ARM TrustZone and KVM Coexistence with RTOS For Automotive
|
|
|
- Beatrice Ramsey
- 10 years ago
- Views:
Transcription
1 ARM TrustZone and KVM Coexistence with RTOS For Automotive Michele Paolino Automotive-grade Linux Summit, , Tokyo, Japan
2 Authorship and sponsorship Michele Paolino, software architect at Virtual Open Systems (VOSYS). His experience includes Linux kernel drivers, KVM hypervisor, QEMU programming, libvirt, API remoting, GP/GPU, TrustZone security and OpenStack. Virtual Open Systems is a high-tech start-up company active in open source virtualization solutions and custom services for complex mixedcriticality automotive, NFV networking infrastructures, consumer electronics, mobile devices and in general for embedded heterogeneous multicore systems around new generation processor architectures. This work is done in the context of the H2020 Trusted APPs for CPS (TAPPS) project (
3 State of the art Beyond the state of the art Status of the work and benchmark Next steps Conclusion
4 Introduction Cars are getting smarter and always connected, combining safety critical applications with In-Vehicle Infotainment (IVI): Instrument Cluster management Park assistant, Heating, Ventilating, and Air Conditioning (HVAC) Advanced Driver Assistance Systems (ADAS) Key-less engine start, Body Control Module (BCM) Web browsing and social networking Internet of Things (IoT), Cyber Physical Systems (CPS) and cloud computing services Third party Apps (Maps, Games, Video, etc.)
5 Connected cars Pedestrian recognition Instrument Cluster Maps Parking assistant IVI Engine start HVAC 3rd party apps BCM IVI system ADAS Safety critical system Source:
6 The challenge Such a concept of the future car, brings new and unprecedented challenges to the automotive industry: Mixed criticality environment with RT requirements Security and trustworthiness of the software Secure the connected IVI environment (Apps installation, web browsing, shared devices, etc.) High performance (object recognition, DRM encoding, 3d acceleration, etc.) Source:
7 State of the art Today's cars are addressing these challenges by means of two platforms, one for the IVI and the other for safety critical applications: RT requirements Performance (Night vision, pedestrian/signs recognition, etc.) Certifiability (e.g., ISO 26262) 3D acceleration Graphical interface Infotainment Apps Web Safety critical system IVI system Source: Two platforms are costly (hardware, cabling, space, weight etc.) and difficult to maintain/extend.
8 State of the art Beyond the state of the art Status of the work and benchmark Next steps Conclusion
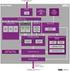
9 Beyond the state of the art IVI system Safety Critical system VMs Shared memory Touch display GPU LTE WiFI NFC Bluetooth RT App vtpm TEE Client vapi TEE Client API TEE Internal API Linux/KVM Hypervisor Safety critical OS VOSYS extended ARM Trusted Firmware ARMv8 Hardware AVB bus Instrument Cluster LIN bus Camera CAN bus Stepper motors
10 Beyond the State of the art (2) Extending open source projects and innovative technologies it is possible to run virtualized IVI and safe-critical systems on the same hardware, by means of: Hardware accelerated virtualization (performance, isolation, OS concurrency) ARM TrustZone (security, trusted computing, mixed criticality) Real Time Operating System support (safety critical functions)
11 Hardware accelerated virtualization Virtualization enables the execution of different operating systems concurrently. VMs isolation Support for multiple IVI guests: AGL distro, Android, Ubuntu, Tizen, etc. Direct hardware assignment and support for hardware acceleration (FPGA, GPU, DSP, etc.) VMs support for LTE and AVB/CAN bus connections Migration, over the air updates, App Store
12 Hardware accelerated virtualization: KVM and SELinux isolation Full Virtualization is the ability of a system to run different partitions concurrently with unmodified software. VMs that exploit the CPU virtualization extensions (i.e. ARM VE, Intel VT), are hardware isolated regarding: Memory Interrupts Exceptions VM svirt uses security kernel features like SELinux to go beyond Discretionary Access Control, using the Mandatory Access Control security policy to isolate VMs. svirt Iso lati on Untrusted App QEMU/KVM process Linux/KVM Hypervisor
13 Hardware accelerated virtualization: Virtualized AGL/Tizen support The AGL community is now working to build an AGL distribution. One of the points in the agenda is the support of QEMU, whose challenges on ARM are: Video acceleration (OpenGL) QEMU ARM audio support Short boot time Security and secure interaction with the safe critical OS
14 ARM TrustZone TrustZone safely runs two OSes by defining a secure operational mode completely isolated from the rest of the system: The two OSes are fully independent if the IVI part crashes, the safety critical OS runs normally TrustZone implements a secure context switch mechanism through the TrustZone Monitor IVI system Safety Critical system RT App vtpm VMs Shared memory TEE Client vapi TEE Internal API Safety critical OS TEE Client API Linux/KVM Hypervisor ARM Trusted Firmware TrustZone Monitor mode ARMv8 Hardware Critical device
15 TrustZone: ARM Trusted Firmware Arm Trusted Firmware (ATF) includes a Secure Monitor (EL3) software implementation for ARMv8-A platforms, which handles the boot procedure and interrupts Normal Modular design Secure world Initialization S-EL1 payload dispatcher Initialize Secure/Normal world isolation SMC (Secure monitor Call) Handling PSCI for secondary core bring-up 15 Secure
16 TrustZone: GlobalPlatform TEE GlobalPlatform's Trusted Execution Environment (TEE) is a secure area that guarantees that sensitive data are stored, processed and protected in a trusted environment. The TEE APIs are standardized set of APIs for Trusted Execution Environment Secure App Untrusted App Shared memory The TEE Client API The TEE Internal API TEE Internal API Safety critical OS TEE Client API Linux/KVM Hypervisor ARM Trusted Firmware TrustZone Monitor mode ARMv8 Hardware Critical device
17 RTOS support The proposed architecture, enables the execution of custom or legacy operating systems in the safety critical system: FreeRTOS, ARC CORE, QNX, etc. The safety critical system boots before the IVI system, and is able to control and attest its execution. The isolation provided by TrustZone to the RTOS is based on security hardware extensions (e.g., cpu signals) System critical devices are allocated exclusively to the RTOS and are not visible to the IVI system
18 RTOS support: why TrustZone? The other approaches which aim to the integration of a safety critical OS with IVI use virtualization to isolate the two systems: Is available in all the latest SoCs Isolates in hardware virtual machines Is a well-known and mature technology Supports the execution of many OSes concurrently Examples are: XEN Automotive Hypervisor and QNX hypervisor But..
