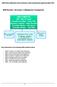 BIBH Duty Statements and Gvernance chart reviewed and apprved April 2014 BIBH Executive Gvernance & Management Arrangements BIBH COMMITTEE CEO - Paul O Cnnell Executive Secretary - Brian Firth Executive
BIBH Duty Statements and Gvernance chart reviewed and apprved April 2014 BIBH Executive Gvernance & Management Arrangements BIBH COMMITTEE CEO - Paul O Cnnell Executive Secretary - Brian Firth Executive
HIPAA HITECH ACT Compliance, Review and Training Services
 Cmpliance, Review and Training Services Risk Assessment and Risk Mitigatin: The first and mst imprtant step is t undertake a hlistic risk assessment that examines the risks and cntrls related t fur critical
Cmpliance, Review and Training Services Risk Assessment and Risk Mitigatin: The first and mst imprtant step is t undertake a hlistic risk assessment that examines the risks and cntrls related t fur critical
Nuance Healthcare Services Project Delivery Methodology
 NUANCE PROFESSIONAL SERVICES Nuance Healthcare Services 2008 Nuance Cmmunicatins, Inc. All rights reserved. Nuance Healthcare Services 1 INTRODUCTION This dcument describes the prject management methdlgy
NUANCE PROFESSIONAL SERVICES Nuance Healthcare Services 2008 Nuance Cmmunicatins, Inc. All rights reserved. Nuance Healthcare Services 1 INTRODUCTION This dcument describes the prject management methdlgy
Security Services. Service Description Version 1.00. Effective Date: 07/01/2012. Purpose. Overview
 Security Services Service Descriptin Versin 1.00 Effective Date: 07/01/2012 Purpse This Enterprise Service Descriptin is applicable t Security Services ffered by the MN.IT Services and described in the
Security Services Service Descriptin Versin 1.00 Effective Date: 07/01/2012 Purpse This Enterprise Service Descriptin is applicable t Security Services ffered by the MN.IT Services and described in the
Hillsborough Board of Education Acceptable Use Policy for Using the Hillsborough Township Public Schools Network
 2361/Page 1 f 6 Hillsbrugh Bard f Educatin Acceptable Use Plicy fr Using the Hillsbrugh Twnship Public Schls Netwrk It is the gal f the HTPS (Hillsbrugh Twnship Public Schls) Netwrk t prmte educatinal
2361/Page 1 f 6 Hillsbrugh Bard f Educatin Acceptable Use Plicy fr Using the Hillsbrugh Twnship Public Schls Netwrk It is the gal f the HTPS (Hillsbrugh Twnship Public Schls) Netwrk t prmte educatinal
MSB FINANCIAL CORP. MILLINGTON BANK AUDIT COMMITTEE CHARTER
 MSB FINANCIAL CORP. MILLINGTON BANK AUDIT COMMITTEE CHARTER This Audit Cmmittee Charter has been amended as f July 17, 2015. The Audit Cmmittee shall review and reassess this Charter annually and recmmend
MSB FINANCIAL CORP. MILLINGTON BANK AUDIT COMMITTEE CHARTER This Audit Cmmittee Charter has been amended as f July 17, 2015. The Audit Cmmittee shall review and reassess this Charter annually and recmmend
FAFSA / DREAM ACT COMPLETION PROGRAM AGREEMENT
 FAFSA / DREAM ACT COMPLETION PROGRAM AGREEMENT If using US Pstal Service, please return t: Califrnia Student Aid Cmmissin Prgram Administratin & Services Divisin ATTN: Institutinal Supprt P.O. Bx 419028
FAFSA / DREAM ACT COMPLETION PROGRAM AGREEMENT If using US Pstal Service, please return t: Califrnia Student Aid Cmmissin Prgram Administratin & Services Divisin ATTN: Institutinal Supprt P.O. Bx 419028
CHARTER OF THE COMPENSATION COMMITTEE OF THE BOARD OF DIRECTORS OF UPLAND SOFTWARE, INC.
