Common Gaps in Data Control: Identifying, Quantifying, and Solving Them Using Best Practices
|
|
|
- Edward Gibson
- 10 years ago
- Views:
Transcription
1 WHITE PAPER Common Gaps in Data Control: Identifying, Quantifying, and Solving Them Using Best Practices Sponsored by: Actifio Phil Goodwin September 2015 IDC OPINION In an effort to ensure absolute data protection, IT organizations make numerous copies of their data, both structured and unstructured. This may be done through snapshots, mirrors, and various replication methodologies (both local and remote) as well as backup/recovery. In fact, each technique helps organizations address different sources of potential data loss. IDC has defined this as an issue of copy data management. Our research indicates that the median number of copies made of critical databases and file systems is 13. While having 13 copies of data may ensure that the data can be recovered, too few IT organizations address the flip side: They now have dozens of copies (when considering multiple databases and file systems). In fact, our research revealed that on average, organizations have 375 separate copy data repositories. Each repository is vulnerable to inadvertent exposure of sensitive data or outright nefarious attempts to access the data. Data control and data security are different, although related. Data control is a superset of data security that adds centralized access management and auditing to the encryption and authentication of security. With organizations now having data spread across private clouds, public clouds, backup to tape, backup as a service, and disaster recovery (DR) as a service, the complexity and possible permutations of data locality are simply too significant for IT administrators to manage manually or ad hoc. Furthermore: The permutations of databases, copies, locations, policies, and access control methods make copy data management a complex matrix of dozens of possibilities that is impractical, if not impossible to track and manage manually. Organizations that rely on manual processes for data control are unlikely to ever achieve best practices because the IT environment is too dynamic for such methods to be consistently successful. Failure to address the data control issue virtually guarantees that sensitive data will be exposed to the risk of unauthorized access (whether nefarious or not), placing organizations at risk of regulatory sanction and negative publicity. Organizations need automated methods to consistently address the data control problem in a best practice manner. September 2015, IDC #259143
2 METHODOLOGY Actifio is well known for backup solutions designed to virtualize data and address the copy data problem in IT organizations. These solutions focus on reducing the significant financial toll that copy data extracts from the IT budget. Regular security breaches in the news highlight the risk that IT organizations face regarding either accidental exposure of sensitive data or the deliberate intrusion of hackers to retrieve sensitive data. The people at Actifio reasoned that the more copies of a data set that exist, the more opportunity there is for disclosure of sensitive information. Moreover, data in different stages, such as development, test/dev, and production, has different data access profiles. Thus there may be points at which some data is more vulnerable than other data. Actifio engaged IDC to determine answers to the following questions: How pervasive is the copy data access problem? At what point in the data life cycle is sensitive data most vulnerable to accidental disclosure? Are data managers aware of the copy data access problem, and how many follow best practices to deal with it? Who is responsible for dealing with the copy data access problem in most organizations? To answer these questions, IDC developed a survey of high-level decision makers regarding their organization's practices around copy data access. The survey netted 429 responses, with key demographics as follows: Organizations with more than 1,000 employees Respondents with titles such as CIO, VP of infrastructure, database architect (DBA), enterprise architect, and application architect Respondents who are intimately or very familiar with the organization's data access practices Organizations from financial services, education (K 16), healthcare, government, and retail industries We chose to focus on the aforementioned industries because all of them deal with some sensitive information, whether it is related to HIPAA, personally identifiable information (PII), or PCI. Each industry was represented equally in our survey results. Some highlights of the respondent profiles are as follows: CIO (45%), VP of infrastructure (29%), and DBA (18%) Firms with 1,000 4,999 employees (44%), 5,000 9,999 employees (43%), 10,000 or more employees (13%) All responses were strictly confidential to ensure respondent candor IDC #
3 IN THIS WHITE PAPER This white paper uses the primary research gathered by IDC from 429 midsize companies to largescale enterprises to quantify the risks associated with inadequate data control and its sources and to identify commonly vulnerable areas. The intended audience of this study is senior IT professionals responsible for data control and security, including CIOs, CSOs, VPs of infrastructure, and datacenter managers. This examination included structured and unstructured data, on-premise and off-premise repositories, data at rest, data in flight, and backup sources of data control vulnerabilities. Best practice guidelines and operations at the various stages in the data life cycle are provided. In addition, the document includes an overview of Actifio's data control solution and discusses challenges and opportunities for organizations addressing the copy data and copy data access problems. SITUATION OVERVIEW IDC defines copy data as all secondary copies of data compared with primary data. As data enters a system via transaction or other input, it is primary as long as it is unique. When IT organizations make copies of the data for data protection, test data, analytics, ETL, or other purposes, these copies collectively constitute copy data. Copy data is a necessity for IT organizations for normal business operations as well as ensuring data survivability for any potential data loss event. Copy data becomes a "problem" when the number of copies exceeds the utility of each copy. Organizations may keep an excessive number of copies out of an abundance of caution bordering on paranoia or simply because copies are created and rarely deleted due to either immature processes or lack of oversight. IDC estimates that copy data will cost IT organizations $50.63 billion in This is obviously a significant sum, especially when one considers that it represents 60% of the typical storage hardware budget. In addition to the financial costs of copy data, excess copies represent unnecessary risk of sensitive data disclosure. When copies are made for data protection, analytics, and the like, the new copy not only must inherit the security of the primary system but may need to be scrubbed for sensitive information. For example, during the development or test/dev process, IT organizations prefer to use real data. However, developers are rarely authorized to view the sensitive information that they can easily see in the data. To avoid this, data scrubbing will either scramble sensitive data or mask it in such a way that it cannot be viewed. Organizations may have as much legal exposure through inadvertent disclosure as they do if a hacker were to gain access. The price may include financial penalties, civil legal liability, and damage to organizational reputation. So, how pervasive is the copy data access problem? The results from our study showed that on average, organizations have 13 copies of individual data repositories containing sensitive information. In fact, 13% of respondents had more than 15 copies. This copy rate is consistent within the margin of error for both databases and file systems. In other words, organizations appear to apply copy policies regardless of whether the data is structured or unstructured IDC #
