Dimitrios P. Pezaros Department of Computer Science University of Glasgow Glasgow, UK David Hutchison
|
|
|
- Gervase Gibson
- 8 years ago
- Views:
Transcription
1 On the Characterization of Network Traffic Dynamics Angelos K. Marnerides Infolab Computing Department Lancaster University Lancaster, UK ABSTRACT Characterizing backbone networks poses a significant challenge due to the unstable and fluctuated behavior exhibited by network traffic dynamics. Modeling techniques developed for volumebased traffic profiling rely on the statistical assumptions of stationarity, Gaussianity and linearity, whose applicability has not been thoroughly investigated throughout past and recent work. We argue that modeling assumptions should be rigorously validated since they determine the accuracy of any model applied to describe the traffic process. In this work we introduce and illustrate the suitability of Time-Frequency TF) representations and the Hinich algorithms for the validation of modeling assumptions on captured backbone and edge link network traces. Through the employment of these algorithms, we statistically show that link traffic is extremely dynamic and model characteristics change in small timescales. Furthermore, we highlight the benefits of a transport-layer traffic decomposition approach where protocols are modeled independently and protocol-specific characteristics are revealed, as opposed to analysis based solely on volume aggregates.. INTRODUCTION Understanding the underlying traffic behavior of backbone and edge networks is vital for traffic engineering tasks such as anomaly diagnosis, traffic classification and capacity planning []. In particular, traffic characterization is typically being tackled using statistical analysis of individual links) and network-wide volume-based characteristics i.e. counts of bytes and packets) [] [], as well as by analyzing the distributional behavior of particular packet header fields [3][4]. Throughout past and current literature, numerous statistical and signal processing techniques have been employed for constructing traffic models. Solutions as in [5][6][7] referring either to a network-wide, single PoP or link volume traffic characterization have employed mathematical models based on the de facto statistical assumptions of stationarity, gaussianity and linearity. The majority assume these properties with no validation, whereas others, as in [][5], use nd order statistics i.e. mean, variance, autocorrelation sequence) to validate these assumptions. However, nd order statistics are problematic in validating such timeseries properties, since they suppress up to a large scale phase Dimitrios P. Pezaros Department of Computer Science University of Glasgow Glasgow, UK dp@dcs.gla.ac.uk David Hutchison Infolab Computing Department Lancaster University Lancaster, UK dh@comp.lancs.ac.uk Hyun-chul Kim Department of Computer Science & Engineering Seoul National University Seoul, South Korea hkim@mmlab.snu.ac.kr characteristics such as magnitude and they stand unable to capture phase transition peaks [8][9]. Hence, any subsequent modeling leads to questionable levels of accuracy which in the case of backbone IP networks results in the inaccurate interpretation of traffic dynamics. In this paper, we focus on the rigorous validation of such statistical properties before they are employed by traffic models. We also show that methodologies derived by nd order statistics which address traffic profiling impose inadequacies in respect to the exact detection of traffic fluctuations throughout the observational time frame. In order to overcome these constraints, we propose the use of the bispectrum which as a tool for examining a timeseries' 3rd order statistical properties. The bispectrum is capable of capturing a signal's i.e. timeseries') phase information and can therefore enable the accurate representation of traffic fluctuations. In general, our work contributes towards the mathematical interpretation of volume-wise traffic dynamics using Time- Frequency TF) representations and 3rd order statistics estimated by the Hinich algorithms and the bispectrum[0][]. The combination of our theoretical and experimental evaluation of sample datasets from monitored backbone and edge links shows that: In contrast to schemes as in [][] where aggregate volume is considered, traffic decomposition enables a detailed characterization of the traffic dynamics shown by each protocol and enables the extraction of hidden patterns. The applicability of any traffic profiling model depends on the underlying statistical assumptions of stationarity, linearity and Gaussianity which cannot be assumed to hold true for the entirety of a traffic trace; hence such assumptions should be rigorously verified before applying any scheme. Failure to fully validate them results in modeling inaccuracies. Link traffic exhibits significant fluctuations in short timescales < 30 mins.) which may be described by diverse rather than holistic models, not adhering to identical statistical assumptions. Byte counts mostly expose different modeling characteristics than packet counts; hence, a volumebased approach should consider them independently. This paper has been submitted to the ACM X Conference and due to the double blind review the name of the conference is not stated. In addition results are partially and not fully presented.
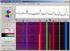
2 Set Date Day Start Duration Link Type Packets Bytes Avg. Util. Flows/min WIDE Fri :45 55min Backbone 3M 4G 35Mbps 63K Keio-I Tue 9:43 30min Edge 7M 6G 75Mbps 3K Keio-II Thu 0:8 30min Edge 5M 6G 75Mbps 9K. DATA & FEATURES Our analysis is based on unidirectional traffic flows extracted from three anonymized payload packet traces collected in US and Japan, as shown above in Table. The WIDE trace was collected at a 00 Mb/s FastEthernet US-JAPAN Trans-Pacific backbone link which is a carrier of commodity traffic for WIDE member organisations[3]. The Keio traces were captured on a Gb/s Ethernet link from the Japanese academic network of the Keio University s Shonan-Fujisawa campus. Our analysis is based on decomposing transport traffic into bytes and packet counts for TCP, UDP and ICMP protocols although ICMP is considered as a network layer protocol, we treat it as transport here, since it carries traffic which is distinct from TCP and UDP). Table : Traces pre-processing. Set Duration TCP UDP WIDE-I 3.75min 4K 30K 4K WIDE-II 3.75min 8K 3K 4K WIDE-III 3.75min 4K 9K 3K WIDE-IV 3.75min 3K 30K 4K Keio-I 30min K 0K 6K Keio-II 30min 8K 9K 4K ICMP and F a v) the Fourier transform of t) frequency is defined as : f t) = d arg G a t) π dt and its group delay is : t G d arg Fa ν ) ν ) = π dν G a the instantaneous In practice ft) denoted the amplitude of frequency we observe in a single count of a packet/byte arrival in time t and t ) is the G ν time distortion occurred due to the signal s instantaneous frequency. However, our experimentation shown Fig. ) that transport layer traffic within all our traces is extremely highly non-stationary since there was never the case of constant behaviour of the two concepts we introduce in formulas ) and ). ) ) 3. METHODOLOGY & RESULTS One of our targets is to illustrate the importance of validating the de-facto assumptions of stationarity, Gaussianity and linearity for volume-based network traffic modeling and further introduce applicable methodologies that accurately achieve this. The theoretical principles we apply on our packets and bytes timeseries originate from statistical signal processing, and following sections highlight their basic concepts. We first introduce the main metrics employed in order to identify stationary characteristics. Then, we discuss the basic principles of bispectrum and bicoherence as the core elements of the Hinich algorithms which enable statistical tests for validating Gaussianity and linearity[0]. 3. Stationarity Test A signal is considered to be stationary if the elements in its analytical form keep a constant instantaneous frequency and group delay respectively. If we map the counts of bytes and packets for each unidirectional flow as the process gt), t) its analytical form after applying a Hilbert transformation G a Figure : Stationarity Analysis on Keio-I 3. Hinich Algorithms Firstly introduced in [0], Hinich algorithms are a set of statistical hypothesis tests to detect non-linear and further Gaussian or non- Gaussian characteristics on a given random stochastic process g t). As mentioned above, the process gt) in our case is
