The Internet of Things Risks and Challenges
|
|
|
- Herbert Summers
- 8 years ago
- Views:
Transcription
1 The Internet of Things Risks and Challenges Providing the insight that enables our customers to make informed business decisions. Antony Price 03rd March 2015
2 Contents Internet of Things - The next threat generation Risks and Challenges Jackpotting How the CIC can help Final thoughts Questions
3 Internet of Things (IoT) The next threat generation Having so many interconnected devices is convenient but represents a risk for organisations as they still lack security. Here are the top five threats to IoT devices identified by CSO last year. In-Car WiFi: This technology is turning cars into mobile hotspots and connects passenger s devices to Internet. But without the firewalls usually present in traditional WiFi hotspots, in-car devices and data will be at risk. Wereable devices: Due to their automatic connection to the Internet, devices like Google Glass are a major attack vector, providing attackers with confidential corporate information and intellectual property. mhealth applications: The wearable wireless devices market across fitness, mhealth and sports growing so quickly, hackers will increasingly attack them to get personal health information. M2M: M2M security being closely connected with the IoT and the number of devices that routinely use the Internet to function increasing, mobile devices are becoming more and more vulnerable to Internet-based attacks. Drones: As drones rely on vulnerable telemetry signals, attackers can leverage them easily using various attacks such as authentication bypasses Deloitte MCS Limited. All rights reserved.
4 Risks and Challenges With more than 30 billion devices expected to be wirelessly connected to the IoT by 2020, imagine again what the lack of a robust security infrastructure would mean for that M2M-enabled car you might be driving ZDNet, Rate of change Rapid proliferation of number, types and capabilities of IoT connected devices and sensors being developed and released is faster than we can understand and manage the unique risks and threats to properly secure them. Privacy concerns Everything will become a node on the network, which means that everything will be monitored and/or reporting its status. This raises concerns on how information will be used, for what purpose, and by who. Will there be a skills drain due to people becoming dependent on their devices or can people opt out into Interne-Free Zones. Software vulnerabilities These devices and sensors are treated like hardware appliances, however these devices and sensors are not just hardware devices they are also software applications that will contain software weaknesses. These weakness will need to managed and patched. Lack of acceptance from vendors - no plan to patch of fix vulnerabilities. Management challenges Geographic disparity, device disparity, operating system disparity, number of devices, different data types will introduce information, security and operation management challenges. This will be Insecure by design These devices and sensors are not built with security in mind: Many have purpose-built features that equate to security flaws. IoT devices include anything from SCADA to consumer products - all flawed with inherent weaknesses Deloitte MCS Limited. Private and confidential
5 Risks and Challenges Figures 70% Of tested devices are vulnerable to attacks. 25% Avg. number of identified vulnerabilities per device. 80% Allow the use of weak passwords. 70% 25 80% 60% 60% Have vulnerable web interfaces. Of tested devices are Avg. number of identified Allow the use of weak Have vulnerable web vulnerable to attack. vulnerabilities per device. passwords. interfaces Deloitte MCS Limited. Private and confidential.
6 Industry-Specific Challenges Category Challenges Category Sample S&P Concerns Motor Vehicle/Location tracking Unauthorised vehicle access Self-driving vehicles (and impacts of malicious intent) Health Mobile health device - data Monitoring privacy Payment transaction security External, distributed physical links to internal corporate systems Home Unauthorised home access POS/Vending Hacking biomedical Automation Privacy issues if video links devices (e.g. are misused/hacked pacemakers) Smart meters HIPPA compliance Household appliances Opt-in, Opt-out criteria hacking Insurance Privacy of loss history Smart Grid & Power grid attacks, Anonymisation of data for Utilities vulnerability statistical analysis National security implications Deloitte MCS Limited. Private and confidential.
7 Jackpotting Malware will often slow down a computer, and when you slow down a medical device it no longer gives the integrity needed to perform as it should. Barnaby Jack was known for his jackpotting presentation at the Black Hat computer security Conference in He demonstrated different kinds of attacks involving both physical access to two ATMs and completely automated remote attacks. He also gave presentation outlining vulnerabilities on various medical devices by hacking insulin pumps, pacemakers and defibrillators Deloitte MCS Limited. Private and confidential.
8 Cyber Intelligence Centre Enabling effective protection and response Helping organisations protect their critical data and services by driving value from their existing security infrastructure via the CIC Services. Cyber Monitor Cyber Watch Cyber Protect Cyber Check Cyber Respond Cyber Govern Deloitte MCS Limited. All rights reserved.
9 Final thoughts What looms on the horizon is even more daunting. With the Internet of Things, every car, consumer appliance, and piece of equipment could be linked and ready for hacking Tech Trends Deloitte University Press IoT is (and always will be) bringing more entry points in to an organisation Security teams need to redefine the scope of security efforts Must address policy and processes while maintaining security and compliance Segment consumer IP devices from data-sensitive systems on corporate network Deloitte MCS Limited. All rights reserved.
10 Deloitte refers to one or more of Deloitte Touche Tohmatsu Limited ( DTTL ), a UK private company limited by guarantee, and its network of member firms, each of which is a legally separate and independent entity. Please see for a detailed description of the legal structure of DTTL and its member firms. Deloitte MCS Limited is a subsidiary of Deloitte LLP, the United Kingdom member firm of DTTL. This publication has been written in general terms and therefore cannot be relied on to cover specific situations; application of the principles set out will depend upon the particular circumstances involved and we recommend that you obtain professional advice before acting or refraining from acting on any of the contents of this publication. Deloitte MCS Limited would be pleased to advise readers on how to apply the principles set out in this publication to their specific circumstances. Deloitte MCS Limited accepts no duty of care or liability for any loss occasioned to any person acting or refraining from action as a result of any material in this publication. Registered office: Hill House, 1 Little New Street, London EC4A 3TR, United Kingdom. Registered in England No Deloitte MCS Limited. Private and confidential.
