A Study on IP Exposure Notification System for IoT Devices Using IP Search Engine Shodan
|
|
|
- Rosalind Wood
- 10 years ago
- Views:
Transcription
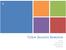
1 , pp A Study on IP Exposure Notification System for IoT Devices Using IP Search Engine Shodan Yun-Seong Ko 1, Il-Kyeun Ra 2 and Chang-Soo Kim 1* 1 Department of IT Convergence and Application Engineering, Pukyong National University, Busan, , Korea 2 Department of Computer Science and Engineering, University of Colorado Denver, Denver, CO 80203, United States of America [[email protected], [email protected], *[email protected]] Abstract As times become increasingly digitized and the importance of IoT_(Internet of Things) technology still growing, the number of IP-based IoT devices is also sharply increasing. This has the advantage of improving the quality of life because by increasing the numbers of IoT devices, but IP-related security threats are also increasing together while the system for preventing these threats is insufficient. In this paper, we study the IP exposure notification system for IoT devices using IP search engine Shodan. First, we study the keywords to search the IP address of IoT devices. After that, we output the result file about those keywords using Shodan API. Finally, we develop a web-based IP exposure notification system for IoT devices using the output file and Google Map API. In the future, we can develop our system combining this study and the IP exposure threat level. It can also prevent the threat of countries or public institutions. Keywords: IoT (Internet of Things), IP Address, IP Search Engine Shodan, IP Exposure, Google Map 1. Introduction As times become digitized and the IT technology is fused to devices, the number of IPbased IoT (Internet of Things) devices is sharply increasing. IoT is a promising technology that expected the economic effect of 1.9 trillion dollars and a market creation of 300 billion dollars. Development of IoT technology helps make life more convenient and increases national competitiveness, but it can also increase security threats of IP exposure at the same time. We can be threatened by invasion of privacy and system hacking of public organization. We can also be threatened by data leakage, data forgery/tampering, camera hacking, DoS (Denial of Service) attack, backdoors, etc. [1-4]. It is urgent that a countermeasure to these threats be created. In this paper, we study an IP exposure notification system for IoT devices using IP search engine Shodan. First, we study the keyword for gathering IoT devices information. After that, we search the IP address and some other information using that keyword, and output the results to XML file. Finally, we develop an IP exposure notification system using the extracted data and Google Map API. It displays how many exposed IoT devices exist in a certain area. Figure 1 shows the system diagram. * Corresponding Author ISSN: IJMUE Copyright c 2015 SERSC
2 2. Related Research 2.1. Internet of Things (IoT) Figure 1. System Diagram IoT is the network of physical objects or things embedded with electronics, software, sensors, and connectivity to enable it to achieve greater value and service by exchanging data with the manufacturer, operator and/or other connected devices based on the infrastructure of International Telecommunication Union s Global Standards Initiative. IoT allows objects to be sensed and controlled remotely across existing network infrastructure, creating opportunities for a more direct integration between the physical world and computer-based systems, and resulting in improved efficiency, accuracy and economic benefit. Each thing is uniquely identifiable through its embedded computing system but is able to interoperate within the existing Internet infrastructure. Experts estimate that the IoT will consist of almost 50 billion objects by IoT devices are used in various cases. It used in Smart Home System, Wearable Devices, Smart Car Devices, Living in Close Contact Devices, Smart Energy Devices, Industrial and Environmental Devices, etc. [5-7] IP Search Engine Shodan Shodan provides searching data for IP addresses and some other information. Although there are a lot of search engines nowadays, Shodan is the most powerful search engine as of now. Shodan lets the user find specific types of computers connected to the Internet using a variety of filters. Some have also described it as a search engine of service banners, which are meta-data that the server sends back to the client. This can be information about the server software, what options the service supports, a welcome message or anything else that the client can find out before interacting with the server. The Shodan IP search engine is designed to crawl the Internet and attempt to identify and index connected devices. Shodan engine collects more than 500 million IoT devices in one month. It also collects data mostly on web servers at the moment (HTTP port 80), but 62 Copyright c 2015 SERSC
3 there are also some data from FTP (21), SSH (22), Telnet (23), SNMP (161) and SIP (5060) services. Using Shodan, researchers identified thousands of Internet-facing devices associated with industrial controls system [8-9]. 3. Gathering Information from IoT Devices Using IP Search Engine Shodan 3.1. The Kinds of Information Provided by the IP Search Engine The kinds of information that can be provided by Shodan search engine can be divided into two types. The first one is provided by the web page, and last one is provided by script console using IP search engine API. First, information provided by the web page has only basic data such as IP address, connected country, connected city, server name. But information provided by script console has more useful data than web pages such as port number, affiliation, latitude/longitude including the data of the web page. We compare the two types of this information in Figure 2. Figure 2. Compare Information between Web Page and Script API Because information provided by web page can get only fragmentary data, it is difficult to use in this study. Information provided by script console can also get many useful data such as location information or port number, which makes it appropriate for use in our study. Also, it is appropriate to produce output using script programming, so we use script API for gathering information A Module Gathering Information from IoT Devices with Python The script API of Shodan, an IP search engine, is used in three ways. The first way is using Python Language, the second way is using Ruby Language, and the final way is using Node.js Language. We use \ Python Language in order to take advantage of the result file variously because it s very useful and makes it easy to interact on the web. In order to use Shodan API in Python, we purchased a Shodan license and input a license key to Python script. After that, we specified the XML file s attributes to make a basic form of XML file. Then we input the query string, and we ran the query to get result data. Copyright c 2015 SERSC 63