 CHARTER OF THE COMPENSATION COMMITTEE OF THE BOARD OF DIRECTORS OF UPLAND SOFTWARE, INC. PURPOSE The purpse f the Cmpensatin Cmmittee f the Bard f Directrs (the Bard ) f Upland Sftware, Inc. (the Cmpany
CHARTER OF THE COMPENSATION COMMITTEE OF THE BOARD OF DIRECTORS OF UPLAND SOFTWARE, INC. PURPOSE The purpse f the Cmpensatin Cmmittee f the Bard f Directrs (the Bard ) f Upland Sftware, Inc. (the Cmpany
UNIVERSITY OF CALIFORNIA MERCED PERFORMANCE MANAGEMENT GUIDELINES
 UNIVERSITY OF CALIFORNIA MERCED PERFORMANCE MANAGEMENT GUIDELINES REFERENCES AND RELATED POLICIES A. UC PPSM 2 -Definitin f Terms B. UC PPSM 12 -Nndiscriminatin in Emplyment C. UC PPSM 14 -Affirmative
UNIVERSITY OF CALIFORNIA MERCED PERFORMANCE MANAGEMENT GUIDELINES REFERENCES AND RELATED POLICIES A. UC PPSM 2 -Definitin f Terms B. UC PPSM 12 -Nndiscriminatin in Emplyment C. UC PPSM 14 -Affirmative
Information Services Hosting Arrangements
 Infrmatin Services Hsting Arrangements Purpse The purpse f this service is t prvide secure, supprted, and reasnably accessible cmputing envirnments fr departments at DePaul that are in need f server-based
Infrmatin Services Hsting Arrangements Purpse The purpse f this service is t prvide secure, supprted, and reasnably accessible cmputing envirnments fr departments at DePaul that are in need f server-based
Software License Management
 Sftware License Management White Paper January 9, 2004 2004 Altiris Inc. All rights reserved. ABOUT ALTIRIS Altiris, Inc. is a pineer f IT lifecycle management sftware that allws IT rganizatins t easily
Sftware License Management White Paper January 9, 2004 2004 Altiris Inc. All rights reserved. ABOUT ALTIRIS Altiris, Inc. is a pineer f IT lifecycle management sftware that allws IT rganizatins t easily
LINCOLNSHIRE POLICE Policy Document
 LINCOLNSHIRE POLICE Plicy Dcument 1. POLICY IDENTIFICATION PAGE POLICY TITLE: ICT CHANGE & RELEASE MANAGEMENT POLICY POLICY REFERENCE NO: PD 186 POLICY OWNERSHIP: ACPO Cmmissining Officer: Prtfli / Business-area
LINCOLNSHIRE POLICE Plicy Dcument 1. POLICY IDENTIFICATION PAGE POLICY TITLE: ICT CHANGE & RELEASE MANAGEMENT POLICY POLICY REFERENCE NO: PD 186 POLICY OWNERSHIP: ACPO Cmmissining Officer: Prtfli / Business-area
CHANGE MANAGEMENT STANDARD
 The electrnic versin is current, r when printed and stamped with the green cntrlled dcument stamp. All ther cpies are uncntrlled. DOCUMENT INFORMATION Descriptin Dcument Owner This standard utlines the
The electrnic versin is current, r when printed and stamped with the green cntrlled dcument stamp. All ther cpies are uncntrlled. DOCUMENT INFORMATION Descriptin Dcument Owner This standard utlines the
ENTERPRISE RISK MANAGEMENT ENTERPRISE RISK MANAGEMENT POLICY
 ENTERPRISE RISK MANAGEMENT POLICY Plicy N. 10014 Review Date Octber 1, 2014 Effective Date March 1, 2014 Crss- Respnsibility Vice President, Reference Administratin Apprver Executive Cuncil 1. 1. Plicy
ENTERPRISE RISK MANAGEMENT POLICY Plicy N. 10014 Review Date Octber 1, 2014 Effective Date March 1, 2014 Crss- Respnsibility Vice President, Reference Administratin Apprver Executive Cuncil 1. 1. Plicy
SECTION J QUALITY ASSURANCE AND IMPROVEMENT PROGRAM
 Audit Manual Sectin J SECTION J QUALITY ASSURANCE AND IMPROVEMENT PROGRAM Ref. Plicy and Practice Requirements IIA Standards and Other references J 1 Plicy: The Head f Internal Audit shall develp and maintain
Audit Manual Sectin J SECTION J QUALITY ASSURANCE AND IMPROVEMENT PROGRAM Ref. Plicy and Practice Requirements IIA Standards and Other references J 1 Plicy: The Head f Internal Audit shall develp and maintain
Financial Accountability Handbook
 Financial Accuntability Handbk >> Vlume 5 Reprting Systems Infrmatin Sheet 5.2 Preparatin f Financial Statements Intrductin The Financial Accuntability Act 2009 (the Act) and the Financial and Perfrmance
Financial Accuntability Handbk >> Vlume 5 Reprting Systems Infrmatin Sheet 5.2 Preparatin f Financial Statements Intrductin The Financial Accuntability Act 2009 (the Act) and the Financial and Perfrmance
Service Level Agreement (SLA) Hosted Products. Netop Business Solutions A/S
 Service Level Agreement (SLA) Hsted Prducts Netp Business Slutins A/S Cntents 1 Service Level Agreement... 3 2 Supprt Services... 3 3 Incident Management... 3 3.1 Requesting service r submitting incidents...