3 Table :Estimated Statistics for the KEIO trace. ZSP denotes the Zero Skewness Probability and Conclusions defined as: L=Linear, NL = Non-Linear, G = Gaussian, NG = Non-Gaussian. Protocol Feature Estimated Ψ ω, ω) Theoretical Υ ω, ω ) Gaussianity metric κ ) Noncentrality parameter η ) ZSP θ ) Conclusion Keio-I Keio- II Bytes L & NG TCP Packets L & NG Bytes NL & NG UDP Packets NL & NG Bytes NL & NG ICMP Packets NL & NG Overall Protocol Bytes L & NG Packets L & NG Feature Estimated Ψ ω, ω) Theoretical Υ ω, ω ) Gaussianity metric κ ) Noncentrality parameter η ) ZSP θ ) Conclusion Bytes NL & NG TCP Packets L & NG Bytes NL & NG UDP Packets NL & NG Bytes L & NG ICMP Packets L & NG Overall Bytes NL & NG Packets L & NG the count of packets and bytes monitored in discrete time bins of length n, denoted as T = {,,... n }. Since the core elements for the Hinich algorithms are those of the bispectrum and bicoherence we following provide their mathematical definitions. The bispectrum provides a dual-frequency representation on the time-frequency plane in contrast to the one-dimensional interpretation of the power spectrum, and considers the 3 rd order cumulant sequence c 3, ) as its basic tuning function: + + j ω + ω ) B ω, ω ) = c3, ) e 3) = t = Bicoherence is used to detect quadratic non-linearities on the time-frequency TF) plane as well as quadratic phase coupling. Nevertheless, this document does not intend to present the properties of bicoherence in detail and therefore we only provide its definition, which in practice is denoted as the squared normalized version of the bispectrum. Hence, if we use formula 3, its squared normalized version looks like: B ω, ω ) b k B = 4) ω, ω ) S ω + ω ) S ω) S ω ) 3.. Gaussianity & Linearity Tests The Gaussianity test focuses on the bicoherence value as the result of the normalized bispectrum estimate. The Gaussian also known as zero-skewness) assumption according to Hinich is considered E b k B ω, ω ) the case where the estimated bicoherence value { } as well as the skewness equal to zero. Since in reality we can never have a flat, zero-bicoherence due to noise), we take the mean bicoherence value which in practice represents a quantitative Gaussianity metric. By using the definition of formula 4) we can calculate the mean bicoherence power estimate κ with: κ = b k 3) B ω, ω ) [4][0] and [5] employ some comparisons of the κ value in order to establish a concrete conclusion on whether the dataset under test actually follows a Gaussian distribution or not. As they suggest the computed value of κ is χ distributed chi-squared distributed) with a Fast Fourier Transform FFT) length function for approximating the number of freedom degrees to the closest Gaussian fit. Therefore, in case the estimated κ indicates that our timeseries has less than or equal to 0 freedom degrees, then we conclude that the dataset was following a Gaussian distribution. In parallel with κ, the Zero Skewness Probability ZSP) of false alarm θ is computed. θ illustrates the probability of the newly approximated value being much larger than the initial κ
4 estimate. Whenθ is small, we can reject the zero-skewness i.e. Gaussian) hypothesis. In our tests we use 0. θ as a valid range for approving Gaussianity, based on findings from [0]and [5]. The linearity assumption holds in case where the bispectrum: B ω, ω) 0 = C, ω,ω 4) where C is a constant value for all ω and ω. As suggested by Swami [], it is essential to approximate values of a sample interquartile range under a new bispectral estimate Ψ ω, ω) derived by B ω, ω) : Ψ ω, ω ) = B ω, ) 5) ω ρ M where Μ is the resulting boxcar window length, after rounding the FFT length with a resolution parameter ρ. The intuition for calculating the interquartile range is to compare it with a theoretical interquartile range Υ ω, ω) which similarly with ω, ω) defined as: Ψ is chi-squared with a non-centrality parameter η ρ η = M ) c, ) 6) 3 In our experimentation we keep the values of an FFT length of 8 and a resolution parameter of 0.5. The main step is to compare Ψ ω, ω) with Υ ω, ω) and if the difference is quite high based on the limits provided by [0] and [], then we reject the linearity hypothesis. The Keio characterization as presented in Table 3 has produced some significant outcomes related to the statistical behavior of each protocol on byte and packet representations. It is observed that during the same day and in such a small temporal interval i.e. 30mins), TCP as well as ICMP may not be modeled under the same assumptions. In general, it is also obvious that not all protocols may be modeled in the same way therefore their independent analysis would be beneficial as we also presented previously in section 4... Throughout the Keio-I, only ICMP and UDP can be modeled in the same way, whereas TCP should be treated under linear but non-gaussian assumptions. All the three protocols for both packets and bytes analyses have a zero probability for exhibiting zero skewness. This zero probability is the main strong evidence for concluding that the data do not exhibit a Gaussian behavior. In addition, the linearity exposed by TCP is attributed to the small numerical difference <0) between the theoretical and the estimated interquartile range. Similarly, we conclude that nonlinearity exists in both UDP and ICMP since the difference between the interquartile ranges gets greater than 0. Similarly, evaluation on the Keio-II compliments the results from the Keio-I indicating again the inability of modeling all protocols together. In addition, it is evident that even a volume-based approach for modeling a single protocol should consider the counts of bytes and packets as independent and analyze them separately. 4. CONCLUSIONS Current trends in network traffic profiling include the examination of aggregate volume characteristics, and the employment of models that inherently assume stationarity, linearity and Gaussianity of the timeseries. In this paper, we have argued that such statistical assumptions do not hold universally, and that they should therefore be rigorously validated. We have proposed the use of Time-Frequency TF) representations for determining stationarity of a timeseries, and the Hinich algorithms for validating its linearity and Gaussianity. Our quantitative evaluation on real network traces challenges the existence of stationarity and Gaussianity in small timescales, while linearity is evident in some traces but not in others. REFERENCES [] Papagiannaki, K., Taft, N., Zhang, Z., Diot, C., 003 Long- Term Forecasting of Internet Back-bone Traffic: Observations and Initial Models. In IEEE INFOCOM, San Francisco, U.S.A., March 003 [] Soule, A., Salamatian, K., Taft, N., Combining filtering and statistical methods for anomaly detection, Proc. of the 5th ACM SIGCOMM on Internet Measurement. Berkeley, CA, USA: USENIX Association, 005, pp. 3 3 [3] Lakhina, A., Crovella, M., Diot, C., Mining Anomalies Using Traffic Feature Distributions, 005, in ACM SIGCOMM Computer Communication Review CCR), vol. 35, no. 4, 005 pp [4] Silveira, F., Diot, C., Taft, N., Govindan, R., Astute: detecting a different class of traffic anomalies, in Proc. of the ACM SIGCOMM, New Delhi, India, Aug 9 Sep., 00. [5] Medina, A., Taft, N., Salamarian, K., Bhattacharrya, S., Diot, C., Traffic Matrix Estimation: Existing Techniques and New Directions, in ACM SIGCOMM Conference, Pittsburgh, PA, USA, August 00. [6] Soule, A., Lakhina, A., Taft, N., Papagiannaki, K., Salamatian, K., Nucci, A., Crovella, M., Diot, C., Traffic Matrices: Balancing Measurements, Inference and Modeling, 005, In Proc. of ACM SIGMETRICS 005, Banff, Alberta, Canada [7] Taft, N., Bhattacharrya, S., Jetcheva, J., Diot, C., Understanding Traffic Dynamics at a Backbone PoP, In Proceedings of SPIE, Vol. 456, 50, 00 [8] Nikias, C.L. and J.M. Mendel, Signal processing with higher-order spectra, IEEE Signal Processing Magazine, Vol. 0, No 3, pp. 0-37, July 993Bowman, M., Debray, S. K., and Peterson, L. L Reasoning about naming systems. ACM Trans. Program. Lang. Syst. 5, 5 Nov. 993), DOI= [9] Nikias, C.L. and M.R. Raghuveer, Bispectrum estimation: A digital signal processing framework, Proc. IEEE, Vol. 75, pp , July 987.