4 After we entered the information of IP address in the <IoT> tag in XML file, creates a XML file finally. Figure 3 is the contests of the resulting XML file. Many <IoT> tags are contained in <Shodan> tag, and <IP>, <PORT>, <LAT>, <LNG>, <CNTRY> tags are contained in each <IoT> tag. <IP> tag is information about IP address, <PORT> tag is information about port number, <LAT> tag is information about latitude, <LNG> tag is information about longitude, and <CNTRY> tag is information about country. Figure 3. Result XML File 4. Developing an IP Exposure Notification System Using Information from IoT Devices and Google Map API In order to develop the IP exposure notification system, we express information of the exposed IoT devices on Google Map using the resulting XML file as input. First, we enter the five attributes stored in the resulting XML file to array list. Information of IP address, port number, latitude, longitude, country is input into individual array. After that, we use this individual array in order to objectify the exposed IoT devices information. Table 1 is a configuration of that object. It has five attributes from Shodan API, which are IP Address, Port Number, Latitude, Longitude, and Country. Table 1. Object of Exposed IoT Devices Information No. Attribute Type Description 1 IP Address String Exposed IoT device s IP address 2 Port Number Integer Exposed IoT device s port number 3 Latitude Float It is used for marking latitude in Google Map 4 Longitude Float It is used for marking longitude in Google Map 5 Country String Exposed IoT device s country 64 Copyright c 2015 SERSC
5 Using the latitude and longitude attributes of that object, we marked information of this object on Google Maps. Because of these marks that indicate the information on Google Maps, we can see how many IP exposures are within a certain area. If public authorities take advantage of that, they can be used as a way to warn that IP exposure is dangerous to that area. Because we also display their information, they will know which IoT devices are dangerous to exposure. Figure 4 is the result of executing this system. Figure 4. Execution Window of the IP Exposure Notification System 5. Discussion and Conclusion Security threats posed by IP exposure of IoT devices have been appearing more often. Although large and small security threats such as hacking of personal web camera or national IP-based CCTVs are affecting our lives, the study for a system that radically prevents exposure of IP is still insufficient. It will become a major security threat of IoT devices. In this paper, we studied an IP exposure notification system for prevent this threats. Through this study, we confirmed how many IP address are being exposed to the Internet, and we could see that access to the system with the exposed IP can be easily done. Because most of the exposed IP-based IoT devices can be easily accessed through their IP address and port number, it would be a big threat for IoT devices in the future. In the future, integrated security management systems combined with IP exposure notification systems and IP exposure levels can be studied. Through this system, we can search the exposed IP address and estimate the IP exposure level to each IP address. Then we can measure the degree of risk of the IP exposure. Also, if you use this system in state institutions, you can reduce the threat in accordance with IP exposure ranging from personal to national. Copyright c 2015 SERSC 65
6 References [1] Y. H. Kim, J. G. Yang and H. B. Kim, Trends and Threats of M2M/IoT, Journal of Information Security, vol. 24, no. 6, (2014). [2] I. S. Lee, H. S. Kim and W. S. Yi, u-city service information security threats and protective measures, Journal of the Korea Institute of Information Security, vol. 18, no. 2, (2008), pp [3] H. W. Kim, Security/Privacy Issues in the IoT Environment, TTA Journal, (2014) [4] D. H. Kim, S. W. Yoon and Y. P. Lee, Security for IoT Services, Journal of the Korean Communication(Information and Communication), vol. 30, no. 8, (2013), pp [5] J. A. Jeon, N. S. Kim, J. K. Ko, T. J. Park, H. Y. Kang and C. S. Pyo, IoT Devices Products and Technology Trends, Journal of The Korean Institute of Communication Sciences, vol. 31, no. 4, (2014), pp [6] Wikipedia: Internet of Things. [7] S. Husain, A. Prasad, A. Kunz, A. Papageorgiou and J. S. Song, Recent Trends in Standards Related to the Internet of Things and Machine-to-Machine Communications, Journal of Information and Communication Convergence Engineering, vol. 12, no. 4, (2014), pp [8] Wikipedia: Shodan. [9] R. Bodenheim, J. Butts, S. Dunlap and B; Mullins, Evaluation of the ability of the Shodan search engine to identify Internet-facing industrial control devices, International Journal of Critical Infrastructure Protection, vol. 7, no. 2, (2014), pp Authors Yun-Seong Ko, He received his B.S. degree in Computer Multimedia Engineering from Pukyong National University, Korea in He is in a master course in Pukyong National University. His current research interests are disaster prevention, Internet of Things, Cloud Service, GIS and u-prevention system. Il-Kyeun Ra, He holds a Ph.D. degree in Computer and Information Science from Syracuse University in 2001, a M.S. degree in Computer Science from University of Colorado Boulder, and B.S. degree and M.S. degree in Computer Science from Sogang University. He was a Research Staff Member at the LG Information and Communications Research Center. He joined the department of Computer Science and Engineering at the University of Colorado Denver His main research interests include computer networks, developing adaptive distributed system software and high speed communication system software to support High Performance Distributed Computing Applications. Chang-Soo Kim, He received a B.S degree in Computer Science from Ulsan University, Korea, in 1979, and a M.S. degree in Computer Engineering and Ph.D. degree in Computer Engineering from Chungang University, Korea, in 1984 and 1991 respectively. He has been a professor at the department of IT Convergence and Application Engineering, Pukyong National University, Korea, since His research interests are operation system, LBS/GIS, WSN and urban disaster prevention system. 66 Copyright c 2015 SERSC