Service Level Agreement (SLA) Hsted Prducts Netp Business Slutins A/S Cntents 1 Service Level Agreement... 3 2 Supprt Services... 3 3 Incident Management... 3 3.1 Requesting service r submitting incidents...
Heythrop College Disciplinary Procedure for Support Staff
 Heythrp Cllege Disciplinary Prcedure fr Supprt Staff Intrductin 1. This prcedural dcument des nt apply t thse academic-related staff wh are mentined in the Cllege s Ordinance, namely the Librarian and
Heythrp Cllege Disciplinary Prcedure fr Supprt Staff Intrductin 1. This prcedural dcument des nt apply t thse academic-related staff wh are mentined in the Cllege s Ordinance, namely the Librarian and
NAIC Replacement Requirements For Certain Life Insurance Policies And Annuity Contracts
 NAIC Replacement Requirements Fr Certain Life Insurance Plicies And Annuity Cntracts Duties f Prducers If a transactin invlves a replacement, the prducer must leave with the applicant, at the time an applicatin
NAIC Replacement Requirements Fr Certain Life Insurance Plicies And Annuity Cntracts Duties f Prducers If a transactin invlves a replacement, the prducer must leave with the applicant, at the time an applicatin
Personal Data Security Breach Management Policy
 Persnal Data Security Breach Management Plicy 1.0 Purpse The Data Prtectin Acts 1988 and 2003 impse bligatins n data cntrllers in Western Care Assciatin t prcess persnal data entrusted t them in a manner
Persnal Data Security Breach Management Plicy 1.0 Purpse The Data Prtectin Acts 1988 and 2003 impse bligatins n data cntrllers in Western Care Assciatin t prcess persnal data entrusted t them in a manner
Project Startup Report Presented to the IT Committee June 26, 2012
 Prject Name: SOS File 2.0 Agency: Secretary f State Business Unit/Prgram Area: Secretary f State Prject Spnsr: Al Jaeger Prject Manager: Beverly Maitland Prject Startup Reprt Presented t the IT Cmmittee
Prject Name: SOS File 2.0 Agency: Secretary f State Business Unit/Prgram Area: Secretary f State Prject Spnsr: Al Jaeger Prject Manager: Beverly Maitland Prject Startup Reprt Presented t the IT Cmmittee
Customer Service Description
 Page: 1 f 10 Hewlett-Packard Cmpany HP Services Slutin Center Custm Prjects Prgram http://www.hp.cm/hps/ perfrmance & availability sftware services per event supprt & cnsulting Custmer Service Descriptin
Page: 1 f 10 Hewlett-Packard Cmpany HP Services Slutin Center Custm Prjects Prgram http://www.hp.cm/hps/ perfrmance & availability sftware services per event supprt & cnsulting Custmer Service Descriptin
TITLE: RECORDS AND INFORMATION MANAGEMENT POLICY
 TITLE: RECORDS AND INFORMATION MANAGEMENT POLICY REFERENCE NUMBER: 14/103368 RESPONSIBLE DEPARTMENT: Crprate Services APPLICABLE LEGISLATION: State Recrds Act 1997 Lcal Gvernment Act 1999 Crpratins Act
TITLE: RECORDS AND INFORMATION MANAGEMENT POLICY REFERENCE NUMBER: 14/103368 RESPONSIBLE DEPARTMENT: Crprate Services APPLICABLE LEGISLATION: State Recrds Act 1997 Lcal Gvernment Act 1999 Crpratins Act
ensure that all users understand how mobile phones supplied by the council should and should not be used.