ISO27032 Guidelines for Cyber Security
 ISO27032 Guidelines for Cyber Security Deloitte Point of View on analysing and implementing the guidelines Deloitte LLP Enterprise Risk Services Security & Resilience Contents Foreword 1 Cyber governance
ISO27032 Guidelines for Cyber Security Deloitte Point of View on analysing and implementing the guidelines Deloitte LLP Enterprise Risk Services Security & Resilience Contents Foreword 1 Cyber governance
Current issues and trends in the Aerospace supply chain
 Current issues and trends in the Aerospace supply chain Iain Subtitle Kirwan runs here 1 line max Director Supply Chain Consulting Global A&D insights and trends Overall global A&D industry expected to
Current issues and trends in the Aerospace supply chain Iain Subtitle Kirwan runs here 1 line max Director Supply Chain Consulting Global A&D insights and trends Overall global A&D industry expected to
Identity & Access Management The Cloud Perspective. Andrea Themistou 08 October 2015
 Identity & Management The Cloud Perspective Andrea Themistou 08 October 2015 Agenda Cloud Adoption Benefits & Risks Security Evolution for Cloud Adoption Securing Cloud Applications with IAM Securing Cloud
Identity & Management The Cloud Perspective Andrea Themistou 08 October 2015 Agenda Cloud Adoption Benefits & Risks Security Evolution for Cloud Adoption Securing Cloud Applications with IAM Securing Cloud
Addressing Cyber Risk Building robust cyber governance
 Addressing Cyber Risk Building robust cyber governance Mike Maddison Partner Head of Cyber Risk Services The future of security The business environment is changing The IT environment is changing The cyber
Addressing Cyber Risk Building robust cyber governance Mike Maddison Partner Head of Cyber Risk Services The future of security The business environment is changing The IT environment is changing The cyber
Internet of Things (IoT): Security Awareness. Sandra Liepkalns, CRISC sandra.liepkalns@netrus.com
 Internet of Things (IoT): Security Awareness Sandra Liepkalns, CRISC sandra.liepkalns@netrus.com So What is the Internet of Things Network of physical objects embedded with: Electronics, software, sensors
Internet of Things (IoT): Security Awareness Sandra Liepkalns, CRISC sandra.liepkalns@netrus.com So What is the Internet of Things Network of physical objects embedded with: Electronics, software, sensors
Security Threats on National Defense ICT based on IoT
 , pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
, pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
30 BILLION RISKS AND REWARDS OF CONNECTED DEVICES THE INTERNET OF THINGS CYBER LANDSCAPE TODAY
 RISKS AND REWARDS OF CONNECTED DEVICES THE HIDDEN INTERNET OF THINGS ISACA 2015 IT RISK / REWARD BAROMETER The Internet of Things paints a vision of a carefree, seamlessly connected world where interconnected
RISKS AND REWARDS OF CONNECTED DEVICES THE HIDDEN INTERNET OF THINGS ISACA 2015 IT RISK / REWARD BAROMETER The Internet of Things paints a vision of a carefree, seamlessly connected world where interconnected
What is Really Needed to Secure the Internet of Things?
 What is Really Needed to Secure the Internet of Things? By Alan Grau, Icon Labs alan.grau@iconlabs.com The Internet of Things (IoT) has become a ubiquitous term to describe the tens of billions of devices
What is Really Needed to Secure the Internet of Things? By Alan Grau, Icon Labs alan.grau@iconlabs.com The Internet of Things (IoT) has become a ubiquitous term to describe the tens of billions of devices
INTRODUCTION. IoT AND IP STRATEGIES
 INTRODUCTION At first, the Internet of Things (IoT) may seem like an idea straight out of science fiction. However, on closer consideration, we realize that the process of connecting everyday electronic
INTRODUCTION At first, the Internet of Things (IoT) may seem like an idea straight out of science fiction. However, on closer consideration, we realize that the process of connecting everyday electronic
Financial Planning & Analysis The Next Frontier of Business Process Outsourcing?
 Financial Planning & Analysis The Next Frontier of Business Process Outsourcing? Financial Planning & Analysis (FP&A) outsourcing is increasingly being used by leading global firms to provide a competitive
Financial Planning & Analysis The Next Frontier of Business Process Outsourcing? Financial Planning & Analysis (FP&A) outsourcing is increasingly being used by leading global firms to provide a competitive
Robotic Process Automation Overview and RPA Case Study. November 2015
 Robotic Process Automation Overview and RPA Case Study November 2015 Big data?! Effective data management?! 2 What is Robotic Process Automation (RPA)? Software! Robots are Robots are not Computer coded
Robotic Process Automation Overview and RPA Case Study November 2015 Big data?! Effective data management?! 2 What is Robotic Process Automation (RPA)? Software! Robots are Robots are not Computer coded
Achieving Information Security
 Achieving Information Security Beyond penetration testing and frameworks ISACA Athens Conference 25 November, 2014. All good information security presentations start with a Bruce Schneier quote - Not Bruce
Achieving Information Security Beyond penetration testing and frameworks ISACA Athens Conference 25 November, 2014. All good information security presentations start with a Bruce Schneier quote - Not Bruce
The Internet of Things (IoT) Opportunities and Risks
 Session No. 744 The Internet of Things (IoT) Opportunities and Risks David Loomis, CSP Risk Specialist Chubb Group of Insurance Companies Brian Wohnsiedler, CSP Risk Specialist Chubb Group of Insurance
Session No. 744 The Internet of Things (IoT) Opportunities and Risks David Loomis, CSP Risk Specialist Chubb Group of Insurance Companies Brian Wohnsiedler, CSP Risk Specialist Chubb Group of Insurance
The Challenges of Securing the Internet of Things (IoT) at Scale
 The Challenges of Securing the Internet of Things (IoT) at Scale Ulf Lindqvist, Ph.D. Program Director, SRI International Chair, IEEE Computer Society s Technical Committee on Security and Privacy Vice
The Challenges of Securing the Internet of Things (IoT) at Scale Ulf Lindqvist, Ph.D. Program Director, SRI International Chair, IEEE Computer Society s Technical Committee on Security and Privacy Vice
The Internet of Things: Opportunities & Challenges
 The Internet of Things: Opportunities & Challenges What is the IoT? Things, people and cloud services getting connected via the Internet to enable new use cases and business models Cloud Services How is
The Internet of Things: Opportunities & Challenges What is the IoT? Things, people and cloud services getting connected via the Internet to enable new use cases and business models Cloud Services How is
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE
 AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
for Critical Infrastructure Protection Supervisory Control and Data Acquisition SCADA SECURITY ADVICE FOR CEOs
