Peace and Justice in Cyberspace
|
|
|
- Katherine Carpenter
- 8 years ago
- Views:
Transcription
1 Peace and Justice in Cyberspace Potential new international legal mechanisms against global cyberattacks and other global cybercrime An International Criminal Tribunal for Cyberspace International cybercrime law Prosecution for the Tribunal Police investigation for the Tribunal By Judge Stein Schjolberg, Court of Appeal, Norway (2012) A discussion of digital risks should be on the agenda of board meetings everywhere as cyber attacks become more frequent, more creative and more disruptive. Cybercrime is an international business aided by those countries without the legislation framework to tackle it. If we are serious about combating cybercrime, we need to increase international communication and collaboration between governments and businesses, and move towards uniform global regulation. Lord Levene, Chairman of Lloyds (2010)
2 Potential new international legal mechanisms against global cyberattacks and other global cybercrime There can be no peace without justice, no justice without law and no meaningful law without a Court to decide what is just and lawful under any given circumstances. Benjamin B. Ferencz, USA, Prosecutor at the Nuremberg War Crimes Tribunal (1920-) 1. An International Criminal Court or Tribunal for Cyberspace The most serious global cyberattacks in the recent years, have revealed that almost nobody has been investigated, and nobody has been prosecuted and sentenced. Such acts need to be included in a global treaty or a set of treaties, and investigated and prosecuted before an international criminal court or tribunal. The international community reached on July 17, 1998, an historic milestone in the development of a permanent International Criminal Law, when 120 States adopted the Rome Statute of the International Criminal Court. 160 States was present in Rome and it is understood that launching the Rome Statute was based on complete consensus among all present States. The Rome Statute entered into force on July 1, 2002, after ratification of 60 States. At the 10th Anniversary on July 1, 2012, 121 States have made their ratification. China, Russia, and the United States have not made a ratification of the Rome Statute of the International Criminal Court. An independent Criminal Court or Tribunal for Cyberspace is urgently needed to enable the global justice to take measures on global cyberattacks of the most serious global concern against critical government and private industry information infrastructures or endanger peace. These could be ensured by expanding the jurisdiction of the International Criminal Court. Considering the ratification positions, any Court solution for Cyberspace that may include acceptance by China, Russia, and the United States. A Tribunal, that traditionally is a preliminary solution, is currently the only global alternative. After some years of experience, the global community may then try for a more permanent global court solution for cyberspace. 2
3 2. The structure of an International Criminal Tribunal The United Nations Security Council should under Chapter Seven of the United Nations Charter establish an International Criminal Tribunal for Cyberspace for the investigation, prosecution, and sentencing of global cyberattacks. The United Nations Charter is a constituent treaty, and it is binding for all members of the United Nations. The United Nations Security Council have previously asserted its rights, authority and jurisdiction based on the United Nations Charter, when it established the International Criminal Tribunal for Rwanda and the International Criminal Tribunal for the former Yugoslavia. The United Nations Security Council has always authority to refer cases to the International Criminal Tribunal for Cyberspace, and may request for an investigation. Cyberspace, as the fifth common space, after land, sea, air and outer space, is in great need for coordination, cooperation and legal measures among all nations. It is necessary to make the international community aware of the need for a global response to the urgent and increasing cyberthreats and acts of cyber warfare. Peace and justice in cyberspace should be protected by international law through a treaty or a set of treaties under the United Nations. An International Criminal Tribunal for Cyberspace should be a fully independent international criminal tribunal established to promote the rule of international law and ensure that the gravest global cyberattacks in cyberspace do not go unpunished. The Chambers of an International Criminal Tribunal for Cyberspace should consist of 16 permanent judges, all appointed by the United Nations. The judges could be divided between 3 Trial Chambers and one Appeals Chamber. The judges should be elected for a period of at least 4 years. One alternative may be that five of the permanent judges should be appointed from each of the five veto-wielding permanent members of the United Nations Security Council China, France, Russia, United Kingdom, and United States. The Seat of the International Criminal Tribunal could be The Hague, or Singapore, or both. 3. Prosecution for the International Criminal Tribunal The Prosecutor, as a separate organ of the International Criminal Tribunal for Cyberspace, should be responsible for the investigation and prosecution of the most serious cyberattacks or cybercrimes of global consern. 3
4 The Prosecutors Office shall act independently of the Security Council, of any State, or any international organization, or of other organs of the Tribunal, as a separate organ of the International Criminal Tribunal. The Prosecutor should not seek or receive instructions from any government or from any external source. The prosecutor could be advised by the Prosecutors Advisory Board that may consists of five prosecutors appointed from the five veto-wielding permanent members of the United Nations Security Council China, France, Russia, United Kingdom, and United States. One alternative may be that the Advisory Board five members could have the power of each to veto any indictments before the International Criminal Tribunal for Cyberspace. Abstenation is not regarded as a veto. Prosedural matters should not be subject to a veto, and a veto should not be used to avoid a decision by the Prosecutor of opening of any investigation, or to avoid discussions of an issue. 4. Investigation for the International Criminal Tribunal The Prosecutors Office may be assisted in the investigation of cyberattacks the most serious global concern, by two pillars: a. Global law enforcements through the coordination of INTERPOL, and b. A Global Virtual Task Force. a. The General Assembly of INTERPOL has at their meeting in 2010 approved to establish the INTERPOL Global Complex for Innovation (IGCI), more recently including a Digital Crime Centre, based in Singapore. It is expected to go into full operation in 2014, and to employ a staff of about 300 people. The INTERPOL Digital Crime Centre (IDCC) will be grouped in three main areas: cybercrime investigative support, research and innovation, and cybersecurity. The IDCC is expected to: to serve as a global hub for cybercrime issues, coordinating with national cybercrime investigatigators and authorities in INTERPOL s member countries and with private partners in the technology industry. The IDCC will bring all affected groups together to generate innovative solutions leading to the ultimate goal of creating a secure cyber world. b. The Prosecutors Office should have the power to seek the most efficient assistance from experts in a Global Virtual Taskforce, established with key stakeholders in the global information and communications technology industry, financial service industry, private sector, non-governmental organizations, academia, and the global law enforcement through 4