Security Threats on National Defense ICT based on IoT
 , pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
, pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
A Survey on Security Threats and Security Technology Analysis for Secured Cloud Services
 , pp.21-30 http://dx.doi.org/10.14257/ijsia.2013.7.6.03 A Survey on Security Threats and Security Technology Analysis for Secured Cloud Services Changsoo Lee 1, Daewon Jung 2 and Keunwang Lee 3 1 Dept.
, pp.21-30 http://dx.doi.org/10.14257/ijsia.2013.7.6.03 A Survey on Security Threats and Security Technology Analysis for Secured Cloud Services Changsoo Lee 1, Daewon Jung 2 and Keunwang Lee 3 1 Dept.
A Study of Key management Protocol for Secure Communication in Personal Cloud Environment
 , pp.51-58 http://dx.doi.org/10.14257/ijsia.2014.8.4.05 A Study of Key management Protocol for Secure Communication in Personal Cloud Environment ByungWook Jin 1 and Keun-Wang Lee 2,* 1 Dept. of Computer
, pp.51-58 http://dx.doi.org/10.14257/ijsia.2014.8.4.05 A Study of Key management Protocol for Secure Communication in Personal Cloud Environment ByungWook Jin 1 and Keun-Wang Lee 2,* 1 Dept. of Computer
The Design and Implementation of the Integrated Model of the Advertisement and Remote Control System for an Elevator
 Vol.8, No.3 (2014), pp.107-118 http://dx.doi.org/10.14257/ijsh.2014.8.3.10 The Design and Implementation of the Integrated Model of the Advertisement and Remote Control System for an Elevator Woon-Yong
Vol.8, No.3 (2014), pp.107-118 http://dx.doi.org/10.14257/ijsh.2014.8.3.10 The Design and Implementation of the Integrated Model of the Advertisement and Remote Control System for an Elevator Woon-Yong
A Research on Security Awareness and Countermeasures for the Single Server
 , pp.31-42 http://dx.doi.org/10.14257/ijsia.2013.7.6.04 A Research on Security Awareness and Countermeasures for the Single Server Hyuk-Jin Son 1 and Seungdo Jeong 2,* 1 IT MBA, Graduate School of Business
, pp.31-42 http://dx.doi.org/10.14257/ijsia.2013.7.6.04 A Research on Security Awareness and Countermeasures for the Single Server Hyuk-Jin Son 1 and Seungdo Jeong 2,* 1 IT MBA, Graduate School of Business
MIS 510: Cyber Analytics Project
 MIS 510: Cyber Analytics Project Team: Never Off Guard SUMEET BHATIA AADIL HUSSAINI SNEHAL NAVALAKHA MO ZHOU 1 Table of Contents Introduction... 2 Hacker Web... 3 Data Collection... 3 Research Question
MIS 510: Cyber Analytics Project Team: Never Off Guard SUMEET BHATIA AADIL HUSSAINI SNEHAL NAVALAKHA MO ZHOU 1 Table of Contents Introduction... 2 Hacker Web... 3 Data Collection... 3 Research Question
Studying Security Weaknesses of Android System
 , pp. 7-12 http://dx.doi.org/10.14257/ijsia.2015.9.3.02 Studying Security Weaknesses of Android System Jae-Kyung Park* and Sang-Yong Choi** *Chief researcher at Cyber Security Research Center, Korea Advanced
, pp. 7-12 http://dx.doi.org/10.14257/ijsia.2015.9.3.02 Studying Security Weaknesses of Android System Jae-Kyung Park* and Sang-Yong Choi** *Chief researcher at Cyber Security Research Center, Korea Advanced
Cyber Security Analytics. Su Zhao Yuan-Jen Lee Ching-Tang Lin Yufeng Mao
 + Cyber Security Analytics Su Zhao Yuan-Jen Lee Ching-Tang Lin Yufeng Mao + How to prevent unauthorized users to access modems? Question 1 + Introduction to SHODAN SHODAN is a search engine which can assist
+ Cyber Security Analytics Su Zhao Yuan-Jen Lee Ching-Tang Lin Yufeng Mao + How to prevent unauthorized users to access modems? Question 1 + Introduction to SHODAN SHODAN is a search engine which can assist
Smart Integrated Multiple Tracking System Development for IOT based Target-oriented Logistics Location and Resource Service
 , pp. 195-204 http://dx.doi.org/10.14257/ijsh.2015.9.5.19 Smart Integrated Multiple Tracking System Development for IOT based Target-oriented Logistics Location and Resource Service Ju-Su Kim, Hak-Jun
, pp. 195-204 http://dx.doi.org/10.14257/ijsh.2015.9.5.19 Smart Integrated Multiple Tracking System Development for IOT based Target-oriented Logistics Location and Resource Service Ju-Su Kim, Hak-Jun
Big Data Collection Study for Providing Efficient Information
 , pp. 41-50 http://dx.doi.org/10.14257/ijseia.2015.9.12.03 Big Data Collection Study for Providing Efficient Information Jun-soo Yun, Jin-tae Park, Hyun-seo Hwang and Il-young Moon Computer Science and
, pp. 41-50 http://dx.doi.org/10.14257/ijseia.2015.9.12.03 Big Data Collection Study for Providing Efficient Information Jun-soo Yun, Jin-tae Park, Hyun-seo Hwang and Il-young Moon Computer Science and
A Study on HL7 Standard Message for Healthcare System Based on ISO/IEEE 11073
 , pp. 113-118 http://dx.doi.org/10.14257/ijsh.2015.9.6.13 A Study on HL7 Standard Message for Healthcare System Based on ISO/IEEE 11073 Am-Suk Oh Dept. of Media Engineering, Tongmyong University, Busan,
, pp. 113-118 http://dx.doi.org/10.14257/ijsh.2015.9.6.13 A Study on HL7 Standard Message for Healthcare System Based on ISO/IEEE 11073 Am-Suk Oh Dept. of Media Engineering, Tongmyong University, Busan,
The Development of an Intellectual Tracking App System based on IoT and RTLS
 , pp.9-13 http://dx.doi.org/10.14257/astl.2015.85.03 The Development of an Intellectual Tracking App System based on IoT and RTLS Hak-Jun Lee 1, Ju-Su Kim 1, Umarov Jamshid 1, Man-Kyo Han 2, Ryum-Duck
, pp.9-13 http://dx.doi.org/10.14257/astl.2015.85.03 The Development of an Intellectual Tracking App System based on IoT and RTLS Hak-Jun Lee 1, Ju-Su Kim 1, Umarov Jamshid 1, Man-Kyo Han 2, Ryum-Duck
Designing and Embodiment of Software that Creates Middle Ware for Resource Management in Embedded System
 , pp.97-108 http://dx.doi.org/10.14257/ijseia.2014.8.6.08 Designing and Embodiment of Software that Creates Middle Ware for Resource Management in Embedded System Suk Hwan Moon and Cheol sick Lee Department
, pp.97-108 http://dx.doi.org/10.14257/ijseia.2014.8.6.08 Designing and Embodiment of Software that Creates Middle Ware for Resource Management in Embedded System Suk Hwan Moon and Cheol sick Lee Department
A Digital Door Lock System for the Internet of Things with Improved Security and Usability
 , pp.33-38 http://dx.doi.org/10.14257/astl.2015.109.08 A Digital Door Lock System for the Internet of Things with Improved Security and Usability Ohsung Doh 1, Ilkyu Ha 1 1 Kyungil University, Gyeongsan,