19 RTOS support: why TrustZone? The other approaches which aim to the integration of a safety critical OS with IVI use virtualization to isolate the two systems: Is available in all the latest SoCs Isolates in hardware virtual machines Is a well-known and mature technology Supports the execution of many OSes concurrently Examples are: XEN Automotive Hypervisor and QNX hypervisor But.. Source:
20 RTOS support: the VENOM vulnerability Virtualization is cheap and provides nice features for automotive, but it could have important security problems VENOM, CVE , is a security vulnerability in the QEMU virtual floppy drive It allows an attacker to escape from the VM isolation (step 1) VENOM could open access to the host and all other VMs, potentially giving adversaries significant elevated access to the adjacent systems (step 2) IVI system Safety critical system RT App vtpm 1 2 Hypervisor
21 State of the art Beyond the state of the art Status of the work and benchmark Next steps Conclusion
22 Proof of Concept: current status A prototype of the proposed architecture can be seen in the booth area of the Tokyo ALS2015. Runs on ARMv8 Hardware with Security and Virtualization extensions Juno development board r0 ARMv8 Dual Cortex-A57@800MHz + Quad CortexA53@700MHz Software: Normal World: Linux v4.1/kvm Secure world: FreeRTOS/bare metal TrustZone Monitor: VOSYS ARM Trusted Firmware
23 VOSYS extended ARM Trusted Firmware By default, the ATF reference world switch procedure is timetriggered, Virtual Open Systems has extended ATF to: Quantify the world switch and FreeRTOS latency Give an insight in the communication overhead between RTOS/GPOS and VM/RTOS Modify the world switch procedure to respond to eventtriggered signals Make usage of the Performance Monitoring Unit (PMU) to have a very detailed view of latency in terms of clock cycles 23
24 Performance measurements Different performance measurements have been performed on the proof of concept presented at the ALS2015: Boot time test Interrupt Latency tests, which aim to assess the RTOS performance World switch latency, to measure the overhead introduced by TrustZone
25 Boot time Boot time is a critical factor both for user experience and for certifiability. CPU frequency is 800MHz for Cortex A57 and 700MHz for Cortex A53 t 102ms 8s 10s Safety critical OS running (FreeRTOS) Linux/KVM running (host) (guests)
26 Boot time Boot time is a critical factor both for user experience and for certifiability. CPU frequency is 800MHz for Cortex A57 and 700MHz for Cortex A53 t 102ms 8s 10s VMs boot optimization will be implemented by: Using faster HW (RAM, CPU and disk) Resuming the VM execution from an existing snapshot Safety critical OS running (FreeRTOS) Tuning VMs QoS and IO scheduling Linux/KVM running The final target is(host) to boot a full virtualized IVI system in less than 8 seconds (guests)
27 Interrupt latency The interrupt latency of the safety critical OS has been measured in the following cases: The interrupt arrives when the CPU is executing the safety critical OS (best case) The interrupt arrives when the CPU is running the IVI virtualized system (worst case) Description Clock cycles Best case Secure Secure World ~1900 ~2.7us Worst case Non Secure Secure ~2500 ~3.5us
28 World switch latency The combination of ARM Virtualization and Security extensions adds isolation which provides high security, but at a cost of additional overhead when a VM wants to communicate with the Security critical OS: Secure Monitor Call (SMC) is the instruction defined by ARM ISA to jump from the Non Secure to the Secure World and vice versa. KVM traps the SMC call from a guest and forwards the request to the Secure World
29 World switch latency (2) Following the path of a Secure Monitor Call (SMC) from the guest to the Secure World, there is a need to consider: Guest-Host context switch (SMC hypervisor trap) Measured with a bare metal QEMU/KVM application which interacts with the Performance Monitoring Unit (PMU) Secure-Non Secure world context switch Measured through a kernel module which executes the SMC assembly instruction causing a world switch into the secure World
30 World switch latency (3) The performed tests aim to measure the minimal round-trip: the Secure World payload here is a bare metal application Clock cycles* Time@700 MHz Guest Host ~1400 ~2us Non Secure Secure ~3700 ~5.2us Round-trip ~5100 ~7.2us *Source: T-KVM: A Trusted architecture for KVM ARM v7 and v8 Virtual Machines, IARIA Cloud Computing 2015 awarded best paper
31 State of the art Beyond the state of the art Status of the work and benchmark Next steps Conclusion
32 Next Steps Virtual Open Systems is carrying on the development of a complete and powerful automotive software stack solution, which includes: High performance for VMs and safety critical OS (hardware accelerators) VMs and safety critical OS QoS (coordinated scheduling) Security and safety (vtpm)
33 High performance - HW accelerators Both the VMs and the safety critical OS, leverages on hardware accelerators (such as FPGA, GPU or DSP) to: 3D rendering and computer vision algorithms Multimedia audio and video codecs Security (encrypted communication, driver recognition, remote connection, etc.) Advanced driving functions (ADAS, park assistant, driver recognition, etc.)
34 HW accelerators Safety critical OS Safety critical functions can be accelerated by: Exclusively using a device ARM TrustZone is used to isolate in hardware the access to a device This device is not seen by the hypervisor and the VMs Securely sharing a device with the VMs The safety critical OS acts as an arbiter for the VMs requests to the device VMs access to the device has a lower priority
35 HW Accelerators - VMs Virtual machines exploit GPUs, DSPs and FPGAs to provide high performance to guests operating systems by means of: Direct Assignment (e.g. VFIO) API Remoting (e.g. OpenCL, CUDA) Description Static allocation of the device to a single VM Virtualization at the API Dynamic allocation of the level device to multiple VMs Pros Performance Flexibility, migration, Performance, fexibility independence from the hardware Cons Space/power consumption, flexibility, migration performance HW assisted virtualization (e.g. SRIOV) Requires HW support, migration
36 High performance - QoS Quality of Service capabilities are important to provide always the right user experience to the driver: The safety critical OS: Has always higher priority Can not be affected by incorrect or malicious software running in the VMs. VMs QoS: A certain VM can be prioritized over the other Priority metrics are: network bandwidth, hardware utilization (CPUs and other devices), etc.
37 VMs QoS When a virtualized system is saturated by concurrent workloads (host and guest), VMs applications start to see an increase in latency. A guest-host scheduler missing link exacerbates these latency issues for: I/O scheduling Process scheduling Interrupt handling and network packet scheduling
38 Highlighting the problem: I/O disk latency The same concept is valid for I/O Disk as well. Consider a system running a guest operating system (guest G) A new application A, is being started in guest G Other applications are already performing I/O in the guest/host 41 The cumulative I/O request pattern of guest G, may exhibit no special property that allows the I/O scheduler in the host, to realize that an application is being loaded in the guest. So, the latency of application A is higher (worse startup time and responsiveness).
39 Solution: Coordinated Scheduling The concept of coordinated scheduling is based on the idea of fast and direct communication of the guest scheduler with the host The guest scheduler can quickly signal the host scheduler that there is a need to increase the priority of the guest First PoC with I/O scheduling: V-BFQ (based on BFQ) I/O host/guest scheduler is extended with virtualized systems in mind Communication between guest V-BFQ and host V-BFQ is done by the Hypervisor-Call ARM instruction (HVC) hvc #1 to indicate the guest needs to be privileged hvc #0 to indicate the guest does not need to be privileged anymore 43
40 Coordinated Scheduling: v-bfq 44
41 Coordinated Scheduling: benchmarks A set of benchmark have been performed modifying the disk and CPU schedulers, resulting in: From 28% to 67% disk latency improvement if compared with BFQ Minimum 58% disk latency improvement CFQ - the default Linux scheduler On a 2 CPUs systems, running a VM with 1 VCPU, CPU latency ~20times better than CFS Maximum latency of 71µs, whatever the number of workloads, against a CPU latency from 71µs up to >6000µs with vanilla CFS 45
42 Security and Safety: Trusted Computing VMs security, attestation and verification is of pivotal importance for connected cars (3rd party apps, IoT, Cloud Computing, etc.), and can be provided using a virtual Trusted Platform Module (vtpm) based on TrustZone: Enables software TPM (vtpm) implementations for Virtual Machines The guest Operating System accesses the TPM functions through the TEE API Supports Tizen, Android, Ubuntu guests Historically, TPMs are custom non-virtualizable solutions which require specific development.