4 A bit of simple math will help us fully quantify the depth of the issue. In addition to finding that organizations make 13 copies of data, we also learned that organizations have an average of databases, of which 42% contain sensitive information. So, we calculated the following: databases x 13 copies of data x 0.42 sensitive information = 70.7 database copies with sensitive information We can run a similar calculation for mission-critical file systems based on responses to our survey: 14 file systems x copies of data x 0.60 sensitive information = file system copies containing sensitive information In addition, we asked respondents to tell us how many copies of sensitive data are kept on tape. The answers average out to 7.4 backup copies per database or file system. Again, some quick math: databases x 7.4 backup copies per database = 95.5 database backup copies 14 file systems x 7.4 backup copies per file system = file system copies Our calculations revealed that a typical organization has an astounding 375 extra copies of data that contain sensitive information. Every one of these extra copies is a point of vulnerability for the organization, and each extra copy must be secured against possible disclosure. Given all these points of vulnerability, it's important that organizations follow formalized procedures and best practices to reduce the risk of data exposure. To find out how well organizations secure access to these repositories, we asked respondents a series of questions regarding their data scrubbing and encryption practices. Respondents were asked whether they scrubbed data routinely whenever they make a copy of a mission-critical, sensitive database or file system. Responses range from "never" to "every time without exception." Responses showed that an average of just 27% of organizations scrub data every time without exception. Among different industries, government is the most diligent sector, but the 40% of government organizations that scrub data is still well below half. Educational organizations had the lowest incidents of data scrubbing, with just 14% doing so every time without exception. Even financial services organizations (27.3%) and healthcare (20.3%) had surprisingly low incidents of data scrubbing every time without exception, given how heavily regulated these industries are and the high-profile nature of any data breaches among them. Retail rounded out the group at 31.4% (see Figure 1) IDC #
5 FIGURE 1 Data Scrubbing Practices by Industry Q. When test/dev, analytical, or any other nonbackup copies are made of either mission-critical or business-critical databases or file systems containing sensitive information, how often is the data scrubbed or masked to eliminate the possibility of exposing sensitive information to unauthorized viewers? Never In some cases, but not a majority of the time In most cases Every time without exception Financial services (n = 88) Education (n = 84) Government (n = 85) Healthcare (n = 86) Retail (n = 86) Government most secure, education least secure Don't know Best practice (% of respondents) n = 429 Base = all respondents Notes: This survey is managed by IDC's Quantitative Research Group. Data is not weighted. Use caution when interpreting small sample sizes. Source: IDC and Actifio's Data Control Survey, June 2015 Encryption is another method of thwarting unauthorized access, so respondents were asked about their practices in that regard. As with data scrubbing, only a minority of organizations always encrypt data at rest. In this case, an average of only 29% of organizations surveyed always encrypt data at rest. From the data that we gathered, we found that 22% of database copies that contain sensitive information are never encrypted. This means that on average, organizations have 15.5 database copies that are vulnerable to data disclosure. Of course, this is an average, so weaker organizations may have substantially more IDC #
6 Results from our questions regarding encryption in flight were slightly higher. In this regard, one in three organizations always encrypts data in flight. However, we were able to determine that it is highly likely that the same 22% of database copies not encrypted at rest are not encrypted in flight either. With respect to encryption, we also asked about respondents' encryption practices for backup tapes. Here, the results were more encouraging. According to the survey, 47.5% of organizations encrypt tape every time and 47.3% encrypt specific data on certain tapes. However, given that 96% of the organizations surveyed move tapes offsite, it makes sense to simply encrypt all tapes by default. After data scrubbing and encryption, access control is the best means of ensuring that sensitive data is viewed only by those authorized to do so. By access control, we mean that the organization authenticates every user user permissions are set strictly and audit reports can be run to determine when and by whom the data was accessed, and the organization can detect when the data is copied outside the organization. Several key findings emerged from our study: Only 39% of organizations have best practice data access (as described previously) for databases. Just 29.6% of organizations have best practices for file system access. In 34% of cases, data access policies are applied ad hoc. 38% of organizations either do not audit their security and access policies or do so only on an ad hoc basis. The point at which policies are applied is also important. In this regard, we found that 36.6% of policies are applied at the time of application development, 34% are applied ad hoc, and 29.6% are applied during dev/test. The earlier that policies are applied, the less opportunity there is for data disclosure; the ideal is at the time of repository (copy) creation. Of course, someone must be responsible for dealing with copy data access. In our study, fully 10 different job titles had responsibility for participating in the establishment and implementation of data access policies. However, one title emerged more than any other: the CIO. According to the responses we received, the CIO was involved in setting policies 71.3% of the time and in implementing policies 68% of the time. The CIO was followed by the storage administrator, who is involved 50.3% of the time. This certainly means that in the event of a data access problem, all eyes will turn to the CIO. In summary, no more than one in three organizations can be considered best practice in any given area of vulnerability, including the areas of data at rest, data in the datacenter, data in flight, backup, and access control. However, being best practice in one area does not ensure best practice in all areas. An organization can measure well in one aspect and be exposed in another. FUTURE OUTLOOK The copy data access problem is simply too large and broad for IT organizations to handle manually. Even if the best processes are in place, the bureaucratic effort associated with managing 375 data copies impedes the agility that organizations need to meet business needs. Moreover, if human error enters the process just 5% of the time, then on average, nearly 20 copies of data will be vulnerable in the organization. An automated solution is the only practical means of addressing the copy data access problem IDC #