, pp.33-38 http://dx.doi.org/10.14257/astl.2015.109.08 A Digital Door Lock System for the Internet of Things with Improved Security and Usability Ohsung Doh 1, Ilkyu Ha 1 1 Kyungil University, Gyeongsan,
A Study on Integrated Operation of Monitoring Systems using a Water Management Scenario
 , pp. 55-64 http://dx.doi.org/10.14257/ijseia.2015.9.9.06 A Study on Integrated Operation of Monitoring Systems using a Water Management Scenario Yong-Hyeon Gwon 1, Seung-Kwon Jung 2, Su-Won Lee 2 and
, pp. 55-64 http://dx.doi.org/10.14257/ijseia.2015.9.9.06 A Study on Integrated Operation of Monitoring Systems using a Water Management Scenario Yong-Hyeon Gwon 1, Seung-Kwon Jung 2, Su-Won Lee 2 and
Development of Integrated Management System based on Mobile and Cloud Service for Preventing Various Hazards
 , pp. 143-150 http://dx.doi.org/10.14257/ijseia.2015.9.7.15 Development of Integrated Management System based on Mobile and Cloud Service for Preventing Various Hazards Ryu HyunKi 1, Yeo ChangSub 1, Jeonghyun
, pp. 143-150 http://dx.doi.org/10.14257/ijseia.2015.9.7.15 Development of Integrated Management System based on Mobile and Cloud Service for Preventing Various Hazards Ryu HyunKi 1, Yeo ChangSub 1, Jeonghyun
Crime Hotspots Analysis in South Korea: A User-Oriented Approach
 , pp.81-85 http://dx.doi.org/10.14257/astl.2014.52.14 Crime Hotspots Analysis in South Korea: A User-Oriented Approach Aziz Nasridinov 1 and Young-Ho Park 2 * 1 School of Computer Engineering, Dongguk
, pp.81-85 http://dx.doi.org/10.14257/astl.2014.52.14 Crime Hotspots Analysis in South Korea: A User-Oriented Approach Aziz Nasridinov 1 and Young-Ho Park 2 * 1 School of Computer Engineering, Dongguk
Multi-level Metadata Management Scheme for Cloud Storage System
 , pp.231-240 http://dx.doi.org/10.14257/ijmue.2014.9.1.22 Multi-level Metadata Management Scheme for Cloud Storage System Jin San Kong 1, Min Ja Kim 2, Wan Yeon Lee 3, Chuck Yoo 2 and Young Woong Ko 1
, pp.231-240 http://dx.doi.org/10.14257/ijmue.2014.9.1.22 Multi-level Metadata Management Scheme for Cloud Storage System Jin San Kong 1, Min Ja Kim 2, Wan Yeon Lee 3, Chuck Yoo 2 and Young Woong Ko 1
Development of Integrated Management System based on Mobile and Cloud service for preventing various dangerous situations
 Development of Integrated Management System based on Mobile and Cloud service for preventing various dangerous situations Ryu HyunKi, Moon ChangSoo, Yeo ChangSub, and Lee HaengSuk Abstract In this paper,
Development of Integrated Management System based on Mobile and Cloud service for preventing various dangerous situations Ryu HyunKi, Moon ChangSoo, Yeo ChangSub, and Lee HaengSuk Abstract In this paper,
Exchange of Data for Big Data in Hybrid Cloud Environment
 , pp. 67-72 http://dx.doi.org/10.14257/ijseia.2015.9.4.08 Exchange of Data for Big Data in Hybrid Cloud Environment Chi-gon Hwang 1, Chang-Pyo Yoon 2 and Daesung Lee 3 1 Dept of Internet Information, Kyungmin
, pp. 67-72 http://dx.doi.org/10.14257/ijseia.2015.9.4.08 Exchange of Data for Big Data in Hybrid Cloud Environment Chi-gon Hwang 1, Chang-Pyo Yoon 2 and Daesung Lee 3 1 Dept of Internet Information, Kyungmin
DBaaS Using HL7 Based on XMDR-DAI for Medical Information Sharing in Cloud
 , pp.111-120 http://dx.doi.org/10.14257/ijmue.2015.10.9.12 DBaaS Using HL7 Based on XMDR-DAI for Medical Information Sharing in Cloud Ho-Kyun Park 1 and Seok-Jae Moon 2 1 School of IT Convergence Engineering,
, pp.111-120 http://dx.doi.org/10.14257/ijmue.2015.10.9.12 DBaaS Using HL7 Based on XMDR-DAI for Medical Information Sharing in Cloud Ho-Kyun Park 1 and Seok-Jae Moon 2 1 School of IT Convergence Engineering,
A Research Using Private Cloud with IP Camera and Smartphone Video Retrieval
 , pp.175-186 http://dx.doi.org/10.14257/ijsh.2014.8.1.19 A Research Using Private Cloud with IP Camera and Smartphone Video Retrieval Kil-sung Park and Sun-Hyung Kim Department of Information & Communication
, pp.175-186 http://dx.doi.org/10.14257/ijsh.2014.8.1.19 A Research Using Private Cloud with IP Camera and Smartphone Video Retrieval Kil-sung Park and Sun-Hyung Kim Department of Information & Communication
A Study on Design of Health Device for U-Health System
 , pp.79-86 http://dx.doi.org/10.14257/ijbsbt.2015.7.2.08 A Study on Design of Health Device for U-Health System Am-Suk Oh Dept. of Media Engineering, Tongmyong University, Busan, Korea [email protected] Abstract
, pp.79-86 http://dx.doi.org/10.14257/ijbsbt.2015.7.2.08 A Study on Design of Health Device for U-Health System Am-Suk Oh Dept. of Media Engineering, Tongmyong University, Busan, Korea [email protected] Abstract
Design and Implementation of Automatic Attendance Check System Using BLE Beacon
 , pp.177-186 http://dx.doi.org/10.14257/ijmue.2015.10.10.19 Design and Implementation of Automatic Attendance Check System Using BLE Beacon Mi-Young Bae and Dae-Jea Cho * Dept. Of Multimedia Engineering,
, pp.177-186 http://dx.doi.org/10.14257/ijmue.2015.10.10.19 Design and Implementation of Automatic Attendance Check System Using BLE Beacon Mi-Young Bae and Dae-Jea Cho * Dept. Of Multimedia Engineering,
Design and Analysis of Mobile Learning Management System based on Web App
 , pp. 417-428 http://dx.doi.org/10.14257/ijmue.2015.10.1.38 Design and Analysis of Mobile Learning Management System based on Web App Shinwon Lee Department of Computer System Engineering, Jungwon University,
, pp. 417-428 http://dx.doi.org/10.14257/ijmue.2015.10.1.38 Design and Analysis of Mobile Learning Management System based on Web App Shinwon Lee Department of Computer System Engineering, Jungwon University,
Internet of Things (IoT): Security Awareness. Sandra Liepkalns, CRISC [email protected]
 Internet of Things (IoT): Security Awareness Sandra Liepkalns, CRISC [email protected] So What is the Internet of Things Network of physical objects embedded with: Electronics, software, sensors
Internet of Things (IoT): Security Awareness Sandra Liepkalns, CRISC [email protected] So What is the Internet of Things Network of physical objects embedded with: Electronics, software, sensors
Development of a Service Robot System for a Remote Child Monitoring Platform
 , pp.153-162 http://dx.doi.org/10.14257/ijsh.2014.8.5.14 Development of a Service Robot System for a Remote Child Monitoring Platform Taewoo Han 1 and Yong-Ho Seo 2, * 1 Department of Game and Multimedia,
, pp.153-162 http://dx.doi.org/10.14257/ijsh.2014.8.5.14 Development of a Service Robot System for a Remote Child Monitoring Platform Taewoo Han 1 and Yong-Ho Seo 2, * 1 Department of Game and Multimedia,