43 TPM for VMs The typical TrustZone program flow Non Secure World Secure World # SMC causes a world switch # through the monitor mode # the application requires # a secure service using # the SMC assembly instruction SMC {<cond>} <imm16> # The application can # continue its execution M O N I T O R Secure routine # when the secure routine has # been executed, the program # goes back into the NS world ERET t
44 TrustZone and virtualization challenges The TrustZone technology has been designed by ARM as a security extension for resource constrained embedded systems. The Secure World is not able to run HW accelerated VMs The SMC does not know the identity of the VM which is requesting the secure service A secure service request (SMC call) performed in the guest should not affect the host Secure World state.. is TrustZone virtualizable?
45 TPM for VMs implementations The VM access to the vtpm can be implemented either trapping the SMC call, or using an API remoting approach API remoting SMC Description The secure service The hypervisor traps the requests are handled by a guests SMC calls specific API Pros Flexibility, hardware independence Guest applications can execute the SMC call directly Cons Guest OS needs to be modified accordingly to support API remoting ARM TrustZone is a mandatory requirement
46 Security and safety: Certification The certification of the system (RTOS, drivers, apps) is of pivotal importance for the automotive market ISO is the target for the VOSYS extended ATF (TrustZone Monitor layer), which supports already existing certified safety critical OS IVI system RT App vtpm VMs Shared memory TEE Client vapi d e i if t r e C TEE Internal API Safety critical OS TEE Client API d e i f rti e C VOSYS extended ATF Linux/KVM Hypervisor ARMv8 Hardware
47 State of the art Beyond the state of the art Status of the work and benchmark Next steps Conclusion
48 Conclusion In this presentation, a novel open source architecture based on TrustZone and KVM has been proposed and implemented as a proof of concept Many different open source projects are involved, with planned future work QEMU/KVM support for Tizen/AGL distribution An open source virtualized TEE implementation VM HW acceleration and QoS Virtual Open Systems will actively contribute to the future AGL distribution for IVI and safety critical OSes convergence and HW accelerators virtualization
49 Thank You come to visit us and see the demo to the Automotive Grade Linux 2015 booth 5!
50
Android Virtualization from Sierraware. Simply Secure
 Android Virtualization from Sierraware Simply Secure Integration Challenges DRM Mandates TrustZone TEE Hypervisor provides the flexibility and security needed for BYOD Power management, responsibility
Android Virtualization from Sierraware Simply Secure Integration Challenges DRM Mandates TrustZone TEE Hypervisor provides the flexibility and security needed for BYOD Power management, responsibility
Intel Graphics Virtualization Technology Update. Zhi Wang, [email protected]
 Intel Graphics Virtualization Technology Update Zhi Wang, [email protected] Agenda The History Intel Graphics Virtualization Technology Update New Usage Scenarios Upstream Status Summary 2 Intel GPU
Intel Graphics Virtualization Technology Update Zhi Wang, [email protected] Agenda The History Intel Graphics Virtualization Technology Update New Usage Scenarios Upstream Status Summary 2 Intel GPU
Comprehensive Security for Internet-of-Things Devices With ARM TrustZone
 Comprehensive Security for Internet-of-Things Devices With ARM TrustZone Howard Williams mentor.com/embedded Internet-of-Things Trends The world is more connected IoT devices are smarter and more complex
Comprehensive Security for Internet-of-Things Devices With ARM TrustZone Howard Williams mentor.com/embedded Internet-of-Things Trends The world is more connected IoT devices are smarter and more complex
Enabling Technologies for Distributed Computing
 Enabling Technologies for Distributed Computing Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF Multi-core CPUs and Multithreading Technologies
Enabling Technologies for Distributed Computing Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF Multi-core CPUs and Multithreading Technologies
Leveraging Thin Hypervisors for Security on Embedded Systems
 Leveraging Thin Hypervisors for Security on Embedded Systems Christian Gehrmann A part of Swedish ICT What is virtualization? Separation of a resource or request for a service from the underlying physical
Leveraging Thin Hypervisors for Security on Embedded Systems Christian Gehrmann A part of Swedish ICT What is virtualization? Separation of a resource or request for a service from the underlying physical
Sierraware Overview. Simply Secure
 Sierraware Overview Simply Secure Sierraware Software Suite SierraTEE/Micro Kernel TrustZone/GlobalPlatform TEE SierraVisor: Bare Metal Hypervisor Hypervisor for ARM Para-virtualization, TrustZone Virtualization,
Sierraware Overview Simply Secure Sierraware Software Suite SierraTEE/Micro Kernel TrustZone/GlobalPlatform TEE SierraVisor: Bare Metal Hypervisor Hypervisor for ARM Para-virtualization, TrustZone Virtualization,
Enabling Technologies for Distributed and Cloud Computing
 Enabling Technologies for Distributed and Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF Multi-core CPUs and Multithreading
Enabling Technologies for Distributed and Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF Multi-core CPUs and Multithreading
Beyond the Hypervisor
 Beyond the Hypervisor A Technical Roadmap for Open Virtualization, Linux, KVM Mike Day Distinguished Engineer, Chief Virtualization Architect, Open Systems Development Saturday, February 22, 2014 1 [email protected]
Beyond the Hypervisor A Technical Roadmap for Open Virtualization, Linux, KVM Mike Day Distinguished Engineer, Chief Virtualization Architect, Open Systems Development Saturday, February 22, 2014 1 [email protected]
Hardware accelerated Virtualization in the ARM Cortex Processors
 Hardware accelerated Virtualization in the ARM Cortex Processors John Goodacre Director, Program Management ARM Processor Division ARM Ltd. Cambridge UK 2nd November 2010 Sponsored by: & & New Capabilities
Hardware accelerated Virtualization in the ARM Cortex Processors John Goodacre Director, Program Management ARM Processor Division ARM Ltd. Cambridge UK 2nd November 2010 Sponsored by: & & New Capabilities
Virtualization. Dr. Yingwu Zhu
 Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Real-Time Virtualization How Crazy Are We?