7 Actifio was founded to address the copy data problem with its Copy Data Virtualization solution. Actifio Copy Data Virtualization technology offers a central point of control for all copies of data within the organization. It eliminates the multiple separate copy data infrastructure stacks. The key aspect of this solution is its "golden image" management, which can significantly reduce the need to create additional copies. It virtualizes the data. It takes a single copy of the data (the golden image) and provides different views to the data. Views function as virtual copies in that they have all the functionality of a full read/writable copy without actually making a copy. There is no practical limit to the number of virtual copies that can be made. There are several advantages to the virtual copy approach. The first is economic in that the use of physical storage can be significantly reduced. This benefit goes beyond just hardware because software licensing is often tied to hardware capacity. In addition, each data copy is normally backed up, even if multiple other replicas exist. This represents not only additional physical cost but hurts the organization's ability to meet RTO/RPO service-level requirements for backup and restore operations. With respect to copy data access management, having a single image means that data access policies can be applied once and inherited by all subsequent virtual images. Policies are applied at the time that the image is created, meaning there is never a gap or an opportunity to be exploited for any nefarious activity. For example, Actifio encrypts the golden image by default, both at rest and in flight. Comprehensive encryption is the first, most obvious, and easiest way to reduce the risk of unauthorized data access. As data is added or deleted from the golden image, the product uses an "incremental forever" approach that reduces resource and bandwidth consumption. This includes copies created for business resilience and DR. To further reduce the possibility of sensitive data exposure, Actifio includes workflow automation to mask sensitive data. This feature automates data scrubbing at the time of virtual copy creation. Therefore, whether the copy is used for application development, test/dev, or any other nonproduction purpose, the data is protected from even the most innocent or inadvertent disclosure. When workflow automation is combined with Actifio's ability to provide audit trails, organizations can assess who accessed what and when. Actifio data virtualization technology is deployed via a virtual or physical appliance. That appliance can reside in the datacenter or in private, public, or hybrid cloud environments. For public cloud environments, Actifio Sky for Amazon Web Services (AWS) gives customers the option of purchasing the appliance through the AWS Marketplace. In fact, many buyers consume Actifio as a cloud service. CHALLENGES AND OPPORTUNITIES IDC's best practice guidelines for addressing the copy data and copy data access problems are as follows: Quantify and understand what copies are made, how many, and why. Having copies of data is OK and, in fact, is a necessity for resilience, ETL, DR, and so forth. However, copies should be made consciously and within the context of business requirements. The organization should have as many copies as it needs to conduct business, but no more. Encrypt data by default, both at rest and in flight. Encryption does involve some processing overhead, but it is a small cost compared with the cost of sensitive data exposure. Moreover, hardware performance simply continues to increase according to Moore's law, meaning that the cost of encryption goes down over time IDC #
8 Scrub copy data of sensitive information by default. In other words, data users should need to justify why the data should not be scrubbed rather than the other way around. Apply data security access policies automatically and systematically at the time of repository creation. Ad hoc or case-by-case policies may seem to be a way to optimize access, but such practices open security gaps because of inadvertent loss of oversight, if nothing else. Waiting to apply access policies, such as during application deployment or test/dev, leaves the data vulnerable in the intervening time. Encrypt all data on tape. It should be simply assumed that tapes will move offsite. If a tape that ought to remain onsite is unexpectedly moved outside the datacenter (including theft), it is too late to encrypt the data. IT organizations must incorporate all best practices to be a best practice organization. While it is possible to do so without an automated approach, the level of effort is so great that it is difficult to sustain over the long haul as various priorities arise and staff members change. CONCLUSION Copy data not only is costly but also introduces significant risk. IT managers must address two key issues: the copy data problem and the copy data access problem. IDC research shows that the copy data problem consumes up to 60% of the IT storage hardware budget. While it may not be possible to completely eliminate copy data, any incremental reduction returns real money to the IT budget. Controlling costs is certainly important, but the bigger organizational risk may be in copy data access. Given that IT organizations have an average of 375 data copies, the time at which data is inappropriately disclosed would seem to be more a matter of "when" than "if." Government regulations regarding disclosure of sensitive data are becoming increasingly strict, led by the European Union. Exposure of sensitive data, no matter how inadvertent or benign, can lead to government sanction and fines. With so much potentially on the line, CIOs should take a proactive approach to solving the copy data access problem, even if they see little need for urgency in addressing the copy data problem. Fortunately, it is possible to address both problems at the same time using automated systems IDC #
9 About IDC International Data Corporation (IDC) is the premier global provider of market intelligence, advisory services, and events for the information technology, telecommunications and consumer technology markets. IDC helps IT professionals, business executives, and the investment community make factbased decisions on technology purchases and business strategy. More than 1,100 IDC analysts provide global, regional, and local expertise on technology and industry opportunities and trends in over 110 countries worldwide. For 50 years, IDC has provided strategic insights to help our clients achieve their key business objectives. IDC is a subsidiary of IDG, the world's leading technology media, research, and events company. Global Headquarters 5 Speen Street Framingham, MA USA idc-insights-community.com Copyright Notice External Publication of IDC Information and Data Any IDC information that is to be used in advertising, press releases, or promotional materials requires prior written approval from the appropriate IDC Vice President or Country Manager. A draft of the proposed document should accompany any such request. IDC reserves the right to deny approval of external usage for any reason. Copyright 2015 IDC. Reproduction without written permission is completely forbidden.