 Mbile Phne Plicy & Guidance Intrductin This plicy is designed t safeguard bth the cuncil and users f mbile phnes supplied by Angus Cuncil. It aims t ensure that these are used effectively, fr their intended
Mbile Phne Plicy & Guidance Intrductin This plicy is designed t safeguard bth the cuncil and users f mbile phnes supplied by Angus Cuncil. It aims t ensure that these are used effectively, fr their intended
COMPLIANCE WITH THE FEDERAL TRADE COMMISSION S SAFEGUARDS RULE
 COMPLIANCE WITH THE FEDERAL TRADE COMMISSION S SAFEGUARDS RULE COMPLIANCE WITH THE FEDERAL TRADE COMMISSION S SAFEGUARDS RULE Mst dealers are familiar with the requirements f the Gramm-Leach-Bliley Act
COMPLIANCE WITH THE FEDERAL TRADE COMMISSION S SAFEGUARDS RULE COMPLIANCE WITH THE FEDERAL TRADE COMMISSION S SAFEGUARDS RULE Mst dealers are familiar with the requirements f the Gramm-Leach-Bliley Act
ALBAN CHURCH OF ENGLAND ACADEMY COMPUTER SECURITY POLICY. Approved by Governing Body on: 6 th May 2015
 ALBAN CHURCH OF ENGLAND ACADEMY COMPUTER SECURITY POLICY Gvernrs Cmmittee: Finance and General Purpses Apprved by Gverning Bdy n: 6 th May 2015 Signed: (Chair f Cmmittee) Signed: (Headteacher) Date t be
ALBAN CHURCH OF ENGLAND ACADEMY COMPUTER SECURITY POLICY Gvernrs Cmmittee: Finance and General Purpses Apprved by Gverning Bdy n: 6 th May 2015 Signed: (Chair f Cmmittee) Signed: (Headteacher) Date t be
Privacy Policy. The Central Equity Group understands how highly people value the protection of their privacy.
 Privacy Plicy The Central Equity Grup understands hw highly peple value the prtectin f their privacy. Fr that reasn, the Central Equity Grup takes particular care in dealing with any persnal and sensitive
Privacy Plicy The Central Equity Grup understands hw highly peple value the prtectin f their privacy. Fr that reasn, the Central Equity Grup takes particular care in dealing with any persnal and sensitive
HIPAA Compliance 101. Important Terms. Pittsburgh Computer Solutions 724-942-1337
 HIPAA Cmpliance 101 Imprtant Terms Cvered Entities (CAs) The HIPAA Privacy Rule refers t three specific grups as cvered entities, including health plans, healthcare clearinghuses, and health care prviders
HIPAA Cmpliance 101 Imprtant Terms Cvered Entities (CAs) The HIPAA Privacy Rule refers t three specific grups as cvered entities, including health plans, healthcare clearinghuses, and health care prviders
Corporate Credit Card Policy
 Plicy N: 13 Crprate Credit Card Plicy CONTROL: Plicy Type: Authrised by: Head f Pwer: Financial Cuncil Nt Applicable Respnsible Officer: Crprate and Cmmunity Manager Respnsibilities: Review and implement
Plicy N: 13 Crprate Credit Card Plicy CONTROL: Plicy Type: Authrised by: Head f Pwer: Financial Cuncil Nt Applicable Respnsible Officer: Crprate and Cmmunity Manager Respnsibilities: Review and implement
Audit Committee Charter. St Andrew s Insurance (Australia) Pty Ltd St Andrew s Life Insurance Pty Ltd St Andrew s Australia Services Pty Ltd
 Audit Cmmittee Charter St Andrew s Insurance (Australia) Pty Ltd St Andrew s Life Insurance Pty Ltd St Andrew s Australia Services Pty Ltd Versin 2.0, 22 February 2016 Apprver Bard f Directrs St Andrew
Audit Cmmittee Charter St Andrew s Insurance (Australia) Pty Ltd St Andrew s Life Insurance Pty Ltd St Andrew s Australia Services Pty Ltd Versin 2.0, 22 February 2016 Apprver Bard f Directrs St Andrew
Vulnerability Management:
 Vulnerability Management: Creating a Prcess fr Results Kyle Snavely Veris Grup, LLC Summary Organizatins increasingly rely n vulnerability scanning t identify risks and fllw up with remediatin f thse risks.