 Siemens Corporate Technology October 2014 Real-Time Virtualization How Crazy Are We? Image: Marcus Quigmire, licensed under CC BY 2.0 Unrestricted Siemens AG 2014. All rights reserved Real-Time Systems
Siemens Corporate Technology October 2014 Real-Time Virtualization How Crazy Are We? Image: Marcus Quigmire, licensed under CC BY 2.0 Unrestricted Siemens AG 2014. All rights reserved Real-Time Systems
Virtualization: Hypervisors for Embedded and Safe Systems. Hanspeter Vogel Triadem Solutions AG
 1 Virtualization: Hypervisors for Embedded and Safe Systems Hanspeter Vogel Triadem Solutions AG 2 Agenda Use cases for virtualization Terminology Hypervisor Solutions Realtime System Hypervisor Features
1 Virtualization: Hypervisors for Embedded and Safe Systems Hanspeter Vogel Triadem Solutions AG 2 Agenda Use cases for virtualization Terminology Hypervisor Solutions Realtime System Hypervisor Features
Enhancing Hypervisor and Cloud Solutions Using Embedded Linux Iisko Lappalainen MontaVista
 Enhancing Hypervisor and Cloud Solutions Using Embedded Linux Iisko Lappalainen MontaVista Setting the Stage This presentation will discuss the usage of Linux as a base component of hypervisor components
Enhancing Hypervisor and Cloud Solutions Using Embedded Linux Iisko Lappalainen MontaVista Setting the Stage This presentation will discuss the usage of Linux as a base component of hypervisor components
The QEMU/KVM Hypervisor
 The /KVM Hypervisor Understanding what's powering your virtual machine Dr. David Alan Gilbert [email protected] 2015-10-14 Topics Hypervisors and where /KVM sits Components of a virtual machine KVM Devices:
The /KVM Hypervisor Understanding what's powering your virtual machine Dr. David Alan Gilbert [email protected] 2015-10-14 Topics Hypervisors and where /KVM sits Components of a virtual machine KVM Devices:
Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014)
 Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014) ManolisMarazakis ([email protected]) Institute of Computer Science (ICS) Foundation
Virtualization in the ARMv7 Architecture Lecture for the Embedded Systems Course CSD, University of Crete (May 20, 2014) ManolisMarazakis ([email protected]) Institute of Computer Science (ICS) Foundation
RED HAT ENTERPRISE VIRTUALIZATION & CLOUD COMPUTING
 RED HAT ENTERPRISE VIRTUALIZATION & CLOUD COMPUTING James Rankin Senior Solutions Architect Red Hat, Inc. 1 KVM BACKGROUND Project started in October 2006 by Qumranet - Submitted to Kernel maintainers
RED HAT ENTERPRISE VIRTUALIZATION & CLOUD COMPUTING James Rankin Senior Solutions Architect Red Hat, Inc. 1 KVM BACKGROUND Project started in October 2006 by Qumranet - Submitted to Kernel maintainers
Mentor Embedded Automotive Solutions
 Mentor Embedded Automotive Solutions Overview May 2013 mentor.com/embedded Android is a trademark of Google Inc. Use of this trademark is subject to Google Permissions. Linux is the registered trademark
Mentor Embedded Automotive Solutions Overview May 2013 mentor.com/embedded Android is a trademark of Google Inc. Use of this trademark is subject to Google Permissions. Linux is the registered trademark
Virtualization. Types of Interfaces
 Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE
 MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
MODULE 3 VIRTUALIZED DATA CENTER COMPUTE Module 3: Virtualized Data Center Compute Upon completion of this module, you should be able to: Describe compute virtualization Discuss the compute virtualization
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines
 Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
Basics in Energy Information (& Communication) Systems Virtualization / Virtual Machines Dr. Johann Pohany, Virtualization Virtualization deals with extending or replacing an existing interface so as to
Next Generation Now: Red Hat Enterprise Linux 6 Virtualization A Unique Cloud Approach. Jeff Ruby Channel Manager [email protected]
 Next Generation Now: Virtualization A Unique Cloud Approach Jeff Ruby Channel Manager [email protected] Introducing Extensive improvements in every dimension Efficiency, scalability and reliability Unprecedented
Next Generation Now: Virtualization A Unique Cloud Approach Jeff Ruby Channel Manager [email protected] Introducing Extensive improvements in every dimension Efficiency, scalability and reliability Unprecedented
KVM Architecture Overview
 KVM Architecture Overview 2015 Edition Stefan Hajnoczi 1 Introducing KVM virtualization KVM hypervisor runs virtual machines on Linux hosts Mature on x86, recent progress on ARM and
KVM Architecture Overview 2015 Edition Stefan Hajnoczi 1 Introducing KVM virtualization KVM hypervisor runs virtual machines on Linux hosts Mature on x86, recent progress on ARM and
KVM, OpenStack, and the Open Cloud
 KVM, OpenStack, and the Open Cloud Adam Jollans, IBM & Mike Kadera, Intel CloudOpen Europe - October 13, 2014 13Oct14 Open VirtualizaGon Alliance 1 Agenda A Brief History of VirtualizaGon KVM Architecture
KVM, OpenStack, and the Open Cloud Adam Jollans, IBM & Mike Kadera, Intel CloudOpen Europe - October 13, 2014 13Oct14 Open VirtualizaGon Alliance 1 Agenda A Brief History of VirtualizaGon KVM Architecture
FPGA Accelerator Virtualization in an OpenPOWER cloud. Fei Chen, Yonghua Lin IBM China Research Lab
 FPGA Accelerator Virtualization in an OpenPOWER cloud Fei Chen, Yonghua Lin IBM China Research Lab Trend of Acceleration Technology Acceleration in Cloud is Taking Off Used FPGA to accelerate Bing search
FPGA Accelerator Virtualization in an OpenPOWER cloud Fei Chen, Yonghua Lin IBM China Research Lab Trend of Acceleration Technology Acceleration in Cloud is Taking Off Used FPGA to accelerate Bing search
Virtualization. Pradipta De [email protected]
 Virtualization Pradipta De [email protected] Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
Virtualization Pradipta De [email protected] Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
A Virtualized Linux Integrity Subsystem for Trusted Cloud Computing
 A Virtualized Linux Integrity Subsystem for Trusted Cloud Computing Stefan Berger Joint work with: Kenneth Goldman, Dimitrios Pendarakis, David Safford, Mimi Zohar IBM T.J. Watson Research Center 09/21/2011
A Virtualized Linux Integrity Subsystem for Trusted Cloud Computing Stefan Berger Joint work with: Kenneth Goldman, Dimitrios Pendarakis, David Safford, Mimi Zohar IBM T.J. Watson Research Center 09/21/2011
A general-purpose virtualization service for HPC on cloud computing: an application to GPUs
 A general-purpose virtualization service for HPC on cloud computing: an application to GPUs R.Montella, G.Coviello, G.Giunta* G. Laccetti #, F. Isaila, J. Garcia Blas *Department of Applied Science University
A general-purpose virtualization service for HPC on cloud computing: an application to GPUs R.Montella, G.Coviello, G.Giunta* G. Laccetti #, F. Isaila, J. Garcia Blas *Department of Applied Science University
KVM: A Hypervisor for All Seasons. Avi Kivity [email protected]
 KVM: A Hypervisor for All Seasons Avi Kivity [email protected] November 2007 Virtualization Simulation of computer system in software Components Processor: register state, instructions, exceptions Memory
KVM: A Hypervisor for All Seasons Avi Kivity [email protected] November 2007 Virtualization Simulation of computer system in software Components Processor: register state, instructions, exceptions Memory
Beyond Virtualization: A Novel Software Architecture for Multi-Core SoCs. Jim Ready September 18, 2012