5 [0] Hinich, M.J., Testing for Gaussianity and linearity of a stationary time series, J. Time Series Analysis, Vol. 3, pp , 98. [] Swami, A., Mendel, J., M., Nikias, C., L., Higher Order Spectral Analysis Toolbox User Guide, MathWorks Inc., January 998 [] Groschwitz, N., K., Polyzos, G., C., A Time Series Model of Long-Term NSFNET Backbone Traffic, in IEEE ICC 94, 994 [3] The WIDE MAWI working group: [4] Hasselman, K., Munk, W., MacDonald, G., Bispectra of Ocean Waves, in Time Series, Ed. New York, Wiley, 963 [5] Nikias, C, L., Petropulu, A, P., Higher Order Spectral Analysis: A Non-linear Signal Processing Framework, New Jersey, Prentice Hall, 993
Network Traffic Characterization using Energy TF Distributions
 Network Traffic Characterization using Energy TF Distributions Angelos K. Marnerides a.marnerides@comp.lancs.ac.uk Collaborators: David Hutchison - Lancaster University Dimitrios P. Pezaros - University
Network Traffic Characterization using Energy TF Distributions Angelos K. Marnerides a.marnerides@comp.lancs.ac.uk Collaborators: David Hutchison - Lancaster University Dimitrios P. Pezaros - University
Network Performance Monitoring at Small Time Scales
 Network Performance Monitoring at Small Time Scales Konstantina Papagiannaki, Rene Cruz, Christophe Diot Sprint ATL Burlingame, CA dina@sprintlabs.com Electrical and Computer Engineering Department University
Network Performance Monitoring at Small Time Scales Konstantina Papagiannaki, Rene Cruz, Christophe Diot Sprint ATL Burlingame, CA dina@sprintlabs.com Electrical and Computer Engineering Department University
AUTONOMOUS NETWORK SECURITY FOR DETECTION OF NETWORK ATTACKS
 AUTONOMOUS NETWORK SECURITY FOR DETECTION OF NETWORK ATTACKS Nita V. Jaiswal* Prof. D. M. Dakhne** Abstract: Current network monitoring systems rely strongly on signature-based and supervised-learning-based
AUTONOMOUS NETWORK SECURITY FOR DETECTION OF NETWORK ATTACKS Nita V. Jaiswal* Prof. D. M. Dakhne** Abstract: Current network monitoring systems rely strongly on signature-based and supervised-learning-based
Network TrafficBehaviorAnalysisby Decomposition into Control and Data Planes
 Network TrafficBehaviorAnalysisby Decomposition into Control and Data Planes Basil AsSadhan, Hyong Kim, José M. F. Moura, Xiaohui Wang Carnegie Mellon University Electrical and Computer Engineering Department
Network TrafficBehaviorAnalysisby Decomposition into Control and Data Planes Basil AsSadhan, Hyong Kim, José M. F. Moura, Xiaohui Wang Carnegie Mellon University Electrical and Computer Engineering Department
A Wavelet Based Prediction Method for Time Series
 A Wavelet Based Prediction Method for Time Series Cristina Stolojescu 1,2 Ion Railean 1,3 Sorin Moga 1 Philippe Lenca 1 and Alexandru Isar 2 1 Institut TELECOM; TELECOM Bretagne, UMR CNRS 3192 Lab-STICC;
A Wavelet Based Prediction Method for Time Series Cristina Stolojescu 1,2 Ion Railean 1,3 Sorin Moga 1 Philippe Lenca 1 and Alexandru Isar 2 1 Institut TELECOM; TELECOM Bretagne, UMR CNRS 3192 Lab-STICC;
A Hybrid Approach to Efficient Detection of Distributed Denial-of-Service Attacks
 Technical Report, June 2008 A Hybrid Approach to Efficient Detection of Distributed Denial-of-Service Attacks Christos Papadopoulos Department of Computer Science Colorado State University 1873 Campus
Technical Report, June 2008 A Hybrid Approach to Efficient Detection of Distributed Denial-of-Service Attacks Christos Papadopoulos Department of Computer Science Colorado State University 1873 Campus
Time-Series Models for Internet Data Traffic. Chun You and Kavitha Chandra
 1 Time-Series Models for Internet Data Traffic Chun You and Kavitha Chandra Center for Advanced Computation and Telecommunications Department of Electrical and Computer Engineering University of Massachusetts
1 Time-Series Models for Internet Data Traffic Chun You and Kavitha Chandra Center for Advanced Computation and Telecommunications Department of Electrical and Computer Engineering University of Massachusetts
Time-Frequency Detection Algorithm of Network Traffic Anomalies
 2012 International Conference on Innovation and Information Management (ICIIM 2012) IPCSIT vol. 36 (2012) (2012) IACSIT Press, Singapore Time-Frequency Detection Algorithm of Network Traffic Anomalies
2012 International Conference on Innovation and Information Management (ICIIM 2012) IPCSIT vol. 36 (2012) (2012) IACSIT Press, Singapore Time-Frequency Detection Algorithm of Network Traffic Anomalies
Structural Analysis of Network Traffic Flows Eric Kolaczyk
 Structural Analysis of Network Traffic Flows Eric Kolaczyk Anukool Lakhina, Dina Papagiannaki, Mark Crovella, Christophe Diot, and Nina Taft Traditional Network Traffic Analysis Focus on Short stationary
Structural Analysis of Network Traffic Flows Eric Kolaczyk Anukool Lakhina, Dina Papagiannaki, Mark Crovella, Christophe Diot, and Nina Taft Traditional Network Traffic Analysis Focus on Short stationary
Network Traffic Analysis Using Principal Component Graphs
 Network Traffic Analysis Using Principal Component Graphs Harsha Sai Thota Indian Institute of Technology Guwahati, Assam, India harsha.sai@iitg.ernet.in V. Vijaya Saradhi Indian Institute of Technology
Network Traffic Analysis Using Principal Component Graphs Harsha Sai Thota Indian Institute of Technology Guwahati, Assam, India harsha.sai@iitg.ernet.in V. Vijaya Saradhi Indian Institute of Technology
Signal Processing Methods for Denial of Service Attack Detection
 0 Signal Processing Methods for Denial of Service Attack Detection Urbashi Mitra Ming Hsieh Department of Electrical Engineering Viterbi School of Engineering University of Southern California Los Angeles,
0 Signal Processing Methods for Denial of Service Attack Detection Urbashi Mitra Ming Hsieh Department of Electrical Engineering Viterbi School of Engineering University of Southern California Los Angeles,
Time Series Analysis of Network Traffic
 Time Series Analysis of Network Traffic Cyriac James IIT MADRAS February 9, 211 Cyriac James (IIT MADRAS) February 9, 211 1 / 31 Outline of the presentation Background Motivation for the Work Network Trace
Time Series Analysis of Network Traffic Cyriac James IIT MADRAS February 9, 211 Cyriac James (IIT MADRAS) February 9, 211 1 / 31 Outline of the presentation Background Motivation for the Work Network Trace
Monitoring of Internet traffic and applications
 Monitoring of Internet traffic and applications Chadi BARAKAT INRIA Sophia Antipolis, France Planète research group ETH Zurich October 2009 Email: Chadi.Barakat@sophia.inria.fr WEB: http://www.inria.fr/planete/chadi
Monitoring of Internet traffic and applications Chadi BARAKAT INRIA Sophia Antipolis, France Planète research group ETH Zurich October 2009 Email: Chadi.Barakat@sophia.inria.fr WEB: http://www.inria.fr/planete/chadi
Internet Traffic Measurement
 Internet Traffic Measurement Internet Traffic Measurement Network Monitor Placement Measurement Analysis Tools Measurement Result Reporting Probing Mechanism Vantage Points Edge vs Core Hardware vs Software
Internet Traffic Measurement Internet Traffic Measurement Network Monitor Placement Measurement Analysis Tools Measurement Result Reporting Probing Mechanism Vantage Points Edge vs Core Hardware vs Software
modeling Network Traffic
 Aalborg Universitet Characterization and Modeling of Network Shawky, Ahmed Sherif Mahmoud; Bergheim, Hans ; Ragnarsson, Olafur ; Wranty, Andrzej ; Pedersen, Jens Myrup Published in: Proceedings of 6th
Aalborg Universitet Characterization and Modeling of Network Shawky, Ahmed Sherif Mahmoud; Bergheim, Hans ; Ragnarsson, Olafur ; Wranty, Andrzej ; Pedersen, Jens Myrup Published in: Proceedings of 6th
SOFTWARE FOR GENERATION OF SPECTRUM COMPATIBLE TIME HISTORY
 3 th World Conference on Earthquake Engineering Vancouver, B.C., Canada August -6, 24 Paper No. 296 SOFTWARE FOR GENERATION OF SPECTRUM COMPATIBLE TIME HISTORY ASHOK KUMAR SUMMARY One of the important
3 th World Conference on Earthquake Engineering Vancouver, B.C., Canada August -6, 24 Paper No. 296 SOFTWARE FOR GENERATION OF SPECTRUM COMPATIBLE TIME HISTORY ASHOK KUMAR SUMMARY One of the important
Echidna: Efficient Clustering of Hierarchical Data for Network Traffic Analysis
 Echidna: Efficient Clustering of Hierarchical Data for Network Traffic Analysis Abdun Mahmood, Christopher Leckie, Parampalli Udaya Department of Computer Science and Software Engineering University of
Echidna: Efficient Clustering of Hierarchical Data for Network Traffic Analysis Abdun Mahmood, Christopher Leckie, Parampalli Udaya Department of Computer Science and Software Engineering University of
Detection of Distributed Denial of Service Attack with Hadoop on Live Network
 Detection of Distributed Denial of Service Attack with Hadoop on Live Network Suchita Korad 1, Shubhada Kadam 2, Prajakta Deore 3, Madhuri Jadhav 4, Prof.Rahul Patil 5 Students, Dept. of Computer, PCCOE,
Detection of Distributed Denial of Service Attack with Hadoop on Live Network Suchita Korad 1, Shubhada Kadam 2, Prajakta Deore 3, Madhuri Jadhav 4, Prof.Rahul Patil 5 Students, Dept. of Computer, PCCOE,
Improving the Performance of TCP Using Window Adjustment Procedure and Bandwidth Estimation
 Improving the Performance of TCP Using Window Adjustment Procedure and Bandwidth Estimation R.Navaneethakrishnan Assistant Professor (SG) Bharathiyar College of Engineering and Technology, Karaikal, India.
