Secure Network Filesystem (Secure NFS) By Travis Zigler
|
|
|
- Mitchell Robinson
- 8 years ago
- Views:
Transcription
1 Secure Network Filesystem (Secure NFS) By Travis Zigler
2 Overview of Secure NFS Problems with NFS Security of Basic NFS Configurations Securing NFS with SSH Tutorial Securing NFS with SSL Overview Conclusions Resources
3 Brief Introduction of NFS NFS is a widely used protocol that allows users to share files across a network. NFS has been around for a long time and is a mature and well understood protocol. Since it has been around for awhile and is well understood, the short comings of NFS are also well understood and exploited. If security is necessary, BASIC NFS IS NOT THE SERVICE TO USE. So Why is NFS so bad?
4 Problems of NFS NFS relies on the inherently insecure UDP protocol Transactions between host and client are NOT encrypted Hosts and users cannot be easily authenticated, IP Spoofing is possible Persmissions are granted by normal access rules Firewall configuration is difficult because of the way NFS daemons work
5 So when is a good time to use basic NFS? The only time that basic NFS should ever be used is on a secured LAN that everyone on the network is trusted. This philosphy is great, but is very impratical and very rarely the case. Most networks don't provide the comfort of having users that are completely trusted. And most networks aren't completely secured LANs. If a hacker/cracker could get into your LAN and basic NFS configurations were in place, any file in your shared directories could be compromised. And if you allow a user to be able to get root UID in the shares, your entire systems could be easily compromised.
6 Security of Basic NFS Configurations 1) Firewall Setup Networking NFS through firewalls is a nightmare for system administrators because port numbers for the service may change between reboots, network restarts, or may be different on other systems. The ports are randomly assigned. To make a firewall that can control NFS, you must first tie down the ports it uses.
7 Port Listings for NFS using rpcinfo p
8 Before After After restarting the service, the ports have changed.
9 If you wish to control NFS you must fix the port settings in their proper configuration files. But since I am going to talk about other protocols that route NFS through their ports, I will not lecture about that now, but have attached the instructions on fixing the ports if you wish to learn how do this. Standard Port Settings for NFS Deamon RPM Standard PortRecommended Port Needs Changed? Portmap Portmap No rpc.statd Nfs-utils Random 4000 Yes rpc.nfsd Nfs-utils No rpc.lockd Nfs-utils and kernel Random 4001 Yes rpc.mountd Nfs-utils Random 4002 Yes rpc.rquotad Quota Random 4003 Yes
10 Changing rpc.statd To change the rpc.statd port, edit the line in /etc/init.d/nfslock, you must edit the start() function, under the line that says something like daemon rpc.statd, you must add p 4000 to assign it port 4000, it is shown in the graphic under xemacs
11 NFS Lock Configuration open /etc/modules.conf and add/edit the line options lockd nlm_udpport=4001 nlm_tcpport=4001 if the lockd is compiled directly into the kernel instead of a loadable module, you will need to add the parameters lockd.udpport=4001 lockd.tcpport=4001 to the kernel command line in lilo or grub configuration instead
12 Mountd port Edit /etc/sysconfig/nfs add the line MOUNTD_PORT=4002
13 Rquotad port configuration Verify your system is running the quota version 3.08 or higher Make sure the /etc/rpc has this line present rquotad rquotaprog quota rquota, do not change any of these values Add or modify /etc/services rquotad 4003/tcp & rquotad 4003/udp
14 Basic Security for NFS Issues Access to NFS is provided by a mount to a particular directory listed in the /etc/exports file. Names or IP addresses are setup for machines that are allowed access. If a clients IP matches a share, it can mount, regardless if it is really the IP it claims to be. This makes it insecure. Someone spoofing IP addresses or a compromised machine can mount on your access points. File access is done using normal file access controls because access control is not a function of NFS particularly. This means, that once a drive is mounted, user and group permissions take over the access control of the files. Example: Let's say I map to UID 7777 on the server, and create a file that is only accessible to me. Then later, on another client, someone else maps to UID 7777 and has full access to files that I made only accessible to myself. Also, if someone has root on the client, they can do su and become ANY user.
15 Basic Security for NFS Issues Continued These steps will help you decrease some security risk, but not all, advanced tips will be given later. Edit /etc/hosts.deny with ALL:ALL to deny everyone Edit /etc/hosts.allow with portmap: your_subnet/subnet_mask Do the same for lockd, rquotad, mountd, and statd this will allow everyone in your subnet to access portmap and other NFS daemons but no one else, these settings can be modified differently if you want more specific ranges Use IP numbers in these fields, not hostnames On the server machine, make sure you specifically add the line root_squash to your shares in the /etc/exports file This tells the server that we don't want to trust root on the client machines
16 Basic Security for NFS Issues Continued root_squash will look something like this in /etc/exports /home/share host_ip(rw, root_squash) These options say the host computer at host_ip is sharing /home/share with read/write access and no root UID Even with this option, someone could still su and change users. That cannot be helped, but you can make all files on the shared drive owned by root, and since root is the only account a client can't change too, the files cannot be changed. Another good option is to make everything read only with ro Some good options for the client machine are nosuid and noexec, nosuid limits root executables on the client, noexec limits all executables on the mount but this may be impractical I have appended at the end, links for Firewall ipchain configurations
17 Now that we have looked at basic security, how secure are we? The answer is still, not secure at all. These options limit the ports used, and access controls on the servers and clients, but what about the transmissions? NFS is sent in Clear Text. This means it is not encrypted. Anyone running a sniffer program can take a look at your packets travelling across the network. This could mean bad news if you're sharing something like PGP keys or SSH keys over your NFS shares. So what can we do to limit and fix our network transmissions? We all know that portmap and other NFS daemons are problems for security, so one of the best options we have to fix these problems are tunneling through other services.
18 Tunneling Programs Overview So now, let's take a step back from the basic configurations and start over with a more secure way of thinking. The things we need to fix about NFS are: What ports should we use for our transmissions Setting up firewall settings to handle a tunneled version of NFS Handling encryption and authentication over a transmission
19 Tunneling Options When it comes to tunneling, the tunnel is only as secure as the protocol that creates it, with that said, the security of your Secure NFS is only as good as the services you use to create it. After doing a whole lot of googling around online, I find very few tutorials on how to setup a Secure NFS, but as it seems most tutorials I found were using SSH or SSL. The details of these tunneling programs will be given to you by other speakers, so I will try not to go into much detail on them. The tutorial I will give, shows secure NFS through SSH, but other ways are definitely possible. Since these configurations are fairly lengthy, I will try to limit them as much as possible, but provide the links to the sources I have used if further clarification is needed. I will also give a brief overview of Secure NFS over SSL.