Development of Real-time Big Data Analysis System and a Case Study on the Application of Information in a Medical Institution
 , pp. 93-102 http://dx.doi.org/10.14257/ijseia.2015.9.7.10 Development of Real-time Big Data Analysis System and a Case Study on the Application of Information in a Medical Institution Mi-Jin Kim and Yun-Sik
, pp. 93-102 http://dx.doi.org/10.14257/ijseia.2015.9.7.10 Development of Real-time Big Data Analysis System and a Case Study on the Application of Information in a Medical Institution Mi-Jin Kim and Yun-Sik
Security Assessment through Google Tools -Focusing on the Korea University Website
 , pp.9-13 http://dx.doi.org/10.14257/astl.2015.93.03 Security Assessment through Google Tools -Focusing on the Korea University Website Mi Young Bae 1,1, Hankyu Lim 1, 1 Department of Multimedia Engineering,
, pp.9-13 http://dx.doi.org/10.14257/astl.2015.93.03 Security Assessment through Google Tools -Focusing on the Korea University Website Mi Young Bae 1,1, Hankyu Lim 1, 1 Department of Multimedia Engineering,
Developing Safety Management Systems for Track Workers Using Smart Phone GPS
 , pp.137-148 http://dx.doi.org/10.14257/ijca.2013.6.5.13 Developing Safety Management Systems for Track Workers Using Smart Phone GPS Jin-Hee Ku 1 and Duk-Kyu Park 2 1 Dept of Liberal Education and 2 Dept
, pp.137-148 http://dx.doi.org/10.14257/ijca.2013.6.5.13 Developing Safety Management Systems for Track Workers Using Smart Phone GPS Jin-Hee Ku 1 and Duk-Kyu Park 2 1 Dept of Liberal Education and 2 Dept
Personal Health Care Management System Developed under ISO/IEEE 11073 with Bluetooth HDP
 Vol.8, No.3 (2014), pp.191-196 http://dx.doi.org/10.14257/ijsh.2014.8.3.18 Personal Health Care Management System Developed under ISO/IEEE 11073 with Bluetooth HDP Am suk Oh 1, Doo Heon Song 2 and Gwan
Vol.8, No.3 (2014), pp.191-196 http://dx.doi.org/10.14257/ijsh.2014.8.3.18 Personal Health Care Management System Developed under ISO/IEEE 11073 with Bluetooth HDP Am suk Oh 1, Doo Heon Song 2 and Gwan
Effective Use of Android Sensors Based on Visualization of Sensor Information
 , pp.299-308 http://dx.doi.org/10.14257/ijmue.2015.10.9.31 Effective Use of Android Sensors Based on Visualization of Sensor Information Young Jae Lee Faculty of Smartmedia, Jeonju University, 303 Cheonjam-ro,
, pp.299-308 http://dx.doi.org/10.14257/ijmue.2015.10.9.31 Effective Use of Android Sensors Based on Visualization of Sensor Information Young Jae Lee Faculty of Smartmedia, Jeonju University, 303 Cheonjam-ro,
The Digital Signage System Supporting Multi-Resources Schedule on an Elevator
 , pp. 219-228 http://dx.doi.org/10.14257/ijsh.2015.9.8.23 The Digital Signage System Supporting Multi-Resources Schedule on an Elevator Woon-Yong Kim and SoonGohn Kim (Corresponding Author) Department
, pp. 219-228 http://dx.doi.org/10.14257/ijsh.2015.9.8.23 The Digital Signage System Supporting Multi-Resources Schedule on an Elevator Woon-Yong Kim and SoonGohn Kim (Corresponding Author) Department
Design of Big Data-based Greenhouse Environment Data Consulting System for Improving Crop Quality
 , pp.182-187 http://dx.doi.org/10.14257/astl.2015.95.35 Design of Big Data-based Greenhouse Environment Data Consulting System for Improving Crop Quality Seongjin Kim, Hyun Yoe 1 Department of Information
, pp.182-187 http://dx.doi.org/10.14257/astl.2015.95.35 Design of Big Data-based Greenhouse Environment Data Consulting System for Improving Crop Quality Seongjin Kim, Hyun Yoe 1 Department of Information
How To Detect An Advanced Persistent Threat Through Big Data And Network Analysis
 , pp.30-36 http://dx.doi.org/10.14257/astl.2013.29.06 Detection of Advanced Persistent Threat by Analyzing the Big Data Log Jisang Kim 1, Taejin Lee, Hyung-guen Kim, Haeryong Park KISA, Information Security
, pp.30-36 http://dx.doi.org/10.14257/astl.2013.29.06 Detection of Advanced Persistent Threat by Analyzing the Big Data Log Jisang Kim 1, Taejin Lee, Hyung-guen Kim, Haeryong Park KISA, Information Security
Home Appliance Control and Monitoring System Model Based on Cloud Computing Technology
 Home Appliance Control and Monitoring System Model Based on Cloud Computing Technology Yun Cui 1, Myoungjin Kim 1, Seung-woo Kum 3, Jong-jin Jung 3, Tae-Beom Lim 3, Hanku Lee 2, *, and Okkyung Choi 2 1
Home Appliance Control and Monitoring System Model Based on Cloud Computing Technology Yun Cui 1, Myoungjin Kim 1, Seung-woo Kum 3, Jong-jin Jung 3, Tae-Beom Lim 3, Hanku Lee 2, *, and Okkyung Choi 2 1
A Resilient Device Monitoring System in Collaboration Environments
 , pp.103-114 http://dx.doi.org/10.14257/ijsh.2014.8.5.10 A Resilient Device Monitoring System in Collaboration Environments KeeHyun Park 1 and JongHwi Lee 1 Department of Computer Engineering, Keimyung
, pp.103-114 http://dx.doi.org/10.14257/ijsh.2014.8.5.10 A Resilient Device Monitoring System in Collaboration Environments KeeHyun Park 1 and JongHwi Lee 1 Department of Computer Engineering, Keimyung
A Study on User Access Control Method using Multi-Factor Authentication for EDMS
 , pp.327-334 http://dx.doi.org/10.14257/ijsia.2013.7.6.33 A Study on User Access Control Method using Multi-Factor Authentication for EDMS Keunwang Lee 1* 1 Dept.of Multimedia Science, Chungwoon University
, pp.327-334 http://dx.doi.org/10.14257/ijsia.2013.7.6.33 A Study on User Access Control Method using Multi-Factor Authentication for EDMS Keunwang Lee 1* 1 Dept.of Multimedia Science, Chungwoon University
Cloud Computing based Livestock Monitoring and Disease Forecasting System
 , pp.313-320 http://dx.doi.org/10.14257/ijsh.2013.7.6.30 Cloud Computing based Livestock Monitoring and Disease Forecasting System Seokkyun Jeong 1, Hoseok Jeong 2, Haengkon Kim 3 and Hyun Yoe 4 1,2,4
, pp.313-320 http://dx.doi.org/10.14257/ijsh.2013.7.6.30 Cloud Computing based Livestock Monitoring and Disease Forecasting System Seokkyun Jeong 1, Hoseok Jeong 2, Haengkon Kim 3 and Hyun Yoe 4 1,2,4
Study of HTML5 WebSocket for a Multimedia Communication
 , pp.61-72 http://dx.doi.org/10.14257/ijmue.2014.9.7.06 Study of HTML5 WebSocket for a Multimedia Communication Jin-tae Park 1, Hyun-seo Hwang 1, Jun-soo Yun 1 and Il-young Moon 1 1 School of Computer
, pp.61-72 http://dx.doi.org/10.14257/ijmue.2014.9.7.06 Study of HTML5 WebSocket for a Multimedia Communication Jin-tae Park 1, Hyun-seo Hwang 1, Jun-soo Yun 1 and Il-young Moon 1 1 School of Computer
Standardization Requirements Analysis on Big Data in Public Sector based on Potential Business Models
 , pp. 165-172 http://dx.doi.org/10.14257/ijseia.2014.8.11.15 Standardization Requirements Analysis on Big Data in Public Sector based on Potential Business Models Suwook Ha 1, Seungyun Lee 2 and Kangchan
