Facebook Smart Card FB _1800
|
|
|
- Donna Magdalen Sutton
- 8 years ago
- Views:
Transcription
1 Facebook Smart Card FB _1800 Social Networks - Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any information about your activities, personal life, or professional life that you post and share. Ensure that your family takes similar precautions with their accounts; their privacy and sharing settings can expose your personal data. Avoid posting or tagging images of you or your family that clearly show your face. Select pictures taken at a distance, at an angle, or otherwise concealed. Never post Smartphone photos and don t use your face as a profile photo, instead, use cartoons or avatars. Use secure browser settings when possible and monitor your browsing history to ensure that you recognize all access points. Minimizing your Facebook Profile Click to access and edit Profile Go to Downward Arrow > Privacy Settings Access Facebook Privacy Setting Here Facebook has hundreds of privacy and sharing options. To control how your personal information is shared, you should use the settings shown below (such as Only Me, ) for (1) Privacy, (2) Connecting, (3) Tags, (4) Apps/Websites, (5) Info Access through Friends, and (6) Past Posts Limit Use of Apps ALL Boxes 5 Disable Personalization Disable Public Search 6 Limit Old Posts to
2 Profile Settings Facebook Smart Card FB _1800 Do not login to or link third-party sites (e.g. twitter, bing) using your Facebook account. Facebook Connect shares your information, and your friends information, with third party sites that may aggregate and misuse personal information. Also, use as few apps as possible. Apps such as Farmville access and share your personal data. Apply and save the Profile settings shown below to ensure that your information is visible to only people of your choosing. - Only Me Click on Info tab to start editing Only Me Only Me Only Me Show Birthday Deactivating / Deleting Your Facebook Account Useful Links A Parent s Guide to Internet Safety Wired Kids Microsoft Safety & Security OnGuard Online To deactivate your Facebook account, go to Account Settings and select Security. To reactivate your account log in to Facebook with your address and password. To delete your Facebook account, go to Help Center from the account menu. Type Delete into the search box. Select How do I permanently delete my account then scroll down to submit your request here. Verify that you want to delete your account. Click Submit. FB will remove your data after 14 days post security check
3 Google+ Smart Card G _2000 Social Networks - Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any information about your activities, personal life, or professional life that you post and share. Ensure that your family takes similar precautions with their accounts; their privacy and sharing settings can expose your personal data. Avoid posting or tagging images of you or your family that clearly show your face. Select pictures taken at a distance, at an angle, or otherwise concealed. Never post Smartphone photos and don t use your face as a profile photo, instead, use cartoons or avatars. Use secure browser settings when possible and monitor your browsing history to ensure that you recognize all access points. Managing Your Google+ Profile Google+ provides privacy and sharing options using Circles. Circles are groups that users create for different types of connections, such as family, friends, or colleagues. Content is shared only with circles you select. Google+ requires that users provide real names - no pseudonyms. Click to access and edit Profile Profile Settings Apply and save the Profile settings shown below to ensure that your information is visible to only people of your choosing. This box is PUBLIC. Do not fill out additional information Select Edit Profile to make changes both Name & Profile Picture are PUBLIC DO NOT add links to other online presences, such as a webpage, Facebook, Twitter, or LinkedIn Your Circles To share information on this page with specific people, select Custom then choose appropriate Circles top button Only You Your Circles
4 Google+ Smart Card G _2000 Account Settings & Minimizing Your Activities Apply the Account settings shown with arrows below to ensure that your information is shared in a limited fashion. Change as indicated Don t Add Phone Number Account settings can be accessed under Account Settings > Google+. Maintain a small Google+ "footprint". Select only important Google+ notifications as shown in the box to the left. Limit notifications to as opposed to text. Do not connect your mobile phone to Google+ or use the Google+ mobile application, and Disable +1 on non-google Websites Do not allow contacts to tag you then automatically link to your profile Disable your circles from accessing your photo tags prior to you Limit Huddle capability only to your circles Off Check as indicated Remove Everyone Do not add outside accounts Deleting Your Google+ Profile Information or Account Useful Links A Parent s Guide to Internet Safety Wired Kids Microsoft Safety & Security OnGuard Online By default, Google+ uses your Google contact information to link your accounts from other online services, aggregating your online identity in one location. To disable this feature: Go to Account Settings > Connected Accounts Click No to Google-suggested 3 rd -party accounts Disable Google+ access to your contact information Do not manually connect other online accounts using Google+ Go to Account Settings > Account Overview Delete Google+ Content removes Google+ related information such as circles, +1 s, posts, and comments Delete your entire Google profile removes all user data from Google services, including your Gmail Disable web history to prevent accumulation of your digital footprint
5 LinkedIn Smart Card LI _1400 Social Networks -Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any information about your activities, personal life, or professional life that you post and share. Ensure that your family takes similar precautions with their accounts; their privacy and sharing settings can expose your personal data. Avoid posting or tagging images of you or your family that clearly show your face. Select pictures taken at a distance, at an angle, or otherwise concealed. Never post Smartphone photos and don t use your face as a profile photo, instead, use cartoons or avatars. Use secure browser settings when possible and monitor your browsing history to ensure that you recognize all access points. Managing Your LinkedIn Profile LinkedIn is a professional networking site whose users establish connections with co-workers, customers, business contacts, and potential employees and employers. Users post and share information about current and previous employment, education, military activities, Use Settings to manage visibility specialties, and interests. To limit exposure of your personal information, you can manage who can view your profile and activities. Profile Settings Apply the Profile settings shown with arrows below to ensure that your information is visible only to people of your choosing. Set to no one Set to Only you Set to totally anonymous Set to Only you Do not use a face photo for your account Set to My Connections Set to Only you LinkedIn Quick Facts There are over 100 million LinkedIn users around the world. Aside from the US, LinkedIn is widely adopted in India, Brazil, and the UK. Users tend to share information related to their careers or jobs as opposed to photographs from parties or social events. LinkedIn profiles tend to be more visible and searchable than in social networks such as Facebook. Paid LinkedIn accounts have access to more information about other users, such as connections, than free accounts. The type of information users can see about each other depends on how closely they are connected (1 st, 2 nd, or 3 rd degree).