 for Critical Infrastructure Protection Supervisory Control and Data Acquisition SCADA SECURITY ADVICE FOR CEOs EXECUTIVE SUMMARY Supervisory Control and Data Acquisition (SCADA) systems are used for remote
for Critical Infrastructure Protection Supervisory Control and Data Acquisition SCADA SECURITY ADVICE FOR CEOs EXECUTIVE SUMMARY Supervisory Control and Data Acquisition (SCADA) systems are used for remote
Under control 2015 Hot topics for IT internal audit in financial services. An Internal Audit viewpoint
 Under control 2015 Hot topics for IT internal audit in financial services An Internal Audit viewpoint Introduction Welcome to our fourth annual review of the IT hot topics for IT internal audit in financial
Under control 2015 Hot topics for IT internal audit in financial services An Internal Audit viewpoint Introduction Welcome to our fourth annual review of the IT hot topics for IT internal audit in financial
Dacorum Borough Council Final Internal Audit Report
 Dacorum Borough Council Final Internal Audit Report ICT Change Management Distribution list: Chris Gordon Group Manager Neil Telkman - Information, Security and Standards Officer Gary Osler ICT Service
Dacorum Borough Council Final Internal Audit Report ICT Change Management Distribution list: Chris Gordon Group Manager Neil Telkman - Information, Security and Standards Officer Gary Osler ICT Service
Keeping sight of your business Hot topics facing Financial Services organisations in IT Internal Audit
 Keeping sight of your business Hot topics facing Financial Services organisations in IT Internal Audit 2014 Welcome to our third annual review of the IT hot topics facing Internal Audit functions within
Keeping sight of your business Hot topics facing Financial Services organisations in IT Internal Audit 2014 Welcome to our third annual review of the IT hot topics facing Internal Audit functions within
Cyber Security Evolved
 Cyber Security Evolved Aware Cyber threats are many, varied and always evolving Being aware is knowing what is going on so you can figure out what to do. The challenge is to know which cyber threats are
Cyber Security Evolved Aware Cyber threats are many, varied and always evolving Being aware is knowing what is going on so you can figure out what to do. The challenge is to know which cyber threats are
How To Deal With A Converged Threat From A Cloud And Mobile Device To A Business Or A Customer'S Computer Or Network To A Cloud Device
 Ten Tips for Managing Risks on Convergent Networks The Risk Management Group April 2012 Sponsored by: Lavastorm Analytics is a global business performance analytics company that enables companies to analyze,
Ten Tips for Managing Risks on Convergent Networks The Risk Management Group April 2012 Sponsored by: Lavastorm Analytics is a global business performance analytics company that enables companies to analyze,
Securing Industrial Control Systems Secure. Vigilant. Resilient. May 2015
 Securing Industrial Control Systems Secure. Vigilant. Resilient. May 2015 Cyber Security Securing industrial control systems: Don t be a victim of cyber-attacks Cyber security Just as the workplace is
Securing Industrial Control Systems Secure. Vigilant. Resilient. May 2015 Cyber Security Securing industrial control systems: Don t be a victim of cyber-attacks Cyber security Just as the workplace is
This session was presented by Jim Stickley of TraceSecurity on Wednesday, October 23 rd at the Cyber Security Summit.
 The hidden risks of mobile applications This session was presented by Jim Stickley of TraceSecurity on Wednesday, October 23 rd at the Cyber Security Summit. To learn more about TraceSecurity visit www.tracesecurity.com
The hidden risks of mobile applications This session was presented by Jim Stickley of TraceSecurity on Wednesday, October 23 rd at the Cyber Security Summit. To learn more about TraceSecurity visit www.tracesecurity.com
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE
 AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
AIRDEFENSE SOLUTIONS PROTECT YOUR WIRELESS NETWORK AND YOUR CRITICAL DATA SECURITY AND COMPLIANCE THE CHALLENGE: SECURE THE OPEN AIR Wirelesss communication lets you take your business wherever your customers,
Global Mobility for Professional Practices Managing a mobile workforce
 Global Mobility for Professional Practices Managing a mobile workforce Overview Global Mobility has become a prominent theme as Professional Practice Firms have expanded internationally. Their global strategies,
Global Mobility for Professional Practices Managing a mobile workforce Overview Global Mobility has become a prominent theme as Professional Practice Firms have expanded internationally. Their global strategies,
SECURITY PRACTICES FOR ADVANCED METERING INFRASTRUCTURE Elif Üstündağ Soykan, Seda Demirağ Ersöz 08.05.2014, ICSG 2014
 SECURITY PRACTICES FOR ADVANCED METERING INFRASTRUCTURE Elif Üstündağ Soykan, Seda Demirağ Ersöz 08.05.2014, ICSG 2014 Table of Contents Introduction AMI Communication Architecture Security Threats Security
SECURITY PRACTICES FOR ADVANCED METERING INFRASTRUCTURE Elif Üstündağ Soykan, Seda Demirağ Ersöz 08.05.2014, ICSG 2014 Table of Contents Introduction AMI Communication Architecture Security Threats Security
Airports and their SCADA Systems. Dr Leigh Armistead, CISSP. Peregrine Technical Solutions
 Airports and their SCADA Systems Dr Leigh Armistead, CISSP Peregrine Technical Solutions What We May Face For an attack to be successful it only has to cause disruption not loss of life to a significant
Airports and their SCADA Systems Dr Leigh Armistead, CISSP Peregrine Technical Solutions What We May Face For an attack to be successful it only has to cause disruption not loss of life to a significant
N-Dimension Solutions Cyber Security for Utilities
 AGENDA ITEM NO.: 3.A. MEETING DATE; 08/18/2014 N-Dimension Solutions Cyber Security for Utilities Cyber Security Protection for Critical Infrastructure Assets The cyber threat is escalating - Confidential
AGENDA ITEM NO.: 3.A. MEETING DATE; 08/18/2014 N-Dimension Solutions Cyber Security for Utilities Cyber Security Protection for Critical Infrastructure Assets The cyber threat is escalating - Confidential
Security Issues with Integrated Smart Buildings
 Security Issues with Integrated Smart Buildings Jim Sinopoli, Managing Principal Smart Buildings, LLC The building automation industry is now at a point where we have legitimate and reasonable concern
Security Issues with Integrated Smart Buildings Jim Sinopoli, Managing Principal Smart Buildings, LLC The building automation industry is now at a point where we have legitimate and reasonable concern
SECURITY IN THE INTERNET OF THINGS
 The Intelligence in the Internet of Things SECURITY IN THE INTERNET OF THINGS Lessons from the Past for the Connected Future By AJ Shipley, Senior Director, Security Solutions, Wind River INNOVATORS START
The Intelligence in the Internet of Things SECURITY IN THE INTERNET OF THINGS Lessons from the Past for the Connected Future By AJ Shipley, Senior Director, Security Solutions, Wind River INNOVATORS START
Salesforce.com capability. 2014 Deloitte MCS Limited. All rights reserved.