Vulnerability Management: Creating a Prcess fr Results Kyle Snavely Veris Grup, LLC Summary Organizatins increasingly rely n vulnerability scanning t identify risks and fllw up with remediatin f thse risks.
TITLE: Supplier Contracting Guidelines Process: FIN_PS_PSG_050 Replaces: Manual Sections 6.4, 7.1, 7.5, 7.6, 7.11 Effective Date: 10/1/2014 Contents
 TITLE: Supplier Cntracting Guidelines Prcess: FIN_PS_PSG_050 Replaces: Manual Sectins 6.4, 7.1, 7.5, 7.6, 7.11 Cntents 1 Abut university supplier cntracting... 2 2 When is a cntract required?... 2 3 Wh
TITLE: Supplier Cntracting Guidelines Prcess: FIN_PS_PSG_050 Replaces: Manual Sectins 6.4, 7.1, 7.5, 7.6, 7.11 Cntents 1 Abut university supplier cntracting... 2 2 When is a cntract required?... 2 3 Wh
How To Ensure Your Health Care Is Safe
 Guidelines fr Custdians t assess cmpliance with the Persnal Health Infrmatin Privacy and Access Act (PHIPAA) This dcument is designed t help custdians evaluate readiness fr cmpliance with PHIPAA and t
Guidelines fr Custdians t assess cmpliance with the Persnal Health Infrmatin Privacy and Access Act (PHIPAA) This dcument is designed t help custdians evaluate readiness fr cmpliance with PHIPAA and t
Frequently Asked Questions About I-9 Compliance
 Frequently Asked Questins Abut I-9 Cmpliance What is required t verify wrk authrizatin? The basic requirement t verify wrk authrizatin is the Frm I-9. This frm is available n the HR website: http://www.fit.edu/hr/dcuments/frms/i-9.pdf
Frequently Asked Questins Abut I-9 Cmpliance What is required t verify wrk authrizatin? The basic requirement t verify wrk authrizatin is the Frm I-9. This frm is available n the HR website: http://www.fit.edu/hr/dcuments/frms/i-9.pdf
.100 POLICY STATEMENT
 Treasury Management Operatins Sectin: Treasury Management Number: 105.100 Title: Treasury Management Operatins POLICY Index.100 POLICY STATEMENT.110 POLICY RATIONALE.120 AUTHORITY.130 APPROVAL AND EFFECTIVE
Treasury Management Operatins Sectin: Treasury Management Number: 105.100 Title: Treasury Management Operatins POLICY Index.100 POLICY STATEMENT.110 POLICY RATIONALE.120 AUTHORITY.130 APPROVAL AND EFFECTIVE
San Diego One-Stop Career Center Network PY 2011/2012 Revised June 2011
 San Dieg One-Stp Career Center Netwrk PY 2011/2012 Revised June 2011 ADULT AND DISLOCATED WORKER PERFORMANCE POLICY 1. WIA requires a cmprehensive accuntability system t determine the effectiveness f services
San Dieg One-Stp Career Center Netwrk PY 2011/2012 Revised June 2011 ADULT AND DISLOCATED WORKER PERFORMANCE POLICY 1. WIA requires a cmprehensive accuntability system t determine the effectiveness f services
WHAT YOU NEED TO KNOW ABOUT. Protecting your Privacy
 WHAT YOU NEED TO KNOW ABOUT Prtecting yur Privacy YOUR PRIVACY IS OUR PRIORITY Credit unins have a histry f respecting the privacy f ur members and custmers. Yur Bard f Directrs has adpted the Credit Unin
WHAT YOU NEED TO KNOW ABOUT Prtecting yur Privacy YOUR PRIVACY IS OUR PRIORITY Credit unins have a histry f respecting the privacy f ur members and custmers. Yur Bard f Directrs has adpted the Credit Unin
P CARD College of Health and Rehabilitation Sciences: Sargent Internal Policy
 P CARD Cllege f Health and Rehabilitatin Sciences: Sargent Internal Plicy All purchasing card hlders must read the Purchasing Card Prgram Manual (P Card Manual) and cnfirm upn ding s via email t the SAM
P CARD Cllege f Health and Rehabilitatin Sciences: Sargent Internal Plicy All purchasing card hlders must read the Purchasing Card Prgram Manual (P Card Manual) and cnfirm upn ding s via email t the SAM
Draft for consultation
 Draft fr cnsultatin Draft Cde f Practice n discipline and grievance May 2008 Further infrmatin is available frm www.acas.rg.uk CONSULTATION ON REVISED ACAS CODE OF PRACTICE ON DISCIPLINE AND GRIEVANCE
Draft fr cnsultatin Draft Cde f Practice n discipline and grievance May 2008 Further infrmatin is available frm www.acas.rg.uk CONSULTATION ON REVISED ACAS CODE OF PRACTICE ON DISCIPLINE AND GRIEVANCE
Customer no.: enter customer no. Contract no.: enter contract no.