6 Account Settings LinkedIn Smart Card LI _1400 Apply the Account settings shown with arrows below to ensure that your information is shared in a limited fashion. Passwords Use a complex password with capital letters and numbers to ensure that attackers cannot access your account information. Closing Your LinkedIn Account If you no longer plan to use the LinkedIn service, you can close your account. Click Close your account and confirm that you want to take this action. to opt out of Partner Advertising on third party websites to opt out of Social Advertising Application Settings Third-party applications and services can access most of your personal information once you grant them permission. You should limit your use of applications to ensure that third parties cannot collect, share, or misuse your personal information. Apply the Application setting shown with arrows below to ensure that your information is visible only to people of your choosing. Do not share with Third Parties Also, avoid using the LinkedIn smartphone app to prevent accidentally collecting and sharing location data. the box. Do not share your information on Third Parties with LinkedIn. LinkedIn, by default, automatically retrieves information about the user on websites with LinkedIn Plug-In integration. Prevent sharing your activities on third-party websites with LinkedIn by unchecking the box. Useful Links A Parent s Guide to Internet Safety Wired Kids Microsoft Safety & Security OnGuard Online
7 Twitter Smart Card Twitter _1631 W2 Social Networks -Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any information about your activities, personal life, or professional life that you post and share. Ensure that your family takes similar precautions with their accounts; their privacy and sharing settings can expose your personal data. Avoid posting or tagging images of you or your family that clearly show your face. Select pictures taken at a distance, at an angle, or otherwise concealed. Never post Smartphone photos and don t use your face as a profile photo, instead, use cartoons or avatars. Use secure browser settings when possible and monitor your browsing history to ensure that you recognize all access points. Managing your Twitter Account Twitter is a social networking and microblogging site whose users send and read text-based posts online. The site surged to worldwide popularity with +300 million active users as of 2011, generating 300 million tweets and 1.6 billion search queries daily. Stream of tweets from people you follow Use Settings to manage visibility Each tweet is timestamped Following are people you subscribe to Followers subscribe to your tweets Private tweets will only be visible to followers you approve Hashtags (#topic) are used to mark a keyword or topic in a Tweet. Posts with hashtag are categorized by topics in the Twitter search engine. Hashtagged words that become popular become Trending Topics (ex. #jan25, #egypt, #sxsw). Mentions (@username) are used to tag a user in a Twitter update. When a public user mentions a private Twitter account, the link to the private account profile becomes public. Tweets Tweets are short text-based messages up to 140 characters that users post to Twitter. "Tweet" can refer to a post as well or to the act of posting to Twitter. Tweets are public, indexed, and searchable unless protected by the user. Many users never Tweet, choosing only to follow persons or topics of interest. Profile Settings Apply the Profile settings shown below to ensure that your information is visible only to people of your choosing. DO NOT use a face photo Use nicknames, initials, or pseudonyms Use general location, such as a country or a metropolitan area This is how your profile page will look to visitors on the web DO NOT connect to Facebook Twitter Best Practices Avoid using hashtags (#) in updates to avoid being indexed and associated with a topic by Twitter Search. Tweet responsibly. Do not provide personal details regarding your whereabouts and activities in your post. Do NOT upload links to personal photos or websites on Twitter. Do NOT allow Twitter to use your location on mobile devices. Change your Twitter username periodically to limit account exposure.
8 Twitter Smart Card Twitter _1631 Account Settings Apply the Account settings shown below to ensure that your information is shared in a limited fashion. DO NOT connect your phone Change every ~6 months Check Protecting your tweets makes all your posts private Only those who you approve can access your tweets Click to delete all location data associated with your account Deactivating / Delete Your Twitter Account To deactive your account, go to Settings and select Account page. At the bottom of the page, click Deactive my account. After deactivation, the user can reactivate the account within 30 days. After 30 days, the account is permanently deleted. Notification & Application Settings Maintain a small digital footprint by minimizing the number of notifications. Revoke access to unnecessary third party applications. Direct message (DM) is never visible to the public Private tweets will become visible to the web when retweeted (RT) by a user with public account Block unknown or unwanted applications from accessing your account Useful Links A Parent s Guide to Internet Safety Wired Kids Microsoft Safety & Security OnGuard Online
9 Enhancing Online Anonymity Smart Card Enhancing Online Anonymity Smart Card HK _1145 Why is striving for online anonymity important? Everything you do on the Internet involves sharing your identity information Identity information can be compared across services by advertisers and data brokers to build consumer profiles This data can also be compiled by identity thieves and malicious actors to gain access to bank accounts and other sensitive information There s no such thing as total anonymity online. Generally, though, how can I make my online activity more anonymous? Use different accounts, user names, and passwords for different kinds of activity (e.g., banking, instant messaging, social media). For more information on creating s, see the Anonymous Services smart card Use a pseudonym whenever possible; don t volunteer information to websites unless they require it For more enhanced anonymity, consider using TOR, a free browser that anonymizes your IP address. To install TOR, see the Anonymous Services smart card Browsing VULNERABILITY: browsers allow websites to install cookies to track your online activity Recommendation: private browsers do not store most cookies Google Chrome Mozilla Firefox Caveats Secure browsing still relays your IP addresses to the websites you visit. You must close the browser for activity to be deleted. Internet Explorer 10 Apple Safari Your Internet Service Provider (ISP) can still see your browsing activity. Internet Searches VULNERABILITY: searches may be recorded and associated with IP address, user agent, or identifiers stored in cookies Recommendation: Search Obfuscation Use general search terms Identify a topic of interest from linked sites DO NOT search using location or individual name, or specific topics DuckDuckGo Uses an encrypted connection by default Only retains cookies related to users settings preferences Does not store users IP addresses, search queries, or personal information. Browser extensions for Firefox, Chrome, Internet Explorer, Safari, and Opera Available at:
10 Enhancing Online Anonymity Smart Card Enhancing Online Anonymity Smart Card HK _1145 Instant Messaging Performed on services such as Adium, Pidgin, Google Chat Allows users to send instant messages from desktop and mobile devices that may contain images, audio clips, and videos Accessed through either explicit registration or implicit registration through an service VULNERABILITY: message histories can be intercepted; packet contents of chats can be intercepted; usernames can link to addresses Recommendation: Off The Record (OTR) Messaging Encrypts instant messages Does not save chat logs Chat clients may store users passwords in a local text file on users PCs (Pidgin); they may also share information such as status, device, contact list, and address in packet File Sharing Allows users to store, share, and create files such as Office Docs, image, video, and audio files Include services such as DropBox, Google Drive, Evernote Cloud or web based VULNERABILITY: sharing private information on SNS; users sharing documents; weak password protection Recommendation: Crabgrass Allows users to register with only an address Supports file sharing, collaborative wikis, group pages Shared content page Each type of shared content page has a control column Best practices include: 1) using separate s for chatting and ing 2) registering for chat clients with a pseudonym used only with that chat client History of document changes including names of Details concerning document permissions Recommendations: File Tea Does not require registration File contents are not cached or stored server side Server never analyzes or processes the files being transferred No cache or log entry of a file transfers are kept IP addresses of users are never stored Once the file is uploaded, a link can be copied and pasted to s or chats; once the browser window is closed, the link expires When sharing files online, be sure to 1) verify sharing permissions are set to ONLY users you wish to share with 2) verify that, if possible, links to shared files can be set to expire 3) ensure that both the sender and receiver have nonidentifying user names
Defense Media Activity Guide To Keeping Your Social Media Accounts Secure
 Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
Are you having trouble logging in with a Username that contains special characters or spaces?