 2 4 5 Gartner: Magic Quadrant for CRM Service Providers, Worldwide, 2013 IDC: Global salesforce.com capability 2014 6 7 9 10 11 12 Basic Reporting & Analytics Inventory Campaigns Opportunities & Quotes
2 4 5 Gartner: Magic Quadrant for CRM Service Providers, Worldwide, 2013 IDC: Global salesforce.com capability 2014 6 7 9 10 11 12 Basic Reporting & Analytics Inventory Campaigns Opportunities & Quotes
Into the cybersecurity breach
 Into the cybersecurity breach Tim Sanouvong State Sector Cyber Risk Services Deloitte & Touche LLP April 3, 2015 Agenda Setting the stage Cyber risks in state governments Cyber attack vectors Preparing
Into the cybersecurity breach Tim Sanouvong State Sector Cyber Risk Services Deloitte & Touche LLP April 3, 2015 Agenda Setting the stage Cyber risks in state governments Cyber attack vectors Preparing
MOBILE SECURITY: DON T FENCE ME IN
 MOBILE SECURITY: DON T FENCE ME IN Apart from the known and the unknown, what else is there? 18 Harold Pinter, Nobel Prize-winning playwright, screenwriter, director, actor 32 INTRODUCTION AND METHODOLOGY
MOBILE SECURITY: DON T FENCE ME IN Apart from the known and the unknown, what else is there? 18 Harold Pinter, Nobel Prize-winning playwright, screenwriter, director, actor 32 INTRODUCTION AND METHODOLOGY
Cyber security. Ideal logo position here
 Cyber security Ideal logo position here Cyber security Cundall IT and audio visual Setting the scene UK construction industry Computer networks Ethical hacker Case studies Summary Final thoughts IT and
Cyber security Ideal logo position here Cyber security Cundall IT and audio visual Setting the scene UK construction industry Computer networks Ethical hacker Case studies Summary Final thoughts IT and
2015 Transit Safety Summit
 2015 Transit Safety Summit Cybersecurity In Transit Vulnerable Systems APTA Enterprise Cyber Security WG update Cyber attacks may be targeted toward one or more of the *system layers that Transit agencies
2015 Transit Safety Summit Cybersecurity In Transit Vulnerable Systems APTA Enterprise Cyber Security WG update Cyber attacks may be targeted toward one or more of the *system layers that Transit agencies
An Introduction to the Internet of Things (IoT)
 An Introduction to the Internet of Things (IoT) Part 1. of The IoT Series November 2013 Lopez Research LLC 2269 Chestnut Street #202 San Francisco, CA 94123 T (866) 849-5750 E sales@lopezresearch.com W
An Introduction to the Internet of Things (IoT) Part 1. of The IoT Series November 2013 Lopez Research LLC 2269 Chestnut Street #202 San Francisco, CA 94123 T (866) 849-5750 E sales@lopezresearch.com W
Network/Cyber Security
 Network/Cyber Security SCAMPS Annual Meeting 2015 Joe Howland,VC3 Source: http://www.information-age.com/technology/security/123458891/how-7-year-old-girl-hacked-public-wi-fi-network-10-minutes Security
Network/Cyber Security SCAMPS Annual Meeting 2015 Joe Howland,VC3 Source: http://www.information-age.com/technology/security/123458891/how-7-year-old-girl-hacked-public-wi-fi-network-10-minutes Security
The Internal Audit fraud challenge Prevention, protection, detection
 The Internal Audit fraud challenge Prevention, protection, detection Contents Introduction to survey 1 Key findings 2 What are the views of senior management? 3 Adequately resourced? 6 Current trends and
The Internal Audit fraud challenge Prevention, protection, detection Contents Introduction to survey 1 Key findings 2 What are the views of senior management? 3 Adequately resourced? 6 Current trends and
New Devices Mean New Risks: The Potential for Liability When Software is a Component of Medical Devices. September 25, 2013
 New Devices Mean New Risks: The Potential for Liability When Software is a Component of Medical Devices September 25, 2013 The Hartford Insuring Innovation Joe Coray Dan Silverman Providing insurance solutions
New Devices Mean New Risks: The Potential for Liability When Software is a Component of Medical Devices September 25, 2013 The Hartford Insuring Innovation Joe Coray Dan Silverman Providing insurance solutions
How To Be Prepared For A Cybercrime
 Cybersecurity and the Internet of Things June 2015 What is the Internet of Things? Agenda What is the Internet of Things?..2 The many and various benefits of IoT...7 The rise of the cyber threat..13 The
Cybersecurity and the Internet of Things June 2015 What is the Internet of Things? Agenda What is the Internet of Things?..2 The many and various benefits of IoT...7 The rise of the cyber threat..13 The
Understanding WiFi Security Vulnerabilities and Solutions. Dr. Hemant Chaskar Director of Technology AirTight Networks
 Understanding WiFi Security Vulnerabilities and Solutions Dr. Hemant Chaskar Director of Technology AirTight Networks WiFi Proliferation Global WiFi Radio Chipset Sales 387 307 Millions 120 200 2005 2006
Understanding WiFi Security Vulnerabilities and Solutions Dr. Hemant Chaskar Director of Technology AirTight Networks WiFi Proliferation Global WiFi Radio Chipset Sales 387 307 Millions 120 200 2005 2006
Internet of Things... Let's Not Forget Security Please!
 Internet of Things... Let's Not Forget Security Please! Distinguished Engineer Cisco @evyncke Eric Vyncke 2014 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 2014 Cisco and/or its affiliates.
Internet of Things... Let's Not Forget Security Please! Distinguished Engineer Cisco @evyncke Eric Vyncke 2014 Cisco and/or its affiliates. All rights reserved. Cisco Public 1 2014 Cisco and/or its affiliates.
WHITE PAPER Security in M2M Communication What is secure enough?