20 Secure NFS over OpenSSH Overview Prerequisites Getting Started Server configuration /etc/exports Firewall design for forwarding / ipchains and iptables Client configuration Find what ports mountd and nfsd are running Set local forwarding rules Mount the shares
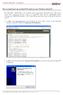
21 Prerequisites Getting Started Make sure SSH is installed. Most major linux distrobutions come with Ssh already installed, you can check by viewing your services, in my case, I am running Mandrake 10.1 and from the picture you can see it is running
22 Server Configuration /etc/exports Setup a directory to share, this could be anything, but in my example I will use /home/username/ssh_share, this can be done by typing mkdir /home/username/ssh_share as root Open and edit the /etc/exports file to contain the share to itself, this will be something like /home/username/ssh_share (rw,insecure,root_squash) This adds the share /home/username/ssh_share and is the IP of my machine, the insecure option just means it can use ports above 1023
23 Server Configuration Firewall Note: when starting the services, NFS must be started before SSH, because SSH may bind the ports used by NFS, and NFS will not start The following rules should be setup for the firewall to allow NFS over SSH to work: IPTABLES iptables A INPUT i eth0 p tcp s client dport ssh j ACCEPT iptables A OUTPUT o eth0 p tcp sport ssh d client j ACCEPT iptables A INPUT i eth0 p tcp s client dport 111 j ACCEPT iptables A OUTPUT o eth0 p tcp sport 111 d client j ACCEPT IPCHAINS ipchains A input i eth0 p tcp s client dport ssh j ACCEPT ipchains A output i eth0 p tcp sport ssh d client j ACCEPT ipchains A input i eth0 p tcp s client dport 111 j ACCEPT ipchains A output i eth0 p tcp sport 111 d client j ACCEPT **client is an IP or network to be allowed, this is for a firewall with default policy of DENY
24 Client Configuration Steps To Follow Find out the port numbers that mountd and nfsd are using Setup forwarding rules locally for SSH Mount the shares Port Numbers On the server, use the rpcinfo p command to find out the server port numbers for mountd and nfsd In my example they are: nfs 2049 and mountd 4002
25 Client Configuration Continued Now that we have the port numbers they can be used to create the tunnels from the server to the client, I will use 2222 as the port nfsd will connect on the local machine, and 3333 as the port mountd will use. We will call our server server, and out client client The user trying to connect will be called user, so on the command line We would type something like this: For connecting the nfsd: ssh f L 2222:server:2049 l user server sleep 600 For connecting mountd: ssh f L 3333:server:4002 l user server sleep 600 OR concatenate the two above commands with extra options: ssh f c blowfish L 3333:server:2049 L 3333:server:4002 l user server /bin/sleep 600 **sleep simply waits the number of seconds specified for connection, the extra option c blowfish just changes the encryption type, which is faster than the default (3des)
26 After adding the tunnels we can now mount them. This is done using the command: mount t nfs o tcp,port=2222,mountport=3333 localhost:/home/username/ssh_share /mnt/nfs/ssh_share **where /mnt/nfs/ssh_share is the local directory for the mount This can be made easier by automating the process with scripts and such but that is not the focus of this presentation. Firewall Config for the Client iptables A INPUT i eth0 p tcp! syn s server sport ssh j ACCEPT iptables A OUTPUT o eth0 p tcp d server dport ssh j ACCEPT iptables A INPUT i eth0 p tcp! syn s server sport 111 j ACCEPT iptables A OUTPUT o eth0 p tcp d server dport 111 j ACCEPT ipchains A input i eth0 p tcp! y s server sport ssh j ACCEPT ipchains A output i eth0 p tcp d server dport ssh j ACCEPT ipchains A input i eth0 p tcp! y s server sport 111 j ACCEPT ipchains A output i eth0 p tcp d server dport 111 j ACCEPT
27 Additions, Comments, and Warnings Generating ssh keys will help with logging on to the mounts by eliminating the need to type in passwords Users are still not authenticated, but hosts can be authenticated by the use of the ssh keys Since all client connections using SSH are encrypted, there will be a Significant increase in CPU overhead, use of different encryptions for the tunnels may decrease this (our example we used blowfish instead of 3des)
28 NFS Over SSL Overview NFS can also be used in a similar way over an SSL tunnel Clients will tunnel to the server via the SSL secured ports, therefore the connections from the nfsd, mountd, etc are coming from the localhost machine, and not directly from the client, therefore you must appropriately edit the /etc/exports file to except mounts from the localhost You may also close the ports used for portmapper, nfsd, mountd, etc because the services are using the SSL ports, and you may setup your firewall in a way that only allows specified IP addresses to contact you SSL ports SSL can provide certificate verification between clients and hosts
29 Conclusions Basic NFS setups are insecure over network transmissions The only use of basic NFS is over a secured LAN with trusted users The only way to increase security of NFS is to use an encrypted channel SSH and SSL can provide the means for an NFS channel from client to server The use of authentication keys will increase security of your connections Increased security also increases the CPU overhead Different kinds of encryption techniques can balance between CPU overhead & security The process of setting up your Secure NFS tunnels can be automated through scripts Secure NFS is only as good as the tunneling services used to implement it
30 Resources Page Secure NFS and NIS via SSH Tunneling Encrypted NFS with OpenSSH and Linux NFS over SSL Implementing NFS snfs Secure NFS Setting Up A NFS Server howto/server.html Security and NFS
31 End of Presentation
SoftNAS Application Guide: In-Flight Encryption 12/7/2015 SOFTNAS LLC
 SoftNAS Application Guide: In-Flight Encryption 12/7/2015 SOFTNAS LLC SoftNAS Application Guide: In-Flight Encryption Contents Introduction to In-Flight Data Encryption... 2 CIFS Encryption In-Flight...
SoftNAS Application Guide: In-Flight Encryption 12/7/2015 SOFTNAS LLC SoftNAS Application Guide: In-Flight Encryption Contents Introduction to In-Flight Data Encryption... 2 CIFS Encryption In-Flight...