 Troubleshooting Guide Forgot your Username or Password? Are you having trouble logging in with a Username that contains special characters or spaces? Can t launch a course in InfoComm University? Can t
Troubleshooting Guide Forgot your Username or Password? Are you having trouble logging in with a Username that contains special characters or spaces? Can t launch a course in InfoComm University? Can t
NAVY COMMAND PRINCIPAL SECURITY ADVISOR RECOMMENDED FACEBOOK SECURITY SETTINGS
 NAVY COMMAND PRINCIPAL SECURITY ADVISOR RECOMMENDED FACEBOOK SECURITY SETTINGS NC PSyA Recommended Facebook Settings - October 2014 1 Introduction 3 Privacy Shortcuts 3 Privacy Settings and Tools 6 General
NAVY COMMAND PRINCIPAL SECURITY ADVISOR RECOMMENDED FACEBOOK SECURITY SETTINGS NC PSyA Recommended Facebook Settings - October 2014 1 Introduction 3 Privacy Shortcuts 3 Privacy Settings and Tools 6 General
MSGCU SECURE MESSAGE CENTER
 MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
New Online Banking Guide for FIRST time Login
 New Online Banking Guide for FIRST time Login Step 1: Login Enter your existing Online Banking User ID and Password. Click Log-In. Step 2: Accepting terms and Conditions to Proceed Click on See the terms
New Online Banking Guide for FIRST time Login Step 1: Login Enter your existing Online Banking User ID and Password. Click Log-In. Step 2: Accepting terms and Conditions to Proceed Click on See the terms
Optimal Browser Settings for Internet Explorer Running on Microsoft Windows
 Optimal Browser Settings for Internet Explorer Running on Microsoft Windows If you have Internet Explorer 7 or 8: Each time you log in to our web site, it evaluates whether you are using the same computer
Optimal Browser Settings for Internet Explorer Running on Microsoft Windows If you have Internet Explorer 7 or 8: Each time you log in to our web site, it evaluates whether you are using the same computer
How we use cookies on our website
 How we use cookies on our website We use cookies on our site to improve performance and enhance your user experience. This policy explains how cookies work. What are cookies? Cookies are small text files
How we use cookies on our website We use cookies on our site to improve performance and enhance your user experience. This policy explains how cookies work. What are cookies? Cookies are small text files
8x8 Click2Pop User Guide
 USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
Protect Your Online Footprint. HINTS & TIPS provided by MWR InfoSecurity and the Data Baby project
 HINTS & TIPS provided by MWR InfoSecurity and the Data Baby project Logging on is now one of the first things we do every day. And every time we do, we leave a trace, often without giving a thought to
HINTS & TIPS provided by MWR InfoSecurity and the Data Baby project Logging on is now one of the first things we do every day. And every time we do, we leave a trace, often without giving a thought to
DESTINATION MELBOURNE PRIVACY POLICY
 DESTINATION MELBOURNE PRIVACY POLICY 2 Destination Melbourne Privacy Policy Statement Regarding Privacy Policy Destination Melbourne Limited recognises the importance of protecting the privacy of personally
DESTINATION MELBOURNE PRIVACY POLICY 2 Destination Melbourne Privacy Policy Statement Regarding Privacy Policy Destination Melbourne Limited recognises the importance of protecting the privacy of personally
Layar Privacy Policy
 Layar Privacy Policy Version 3.2 November 25, 2014 1. Information Collection and Use 2. Collection, Use and Transfer of Personal Data 3. User Account 4. Data Security 5. Cookies 6. Your Rights At Layar,
Layar Privacy Policy Version 3.2 November 25, 2014 1. Information Collection and Use 2. Collection, Use and Transfer of Personal Data 3. User Account 4. Data Security 5. Cookies 6. Your Rights At Layar,
Vyve Broadband Website Privacy Policy. What Information About Me Is Collected and Stored?
 Vyve Broadband Website Privacy Policy Effective: July 31, 2015 Vyve Broadband ( Vyve, we, us, our ) is committed to letting you know how we will collect and use your information. This Website Privacy Policy
Vyve Broadband Website Privacy Policy Effective: July 31, 2015 Vyve Broadband ( Vyve, we, us, our ) is committed to letting you know how we will collect and use your information. This Website Privacy Policy
How To Login To A Website On A Pc Or Mac Or Mac (For Pc Or Ipad)
 What browser types are supported? Do I need to allow cookies? What are session cookies? The system is asking me to login again and says my session has timed out. What does this mean? I am locked out after
What browser types are supported? Do I need to allow cookies? What are session cookies? The system is asking me to login again and says my session has timed out. What does this mean? I am locked out after
Accessing Websites. Mac/PC Compatibility: QuickStart Guide for Business
 Accessing Websites Mac/PC Compatibility: QuickStart Guide for Business 2 Accessing Websites QuickStart Guide for Business The Basics People use the web for research, entertainment, and business. And it
Accessing Websites Mac/PC Compatibility: QuickStart Guide for Business 2 Accessing Websites QuickStart Guide for Business The Basics People use the web for research, entertainment, and business. And it
Single Sign On: Volunteer User Guide
 Single Sign On: Volunteer User Guide V3.0 Document Owner: Pathways Project Issue Date: 11-Jun-15 Purpose of the Document The Single Sign On (SSO) User Guide has been developed to provide users with instructions
Single Sign On: Volunteer User Guide V3.0 Document Owner: Pathways Project Issue Date: 11-Jun-15 Purpose of the Document The Single Sign On (SSO) User Guide has been developed to provide users with instructions
Protecting Yourself Against Identity Theft. Identity theft is a serious. What is Identity Theft?
 Protecting Yourself Against Identity Theft Identity theft is a serious crime. Identity theft happens when someone steals your personal information and uses it without your permission. It is a growing threat
Protecting Yourself Against Identity Theft Identity theft is a serious crime. Identity theft happens when someone steals your personal information and uses it without your permission. It is a growing threat
Secure Email Client Guide
 PRESIDIO BANK 33 Secure Email Client Guide THE BUSINESS BANK THAT WORKS 8/2013 Table of Contents Introduction.....3 Our Responsibility to Protect Confidential Information....4 Registering and Accessing
PRESIDIO BANK 33 Secure Email Client Guide THE BUSINESS BANK THAT WORKS 8/2013 Table of Contents Introduction.....3 Our Responsibility to Protect Confidential Information....4 Registering and Accessing
Introduction to Cloud Storage GOOGLE DRIVE
 Introduction to Cloud Storage What is Cloud Storage? Cloud computing is one method to store and access data over the internet instead of using a physical hard drive (e.g. computer s hard drive, flash drive,
Introduction to Cloud Storage What is Cloud Storage? Cloud computing is one method to store and access data over the internet instead of using a physical hard drive (e.g. computer s hard drive, flash drive,
How to Create a Voicethread PowerPoint Presentation
 CREATE A FREE VOICETHREAD ACCOUNT 1. Open a browser like Internet Explorer, Firefox, or Safari. Navigate to http://voicethread.com. 2. To create an account, click Sign in or Register. 3. Underneath the
CREATE A FREE VOICETHREAD ACCOUNT 1. Open a browser like Internet Explorer, Firefox, or Safari. Navigate to http://voicethread.com. 2. To create an account, click Sign in or Register. 3. Underneath the
CDUfiles User Guide. Chapter 1: Accessing your data with CDUfiles. Sign In. CDUfiles User Guide Page 1. Here are the first steps to using CDUfiles.