Perspective: Cloud Solutions and Deployment for Healthcare Payers in 2014
 Perspective Perspective: Cloud Solutions and Deployment for Healthcare Payers in 2014 Lynne A. Dunbrack Judy Hanover IN THIS PERSPECTIVE This IDC Health Insights Perspective examines the current status
Perspective Perspective: Cloud Solutions and Deployment for Healthcare Payers in 2014 Lynne A. Dunbrack Judy Hanover IN THIS PERSPECTIVE This IDC Health Insights Perspective examines the current status
How To Understand Cloud Economics
 WHITE PAPER Cloud Economics: A Financial Analysis of Information Management IT Delivery Models Sponsored by: Viewpointe LLC Michael Versace October 2013 Randy Perry IDC OPINION Executive Summary Cost optimization
WHITE PAPER Cloud Economics: A Financial Analysis of Information Management IT Delivery Models Sponsored by: Viewpointe LLC Michael Versace October 2013 Randy Perry IDC OPINION Executive Summary Cost optimization
Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments
 BUYER CASE STUDY Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments Iris Feng Eric Sheppard IDC OPINION Today's datacenter is dominated by virtualized workloads
BUYER CASE STUDY Long Term Care Group Deploys Zerto for Data Protection and Recovery for Virtual Environments Iris Feng Eric Sheppard IDC OPINION Today's datacenter is dominated by virtualized workloads
Using Converged Infrastructure to Enable Rapid, Cost-Effective Private Cloud Deployments
 Sponsored by: VCE Authors: Richard L. Villars Matthew Marden June 2014 Business Value Highlights Customers using Vblock Systems as a platform for deploying private cloud workloads are realizing significant
Sponsored by: VCE Authors: Richard L. Villars Matthew Marden June 2014 Business Value Highlights Customers using Vblock Systems as a platform for deploying private cloud workloads are realizing significant
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R T h e B e n e f i t s o f C l o u d - B a s e d B a c k u p : A d d r e s s i
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R T h e B e n e f i t s o f C l o u d - B a s e d B a c k u p : A d d r e s s i
Data Management: Foundational Technologies for Health Insurance Exchange Success
 INDUSTRY BRIEF Data Management: Foundational Technologies for Health Insurance Exchange Success Sponsored by: Informatica Janice W. Young November 2013 IN THIS INDUSTRY BRIEF U.S. health plans have been
INDUSTRY BRIEF Data Management: Foundational Technologies for Health Insurance Exchange Success Sponsored by: Informatica Janice W. Young November 2013 IN THIS INDUSTRY BRIEF U.S. health plans have been
Mining for Insight: Rediscovering the Data Archive
 WHITE PAPER Mining for Insight: Rediscovering the Data Archive Sponsored by: Iron Mountain Laura DuBois June 2015 Sean Pike EXECUTIVE SUMMARY In the past, the main drivers for data archiving centered on
WHITE PAPER Mining for Insight: Rediscovering the Data Archive Sponsored by: Iron Mountain Laura DuBois June 2015 Sean Pike EXECUTIVE SUMMARY In the past, the main drivers for data archiving centered on
DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified
 Insight DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified Stephen Elliot IDC OPINION Based on a research survey conducted during October and November of 2014 across multiple
Insight DevOps and the Cost of Downtime: Fortune 1000 Best Practice Metrics Quantified Stephen Elliot IDC OPINION Based on a research survey conducted during October and November of 2014 across multiple
The Copy Data Problem: An Order of Magnitude Analysis
 INSIGHT The Copy Data Problem: An Order of Magnitude Analysis Laura DuBois Ashish Nadkarni Natalya Yezhkova IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
INSIGHT The Copy Data Problem: An Order of Magnitude Analysis Laura DuBois Ashish Nadkarni Natalya Yezhkova IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015
Nimble Storage Leverages Operational Data to Drive Its Business with Analytics Delivered by HP Vertica
 IDC ExpertROI SPOTLIGHT Nimble Storage Leverages Operational Data to Drive Its Business with Analytics Delivered by HP Vertica Sponsored by: HP Matthew Marden September 2014 Overview Nimble Storage (Nimble)
IDC ExpertROI SPOTLIGHT Nimble Storage Leverages Operational Data to Drive Its Business with Analytics Delivered by HP Vertica Sponsored by: HP Matthew Marden September 2014 Overview Nimble Storage (Nimble)
IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era
 Customer Needs and Strategies IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era Mary Johnston Turner IDC OPINION IT as a service (ITaaS) represents a fundamentally
Customer Needs and Strategies IT as a Service Emerges as a New Management Paradigm in the Software-Defined Datacenter Era Mary Johnston Turner IDC OPINION IT as a service (ITaaS) represents a fundamentally
W H I T E P A P E R T h e R O I o f C o n s o l i d a t i n g B a c k u p a n d A r c h i v e D a t a
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R T h e R O I o f C o n s o l i d a t i n g B a c k u p a n d A r c h i v e D a
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R T h e R O I o f C o n s o l i d a t i n g B a c k u p a n d A r c h i v e D a
"Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona
 Buyer Case Study "Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona Dan Vesset IDC OPINION Investment in analytics, business intelligence, and big data technologies
Buyer Case Study "Why Didn't We Do It Sooner?" Deployment of a New BI Solution at The Pain Center of Arizona Dan Vesset IDC OPINION Investment in analytics, business intelligence, and big data technologies
Allstate Getting Much More from Its IT Services with ServiceNow Cloud-Based IT Service Management Solution
 IDC ExpertROI SPOTLIGHT Allstate Getting Much More from Its IT Services with ServiceNow Cloud-Based IT Service Management Solution Sponsored by: ServiceNow Matthew Marden March 2015 Overview The Allstate
IDC ExpertROI SPOTLIGHT Allstate Getting Much More from Its IT Services with ServiceNow Cloud-Based IT Service Management Solution Sponsored by: ServiceNow Matthew Marden March 2015 Overview The Allstate
The Growth Opportunity for SMB Cloud and Hybrid Business Continuity
 WHITE PAPER The Growth Opportunity for SMB Cloud and Hybrid Business Continuity Sponsored by: Carbonite Raymond Boggs Laura DuBois April 2015 Christopher Chute EXECUTIVE SUMMARY To mitigate the economic
WHITE PAPER The Growth Opportunity for SMB Cloud and Hybrid Business Continuity Sponsored by: Carbonite Raymond Boggs Laura DuBois April 2015 Christopher Chute EXECUTIVE SUMMARY To mitigate the economic
The Business Value of IT Certification
 Sponsored by: Microsoft Authors: Cushing Anderson Matthew Marden Randy Perry The Business Value of IT November 2015 EXECUTIVE SUMMARY Business Value Highlights Higher productivity for server, database,
Sponsored by: Microsoft Authors: Cushing Anderson Matthew Marden Randy Perry The Business Value of IT November 2015 EXECUTIVE SUMMARY Business Value Highlights Higher productivity for server, database,
Equinix Increases IT and Employee Productivity with ServiceNow Cloud-Based IT Service Automation Solution
 IDC ExpertROI SPOTLIGHT Equinix Increases IT and Employee Productivity with ServiceNow Cloud-Based IT Service Automation Solution Sponsored by: ServiceNow Matthew Marden April 2014 Randy Perry Overview