Improving the Performance of TCP Using Window Adjustment Procedure and Bandwidth Estimation R.Navaneethakrishnan Assistant Professor (SG) Bharathiyar College of Engineering and Technology, Karaikal, India.
Internet Traffic Variability (Long Range Dependency Effects) Dheeraj Reddy CS8803 Fall 2003
 Internet Traffic Variability (Long Range Dependency Effects) Dheeraj Reddy CS8803 Fall 2003 Self-similarity and its evolution in Computer Network Measurements Prior models used Poisson-like models Origins
Internet Traffic Variability (Long Range Dependency Effects) Dheeraj Reddy CS8803 Fall 2003 Self-similarity and its evolution in Computer Network Measurements Prior models used Poisson-like models Origins
Seamless Congestion Control over Wired and Wireless IEEE 802.11 Networks
 Seamless Congestion Control over Wired and Wireless IEEE 802.11 Networks Vasilios A. Siris and Despina Triantafyllidou Institute of Computer Science (ICS) Foundation for Research and Technology - Hellas
Seamless Congestion Control over Wired and Wireless IEEE 802.11 Networks Vasilios A. Siris and Despina Triantafyllidou Institute of Computer Science (ICS) Foundation for Research and Technology - Hellas
Measurement and Modelling of Internet Traffic at Access Networks
 Measurement and Modelling of Internet Traffic at Access Networks Johannes Färber, Stefan Bodamer, Joachim Charzinski 2 University of Stuttgart, Institute of Communication Networks and Computer Engineering,
Measurement and Modelling of Internet Traffic at Access Networks Johannes Färber, Stefan Bodamer, Joachim Charzinski 2 University of Stuttgart, Institute of Communication Networks and Computer Engineering,
Network Traffic Invariant Characteristics:Metering Aspects
 etwork Traffic Invariant Characteristics:Metering Aspects Vladimir Zaborovsky, Andrey Rudskoy, Alex Sigalov Politechnical University, Robotics Institute St.Petersburg, Russia; Fractel Inc., USA, E-mail:
etwork Traffic Invariant Characteristics:Metering Aspects Vladimir Zaborovsky, Andrey Rudskoy, Alex Sigalov Politechnical University, Robotics Institute St.Petersburg, Russia; Fractel Inc., USA, E-mail:
An Anomaly-Based Method for DDoS Attacks Detection using RBF Neural Networks
 2011 International Conference on Network and Electronics Engineering IPCSIT vol.11 (2011) (2011) IACSIT Press, Singapore An Anomaly-Based Method for DDoS Attacks Detection using RBF Neural Networks Reyhaneh
2011 International Conference on Network and Electronics Engineering IPCSIT vol.11 (2011) (2011) IACSIT Press, Singapore An Anomaly-Based Method for DDoS Attacks Detection using RBF Neural Networks Reyhaneh
Analysis of Internet Topologies: A Historical View
 Analysis of Internet Topologies: A Historical View Mohamadreza Najiminaini, Laxmi Subedi, and Ljiljana Trajković Communication Networks Laboratory http://www.ensc.sfu.ca/cnl Simon Fraser University Vancouver,
Analysis of Internet Topologies: A Historical View Mohamadreza Najiminaini, Laxmi Subedi, and Ljiljana Trajković Communication Networks Laboratory http://www.ensc.sfu.ca/cnl Simon Fraser University Vancouver,
Detecting Network Anomalies. Anant Shah
 Detecting Network Anomalies using Traffic Modeling Anant Shah Anomaly Detection Anomalies are deviations from established behavior In most cases anomalies are indications of problems The science of extracting
Detecting Network Anomalies using Traffic Modeling Anant Shah Anomaly Detection Anomalies are deviations from established behavior In most cases anomalies are indications of problems The science of extracting
Traffic Behavior Analysis with Poisson Sampling on High-speed Network 1
 Traffic Behavior Analysis with Poisson Sampling on High-speed etwork Guang Cheng Jian Gong (Computer Department of Southeast University anjing 0096, P.R.China) Abstract: With the subsequent increasing
Traffic Behavior Analysis with Poisson Sampling on High-speed etwork Guang Cheng Jian Gong (Computer Department of Southeast University anjing 0096, P.R.China) Abstract: With the subsequent increasing
Dynamics of Prefix Usage at an Edge Router
 Dynamics of Prefix Usage at an Edge Router Kaustubh Gadkari, Daniel Massey, and Christos Papadopoulos Computer Science Department, Colorado State University, USA {kaustubh, massey, christos@cs.colostate.edu}
Dynamics of Prefix Usage at an Edge Router Kaustubh Gadkari, Daniel Massey, and Christos Papadopoulos Computer Science Department, Colorado State University, USA {kaustubh, massey, christos@cs.colostate.edu}
Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches
 Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches PhD Thesis by Payam Birjandi Director: Prof. Mihai Datcu Problematic
Modelling, Extraction and Description of Intrinsic Cues of High Resolution Satellite Images: Independent Component Analysis based approaches PhD Thesis by Payam Birjandi Director: Prof. Mihai Datcu Problematic
Hadoop Technology for Flow Analysis of the Internet Traffic
 Hadoop Technology for Flow Analysis of the Internet Traffic Rakshitha Kiran P PG Scholar, Dept. of C.S, Shree Devi Institute of Technology, Mangalore, Karnataka, India ABSTRACT: Flow analysis of the internet
Hadoop Technology for Flow Analysis of the Internet Traffic Rakshitha Kiran P PG Scholar, Dept. of C.S, Shree Devi Institute of Technology, Mangalore, Karnataka, India ABSTRACT: Flow analysis of the internet
Load Distribution in Large Scale Network Monitoring Infrastructures
 Load Distribution in Large Scale Network Monitoring Infrastructures Josep Sanjuàs-Cuxart, Pere Barlet-Ros, Gianluca Iannaccone, and Josep Solé-Pareta Universitat Politècnica de Catalunya (UPC) {jsanjuas,pbarlet,pareta}@ac.upc.edu
Load Distribution in Large Scale Network Monitoring Infrastructures Josep Sanjuàs-Cuxart, Pere Barlet-Ros, Gianluca Iannaccone, and Josep Solé-Pareta Universitat Politècnica de Catalunya (UPC) {jsanjuas,pbarlet,pareta}@ac.upc.edu
An iterative tomogravity algorithm for the estimation of network traffic
 IMS Lecture Notes Monograph Series Complex Datasets and Inverse Problems: Tomography, Networks and Beyond Vol. 54 (2007) 12 23 c Institute of Mathematical Statistics, 2007 DOI: 10.1214/074921707000000030
IMS Lecture Notes Monograph Series Complex Datasets and Inverse Problems: Tomography, Networks and Beyond Vol. 54 (2007) 12 23 c Institute of Mathematical Statistics, 2007 DOI: 10.1214/074921707000000030
Estimation of available bandwidth and measurement infrastructure for. Russian segment of Internet
 1 Estimation of available bandwidth and measurement infrastructure for Abstracts Russian segment of Internet Platonov A.P. 1), Sidelnikov D.I. 2), Strizhov M.V. 3), Sukhov A.M. 4) 1) Russian Institute
1 Estimation of available bandwidth and measurement infrastructure for Abstracts Russian segment of Internet Platonov A.P. 1), Sidelnikov D.I. 2), Strizhov M.V. 3), Sukhov A.M. 4) 1) Russian Institute
TRAFFIC control and bandwidth management in ATM
 134 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 5, NO. 1, FEBRUARY 1997 A Framework for Bandwidth Management in ATM Networks Aggregate Equivalent Bandwidth Estimation Approach Zbigniew Dziong, Marek Juda,
134 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 5, NO. 1, FEBRUARY 1997 A Framework for Bandwidth Management in ATM Networks Aggregate Equivalent Bandwidth Estimation Approach Zbigniew Dziong, Marek Juda,
This document is downloaded from DR-NTU, Nanyang Technological University Library, Singapore.