 CDUfiles User Guide Chapter 1: Accessing your data with CDUfiles Here are the first steps to using CDUfiles. Sign In Open your web browser and enter cdufiles.cdu.edu.au or Note: Use cdufiles.egnyte.com
CDUfiles User Guide Chapter 1: Accessing your data with CDUfiles Here are the first steps to using CDUfiles. Sign In Open your web browser and enter cdufiles.cdu.edu.au or Note: Use cdufiles.egnyte.com
What is the Cloud? Computer Basics Web Apps and the Cloud. Page 1
 Computer Basics Web Apps and the Cloud What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the cloud? Basically, the cloud is
Computer Basics Web Apps and the Cloud What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the cloud? Basically, the cloud is
The GIJP Tech team can offer assistance setting up and implementing any of the services mentioned in this document.
 TWITTER Twitter (www.twitter.com) allows users to answer the question, What are you doing in 140 characters or less. Users post about their activities, links of interest, and even ask questions on Twitter.
TWITTER Twitter (www.twitter.com) allows users to answer the question, What are you doing in 140 characters or less. Users post about their activities, links of interest, and even ask questions on Twitter.
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE
 GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE Defense Media Activity TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE Defense Media Activity TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING
Do I need anything special to use it? All you need to use Twitter is an Internet connection or a mobile phone with Internet capability.
 Twitter Guide What is Twitter? Twitter is a real-time communication platform that allows you to quickly share thoughts, opinions, and interesting links with friends, family, and the general public. People
Twitter Guide What is Twitter? Twitter is a real-time communication platform that allows you to quickly share thoughts, opinions, and interesting links with friends, family, and the general public. People
Frequently Asked Questions for the USA TODAY e-newspaper
 Frequently Asked Questions for the USA TODAY e-newspaper Navigating the USA TODAY e-newspaper A look at the toolbar Toolbar Functions, Buttons, and Descriptions The tab marked Contents will take the e-reader
Frequently Asked Questions for the USA TODAY e-newspaper Navigating the USA TODAY e-newspaper A look at the toolbar Toolbar Functions, Buttons, and Descriptions The tab marked Contents will take the e-reader
Recommended Browser Setting for MySBU Portal
 The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
The Internet and Network Technologies
 The Internet and Network Technologies Don Mason Associate Director Copyright 2013 National Center for Justice and the Rule of Law All Rights Reserved Inside vs. Outside Inside the Box What the computer
The Internet and Network Technologies Don Mason Associate Director Copyright 2013 National Center for Justice and the Rule of Law All Rights Reserved Inside vs. Outside Inside the Box What the computer
UPDATE Appendix H: How to set Facebook s privacy settings to increase security
 UPDATE Appendix H: How to set Facebook s privacy settings to increase security (October 2012) Please note that in order to protect yourself you should also change your Security Settings and all the options
UPDATE Appendix H: How to set Facebook s privacy settings to increase security (October 2012) Please note that in order to protect yourself you should also change your Security Settings and all the options
Drive. Etobicoke-Mimico Watershed Coalition
 Drive Etobicoke-Mimico Watershed Coalition (Adapted from Google Drive for Academics available at https://docs.google.com/document/d/1hvbqob26dkpeimv6srdgwvpupuo5ntvojqjxorq0n20/edit?pli=1) Table of Contents
Drive Etobicoke-Mimico Watershed Coalition (Adapted from Google Drive for Academics available at https://docs.google.com/document/d/1hvbqob26dkpeimv6srdgwvpupuo5ntvojqjxorq0n20/edit?pli=1) Table of Contents
OET Cloud Services Getting Started Guide
 OET Cloud Services Getting Started Guide Introduction OET Cloud Services uses Google Drive to let you store and access OET files anywhere -- on the web, and access them on your PC, or on any device connected
OET Cloud Services Getting Started Guide Introduction OET Cloud Services uses Google Drive to let you store and access OET files anywhere -- on the web, and access them on your PC, or on any device connected
P WEBSITE P CATALOGUES P PRICE GUIDES P ONLINE CLOUD STORAGE P e-commerce System. Printed and Electronic (e-documents) Users Guide. vbradug-15.10.
 P WEBSITE P CATALOGUES P PRICE GUIDES P ONLINE CLOUD STORAGE P e-commerce System Printed and Electronic (e-documents) vbradug-5.0.02 Users Guide 205 Bradfield Trading Ltd. All rights reserved. Reproduction
P WEBSITE P CATALOGUES P PRICE GUIDES P ONLINE CLOUD STORAGE P e-commerce System Printed and Electronic (e-documents) vbradug-5.0.02 Users Guide 205 Bradfield Trading Ltd. All rights reserved. Reproduction
Privacy Policy/Your California Privacy Rights Last Updated: May 28, 2015 Introduction
 Privacy Policy/Your California Privacy Rights Last Updated: May 28, 2015 Introduction Welcome! TripleFirrre, LLC, dba Just Seconds Apart knows that safeguarding your privacy is serious business. Your privacy
Privacy Policy/Your California Privacy Rights Last Updated: May 28, 2015 Introduction Welcome! TripleFirrre, LLC, dba Just Seconds Apart knows that safeguarding your privacy is serious business. Your privacy
TxEIS Browser Settings
 TxEIS Browser Settings Updated May 2016 The TxEIS Browser Settings document lists supported browsers and recommended browser settings which will allow you to utilize the TxEIS system at its fullest potential
TxEIS Browser Settings Updated May 2016 The TxEIS Browser Settings document lists supported browsers and recommended browser settings which will allow you to utilize the TxEIS system at its fullest potential
Cloud Controls. Quick Start Guide Version 3.5.1 April 2014
 Cloud Controls Quick Start Guide Version 3.5.1 April 2014 W HE A NY ANY TIME ONLINE RE Table of Contents Welcome to imeet Cloud Controls. 1 Getting started. 2 Add hosts and meeting rooms. 4 Enterprise-wide
Cloud Controls Quick Start Guide Version 3.5.1 April 2014 W HE A NY ANY TIME ONLINE RE Table of Contents Welcome to imeet Cloud Controls. 1 Getting started. 2 Add hosts and meeting rooms. 4 Enterprise-wide
1. Open up your Internet browser and go to https://hootsuite.com
 HootSuite Tutorial HootSuite is an excellent social media management website. Through HootSuite you can track things like when your Twitter account (called a handle ) is mentioned by another Twitter user,
HootSuite Tutorial HootSuite is an excellent social media management website. Through HootSuite you can track things like when your Twitter account (called a handle ) is mentioned by another Twitter user,
Using OwnCloud. OwnCloud is a very easy to use file storage and sharing system that you can access anywhere you have an internet connection.