 WHITE PAPER Security in M2M Communication What is secure enough? Motivation Wireless Machine-To-Machine (M2M) communication has grown dramatically over the past decade and is still growing rapidly. In
WHITE PAPER Security in M2M Communication What is secure enough? Motivation Wireless Machine-To-Machine (M2M) communication has grown dramatically over the past decade and is still growing rapidly. In
Hands on, field experiences with BYOD. BYOD Seminar
 Hands on, field experiences with BYOD. BYOD Seminar Brussel, 25 september 2012 Agenda Challenges RIsks Strategy Before We Begin Thom Schiltmans Deloitte Risk Services Security & Privacy Amstelveen tschiltmans@deloitte.nl
Hands on, field experiences with BYOD. BYOD Seminar Brussel, 25 september 2012 Agenda Challenges RIsks Strategy Before We Begin Thom Schiltmans Deloitte Risk Services Security & Privacy Amstelveen tschiltmans@deloitte.nl
CONECTIVIDAD EN LA ERA DEL IOT THE INTERNET OF THINGS
 CONECTIVIDAD EN LA ERA DEL IOT THE INTERNET OF THINGS Didier Mora System Engineer Cisco Mayo, 2015 Converging Digital Disruptions The Nexus of Forces The 3rd Platform The Industrial Internet IoT = $1.9
CONECTIVIDAD EN LA ERA DEL IOT THE INTERNET OF THINGS Didier Mora System Engineer Cisco Mayo, 2015 Converging Digital Disruptions The Nexus of Forces The 3rd Platform The Industrial Internet IoT = $1.9
Unleashing the Power of the Internet of Things
 Gemalto M2M Make an M2M wish! Unleashing the Power of the Internet of Things Our M2M portfolio is enabling secure solutions in industries ranging from healthcare, retail services, smart energy, transportation,
Gemalto M2M Make an M2M wish! Unleashing the Power of the Internet of Things Our M2M portfolio is enabling secure solutions in industries ranging from healthcare, retail services, smart energy, transportation,
SCADA Security Training
 SCADA Security Training 1-Day Course Outline Wellington, NZ 6 th November 2015 > Version 3.1 web: www.axenic.co.nz phone: +64 21 689998 page 1 of 6 Introduction Corporate Background Axenic Ltd Since 2009,
SCADA Security Training 1-Day Course Outline Wellington, NZ 6 th November 2015 > Version 3.1 web: www.axenic.co.nz phone: +64 21 689998 page 1 of 6 Introduction Corporate Background Axenic Ltd Since 2009,
Testing the Internet of Things
 Presentation to TMF Testing the Internet of Things Test and Verification Solutions Delivering Tailored Solutions for Hardware Verification and Software Testing What is the IoT? Wikipedia The Internet of
Presentation to TMF Testing the Internet of Things Test and Verification Solutions Delivering Tailored Solutions for Hardware Verification and Software Testing What is the IoT? Wikipedia The Internet of
North Dakota 2013 IT Security Audit Vulnerability Assessment & Penetration Test Project Briefing
 North Dakota 2013 IT Security Audit Vulnerability Assessment & Penetration Test Project Briefing Introduction ManTech Project Manager Mark Shaw, Senior Executive Director Cyber Security Solutions Division
North Dakota 2013 IT Security Audit Vulnerability Assessment & Penetration Test Project Briefing Introduction ManTech Project Manager Mark Shaw, Senior Executive Director Cyber Security Solutions Division
I ve been breached! Now what?
 I ve been breached! Now what? THE AFTERMATH OF A BREACH & STEPS TO REDUCE RISK The number of data breaches in the United States in 2014 hit a record high. And 2015 is not looking any better. There have
I ve been breached! Now what? THE AFTERMATH OF A BREACH & STEPS TO REDUCE RISK The number of data breaches in the United States in 2014 hit a record high. And 2015 is not looking any better. There have
How To Understand The Power Of The Internet Of Things
 Next Internet Evolution: Getting Big Data insights from the Internet of Things Internet of things are fast becoming broadly accepted in the world of computing and they should be. Advances in Cloud computing,
Next Internet Evolution: Getting Big Data insights from the Internet of Things Internet of things are fast becoming broadly accepted in the world of computing and they should be. Advances in Cloud computing,
KASPERSKY SECURITY INTELLIGENCE SERVICES. EXPERT SERVICES. www.kaspersky.com
 KASPERSKY SECURITY INTELLIGENCE SERVICES. EXPERT SERVICES www.kaspersky.com EXPERT SERVICES Expert Services from Kaspersky Lab are exactly that the services of our in-house experts, many of them global
KASPERSKY SECURITY INTELLIGENCE SERVICES. EXPERT SERVICES www.kaspersky.com EXPERT SERVICES Expert Services from Kaspersky Lab are exactly that the services of our in-house experts, many of them global
The Internet of Things
 SIGNALS for strategists The Internet of Things THE Internet of Things concept involves connecting machines, facilities, fleets, networks, and even people to sensors and controls; feeding sensor data into
SIGNALS for strategists The Internet of Things THE Internet of Things concept involves connecting machines, facilities, fleets, networks, and even people to sensors and controls; feeding sensor data into
Robert Malmgren. Smart Grid. Security Challenges - Legacy and Infrastructure Burdens
 Robert Malmgren Smart Grid Security Challenges - Legacy and Infrastructure Burdens Short bio Robert Malmgren Independent consultant that have worked with utility companies regarding IT- and info sec since
Robert Malmgren Smart Grid Security Challenges - Legacy and Infrastructure Burdens Short bio Robert Malmgren Independent consultant that have worked with utility companies regarding IT- and info sec since
Intelligent. Buildings: Understanding and managing the security risks
 Version 2 IET Sector Insights Intelligent Buildings: Understanding and managing the security risks More efficient and cost-effective use of the built environment is increasingly being driven by economic
Version 2 IET Sector Insights Intelligent Buildings: Understanding and managing the security risks More efficient and cost-effective use of the built environment is increasingly being driven by economic
NETWORK SECURITY, REIMAGINED FPO
 FPO NETWORK SECURITY, REIMAGINED by Derek Korte AS TENS OF BILLIONS OF NEW DEVICES GET CONNECTED, BUSINESS AND SOCIETY MUST RETHINK SECURITY, PRIVACY, AND OPPORTUNITY Illustration JUSTIN GABBARD Smart
FPO NETWORK SECURITY, REIMAGINED by Derek Korte AS TENS OF BILLIONS OF NEW DEVICES GET CONNECTED, BUSINESS AND SOCIETY MUST RETHINK SECURITY, PRIVACY, AND OPPORTUNITY Illustration JUSTIN GABBARD Smart
HEALTH CARE AND CYBER SECURITY:
 HEALTH CARE AND CYBER SECURITY: Increasing Threats Require Increased Capabilities kpmg.com 1 HEALTH CARE AND CYBER SECURITY EXECUTIVE SUMMARY Four-fifths of executives at healthcare providers and payers
HEALTH CARE AND CYBER SECURITY: Increasing Threats Require Increased Capabilities kpmg.com 1 HEALTH CARE AND CYBER SECURITY EXECUTIVE SUMMARY Four-fifths of executives at healthcare providers and payers