How To Set Up A Network Map In Linux On A Ubuntu 2.5 (Amd64) On A Raspberry Mobi) On An Ubuntu 3.5.2 (Amd66) On Ubuntu 4.5 On A Windows Box
 CSC-NETLAB Packet filtering with Iptables Group Nr Name1 Name2 Name3 Date Instructor s Signature Table of Contents 1 Goals...2 2 Introduction...3 3 Getting started...3 4 Connecting to the virtual hosts...3
CSC-NETLAB Packet filtering with Iptables Group Nr Name1 Name2 Name3 Date Instructor s Signature Table of Contents 1 Goals...2 2 Introduction...3 3 Getting started...3 4 Connecting to the virtual hosts...3
Using Network Attached Storage with Linux. by Andy Pepperdine
 Using Network Attached Storage with Linux by Andy Pepperdine I acquired a WD My Cloud device to act as a demonstration, and decide whether to use it myself later. This paper is my experience of how to
Using Network Attached Storage with Linux by Andy Pepperdine I acquired a WD My Cloud device to act as a demonstration, and decide whether to use it myself later. This paper is my experience of how to
Swiss Cyber Storm II Case: NFS Hacking
 Swiss Cyber Storm II Case: NFS Hacking Axel Neumann Compass Security AG Glärnischstrasse 7 Postfach 1628 CH-8640 Rapperswil Tel +41 55-214 41 60 Fax +41 55-214 41 61 team@csnc.ch
Swiss Cyber Storm II Case: NFS Hacking Axel Neumann Compass Security AG Glärnischstrasse 7 Postfach 1628 CH-8640 Rapperswil Tel +41 55-214 41 60 Fax +41 55-214 41 61 team@csnc.ch
1:1 NAT in ZeroShell. Requirements. Overview. Network Setup
 1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
1:1 NAT in ZeroShell Requirements The version of ZeroShell used for writing this document is Release 1.0.beta11. This document does not describe installing ZeroShell, it is assumed that the user already
Netfilter. GNU/Linux Kernel version 2.4+ Setting up firewall to allow NIS and NFS traffic. January 2008
 Netfilter GNU/Linux Kernel version 2.4+ Setting up firewall to allow NIS and NFS traffic January 2008 Netfilter Features Address Translation S NAT, D NAT IP Accounting and Mangling IP Packet filtering
Netfilter GNU/Linux Kernel version 2.4+ Setting up firewall to allow NIS and NFS traffic January 2008 Netfilter Features Address Translation S NAT, D NAT IP Accounting and Mangling IP Packet filtering
Firewall implementation and testing
 Firewall implementation and testing Patrik Ragnarsson, Niclas Gustafsson E-mail: ragpa737@student.liu.se, nicgu594@student.liu.se Supervisor: David Byers, davby@ida.liu.se Project Report for Information
Firewall implementation and testing Patrik Ragnarsson, Niclas Gustafsson E-mail: ragpa737@student.liu.se, nicgu594@student.liu.se Supervisor: David Byers, davby@ida.liu.se Project Report for Information
+ iptables. packet filtering && firewall
 + iptables packet filtering && firewall + what is iptables? iptables is the userspace command line program used to configure the linux packet filtering ruleset + a.k.a. firewall + iptable flow chart what?
+ iptables packet filtering && firewall + what is iptables? iptables is the userspace command line program used to configure the linux packet filtering ruleset + a.k.a. firewall + iptable flow chart what?
Firewall Piercing. Alon Altman Haifa Linux Club
 Firewall Piercing Alon Altman Haifa Linux Club Introduction Topics of this lecture Basic topics SSH Forwarding PPP over SSH Using non-standard TCP ports Advanced topics TCP over HTTP Tunneling over UDP
Firewall Piercing Alon Altman Haifa Linux Club Introduction Topics of this lecture Basic topics SSH Forwarding PPP over SSH Using non-standard TCP ports Advanced topics TCP over HTTP Tunneling over UDP
Linux Networking Basics
 Linux Networking Basics Naveen.M.K, Protocol Engineering & Technology Unit, Electrical Engineering Department, Indian Institute of Science, Bangalore - 12. Outline Basic linux networking commands Servers
Linux Networking Basics Naveen.M.K, Protocol Engineering & Technology Unit, Electrical Engineering Department, Indian Institute of Science, Bangalore - 12. Outline Basic linux networking commands Servers
BF2CC Daemon Linux Installation Guide
 BF2CC Daemon Linux Installation Guide Battlefield 2 + BF2CC Installation Guide (Linux) 1 Table of contents 1. Introduction... 3 2. Opening ports in your firewall... 4 3. Creating a new user account...
BF2CC Daemon Linux Installation Guide Battlefield 2 + BF2CC Installation Guide (Linux) 1 Table of contents 1. Introduction... 3 2. Opening ports in your firewall... 4 3. Creating a new user account...
Linux Operating System Security
 Linux Operating System Security Kenneth Ingham and Anil Somayaji September 29, 2009 1 Course overview This class is for students who want to learn how to configure systems to be secure, test the security
Linux Operating System Security Kenneth Ingham and Anil Somayaji September 29, 2009 1 Course overview This class is for students who want to learn how to configure systems to be secure, test the security
Lab Objectives & Turn In
 Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
Firewall Lab This lab will apply several theories discussed throughout the networking series. The routing, installing/configuring DHCP, and setting up the services is already done. All that is left for
NRPE Documentation CONTENTS. 1. Introduction... a) Purpose... b) Design Overview... 2. Example Uses... a) Direct Checks... b) Indirect Checks...
 Copyright (c) 1999-2007 Ethan Galstad Last Updated: May 1, 2007 CONTENTS Section 1. Introduction... a) Purpose... b) Design Overview... 2. Example Uses... a) Direct Checks... b) Indirect Checks... 3. Installation...
Copyright (c) 1999-2007 Ethan Galstad Last Updated: May 1, 2007 CONTENTS Section 1. Introduction... a) Purpose... b) Design Overview... 2. Example Uses... a) Direct Checks... b) Indirect Checks... 3. Installation...
How To Set Up An Ip Firewall On Linux With Iptables (For Ubuntu) And Iptable (For Windows)
 Security principles Firewalls and NAT These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) Host vs Network
Security principles Firewalls and NAT These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) Host vs Network
Track 2 Workshop PacNOG 7 American Samoa. Firewalling and NAT
 Track 2 Workshop PacNOG 7 American Samoa Firewalling and NAT Core Concepts Host security vs Network security What is a firewall? What does it do? Where does one use it? At what level does it function?
Track 2 Workshop PacNOG 7 American Samoa Firewalling and NAT Core Concepts Host security vs Network security What is a firewall? What does it do? Where does one use it? At what level does it function?
Defeating Firewalls : Sneaking Into Office Computers From Home
 1 of 6 Defeating Firewalls : Sneaking Into Office Computers From Home Manu Garg Overview Yes, it's possible. Let me first give you an overview of the setup. You work with a company
1 of 6 Defeating Firewalls : Sneaking Into Office Computers From Home Manu Garg Overview Yes, it's possible. Let me first give you an overview of the setup. You work with a company
TECHNICAL NOTE. Technical Note P/N 300-999-649 REV 03. EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.
 TECHNICAL NOTE EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.0 and later Technical Note P/N 300-999-649 REV 03 February 6, 2014 This technical note describes how to configure
TECHNICAL NOTE EMC NetWorker Simplifying firewall port requirements with NSR tunnel Release 8.0 and later Technical Note P/N 300-999-649 REV 03 February 6, 2014 This technical note describes how to configure
Firewall Tutorial. KAIST Dept. of EECS NC Lab.