5 INTERPOL. That may include experts from Google, Facebook, YouTube, Apple, Microsoft, and more. A Global Virtual Taskforce for the investigation and prosecution of global cyberattacks and other cybercrimes should be working together in a strong partnership, to coordinate, integrate and share information for the prevention and effectively combating such global crimes, especially for delivering real-time responses to cyberattacks. The goal is to ensure that all global legal means and resources available are used to prevent, identfy, and take realtime actions against cyber threats of the most global concern. The experts in an international taskforce should be working together as fully integrated task force partners in daily operations, either at the International Criminal Tribunal or in a Virtual collaboration. The Partnership could be agreed on in Memorandum of Understanding (MoU) with each of the partners. Such partnership may dramatically improve the Prosecutors Office ability to investigate and prosecute global cyberattacks. 5. Substantive criminal law in the Statute for an International Criminal Tribunal No international substantive cybercrime law has been recognized globally. Several governments, international organizations, and vital private institutions in the global information and financial infrastructures have been targets by global cyberattacks in the recent years. Cyberattacks of the most serious global concern, that intentionally causes substantial and comprehensive disturbance against critical communications and information infrastructure, should be included in a Statute for a International Criminal Tribunal. Illegal access, illegal interception, data interference, system interference, misuse of devices, forgery, fraud, and offences related to child pornography, could also be included in the Statute. Those acts may be prosecuted independently, whenever the conducts are considered as of the most serious cybercrimes of global concern. But the most practical applications may be as included in indictments on global cyberattacks. Including infringements on religious or political values in cybercrime legislation should be avoided. 5
6 A proposal for a provision on global cyberattaks against critical communication and information infrastructure, may be as follows: The International Tribunal shall have the power to prosecute persons committing or ordering to be committed the most serious violations of international cybercrime law, namely the following acts committed wilfully against computer systems, information systems, data, information or other property protected under the relevant international criminal law; whoever by destroying, damaging, or rendering unusable critical communication and information infrastructures, causes substantial and comprehensive disturbance to the national security, civil defence, public administration and services, public health or safety, or banking and financial services. -Those who fail to anticipate the future are in for a rude shock when it arrives. Professor Peter Grabosky Australia 6
Recommendations for potential new global legal mechanisms against global cyberattacks and other global cybercrimes
 1 Recommendations for potential new global legal mechanisms against global cyberattacks and other global cybercrimes An International Criminal Tribunal for Cyberspace (ICTC) Prosecution for the Tribunal
1 Recommendations for potential new global legal mechanisms against global cyberattacks and other global cybercrimes An International Criminal Tribunal for Cyberspace (ICTC) Prosecution for the Tribunal
A Global Treaty on Cybersecurity and Cybercrime
 Stein Schjolberg and Solange Ghernaouti-Helie A Global Treaty on Cybersecurity and Cybercrime Second edition 2011 Those who fail to anticipate the future are in for a rude shock when it arrives Professor
Stein Schjolberg and Solange Ghernaouti-Helie A Global Treaty on Cybersecurity and Cybercrime Second edition 2011 Those who fail to anticipate the future are in for a rude shock when it arrives Professor
The global challenge
 The global challenge CYBERCRIME The global challenge Cybercrime has developed from an emerging crime to a serious manifestation of crime with great practical relevance With the emerging use of computer
The global challenge CYBERCRIME The global challenge Cybercrime has developed from an emerging crime to a serious manifestation of crime with great practical relevance With the emerging use of computer
A Global Protocol on Cybersecurity and Cybercrime
 Stein Schjølberg and Solange Ghernaouti-Hélie A Global Protocol on Cybersecurity and Cybercrime An initiative for peace and security in cyberspace Cybercrimedata Stein Schjolberg and Solange Ghernaouti-Hélie
Stein Schjølberg and Solange Ghernaouti-Hélie A Global Protocol on Cybersecurity and Cybercrime An initiative for peace and security in cyberspace Cybercrimedata Stein Schjolberg and Solange Ghernaouti-Hélie
CYBERCRIME AND THE LAW
 CYBERCRIME AND THE LAW INTERNATIONAL LAW CYBERCRIME CONVENTION Convention on Cybercrime / Budapest Convention first international treaty seeking to address Internet and computer crime by harmonizing national
CYBERCRIME AND THE LAW INTERNATIONAL LAW CYBERCRIME CONVENTION Convention on Cybercrime / Budapest Convention first international treaty seeking to address Internet and computer crime by harmonizing national
Information and Observations on the Scope and Application of Universal Jurisdiction. Resolution 65/33 of the General Assembly
 United Nations General Assembly Sixty-seventh Session Sixth Committee Information and Observations on the Scope and Application of Universal Jurisdiction Resolution 65/33 of the General Assembly pursuant
United Nations General Assembly Sixty-seventh Session Sixth Committee Information and Observations on the Scope and Application of Universal Jurisdiction Resolution 65/33 of the General Assembly pursuant
We have concluded that the International Criminal Court does not advance these principles. Here is why:
 American Foreign Policy and the International Criminal Court Marc Grossman, Under Secretary for Political Affairs Remarks to the Center for Strategic and International Studies Washington, DC May 6, 2002
American Foreign Policy and the International Criminal Court Marc Grossman, Under Secretary for Political Affairs Remarks to the Center for Strategic and International Studies Washington, DC May 6, 2002
Executive Director Centre for Cyber Victim Counselling www.drjaishankar.co.nr / www.cybervictims.org
 Dr. K. Jaishankar Senior Assistant Professor Department of Criminology and Criminal Justice Manonmaniam Sundaranar University Tirunelveli, Tamil Nadu, India Executive Director Centre for Cyber Victim Counselling
Dr. K. Jaishankar Senior Assistant Professor Department of Criminology and Criminal Justice Manonmaniam Sundaranar University Tirunelveli, Tamil Nadu, India Executive Director Centre for Cyber Victim Counselling
ALBERTA S JUSTICE SYSTEM AND YOU
 ALBERTA S JUSTICE SYSTEM AND YOU This brochure will give you the facts about your justice system the major participants and the important roles that each plays. In addition, it will help you better understand
ALBERTA S JUSTICE SYSTEM AND YOU This brochure will give you the facts about your justice system the major participants and the important roles that each plays. In addition, it will help you better understand
Australia s proposed accession to the Council of Europe Convention on Cybercrime
 Assistant Secretary Telecommunications and Surveillance Law Branch National Security Law and Policy Division Attorney-General's Department 3-5 National Circuit Barton ACT 2600 Email: tslb@ag.gov.au Australia
Assistant Secretary Telecommunications and Surveillance Law Branch National Security Law and Policy Division Attorney-General's Department 3-5 National Circuit Barton ACT 2600 Email: tslb@ag.gov.au Australia
An Overview of Cybersecurity and Cybercrime in Taiwan
 An Overview of Cybersecurity and Cybercrime in Taiwan I. Introduction To strengthen Taiwan's capability to deal with information and communication security issues, the National Information and Communication
An Overview of Cybersecurity and Cybercrime in Taiwan I. Introduction To strengthen Taiwan's capability to deal with information and communication security issues, the National Information and Communication
Cyber Crime and Data Retention
 COE Convention nr 185 on cybercrime Concluded in Budapest on 23 November 2001 First comprehensive instrument underlining the seriousness of cybercrime and the possible remedies Defines a series of offences
COE Convention nr 185 on cybercrime Concluded in Budapest on 23 November 2001 First comprehensive instrument underlining the seriousness of cybercrime and the possible remedies Defines a series of offences
International Criminal Law Services. and
 International Criminal Law Services and INTERNATIONAL CRIMINAL LAW TRAINING MATERIALS FOR THE EXTRAORDINARY CHAMBERS IN THE COURTS OF CAMBODIA Copyright 2009 by International Criminal Law Services and
International Criminal Law Services and INTERNATIONAL CRIMINAL LAW TRAINING MATERIALS FOR THE EXTRAORDINARY CHAMBERS IN THE COURTS OF CAMBODIA Copyright 2009 by International Criminal Law Services and
The Geneva Protocol on Cybersecurity and Cybercrime
 The Geneva Protocol on Cybersecurity and Cybercrime Proposal for a Memorandum of Understanding (MoU) by Stein Schjolberg 1 Chief Judge I. Introduction Cyberspace is one of the great legal frontiers of
The Geneva Protocol on Cybersecurity and Cybercrime Proposal for a Memorandum of Understanding (MoU) by Stein Schjolberg 1 Chief Judge I. Introduction Cyberspace is one of the great legal frontiers of
Thank you for your communication concerning the situation in Venezuela.