Innovative Defense Strategies for Securing SCADA & Control Systems
 1201 Louisiana Street Suite 400 Houston, Texas 77002 Phone: 877.302.DATA Fax: 800.864.6249 Email: info@plantdata.com Innovative Defense Strategies for Securing SCADA & Control Systems By: Jonathan Pollet
1201 Louisiana Street Suite 400 Houston, Texas 77002 Phone: 877.302.DATA Fax: 800.864.6249 Email: info@plantdata.com Innovative Defense Strategies for Securing SCADA & Control Systems By: Jonathan Pollet
CYBERSECURITY & EXPECTATIONS FOR INDEPENDENT GROCERS
 October 21, 2015 CYBERSECURITY & EXPECTATIONS FOR INDEPENDENT GROCERS Cerone F. Cy Sturdivant Managing Consultant csturdivant@bkd.com 1 TO RECEIVE CPE CREDIT Participate in entire webinar Answer polls
October 21, 2015 CYBERSECURITY & EXPECTATIONS FOR INDEPENDENT GROCERS Cerone F. Cy Sturdivant Managing Consultant csturdivant@bkd.com 1 TO RECEIVE CPE CREDIT Participate in entire webinar Answer polls
PCI Compliance in Multi-Site Retail Environments
 TECHNICAL ASSESSMENT WHITE PAPER PCI Compliance in Multi-Site Retail Environments Executive Summary As an independent auditor, Coalfire seeks to be a trusted advisor to our clients. Our role is to help
TECHNICAL ASSESSMENT WHITE PAPER PCI Compliance in Multi-Site Retail Environments Executive Summary As an independent auditor, Coalfire seeks to be a trusted advisor to our clients. Our role is to help
Cloud and Critical Infrastructures how Cloud services are factored in from a risk perspective
 Cloud and Critical Infrastructures how Cloud services are factored in from a risk perspective Reaching the Cloud era in the EU Riga 16 June 2015 Jonathan Sage Government and Regulatory Affairs Cyber Security
Cloud and Critical Infrastructures how Cloud services are factored in from a risk perspective Reaching the Cloud era in the EU Riga 16 June 2015 Jonathan Sage Government and Regulatory Affairs Cyber Security
The Evolution of Data Breaches
 The Evolution of Data Breaches 2015 Data Privacy & Security Summit June 29, 2015 Mark Shelhart Incident Response & Forensics Retail Data Security recent victims The Largest Cyber Risks to your Organization
The Evolution of Data Breaches 2015 Data Privacy & Security Summit June 29, 2015 Mark Shelhart Incident Response & Forensics Retail Data Security recent victims The Largest Cyber Risks to your Organization
Security in Internet-Connected Building Automation and Energy Management Systems
 Security in Internet-Connected Building Automation and Energy Management Systems Executive Summary Thermostats, lights, meters, and sensors are joining the Internet of Things, increasing the power and
Security in Internet-Connected Building Automation and Energy Management Systems Executive Summary Thermostats, lights, meters, and sensors are joining the Internet of Things, increasing the power and
A guide to investing. Appendix 7 Raising finance
 A guide to investing in Wales Appendix 7 Raising finance August 2013 Appendix 7 Raising finance Wales benefits greatly from the prominence of the UK in the global economy. The UK has the best developed
A guide to investing in Wales Appendix 7 Raising finance August 2013 Appendix 7 Raising finance Wales benefits greatly from the prominence of the UK in the global economy. The UK has the best developed
Security and the Internet of Things (IoT)
 Security and the Internet of Things (IoT) Analysis and Recommendations for IoT Manufacturers and IT/Business Executives Wei (Weslay) Xu Tuck School of Business at Dartmouth 03/20/2015 High Level Description
Security and the Internet of Things (IoT) Analysis and Recommendations for IoT Manufacturers and IT/Business Executives Wei (Weslay) Xu Tuck School of Business at Dartmouth 03/20/2015 High Level Description
Mitigating Bring Your Own Device (BYOD) Risk for Organisations
 Mitigating Bring Your Own Device (BYOD) Risk for Organisations Harness the benefits and mitigate the risks of BYOD espiongroup.com Executive Summary Mobile devices such as smart phones, tablets, or laptops
Mitigating Bring Your Own Device (BYOD) Risk for Organisations Harness the benefits and mitigate the risks of BYOD espiongroup.com Executive Summary Mobile devices such as smart phones, tablets, or laptops
 01/ 02/ 03/ 04/ 05/ Beyond borders Deloitte Discovery April 23 rd 2015 Cyprus 1 Going beyond borders to move our clients ahead Deloitte Discovery Services - Deloitte Legal 2 The Deloitte
01/ 02/ 03/ 04/ 05/ Beyond borders Deloitte Discovery April 23 rd 2015 Cyprus 1 Going beyond borders to move our clients ahead Deloitte Discovery Services - Deloitte Legal 2 The Deloitte
The President s Critical Infrastructure Protection Board. Office of Energy Assurance U.S. Department of Energy 202/ 287-1808
 cover_comp_01 9/9/02 5:01 PM Page 1 For further information, please contact: The President s Critical Infrastructure Protection Board Office of Energy Assurance U.S. Department of Energy 202/ 287-1808
cover_comp_01 9/9/02 5:01 PM Page 1 For further information, please contact: The President s Critical Infrastructure Protection Board Office of Energy Assurance U.S. Department of Energy 202/ 287-1808
Deloitte Shared Services, GBS & BPO Conference SMAC / Enabling Technologies and Shared Services in the Public Sector
 Deloitte Shared Services, GBS & BPO Conference SMAC / Enabling Technologies and Shared Services in the Public Sector Carolyn Williamson, Hampshire County Council; David Harker, Deloitte 22 23 September
Deloitte Shared Services, GBS & BPO Conference SMAC / Enabling Technologies and Shared Services in the Public Sector Carolyn Williamson, Hampshire County Council; David Harker, Deloitte 22 23 September
Connected Intelligence and the 21 st Century Digital Enterprise
 Connected Intelligence and the 21 st Century Digital Enterprise Lewis Carr Senior Director, HP Software May 25 th, 2015 By 2025 we will become a deeply connected, digital world Digital everything everywhere,
Connected Intelligence and the 21 st Century Digital Enterprise Lewis Carr Senior Director, HP Software May 25 th, 2015 By 2025 we will become a deeply connected, digital world Digital everything everywhere,
IoT Security & Privacy
 Page 1: IoT Security & Privacy Technical White Paper June 2015 Page 2: Table of Contents The IoT ecosystem 3 A gold rush 3 Two major issues need to be overcome: Usability and Security 4 A centralised IoT
Page 1: IoT Security & Privacy Technical White Paper June 2015 Page 2: Table of Contents The IoT ecosystem 3 A gold rush 3 Two major issues need to be overcome: Usability and Security 4 A centralised IoT
Connecting things. Creating possibilities. A point of view
 Connecting things. Creating possibilities. A point of view Is the next technological revolution already here? The Internet of Things is already transforming our daily lives, our health, education and businesses.