 Beyond Virtualization: A Novel Software Architecture for Multi-Core SoCs Jim Ready September 18, 2012 How HW guys view the world SW Software HW How SW guys view the world SW HW Reality The SoC Software
Beyond Virtualization: A Novel Software Architecture for Multi-Core SoCs Jim Ready September 18, 2012 How HW guys view the world SW Software HW How SW guys view the world SW HW Reality The SoC Software
COM 444 Cloud Computing
 COM 444 Cloud Computing Lec 3: Virtual Machines and Virtualization of Clusters and Datacenters Prof. Dr. Halûk Gümüşkaya [email protected] [email protected] http://www.gumuskaya.com Virtual
COM 444 Cloud Computing Lec 3: Virtual Machines and Virtualization of Clusters and Datacenters Prof. Dr. Halûk Gümüşkaya [email protected] [email protected] http://www.gumuskaya.com Virtual
Enterprise-Class Virtualization with Open Source Technologies
 Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Enterprise-Class Virtualization with Open Source Technologies Alex Vasilevsky CTO & Founder Virtual Iron Software June 14, 2006 Virtualization Overview Traditional x86 Architecture Each server runs single
Lecture 2 Cloud Computing & Virtualization. Cloud Application Development (SE808, School of Software, Sun Yat-Sen University) Yabo (Arber) Xu
 Lecture 2 Cloud Computing & Virtualization Cloud Application Development (SE808, School of Software, Sun Yat-Sen University) Yabo (Arber) Xu Outline Introduction to Virtualization The Major Approaches
Lecture 2 Cloud Computing & Virtualization Cloud Application Development (SE808, School of Software, Sun Yat-Sen University) Yabo (Arber) Xu Outline Introduction to Virtualization The Major Approaches
SierraVMI Sizing Guide
 SierraVMI Sizing Guide July 2015 SierraVMI Sizing Guide This document provides guidelines for choosing the optimal server hardware to host the SierraVMI gateway and the Android application server. The
SierraVMI Sizing Guide July 2015 SierraVMI Sizing Guide This document provides guidelines for choosing the optimal server hardware to host the SierraVMI gateway and the Android application server. The
Virtualization for Hard Real-Time Applications Partition where you can Virtualize where you have to
 Virtualization for Hard Real-Time Applications Partition where you can Virtualize where you have to Hanspeter Vogel Triadem Solutions AG Real-Time Systems GmbH Gartenstrasse 33 D-88212 Ravensburg Germany
Virtualization for Hard Real-Time Applications Partition where you can Virtualize where you have to Hanspeter Vogel Triadem Solutions AG Real-Time Systems GmbH Gartenstrasse 33 D-88212 Ravensburg Germany
Microkernels, virtualization, exokernels. Tutorial 1 CSC469
 Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Secure Containers. Jan 2015 www.imgtec.com. Imagination Technologies HGI Dec, 2014 p1
 Secure Containers Jan 2015 www.imgtec.com Imagination Technologies HGI Dec, 2014 p1 What are we protecting? Sensitive assets belonging to the user and the service provider Network Monitor unauthorized
Secure Containers Jan 2015 www.imgtec.com Imagination Technologies HGI Dec, 2014 p1 What are we protecting? Sensitive assets belonging to the user and the service provider Network Monitor unauthorized
Uses for Virtual Machines. Virtual Machines. There are several uses for virtual machines:
 Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
H MICRO CASE STUDY. Device API + IPC mechanism. Electrical and Functional characterization of HMicro s ECG patch
 H MICRO CASE STUDY HMicro HMicro is a wireless healthcare chip company to enable industry s first fully disposable wireless patches with high reliability, high data integrity, low cost, small form factor
H MICRO CASE STUDY HMicro HMicro is a wireless healthcare chip company to enable industry s first fully disposable wireless patches with high reliability, high data integrity, low cost, small form factor
Best Practices for Monitoring Databases on VMware. Dean Richards Senior DBA, Confio Software
 Best Practices for Monitoring Databases on VMware Dean Richards Senior DBA, Confio Software 1 Who Am I? 20+ Years in Oracle & SQL Server DBA and Developer Worked for Oracle Consulting Specialize in Performance
Best Practices for Monitoring Databases on VMware Dean Richards Senior DBA, Confio Software 1 Who Am I? 20+ Years in Oracle & SQL Server DBA and Developer Worked for Oracle Consulting Specialize in Performance
Chapter 14 Virtual Machines
 Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Operating Systems: Internals and Design Principles Chapter 14 Virtual Machines Eighth Edition By William Stallings Virtual Machines (VM) Virtualization technology enables a single PC or server to simultaneously
Deeply Embedded Real-Time Hypervisors for the Automotive Domain Dr. Gary Morgan, ETAS/ESC
 Deeply Embedded Real-Time Hypervisors for the Automotive Domain Dr. Gary Morgan, ETAS/ESC 1 Public ETAS/ESC 2014-02-20 ETAS GmbH 2014. All rights reserved, also regarding any disposal, exploitation, reproduction,
Deeply Embedded Real-Time Hypervisors for the Automotive Domain Dr. Gary Morgan, ETAS/ESC 1 Public ETAS/ESC 2014-02-20 ETAS GmbH 2014. All rights reserved, also regarding any disposal, exploitation, reproduction,
Full and Para Virtualization
 Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
KVM, OpenStack, and the Open Cloud
 KVM, OpenStack, and the Open Cloud Adam Jollans, IBM Southern California Linux Expo February 2015 1 Agenda A Brief History of VirtualizaJon KVM Architecture OpenStack Architecture KVM and OpenStack Case
KVM, OpenStack, and the Open Cloud Adam Jollans, IBM Southern California Linux Expo February 2015 1 Agenda A Brief History of VirtualizaJon KVM Architecture OpenStack Architecture KVM and OpenStack Case
Next Generation Operating Systems
 Next Generation Operating Systems Zeljko Susnjar, Cisco CTG June 2015 The end of CPU scaling Future computing challenges Power efficiency Performance == parallelism Cisco Confidential 2 Paradox of the
Next Generation Operating Systems Zeljko Susnjar, Cisco CTG June 2015 The end of CPU scaling Future computing challenges Power efficiency Performance == parallelism Cisco Confidential 2 Paradox of the
Red Hat enterprise virtualization 3.0 feature comparison
 Red Hat enterprise virtualization 3.0 feature comparison at a glance Red Hat Enterprise is the first fully open source, enterprise ready virtualization platform Compare the functionality of RHEV to VMware
Red Hat enterprise virtualization 3.0 feature comparison at a glance Red Hat Enterprise is the first fully open source, enterprise ready virtualization platform Compare the functionality of RHEV to VMware
Hardware Based Virtualization Technologies. Elsie Wahlig [email protected] Platform Software Architect
 Hardware Based Virtualization Technologies Elsie Wahlig [email protected] Platform Software Architect Outline What is Virtualization? Evolution of Virtualization AMD Virtualization AMD s IO Virtualization
Hardware Based Virtualization Technologies Elsie Wahlig [email protected] Platform Software Architect Outline What is Virtualization? Evolution of Virtualization AMD Virtualization AMD s IO Virtualization
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies
 Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
Virtualization Technologies and Blackboard: The Future of Blackboard Software on Multi-Core Technologies Kurt Klemperer, Principal System Performance Engineer [email protected] Agenda Session Length:
Virtual Machine Security
 Virtual Machine Security CSE497b - Spring 2007 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse497b-s07/ 1 Operating System Quandary Q: What is the primary goal
Virtual Machine Security CSE497b - Spring 2007 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse497b-s07/ 1 Operating System Quandary Q: What is the primary goal