 Le Bureau du Procureur The Office of the Prosecutor The Hague, 9 February 2006 Thank you for your communication concerning the situation in Venezuela. The Office of the Prosecutor has received twelve communications
Le Bureau du Procureur The Office of the Prosecutor The Hague, 9 February 2006 Thank you for your communication concerning the situation in Venezuela. The Office of the Prosecutor has received twelve communications
Global Alliance against Child Sexual Abuse Online Report of Republic of Serbia
 Global Alliance against Child Sexual Abuse Online Report of Republic of Serbia Criminal legal framework In 2009 the Republic of Serbia ratified the Convention on Cybercrime adopted in Budapest 2001 as
Global Alliance against Child Sexual Abuse Online Report of Republic of Serbia Criminal legal framework In 2009 the Republic of Serbia ratified the Convention on Cybercrime adopted in Budapest 2001 as
Harmful Interference into Satellite Telecommunications by Cyber Attack
 Kobe and QM Symposium on International Law "Diversity of Transnational Criminal Justice" Harmful Interference into Satellite Telecommunications by Cyber Attack 10 April 2015 Yuri Takaya Research Fellow/Lecturer,
Kobe and QM Symposium on International Law "Diversity of Transnational Criminal Justice" Harmful Interference into Satellite Telecommunications by Cyber Attack 10 April 2015 Yuri Takaya Research Fellow/Lecturer,
In an age where so many businesses and systems are reliant on computer systems,
 Cyber Security Laws and Policy Implications of these Laws In an age where so many businesses and systems are reliant on computer systems, there is a large incentive for maintaining the security of their
Cyber Security Laws and Policy Implications of these Laws In an age where so many businesses and systems are reliant on computer systems, there is a large incentive for maintaining the security of their
Good practices and tools for use in case management, including by front-line law enforcement authorities responding to trafficking in persons
 Distr.: General 9 December 2009 Original: English Working Group on Trafficking in Persons Vienna, 27-29 January 2010 Item 6 of the provisional agenda * Good practices and tools for use in case management,
Distr.: General 9 December 2009 Original: English Working Group on Trafficking in Persons Vienna, 27-29 January 2010 Item 6 of the provisional agenda * Good practices and tools for use in case management,
Council of Europe Project on Cybercrime in Georgia Report by Virgil Spiridon and Nigel Jones. Tbilisi 28-29, September 2009
 Council of Europe Project on Cybercrime in Georgia Report by Virgil Spiridon and Nigel Jones Tbilisi 28-29, September 2009 Presentation Contents An assessment of the Georgian view of cybercrime and current
Council of Europe Project on Cybercrime in Georgia Report by Virgil Spiridon and Nigel Jones Tbilisi 28-29, September 2009 Presentation Contents An assessment of the Georgian view of cybercrime and current
The Massachusetts Strategic Plan for Cyber Crime
 The Massachusetts Strategic Plan for Cyber Crime FALL 2007 Commonwealth of Massachusetts OFFICE OF ATTORNEY GENERAL MARTHA COAKLEY Introduction Introduction The (AGO) takes a broad view of cyber crime,
The Massachusetts Strategic Plan for Cyber Crime FALL 2007 Commonwealth of Massachusetts OFFICE OF ATTORNEY GENERAL MARTHA COAKLEY Introduction Introduction The (AGO) takes a broad view of cyber crime,
LEGISLATION ON CYBERCRIME IN NIGERIA: IMPERATIVES AND CHALLENGES
 LEGISLATION ON CYBERCRIME IN NIGERIA: IMPERATIVES AND CHALLENGES T.G. George-Maria Tyendezwa, Head, Computer Crime Prosecution Unit, Federal Ministry of Justice, OUTLINE Interconnected world The Nigerian
LEGISLATION ON CYBERCRIME IN NIGERIA: IMPERATIVES AND CHALLENGES T.G. George-Maria Tyendezwa, Head, Computer Crime Prosecution Unit, Federal Ministry of Justice, OUTLINE Interconnected world The Nigerian
Speech on Cyber Risks & Security Seminar, The EU Digital Agenda and the Cyber-security proposed Directive: A legal and a contextual approach,
 Speech on Cyber Risks & Security Seminar, The EU Digital Agenda and the Cyber-security proposed Directive: A legal and a contextual approach, Organized by American Chamber of Commerce in Cyprus, 30 October
Speech on Cyber Risks & Security Seminar, The EU Digital Agenda and the Cyber-security proposed Directive: A legal and a contextual approach, Organized by American Chamber of Commerce in Cyprus, 30 October
Global Alliance Against Child Sexual Abuse Online 2014 Reporting Form
 Global Alliance Against Child Sexual Abuse Online 2014 Reporting Form HUNGARY Policy Target No. 1 Enhancing efforts to identify victims and ensuring that they receive the necessary assistance, support
Global Alliance Against Child Sexual Abuse Online 2014 Reporting Form HUNGARY Policy Target No. 1 Enhancing efforts to identify victims and ensuring that they receive the necessary assistance, support
The History of Global Harmonization on Cybercrime Legislation - The Road to Geneva
 1 By Stein Schjolberg Chief Judge December, 2008 The History of Global Harmonization on Cybercrime Legislation - The Road to Geneva 1. Introduction... 1 2. The History... 2 3. What is cybercrime? The history
1 By Stein Schjolberg Chief Judge December, 2008 The History of Global Harmonization on Cybercrime Legislation - The Road to Geneva 1. Introduction... 1 2. The History... 2 3. What is cybercrime? The history
CYBERTERRORISM THE USE OF THE INTERNET FOR TERRORIST PURPOSES
 COMMITTEE OF EXPERTS ON TERRORISM (CODEXTER) CYBERTERRORISM THE USE OF THE INTERNET FOR TERRORIST PURPOSES UNITED STATES OF AMERICA September 2007 Kapitel 1 www.coe.int/gmt The responses provided below
COMMITTEE OF EXPERTS ON TERRORISM (CODEXTER) CYBERTERRORISM THE USE OF THE INTERNET FOR TERRORIST PURPOSES UNITED STATES OF AMERICA September 2007 Kapitel 1 www.coe.int/gmt The responses provided below
GUIDE. Guide to the Legal System of the Cayman Islands
 GUIDE Guide to the Legal System of the Cayman Islands TABLE OF CONTENTS Preface... 2 Introduction...3 The Cayman Islands Constitution... 3 The Governor......3 The Legislature... 3 The Executive...4 Sources
GUIDE Guide to the Legal System of the Cayman Islands TABLE OF CONTENTS Preface... 2 Introduction...3 The Cayman Islands Constitution... 3 The Governor......3 The Legislature... 3 The Executive...4 Sources
Understanding the International Criminal Court
 Understanding the International Criminal Court Understanding the International Criminal Court Table of Contents I. The International Criminal Court at a glance 3 II. Structure of the ICC 9 III. Crimes
Understanding the International Criminal Court Understanding the International Criminal Court Table of Contents I. The International Criminal Court at a glance 3 II. Structure of the ICC 9 III. Crimes
DAPTO HIGH SCHOOL. YEAR 11 LEGAL STUDIES Preliminary Mid-Course Examination 2009
 DAPTO HIGH SCHOOL YEAR 11 LEGAL STUDIES Preliminary Mid-Course Examination 2009 General Instructions: Reading time 5 minutes Working time 1 ½ hours Write using blue or black pen Write your Student Number/Name
DAPTO HIGH SCHOOL YEAR 11 LEGAL STUDIES Preliminary Mid-Course Examination 2009 General Instructions: Reading time 5 minutes Working time 1 ½ hours Write using blue or black pen Write your Student Number/Name
QUESTIONS AND ANSWERS on the International Criminal Court