, pp. 165-172 http://dx.doi.org/10.14257/ijseia.2014.8.11.15 Standardization Requirements Analysis on Big Data in Public Sector based on Potential Business Models Suwook Ha 1, Seungyun Lee 2 and Kangchan
Implementation of IR-UWB MAC Development Tools Based on IEEE 802.15.4a
 Vol. 8, No. 4 (2015), pp. 275-286 http://dx.doi.org/10.14257/ijca.2015.8.4.27 Implementation of IR-UWB MAC Development Tools Based on IEEE 802.15.4a Sol Lim, Kye Joo Lee, So Yeon Kim, Chang Seok Chae,
Vol. 8, No. 4 (2015), pp. 275-286 http://dx.doi.org/10.14257/ijca.2015.8.4.27 Implementation of IR-UWB MAC Development Tools Based on IEEE 802.15.4a Sol Lim, Kye Joo Lee, So Yeon Kim, Chang Seok Chae,
Design of Media measurement and monitoring system based on Internet of Things
 Design of Media measurement and monitoring system based on Internet of Things Hyunjoong Kang 1, Marie Kim 1, MyungNam Bae 1, Hyo-Chan Bang 1, 1 Electronics and Telecommunications Research Institute, 138
Design of Media measurement and monitoring system based on Internet of Things Hyunjoong Kang 1, Marie Kim 1, MyungNam Bae 1, Hyo-Chan Bang 1, 1 Electronics and Telecommunications Research Institute, 138
A Sound Analysis and Synthesis System for Generating an Instrumental Piri Song
 , pp.347-354 http://dx.doi.org/10.14257/ijmue.2014.9.8.32 A Sound Analysis and Synthesis System for Generating an Instrumental Piri Song Myeongsu Kang and Jong-Myon Kim School of Electrical Engineering,
, pp.347-354 http://dx.doi.org/10.14257/ijmue.2014.9.8.32 A Sound Analysis and Synthesis System for Generating an Instrumental Piri Song Myeongsu Kang and Jong-Myon Kim School of Electrical Engineering,
FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany [email protected] www.frafos.com
 WebRTC for Service Providers FRAFOS GmbH FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany [email protected] www.frafos.com This document is copyright of FRAFOS GmbH. Duplication or propagation or
WebRTC for Service Providers FRAFOS GmbH FRAFOS GmbH Windscheidstr. 18 Ahoi 10627 Berlin Germany [email protected] www.frafos.com This document is copyright of FRAFOS GmbH. Duplication or propagation or
Attack Vector Detail Report Atlassian
 Attack Vector Detail Report Atlassian Report As Of Tuesday, March 24, 2015 Prepared By Report Description Notes [email protected] The Attack Vector Details report provides details of vulnerability
Attack Vector Detail Report Atlassian Report As Of Tuesday, March 24, 2015 Prepared By Report Description Notes [email protected] The Attack Vector Details report provides details of vulnerability
Research and Performance Analysis of HTML5 WebSocket for a Real-time Multimedia Data Communication Environment
 Vol.46 (Multimedia 2014), pp.307-312 http://dx.doi.org/10.14257/astl.2014.46.64 Research and Performance Analysis of HTML5 WebSocket for a Real-time Multimedia Data Communication Environment Jin-tae Park
Vol.46 (Multimedia 2014), pp.307-312 http://dx.doi.org/10.14257/astl.2014.46.64 Research and Performance Analysis of HTML5 WebSocket for a Real-time Multimedia Data Communication Environment Jin-tae Park
A SURVEY OF CLOUD COMPUTING: NETWORK BASED ISSUES PERFORMANCE AND ANALYSIS
 A SURVEY OF CLOUD COMPUTING: NETWORK BASED ISSUES PERFORMANCE AND ANALYSIS *Dr Umesh Sehgal, #Shalini Guleria *Associate Professor,ARNI School of Computer Science,Arni University,[email protected]
A SURVEY OF CLOUD COMPUTING: NETWORK BASED ISSUES PERFORMANCE AND ANALYSIS *Dr Umesh Sehgal, #Shalini Guleria *Associate Professor,ARNI School of Computer Science,Arni University,[email protected]
Development of an Ignition Interlock Device to Prevent Illegal Driving of a Drunk Driver
 , pp.161-165 http://dx.doi.org/10.14257/astl.205.98.41 Development of an Ignition Interlock Device to Prevent Illegal Driving of a Drunk Driver Jeong MyeongSu 1, Moon ChangSoo 1, Gwon DaeHyeok 1 and Cho
, pp.161-165 http://dx.doi.org/10.14257/astl.205.98.41 Development of an Ignition Interlock Device to Prevent Illegal Driving of a Drunk Driver Jeong MyeongSu 1, Moon ChangSoo 1, Gwon DaeHyeok 1 and Cho
Secure VoIP for optimal business communication
 White Paper Secure VoIP for optimal business communication Learn how to create a secure environment for real-time audio, video and data communication over IP based networks. Andreas Åsander Manager, Product
White Paper Secure VoIP for optimal business communication Learn how to create a secure environment for real-time audio, video and data communication over IP based networks. Andreas Åsander Manager, Product
Research into a Visualization Analysis of Bigdata for the Decision Making of a Tourism Policy
 , pp.42-46 http://dx.doi.org/10.14257/astl.2016.129.09 Research into a Visualization Analysis of Bigdata for the Decision Making of a Tourism Policy Sungwook Yoon, Jeonghyun Lee, Hyenki Kim * Dept. of
, pp.42-46 http://dx.doi.org/10.14257/astl.2016.129.09 Research into a Visualization Analysis of Bigdata for the Decision Making of a Tourism Policy Sungwook Yoon, Jeonghyun Lee, Hyenki Kim * Dept. of
Enterprise Resource Planning System Deployment on Mobile Cloud Computing
 Asia-pacific Journal of Multimedia Services Convergence with Art, Humanities and Sociology Vol.3, No.1 (2013), pp. 1-8 http://dx.doi.org/10.14257/ajmscahs.2013.06.02 Enterprise Resource Planning System
Asia-pacific Journal of Multimedia Services Convergence with Art, Humanities and Sociology Vol.3, No.1 (2013), pp. 1-8 http://dx.doi.org/10.14257/ajmscahs.2013.06.02 Enterprise Resource Planning System
Chapter 11 Cloud Application Development
 Chapter 11 Cloud Application Development Contents Motivation. Connecting clients to instances through firewalls. Chapter 10 2 Motivation Some of the questions of interest to application developers: How
Chapter 11 Cloud Application Development Contents Motivation. Connecting clients to instances through firewalls. Chapter 10 2 Motivation Some of the questions of interest to application developers: How
The Sensitive Information Management System for Merger and Acquisition (M&A) Transactions
 , pp.203-212 http://dx.doi.org/10.14257/ijmue.2014.9.3.19 The Sensitive Information Management System for Merger and Acquisition (M&A) Transactions Kyong-jin Kim * and Seng-phil Hong ** Sungshin Women
, pp.203-212 http://dx.doi.org/10.14257/ijmue.2014.9.3.19 The Sensitive Information Management System for Merger and Acquisition (M&A) Transactions Kyong-jin Kim * and Seng-phil Hong ** Sungshin Women
Developing a Video-based Smart Mastery Learning through Adaptive Evaluation