 Using OwnCloud OwnCloud is a very easy to use file storage and sharing system that you can access anywhere you have an internet connection. 1. Contact the IT Department to set up your account. 2. Once
Using OwnCloud OwnCloud is a very easy to use file storage and sharing system that you can access anywhere you have an internet connection. 1. Contact the IT Department to set up your account. 2. Once
Posting Job Orders. mindscope Staffing and Recruiting Software www.mindscope.com
 Posting Job Orders CURA Technical Support Email: cura_support@mindscope.com Phone: 1.888.322.2362 x 555 Posting Job Orders Page 1 Table of Contents Posting Jobs Orders... 2 Posting Jobs on Your Website...
Posting Job Orders CURA Technical Support Email: cura_support@mindscope.com Phone: 1.888.322.2362 x 555 Posting Job Orders Page 1 Table of Contents Posting Jobs Orders... 2 Posting Jobs on Your Website...
Instructions for Configuring Your Browser Settings and Online Security FAQ s. ios8 Settings for iphone and ipad app
 Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Secure File Transfer Help Guide
 Secure File Transfer Help Guide Establish a Secure File Transfer Account When a package is sent to your email address, you will receive an email from the sender that includes a link to instructions to
Secure File Transfer Help Guide Establish a Secure File Transfer Account When a package is sent to your email address, you will receive an email from the sender that includes a link to instructions to
How to sync Office 365 email with Gmail
 How to sync Office 365 email with Gmail Why would you want to sync your Office 365 email account with Gmail? Send and receive emails from multiple accounts at one website location Sync Gmail with all of
How to sync Office 365 email with Gmail Why would you want to sync your Office 365 email account with Gmail? Send and receive emails from multiple accounts at one website location Sync Gmail with all of
DDN CUSTOMER SUPPORT COMMUNITY QUICK START GUIDE
 DDN CUSTOMER SUPPORT COMMUNITY QUICK START GUIDE March 10, 2015 v2 Contents Getting an Account Logging In Creating a New Case Updating an Existing Case Using the Knowledgebase Welcome to the DDN Customer
DDN CUSTOMER SUPPORT COMMUNITY QUICK START GUIDE March 10, 2015 v2 Contents Getting an Account Logging In Creating a New Case Updating an Existing Case Using the Knowledgebase Welcome to the DDN Customer
Mac OS X. Staff members using NEIU issued laptops and computers on Active Directory can access NEIU resources that are available on the wired network.
 Mac OS X The University Technology Services is privileged to offer a secure wifi network to the university community. Connecting to this network will provide you with benefits in security and improved
Mac OS X The University Technology Services is privileged to offer a secure wifi network to the university community. Connecting to this network will provide you with benefits in security and improved
ONLINE ACCOUNTABILITY FOR EVERY DEVICE. Quick Reference Guide V1.0
 ONLINE ACCOUNTABILITY FOR EVERY DEVICE Quick Reference Guide V1.0 TABLE OF CONTENTS ACCOUNT SET UP Creating an X3watch account DOWNLOADING AND INSTALLING X3WATCH System Requirements How to install on a
ONLINE ACCOUNTABILITY FOR EVERY DEVICE Quick Reference Guide V1.0 TABLE OF CONTENTS ACCOUNT SET UP Creating an X3watch account DOWNLOADING AND INSTALLING X3WATCH System Requirements How to install on a
Easy Social Media Management with Hootsuite
 Easy Social Media Management with Hootsuite Hootsuite is the largest social media integration and management platform on the Internet. It has sent over 700 million messages to date and has over 3 million
Easy Social Media Management with Hootsuite Hootsuite is the largest social media integration and management platform on the Internet. It has sent over 700 million messages to date and has over 3 million
INTRODUCTION TO CLOUD STORAGE
 University of North Carolina at Chapel Hill Libraries Carrboro Cybrary Chapel Hill Public Library Durham County Public Library INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What
University of North Carolina at Chapel Hill Libraries Carrboro Cybrary Chapel Hill Public Library Durham County Public Library INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What
Unified Meeting 5 User guide for MAC
 Unified Meeting 5 User guide for MAC Unified Meeting 5 is a web based tool that puts you in complete control of all aspects of your meeting including scheduling, managing and securing your meetings.. Whether
Unified Meeting 5 User guide for MAC Unified Meeting 5 is a web based tool that puts you in complete control of all aspects of your meeting including scheduling, managing and securing your meetings.. Whether
Adaptive Business Management Systems Privacy Policy
 Adaptive Business Management Systems Privacy Policy Updated policy: Effective on July 01, 2013 This privacy statement describes how Adaptive Business Management Systems collects and uses the personal information
Adaptive Business Management Systems Privacy Policy Updated policy: Effective on July 01, 2013 This privacy statement describes how Adaptive Business Management Systems collects and uses the personal information
How to create database in GlycomcsPortal?
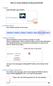 How to create database in GlycomcsPortal? 1. Log- in Log in through Log in 2. Submit Content Click Submit Content on the menu. 3. Choose Database Choose Database as a type of entry you desire to create.
How to create database in GlycomcsPortal? 1. Log- in Log in through Log in 2. Submit Content Click Submit Content on the menu. 3. Choose Database Choose Database as a type of entry you desire to create.
Hosted PBX. TelePacific Communicator User Guide. Desktop Edition
 Hosted PBX TelePacific Communicator User Guide Desktop Edition 11/19/2014 CONTENTS Login... 2 Home Window... 3 Status Flag... 4 My Room... 6 Contacts Screen... 6 History... 8 Directory... 9 Dialpad...