 C o a l i t i o n f o r t h e I n t e r n a t i o n a l C r i m i n a l C o u r t C o n t a c t : A d e l e W a u g a m a n M e d i a L i a i s o n t e l e p h o n e : + 2 1 2. 6 8 7. 2 1 7 6 e m a i l
C o a l i t i o n f o r t h e I n t e r n a t i o n a l C r i m i n a l C o u r t C o n t a c t : A d e l e W a u g a m a n M e d i a L i a i s o n t e l e p h o n e : + 2 1 2. 6 8 7. 2 1 7 6 e m a i l
Cybersecurity Global status update. Dr. Hamadoun I. Touré Secretary-General, ITU
 Cybersecurity Global status update Dr. Hamadoun I. Touré Secretary-General, ITU Cybercrime takes a toll on the global economy - Online fraud, identity theft, and lost intellectual property; - On governments,
Cybersecurity Global status update Dr. Hamadoun I. Touré Secretary-General, ITU Cybercrime takes a toll on the global economy - Online fraud, identity theft, and lost intellectual property; - On governments,
Five Principles for Shaping Cybersecurity Norms
 TRANSPARENCY PROPORTIONALITY HARMONIZATION RISK REDUCTION COLLABORATION Five Principles for Shaping Cybersecurity Norms Contents Introduction 3 Cybersecurity Norms 5 The Role of the Public Sector 6 Cybersecurity
TRANSPARENCY PROPORTIONALITY HARMONIZATION RISK REDUCTION COLLABORATION Five Principles for Shaping Cybersecurity Norms Contents Introduction 3 Cybersecurity Norms 5 The Role of the Public Sector 6 Cybersecurity
Models for Cyber-legislation in ESCWA member countries
 Models for Cyber-legislation in ESCWA member countries Presented by Jean Akl & Roula Zayat Amman, December 11, 2007 Cyber Space Cyber space (non-jurisdictional International Space; jurisdictional National
Models for Cyber-legislation in ESCWA member countries Presented by Jean Akl & Roula Zayat Amman, December 11, 2007 Cyber Space Cyber space (non-jurisdictional International Space; jurisdictional National
Cyber Security Strategy for Germany
 Cyber Security Strategy for Germany Contents Introduction 2 IT threat assessment 3 Framework conditions 4 Basic principles of the Cyber Security Strategy 4 Strategic objectives and measures 6 Sustainable
Cyber Security Strategy for Germany Contents Introduction 2 IT threat assessment 3 Framework conditions 4 Basic principles of the Cyber Security Strategy 4 Strategic objectives and measures 6 Sustainable
International Criminal Court: Review Conference
 International Criminal Court: Review Conference Keynote Address by Ambassador Yasuji ISHIGAKI Special Assistant to Minister for Foreign Affairs of Japan Round-Table Meeting of Legal Experts on the Review
International Criminal Court: Review Conference Keynote Address by Ambassador Yasuji ISHIGAKI Special Assistant to Minister for Foreign Affairs of Japan Round-Table Meeting of Legal Experts on the Review
STRATEGIC OBJECTIVE 2.4 OVERCOME GLOBAL SECURITY CHALLENGES THROUGH DIPLOMATIC ENGAGEMENT AND DEVELOPMENT COOPERATION
 Performance Goal 2.4.1 By September 30, 2017, achieve key milestones to promote arms control and nonproliferation by implementing the President s Prague Agenda of steps toward a world without nuclear weapons;
Performance Goal 2.4.1 By September 30, 2017, achieve key milestones to promote arms control and nonproliferation by implementing the President s Prague Agenda of steps toward a world without nuclear weapons;
Section 17: Offenses against the Administration of Justice
 399 Section 17: Offenses against the Administration of Justice General Very often, the legislation of post-conflict states lacks adequate administration-ofjustice offenses. This section is a relatively
399 Section 17: Offenses against the Administration of Justice General Very often, the legislation of post-conflict states lacks adequate administration-ofjustice offenses. This section is a relatively
Chairman's Summary of the Outcomes of the G8 Justice and Home Affairs Ministerial Meeting. (Moscow, 15-16 June 2006)
 Chairman's Summary of the Outcomes of the G8 Justice and Home Affairs Ministerial Meeting (Moscow, 15-16 June 2006) At their meeting in Moscow on 15-16 June 2006 the G8 Justice and Home Affairs Ministers
Chairman's Summary of the Outcomes of the G8 Justice and Home Affairs Ministerial Meeting (Moscow, 15-16 June 2006) At their meeting in Moscow on 15-16 June 2006 the G8 Justice and Home Affairs Ministers
The final version of the Cyber Security Strategy and Action Plan note the following priorities to be implemented in 2012-2015:
 COMMITTEE OF EXPERTS ON TERRORISM (CODEXTER) CYBERTERRORISM THE USE OF THE INTERNET FOR Kapitel 1 TERRORIST PURPOSES GEORGIA January 2013 www.coe.int/terrorism A. National policy 1. Is there a national
COMMITTEE OF EXPERTS ON TERRORISM (CODEXTER) CYBERTERRORISM THE USE OF THE INTERNET FOR Kapitel 1 TERRORIST PURPOSES GEORGIA January 2013 www.coe.int/terrorism A. National policy 1. Is there a national
STATE OF NEW HAMPSHIRE STRATEGIC PLAN TO ADDRESS CYBER CRIME
 STATE OF NEW HAMPSHIRE STRATEGIC PLAN TO ADDRESS CYBER CRIME MAY 2004 Page 1 of 7 State of New Hampshire Strategic Plan to Address Cyber Crime May 2004 Introduction Cyber crime, or more broadly, electronic
STATE OF NEW HAMPSHIRE STRATEGIC PLAN TO ADDRESS CYBER CRIME MAY 2004 Page 1 of 7 State of New Hampshire Strategic Plan to Address Cyber Crime May 2004 Introduction Cyber crime, or more broadly, electronic
I n h a l t sve r ze i c h n i s
 Inhaltsverzeichnis The Paths to the Swiss Federal Supreme Court An Outline of Switzerland s Judiciary Structure Content Content Content Preface I. Courts and Judges A Cantonal Level 1 Civil Courts a Conciliation
Inhaltsverzeichnis The Paths to the Swiss Federal Supreme Court An Outline of Switzerland s Judiciary Structure Content Content Content Preface I. Courts and Judges A Cantonal Level 1 Civil Courts a Conciliation
A SHORT NOTE ON THE DEVELOPMENT OF THE CRIMINAL JUSTICE SYSTEM AFTER THE ACCESSION OF CRIMEA AND SEVASTOPOL TO THE RUSSIAN FEDERATION
 A SHORT NOTE ON THE DEVELOPMENT OF THE CRIMINAL JUSTICE SYSTEM AFTER THE ACCESSION OF CRIMEA AND SEVASTOPOL TO THE RUSSIAN FEDERATION Elena A. Kremyanskaya* ABSTRACT In March 2014, when Crimea and Sevastopol
A SHORT NOTE ON THE DEVELOPMENT OF THE CRIMINAL JUSTICE SYSTEM AFTER THE ACCESSION OF CRIMEA AND SEVASTOPOL TO THE RUSSIAN FEDERATION Elena A. Kremyanskaya* ABSTRACT In March 2014, when Crimea and Sevastopol
International Transfer of Prisoners (South Australia) Act 1998
 Version: 2.4.2000 South Australia International Transfer of Prisoners (South Australia) Act 1998 An Act relating to the transfer of prisoners to and from Australia. Contents Part 1 Preliminary 1 Short
Version: 2.4.2000 South Australia International Transfer of Prisoners (South Australia) Act 1998 An Act relating to the transfer of prisoners to and from Australia. Contents Part 1 Preliminary 1 Short
Cybercrime: Improving international cooperation
 The Hague, 12/06/2015 Cybercrime: Improving international cooperation GCCS2015 Parallel session 4 Document Reference [765004] Version [2] Discussion paper Europol Public Information 1 Introduction In preparation
The Hague, 12/06/2015 Cybercrime: Improving international cooperation GCCS2015 Parallel session 4 Document Reference [765004] Version [2] Discussion paper Europol Public Information 1 Introduction In preparation
T-CY Guidance Note #5
 www.coe.int/tcy Strasbourg, 5 June 2013 T-CY (2013)10E Rev Cybercrime Convention Committee (T-CY) T-CY Guidance Note #5 DDOS attacks Adopted by the 9 th Plenary of the T-CY (4-5 June 2013) Contact: Alexander