 Firewall Tutorial KAIST Dept. of EECS NC Lab. Contents What is Firewalls? Why Firewalls? Types of Firewalls Limitations of firewalls and gateways Firewalls in Linux What is Firewalls? firewall isolates
Firewall Tutorial KAIST Dept. of EECS NC Lab. Contents What is Firewalls? Why Firewalls? Types of Firewalls Limitations of firewalls and gateways Firewalls in Linux What is Firewalls? firewall isolates
ReadyNAS Remote White Paper. NETGEAR May 2010
 ReadyNAS Remote White Paper NETGEAR May 2010 Table of Contents Overview... 3 Architecture... 3 Security... 4 Remote Firewall... 5 Performance... 5 Overview ReadyNAS Remote is a software application that
ReadyNAS Remote White Paper NETGEAR May 2010 Table of Contents Overview... 3 Architecture... 3 Security... 4 Remote Firewall... 5 Performance... 5 Overview ReadyNAS Remote is a software application that
GL254 - RED HAT ENTERPRISE LINUX SYSTEMS ADMINISTRATION III
 QWERTYUIOP{ GL254 - RED HAT ENTERPRISE LINUX SYSTEMS ADMINISTRATION III This GL254 course is designed to follow an identical set of topics as the Red Hat RH254, RH255 RHCE exam prep courses with the added
QWERTYUIOP{ GL254 - RED HAT ENTERPRISE LINUX SYSTEMS ADMINISTRATION III This GL254 course is designed to follow an identical set of topics as the Red Hat RH254, RH255 RHCE exam prep courses with the added
Setting up VNC, SAMBA and SSH on Ubuntu Linux PCs Getting More Benefit out of Your Local Area Network
 What Are These Programs? VNC (Virtual Network Computing) is a networking application that allows one computer's screen to be viewed by, and optionally controlled by one or more other computers through
What Are These Programs? VNC (Virtual Network Computing) is a networking application that allows one computer's screen to be viewed by, and optionally controlled by one or more other computers through
SSH, SCP, SFTP, Denyhosts. Süha TUNA Res. Assist.
 SSH, SCP, SFTP, Denyhosts Süha TUNA Res. Assist. Outline 1. What is Secure Shell? 2. ssh (Install and Configuration) 3. scp 4. sftp 5. X11 Forwarding 6. Generating Key Pairs 7. Disabling root Access 8.
SSH, SCP, SFTP, Denyhosts Süha TUNA Res. Assist. Outline 1. What is Secure Shell? 2. ssh (Install and Configuration) 3. scp 4. sftp 5. X11 Forwarding 6. Generating Key Pairs 7. Disabling root Access 8.
Guideline for setting up a functional VPN
 Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Guideline for setting up a functional VPN Why do I want a VPN? VPN by definition creates a private, trusted network across an untrusted medium. It allows you to connect offices and people from around the
Getting Started with RES Automation Manager Agent for Linux
 Getting Started with RES Automation Manager Agent for Linux Contents Chapter 1: Introduction 1 Chapter 2: Prerequisites and General Guidelines 2 Chapter 3: Installation 3 3.1 Manual Installation... 3 3.2
Getting Started with RES Automation Manager Agent for Linux Contents Chapter 1: Introduction 1 Chapter 2: Prerequisites and General Guidelines 2 Chapter 3: Installation 3 3.1 Manual Installation... 3 3.2
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Firewalling and Network Security I -Linux. Jeff Muday Academic Computing Specialist Wake Forest University
 Firewalling and Network Security I -Linux Jeff Muday Academic Computing Specialist Wake Forest University Objectives: Firewalling and Network Security After completing this module you should be able to
Firewalling and Network Security I -Linux Jeff Muday Academic Computing Specialist Wake Forest University Objectives: Firewalling and Network Security After completing this module you should be able to
Testing New Applications In The DMZ Using VMware ESX. Ivan Dell Era Software Engineer IBM
 Testing New Applications In The DMZ Using VMware ESX Ivan Dell Era Software Engineer IBM Agenda Problem definition Traditional solution The solution with VMware VI Remote control through the firewall Problem
Testing New Applications In The DMZ Using VMware ESX Ivan Dell Era Software Engineer IBM Agenda Problem definition Traditional solution The solution with VMware VI Remote control through the firewall Problem
Chapter 7. Firewalls http://www.redhat.com/docs/manuals/enterprise/rhel-4-manual/security-guide/ch-fw.html
 Red Hat Docs > Manuals > Red Hat Enterprise Linux Manuals > Red Hat Enterprise Linux 4: Security Guide Chapter 7. Firewalls http://www.redhat.com/docs/manuals/enterprise/rhel-4-manual/security-guide/ch-fw.html
Red Hat Docs > Manuals > Red Hat Enterprise Linux Manuals > Red Hat Enterprise Linux 4: Security Guide Chapter 7. Firewalls http://www.redhat.com/docs/manuals/enterprise/rhel-4-manual/security-guide/ch-fw.html
NATIONAL POPULATION REGISTER (NPR)
 NATIONAL POPULATION REGISTER (NPR) Project Name: NPR Version No: 1.0.0 Release Date: Group Name: NPR-ECIL Version Date: LINUX SERVER INSTALLATION AND CONFIGURATION FOR JAVA BASED NPR DATAENTRY SOFTWARE
NATIONAL POPULATION REGISTER (NPR) Project Name: NPR Version No: 1.0.0 Release Date: Group Name: NPR-ECIL Version Date: LINUX SERVER INSTALLATION AND CONFIGURATION FOR JAVA BASED NPR DATAENTRY SOFTWARE
CS 5410 - Computer and Network Security: Firewalls
 CS 5410 - Computer and Network Security: Firewalls Professor Kevin Butler Fall 2015 Firewalls A firewall... is a physical barrier inside a building or vehicle, designed to limit the spread of fire, heat
CS 5410 - Computer and Network Security: Firewalls Professor Kevin Butler Fall 2015 Firewalls A firewall... is a physical barrier inside a building or vehicle, designed to limit the spread of fire, heat
IMF Tune Quarantine & Reporting Running SQL behind a Firewall. WinDeveloper Software Ltd.
 IMF Tune Quarantine & Reporting Running SQL behind a Firewall WinDeveloper Software Ltd. 1 Basic Setup Quarantine & Reporting Web Interface must be installed on the same Windows Domain as the SQL Server
IMF Tune Quarantine & Reporting Running SQL behind a Firewall WinDeveloper Software Ltd. 1 Basic Setup Quarantine & Reporting Web Interface must be installed on the same Windows Domain as the SQL Server
File Transfer Examples. Running commands on other computers and transferring files between computers
 Running commands on other computers and transferring files between computers 1 1 Remote Login Login to remote computer and run programs on that computer Once logged in to remote computer, everything you
Running commands on other computers and transferring files between computers 1 1 Remote Login Login to remote computer and run programs on that computer Once logged in to remote computer, everything you
FreeBSD OpenVPN Server/Routed - Secure Computing Wiki
 1 z 5 01.10.2012 08:16 FreeBSD OpenVPN Server/Routed From Secure Computing Wiki OpenVPN Topics GENERAL: Routing RIP Routing Bridging FAQ Firewall VPN Chaining Troubleshooting Donations IRC meetings Developer
1 z 5 01.10.2012 08:16 FreeBSD OpenVPN Server/Routed From Secure Computing Wiki OpenVPN Topics GENERAL: Routing RIP Routing Bridging FAQ Firewall VPN Chaining Troubleshooting Donations IRC meetings Developer
SSL Tunnels. Introduction
 SSL Tunnels Introduction As you probably know, SSL protects data communications by encrypting all data exchanged between a client and a server using cryptographic algorithms. This makes it very difficult,
SSL Tunnels Introduction As you probably know, SSL protects data communications by encrypting all data exchanged between a client and a server using cryptographic algorithms. This makes it very difficult,
Easy Setup Guide 1&1 CLOUD SERVER. Creating Backups. for Linux
 Easy Setup Guide 1&1 CLOUD SERVER Creating Backups for Linux Legal notice 1&1 Internet Inc. 701 Lee Road, Suite 300 Chesterbrook, PA 19087 USA www.1and1.com info@1and1.com August 2015 Copyright 2015 1&1
Easy Setup Guide 1&1 CLOUD SERVER Creating Backups for Linux Legal notice 1&1 Internet Inc. 701 Lee Road, Suite 300 Chesterbrook, PA 19087 USA www.1and1.com info@1and1.com August 2015 Copyright 2015 1&1
Project 2: Firewall Design (Phase I)
 Project 2: Firewall Design (Phase I) CS 161 - Joseph/Tygar November 12, 2006 1 Edits If we need to make clarifications or corrections to this document after distributing it, we will post a new version
Project 2: Firewall Design (Phase I) CS 161 - Joseph/Tygar November 12, 2006 1 Edits If we need to make clarifications or corrections to this document after distributing it, we will post a new version
Linux NFS HOWTO. Tavis Barr. Nicolai Langfeldt. Seth Vidal. Tom McNeal. tavis dot barr at liu dot edu. janl at linpro dot no
 Tavis Barr tavis dot barr at liu dot edu Nicolai Langfeldt janl at linpro dot no Seth Vidal skvidal at phy dot duke dot edu Tom McNeal trmcneal at attbi dot com 2002 08 25 Revision History Revision v3.1
Tavis Barr tavis dot barr at liu dot edu Nicolai Langfeldt janl at linpro dot no Seth Vidal skvidal at phy dot duke dot edu Tom McNeal trmcneal at attbi dot com 2002 08 25 Revision History Revision v3.1
Firewalls with IPTables. Jason Healy, Director of Networks and Systems
 Firewalls with IPTables Jason Healy, Director of Networks and Systems Last Updated Mar 18, 2008 2 Contents 1 Host-based Firewalls with IPTables 5 1.1 Introduction.............................. 5 1.2 Concepts...............................