Hosted PBX TelePacific Communicator User Guide Desktop Edition 11/19/2014 CONTENTS Login... 2 Home Window... 3 Status Flag... 4 My Room... 6 Contacts Screen... 6 History... 8 Directory... 9 Dialpad...
dotmailer for Salesforce Installation Guide Winter 2015 Version 2.30.1
 for Salesforce Installation Guide Winter 2015 Version 2.30.1 Page 1 CONTENTS 1 Introduction 2 Browser support 2 Self-Installation Steps 2 Checks 3 Package Download and Installation 4 Users for Email Automation
for Salesforce Installation Guide Winter 2015 Version 2.30.1 Page 1 CONTENTS 1 Introduction 2 Browser support 2 Self-Installation Steps 2 Checks 3 Package Download and Installation 4 Users for Email Automation
Getting Started. Getting Started with Time Warner Cable Business Class. Voice Manager. A Guide for Administrators and Users
 Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Hootsuite instructions
 Hootsuite instructions Posting to Facebook Posting to Twitter Cross-posting Adding Twitter Stream Twitter Lists Twitter searches Replying and Retweeting Definitions Hootsuite video training Hootsuite is
Hootsuite instructions Posting to Facebook Posting to Twitter Cross-posting Adding Twitter Stream Twitter Lists Twitter searches Replying and Retweeting Definitions Hootsuite video training Hootsuite is
UNIFIED MEETING 5 Frequently Asked Questions
 UNIFIED MEETING 5 Frequently Asked Questions Unified Meeting 5 is InterCall s meeting and collaboration application that puts you in control of all aspects of your meeting including scheduling, participant
UNIFIED MEETING 5 Frequently Asked Questions Unified Meeting 5 is InterCall s meeting and collaboration application that puts you in control of all aspects of your meeting including scheduling, participant
H&R Block Digital Tax Preparation, Online, and Mobile Application Privacy Practices and Principles
 Privacy Notice H&R Block Digital Tax Preparation, Online, and Mobile Application Privacy Practices and Principles Protecting your information is important to us. The following guidelines set forth our
Privacy Notice H&R Block Digital Tax Preparation, Online, and Mobile Application Privacy Practices and Principles Protecting your information is important to us. The following guidelines set forth our
NBA Math Hoops Privacy Statement and Children s Privacy Statement Updated October 17, 2013.
 NBA Math Hoops Privacy Statement and Children s Privacy Statement Updated October 17, 2013. This Privacy Statement applies to the web sites mobile applications provided by Learn Fresh Education Co. (collectively,
NBA Math Hoops Privacy Statement and Children s Privacy Statement Updated October 17, 2013. This Privacy Statement applies to the web sites mobile applications provided by Learn Fresh Education Co. (collectively,
Send and receive encrypted e-mails
 Manual Send and receive encrypted e-mails Bank J. Safra Sarasin Ltd Document Owner Security Classification Document Type Bank J. Safra Sarasin Ltd internal and external use Manual Document change history
Manual Send and receive encrypted e-mails Bank J. Safra Sarasin Ltd Document Owner Security Classification Document Type Bank J. Safra Sarasin Ltd internal and external use Manual Document change history
Lifesize Cloud Privacy Statement
 Lifesize Cloud Privacy Statement When you use Lifesize Cloud, you provide certain information to Lifesize, Inc. and its affiliates, successors and assigns (collectively referred to as Lifesize ), including
Lifesize Cloud Privacy Statement When you use Lifesize Cloud, you provide certain information to Lifesize, Inc. and its affiliates, successors and assigns (collectively referred to as Lifesize ), including
Zoom Cloud Meetings: Leader Guide
 Zoom Cloud Meetings: Leader Guide Zoom is a cloud-based conferencing solution that provides both video conferencing and screen share capabilities. Zoom can be used for meetings among individuals or to
Zoom Cloud Meetings: Leader Guide Zoom is a cloud-based conferencing solution that provides both video conferencing and screen share capabilities. Zoom can be used for meetings among individuals or to
SAP VIRTUAL AGENCY GETTING STARTED GUIDE: SELF SERVICE MARKETING
 GETTING STARTED GUIDE: SELF SERVICE MARKETING SELF SERVICE MARKETING TABLE OF CONTENTS Introduction 3 Starting Out 4 Creating Campaigns and Collateral 8 Customizing and Executing a Pre-Packaged Campaign
GETTING STARTED GUIDE: SELF SERVICE MARKETING SELF SERVICE MARKETING TABLE OF CONTENTS Introduction 3 Starting Out 4 Creating Campaigns and Collateral 8 Customizing and Executing a Pre-Packaged Campaign
OneDrive for Business FAQ s Updated 6/19/14
 OneDrive for Business FAQ s Updated 6/19/14 What is OneDrive for Business? OneDrive for Business is an online service that provides resources for file storage, collaboration, and communication. It provides
OneDrive for Business FAQ s Updated 6/19/14 What is OneDrive for Business? OneDrive for Business is an online service that provides resources for file storage, collaboration, and communication. It provides
webcrm App for HootSuite User Guide
 webcrm App for HootSuite User Guide 07 December 2014 Contents General... 3 Install the webcrm App on HootSuite... 4 Configure webcrm HootSuite Integration in webcrm... 6 Add Custom Attributes... 6 Map
webcrm App for HootSuite User Guide 07 December 2014 Contents General... 3 Install the webcrm App on HootSuite... 4 Configure webcrm HootSuite Integration in webcrm... 6 Add Custom Attributes... 6 Map
Introducing OneDrive for Business
 Introducing OneDrive for Business OneDrive for Business is Microsoft s cloud storage service, which comes as part of the Conservatoire s Office365 subscription. OneDrive for Business allows you to access
Introducing OneDrive for Business OneDrive for Business is Microsoft s cloud storage service, which comes as part of the Conservatoire s Office365 subscription. OneDrive for Business allows you to access
Store & Share Quick Start
 Store & Share Quick Start What is Store & Share? Store & Share is a service that allows you to upload all of your content (documents, music, video, executable files) into a centralized cloud storage. You
Store & Share Quick Start What is Store & Share? Store & Share is a service that allows you to upload all of your content (documents, music, video, executable files) into a centralized cloud storage. You
Student ANGEL FAQs. General Issues: System Requirements:
 Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
BlackBerry Internet Service. Version: 4.5.1. Administration Guide
 BlackBerry Internet Service Version: 4.5.1 Administration Guide Published: 2014-01-22 SWD-20140122155744258 Contents 1 Getting started...6 Administrative feature availability... 6 Availability of features
BlackBerry Internet Service Version: 4.5.1 Administration Guide Published: 2014-01-22 SWD-20140122155744258 Contents 1 Getting started...6 Administrative feature availability... 6 Availability of features
Administration Guide. WatchDox Server. Version 4.8.0
 Administration Guide WatchDox Server Version 4.8.0 Published: 2015-11-01 SWD-20151101091846278 Contents Introduction... 7 Getting started... 11 Signing in to WatchDox... 11 Signing in with username and
Administration Guide WatchDox Server Version 4.8.0 Published: 2015-11-01 SWD-20151101091846278 Contents Introduction... 7 Getting started... 11 Signing in to WatchDox... 11 Signing in with username and
Criminal Justice Social Work Community of Practice Subscription, registration and login manual
 Criminal Justice Social Work Community of Practice Subscription, registration and login manual Version: concept 08102014 Introduction Before you can access the Criminal Justice Social Work - Community
Criminal Justice Social Work Community of Practice Subscription, registration and login manual Version: concept 08102014 Introduction Before you can access the Criminal Justice Social Work - Community
Google Apps Migration
 Academic Technology Services Google Apps Migration Getting Started 1 Table of Contents How to Use This Guide... 4 How to Get Help... 4 Login to Google Apps:... 5 Import Data from Microsoft Outlook:...