 This document is downloaded from DR-NTU, Nanyang Technological University Library, Singapore. Title Transcription of polyphonic signals using fast filter bank( Accepted version ) Author(s) Foo, Say Wei;
This document is downloaded from DR-NTU, Nanyang Technological University Library, Singapore. Title Transcription of polyphonic signals using fast filter bank( Accepted version ) Author(s) Foo, Say Wei;
Monitoring Large Flows in Network
 Monitoring Large Flows in Network Jing Li, Chengchen Hu, Bin Liu Department of Computer Science and Technology, Tsinghua University Beijing, P. R. China, 100084 { l-j02, hucc03 }@mails.tsinghua.edu.cn,
Monitoring Large Flows in Network Jing Li, Chengchen Hu, Bin Liu Department of Computer Science and Technology, Tsinghua University Beijing, P. R. China, 100084 { l-j02, hucc03 }@mails.tsinghua.edu.cn,
OpenTM: Traffic Matrix Estimator for OpenFlow Networks
 OpenTM: Traffic Matrix Estimator for OpenFlow Networks Amin Tootoonchian, Monia Ghobadi, Yashar Ganjali {amin,monia,yganjali}@cs.toronto.edu Department of Computer Science University of Toronto, Toronto,
OpenTM: Traffic Matrix Estimator for OpenFlow Networks Amin Tootoonchian, Monia Ghobadi, Yashar Ganjali {amin,monia,yganjali}@cs.toronto.edu Department of Computer Science University of Toronto, Toronto,
Effect of sampling rate and monitoring granularity on anomaly detectability
 Effect of sampling rate and monitoring granularity on anomaly detectability Keisuke Ishibashi, Ryoichi Kawahara, Mori Tatsuya, Tsuyoshi Kondoh and Shoichiro Asano Information Sharing Platform Labs. NTT
Effect of sampling rate and monitoring granularity on anomaly detectability Keisuke Ishibashi, Ryoichi Kawahara, Mori Tatsuya, Tsuyoshi Kondoh and Shoichiro Asano Information Sharing Platform Labs. NTT
Probability and Random Variables. Generation of random variables (r.v.)
 Probability and Random Variables Method for generating random variables with a specified probability distribution function. Gaussian And Markov Processes Characterization of Stationary Random Process Linearly
Probability and Random Variables Method for generating random variables with a specified probability distribution function. Gaussian And Markov Processes Characterization of Stationary Random Process Linearly
Analysis of Internet Topologies
 Analysis of Internet Topologies Ljiljana Trajković ljilja@cs.sfu.ca Communication Networks Laboratory http://www.ensc.sfu.ca/cnl School of Engineering Science Simon Fraser University, Vancouver, British
Analysis of Internet Topologies Ljiljana Trajković ljilja@cs.sfu.ca Communication Networks Laboratory http://www.ensc.sfu.ca/cnl School of Engineering Science Simon Fraser University, Vancouver, British
Probability-Model based Network Traffic Matrix Estimation
 Computer Science and Information Systems ():309 30 DOI: 0.98/CSIS3000T Probability-Model based Network Traffic Matrix Estimation Hui Tian, Yingpeng Sang, Hong Shen 3,4, and Chunyue Zhou School of Electronics
Computer Science and Information Systems ():309 30 DOI: 0.98/CSIS3000T Probability-Model based Network Traffic Matrix Estimation Hui Tian, Yingpeng Sang, Hong Shen 3,4, and Chunyue Zhou School of Electronics
Univariate and Multivariate Methods PEARSON. Addison Wesley
 Time Series Analysis Univariate and Multivariate Methods SECOND EDITION William W. S. Wei Department of Statistics The Fox School of Business and Management Temple University PEARSON Addison Wesley Boston
Time Series Analysis Univariate and Multivariate Methods SECOND EDITION William W. S. Wei Department of Statistics The Fox School of Business and Management Temple University PEARSON Addison Wesley Boston
CONTROL SYSTEM FOR INTERNET BANDWIDTH BASED ON JAVA TECHNOLOGY
 CONTROL SYSTEM FOR INTERNET BANDWIDTH BASED ON JAVA TECHNOLOGY SEIFEDINE KADRY, KHALED SMAILI Lebanese University-Faculty of Sciences Beirut-Lebanon E-mail: skadry@gmail.com ABSTRACT This paper presents
CONTROL SYSTEM FOR INTERNET BANDWIDTH BASED ON JAVA TECHNOLOGY SEIFEDINE KADRY, KHALED SMAILI Lebanese University-Faculty of Sciences Beirut-Lebanon E-mail: skadry@gmail.com ABSTRACT This paper presents
Co-integration of Stock Markets using Wavelet Theory and Data Mining
 Co-integration of Stock Markets using Wavelet Theory and Data Mining R.Sahu P.B.Sanjeev rsahu@iiitm.ac.in sanjeev@iiitm.ac.in ABV-Indian Institute of Information Technology and Management, India Abstract
Co-integration of Stock Markets using Wavelet Theory and Data Mining R.Sahu P.B.Sanjeev rsahu@iiitm.ac.in sanjeev@iiitm.ac.in ABV-Indian Institute of Information Technology and Management, India Abstract
Comparative Analysis of Congestion Control Algorithms Using ns-2
 www.ijcsi.org 89 Comparative Analysis of Congestion Control Algorithms Using ns-2 Sanjeev Patel 1, P. K. Gupta 2, Arjun Garg 3, Prateek Mehrotra 4 and Manish Chhabra 5 1 Deptt. of Computer Sc. & Engg,
www.ijcsi.org 89 Comparative Analysis of Congestion Control Algorithms Using ns-2 Sanjeev Patel 1, P. K. Gupta 2, Arjun Garg 3, Prateek Mehrotra 4 and Manish Chhabra 5 1 Deptt. of Computer Sc. & Engg,
Time series analysis of data from stress ECG
 Communications to SIMAI Congress, ISSN 827-905, Vol. 3 (2009) DOI: 0.685/CSC09XXX Time series analysis of data from stress ECG Camillo Cammarota Dipartimento di Matematica La Sapienza Università di Roma,
Communications to SIMAI Congress, ISSN 827-905, Vol. 3 (2009) DOI: 0.685/CSC09XXX Time series analysis of data from stress ECG Camillo Cammarota Dipartimento di Matematica La Sapienza Università di Roma,
Enhancing the SNR of the Fiber Optic Rotation Sensor using the LMS Algorithm
 1 Enhancing the SNR of the Fiber Optic Rotation Sensor using the LMS Algorithm Hani Mehrpouyan, Student Member, IEEE, Department of Electrical and Computer Engineering Queen s University, Kingston, Ontario,
1 Enhancing the SNR of the Fiber Optic Rotation Sensor using the LMS Algorithm Hani Mehrpouyan, Student Member, IEEE, Department of Electrical and Computer Engineering Queen s University, Kingston, Ontario,
Synchronization of sampling in distributed signal processing systems
 Synchronization of sampling in distributed signal processing systems Károly Molnár, László Sujbert, Gábor Péceli Department of Measurement and Information Systems, Budapest University of Technology and
Synchronization of sampling in distributed signal processing systems Károly Molnár, László Sujbert, Gábor Péceli Department of Measurement and Information Systems, Budapest University of Technology and
Research on Errors of Utilized Bandwidth Measured by NetFlow
 Research on s of Utilized Bandwidth Measured by NetFlow Haiting Zhu 1, Xiaoguo Zhang 1,2, Wei Ding 1 1 School of Computer Science and Engineering, Southeast University, Nanjing 211189, China 2 Electronic
Research on s of Utilized Bandwidth Measured by NetFlow Haiting Zhu 1, Xiaoguo Zhang 1,2, Wei Ding 1 1 School of Computer Science and Engineering, Southeast University, Nanjing 211189, China 2 Electronic
4F7 Adaptive Filters (and Spectrum Estimation) Least Mean Square (LMS) Algorithm Sumeetpal Singh Engineering Department Email : sss40@eng.cam.ac.