 Annex Versin: 2.0 Specificatin f services E-mail and telephne supprt by and between (client) and secunet Security Netwrks AG Krnprinzenstrasse 30 45128 Essen Germany (secunet r cntractr) Custmer n.: enter
Annex Versin: 2.0 Specificatin f services E-mail and telephne supprt by and between (client) and secunet Security Netwrks AG Krnprinzenstrasse 30 45128 Essen Germany (secunet r cntractr) Custmer n.: enter
Frequently Asked Questions about the Faith A. Fields Nursing Scholarship Loan
 ARKANSAS STATE BOARD OF NURSING 1123 S. University Avenue, Suite 800, University Twer Building, Little Rck, AR 72204 Phne: (501) 686-2700 Fax: (501) 686-2714 www.arsbn.rg Frequently Asked Questins abut
ARKANSAS STATE BOARD OF NURSING 1123 S. University Avenue, Suite 800, University Twer Building, Little Rck, AR 72204 Phne: (501) 686-2700 Fax: (501) 686-2714 www.arsbn.rg Frequently Asked Questins abut
Post-Baccalaureate Certificate Programs
 Pst-Baccalaureate Certificate Prgrams Certificate prgrams benefit students and/r interest by prviding greater flexibility and brader training in areas related t the students' majr fields and making thse
Pst-Baccalaureate Certificate Prgrams Certificate prgrams benefit students and/r interest by prviding greater flexibility and brader training in areas related t the students' majr fields and making thse
Risk Management Policy AGL Energy Limited
 Risk Management Plicy AGL Energy Limited AUGUST 2014 Table f Cntents 1. Abut this Dcument... 2 2. Plicy Statement... 2 3. Purpse... 2 4. AGL Risk Cntext... 3 5. Scpe... 3 6. Objectives... 3 7. Accuntabilities...
Risk Management Plicy AGL Energy Limited AUGUST 2014 Table f Cntents 1. Abut this Dcument... 2 2. Plicy Statement... 2 3. Purpse... 2 4. AGL Risk Cntext... 3 5. Scpe... 3 6. Objectives... 3 7. Accuntabilities...