Firewalls with IPTables Jason Healy, Director of Networks and Systems Last Updated Mar 18, 2008 2 Contents 1 Host-based Firewalls with IPTables 5 1.1 Introduction.............................. 5 1.2 Concepts...............................
CS 5410 - Computer and Network Security: Firewalls
 CS 5410 - Computer and Network Security: Firewalls Professor Patrick Traynor Spring 2015 Firewalls A firewall... is a physical barrier inside a building or vehicle, designed to limit the spread of fire,
CS 5410 - Computer and Network Security: Firewalls Professor Patrick Traynor Spring 2015 Firewalls A firewall... is a physical barrier inside a building or vehicle, designed to limit the spread of fire,
Definition of firewall
 Internet Firewalls Definitions: firewall, policy, router, gateway, proxy NAT: Network Address Translation Source NAT, Destination NAT, Port forwarding NAT firewall compromise via UPnP/IGD Packet filtering
Internet Firewalls Definitions: firewall, policy, router, gateway, proxy NAT: Network Address Translation Source NAT, Destination NAT, Port forwarding NAT firewall compromise via UPnP/IGD Packet filtering
for NewTech United, London
 JANUARY 02, 2015 SECURITY REPORT MADE 02.01.2015 BETWEEN 18:00 22:00 by John Doe Security Specialist at Keios Solutions for NewTech United, London WWW.KEIOS.EU CLUSTER INFORMATION Number of servers: 1
JANUARY 02, 2015 SECURITY REPORT MADE 02.01.2015 BETWEEN 18:00 22:00 by John Doe Security Specialist at Keios Solutions for NewTech United, London WWW.KEIOS.EU CLUSTER INFORMATION Number of servers: 1
Firewalls. Firewalls. Idea: separate local network from the Internet 2/24/15. Intranet DMZ. Trusted hosts and networks. Firewall.
 Firewalls 1 Firewalls Idea: separate local network from the Internet Trusted hosts and networks Firewall Intranet Router DMZ Demilitarized Zone: publicly accessible servers and networks 2 1 Castle and
Firewalls 1 Firewalls Idea: separate local network from the Internet Trusted hosts and networks Firewall Intranet Router DMZ Demilitarized Zone: publicly accessible servers and networks 2 1 Castle and
AlienVault Unified Security Management (USM) 4.x-5.x. Deploying HIDS Agents to Linux Hosts
 AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
AlienVault Unified Security Management (USM) 4.x-5.x Deploying HIDS Agents to Linux Hosts USM 4.x-5.x Deploying HIDS Agents to Linux Hosts, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. AlienVault,
CS 640 Introduction to Computer Networks. Network security (continued) Key Distribution a first step. Lecture24
 Introduction to Computer Networks Lecture24 Network security (continued) Key distribution Secure Shell Overview Authentication Practical issues Firewalls Denial of Service Attacks Definition Examples Key
Introduction to Computer Networks Lecture24 Network security (continued) Key distribution Secure Shell Overview Authentication Practical issues Firewalls Denial of Service Attacks Definition Examples Key
HP Device Manager 4.6
 Technical white paper HP Device Manager 4.6 Installation and Update Guide Table of contents Overview... 3 HPDM Server preparation... 3 FTP server configuration... 3 Windows Firewall settings... 3 Firewall
Technical white paper HP Device Manager 4.6 Installation and Update Guide Table of contents Overview... 3 HPDM Server preparation... 3 FTP server configuration... 3 Windows Firewall settings... 3 Firewall
How to Secure RHEL 6.2 Part 2
 How to Secure RHEL 6.2 Part 2 Motivation This paper is part of a multi-part series on securing Redhat Enterprise Linux 6.2. This paper focuses on implementing IPtables as a host based firewall. If you
How to Secure RHEL 6.2 Part 2 Motivation This paper is part of a multi-part series on securing Redhat Enterprise Linux 6.2. This paper focuses on implementing IPtables as a host based firewall. If you
How to install PowerChute Network Shutdown on VMware ESXi 3.5, 4.0 and 4.1
 How to install PowerChute Network Shutdown on VMware ESXi 3.5, 4.0 and 4.1 Basic knowledge of Linux commands and Linux administration is needed before user should attempt the installation of the software.
How to install PowerChute Network Shutdown on VMware ESXi 3.5, 4.0 and 4.1 Basic knowledge of Linux commands and Linux administration is needed before user should attempt the installation of the software.
Pen Test Tips 2. Shell vs. Terminal
 Pen Test Tips 2 Shell vs. Terminal Once you have successfully exploited a target machine you may be faced with a common dilemma that many penetration testers have, do I have shell access or terminal access?
Pen Test Tips 2 Shell vs. Terminal Once you have successfully exploited a target machine you may be faced with a common dilemma that many penetration testers have, do I have shell access or terminal access?