 , pp. 101-114 http://dx.doi.org/10.14257/ijseia.2014.8.11.09 Developing a Video-based Smart Mastery Learning through Adaptive Evaluation Jeongim Kang 1, Moonhee Kim 1 and Seong Baeg Kim 1,1 1 Department
, pp. 101-114 http://dx.doi.org/10.14257/ijseia.2014.8.11.09 Developing a Video-based Smart Mastery Learning through Adaptive Evaluation Jeongim Kang 1, Moonhee Kim 1 and Seong Baeg Kim 1,1 1 Department
Implementation of Home Network Security System based on Remote Management Server
 IJCSNS International Journal of Computer Science and Network Security, VOL.7 No.2, February 2007 267 Implementation of Home Network Security System based on Remote Management Server Young Gun Jang, Hoon
IJCSNS International Journal of Computer Science and Network Security, VOL.7 No.2, February 2007 267 Implementation of Home Network Security System based on Remote Management Server Young Gun Jang, Hoon
SHODAN for Penetration Testers. Michael theprez98 Schearer
 SHODAN for Penetration Testers Michael theprez98 Schearer SHODAN for Penetration Testers What is SHODAN? Basic Operations Penetration Testing Case Study 1: Cisco Devices Case Study 2: Default Passwords
SHODAN for Penetration Testers Michael theprez98 Schearer SHODAN for Penetration Testers What is SHODAN? Basic Operations Penetration Testing Case Study 1: Cisco Devices Case Study 2: Default Passwords
Security Measures of Personal Information of Smart Home PC
 , pp.227-236 http://dx.doi.org/10.14257/ijsh.2013.7.6.22 Security Measures of Personal Information of Smart Home PC Mi-Sook Seo 1 and Dea-Woo Park 2 1, 2 Department of Integrative Engineering, Hoseo Graduate
, pp.227-236 http://dx.doi.org/10.14257/ijsh.2013.7.6.22 Security Measures of Personal Information of Smart Home PC Mi-Sook Seo 1 and Dea-Woo Park 2 1, 2 Department of Integrative Engineering, Hoseo Graduate
N-CAP Users Guide Everything You Need to Know About Using the Internet! How Firewalls Work
 N-CAP Users Guide Everything You Need to Know About Using the Internet! How Firewalls Work How Firewalls Work By: Jeff Tyson If you have been using the internet for any length of time, and especially if
N-CAP Users Guide Everything You Need to Know About Using the Internet! How Firewalls Work How Firewalls Work By: Jeff Tyson If you have been using the internet for any length of time, and especially if
VOIP SECURITY: BEST PRACTICES TO SAFEGUARD YOUR NETWORK ======
 VOIP SECURITY: BEST PRACTICES TO SAFEGUARD YOUR NETWORK ====== Table of Contents Introduction to VoIP Security... 2 Meet Our Expert - Momentum Telecom... 2 BroadWorks... 2 VoIP Vulnerabilities... 3 Call
VOIP SECURITY: BEST PRACTICES TO SAFEGUARD YOUR NETWORK ====== Table of Contents Introduction to VoIP Security... 2 Meet Our Expert - Momentum Telecom... 2 BroadWorks... 2 VoIP Vulnerabilities... 3 Call
How To Test A Robot Platform And Its Components
 An Automated Test Method for Robot Platform and Its Components Jae-Hee Lim 1, Suk-Hoon Song 1, Jung-Rye Son 1, Tae-Yong Kuc 2, Hong-Seong Park 3, Hong-Seok Kim 4 1,2 School of Information and Communication,
An Automated Test Method for Robot Platform and Its Components Jae-Hee Lim 1, Suk-Hoon Song 1, Jung-Rye Son 1, Tae-Yong Kuc 2, Hong-Seong Park 3, Hong-Seok Kim 4 1,2 School of Information and Communication,
How To Write A Privacy Preserving Firewall Optimization Protocol
 Asia-pacific Journal of Multimedia Services Convergence with Art, Humanities and Sociology Vol.1, No.2 (2011), pp. 93-100 http://dx.doi.org/10.14257/ajmscahs.2011.12.06 Secure Multi-Party Computation in
Asia-pacific Journal of Multimedia Services Convergence with Art, Humanities and Sociology Vol.1, No.2 (2011), pp. 93-100 http://dx.doi.org/10.14257/ajmscahs.2011.12.06 Secure Multi-Party Computation in
A Study of the Design of Wireless Medical Sensor Network based u- Healthcare System
 , pp.91-96 http://dx.doi.org/10.14257/ijbsbt.2014.6.3.11 A Study of the Design of Wireless Medical Sensor Network based u- Healthcare System Ronnie D. Caytiles and Sungwon Park 1* 1 Hannam University 133
, pp.91-96 http://dx.doi.org/10.14257/ijbsbt.2014.6.3.11 A Study of the Design of Wireless Medical Sensor Network based u- Healthcare System Ronnie D. Caytiles and Sungwon Park 1* 1 Hannam University 133
DESIGN AND IMPLEMENTATION OF AN INTRANET SECURITY AND ACCESS CONTROL SYSTEM IN UBI-COM
 Computing and Informatics, Vol. 30, 2011, 419 428 DESIGN AND IMPLEMENTATION OF AN INTRANET SECURITY AND ACCESS CONTROL SYSTEM IN UBI-COM Malrey Lee Center for Advanced Image and Information Technology
Computing and Informatics, Vol. 30, 2011, 419 428 DESIGN AND IMPLEMENTATION OF AN INTRANET SECURITY AND ACCESS CONTROL SYSTEM IN UBI-COM Malrey Lee Center for Advanced Image and Information Technology
Fast Device Discovery for Remote Device Management in Lighting Control Networks
 J Inf Process Syst, Vol.11, No.1, pp.125~133, March 2015 http://dx.doi.org/10.3745/jips.03.0011 ISSN 1976-913X (Print) ISSN 2092-805X (Electronic) Fast Device Discovery for Remote Device Management in
J Inf Process Syst, Vol.11, No.1, pp.125~133, March 2015 http://dx.doi.org/10.3745/jips.03.0011 ISSN 1976-913X (Print) ISSN 2092-805X (Electronic) Fast Device Discovery for Remote Device Management in
AP-GSS3000 TM 512Ch GSM SIM Server
 AP-GSS3000 TM 512Ch GSM SIM Server High Performance GSM SIM Server Solution Preliminary Product Overview (Without notice, following described technical spec. can be changed) www.addpac.com AddPac Technology
AP-GSS3000 TM 512Ch GSM SIM Server High Performance GSM SIM Server Solution Preliminary Product Overview (Without notice, following described technical spec. can be changed) www.addpac.com AddPac Technology
AP-GSS1500 TM 256Ch GSM SIM Server High Performance GSM SIM Server Solution
 AP-GSS1500 TM 256Ch GSM SIM Server High Performance GSM SIM Server Solution www.addpac.com AddPac Technology 2013, Sales and Marketing Contents Product Overview Hardware Specification SIM Bank Module Specification
AP-GSS1500 TM 256Ch GSM SIM Server High Performance GSM SIM Server Solution www.addpac.com AddPac Technology 2013, Sales and Marketing Contents Product Overview Hardware Specification SIM Bank Module Specification
A Platform as a Service for Smart Home
 A Platform as a Service for Smart Home Boyun Eom, Choonhwa Lee, Changwoo Yoon, Hyunwoo Lee, and Won Ryu Abstract Owing to the convergence of home network, smart home technologies have been developing rapidly.
A Platform as a Service for Smart Home Boyun Eom, Choonhwa Lee, Changwoo Yoon, Hyunwoo Lee, and Won Ryu Abstract Owing to the convergence of home network, smart home technologies have been developing rapidly.