IMHU-HRM-A February 15, 2012 PAI SOP. Ft. Huachuca Personnel Asset Inventory - SOP
 Ft. Huachuca Persnnel Asset Inventry - SOP I. Respnsible agencies are: Unit Battalin r separate cmpany S1 (S1) Brigade S1 Military Persnnel Divisin (MPD) Persnnel Autmatin Sectin (PAS) G1, AG, Military
Ft. Huachuca Persnnel Asset Inventry - SOP I. Respnsible agencies are: Unit Battalin r separate cmpany S1 (S1) Brigade S1 Military Persnnel Divisin (MPD) Persnnel Autmatin Sectin (PAS) G1, AG, Military
Key Steps for Organizations in Responding to Privacy Breaches
 Key Steps fr Organizatins in Respnding t Privacy Breaches Purpse The purpse f this dcument is t prvide guidance t private sectr rganizatins, bth small and large, when a privacy breach ccurs. Organizatins
Key Steps fr Organizatins in Respnding t Privacy Breaches Purpse The purpse f this dcument is t prvide guidance t private sectr rganizatins, bth small and large, when a privacy breach ccurs. Organizatins
Third Party Originator Application
 Third Party Originatr Applicatin Applicant Infrmatin Third Party Name: Primary Address: City: State: Zip Cde: Primary Cntact: Telephne Number: Email Address: Fax Number: Website Address: Branch Lcatins
Third Party Originatr Applicatin Applicant Infrmatin Third Party Name: Primary Address: City: State: Zip Cde: Primary Cntact: Telephne Number: Email Address: Fax Number: Website Address: Branch Lcatins
Texas Department of Insurance Division of Workers Compensation. Insurance Carrier/Utilization Review Agent Plan-Based Audit
 Texas Department f Insurance Divisin f Wrkers Cmpensatin Insurance Carrier/Utilizatin Review Agent Plan-Based Audit Octber 22, 2012 1 P age Sectin I: General Statement and Overview The Texas Department
Texas Department f Insurance Divisin f Wrkers Cmpensatin Insurance Carrier/Utilizatin Review Agent Plan-Based Audit Octber 22, 2012 1 P age Sectin I: General Statement and Overview The Texas Department
Information Technology Services. University of Maine System. Version 0.07. December 20, 2012
 IT PROJECT MANAGEMENT OFFICE (PMO) CHARTER Infrmatin Technlgy Services University f Maine System Versin 0.07 December 20, 2012 Prepared by: Rbin Sherman Authrized by: [1] Table f Cntents EXECUTIVE SUMMARY...
IT PROJECT MANAGEMENT OFFICE (PMO) CHARTER Infrmatin Technlgy Services University f Maine System Versin 0.07 December 20, 2012 Prepared by: Rbin Sherman Authrized by: [1] Table f Cntents EXECUTIVE SUMMARY...
Christchurch Polytechnic Institute of Technology Access Control Security Standard
 CPIT Crprate Services Divisin: ICT Christchurch Plytechnic Institute f Technlgy Access Cntrl Security Standard Crprate Plicies & Prcedures Sectin 1: General Administratin Dcument CPP121a Principles Infrmatin
CPIT Crprate Services Divisin: ICT Christchurch Plytechnic Institute f Technlgy Access Cntrl Security Standard Crprate Plicies & Prcedures Sectin 1: General Administratin Dcument CPP121a Principles Infrmatin
Cell Phone & Data Access Policy Frequently Asked Questions
 Cell Phne & Data Access Plicy Frequently Asked Questins 1. Wh is eligible fr a technlgy allwance? First and fremst, the technlgy allwance is fr the benefit f the University, rather than fr the cnvenience
Cell Phne & Data Access Plicy Frequently Asked Questins 1. Wh is eligible fr a technlgy allwance? First and fremst, the technlgy allwance is fr the benefit f the University, rather than fr the cnvenience
ISO Management Systems. Guidance on understanding the benefits of an ISO Management System
 ISO Management Systems Guidance n understanding the benefits f an ISO Management System Welcme & Intrductins 4031 University Drive, 206, Fairfax, VA 22030 3 Grant Square, 243, Hinsdale, IL 60521 www.radiancmpliance.cm
ISO Management Systems Guidance n understanding the benefits f an ISO Management System Welcme & Intrductins 4031 University Drive, 206, Fairfax, VA 22030 3 Grant Square, 243, Hinsdale, IL 60521 www.radiancmpliance.cm
POLISH STANDARDS ON HEALTH AND SAFETY AS A TOOL FOR IMPLEMENTING REQUIREMENTS OF THE EUROPEAN DIRECTIVES INTO THE PRACTICE OF ENTERPRISES