www.coe.int/tcy Strasbourg, 5 June 2013 T-CY (2013)10E Rev Cybercrime Convention Committee (T-CY) T-CY Guidance Note #5 DDOS attacks Adopted by the 9 th Plenary of the T-CY (4-5 June 2013) Contact: Alexander
Department of District Attorney
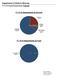 Department of District Attorney FY 15-16 Proposed Requirements: $9,805,684 FY 15-16 Requirements by Division FY 15-16 Requirements by Fund Alex Gardner District Attorney 541-682-4261 Department Purpose
Department of District Attorney FY 15-16 Proposed Requirements: $9,805,684 FY 15-16 Requirements by Division FY 15-16 Requirements by Fund Alex Gardner District Attorney 541-682-4261 Department Purpose
Summary of key points & outcomes
 Roundtable discussion on Prospects for international criminal justice in Africa: lessons from eastern and southern Africa, and Sudan 8 Dec 2008, Pretoria Summary of key points & outcomes Aims of the roundtable
Roundtable discussion on Prospects for international criminal justice in Africa: lessons from eastern and southern Africa, and Sudan 8 Dec 2008, Pretoria Summary of key points & outcomes Aims of the roundtable
Department of Communications. Enhancing Online Safety for Children Discussion Paper. Submission by the Australian Federal Police
 Department of Communications Enhancing Online Safety for Children Discussion Paper Submission by the Australian Federal Police March 2014 1 Introduction The AFP welcomes the opportunity to make a submission
Department of Communications Enhancing Online Safety for Children Discussion Paper Submission by the Australian Federal Police March 2014 1 Introduction The AFP welcomes the opportunity to make a submission
Cyberterrorism: Addressing the Challenges for Establishing an International Legal Framework
 Edith Cowan University Research Online Australian Counter Terrorism Conference Security Research Institute Conferences 2012 Cyberterrorism: Addressing the Challenges for Establishing an International Legal
Edith Cowan University Research Online Australian Counter Terrorism Conference Security Research Institute Conferences 2012 Cyberterrorism: Addressing the Challenges for Establishing an International Legal
THE CRIMINAL JUSTICE RESPONSE TO CORRUPTION (IN THE CONTEXT OF NEPAL)
 139TH INTERNATIONAL TRAINING COURSE RESOURCE VISITING MATERIAL EXPERTS SERIES PAPERS No.79 THE CRIMINAL JUSTICE RESPONSE TO CORRUPTION (IN THE CONTEXT OF NEPAL) Rajan Prasad Bhattarai * I. HISTORICAL BACKGROUND
139TH INTERNATIONAL TRAINING COURSE RESOURCE VISITING MATERIAL EXPERTS SERIES PAPERS No.79 THE CRIMINAL JUSTICE RESPONSE TO CORRUPTION (IN THE CONTEXT OF NEPAL) Rajan Prasad Bhattarai * I. HISTORICAL BACKGROUND
PRISONERS INTERNATIONAL TRANSFER (QUEENSLAND) ACT 1997
 Queensland PRISONERS INTERNATIONAL TRANSFER (QUEENSLAND) ACT 1997 Reprinted as in force on 1 April 1999 (Act not amended up to this date) Reprint No. 1 This reprint is prepared by the Office of the Queensland
Queensland PRISONERS INTERNATIONAL TRANSFER (QUEENSLAND) ACT 1997 Reprinted as in force on 1 April 1999 (Act not amended up to this date) Reprint No. 1 This reprint is prepared by the Office of the Queensland
SUMMARY OF THE ESTONIAN INFORMATION SYSTEM S AUTHORITY ON ENSURING CYBER SECURITY IN 2012
 SUMMARY OF THE ESTONIAN INFORMATION SYSTEM S AUTHORITY ON ENSURING CYBER SECURITY IN 2012 Cyberspace is both an ecosystem consisting of an infrastructure and services, and an environment where and through
SUMMARY OF THE ESTONIAN INFORMATION SYSTEM S AUTHORITY ON ENSURING CYBER SECURITY IN 2012 Cyberspace is both an ecosystem consisting of an infrastructure and services, and an environment where and through
Promoting a cyber security culture and demand compliance with minimum security standards;
 Input by Dr. S.C. Cwele Minister of State Security, Republic of South Africa Cyber Security Meeting, Johannesburg 27 March 2014 I would like to thank the Wits School of Governance for inviting us to contribute
Input by Dr. S.C. Cwele Minister of State Security, Republic of South Africa Cyber Security Meeting, Johannesburg 27 March 2014 I would like to thank the Wits School of Governance for inviting us to contribute
The Future of Internationalized Criminal Courts
 Slide 1 4th edition of International Spring Course Crime Prevention through Criminal Law & Security Studies t "Law and Politics of Transnational Justice: The Past, Present and Future of International Criminal
Slide 1 4th edition of International Spring Course Crime Prevention through Criminal Law & Security Studies t "Law and Politics of Transnational Justice: The Past, Present and Future of International Criminal
Chapter 15 Criminal Law and Procedures
 Chapter 15 Criminal Law and Procedures Chapter Outline 1. Introduction 2. What Is a Crime? 3. Elements of Criminal Liability 4. Types of Crimes 5. Cyber Crime 6. Constitutional Safeguards 7. Criminal Procedures
Chapter 15 Criminal Law and Procedures Chapter Outline 1. Introduction 2. What Is a Crime? 3. Elements of Criminal Liability 4. Types of Crimes 5. Cyber Crime 6. Constitutional Safeguards 7. Criminal Procedures
SENATE STANDING COMMITTEE ON LEGAL AND CONSTITUTIONAL AFFAIRS AUSTRALIAN FEDERAL POLICE. Question No. 100
 SENATE STANDING COMMITTEE ON LEGAL AND CONSTITUTIONAL AFFAIRS AUSTRALIAN FEDERAL POLICE Question No. 100 Senator McKenzie asked the following question at the hearing on 24 May 2012: a) How do you define
SENATE STANDING COMMITTEE ON LEGAL AND CONSTITUTIONAL AFFAIRS AUSTRALIAN FEDERAL POLICE Question No. 100 Senator McKenzie asked the following question at the hearing on 24 May 2012: a) How do you define
The technical and legal obstacles to the use of videoconferencing
 13 September 2010 Original: English Fifth session Vienna, 18-22 October 2010 Item 6 of the provisional agenda International cooperation with particular emphasis on extradition, mutual legal assistance
13 September 2010 Original: English Fifth session Vienna, 18-22 October 2010 Item 6 of the provisional agenda International cooperation with particular emphasis on extradition, mutual legal assistance
Michael Yakushev PIR-Center, Moscow (Russia)
 Michael Yakushev PIR-Center, Moscow (Russia) Terminological conflict: Cyber-Security, Internet Governance etc. Legal conflict (gap): lack of globally recognized legal instruments Organizational conflict:
Michael Yakushev PIR-Center, Moscow (Russia) Terminological conflict: Cyber-Security, Internet Governance etc. Legal conflict (gap): lack of globally recognized legal instruments Organizational conflict:
CYBERTERRORISM THE USE OF THE INTERNET FOR TERRORIST PURPOSES
 COMMITTEE OF EXPERTS ON TERRORISM (CODEXTER) CYBERTERRORISM THE USE OF THE INTERNET FOR TERRORIST PURPOSES GERMANY September 2007 Kapitel 1 www.coe.int/gmt A. National policy 1. Is there a national policy
COMMITTEE OF EXPERTS ON TERRORISM (CODEXTER) CYBERTERRORISM THE USE OF THE INTERNET FOR TERRORIST PURPOSES GERMANY September 2007 Kapitel 1 www.coe.int/gmt A. National policy 1. Is there a national policy
Chief Executive. Secretary for Justice. Department of Justice
 #751317v1 1 Chief Executive Secretary for Justice Department of Justice 2 Secretary for Justice Mr Rimsky Yuen, SC International Law Division Law Drafting Division Paul Wan Law Draftsman Legal Policy Division