 4F7 Adaptive Filters (and Spectrum Estimation) Least Mean Square (LMS) Algorithm Sumeetpal Singh Engineering Department Email : sss40@eng.cam.ac.uk 1 1 Outline The LMS algorithm Overview of LMS issues
4F7 Adaptive Filters (and Spectrum Estimation) Least Mean Square (LMS) Algorithm Sumeetpal Singh Engineering Department Email : sss40@eng.cam.ac.uk 1 1 Outline The LMS algorithm Overview of LMS issues
The Combination Forecasting Model of Auto Sales Based on Seasonal Index and RBF Neural Network
 , pp.67-76 http://dx.doi.org/10.14257/ijdta.2016.9.1.06 The Combination Forecasting Model of Auto Sales Based on Seasonal Index and RBF Neural Network Lihua Yang and Baolin Li* School of Economics and
, pp.67-76 http://dx.doi.org/10.14257/ijdta.2016.9.1.06 The Combination Forecasting Model of Auto Sales Based on Seasonal Index and RBF Neural Network Lihua Yang and Baolin Li* School of Economics and
Denial of Service and Anomaly Detection
 Denial of Service and Anomaly Detection Vasilios A. Siris Institute of Computer Science (ICS) FORTH, Crete, Greece vsiris@ics.forth.gr SCAMPI BoF, Zagreb, May 21 2002 Overview! What the problem is and
Denial of Service and Anomaly Detection Vasilios A. Siris Institute of Computer Science (ICS) FORTH, Crete, Greece vsiris@ics.forth.gr SCAMPI BoF, Zagreb, May 21 2002 Overview! What the problem is and
Obfuscation of sensitive data in network flows 1
 Obfuscation of sensitive data in network flows 1 D. Riboni 2, A. Villani 1, D. Vitali 1 C. Bettini 2, L.V. Mancini 1 1 Dipartimento di Informatica,Universitá di Roma, Sapienza. E-mail: {villani, vitali,
Obfuscation of sensitive data in network flows 1 D. Riboni 2, A. Villani 1, D. Vitali 1 C. Bettini 2, L.V. Mancini 1 1 Dipartimento di Informatica,Universitá di Roma, Sapienza. E-mail: {villani, vitali,
Attenuation (amplitude of the wave loses strength thereby the signal power) Refraction Reflection Shadowing Scattering Diffraction
 Wireless Physical Layer Q1. Is it possible to transmit a digital signal, e.g., coded as square wave as used inside a computer, using radio transmission without any loss? Why? It is not possible to transmit
Wireless Physical Layer Q1. Is it possible to transmit a digital signal, e.g., coded as square wave as used inside a computer, using radio transmission without any loss? Why? It is not possible to transmit
MUSIC-like Processing of Pulsed Continuous Wave Signals in Active Sonar Experiments
 23rd European Signal Processing Conference EUSIPCO) MUSIC-like Processing of Pulsed Continuous Wave Signals in Active Sonar Experiments Hock Siong LIM hales Research and echnology, Singapore hales Solutions
23rd European Signal Processing Conference EUSIPCO) MUSIC-like Processing of Pulsed Continuous Wave Signals in Active Sonar Experiments Hock Siong LIM hales Research and echnology, Singapore hales Solutions
IN current film media, the increase in areal density has
 IEEE TRANSACTIONS ON MAGNETICS, VOL. 44, NO. 1, JANUARY 2008 193 A New Read Channel Model for Patterned Media Storage Seyhan Karakulak, Paul H. Siegel, Fellow, IEEE, Jack K. Wolf, Life Fellow, IEEE, and
IEEE TRANSACTIONS ON MAGNETICS, VOL. 44, NO. 1, JANUARY 2008 193 A New Read Channel Model for Patterned Media Storage Seyhan Karakulak, Paul H. Siegel, Fellow, IEEE, Jack K. Wolf, Life Fellow, IEEE, and
ANALYZER BASICS WHAT IS AN FFT SPECTRUM ANALYZER? 2-1
 WHAT IS AN FFT SPECTRUM ANALYZER? ANALYZER BASICS The SR760 FFT Spectrum Analyzer takes a time varying input signal, like you would see on an oscilloscope trace, and computes its frequency spectrum. Fourier's
WHAT IS AN FFT SPECTRUM ANALYZER? ANALYZER BASICS The SR760 FFT Spectrum Analyzer takes a time varying input signal, like you would see on an oscilloscope trace, and computes its frequency spectrum. Fourier's
Joint Entropy Analysis Model for DDoS Attack Detection
 2009 Fifth International Conference on Information Assurance and Security Joint Entropy Analysis Model for DDoS Attack Detection Hamza Rahmani, Nabil Sahli, Farouk Kammoun CRISTAL Lab., National School
2009 Fifth International Conference on Information Assurance and Security Joint Entropy Analysis Model for DDoS Attack Detection Hamza Rahmani, Nabil Sahli, Farouk Kammoun CRISTAL Lab., National School
Mining Trends From Network Traffic Data for Security Systems
 Mining Trends From Network Traffic Data for Security Systems Jennifer Li Computer Science Department Louisiana State University jli13@tigers.lsu.edu Graduate Mentor: Blaine Nelson, Saurabh Amin, and Dr.
Mining Trends From Network Traffic Data for Security Systems Jennifer Li Computer Science Department Louisiana State University jli13@tigers.lsu.edu Graduate Mentor: Blaine Nelson, Saurabh Amin, and Dr.
CLASSIFYING NETWORK TRAFFIC IN THE BIG DATA ERA
 CLASSIFYING NETWORK TRAFFIC IN THE BIG DATA ERA Professor Yang Xiang Network Security and Computing Laboratory (NSCLab) School of Information Technology Deakin University, Melbourne, Australia http://anss.org.au/nsclab
CLASSIFYING NETWORK TRAFFIC IN THE BIG DATA ERA Professor Yang Xiang Network Security and Computing Laboratory (NSCLab) School of Information Technology Deakin University, Melbourne, Australia http://anss.org.au/nsclab
SNMP Simple Network Measurements Please!
 SNMP Simple Network Measurements Please! Matthew Roughan (+many others) 1 Outline Part I: SNMP traffic data Simple Network Management Protocol Why? How? What? Part II: Wavelets
SNMP Simple Network Measurements Please! Matthew Roughan (+many others) 1 Outline Part I: SNMP traffic data Simple Network Management Protocol Why? How? What? Part II: Wavelets
Detecting Flooding Attacks Using Power Divergence
 Detecting Flooding Attacks Using Power Divergence Jean Tajer IT Security for the Next Generation European Cup, Prague 17-19 February, 2012 PAGE 1 Agenda 1- Introduction 2- K-ary Sktech 3- Detection Threshold
Detecting Flooding Attacks Using Power Divergence Jean Tajer IT Security for the Next Generation European Cup, Prague 17-19 February, 2012 PAGE 1 Agenda 1- Introduction 2- K-ary Sktech 3- Detection Threshold
ON THE FRACTAL CHARACTERISTICS OF NETWORK TRAFFIC AND ITS UTILIZATION IN COVERT COMMUNICATIONS
 ON THE FRACTAL CHARACTERISTICS OF NETWORK TRAFFIC AND ITS UTILIZATION IN COVERT COMMUNICATIONS Rashiq R. Marie Department of Computer Science email: R.R.Marie@lboro.ac.uk Helmut E. Bez Department of Computer
ON THE FRACTAL CHARACTERISTICS OF NETWORK TRAFFIC AND ITS UTILIZATION IN COVERT COMMUNICATIONS Rashiq R. Marie Department of Computer Science email: R.R.Marie@lboro.ac.uk Helmut E. Bez Department of Computer
Short-time FFT, Multi-taper analysis & Filtering in SPM12
 Short-time FFT, Multi-taper analysis & Filtering in SPM12 Computational Psychiatry Seminar, FS 2015 Daniel Renz, Translational Neuromodeling Unit, ETHZ & UZH 20.03.2015 Overview Refresher Short-time Fourier
Short-time FFT, Multi-taper analysis & Filtering in SPM12 Computational Psychiatry Seminar, FS 2015 Daniel Renz, Translational Neuromodeling Unit, ETHZ & UZH 20.03.2015 Overview Refresher Short-time Fourier
Observingtheeffectof TCP congestion controlon networktraffic
 Observingtheeffectof TCP congestion controlon networktraffic YongminChoi 1 andjohna.silvester ElectricalEngineering-SystemsDept. UniversityofSouthernCalifornia LosAngeles,CA90089-2565 {yongminc,silvester}@usc.edu
Observingtheeffectof TCP congestion controlon networktraffic YongminChoi 1 andjohna.silvester ElectricalEngineering-SystemsDept. UniversityofSouthernCalifornia LosAngeles,CA90089-2565 {yongminc,silvester}@usc.edu
Defend against Anomaly Intrusion Detection using SWT Mechanism