Vulnerability Analysis on Mobile VoIP Supplementary Services and MITM Attack
 Vulnerability Analysis on Mobile VoIP Supplementary Services and MITM Attack You Joung Ham Graduate School of Computer Engineering, Hanshin University, 411, Yangsan-dong, Osan, Gyeonggi, Rep. of Korea
Vulnerability Analysis on Mobile VoIP Supplementary Services and MITM Attack You Joung Ham Graduate School of Computer Engineering, Hanshin University, 411, Yangsan-dong, Osan, Gyeonggi, Rep. of Korea
Web Application Report
 Web Application Report This report includes important security information about your Web Application. Security Report This report was created by IBM Rational AppScan 8.5.0.1 11/14/2012 8:52:13 AM 11/14/2012
Web Application Report This report includes important security information about your Web Application. Security Report This report was created by IBM Rational AppScan 8.5.0.1 11/14/2012 8:52:13 AM 11/14/2012
Patent Big Data Analysis by R Data Language for Technology Management
 , pp. 69-78 http://dx.doi.org/10.14257/ijseia.2016.10.1.08 Patent Big Data Analysis by R Data Language for Technology Management Sunghae Jun * Department of Statistics, Cheongju University, 360-764, Korea
, pp. 69-78 http://dx.doi.org/10.14257/ijseia.2016.10.1.08 Patent Big Data Analysis by R Data Language for Technology Management Sunghae Jun * Department of Statistics, Cheongju University, 360-764, Korea
1 Log visualization at CNES (Part II)
 1 Log visualization at CNES (Part II) 1.1 Background For almost 2 years now, CNES has set up a team dedicated to "log analysis". Its role is multiple: This team is responsible for analyzing the logs after
1 Log visualization at CNES (Part II) 1.1 Background For almost 2 years now, CNES has set up a team dedicated to "log analysis". Its role is multiple: This team is responsible for analyzing the logs after
Review of the Techniques for Smart Learning Systems
 , pp.1-5 http://dx.doi.org/10.14257/astl.2016. Review of the Techniques for Smart Learning Systems Jaegeol Yim, Sangheon Kim 1 Departmet of Computer Engineering, Dongguk University at Gyeongju, 38066 Korea
, pp.1-5 http://dx.doi.org/10.14257/astl.2016. Review of the Techniques for Smart Learning Systems Jaegeol Yim, Sangheon Kim 1 Departmet of Computer Engineering, Dongguk University at Gyeongju, 38066 Korea
Development of Object-Oriented Analysis and Design Methodology for Secure Web Applications
 , pp.71-80 http://dx.doi.org/10.14257/ijsia.2014.8.1.07 Development of Object-Oriented Analysis and Design Methodology for Secure Web Applications Kyung-Soo Joo 1 and Jung-Woong Woo 2 1 Department of Computer
, pp.71-80 http://dx.doi.org/10.14257/ijsia.2014.8.1.07 Development of Object-Oriented Analysis and Design Methodology for Secure Web Applications Kyung-Soo Joo 1 and Jung-Woong Woo 2 1 Department of Computer
Study of SAP ERP Connection System Driven in Smartphone
 Study of SAP ERP Connection System Driven in Smartphone 1 Jong Youel Park, * 2 Dea-Woo Park, 3 Young Hyun Chang, 4 Kyung Bae Yoon 1, First Author Hoseo Graduate School of Venture Korea, [email protected]
Study of SAP ERP Connection System Driven in Smartphone 1 Jong Youel Park, * 2 Dea-Woo Park, 3 Young Hyun Chang, 4 Kyung Bae Yoon 1, First Author Hoseo Graduate School of Venture Korea, [email protected]
Device-based Secure Data Management Scheme in a Smart Home
 Int'l Conf. Security and Management SAM'15 231 Device-based Secure Data Management Scheme in a Smart Home Ho-Seok Ryu 1, and Jin Kwak 2 1 ISAA Lab., Department of Computer Engineering, Ajou University,
Int'l Conf. Security and Management SAM'15 231 Device-based Secure Data Management Scheme in a Smart Home Ho-Seok Ryu 1, and Jin Kwak 2 1 ISAA Lab., Department of Computer Engineering, Ajou University,
Cyber Forensic for Hadoop based Cloud System
 Cyber Forensic for Hadoop based Cloud System ChaeHo Cho 1, SungHo Chin 2 and * Kwang Sik Chung 3 1 Korea National Open University graduate school Dept. of Computer Science 2 LG Electronics CTO Division
Cyber Forensic for Hadoop based Cloud System ChaeHo Cho 1, SungHo Chin 2 and * Kwang Sik Chung 3 1 Korea National Open University graduate school Dept. of Computer Science 2 LG Electronics CTO Division
A Proxy-Based Data Security Solution in Mobile Cloud
 , pp. 77-84 http://dx.doi.org/10.14257/ijsia.2015.9.5.08 A Proxy-Based Data Security Solution in Mobile Cloud Xiaojun Yu 1,2 and Qiaoyan Wen 1 1 State Key Laboratory of Networking and Switching Technology,
, pp. 77-84 http://dx.doi.org/10.14257/ijsia.2015.9.5.08 A Proxy-Based Data Security Solution in Mobile Cloud Xiaojun Yu 1,2 and Qiaoyan Wen 1 1 State Key Laboratory of Networking and Switching Technology,
Beyond Internet Scanning: Banner Processing for Passive Software Vulnerability Assessment
 Beyond Internet Scanning: Banner Processing for Passive Software Vulnerability Assessment Béla Genge, Piroska Haller, and Călin Enăchescu Petru Maior University of Tg. Mureş, Department of Informatics.
Beyond Internet Scanning: Banner Processing for Passive Software Vulnerability Assessment Béla Genge, Piroska Haller, and Călin Enăchescu Petru Maior University of Tg. Mureş, Department of Informatics.
Make search become the internal function of Internet
 Make search become the internal function of Internet Wang Liang 1, Guo Yi-Ping 2, Fang Ming 3 1, 3 (Department of Control Science and Control Engineer, Huazhong University of Science and Technology, WuHan,
Make search become the internal function of Internet Wang Liang 1, Guo Yi-Ping 2, Fang Ming 3 1, 3 (Department of Control Science and Control Engineer, Huazhong University of Science and Technology, WuHan,
Open-Source-based Visualization of Flight Waypoint Tracking Using Flight Manipulation System
 Open-Source-based Visualization of Flight Waypoint Tracking Using Flight Manipulation System Myeong-Chul Park a, Hyeon-Gab Shin b, Yong Ho Moon b, Seok-Wun Ha b*, a Dept. of Biomedical Electronics, Songho
Open-Source-based Visualization of Flight Waypoint Tracking Using Flight Manipulation System Myeong-Chul Park a, Hyeon-Gab Shin b, Yong Ho Moon b, Seok-Wun Ha b*, a Dept. of Biomedical Electronics, Songho
International Journal of Software and Web Sciences (IJSWS) www.iasir.net. GPS and GSM Based Database Systems for User Access
 International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0063 ISSN (Online): 2279-0071 International
International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0063 ISSN (Online): 2279-0071 International