Administrasi dan Manajemen Jaringan 2. File Transfer Protocol (FTP)
 Administrasi dan Manajemen Jaringan 2. File Transfer Protocol (FTP) M. Udin Harun Al Rasyid, Ph.D http://lecturer.eepis-its.edu/~udinharun udinharun@eepis-its.edu Lab Jaringan Komputer (C-307) Table of
Administrasi dan Manajemen Jaringan 2. File Transfer Protocol (FTP) M. Udin Harun Al Rasyid, Ph.D http://lecturer.eepis-its.edu/~udinharun udinharun@eepis-its.edu Lab Jaringan Komputer (C-307) Table of
Red Hat Linux Networking
 The information presented should act as a guide to Red Hat Linux networking. It is intended to be accompanied with training and self study. To access most of these items you will need to have root access,
The information presented should act as a guide to Red Hat Linux networking. It is intended to be accompanied with training and self study. To access most of these items you will need to have root access,
Linux Cluster Security Neil Gorsuch NCSA, University of Illinois, Urbana, Illinois.
 Linux Cluster Security Neil Gorsuch NCSA, University of Illinois, Urbana, Illinois. Abstract Modern Linux clusters are under increasing security threats. This paper will discuss various aspects of cluster
Linux Cluster Security Neil Gorsuch NCSA, University of Illinois, Urbana, Illinois. Abstract Modern Linux clusters are under increasing security threats. This paper will discuss various aspects of cluster
Assignment 3 Firewalls
 LEIC/MEIC - IST Alameda ONLY For ALAMEDA LAB equipment Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
LEIC/MEIC - IST Alameda ONLY For ALAMEDA LAB equipment Network and Computer Security 2013/2014 Assignment 3 Firewalls Goal: Configure a firewall using iptables and fwbuilder. 1 Introduction This lab assignment
How to protect your home/office network?
 How to protect your home/office network? Using IPTables and Building a Firewall - Background, Motivation and Concepts Adir Abraham adir@vipe.technion.ac.il Do you think that you are alone, connected from
How to protect your home/office network? Using IPTables and Building a Firewall - Background, Motivation and Concepts Adir Abraham adir@vipe.technion.ac.il Do you think that you are alone, connected from
Configuring Secure Linux Hosts
 A Perspective on Practical Security 2005 by Landon Curt Noll BOSTON NEW YORK SAN FRANCISCO SACRAMENTO CHARLOTTE WASHINGTON DC Introduction Congratulations! You have just installed Linux; an Open Source
A Perspective on Practical Security 2005 by Landon Curt Noll BOSTON NEW YORK SAN FRANCISCO SACRAMENTO CHARLOTTE WASHINGTON DC Introduction Congratulations! You have just installed Linux; an Open Source
Linux Firewalls (Ubuntu IPTables) II
 Linux Firewalls (Ubuntu IPTables) II Here we will complete the previous firewall lab by making a bridge on the Ubuntu machine, to make the Ubuntu machine completely control the Internet connection on the
Linux Firewalls (Ubuntu IPTables) II Here we will complete the previous firewall lab by making a bridge on the Ubuntu machine, to make the Ubuntu machine completely control the Internet connection on the
Linux firewall. Need of firewall Single connection between network Allows restricted traffic between networks Denies un authorized users
 Linux firewall Need of firewall Single connection between network Allows restricted traffic between networks Denies un authorized users Linux firewall Linux is a open source operating system and any firewall
Linux firewall Need of firewall Single connection between network Allows restricted traffic between networks Denies un authorized users Linux firewall Linux is a open source operating system and any firewall
WHM Administrator s Guide
 Fasthosts Customer Support WHM Administrator s Guide This manual covers everything you need to know in order to get started with WHM and perform day to day administrative tasks. Contents Introduction...
Fasthosts Customer Support WHM Administrator s Guide This manual covers everything you need to know in order to get started with WHM and perform day to day administrative tasks. Contents Introduction...
CSC574 - Computer and Network Security Module: Firewalls
 CSC574 - Computer and Network Security Module: Firewalls Prof. William Enck Spring 2013 1 Firewalls A firewall... is a physical barrier inside a building or vehicle, designed to limit the spread of fire,
CSC574 - Computer and Network Security Module: Firewalls Prof. William Enck Spring 2013 1 Firewalls A firewall... is a physical barrier inside a building or vehicle, designed to limit the spread of fire,
COURCE TITLE DURATION LPI-202 Advanced Linux Professional Institute 40 H.
 COURCE TITLE DURATION LPI-202 Advanced Linux Professional Institute 40 H. IMPLEMENTING A WEB SERVER Apache Architecture Installing PHP Apache Configuration Files httpd.conf Server Settings httpd.conf Main
COURCE TITLE DURATION LPI-202 Advanced Linux Professional Institute 40 H. IMPLEMENTING A WEB SERVER Apache Architecture Installing PHP Apache Configuration Files httpd.conf Server Settings httpd.conf Main
Distributed File System
 Petru Maior University, Târgu-Mureș Science Department Information Technolgy Master Course Distributed File System Students: Bardosi Florin Cifor Crina Danciu Ioana Hintea Dan Alexandru Table of Contents
Petru Maior University, Târgu-Mureș Science Department Information Technolgy Master Course Distributed File System Students: Bardosi Florin Cifor Crina Danciu Ioana Hintea Dan Alexandru Table of Contents
Cisco Secure PIX Firewall with Two Routers Configuration Example
 Cisco Secure PIX Firewall with Two Routers Configuration Example Document ID: 15244 Interactive: This document offers customized analysis of your Cisco device. Contents Introduction Prerequisites Requirements
Cisco Secure PIX Firewall with Two Routers Configuration Example Document ID: 15244 Interactive: This document offers customized analysis of your Cisco device. Contents Introduction Prerequisites Requirements
Building a Home Gateway/Firewall with Linux (aka Firewalling and NAT with iptables )
 Building a Home Gateway/Firewall with Linux (aka Firewalling and NAT with iptables ) Michael Porkchop Kaegler mkaegler@nic.com http://www.nic.com/~mkaegler/ Hardware Requirements Any machine capable of
Building a Home Gateway/Firewall with Linux (aka Firewalling and NAT with iptables ) Michael Porkchop Kaegler mkaegler@nic.com http://www.nic.com/~mkaegler/ Hardware Requirements Any machine capable of
Network Monitoring & Management Log Management
 Network Monitoring & Management Log Management These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) Syslog
Network Monitoring & Management Log Management These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) Syslog
Load Balancing/High Availability Configuration for neoninsight Server
 Load Balancing/High Availability Configuration for neoninsight Server Introduction: This document provides details on the configuration and the components used for a two node load balancing system with
Load Balancing/High Availability Configuration for neoninsight Server Introduction: This document provides details on the configuration and the components used for a two node load balancing system with
6WRUP:DWFK. Policies for Dedicated IIS Web Servers Group. V2.1 policy module to restrict ALL network access
 OKENA 71 Second Ave., 3 rd Floor Waltham, MA 02451 Phone 781 209 3200 Fax 781 209 3199 6WRUP:DWFK Policies for Dedicated IIS Web Servers Group The policies shipped with StormWatch address both application-specific
OKENA 71 Second Ave., 3 rd Floor Waltham, MA 02451 Phone 781 209 3200 Fax 781 209 3199 6WRUP:DWFK Policies for Dedicated IIS Web Servers Group The policies shipped with StormWatch address both application-specific
IP Address: the per-network unique identifier used to find you on a network
 Linux Networking What is a network? A collection of devices connected together Can use IPv4, IPv6, other schemes Different devices on a network can talk to each other May be walls to separate different
Linux Networking What is a network? A collection of devices connected together Can use IPv4, IPv6, other schemes Different devices on a network can talk to each other May be walls to separate different
Linux Routers and Community Networks
 Summer Course at Mekelle Institute of Technology. July, 2015. Linux Routers and Community Networks Llorenç Cerdà-Alabern http://personals.ac.upc.edu/llorenc llorenc@ac.upc.edu Universitat Politènica de
Summer Course at Mekelle Institute of Technology. July, 2015. Linux Routers and Community Networks Llorenç Cerdà-Alabern http://personals.ac.upc.edu/llorenc llorenc@ac.upc.edu Universitat Politènica de
Password Reset PRO INSTALLATION GUIDE
 Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
Password Reset PRO INSTALLATION GUIDE This guide covers the new features and settings available in Password Reset PRO. Please read this guide completely to ensure a trouble-free installation. March 2009
Main functions of Linux Netfilter
 Main functions of Linux Netfilter Filter Nat Packet filtering (rejecting, dropping or accepting packets) Network Address Translation including DNAT, SNAT and Masquerading Mangle General packet header modification
Main functions of Linux Netfilter Filter Nat Packet filtering (rejecting, dropping or accepting packets) Network Address Translation including DNAT, SNAT and Masquerading Mangle General packet header modification
Load Balancing Trend Micro InterScan Web Gateway
 Load Balancing Trend Micro InterScan Web Gateway Deployment Guide rev. 1.1.7 Copyright 2002 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...