#751317v1 1 Chief Executive Secretary for Justice Department of Justice 2 Secretary for Justice Mr Rimsky Yuen, SC International Law Division Law Drafting Division Paul Wan Law Draftsman Legal Policy Division
Address to the United Nations General Assembly. 30 October 2008. Judge Philippe Kirsch President of the International Criminal Court
 Address to the United Nations General Assembly 30 October 2008 Judge Philippe Kirsch President of the International Criminal Court (English only version) Check against delivery Maanweg 174, 2516 AB The
Address to the United Nations General Assembly 30 October 2008 Judge Philippe Kirsch President of the International Criminal Court (English only version) Check against delivery Maanweg 174, 2516 AB The
Cybersecurity in the Commonwealth: Setting the Stage
 Cybersecurity in the Commonwealth: Setting the Stage Tim Unwin Secretary General Commonwealth Telecommunications Organisation CTO Cybersecurity Forum, Yaoundé 24 th April 2013 For governments Imagine if
Cybersecurity in the Commonwealth: Setting the Stage Tim Unwin Secretary General Commonwealth Telecommunications Organisation CTO Cybersecurity Forum, Yaoundé 24 th April 2013 For governments Imagine if
Cyber Security Strategy of Georgia
 Cyber Security Strategy of Georgia 1 1. Introduction The Government of Georgia publishes its Cyber Security Strategy for the first time. Large-scale cyber attacks launched by Russia against Georgia in
Cyber Security Strategy of Georgia 1 1. Introduction The Government of Georgia publishes its Cyber Security Strategy for the first time. Large-scale cyber attacks launched by Russia against Georgia in
How To Protect Yourself From Cyber Crime
 The Global Polity Cybercrime, Cybersecurity and the Future of the Internet The Challenges Cybercrime is now the fastest growing sector of cross-border organized crime. In 2009, reported losses in the US
The Global Polity Cybercrime, Cybersecurity and the Future of the Internet The Challenges Cybercrime is now the fastest growing sector of cross-border organized crime. In 2009, reported losses in the US
UPDATED STATUTE OF THE INTERNATIONAL CRIMINAL TRIBUNAL FOR THE FORMER YUGOSLAVIA
 UNITED NATIONS International Tribunal for the Prosecution of Persons Responsible for Serious Violations of International Humanitarian Law Committed in the Territory of the Former Yugoslavia since 1991
UNITED NATIONS International Tribunal for the Prosecution of Persons Responsible for Serious Violations of International Humanitarian Law Committed in the Territory of the Former Yugoslavia since 1991
COMPUTER MISUSE AND CYBERSECURITY ACT (CHAPTER 50A)
 COMPUTER MISUSE AND CYBERSECURITY ACT (CHAPTER 50A) (Original Enactment: Act 19 of 1993) REVISED EDITION 2007 (31st July 2007) An Act to make provision for securing computer material against unauthorised
COMPUTER MISUSE AND CYBERSECURITY ACT (CHAPTER 50A) (Original Enactment: Act 19 of 1993) REVISED EDITION 2007 (31st July 2007) An Act to make provision for securing computer material against unauthorised
Cybersecurity in SMEs: Evaluating the Risks and Possible Solutions. BANCHE E SICUREZZA 2015 Rome, Italy 5 June 2015 Arthur Brocato, UNICRI
 Cybersecurity in SMEs: Evaluating the Risks and Possible Solutions BANCHE E SICUREZZA 2015 Rome, Italy 5 June 2015 Arthur Brocato, UNICRI UNICRI s Main Goals The United Nations Interregional Crime and
Cybersecurity in SMEs: Evaluating the Risks and Possible Solutions BANCHE E SICUREZZA 2015 Rome, Italy 5 June 2015 Arthur Brocato, UNICRI UNICRI s Main Goals The United Nations Interregional Crime and
GUIDANCE Implementing Section 176 of the Anti-social Behaviour, Crime and Policing Act 2014: Lowvalue
 GUIDANCE Implementing Section 176 of the Anti-social Behaviour, Crime and Policing Act 2014: Lowvalue shoplifting Guidance for police in England and Wales First publication: June 2014 1 Introduction 1.
GUIDANCE Implementing Section 176 of the Anti-social Behaviour, Crime and Policing Act 2014: Lowvalue shoplifting Guidance for police in England and Wales First publication: June 2014 1 Introduction 1.
Negotiated Relationship Agreement between the International Criminal Court and the United Nations. Preamble
 Negotiated Relationship Agreement between the International Criminal Court and the United Nations Preamble The International Criminal Court and the United Nations, Bearing in mind the Purposes and Principles
Negotiated Relationship Agreement between the International Criminal Court and the United Nations Preamble The International Criminal Court and the United Nations, Bearing in mind the Purposes and Principles
New Hampshire Cyber Crime Initiative Overview Briefing. NH Assistant Attorney General Lucy H. Carrillo Internet Crimes Prosecutor
 New Hampshire Cyber Crime Initiative Overview Briefing NH Assistant Attorney General Lucy H. Carrillo Internet Crimes Prosecutor Background: Cyber Crime Many traditional crimes now have a cyber component
New Hampshire Cyber Crime Initiative Overview Briefing NH Assistant Attorney General Lucy H. Carrillo Internet Crimes Prosecutor Background: Cyber Crime Many traditional crimes now have a cyber component
Guide for applicants to the ICC List of Counsel and Assistants to Counsel
 Guide for applicants to the ICC List of Counsel and Assistants to Counsel Please note: It is of utmost importance to fully understand and properly follow the instructions provided in the present guide,
Guide for applicants to the ICC List of Counsel and Assistants to Counsel Please note: It is of utmost importance to fully understand and properly follow the instructions provided in the present guide,
1.2 Distinguish between civil law and criminal law. 1.3 Distinguish between common law and equity
 Tech Level Unit Title: Level: Level 3 Credit Value: 10 INTRODUCTION TO LAW AND THE LEGAL SYSTEM IN ENGLAND AND WALES Guided Learning Hours 60 Learning outcomes Assessment criteria Knowledge, understanding
Tech Level Unit Title: Level: Level 3 Credit Value: 10 INTRODUCTION TO LAW AND THE LEGAL SYSTEM IN ENGLAND AND WALES Guided Learning Hours 60 Learning outcomes Assessment criteria Knowledge, understanding
Panel 3: Applicability of International Law to Cyberspace & Characterization of Cyber Incidents
 Panel 3: Applicability of International Law to Cyberspace & Characterization of Cyber Incidents Catherine Lotrionte and Eneken Tikk, co-chairs Cyber security and the acceptable behavior of state and non-state
Panel 3: Applicability of International Law to Cyberspace & Characterization of Cyber Incidents Catherine Lotrionte and Eneken Tikk, co-chairs Cyber security and the acceptable behavior of state and non-state
ATTORNEY GENERAL S GUIDELINES ON PLEA DISCUSSIONS IN CASES OF SERIOUS OR COMPLEX FRAUD
 ATTORNEY GENERAL S GUIDELINES ON PLEA DISCUSSIONS IN CASES OF SERIOUS OR COMPLEX FRAUD A FOREWORD A1. These Guidelines set out a process by which a prosecutor may discuss an allegation of serious or complex
ATTORNEY GENERAL S GUIDELINES ON PLEA DISCUSSIONS IN CASES OF SERIOUS OR COMPLEX FRAUD A FOREWORD A1. These Guidelines set out a process by which a prosecutor may discuss an allegation of serious or complex
Full list of mistakes and omissions of the English Version of the Hungarian draft- Constitution
 Full list of mistakes and omissions of the English Version of the Hungarian draft- Constitution This document contains the full list of mistakes and omissions of the draft-constitution English version.