Intro to Virtualization
 Cloud@Ceid Seminars Intro to Virtualization Christos Alexakos Computer Engineer, MSc, PhD C. Sysadmin at Pattern Recognition Lab 1 st Seminar 19/3/2014 Contents What is virtualization How it works Hypervisor
Cloud@Ceid Seminars Intro to Virtualization Christos Alexakos Computer Engineer, MSc, PhD C. Sysadmin at Pattern Recognition Lab 1 st Seminar 19/3/2014 Contents What is virtualization How it works Hypervisor
The MIPS architecture and virtualization
 The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
The High Performance Internet of Things: using GVirtuS for gluing cloud computing and ubiquitous connected devices
 WS on Models, Algorithms and Methodologies for Hierarchical Parallelism in new HPC Systems The High Performance Internet of Things: using GVirtuS for gluing cloud computing and ubiquitous connected devices
WS on Models, Algorithms and Methodologies for Hierarchical Parallelism in new HPC Systems The High Performance Internet of Things: using GVirtuS for gluing cloud computing and ubiquitous connected devices
How To Stop A Malicious Process From Running On A Hypervisor
 Hypervisor-Based Systems for Malware Detection and Prevention Yoshihiro Oyama ( 大 山 恵 弘 ) The University of Electro-Communications ( 電 気 通 信 大 学 ), Tokyo, Japan This Talk I introduce two hypervisor-based
Hypervisor-Based Systems for Malware Detection and Prevention Yoshihiro Oyama ( 大 山 恵 弘 ) The University of Electro-Communications ( 電 気 通 信 大 学 ), Tokyo, Japan This Talk I introduce two hypervisor-based
A quantitative comparison between xen and kvm
 Home Search Collections Journals About Contact us My IOPscience A quantitative comparison between xen and kvm This content has been downloaded from IOPscience. Please scroll down to see the full text.
Home Search Collections Journals About Contact us My IOPscience A quantitative comparison between xen and kvm This content has been downloaded from IOPscience. Please scroll down to see the full text.
Securing your Virtual Datacenter. Part 1: Preventing, Mitigating Privilege Escalation
 Securing your Virtual Datacenter Part 1: Preventing, Mitigating Privilege Escalation Before We Start... Today's discussion is by no means an exhaustive discussion of the security implications of virtualization
Securing your Virtual Datacenter Part 1: Preventing, Mitigating Privilege Escalation Before We Start... Today's discussion is by no means an exhaustive discussion of the security implications of virtualization
Hypervisors. Introduction. Introduction. Introduction. Introduction. Introduction. Credits:
 Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Hypervisors Credits: P. Chaganti Xen Virtualization A practical handbook D. Chisnall The definitive guide to Xen Hypervisor G. Kesden Lect. 25 CS 15-440 G. Heiser UNSW/NICTA/OKL Virtualization is a technique
Mentor Embedded IVI Solutions
 Mentor Embedded IVI Solutions Infotainment Instrument Cluster Andrew Patterson [email protected] Business Development Director Automotive Embedded Software mentor.com/embedded Android is a trademark
Mentor Embedded IVI Solutions Infotainment Instrument Cluster Andrew Patterson [email protected] Business Development Director Automotive Embedded Software mentor.com/embedded Android is a trademark
Virtualization for Cloud Computing
 Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
CSE597a - Cell Phone OS Security. Cellphone Hardware. William Enck Prof. Patrick McDaniel
 CSE597a - Cell Phone OS Security Cellphone Hardware William Enck Prof. Patrick McDaniel CSE597a - Cellular Phone Operating Systems Security - Spring 2009 - Instructors McDaniel and Enck 1 2 Embedded Systems
CSE597a - Cell Phone OS Security Cellphone Hardware William Enck Prof. Patrick McDaniel CSE597a - Cellular Phone Operating Systems Security - Spring 2009 - Instructors McDaniel and Enck 1 2 Embedded Systems
Operating Systems. Lecture 03. February 11, 2013
 Operating Systems Lecture 03 February 11, 2013 Goals for Today Interrupts, traps and signals Hardware Protection System Calls Interrupts, Traps, and Signals The occurrence of an event is usually signaled
Operating Systems Lecture 03 February 11, 2013 Goals for Today Interrupts, traps and signals Hardware Protection System Calls Interrupts, Traps, and Signals The occurrence of an event is usually signaled
Cloud Operating Systems for Servers
 Cloud Operating Systems for Servers Mike Day Distinguished Engineer, Virtualization and Linux August 20, 2014 [email protected] 1 What Makes a Good Cloud Operating System?! Consumes Few Resources! Fast
Cloud Operating Systems for Servers Mike Day Distinguished Engineer, Virtualization and Linux August 20, 2014 [email protected] 1 What Makes a Good Cloud Operating System?! Consumes Few Resources! Fast
KVM: Kernel-based Virtualization Driver
 KVM: Kernel-based Virtualization Driver White Paper Overview The current interest in virtualization has led to the creation of several different hypervisors. Most of these, however, predate hardware-assisted
KVM: Kernel-based Virtualization Driver White Paper Overview The current interest in virtualization has led to the creation of several different hypervisors. Most of these, however, predate hardware-assisted
Monitoring Databases on VMware
 Monitoring Databases on VMware Ensure Optimum Performance with the Correct Metrics By Dean Richards, Manager, Sales Engineering Confio Software 4772 Walnut Street, Suite 100 Boulder, CO 80301 www.confio.com
Monitoring Databases on VMware Ensure Optimum Performance with the Correct Metrics By Dean Richards, Manager, Sales Engineering Confio Software 4772 Walnut Street, Suite 100 Boulder, CO 80301 www.confio.com
Performance tuning Xen
 Performance tuning Xen Roger Pau Monné [email protected] Madrid 8th of November, 2013 Xen Architecture Control Domain NetBSD or Linux device model (qemu) Hardware Drivers toolstack netback blkback Paravirtualized
Performance tuning Xen Roger Pau Monné [email protected] Madrid 8th of November, 2013 Xen Architecture Control Domain NetBSD or Linux device model (qemu) Hardware Drivers toolstack netback blkback Paravirtualized
Module I-7410 Advanced Linux FS-11 Part1: Virtualization with KVM
 Bern University of Applied Sciences Engineering and Information Technology Module I-7410 Advanced Linux FS-11 Part1: Virtualization with KVM By Franz Meyer Version 1.0 February 2011 Virtualization Architecture
Bern University of Applied Sciences Engineering and Information Technology Module I-7410 Advanced Linux FS-11 Part1: Virtualization with KVM By Franz Meyer Version 1.0 February 2011 Virtualization Architecture
Compromise-as-a-Service
 ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg 3/31/14 Compromise-as-a-Service Our PleAZURE Felix Wilhelm & Matthias Luft {fwilhelm, mluft}@ernw.de ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg Agenda
ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg 3/31/14 Compromise-as-a-Service Our PleAZURE Felix Wilhelm & Matthias Luft {fwilhelm, mluft}@ernw.de ERNW GmbH Carl-Bosch-Str. 4 D-69115 Heidelberg Agenda
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR
 GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
GUEST OPERATING SYSTEM BASED PERFORMANCE COMPARISON OF VMWARE AND XEN HYPERVISOR ANKIT KUMAR, SAVITA SHIWANI 1 M. Tech Scholar, Software Engineering, Suresh Gyan Vihar University, Rajasthan, India, Email:
Virtual Machine Monitors. Dr. Marc E. Fiuczynski Research Scholar Princeton University
 Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
High Performance or Cycle Accuracy?