Academic Technology Services Google Apps Migration Getting Started 1 Table of Contents How to Use This Guide... 4 How to Get Help... 4 Login to Google Apps:... 5 Import Data from Microsoft Outlook:...
Cloud Web Portal User Guide Version 2.0
 Cloud Web Portal User Guide Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
Cloud Web Portal User Guide Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
Wimba Pronto. Version 3.1. Administrator Guide
 Wimba Pronto Version 3.1 Administrator Guide Wimba Pronto 3.1 Administrator Guide Overview 1 Accessing the Wimba Pronto Administration Interface 2 Managing Multiple Institutions 3 General Features 4 Configuring
Wimba Pronto Version 3.1 Administrator Guide Wimba Pronto 3.1 Administrator Guide Overview 1 Accessing the Wimba Pronto Administration Interface 2 Managing Multiple Institutions 3 General Features 4 Configuring
WYOMINGTOURISM.ORG Deal Listings How To Guide Version 1 Published November 26 th, 2014
 WYOMINGTOURISM.ORG Deal Listings How To Guide Version 1 Published November 26 th, 2014 Getting Started SYSTEM REQUIREMENTS Internet Explorer 8 & Newer Firefox 3.5 + 18 and newer Google Chrome (18 and newer)
WYOMINGTOURISM.ORG Deal Listings How To Guide Version 1 Published November 26 th, 2014 Getting Started SYSTEM REQUIREMENTS Internet Explorer 8 & Newer Firefox 3.5 + 18 and newer Google Chrome (18 and newer)
Internet Explorer Services - What Makes Them Different?
 Privacy Policy Effective Starting: June 23, 2015 (view archived versions) Introduction This Privacy Policy explains what information Atlassian Pty Ltd and its related entities ("Atlassian") collect about
Privacy Policy Effective Starting: June 23, 2015 (view archived versions) Introduction This Privacy Policy explains what information Atlassian Pty Ltd and its related entities ("Atlassian") collect about
Reference Guide for WebCDM Application 2013 CEICData. All rights reserved.
 Reference Guide for WebCDM Application 2013 CEICData. All rights reserved. Version 1.2 Created On February 5, 2007 Last Modified August 27, 2013 Table of Contents 1 SUPPORTED BROWSERS... 3 1.1 INTERNET
Reference Guide for WebCDM Application 2013 CEICData. All rights reserved. Version 1.2 Created On February 5, 2007 Last Modified August 27, 2013 Table of Contents 1 SUPPORTED BROWSERS... 3 1.1 INTERNET
IT Information Packet
 IT Information Packet Welcome to the University of Mount Olive! Beginning college is an exciting time where you will be experiencing many new things in a short amount of time. We understand that technology
IT Information Packet Welcome to the University of Mount Olive! Beginning college is an exciting time where you will be experiencing many new things in a short amount of time. We understand that technology
RIDICULOUSLY EASY GUIDE TO SOCIAL MEDIA TWITTER
 RIDICULOUSLY EASY GUIDE TO SOCIAL MEDIA Alberta s a big place and while you could run round the province telling everyone you see about Change Day AB, it s probably not the best use of your time and could
RIDICULOUSLY EASY GUIDE TO SOCIAL MEDIA Alberta s a big place and while you could run round the province telling everyone you see about Change Day AB, it s probably not the best use of your time and could
Welcome to the TransPerfect Translations Secure File Transfer Website What is Secure FTP?
 Welcome to the TransPerfect Translations Secure File Transfer Website What is Secure FTP? SFTP (Secure File Transfer Protocol) is an added layer of security provided to our clients. SFTP requires an encrypted
Welcome to the TransPerfect Translations Secure File Transfer Website What is Secure FTP? SFTP (Secure File Transfer Protocol) is an added layer of security provided to our clients. SFTP requires an encrypted
Peru State College Distance Education Student s Guide
 Using YouTube for Online Courses - Peru State College Distance Education Student s Guide - YouTube Videos & Your Blackboard Course Introduction & Reasons for Using YouTube 1 Creating a YouTube Account
Using YouTube for Online Courses - Peru State College Distance Education Student s Guide - YouTube Videos & Your Blackboard Course Introduction & Reasons for Using YouTube 1 Creating a YouTube Account
The Winnipeg Foundation Privacy Policy
 The Winnipeg Foundation Privacy Policy The http://www.wpgfdn.org (the Website ) is operated by The Winnipeg Foundation (the Foundation ). The Winnipeg Foundation Privacy Policy Foundation is committed
The Winnipeg Foundation Privacy Policy The http://www.wpgfdn.org (the Website ) is operated by The Winnipeg Foundation (the Foundation ). The Winnipeg Foundation Privacy Policy Foundation is committed
Compliance Document Manager User Guide
 Compliance Document Manager User Guide CONTENTS Overview...2 System Requirements...2 Log In...3 Navigation...4 Navigating Compliance Manager...4 Screen Vendors...5 Manage Oversight...6 My Calendar...6
Compliance Document Manager User Guide CONTENTS Overview...2 System Requirements...2 Log In...3 Navigation...4 Navigating Compliance Manager...4 Screen Vendors...5 Manage Oversight...6 My Calendar...6
UNIFIED MEETING 5 HELP
 UNIFIED MEETING 5 HELP Table of Contents Conference Manager... 1 About Conference Manager... 1 From Conference Manager, you can... 1 Signing in to Conference Manager... 2 To sign in to the Conference
UNIFIED MEETING 5 HELP Table of Contents Conference Manager... 1 About Conference Manager... 1 From Conference Manager, you can... 1 Signing in to Conference Manager... 2 To sign in to the Conference
SmartGrant Web Browser Set-Up
 SmartGrant Web Browser Set-Up TABLE OF CONTENTS SmartGrant Supported Web Browsers for Windows... 2 Configuring Your Web Browser for SmartGrant... 3 Internet Explorer... 3 Firefox... 10 Chrome... 15 Safari...
SmartGrant Web Browser Set-Up TABLE OF CONTENTS SmartGrant Supported Web Browsers for Windows... 2 Configuring Your Web Browser for SmartGrant... 3 Internet Explorer... 3 Firefox... 10 Chrome... 15 Safari...
Ontario College Online Application. Your future starts here...