IDC ExpertROI SPOTLIGHT Equinix Increases IT and Employee Productivity with ServiceNow Cloud-Based IT Service Automation Solution Sponsored by: ServiceNow Matthew Marden April 2014 Randy Perry Overview
Impact of Juniper Training and Certification on Network Management Activities
 WHITE PAPER Impact of Juniper Training and Certification on Network Management Activities Sponsored by: Juniper Networks Cushing Anderson January 2014 IDC OPINION IDC believes sufficient training and appropriate
WHITE PAPER Impact of Juniper Training and Certification on Network Management Activities Sponsored by: Juniper Networks Cushing Anderson January 2014 IDC OPINION IDC believes sufficient training and appropriate
KPMG Unlocks Hidden Value in Client Information with Smartlogic Semaphore
 CASE STUDY KPMG Unlocks Hidden Value in Client Information with Smartlogic Semaphore Sponsored by: IDC David Schubmehl July 2014 IDC OPINION Dan Vesset Big data in all its forms and associated technologies,
CASE STUDY KPMG Unlocks Hidden Value in Client Information with Smartlogic Semaphore Sponsored by: IDC David Schubmehl July 2014 IDC OPINION Dan Vesset Big data in all its forms and associated technologies,
University of Kentucky Leveraging SAP HANA to Lead the Way in Use of Analytics in Higher Education
 IDC ExpertROI SPOTLIGHT University of Kentucky Leveraging SAP HANA to Lead the Way in Use of Analytics in Higher Education Sponsored by: SAP Matthew Marden April 2014 Randy Perry Overview Founded in 1865
IDC ExpertROI SPOTLIGHT University of Kentucky Leveraging SAP HANA to Lead the Way in Use of Analytics in Higher Education Sponsored by: SAP Matthew Marden April 2014 Randy Perry Overview Founded in 1865
Affordable, Scalable, Reliable OLTP in a Cloud and Big Data World: IBM DB2 purescale
 WHITE PAPER Affordable, Scalable, Reliable OLTP in a Cloud and Big Data World: IBM DB2 purescale Sponsored by: IBM Carl W. Olofson December 2014 IN THIS WHITE PAPER This white paper discusses the concept
WHITE PAPER Affordable, Scalable, Reliable OLTP in a Cloud and Big Data World: IBM DB2 purescale Sponsored by: IBM Carl W. Olofson December 2014 IN THIS WHITE PAPER This white paper discusses the concept
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 BUYER CASE STUDY EMC IT Increasing Efficiency, Reducing Costs, and Optimizing IT with Data Deduplication Sponsored by: EMC Corporation Robert Amatruda February 2011 Laura DuBois Global Headquarters: 5
BUYER CASE STUDY EMC IT Increasing Efficiency, Reducing Costs, and Optimizing IT with Data Deduplication Sponsored by: EMC Corporation Robert Amatruda February 2011 Laura DuBois Global Headquarters: 5
IDC MarketScape: Worldwide Life Science Social Media Analytics 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Life Science Social Media Analytics 2014 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape: Worldwide Life Science Social Media Analytics 2014 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Methods and Practices: Cloud in Retail
 Methods and Practices: Cloud in Retail IDC Retail Insights: Retail IT Infrastructure Strategies METHODS AND PRACTICES #RI243398 Kimberly Knickle Leslie Hand Global Headquarters: 5 Speen Street Framingham,
Methods and Practices: Cloud in Retail IDC Retail Insights: Retail IT Infrastructure Strategies METHODS AND PRACTICES #RI243398 Kimberly Knickle Leslie Hand Global Headquarters: 5 Speen Street Framingham,
Pulsant Delivers Agile and Cost-Effective Hybrid Cloud Services with Cisco ACI
 IDC ExpertROI SPOTLIGHT Pulsant Delivers Agile and Cost-Effective Hybrid Cloud Services with Cisco ACI Sponsored by: Cisco Matthew Marden December 2015 Overview Pulsant is a United Kingdom-based IT infrastructure
IDC ExpertROI SPOTLIGHT Pulsant Delivers Agile and Cost-Effective Hybrid Cloud Services with Cisco ACI Sponsored by: Cisco Matthew Marden December 2015 Overview Pulsant is a United Kingdom-based IT infrastructure
Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research
 INSIGHT Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research David Schubmehl IDC OPINION Organizations are looking for better ways to perform
INSIGHT Content Analyst's Cerebrant Combines SaaS Discovery, Machine Learning, and Content to Perform Next-Generation Research David Schubmehl IDC OPINION Organizations are looking for better ways to perform
Assessing the Business Value of SDN Datacenter Security Solutions
 IDC SOLUTION BRIEF Assessing the Business Value of SDN Datacenter Security Solutions Sponsored by: Cisco Pete Lindstrom Matthew Marden May 2015 Richard L. Villars Overview CTOs, CIOs, and application architects
IDC SOLUTION BRIEF Assessing the Business Value of SDN Datacenter Security Solutions Sponsored by: Cisco Pete Lindstrom Matthew Marden May 2015 Richard L. Villars Overview CTOs, CIOs, and application architects
Converged and Integrated Datacenter Systems: Creating Operational Efficiencies
 Insight Converged and Integrated Datacenter Systems: Creating Operational Efficiencies Rob Brothers IDC OPINION Enterprise IT has moved away from siloed servers, storage, information, and processes and
Insight Converged and Integrated Datacenter Systems: Creating Operational Efficiencies Rob Brothers IDC OPINION Enterprise IT has moved away from siloed servers, storage, information, and processes and
Don't Wait Until It's Too Late: Choose Next-Generation Backup to Protect Your Business from Disaster
 WHITE PAPER: DON'T WAIT UNTIL IT'S TOO LATE: CHOOSE NEXT-GENERATION................. BACKUP........ TO... PROTECT............ Don't Wait Until It's Too Late: Choose Next-Generation Backup to Protect Your
WHITE PAPER: DON'T WAIT UNTIL IT'S TOO LATE: CHOOSE NEXT-GENERATION................. BACKUP........ TO... PROTECT............ Don't Wait Until It's Too Late: Choose Next-Generation Backup to Protect Your
Achieving Organizational Transformation with HP Converged Infrastructure Solutions for SDDC
 IDC ExpertROI SPOTLIGHT Achieving Organizational Transformation with HP Converged Infrastructure Solutions for SDDC Sponsored by: HP Matthew Marden January 2014 Randy Perry Overview Seeking the business
IDC ExpertROI SPOTLIGHT Achieving Organizational Transformation with HP Converged Infrastructure Solutions for SDDC Sponsored by: HP Matthew Marden January 2014 Randy Perry Overview Seeking the business
IDC FutureScape: Worldwide Big Data & Analytics 2016 Predictions. IDC Web Conference November 2015
 IDC FutureScape: Worldwide Big Data & Analytics 2016 Predictions IDC Web Conference November 2015 Logistics Today s Speakers Submit any questions to [email protected] You can download slides from
IDC FutureScape: Worldwide Big Data & Analytics 2016 Predictions IDC Web Conference November 2015 Logistics Today s Speakers Submit any questions to [email protected] You can download slides from
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 WHITE PAPER The IT Manager's Role in Proactive Information Retention and Disposition Management: Balancing ediscovery and Compliance Obligations with IT Operational and Budget Constraints Sponsored by:
WHITE PAPER The IT Manager's Role in Proactive Information Retention and Disposition Management: Balancing ediscovery and Compliance Obligations with IT Operational and Budget Constraints Sponsored by:
Understanding the Business Value of Migrating to Windows Server 2012
 WHITE PAPER Understanding the Business Value of Migrating to Windows Server 2012 Sponsored by: Microsoft and Intel Simon Piff February 2015 EXECUTIVE SUMMARY In December 2014, IDC Asia/Pacific undertook