 CHIP DESIGN High Performance or Cycle Accuracy? You can have both! Bill Neifert, Carbon Design Systems Rob Kaye, ARM ATC-100 AGENDA Modelling 101 & Programmer s View (PV) Models Cycle Accurate Models Bringing
CHIP DESIGN High Performance or Cycle Accuracy? You can have both! Bill Neifert, Carbon Design Systems Rob Kaye, ARM ATC-100 AGENDA Modelling 101 & Programmer s View (PV) Models Cycle Accurate Models Bringing
Virtualization System Vulnerability Discovery Framework. Speaker: Qinghao Tang Title:360 Marvel Team Leader
 Virtualization System Vulnerability Discovery Framework Speaker: Qinghao Tang Title:360 Marvel Team Leader 1 360 Marvel Team Established in May 2015, the first professional could computing and virtualization
Virtualization System Vulnerability Discovery Framework Speaker: Qinghao Tang Title:360 Marvel Team Leader 1 360 Marvel Team Established in May 2015, the first professional could computing and virtualization
PERFORMANCE ANALYSIS OF KERNEL-BASED VIRTUAL MACHINE
 PERFORMANCE ANALYSIS OF KERNEL-BASED VIRTUAL MACHINE Sudha M 1, Harish G M 2, Nandan A 3, Usha J 4 1 Department of MCA, R V College of Engineering, Bangalore : 560059, India [email protected] 2 Department
PERFORMANCE ANALYSIS OF KERNEL-BASED VIRTUAL MACHINE Sudha M 1, Harish G M 2, Nandan A 3, Usha J 4 1 Department of MCA, R V College of Engineering, Bangalore : 560059, India [email protected] 2 Department
KVM in Embedded Requirements, Experiences, Open Challenges
 Corporate Technology KVM in Embedded Requirements, Experiences, Open Challenges Jan Kiszka, Siemens AG Corporate Competence Center Embedded Linux [email protected] Copyright Siemens AG 2009. All rights
Corporate Technology KVM in Embedded Requirements, Experiences, Open Challenges Jan Kiszka, Siemens AG Corporate Competence Center Embedded Linux [email protected] Copyright Siemens AG 2009. All rights
Cloud^H^H^H^H^H Virtualization Technology. Andrew Jones ([email protected]) May 2011
 Cloud^H^H^H^H^H Virtualization Technology Andrew Jones ([email protected]) May 2011 Outline Promise to not use the word Cloud again...but still give a couple use cases for Virtualization Emulation it's
Cloud^H^H^H^H^H Virtualization Technology Andrew Jones ([email protected]) May 2011 Outline Promise to not use the word Cloud again...but still give a couple use cases for Virtualization Emulation it's
Virtualization Technologies
 12 January 2010 Virtualization Technologies Alex Landau ([email protected]) IBM Haifa Research Lab What is virtualization? Virtualization is way to run multiple operating systems and user applications on
12 January 2010 Virtualization Technologies Alex Landau ([email protected]) IBM Haifa Research Lab What is virtualization? Virtualization is way to run multiple operating systems and user applications on
StACC: St Andrews Cloud Computing Co laboratory. A Performance Comparison of Clouds. Amazon EC2 and Ubuntu Enterprise Cloud
 StACC: St Andrews Cloud Computing Co laboratory A Performance Comparison of Clouds Amazon EC2 and Ubuntu Enterprise Cloud Jonathan S Ward StACC (pronounced like 'stack') is a research collaboration launched
StACC: St Andrews Cloud Computing Co laboratory A Performance Comparison of Clouds Amazon EC2 and Ubuntu Enterprise Cloud Jonathan S Ward StACC (pronounced like 'stack') is a research collaboration launched
Fastboot Techniques for x86 Architectures. Marcus Bortel Field Application Engineer QNX Software Systems
 Fastboot Techniques for x86 Architectures Marcus Bortel Field Application Engineer QNX Software Systems Agenda Introduction BIOS and BIOS boot time Fastboot versus BIOS? Fastboot time Customizing the boot
Fastboot Techniques for x86 Architectures Marcus Bortel Field Application Engineer QNX Software Systems Agenda Introduction BIOS and BIOS boot time Fastboot versus BIOS? Fastboot time Customizing the boot
KVM, OpenStack and the Open Cloud SUSECon November 2015
 KVM, OpenStack and the Open Cloud SUSECon November 2015 Adam Jollans Program Director, Linux & Open Virtualization Strategy IBM Agenda A Brief History of Virtualization KVM Architecture OpenStack Architecture
KVM, OpenStack and the Open Cloud SUSECon November 2015 Adam Jollans Program Director, Linux & Open Virtualization Strategy IBM Agenda A Brief History of Virtualization KVM Architecture OpenStack Architecture
Flight Processor Virtualization
 National Aeronautics and Space Administration Flight Processor Virtualization Alan Cudmore / Code 582 9/11/2013 www.nasa.gov 1 Agenda Introduction to Virtualization Benefits of Virtualization for Satellite
National Aeronautics and Space Administration Flight Processor Virtualization Alan Cudmore / Code 582 9/11/2013 www.nasa.gov 1 Agenda Introduction to Virtualization Benefits of Virtualization for Satellite
Distributed and Cloud Computing
 Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
Distributed and Cloud Computing K. Hwang, G. Fox and J. Dongarra Chapter 3: Virtual Machines and Virtualization of Clusters and datacenters Adapted from Kai Hwang University of Southern California March
7 Things You Need to Know about Virtual Mobile Infrastructure
 7 Things You Need to Know about Virtual Mobile Infrastructure Executive Summary Employees are bringing their phones and tablets to work in droves. This tidal wave of unmanaged devices has forced IT departments
7 Things You Need to Know about Virtual Mobile Infrastructure Executive Summary Employees are bringing their phones and tablets to work in droves. This tidal wave of unmanaged devices has forced IT departments
Real-time KVM from the ground up
 Real-time KVM from the ground up KVM Forum 2015 Rik van Riel Red Hat Real-time KVM What is real time? Hardware pitfalls Realtime preempt Linux kernel patch set KVM & qemu pitfalls KVM configuration Scheduling
Real-time KVM from the ground up KVM Forum 2015 Rik van Riel Red Hat Real-time KVM What is real time? Hardware pitfalls Realtime preempt Linux kernel patch set KVM & qemu pitfalls KVM configuration Scheduling
Chapter 16: Virtual Machines. Operating System Concepts 9 th Edition
 Chapter 16: Virtual Machines Silberschatz, Galvin and Gagne 2013 Chapter 16: Virtual Machines Overview History Benefits and Features Building Blocks Types of Virtual Machines and Their Implementations
Chapter 16: Virtual Machines Silberschatz, Galvin and Gagne 2013 Chapter 16: Virtual Machines Overview History Benefits and Features Building Blocks Types of Virtual Machines and Their Implementations
High-performance vnic framework for hypervisor-based NFV with userspace vswitch Yoshihiro Nakajima, Hitoshi Masutani, Hirokazu Takahashi NTT Labs.