Connecting things. Creating possibilities. A point of view Is the next technological revolution already here? The Internet of Things is already transforming our daily lives, our health, education and businesses.
PKI: THE SECURITY SOLUTION FOR THE INTERNET OF THINGS
 PKI: THE SECURITY SOLUTION FOR THE INTERNET OF THINGS TABLE OF CONTENTS 2 EXECUTIVE SUMMARY 3 THE EMERGENCE OF THE INTERNET OF THINGS 4 SECURITY RISKS IN NETWORKED DEVICES 6 PKI S FOUNDATION OF STRONG
PKI: THE SECURITY SOLUTION FOR THE INTERNET OF THINGS TABLE OF CONTENTS 2 EXECUTIVE SUMMARY 3 THE EMERGENCE OF THE INTERNET OF THINGS 4 SECURITY RISKS IN NETWORKED DEVICES 6 PKI S FOUNDATION OF STRONG
Deloitte. Summary of the Independent Expert review of proposed amendments to Standard Life Scheme of Demutualisation.
 Deloitte. Summary of the Independent Expert review of proposed amendments to Standard Life Scheme of Demutualisation 27 April 216 ( Introduction The purpose of this document is to provide policyholders,
Deloitte. Summary of the Independent Expert review of proposed amendments to Standard Life Scheme of Demutualisation 27 April 216 ( Introduction The purpose of this document is to provide policyholders,
Rethinking Cyber Security for the 21 st Century. Ira A. (Gus) Hunt Senior Operating Advisor LLR Partners
 Rethinking Cyber Security for the 21 st Century Ira A. (Gus) Hunt Senior Operating Advisor LLR Partners 12 Months of Cyber Attacks A Sampler Putting it in Perspective US Cyber Crime Cost: ~$100-120B/year
Rethinking Cyber Security for the 21 st Century Ira A. (Gus) Hunt Senior Operating Advisor LLR Partners 12 Months of Cyber Attacks A Sampler Putting it in Perspective US Cyber Crime Cost: ~$100-120B/year
Cybersecurity. Are you prepared?
 Cybersecurity Are you prepared? First Cash, then your customer, now YOU! What is Cybersecurity? The body of technologies, processes, practices designed to protect networks, computers, programs, and data
Cybersecurity Are you prepared? First Cash, then your customer, now YOU! What is Cybersecurity? The body of technologies, processes, practices designed to protect networks, computers, programs, and data
What is Quantified Self (QS)?
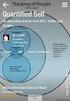 Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
Subtitle Title Content Quantified Self (QS) (Sensitive) Personal data Security risks QS Privacy risks QS Art. 29 Working Party (WP29) on QS WP29 on ehealth WP29 on Internet of Things (IoT) QS data at risk
A guide to investing. Appendix 11 Protecting your business intellectual property rights
 A guide to investing in Wales Appendix 11 Protecting your business intellectual property rights August 2013 Appendix 11 Protecting your business intellectual property rights Intellectual property rights
A guide to investing in Wales Appendix 11 Protecting your business intellectual property rights August 2013 Appendix 11 Protecting your business intellectual property rights Intellectual property rights
Smart (and safe) Lighting:
 Smart (and safe) Lighting: An Overview of Cyber Security October 29, 2015 Jason Brown CISO, Merit Network Agenda 2 The New Normal Discuss Methodologies of Security Recap Q & A Target Hack 3 40,000 credit
Smart (and safe) Lighting: An Overview of Cyber Security October 29, 2015 Jason Brown CISO, Merit Network Agenda 2 The New Normal Discuss Methodologies of Security Recap Q & A Target Hack 3 40,000 credit
CLOUD BASED SCADA. Removing Implementation and Deployment Barriers. Liam Kearns Open Systems International, Inc.
 CLOUD BASED SCADA Removing Implementation and Deployment Barriers Liam Kearns Open Systems International, Inc. SCADA Traditional definition and application. SCADA DEFINITION Definition Supervisory Control
CLOUD BASED SCADA Removing Implementation and Deployment Barriers Liam Kearns Open Systems International, Inc. SCADA Traditional definition and application. SCADA DEFINITION Definition Supervisory Control
Threat Intelligence Pty Ltd info@threatintelligence.com 1300 809 437. Specialist Security Training Catalogue
 Threat Intelligence Pty Ltd info@threatintelligence.com 1300 809 437 Specialist Security Training Catalogue Did you know that the faster you detect a security breach, the lesser the impact to the organisation?
Threat Intelligence Pty Ltd info@threatintelligence.com 1300 809 437 Specialist Security Training Catalogue Did you know that the faster you detect a security breach, the lesser the impact to the organisation?