Full list of mistakes and omissions of the English Version of the Hungarian draft- Constitution This document contains the full list of mistakes and omissions of the draft-constitution English version.
How To Be Tried In A Court In Canada
 Community Legal Information Association of Prince Edward Island, Inc. Defending Yourself in Criminal Court If you are charged with a criminal offence, certain federal offences, or a provincial offence,
Community Legal Information Association of Prince Edward Island, Inc. Defending Yourself in Criminal Court If you are charged with a criminal offence, certain federal offences, or a provincial offence,
GLOBAL CONFERENCE ON CYBERSPACE 2015 CHAIR S STATEMENT
 GLOBAL CONFERENCE ON CYBERSPACE 2015 CHAIR S STATEMENT Introduction 1. On 16 and 17 April 2015 representatives of governments, international organisations, businesses, civil society, academia and the technical
GLOBAL CONFERENCE ON CYBERSPACE 2015 CHAIR S STATEMENT Introduction 1. On 16 and 17 April 2015 representatives of governments, international organisations, businesses, civil society, academia and the technical
Campaign for Justice 403 Seymour, Suite 201 Lansing, MI 48933 info@mijustice.org www.mijustice.org
 ELEVEN PRINCIPLES of a Public Defense Delivery System Adopted by the State Bar of Michigan Representative Assembly, April 2002 State Bar of Michigan www.michbar.org Michigan Public Defense Taskforce www.mipublicdefense.org
ELEVEN PRINCIPLES of a Public Defense Delivery System Adopted by the State Bar of Michigan Representative Assembly, April 2002 State Bar of Michigan www.michbar.org Michigan Public Defense Taskforce www.mipublicdefense.org
Legal protection of children from sexual exploitation: The Lanzarote Convention and the ONE in FIVE campaign
 PARLIAMENTS UNITED in combating sexual violence against children Legal protection of children from sexual exploitation: The Lanzarote Convention and the ONE in FIVE campaign Tanja Kleinsorge Head of the
PARLIAMENTS UNITED in combating sexual violence against children Legal protection of children from sexual exploitation: The Lanzarote Convention and the ONE in FIVE campaign Tanja Kleinsorge Head of the
Exploring an online Administrative Monetary Penalty System for infractions of provincial statutes and municipal bylaws
 Ministry of the Attorney General Exploring an online Administrative Monetary Penalty System for infractions of provincial statutes and municipal bylaws in Ontario Ministry of the Attorney General March
Ministry of the Attorney General Exploring an online Administrative Monetary Penalty System for infractions of provincial statutes and municipal bylaws in Ontario Ministry of the Attorney General March
The Witness and the Justice System in Alberta
 The Witness and the Justice System in Alberta Introduction This booklet provides basic information about appearing as a witness in the courts of Alberta. It is designed to explain your role as a witness,
The Witness and the Justice System in Alberta Introduction This booklet provides basic information about appearing as a witness in the courts of Alberta. It is designed to explain your role as a witness,
Legal Studies. Total marks 100
 2014 HIGHER SCHOOL CERTIFICATE EXAMINATION Legal Studies Total marks 100 Section I Pages 2 6 20 marks Attempt Questions 1 20 Allow about 30 minutes for this section General Instructions Reading time 5
2014 HIGHER SCHOOL CERTIFICATE EXAMINATION Legal Studies Total marks 100 Section I Pages 2 6 20 marks Attempt Questions 1 20 Allow about 30 minutes for this section General Instructions Reading time 5
Paper on some policy issues before the Office of the Prosecutor
 This policy paper defines a general strategy for the Office of the Prosecutor, highlights the priority tasks to be performed and determines an institutional framework capable of ensuring the proper exercise
This policy paper defines a general strategy for the Office of the Prosecutor, highlights the priority tasks to be performed and determines an institutional framework capable of ensuring the proper exercise
National Cyber Security Strategy 2015-2017
 National Cyber Security Strategy 2015-2017 Table of Contents Table of Contents...i Executive Summary... 1 1. Introduction... 2 2. Context - People, Economy, and State... 4 3. Guiding Principles... 10 4.
National Cyber Security Strategy 2015-2017 Table of Contents Table of Contents...i Executive Summary... 1 1. Introduction... 2 2. Context - People, Economy, and State... 4 3. Guiding Principles... 10 4.
CTC Special Meeting on Communications and IT New York May 2013. Thank you very much. I am very pleased to be here to participate in
 1 CTC Special Meeting on Communications and IT New York May 2013 Ms Marta Requena Chief, Terrorism Prevention Branch United Nations Office on Drugs and Crime Excellencies, Distinguished Delegates, Ladies
1 CTC Special Meeting on Communications and IT New York May 2013 Ms Marta Requena Chief, Terrorism Prevention Branch United Nations Office on Drugs and Crime Excellencies, Distinguished Delegates, Ladies
International Journal of Enterprise Computing and Business Systems
 PREVENTING CYBER CRIME: A STUDY REGARDING AWARENESS OF CYBER CRIME IN TRICITY Ms.Arpana(PhD in Progress) Lecturer GJIMT, Ph-II,Mohali,India Dr.Meenal Chauhan Assistant Professor GJIMT,Ph-II, Mohali, India
PREVENTING CYBER CRIME: A STUDY REGARDING AWARENESS OF CYBER CRIME IN TRICITY Ms.Arpana(PhD in Progress) Lecturer GJIMT, Ph-II,Mohali,India Dr.Meenal Chauhan Assistant Professor GJIMT,Ph-II, Mohali, India
Legal Framework to Combat Cyber Crimes in the Region: Qatar as a Model. Judge Dr. Ehab Elsonbaty Cyber Crime expert ehabelsonbaty@hotmail.