Load Balancing Trend Micro InterScan Web Gateway Deployment Guide rev. 1.1.7 Copyright 2002 2015 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 3 Loadbalancer.org Appliances Supported...
Using Red Hat Enterprise Linux with Georgia Tech's RHN Satellite Server Installing Red Hat Enterprise Linux
 Using Red Hat Enterprise Linux with Georgia Tech's RHN Satellite Server Installing Red Hat Enterprise Linux NOTE: If you need more information regarding the installation process for other distributions
Using Red Hat Enterprise Linux with Georgia Tech's RHN Satellite Server Installing Red Hat Enterprise Linux NOTE: If you need more information regarding the installation process for other distributions
ipchains and iptables for Firewalling and Routing
 ipchains and iptables for Firewalling and Routing Jeff Muday Instructional Technology Consultant Department of Biology, Wake Forest University The ipchains utility Used to filter packets at the Kernel
ipchains and iptables for Firewalling and Routing Jeff Muday Instructional Technology Consultant Department of Biology, Wake Forest University The ipchains utility Used to filter packets at the Kernel
Network Monitoring & Management Log Management
 Network Monitoring & Management Log Management Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
Network Monitoring & Management Log Management Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/)
LINUX SECURITY COOKBOOK. DanieIJ. Barren, Richard E Silverman, and Robert G. Byrnes
 LINUX SECURITY COOKBOOK DanieIJ. Barren, Richard E Silverman, and Robert G. Byrnes ORELLY Beijing " Cambridge " Farnham " Koln " Paris " Sebastopol " Taipei - Tokyo Table of Contents Preface............,....................................................A
LINUX SECURITY COOKBOOK DanieIJ. Barren, Richard E Silverman, and Robert G. Byrnes ORELLY Beijing " Cambridge " Farnham " Koln " Paris " Sebastopol " Taipei - Tokyo Table of Contents Preface............,....................................................A
Linux Networking: IP Packet Filter Firewalling
 Linux Networking: IP Packet Filter Firewalling David Morgan Firewall types Packet filter Proxy server 1 Linux Netfilter Firewalling Packet filter, not proxy Centerpiece command: iptables Starting point:
Linux Networking: IP Packet Filter Firewalling David Morgan Firewall types Packet filter Proxy server 1 Linux Netfilter Firewalling Packet filter, not proxy Centerpiece command: iptables Starting point:
How to Backup XenServer VM with VirtualIQ
 How to Backup XenServer VM with VirtualIQ 1. Using Live Backup of VM option: Live Backup: This option can be used, if user does not want to power off the VM during the backup operation. This approach takes
How to Backup XenServer VM with VirtualIQ 1. Using Live Backup of VM option: Live Backup: This option can be used, if user does not want to power off the VM during the backup operation. This approach takes
How to install and run an OpenVPN client on your Windows-based PC
 How to install and run an OpenVPN client on your Windows-based PC The DIL/NetPC ADNP/9200 is also available with a preinstalled OpenVPN server. This allows secure VPN connections between a PC as an OpenVPN
How to install and run an OpenVPN client on your Windows-based PC The DIL/NetPC ADNP/9200 is also available with a preinstalled OpenVPN server. This allows secure VPN connections between a PC as an OpenVPN
Load Balancing VMware Horizon View. Deployment Guide
 Load Balancing VMware Horizon View Deployment Guide v1.1.0 Copyright 2014 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Appliances Supported... 4 VMware Horizon View Versions Supported...4
Load Balancing VMware Horizon View Deployment Guide v1.1.0 Copyright 2014 Loadbalancer.org, Inc. 1 Table of Contents About this Guide... 4 Appliances Supported... 4 VMware Horizon View Versions Supported...4
Linux: 20 Iptables Examples For New SysAdmins
 Copyrighted material Linux: 20 Iptables Examples For New SysAdmins Posted By nixcraft On December 13, 2011 @ 8:29 am [ 64 Comments ] L inux comes with a host based firewall called
Copyrighted material Linux: 20 Iptables Examples For New SysAdmins Posted By nixcraft On December 13, 2011 @ 8:29 am [ 64 Comments ] L inux comes with a host based firewall called
CUIT UNIX Standard Operating Environment and Security Best Practices
 Objective and Scope Effective Date: August 2008 This CUIT UNIX Standard Operating Environment (SOE) document defines the agreed system hardening requirements as well as security best practices for CUIT
Objective and Scope Effective Date: August 2008 This CUIT UNIX Standard Operating Environment (SOE) document defines the agreed system hardening requirements as well as security best practices for CUIT
Directory and File Transfer Services. Chapter 7
 Directory and File Transfer Services Chapter 7 Learning Objectives Explain benefits offered by centralized enterprise directory services such as LDAP over traditional authentication systems Identify major
Directory and File Transfer Services Chapter 7 Learning Objectives Explain benefits offered by centralized enterprise directory services such as LDAP over traditional authentication systems Identify major
6WRUP:DWFK. Policies for Dedicated SQL Servers Group
 OKENA 71 Second Ave., 3 rd Floor Waltham, MA 02451 Phone 781 209 3200 Fax 781 209 3199 6WRUP:DWFK Policies for Dedicated SQL Servers Group The sample policies shipped with StormWatch address both application-specific
OKENA 71 Second Ave., 3 rd Floor Waltham, MA 02451 Phone 781 209 3200 Fax 781 209 3199 6WRUP:DWFK Policies for Dedicated SQL Servers Group The sample policies shipped with StormWatch address both application-specific
Installing and Configuring Websense Content Gateway
 Installing and Configuring Websense Content Gateway Websense Support Webinar - September 2009 web security data security email security Support Webinars 2009 Websense, Inc. All rights reserved. Webinar
Installing and Configuring Websense Content Gateway Websense Support Webinar - September 2009 web security data security email security Support Webinars 2009 Websense, Inc. All rights reserved. Webinar
Ciphermail Gateway Separate Front-end and Back-end Configuration Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway Separate Front-end and Back-end Configuration Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction
CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway Separate Front-end and Back-end Configuration Guide June 19, 2014, Rev: 8975 Copyright 2010-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction
LOCKSS on LINUX. CentOS6 Installation Manual 08/22/2013
 LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
LOCKSS on LINUX CentOS6 Installation Manual 08/22/2013 1 Table of Contents Overview... 3 LOCKSS Hardware... 5 Installation Checklist... 6 BIOS Settings... 9 Installation... 10 Firewall Configuration...