CONTENTS. Introduction 3. IoT- the next evolution of the internet..3. IoT today and its importance..4. Emerging opportunities of IoT 5
 #924, 5 A The catchy phrase Internet of Things (IoT) or the Web of Things has become inevitable to the modern world. Today wireless technology has reached its zenith making it possible to interact with
#924, 5 A The catchy phrase Internet of Things (IoT) or the Web of Things has become inevitable to the modern world. Today wireless technology has reached its zenith making it possible to interact with
SECURITY IN THE INTERNET OF THINGS
 Lessons from the Past for the Connected Future INNOVATORS START HERE. EXECUTIVE SUMMARY Although it has been with us in some form and under different names for many years, the Internet of Things (IoT)
Lessons from the Past for the Connected Future INNOVATORS START HERE. EXECUTIVE SUMMARY Although it has been with us in some form and under different names for many years, the Internet of Things (IoT)
Understanding SCADA System Security Vulnerabilities
 Understanding SCADA System Security Vulnerabilities Talking Points Executive Summary Common Misconceptions about SCADA System Security Common Vulnerabilities Affecting SCADA Networks Tactics to Strengthen
Understanding SCADA System Security Vulnerabilities Talking Points Executive Summary Common Misconceptions about SCADA System Security Common Vulnerabilities Affecting SCADA Networks Tactics to Strengthen
The Importance of Cybersecurity Monitoring for Utilities
 The Importance of Cybersecurity Monitoring for Utilities www.n-dimension.com Cybersecurity threats against energy companies, including utilities, have been increasing at an alarming rate. A comprehensive
The Importance of Cybersecurity Monitoring for Utilities www.n-dimension.com Cybersecurity threats against energy companies, including utilities, have been increasing at an alarming rate. A comprehensive
SOUTH NORTHAMPTONSHIRE COUNCIL 10/11 REMOTE WORKING FINAL REPORT MARCH 2011
 SOUTH NORTHAMPTONSHIRE COUNCIL 10/11 REMOTE WORKING FINAL REPORT MARCH 2011 This report and the work connected therewith are subject to the Terms and Conditions of the contract dated 18/06/07 between South
SOUTH NORTHAMPTONSHIRE COUNCIL 10/11 REMOTE WORKING FINAL REPORT MARCH 2011 This report and the work connected therewith are subject to the Terms and Conditions of the contract dated 18/06/07 between South
Emerging SCADA and Security Solutions Presented by; Michael F. Graves, P.E. Chris Murphy, CISSP
 Emerging SCADA and Security Solutions Presented by; Michael F. Graves, P.E. Chris Murphy, CISSP July 25, 2014 Topics Improved 4G Communications Mobile Devices Cyber Security Threats Cyber Security Guidance
Emerging SCADA and Security Solutions Presented by; Michael F. Graves, P.E. Chris Murphy, CISSP July 25, 2014 Topics Improved 4G Communications Mobile Devices Cyber Security Threats Cyber Security Guidance
Hong Kong Information Security Outlook 2015 香 港 資 訊 保 安 展 望
 Hong Kong Information Security Outlook 2015 香 港 資 訊 保 安 展 望 Agenda Information Security Trends Year 2014 in Review Outlook for 2015 Advice to the Public Hong Kong Computer Emergency Response Team Coordination
Hong Kong Information Security Outlook 2015 香 港 資 訊 保 安 展 望 Agenda Information Security Trends Year 2014 in Review Outlook for 2015 Advice to the Public Hong Kong Computer Emergency Response Team Coordination
Critical Controls for Cyber Security. www.infogistic.com
 Critical Controls for Cyber Security www.infogistic.com Understanding Risk Asset Threat Vulnerability Managing Risks Systematic Approach for Managing Risks Identify, characterize threats Assess the vulnerability
Critical Controls for Cyber Security www.infogistic.com Understanding Risk Asset Threat Vulnerability Managing Risks Systematic Approach for Managing Risks Identify, characterize threats Assess the vulnerability
The Internet of Things (IoT) and Industrial Networks. Guy Denis gudenis@cisco.com Rockwell Automation Alliance Manager Europe 2015
 The Internet of Things (IoT) and Industrial Networks Guy Denis gudenis@cisco.com Rockwell Automation Alliance Manager Europe 2015 Increasingly Everything will be interconnected 50 Billion Smart Objects
The Internet of Things (IoT) and Industrial Networks Guy Denis gudenis@cisco.com Rockwell Automation Alliance Manager Europe 2015 Increasingly Everything will be interconnected 50 Billion Smart Objects
Frost & Sullivan s. Aerospace, Defence & Security Practice. Global Industrial Cyber Security Trends
 Frost & Sullivan s Aerospace, Defence & Security Practice Global Industrial Cyber Security Trends Presented by Philipp Reuter Director Frost & Sullivan, Turkey 1 Worth over $ 50 Billion globally in 2014
Frost & Sullivan s Aerospace, Defence & Security Practice Global Industrial Cyber Security Trends Presented by Philipp Reuter Director Frost & Sullivan, Turkey 1 Worth over $ 50 Billion globally in 2014
Network Security in Building Networks
 Network Security in Building Networks Prof. Dr. (TU NN) Norbert Pohlmann Institute for Internet Security - if(is) Westphalian University of Applied Sciences Gelsenkirchen, Germany www.if-is.net Content
Network Security in Building Networks Prof. Dr. (TU NN) Norbert Pohlmann Institute for Internet Security - if(is) Westphalian University of Applied Sciences Gelsenkirchen, Germany www.if-is.net Content
Enhanced Portfolio Management in uncertain times
 Enhanced Portfolio Management in uncertain times How businesses can generate and protect value through enhanced, risk return techniques improving portfolio and capital allocation decisions Contents Executive
Enhanced Portfolio Management in uncertain times How businesses can generate and protect value through enhanced, risk return techniques improving portfolio and capital allocation decisions Contents Executive
1. Fault Attacks for Virtual Machines in Embedded Platforms. Supervisor: Dr Konstantinos Markantonakis, K.Markantonakis@rhul.ac.uk
 Proposed PhD Research Areas I am looking for strong PhD candidates to work on the projects listed below. The ideal candidate would have a mix of theoretical and practical skills, achieved a distinction
Proposed PhD Research Areas I am looking for strong PhD candidates to work on the projects listed below. The ideal candidate would have a mix of theoretical and practical skills, achieved a distinction
Cybersecurity and internal audit. August 15, 2014
 Cybersecurity and internal audit August 15, 2014 arket insights: what we are seeing so far? 60% of organizations see increased risk from using social networking, cloud computing and personal mobile devices
Cybersecurity and internal audit August 15, 2014 arket insights: what we are seeing so far? 60% of organizations see increased risk from using social networking, cloud computing and personal mobile devices
G- Cloud Specialist Cloud Services. Security and Penetration Testing. Overview
 Description C Service Overview G- Cloud Specialist Cloud Services Security and Penetration Testing This document provides a description of TVS s Security and Penetration Testing Service offered under the
Description C Service Overview G- Cloud Specialist Cloud Services Security and Penetration Testing This document provides a description of TVS s Security and Penetration Testing Service offered under the
It Won t Happen To Me! A Network and PCI Security Webinar Presented By FMS and VendorSafe
 It Won t Happen To Me! A Network and PCI Security Webinar Presented By FMS and VendorSafe Agenda Who Is VendorSafe Technologies? It Won t Happen to Me! PCI DSS Overview The VendorSafe Solution Questions
It Won t Happen To Me! A Network and PCI Security Webinar Presented By FMS and VendorSafe Agenda Who Is VendorSafe Technologies? It Won t Happen to Me! PCI DSS Overview The VendorSafe Solution Questions
Transforming customer management in the water sector How to become a leader in customer service
 Transforming customer management in the water sector How to become a leader in customer service management strategies have always been important to water companies, with a focus on resolving issues first
Transforming customer management in the water sector How to become a leader in customer service management strategies have always been important to water companies, with a focus on resolving issues first