 Legal Framework to Combat Cyber Crimes in the Region: Qatar as a Model Judge Dr. Ehab Elsonbaty Cyber Crime expert ehabelsonbaty@hotmail.com Why should we care about CYBER CRIME & CYBER SECURITY? Clarification
Legal Framework to Combat Cyber Crimes in the Region: Qatar as a Model Judge Dr. Ehab Elsonbaty Cyber Crime expert ehabelsonbaty@hotmail.com Why should we care about CYBER CRIME & CYBER SECURITY? Clarification
Expert Group Meeting on the Technical and Legal Obstacles to the Use of Videoconferencing
 20 October 2010 Original: English Conference of the Parties to the United Nations Convention against Transnational Organized Crime Fifth session Vienna, 18-22 October 2010 Agenda item 6 * International
20 October 2010 Original: English Conference of the Parties to the United Nations Convention against Transnational Organized Crime Fifth session Vienna, 18-22 October 2010 Agenda item 6 * International
Strategic Priorities for the Cooperation against Cybercrime in the Eastern Partnership Region
 CyberCrime@EAP EU/COE Eastern Partnership Council of Europe Facility: Cooperation against Cybercrime Strategic Priorities for the Cooperation against Cybercrime in the Eastern Partnership Region Adopted
CyberCrime@EAP EU/COE Eastern Partnership Council of Europe Facility: Cooperation against Cybercrime Strategic Priorities for the Cooperation against Cybercrime in the Eastern Partnership Region Adopted
5957/1/10 REV 1 GS/np 1 DG H 2 B LIMITE EN
 COUNCIL OF THE EUROPEAN UNION Brussels, 8 March 2010 5957/1/10 REV 1 LIMITE CRIMORG 22 ENFOPOL 32 NOTE from: to: Subject: Presidency Multidisciplinary Group on Organised Crime (MDG) Draft Council Conclusions
COUNCIL OF THE EUROPEAN UNION Brussels, 8 March 2010 5957/1/10 REV 1 LIMITE CRIMORG 22 ENFOPOL 32 NOTE from: to: Subject: Presidency Multidisciplinary Group on Organised Crime (MDG) Draft Council Conclusions
DECLARATION STRENGTHENING CYBER-SECURITY IN THE AMERICAS
 DECLARATION STRENGTHENING CYBER-SECURITY IN THE AMERICAS INTER-AMERICAN COMMITTEE AGAINST TERRORISM (CICTE) TWELFTH REGULAR SESSION OEA/Ser.L/X.2.12 7 March, 2012 CICTE/DEC.1/12 rev. 1 Washington, D.C.
DECLARATION STRENGTHENING CYBER-SECURITY IN THE AMERICAS INTER-AMERICAN COMMITTEE AGAINST TERRORISM (CICTE) TWELFTH REGULAR SESSION OEA/Ser.L/X.2.12 7 March, 2012 CICTE/DEC.1/12 rev. 1 Washington, D.C.
Summer Law Program on International Criminal Law and International Legal and Comparative Approaches to Counter-Terrorism
 Photo: Den Haag Marketing/Jurjen Drenth Summer Law Program on International Criminal Law and International Legal and Comparative Approaches to Counter-Terrorism 18 May - 12 June 2015 The Hague www.asser.nl/summerprogrammes
Photo: Den Haag Marketing/Jurjen Drenth Summer Law Program on International Criminal Law and International Legal and Comparative Approaches to Counter-Terrorism 18 May - 12 June 2015 The Hague www.asser.nl/summerprogrammes
EU-U.S. DECLARATION ON COMBATING TERRORISM DROMOLAND CASTLE, 26 JUNE 2004
 COUNCIL OF THE EUROPEAN UNION Dromoland Castle, 26 June 2004 10760/04 (Presse 205) EU-U.S. DECLARATION ON COMBATING TERRORISM DROMOLAND CASTLE, 26 JUNE 2004 Since the attacks of 11 September 2001, the
COUNCIL OF THE EUROPEAN UNION Dromoland Castle, 26 June 2004 10760/04 (Presse 205) EU-U.S. DECLARATION ON COMBATING TERRORISM DROMOLAND CASTLE, 26 JUNE 2004 Since the attacks of 11 September 2001, the
CRIMINAL INVESTIGATION IN THE SLOVAK REPUBLIC
 124 CRIMINAL INVESTIGATION IN THE SLOVAK REPUBLIC Vladimíra Trnkócyová 56 General background Historical overview and future vision of investigation in the Slovak Republic The 2001 Accession Partnership
124 CRIMINAL INVESTIGATION IN THE SLOVAK REPUBLIC Vladimíra Trnkócyová 56 General background Historical overview and future vision of investigation in the Slovak Republic The 2001 Accession Partnership
Commonwealth Approach to Cybergovernance and Cybersecurity. By the Commonwealth Telecommunications Organisation
 Commonwealth Approach to Cybergovernance and Cybersecurity By the Commonwealth Telecommunications Organisation Trends in Cyberspace Cyberspace provides access to ICT Bridging the digital divide and influencing
Commonwealth Approach to Cybergovernance and Cybersecurity By the Commonwealth Telecommunications Organisation Trends in Cyberspace Cyberspace provides access to ICT Bridging the digital divide and influencing
Cyber-Crime, Cyber-Espionage, Cyber-War, & Cyber-Threats: An Exploration of Illegal Conduct & Warfare in the Cyber-World
 Cyber-Crime, Cyber-Espionage, Cyber-War, & Cyber-Threats: An Exploration of Illegal Conduct & Warfare in the Cyber-World Moderator: Panelists: Honorable Preet Bharara, United States Attorney, Southern
Cyber-Crime, Cyber-Espionage, Cyber-War, & Cyber-Threats: An Exploration of Illegal Conduct & Warfare in the Cyber-World Moderator: Panelists: Honorable Preet Bharara, United States Attorney, Southern
CHAPTER. What is Criminal Justice? Criminal Justice: Criminal Justice: Criminal Justice: What is the Definition of Crime?
 CHAPTER What is Criminal Justice? What is the Definition of Crime? Crime: What is Justice? Justice: Social Justice: Civil Justice: The Theme of this Book Individual Rights vs. Public Order The Theme of
CHAPTER What is Criminal Justice? What is the Definition of Crime? Crime: What is Justice? Justice: Social Justice: Civil Justice: The Theme of this Book Individual Rights vs. Public Order The Theme of
Public Policy Meeting, Legal Issues on Cyber Security in Africa Dakar, Senegal 21-27 November 2009
 Public Policy Meeting, Legal Issues on Cyber Security in Africa Dakar, Senegal 21-27 November 2009 Presenter Adam Mambi,(Advocate of High Court) -Deputy Executive Secretary, Law Reform Commission Tanzania
Public Policy Meeting, Legal Issues on Cyber Security in Africa Dakar, Senegal 21-27 November 2009 Presenter Adam Mambi,(Advocate of High Court) -Deputy Executive Secretary, Law Reform Commission Tanzania
Compensation. International framework Marjan Wijers
 Compensation International framework Marjan Wijers Why? Legal basis International human rights law ECrtHR, Rantsev vs Russia and Cyprus (2010): trafficking falls within the scope of Art. 4 ECHR without
Compensation International framework Marjan Wijers Why? Legal basis International human rights law ECrtHR, Rantsev vs Russia and Cyprus (2010): trafficking falls within the scope of Art. 4 ECHR without
GUIDELINES ON COMPLIANCE WITH AND ENFORCEMENT OF MULTILATERAL ENVIRONMENTAL AGREEMENTS
 GUIDELINES ON COMPLIANCE WITH AND ENFORCEMENT OF MULTILATERAL ENVIRONMENTAL AGREEMENTS 1. In its decision 21/27, dated 9 February 2001, the Governing Council of the United Nations Environment Programme
GUIDELINES ON COMPLIANCE WITH AND ENFORCEMENT OF MULTILATERAL ENVIRONMENTAL AGREEMENTS 1. In its decision 21/27, dated 9 February 2001, the Governing Council of the United Nations Environment Programme