 Defend against Anomaly Intrusion Detection using SWT Mechanism M.Thangavel 1, Dr. P.Thangaraj 2 and K.Saravanan 3 Abstract In the fast growing internet commercial transaction base, attacks on Internet
Defend against Anomaly Intrusion Detection using SWT Mechanism M.Thangavel 1, Dr. P.Thangaraj 2 and K.Saravanan 3 Abstract In the fast growing internet commercial transaction base, attacks on Internet
Time series analysis as a framework for the characterization of waterborne disease outbreaks
 Interdisciplinary Perspectives on Drinking Water Risk Assessment and Management (Proceedings of the Santiago (Chile) Symposium, September 1998). IAHS Publ. no. 260, 2000. 127 Time series analysis as a
Interdisciplinary Perspectives on Drinking Water Risk Assessment and Management (Proceedings of the Santiago (Chile) Symposium, September 1998). IAHS Publ. no. 260, 2000. 127 Time series analysis as a
Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT)
 Page 1 Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT) ECC RECOMMENDATION (06)01 Bandwidth measurements using FFT techniques
Page 1 Electronic Communications Committee (ECC) within the European Conference of Postal and Telecommunications Administrations (CEPT) ECC RECOMMENDATION (06)01 Bandwidth measurements using FFT techniques
Algorithms for Interference Sensing in Optical CDMA Networks
 Algorithms for Interference Sensing in Optical CDMA Networks Purushotham Kamath, Joseph D. Touch and Joseph A. Bannister {pkamath, touch, joseph}@isi.edu Information Sciences Institute, University of Southern
Algorithms for Interference Sensing in Optical CDMA Networks Purushotham Kamath, Joseph D. Touch and Joseph A. Bannister {pkamath, touch, joseph}@isi.edu Information Sciences Institute, University of Southern
Linking Network Usage Patterns to Traffic Gaussianity Fit
 Linking Network Usage Patterns to Traffic Gaussianity Fit Ricardo de O. Schmidt, Ramin Sadre, Nikolay Melnikov, Jürgen Schönwälder, Aiko Pras University of Twente, The Netherlands Email: {r.schmidt,a.pras}@utwente.nl
Linking Network Usage Patterns to Traffic Gaussianity Fit Ricardo de O. Schmidt, Ramin Sadre, Nikolay Melnikov, Jürgen Schönwälder, Aiko Pras University of Twente, The Netherlands Email: {r.schmidt,a.pras}@utwente.nl
Bandwidth Measurement in xdsl Networks
 Bandwidth Measurement in xdsl Networks Liang Cheng and Ivan Marsic Center for Advanced Information Processing (CAIP) Rutgers The State University of New Jersey Piscataway, NJ 08854-8088, USA {chengl,marsic}@caip.rutgers.edu
Bandwidth Measurement in xdsl Networks Liang Cheng and Ivan Marsic Center for Advanced Information Processing (CAIP) Rutgers The State University of New Jersey Piscataway, NJ 08854-8088, USA {chengl,marsic}@caip.rutgers.edu
Hashdoop: A MapReduce Framework for Network Anomaly Detection
 Hashdoop: A MapReduce Framework for Network Anomaly Detection Romain Fontugne, Johan Mazel, Kensuke Fukuda National Institute of Informatics Japanese - French Laboratory for Informatics Tokyo, Japan Abstract
Hashdoop: A MapReduce Framework for Network Anomaly Detection Romain Fontugne, Johan Mazel, Kensuke Fukuda National Institute of Informatics Japanese - French Laboratory for Informatics Tokyo, Japan Abstract
Sequential Non-Bayesian Network Traffic Flows Anomaly Detection and Isolation
 Sequential Non-Bayesian Network Traffic Flows Anomaly Detection and Isolation Lionel Fillatre 1, Igor Nikiforov 1, Sandrine Vaton 2, and Pedro Casas 2 1 Institut Charles Delaunay/LM2S, FRE CNRS 2848, Université
Sequential Non-Bayesian Network Traffic Flows Anomaly Detection and Isolation Lionel Fillatre 1, Igor Nikiforov 1, Sandrine Vaton 2, and Pedro Casas 2 1 Institut Charles Delaunay/LM2S, FRE CNRS 2848, Université
Time Series Analysis and Forecasting Methods for Temporal Mining of Interlinked Documents
 Time Series Analysis and Forecasting Methods for Temporal Mining of Interlinked Documents Prasanna Desikan and Jaideep Srivastava Department of Computer Science University of Minnesota. @cs.umn.edu
Time Series Analysis and Forecasting Methods for Temporal Mining of Interlinked Documents Prasanna Desikan and Jaideep Srivastava Department of Computer Science University of Minnesota. @cs.umn.edu
Application of Netflow logs in Analysis and Detection of DDoS Attacks
 International Journal of Computer and Internet Security. ISSN 0974-2247 Volume 8, Number 1 (2016), pp. 1-8 International Research Publication House http://www.irphouse.com Application of Netflow logs in
International Journal of Computer and Internet Security. ISSN 0974-2247 Volume 8, Number 1 (2016), pp. 1-8 International Research Publication House http://www.irphouse.com Application of Netflow logs in
Reformulating the Monitor Placement Problem: Optimal Network-Wide Sampling
 1 Reformulating the Monitor Placement Problem: Optimal Network-Wide Sampling Gion Reto Cantieni, Gianluca Iannaccone, Chadi Barakat, Christophe Diot, Patrick Thiran Abstract Confronted with the generalization
1 Reformulating the Monitor Placement Problem: Optimal Network-Wide Sampling Gion Reto Cantieni, Gianluca Iannaccone, Chadi Barakat, Christophe Diot, Patrick Thiran Abstract Confronted with the generalization
How To Use Neural Networks In Data Mining
 International Journal of Electronics and Computer Science Engineering 1449 Available Online at www.ijecse.org ISSN- 2277-1956 Neural Networks in Data Mining Priyanka Gaur Department of Information and
International Journal of Electronics and Computer Science Engineering 1449 Available Online at www.ijecse.org ISSN- 2277-1956 Neural Networks in Data Mining Priyanka Gaur Department of Information and
Summary Nonstationary Time Series Multitude of Representations Possibilities from Applied Computational Harmonic Analysis Tests of Stationarity
 Nonstationary Time Series, Priestley s Evolutionary Spectra and Wavelets Guy Nason, School of Mathematics, University of Bristol Summary Nonstationary Time Series Multitude of Representations Possibilities
Nonstationary Time Series, Priestley s Evolutionary Spectra and Wavelets Guy Nason, School of Mathematics, University of Bristol Summary Nonstationary Time Series Multitude of Representations Possibilities
How is SUNET really used?
 MonNet a project for network and traffic monitoring How is SUNET really used? Results of traffic classification on backbone data Wolfgang John and Sven Tafvelin Dept. of Computer Science and Engineering
MonNet a project for network and traffic monitoring How is SUNET really used? Results of traffic classification on backbone data Wolfgang John and Sven Tafvelin Dept. of Computer Science and Engineering
Time-frequency segmentation : statistical and local phase analysis
 Time-frequency segmentation : statistical and local phase analysis Florian DADOUCHI 1, Cornel IOANA 1, Julien HUILLERY 2, Cédric GERVAISE 1,3, Jérôme I. MARS 1 1 GIPSA-Lab, University of Grenoble 2 Ampère
Time-frequency segmentation : statistical and local phase analysis Florian DADOUCHI 1, Cornel IOANA 1, Julien HUILLERY 2, Cédric GERVAISE 1,3, Jérôme I. MARS 1 1 GIPSA-Lab, University of Grenoble 2 Ampère
The CUSUM algorithm a small review. Pierre Granjon
 The CUSUM algorithm a small review Pierre Granjon June, 1 Contents 1 The CUSUM algorithm 1.1 Algorithm............................... 1.1.1 The problem......................... 1.1. The different steps......................
The CUSUM algorithm a small review Pierre Granjon June, 1 Contents 1 The CUSUM algorithm 1.1 Algorithm............................... 1.1.1 The problem......................... 1.1. The different steps......................