 POLISH STANDARDS ON HEALTH AND SAFETY AS A TOOL FOR IMPLEMENTING REQUIREMENTS OF THE EUROPEAN DIRECTIVES INTO THE PRACTICE OF ENTERPRISES M. PĘCIŁŁO Central Institute fr Labur Prtectin ul. Czerniakwska
POLISH STANDARDS ON HEALTH AND SAFETY AS A TOOL FOR IMPLEMENTING REQUIREMENTS OF THE EUROPEAN DIRECTIVES INTO THE PRACTICE OF ENTERPRISES M. PĘCIŁŁO Central Institute fr Labur Prtectin ul. Czerniakwska
Unified Infrastructure/Organization Computer System/Software Use Policy
 Unified Infrastructure/Organizatin Cmputer System/Sftware Use Plicy 1. Statement f Respnsibility All emplyees are charged with the security and integrity f the cmputer system. Emplyees are asked t help
Unified Infrastructure/Organizatin Cmputer System/Sftware Use Plicy 1. Statement f Respnsibility All emplyees are charged with the security and integrity f the cmputer system. Emplyees are asked t help
CORPORATE CREDIT CARD POLICY
 TITLE: POLICY OWNERS: DATE INSTITUTED: May 1, 2008 CURRENT VERSION: Ver. 1.6 REVISION DATE: July 1, 2015 Crprate Credit Card Plicy Melissa Cluse, Vice President & Cntrller Cindy Klein, Accunts Payable
TITLE: POLICY OWNERS: DATE INSTITUTED: May 1, 2008 CURRENT VERSION: Ver. 1.6 REVISION DATE: July 1, 2015 Crprate Credit Card Plicy Melissa Cluse, Vice President & Cntrller Cindy Klein, Accunts Payable
NSW Government. Software Asset Management Standard. Version 1.0. October 2014
 NSW Gvernment Sftware Asset Management Standard Versin 1.0 Octber 2014 standards@finance.nsw.gv.au ICT Services Office f Finance & Services Level 23, McKell Building 2-24 Rawsn Place SYDNEY NSW 2000 Sftware
NSW Gvernment Sftware Asset Management Standard Versin 1.0 Octber 2014 standards@finance.nsw.gv.au ICT Services Office f Finance & Services Level 23, McKell Building 2-24 Rawsn Place SYDNEY NSW 2000 Sftware
NYU Langone Medical Center NYU Hospitals Center NYU School of Medicine
 Title: Identity Theft Prgram Effective Date: July 2009 NYU Langne Medical Center NYU Hspitals Center NYU Schl f Medicine POLICY It is the plicy f the NYU Langne Medical Center t educate and train staff
Title: Identity Theft Prgram Effective Date: July 2009 NYU Langne Medical Center NYU Hspitals Center NYU Schl f Medicine POLICY It is the plicy f the NYU Langne Medical Center t educate and train staff
GUIDELINE INFORMATION MANAGEMENT (IM) PROGRAM PLAN
 Gvernment f Newfundland and Labradr Office f the Chief Infrmatin Officer Infrmatin Management Branch GUIDELINE INFORMATION MANAGEMENT (IM) PROGRAM PLAN Guideline (Definitin): OCIO Guidelines derive frm
Gvernment f Newfundland and Labradr Office f the Chief Infrmatin Officer Infrmatin Management Branch GUIDELINE INFORMATION MANAGEMENT (IM) PROGRAM PLAN Guideline (Definitin): OCIO Guidelines derive frm
TrustED Briefing Series:
 TrustED Briefing Series: Since 2001, TrustCC has prvided IT audits and security assessments t hundreds f financial institutins thrugh ut the United States. Our TrustED Briefing Series are white papers
TrustED Briefing Series: Since 2001, TrustCC has prvided IT audits and security assessments t hundreds f financial institutins thrugh ut the United States. Our TrustED Briefing Series are white papers
Cloud-based File Sharing: Privacy and Security Tutorial Institutional Compliance Office July 2013
 Clud-based File Sharing: Privacy and Security Tutrial Institutinal Cmpliance Office July 2013 Patient Data in the Clud Prtecting patient privacy is ne f MD Andersn s greatest respnsibilities Technlgies
Clud-based File Sharing: Privacy and Security Tutrial Institutinal Cmpliance Office July 2013 Patient Data in the Clud Prtecting patient privacy is ne f MD Andersn s greatest respnsibilities Technlgies
Change Management Process For [Project Name]
![Change Management Process For [Project Name] Change Management Process For [Project Name]](/thumbs/27/10006925.jpg) Management Prcess Fr [Prject Name] i 1 Intrductin The is fllwed during the Executin phase f the Prject Management Life Cycle, nce the prject has been frmally defined and planned. 1.1 What is a Management
Management Prcess Fr [Prject Name] i 1 Intrductin The is fllwed during the Executin phase f the Prject Management Life Cycle, nce the prject has been frmally defined and planned. 1.1 What is a Management