WHITE PAPER Understanding the Business Value of Migrating to Windows Server 2012 Sponsored by: Microsoft and Intel Simon Piff February 2015 EXECUTIVE SUMMARY In December 2014, IDC Asia/Pacific undertook
Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure
 EXECUTIVE BRIEF Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure Sponsored by: Symantec Carla Arend December 2014 Andrew Buss IDC Opinion Microsoft will be ending Extended Support
EXECUTIVE BRIEF Windows Server 2003 Migration: Take a Fresh Look at Your IT Infrastructure Sponsored by: Symantec Carla Arend December 2014 Andrew Buss IDC Opinion Microsoft will be ending Extended Support
Enterprise Workloads on the IBM X6 Portfolio: Driving Business Advantages
 WHITE PAPER Enterprise Workloads on the IBM X6 Portfolio: Driving Business Advantages Sponsored by: IBM Jed Scaramella January 2014 EXECUTIVE SUMMARY Enterprise information technology (IT) leaders are
WHITE PAPER Enterprise Workloads on the IBM X6 Portfolio: Driving Business Advantages Sponsored by: IBM Jed Scaramella January 2014 EXECUTIVE SUMMARY Enterprise information technology (IT) leaders are
Understanding the Business Value of Social Solutions in Sales
 WHITE PAPER Understanding the Business Value of Social Solutions in Sales Sponsored by: SAP Vanessa Thompson April 2014 IDC OPINION The confluence of the changing competitive landscape, strategic business
WHITE PAPER Understanding the Business Value of Social Solutions in Sales Sponsored by: SAP Vanessa Thompson April 2014 IDC OPINION The confluence of the changing competitive landscape, strategic business
WHITE PAPER Making Cloud an Integral Part of Your Enterprise Storage and Data Protection Strategy
 WHITE PAPER Making Cloud an Integral Part of Your Enterprise Storage and Data Protection Strategy Sponsored by: Riverbed Technology Brad Nisbet December 2010 Richard L. Villars Global Headquarters: 5 Speen
WHITE PAPER Making Cloud an Integral Part of Your Enterprise Storage and Data Protection Strategy Sponsored by: Riverbed Technology Brad Nisbet December 2010 Richard L. Villars Global Headquarters: 5 Speen
O p t i m i z i n g t h e N e t w o r k t o M e e t T o m o r r o w ' s I C T D e m a n d s
 EXECUTIVE BRIEF O p t i m i z i n g t h e N e t w o r k t o M e e t T o m o r r o w ' s I C T D e m a n d s Adapted from IDC research by Eric Owen Click here to enter text. September 2014 INTRODUCTION
EXECUTIVE BRIEF O p t i m i z i n g t h e N e t w o r k t o M e e t T o m o r r o w ' s I C T D e m a n d s Adapted from IDC research by Eric Owen Click here to enter text. September 2014 INTRODUCTION
W H I T E P A P E R T h e C r i t i c a l N e e d t o P r o t e c t M a i n f r a m e B u s i n e s s - C r i t i c a l A p p l i c a t i o n s
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R T h e C r i t i c a l N e e d t o P r o t e c t M a i n f r a m e B u s i n e
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R T h e C r i t i c a l N e e d t o P r o t e c t M a i n f r a m e B u s i n e
ProtectV. Securing Sensitive Data in Virtual and Cloud Environments. Executive Summary
 VISIBILITY DATA GOVERNANCE SYSTEM OS PARTITION UNIFIED MANAGEMENT CENTRAL AUDIT POINT ACCESS MONITORING ENCRYPTION STORAGE VOLUME POLICY ENFORCEMENT ProtectV SECURITY SNAPSHOT (backup) DATA PROTECTION
VISIBILITY DATA GOVERNANCE SYSTEM OS PARTITION UNIFIED MANAGEMENT CENTRAL AUDIT POINT ACCESS MONITORING ENCRYPTION STORAGE VOLUME POLICY ENFORCEMENT ProtectV SECURITY SNAPSHOT (backup) DATA PROTECTION
Converged Infrastructure: Meeting the New Challenges of Healthcare IT
 WHITE PAPER Converged Infrastructure: Meeting the New Challenges of Healthcare IT Sponsored by: VCE Lynne Dunbrack March 2015 IDC HEALTH INSIGHTS OPINION Healthcare IT will play a central role in achieving
WHITE PAPER Converged Infrastructure: Meeting the New Challenges of Healthcare IT Sponsored by: VCE Lynne Dunbrack March 2015 IDC HEALTH INSIGHTS OPINION Healthcare IT will play a central role in achieving
WSSC Building on Oracle Engineered Systems to Become a Smart, Real-Time Utility Provider
 IDC ExpertROI SPOTLIGHT WSSC Building on Oracle Engineered Systems to Become a Smart, Real-Time Utility Provider Sponsored by: Oracle Corp. Matthew Marden August 2015 Overview Washington Suburban Sanitary
IDC ExpertROI SPOTLIGHT WSSC Building on Oracle Engineered Systems to Become a Smart, Real-Time Utility Provider Sponsored by: Oracle Corp. Matthew Marden August 2015 Overview Washington Suburban Sanitary
Buyer Conversations: Cairn India Works with Tech Mahindra to Enable Geotech IT Business Continuity
 BUYER CASE STUDY Buyer Conversations: Cairn India Works with Tech Mahindra to Enable Geotech IT Business Continuity Rajkumar P Mayur Sahni IDC OPINION Business continuity and disaster recovery (BCDR) is
BUYER CASE STUDY Buyer Conversations: Cairn India Works with Tech Mahindra to Enable Geotech IT Business Continuity Rajkumar P Mayur Sahni IDC OPINION Business continuity and disaster recovery (BCDR) is
WHITE PAPER Linux Management with Red Hat Network Satellite Server: Measuring Business Impact and ROI
 WHITE PAPER Linux Management with Red Hat Network Satellite Server: Measuring Business Impact and ROI Sponsored by: Red Hat Tim Grieser Randy Perry October 2009 Eric Hatcher Global Headquarters: 5 Speen
WHITE PAPER Linux Management with Red Hat Network Satellite Server: Measuring Business Impact and ROI Sponsored by: Red Hat Tim Grieser Randy Perry October 2009 Eric Hatcher Global Headquarters: 5 Speen
Enable unified data protection
 Business white paper Enable unified data protection HP Data Protector Table of contents 3 The latest backup and recovery strategies 3 Are legacy approaches meeting current challenges? 4 The deployment
Business white paper Enable unified data protection HP Data Protector Table of contents 3 The latest backup and recovery strategies 3 Are legacy approaches meeting current challenges? 4 The deployment
How to Determine the Right Sourcing Strategy for Hosted Application Management
 WHITE PAPER How to Determine the Right Sourcing Strategy for Hosted Application Management Sponsored by: AT&T Peter Marston July 2014 EXECUTIVE SUMMARY As the global economy continues its recovery, businesses
WHITE PAPER How to Determine the Right Sourcing Strategy for Hosted Application Management Sponsored by: AT&T Peter Marston July 2014 EXECUTIVE SUMMARY As the global economy continues its recovery, businesses
Reducing Cost While Simplifying Administration: Monetizing the Benefits of SAP ASE
 WHITE PAPER Reducing Cost While Simplifying Administration: Monetizing the Benefits of SAP ASE Sponsored by: SAP Carl W. Olofson June 2014 Randy Perry EXECUTIVE SUMMARY In 2011, SAP asked IDC to study
WHITE PAPER Reducing Cost While Simplifying Administration: Monetizing the Benefits of SAP ASE Sponsored by: SAP Carl W. Olofson June 2014 Randy Perry EXECUTIVE SUMMARY In 2011, SAP asked IDC to study
WHITE PAPER Comparing the Total Cost of Ownership of SME On- Premises Business Management Applications and SAP Business By Design
 WHITE PAPER Comparing the Total Cost of Ownership of SME On- Premises Business Management Applications and SAP Business By Design Sponsored by: SAP David Bradshaw January 2010 Global Headquarters: 5 Speen
WHITE PAPER Comparing the Total Cost of Ownership of SME On- Premises Business Management Applications and SAP Business By Design Sponsored by: SAP David Bradshaw January 2010 Global Headquarters: 5 Speen
IDC MarketScape: Worldwide Life Science CRM Software 2015 Vendor Assessment