SYNCHRONIZATION IN PACKET NETWORKS: TIMING METRICS AND MONITORING
 SYNCHRONIZATION IN PACKET NETWORKS: TIMING METRICS AND MONITORING Charles Barry and Srinivas Bangalore Brilliant Telecommunications 307 Orchard City Drive, San Jose, CA 95008, USA E-mail: srinivas@brillianttelecom.com
SYNCHRONIZATION IN PACKET NETWORKS: TIMING METRICS AND MONITORING Charles Barry and Srinivas Bangalore Brilliant Telecommunications 307 Orchard City Drive, San Jose, CA 95008, USA E-mail: srinivas@brillianttelecom.com
Mining Anomalies in Network-Wide Flow Data. Anukool Lakhina, Ph.D. with Mark Crovella and Christophe Diot
 Mining Anomalies in Network-Wide Flow Data Anukool Lakhina, Ph.D. with Mark Crovella and Christophe Diot SANOG-7, Mumbai, January, 00 Network Anomaly Diagnosis Am I being attacked? Is someone scanning
Mining Anomalies in Network-Wide Flow Data Anukool Lakhina, Ph.D. with Mark Crovella and Christophe Diot SANOG-7, Mumbai, January, 00 Network Anomaly Diagnosis Am I being attacked? Is someone scanning
Least Squares Estimation
 Least Squares Estimation SARA A VAN DE GEER Volume 2, pp 1041 1045 in Encyclopedia of Statistics in Behavioral Science ISBN-13: 978-0-470-86080-9 ISBN-10: 0-470-86080-4 Editors Brian S Everitt & David
Least Squares Estimation SARA A VAN DE GEER Volume 2, pp 1041 1045 in Encyclopedia of Statistics in Behavioral Science ISBN-13: 978-0-470-86080-9 ISBN-10: 0-470-86080-4 Editors Brian S Everitt & David
A Reliability Point and Kalman Filter-based Vehicle Tracking Technique
 A Reliability Point and Kalman Filter-based Vehicle Tracing Technique Soo Siang Teoh and Thomas Bräunl Abstract This paper introduces a technique for tracing the movement of vehicles in consecutive video
A Reliability Point and Kalman Filter-based Vehicle Tracing Technique Soo Siang Teoh and Thomas Bräunl Abstract This paper introduces a technique for tracing the movement of vehicles in consecutive video
NETWORK REQUIREMENTS FOR HIGH-SPEED REAL-TIME MULTIMEDIA DATA STREAMS
 NETWORK REQUIREMENTS FOR HIGH-SPEED REAL-TIME MULTIMEDIA DATA STREAMS Andrei Sukhov 1), Prasad Calyam 2), Warren Daly 3), Alexander Iliin 4) 1) Laboratory of Network Technologies, Samara Academy of Transport
NETWORK REQUIREMENTS FOR HIGH-SPEED REAL-TIME MULTIMEDIA DATA STREAMS Andrei Sukhov 1), Prasad Calyam 2), Warren Daly 3), Alexander Iliin 4) 1) Laboratory of Network Technologies, Samara Academy of Transport
Trends and Differences in Connection-behavior within Classes of Internet Backbone Traffic
 MonNet a project for network and traffic monitoring Trends and Differences in Connection-behavior within Classes of Internet Backbone Traffic Wolfgang John, Sven Tafvelin and Tomas Olovsson Department
MonNet a project for network and traffic monitoring Trends and Differences in Connection-behavior within Classes of Internet Backbone Traffic Wolfgang John, Sven Tafvelin and Tomas Olovsson Department
Internet Traffic Analysis and the Unidirectional Classifier
 Classification of emerging protocols in the presence of asymmetric routing M. Crotti, F. Gringoli, L. Salgarelli Università degli Studi di Brescia, Brescia, Italy, @ing.unibs.it Summary.
Classification of emerging protocols in the presence of asymmetric routing M. Crotti, F. Gringoli, L. Salgarelli Università degli Studi di Brescia, Brescia, Italy, @ing.unibs.it Summary.
Network Traffic Modeling and Prediction with ARIMA/GARCH
 Network Traffic Modeling and Prediction with ARIMA/GARCH Bo Zhou, Dan He, Zhili Sun and Wee Hock Ng Centre for Communication System Research University of Surrey Guildford, Surrey United Kingdom +44(0)
Network Traffic Modeling and Prediction with ARIMA/GARCH Bo Zhou, Dan He, Zhili Sun and Wee Hock Ng Centre for Communication System Research University of Surrey Guildford, Surrey United Kingdom +44(0)
Time series Forecasting using Holt-Winters Exponential Smoothing
 Time series Forecasting using Holt-Winters Exponential Smoothing Prajakta S. Kalekar(04329008) Kanwal Rekhi School of Information Technology Under the guidance of Prof. Bernard December 6, 2004 Abstract
Time series Forecasting using Holt-Winters Exponential Smoothing Prajakta S. Kalekar(04329008) Kanwal Rekhi School of Information Technology Under the guidance of Prof. Bernard December 6, 2004 Abstract
A Systemfor Scanning Traffic Detection in 3G WCDMA Network
 2012 IACSIT Hong Kong Conferences IPCSIT vol. 30 (2012) (2012) IACSIT Press, Singapore A Systemfor Scanning Traffic Detection in 3G WCDMA Network Sekwon Kim +, Joohyung Oh and Chaetae Im Advanced Technology
2012 IACSIT Hong Kong Conferences IPCSIT vol. 30 (2012) (2012) IACSIT Press, Singapore A Systemfor Scanning Traffic Detection in 3G WCDMA Network Sekwon Kim +, Joohyung Oh and Chaetae Im Advanced Technology
Predict the Popularity of YouTube Videos Using Early View Data
 000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
000 001 002 003 004 005 006 007 008 009 010 011 012 013 014 015 016 017 018 019 020 021 022 023 024 025 026 027 028 029 030 031 032 033 034 035 036 037 038 039 040 041 042 043 044 045 046 047 048 049 050
Towards Streaming Media Traffic Monitoring and Analysis. Hun-Jeong Kang, Hong-Taek Ju, Myung-Sup Kim and James W. Hong. DP&NM Lab.
 Towards Streaming Media Traffic Monitoring and Analysis Hun-Jeong Kang, Hong-Taek Ju, Myung-Sup Kim and James W. Hong Dept. of Computer Science and Engineering, Pohang Korea Email: {bluewind, juht, mount,
Towards Streaming Media Traffic Monitoring and Analysis Hun-Jeong Kang, Hong-Taek Ju, Myung-Sup Kim and James W. Hong Dept. of Computer Science and Engineering, Pohang Korea Email: {bluewind, juht, mount,
The Role of Size Normalization on the Recognition Rate of Handwritten Numerals
 The Role of Size Normalization on the Recognition Rate of Handwritten Numerals Chun Lei He, Ping Zhang, Jianxiong Dong, Ching Y. Suen, Tien D. Bui Centre for Pattern Recognition and Machine Intelligence,
The Role of Size Normalization on the Recognition Rate of Handwritten Numerals Chun Lei He, Ping Zhang, Jianxiong Dong, Ching Y. Suen, Tien D. Bui Centre for Pattern Recognition and Machine Intelligence,
Adaptive Equalization of binary encoded signals Using LMS Algorithm
 SSRG International Journal of Electronics and Communication Engineering (SSRG-IJECE) volume issue7 Sep Adaptive Equalization of binary encoded signals Using LMS Algorithm Dr.K.Nagi Reddy Professor of ECE,NBKR
SSRG International Journal of Electronics and Communication Engineering (SSRG-IJECE) volume issue7 Sep Adaptive Equalization of binary encoded signals Using LMS Algorithm Dr.K.Nagi Reddy Professor of ECE,NBKR
Examining Self-Similarity Network Traffic intervals
 Examining Self-Similarity Network Traffic intervals Hengky Susanto Byung-Guk Kim Computer Science Department University of Massachusetts at Lowell {hsusanto, kim}@cs.uml.edu Abstract Many studies have
Examining Self-Similarity Network Traffic intervals Hengky Susanto Byung-Guk Kim Computer Science Department University of Massachusetts at Lowell {hsusanto, kim}@cs.uml.edu Abstract Many studies have
WAVELET ANALYSIS BASED ULTRASONIC NONDESTRUCTIVE TESTING OF POLYMER BONDED EXPLOSIVE
 WAVELET ANALYSIS BASED ULTRASONIC NONDESTRUCTIVE TESTING OF POLYMER BONDED EXPLOSIVE Weibin Zhang, Yong Tian, Zhanfeng Yang, Liling Wang Institute of Chemical Materials, China Academy of Engineering Physics,
WAVELET ANALYSIS BASED ULTRASONIC NONDESTRUCTIVE TESTING OF POLYMER BONDED EXPLOSIVE Weibin Zhang, Yong Tian, Zhanfeng Yang, Liling Wang Institute of Chemical Materials, China Academy of Engineering Physics,
Metrics for Characterizing Complexity of Network Traffic
 Metrics for Characterizing Complexity of Network Traffic Janne Riihijärvi, Petri Mähönen and Matthias Wellens Department of Wireless Networks, RWTH Aachen University Kackertstrasse 9, D-52072 Aachen, Germany
Metrics for Characterizing Complexity of Network Traffic Janne Riihijärvi, Petri Mähönen and Matthias Wellens Department of Wireless Networks, RWTH Aachen University Kackertstrasse 9, D-52072 Aachen, Germany
Low-resolution Character Recognition by Video-based Super-resolution
 2009 10th International Conference on Document Analysis and Recognition Low-resolution Character Recognition by Video-based Super-resolution Ataru Ohkura 1, Daisuke Deguchi 1, Tomokazu Takahashi 2, Ichiro
2009 10th International Conference on Document Analysis and Recognition Low-resolution Character Recognition by Video-based Super-resolution Ataru Ohkura 1, Daisuke Deguchi 1, Tomokazu Takahashi 2, Ichiro
Profit Maximization and Power Management of Green Data Centers Supporting Multiple SLAs
 Profit Maximization and Power Management of Green Data Centers Supporting Multiple SLAs Mahdi Ghamkhari and Hamed Mohsenian-Rad Department of Electrical Engineering University of California at Riverside,
Profit Maximization and Power Management of Green Data Centers Supporting Multiple SLAs Mahdi Ghamkhari and Hamed Mohsenian-Rad Department of Electrical Engineering University of California at Riverside,