 High-performance vnic framework for hypervisor-based NFV with userspace vswitch Yoshihiro Nakajima, Hitoshi Masutani, Hirokazu Takahashi NTT Labs. 0 Outline Motivation and background Issues on current
High-performance vnic framework for hypervisor-based NFV with userspace vswitch Yoshihiro Nakajima, Hitoshi Masutani, Hirokazu Takahashi NTT Labs. 0 Outline Motivation and background Issues on current
Virtual Switching Without a Hypervisor for a More Secure Cloud
 ing Without a for a More Secure Cloud Xin Jin Princeton University Joint work with Eric Keller(UPenn) and Jennifer Rexford(Princeton) 1 Public Cloud Infrastructure Cloud providers offer computing resources
ing Without a for a More Secure Cloud Xin Jin Princeton University Joint work with Eric Keller(UPenn) and Jennifer Rexford(Princeton) 1 Public Cloud Infrastructure Cloud providers offer computing resources
SUSE Linux Enterprise 10 SP2: Virtualization Technology Support
 Technical White Paper LINUX OPERATING SYSTEMS www.novell.com SUSE Linux Enterprise 10 SP2: Virtualization Technology Support Content and modifications. The contents of this document are not part of the
Technical White Paper LINUX OPERATING SYSTEMS www.novell.com SUSE Linux Enterprise 10 SP2: Virtualization Technology Support Content and modifications. The contents of this document are not part of the
Customer Experience. Silicon. Support & Professional Eng. Services. Freescale Provided SW & Solutions
 September 2013 Silicon Support & Professional Eng. Services Customer Experience Freescale Provided SW & Solutions Provide Valued Software, Support & Professional Engineering Services, Competitively 2 Customer
September 2013 Silicon Support & Professional Eng. Services Customer Experience Freescale Provided SW & Solutions Provide Valued Software, Support & Professional Engineering Services, Competitively 2 Customer
Comparing Free Virtualization Products
 A S P E I T Tr a i n i n g Comparing Free Virtualization Products A WHITE PAPER PREPARED FOR ASPE BY TONY UNGRUHE www.aspe-it.com toll-free: 877-800-5221 Comparing Free Virtualization Products In this
A S P E I T Tr a i n i n g Comparing Free Virtualization Products A WHITE PAPER PREPARED FOR ASPE BY TONY UNGRUHE www.aspe-it.com toll-free: 877-800-5221 Comparing Free Virtualization Products In this
Nested Virtualization
 Nested Virtualization Dongxiao Xu, Xiantao Zhang, Yang Zhang May 9, 2013 Agenda Nested Virtualization Overview Dive into Nested Virtualization Details Nested CPU Virtualization Nested MMU Virtualization
Nested Virtualization Dongxiao Xu, Xiantao Zhang, Yang Zhang May 9, 2013 Agenda Nested Virtualization Overview Dive into Nested Virtualization Details Nested CPU Virtualization Nested MMU Virtualization
x86 ISA Modifications to support Virtual Machines
 x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
x86 ISA Modifications to support Virtual Machines Douglas Beal Ashish Kumar Gupta CSE 548 Project Outline of the talk Review of Virtual Machines What complicates Virtualization Technique for Virtualization
Virtual Machines. www.viplavkambli.com
 1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
1 Virtual Machines A virtual machine (VM) is a "completely isolated guest operating system installation within a normal host operating system". Modern virtual machines are implemented with either software
How to Secure Infrastructure Clouds with Trusted Computing Technologies
 How to Secure Infrastructure Clouds with Trusted Computing Technologies Nicolae Paladi Swedish Institute of Computer Science 2 Contents 1. Infrastructure-as-a-Service 2. Security challenges of IaaS 3.
How to Secure Infrastructure Clouds with Trusted Computing Technologies Nicolae Paladi Swedish Institute of Computer Science 2 Contents 1. Infrastructure-as-a-Service 2. Security challenges of IaaS 3.
Assessing the Performance of Virtualization Technologies for NFV: a Preliminary Benchmarking
 Assessing the Performance of Virtualization Technologies for NFV: a Preliminary Benchmarking Roberto Bonafiglia, Ivano Cerrato, Francesco Ciaccia, Mario Nemirovsky, Fulvio Risso Politecnico di Torino,
Assessing the Performance of Virtualization Technologies for NFV: a Preliminary Benchmarking Roberto Bonafiglia, Ivano Cerrato, Francesco Ciaccia, Mario Nemirovsky, Fulvio Risso Politecnico di Torino,
Virtualization: Know your options on Ubuntu. Nick Barcet. Ubuntu Server Product Manager [email protected]
 Virtualization: Know your options on Ubuntu Nick Barcet Ubuntu Server Product Manager [email protected] Agenda Defi nitions Host virtualization tools Desktop virtualization tools Ubuntu as a guest
Virtualization: Know your options on Ubuntu Nick Barcet Ubuntu Server Product Manager [email protected] Agenda Defi nitions Host virtualization tools Desktop virtualization tools Ubuntu as a guest
WIND RIVER SECURE ANDROID CAPABILITY
 WIND RIVER SECURE ANDROID CAPABILITY Cyber warfare has swiftly migrated from hacking into enterprise networks and the Internet to targeting, and being triggered from, mobile devices. With the recent explosion
WIND RIVER SECURE ANDROID CAPABILITY Cyber warfare has swiftly migrated from hacking into enterprise networks and the Internet to targeting, and being triggered from, mobile devices. With the recent explosion
IOS110. Virtualization 5/27/2014 1
 IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
IOS110 Virtualization 5/27/2014 1 Agenda What is Virtualization? Types of Virtualization. Advantages and Disadvantages. Virtualization software Hyper V What is Virtualization? Virtualization Refers to
9/26/2011. What is Virtualization? What are the different types of virtualization.
 CSE 501 Monday, September 26, 2011 Kevin Cleary [email protected] What is Virtualization? What are the different types of virtualization. Practical Uses Popular virtualization products Demo Question,
CSE 501 Monday, September 26, 2011 Kevin Cleary [email protected] What is Virtualization? What are the different types of virtualization. Practical Uses Popular virtualization products Demo Question,
HRG Assessment: Stratus everrun Enterprise
 HRG Assessment: Stratus everrun Enterprise Today IT executive decision makers and their technology recommenders are faced with escalating demands for more effective technology based solutions while at
HRG Assessment: Stratus everrun Enterprise Today IT executive decision makers and their technology recommenders are faced with escalating demands for more effective technology based solutions while at