 IDC MarketScape IDC MarketScape: Worldwide Life Science CRM Software 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape IDC MarketScape: Worldwide Life Science CRM Software 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
The Business Value of VCE Vblock Systems: Leveraging Convergence to Drive Business Agility
 Sponsored by: VCE Authors: Richard L. Villars Randy Perry May 2015 Business Value Highlights 4.6 times more applications developed/delivered per year 41% less IT time spent keeping the lights on 4.4 times
Sponsored by: VCE Authors: Richard L. Villars Randy Perry May 2015 Business Value Highlights 4.6 times more applications developed/delivered per year 41% less IT time spent keeping the lights on 4.4 times
IDC MarketScape Excerpt: Worldwide Life Science R&D Strategic Consulting Services 2014 Vendor Assessment
 IDC MarketScape IDC MarketScape Excerpt: Worldwide Life Science R&D Strategic Consulting Services 2014 Vendor Assessment Alan S. Louie, Ph.D. THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE
IDC MarketScape IDC MarketScape Excerpt: Worldwide Life Science R&D Strategic Consulting Services 2014 Vendor Assessment Alan S. Louie, Ph.D. THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE
How To Manage Cloud Management
 WHITE PAPER Five Steps to Successful Integrated Cloud Management Sponsored by: HP Mary Johnston Turner May 2011 Robert P. Mahowald IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA
WHITE PAPER Five Steps to Successful Integrated Cloud Management Sponsored by: HP Mary Johnston Turner May 2011 Robert P. Mahowald IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA 01701 USA
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.935.4445 F.508.988.7881 www.idc-hi.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.935.4445 F.508.988.7881 www.idc-hi.com L e v e raging Big Data to Build a F o undation f o r Accountable Healthcare C U S T O M I N D
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.935.4445 F.508.988.7881 www.idc-hi.com L e v e raging Big Data to Build a F o undation f o r Accountable Healthcare C U S T O M I N D
Improving Small Business Profitability by Optimizing IT Management
 I D C E X E C U T I V E B R I E F Improving Small Business Profitability by Optimizing IT Management Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
I D C E X E C U T I V E B R I E F Improving Small Business Profitability by Optimizing IT Management Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
W H I T E P A P E R C l i m a t e C h a n g e : C l o u d ' s I m p a c t o n I T O r g a n i z a t i o n s a n d S t a f f i n g
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R C l i m a t e C h a n g e : C l o u d ' s I m p a c t o n I T O r g a n i z a
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R C l i m a t e C h a n g e : C l o u d ' s I m p a c t o n I T O r g a n i z a
Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares
 Market Analysis Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares Charles J. Kolodgy IN THIS EXCERPT The content for this excerpt was taken directly from IDC Market
Market Analysis Worldwide Security and Vulnerability Management 2014 2018 Forecast and 2013 Vendor Shares Charles J. Kolodgy IN THIS EXCERPT The content for this excerpt was taken directly from IDC Market
AT&T Leverages HP Vertica Analytics Platform to Change the Economics of Providing Actionable Insights to Decision Makers
 IDC ExpertROI SPOTLIGHT AT&T Leverages HP Vertica Analytics Platform to Change the Economics of Providing Actionable Insights to Decision Makers Sponsored by: HP Matthew Marden November 2014 Overview AT&T
IDC ExpertROI SPOTLIGHT AT&T Leverages HP Vertica Analytics Platform to Change the Economics of Providing Actionable Insights to Decision Makers Sponsored by: HP Matthew Marden November 2014 Overview AT&T
Worldwide Cloud Systems Management Software 2013 Vendor Shares
 COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide cloud systems management software competitive market showed very
COMPETITIVE ANALYSIS Worldwide Cloud Systems Management Software 2013 Vendor Shares Mary Johnston Turner IDC OPINION In 2013, the worldwide cloud systems management software competitive market showed very
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 B U Y E R C A S E S T U D Y U. S. B a n k i n g I n s t i t u t i o n I m p l e m e n t s V a r o n i s t o G a i n C o n t r o l o f U n s t r u c t u r e d F i l e S e r v e r D a t a Laura DuBois I
B U Y E R C A S E S T U D Y U. S. B a n k i n g I n s t i t u t i o n I m p l e m e n t s V a r o n i s t o G a i n C o n t r o l o f U n s t r u c t u r e d F i l e S e r v e r D a t a Laura DuBois I
Is online backup right for your business? Eight reasons to consider protecting your data with a hybrid backup solution
 PARTNER BRIEF: IS ONLINE BACKUP RIGHT FOR YOUR BUSINESS?........................................ Is online backup right for your business? Eight reasons to consider protecting your data with a hybrid Who
PARTNER BRIEF: IS ONLINE BACKUP RIGHT FOR YOUR BUSINESS?........................................ Is online backup right for your business? Eight reasons to consider protecting your data with a hybrid Who
Why cloud backup? Top 10 reasons
 Why cloud backup? Top 10 reasons HP Autonomy solutions Table of contents 3 Achieve disaster recovery with secure offsite cloud backup 4 Free yourself from manual and complex tape backup tasks 4 Get predictable
Why cloud backup? Top 10 reasons HP Autonomy solutions Table of contents 3 Achieve disaster recovery with secure offsite cloud backup 4 Free yourself from manual and complex tape backup tasks 4 Get predictable
WHITE PAPER Using SAP Solution Manager to Improve IT Staff Efficiency While Reducing IT Costs and Improving Availability
 WHITE PAPER Using SAP Solution Manager to Improve IT Staff Efficiency While Reducing IT Costs and Improving Availability Sponsored by: SAP Elaina Stergiades November 2009 Eric Hatcher EXECUTIVE SUMMARY
WHITE PAPER Using SAP Solution Manager to Improve IT Staff Efficiency While Reducing IT Costs and Improving Availability Sponsored by: SAP Elaina Stergiades November 2009 Eric Hatcher EXECUTIVE SUMMARY
Table of contents 3 4 4 5 5 6 7
 Business white paper Unified data protection with HP Data Protector Leverage on-premise, cloud, and hybrid backup and recovery strategies Table of contents 3 Introduction 4 Are legacy approaches meeting
Business white paper Unified data protection with HP Data Protector Leverage on-premise, cloud, and hybrid backup and recovery strategies Table of contents 3 Introduction 4 Are legacy approaches meeting
WHITE PAPER Improving Storage Efficiencies with Data Deduplication and Compression
 WHITE PAPER Improving Storage Efficiencies with Data Deduplication and Compression Sponsored by: Oracle Steven Scully May 2010 Benjamin Woo IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA
WHITE PAPER Improving Storage Efficiencies with Data Deduplication and Compression Sponsored by: Oracle Steven Scully May 2010 Benjamin Woo IDC OPINION Global Headquarters: 5 Speen Street Framingham, MA
Privilege Gone Wild: The State of Privileged Account Management in 2015
 Privilege Gone Wild: The State of Privileged Account Management in 2015 March 2015 1 Table of Contents... 4 Survey Results... 5 1. Risk is Recognized, and Control is Viewed as a Cross-Functional Need...
Privilege Gone Wild: The State of Privileged Account Management in 2015 March 2015 1 Table of Contents... 4 Survey Results... 5 1. Risk is Recognized, and Control is Viewed as a Cross-Functional Need...
SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production
 Buyer Case Study SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production Brian McDonough IDC OPINION The goal of decision
Buyer Case Study SAS Enterprise Decision Management at a Global Financial Services Firm: Enabling More Rapid Implementation of Decision Models into Production Brian McDonough IDC OPINION The goal of decision
Managing IT Security with Penetration Testing
 Managing IT Security with Penetration Testing Introduction Adequately protecting an organization s information assets is a business imperative one that requires a comprehensive, structured approach to
Managing IT Security with Penetration Testing Introduction Adequately protecting an organization s information assets is a business imperative one that requires a comprehensive, structured approach to
WHITE PAPER IN THIS WHITE PAPER EXECUTIVE SUMMARY. Sponsored by: Salesforce. August 2015
 WHITE PAPER The Salesforce Economy: How Salesforce, Its Ecosystem of Partners, and Its Customers Will Create More Than 1 Million Jobs and Add $272 Billion to Local Economies in the Next Four Years Sponsored
WHITE PAPER The Salesforce Economy: How Salesforce, Its Ecosystem of Partners, and Its Customers Will Create More Than 1 Million Jobs and Add $272 Billion to Local Economies in the Next Four Years Sponsored
Software as a Service Offers Broadening Appeal for Small and Medium-Sized Discrete Manufacturers
 Software as a Service Offers Broadening Appeal for Small and Medium-Sized Discrete Manufacturers WHITE PAPER Sponsored by: SAP Simon Ellis November 2010 IDC MANUFACTURING INSIGHTS OPINION Software as a
Software as a Service Offers Broadening Appeal for Small and Medium-Sized Discrete Manufacturers WHITE PAPER Sponsored by: SAP Simon Ellis November 2010 IDC MANUFACTURING INSIGHTS OPINION Software as a
IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment Jill Feblowitz THIS IDC MARKETSCAPE EXCERPT FEATURES: TIETO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MARKETSCAPE IDC MarketScape: Worldwide Hydrocarbon Accounting Software 2013 Vendor Assessment Jill Feblowitz THIS IDC MARKETSCAPE EXCERPT FEATURES: TIETO IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Life Science Manufacturing and Supply Chain ITO 2015 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Manufacturing and Supply Chain ITO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES HCL TECHNOLOGIES, LTD. (INDIA) IDC MARKETSCAPE
IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Manufacturing and Supply Chain ITO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES HCL TECHNOLOGIES, LTD. (INDIA) IDC MARKETSCAPE
IDC MarketScape: U.S. Population Health Management 2014 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: U.S. Population Health Management 2014 Vendor Assessment Cynthia Burghard THIS IDC MARKETSCAPE EXCERPT FEATURES: WELLCENTIVE IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MARKETSCAPE IDC MarketScape: U.S. Population Health Management 2014 Vendor Assessment Cynthia Burghard THIS IDC MARKETSCAPE EXCERPT FEATURES: WELLCENTIVE IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape
IDC MarketScape: Worldwide Life Science Sales and Marketing ITO 2015 Vendor Assessment
 IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Sales and Marketing ITO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MARKETSCAPE IDC MarketScape: Worldwide Life Science Sales and Marketing ITO 2015 Vendor Assessment Eric Newmark THIS IDC MARKETSCAPE EXCERPT FEATURES: IMS HEALTH IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R L e v e r a g e R e c o r d s M a n a g e m e n t B e s t P r a c t i c e s t
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com W H I T E P A P E R L e v e r a g e R e c o r d s M a n a g e m e n t B e s t P r a c t i c e s t
NETWORK SECURITY FOR SMALL AND MID-SIZE BUSINESSES
 NETWORK SECURITY FOR SMALL AND MID-SIZE BUSINESSES September, 2015 Derek E. Brink, CISSP, Vice President and Research Fellow IT Security and IT GRC Report Highlights p2 p4 p6 p7 SMBs need to adopt a strategy
NETWORK SECURITY FOR SMALL AND MID-SIZE BUSINESSES September, 2015 Derek E. Brink, CISSP, Vice President and Research Fellow IT Security and IT GRC Report Highlights p2 p4 p6 p7 SMBs need to adopt a strategy
IDC research shows that the top 5 concerns among medium-sized businesses are:
 Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com SPECIAL STUDY Managing Risk in Medium Sized-Businesses: A Storage Software Solution Duncan Brown IN
Global Headquarters: 5 Speen Street Framingham, MA 01701 USA P.508.872.8200 F.508.935.4015 www.idc.com SPECIAL STUDY Managing Risk in Medium Sized-Businesses: A Storage Software Solution Duncan Brown IN
Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption
 INDUSTRY DEVELOPMENTS AND MODELS Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption Christopher Chute IDC OPINION Office 365 is Microsoft's next-generation email and
INDUSTRY DEVELOPMENTS AND MODELS Microsoft Office 365: How the Hosted Exchange Server Is Redefining SMB Cloud IT Adoption Christopher Chute IDC OPINION Office 365 is Microsoft's next-generation email and
IDC MarketScape Excerpt: Worldwide Life Science R&D ITO 2013 Vendor Assessment
 IDC MarketScape IDC MarketScape Excerpt: Worldwide Life Science R&D ITO 2013 Vendor Assessment Alan S. Louie, Ph.D. THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE FIGURE FIGURE 1 IDC
IDC MarketScape IDC MarketScape Excerpt: Worldwide Life Science R&D ITO 2013 Vendor Assessment Alan S. Louie, Ph.D. THIS IDC MARKETSCAPE EXCERPT FEATURES: ACCENTURE IDC MARKETSCAPE FIGURE FIGURE 1 IDC
Cloud, Appliance, or Software? How to Decide Which Backup Solution Is Best for Your Small or Midsize Organization.
 WHITE PAPER: CLOUD, APPLIANCE, OR SOFTWARE?........................................ Cloud, Appliance, or Software? How to Decide Which Backup Solution Is Best for Your Small or Midsize Who should read
WHITE PAPER: CLOUD, APPLIANCE, OR SOFTWARE?........................................ Cloud, Appliance, or Software? How to Decide Which Backup Solution Is Best for Your Small or Midsize Who should read
Worldwide Workload Management Software 2013 Vendor Shares
 EXCERPT Worldwide Workload Management Software 2013 Vendor Shares Mary Johnston Turner IN THIS EXCERPT The content for this paper is excerpted from the IDC Competitive Analysis Report, Worldwide Workload
EXCERPT Worldwide Workload Management Software 2013 Vendor Shares Mary Johnston Turner IN THIS EXCERPT The content for this paper is excerpted from the IDC Competitive Analysis Report, Worldwide Workload
W H I T E P A P E R R e a l i z i n g t h e B e n e f i t s o f Deduplication in a Backup and Restore System
 W H I T E P A P E R R e a l i z i n g t h e B e n e f i t s o f Deduplication in a Backup and Restore System Sponsored by: HP Noemi Greyzdorf November 2008 Robert Amatruda INTRODUCTION Global Headquarters:
W H I T E P A P E R R e a l i z i n g t h e B e n e f i t s o f Deduplication in a Backup and Restore System Sponsored by: HP Noemi Greyzdorf November 2008 Robert Amatruda INTRODUCTION Global Headquarters:
Assessing the Risk: Yes, the Cloud Can Be More Secure Than Your On-Premises Environment
 WHITE PAPER Assessing the Risk: Yes, the Cloud Can Be More Secure Than Your On-Premises Environment Sponsored by: Amazon Web Services Pete Lindstrom July 2015 SECURITY PERCEPTIONS RESULT IN CLOUD TREPIDATION
WHITE PAPER Assessing the Risk: Yes, the Cloud Can Be More Secure Than Your On-Premises Environment Sponsored by: Amazon Web Services Pete Lindstrom July 2015 SECURITY PERCEPTIONS RESULT IN CLOUD TREPIDATION
Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail
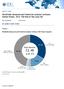 MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
MARKET SHARE Worldwide Advanced and Predictive Analytics Software Market Shares, 2014: The Rise of the Long Tail Alys Woodward Dan Vesset IDC MARKET SHARE FIGURE FIGURE 1 Worldwide Advanced and Predictive