Cloud.com CloudStack Community Edition 2.1 Beta Installation Guide
 Cloud.com CloudStack Community Edition 2.1 Beta Installation Guide July 2010 1 Specifications are subject to change without notice. The Cloud.com logo, Cloud.com, Hypervisor Attached Storage, HAS, Hypervisor
Cloud.com CloudStack Community Edition 2.1 Beta Installation Guide July 2010 1 Specifications are subject to change without notice. The Cloud.com logo, Cloud.com, Hypervisor Attached Storage, HAS, Hypervisor
Network Security and Firewall 1
 Department/program: Networking Course Code: CPT 224 Contact Hours: 96 Subject/Course WEB Access & Network Security: Theoretical: 2 Hours/week Year Two Semester: Two Prerequisite: NET304 Practical: 4 Hours/week
Department/program: Networking Course Code: CPT 224 Contact Hours: 96 Subject/Course WEB Access & Network Security: Theoretical: 2 Hours/week Year Two Semester: Two Prerequisite: NET304 Practical: 4 Hours/week
Isilon OneFS. Version 7.2. OneFS Migration Tools Guide
 Isilon OneFS Version 7.2 OneFS Migration Tools Guide Copyright 2014 EMC Corporation. All rights reserved. Published in USA. Published November, 2014 EMC believes the information in this publication is
Isilon OneFS Version 7.2 OneFS Migration Tools Guide Copyright 2014 EMC Corporation. All rights reserved. Published in USA. Published November, 2014 EMC believes the information in this publication is
UNICORE UFTPD server UNICORE UFTPD SERVER. UNICORE Team
 UNICORE UFTPD server UNICORE UFTPD SERVER UNICORE Team Document Version: 1.0.0 Component Version: 2.3.2 Date: 14 09 2015 UNICORE UFTPD server Contents 1 UNICORE UFTP 1 1.1 UFTP features...................................
UNICORE UFTPD server UNICORE UFTPD SERVER UNICORE Team Document Version: 1.0.0 Component Version: 2.3.2 Date: 14 09 2015 UNICORE UFTPD server Contents 1 UNICORE UFTP 1 1.1 UFTP features...................................
Troubleshooting This document outlines some of the potential issues which you may encouter while administering an atech Telecoms installation.
 Troubleshooting This document outlines some of the potential issues which you may encouter while administering an atech Telecoms installation. Please consult this document before contacting atech Telecoms
Troubleshooting This document outlines some of the potential issues which you may encouter while administering an atech Telecoms installation. Please consult this document before contacting atech Telecoms
How To Install Storegrid Server On Linux On A Microsoft Ubuntu 7.5 (Amd64) Or Ubuntu (Amd86) (Amd77) (Orchestra) (For Ubuntu) (Permanent) (Powerpoint
 StoreGrid Linux Server Installation Guide Before installing StoreGrid as Backup Server (or) Replication Server in your machine, you should install MySQL Server in your machine (or) in any other dedicated
StoreGrid Linux Server Installation Guide Before installing StoreGrid as Backup Server (or) Replication Server in your machine, you should install MySQL Server in your machine (or) in any other dedicated
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Printing Date: August 15, 2007 This guide provides detailed description on configuration of the local network which
TELE 301 Network Management. Lecture 17: File Transfer & Web Caching
 TELE 301 Network Management Lecture 17: File Transfer & Web Caching Haibo Zhang Computer Science, University of Otago TELE301 Lecture 17: File Transfer & Web Caching 1 Today s Focus FTP & Web Caching!
TELE 301 Network Management Lecture 17: File Transfer & Web Caching Haibo Zhang Computer Science, University of Otago TELE301 Lecture 17: File Transfer & Web Caching 1 Today s Focus FTP & Web Caching!
Asterisk SIP Trunk Settings - Vestalink
 Asterisk SIP Trunk Settings - Vestalink Vestalink is a new SIP trunk provider that has sprung up as a replacement for Google Voice trunking within Asterisk servers. They offer a very attractive pricing
Asterisk SIP Trunk Settings - Vestalink Vestalink is a new SIP trunk provider that has sprung up as a replacement for Google Voice trunking within Asterisk servers. They offer a very attractive pricing
Introduction to Operating Systems
 Introduction to Operating Systems It is important that you familiarize yourself with Windows and Linux in preparation for this course. The exercises in this book assume a basic knowledge of both of these
Introduction to Operating Systems It is important that you familiarize yourself with Windows and Linux in preparation for this course. The exercises in this book assume a basic knowledge of both of these
Back Up Linux And Windows Systems With BackupPC
 By Falko Timme Published: 2007-01-25 14:33 Version 1.0 Author: Falko Timme Last edited 01/19/2007 This tutorial shows how you can back up Linux and Windows systems with BackupPC.
By Falko Timme Published: 2007-01-25 14:33 Version 1.0 Author: Falko Timme Last edited 01/19/2007 This tutorial shows how you can back up Linux and Windows systems with BackupPC.
Make a folder named Lab3. We will be using Unix redirection commands to create several output files in that folder.
 CMSC 355 Lab 3 : Penetration Testing Tools Due: September 31, 2010 In the previous lab, we used some basic system administration tools to figure out which programs where running on a system and which files
CMSC 355 Lab 3 : Penetration Testing Tools Due: September 31, 2010 In the previous lab, we used some basic system administration tools to figure out which programs where running on a system and which files
Vertigo's Running Dedicated Server HOWTO (v1.2)
 Vertigo's Running Dedicated Server HOWTO (v1.2) 1. Overview This document will describe the configuration details about running a megamek dedicated server in a MegaMekNET campaign setting. This document
Vertigo's Running Dedicated Server HOWTO (v1.2) 1. Overview This document will describe the configuration details about running a megamek dedicated server in a MegaMekNET campaign setting. This document
Table of Contents. Cisco Cisco VPN Client FAQ
 Table of Contents Cisco VPN Client FAQ...1 Questions...1 Introduction...2 Q. Why does the VPN Client disconnect after 30 minutes? Can I extend this time period?...2 Q. I upgraded to Mac OS X 10.3 (known
Table of Contents Cisco VPN Client FAQ...1 Questions...1 Introduction...2 Q. Why does the VPN Client disconnect after 30 minutes? Can I extend this time period?...2 Q. I upgraded to Mac OS X 10.3 (known