 Ontario College Online Application Your future starts here... Step 1 Research colleges and programs FIND A COLLEGE view the map FIND A COLLEGE Visit ontariocolleges.ca and click on the Choose a College
Ontario College Online Application Your future starts here... Step 1 Research colleges and programs FIND A COLLEGE view the map FIND A COLLEGE Visit ontariocolleges.ca and click on the Choose a College
Help. F-Secure Online Backup
 Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
The Internet, the Web, and Electronic Commerce
 The Internet, the Web, and Electronic Commerce Chapter 2 2014 by McGraw-Hill Education. This proprietary material solely for authorized instructor use. Not authorized for sale or distribution in any manner.
The Internet, the Web, and Electronic Commerce Chapter 2 2014 by McGraw-Hill Education. This proprietary material solely for authorized instructor use. Not authorized for sale or distribution in any manner.
How To Use Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
NDSU Technology Learning & Media Center. Introduction to Google Sites
 NDSU Technology Learning & Media Center QBB 150C 231-5130 www.ndsu.edu/its/tlmc Introduction to Google Sites Get Help at the TLMC 1. Get help with class projects on a walk-in basis; student learning assistants
NDSU Technology Learning & Media Center QBB 150C 231-5130 www.ndsu.edu/its/tlmc Introduction to Google Sites Get Help at the TLMC 1. Get help with class projects on a walk-in basis; student learning assistants
How to register and use our Chat System
 How to register and use our Chat System Why this document? We have a very good chat system and easy to use when you are set up, but getting registered and into the system can be a bit complicated. If you
How to register and use our Chat System Why this document? We have a very good chat system and easy to use when you are set up, but getting registered and into the system can be a bit complicated. If you
Online Banking and Bill Pay FAQs
 Online Banking Why does it say Jack Henry and Associates in the URL in my browser bar when I log in to online banking? When you log in to Cape Cod Five Online Banking, you may have noticed that Jack Henry
Online Banking Why does it say Jack Henry and Associates in the URL in my browser bar when I log in to online banking? When you log in to Cape Cod Five Online Banking, you may have noticed that Jack Henry
Dropbox for Business. Secure file sharing, collaboration and cloud storage. G-Cloud Service Description
 Dropbox for Business Secure file sharing, collaboration and cloud storage G-Cloud Service Description Table of contents Introduction to Dropbox for Business 3 Security 7 Infrastructure 7 Getting Started
Dropbox for Business Secure file sharing, collaboration and cloud storage G-Cloud Service Description Table of contents Introduction to Dropbox for Business 3 Security 7 Infrastructure 7 Getting Started
Mobile Merchant Reference Guide
 COPYRIGHT NOTICE Copyright 2013 Blackstone Merchant Services, Inc. All rights reserved. This document is for internal use only. No part of this publication may be reproduced, transmitted, transcribed,
COPYRIGHT NOTICE Copyright 2013 Blackstone Merchant Services, Inc. All rights reserved. This document is for internal use only. No part of this publication may be reproduced, transmitted, transcribed,
Privacy Policy. Peeptrade LLC ( Company or We ) respect your privacy and are committed to protecting it through our compliance with this policy.
 Privacy Policy Introduction Peeptrade LLC ( Company or We ) respect your privacy and are committed to protecting it through our compliance with this policy. This policy describes the types of information
Privacy Policy Introduction Peeptrade LLC ( Company or We ) respect your privacy and are committed to protecting it through our compliance with this policy. This policy describes the types of information
isupplygw Site Login Troubleshooting
 Site Login Troubleshooting Tips User name is administrator s email address Password requirements: o Passwords must be at least 8 characters long and can be as long as 30 characters. o Passwords must contain
Site Login Troubleshooting Tips User name is administrator s email address Password requirements: o Passwords must be at least 8 characters long and can be as long as 30 characters. o Passwords must contain
ONLINE PRIVACY POLICY
 ONLINE PRIVACY POLICY The City of New Westminster is committed to protecting your privacy. Any personal information collected, used or disclosed by the City is in accordance with the Freedom of Information
ONLINE PRIVACY POLICY The City of New Westminster is committed to protecting your privacy. Any personal information collected, used or disclosed by the City is in accordance with the Freedom of Information
Web Conferencing Version 8.3 Troubleshooting Guide
 System Requirements General Requirements Web Conferencing Version 8.3 Troubleshooting Guide Listed below are the minimum requirements for participants accessing the web conferencing service. Systems which
System Requirements General Requirements Web Conferencing Version 8.3 Troubleshooting Guide Listed below are the minimum requirements for participants accessing the web conferencing service. Systems which
Connecting With Lifesize Cloud
 There are several different ways to connect to a Lifesize Cloud video conference meeting. This guide will provide you instructions for each way. Ways to Join a Lifesize Cloud Video Conference After getting
There are several different ways to connect to a Lifesize Cloud video conference meeting. This guide will provide you instructions for each way. Ways to Join a Lifesize Cloud Video Conference After getting
RDM on Demand Privacy Policy
 RDM on Demand Privacy Policy Ataccama Corp. www.ataccama.com info@ataccama.com Toronto, CA Prague, CZ London, UK Stamford, US 1 ATACCAMA RDM ON DEMAND PRIVACY POLICY 1. Ataccama Corp. ("Ataccama") and
RDM on Demand Privacy Policy Ataccama Corp. www.ataccama.com info@ataccama.com Toronto, CA Prague, CZ London, UK Stamford, US 1 ATACCAMA RDM ON DEMAND PRIVACY POLICY 1. Ataccama Corp. ("Ataccama") and
Using Avaya Aura Messaging Web Access
 Using Avaya Aura Messaging Web Access Release 6.3.2 Issue 1 December 2014 Contents Chapter 1: Getting started... 5 Avaya Aura Messaging Web Access... 5 Requirements... 5 Logging in to Messaging Web Access...
Using Avaya Aura Messaging Web Access Release 6.3.2 Issue 1 December 2014 Contents Chapter 1: Getting started... 5 Avaya Aura Messaging Web Access... 5 Requirements... 5 Logging in to Messaging Web Access...
mystanwell.com Installing Citrix Client Software Information and Business Systems
 mystanwell.com Installing Citrix Client Software Information and Business Systems Doc No: 020/12 Revision No: Revision Date: Page: 1 of 16 Contents Overview... 3 1. Microsoft Internet Explorer... 3 2.
mystanwell.com Installing Citrix Client Software Information and Business Systems Doc No: 020/12 Revision No: Revision Date: Page: 1 of 16 Contents Overview... 3 1. Microsoft Internet Explorer... 3 2.
30 Minutes to Automated Online Income (ver. 2)
 30 Minutes to Automated Online Income (ver. 2) BONUS: How to make $1000 per month using this system You do NOT require: - Money (no signup fees, no hidden charges, no credit card required) - A Website
30 Minutes to Automated Online Income (ver. 2) BONUS: How to make $1000 per month using this system You do NOT require: - Money (no signup fees, no hidden charges, no credit card required) - A Website
